AWS Certified Solutions Architect - Associate (SAA-C03) - Course Curriculum
INTRODUCTION & SCENARIO
Public Introduction (4:04)
Finding and Using the Course Resources (14:31)
Site tools and features (8:36)
AWS Exams (17:32)
Scenario - Animals4life (13:28)
Connect with other students and your instructor (3:10)
SHARED LESSONS [] etc
COURSE FUNDAMENTALS AND AWS ACCOUNTS
AWS Accounts - The basics (11:33)
[DEMO] ACCOUNTS - STEP1 - Creating GENERAL AWS Account (14:44)
Multi-factor Authentication (MFA) (8:25)
[DEMO] ACCOUNTS - STEP2 - Securing GENERAL AWS Account (9:44)
[DEMO] ACCOUNTS - STEP3 - Creating a Budget (6:46)
[DO_IT_YOURSELF] Creating the Production Account (4:59)
Identity and Access Management (IAM) Basics (13:01)
[DEMO] ACCOUNTS - STEP4 - Adding IAMADMIN to GENERAL Account (12:36)
[DEMO] ACCOUNTS - STEP4 - Adding IAMADMIN to PRODUCTION Account (10:17)
IAM Access Keys (7:10)
[DEMO] Creating Access keys and setting up AWS CLI v2 tools (17:43)
NETWORKING AND TECHNICAL FUNDAMENTALS
OSI 7-Layer Networking Model
OSI Model Introduction (4:46)
Layer 1 - Physical (10:00)
Layer 2 - DataLink - PART1 (8:47)
Layer 2 - DataLink - PART2 (14:24)
Layer 3 - Network - PART1 (12:06)
Layer 3 - Network - PART2 (19:13)
Layer 3 - Network - PART3 (15:15)
Layer 4&5 - Transport & Session - PART1 (15:39)
Layer 4&5 - Transport & Session - PART2 (13:54)
Other Networking (MORE COMING SOON)
Network Address Translation (NAT) - PART1 (11:00)
Network Address Translation (NAT) - PART2 (9:38)
IP Address Space & Subnetting - PART1 (14:37)
IP Address Space & Subnetting - PART2 (10:32)
Distributed Denial of Service (DDOS) Attacks (14:35)
VLANs, TRUNKS & QinQ (16:14)
Decimal to Binary Conversion (IP Addressing) (17:12)
SSL & TLS (11:19)
Border Gateway Protocol (BGP) 101 (17:03)
Stateful vs Stateless Firewalls (14:04)
JumboFrames (4:35)
Layer 7 Firewalls (7:44)
IP Sec VPN Fundamentals (14:48)
Fibre Optic Cable 101 (11:21)
Security (MORE COMING SOON)
Encryption 101 - PART1 (13:56)
Encryption 101 - PART2 (6:42)
Envelope Encryption (8:06)
Hardware Security Modules (HSMs) (6:40)
Hash Functions & Hashing (13:19)
Digital Signatures (9:26)
DNS & DNSSEC
DNS #1 - What does DNS do (2:56)
DNS #2 - Why does DNS need a complex architecture (13:19)
DNS #3 - How DNS actually works … walking the tree (8:46)
DNS #4 - What happens when a domain is registered? (4:27)
DNSSEC #1 - Why do we need DNSSEC (11:08)
DNSSEC #2 - How DNSSEC Works within a Zone (17:34)
DNSSEC #3 - DNSSEC Chain of Trust (8:16)
DNSSEC #4 - DNSSEC Root Signing Ceremony (7:53)
Containers & Virtualization (MORE COMING SOON)
Kubernetes 101 (11:27)
Backups & DR (MORE COMING SOON)
Recovery Point Objective (RPO) & Recovery Time Objective (RTO) (16:54)
Data Formats & Configuration Formats (MORE COMING SOON)
YAML aint markup language (YAML) 101 (6:12)
Javascript Object Notation (JSON) 101 (4:25)
CLOUD COMPUTING FUNDAMENTALS
What is Cloud Computing? (13:30)
Public vs Private vs Multi vs Hybrid Cloud .. (8:38)
Cloud Service Models (IAAS, PAAS, SAAS) (10:25)
AWS FUNDAMENTALS
AWS Public vs Private Services (7:04)
AWS Global Infrastructure (14:53)
AWS Default Virtual Private Cloud (VPC) (15:19)
Elastic Compute Cloud (EC2) Basics (14:46)
[DEMO] My First EC2 Instance - PART1 (10:58)
[DEMO] My First EC2 Instance - PART2 (9:40)
Simple Storage Service (S3) Basics (15:48)
[DEMO] My First S3 Bucket (18:34)
CloudFormation (CFN) Basics (12:28)
[DEMO] Simple Automation With CloudFormation (CFN) (15:52)
CloudWatch (CW) Basics (13:45)
[Demo] Simple Monitoring with Cloudwatch (15:31)
Shared Responsibility Model (6:20)
High-Availability vs Fault-Tolerance vs Disaster Recovery (17:21)
Route53 (R53) Fundamentals (6:29)
[DEMO] Registering a Domain with route53 (9:49)
DNS Record Types (13:25)
Fundamentals Section Quiz
IAM, ACCOUNTS AND AWS ORGANIZATIONS
IAM Identity Policies (15:52)
IAM Users and ARNs (13:49)
[DEMO] Simple Identity Permissions in AWS (16:06)
IAM Groups (7:48)
[DEMO] Permissions control using IAM Groups (9:24)
IAM Roles - The Tech (8:13)
When to use IAM Roles (15:27)
Service-linked Roles & PassRole (5:16)
AWS Organizations (12:56)
[DEMO] AWS Organizations (19:48)
Service Control Policies (SCPs) (12:44)
[DEMO] Using Service Control Policies (16:45)
CloudWatch Logs (7:16)
CloudTrail (11:40)
[DEMO] Implementing an Organizational Trail (18:23)
AWS Control Tower 101 (15:42)
IAM & Orgs Section Quiz
SIMPLE STORAGE SERVICE (S3)
S3 Security (Resource Policies & ACLs) (18:19)
S3 Static Hosting (10:36)
[Demo] Creating a static website with S3 (17:55)
Object Versioning & MFA Delete (7:41)
[DEMO] - S3 Versioning (15:45)
S3 Performance Optimization (11:42)
[DEMO] - S3 Performance (5:06)
Key Management Service (KMS) (18:38)
[DEMO] KMS - Encrypting the battle-plans with KMS (12:43)
S3 Object Encryption CSE/SSE (23:31)
[DEMO] Object Encryption and Role Separation (14:50)
S3 Bucket Keys (5:59)
S3 Object Storage Classes - PART1 (9:23)
S3 Object Storage Classes - PART2 (11:41)
S3 Lifecycle Configuration (8:13)
S3 Replication (13:59)
[DEMO] Cross-Region Replication of an S3 Static Website (19:52)
S3 PreSigned URLs (11:11)
[DEMO] Creating and using PresignedURLs (18:23)
S3 Select and Glacier Select (5:32)
S3 Events (4:32)
S3 Access Logs (3:05)
S3 Object Lock (9:52)
S3 Access Points (5:52)
[DEMO] Multi-Region Access Points (MRAP) (20:25)
S3 Section Quiz
VIRTUAL PRIVATE CLOUD (VPC) BASICS
VPC Sizing and Structure - PART1 (11:48)
VPC Sizing and Structure - PART2 (11:16)
Custom VPCs - PART1 - THEORY (10:10)
[DEMO] Custom VPCs - PART2 - DEMO (5:40)
VPC Subnets (10:42)
[DEMO] Implement multi-tier VPC subnets (15:24)
VPC Routing, Internet Gateway & Bastion Hosts (17:35)
[DEMO] Configuring A4l public subnets and Jump-box - PART1 (13:45)
[DEMO] Configuring A4l public subnets and Jump-box - PART2 (11:45)
Stateful vs Stateless Firewalls (14:04)
Network Access Control Lists (NACLs) (12:38)
Security Groups (SG) (11:48)
Network Address Translation (NAT) & NAT Gateway - PART1 (13:43)
Network Address Translation (NAT) & NAT Gateway - PART2 (11:08)
[DEMO] Implementing private internet access using NAT Gateways (19:25)
VPC Basics Section Quiz
ELASTIC COMPUTE CLOUD (EC2) BASICS
Virtualization 101 (12:27)
EC2 Architecture and Resilience (12:36)
EC2 Instance Types - PART1 (11:52)
EC2 Instance Types - PART2 (8:13)
[DEMO] EC2 SSH vs EC2 Instance Connect (17:06)
Storage Refresher (14:16)
Elastic Block Store (EBS) Service Architecture (8:43)
EBS Volume Types - General Purpose (9:23)
EBS Volume Types - Provisioned IOPS (6:15)
EBS Volume Types - HDD-Based (4:32)
Instance Store Volumes - Architecture (9:00)
Choosing between the EC2 Instance Store and EBS (8:49)
Snapshots, Restore & Fast Snapshot Restore (FSR) (10:55)
[DEMO] EBS Volumes - PART1 (15:16)
[DEMO] EBS Volumes - PART2 (14:13)
[DEMO] EBS Volumes - PART3 (14:27)
EBS Encryption (8:22)
Network Interfaces, Instance IPs and DNS (15:58)
[DEMO] Manual Install of Wordpress on EC2 - PART1 (12:27)
[DEMO] Manual Install of Wordpress on EC2 - PART2 (12:36)
Amazon Machine Images (AMI) (13:58)
[DEMO] Creating an Animals4life AMI - PART1 (9:38)
[DEMO] Creating an Animals4life AMI - PART2 (10:57)
[DEMO] Copying & Sharing an AMI (8:35)
EC2 Purchase Options - PART1 (9:22)
EC2 Purchase Options - PART2 (11:56)
Reserved Instances - the rest (11:58)
Instance Status Checks & Auto Recovery (7:42)
[DEMO] Shutdown, Terminate & Termination Protection (5:40)
Horizontal & Vertical Scaling (11:23)
Instance Metadata [THEORY & DEMO] (15:46)
EC2 Basics Section Quiz
CONTAINERS & ECS
Introduction to Containers (17:13)
[DEMO] Creating ‘container of cats’ Docker Image (18:15)
ECS - Concepts (10:25)
ECS - Cluster Mode (13:09)
[DEMO] - Deploying ‘container of cats’ using Fargate (13:13)
Elastic Container Registry (ECR) (4:14)
Kubernetes 101 (11:27)
Elastic Kubernetes Service (EKS) 101 (6:14)
Containers Section Quiz
ADVANCED EC2
Bootstrapping EC2 using User Data (10:25)
[DEMO] Bootstrapping Wordpress Installation - PART1 (15:00)
[DEMO] Bootstrapping Wordpress Installation - PART2 (6:45)
Enhanced Bootstrapping with CFN-INIT (11:52)
[DEMO] CFN-INIT and CFN Creation Policies (12:29)
EC2 Instance Roles & Profile (4:18)
[DEMO] Using EC2 Instance Roles (13:31)
SSM Parameter Store (6:16)
[DEMO] Parameter Store (16:11)
System and Application Logging on EC2 (6:15)
[DEMO] Logging and Metrics with CloudWatch Agent-PART1 (11:51)
[DEMO] Logging and Metrics with CloudWatch Agent-PART2 (8:08)
EC2 Placement Groups (14:29)
Dedicated Hosts (8:56)
Enhanced Networking & EBS Optimized (6:57)
Advanced EC2 Section Quiz
ROUTE 53 - GLOBAL DNS
R53 Public Hosted Zones (6:28)
R53 Private Hosted Zones (5:10)
CNAME vs R53 Alias (5:19)
Simple Routing (2:17)
R53 Health Checks (12:41)
Failover Routing (1:53)
[DEMO] Using R53 and Failover Routing-PART1 (16:41)
[DEMO] Using R53 and Failover Routing-PART2 (6:28)
Multi Value Routing (2:32)
Weighted Routing (3:24)
Latency Routing (2:44)
Geo-location Routing (5:02)
Geo-proximity (4:50)
R53 Interoperability (11:50)
Implementing DNS-SEC using Route53 (17:43)
Route53 Section Quiz
RELATIONAL DATABASE SERVICE (RDS)
Database Refresher & MODELS - PART1 (8:51)
Database Refresher & MODELS - PART2 (14:45)
ACID vs BASE (11:02)
Databases on EC2 (13:08)
[DEMO] Splitting Wordpress Monolith => APP & DB (18:01)
Relational Database Service (RDS) Architecture (11:39)
[DEMO] Migrating EC2 DB into RDS - PART1 (18:20)
[DEMO] Migrating EC2 DB into RDS - PART2 (12:58)
Relational Database Service (RDS) MultiAZ - Instance and Cluster (11:54)
RDS Automatic Backup, RDS Snapshots and Restore (8:52)
RDS Read-Replicas (6:36)
[DEMO] MultiAZ & Snapshot Restore with RDS - PART1 (14:05)
[DEMO] MultiAZ & Snapshot Restore with RDS - PART2 (12:07)
RDS Data Security (7:03)
RDS Custom (5:22)
Aurora Architecture (13:44)
Aurora Serverless (9:52)
[DEMO] Migrating to Aurora Serverless [DON’T DO THIS DEMO, IT WON’T WORK, UPDATING to SERVERLESSv2] (14:47)
Aurora Global Database (5:08)
Multi-master writes (7:51)
Relational Database Service (RDS) - RDS Proxy (9:47)
Database Migration Service (DMS) (11:03)
RDS Section Quiz
NETWORK STORAGE & DATA LIFECYCLE
EFS Architecture (9:05)
[DEMO] Implementing EFS - PART1 (8:51)
[DEMO] Implementing EFS - PART2 (11:32)
[DEMO] Using EFS with Wordpress (16:00)
AWS Backup (6:36)
Network Storage Section Quiz
HA & SCALING
Regional and Global AWS Architecture (10:42)
Evolution of the Elastic Load Balancer (4:10)
Elastic Load Balancer Architecture - PART1 (10:18)
Elastic Load Balancer Architecture - PART2 (12:32)
Application Load balancing (ALB) vs Network Load Balancing (NLB) (16:20)
Launch Configuration and Templates (4:00)
Auto-Scaling Groups (16:01)
ASG Scaling Policies (10:23)
ASG Lifecycle Hooks (4:41)
ASG HealthCheck Comparison - EC2 vs ELB (3:38)
SSL Offload & Session Stickiness (12:11)
[DEMO] Seeing Session Stickiness in Action (12:57)
[ADVANCED_DEMO] Architecture Evolution - STAGE1 - PART1 (14:24)
[ADVANCED_DEMO] Architecture Evolution - STAGE1 - PART2 (10:43)
[ADVANCED_DEMO] Architecture Evolution - STAGE2 (12:58)
[ADVANCED_DEMO] Architecture Evolution - STAGE3 (19:30)
[ADVANCED_DEMO] Architecture Evolution - STAGE4 (18:04)
[ADVANCED_DEMO] Architecture Evolution - STAGE 5 - PART1 (11:31)
[ADVANCED_DEMO] Architecture Evolution - STAGE 5 - PART2 (14:56)
[ADVANCED_DEMO] Architecture Evolution - STAGE6 (5:48)
Gateway Load Balancer (13:40)
HA and Scaling Section Quiz
SERVERLESS AND APPLICATION SERVICES
Architecture Deep Dive - PART1 (8:52)
Architecture Deep Dive - PART2 (13:09)
AWS Lambda - PART1 (11:25)
AWS Lambda - PART2 (13:59)
AWS Lambda - PART3 (17:03)
CloudWatchEvents and EventBridge (6:54)
[DEMO] Automated EC2 Control using Lambda and Events - PART1 (13:44)
[DEMO] Automated EC2 Control using Lambda and Events - PART2 (18:49)
Serverless Architecture (12:56)
Simple Notification Service (7:49)
Step Functions (16:09)
API Gateway 101 (16:27)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART1 (5:01)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART2 (8:24)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART3 (12:31)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART4 (13:31)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART5 (12:55)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART6 (2:39)
Simple Queue Service (15:30)
SQS Standard vs FIFO Queues (3:29)
SQS Delay Queues (4:38)
SQS Dead-Letter Queues (4:17)
Kinesis Data Streams (7:52)
Kinesis Data Firehose (9:11)
Kinesis Data Analytics (8:51)
Kinesis Video Streams (5:09)
Amazon Cognito - User and Identity Pools (14:44)
AWS Glue 101 (6:23)
Amazon MQ 101 (8:15)
Amazon AppFlow (3:30)
Serverless and App Services Section Quiz
GLOBAL CONTENT DELIVERY AND OPTIMIZATION
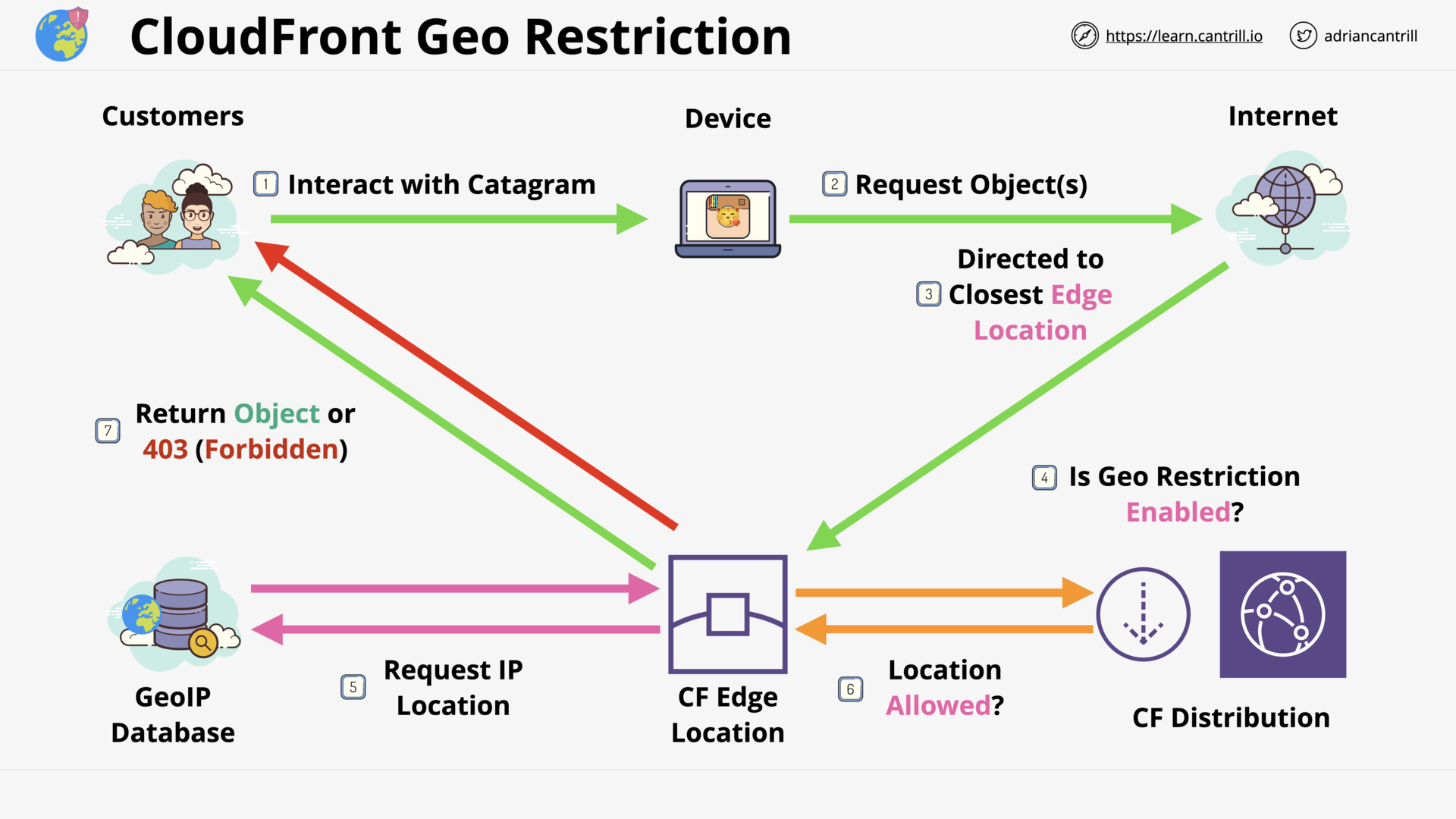
Cloudfront Architecture (14:56)
CloudFront (CF) - Behaviors (9:21)
CloudFront - TTL and Invalidations (13:48)
ACM (11:21)
Cloudfront and SSL/TLS (14:59)
CloudFront (CF) - Origin Types & Origin Architecture (10:20)
[DEMO] CloudFront (CF) - Adding a CDN to a static Website-PART1 (16:23)
[DEMO] CloudFront (CF) - Adding a CDN to a static Website-PART2 (12:24)
[DEMO] CloudFront (CF) - Adding an Alternate CNAME and SSL (11:12)
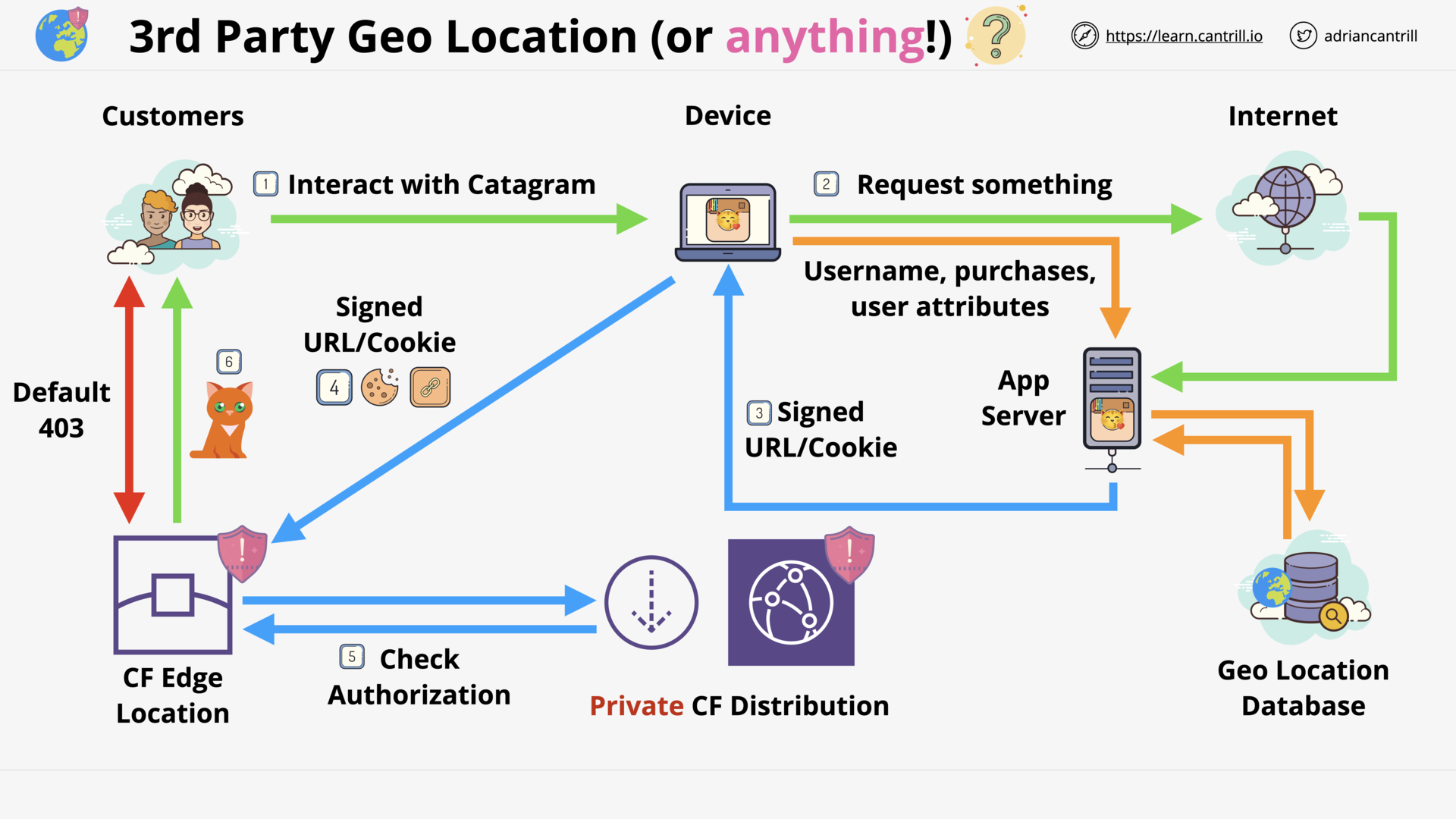
CloudFront - Security - OAI & Custom Origins (8:50)
CloudFront - Private Distribution & Behaviors (7:49)
[DEMO] CloudFront (CF) - Using Origin Access Control (OAC) (new version of OAI) (11:21)
Lambda@Edge (8:03)
Global Accelerator (10:29)
CDN and Optimization Section Quiz
ADVANCED VPC NETWORKING
VPC Flow Logs (9:56)
Egress-Only Internet gateway (6:46)
VPC Endpoints (Gateway) (11:14)
VPC Endpoints (Interface) (11:26)
[DEMO] VPC Endpoints - Interface - PART1 (11:59)
[DEMO] VPC Endpoints - Gateway - PART2 (9:59)
[DEMO] Egress-Only Internet Gateway - PART3 (7:57)
VPC Peering (9:04)
[DEMO] VPC Peering (22:38)
Advanced VPC Section Quiz
HYBRID ENVIRONMENTS AND MIGRATION
Border Gateway Protocol 101 (17:29)
IPSec VPN Fundamentals (14:54)
AWS Site-to-Site VPN (18:05)
[DEMO] Simple Site2Site VPN - STAGE0 - SETUP (4:52)
[DEMO] Simple Site2Site VPN - STAGE1 - AWS VPN (10:01)
[DEMO] Simple Site2Site VPN - STAGE2 - on-prep pfSense Config (17:09)
[DEMO] Simple Site2Site VPN - STAGE3 - Routing & Security (10:29)
[DEMO] Simple Site2Site VPN - STAGE4 - Testing (5:42)
[DEMO] Simple Site2Site VPN - STAGE5 - Cleanup (1:50)
Direct Connect (DX) Concepts (9:37)
Direct Connect (DX) Resilience (13:50)
Direct Connect (DX) - Public VIF + VPN (Encryption) (6:43)
Transit Gateway (10:26)
Storage Gateway - Volume (14:15)
Storage Gateway - Tape (VTL) (12:11)
Storage Gateway - File (12:15)
Snowball / Edge / Snowmobile [NEW VERSION COMING SOON] (10:47)
Directory Service (15:50)
DataSync (9:27)
FSx for Windows Servers (11:32)
FSx For Lustre (13:57)
AWS Transfer Family (10:24)
Hybrid and Migration Section Quiz
SECURITY, DEPLOYMENT & OPERATIONS
AWS Secrets Manager (7:44)
Application Layer (L7) Firewall (7:44)
Web Application Firewall (WAF), WebACLs, Rule Groups and Rules (19:18)
AWS Shield (9:47)
CloudHSM (14:36)
AWS Config (6:14)
Amazon Macie (12:04)
[DEMO] Amazon Macie (15:35)
Amazon Inspector (6:28)
Amazon Guard Duty (4:14)
Section Quiz
INFRASTRUCTURE AS CODE (CLOUDFORMATION)
CloudFormation Physical & Logical Resources (7:30)
[DEMO] Simple Non Portable Template - PART1 (10:28)
[DEMO] Simple Non Portable Template - PART2 (11:28)
CloudFormation Template and Pseudo Parameters (6:53)
CloudFormation Intrinsic Functions (14:28)
CloudFormation Mappings (4:30)
CloudFormation Outputs (3:37)
[DEMO] Template v2 - Portable (13:34)
CloudFormation Conditions (7:24)
CloudFormation DependsOn (7:14)
CloudFormation Wait Conditions & cfn-signal (11:52)
CloudFormation Nested Stacks (13:55)
CloudFormation Cross-Stack References (10:05)
CloudFormation Stack Sets (9:12)
CloudFormation Deletion Policy (5:24)
CloudFormation Stack Roles (6:47)
CloudFormation Init (CFN-INIT) (8:48)
CloudFormation cfn-hup (4:13)
[DEMO] wait conditions, cfn-signal, cfn-init and cfn-hup - PART1 (12:51)
[DEMO] wait conditions, cfn-signal, cfn-init and cfn-hup - PART2 (14:42)
CloudFormation ChangeSets [NEW VERSION COMING SOON] (11:03)
CloudFormation Custom Resources (11:03)
[DEMO] CloudFormation Custom Resources-PART1 (9:12)
[DEMO] CloudFormation Custom Resources-PART2 (13:27)
NoSQL DATABASES & DYNAMODB
DynamoDB - Architecture (10:49)
DynamoDB - Operations, Consistency and Performance-PART1 (13:06)
DynamoDB - Operations, Consistency and Performance-PART2 (11:24)
DynamoDB Local and Global Secondary Indexes (12:35)
DynamoDB - Streams & Lambda Triggers (9:10)
DynamoDB - Global Tables (5:09)
DynamoDB - Accelerator (DAX) (10:58)
DynamoDB - TTL (4:49)
Amazon Athena (8:19)
[DEMO] Athena Demo - PART1 (13:31)
[DEMO] Athena Demo - PART2 (11:37)
Elasticache (12:51)
Redshift Architecture (11:32)
Redshift DR and Resilience (3:40)
NoSQL Section Quiz
MACHINE LEARNING 101
Amazon Comprehend (7:28)
Amazon Kendra (5:00)
Amazon Lex (5:51)
Amazon Polly (4:04)
Amazon Rekognition (4:18)
Amazon Textract (8:42)
Amazon Transcribe (4:55)
Amazon Translate (4:32)
Amazon Forecast 101 (4:04)
Amazon Fraud Detector (3:34)
Amazon SageMaker (5:39)
OTHER SERVICES & FEATURES
AWS Local Zones (8:52)
EXAM
General AWS Exam Technique - 3 Phase Approach (8:56)
General AWS Question Technique - PART1 (14:12)
General AWS Question Technique - PART2 (9:01)
Practice Exam #1
Practice Exam #2
FINISHING UP
Thanks! and a favour (3:15)
Notes
AWS PRODUCTS (279)
Analytics (18)
| Amazon AppFlow | No-code integration for SaaS apps and AWS services |
| Amazon Athena | Query data in Amazon S3 using SQL |
| AWS Clean Rooms | Collaborate and analyze collective datasets without sharing raw data |
| Amazon CloudSearch | Managed search service |
| AWS Data Exchange | Find, subscribe to, and use third-party data in the cloud |
| AWS Data Pipeline | Orchestration service for periodic, data-driven workflows |
| Amazon DataZone | Unlock data across organizational boundaries with built-in governance |
| AWS Entity Resolution | Link records stored across multiple applications, channels, and data stores |
| Amazon EMR | Hosted Hadoop framework |
| Amazon FinSpace | Store, catalog, prepare, and analyze financial industry data |
| AWS Glue | Simple, scalable, and serverless data integration |
| Amazon Kinesis | Analyze real-time video and data streams |
| AWS Lake Formation | Build a secure data lake in days |
| Amazon Managed Service for Apache Flink | Process and analyze streaming data using Apache Flink |
| Amazon MSK | Fully managed Apache Kafka service |
| Amazon OpenSearch Service | Deploy, operate, and scale OpenSearch clusters in the AWS Cloud |
| Amazon QuickSight | Fast business analytics service |
| Amazon Redshift | Fast, simple, cost-effective data warehouse service |
Application Integration (7)
| Amazon EventBridge | Serverless event bus for SaaS apps and AWS services |
| Amazon MQ | Managed message broker service |
| Amazon MWAA | Managed orchestration service for Apache Airflow |
| Amazon SNS | Pub/sub, SMS, email, and mobile push notifications |
| Amazon SQS | Managed message queues |
| AWS Step Functions | Coordination for distributed applications |
| Amazon SWF | Build applications that coordinate work across distributed components |
AWS Management Console (3)
| AWS Console Mobile Application | View and manage resources to support incident response while on the go |
| AWS Management Console | Web-based user interface comprising multiple AWS service consoles |
| AWS Sign-In | Find help signing in and out of your account |
Blockchain (2)
| AWS Blockchain Templates | Quickly create and deploy open-source blockchain frameworks on AWS |
| Amazon Managed Blockchain | Create and manage scalable blockchain networks |
Business Applications (11)
| AWS AppFabric | Aggregate and analyze data across SaaS applications |
| Amazon Chime | Frustration-free meetings, video calls, and chat |
| Amazon Chime SDK | Real-time messaging, audio, video, and screen sharing |
| Amazon Connect | Omnichannel cloud contact center |
| Amazon Honeycode | Build mobile and web apps without programming |
| Amazon Pinpoint | Multichannel marketing communications |
| Amazon SES | High-scale inbound and outbound email |
| AWS Supply Chain | Reduce risks and lower costs with ML-powered supply chain application |
| AWS Wickr | Protect enterprise communications with end-to-end encryption |
| Amazon WorkDocs | Secure enterprise document storage and sharing |
| Amazon WorkMail | Secure email and calendaring |
Cloud Financial Management (4)
| AWS Application Cost Profiler | Provides granular cost insights for your multi-tenant applications |
| AWS Billing and Cost Management | Find features that help you pay your bills and optimize your costs |
| AWS Pricing Calculator | Create cost estimates that match your AWS use case |
| Savings Plans | Save on compute usage with flexible pricing |
Compute (15)
| AWS App Runner | Production web applications at scale made easy for developers |
| AWS Batch | Run batch jobs at any scale |
| Amazon EC2 | Create and run virtual servers in the cloud |
| Amazon EC2 Image Builder | Automate lifecycle management of “golden” server images |
| AWS Elastic Beanstalk | Run and manage web apps |
| AWS End-of-Support Migration Program (EMP) for Windows Server | Migrate legacy apps to AWS supported versions without code refactoring |
| AWS Lambda | Run code without thinking about servers |
| Amazon Lightsail | Launch and manage virtual private servers |
| AWS Local Zones | Run latency sensitive applications closer to end users |
| AWS Outposts | Run AWS infrastructure on-premises |
| AWS ParallelCluster | Deploy and manage high performance computing clusters in the AWS Cloud |
| AWS SAM | Build serverless applications on AWS |
| AWS Serverless Application Repository | Discover, deploy, and publish serverless applications |
| AWS SimSpace Weaver | Build and run large-scale spatial simulations in the AWS Cloud |
| AWS Wavelength | Deliver ultra-low latency applications for 5G devices |
Containers (5)
| AWS App2Container | Containerize and migrate existing applications |
| Amazon ECR | Easily store, manage, and deploy container images |
| Amazon ECS | Highly secure, reliable, and scalable way to run containers |
| Amazon EKS | Run Kubernetes on AWS without operating your own Kubernetes clusters |
| Red Hat OpenShift Service on AWS | Managed OpenShift in the cloud |
Cryptography & PKI (8)
| AWS Certificate Manager | Provision, manage, and deploy SSL/TLS certificates |
| AWS CloudHSM | Hardware-based key storage for regulatory compliance |
| AWS Crypto Tools | Helping you do cryptography right, even without special expertise |
| AWS Cryptographic Services Overview | Find crypto services to help protect your data |
| AWS KMS | Managed creation and control of encryption keys |
| AWS PKI Services Overview | Find multiple services to help protect your data at rest or in transit |
| AWS Private Certificate Authority | Create private certificates to identify resources and protect data |
| AWS Signer | Validate AWS Lambda and IoT device code against a digital signature |
Customer Enablement Services (5)
| AWS IQ | Find AWS Certified third-party experts for on-demand project work |
| AWS Incident Detection and Response | Proactive monitoring and incident management for production workloads |
| AWS Managed Services | Infrastructure operations management for AWS |
| AWS Professional Services | Get help executing your enterprise cloud computing initiatives |
| AWS Training and Certification | Explore AWS learning opportunities |
Database (10)
| Amazon Aurora | High performance managed relational database engine |
| Amazon DocumentDB | Fully managed document database |
| Amazon DynamoDB | Managed NoSQL database |
| Amazon ElastiCache | In-memory caching service |
| Amazon Keyspaces (for Apache Cassandra) | Managed Cassandra-compatible database |
| Amazon MemoryDB for Redis | Redis-compatible, durable, in-memory database service |
| Amazon Neptune | Fully managed graph database service |
| Amazon QLDB | Fully managed ledger database |
| Amazon RDS | Set up, operate, and scale a relational database in the cloud |
| Amazon Timestream | Fully managed time series database |
Developer Tools (18)
| AWS Application Composer | Visually design and build serverless applications quickly |
| AWS Cloud Control API | Manage AWS and third-party cloud infrastructure with consistent APIs |
| AWS Cloud9 | Write, run, and debug code on a cloud IDE |
| AWS CloudShell | Command line access to AWS resources and tools directly from a browser |
| AWS CodeArtifact | Artifact management for software development |
| AWS CodeBuild | Build and test code |
| Amazon CodeCatalyst | Unified software development service to develop and deliver on AWS |
| AWS CodeCommit | Store code in private Git repositories |
| AWS CodeDeploy | Automate code deployments |
| AWS CodePipeline | Release software using continuous delivery |
| AWS CodeStar | Develop and deploy AWS applications |
| Amazon CodeWhisperer | Build applications faster with the ML-powered coding companion |
| AWS Fault Injection Simulator | Improve resiliency and performance with controlled experiments |
| AWS Microservice Extractor for .NET | Reduce time and effort to convert large applications to microservices |
| Porting Assistant for .NET | Port Microsoft .NET Framework applications to .NET Core |
| SDKs and Tools Reference Guide | Find information applicable to multiple SDKs and tools |
| Toolkit for .NET Refactoring | Reduce time and effort to refactor legacy .NET apps for AWS Cloud |
| AWS X-Ray | Analyze and debug your applications |
End User Computing (6)
| AppStream 2.0 | Stream desktop applications securely to a browser |
| NICE DCV | Connect securely to graphic-intensive 3D apps on remote servers |
| Amazon WAM | Deploy and manage applications for Amazon WorkSpaces |
| Amazon WorkSpaces | Virtual desktops in the cloud |
| Amazon WorkSpaces Core | Virtual desktop infrastructure that works with third-party solutions |
| Amazon WorkSpaces Web | Provide secure access to internal websites and SaaS applications |
Front-End Web & Mobile (8)
| AWS Amplify | Build, deploy, host, and manage scalable web and mobile apps |
| AWS Amplify (AWS Mobile SDK for Android) | Build native Android applications powered by AWS |
| AWS Amplify iOS (AWS Mobile SDK for iOS) | Build native iOS applications powered by AWS |
| AWS AppSync | Accelerate app development with fully-managed, scalable GraphQL APIs |
| AWS Device Farm | Test Android, iOS, and web apps on real devices in the AWS Cloud |
| Amazon Location Service | Securely and easily add location data to applications |
| AWS Mobile SDK for Unity | Find .NET classes that enable games written with Unity to utilize AWS |
| Amazon Silk | Create a faster, more responsive mobile browsing experience |
Game Development (4)
| AWS GameKit | Build game backend services with AWS while working in a game engine |
| Amazon GameLift | Simple, fast, cost-effective dedicated game server hosting |
| Amazon GameSparks | Multi-service backend for game developers |
| Amazon Lumberyard | A free cross-platform 3D game engine (binaries no longer offered) |
General Reference (6)
| AWS Glossary | Find definitions for AWS terms |
| AWS Security Credentials | Learn how to specify AWS security credentials |
| AWS Service Endpoints | Connect programmatically to an AWS service using endpoints |
| Service Quotas reference | View the AWS workload quotas for AWS services |
| Tagging AWS Resources | Assign metadata to your AWS resources in the form of tags |
| AWS Support | Learn about the components and features that AWS Support provides |
Internet of Things (IoT) (13)
| FreeRTOS | Real-time operating system for microcontrollers |
| AWS IoT 1-Click | One click creation of an AWS Lambda trigger |
| AWS IoT Analytics | Analytics for IoT devices |
| AWS IoT Core | Connect devices to the cloud |
| AWS IoT Device Defender | Security management for IoT devices |
| AWS IoT Device Management | Onboard, organize, and remotely manage IoT devices |
| AWS IoT Events | IoT event detection and response |
| AWS IoT ExpressLink | Quickly and easily develop secure IoT devices |
| AWS IoT FleetWise | Collect, transform, and transfer vehicle data to the cloud |
| AWS IoT Greengrass | Local compute, messaging, and sync for devices |
| AWS IoT RoboRunner | Build applications that help fleets of robots work together seamlessly |
| AWS IoT SiteWise | IoT data collector and interpreter |
| AWS IoT TwinMaker | Optimize operations by creating digital twins of real-world systems |
Machine Learning (34)
| Amazon A2I | Easily implement human review of ML predictions |
| Apache MXNet on AWS | Scalable, open-source deep learning framework |
| Amazon Bedrock | Access best-in-class foundation models to build generative AI applications |
| Amazon CodeGuru | Find your most expensive lines of code |
| Amazon CodeWhisperer | Build applications faster with the ML-powered coding companion |
| Amazon Comprehend | Discover insights and relationships in text |
| Amazon Comprehend Medical | Detect and return useful information in unstructured clinical text |
| AWS Deep Learning AMI | Deep learning on Amazon EC2 |
| AWS Deep Learning Containers | Docker images for deep learning |
| AWS DeepComposer | ML enabled musical keyboard |
| AWS DeepLens | Deep learning enabled video camera |
| AWS DeepRacer | Autonomous 1/18th scale race car, driven by ML |
| Amazon DevOps Guru | Improve application availability with ML-powered cloud operations |
| Amazon Elastic Inference | Deep learning inference acceleration |
| Amazon Forecast | Increase forecast accuracy using machine learning |
| Amazon Fraud Detector | Detect more online fraud faster |
| AWS HealthImaging | Manage medical imaging data |
| AWS HealthLake | Securely store, transform, query, and analyze health data in minutes |
| AWS HealthOmics | Transform omics data into insights |
| Amazon Kendra | Reinvent enterprise search with ML |
| Amazon Lex | Build voice and text chatbots |
| Amazon Lookout for Equipment | Detect abnormal equipment behavior by analyzing sensor data |
| Amazon Lookout for Metrics | Automatically detect anomalies in metrics and identify the root cause |
| Amazon Lookout for Vision | Spot product defects and automate quality inspection |
| Amazon Machine Learning | Learn about Amazon machine learning services |
| Amazon Monitron | Reduce unplanned equipment downtime with predictive maintenance and ML |
| AWS Panorama | Improve your operations with computer vision at the edge |
| Amazon Personalize | Build real-time recommendations into your applications |
| Amazon Polly | Turn text into life-like speech |
| Amazon Rekognition | Analyze image and video |
| Amazon SageMaker | Build, train, and deploy machine learning models at scale |
| Amazon Textract | Extract text and data from documents |
| Amazon Transcribe | Automatic speech recognition |
| Amazon Translate | Natural and fluent language translation |
Management & Governance (35)
| AWS AppConfig | Quickly deploy application configurations to applications of any size |
| Auto Scaling | Scale multiple resources to meet demand |
| AWS Account Management | Manage your AWS accounts as a group |
| AWS Chatbot | ChatOps for AWS |
| AWS CloudFormation | Create and manage resources with templates |
| AWS CloudTrail | Track and monitor activities by users, roles, or AWS services |
| Amazon CloudWatch | Monitor resources and applications |
| AWS CLI | Command line interface tool to manage AWS services |
| AWS Compute Optimizer | Identify optimal AWS compute resources |
| AWS Config | Track and evaluate configuration changes |
| AWS Console Mobile Application | View and manage resources to support incident response while on-the-go |
| AWS Control Tower | Set up and govern a secure, compliant multi-account environment |
| Amazon Data Lifecycle Manager | Automate management of Amazon EBS snapshots and Amazon EBS-backed AMIs |
| AWS Health | Find information about events that can affect your AWS resources |
| AWS Launch Wizard | Easily size, configure, and deploy third-party applications on AWS |
| AWS License Manager | Track and manage software licenses across multiple AWS Regions |
| Amazon Managed Grafana | Visualize and analyze your operational data at scale |
| Amazon Managed Service for Prometheus | Highly available, secure, and managed monitoring for your containers |
| AWS Management Console | Web-based user interface comprising multiple AWS service consoles |
| AWS OpsWorks | Automate operations with Chef and Puppet |
| AWS Organizations | Central governance and management across AWS accounts |
| AWS Proton | Automate management for container and serverless deployments |
| AWS Resilience Hub | Prepare and protect your applications from disruptions |
| AWS Resource Explorer | Search for and discover relevant resources across AWS |
| AWS Resource Groups | See your resources across the AWS Regions in your AWS account |
| AWS Service Catalog | Create and use standardized products |
| AWS Service Management Connector | Provision, manage, and operate AWS resources within ITSM tools |
| Service Quotas | View and manage your AWS workload quotas easily and at scale |
| AWS Systems Manager | Gain operational insights and take action |
| Tag Editor | Add, edit, or delete tags on multiple AWS resources |
| AWS Telco Network Builder | Automate the deployment and management of your telco networks on AWS |
| AWS Tools for PowerShell | Script operations on AWS resources from the PowerShell command line |
| AWS Trusted Advisor | Optimize performance and security |
| AWS User Notifications | Unifies the notification experience across AWS services |
| AWS Well-Architected Tool | Review and improve your workloads |
Marketplace (1)
| AWS Marketplace | Buy or sell software that runs on AWS |
Media Services (11)
| AWS Cloud Digital Interface SDK | Migrate timing-critical uncompressed video workflows to the cloud |
| Amazon Elastic Transcoder | Easy-to-use scalable media transcoding |
| AWS Elemental MediaConnect | Reliable and secure live video transport |
| AWS Elemental MediaConvert | Convert file-based video content |
| AWS Elemental MediaLive | Convert live video content |
| AWS Elemental MediaPackage | Video origination and packaging |
| AWS Elemental MediaStore | Store and deliver video assets for live streaming media workflows |
| AWS Elemental MediaTailor | Video personalization and monetization |
| AWS Elemental On-Premises | Encode and package video assets with on-premises software |
| Amazon Interactive Video Service | Build engaging live stream experiences |
| Amazon Nimble Studio | Accelerate content creation in the cloud |
Migration & Transfer (8)
| AWS Application Discovery Service | Discover on-premises applications to streamline migration |
| AWS Application Migration Service | Automate application migration and modernization |
| AWS Database Migration Service | Migrate databases with minimal downtime |
| AWS DataSync | Simple, fast, online data transfer |
| AWS Mainframe Modernization | Migrate, modernize, operate, and run mainframe workloads |
| AWS Migration Hub | Track migrations from a single place |
| AWS Schema Conversion Tool | Convert source schema and most code to target-compatible format |
| AWS Transfer Family | Fully managed SFTP, FTPS, and FTP service |
Networking & Content Delivery (14)
| Amazon API Gateway | Build, deploy, and manage APIs |
| AWS App Mesh | Monitor and control microservices |
| Amazon CloudFront | Global content delivery network |
| AWS Cloud Map | Service discovery for cloud resources |
| AWS Direct Connect | Dedicated network connection to AWS |
| Elastic Load Balancing | Distribute incoming traffic across multiple targets |
| AWS Global Accelerator | Improve global application availability and performance |
| AWS Private 5G | Easily deploy, manage, and scale a private cellular network |
| Amazon Route 53 | Highly available and scalable Domain Name System (DNS) web service |
| Amazon Route 53 Application Recovery Controller | Move traffic for application disaster recovery |
| AWS Verified Access | Provide secure access to corporate applications without a VPN |
| Amazon VPC | Isolated cloud resources |
| Amazon VPC Lattice | Simplify service-to-service connectivity, security, and monitoring |
| AWS VPN | Securely access your network resources |
Quantum Computing (1)
| Amazon Braket | Accelerate quantum computing research |
Robotics (1)
| AWS RoboMaker | Develop, test, and deploy robotics applications |
Satellite (1)
| AWS Ground Station | Fully managed ground station as a service |
Security, Identity, & Compliance (23)
| AWS Artifact | On-demand access to AWS compliance reports |
| AWS Audit Manager | Audit your AWS usage to simplify how you assess risk and compliance |
| Amazon Cloud Directory | Store hundreds of millions of application-specific objects |
| Amazon Cognito | Identity management for your apps |
| Amazon Detective | Investigate potential security issues |
| AWS Directory Service | Set up and run Microsoft Active Directory with AWS services |
| AWS Firewall Manager | Deploy network security across your VPCs with just a few clicks |
| AWS GovCloud (US) | Move sensitive workloads into the cloud |
| Amazon GuardDuty | Managed threat detection service |
| AWS Identity and Access Management | Securely manage access to services and resources |
| AWS IAM Identity Center | Manage single sign-on access to AWS accounts and apps |
| Amazon Inspector | Automated and continual vulnerability management at scale |
| Amazon Macie | Discover and protect your sensitive data at scale |
| AWS Network Firewall | Deploy network security across your Amazon VPCs with just a few clicks |
| AWS Payment Cryptography | Fully managed payment cryptography service |
| AWS Resource Access Manager | Simple, secure service to share AWS resources |
| AWS Secrets Manager | Rotate, manage, and retrieve secrets |
| Security Documentation | Security documentation by category |
| AWS Security Hub | Unified security and compliance center |
| Amazon Security Lake | Automatically centralize your security data with a few clicks |
| AWS Shield | DDoS protection |
| Amazon Verified Permissions | Permissions management and authorization for custom applications |
| AWS WAF | Filter malicious web traffic |
Serverless (10)
| Amazon API Gateway | Build, deploy, and manage APIs |
| AWS AppSync | Accelerate app development with fully-managed, scalable GraphQL APIs |
| Amazon DynamoDB | Managed NoSQL database |
| Amazon EventBridge | Serverless event bus for SaaS apps and AWS services |
| AWS Fargate | Serverless compute for containers |
| AWS Lambda | Run code without thinking about servers |
| Amazon S3 | Object storage built to retrieve any amount of data from anywhere |
| Amazon SNS | Pub/sub, SMS, email, and mobile push notifications |
| AWS Step Functions | Coordinate components for distributed applications |
| Amazon SQS | Managed message queues |
Storage (9)
| AWS Backup | Centralized backup across AWS services |
| Amazon EBS | Amazon EC2 block storage volumes |
| Amazon EFS | Fully managed file system for Amazon EC2 |
| AWS Elastic Disaster Recovery | Scalable, cost-effective application recovery to AWS |
| Amazon FSx | Launch, run, and scale feature-rich and high-performing file systems |
| Amazon S3 | Object storage built to retrieve any amount of data from anywhere |
| Amazon S3 Glacier | Low-cost archive storage in the AWS Cloud |
| AWS Snow Family | Move petabytes of data to and from AWS, or process data at the edge |
| AWS Storage Gateway | Hybrid storage integration |
AWS MARKETPLACE
| Name | Description | What to buy? | Where to buy? |
|---|---|---|---|
| AWS Marketplace | Online store where you can buy or sell software that runs on Amazon Web Services. | ||
| Amazon EC2 Reserved Instance Marketplace 1 | Paid AMI (OS) | ||
Metrics collected by the CloudWatch Agent
CloudWatch Agent allows do the following:
-
Collect internal system-level metrics from Amazon EC2 instances across operating systems
Platform Where CloudWatch Agent collects metrics from? Metrics Windows Windows Performance Monitor Available bytes Cache Faults/sec Page Faults/sec Pages/sec Linux Memory metrics: /proc/meminfoActive (Bytes) Available (Bytes) Available Percent (Percent) Buffered (Bytes) Cached (Bytes) Free (Bytes) Inactive (Bytes) Total (Bytes) Used (Bytes) Used Percent (Percent) Mac ~ Linux ~ Linux -
Collect system-level metrics from on-premises servers.
-
Retrieve custom metrics from your applications or services using the
StatsDandcollectdprotocols. -
Collect logs from Amazon EC2 instances and on-premises servers,
AWS SAA-C03 - EXAM TRACKING
| No | Exam | Score | Score Percent | Final | Exam Time | Test Date |
|---|---|---|---|---|---|---|
| 1 | Cantrill 1 | 49/61 | 76% | X | Oct 16, 2023 | |
| 2 | Cantrill 2 | 49/61 | 80% | X | Oct 17, 2023 | |
| 3 | Tutorials Dojo 1 | 43/65 | 66% | X | 01:15:26 | Oct 18, 2023 |
| 4 | Tutorials Dojo 2 | 49/65 | 75% | Passed | 01:03:59 | Oct 19, 2023 |
| 5 | Tutorials Dojo 1 (2nd time) | 59/65 | 91% | Passed | 00:36:26 | Oct 20, 2023 |
| 6 | Tutorials Dojo 3 | 46/65 | 71% | X | 00:56:51 | Oct 21, 2023 |
| 7 | Tutorials Dojo 4 | 46/65 | 71% | X | 01:03:39 | Oct 22, 2023 |
| 8 | Tutorials Dojo 5 | 49/65 | 75% | Passed | 00:52:07 | Oct 23, 2023, 15h |
| 9 | Tutorials Dojo 6 | 48/65 | 74% | Passed | 00:58:01 | Oct 23, 2023, 20h |
| 10 | Tutorials Dojo Bonus Test | 34/45 | 75% | Passed | 00:44:37 | Oct 24, 2023, 10h |
| 11 | Tutorials Dojo 3 (2nd time) | 56/65 | 86% | Passed | 01:10:00 | Oct 24, 2023, 15h |
| 12 | Tutorials Dojo 4 (2nd time) | 59/65 | 91% | Passed | 00:51:06 | Oct 24, 2023, 18h |
| 13 | Tutorials Dojo Final Test | 60/65 | 92% | Passed | 00:46:49 | Oct 25, 2023, 0h |
| 14 | REAL AWS EXAM | 50/65 (Maybe) | 785/1000 | Passed | 02:10:00 | Oct 26, 2023, 9h |
AWS BACKUPS
S3
Amazon S3 is natively integrated with AWS Backup:
- Continuous backups (PITR)
- Periodic backups.
EBS
-
Snapshot are incremental volume copied to S3.
-
The snapshot deletion process is designed so that you need to retain only the most recent snapshot in order to create volumes.
-
Manually Snapshots:
-
Automatic snapshot creation (NOT NATIVE):
- Amazon Data Lifecycle Manager
- AWS Backup.
RDS
- Manually Snapshots
- Automated Backups:
- 0 to 35 days retention.
- RDS also use S3 to store transaction logs every 5 minutes.
DynamoDB
- On-Demand Backup
- PITR:
- 35 day recovery window
- 1s Granularity
Redshift
- Manually Snapshots
- Automatically increment backup:
- Every 8 hours or 5 GB of data
- 1-day retention (default, configurable up to 35 days)
Backup to S3 bucket, configurable to copy snapshots to another region for DR.
AWS AUTO-SCALING
AWS provides multiple services that you can use to scale your application.
Auto scaling is enabled by Amazon CloudWatch and is available at no additional charge beyond the service fees for CloudWatch and the other AWS resources that you use.
Amazon EC2 Auto Scaling (Auto Scaling groups)
Ensure that you have the correct number of Amazon EC2 instances available to handle the load for your application.
Application Auto Scaling
Auto scaling for resources beyond just EC2, e.g.
- Aurora replicas
- DynamoDB tables and global secondary indexes
- Amazon Elastic Container Service (ECS) services
- AWS Fargate
- Lambda function provisioned concurrency
- Spot Fleet requests
AWS Scaling Plan
Configure auto scaling for related or associated scalable resources (Aurora, DynamoDB, (EC2) Spot Fleet, EC2 Auto Scaling, and ECS)
Amazon Elastic Kubernetes Services (EKS)’s autoscaling
Cluster Autoscaling
- Kubernetes Cluster Autoscaler
- Karpenter
Pod Scaling
-
Horizontal Pod Autoscaler: automatically scales the number of Pods in a deployment, replication controller, or replica set based on that resource’s CPU utilization.
-
Vertical Pod Autoscaler: automatically adjusts the CPU and memory reservations for your Pods to help “right size” your applications
AWS Services with Infrequently Access (IA)
Amazon S3
Amazon S3 Standard-IA
Amazon S3 One Zone–IA
Ref: https://docs.aws.amazon.com/AmazonS3/latest/userguide/storage-class-intro.html#sc-infreq-data-access
Amazon EFS
Amazon EFS Standard-IA
Amazon EFS One Zone–IA
Ref: https://docs.aws.amazon.com/efs/latest/ug/storage-classes.html
Amazon DynamoDB Standard-IA
Reduce DynamoDB costs by up to 60 percent
Tutorials Dojo Exams
EXAM PRACTICE - 1
Scored: 49/61 (76%)
q8. ebs: inspect
CloudWatch, not CloudWatch Logs ???
q9. dynamodb: eventually consistent read
- Can receive outdated data
- Use less RCU than a strong consistent read ???
q11. s3: maximum performance
S3 Transfer Acceleration ???
q13. s3: access from external account
Use an IAM role ???
q18 ec2: ephemeral0 data
Won’t be lost after a restart
q20. vpc: 3 azs, 2 tier, subnets?
6 = 3 x 2
q28. ebs: backup
Snapshot backup ???
q29. cloudwatch: ec2 metrics
Without CWAgents
- CPU
- Disk
- Network
With CWAgent
- Memory
q34. elastic ip
Cost money event if not associated with anything
q37. ec2 - placement group: number of instance?
q45. allow network connectivity between 2+ vpc?
- VPC Peer
- Transit Gateway ???
q47. storage gateway vs nat gateway
Which one can extend capacity of on-premise?
q49. dynamodb: increase rcu vs dax?
q52. ec2 - instance store: when will the cache data be lost?
q54. cloudfront: can improve performance of static or dynamic content.
q55. s3 - storage classes
S3 Standard IA: Same performance as S3 Standard
q59. vpc: direct connect
Won’t traverse the public internet.
EXAM PRACTICE - 2
Scored: 49/61 (80%)
Q4. EC2: Access AWS resources?
EC2 Instance Role (EC2 Instance Profile)
Q28. S3: Encryption
SSE-S3: Admin can see the data ⭐ SSE-C: Custom’s Key ⭐⭐ SSE-KMS: Key Rotation, Role Separation ⭐⭐⭐
Q30. Site to Site VPN - Problem
Q31. DDoS Attach + ALB
AWS Shield Standard: L3/L4 AWS Shield Advanced: L7 👉 DDoS Protection
Q35. Scale out based on S3 event
SNS -> SQS -> ASG
Q36. NACL vs SG
-
NACL:
- Associated with a subnet 👉 applied to all instances in that subnet
- Support both ALLOW/DENY rule
-
SG:
- Associated with an instance
- Only support ALLOW rule
Q46. Which components are needed to create a custom public VPC for an EC2 instance to access public internet?
 VPC Resource Map
VPC Resource Map
-
Virtual Private Cloud (VPC)
-
Availability Zones
-
AZ-A
-
Subnets: Need connect to public internet
-
Subnet: (Public)
-
EC2 Instance:
- Associated SG
- Be default has no public IPv4 address 👉 Be default, these instances can communicate with each other, but can’t access the internet.
-
Associated NACL.
-
Associated Route Table (or default main route table)
- route traffics to IGW
-
-
Subnet: (Private)
-
EC2 Instance:
- Associated SG
-
Associated NACL.
-
Associated Route Table (or default main route table)
- route traffics to NATGW
-
-
-
NAT Gateways (NATGW)
-
-
AZ-B
-
-
Router:
- Route Tables: Explicitly associate a subnet with a particular route table.
- Main Route Table: Otherwise, the subnet is implicitly associated with the main route table.
-
NACLs:
- Associated with subnets
- ALLOW/DENY IN OR OUTBOUND
-
Default NACL: ALLOW all traffics (~ Has no effect)
-
Security Groups (SGs):
- Associated with AWS resources
- ALLOW IN (& OUTBOUND)
-
-
AWS Public Zone
- Internet Gateway (IGW)
-
Public Internet

-
Default VPC:
172.31.0.0/16-
AZs:
-
AZ-A
-
Default Subnet (Public):
/20-
EC2 instance: (if created)
- Automatically assign public DNS hostname with public IP addresses
-
Associated with default NACL
-
Associated with main route table
-
-
-
AZ-B
-
AZ-C
-
-
Router:
-
Main Route Table:

- Send all (
0.0.0.0/0) traffics to the IGW.
- Send all (
-
-
Default NACL: ALLOW all traffics (~ Has no effect): associated with default VPC

-
Default SG: associated with default VPC

-
Associate the default DHCP options set for your AWS account with default VPC.
-
-
AWS Public Zone:
- IGW: connected to default VPC.
Q58. VPC: Private Subnet. How to ensure the instance have outgoing access to the internet?
-
IPv4: Use a NATGW
-
IPv6: Use a Egress-Only IGW
Q47. RDS Single AZ vs RDS Multi-AZ vs RDS Multi-Region vs RDS Read Replicas
-
RDS Single AZ
-
RDS Multi-AZ: 1 or 2 standby DB instances 👉 high availability
-
RDS Multi-AZ Instance: Multi-AZ with one standby
-
1 Primary instance
-
1 Standby replica:
- can’t be used for reads / write 👈 not for performance scaling, only for availability
- kept in sync Synchronously with the primary instance
-
-
[RDS Multi-AZ Cluster](https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/Concepts.RDS_Fea_Regions_DB-eng.Feature.MultiAZDBClusters.html: Multi-AZ with two readable standbys
-
1 Writer DB instance
-
2 Reader DB instances:
- can be used for read 👈 limited read scaling
- kept in sync Synchronously with the Writer instance 👈 replication lag (aka Replica lag)
-
-
-
RDS Multi-Region: 👉 disaster recovery and local performance (Not supported for all DB engines)
-
Aurora:
- Aurora Global Databases
- Aurora Multi-Master:
- Multiple read-write instances of your Aurora database across multiple AZs.
- Multi-Master is no longer available as of Feb 28, 2023. Source
-
Other engines:
- Multi-Region = Cross-Region Read Replicas
- Multi-Region = Cross-Region automated backups
-
-
RDS Read Replica: 👉 scalability (performance)
Scale out beyond the capacity constraints of a single DB instance for read-heavy database workloads.
Maximum Read Replica per DB instance:
- 5: Oracle, SQL Server
- 15: MySQL, MariaDB, PostgreSQL, (and Aurora)
References:
| Endpoints | High Availability | Read Scalability | |
|---|---|---|---|
| Single AZ | Instance endpoint 1 | 🔳 | 🔳 |
| Multi-AZ Instance | Instance endpoint | ⬜ | 🔳 |
| (Automatically failover to standby replica 5) | |||
| Multi-AZ Cluster 10 | Multiple: | ⬜⬜ | ⬜⬜ |
| - Cluster endpoint (Writer endpoint) | |||
| - Reader endpoint | |||
| - Instance endpoints | |||
| Read Replicas | Multiple: | ⬜⬜⬜ | ⬜⬜⬜ |
| - Source DB instance endpoint | |||
| - Each replica has its own instance endpoint 20 | |||
| - (Aurora) Custom endpoints 21 |
Q50. ENI
An EC2 instance can have multiple ENIs attached, but these ENIs must be in the same AZ.
Q54. Multicast for EC2
Transit Gateway supports routing multicast traffic between subnets of attached VPCs
Q55. Big number of users need to access AWS resources?
Q56. EC2 - Connect to Linux instance
-
Connect from your local OS (machine)
- SSH
-
Connect from any local OS (machine)
-
-
Introduced in Sep 2018
-
Provides a browser-based
- interactive shell, CLI
- remote desktop access for managing instances on your cloud, or on-premises and edge devices
without the need to open inbound ports, manage SSH keys, or use bastion hosts
-
-
-
Introduced in June 2019.
-
With EC2 Instance Connect, you use IAM policies and principals to control SSH access to your instances, removing the need to share and manage SSH key.
-
Option 1: Using your own key and any SSH client
-
Manually create SSH.
$ ssh-keygen -t rsa -f my_key -
Use EC2 Instance Connect to push our SSH public key to the instance.
$ aws ec2-instance-connect send-ssh-public-key -
Connect to the instance using our private key
$ ssh 0i my_key <EC2_INSTANCE_DNS_NAME_OR_IP_ADDRESS>
-
-
Option 2: Using AWS CLI
ec2-instance-connect sshcommand-
Specify the instance ID
$ aws ec2-instance-connect ssh --instance-id i-1234567890example -
Specify the instance ID and our own key
$ aws ec2-instance-connect ssh --instance-id i-1234567890example --private-key-file /path/to/key.pem
-
-
-
With EC2 Instance Connect Endpoint (introduced in Jun 2023), the EC2 instance even doesn’t need a public IP address.
-
-
Q57. SQS & ASG scale based on queue length: What will happen if SQS doesn’t have Dead Letter Queue?
Messages fill up the queue, ASG scale up 👉 A lot of money will go away
Q58. How to ensure EC2 instances in a private subnet have only outgoing access to the internet?
Tutorials Dojo Exams
TUTORIALS DOJO - Practice Exam - Time-mode Set 1
Scored: 43/65 (66.15%)
- SAA – Design Cost-Optimized Architectures: 50%
- SAA – Design High-Performing Architectures: 68.18%
- SAA – Design Resilient Architectures: 73.68%
- SAA – Design Secure Architectures: 59.09%
SAA - Design Cost-Optimized Architectures
2
A company is using AWS Fargate to run a batch job whenever an object is uploaded to an Amazon S3 bucket. The minimum ECS task count is initially set to 1 to save on costs and should only be increased based on new objects uploaded to the S3 bucket.
Which is the most suitable option to implement with the LEAST amount of effort?
- Set up an Amazon EventBridge (Amazon CloudWatch Events) rule to detect S3 object PUT operations and set the target to a Lambda function that will run the StartTask API command.
- Set up an Amazon EventBridge (Amazon CloudWatch Events) rule to detect S3 object PUT operations and set the target to the ECS cluster to run a new ECS task.
- Set up an alarm in Amazon CloudWatch to monitor S3 object-level operations that are recorded on CloudTrail. Create an Amazon EventBridge (Amazon CloudWatch Events) rule that triggers the ECS cluster when new CloudTrail events are detected.
- Set up an alarm in CloudWatch to monitor S3 object-level operations recorded on CloudTrail. Set two alarm actions to update the ECS task count to scale-out/scale-in depending on the S3 event.
cloudwatch - cloudwatch logs - cloudtrail - cloudwatch events - eventbridge?
-
CloudWatch: Monitor resources and applications
-
CloudWatch Logs: Monitor, store, and access your log files from Amazon Elastic Compute Cloud instances, AWS CloudTrail, or other sources.
-
CLoudWatch Events: Is now Amazon EventBridge
-
-
CloudTrail: Track and monitor activities by users, roles, or AWS services
-
EventBridge: Serverless event bus for SaaS apps and AWS services
4
An AI-powered Forex trading application consumes thousands of data sets to train its machine learning model. The application’s workload requires a high-performance, parallel hot storage to process the training datasets concurrently. It also needs cost-effective cold storage to archive those datasets that yield low profit.
Which of the following Amazon storage services should the developer use?
- Use Amazon FSx For Lustre and Amazon EBS Provisioned IOPS SSD (io1) volumes for hot and cold storage respectively.
- Use Amazon FSx For Lustre and Amazon S3 for hot and cold storage respectively.
- Use Amazon Elastic File System and Amazon S3 for hot and cold storage respectively.
- Use Amazon FSx For Windows File Server and Amazon S3 for hot and cold storage respectively.
ebs is not suitable for archiving datasets -> s3 is better option
9
An e-commerce company operates a highly scalable web application that relies on an Amazon Aurora database. As their users multiply, they've noticed that the read replica struggles to keep up with the increasing read traffic, leading to performance bottlenecks during peak periods.
As a solutions architect, which of the following will address the issue with the most cost-effective solution?
- Increase the size of the Amazon Aurora DB cluster.
- Use automatic scaling for the Amazon Aurora read replica using Aurora Auto Scaling.
- Implement read scaling with Amazon Aurora Global Database.
- Set up a read replica that can operate across different regions.
aurora auto scaling vs aurora serverless
-
Aurora Auto Scaling: Dynamically adjusts the number of Aurora Replicas (reader DB instances) provisioned for an Aurora DB cluster.
-
Aurora Serverless: On-demand, autoscaling the capacity of Aurora DB cluster resource
11
A retail company receives raw .csv data files into its Amazon S3 bucket from various sources on an hourly basis. The average file size of these data files is 2 GB.
An automated process must be set up to convert these .csv files to a more efficient Apache Parquet format and store the output files in another S3 bucket. Additionally, the conversion process must be automatically triggered whenever a new file is uploaded into the S3 bucket.
Which of the following options must be implemented to meet these requirements with the LEAST operational overhead?
- Use a Lambda function triggered by an S3 PUT event to convert the .csv files to Parquet format. Use the AWS Transfer Family with SFTP service to move the output files to the target S3 bucket.
- Utilize an AWS Glue extract, transform, and load (ETL) job to process and convert the .csv files to Apache Parquet format and then store the output files into the target S3 bucket. Set up an S3 Event Notification to track every S3 PUT event and invoke the ETL job in AWS Glue through Amazon SQS.
- Set up an Apache Spark job running in an Amazon EC2 instance and create an Amazon EventBridge (Amazon CloudWatch Events) rule to monitor S3 PUT events in the S3 bucket. Configure AWS Lambda to invoke the Spark job for every new .csv file added via a Function URL.
- Create an ETL (Extract, Transform, Load) job and a Data Catalog table in AWS Glue. Configure the AWS Glue crawler to run on a schedule to check for new files in the S3 bucket every hour and convert them to Parquet format.
aws glue
- Simple, scalable, and serverless data integration
- Serverless ETL
- Glue Job can be triggered manually or via events using EventBridge
13
A company is using a combination of API Gateway and Lambda for the web services of the online web portal that is being accessed by hundreds of thousands of clients each day. They will be announcing a new revolutionary product and it is expected that the web portal will receive a massive number of visitors all around the globe.
How can you protect the backend systems and applications from traffic spikes?
- Use throttling limits in API Gateway
- API Gateway will automatically scale and handle massive traffic spikes so you do not have to do anything.
- Manually upgrade the EC2 instances being used by API Gateway
- Deploy Multi-AZ in API Gateway with Read Replica
api gateway works at any scale, just pay money.
Throttle API requests for our budget (and for better throughtput)
14
An online learning company hosts its Microsoft .NET e-Learning application on a Windows Server in its on-premises data center. The application uses an Oracle Database Standard Edition as its backend database.
The company wants a high-performing solution to migrate this workload to the AWS cloud to take advantage of the cloud’s high availability. The migration process should minimize development changes, and the environment should be easier to manage.
Which of the following options should be implemented to meet the company requirements? (Select TWO.)
- Migrate the Oracle database to Amazon RDS for Oracle in a Multi-AZ deployment by using AWS Database Migration Service (AWS DMS).
- Refactor the application to .NET Core and run it as a serverless container service using Amazon Elastic Kubernetes Service (Amazon EKS) with AWS Fargate.
- Use AWS Application Migration Service (AWS MGN) to migrate the on-premises Oracle database server to a new Amazon EC2 instance.
- Rehost the on-premises .NET application to an AWS Elastic Beanstalk Multi-AZ environment which runs in multiple Availability Zones.
- Provision and replatform the application to Amazon Elastic Container Service (Amazon ECS) with Amazon EC2 worker nodes. Use the Windows Server Amazon Machine Image (AMI) and deploy the .NET application using to the ECS cluster via the Amazon ECS Anywhere service.
aws database migration service (aws dms)
Migrate on-premises databases to the AWS Cloud.
aws beanstalk: run and manage web apps
Reduces the operational overhead by taking care of provisioning the needed resources for your application.
15
A popular social media website uses a CloudFront web distribution to serve their static contents to their millions of users around the globe. They are receiving a number of complaints recently that their users take a lot of time to log into their website. There are also occasions when their users are getting HTTP 504 errors. You are instructed by your manager to significantly reduce the user's login time to further optimize the system.
Which of the following options should you use together to set up a cost-effective solution that can improve your application's performance? (Select TWO.)
- Customize the content that the CloudFront web distribution delivers to your users using Lambda@Edge, which allows your Lambda functions to execute the authentication process in AWS locations closer to the users.
- Use multiple and geographically disperse VPCs to various AWS regions then create a transit VPC to connect all of your resources. In order to handle the requests faster, set up Lambda functions in each region using the AWS Serverless Application Model (SAM) service.
- Configure your origin to add a Cache-Control max-age directive to your objects, and specify the longest practical value for max-age to increase the cache hit ratio of your CloudFront distribution.
- Deploy your application to multiple AWS regions to accommodate your users around the world. Set up a Route 53 record with latency routing policy to route incoming traffic to the region that provides the best latency to the user.
- Set up an origin failover by creating an origin group with two origins. Specify one as the primary origin and the other as the second origin which CloudFront automatically switches to when the primary origin returns specific HTTP status code failure responses.
lambda@edge: run lambda functions to customize the content that cloudfront delivers
cloudfront - origin failover
19
A company wishes to query data that resides in multiple AWS accounts from a central data lake. Each account has its own Amazon S3 bucket that stores data unique to its business function. Users from different accounts must be granted access to the data lake based on their roles.
Which solution will minimize overhead and costs while meeting the required access patterns?
- Use AWS Lake Formation to consolidate data from multiple accounts into a single account.
- Use AWS Kinesis Firehose to consolidate data from multiple accounts into a single account.
- Create a scheduled Lambda function for transferring data from multiple accounts to the S3 buckets of a central account
- Use AWS Control Tower to centrally manage each account's S3 buckets.
aws lake formation: build a secure data lake in days
aws kinesis: analyze real-time video and data streams
- Kinesis Video Streams: Capture, process, and store video streams for analytics and machine learning.
- Kinesis Data Streams: Build custom applications that analyze data streams using popular stream-processing frameworks.
- Kinesis Data Firehose: Load data streams into AWS data stores.
aws control tower: set up and govern a secure, compliant multi-account environment
aws organizations: central governance and management across aws accounts
3
An online cryptocurrency exchange platform is hosted in AWS which uses ECS Cluster and RDS in Multi-AZ Deployments configuration. The application is heavily using the RDS instance to process complex read and write database operations. To maintain the reliability, availability, and performance of your systems, you have to closely monitor how the different processes or threads on a DB instance use the CPU, including the percentage of the CPU bandwidth and total memory consumed by each process.
Which of the following is the most suitable solution to properly monitor your database?
- Use Amazon CloudWatch to monitor the CPU Utilization of your database.
- Create a script that collects and publishes custom metrics to CloudWatch, which tracks the real-time CPU Utilization of the RDS instance, and then set up a custom CloudWatch dashboard to view the metrics.
- Enable Enhanced Monitoring in RDS.
- Check the CPU% and MEM% metrics which are readily available in the Amazon RDS console that shows the percentage of the CPU bandwidth and total memory consumed by each database process of your RDS instance.
rds enhanced monitoring
- CloudWatch gathers metrics about CPU utilization from the hypervisor for a DB instance
- Enhanced Monitoring gathers its metrics from an agent on the instance ~ EC2 CloudWatch Agent
10
A suite of web applications is hosted in an Auto Scaling group of EC2 instances across three Availability Zones and is configured with default settings. There is an Application Load Balancer that forwards the request to the respective target group on the URL path. The scale-in policy has been triggered due to the low number of incoming traffic to the application.
Which EC2 instance will be the first one to be terminated by your Auto Scaling Group?
- The EC2 instance which has the least number of user sessions
- The EC2 instance which has been running for the longest time
- The EC2 instance launched from the oldest launch configuration
- The instance will be randomly selected by the Auto Scaling group
auto scaling group's [termination policy](https://docs.aws.amazon.com/autoscaling/ec2/userguide/as-instance-termination.html#default-termination-policy)
- Maximum availability: Kill instance in the AZs with the most instances (and oldest Launch Configuration)
- Keep most updated instance: Kill instance with oldest LC
- Maximum instance usage: Kill the instance closest to billing hour.
- Finally: random.
12
An online shopping platform is hosted on an Auto Scaling group of Spot EC2 instances and uses Amazon Aurora PostgreSQL as its database. There is a requirement to optimize your database workloads in your cluster where you have to direct the production traffic to your high-capacity instances and point the reporting queries sent by your internal staff to the low-capacity instances.
Which is the most suitable configuration for your application as well as your Aurora database cluster to achieve this requirement?
- Configure your application to use the reader endpoint for both production traffic and reporting queries, which will enable your Aurora database to automatically perform load-balancing among all the Aurora Replicas.
- In your application, use the instance endpoint of your Aurora database to handle the incoming production traffic and use the cluster endpoint to handle reporting queries.
- Create a custom endpoint in Aurora based on the specified criteria for the production traffic and another custom endpoint to handle the reporting queries.
- Do nothing since by default, Aurora will automatically direct the production traffic to your high-capacity instances and the reporting queries to your low-capacity instances.
aurora custom endpoint: provides load-balanced database connections based on criteria other than the read-only or read-write capability of the db instances
14.
A company has recently migrated its microservices-based application to Amazon Elastic Kubernetes Service (Amazon EKS). As part of the migration, the company must ensure that all sensitive configuration data and credentials, such as database passwords and API keys, are stored securely and encrypted within the Amazon EKS cluster's etcd key-value store.
What is the most suitable solution to meet the company's requirements?
- Enable secret encryption with a new AWS KMS key on an existing Amazon EKS cluster to encrypt sensitive data stored in the EKS cluster's etcd key-value store.
- Use AWS Secrets Manager with a new AWS KMS key to securely manage and store sensitive data within the EKS cluster's etcd key-value store.
- Enable default Amazon EBS volume encryption for the account with a new AWS KMS key to ensure encryption of sensitive data within the Amazon EKS cluster.
- Use Amazon EKS default options and the Amazon Elastic Block Store (Amazon EBS) Container Storage Interface (CSI) driver as an add-on to securely store sensitive data within the Amazon EKS cluster.
k8s has its own mechanism for storing secret, which are default store as plain text in etcd key-value store.
We can apply envelope encryption to encrypt these secrets with AWS KMS before stored them in etcd store.
1.
A financial application is composed of an Auto Scaling group of EC2 instances, an Application Load Balancer, and a MySQL RDS instance in a Multi-AZ Deployments configuration. To protect the confidential data of your customers, you have to ensure that your RDS database can only be accessed using the profile credentials specific to your EC2 instances via an authentication token.
As the Solutions Architect of the company, which of the following should you do to meet the above requirement?
- Enable the IAM DB Authentication.
- Configure SSL in your application to encrypt the database connection to RDS.
- Create an IAM Role and assign it to your EC2 instances which will grant exclusive access to your RDS instance.
- Use a combination of IAM and STS to restrict access to your RDS instance via a temporary token.
rds - [iam db authentication](https://docs.aws.amazon.com/amazonrds/latest/userguide/usingwithrds.iamdbauth.html)
To connect to DB instance, we’ll use an authentication token (generated using the IAM role’s credential).
2.
An online medical system hosted in AWS stores sensitive Personally Identifiable Information (PII) of the users in an Amazon S3 bucket. Both the master keys and the unencrypted data should never be sent to AWS to comply with the strict compliance and regulatory requirements of the company.
Which S3 encryption technique should the Architect use?
- Use S3 client-side encryption with a KMS-managed customer master key.
- Use S3 client-side encryption with a client-side master key.
- Use S3 server-side encryption with a KMS managed key.
- Use S3 server-side encryption with customer provided key.
kms-managed cmk: key will be sent to aws
Server-side encryption: unencrypted data will be sent to AWS
-> Client-side encryption with a client-side master key.
10
A tech company that you are working for has undertaken a Total Cost Of Ownership (TCO) analysis evaluating the use of Amazon S3 versus acquiring more storage hardware. The result was that all 1200 employees would be granted access to use Amazon S3 for the storage of their personal documents.
Which of the following will you need to consider so you can set up a solution that incorporates a single sign-on feature from your corporate AD or LDAP directory and also restricts access for each individual user to a designated user folder in an S3 bucket? (Select TWO.)
[identity federation (with saml)](https://docs.aws.amazon.com/singlesignon/latest/userguide/samlfederationconcept.html): pass information about a user between
- a SAML authority (called an identity provider or IdP)
- a SAML consumer (called a service provider or SP)
iam identity provider (idp): manage user identities outside of aws and give these external user identities permissions to use aws resources in your account.
- Setup Identity Provider and Identity Federation.
- Setup an AWS Security Token Service to generate temporary tokens (STS supports SAML)
- Configure an IAM role and an IAM Policy to access the bucket.
11
A business has recently migrated its applications to AWS. The audit team must be able to assess whether the services the company is using meet common security and regulatory standards. A solutions architect needs to provide the team with a report of all compliance-related documents for their account.
Which action should a solutions architect consider?
- Run an Amazon Inspector assessment job to download all of the AWS compliance-related information.
- Use AWS Artifact to view the security reports as well as other AWS compliance-related information.
- Run an Amazon Macie job to view the Service Organization Control (SOC), Payment Card Industry (PCI), and other compliance reports from AWS Certificate Manager (ACM).
- View all of the AWS security compliance reports from AWS Security Hub.
amazon macie: discover and protect your sensitive data at scale -> s3
amazon inspector: automated and continual vulnerability management at scale -> ec2, ecr, lambda
amazon artifact: on-demand access to aws compliance reports: soc, pci, baa, nda -> reports
amazon security hub: unified security and compliance center -> dashboard / overview
15.
A company uses an Application Load Balancer (ALB) for its public-facing multi-tier web applications. The security team has recently reported that there has been a surge of SQL injection attacks lately, which causes critical data discrepancy issues. The same issue is also encountered by its other web applications in other AWS accounts that are behind an ALB. An immediate solution is required to prevent the remote injection of unauthorized SQL queries and protect their applications hosted across multiple accounts.
As a Solutions Architect, what solution would you recommend?
- Use AWS Network Firewall to filter web vulnerabilities and brute force attacks using stateful rule groups across all Application Load Balancers on all AWS accounts. Refactor the web application to be less susceptible to SQL injection attacks based on the security assessment.
- Use AWS WAF and set up a managed rule to block request patterns associated with the exploitation of SQL databases, like SQL injection attacks. Associate it with the Application Load Balancer. Integrate AWS WAF with AWS Firewall Manager to reuse the rules across all the AWS accounts.
- Use Amazon Macie to scan for vulnerabilities and unintended network exposure. Refactor the web application to be less susceptible to SQL injection attacks based on the security assessment. Utilize the AWS Audit Manager to reuse the security assessment across all AWS accounts.
- Use Amazon GuardDuty and set up a managed rule to block request patterns associated with the exploitation of SQL databases, like SQL injection attacks. Associate it with the Application Load Balancer and utilize the AWS Security Hub service to reuse the managed rules across all the AWS accounts
aws network firewall: a stateful, managed, network firewall and intrusion detection and prevention service for your virtual private cloud (vpc).
aws firewall manager: simplifies your aws waf administration and maintenance tasks across multiple accounts and resources
aws waf: filter malicious web traffic
amazon guard duty: managed threat detection service; identify unexpected and potentially unauthorized or malicious activity in your aws environment.
17
A company requires all the data stored in the cloud to be encrypted at rest. To easily integrate this with other AWS services, they must have full control over the encryption of the created keys and also the ability to immediately remove the key material from AWS KMS. The solution should also be able to audit the key usage independently of AWS CloudTrail.
Which of the following options will meet this requirement?
- Use AWS Key Management Service to create AWS-owned CMKs and store the non-extractable key material in AWS CloudHSM.
- Use AWS Key Management Service to create a CMK in a custom key store and store the non-extractable key material in Amazon S3.
- Use AWS Key Management Service to create AWS-managed CMKs and store the non-extractable key material in AWS CloudHSM.
- Use AWS Key Management Service to create a CMK in a custom key store and store the non-extractable key material in AWS CloudHSM.
kms - [custom key store](https://docs.aws.amazon.com/kms/latest/developerguide/custom-key-store-overview.html)
-> We own and manage
20
A medical records company is planning to store sensitive clinical trial data in an Amazon S3 repository with the object-level versioning feature enabled. The Solutions Architect is tasked with ensuring that no object can be overwritten or deleted by any user in a period of one year only. To meet the strict compliance requirements, the root user of the company’s AWS account must also be restricted from making any changes to an object in the S3 bucket.
Which of the following is the most secure way of storing the data in Amazon S3?
- Enable S3 Object Lock in governance mode with a retention period of one year.
- Enable S3 Object Lock in compliance mode with a retention period of one year.
- Enable S3 Object Lock in governance mode with a legal hold of one year.
- Enable S3 Object Lock in compliance mode with a legal hold of one year.
s3 object lock
-
Retention:
-
Retention Mode:
- Governance: Big Brother can by pass it.
- Compliance: It’s universe law, nobody can do anything
-
Retention Period: A fixed period of time during which an object remains locked
-
-
Legal holds: ~ Retention Periods but has no expiration date
21
A government entity is conducting a population and housing census in the city. Each household information uploaded on their online portal is stored in encrypted files in Amazon S3. The government assigned its Solutions Architect to set compliance policies that verify data containing personally identifiable information (PII) in a manner that meets their compliance standards. They should also be alerted if there are potential policy violations with the privacy of their S3 buckets.
Which of the following should the Architect implement to satisfy this requirement?
- Set up and configure Amazon Macie to monitor their Amazon S3 data.
- Set up and configure Amazon Kendra to monitor malicious activity on their Amazon S3 data
- Set up and configure Amazon Polly to scan for usage patterns on Amazon S3 data
- Set up and configure Amazon Fraud Detector to send out alert notifications whenever a security violation is detected on their Amazon S3 data.
amazon kendra: reinvent enterprise search with ml
amazon polly: turn text into life-like speech
amazon fraud detector: detect more online fraud faster
TUTORIALS DOJO - Practice Exam - Time-mode Set 2
Scored: 49 of 65 point(s), (75.38%) - 01:03:59
- SAA – Design Cost-Optimized Architectures: 72.73%
- SAA – Design High-Performing Architectures: 92.86%
- SAA – Design Resilient Architectures: 68.42%
- SAA – Design Secure Architectures: 71.43%
Category: SAA - Design Cost-Optimized Architectures
3
A media company hosts large volumes of archive data that are about 250 TB in size on their internal servers. They have decided to move these data to S3 because of its durability and redundancy. The company currently has a 100 Mbps dedicated line connecting their head office to the Internet.
Which of the following is the FASTEST and the MOST cost-effective way to import all these data to Amazon S3?
- Upload it directly to S3
- Establish an AWS Direct Connect connection then transfer the data over to S3.
- Use AWS Snowmobile to transfer the data over to S3.
- Order multiple AWS Snowball devices to upload the files to Amazon S3.
aws snow family:
- Snowcone: 8TB - 14TB
- Snowball: 80TB
- Snowball Edge:
- Snowball Edge Compute Optimized: 80TB + EC2
- Snowball Edge Storage Optimized: 210TB + EC2
- Snowmobile: 100PB
5
A company has a serverless application made up of AWS Amplify, Amazon API Gateway and a Lambda function. The application is connected to an Amazon RDS MySQL database instance inside a private subnet. A Lambda Function URL is also implemented as the dedicated HTTPS endpoint for the function, which has the following value:
https://12june1898pil1pinas.lambda-url.us-west-2.on.aws/
There are times during peak loads when the database throws a “too many connections” error preventing the users from accessing the application.
Which solution could the company take to resolve the issue?
- Increase the concurrency limit of the Lambda function
- Provision an RDS Proxy between the Lambda function and RDS database instance
- Increase the rate limit of API Gateway
- Increase the memory allocation of the Lambda function
rds - “too many connections”
rds proxy: allow your applications to pool and share database connections to improve their ability to scale.
6
A company is building an internal application that serves as a repository for images uploaded by a couple of users. Whenever a user uploads an image, it would be sent to Kinesis Data Streams for processing before it is stored in an S3 bucket. If the upload was successful, the application will return a prompt informing the user that the operation was successful. The entire processing typically takes about 5 minutes to finish.
Which of the following options will allow you to asynchronously process the request to the application from upload request to Kinesis, S3, and return a reply in the most cost-effective manner?
- Use a combination of Lambda and Step Functions to orchestrate service components and asynchronously process the requests.
- Use a combination of SQS to queue the requests and then asynchronously process them using On-Demand EC2 Instances.
- Replace the Kinesis Data Streams with an Amazon SQS queue. Create a Lambda function that will asynchronously process the requests.
- Use a combination of SNS to buffer the requests and then asynchronously process them using On-Demand EC2 Instances.
kinesis data streams vs sqs
- Kinesis Data Streams: Provide real-time analyzing, but required provisioning shards
- SQS: Use with Lambda (and its Event Sourcing) provides a cost-efficient solution
SAA - Design High-Performing Architectures
6
A software company has resources hosted in AWS and on-premises servers. You have been requested to create a decoupled architecture for applications which make use of both resources.
Which of the following options are valid? (Select TWO.)
- Use SWF to utilize both on-premises servers and EC2 instances for your decoupled application
- Use RDS to utilize both on-premises servers and EC2 instances for your decoupled application
- Use SQS to utilize both on-premises servers and EC2 instances for your decoupled application
- Use VPC peering to connect both on-premises servers and EC2 instances for your decoupled application
amazon simple workflow service (swf): build applications that coordinate work across distributed components.
vpc peering: only works for vpcs, doesn't work with on-premise networks
SAA - Design Resilient Architectures
4
A company has a static corporate website hosted in a standard S3 bucket and a new web domain name that was registered using Route 53. You are instructed by your manager to integrate these two services in order to successfully launch their corporate website.
What are the prerequisites when routing traffic using Amazon Route 53 to a website that is hosted in an Amazon S3 Bucket? (Select TWO.)
- The S3 bucket name must be the same as the domain name
- A registered domain name
- The record set must be of type "MX"
- The S3 bucket must be in the same region as the hosted zone
- The Cross-Origin Resource Sharing (CORS) option should be enabled in the S3 bucket
s3 static website - custom domain: "the s3 bucket name must be the same as the domain name"
What if someone use my domain name for their bucket???
6
As part of the Business Continuity Plan of your company, your IT Director instructed you to set up an automated backup of all of the EBS Volumes for your EC2 instances as soon as possible.
What is the fastest and most cost-effective solution to automatically back up all of your EBS Volumes?
- For an automated solution, create a scheduled job that calls the "create-snapshot" command via the AWS CLI to take a snapshot of production EBS volumes periodically.
- Set your Amazon Storage Gateway with EBS volumes as the data source and store the backups in your on-premises servers through the storage gateway.
- Use an EBS-cycle policy in Amazon S3 to automatically back up the EBS volumes.
- Use Amazon Data Lifecycle Manager (Amazon DLM) to automate the creation of EBS snapshots.
ebs - backup: use amazon dlm
amazon data lifecycle manager (amazon dlm): automate management of amazon ebs snapshots and amazon ebs-backed amis
7
A DevOps Engineer is required to design a cloud architecture in AWS. The Engineer is planning to develop a highly available and fault-tolerant architecture consisting of an Elastic Load Balancer and an Auto Scaling group of EC2 instances deployed across multiple Availability Zones. This will be used by an online accounting application that requires path-based routing, host-based routing, and bi-directional streaming using Remote Procedure Call (gRPC).
Which configuration will satisfy the given requirement?
- Configure an Application Load Balancer in front of the auto-scaling group. Select gRPC as the protocol version.
- Configure a Network Load Balancer in front of the auto-scaling group. Use a UDP listener for routing.
- Configure a Network Load Balancer in front of the auto-scaling group. Create an AWS Global Accelerator accelerator and set the load balancer as an endpoint.
- Configure a Gateway Load Balancer in front of the auto-scaling group. Ensure that the IP Listener Routing uses the GENEVE protocol on port 6081 to allow gRPC response traffic.
elastic load balancer protocol:
- Application Load Balancer: HTTP/s and gRPC
- Network Load Balancer: TCP, UDP, TLS
- Gateway Load Balancer: IP
11
A company has multiple VPCs with IPv6 enabled for its suite of web applications. The Solutions Architect tried to deploy a new Amazon EC2 instance but she received an error saying that there is no IP address available on the subnet.
How should the Solutions Architect resolve this problem?
- Set up a new IPv4 subnet with a larger CIDR range. Associate the new subnet with the VPC and then launch the instance.
- Ensure that the VPC has IPv6 CIDRs only. Remove any IPv4 CIDRs associated with the VPC.
- Set up a new IPv6-only subnet with a large CIDR range. Associate the new subnet with the VPC then launch the instance.
- Disable the IPv4 support in the VPC and use the available IPv6 addresses.
vpc: ipv4 vs ipv6
- IPv4 is the default IP addressing system for VPC => Cannot be disabled
- IPv6: optional
13
A company hosts its web application on a set of Amazon EC2 instances in an Auto Scaling group behind an Application Load Balancer (ALB). The application has an embedded NoSQL database. As the application receives more traffic, the application becomes overloaded mainly due to database requests. The management wants to ensure that the database is eventually consistent and highly available.
Which of the following options can meet the company requirements with the least operational overhead?
- Change the ALB with a Network Load Balancer (NLB) to handle more traffic and integrate AWS Global Accelerator to ensure high availability. Configure replication of the NoSQL database on the set of Amazon EC2 instances to spread the database load.
- Configure the Auto Scaling group to spread the Amazon EC2 instances across three Availability Zones. Use the AWS Database Migration Service (DMS) with a replication server and an ongoing replication task to migrate the embedded NoSQL database to Amazon DynamoDB
- Change the ALB with a Network Load Balancer (NLB) to handle more traffic. Use the AWS Migration Service (DMS) to migrate the embedded NoSQL database to Amazon DynamoDB.
- Configure the Auto Scaling group to spread the Amazon EC2 instances across three Availability Zones. Configure replication of the NoSQL database on the set of Amazon EC2 instances to spread the database load.
Least operational overhead: No need to change ALB to NLB
18
A company runs a messaging application in the ap-northeast-1 and ap-southeast-2 region. A Solutions Architect needs to create a routing policy wherein a larger portion of traffic from the Philippines and North India will be routed to the resource in the ap-northeast-1 region.
Which Route 53 routing policy should the Solutions Architect use?
- Geoproximity Routing
- Geolocation Routing
- Latency Routing
- Weighted Routing
route 53: geoproximity routing vs geolocation routing vs latency-based routing
- Geolocation Routing: Location of user
- GeoProximity Routing: Location of user AND AWS resources (with bias)
- Latency-based Routing
SAA - Design Secure Architectures
1
A solutions architect is designing a three-tier website that will be hosted on an Amazon EC2 Auto Scaling group fronted by an Internet-facing Application Load Balancer (ALB). The website will persist data to an Amazon Aurora Serverless DB cluster, which will also be used for generating monthly reports.
The company requires a network topology that follows a layered approach to reduce the impact of misconfigured security groups or network access lists. Web filtering must also be enabled to automatically stop traffic to known malicious URLs and to immediately drop requests coming from blacklisted fully qualified domain names (FQDNs).
Which network topology provides the minimum resources needed for the website to work?
- Set up an Application Load Balancer deployed in a public subnet, then host the Auto Scaling Group of Amazon EC2 instances and the Aurora Serverless DB cluster in private subnets. Launch an AWS Network Firewall with the appropriate firewall policy to automatically stop traffic to known malicious URLs and drop requests coming from blacklisted FQDNs. Reroute your Amazon VPC network traffic through the firewall endpoints.
- Set up an Application Load Balancer and a NAT Gateway deployed in public subnets. Launch the Auto Scaling Group of Amazon EC2 instances and Aurora Serverless DB cluster in private subnets. Directly integrate the AWS Network Firewall with the Application Load Balancer to automatically stop traffic to known malicious URLs and drop requests coming from blacklisted FQDNs.
- Set up an Application Load Balancer in front of an Auto Scaling group of Amazon EC2 instances with an Aurora Serverless DB cluster to persist data. Launch a NAT Gateway in a public subnet to restrict external services from initiating a connection to the EC2 instances and immediately drop requests from unauthorized FQDNs. Deploy all other resources in private subnets.
- Set up an Auto Scaling group of Amazon EC2 instances behind an Application Load Balancer with an Aurora Serverless DB cluster to store application data. Deploy all resources in a public subnet. Configure host-based routing to the Application Load Balancer to stop traffic to known malicious URLs and drop requests from blacklisted FQDNs.
aws network firewall
Traffic from VPC need to be routed to Network Firewall through the firewall endpoints.
7
A company needs to assess and audit all the configurations in their AWS account. It must enforce strict compliance by tracking all configuration changes made to any of its Amazon S3 buckets. Publicly accessible S3 buckets should also be identified automatically to avoid data breaches.
Which of the following options will meet this requirement?
- Use AWS Trusted Advisor to analyze your AWS environment.
- Use AWS IAM to generate a credential report.
- Use AWS Config to set up a rule in your AWS account.
- Use AWS CloudTrail and review the event history of your AWS account.
aws config: _track_ and _evaluate_ configuration changes
aws trusted advisor: optimize performance and security
- Inspects your AWS environment and recommends ways to save money, close security gaps, and improve system availability and performance.
10
A media company has two VPCs: VPC-1 and VPC-2 with peering connection between each other. VPC-1 only contains private subnets while VPC-2 only contains public subnets. The company uses a single AWS Direct Connect connection and a virtual interface to connect their on-premises network with VPC-1.
Which of the following options increase the fault tolerance of the connection to VPC-1? (Select TWO.)
- Establish a new AWS Direct Connect connection and private virtual interface in the same region as VPC-2.
- Establish a hardware VPN over the Internet between VPC-2 and the on-premises network.
- Establish a hardware VPN over the Internet between VPC-1 and the on-premises network.
- Use the AWS VPN CloudHub to create a new AWS Direct Connect connection and private virtual interface in the same region as VPC-2.
- Establish another AWS Direct Connect connection and private virtual interface in the same AWS region as VPC-1.
aws vpn: securely access your network resources (by establishing a secure and private tunnel from your network or device to the aws cloud.)
- AWS Site-to-Site VPN: AWS managed VPN services
- AWS Client VPN: client-based managed VPN service
aws direct connect: dedicated network connection to aws (from your on-premises network)
16
A multinational company currently operates multiple AWS accounts to support its operations across various branches and business units. The company needs a more efficient and secure approach in managing its vast AWS infrastructure to avoid costly operational overhead.
To address this, they plan to transition to a consolidated, multi-account architecture while integrating a centralized corporate directory service for authentication purposes.
Which combination of options can be used to meet the above requirements? (Select TWO.)
- Set up a new entity in AWS Organizations and configure its authentication system to utilize AWS Directory Service directly.
- Establish an identity pool through Amazon Cognito and adjust the AWS IAM Identity Center settings to allow Amazon Cognito authentication.
- Utilize AWS CloudTrail to enable centralized logging and monitoring across all AWS accounts.
- Integrate AWS IAM Identity Center with the corporate directory service for centralized authentication. Configure a service control policy (SCP) to manage the AWS accounts.
- Implement AWS Organizations to create a multi-account architecture that provides a consolidated view and centralized management of AWS accounts.
service control policy (scp): a feature of aws organizations
- A type of organization policy that you can use to manage permissions in your organization.
18
A startup has multiple AWS accounts that are assigned to its development teams. Since the company is projected to grow rapidly, the management wants to consolidate all of its AWS accounts into a multi-account setup. To simplify the login process on the AWS accounts, the management wants to utilize its existing directory service for user authentication
Which combination of actions should a solutions architect recommend to meet these requirements? (Select TWO.)
- Create an identity pool on Amazon Cognito and configure it to use the company’s directory service. Configure AWS IAM Identity Center (AWS Single Sign-On) to accept Cognito authentication.
- On the master account, use AWS Organizations to create a new organization with all features turned on. Enable the organization’s external authentication and point it to use the company’s directory service.
- Create Service Control Policies (SCP) in the organization to manage the child accounts. Configure AWS IAM Identity Center (AWS Single Sign-On) to use AWS Directory Service.
- On the master account, use AWS Organizations to create a new organization with all features turned on. Invite the child accounts to this new organization.
- Configure AWS IAM Identity Center (AWS Single Sign-On) for the organization and integrate it with the company’s directory service using the Active Directory Connector
aws iam identity center: manage single sign-on access to aws accounts and apps
amazon cognito: identity management for your apps
- Customer already has Active Directory Service -> No need to use Amazon Cognito -> use AWS IAM Identity Center with the Active Director Connector
19
A company is hosting its web application in an Auto Scaling group of EC2 instances behind an Application Load Balancer. Recently, the Solutions Architect identified a series of SQL injection attempts and cross-site scripting attacks to the application, which had adversely affected their production data.
Which of the following should the Architect implement to mitigate this kind of attack?
- Use Amazon GuardDuty to prevent any further SQL injection and cross-site scripting attacks in your application.
- Using AWS Firewall Manager, set up security rules that block SQL injection and cross-site scripting attacks. Associate the rules to the Application Load Balancer.
- Block all the IP addresses where the SQL injection and cross-site scripting attacks originated using the Network Access Control List.
- Set up security rules that block SQL injection and cross-site scripting attacks in AWS Web Application Firewall (WAF). Associate the rules to the Application Load Balancer.
block sql injection
-
AWS Web Application Firewall (WAF): can block SQL injection.
-
GuardDuty: only detect SQL injection, not block.
[aws waf, aws shield, and aws firewall manager](https://docs.aws.amazon.com/waf/latest/developerguide/what-is-aws-waf.html): used together to create a comprehensive security solution
-
AWS WAF: Protect your web applications from common exploits
-
Monitor web requests that your end users send to your applications and to control access to your content.
-
Used for API Gateway, Load Balancer, Cloudfront.
-
Block SQL injection, XSS (cross-site scripting)
-
Can minimize the effects of a DDOS attack
-
-
AWS Shield: Managed DDoS protection
-
Provides protection against distributed denial of service (DDoS) attacks for AWS resources, at the network and transport layers (layer 3 and 4) and the application layer (layer 7)
-
Can use for more services: EC2, Route53
-
Shield Standard: Free, L3-L4
-
Shield Advanced: Cost money, L7
-
-
AWS Firewall Manager: Centrally configure and manage firewall rules across your accounts
Provides management of protections like AWS WAF and Shield Advanced across accounts and resources, even as new resources are added.
how about aws network firewall?
AWS Network Firewall: Deploy network firewall security across your VPCs
TUTORIALS DOJO - Practice Exam - Time-mode Set 3
- Scored: 46/65 (70.77%)
- SAA – Design Cost-Optimized Architectures: 55.56%
- SAA – Design High-Performing Architectures: 71.43%
- SAA – Design Resilient Architectures: 72.22%
- SAA – Design Secure Architectures: 76.47%
- Time: 00:56:51
- Date: Oct 21, 2023
SAA - Design Cost-Optimized Architectures
2
A solutions architect is managing an application that runs on a Windows EC2 instance with an attached Amazon FSx for Windows File Server. To save cost, management has decided to stop the instance during off-hours and restart it only when needed. It has been observed that the application takes several minutes to become fully operational which impacts productivity.
How can the solutions architect speed up the instance’s loading time without driving the cost up?
- Migrate the application to a Linux-based EC2 instance.
- Migrate the application to an EC2 instance with hibernation enabled.
- Enable the hibernation mode on the EC2 instance.
- Disable the Instance Metadata Service to reduce the things that need to be loaded at startup.
ec2 - hibernation
- Quickly pausing and resuming the instances, by saving the memory footprint to disk.
- Can only be enable at launch
- Pay as stopped instances:
- No hourly charging
- EBS volume.
- Elastic IP Address.
7
In Amazon EC2, you can manage your instances from the moment you launch them up to their termination. You can flexibly control your computing costs by changing the EC2 instance state.
Which of the following statements is true regarding EC2 billing? (Select TWO.)
- You will be billed when your On-Demand instance is in pending state.
- You will be billed when your Spot instance is preparing to stop with a stopping state.
- You will be billed when your On-Demand instance is preparing to hibernate with a stopping state.
- You will be billed when your Reserved instance is in terminated state.
- You will not be billed for any instance usage while an instance is not in the running state.
ec2 states:
- pending
- running 💸
- rebooting
- stopping - stopped (EBS-backed instances)
- hibernate 💸
- shutting-down
- terminated (Terminated Reserver Instances are still billed 💸)
8
A company has established a dedicated network connection from its on-premises data center to AWS Cloud using AWS Direct Connect (DX). The core network services, such as the Domain Name System (DNS) service and Active Directory services, are all hosted on-premises. The company has new AWS accounts that will also require consistent and dedicated access to these network services.
Which of the following can satisfy this requirement with the LEAST amount of operational overhead and in a cost-effective manner?
- Set up another Direct Connect connection for each and every new AWS account that will be added.
- Set up a new Direct Connect gateway and integrate it with the existing Direct Connect connection. Configure a VPC peering connection between AWS accounts and associate it with Direct Connect gateway.
- Create a new AWS VPN CloudHub. Set up a Virtual Private Network (VPN) connection for additional AWS accounts.
- Create a new Direct Connect gateway and integrate it with the existing Direct Connect connection. Set up a Transit Gateway between AWS accounts and associate it with the Direct Connect gateway.
transit gateway & direct connect gateway ??? todo
direct connect connection/gateway ??? todo
vpn traverses the public internet, doesn't use a dedicated connection
9
A company is hosting an application on EC2 instances that regularly pushes and fetches data in Amazon S3. Due to a change in compliance, the instances need to be moved on a private subnet. Along with this change, the company wants to lower the data transfer costs by configuring its AWS resources.
How can this be accomplished in the MOST cost-efficient manner?
- Set up a NAT Gateway in the public subnet to connect to Amazon S3.
- Create an Amazon S3 interface endpoint to enable a connection between the instances and Amazon S3.
- Create an Amazon S3 gateway endpoint to enable a connection between the instances and Amazon S3.
- Set up an AWS Transit Gateway to access Amazon S3.
vpc endpoints for s3: provide _private_ access to aws public services (s3)
-
Gateway endpoint:
-
via Route Table’s Prefix List, without IGW, NATGW, PrivateLink
-
Free
-
-
Interface endpoint:
-
via DNS using Private IP Address 👉 more features
- access from on-premises
- access from VPC in another AWS Region (using VPC Peering, Transit Gateway)
-
Billed 💸
-
SAA - Design High-Performing Architectures
3
A data analytics company is setting up an innovative checkout-free grocery store. Their Solutions Architect developed a real-time monitoring application that uses smart sensors to collect the items that the customers are getting from the grocery’s refrigerators and shelves then automatically deduct it from their accounts. The company wants to analyze the items that are frequently being bought and store the results in S3 for durable storage to determine the purchase behavior of its customers.
What service must be used to easily capture, transform, and load streaming data into Amazon S3, Amazon OpenSearch Service, and Splunk?
- Amazon Kinesis Data Firehose
- Amazon DynamoDB Streams
- Amazon Redshift
- Amazon SQS
amazon kinesis data firehose: load data streams into aws data stores.
amazon athena: query data in amazon s3 using sql
amazon redshift: fast, simple, cost-effective data warehouse service
6
A large financial firm in the country has an AWS environment that contains several Reserved EC2 instances hosting a web application that has been decommissioned last week. To save costs, you need to stop incurring charges for the Reserved instances as soon as possible.
What cost-effective steps will you take in this circumstance? (Select TWO.)
- Stop the Reserved instances as soon as possible.
- Contact AWS to cancel your AWS subscription.
- Go to the AWS Reserved Instance Marketplace and sell the Reserved instances.
- Terminate the Reserved instances as soon as possible to avoid getting billed at the on-demand price when it expires.
- Go to the Amazon.com online shopping website and sell the Reserved instances.
ec2 - reserved instance
Reserved Instance Marketplace: Resell unused Standard Reserved Instances
ec2 - stop instance vs terminate instance
- Stopped: still be billed
- Terminated: not billed
15
An on-premises server uses an SMB network file share to store application data. The application produces around 50 MB of data per day, but it only needs to access some of it for daily processes. To save on storage costs, the company plans to copy all the application data to AWS, however, they want to retain the ability to retrieve data with the same low-latency access as the local file share. The company does not have the capacity to develop the needed tool for this operation.
Which AWS service should the company use?
- AWS Virtual Private Network (VPN)
- Amazon FSx for Windows File Server
- AWS Snowball Edge
- AWS Storage Gateway
nfs vs storage gateway
- NFS: files are stored on AWS -> high-latency
- Storage Gateway - File: low-latency
17
A Data Analyst in a financial company is tasked to provide insights on stock market trends to the company's clients. The company uses AWS Glue extract, transform, and load (ETL) jobs in daily report generation, which involves fetching data from an Amazon S3 bucket. The analyst discovered that old data from previous runs were being reprocessed, causing the jobs to take longer to complete.
Which solution would resolve the issue in the most operationally efficient way?
- Increase the size of the dataset used in the job to speed up the extraction and analysis process.
- Parallelize the job by splitting the dataset into smaller partitions and processing them simultaneously using multiple EC2 instances.
- Create a Lambda function that removes any data already processed. Then, use Amazon EventBridge (Amazon CloudWatch Events) to trigger this function whenever the ETL job's status switches to SUCCEEDED.
- Enable job bookmark for the ETL job.
aws glue - job bookmarking
- maintain state information and prevent the reprocessing of old data.
20
A company is deploying a Microsoft SharePoint Server environment on AWS using CloudFormation. The Solutions Architect needs to install and configure the architecture that is composed of Microsoft Active Directory (AD) domain controllers, Microsoft SQL Server 2012, multiple Amazon EC2 instances to host the Microsoft SharePoint Server and many other dependencies. The Architect needs to ensure that the required components are properly running before the stack creation proceeds.
Which of the following should the Architect do to meet this requirement?
- Configure the DependsOn attribute in the CloudFormation template. Send a success signal after the applications are installed and configured using the cfn-init helper script.
- Configure a UpdatePolicy attribute to the instance in the CloudFormation template. Send a success signal after the applications are installed and configured using the cfn-signal helper script.
- Configure the UpdateReplacePolicy attribute in the CloudFormation template. Send a success signal after the applications are installed and configured using the cfn-signal helper script.
- Configure a CreationPolicy attribute to the instance in the CloudFormation template. Send a success signal after the applications are installed and configured using the cfn-signal helper script.
cloudformation: creationpolicy & cfn-signal
- CreationPolicy: Wait on resource configuration actions before stack creation proceeds.
- cfn-signal: Signals CloudFormation to indicate whether Amazon EC2 instances have been successfully created/updated
21
A solutions architect is in charge of preparing the infrastructure for a serverless application. The application is built from a Docker image pulled from an Amazon Elastic Container Registry (ECR) repository. It is compulsory that the application has access to 5 GB of ephemeral storage.
Which action satisfies the requirements?
- Deploy the application to an Amazon ECS cluster that uses Fargate tasks.
- Deploy the application in a Lambda function with Container image support. Set the function’s storage to 5 GB.
- Deploy the application in a Lambda function with Container image support. Attach an Amazon Elastic File System (EFS) volume to the function.
- Deploy the application Amazon ECS cluster with EC2 worker nodes and attach a 5 GB Amazon EBS volume.
aws fargate: serverless compute for containers
By default, Fargate tasks are given a minimum of 20 GiB of free ephemeral storage
SAA - Design Resilient Architectures
2
A tech startup is launching an on-demand food delivery platform using Amazon ECS cluster with an AWS Fargate serverless compute engine and Amazon Aurora. It is expected that the database read queries will significantly increase in the coming weeks ahead. A Solutions Architect recently launched two Read Replicas to the database cluster to improve the platform's scalability.
Which of the following is the MOST suitable configuration that the Architect should implement to load balance all of the incoming read requests equally to the two Read Replicas?
- Use the built-in Reader endpoint of the Amazon Aurora database.
- Use the built-in Cluster endpoint of the Amazon Aurora database.
- Enable Amazon Aurora Parallel Query.
- Create a new Network Load Balancer to evenly distribute the read queries to the Read Replicas of the Amazon Aurora database.
aurora - reader endpoint:
- A reader endpoint for an Aurora DB cluster provides load-balancing support for read-only connections to the DB cluster
7
An online registration system hosted in an Amazon EKS cluster stores data to a db.t4g.medium Amazon Aurora DB cluster. The database performs well during regular hours but is unable to handle the traffic surge that occurs during flash sales. A solutions architect must move the database to Aurora Serverless while minimizing downtime and the impact on the operation of the application.
Which change should be taken to meet the objective?
- Use AWS Database Migration Service (AWS DMS) to migrate to a new Aurora Serverless database.
- Change the Aurora Instance class to Serverless
- Take a snapshot of the DB cluster. Use the snapshot to create a new Aurora DB cluster.
- Add an Aurora Replica to the cluster and set its instance class to Serverless. Failover to the read replica and promote it to primary.
aurora serverless
-
The DB instance cannot be changed from Provisioned to Serverless after created.
-
After the DB instanced is created, need to use AWS Database Migration Service (AWS DMS) to migrate data from the existing DB cluster to a new Aurora Serverless database.
8
An online stocks trading application that stores financial data in an S3 bucket has a lifecycle policy that moves older data to Glacier every month. There is a strict compliance requirement where a surprise audit can happen at anytime and you should be able to retrieve the required data in under 15 minutes under all circumstances. Your manager instructed you to ensure that retrieval capacity is available when you need it and should handle up to 150 MB/s of retrieval throughput.
Which of the following should you do to meet the above requirement? (Select TWO.)
- Retrieve the data using Amazon Glacier Select.
- Use Expedited Retrieval to access the financial data.
- Use Bulk Retrieval to access the financial data.
- Specify a range, or portion, of the financial data archive to retrieve.
- Purchase provisioned retrieval capacity.
s3 - read data from glacier
- Bulk: Lowest (5-12 hours), cheapest
- Standard: 3-5 hours
- Expedited: Fastest (1-5 mins)
- Buy Provisioned capacity to ensure Expedited retrievals is available.
amazon glacier select: filter objects using sql
14
A FinTech startup deployed an application on an Amazon EC2 instance with attached Instance Store volumes and an Elastic IP address. The server is only accessed from 8 AM to 6 PM and can be stopped from 6 PM to 8 AM for cost efficiency using Lambda with the script that automates this based on tags.
Which of the following will occur when the EC2 instance is stopped and started? (Select TWO.)
- The underlying host for the instance is possibly changed.
- The ENI (Elastic Network Interface) is detached.
- All data on the attached instance-store devices will be lost.
- The Elastic IP address is disassociated with the instance.
- There will be no changes.
ec2 - instance store:
- Its data will be lost if the EC2 instance is stopped / terminated.
ec2 - elastic ip address and ebs storage won't be effect after an instance is stopped.
18
An aerospace engineering company recently adopted a hybrid cloud infrastructure with AWS. One of the Solutions Architect’s tasks is to launch a VPC with both public and private subnets for their EC2 instances as well as their database instances.
Which of the following statements are true regarding Amazon VPC subnets?
(Select TWO.)
- EC2 instances in a private subnet can communicate with the Internet only if they have an Elastic IP.
- Each subnet maps to a single Availability Zone.
- The allowed block size in VPC is between a /16 netmask (65,536 IP addresses) and /27 netmask (32 IP addresses).
- Every subnet that you create is automatically associated with the main route table for the VPC.
- Each subnet spans to 2 Availability Zones.
vpc supports cidr blocks from /16 to /28
SAA - Design Secure Architectures
2
A solutions architect is writing an AWS Lambda function that will process encrypted documents from an Amazon FSx for NetApp ONTAP file system. The documents are protected by an AWS KMS customer key. After processing the documents, the Lambda function will store the results in an S3 bucket with an Amazon S3 Glacier Flexible Retrieval storage class. The solutions architect must ensure that the files can be decrypted by the Lambda function.
Which action accomplishes the requirement?
- Attach the kms:decrypt permission to the Lambda function’s execution role. Add a statement to the AWS KMS key’s policy that grants the function’s execution role the kms:decrypt permission.
- Attach the kms:decrypt permission to the Lambda function’s resource policy. Add a statement to the AWS KMS key’s policy that grants the function’s resource policy ARN the kms:decrypt permission.
- Attach the kms:decrypt permission to the Lambda function’s execution role. Add a statement to the AWS KMS key’s policy that grants the function’s ARN the kms:decrypt permission.
- Attach the kms:decrypt permission to the Lambda function’s resource policy. Add a statement to the AWS KMS key’s policy that grants the function’s execution role the kms:decrypt permission.
allow an lambda permission to use kms:
- Attach the kms:decrypt permission to the Lambda function’s
execution role - Add a statement to the AWS KMS
key policythat grants the function’s execution role the kms:decrypt permission.
10
A company that is rapidly growing in recent months has been in the process of setting up IAM users on its single AWS Account. A solutions architect has been tasked to handle the user management, which includes granting read-only access to users and denying permissions whenever an IAM user has no MFA setup. New users will be added frequently based on their respective departments.
Which of the following action is the MOST secure way to grant permissions to the new users?
- Launch an IAM Group for each department. Create an IAM Policy that enforces MFA authentication with the least privilege permission. Attach the IAM Policy to each IAM Group.
- Create a Service Control Policy (SCP) that enforces MFA authentication for each department. Add a trust relationship to every SCP and attach it to each IAM User.
- Create an IAM Role that enforces MFA authentication with the least privilege permission. Set up a corresponding IAM Group for each department. Attach the IAM Role to the IAM Groups.
- Set up IAM roles for each IAM user and associate a permissions boundary that defines the maximum permissions.
iam group
- Cannot attach an IAM Role to an IAM Group.
13
A company hosted a web application on a Linux Amazon EC2 instance in the public subnet that uses a non-default network ACL. The instance uses a default security group and has an attached Elastic IP address. The network ACL is configured to block all inbound and outbound traffic. The Solutions Architect must allow incoming traffic on port 443 to access the application from any source.
Which combination of steps will accomplish this requirement? (Select TWO.)
- In the Security Group, add a new rule to allow TCP connection on port 443 from source 0.0.0.0/0
- In the Network ACL, update the rule to allow both inbound and outbound TCP connection on port 443 from source 0.0.0.0/0 and to destination 0.0.0.0/0
- In the Security Group, create a new rule to allow TCP connection on port 443 to destination 0.0.0.0/0
- In the Network ACL, update the rule to allow outbound TCP connection on port 32768 - 65535 to destination 0.0.0.0/0
- In the Network ACL, update the rule to allow inbound TCP connection on port 443 from source 0.0.0.0/0 and outbound TCP connection on port 32768 - 65535 to destination 0.0.0.0/0
vpc - nacl:
- The client that initiates the request chooses the ephemeral port range.
- In practice, to cover the different types of clients that might initiate traffic to public-facing instances in your VPC, you can open ephemeral ports 1024-65535.
To turn on the connection to a service running on an instance, the associated network ACL must allow the following:
- Inbound traffic on the port that the service is listening on
- Outbound traffic to ephemeral ports
17
A company is generating confidential data that is saved on their on-premises data center. As a backup solution, the company wants to upload their data to an Amazon S3 bucket. In compliance with its internal security mandate, the encryption of the data must be done before sending it to Amazon S3. The company must spend time managing and rotating the encryption keys as well as controlling who can access those keys.
Which of the following methods can achieve this requirement? (Select TWO.)
- Set up Server-Side Encryption with keys stored in a separate S3 bucket.
- Set up Client-Side Encryption with a customer master key stored in AWS Key Management Service (AWS KMS).
- Set up Client-Side Encryption with Amazon S3 managed encryption keys.
- Set up Server-Side Encryption (SSE) with EC2 key pair.
- Set up Client-Side Encryption using a client-side master key.
s3 object encryption:
-
Server-Side Encryption (SSE):
- SSE-S3 (Amazon S3 managed keys)
- SSE-KMS (AWS KMS)
- SSE-C (Customer-provided keys)
-
Client-Side Encryption (CSE):
- CSE-KMS-CMK
- CSE-Client Master key
TUTORIALS DOJO - Practice Exam - Time-mode Set 4
- Scored: 46/65 (71%)
- SAA – Design Cost-Optimized Architectures: 75%
- SAA – Design High-Performing Architectures: 81.82%
- SAA – Design Resilient Architectures: 55.56%
- SAA – Design Secure Architectures: 70.59%
- Time: 01:03:40
- Date: Oct 22, 2023
SAA - Design Cost-Optimized Architectures
3
A company is looking to store their confidential financial files in AWS which are accessed every week. The Architect was instructed to set up the storage system which uses envelope encryption and automates key rotation. It should also provide an audit trail that shows who used the encryption key and by whom for security purposes.
Which combination of actions should the Architect implement to satisfy the requirement in the most cost-effective way? (Select TWO.)
- Use Amazon S3 to store the data.
- Use Amazon S3 Glacier Deep Archive to store the data.
- Configure Server-Side Encryption with Customer-Provided Keys (SSE-C).
- Configure Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3).
- Configure Server-Side Encryption with AWS KMS-Managed Keys (SSE-KMS).
s3 - server-side encryption
- SSE-S3
- SSE-KMS: support audit
- SSE-C:
| Encryption | Fullname | Who Manages Key? | Who Manages Encryption Process? | Notes |
|---|---|---|---|---|
| SSE-S3 | SSE with Amazon S3 managed keys | S3 | S3 | Default |
| SSE-KMS | SSE with AWS KMS keys | AWS managed key | S3 | Support audit keys usage… |
| Customer managed key (CMK) - Renamed to KMS Key | ||||
| SSE-C | SSE with Customer-Provided Key | Customer | S3 | Use your own encryption key |
| CSE | Customer | Customer |
5
A web application is hosted in an Auto Scaling group of EC2 instances deployed across multiple Availability Zones behind an Application Load Balancer. You need to implement an SSL solution for your system to improve its security which is why you requested an SSL/TLS certificate from a third-party certificate authority (CA).
Where can you safely import the SSL/TLS certificate of your application? (Select TWO.)
- AWS Certificate Manager
- IAM SSL certificate storage
- A private S3 bucket with versioning enabled
- An S3 bucket configured with server-side encryption with customer-provided encryption keys (SSE-C)
- CloudFront
which services support storing ssl certificate?
- AWS Certificate Manager (ACM)
- IAM SSL certificate storage (Used for region that not support ACM)
SAA - Design High-Performing Architectures
13
A company hosts all its applications on its data center on the US East Coast. Most of the workloads are legacy applications that are hosted on individual virtual machines running in Linux and Windows operating systems. The company plans to migrate all of its VM workloads to the AWS cloud. To minimize changes in the applications during the migration process, it has been decided that the company will use a “lift-and-shift” strategy. The company also wants to minimize downtime during the migration process.
Which of the following options should the Solutions Architect implement for this scenario?
- Export the on-premises VMs and upload the images to an Amazon S3 bucket. Use VM Import/Export service to import the images and launch them as Amazon EC2 instances.
- Install the AWS Replication Agent on each of the on-premises VMs to continuously replicate the servers to AWS. Use AWS Migration Service (AWS MGN) to launch test instances and perform cutover once testing is completed.
- Use the AWS Application Discovery Service for lift-and-shift migrations. Deploy the AWS Application Discovery Agent to the on-premises data center to start the replication process. After the replication task is completed, launch Amazon EC2 instances based on the created AMIs.
- Utilize AWS DataSync to migrate the application workloads to AWS. Deploy the AWS DataSync VM on the on-premises data center. Once replication is completed, launch Amazon EC2 instances based on the created AMIs.
aws application migration service: automate application migration and modernization
aws application discovery service: discover on-premises applications to streamline migration
aws database migration service: migrate databases with minimal downtime
aws datasync: simple, fast, online data transfer
18
An automotive company is working on an autonomous vehicle development and deployment project using AWS. The solution requires High Performance Computing (HPC) in order to collect, store and manage massive amounts of data as well as to support deep learning frameworks. The Linux EC2 instances that will be used should have a lower latency and higher throughput than the TCP transport traditionally used in cloud-based HPC systems. It should also enhance the performance of inter-instance communication and must include an OS-bypass functionality to allow the HPC to communicate directly with the network interface hardware to provide low-latency, reliable transport functionality.
Which of the following is the MOST suitable solution that you should implement to achieve the above requirements?
- Attach an Elastic Network Adapter (ENA) on each Amazon EC2 instance to accelerate High Performance Computing (HPC).
- Attach an Elastic Fabric Adapter (EFA) on each Amazon EC2 instance to accelerate High Performance Computing (HPC).
- Attach an Elastic Network Interface (ENI) on each Amazon EC2 instance to accelerate High Performance Computing (HPC).
- Attach a Private Virtual Interface (VIF) on each Amazon EC2 instance to accelerate High Performance Computing (HPC).
eni - ena - efa
-
Elastic Network Interface (ENI): logical networking component in a VPC that represents a virtual network card
-
Elastic Network Adapter (ENA): High Performance Network Interface for Amazon EC2
- Enhanced networking: up to 100 Gbps
- provide traditional IP networking features
-
Elastic Fabric Adapter (EFA): network device to accelerate High Performance Computing (HPC) applications
- support OS-bypass capabilities: allow HPC communicate directly with the EFA device.
19
A company has a High Performance Computing (HPC) cluster that is composed of EC2 Instances with Provisioned IOPS (io1) volume to process transaction-intensive, low-latency workloads. The Solutions Architect must maintain high IOPS while keeping the latency down by setting the optimal queue length for the volume. The size of each volume is 10 GiB.
Which of the following is the MOST suitable configuration that the Architect should set up?
21
A company has a web-based order processing system that is currently using a standard queue in Amazon SQS. The IT Manager noticed that there are a lot of cases where an order was processed twice. This issue has caused a lot of trouble in processing and made the customers very unhappy. The manager has asked you to ensure that this issue will not recur.
What can you do to prevent this from happening again in the future? (Select TWO.)
- Alter the retention period in Amazon SQS.
- Alter the visibility timeout of SQS.
- Replace Amazon SQS and instead, use Amazon Simple Workflow service.
- Change the message size in SQS.
- Use an Amazon SQS FIFO Queue instead.
ensure a queue's messages are not process twice:
- SQS FIFO Queue
- Amazon Simple Workflow Service (Amazon SWF)
SAA - Design Resilient Architectures
2
A company recently launched an e-commerce application that is running in eu-east-2 region, which strictly requires six EC2 instances running at all times. In that region, there are 3 Availability Zones (AZ) that you can use - eu-east-2a, eu-east-2b, and eu-east-2c.
Which of the following deployments provide 100% fault tolerance if any single AZ in the region becomes unavailable? (Select TWO.)
- eu-east-2a with two EC2 instances, eu-east-2b with two EC2 instances, and eu-east-2c with two EC2 instances
- eu-east-2a with two EC2 instances, eu-east-2b with four EC2 instances, and eu-east-2c with two EC2 instances
- eu-east-2a with four EC2 instances, eu-east-2b with two EC2 instances, and eu-east-2c with two EC2 instances
- eu-east-2a with six EC2 instances, eu-east-2b with six EC2 instances, and eu-east-2c with no EC2 instances
- eu-east-2a with three EC2 instances, eu-east-2b with three EC2 instances, and eu-east-2c with three EC2 instances
fault tolerance: ability of a system to remain in operation even if some of the components used to build the system fail
5
A company has a web application hosted in AWS cloud where the application logs are sent to Amazon CloudWatch. Lately, the web application has recently been encountering some errors which can be resolved simply by restarting the instance.
What will you do to automatically restart the EC2 instances whenever the same application error occurs?
- First, look at the existing CloudWatch logs for keywords related to the application error to create a custom metric. Then, create a CloudWatch alarm for that custom metric which invokes an action to restart the EC2 instance.
- First, look at the existing CloudWatch logs for keywords related to the application error to create a custom metric. Then, create an alarm in Amazon SNS for that custom metric which invokes an action to restart the EC2 instance.
- First, look at the existing Flow logs for keywords related to the application error to create a custom metric. Then, create a CloudWatch alarm for that custom metric which invokes an action to restart the EC2 instance.
- First, look at the existing Flow logs for keywords related to the application error to create a custom metric. Then, create a CloudWatch alarm for that custom metric which calls a Lambda function that invokes an action to restart the EC2 instance.
cloudwatch alarm can stop, terminate, reboot, recover an ec2 instance
8
A company plans to deploy an application in an Amazon EC2 instance. The application will perform the following tasks:
Read large datasets from an Amazon S3 bucket.
Execute multi-stage analysis on the datasets.
Save the results to Amazon RDS.
During multi-stage analysis, the application will store a large number of temporary files in the instance storage. As the Solutions Architect, you need to recommend the fastest storage option with high I/O performance for the temporary files.
Which of the following options fulfills this requirement?
- Enable Transfer Acceleration in Amazon S3.
- Configure RAID 1 in multiple instance store volumes.
- Attach multiple Provisioned IOPS SSD volumes in the instance.
- Configure RAID 0 in multiple instance store volumes.
raid 0:
- I/O is distributed across the volumes in a stripe
- higher level of performance for a file system than you can provision on a single Amazon EBS volume
raid 1, 2, 3, 4, 5, 6: not recommended for ebs
12
A company deployed an online enrollment system database on a prestigious university, which is hosted in RDS. The Solutions Architect is required to monitor the database metrics in Amazon CloudWatch to ensure the availability of the enrollment system.
What are the enhanced monitoring metrics that Amazon CloudWatch gathers from Amazon RDS DB instances which provide more accurate information? (Select TWO.)
monitor ec2:
-
CloudWatch default metric
- CPU utilization from hypervisor
- Disk
- Network
-
CloudWatch Agent:
- Memory
- Sub-resource metrics such as per-CPU core
monitor rds:
-
Default metric
- CPU utilization from hypervisor
- Database connections
- Free memory
-
Enhanced Monitoring:
- OS processes
- RDS processes
13
A data analytics company, which uses machine learning to collect and analyze consumer data, is using Redshift cluster as their data warehouse. You are instructed to implement a disaster recovery plan for their systems to ensure business continuity even in the event of an AWS region outage.
Which of the following is the best approach to meet this requirement?
- Create a scheduled job that will automatically take the snapshot of your Redshift Cluster and store it to an S3 bucket. Restore the snapshot in case of an AWS region outage.
- Do nothing because Amazon Redshift is a highly available, fully-managed data warehouse which can withstand an outage of an entire AWS region.
- Use Automated snapshots of your Redshift Cluster.
- Enable Cross-Region Snapshots Copy in your Amazon Redshift Cluster.
amazon redshift backup:
- Manually Snapshots
- Automatically increment backup:
- Every 8 hours or 5 GB of data
- 1-day retention (default, configurable up to 35 days)
Backup to S3 bucket, configurable to copy snapshots to another region for DR.
14
Every week, an e-commerce company announces a sales promotion, causing its application hosted on an Auto Scaling group to experience intermittent downtime. Because of long initialization times, the application only becomes operational minutes before a new EC2 instance turns into RUNNING state. A solutions architect must devise a solution that launches capacity in advance based on a forecasted load in order to scale faster.
Which solution meets the requirements with the least amount of effort?
- Configure the Auto Scaling group to use predictive scaling.
- Use Amazon Forecast to analyze and predict the workload pattern of the application. Create a scheduled scaling policy based on the prediction results.
- Create a dynamic scaling policy based on the historical average CPU load of the application.
- Create a Scheduled Amazon EventBridge (Amazon CloudWatch Events) Rule that runs a scaling job on a Lambda function every midnight.
auto scaling group (asg) policies:
- Manually
- Scheduled
- Dynamic
- Simple
- Stepped
- Target Tracking
- Predictive
15
A company has a fixed set of Amazon EC2 instances inside a VPC in the AWS cloud. The instances run a mission-critical application. In a recent incident, one of the EC2 instances suddenly powered down which affected the availability of the application. To avoid this incident in the future, the management wants to get notified of any upcoming AWS events that may affect these EC2 instances.
Which of the following options is the recommended action to meet the above requirements?
- Create an Amazon EventBridge (Amazon CloudWatch Events) rule that is scheduled to run every 24 hours. Set the target to an AWS Lambda function that will check AWS Service Health Dashboard and send notifications for any events that may affect Amazon EC2 instances.
- Set up an Amazon EventBridge (Amazon CloudWatch Events) rule to check for any status change for Amazon EC2 instances. Set the target to an AWS Lambda function that will send a notification and restart the affected Amazon EC2 instances.
- Create an Amazon EventBridge (Amazon CloudWatch Events) rule to check for AWS Personal Health Dashboard events that are related to Amazon EC2 instances. To send notifications, set an Amazon SNS topic as a target for the rule.
- Set up an Amazon EventBridge (Amazon CloudWatch Events) rule to check for AWS Service Health Dashboard events that are related to Amazon EC2 instances. To send notifications, set an Amazon SNS topic as a target for the rule.
notify for ec2 instance:
-
All EC2 instances:
- Create an Amazon EventBridge (Amazon CloudWatch Events) rule to check for AWS Personal Health Dashboard events that are related to Amazon EC2 instances.
- To send notifications, set an Amazon SNS topic as a target for the rule.
-
A specific EC2 instance:
Use CloudWatch Alarm and EC2 Action to interact with EC2 instance.
17
A newly hired Solutions Architect is checking all of the security groups and network access control list rules of the company's AWS resources. For security purposes, the MS SQL connection via port 1433 of the database tier should be secured. Below is the security group configuration of their Microsoft SQL Server database:
The application tier hosted in an Auto Scaling group of EC2 instances is the only identified resource that needs to connect to the database. The Architect should ensure that the architecture complies with the best practice of granting least privilege.
Which of the following changes should be made to the security group configuration?
- For the MS SQL rule, change the Source to the security group ID attached to the application tier.
- For the MS SQL rule, change the Source to the EC2 instance IDs of the underlying instances of the Auto Scaling group.
- For the MS SQL rule, change the Source to the static AnyCast IP address attached to the application tier.
- For the MS SQL rule, change the Source to the Network ACL ID attached to the application tier.
security group referencing
When you specify a security group as the source or destination for a rule (of a security group), the rule affects all instances that are associated with the security groups.
SAA - Design Secure Architectures
2
A startup launched a new FTP server using an On-Demand EC2 instance in a newly created VPC with default settings. The server should not be accessible publicly but only through the IP address 175.45.116.100 and nowhere else.
Which of the following is the most suitable way to implement this requirement?
- Create a new inbound rule in the security group of the EC2 instance with the following details: Protocol: TCP Port Range: 20 - 21 Source: 175.45.116.100/32
- Create a new inbound rule in the security group of the EC2 instance with the following details: Protocol: UDP Port Range: 20 - 21 Source: 175.45.116.100/32
- Create a new Network ACL inbound rule in the subnet of the EC2 instance with the following details: Protocol: TCP Port Range: 20 - 21 Source: 175.45.116.100/0 Allow/Deny: ALLOW
- Create a new Network ACL inbound rule in the subnet of the EC2 instance with the following details: Protocol: UDP Port Range: 20 - 21 Source: 175.45.116.100/0 Allow/Deny: ALLOW
default nacl allows all inbound and outbound traffic
cidr `/0`: the entire network -> is not used in sg and nacl.
CIDR /32: One IP address.
4
A food company bought 50 licenses of Windows Server to be used by the developers when launching Amazon EC2 instances to deploy and test applications. The developers are free to provision EC2 instances as long as there is a license available. The licenses are tied to the total CPU count of each virtual machine. The company wants to ensure that developers won’t be able to launch new instances once the licenses are exhausted. The company wants to receive notifications when all licenses are in use.
Which of the following options is the recommended solution to meet the company's requirements?
- Define licensing rules on AWS License Manager to track and control license usage. Enable the option to “Enforce license limit” to prevent going over the number of allocated licenses. Add an Amazon SNS topic to send notifications and alerts.
- Define license configuration rules on AWS Certificate Manager to track and control license usage. Enable the option to “Enforce certificate limit” to prevent going over the number of allocated licenses. Add an Amazon SQS queue with ChangeVisibility Timeout configured to send notifications and alerts.
- Upload the licenses on AWS Systems Manager Fleet Manager to be encrypted and distributed to Amazon EC2 instances. Attach an IAM role on the EC2 instances to request a license from the Fleet Manager. Set up an Amazon SNS to send notifications and alerts once all licenses are used
- Configure AWS Resource Access Manager (AWS RAM) to track and control the licenses used by AWS resources. Configure AWS RAM to provide available licenses for Amazon EC2 instances. Set up an Amazon SNS to send notifications and alerts once all licenses are used.
aws license manager: track and manage software licenses across multiple aws regions
aws systems manager's fleet manager: ui for managing nodes/ec2 instance.
aws resource access manager (aws ram): simple, secure service to share aws resources
8
A company has a regional API Gateway in the us-east-2 region that serves as a proxy to a backend service. Clients connect to the service using the invoke URL of the API stage. To improve usability, the company wants to associate a custom domain name (api.tutorialsdojo.com) with the API. Moreover, the domain name must support HTTPS to ensure secure connections. The company has an existing hosted zone for its domain on Amazon Route 53.
Which of the following would be the next step to achieve the company's objective?
- Request a public certificate in the us-east-1 region for api.tutorialsdojo.com using AWS Certificate Manager (ACM). Create a regional API Gateway domain name and associate it with api.tutorialsdojo.com and the ACM certificate. In Route 53, create an alias record for api.tutorialsdojo.com that points to the API Gateway domain name.
- Import an existing public certificate for api.tutorialsdojo.com into AWS Certificate Manager (ACM) in the us-east-2. In Route 53, create a CNAME record for api.tutorialsdojo.com that points to the invoke URL of the API Gateway stage.
- Use the AWS Certificate Manager Private Certificate Authority (ACM PCA) to generate a private certificate for api.tutorialsdojo.com. Override the invoke URL using stage variables.
- Request a public certificate in the us-east-2 region for api.tutorialsdojo.com using AWS Certificate Manager (ACM). Create a regional API Gateway domain name and associate it with api.tutorialsdojo.com and the ACM certificate. In Route 53, create an alias record for api.tutorialsdojo.com that points to the API Gateway domain name.
when using regional api gateway, the certificate for the domain name needs to be in the same region.
12
A media company needs to configure an Amazon S3 bucket to serve static assets for the public-facing web application. Which methods ensure that all of the objects uploaded to the S3 bucket can be read publicly all over the Internet? (Select TWO.)
- Grant public read access to the object when uploading it using the S3 Console.
- Configure the cross-origin resource sharing (CORS) of the S3 bucket to allow objects to be publicly accessible from all domains.
- Configure the S3 bucket policy to set all objects to public read.
- Create an IAM role to set the objects inside the S3 bucket to public read.
- Do nothing. Amazon S3 objects are already public by default.
by default, all amazon s3 resources such as buckets, objects, and related subresources are private.
To public all objects in a bucket:
- Unblocking the bucket. -> Configure the S3 bucket policy to set all objects to public read.
- Explicit allows public read -> Using bucket policy.
- Or manually public objects -> Grant public read access to the object when uploading it using the S3 Console.
15
An online survey startup is collecting real estate data in the United States for several years. The startup already has a total of 5 TB of data stored in an Amazon S3 bucket located in the us-east-1 Region. All real estate data must be shared with a European AWS Managed Service Provider (MSP) Partner which also uses Amazon S3 for storage. Due to budget constraints, the startup must keep its data transfer costs in S3 as low as possible and disable anonymous access.
Which solution meets this requirement MOST cost-effectively?
- Enable the Requester Pays feature on the Amazon S3 bucket to lower data transfer costs and disable anonymous access
- Enable Cross-Region Replication(CRR) on the startup’s S3 bucket to automatically copy the S3 content to the partner’s S3 bucket in Europe.
- Enable cross-account access of the startup’s S3 bucket to allow the data downloads and exclusive access from the partner’s AWS account
- Enable S3 Object Lock in governance mode to lower data transfer costs and set a Legal Hold for each object to disable anonymous access
s3 - requester pay
- In general, bucket owners pay for all Amazon S3 storage and data transfer costs that are associated with their bucket.
- With Requester Pays buckets,
- The requester (instead of the bucket owner) pays the cost of the request and the data download from the bucket.
- The bucket owner always pays the cost of storing data.
TUTORIALS DOJO - Practice Exam - Time-mode Set 5
-
Scored: 49/65 (75%)
- SAA – Design Cost-Optimized Architectures: 100%
- SAA – Design High-Performing Architectures: 73.08%
- SAA – Design Resilient Architectures: 75%
- SAA – Design Secure Architectures: 73.91%
-
Time: 00:52:07
-
Date: Oct 23, 2023, 15h
SAA - Design Cost-Optimized Architectures
SAA - Design High-Performing Architectures
1
A Solutions Architect is migrating several Windows-based applications to AWS that require a scalable file system storage for high-performance computing (HPC). The storage service must have full support for the SMB protocol and Windows NTFS, Active Directory (AD) integration, and Distributed File System (DFS).
Which of the following is the MOST suitable storage service that the Architect should use to fulfill this scenario?
- Amazon FSx for Windows File Server
- Amazon S3 Glacier Deep Archive
- AWS DataSync
- Amazon FSx for Lustre
fsx
- FSx for Lustre: Linux, HPC
- FSx for Windows File Server
2
A company has a web application hosted in their on-premises infrastructure that they want to migrate to AWS cloud. Your manager has instructed you to ensure that there is no downtime while the migration process is on-going. In order to achieve this, your team decided to divert 50% of the traffic to the new application in AWS and the other 50% to the application hosted in their on-premises infrastructure. Once the migration is over and the application works with no issues, a full diversion to AWS will be implemented. The company's VPC is connected to its on-premises network via an AWS Direct Connect connection.
Which of the following are the possible solutions that you can implement to satisfy the above requirement? (Select TWO.)
- Use a Network Load balancer with Weighted Target Groups to divert the traffic between the on-premises and AWS-hosted application. Divert 50% of the traffic to the new application in AWS and the other 50% to the application hosted in their on-premises infrastructure.
- Use an Application Elastic Load balancer with Weighted Target Groups to divert and proportion the traffic between the on-premises and AWS-hosted application. Divert 50% of the traffic to the new application in AWS and the other 50% to the application hosted in their on-premises infrastructure.
- Use Route 53 with Failover routing policy to divert and proportion the traffic between the on-premises and AWS-hosted application. Divert 50% of the traffic to the new application in AWS and the other 50% to the application hosted in their on-premises infrastructure.
- Use Route 53 with Weighted routing policy to divert the traffic between the on-premises and AWS-hosted application. Divert 50% of the traffic to the new application in AWS and the other 50% to the application hosted in their on-premises infrastructure.
application load balancer: supports weighted target groups
5
A research institute has developed simulation software that requires significant computational power. Currently, the software runs on a local server with limited resources, taking several hours to complete each simulation. The server has 32 virtual CPUs (vCPUs) and 256 GiB of memory. The institute plans to migrate the software to AWS. Their objective is to speed up the simulations by running them in parallel.
As a Solutions Architect, which solution will achieve this goal with the LEAST operational overhead?
- Utilize AWS Batch to manage the execution of the software.
- Consider using Amazon EC2 Spot Instances to run the simulations.
- Use Lambda functions to process simulation tasks in parallel.
- Run the simulations using AWS Fargate.
aws batch: run batch jobs at any scale
6
A company plans to implement a hybrid architecture. They need to create a dedicated connection from their Amazon Virtual Private Cloud (VPC) to their on-premises network. The connection must provide high bandwidth throughput and a more consistent network experience than Internet-based solutions.
Which of the following can be used to create a private connection between the VPC and the company's on-premises network?
- AWS Direct Connect
- Transit VPC
- Transit Gateway with equal-cost multipath routing (ECMP)
- AWS Site-to-Site VPN
aws direct connect: dedicated network connection to aws
10
A healthcare company manages patient data using a distributed system. The organization utilizes a microservice-based serverless application to handle various aspects of patient care. Data has to be retrieved and written from multiple Amazon DynamoDB tables.
The primary goal is to enable efficient retrieval and writing of data without impacting the baseline performance of the application as well as ensuring seamless access to patient information for healthcare professionals.
Which of the following is the MOST operationally efficient solution?
- Utilize AWS AppSync pipeline resolvers
- Launched AWS Lambda functions with an edge-optimized Amazon API Gateway
- Set up DynamoDB connector for Amazon Athena Federated Query
- Use CloudFront function
aws appsync: accelerate app development with fully-managed, scalable graphql apis
-
AWS AppSync Pipeline Resolver: orchestrating requests to multiple data sources.
Simplify client-side application complexity and help enforce server-side business logic controls by
16
A company has multiple research departments that have deployed several resources to the AWS cloud. The departments are free to provision their own resources as they are needed. To ensure normal operations, the company wants to track its AWS resource usage so that it is not reaching the AWS service quotas unexpectedly.
Which combination of actions should the Solutions Architect implement to meet the company requirements? (Select TWO.)
- Create an Amazon Simple Notification Service (Amazon SNS) topic and configure it as a target for notifications.
- Capture the events using Amazon EventBridge (Amazon CloudWatch Events) and use an Amazon Simple Notification Service (Amazon SNS) topic as the target for notifications.
- Query the AWS Trusted Advisor Service Limits check every 24 hours by calling the DescribeTrustedAdvisorChecks API operation. Ensure that your AWS account has a Developer support plan.
- Write an AWS Lambda function that refreshes the AWS Trusted Advisor Service Limits checks and set it to run every 24 hours.
- Utilize the AWS managed rule on AWS Config to monitor AWS resource service quotas. Schedule this checking using an AWS Lambda function.
**aws trusted advisor**: optimize performance and security
Trusted Advisor inspects your AWS environment and recommends ways to save money, close security gaps, and improve system availability and performance.
- AWS Trusted Advisor Service Limits:
- Monitor the service quotas in all Regions.
- Alerts you if your account reaches more than 80% of a service quota in any Region.
19
A company has multiple AWS Site-to-Site VPN connections placed between their VPCs and their remote network. During peak hours, many employees are experiencing slow connectivity issues, which limits their productivity. The company has asked a solutions architect to scale the throughput of the VPN connections.
Which solution should the architect carry out?
- Associate the VPCs to an Equal Cost Multipath Routing (ECMR)-enabled transit gateway and attach additional VPN tunnels.
- Add more virtual private gateways to a VPC and enable Equal Cost Multipath Routing (ECMR) to get higher VPN bandwidth.
- Modify the VPN configuration by increasing the number of tunnels to scale the throughput.
- Re-route some of the VPN connections to a secondary customer gateway device on the remote network’s end.
aws site-to-site vpn throughput limit: 1.25 gbps
-
Scale VPN with Transit Gateway - Equal Cost Multipath Routing (ECMP).
Establish multiple VPN tunnels to an ECMP-enabled transit gateway
SAA - Design Resilient Architectures
2
A company needs to accelerate the performance of its AI-powered medical diagnostic application by running its machine learning workloads on the edge of telecommunication carriers' 5G networks. The application must be deployed to a Kubernetes cluster and have role-based access control (RBAC) access to IAM users and roles for cluster authentication.
Which of the following should the Solutions Architect implement to ensure single-digit millisecond latency for the application?
- Launch the application to an Amazon Elastic Kubernetes Service (Amazon EKS) cluster. Create node groups in Wavelength Zones for the Amazon EKS cluster via the AWS Wavelength service. Apply the AWS authenticator configuration map (aws-auth ConfigMap) to your cluster.
- Host the application to an Amazon Elastic Kubernetes Service (Amazon EKS) cluster. Set up node groups in AWS Wavelength Zones for the Amazon EKS cluster. Attach the Amazon EKS connector agent role (AmazonECSConnectorAgentRole) to your cluster and use AWS Control Tower for RBAC access.
- Launch the application to an Amazon Elastic Kubernetes Service (Amazon EKS) cluster. Create VPC endpoints for the AWS Wavelength Zones and apply them to the Amazon EKS cluster. Install the AWS IAM Authenticator for Kubernetes (aws-iam-authenticator) to your cluster.
- Host the application to an Amazon EKS cluster and run the Kubernetes pods on AWS Fargate. Create node groups in AWS Wavelength Zones for the Amazon EKS cluster. Add the EKS pod execution IAM role (AmazonEKSFargatePodExecutionRole) to your cluster and ensure that the Fargate profile has the same IAM role as your Amazon EC2 node groups.
aws wavelength: deliver ultra-low latency applications for 5g devices
- Application traffic can reach application servers running in Wavelength Zones without leaving the mobile providers’ network
iam and k8s:
- Enable with AWS IAM Authenticator for Kubernetes, which runs on the Amazon EKS control plane.
- The authenticator gets its configuration information from the aws-auth ConfigMap (AWS authenticator configuration map).
8
A top investment bank is in the process of building a new Forex trading platform. To ensure high availability and scalability, you designed the trading platform to use an Elastic Load Balancer in front of an Auto Scaling group of On-Demand EC2 instances across multiple Availability Zones. For its database tier, you chose to use a single Amazon Aurora instance to take advantage of its distributed, fault-tolerant, and self-healing storage system.
In the event of system failure on the primary database instance, what happens to Amazon Aurora during the failover?
- Amazon Aurora flips the canonical name record (CNAME) for your DB Instance to point at the healthy replica, which in turn is promoted to become the new primary.
- Aurora will attempt to create a new DB Instance in the same Availability Zone as the original instance and is done on a best-effort basis.
- Amazon Aurora flips the A record of your DB Instance to point at the healthy replica, which in turn is promoted to become the new primary.
- Aurora will first attempt to create a new DB Instance in a different Availability Zone of the original instance. If unable to do so, Aurora will attempt to create a new DB Instance in the original Availability Zone in which the instance was first launched.
aurora failover: automatically handled by amazon aurora
-
If you have an Amazon Aurora Replica
Amazon Aurora flips the canonical name record (CNAME) for your DB Instance to point at the healthy replica
-
If you are running Aurora Serverless and the DB instance or AZ becomes unavailable
Aurora will automatically recreate the DB instance in a different AZ.
-
Otherwise:
Aurora will attempt to create a new DB Instance in the same Availability Zone as the original instance.
The replacement is done on a best-effort basis and may not succeed
12
A client is hosting their company website on a cluster of web servers that are behind a public-facing load balancer. The client also uses Amazon Route 53 to manage their public DNS.
How should the client configure the DNS zone apex record to point to the load balancer?###
SAA - Design Secure Architectures
3
An application is hosted on an EC2 instance with multiple EBS Volumes attached and uses Amazon Neptune as its database. To improve data security, you encrypted all of the EBS volumes attached to the instance to protect the confidential data stored in the volumes.
Which of the following statements are true about encrypted Amazon Elastic Block Store volumes? (Select TWO.)
- All data moving between the volume and the instance are encrypted.
- Snapshots are automatically encrypted.
- Snapshots are not automatically encrypted.
- Only the data in the volume is encrypted and not all the data moving between the volume and the instance.
- The volumes created from the encrypted snapshot are not encrypted.
ebs encryption
- Data at rest inside the volume 👈 Encryption at rest
- All data moving between the volume and the instance 👈 Encryption in-transit
- All snapshots created from the volume
- All volumes created from those snapshots
4
A company has a UAT and production EC2 instances running on AWS. They want to ensure that employees who are responsible for the UAT instances don't have access to work on the production instances to minimize security risks.
Which of the following would be the best way to achieve this?
- Launch the UAT and production EC2 instances in separate VPC's connected by VPC peering.
- Provide permissions to the users via the AWS Resource Access Manager (RAM) service to only access EC2 instances that are used for production or development.
- Launch the UAT and production instances in different Availability Zones and use Multi Factor Authentication.
- Define the tags on the UAT and production servers and add a condition to the IAM policy which allows access to specific tags.
best practice to control access to ec2 instances:
- Tag the EC2 instances, to categorize by purpose, owner, or environment…
- Control access using resource tags and IAM policy.
10
A Solutions Architect is working for a fast-growing startup that just started operations during the past 3 months. They currently have an on-premises Active Directory and 10 computers. To save costs in procuring physical workstations, they decided to deploy virtual desktops for their new employees in a virtual private cloud in AWS. The new cloud infrastructure should leverage the existing security controls in AWS but can still communicate with their on-premises network.
Which set of AWS services will the Architect use to meet these requirements?
- AWS Directory Services, VPN connection, and ClassicLink
- AWS Directory Services, VPN connection, and Amazon Workspaces
- AWS Directory Services, VPN connection, and AWS Identity and Access Management
- AWS Directory Services, VPN connection, and Amazon S3
aws workspaces: virtual desktops in the cloud
11
An operations team has an application running on EC2 instances inside two custom VPCs. The VPCs are located in the Ohio and N.Virginia Region respectively. The team wants to transfer data between the instances without traversing the public internet.
Which combination of steps will achieve this? (Select TWO.)
- Set up a VPC peering connection between the VPCs.
- Create an Egress-only Internet Gateway.
- Re-configure the route table’s target and destination of the instances’ subnet.
- Launch a NAT Gateway in the public subnet of each VPC.
- Deploy a VPC endpoint on each region to enable a private connection.
peering vpc - setup
- Create, invite, accept VPC Peering Connection
- Update each VPC’s Route Table to point to IP range of other VPC.
13
A company troubleshoots the operational issues of their cloud architecture by logging the AWS API call history of all AWS resources. The Solutions Architect must implement a solution to quickly identify the most recent changes made to resources in their environment, including creation, modification, and deletion of AWS resources. One of the requirements is that the generated log files should be encrypted to avoid any security issues.
Which of the following is the most suitable approach to implement the encryption?
- Use CloudTrail and configure the destination Amazon Glacier archive to use Server-Side Encryption (SSE).
- Use CloudTrail and configure the destination S3 bucket to use Server-Side Encryption (SSE).
- Use CloudTrail and configure the destination S3 bucket to use Server Side Encryption (SSE) with AES-128 encryption algorithm.
- Use CloudTrail with its default settings.
cloudtrail - encryption
By default, CloudTrail event log files are encrypted using Amazon S3 server-side encryption (SSE)
17
An e-commerce company’s Chief Information Security Officer (CISO) has taken necessary measures to ensure that sensitive customer data is secure in the cloud. However, the company recently discovered that some customer Personally Identifiable Information (PII) was mistakenly uploaded to an S3 bucket.
The company aims to rectify this mistake and prevent any similar incidents from happening again in the future. Additionally, the company would like to be notified if this error occurs again.
As the Solutions Architect, which combination of options should you implement in this scenario? (Select TWO.### )
- Identify sensitive data using Amazon Macie and create an Amazon EventBridge (Amazon CloudWatch Events) rule to capture the SensitiveData event type.
- Set up an Amazon SNS topic as the target for an Amazon EventBridge (Amazon CloudWatch Events) rule that sends notifications when the error occurs again.
- Identify sensitive data using Amazon GuardDuty by creating an Amazon EventBridge (Amazon CloudWatch Events) rule to include the CRITICAL event types from GuardDuty findings.
- Set up an Amazon SQS as the target for an Amazon EventBridge (Amazon CloudWatch Events) rule that sends notifications when the error occurs again.
- Set up an AWS IoT Message Broker as the target for an Amazon EventBridge (Amazon CloudWatch Events) rule that sends notifications when the SensitiveData:S3Object/Personal event occurs again.
s3 - pii:
- Use Amazon Macie to automatically detect sensitive data.
- Then use EventBridge and SNS to send notification.
TUTORIALS DOJO - Practice Exam - Time-mode Set 6
-
Scored: 48/65 (74%)
- SAA – Design Cost-Optimized Architectures: 50%
- SAA – Design High-Performing Architectures: 78.26%
- SAA – Design Resilient Architectures: 72.73%
- SAA – Design Secure Architectures: 75%
-
Time: 00:58:01
-
Date: Oct 23, 2023, 20h
SAA - Design Cost-Optimized Architectures
1
A multinational corporate and investment bank is regularly processing steady workloads of accruals, loan interests, and other critical financial calculations every night from 10 PM to 3 AM on their on-premises data center for their corporate clients. Once the process is done, the results are then uploaded to the Oracle General Ledger which means that the processing should not be delayed or interrupted. The CTO has decided to move its IT infrastructure to AWS to save costs. The company needs to reserve compute capacity in a specific Availability Zone to properly run their workloads.
As the Senior Solutions Architect, how can you implement a cost-effective architecture in AWS for their financial system?
- Use On-Demand EC2 instances which allows you to pay for the instances that you launch and use by the second. Reserve compute capacity in a specific Availability Zone to avoid any interruption.
- Use Regional Reserved Instances to reserve capacity on a specific Availability Zone and lower down the operating cost through its billing discounts.
- Use On-Demand Capacity Reservations, which provide compute capacity that is always available on the specified recurring schedule.
- Use Dedicated Hosts which provide a physical host that is fully dedicated to running your instances, and bring your existing per-socket, per-core, or per-VM software licenses to reduce costs.
ec2 - capacity reservations vs reserved instances
-
(On-demand) Capacity Reservations:
- Reserve compute capacity for your Amazon EC2 instances in a specific Availability Zone for any duration
- Full price
-
Reserve Instances:
- Regional Reserve Instances: Save money
- Zone Reserve Instances: Save money
4
A company plans to use a cloud storage service to temporarily store its log files. The number of files to be stored is still unknown, but it only needs to be kept for 12 hours.
Which of the following is the most cost-effective storage class to use in this scenario?
- Amazon S3 Standard
- Amazon S3 One Zone-IA
- Amazon S3 Standard-IA
- Amazon S3 Glacier Deep Archive
s3 - min storage duration
| Storage Class | Min Storage Duration |
|---|---|
| Standard, Intelligent-Tier | - |
| Standard-IA, One Zone - IA | 30 days |
| Glacier Instant/Flexible Retrieval | 90 days |
| Glacier Deep Archive | 180 days |
SAA - Design High-Performing Architectures
5
A Solutions Architect needs to launch a web application that will be served globally using Amazon CloudFront. The application is hosted in an Amazon EC2 instance which will be configured as the origin server to process and serve dynamic content to its customers.
Which of the following options provides high availability for the application?
- Use Amazon S3 to serve the dynamic content of your web application and configure the S3 bucket to be part of an origin group.
- Launch an Auto Scaling group of EC2 instances and configure it to be part of an origin group.
- Provision two EC2 instances deployed in different Availability Zones and configure them to be part of an origin group.
- Use Lambda@Edge to improve the performance of your web application and ensure high availability. Set the Lambda@Edge functions to be part of an origin group.
cloudfront - origin _failover_
Needs an origin groups with 2 origin:
- a primary origin
- a secondary origin
9
A company requires corporate IT governance and cost oversight of all of its AWS resources across its divisions around the world. Their corporate divisions want to maintain administrative control of the discrete AWS resources they consume and ensure that those resources are separate from other divisions.
Which of the following options will support the autonomy of each corporate division while enabling the corporate IT to maintain governance and cost oversight? (Select TWO.)
- Use AWS Trusted Advisor and AWS Resource Groups Tag Editor
- Enable IAM cross-account access for all corporate IT administrators in each child account.
- Create separate VPCs for each division within the corporate IT AWS account. Launch an AWS Transit Gateway with equal-cost multipath routing (ECMP) and VPN tunnels for intra-VPC communication.
- Use AWS Consolidated Billing by creating AWS Organizations to link the divisions’ accounts to a parent corporate account.
- Create separate Availability Zones for each division within the corporate IT AWS account. Improve communication between the two AZs using the AWS Global Accelerator.
iam cross-account access: delegate access across aws accounts
e.g. 2 accounts for resources:
Productionaccount: For production resourcesDevelopmentaccount: For developments resources
IAM user groups: Developers can
- Always access resources in
Development - From time to time, access resources in
Productionaccount.
16
A company has a fleet of running Spot EC2 instances behind an Application Load Balancer. The incoming traffic comes from various users across multiple AWS regions, and you would like to have the user's session shared among the fleet of instances.
A Solutions Architect is required to set up a distributed session management layer that will provide scalable and shared data storage for the user sessions that supports multithreaded performance. The cache layer must also detect any node failures and replace the failed ones automatically.
Which of the following would be the best choice to meet the requirement while still providing sub-millisecond latency for the users?
elasticache - redis vs memcached
-
Redis: Advance structure, replicas
-
Memcached: Multi-threads, multi-nodes.
17
A Solutions Architect is working for a weather station in Asia with a weather monitoring system that needs to be migrated to AWS. Since the monitoring system requires a low network latency and high network throughput, the Architect decided to launch the EC2 instances to a new cluster placement group. The system was working fine for a couple of weeks, however, when they try to add new instances to the placement group that already has running EC2 instances, they receive an 'insufficient capacity error'.
How will the Architect fix this issue?
- Stop and restart the instances in the Placement Group and then try the launch again.
- Create another Placement Group and launch the new instances in the new group.
- Verify all running instances are of the same size and type and then try the launch again.
- Submit a capacity increase request to AWS as you are initially limited to only 12 instances per Placement Group.
ec2 - placement group - error adding instance 'insufficient capacity error'
- Amazon does not currently have enough available On-Demand capacity on the existing host to fulfill your request.
Workaround: Stop all instances, then start -> Maybe a new host have enough capacity
22
A manufacturing company launched a new type of IoT sensor. The sensor will be used to collect large streams of data records. You need to create a solution that can ingest and analyze the data in real-time with millisecond response times.
Which of the following is the best option that you should implement in this scenario?
- Ingest the data using Amazon Kinesis Data Streams and create an AWS Lambda function to store the data in Amazon Redshift.
- Ingest the data using Amazon Kinesis Data Firehose and create an AWS Lambda function to store the data in Amazon DynamoDB.
- Ingest the data using Amazon Simple Queue Service and create an AWS Lambda function to store the data in Amazon Redshift.
- Ingest the data using Amazon Kinesis Data Streams and create an AWS Lambda function to store the data in Amazon DynamoDB.
latency: redshift vs dynamodb
- Redshift: sub-second (s)
- DynamoDB: millisecond (ms)
SAA - Design Resilient Architectures
6
A company developed a financial analytics web application hosted in a Docker container using MEAN (MongoDB, Express.js, AngularJS, and Node.js) stack. You want to easily port that web application to AWS Cloud which can automatically handle all the tasks such as balancing load, auto-scaling, monitoring, and placing your containers across your cluster.
Which of the following services can be used to fulfill this requirement?
- AWS CloudFormation
- AWS Compute Optimizer
- Amazon Elastic Container Service (Amazon ECS)
- AWS Elastic Beanstalk
elastic beanstalk: run and manage web apps
-
Reduces the operational overhead by taking care of provisioning the needed resources for your application
-
Elastic Beanstalk supports:
- applications developed in Go, Java, .NET, Node.js, PHP, Python, and Ruby
- custom environment with Docker
-
When you deploy your application, Elastic Beanstalk
- builds the selected supported platform version
- provisions one or more AWS resources, such as Amazon EC2 instances, to run your application.
ecs: run highly secure, reliable, and scalable containers
elastic beanstalk vs ecs
-
Elastic Beanstalk:
Automatically handles the details of capacity provisioning, load balancing, scaling, and application health monitoring.
=> Quickly deploy and manage applications in the AWS Cloud without having to learn about the infrastructure that runs those applications
-
ECS:
Need to manually config Service Auto Scaling, Service Load Balancing, and Monitoring with CloudWatch
14
A company is running an on-premises application backed by a 1TB MySQL 8.0 database. A couple of times each month, the production data is fully copied to a staging database at the request of the analytics team. The team can't work on the staging database until the copy is finished, which takes hours.
Throughout this period, the application experiences intermittent downtimes as well. To expedite the process for the analytics team, a solutions architect must redesign the application's architecture in AWS. The application must also be highly resilient to disruptions.
Which combination of actions best satisfies the given set of requirements while being the most cost-effective? (Select TWO)
aurora - clone:
-
Creating a Aurora clone is faster and more space-efficient than physically copying the data using other techniques, such as restoring from a snapshot like you would in Amazon RDS
-
Aurora uses a copy-on-write protocol to create a clone.
aurora - storage:
- Aurora data is stored in the cluster volume, which is a single, virtual volume that uses solid state drives (SSDs)
- A cluster volume consists of copies of the data across three Availability Zones in a single AWS Region.
- The data is automatically replicated across Availability Zones,
- A cluster volume consists of copies of the data across three Availability Zones in a single AWS Region.
18
A cryptocurrency company wants to go global with its international money transfer app. Your project is to make sure that the database of the app is highly available in multiple regions.
What are the benefits of adding Multi-AZ deployments in Amazon RDS? (Select TWO.)
- Provides enhanced database durability in the event of a DB instance component failure or an Availability Zone outage.
- Significantly increases the database performance.
- Creates a primary DB Instance and synchronously replicates the data to a standby instance in a different Availability Zone (AZ) in a different region.
- Increased database availability in the case of system upgrades like OS patching or DB Instance scaling.
- Provides SQL optimization.
rds multi-az failover:
-
Loss of availability in primary Availability Zone
-
Primary DB instance:
- Loss of network connectivity to primary
- Compute unit failure on primary
- Storage failure on primary
-
DB instance scaling or system upgrades:
Applied first on the standby prior then automatic failover
19
A Solutions Architect is managing a three-tier web application that processes credit card payments and online transactions. Static web pages are used on the front-end tier while the application tier contains a single Amazon EC2 instance that handles long-running processes. The data is stored in a MySQL database. The Solutions Architect is instructed to decouple the tiers to create a highly available application.
Which of the following options can satisfy the given requirement?
- Move all the static assets and web pages to Amazon CloudFront. Use Auto Scaling in Amazon EC2 instance. Migrate the database to Amazon RDS with Multi-AZ deployments configuration.
- Move all the static assets, web pages, and the backend application to a larger instance. Use Auto Scaling in Amazon EC2 instance. Migrate the database to Amazon Aurora.
- Move all the static assets to Amazon S3. Set concurrency limit in AWS Lambda to move the application to a serverless architecture. Migrate the database to Amazon DynamoDB.
- Move all the static assets and web pages to Amazon S3. Re-host the application to Amazon Elastic Container Service (Amazon ECS) containers and enable Service Auto Scaling. Migrate the database to Amazon RDS with Multi-AZ deployments configuration.
cloudfront cannot host data, only cache data.
20
A disaster recovery team is planning to back up on-premises records to a local file server share through SMB protocol. To meet the company’s business continuity plan, the team must ensure that a copy of data from 48 hours ago is available for immediate access. Accessing older records with delay is tolerable.
Which should the DR team implement to meet the objective with the LEAST amount of configuration effort?
- Use an AWS Storage File gateway with enough storage to keep data from the last 48 hours. Send the backups to an SMB share mounted as a local disk.
- Create an SMB file share in Amazon FSx for Windows File Server that has enough storage to store all backups. Access the file share from on-premises.
- Mount an Amazon EFS file system on the on-premises client and copy all backups to an NFS share.
- Create an AWS Backup plan to copy data backups to a local SMB share every 48 hours.
aws file gateway - handle writes
-
When a client writes data to a file via File Gateway, that data is first written to the local cache disk on the gateway itself.
- Once the data has been safely persisted to the local cache, only then does the File Gateway acknowledge the write back to the client.
-
From there, File Gateway transfers the data to the S3 bucket asynchronously in the background, optimizing data transfer using multipart parallel uploads, and encrypting data in transit using HTTPS.
21
A website hosted on Amazon ECS container instances loads slowly during peak traffic, affecting its availability. Currently, the container instances are run behind an Application Load Balancer, and CloudWatch alarms are configured to send notifications to the operations team if there is a problem in availability so they can scale out if needed. A solutions architect needs to create an automatic scaling solution when such problems occur.
Which solution could satisfy the requirement? (Select TWO.)
- Create an AWS Auto Scaling policy that scales out an ECS service when the ALB endpoint becomes unreachable.
- Create an AWS Auto Scaling policy that scales out the ECS service when the ALB hits a high CPU utilization.
- Create an AWS Auto Scaling policy that scales out the ECS cluster when the ALB target group’s CPU utilization is too high.
- Create an AWS Auto Scaling policy that scales out the ECS service when the service’s memory utilization is too high.
- Create an AWS Auto Scaling policy that scales out the ECS cluster when the service’s CPU utilization is too high.
ecs auto scaling - metric:
-
ECS Instances (~ K8s Node):
- CPU Utilization
- Disk
- Disk Reads
- Disk Read Operations
- Disk Writes
- Disk Write Operations
- Network
- Network In
- Network Out
- Status Check Failed
- Status Check Failed (Any)
- Status Check Failed (Instance)
- Status Check Failed (System)
-
ECS Service (~ K8s Pod):
- ECSServiceAverageCPUUtilization
- ECSServiceAverageMemoryUtilization
- ALBRequestCountPerTarget
SAA - Design Secure Architectures
2
A company has several websites and hosts its infrastructure on the AWS Cloud. The mission-critical web applications are hosted on fleets of Amazon EC2 instances behind Application Load Balancers. The company uses AWS Certificate Manager (ACM) provided certificate on the ALBs to enable HTTPS access on its websites. The security team wants to get notified 30 days before the expiration of the SSL certificates.
Which of the following can the Solutions Architect implement to meet this request? (Select TWO.)
- Use AWS Config to manually create a rule that checks for certificate expiry on ACM. Create an Amazon EventBridge (Amazon CloudWatch Events) rule to send an alert to an Amazon Simple Notification Service (Amazon SNS) topic when AWS Config flags a resource.
- Create an Amazon EventBridge (Amazon CloudWatch Events) rule that will check AWS Health or ACM expiration events related to ACM certificates. Send an alert notification to an Amazon Simple Notification Service (Amazon SNS) topic when a certificate is going to expire in 30 days.
- Modify all certificates to use the AWS Certificate Manager Private Certificate Authority. Create an Amazon EventBridge (Amazon CloudWatch Events) rule that will check for ACM events that shows certificates expiring within 30 days. Set the target to invoke an AWS Lambda function to send a message to an Amazon SNS topic.
- Utilize AWS Trusted Advisor to check for the ACM certificates that will expire in 30 days. Using this metric, create an Amazon CloudWatch alarm that will send an alert to an AWS Systems Manager OpsItem.
- Create an Amazon EventBridge (Amazon CloudWatch Events) rule and schedule it to run every day to identify the expiring ACM certificates. Configure to rule to check the DaysToExpiry metric of all ACM certificates in Amazon CloudWatch. Send an alert notification to an Amazon Simple Notification Service (Amazon SNS) topic when a certificate is going to expire in 30 days.
monitor expiration of certificates
- Option 1: Use the ACM built-in Certificate Expiration event
- ACM sends daily expiration events for all active certificates (public, private and imported) starting 45 days prior to expiration.
- AWS Health events are generated for ACM certificates that are eligible for renewal.
- Option 2: Use the
DaysToExpirymetric
3
An application is hosted in an Auto Scaling group of EC2 instances and a Microsoft SQL Server on Amazon RDS. There is a requirement that all in-flight data between your web servers and RDS should be secured.
Which of the following options is the MOST suitable solution that you should implement? (Select TWO.)
- Force all connections to your DB instance to use SSL by setting the rds.force_ssl parameter to true. Once done, reboot your DB instance.
- Download the Amazon RDS Root CA certificate. Import the certificate to your servers and configure your application to use SSL to encrypt the connection to RDS.
- Specify the TDE option in an RDS option group that is associated with that DB instance to enable transparent data encryption (TDE).
- Enable the IAM DB authentication in RDS using the AWS Management Console.
- Configure the security groups of your EC2 instances and RDS to only allow traffic to and from port 443.
use secure sockets layer (ssl) to encrypt connections between your client applications and your amazon rds db instances running microsoft sql server.
- Download the Amazon RDS Root CA certificate. Import the certificate to your servers and configure your application to use SSL to encrypt the connection to RDS.
- Force all connections to your DB instance to use SSL by setting the rds.force_ssl parameter to true. Once done, reboot your DB instance.
5
A company is designing a customized text messaging service that targets its mobile app users. As part of its multi-engagement marketing campaign, a company needs to send a one-time confirmation message to all of its subscribers using Short Message Service (SMS). The solutions architect must design the system to allow a subscriber to reply to the SMS messages.
The customer responses must be kept for an entire year for analysis and targeted sale promotions. In addition, the SMS responses must also be collected, processed, and analyzed in near-real-time.
Which solution will meet these requirements with the LEAST operational overhead?
- Create a new topic in Amazon Simple Notification Service (Amazon SNS) and an Amazon Kinesis data stream configured with all its default settings. Send SMS messages using Amazon SNS. Integrate the Kinesis data stream to the SNS topic for data collection, archiving, and analysis.
- Launch a new Amazon Simple Queue Service (Amazon SQS) queue to send out SMS messages. Use AWS Step Functions and AWS Lambda to collect, process, and analyze responses. Store the data to Amazon S3 Glacier Instant Retrieval.
- Create an Amazon Pinpoint journey for the multi-engagement SMS marketing campaign and an Amazon Kinesis Data Stream for analysis. Configure Amazon Pinpoint to send events to the Kinesis data stream for collection, processing, and analysis. Set the retention period of the Kinesis data stream to 365 days.
- Set up an Amazon Connect contact flow to send the confirmation SMS messages to the mobile app users. Deploy an AWS Lambda function to process and analyze the responses. Store the data to Amazon S3 Glacier Flexible Retrieval
amazon pinpoint: multichannel marketing communications
Engage your customers by sending them email, SMS and voice messages, and push notifications.
- send targeted messages (such as promotions and retention campaigns)
- send transactional messages (such as order confirmations and password reset messages)
13
A Solutions Architect created a brand new IAM User with a default setting using AWS CLI. This is intended to be used to send API requests to Amazon S3, DynamoDB, Lambda, and other AWS resources of the company’s cloud infrastructure.
Which of the following must be done to allow the user to make API calls to the AWS resources?
- Do nothing as the IAM User is already capable of sending API calls to your AWS resources.
- Enable Multi-Factor Authentication for the user.
- Assign an IAM Policy to the user to allow it to send API calls.
- Create a set of Access Keys for the user and attach the necessary permissions.
authenticate for making api calls to aws resources
- Long-term credentials: Access key
TUTORIALS DOJO - Practice Exam - Time-mode Set 7 - Bonus
-
Scored: 34/45 (75%)
- SAA – Design Cost-Optimized Architectures: 57.14%
- SAA – Design High-Performing Architectures: 100%
- SAA – Design Resilient Architectures: 75%
- SAA – Design Secure Architectures: 70.59%
-
Time: 00:44:37
-
Date: Oct 24, 2023, 10h
SAA - Design Cost-Optimized Architectures
1
A large corporation has several Windows file servers in various departments within its on-premises data center. To improve its data management and scalability, the corporation has to migrate and integrate its files into an Amazon FSx for Windows File Server file system while keeping the current file permissions intact.
Which of the following solutions will fulfill the company's requirements? (Select TWO.)
- Set up AWS DataSync agents on the corporation's on-premises file servers and schedule DataSync tasks for transferring data to the Amazon FSx for Windows File Server file system.
- Utilize the AWS CLI to copy the file shares from each on-premises file server to an Amazon S3 bucket. Then, schedule AWS DataSync tasks to move the data from S3 to the Amazon FSx for Windows File Server file system
- Extract the drives from the individual file servers and transport them to AWS via the AWS Snowmobile service. Import the file server data into Amazon S3 from Snowmobile. Afterward, configure the AWS DataSync tasks to sync the data from S3 to the Amazon FSx for Windows File Server file system.
- Acquire an AWS Snowcone device, then connect with the on-premises network. Use AWS OpsHub to launch the AWS DataSync agent AMI and activate the agent via the AWS Management Console. Schedule DataSync tasks to transfer the data to the Amazon FSx for Windows File Server file system.
- Order an AWS Snowball Edge Storage Optimized device, link it to the on-premises network, and transfer data using the AWS CLI. Return the device to AWS for data import into Amazon S3. Configure AWS DataSync tasks to migrate the data from S3 to the Amazon FSx for Windows File Server file system
aws datasync: simple, fast, online data transfer
An online data movement and discovery service that simplifies data migration and helps you quickly, easily, and securely transfer your file or object data to, from, and between AWS storage services.
aws opshub: graphical user interface to manage aws snowball devices
3
A FinTech company has been running its compute workload on the AWS Cloud. In order to quickly release the application, the developers have deployed several Amazon EC2 instances, Auto Scaling groups and AWS Lambda functions for the different components of the application stack. After a few weeks of operation, the users are complaining of slow performance in certain components of the application. The QA engineers suspect that the servers are not able to handle the traffic being sent to the application.
Which of the following actions should be taken to verify and resolve the above issue?
- Enable AWS Compute Optimizer to see recommendations on optimal sizing of compute-related resources. Implement changes based on the recommendations.
- Use AWS Trusted Advisor and select the cost optimization category to identify overutilized and underutilized resources. Resize the compute resources based on the recommendations.
- Use AWS Cost Explorer to gather cost information on all compute-related resources. Increase the size of the instances based on how much budget is allowed by the company.
- Use AWS CloudWatch to view performance metrics of the compute resources. Create a CloudWatch dashboard to identify overutilized or underutilized resources.
aws compute optimizer: identify optimal aws compute resources
- Analyzes the configuration and utilization metrics of your AWS resources
- Reports whether your resources are optimal
- Generates optimization recommendations to reduce the cost and improve the performance of your workloads
6
A Solutions Architect needs to ensure that all of the AWS resources in Amazon VPC don’t go beyond their respective service limits. The Architect should prepare a system that provides real-time guidance in provisioning resources that adheres to the AWS best practices.
Which of the following is the MOST appropriate service to use to satisfy this task?
- AWS Cost Explorer
- AWS Budgets
- AWS Trusted Advisor
- Amazon Inspector
aws inspector: continual vulnerability management at scale
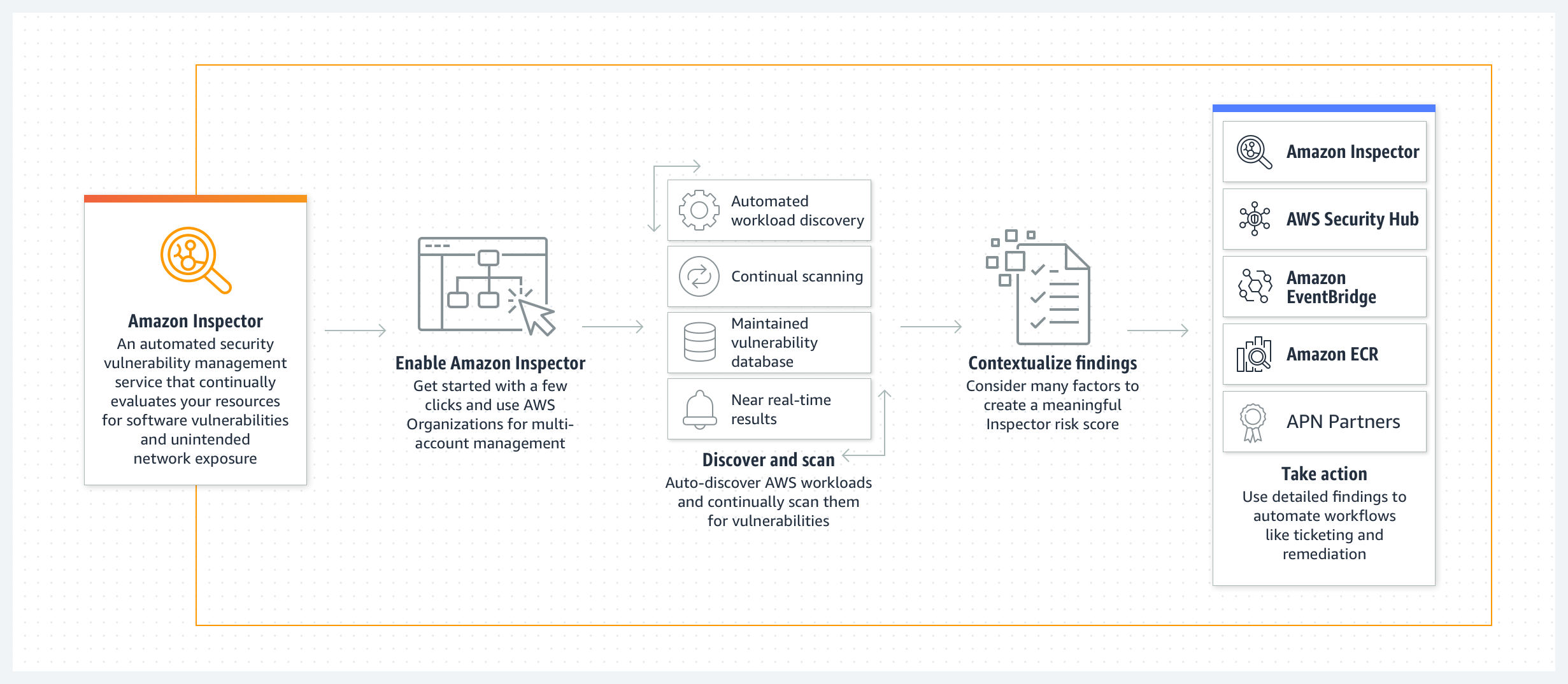
aws trusted advisor: optimize performance and securityimage
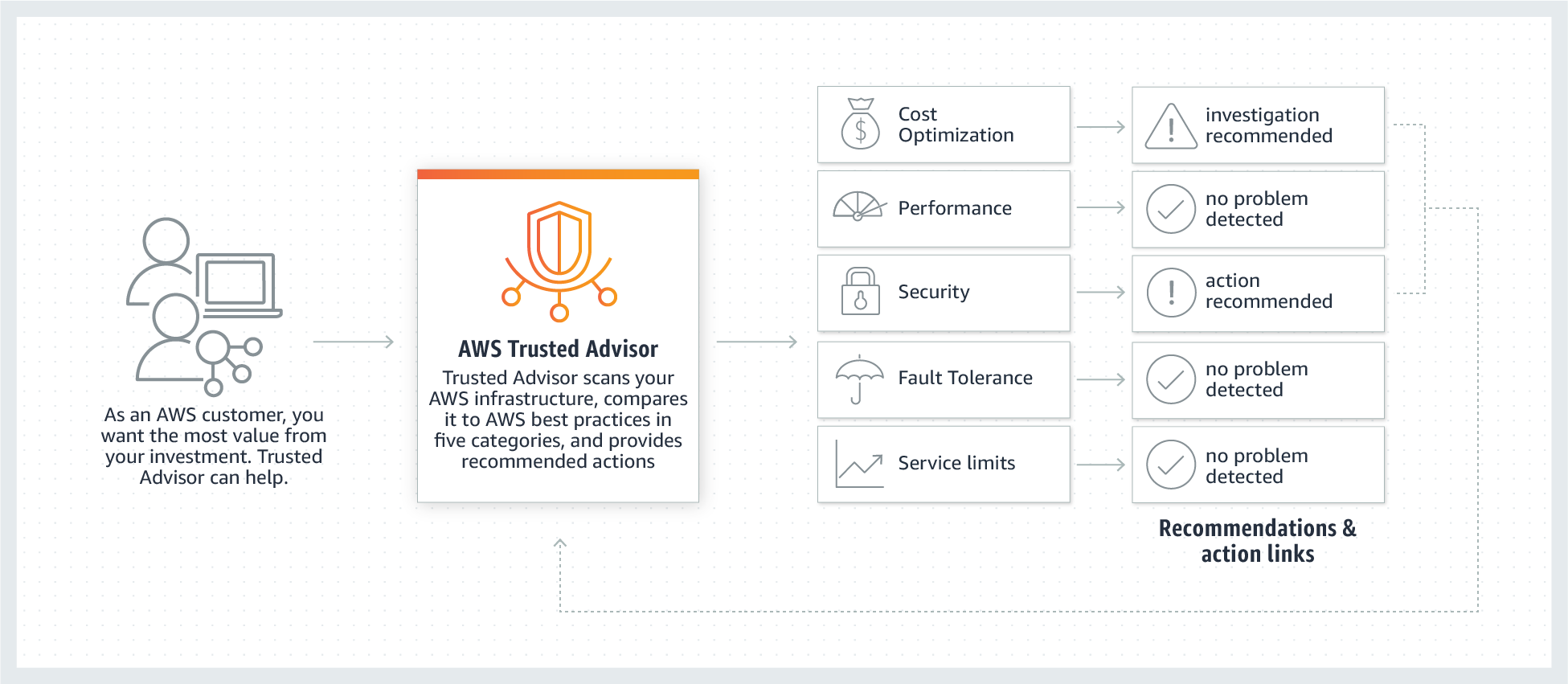
aws budgets: set custom budgets and receive alerts
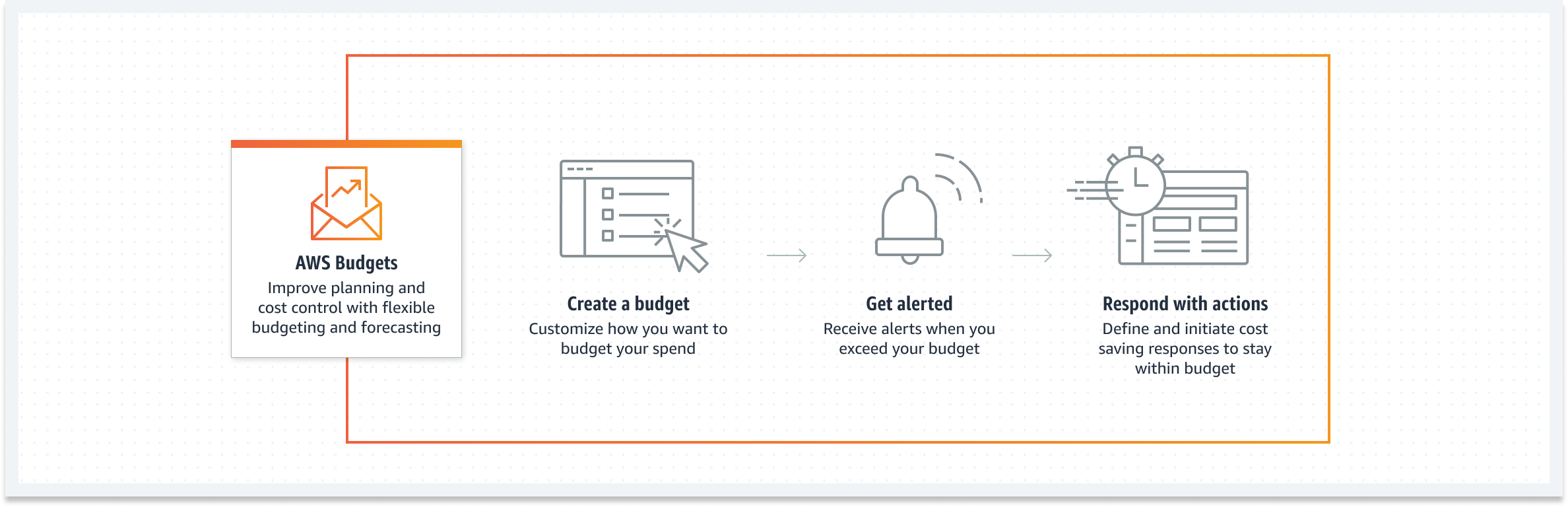
aws cost explorer: visualize and explore your aws costs and usage
SAA - Design High-Performing Architectures
SAA - Design Resilient Architectures
4
A company faces performance degradation due to intermittent traffic spikes in its application. The application is deployed across multiple EC2 instances within an Auto Scaling group and is fronted by a Network Load Balancer (NLB). The operations team found out that HTTP errors are not being detected by the NLB. As a result, clients are continuously routed to unhealthy targets and are never replaced, which impacts the availability of the application.
Which solution could resolve the issue with the least amount of development overhead?
- Use an Application Load Balancer (ALB) in place of the NLB. Enable HTTP health checks using the application's path.
- Increase the NLB's idle timeout to allow more time for requests to be processed, reducing the occurrence of intermittent HTTP/s errors.
- Configure CloudFront as a content delivery network (CDN) in front of the NLB to reduce the load on the instances and improve performance.
- Configure the NLB to perform HTTP health checks on the critical paths of the application.
nlb: only support tcp, udp, tls, but it can perform http/s health check.
6
A company plans to design an application that can handle batch processing of large amounts of financial data. The Solutions Architect is tasked to create two Amazon S3 buckets to store the input and output data. The application will transfer the data between multiple EC2 instances over the network to complete the data processing.
Which of the following options would reduce the data transfer costs?
- Deploy the Amazon EC2 instances behind an Application Load Balancer.
- Deploy the Amazon EC2 instances in the same Availability Zone.
- Deploy the Amazon EC2 instances in the same AWS Region.
- Deploy the Amazon EC2 instances in private subnets in different Availability Zones.
data transfer within the same availability zone is free.
7
An advertising company is currently working on a proof of concept project that automatically provides SEO analytics for its clients. Your company has a VPC in AWS that operates in a dual-stack mode in which IPv4 and IPv6 communication is allowed. You deployed the application to an Auto Scaling group of EC2 instances with an Application Load Balancer in front that evenly distributes the incoming traffic. You are ready to go live but you need to point your domain name (tutorialsdojo.com) to the Application Load Balancer.
In Route 53, which record types will you use to point the DNS name of the Application Load Balancer? (Select TWO.)
- Non-Alias with a type "A" record set
- Alias with a type "AAAA" record set
- Alias with a type "CNAME" record set
- Alias with a type "A" record set
- Alias with a type of “MX” record set
cname record vs route 53 alias record
-
CNAME record: doesn’t work with zone apex (root domain name)
-
Route 53 alias record:
- make CNAME record work with zone apex 👉 can create alias CNAME to point to another domain
- make other record point to domain name
- can point to AWS resources e.g. An alias A Record point to DNS name of a LB
SAA - Design Secure Architectures
3
A serverless application has been launched on the DevOps team’s AWS account. Users from the development team’s account must be granted permission to invoke the Lambda function that runs the application. The solution must use the principle of least privilege access.
Which solution will fulfill these criteria?
- On the function’s resource-based policy, add a permission that includes the lambda:InvokeFunction as action and arn:aws:iam::[DEV AWSAccount Number]:root as principal.
- On the function’s resource-based policy, add a permission that includes the lambda:* as action and arn:aws:iam::[DevOps AWS Account Number]:root as principal.
- On the function’s execution role, add a permission that includes the lambda:* as action and arn:aws:iam::[DevOps AWS Account Number]:root as principal.
- On the function’s execution role, add a permission that includes the lambda:InvokeFunction as action and arn:aws:iam::[DEV AWS Account Number]:root as principal.
permission to invoke a lambda function
Use the Lambda function’s resource policy:
- Principal: the ARN of dev account
- Action: lambda:InvokeFunction
lambda function's `execution role`
Give the Lambda function permissions to access AWS resources.
8
A large electronics company is using Amazon Simple Storage Service to store important documents. For reporting purposes, they want to track and log every request access to their S3 buckets including the requester, bucket name, request time, request action, referrer, turnaround time, and error code information. The solution should also provide more visibility into the object-level operations of the bucket.
Which is the best solution among the following options that can satisfy the requirement?
- Enable AWS CloudTrail to audit all Amazon S3 bucket access.
- Enable server access logging for all required Amazon S3 buckets.
- Enable the Requester Pays option to track access via AWS Billing.
- Enable Amazon S3 Event Notifications for PUT and POST.
cloudtrail logs vs s3 server access logs
- CloudTrail Logs: record of actions taken by a user, role, or an AWS service in Amazon S3
- S3 server access logs: detailed records for the requests that are made to an S3 bucket
- Fields for Object Size, Total Time, Turn-Around Time, and HTTP Referrer for log records
- Lifecycle transitions, expirations, restores
- Invalid Authentication
Ref:
9
A company runs its multitier online shopping platform on AWS. Every new sale transaction is published as a message in an open-source RabbitMQ queue that runs on an Amazon EC2 instance. There is a consumer application is hosted on a separate EC2 instance that consumes the incoming messages, which then stores the transaction in a self-hosted PostgreSQL database on another EC2 instance.
All of the EC2 instances used are in the same Availability Zone in the eu-central-1 Region. A solutions architect needs to redesign its cloud architecture to provide the highest availability with the least amount of operational overhead.
What should a solutions architect do to meet the company’s requirements above?
- Migrate the RabbitMQ queue to Amazon Simple Queue Service (SQS). Rehost the consumer application to an Amazon OpenSearch Service (Amazon Elasticsearch) cluster. Migrate the PostgreSQL database to an Amazon Aurora Serverless cluster
- Migrate the RabbitMQ queue to Amazon MQ to a cluster broker deployment setup. Launch a Multi-AZ Auto Scaling group for the Amazon EC2 instances that host the consumer application. Migrate the existing database to Amazon RDS for PostgreSQL in a Multi-AZ Deployment configuration.
- Migrate the RabbitMQ queue to an Auto Scaling group of EC2 instances. Rehost the consumer application to an Amazon ECS cluster with AWS Fargate. Migrate the PostgreSQL database to Amazon Aurora PostgreSQL using the Aurora cloning feature.
- Migrate the RabbitMQ queue to a redundant pair (active/standby) of Amazon MQ brokers in AWS. Launch a Multi-AZ Auto Scaling group for the Amazon EC2 instances that host the consumer application. Migrate the PostgreSQL database to Amazon RDS for PostgreSQL with cross-Region read replicas
amazon mq:
-
A single-instance broker: is comprised of one broker in one Availability Zone behind a Network Load Balancer (NLB) The broker communicates with your application and with an Amazon EBS storage volume.
-
A cluster deployment: is a logical grouping of three RabbitMQ broker nodes behind a Network Load Balancer, each sharing users, queues, and a distributed state across multiple Availability Zones (AZ).
12
A company has both on-premises data center as well as AWS cloud infrastructure. They store their graphics, audio, videos, and other multimedia assets primarily in their on-premises storage server and use an S3 Standard storage class bucket as a backup. Their data is heavily used for only a week (7 days) but after that period, it will only be infrequently used by their customers. The Solutions Architect is instructed to save storage costs in AWS yet maintain the ability to fetch a subset of their media assets in a matter of minutes for a surprise annual data audit, which will be conducted on their cloud storage.
Which of the following are valid options that the Solutions Architect can implement to meet the above requirement? (Select TWO.)
- Set a lifecycle policy in the bucket to transition the data from Standard storage class to Glacier after one week (7 days).
- Set a lifecycle policy in the bucket to transition the data to S3 - Standard IA storage class after one week (7 days).
- Set a lifecycle policy in the bucket to transition the data to S3 - One Zone-Infrequent Access storage class after one week (7 days).
- Set a lifecycle policy in the bucket to transition the data to S3 Glacier Deep Archive storage class after one week (7 days).
- Set a lifecycle policy in the bucket to transition to S3 - Standard IA after 30 days
s3 standard-ia or s3 one zone-ia:
- Minimum Days for Transition from Standard: 30 days
- Minimum 30-Day Storage Charge: 30 days
17
A well-known music streaming service is planning to broaden its platform globally. However, the company must ensure that listeners in certain countries cannot access specific music content until it is officially launched in their respective regions, in accordance with its music licensing agreements and restrictions.
To achieve this, the company will utilize Amazon CloudFront's content delivery network and Origin Access Control (OAC) feature to prevent unauthorized users from accessing the content. Customized error messages must also be configured for users who are not authorized to access particular music tracks.
What solution would be able to fulfill these requirements?
- Configure CloudFront to return a custom error response to the viewer. Use both signed URLs and signed cookies for secure content access.
- Configure CloudFront to return a custom error response to the viewer. Implement a time-restricted IAM access policy for CloudFront distribution.
- Configure CloudFront to return a custom error response to the viewer. Set up a CloudFront Function URL to control access.
- Configure CloudFront to return a custom error response to the viewer and apply geographic restrictions using an Allow list.
cloudfront supports `geo blocking` (`geographic restrictions`)
Correct answers
33
amazon managed service for prometheus: highly available, secure, and managed monitoring for your containers
Collects metrics
amazon managed grafana: visualize and analyze your operational data at scale
Visualize metrics to dashboard
amazon quantum ledger database (qldb): fully managed ledger database
Provides a transparent, immutable, and cryptographically verifiable transaction log owned by a central trusted authority.
👉 Track all application data changes, and maintain a complete and verifiable history of changes over time.
TUTORIALS DOJO - Practice Exam - Time-mode Set 8 - Final Test
-
Scored: 60/65 (92%)
- SAA - Design Cost-Optimized Architectures: 85.71%
- SAA - Design High-Performing Architectures: 94.12%
- SAA - Design Resilient Architectures: 95.24%
- SAA - Design Secure Architectures: 90%
-
Time: 00:46:52
-
Date: 2023/10/25, 0h
SAA - Design Cost-Optimized Architectures
3
A company is building an internal application that serves as a repository for images uploaded by a couple of users. Whenever a user uploads an image, it would be sent to Kinesis Data Streams for processing before it is stored in an S3 bucket. If the upload was successful, the application will return a prompt informing the user that the operation was successful. The entire processing typically takes about 5 minutes to finish.
Which of the following options will allow you to asynchronously process the request to the application from upload request to Kinesis, S3, and return a reply in the most cost-effective manner?
- Use a combination of Lambda and Step Functions to orchestrate service components and asynchronously process the requests.
- Use a combination of SQS to queue the requests and then asynchronously process them using On-Demand EC2 Instances.
- Replace the Kinesis Data Streams with an Amazon SQS queue. Create a Lambda function that will asynchronously process the requests.
- Use a combination of SNS to buffer the requests and then asynchronously process them using On-Demand EC2 Instances.
asynchronous process, cost-effective
SQS + Lambda
SAA - Design High-Performing Architectures
4
A company has an on-premises MySQL database that needs to be replicated in Amazon S3 as CSV files. The database will eventually be launched to an Amazon Aurora Serverless cluster and be integrated with an RDS Proxy to allow the web applications to pool and share database connections. Once data has been fully copied, the ongoing changes to the on-premises database should be continually streamed into the S3 bucket. The company wants a solution that can be implemented with little management overhead yet still highly secure.
Which ingestion pattern should a solutions architect take?
- Set up a full load replication task using AWS Database Migration Service (AWS DMS). Launch an AWS DMS endpoint with SSL using the AWS Network Firewall service.
- Create a full load and change data capture (CDC) replication task using AWS Database Migration Service (AWS DMS). Add a new Certificate Authority (CA) certificate and create an AWS DMS endpoint with SSL.
- Use an AWS Snowball Edge cluster to migrate data to Amazon S3 and AWS DataSync to capture ongoing changes. Create your own custom AWS KMS envelope encryption key for the associated AWS Snowball Edge job.
- Use AWS Schema Conversion Tool (AWS SCT) to convert MySQL data to CSV files. Set up the AWS Server Migration Service (AWS MGN) to capture ongoing changes from the on-premises MySQL database and send them to Amazon S3.
replicate database on s3 as csv, stream on-going changes, min management overhead
AWS Database Migration Service + Change Data Capture (CDC)
SAA - Design Resilient Architectures
6
An e-commerce company is receiving a large volume of sales data files in .csv format from its external partners on a daily basis. These data files are then stored in an Amazon S3 Bucket for processing and reporting purposes.
The company wants to create an automated solution to convert these .csv files into Apache Parquet format and store the output of the processed files in a new S3 bucket called “tutorialsdojo-data-transformed”. This new solution is meant to enhance the company’s data processing and analytics workloads while keeping its operating costs low.
Which of the following options must be implemented to meet these requirements with the LEAST operational overhead?
- Integrate Amazon EMR File System (EMRFS) with the source S3 bucket to automatically discover the new data files. Use an Amazon EMR Serverless with Apache Spark to convert the .csv files to the Apache Parquet format and then store the output in the "tutorialsdojo-data-transformed" bucket.
- Utilize an AWS Batch job definition with Bash syntax to convert the .csv files to the Apache Parquet format. Configure the job definition to run automatically whenever a new .csv file is uploaded to the source bucket.
- Use Amazon S3 event notifications to trigger an AWS Lambda function that converts .csv files to Apache Parquet format using Apache Spark on an Amazon EMR cluster. Save the processed files to the “tutorialsdojo-data-transformed" bucket.
- Use AWS Glue crawler to automatically discover the raw data file in S3 as well as check its corresponding schema. Create a scheduled ETL job in AWS Glue that will convert .csv files to Apache Parquet format and store the output of the processed files in the “tutorialsdojo-data-transformed" bucket.
csv store in s3, automated convert to parquet -> store in a s3 bucket; min operation cost
- Working Solutions:
- AWS Batch + bash script
- Amazon EMR
amazon emr: hosted hadoop framework
- Amazon EMR Serverless
SAA - Design Secure Architectures
4
A government agency plans to store confidential tax documents on AWS. Due to the sensitive information in the files, the Solutions Architect must restrict the data access requests made to the storage solution to a specific Amazon VPC only. The solution should also prevent the files from being deleted or overwritten to meet the regulatory requirement of having a write-once-read-many (WORM) storage model.
Which combination of the following options should the Architect implement? (Select TWO.)
- Set up a new Amazon S3 bucket to store the tax documents and integrate it with AWS Network Firewall. Configure the Network Firewall to only accept data access requests from a specific Amazon VPC.
- Configure an Amazon S3 Access Point for the S3 bucket to restrict data access to a particular Amazon VPC only.
- Create a new Amazon S3 bucket with the S3 Object Lock feature enabled. Store the documents in the bucket and set the Legal Hold option for object retention.
- Store the tax documents in the Amazon S3 Glacier Instant Retrieval storage class to restrict fast data retrieval to a particular Amazon VPC of your choice.
- Enable Object Lock but disable Object Versioning on the new Amazon S3 bucket to comply with the write-once-read-many (WORM) storage model requirement.
s3 - worm
👉 S3 - Object Lock + Legal Hold
s3 - restrict access to a vpc
👉 S3 Access Point
16
A social media company needs to capture the detailed information of all HTTP requests that went through their public-facing Application Load Balancer every five minutes. The client's IP address and network latencies must also be tracked. They want to use this data for analyzing traffic patterns and for troubleshooting their Docker applications orchestrated by the Amazon ECS Anywhere service.
Which of the following options meets the customer requirements with the LEAST amount of overhead?
- Enable AWS CloudTrail for their Application Load Balancer. Use the AWS CloudTrail Lake to analyze and troubleshoot the application traffic.
- Enable access logs on the Application Load Balancer. Integrate the Amazon ECS cluster with Amazon CloudWatch Application Insights to analyze traffic patterns and simplify troubleshooting.
- Install and run the AWS X-Ray daemon on the Amazon ECS cluster. Use the Amazon CloudWatch ServiceLens to analyze the traffic that goes through the application.
- Integrate Amazon EventBridge (Amazon CloudWatch Events) metrics on the Application Load Balancer to capture the client IP address. Use Amazon CloudWatch Container Insights to analyze traffic patterns.
elb - access logs
Capture detailed information about requests sent to your load balancer
- Disabled by default
Ref:
aws services with access logs:
- S3
- ELB
- CloudFront: or standard logs
- API Gateway
TUTORIALS DOJO - TIPS AND TRICKS
Analytics
Amazon Athena: Query data in Amazon S3 using SQL
athena vs redshift spectrum
SQL query data in S3
- Athena: Serverless, simple query
- Redshift Spectrum: Provision resources, complex query
Amazon EMR: Hosted Hadoop framework
csv store in s3, automated convert to parquet -> store in a s3 bucket; min operation cost
- Working Solutions:
- AWS Batch + bash script
- Amazon EMR
amazon emr: hosted hadoop framework
- Amazon EMR Serverless
AWS Glue: Simple, scalable, and serverless data integration
aws glue
- Serverless ETL
- Glue Job can be triggered manually or via events using EventBridge
aws glue - job bookmarking
- maintain state information and prevent the reprocessing of old data.
Amazon Kinesis: Analyze real-time video and data streams
- kinesis video streams: capture, process, and store video streams for analytics and machine learning.
- Kinesis Data Streams: Build custom applications that analyze data streams using popular stream-processing frameworks.
- Kinesis Data Firehose: Load data streams into AWS data stores.
kinesis data streams vs sqs
- Kinesis Data Streams: Provide real-time analyzing, but required provisioning shards
- SQS: Use with Lambda (and its Event Sourcing) provides a cost-efficient solution
asynchronous process, cost-effective (alternative to kinesis data streams)
SQS + Lambda
AWS Lake Formation: Build a secure data lake in days
Amazon QuickSight: Fast business analytics service
Amazon Redshift: Fast, simple, cost-effective data warehouse service
amazon redshift backup:
- Manually Snapshots
- Automatically increment backup:
- Every 8 hours or 5 GB of data
- 1-day retention (default, configurable up to 35 days)
Backup to S3 bucket, configurable to copy snapshots to another region for DR.
latency: redshift vs dynamodb
- Redshift: sub-second (s)
- DynamoDB: millisecond (ms)
redshift spectrum vs athena
SQL query data in S3
- Redshift Spectrum: Provision resources, complex query
- Athena: Serverless, simple query
Application Integration
Amazon EventBridge: Serverless event bus for SaaS apps and AWS services
Amazon MQ: Managed message broker service
amazon mq:
- A single-instance broker: is comprised of one broker in one Availability Zone behind a Network Load Balancer (NLB) The broker communicates with your application and with an Amazon EBS storage volume.
- A cluster deployment: is a logical grouping of three RabbitMQ broker nodes behind a Network Load Balancer, each sharing users, queues, and a distributed state across multiple Availability Zones (AZ).
Amazon SNS: Pub/sub, SMS, email, and mobile push notifications
Amazon SQS: Managed message queues
AWS Step Functions: Coordination for distributed applications
Amazon SWF: Build applications that coordinate work across distributed components
ensure a queue's messages are not process twice:
- SQS FIFO Queue
- Amazon Simple Workflow Service (Amazon SWF)
Business Applications
Amazon SES: High-scale inbound and outbound email
Amazon Pinpoint: Multichannel marketing communications |
Engage your customers by sending them email, SMS and voice messages, and push notifications.
- send targeted messages (such as promotions and retention campaigns)
- send transactional messages (such as order confirmations and password reset messages)
Cloud Financial Management
AWS Billing and Cost Management: Find features that help you pay your bills and optimize your costs
aws budgets: set custom budgets and receive alerts

aws cost explorer: visualize and explore your aws costs and usage

Compute
AWS Batch: Run batch jobs at any scale
csv store in s3, automated convert to parquet -> store in a s3 bucket; min operation cost
- Working Solutions:
- AWS Batch + bash script
- Amazon EMR
amazon emr: hosted hadoop framework
- Amazon EMR Serverless
Amazon EC2: Create and run virtual servers in the cloud
ec2 - hibernation
- Quickly pausing and resuming the instances, by saving the memory footprint to disk.
- Can only be enable at launch
- Pay as stopped instances:
- No hourly charging
- EBS volume.
- Elastic IP Address.
ec2 states:
- pending
- running 💸
- rebooting
- stopping - stopped (EBS-backed instances)
- hibernate 💸
- shutting-down
- terminated (Terminated Reserver Instances are still billed 💸)
ec2 - reserved instance
Reserved Instance Marketplace: Resell unused Standard Reserved Instances
ec2 - stop instance vs terminate instance
- Stopped: still be billed
- Terminated: not billed
ec2 - instance store:
- Its data will be lost if the EC2 instance is stopped / terminated.
ec2 - elastic ip address and ebs storage won't be effect after an instance is stopped.
security group referencing
When you specify a security group as the source or destination for a rule (of a security group), the rule affects all instances that are associated with the security groups.
eni - ena - efa
-
Elastic Network Interface (ENI): logical networking component in a VPC that represents a virtual network card
-
Elastic Network Adapter (ENA): High Performance Network Interface for Amazon EC2
- Enhanced networking: up to 100 Gbps
- provide traditional IP networking features
-
Elastic Fabric Adapter (EFA): network device to accelerate High Performance Computing (HPC) applications
- support OS-bypass capabilities: allow HPC communicate directly with the EFA device.
fault tolerance: ability of a system to remain in operation even if some of the components used to build the system fail
cloudwatch alarm can stop, terminate, reboot, recover an ec2 instance
monitor ec2:
-
CloudWatch default metric
- CPU utilization from hypervisor
- Disk
- Network
-
CloudWatch Agent:
- Memory
- Sub-resource metrics such as per-CPU core
notify for ec2 instance:
-
All EC2 instances:
- Create an Amazon EventBridge (Amazon CloudWatch Events) rule to check for AWS Personal Health Dashboard events that are related to Amazon EC2 instances.
- To send notifications, set an Amazon SNS topic as a target for the rule.
-
A specific EC2 instance:
Use CloudWatch Alarm and EC2 Action to interact with EC2 instance.
best practice to control access to ec2 instances:
- Tag the EC2 instances, to categorize by purpose, owner, or environment…
- Control access using resource tags and IAM policy.
ec2 - capacity reservations vs reserved instances
-
(On-demand) Capacity Reservations:
- Reserve compute capacity for your Amazon EC2 instances in a specific Availability Zone for any duration
- Full price
-
Reserve Instances:
- Regional Reserve Instances: Save money
- Zone Reserve Instances: Save money
ec2 - placement group - error adding instance 'insufficient capacity error'
- Amazon does not currently have enough available On-Demand capacity on the existing host to fulfill your request.
Workaround: Stop all instances, then start -> Maybe a new host have enough capacity
ec2 auto scaling group's [termination policy](https://docs.aws.amazon.com/autoscaling/ec2/userguide/as-instance-termination.html#default-termination-policy)
- Maximum availability: Kill instance in the AZs with the most instances (and oldest Launch Configuration)
- Keep most updated instance: Kill instance with oldest LC
- Maximum instance usage: Kill the instance closest to billing hour.
- Finally: random.
auto scaling group (asg) policies:
- Manually
- Scheduled
- Dynamic
- Simple
- Stepped
- Target Tracking
- Predictive
[data transfer]
- Data transferred between EC2 & RDS, Redshift, ElastiCache instances, and ENI in the same AZ is free.
- Data transferred directly between EC2 & S3, EBS direct APIs, Glacier, DynamoDB, SES, SQS, Kinesis, ECR, SNS or SimpleDB in the same AWS Region is free.
AWS Elastic Beanstalk: Run and manage web apps
Reduces the operational overhead by taking care of provisioning the needed resources for your application.
elastic beanstalk: run and manage web apps
-
Reduces the operational overhead by taking care of provisioning the needed resources for your application
-
Elastic Beanstalk supports:
- applications developed in Go, Java, .NET, Node.js, PHP, Python, and Ruby
- custom environment with Docker
-
When you deploy your application, Elastic Beanstalk
- builds the selected supported platform version
- provisions one or more AWS resources, such as Amazon EC2 instances, to run your application.
elastic beanstalk vs ecs
-
Elastic Beanstalk:
Automatically handles the details of capacity provisioning, load balancing, scaling, and application health monitoring.
=> Quickly deploy and manage applications in the AWS Cloud without having to learn about the infrastructure that runs those applications
-
ECS:
Need to manually config Service Auto Scaling, Service Load Balancing, and Monitoring with CloudWatch
AWS Lambda: Run code without thinking about servers
allow an lambda permission to use kms:
- Attach the kms:decrypt permission to the Lambda function’s
execution role - Add a statement to the AWS KMS
key policythat grants the function’s execution role the kms:decrypt permission.
permission to invoke a lambda function
Use the Lambda function’s resource policy:
- Principal: the ARN of dev account
- Action: lambda:InvokeFunction
lambda function's `execution role`
Give the Lambda function permissions to access AWS resources.
AWS Wavelength: Deliver ultra-low latency applications for 5G devices
- Application traffic can reach application servers running in Wavelength Zones without leaving the mobile providers’ network
Containers
Amazon ECR: Easily store, manage, and deploy container images
Amazon ECS: Highly secure, reliable, and scalable way to run containers
elastic beanstalk vs ecs
-
Elastic Beanstalk:
Automatically handles the details of capacity provisioning, load balancing, scaling, and application health monitoring.
=> Quickly deploy and manage applications in the AWS Cloud without having to learn about the infrastructure that runs those applications
-
ECS:
Need to manually config Service Auto Scaling, Service Load Balancing, and Monitoring with CloudWatch
ecs auto scaling - metric:
-
ECS Instances (~ K8s Node):
- CPU Utilization
- Disk
- Disk Reads
- Disk Read Operations
- Disk Writes
- Disk Write Operations
- Network
- Network In
- Network Out
- Status Check Failed
- Status Check Failed (Any)
- Status Check Failed (Instance)
- Status Check Failed (System)
-
ECS Service (~ K8s Pod):
- ECSServiceAverageCPUUtilization
- ECSServiceAverageMemoryUtilization
- ALBRequestCountPerTarget
Amazon EKS: Run Kubernetes on AWS without operating your own Kubernetes clusters
iam and k8s:
- Enable with AWS IAM Authenticator for Kubernetes, which runs on the Amazon EKS control plane.
- The authenticator gets its configuration information from the aws-auth ConfigMap (AWS authenticator configuration map).
Cryptography & PKI
AWS Certificate Manager (ACM): Provision, manage, and deploy SSL/TLS certificates
which services support storing ssl certificate?
- AWS Certificate Manager (ACM)
- IAM SSL certificate storage (Used for region that not support ACM)
when using regional api gateway, the certificate for the domain name needs to be in the same region.
monitor expiration of certificates
- Option 1: Use the ACM built-in Certificate Expiration event
- ACM sends daily expiration events for all active certificates (public, private and imported) starting 45 days prior to expiration.
- AWS Health events are generated for ACM certificates that are eligible for renewal.
- Option 2: Use the
DaysToExpirymetric
AWS CloudHSM: Hardware-based key storage for regulatory compliance
AWS KMS: Managed creation and control of encryption keys
k8s has its own mechanism for storing secret, which are default store as plain text in etcd key-value store.
We can apply envelope encryption to encrypt these secrets with AWS KMS before stored them in etcd store.
kms - [custom key store](https://docs.aws.amazon.com/kms/latest/developerguide/custom-key-store-overview.html)
-> We own and manage
allow an lambda permission to use kms:
- Attach the kms:decrypt permission to the Lambda function’s
execution role - Add a statement to the AWS KMS
key policythat grants the function’s execution role the kms:decrypt permission.
s3 object encryption:
-
Server-Side Encryption (SSE):
- SSE-S3 (Amazon S3 managed keys)
- SSE-KMS (AWS KMS)
- SSE-C (Customer-provided keys)
-
Client-Side Encryption (CSE):
- CSE-KMS-CMK
- CSE-Client Master key
| Encryption | Fullname | Who Manages Key? | Who Manages Encryption Process? | Notes |
|---|---|---|---|---|
| SSE-S3 | SSE with Amazon S3 managed keys | S3 | S3 | Default |
| SSE-KMS | SSE with AWS KMS keys | AWS managed key | S3 | Support audit keys usage… |
| Customer managed key (CMK) - Renamed to KMS Key | ||||
| SSE-C | SSE with Customer-Provided Key | Customer | S3 | Use your own encryption key |
| CSE | Customer | Customer |
Database
Amazon Aurora: High performance managed relational database engine
aurora auto scaling vs aurora serverless
- Aurora Auto Scaling: Dynamically adjusts the number of Aurora Replicas (reader DB instances) provisioned for an Aurora DB cluster.
- Aurora Serverless: On-demand, autoscaling the capacity of Aurora DB cluster resource
aurora serverless
- The DB instance cannot be changed from Provisioned to Serverless after created.
- After the DB instanced is created, need to use AWS Database Migration Service (AWS DMS) to migrate data from the existing DB cluster to a new Aurora Serverless database.
aurora custom endpoint: provides load-balanced database connections based on criteria other than the read-only or read-write capability of the db instances
aurora - reader endpoint:
- A reader endpoint for an Aurora DB cluster provides load-balancing support for read-only connections to the DB cluster
aurora failover: automatically handled by amazon aurora
-
If you have an Amazon Aurora Replica
Amazon Aurora flips the canonical name record (CNAME) for your DB Instance to point at the healthy replica
-
If you are running Aurora Serverless and the DB instance or AZ becomes unavailable
Aurora will automatically recreate the DB instance in a different AZ.
-
Otherwise:
Aurora will attempt to create a new DB Instance in the same Availability Zone as the original instance.
The replacement is done on a best-effort basis and may not succeed
aurora - clone:
- Creating a Aurora clone is faster and more space-efficient than physically copying the data using other techniques, such as restoring from a snapshot like you would in Amazon RDS
- Aurora uses a copy-on-write protocol to create a clone.
aurora - storage:
- Aurora data is stored in the cluster volume, which is a single, virtual volume that uses solid state drives (SSDs)
- A cluster volume consists of copies of the data across three Availability Zones in a single AWS Region.
- The data is automatically replicated across Availability Zones,
- A cluster volume consists of copies of the data across three Availability Zones in a single AWS Region.
Amazon DynamoDB: Managed NoSQL database
latency: redshift vs dynamodb
- Redshift: sub-second (s)
- DynamoDB: millisecond (ms)
Amazon ElastiCache: In-memory caching service
elasticache - redis vs memcached
- Redis: Advance structure, replicas
- Memcached: Multi-threads, multi-nodes.
Amazon Quantum Ledger Database - QLDB: Fully managed ledger database
Provides a transparent, immutable, and cryptographically verifiable transaction log owned by a central trusted authority.
👉 Track all application data changes, and maintain a complete and verifiable history of changes over time.
Amazon RDS: Set up, operate, and scale a relational database in the cloud
rds enhanced monitoring
- CloudWatch gathers metrics about CPU utilization from the hypervisor for a DB instance
- Enhanced Monitoring gathers its metrics from an agent on the instance ~ EC2 CloudWatch Agent
monitor rds:
-
Default metric
- CPU utilization from hypervisor
- Database connections
- Free memory
-
Enhanced Monitoring:
- OS processes
- RDS processes
rds - [iam db authentication](https://docs.aws.amazon.com/amazonrds/latest/userguide/usingwithrds.iamdbauth.html)
To connect to DB instance, we’ll use an authentication token (generated using the IAM role’s credential).
rds - “too many connections”
RDS Proxy: allow your applications to pool and share database connections to improve their ability to scale.
rds multi-az failover:
-
Loss of availability in primary Availability Zone
-
Primary DB instance:
- Loss of network connectivity to primary
- Compute unit failure on primary
- Storage failure on primary
-
DB instance scaling or system upgrades:
Applied first on the standby prior then automatic failover
use secure sockets layer (ssl) to encrypt connections between your client applications and your amazon rds db instances running microsoft sql server.
- Download the Amazon RDS Root CA certificate. Import the certificate to your servers and configure your application to use SSL to encrypt the connection to RDS.
- Force all connections to your DB instance to use SSL by setting the rds.force_ssl parameter to true. Once done, reboot your DB instance.
Front-End Web & Mobile
AWS AppSync: Accelerate app development with fully-managed, scalable GraphQL APIs
aws appsync pipeline resolver: orchestrating requests to multiple data sources.
Simplify client-side application complexity and help enforce server-side business logic controls by
Machine Learning
Amazon Comprehend: Discover insights and relationships in text
Amazon Comprehend Medical: Detect and return useful information in unstructured clinical text
AWS Deep Learning AMI: Deep learning on Amazon EC2
Amazon Forecast: Increase forecast accuracy using machine learning
Amazon Fraud Detector: Detect more online fraud faster
Amazon Kendra: Reinvent enterprise search with ML
Amazon Lex: Build voice and text chatbots
Amazon Polly: Turn text into life-like speech
Amazon Rekognition: Analyze image and video
Amazon SageMaker: Build, train, and deploy machine learning models at scale
Amazon Textract: Extract text and data from documents
Amazon Transcribe: Automatic speech recognition
Amazon Translate: Natural and fluent language translation
Management & Governance
Auto Scaling: Scale multiple resources to meet demand
AWS CloudFormation: Create and manage resources with templates
cloudformation: creationpolicy & cfn-signal
- CreationPolicy: Wait on resource configuration actions before stack creation proceeds.
- cfn-signal: Signals CloudFormation to indicate whether Amazon EC2 instances have been successfully created/updated
AWS CloudTrail: Track and monitor activities by users, roles, or AWS services
cloudtrail - encryption
By default, CloudTrail event log files are encrypted using Amazon S3 server-side encryption (SSE)
cloudtrail logs vs s3 server access logs
- CloudTrail Logs: record of actions taken by a user, role, or an AWS service in Amazon S3
- S3 server access logs: detailed records for the requests that are made to an S3 bucket
- Fields for Object Size, Total Time, Turn-Around Time, and HTTP Referrer for log records
- Lifecycle transitions, expirations, restores
- Invalid Authentication
Amazon CloudWatch: Monitor resources and applications
cloudwatch alarm can stop, terminate, reboot, recover an ec2 instance
monitor ec2:
-
CloudWatch default metric
- CPU utilization from hypervisor
- Disk
- Network
-
CloudWatch Agent:
- Memory
- Sub-resource metrics such as per-CPU core
monitor rds:
-
Default metric
- CPU utilization from hypervisor
- Database connections
- Free memory
-
Enhanced Monitoring:
- OS processes
- RDS processes
monitor expiration of certificates
- Option 1: Use the ACM built-in Certificate Expiration event
- ACM sends daily expiration events for all active certificates (public, private and imported) starting 45 days prior to expiration.
- AWS Health events are generated for ACM certificates that are eligible for renewal.
- Option 2: Use the
DaysToExpirymetric
AWS CLI: Command line interface tool to manage AWS services
AWS Compute Optimizer: Identify optimal AWS compute resources |
- analyzes the configuration and utilization metrics of your aws resources
- Reports whether your resources are optimal
- Generates optimization recommendations to reduce the cost and improve the performance of your workloads
AWS Config: Track and evaluate configuration changes
AWS Control Tower: Set up and govern a secure, compliant multi-account environment
Amazon Data Lifecycle Manager: Automate management of Amazon EBS snapshots and Amazon EBS-backed AMIs
AWS Health: Find information about events that can affect your AWS resources
AWS License Manager: Track and manage software licenses across multiple AWS Regions
Amazon Managed Grafana: Visualize and analyze your operational data at scale
Visualize metrics to dashboard
Amazon Managed Service for Prometheus: Highly available, secure, and managed monitoring for your containers
Collects metrics
AWS Management Console: Web-based user interface comprising multiple AWS service consoles
AWS Organizations: Central governance and management across AWS accounts
service control policy (scp): a feature of aws organizations
- A type of organization policy that you can use to manage permissions in your organization.
AWS Proton: Automate management for container and serverless deployments
AWS Systems Manager: Gain operational insights and take action
aws systems manager's fleet manager: ui for managing nodes/ec2 instance.
Tag Editor: Add, edit, or delete tags on multiple AWS resources
AWS Trusted Advisor: Optimize performance and security

Inspects your AWS environment and recommends ways to save money, close security gaps, and improve system availability and performance.
**aws trusted advisor** _service limits_:
- Monitor the service quotas in all Regions.
- Alerts you if your account reaches more than 80% of a service quota in any Region.
AWS Well-Architected Tool: Review and improve your workloads
CloudWatch
cloudwatch - cloudwatch logs - cloudtrail - cloudwatch events - eventbridge?
-
CloudWatch: Monitor resources and applications
Monitor your AWS resources and the applications you run on AWS in real time.
- CloudWatch Logs: Monitor, store, and access your log files from Amazon Elastic Compute Cloud instances, AWS CloudTrail, or other sources.
- CloudWatch Logs Insights: query logs with SQL-like syntax
- CLoudWatch Events: Is now Amazon EventBridge
CloudTrail
- cloudtrail: track and monitor activities by users, roles, or aws services
Migration & Transfer
AWS Application Discovery Service: Discover on-premises applications to streamline migration
AWS Application Migration Service: Automate application migration and modernization
AWS Database Migration Service: Migrate databases with minimal downtime
Migrate on-premises databases to the AWS Cloud.
replicate database on s3 as csv, stream on-going changes, min management overhead
AWS Database Migration Service + Change Data Capture (CDC)
AWS DataSync: Simple, fast, online data transfer
An online data movement and discovery service that simplifies data migration and helps you quickly, easily, and securely transfer your file or object data to, from, and between AWS storage services.
AWS Schema Conversion Tool: Convert source schema and most code to target-compatible format
Networking & Content Delivery
Amazon API Gateway: Build, deploy, and manage APIs
api gateway works at any scale, just pay money.
Throttle API requests for our budget (and for better throughtput)
when using regional api gateway, the certificate for the domain name needs to be in the same region.
Amazon CloudFront: Global content delivery network
cloudfront supports `geo blocking` (`geographic restrictions`)
lambda@edge: run lambda functions to customize the content that cloudfront delivers
cloudfront - origin _failover_
Needs an origin groups with 2 origin:
- a primary origin
- a secondary origin
cloudfront cannot host data, only cache data.
AWS Direct Connect: Dedicated network connection to AWS
from your on-premises network
Elastic Load Balancing: Distribute incoming traffic across multiple targets
elastic load balancer protocol:
- Application Load Balancer: HTTP/s and gRPC
- Network Load Balancer: TCP, UDP, TLS
- Gateway Load Balancer: IP
application load balancer: supports weighted target groups
nlb: only support tcp, udp, tls, but it can perform http/s health check.
elb - access logs
Capture detailed information about requests sent to your load balancer
- Disabled by default
Ref:
aws services with access logs:
- S3
- ELB
- CloudFront: or standard logs
- API Gateway
AWS Global Accelerator: Improve global application availability and performance
Improve application availability, performance, and security using the AWS global network
What is it?
A service in which you create accelerators to improve the performance of your applications for local and global users
How it works?
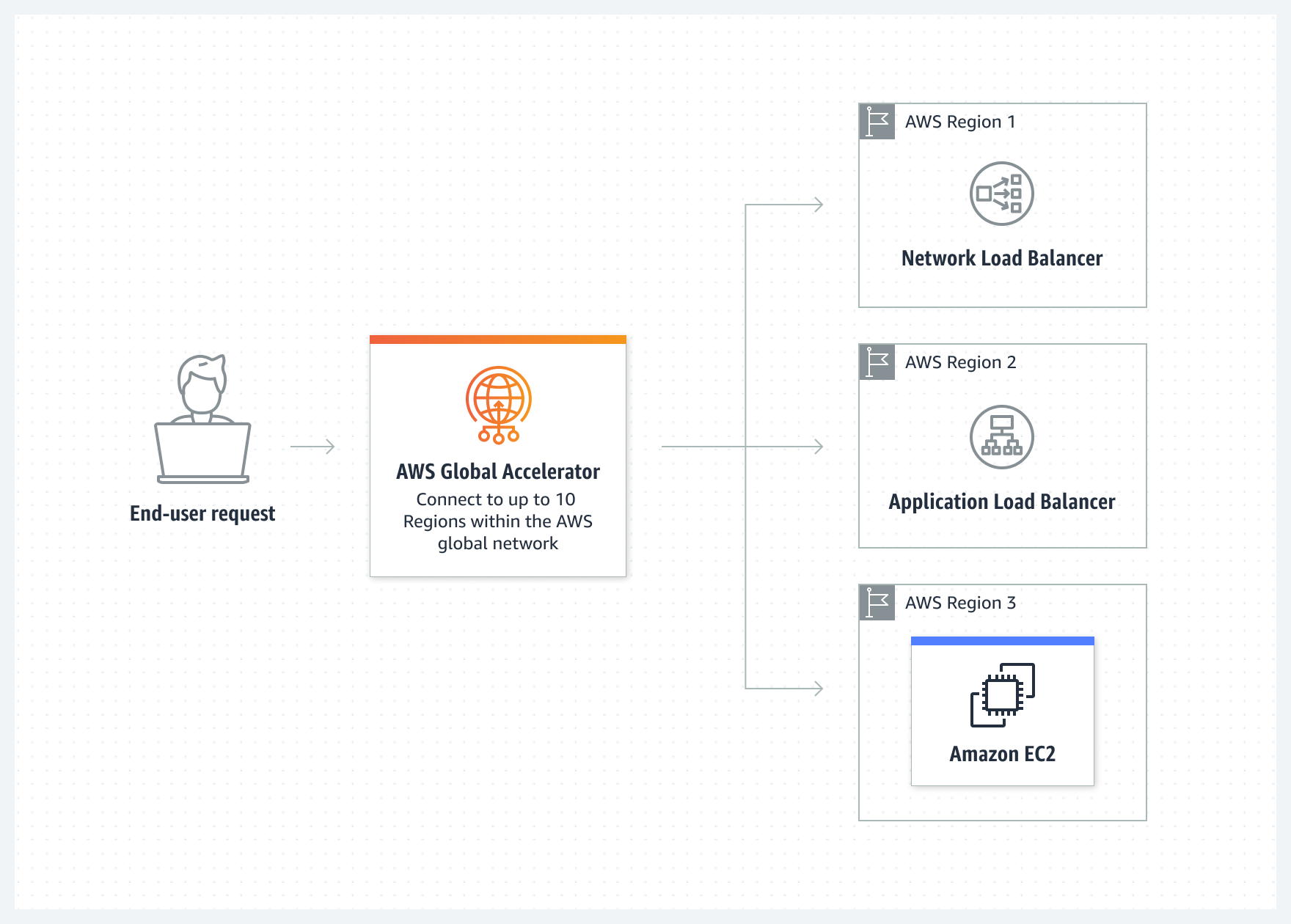
Why use it?
- Take advantage of AWS Global Infrastructure to onboard your user traffic at one of the Global Accelerator edge locations.
- Users can access your application endpoints through static IP addresses to enjoy deterministic routing independent of DNS.
Use cases
-
Global traffic manager Use traffic dials to route traffic to the nearest Region or achieve fast failover across Regions.
-
API acceleration Accelerate API workloads by up to 60%, leveraging TCP termination at the edge.
-
Global static IP Simplify allowlisting in enterprise firewalling and IoT use cases.
-
Low-latency gaming and media workloads Use custom routing to deterministically route traffic to a fleet of EC2 instances.
Related Services
global accelerator & elb
global accelerator vs cloudfront
Notes
Amazon Route 53: Highly available and scalable Domain Name System (DNS) web service
route 53: geoproximity routing vs geolocation routing vs latency-based routing
- Geolocation Routing: Location of user
- GeoProximity Routing: Location of user AND AWS resources (with bias)
- Latency-based Routing
cname record vs route 53 alias record
- CNAME record: doesn’t work with zone apex (root domain name)
- Route 53 alias record:
- make CNAME record work with zone apex 👉 can create alias CNAME to point to another domain
- make other record point to domain name
- can point to AWS resources e.g. An alias A Record point to DNS name of a LB
Amazon VPC: Isolated cloud resources
data transfer
- S3: within the same Region is free.
- Others (EC2) within the same Availability Zone is free.
vpc peering: only works for vpcs, doesn't work with on-premise networks
vpc peering - setup
- Create, invite, accept VPC Peering Connection
- Update each VPC’s Route Table to point to IP range of other VPC.
vpc: ipv4 vs ipv6
- IPv4 is the default IP addressing system for VPC => Cannot be disabled
- IPv6: optional
vpc supports cidr blocks from /16 to /28
cidr `/0`: the entire network -> is not used in sg and nacl.
CIDR /32: One IP address.
vpc endpoints for s3: provide _private_ access to aws public services (s3)
-
Gateway endpoint:
- via Route Table’s Prefix List, without IGW, NATGW, PrivateLink
- Free
-
Interface endpoint:
-
via DNS using Private IP Address 👉 more features
- access from on-premises
- access from VPC in another AWS Region (using VPC Peering, Transit Gateway)
-
Billed 💸
-
vpc - nacl:
- The client that initiates the request chooses the ephemeral port range.
- In practice, to cover the different types of clients that might initiate traffic to public-facing instances in your VPC, you can open ephemeral ports 1024-65535.
To turn on the connection to a service running on an instance, the associated network ACL must allow the following:
- Inbound traffic on the port that the service is listening on
- Outbound traffic to ephemeral ports
eni - ena - efa
-
Elastic Network Interface (ENI): logical networking component in a VPC that represents a virtual network card
-
Elastic Network Adapter (ENA): High Performance Network Interface for Amazon EC2
- Enhanced networking: up to 100 Gbps
- provide traditional IP networking features
-
Elastic Fabric Adapter (EFA): network device to accelerate High Performance Computing (HPC) applications
- support OS-bypass capabilities: allow HPC communicate directly with the EFA device.
security group referencing
When you specify a security group as the source or destination for a rule (of a security group), the rule affects all instances that are associated with the security groups.
default nacl allows all inbound and outbound traffic
s3 - restrict access to a vpc
👉 S3 Access Point
AWS VPN: Securely access your network resources
By establishing a secure and private tunnel from your network or device to the AWS Cloud.)
- aws site-to-site vpn: aws managed vpn services
- AWS Client VPN: client-based managed VPN service
aws site-to-site vpn throughput limit: 1.25 gbps
-
Scale VPN with Transit Gateway - Equal Cost Multipath Routing (ECMP).
Establish multiple VPN tunnels to an ECMP-enabled transit gateway
Security, Identity, & Compliance
AWS Artifact: On-demand access to AWS compliance reports
Reports
Amazon Cognito: Identity management for your apps
- Customer already has Active Directory Service -> No need to use Amazon Cognito -> use AWS IAM Identity Center with the Active Director Connector
AWS Directory Service: Set up and run Microsoft Active Directory with AWS services
AWS Firewall Manager: Deploy network security across your VPCs with just a few clicks
Simplifies your AWS WAF administration and maintenance tasks across multiple accounts and resources
Amazon GuardDuty: Managed threat detection service
Identify unexpected and potentially unauthorized or malicious activity in your AWS environment.
block sql injection
- AWS Web Application Firewall (WAF): can block SQL injection.
- GuardDuty: only detect SQL injection, not block.
AWS Identity and Access Management - IAM: Securely manage access to services and resources
authenticate for making api calls to aws resources
- Long-term credentials: Access key
[identity federation (with saml)](https://docs.aws.amazon.com/singlesignon/latest/userguide/samlfederationconcept.html): pass information about a user between
- a SAML authority (called an identity provider or IdP)
- a SAML consumer (called a service provider or SP)
iam identity provider (idp): manage user identities outside of aws and give these external user identities permissions to use aws resources in your account.
- Setup Identity Provider and Identity Federation.
- Setup an AWS Security Token Service to generate temporary tokens (STS supports SAML)
- Configure an IAM role and an IAM Policy to access the bucket.
iam group
- Cannot attach an IAM Role to an IAM Group.
which services support storing ssl certificate?
- AWS Certificate Manager (ACM)
- IAM SSL certificate storage (Used for region that not support ACM)
iam and eks:
- Enable with AWS IAM Authenticator for Kubernetes, which runs on the Amazon EKS control plane.
- The authenticator gets its configuration information from the aws-auth ConfigMap (AWS authenticator configuration map).
iam cross-account access: delegate access across aws accounts
e.g. 2 accounts for resources:
Productionaccount: For production resourcesDevelopmentaccount: For developments resources
IAM user groups: Developers can
- Always access resources in
Development - From time to time, access resources in
Productionaccount.
AWS IAM Identity Center: Manage single sign-on access to AWS accounts and apps
Amazon Inspector: Automated and continual vulnerability management at scale
EC2, ECR, Lambda

Amazon Macie: Discover and protect your sensitive data at scale
S3
AWS Network Firewall: Deploy network security across your Amazon VPCs with just a few clicks
A stateful, managed, network firewall and intrusion detection and prevention service for your virtual private cloud (VPC).
Traffic from VPC need to be routed to Network Firewall through the firewall endpoints.
AWS Resource Access Manager: Simple, secure service to share AWS resources
AWS Secrets Manager: Rotate, manage, and retrieve secrets
AWS Security Hub: Unified security and compliance center |
Dashboard / Overview
AWS Shield: DDoS protection
AWS WAF: Filter malicious web traffic
XSS, SQL-injection
[aws waf, aws shield, and aws firewall manager](https://docs.aws.amazon.com/waf/latest/developerguide/what-is-aws-waf.html): used together to create a comprehensive security solution
-
AWS WAF: Protect your web applications from common exploits
- Monitor web requests that your end users send to your applications and to control access to your content.
- Used for API Gateway, Load Balancer, Cloudfront.
- Block SQL injection, XSS (cross-site scripting)
- Can minimize the effects of a DDOS attack
-
AWS Shield: Managed DDoS protection
- Provides protection against distributed denial of service (DDoS) attacks for AWS resources, at the network and transport layers (layer 3 and 4) and the application layer (layer 7)
- Can use for more services: EC2, Route53
- Shield Standard: Free, L3-L4
- Shield Advanced: Cost money, L7
-
AWS Firewall Manager: Centrally configure and manage firewall rules across your accounts
Provides management of protections like AWS WAF and Shield Advanced across accounts and resources, even as new resources are added.
Serverless
Amazon API Gateway: Build, deploy, and manage APIs
AWS AppSync: Accelerate app development with fully-managed, scalable GraphQL APIs
Amazon DynamoDB: Managed NoSQL database
Amazon EventBridge: Serverless event bus for SaaS apps and AWS services
AWS Fargate: Serverless compute for containers
aws fargate: serverless compute for containers
By default, Fargate tasks are given a minimum of 20 GiB of free ephemeral storage
AWS Lambda: Run code without thinking about servers
Amazon S3: Object storage built to retrieve any amount of data from anywhere
Amazon SNS: Pub/sub, SMS, email, and mobile push notifications
AWS Step Functions: Coordinate components for distributed applications
Amazon SQS: Managed message queues
ensure a queue's messages are not process twice:
- SQS FIFO Queue
- Amazon Simple Workflow Service (Amazon SWF)
asynchronous process, cost-effective
SQS + Lambda
Storage
AWS Backup: Centralized backup across AWS services
Amazon EBS: Amazon EC2 block storage volumes
ebs is not suitable for archiving datasets -> s3 is better option
ebs - backup: use amazon data lifecycle manager (amazon dlm)
raid 0:
- I/O is distributed across the volumes in a stripe
- higher level of performance for a file system than you can provision on a single Amazon EBS volume
RAID 1, 2, 3, 4, 5, 6: NOT recommended for EBS
ebs encryption
- Data at rest inside the volume 👈 Encryption at rest
- All data moving between the volume and the instance 👈 Encryption in-transit
- All snapshots created from the volume
- All volumes created from those snapshots
Amazon EFS: Fully managed file system for Amazon EC2
efs vs storage gateway
- EFS: files are stored on AWS -> high-latency
- Storage Gateway - File: low-latency
Amazon FSx: Launch, run, and scale feature-rich and high-performing file systems
fsx
- FSx for Lustre: Linux, HPC
- FSx for Windows File Server
Amazon S3: Object storage built to retrieve any amount of data from anywhere
kms-managed cmk: key will be sent to aws
Server-side encryption: unencrypted data will be sent to AWS
-> Client-side encryption with a client-side master key.
s3 object lock
-
Retention:
-
Retention Mode:
- Governance: Big Brother can by pass it.
- Compliance: It’s universe law, nobody can do anything
-
Retention Period: A fixed period of time during which an object remains locked
-
-
Legal holds: ~ Retention Periods but has no expiration date
s3 static website - custom domain: "the s3 bucket name must be the same as the domain name"
What if someone use my domain name for their bucket ??? TODO
s3 - read data from glacier
- Bulk: Lowest (5-12 hours), cheapest
- Standard: 3-5 hours
- Expedited: Fastest (1-5 mins)
- Buy Provisioned capacity to ensure Expedited retrievals is available.
s3 object encryption:
-
Server-Side Encryption (SSE):
- SSE-S3 (Amazon S3 managed keys)
- SSE-KMS (AWS KMS)
- SSE-C (Customer-provided keys)
-
Client-Side Encryption (CSE):
- CSE-KMS-CMK
- CSE-Client Master key
by default, all amazon s3 resources such as buckets, objects, and related subresources are private.
To public all objects in a bucket:
- Unblocking the bucket. -> Configure the S3 bucket policy to set all objects to public read.
- Explicit allows public read -> Using bucket policy.
- Or manually public objects -> Grant public read access to the object when uploading it using the S3 Console.
vpc endpoints for s3: provide _private_ access to aws public services (s3)
-
Gateway endpoint:
- via Route Table’s Prefix List, without IGW, NATGW, PrivateLink
- Free
-
Interface endpoint:
-
via DNS using Private IP Address 👉 more features
- access from on-premises
- access from VPC in another AWS Region (using VPC Peering, Transit Gateway)
-
Billed 💸
-
s3 select: filter objects with sql syntax using bucket name & object key
s3 - requester pay
- In general, bucket owners pay for all Amazon S3 storage and data transfer costs that are associated with their bucket.
- With Requester Pays buckets,
- The requester (instead of the bucket owner) pays the cost of the request and the data download from the bucket.
- The bucket owner always pays the cost of storing data.
s3 - pii:
- Use Amazon Macie to automatically detect sensitive data.
- Then use EventBridge and SNS to send notification.
s3 - min storage duration
| Storage Class | Min Storage Duration |
|---|---|
| Standard, Intelligent-Tier | - |
| Standard-IA, One Zone - IA | 30 days |
| Glacier Instant/Flexible Retrieval | 90 days |
| Glacier Deep Archive | 180 days |
s3 standard-ia or s3 one zone-ia:
- Minimum Days for Transition from Standard: 30 days
- Minimum 30-Day Storage Charge: 30 days
data transfer
- S3: within the same Region is free.
- Others (EC2) within the same Availability Zone is free.
replicate database on s3 as csv, stream on-going changes, min management overhead
AWS Database Migration Service + Change Data Capture (CDC)
s3 - worm
👉 S3 - Object Lock + Legal Hold
s3 - restrict access to a vpc
👉 S3 Access Point
s3 server access logs vs cloudtrail logs
- CloudTrail Logs: record of actions taken by a user, role, or an AWS service in Amazon S3
- S3 server access logs: detailed records for the requests that are made to an S3 bucket
- Fields for Object Size, Total Time, Turn-Around Time, and HTTP Referrer for log records
- Lifecycle transitions, expirations, restores
- Invalid Authentication
aws services with access logs:
- S3
- ELB
- CloudFront: or standard logs
- API Gateway
Amazon S3 Glacier: Low-cost archive storage in the AWS Cloud
amazon glacier select: ffilter objects with sql syntax using bucket name & object key
AWS Snow Family: Move petabytes of data to and from AWS, or process data at the edge
aws snow family:
- Snowcone: 8TB - 14TB
- Snowball: 80TB
- Snowball Edge:
- Snowball Edge Compute Optimized: 80TB + EC2
- Snowball Edge Storage Optimized: 210TB + EC2
- Snowmobile: 100PB
aws opshub: graphical user interface to manage aws snowball devices
AWS Storage Gateway: Hybrid storage integration
nfs vs storage gateway
- NFS: files are stored on AWS -> high-latency
- Storage Gateway - File: low-latency
aws file gateway - handle writes
-
When a client writes data to a file via File Gateway, that data is first written to the local cache disk on the gateway itself.
- Once the data has been safely persisted to the local cache, only then does the File Gateway acknowledge the write back to the client.
-
From there, File Gateway transfers the data to the S3 bucket asynchronously in the background, optimizing data transfer using multipart parallel uploads, and encrypting data in transit using HTTPS.
COURSE FUNDAMENTALS AND AWS ACCOUNTS
AWS Accounts - The basics (11:33)
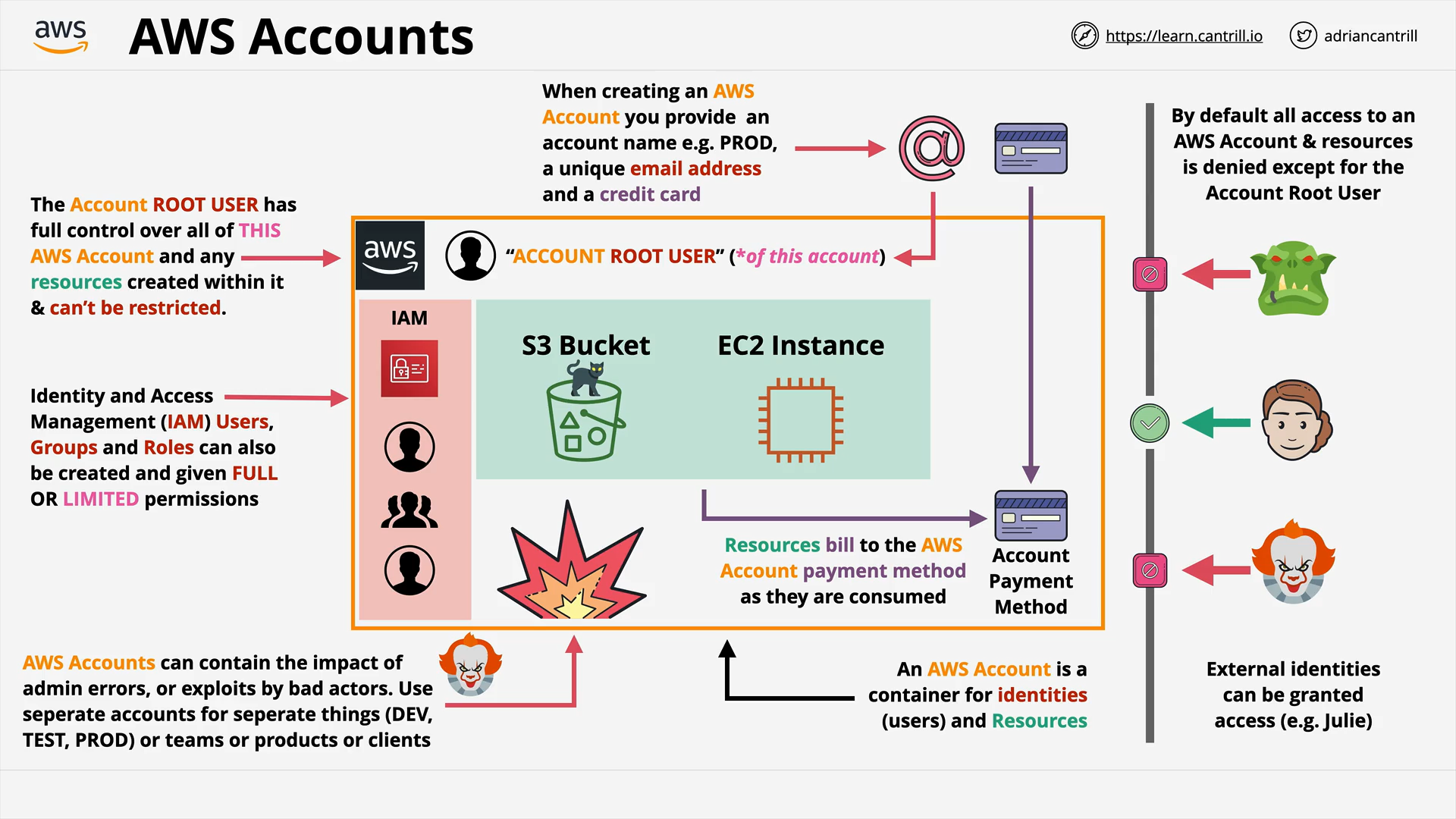
[DEMO] ACCOUNTS - STEP1 - Creating GENERAL AWS Account (14:44)
Multi-factor Authentication (MFA) (8:25)
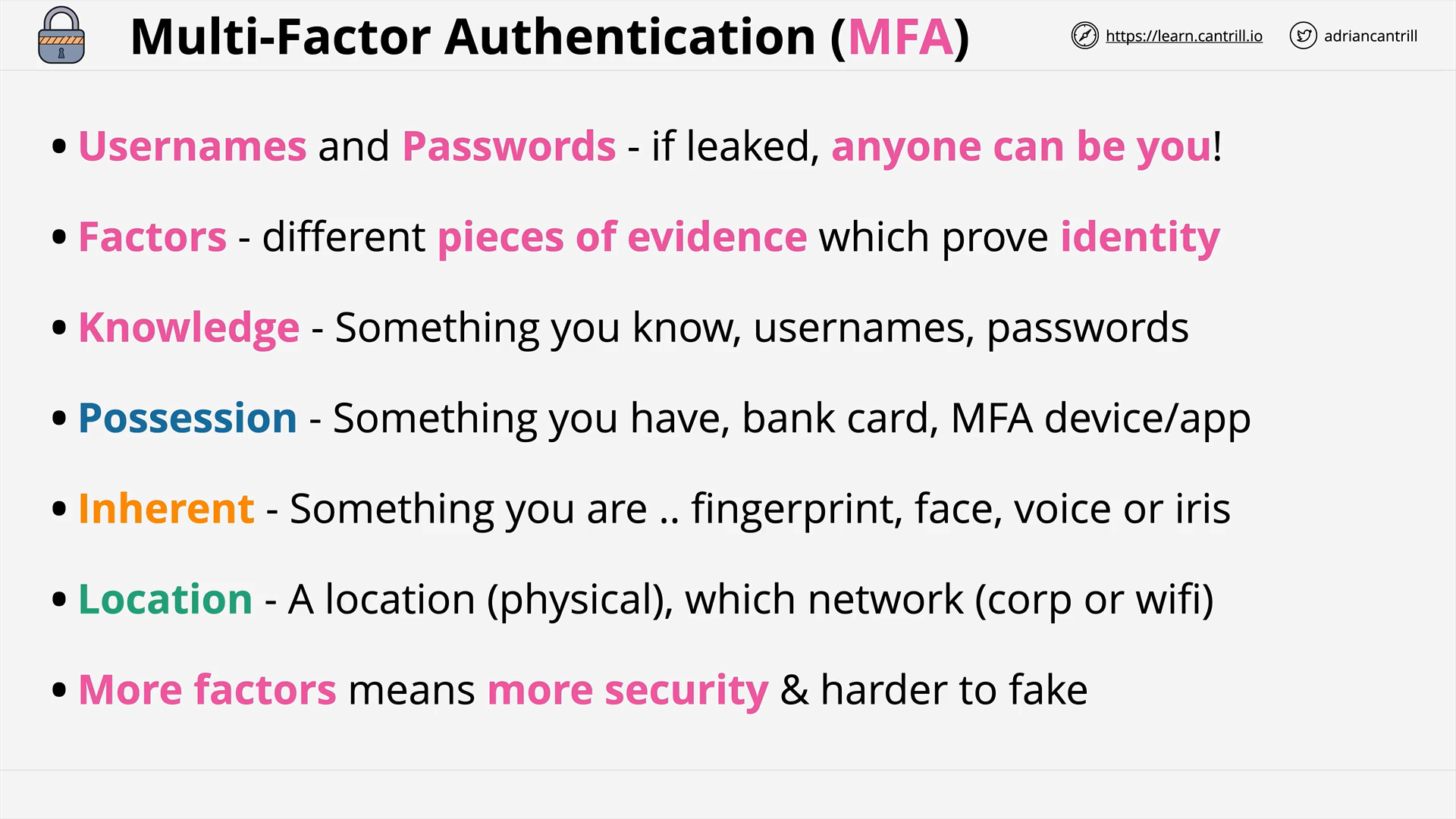
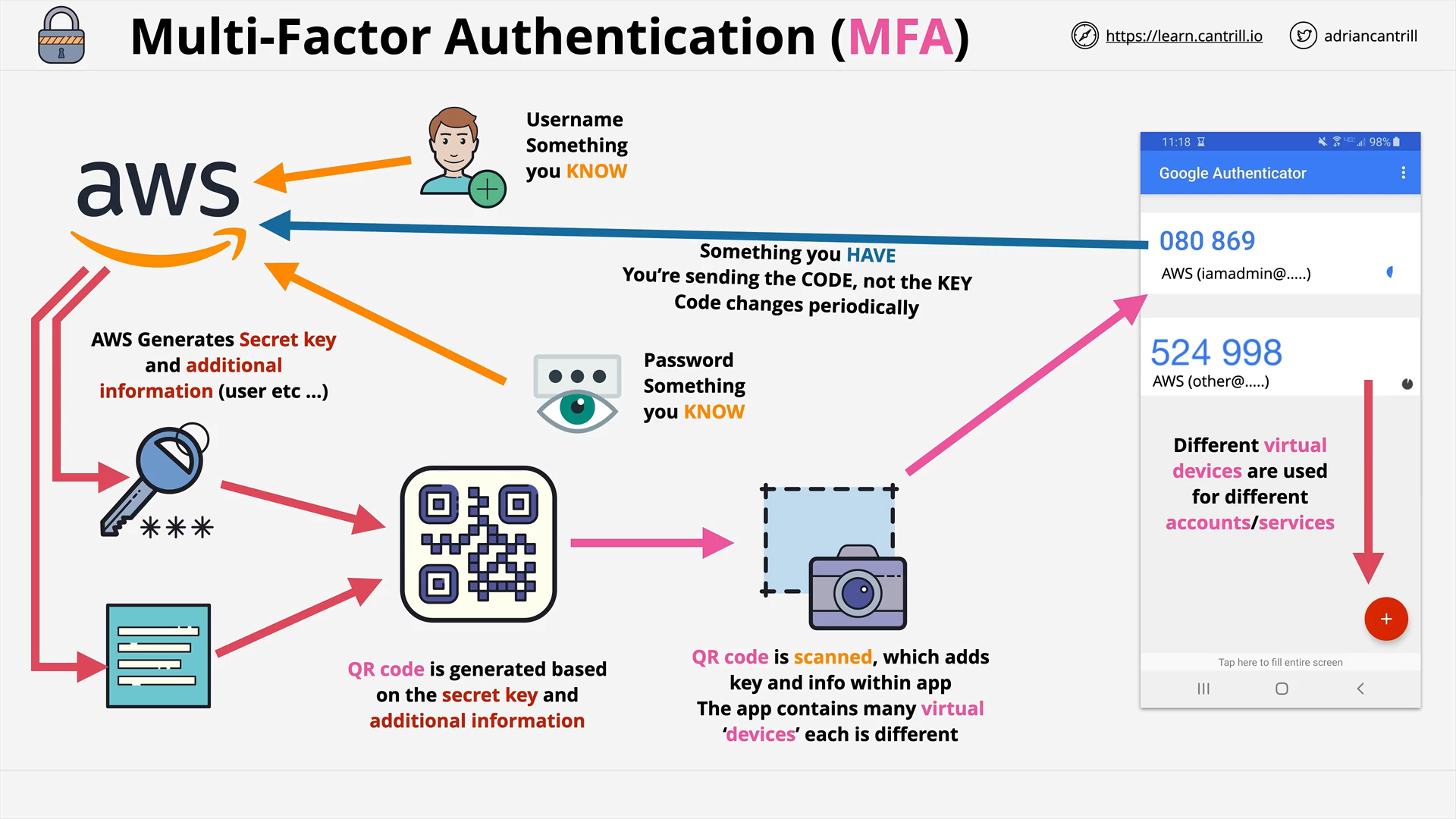
[DEMO] ACCOUNTS - STEP2 - Securing GENERAL AWS Account (9:44)
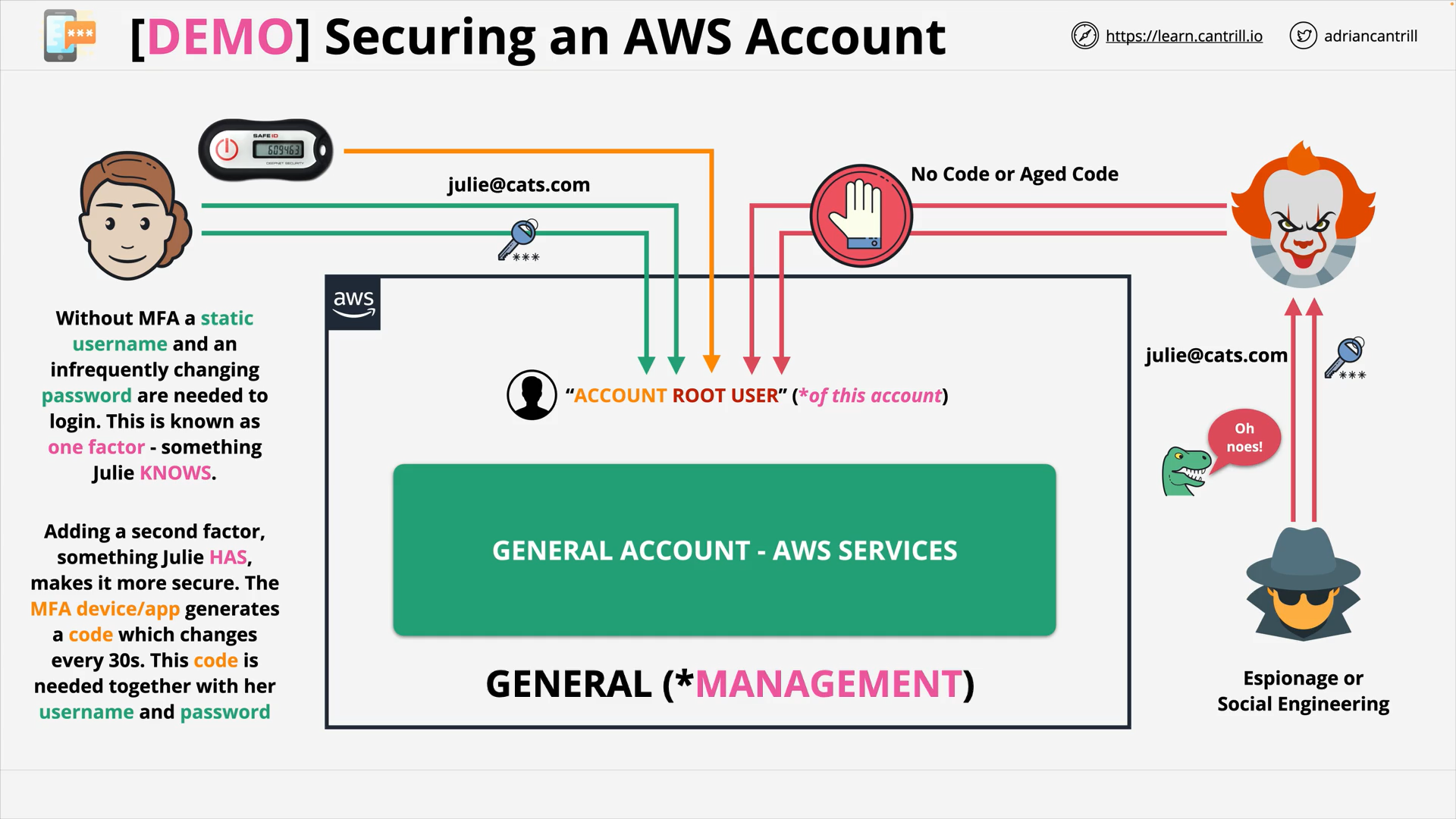
[DEMO] ACCOUNTS - STEP3 - Creating a Budget (6:46)
[DO_IT_YOURSELF] Creating the Production Account (4:59)
Identity and Access Management (IAM) Basics (13:01)
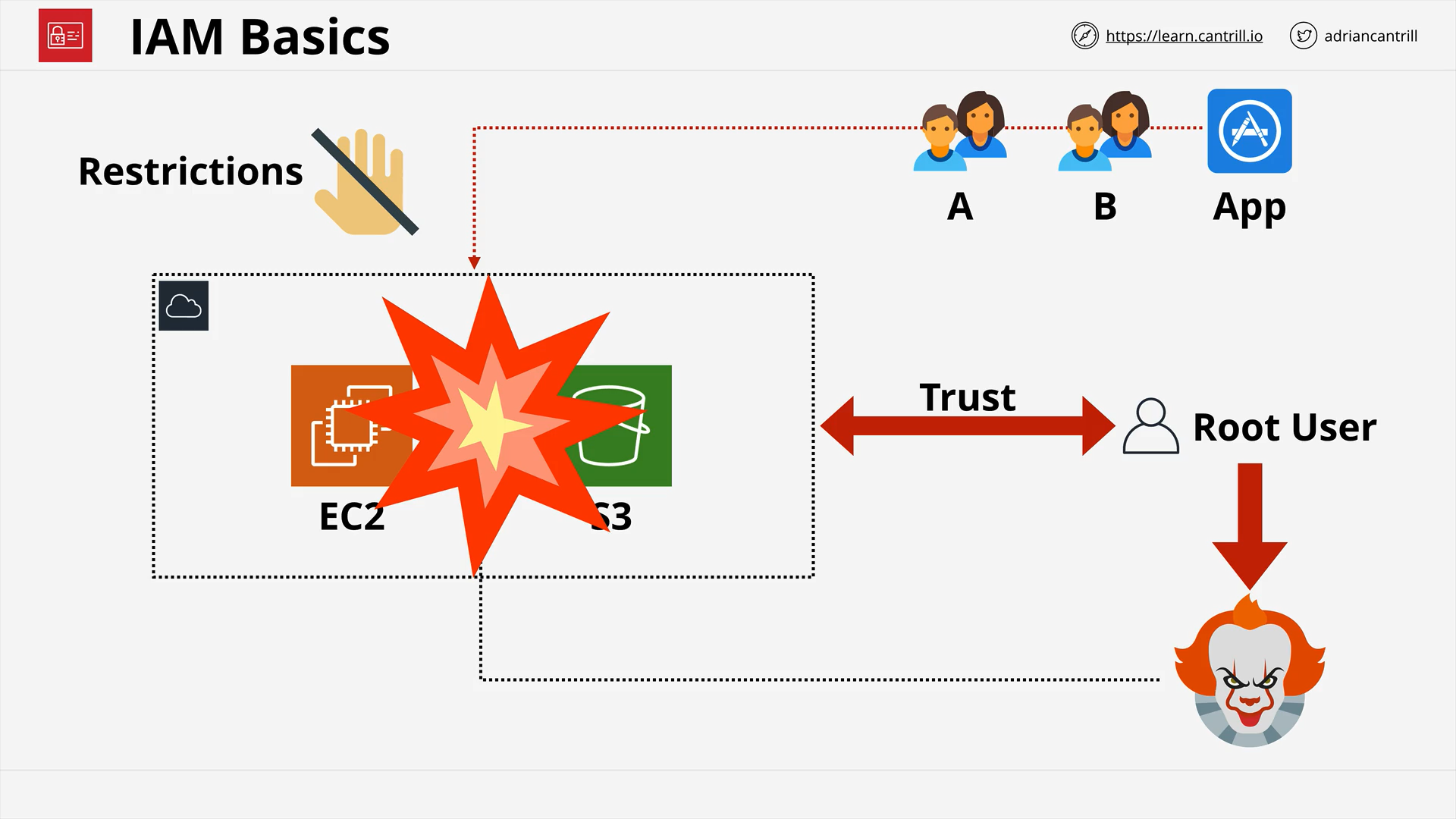
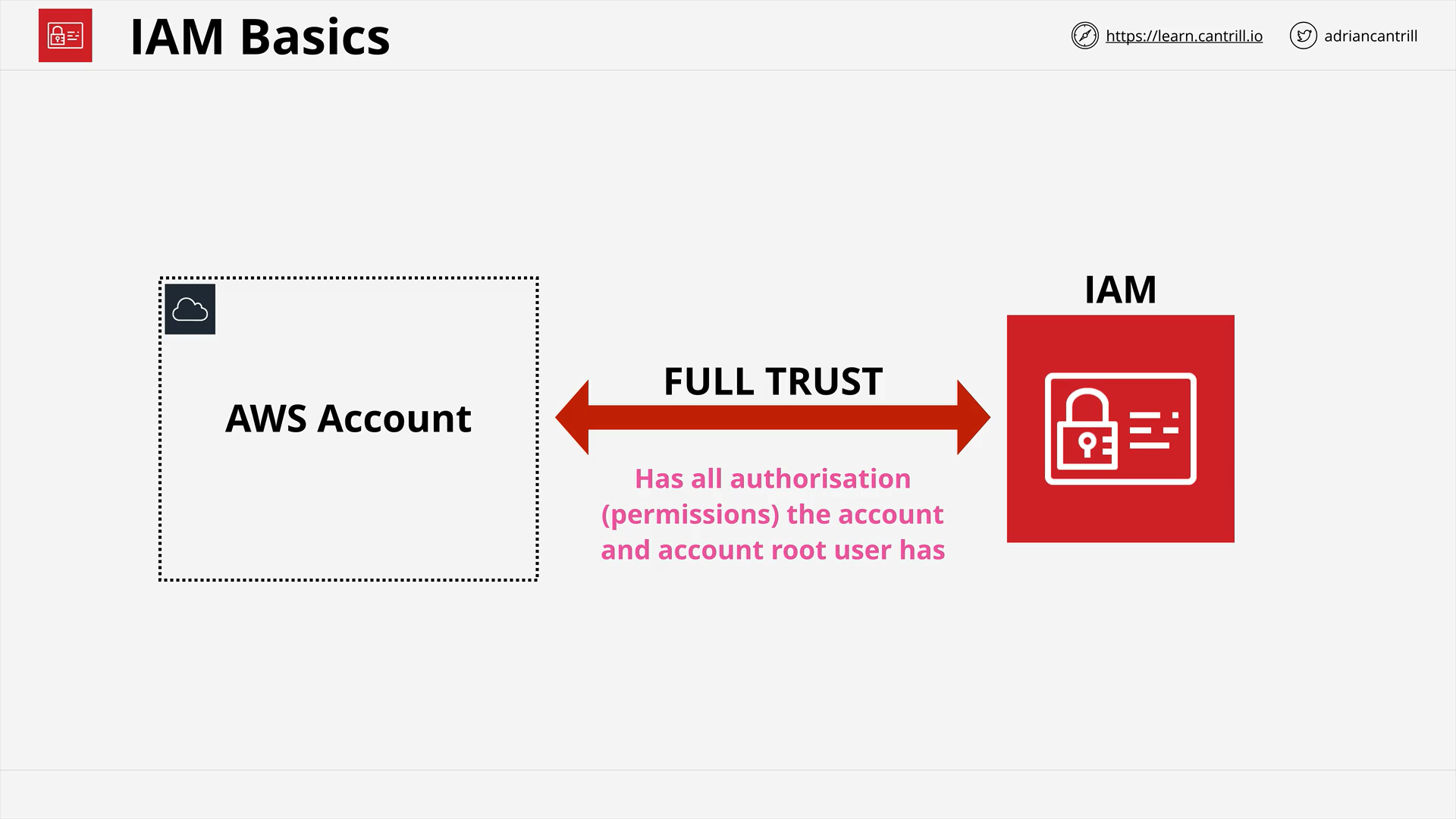
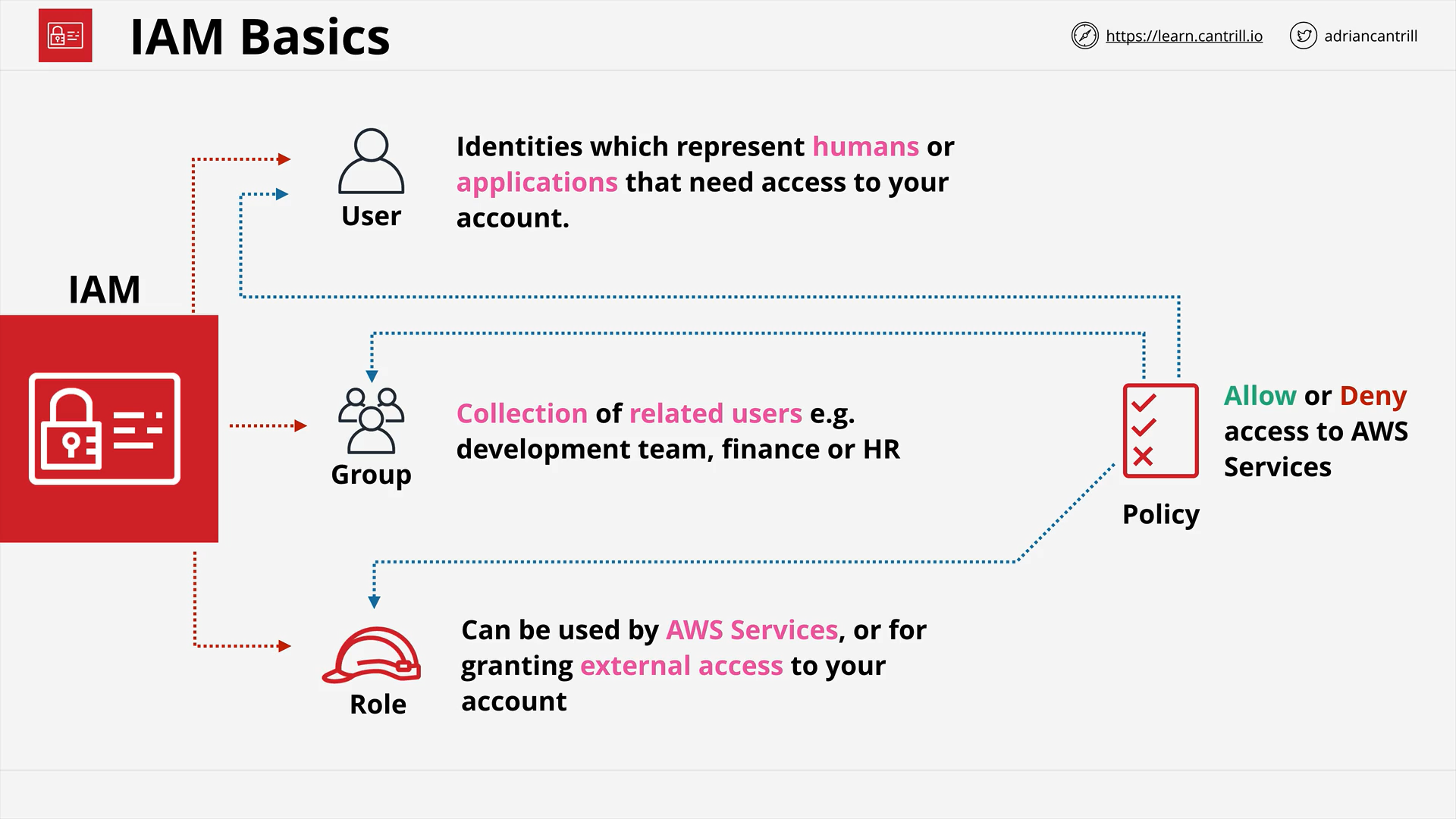
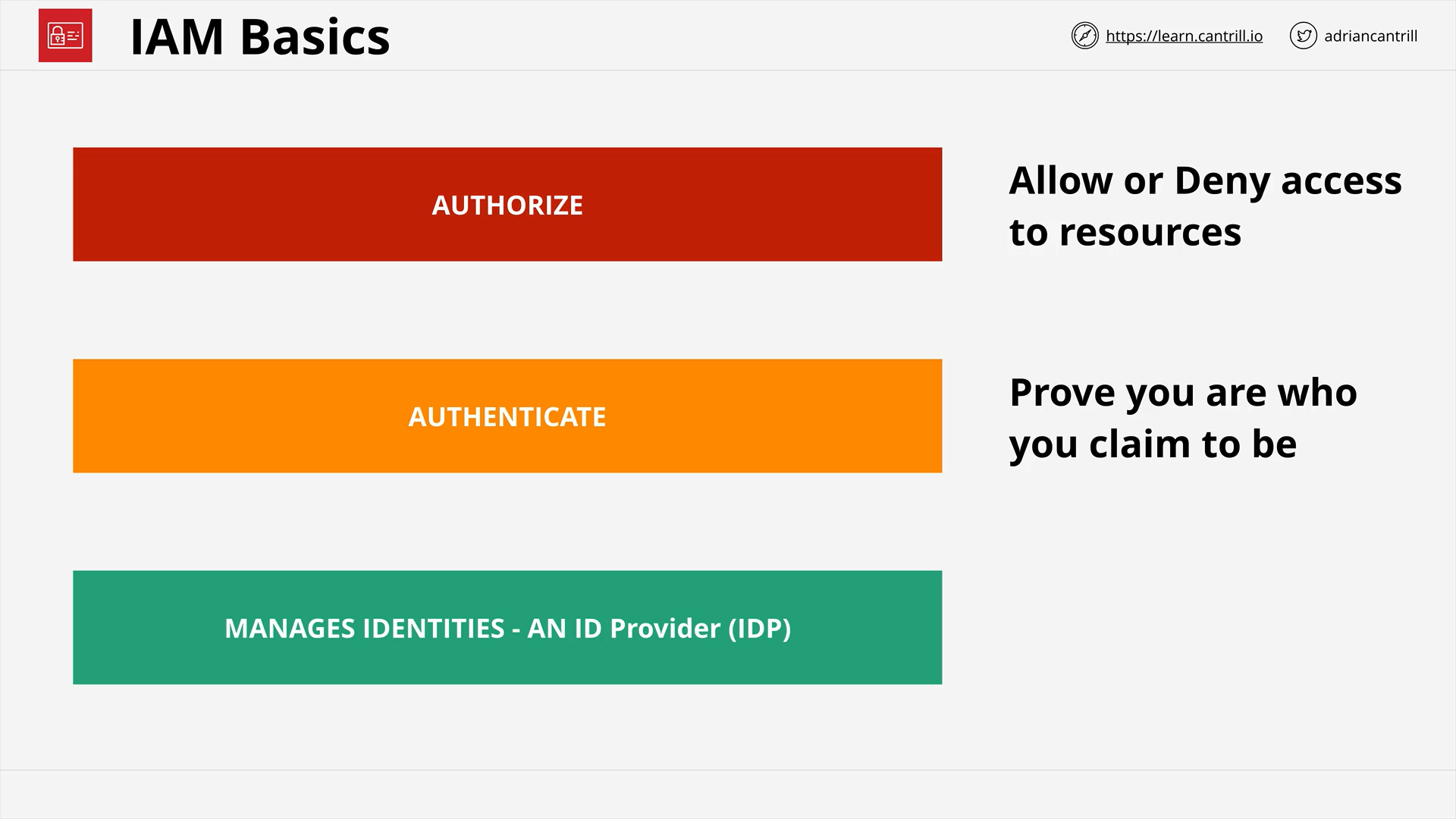
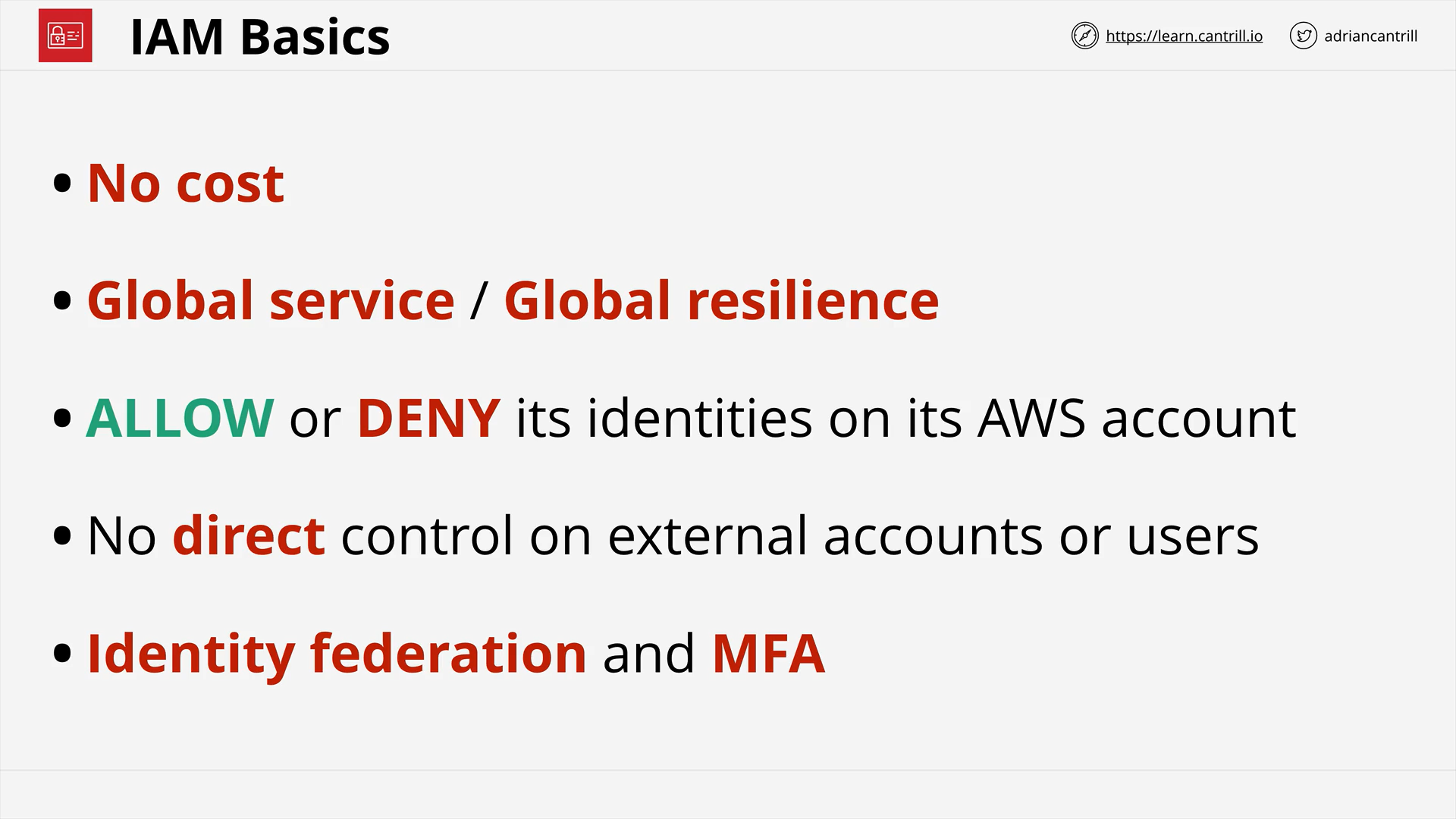
[DEMO] ACCOUNTS - STEP4 - Adding IAMADMIN to GENERAL Account (12:36)
[DEMO] ACCOUNTS - STEP4 - Adding IAMADMIN to PRODUCTION Account (10:17)
IAM Access Keys (7:10)
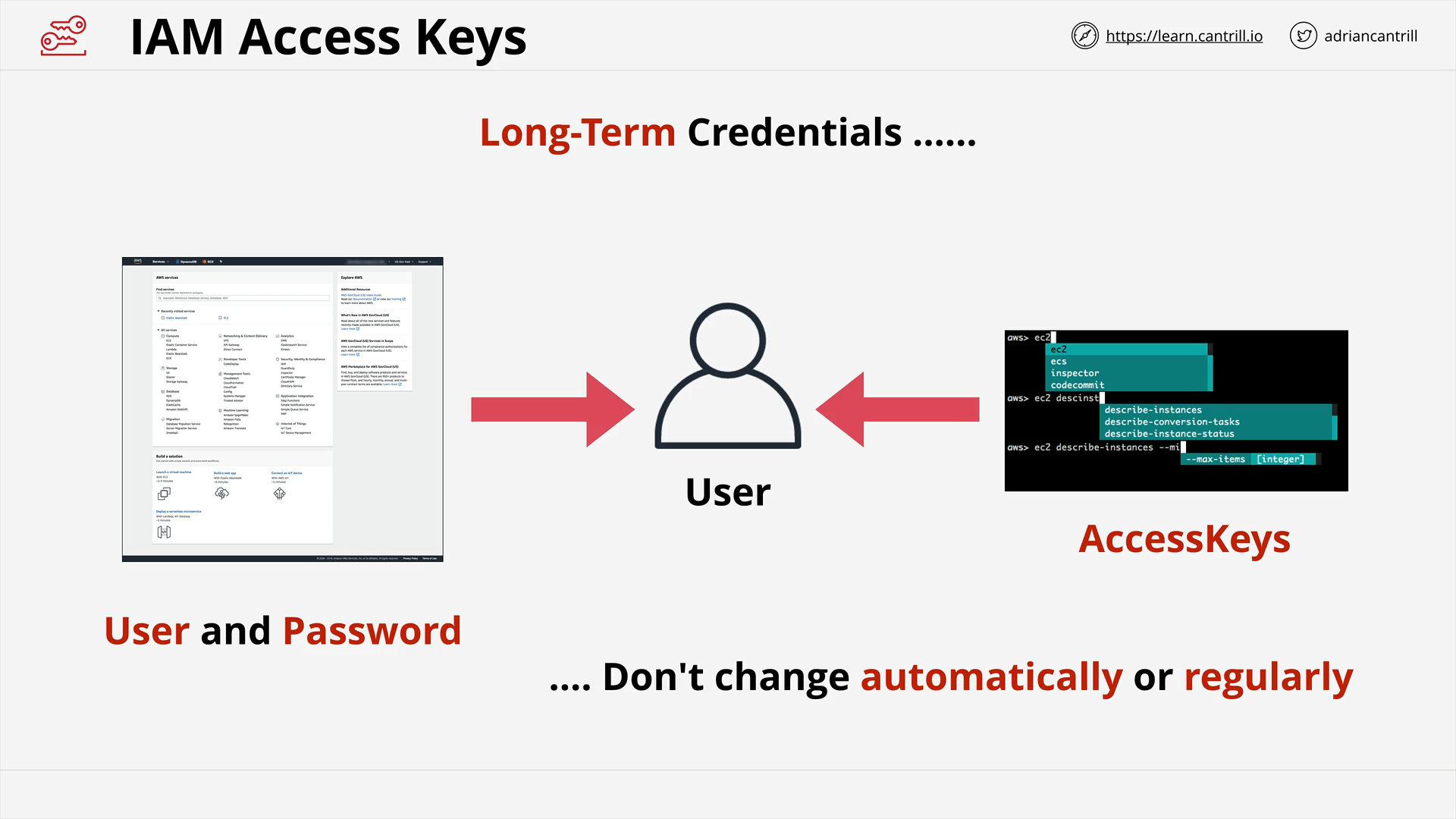
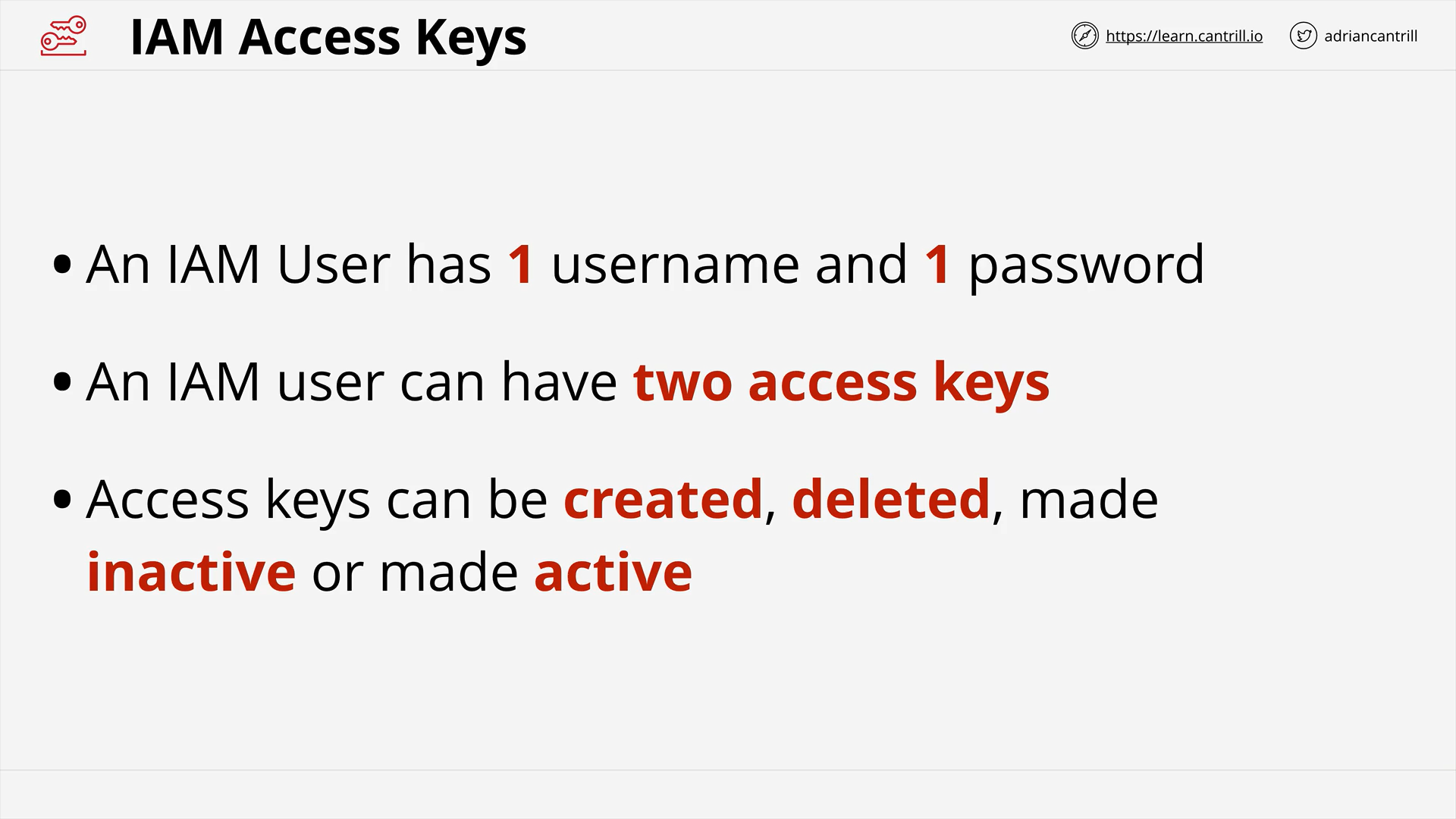
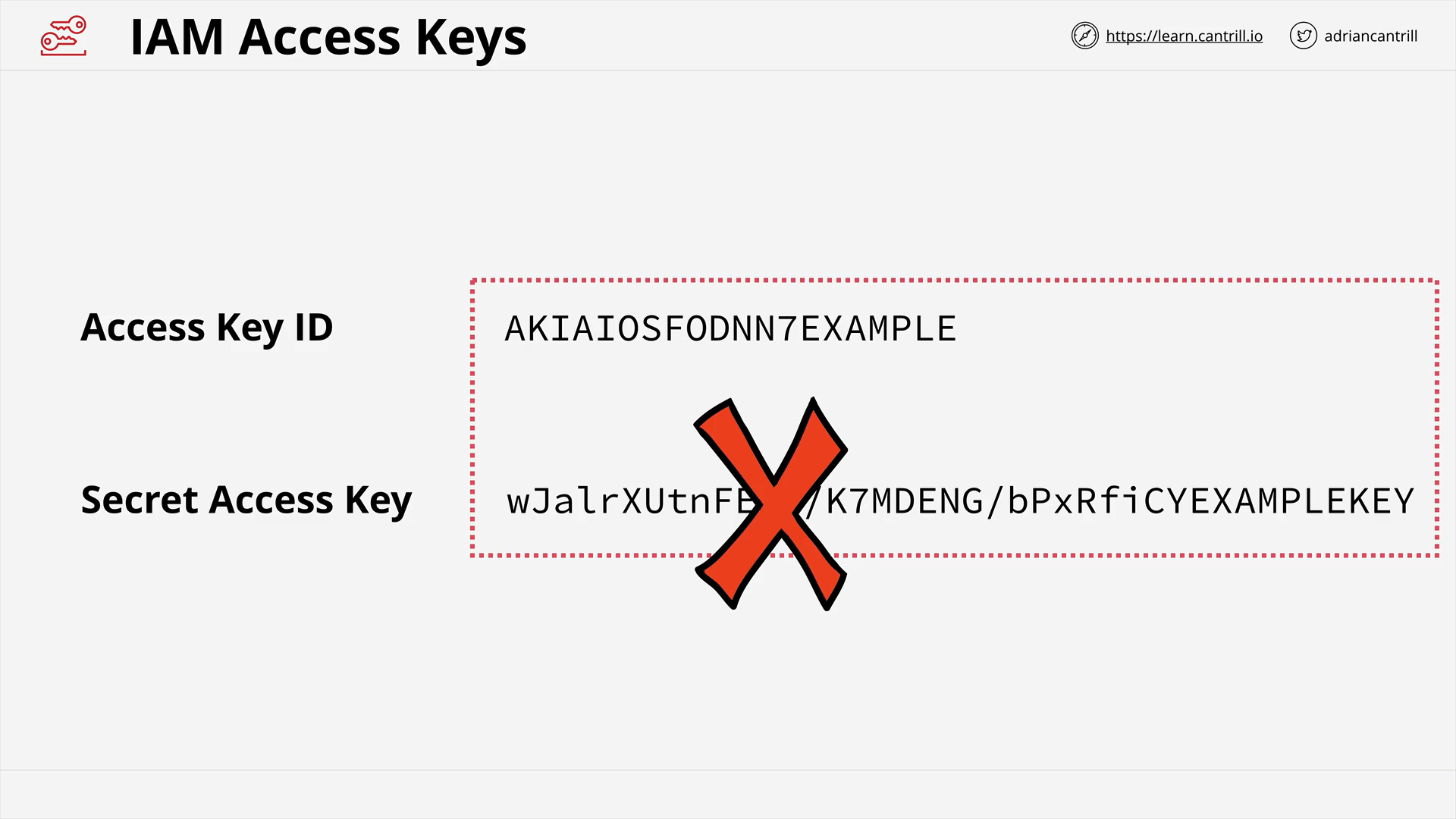
[DEMO] Creating Access keys and setting up AWS CLI v2 tools (17:43)
NETWORKING AND TECHNICAL FUNDAMENTALS
OSI 7-Layer Networking Model
OSI Model Introduction (4:46)

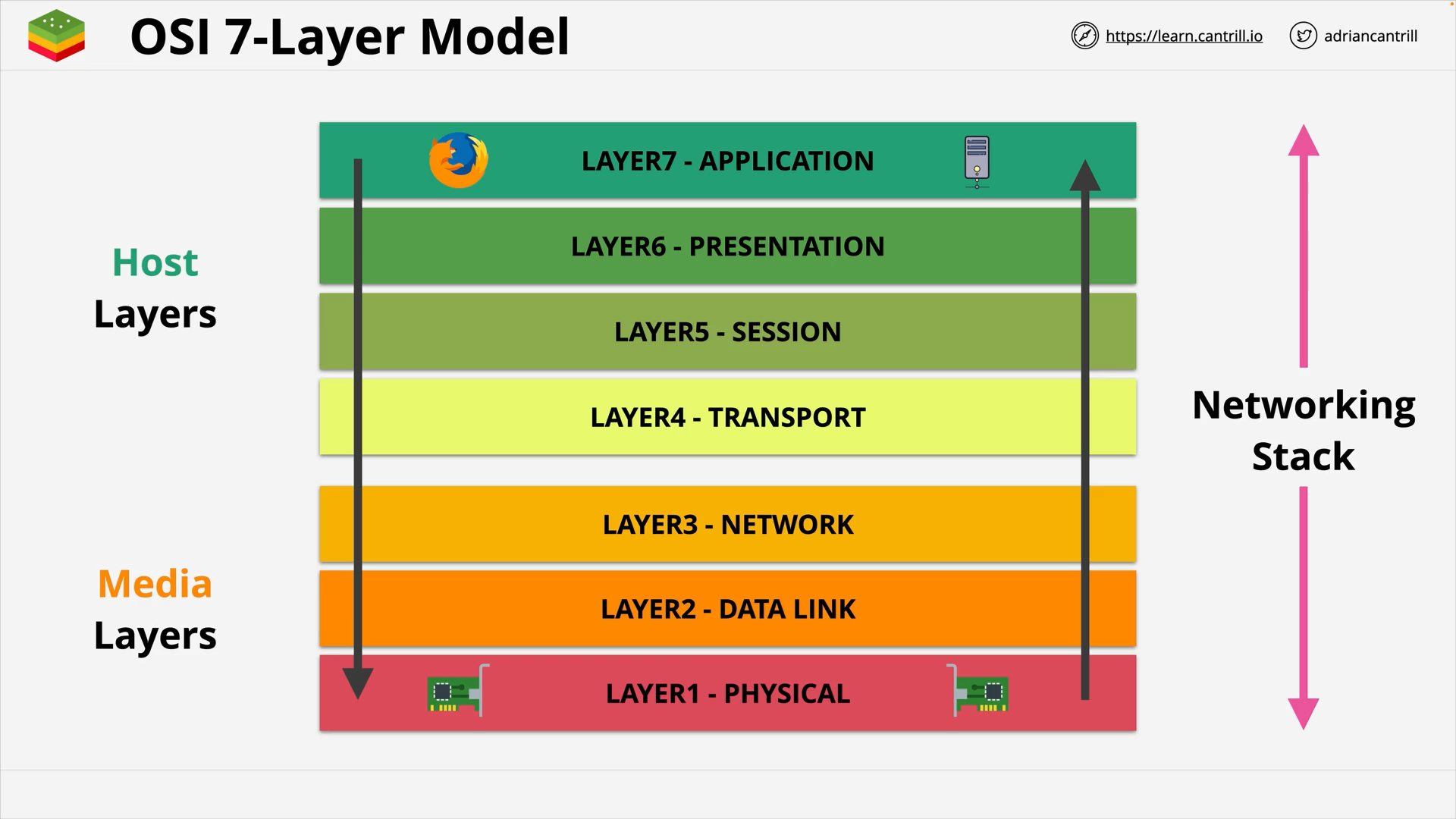
Layer 1 - Physical (10:00)
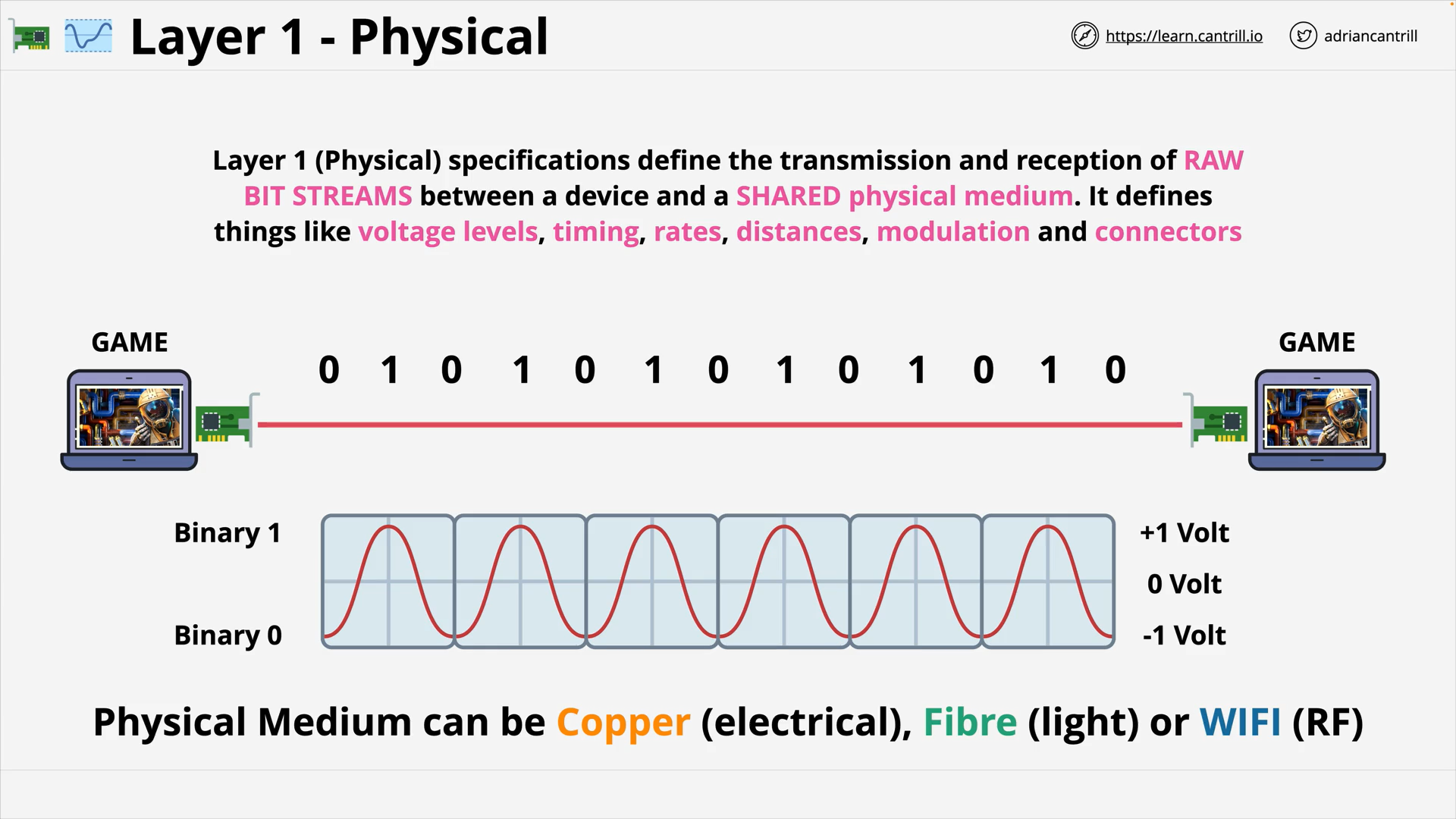
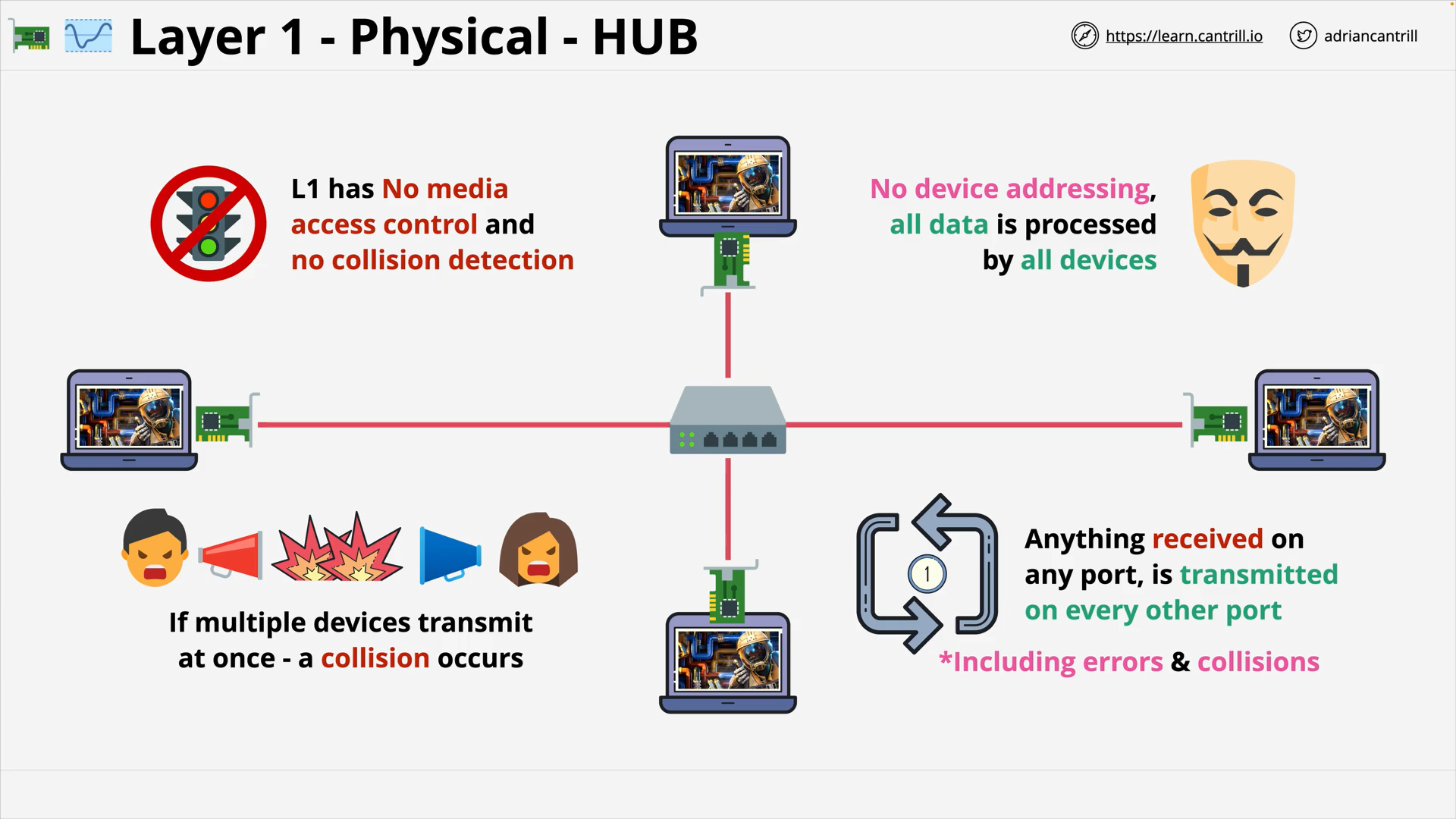
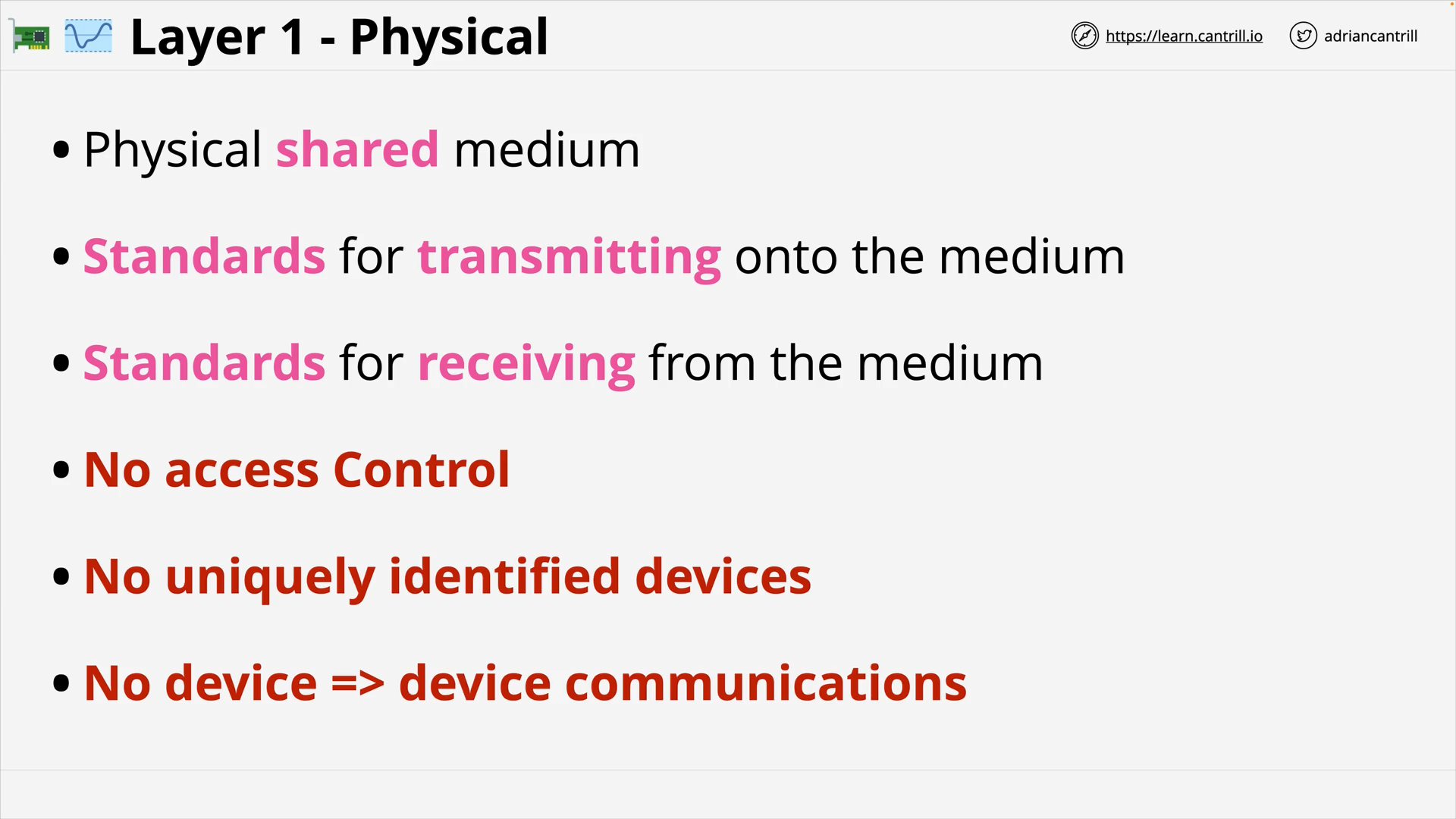
Layer 2 - DataLink - PART1 (8:47)
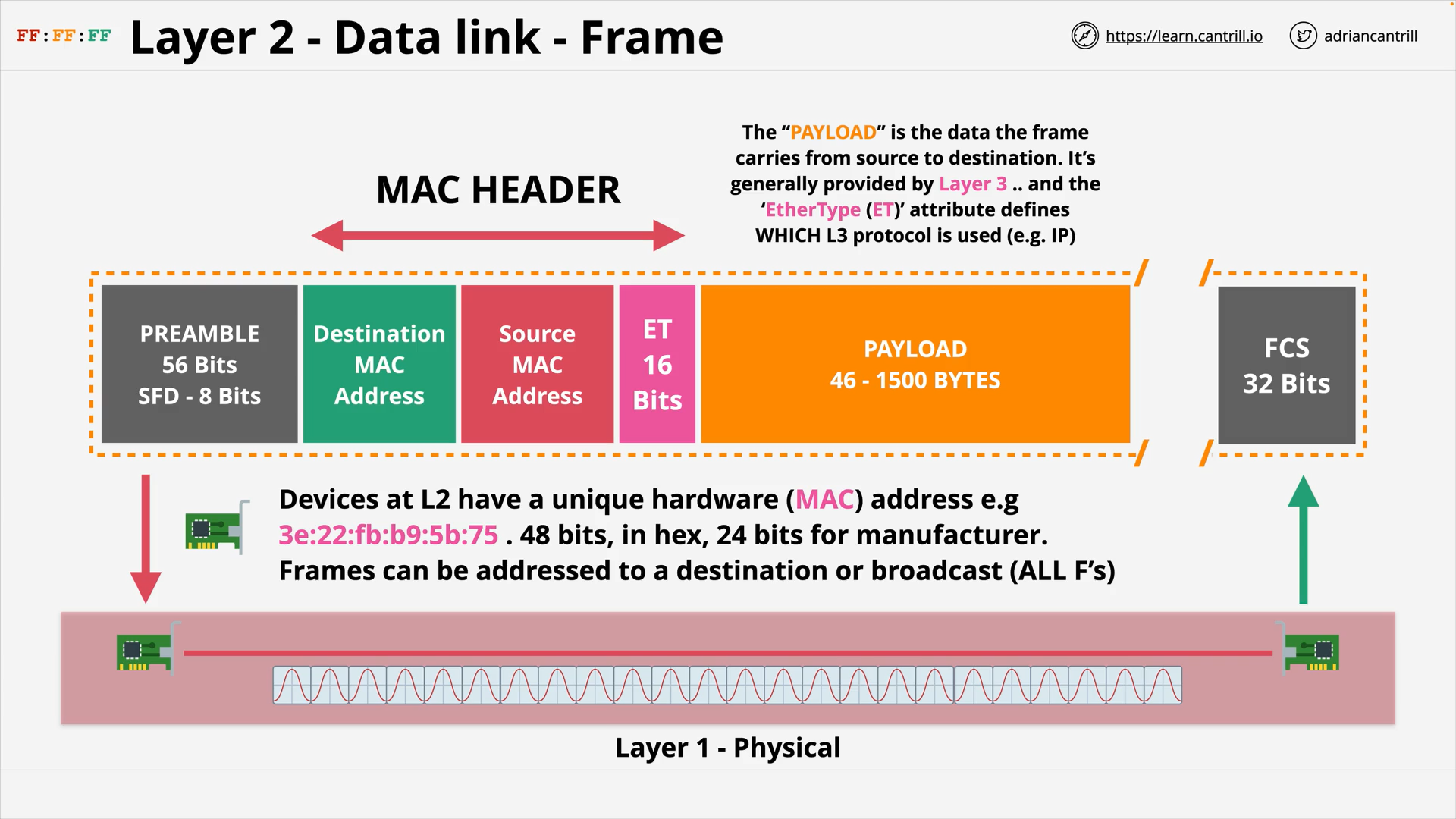
**mac vs mac address**?
-
MAC: Medium Access Control, also called Media Access Control
-
MAC Address: Medium Access Control Address,
- also known as hardware address, or physical address
- a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment
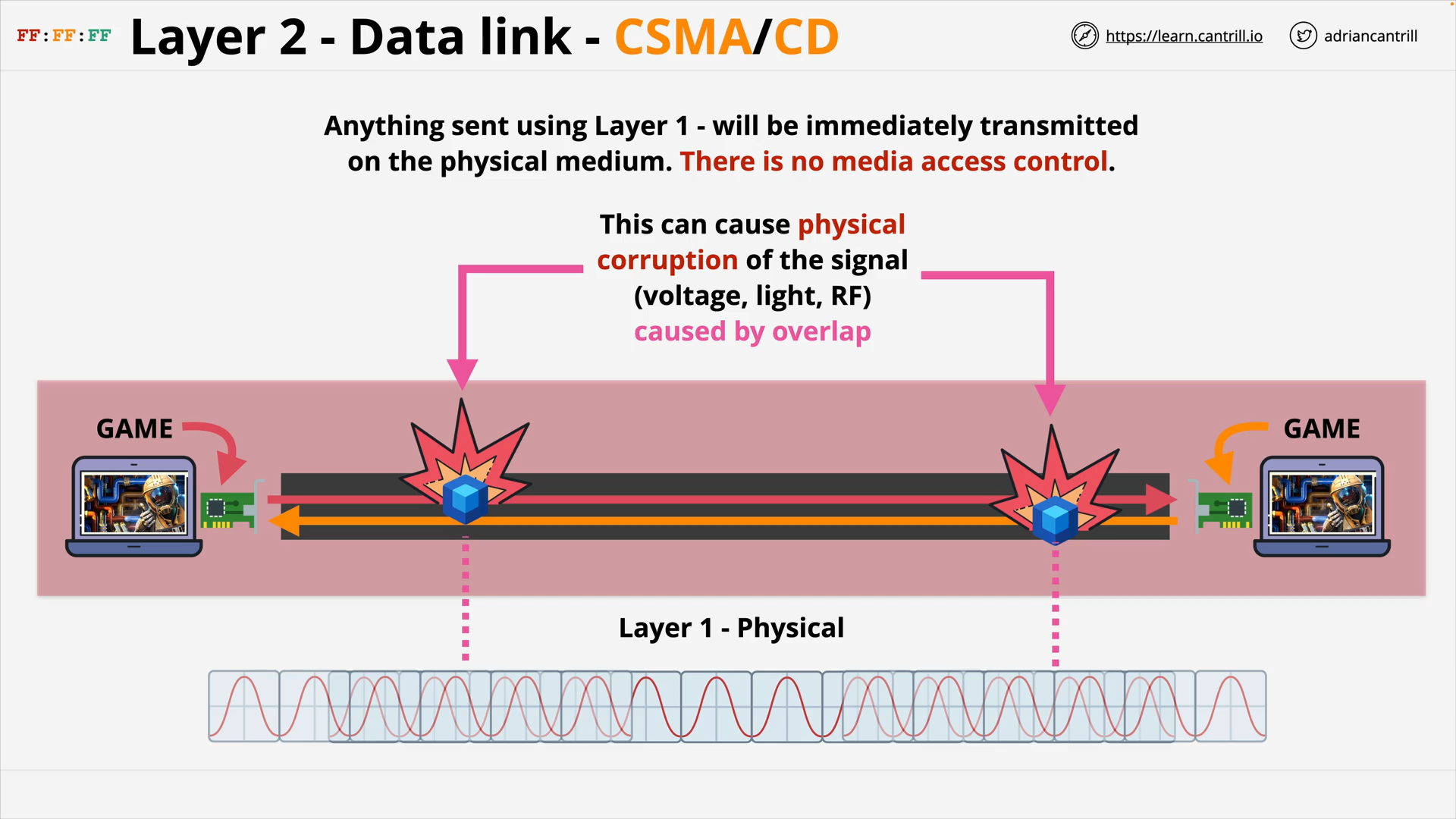
Layer 2 - DataLink - PART2 (14:24)
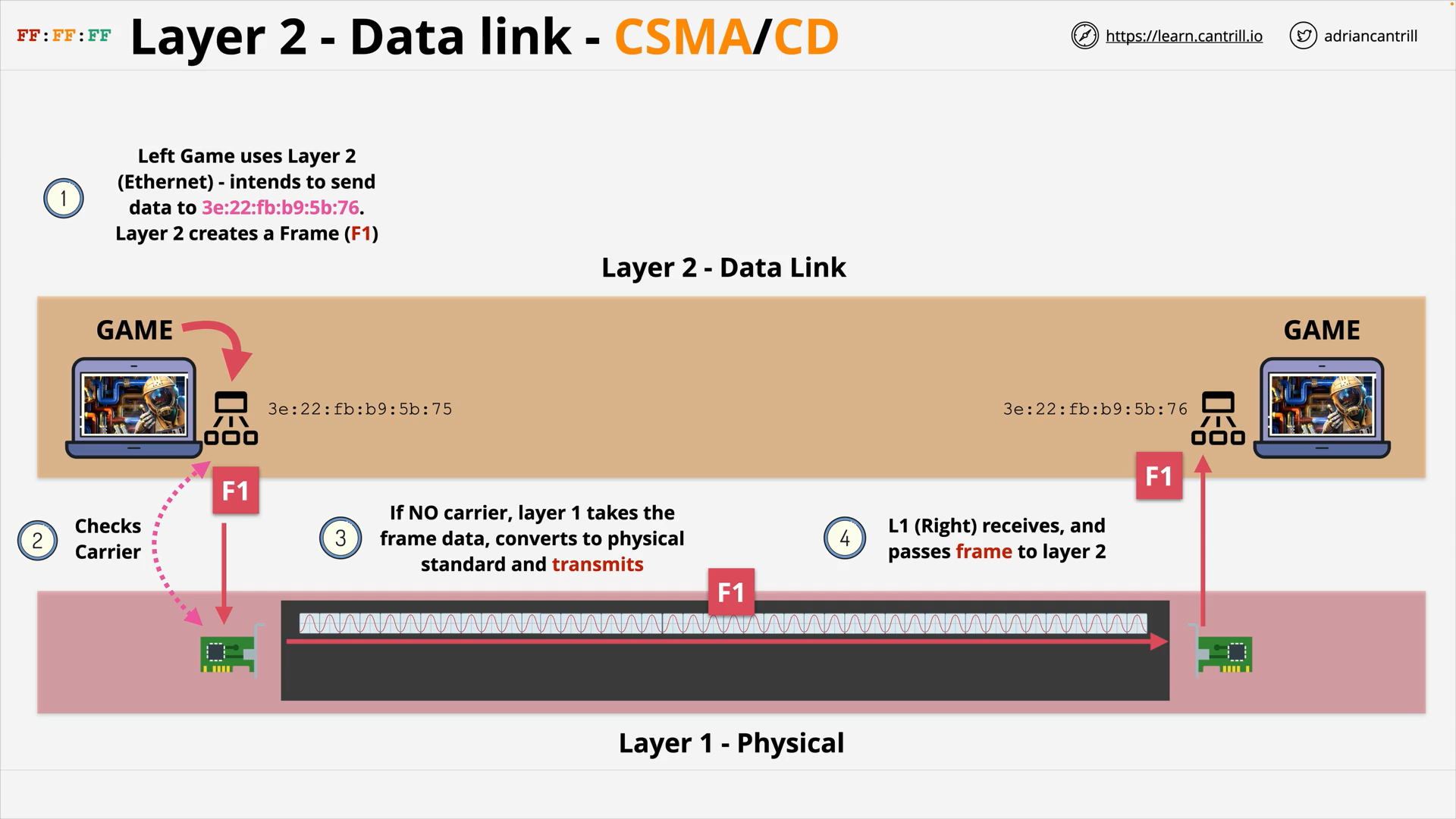 Left game sends Frame F1 to Right game
Left game sends Frame F1 to Right game
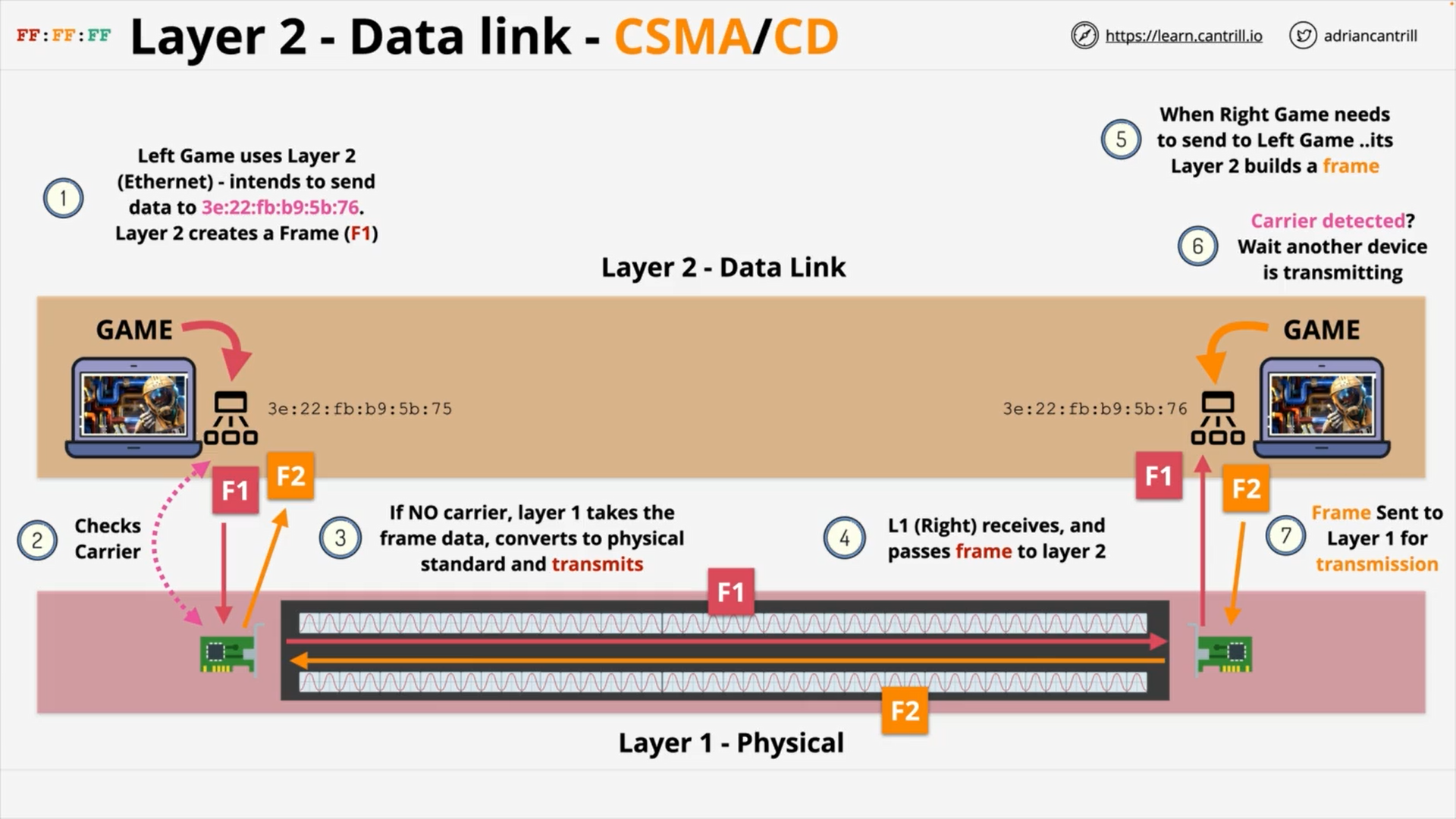 Right game sends Frame F2 to Left game - Carrier Sense Multiple Access (CSMA)
Right game sends Frame F2 to Left game - Carrier Sense Multiple Access (CSMA)
layers are independent
Conceptually, left L2 is talking to right L2.
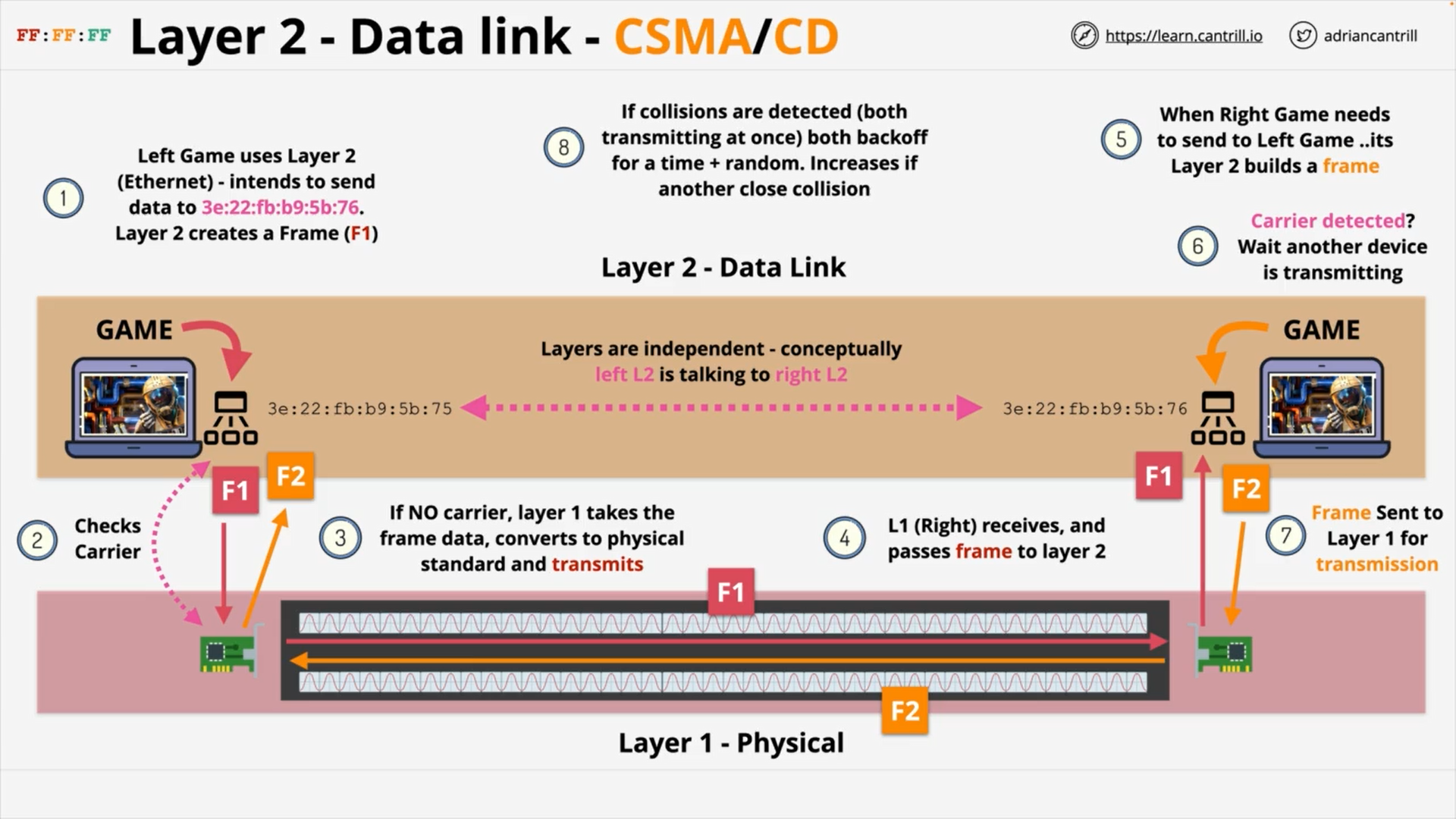 Collision Detection (CD)
Collision Detection (CD)
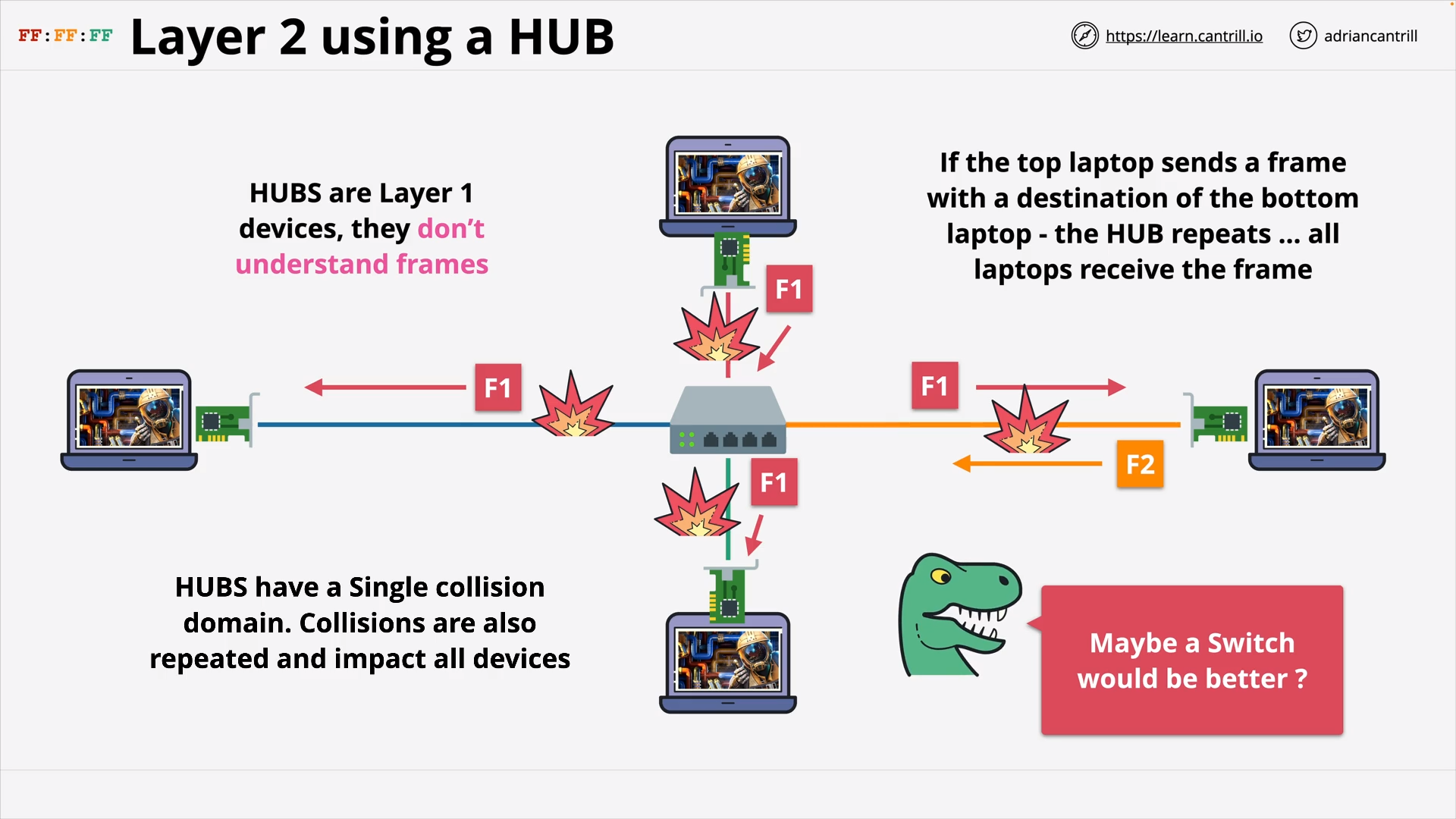 OSI Layer 2 - Try using a Hub
OSI Layer 2 - Try using a Hub
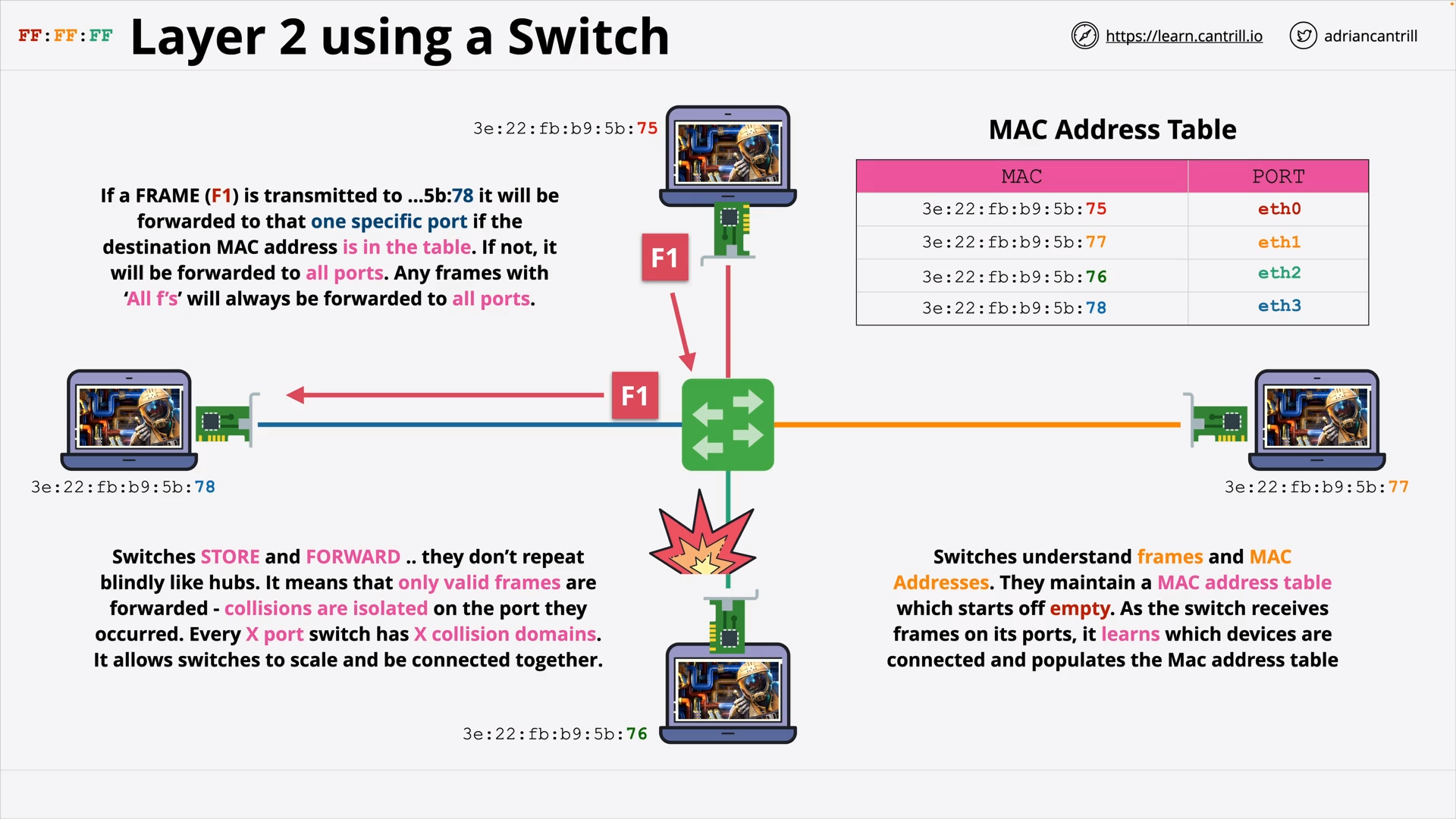 OSI Layer 2 - Using a Switch - MAC Address Table
OSI Layer 2 - Using a Switch - MAC Address Table
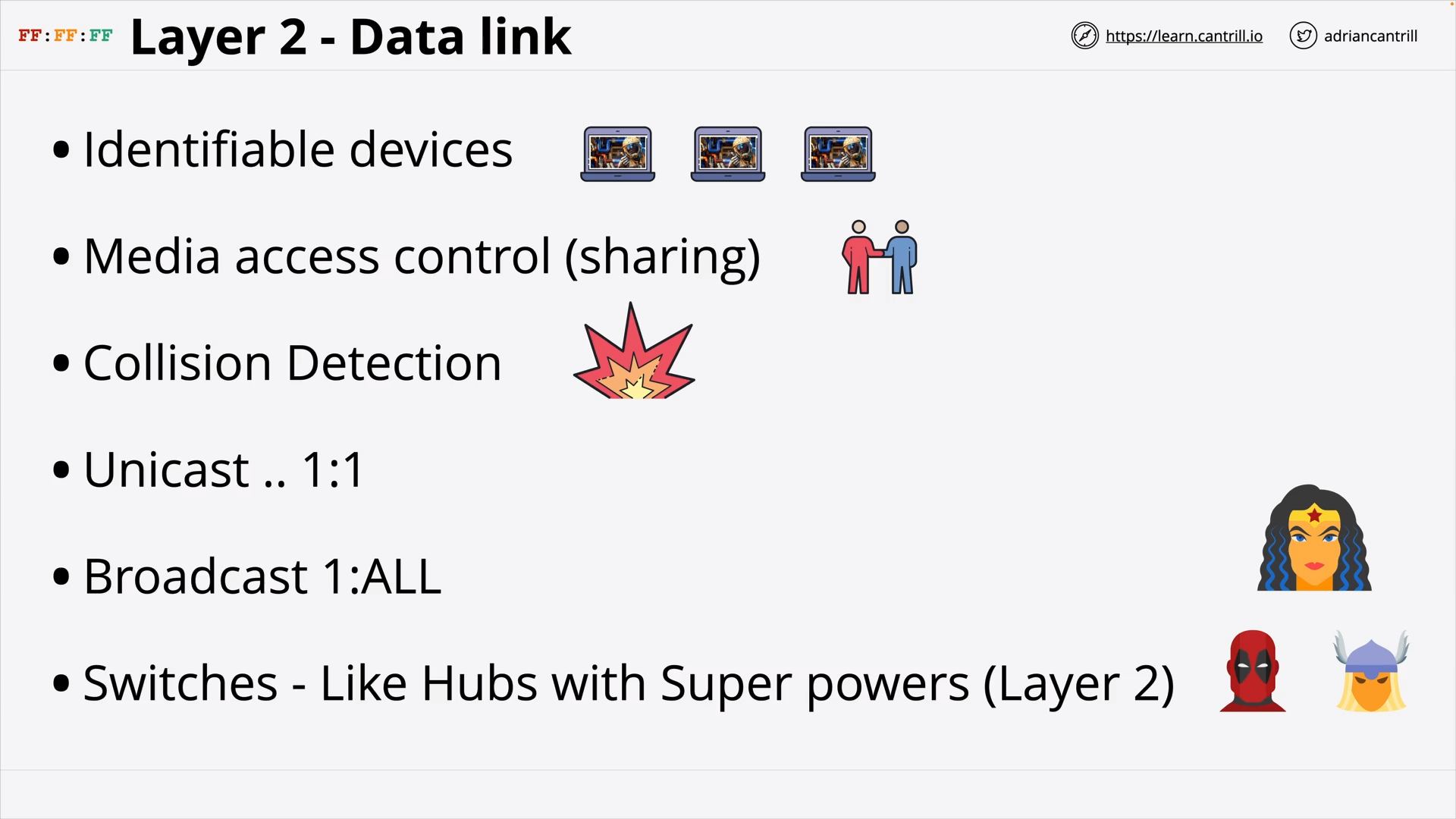 OSI Layer 2 Data Link: MAC Address 👉️ Median Access Control & Collision Detection, Switch
OSI Layer 2 Data Link: MAC Address 👉️ Median Access Control & Collision Detection, Switch
Layer 3 - Network - PART1 (12:06)
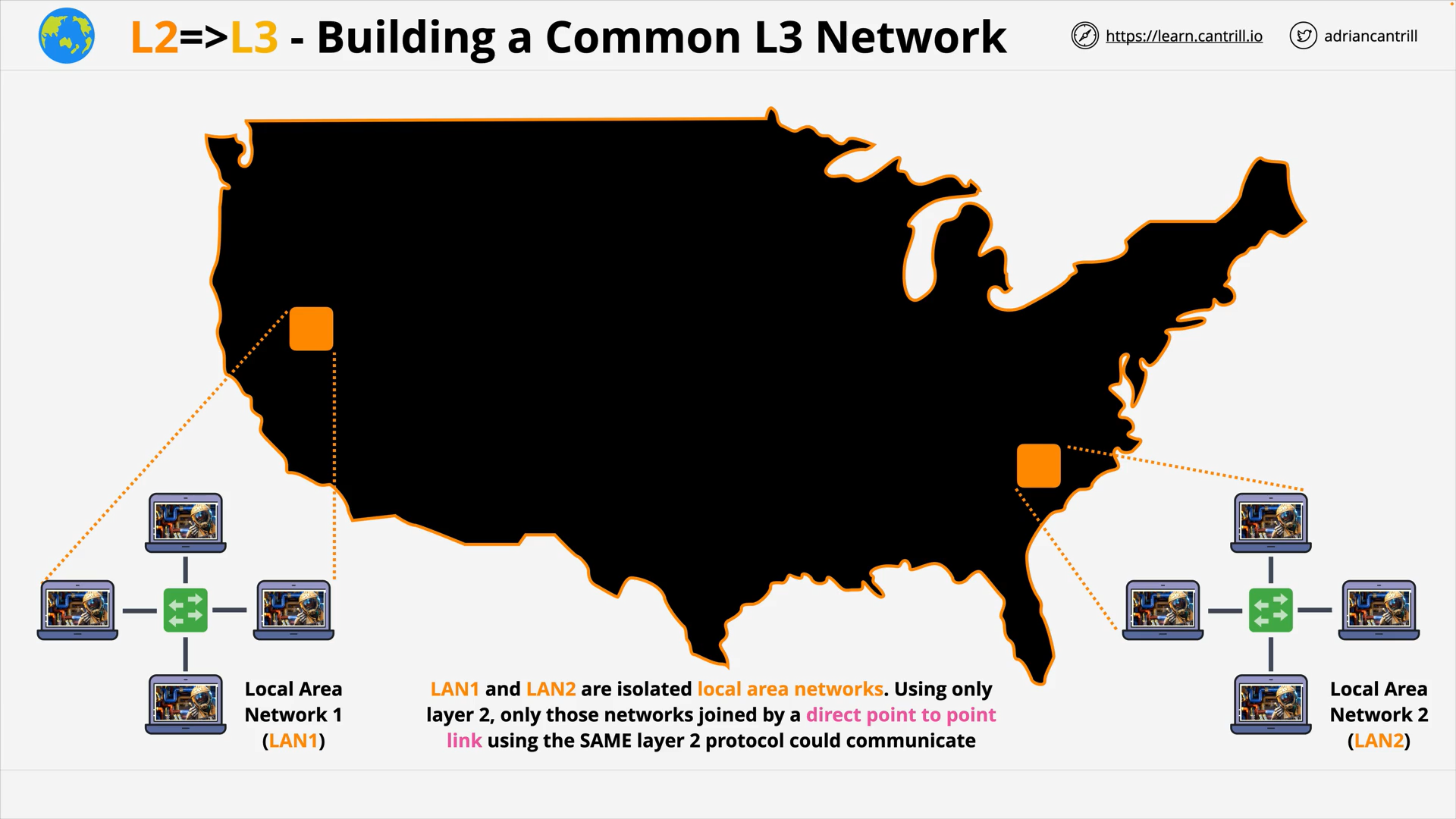 OSI Layer 3 - Layer 3LAN (Local Area Network) use Ethernet protocol
OSI Layer 3 - Layer 3LAN (Local Area Network) use Ethernet protocol
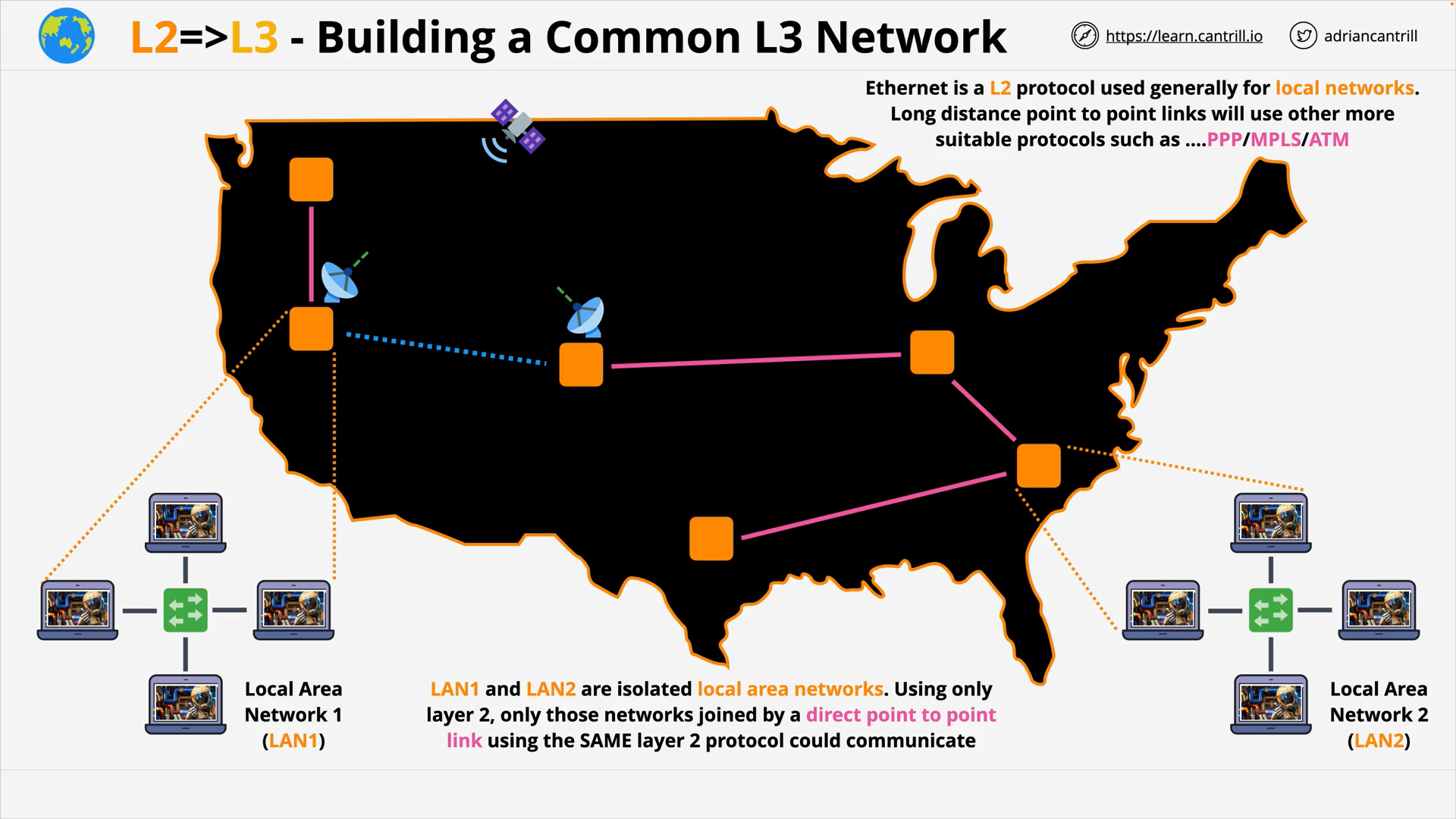 OSI Layer 3 - Long distant point to point (P2P) links use other protocols: PPP/MPLS/ATM…
OSI Layer 3 - Long distant point to point (P2P) links use other protocols: PPP/MPLS/ATM…
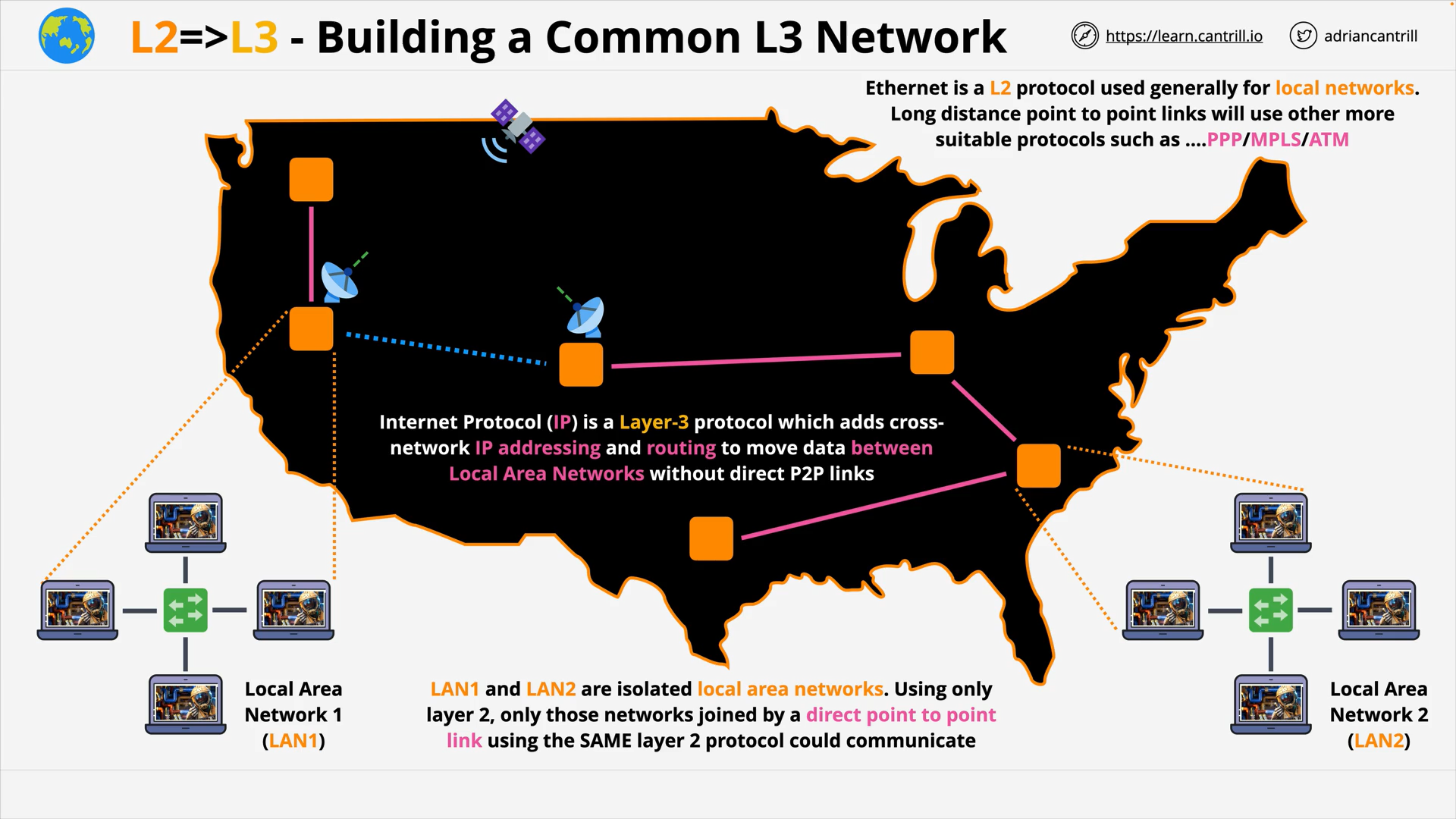 OSI Layer 3 - Internet Protocol (IP), a Layer-3 protocol, moves data between LAN without direct P2P links, by adding cross network IP addressing and routing
OSI Layer 3 - Internet Protocol (IP), a Layer-3 protocol, moves data between LAN without direct P2P links, by adding cross network IP addressing and routing
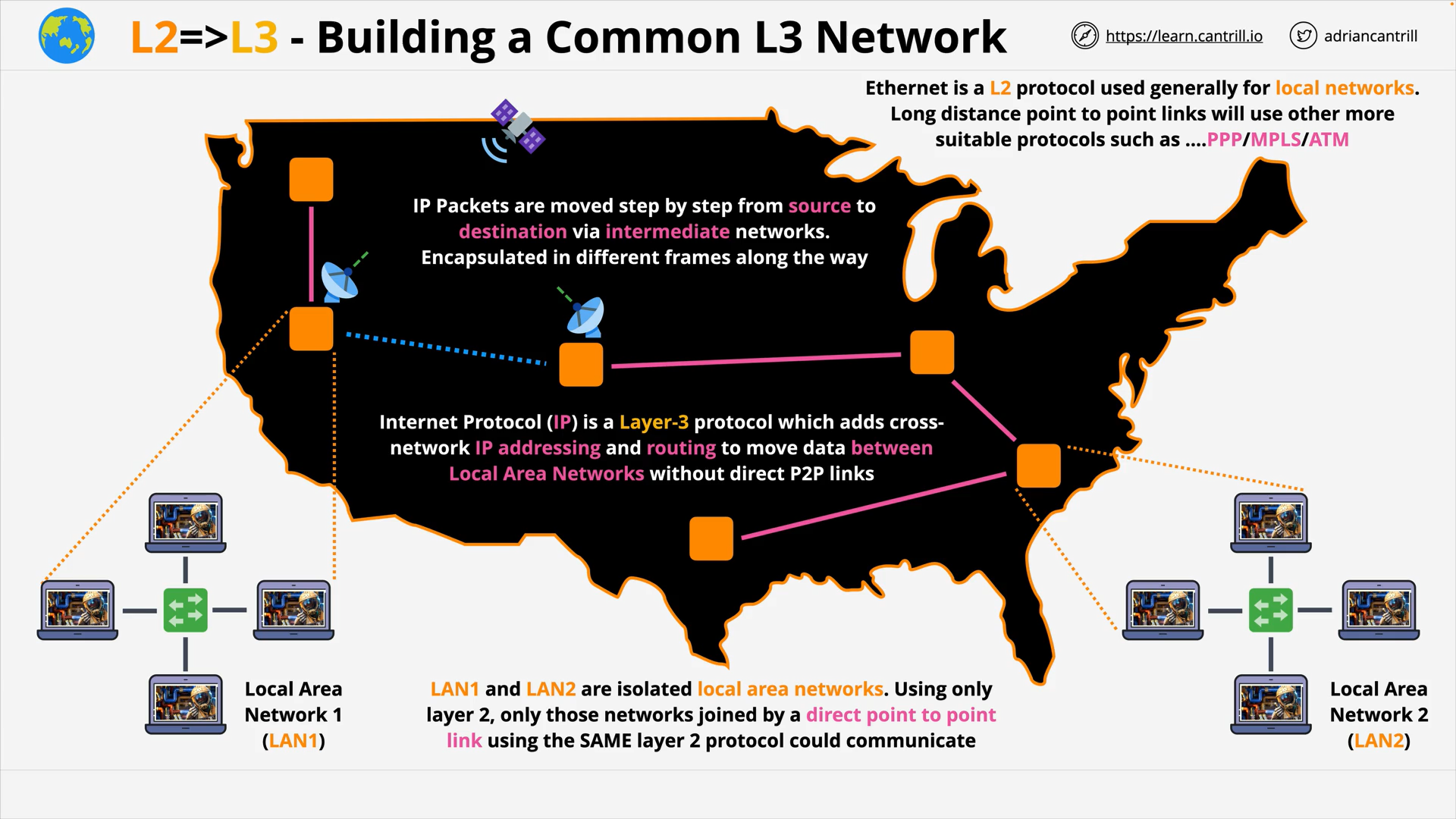 OSI Layer 3 - IP Packets are moved step by step from source to destination via intermediate networks, encapsulated in different frames along the way.
OSI Layer 3 - IP Packets are moved step by step from source to destination via intermediate networks, encapsulated in different frames along the way.
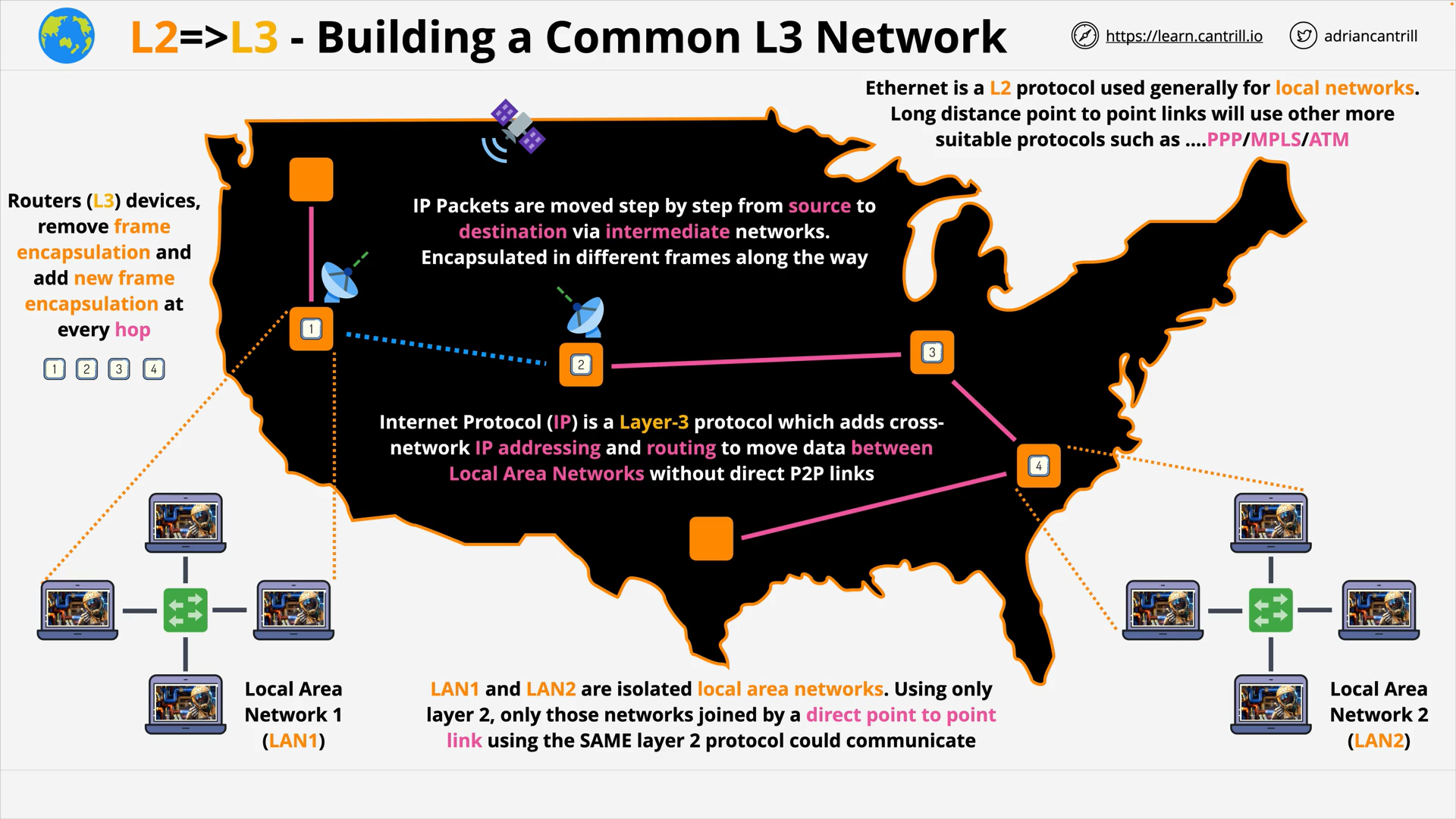 OSI Layer 3 - Routers (L3) devices, remove frame encapsulation and add new frame encapsulation at every hop 1️⃣2️⃣3️⃣4️⃣
OSI Layer 3 - Routers (L3) devices, remove frame encapsulation and add new frame encapsulation at every hop 1️⃣2️⃣3️⃣4️⃣
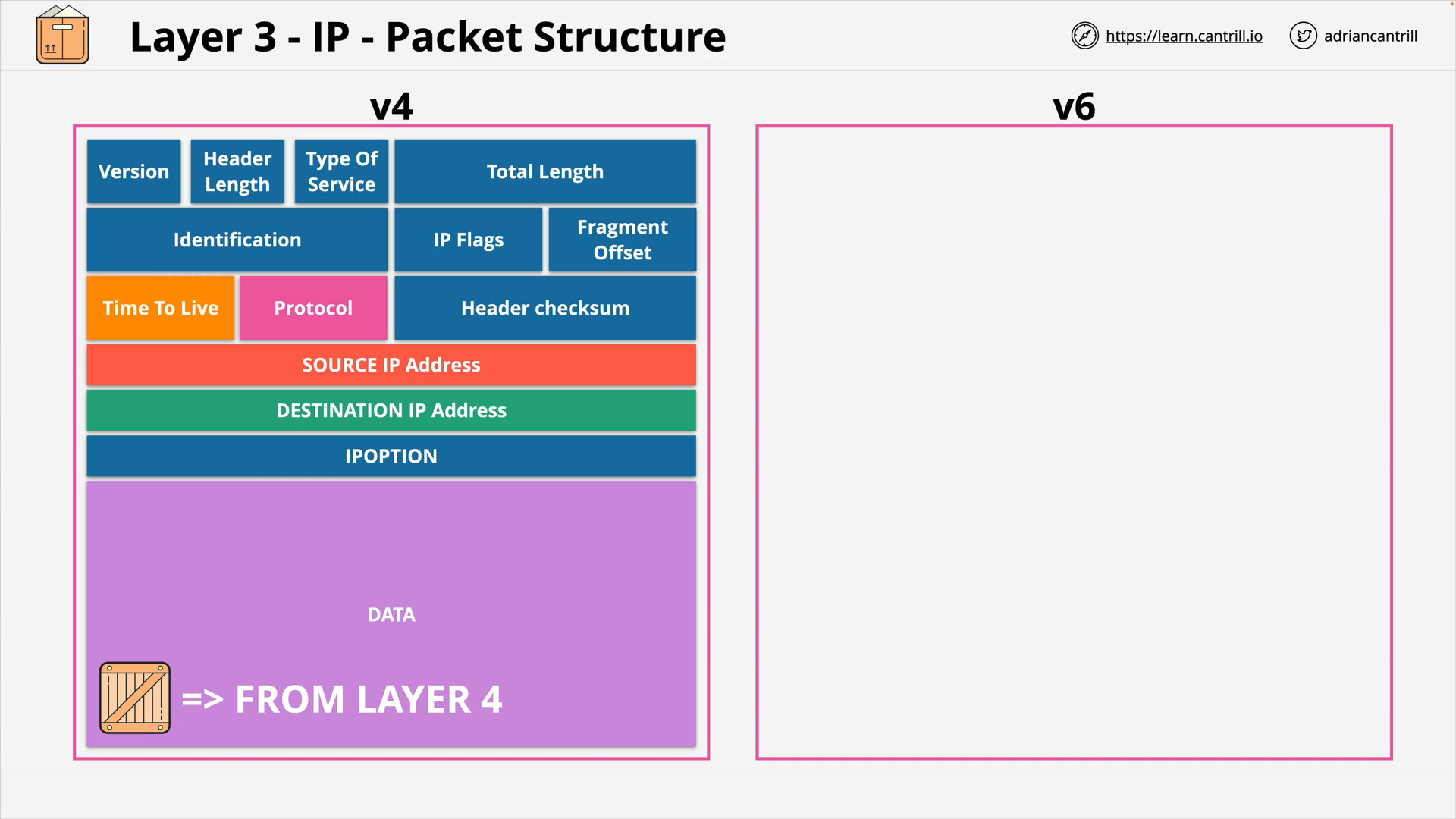 OSI Layer 3 - IP v4 package structure
OSI Layer 3 - IP v4 package structure
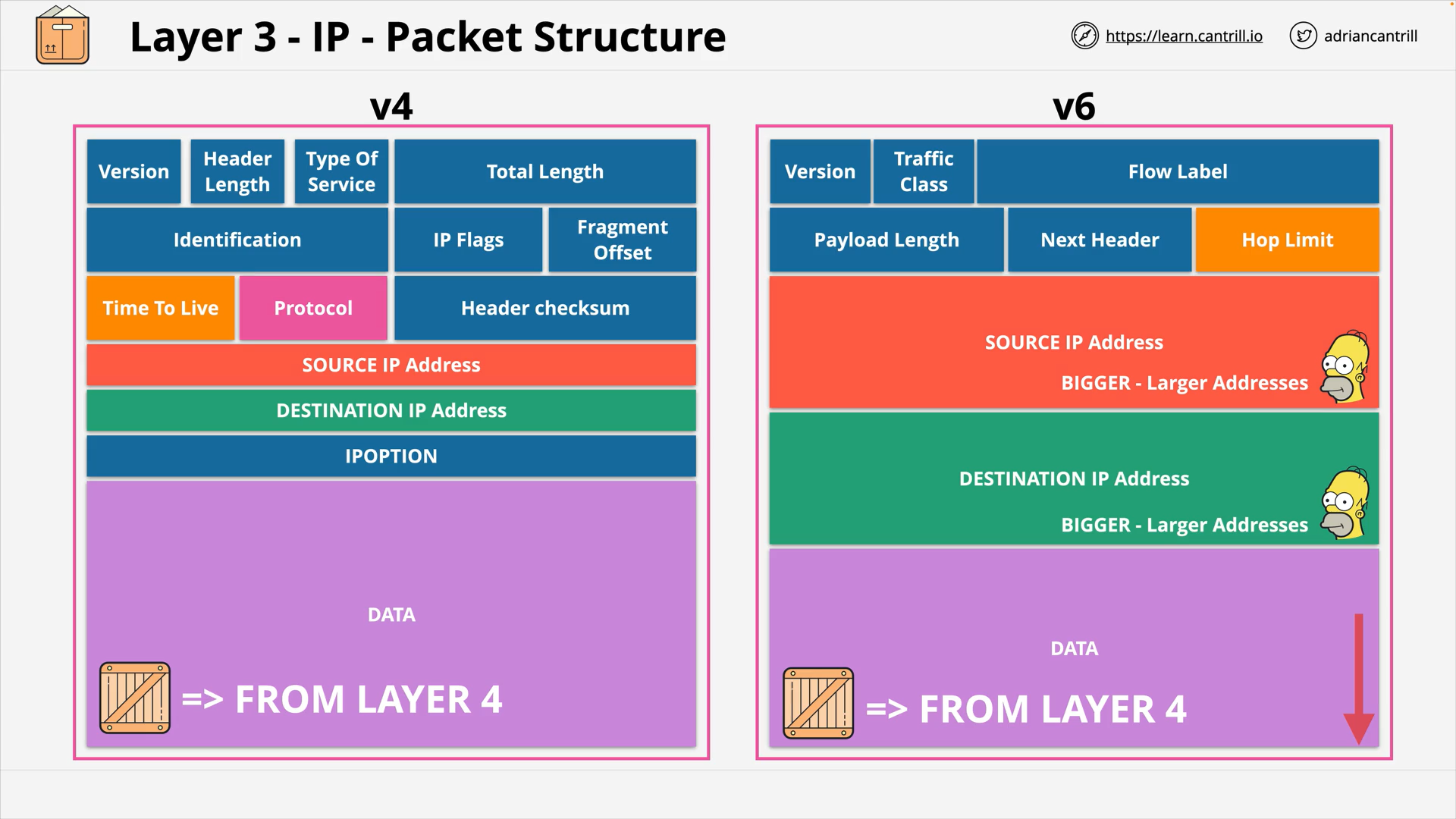 OSI Layer 3 - IP v6 package structure
OSI Layer 3 - IP v6 package structure
Layer 3 - Network - PART2 (19:13)
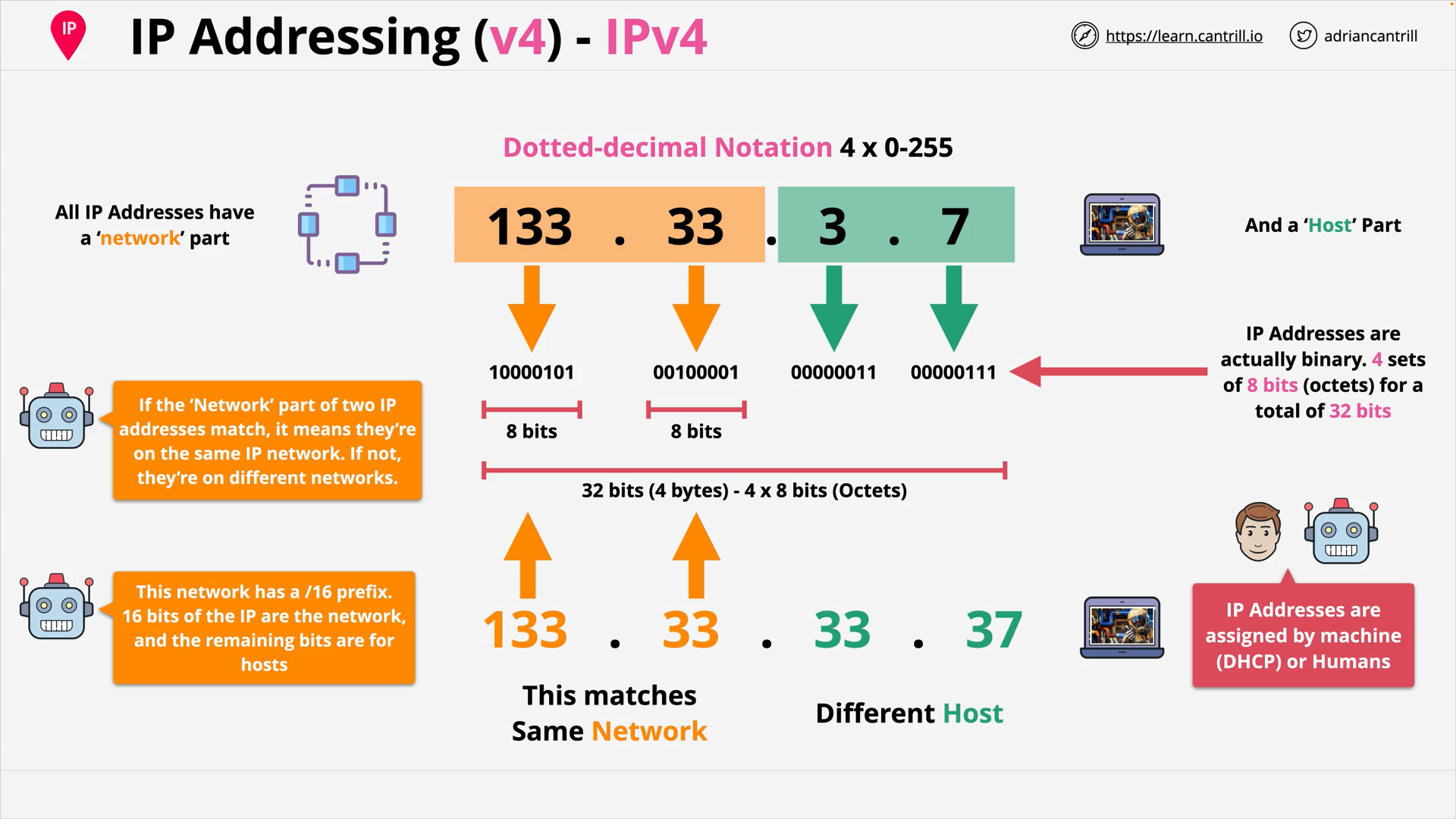 OSI Layer 3 - IPv4 Addressing
OSI Layer 3 - IPv4 Addressing
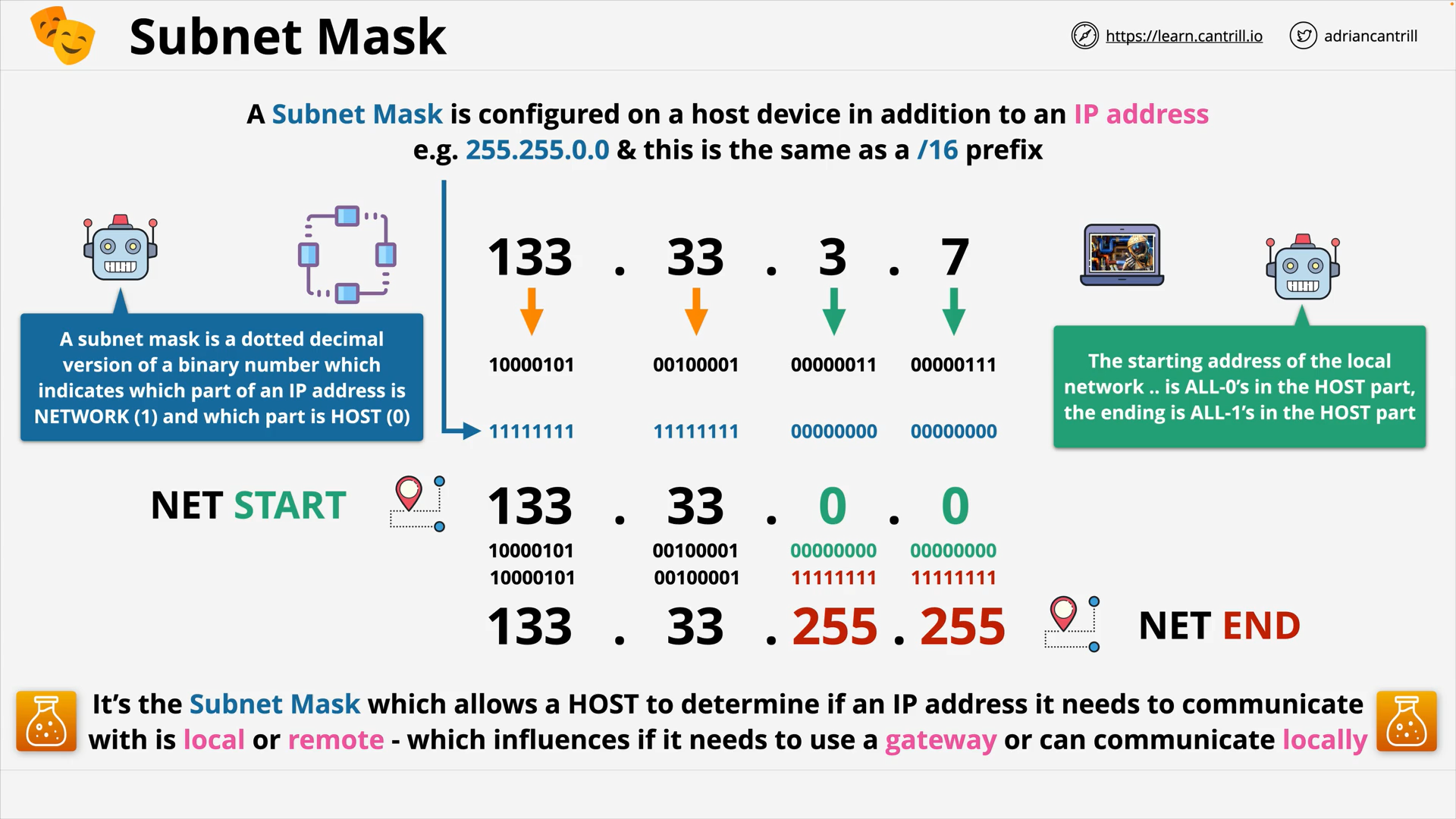 OSI Layer 3 - Subnet Mask
OSI Layer 3 - Subnet Mask
ipv4 classful addressing
Class A, class B, class C
ipv4 reserved ip address
-
Class A
- 0.0.0.0/8: Local network
- 10.0.0.0/8: Private network
- 127.0.0.0./8: Loopback of local host
-
Class B
-
169.254.0.0/16: Link-local address when no IP address is specified
- 169.254.169.254/32: AWS EC2 Instance Metadata Service
-
172.16.0.0/12: Private network
- 127.31.0.0/16: AWS default VPC size
-
-
Class C
- 192.168.0.0/16: Private network
Ref:
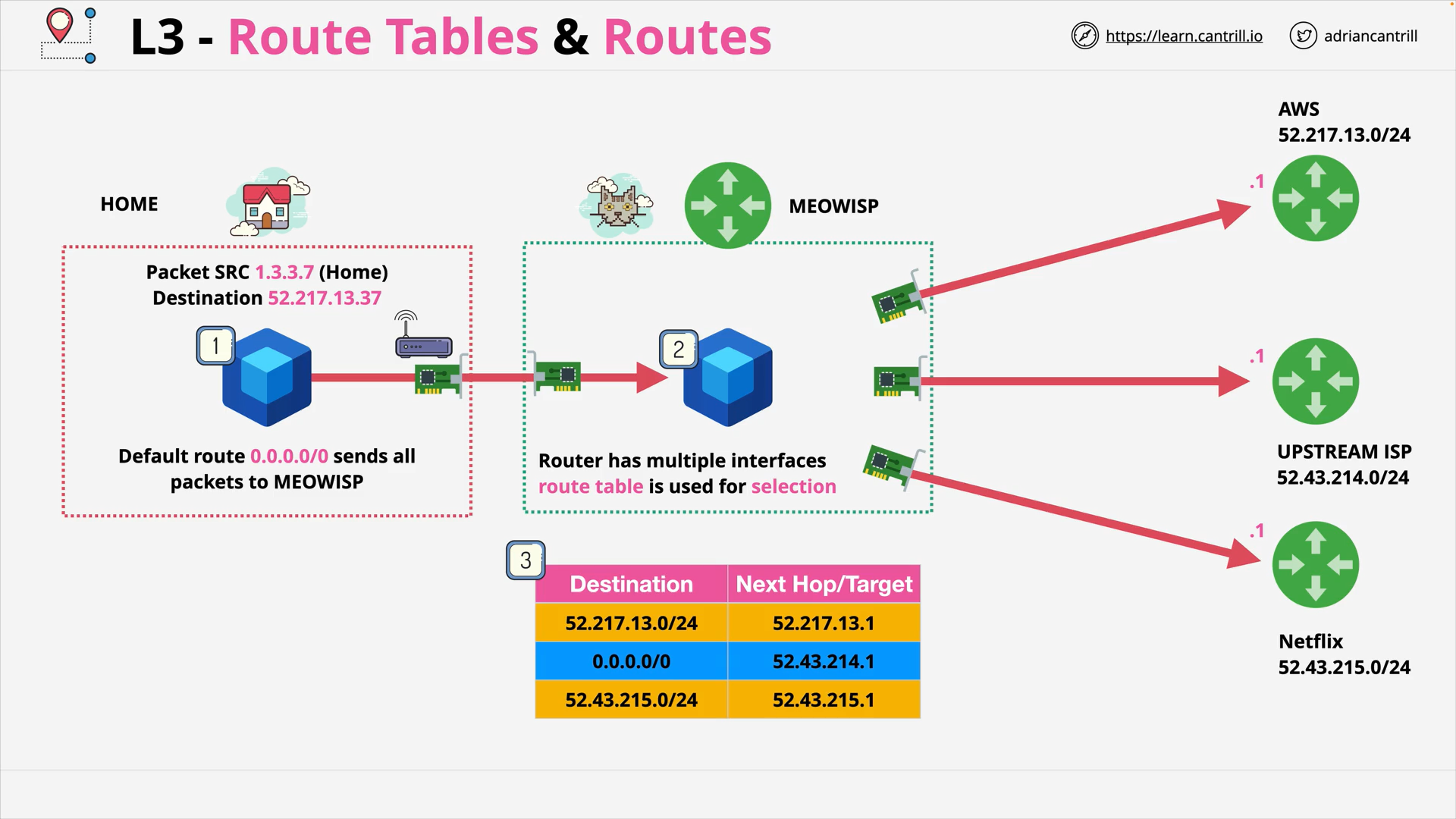 OSI Layer 3 - Route Tables & Routes
OSI Layer 3 - Route Tables & Routes
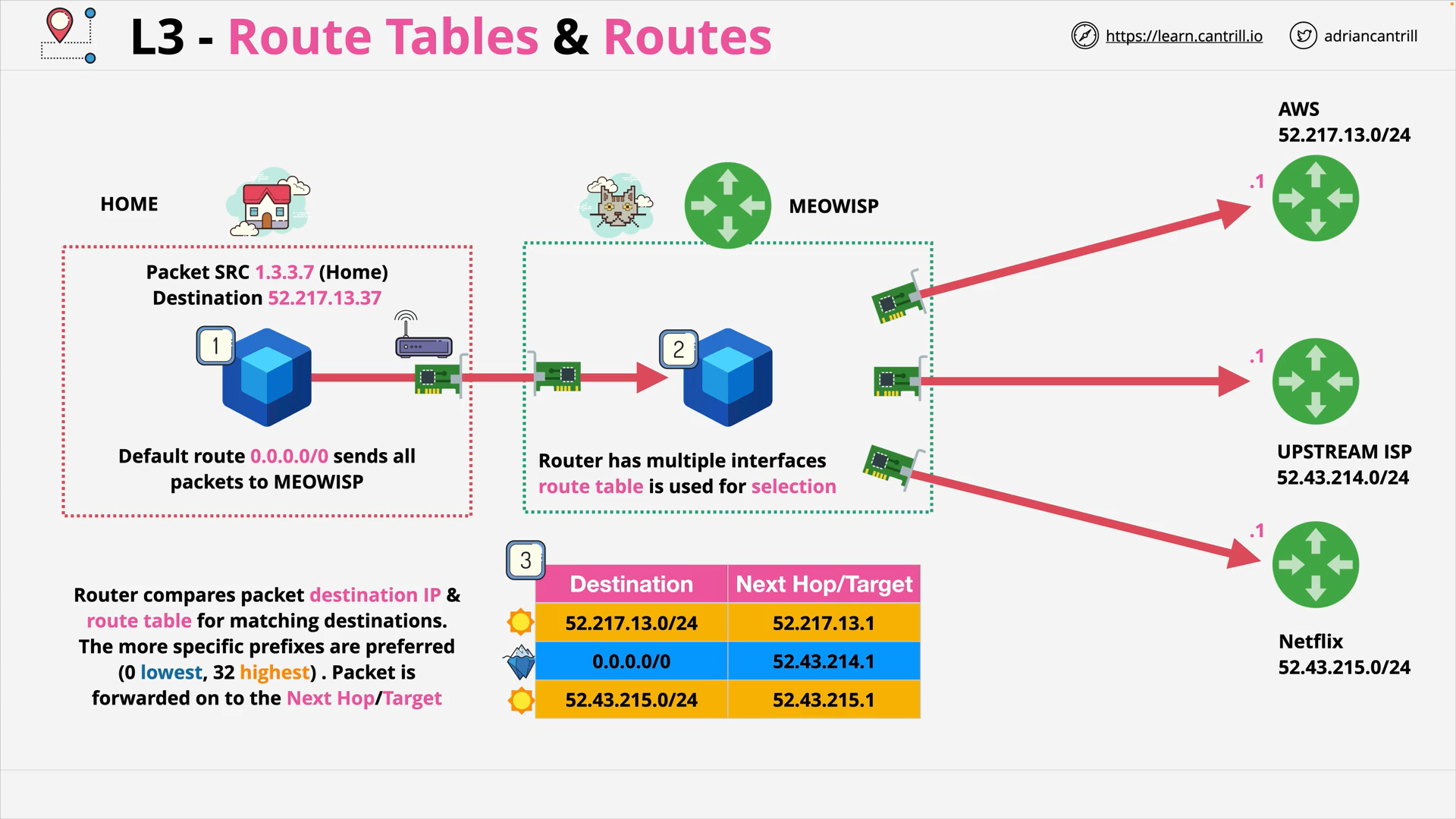 OSI Layer 3 - Router compares packet destination IP & route table for matching destinations and is forwarded on to the Next Hop/Target. The more specific prefixes are preferred (0 lowest. 32 highest)
OSI Layer 3 - Router compares packet destination IP & route table for matching destinations and is forwarded on to the Next Hop/Target. The more specific prefixes are preferred (0 lowest. 32 highest)
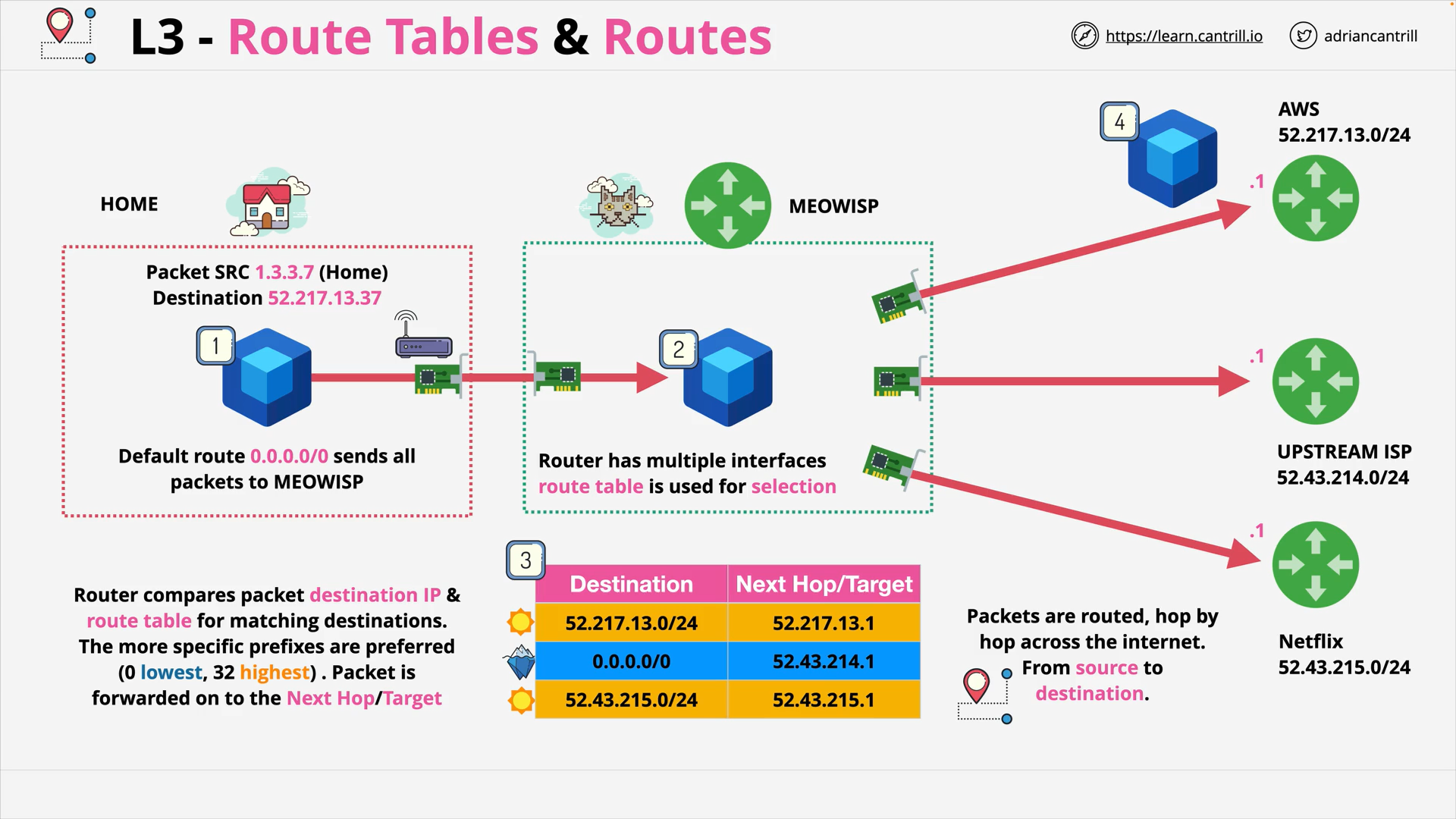 OSI Layer 3 - Packets are routed, hop by hop across the internet. From source to destination.
OSI Layer 3 - Packets are routed, hop by hop across the internet. From source to destination.
Layer 3 - Network - PART3 (15:15)
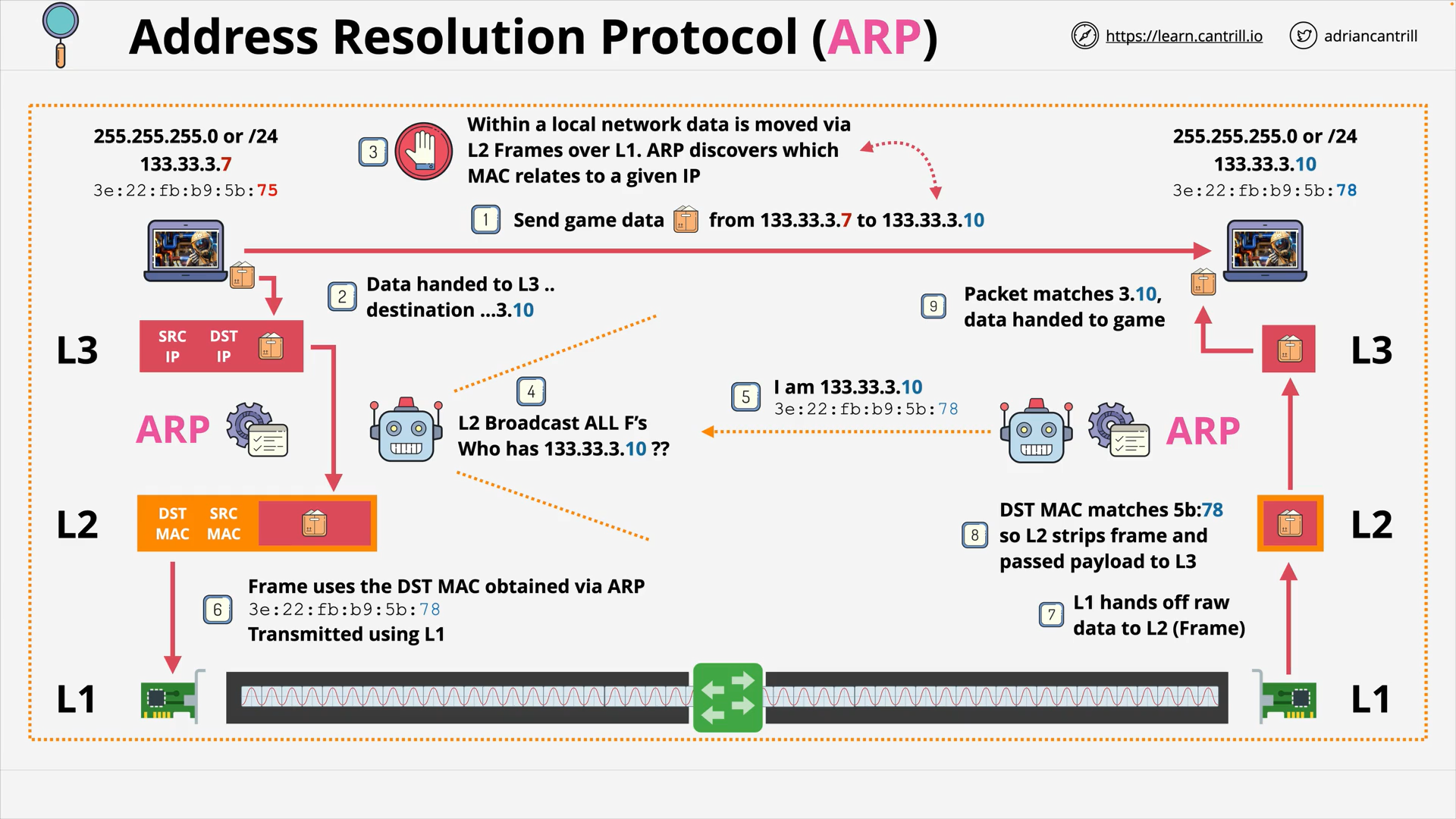 OSI Layer 3 - Address Resolution Protocol (ARP)
OSI Layer 3 - Address Resolution Protocol (ARP)
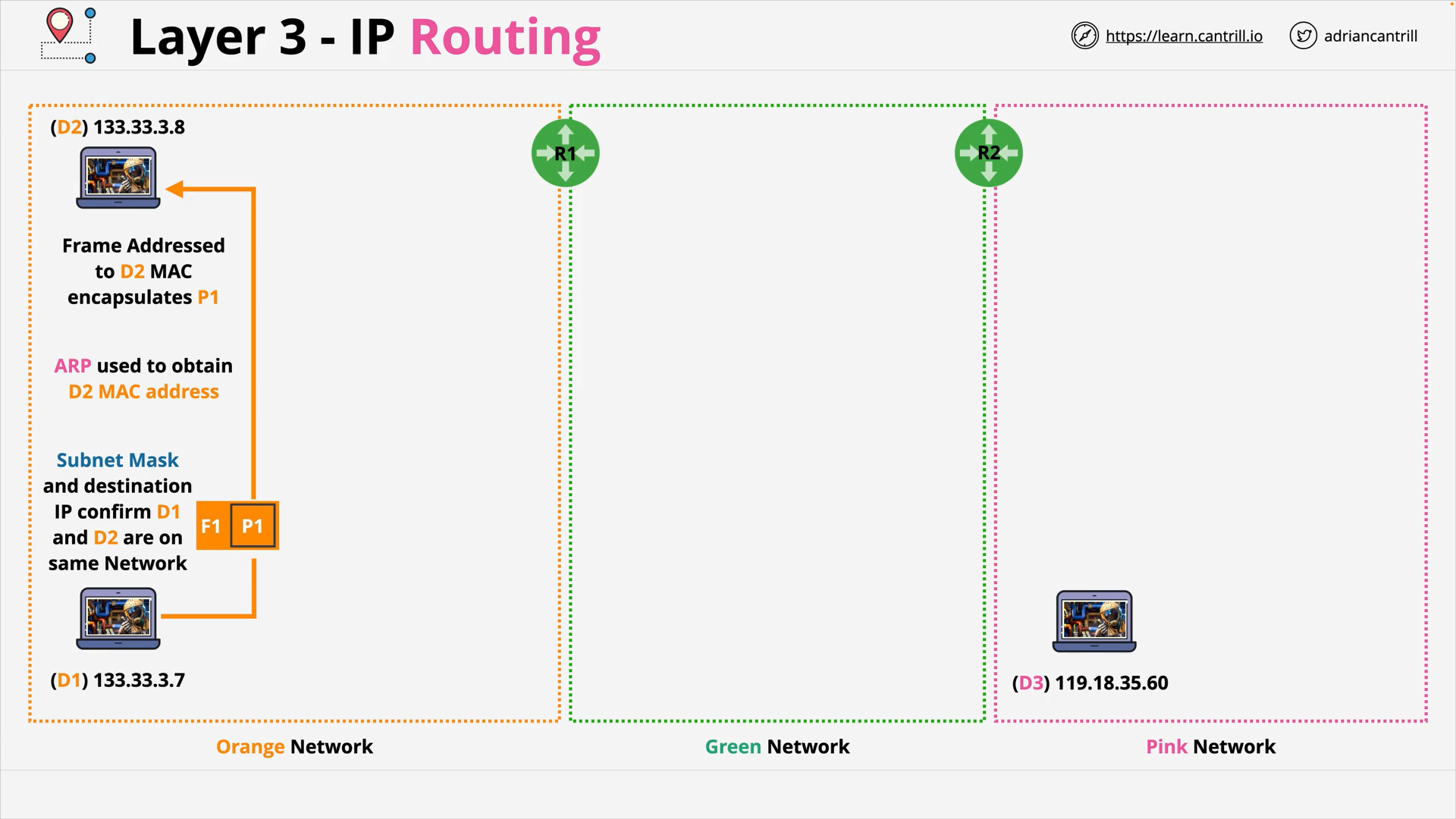 OSI Layer 3 - IP Routing - Same local network
OSI Layer 3 - IP Routing - Same local network
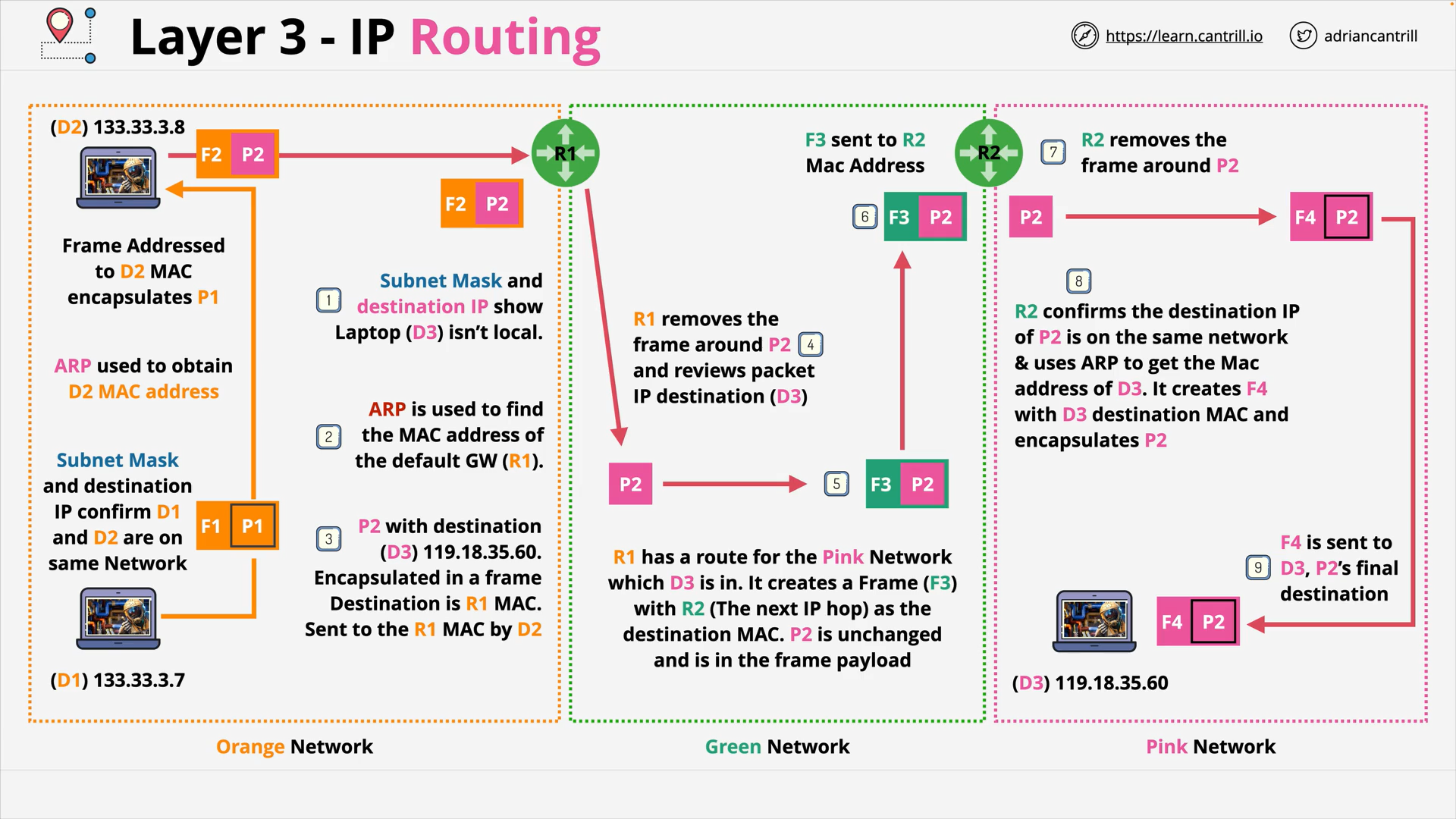 OSI Layer 3 - IP Routing - 2 different networks
OSI Layer 3 - IP Routing - 2 different networks
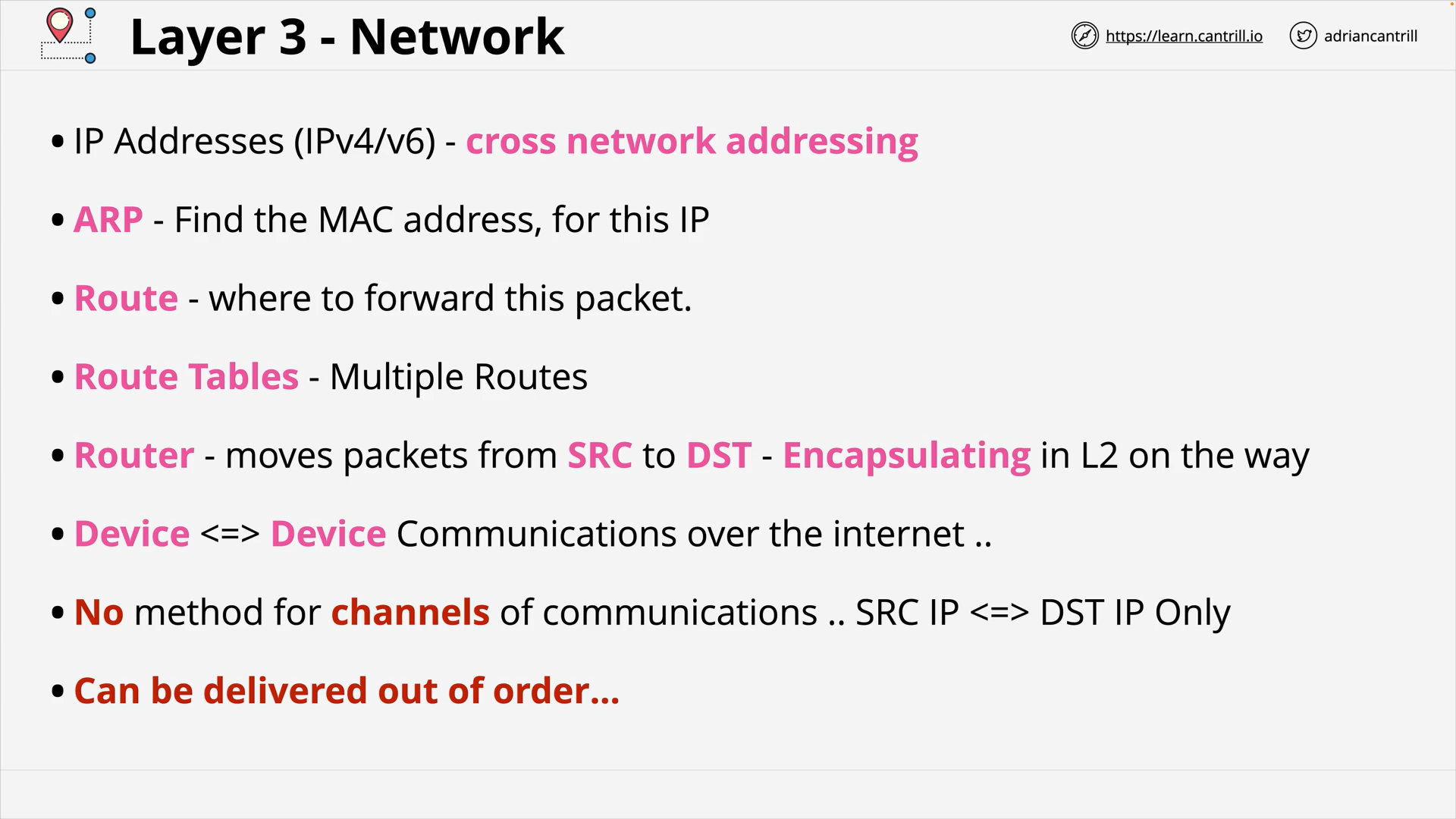 OSI Layer 3 - L3 Summary
OSI Layer 3 - L3 Summary
Layer 4&5 - Transport & Session - PART1 (15:39)
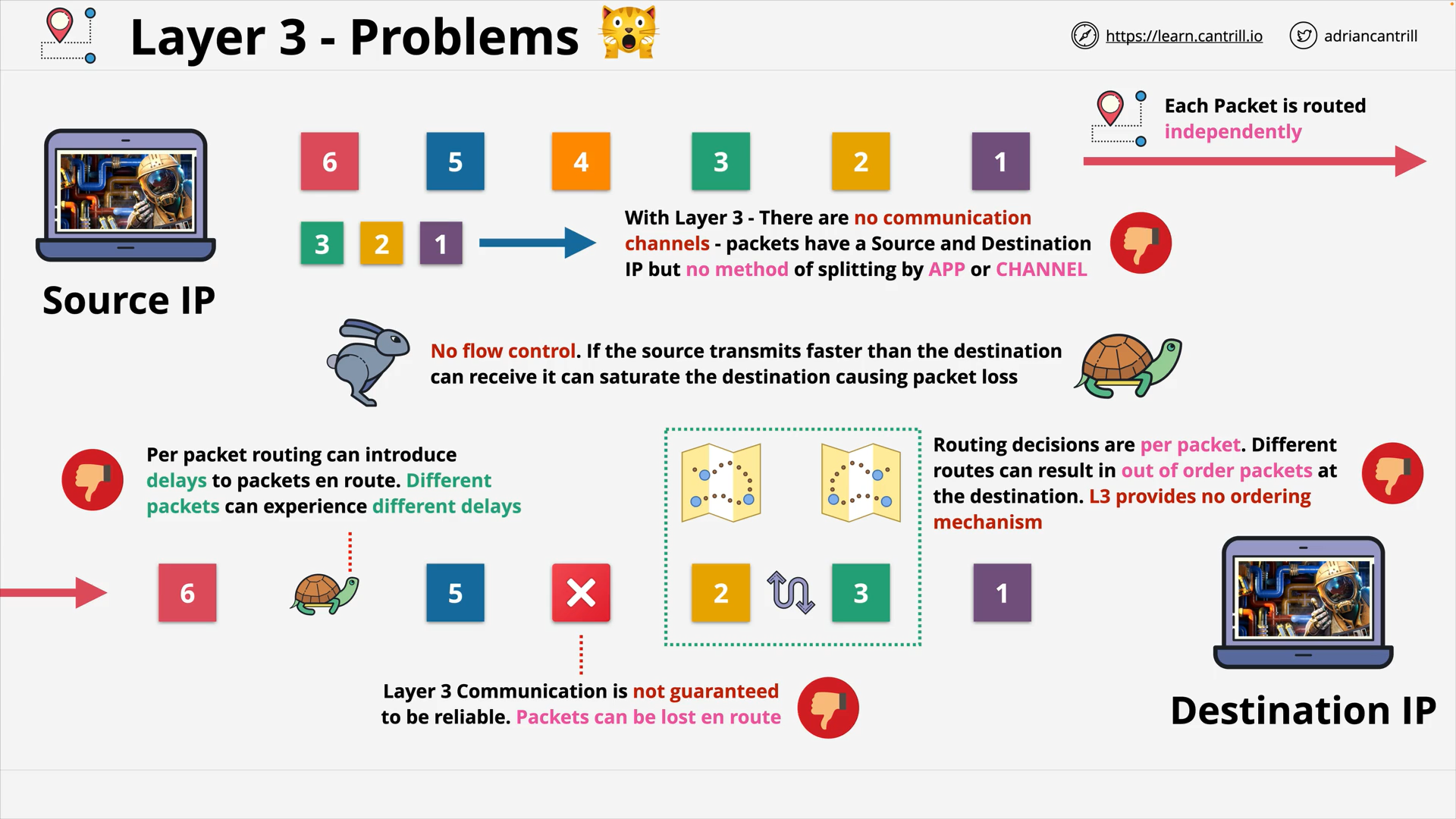 L3 problems
L3 problems
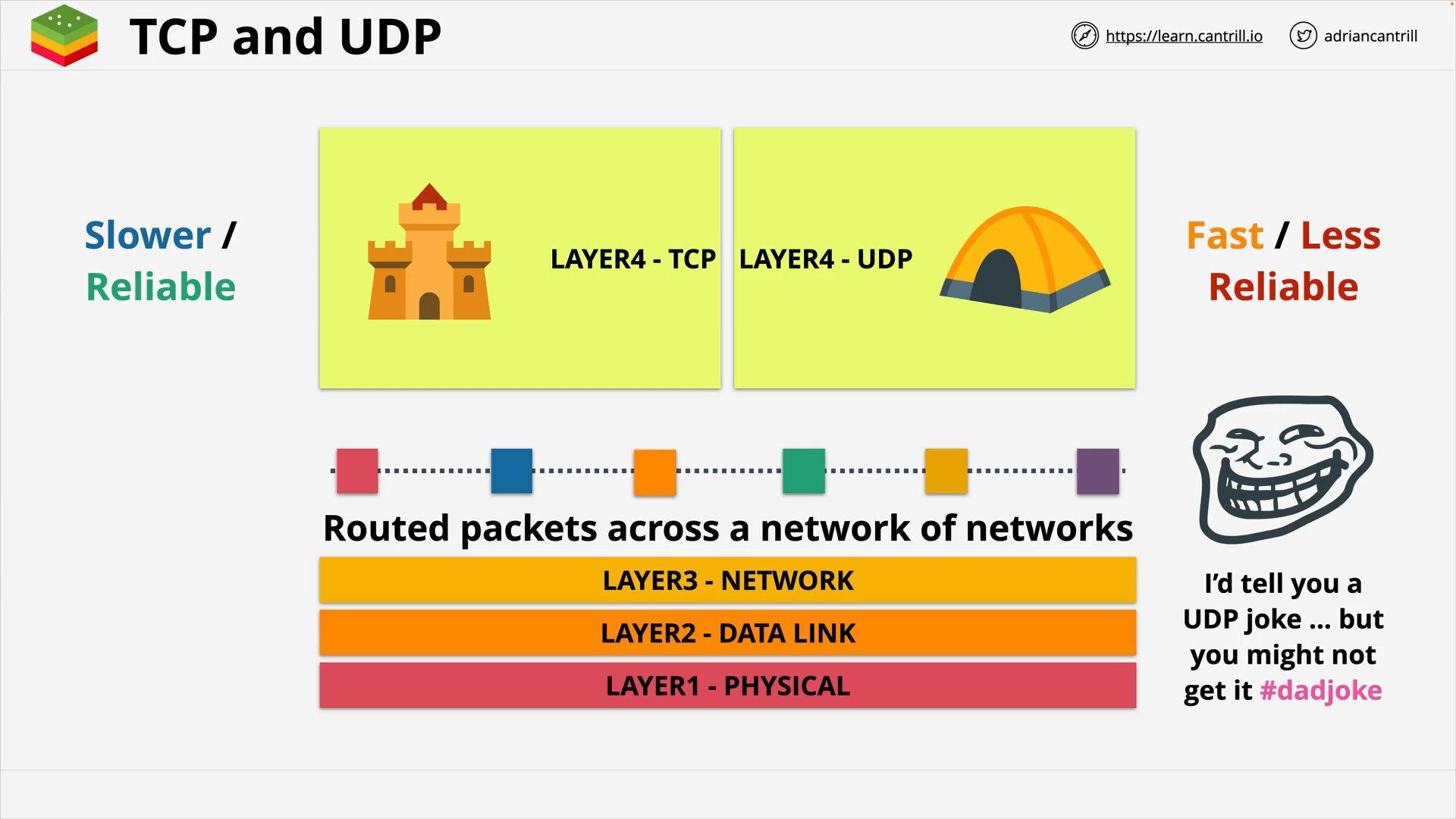 TCP & UDP
TCP & UDP
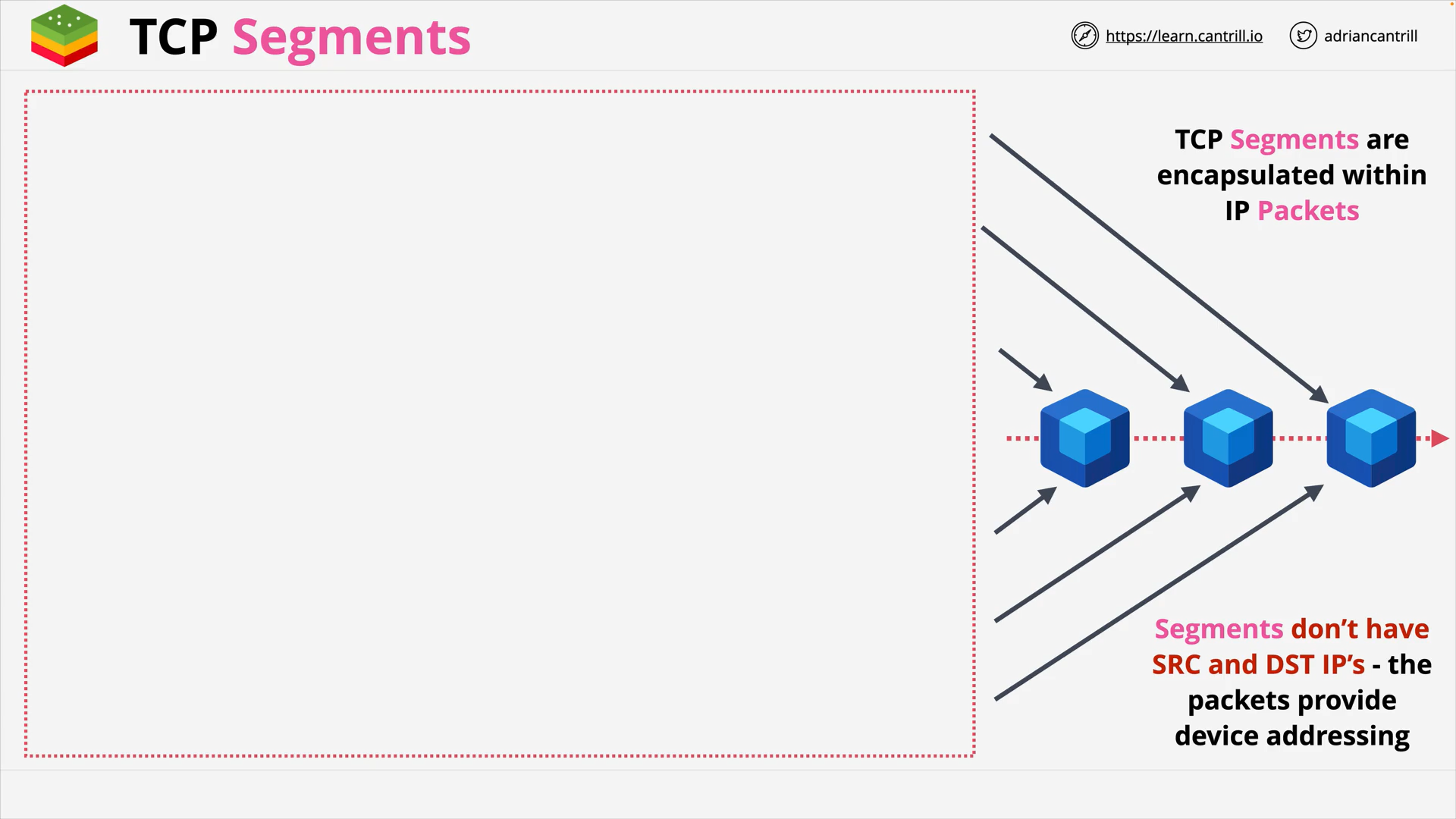 TCP Segments
TCP Segments
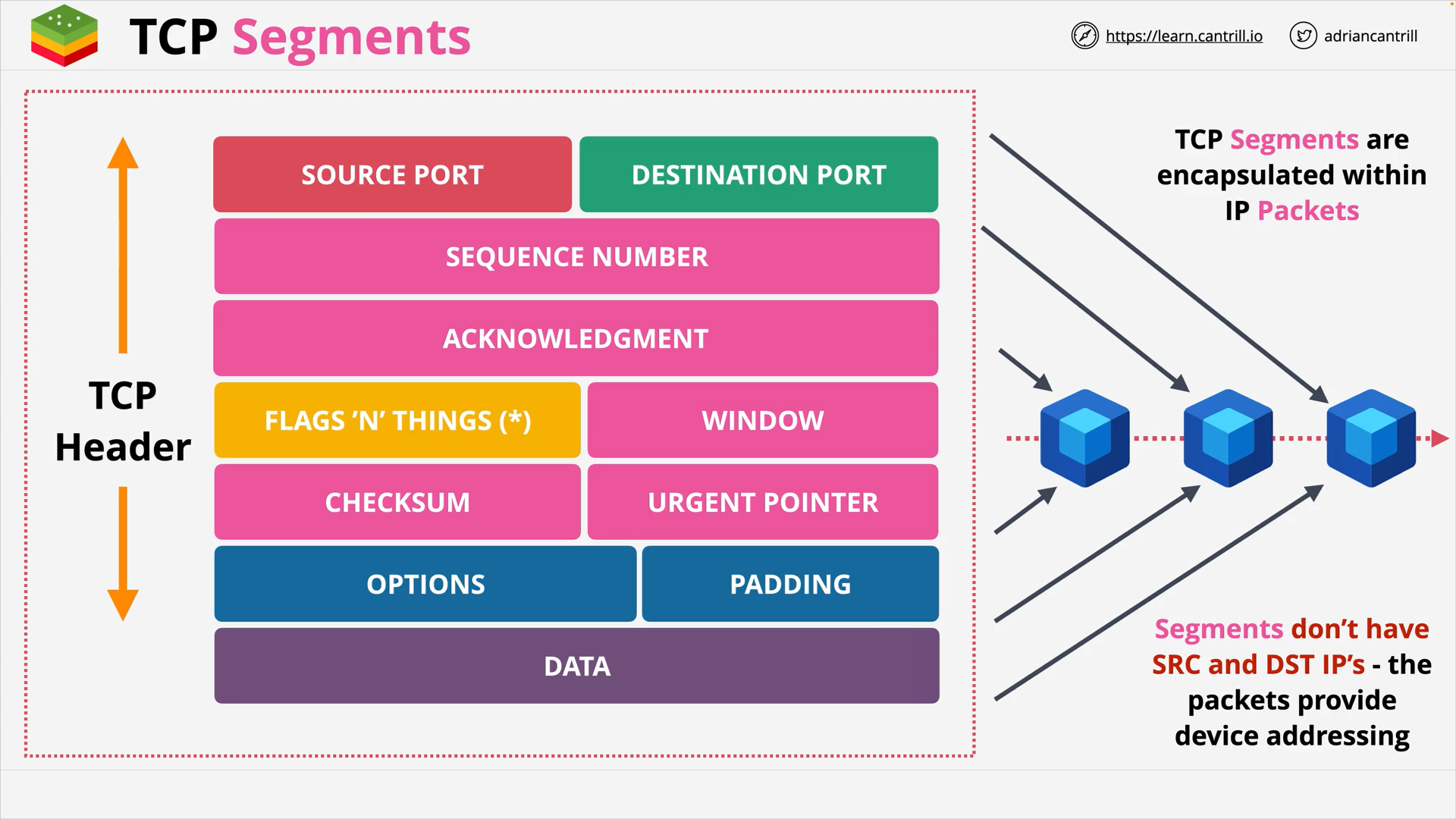 TCP Header
TCP Header
Layer 4&5 - Transport & Session - PART2 (13:54)
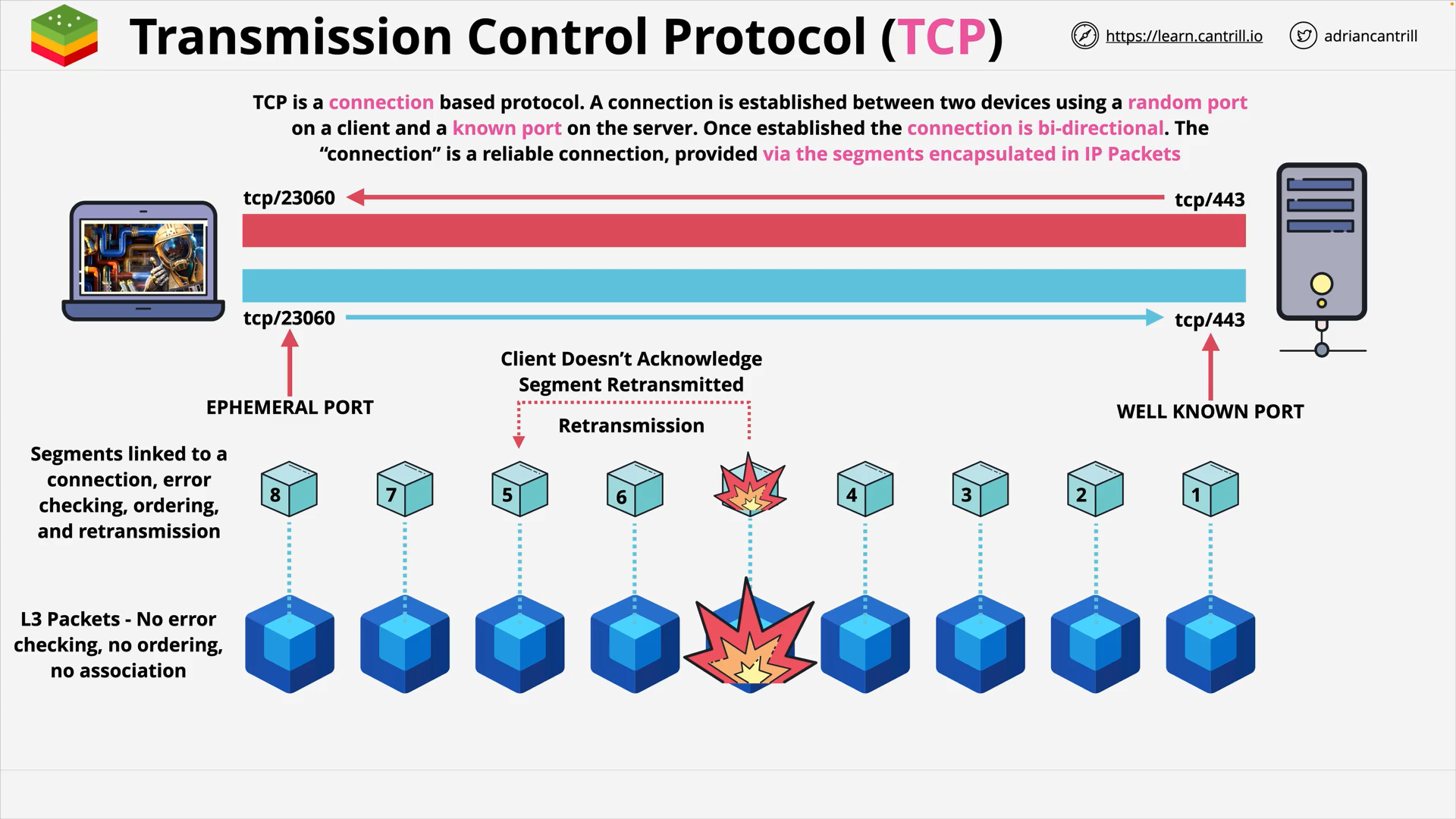 Transmission Control Protocol (TCP) is a connection based protocol.
Transmission Control Protocol (TCP) is a connection based protocol.
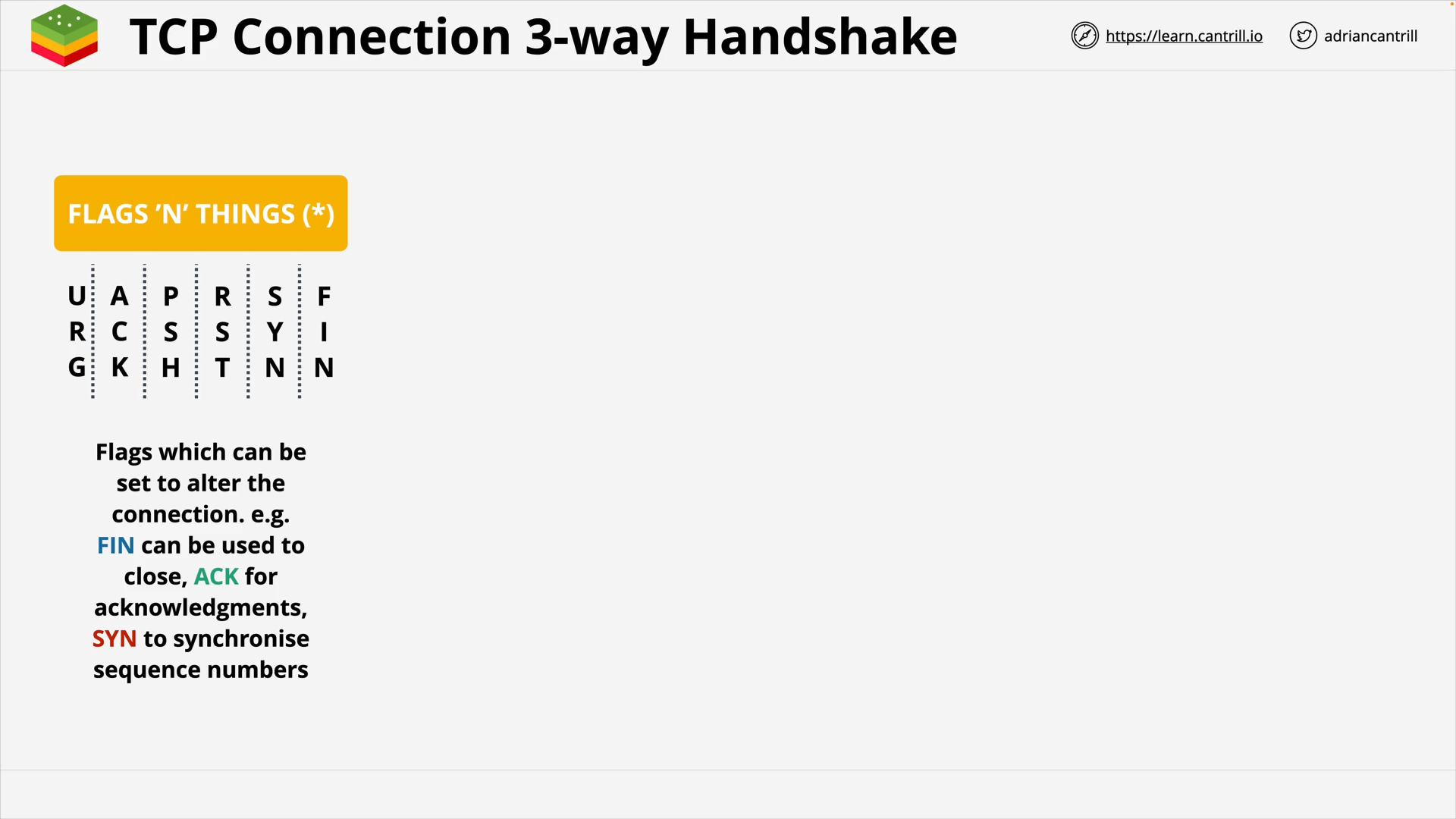 TCP Flags 🏴🏳️
TCP Flags 🏴🏳️
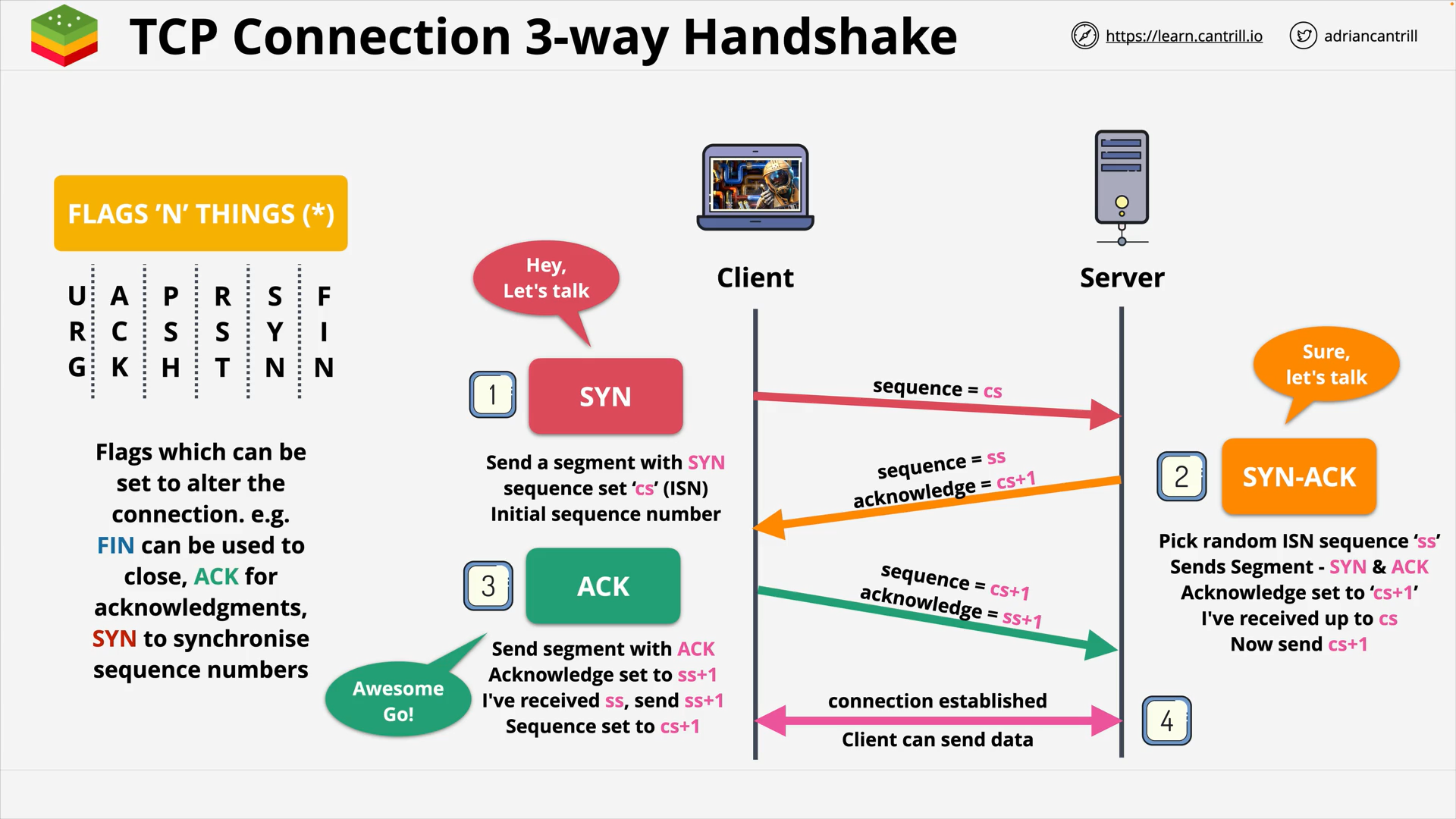 TCP Connection 3-way Handshake 🤝
TCP Connection 3-way Handshake 🤝
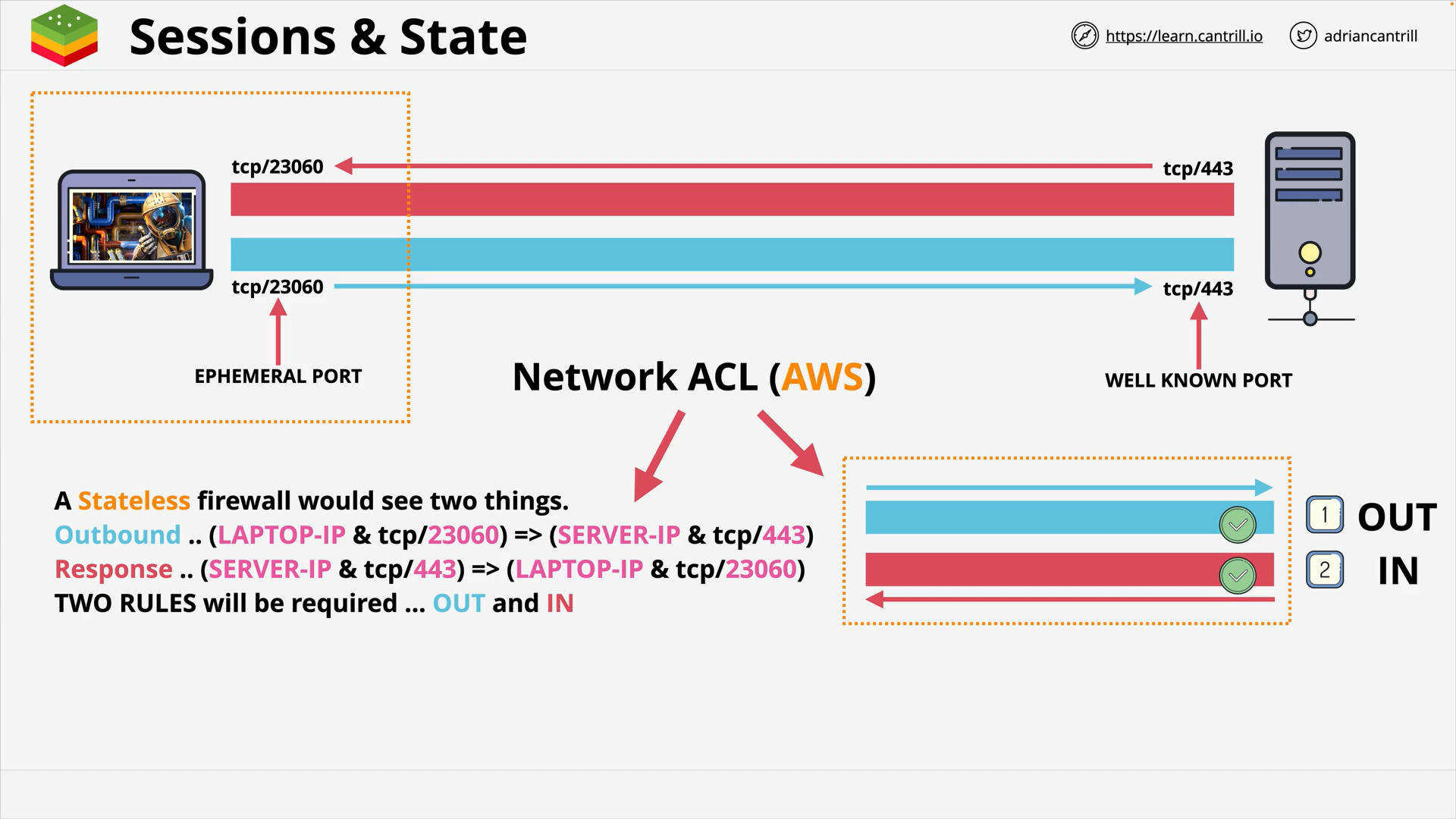 Stateless firewall
Stateless firewall
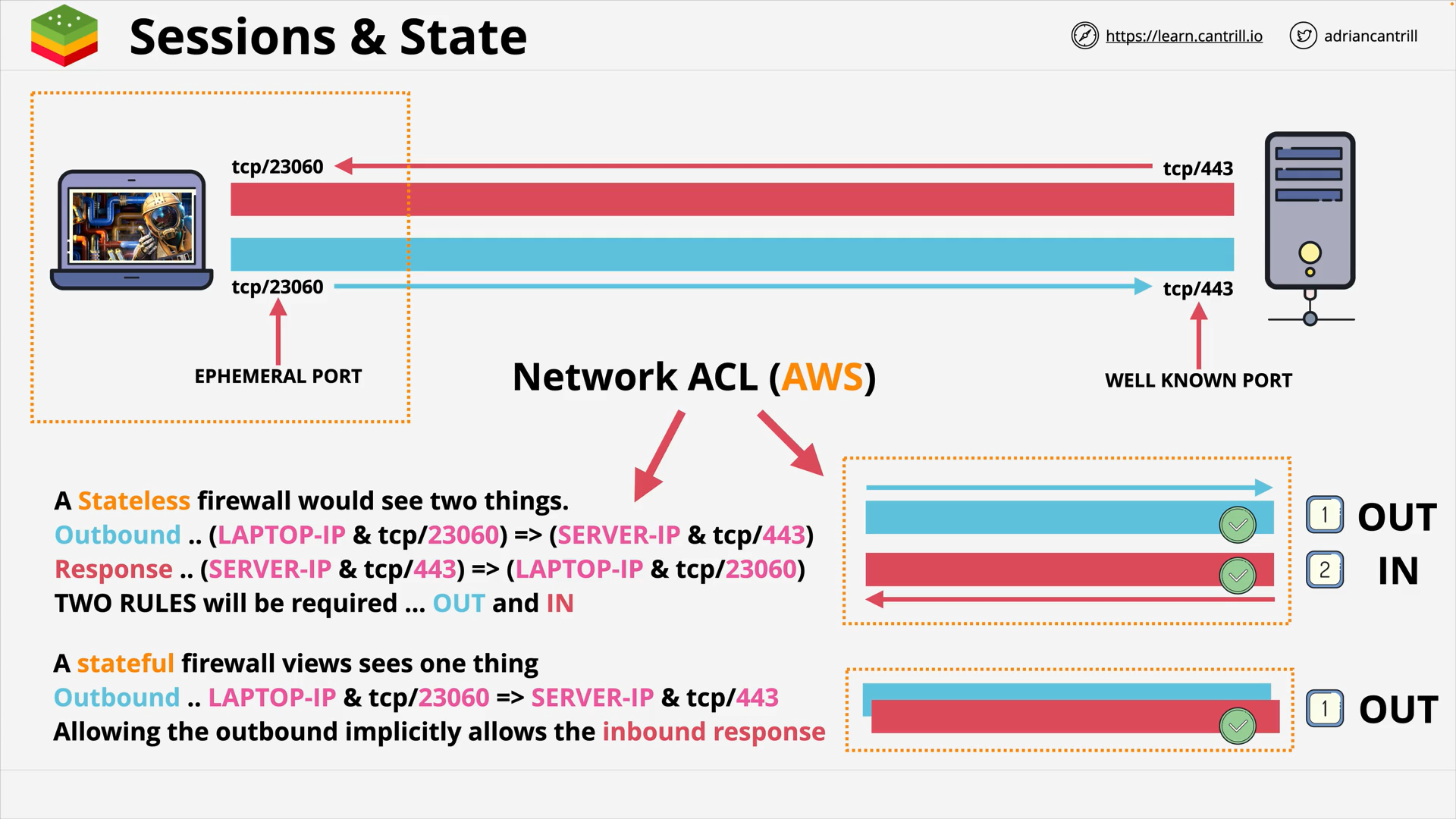 Stateful firewall
Stateful firewall
Other Networking (MORE COMING SOON)
Network Address Translation (NAT) - PART1 (11:00)
_-_PART1__learn.c.png) NAT - Types of NATs
NAT - Types of NATs
why nat?
- Overcome IPv4 shortages.
- Security: hide private IP
_-_PART1__learn.c.png) Static NAT - Outbound Traffic
Static NAT - Outbound Traffic
static nat maintains a nat table to map privateip : public ip (1:1)>
👉️ In AWS, Internet Gateway (IGW) is a static NAT.
_-_PART1__learn.c.png) Static NAT - Inbound Traffic👉️
Static NAT - Inbound Traffic👉️
Network Address Translation (NAT) - PART2 (9:38)
_-_PART2__learn.c.png) Dynamic NAT
Dynamic NAT
dynamic nat maintains a nat table:
- Dynamic NAT maps PrivateIP : Public IP (1:1 first available).
- Public IP allocations are temporary allocations from a Public IP Pool, the pool may be out-of-public IPs.
_-_PART2__learn.c.png) Port Address Translating (PAT)
Port Address Translating (PAT)
pat records the source (private) ip and source port:
- PAT replaces the source IP with the single Public IP and a public source port
- The Public IP and public source port are allocated from a pool which allows IP Overloading (many to one)
in aws, nat gateway (natgw) is a pat.
nat vs pat
- NAT
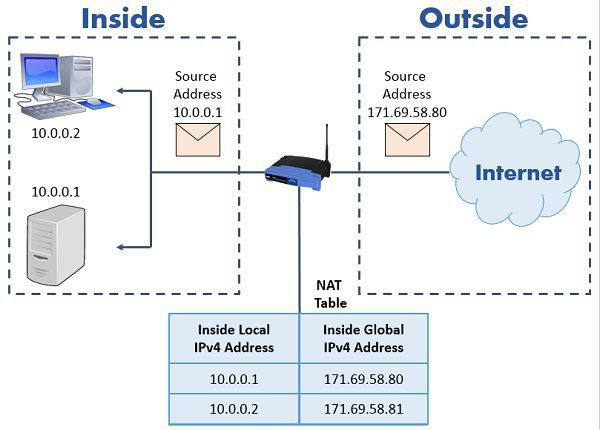
- PAT: is a type of Dynamic NAT
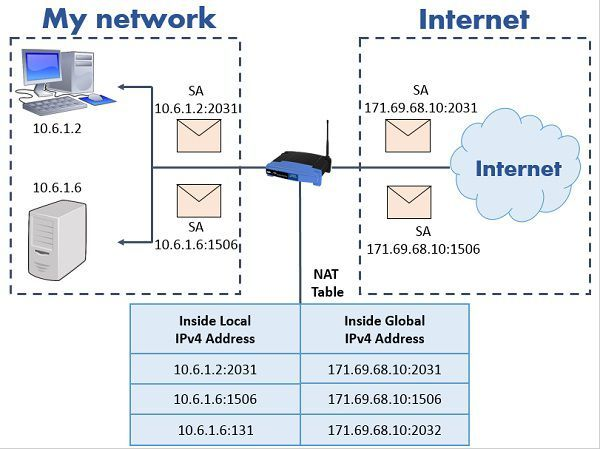
Ref: https://techdifferences.com/difference-between-nat-and-pat.html
IP Address Space & Subnetting - PART1 (14:37)
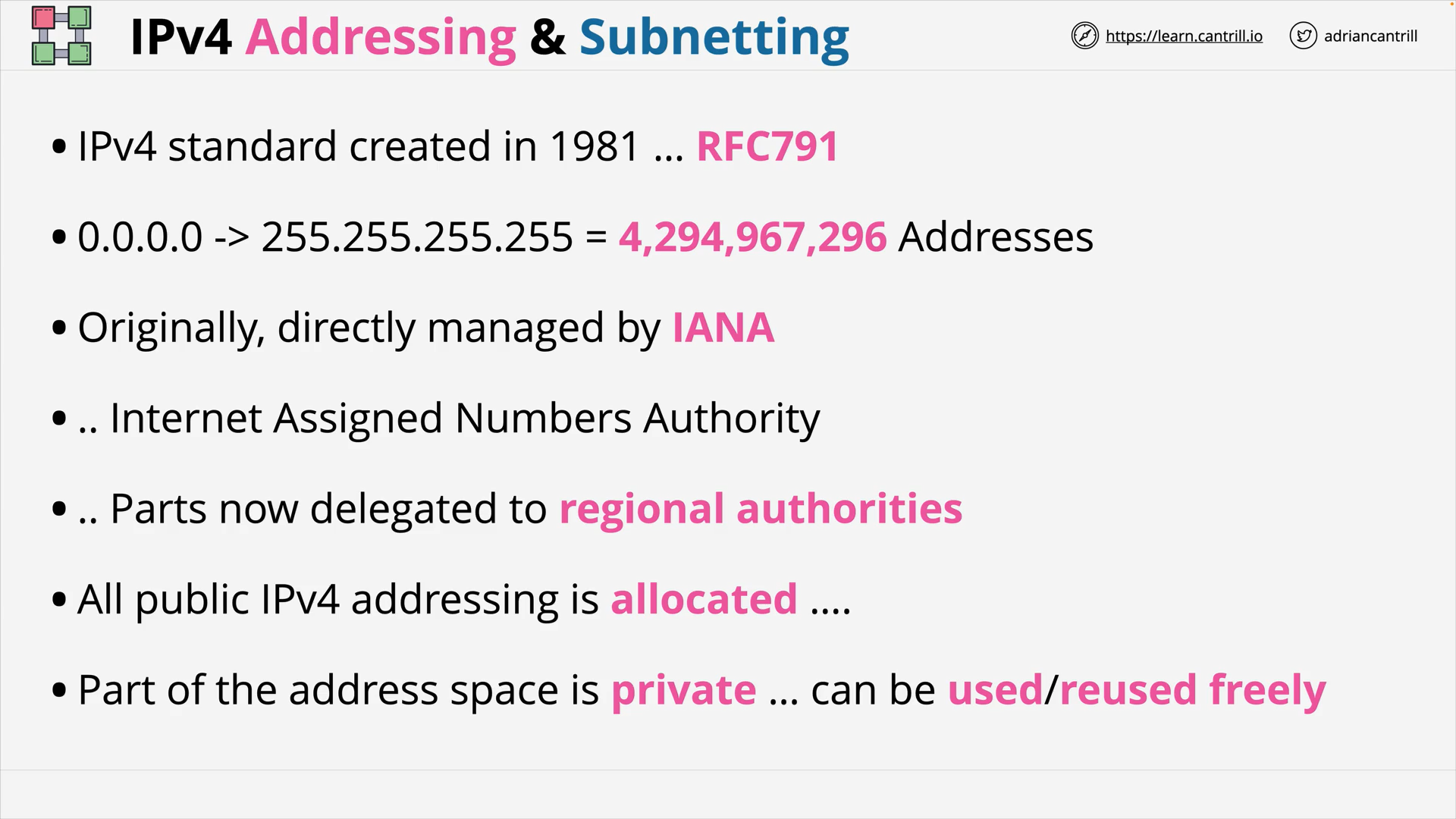 IPv4 Addressing
IPv4 Addressing
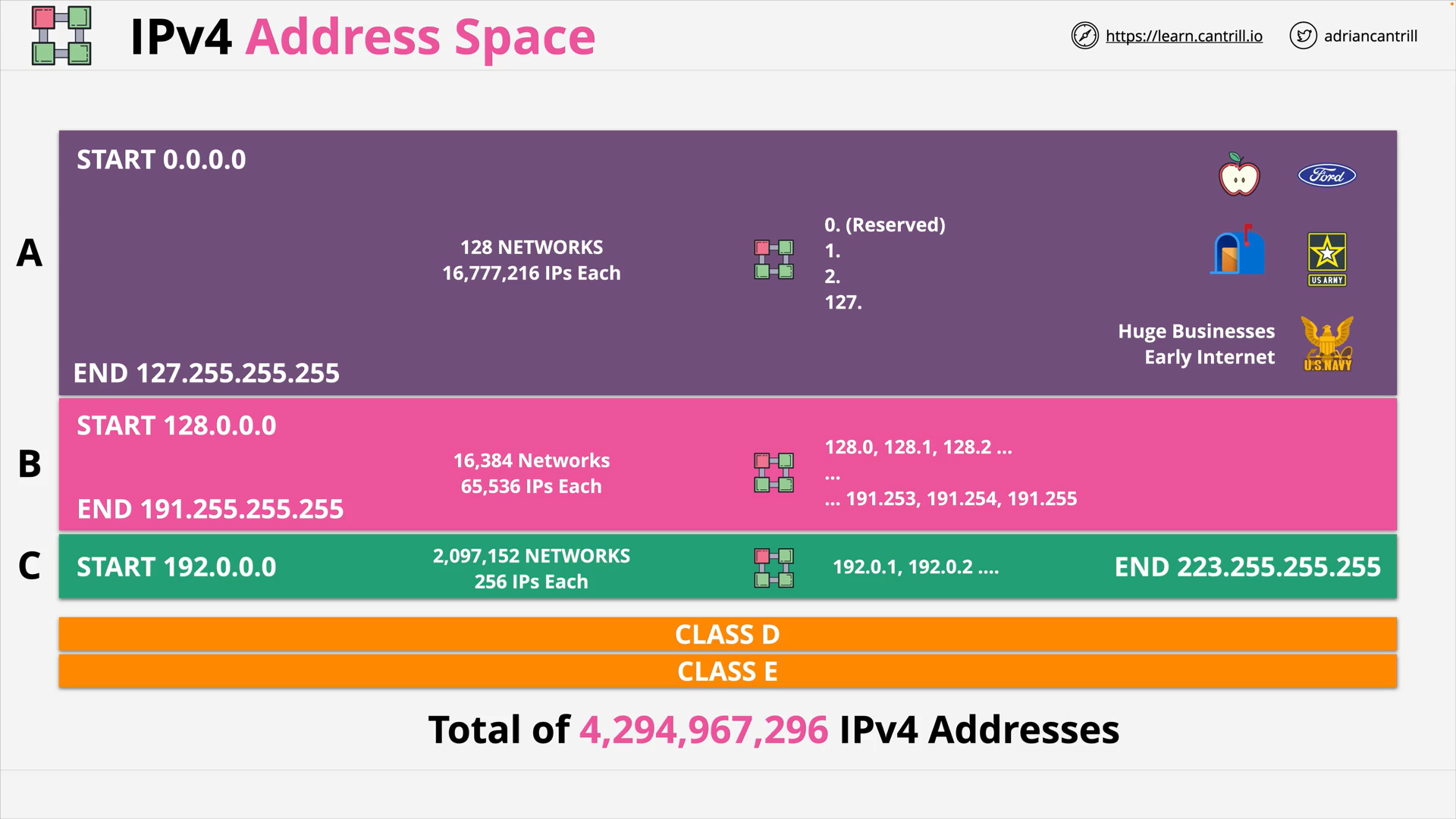 IPv4 Address Space
IPv4 Address Space
IP Address Space & Subnetting - PART2 (10:32)
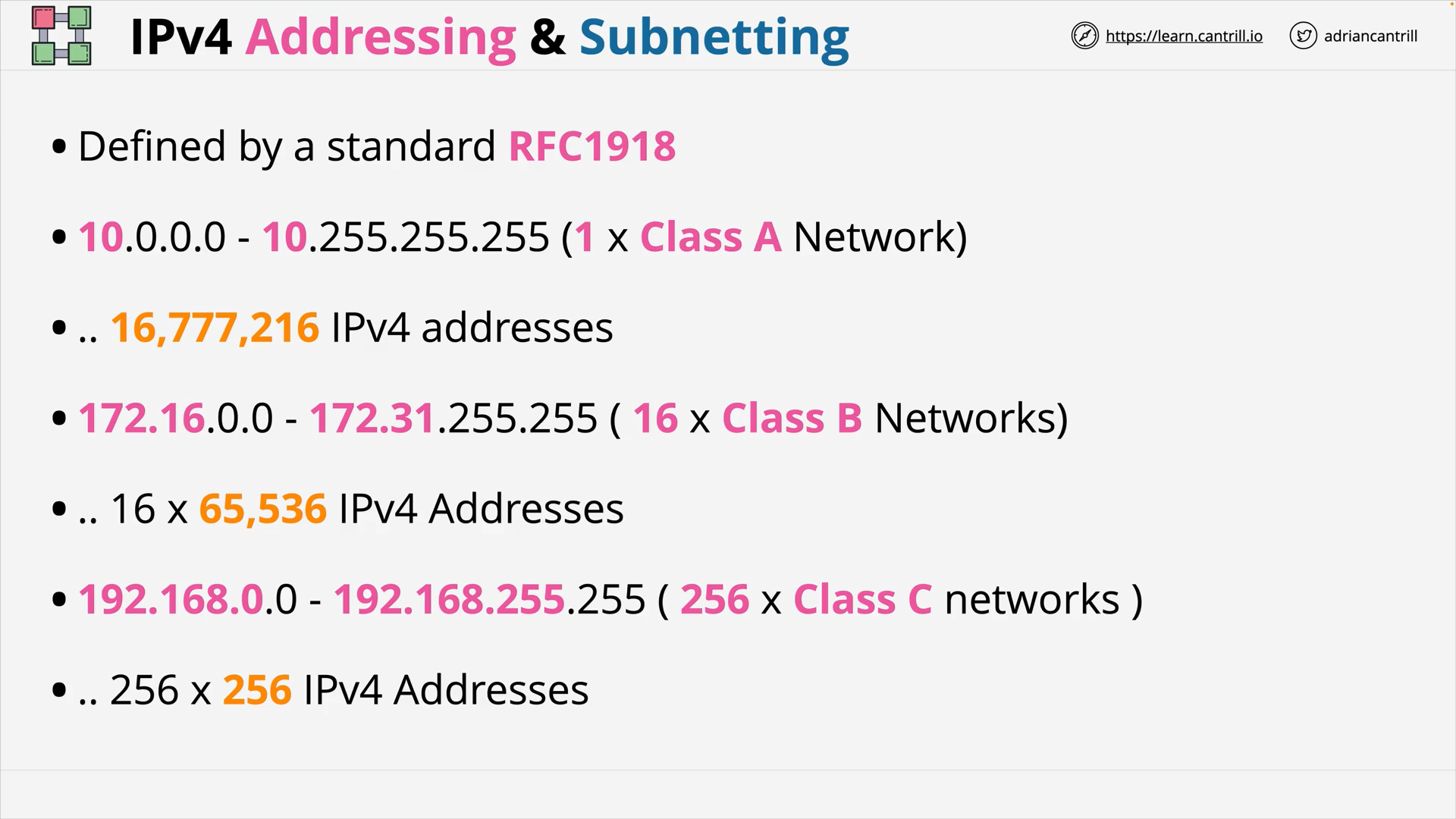 IPv4 - Private Ranges
IPv4 - Private Ranges
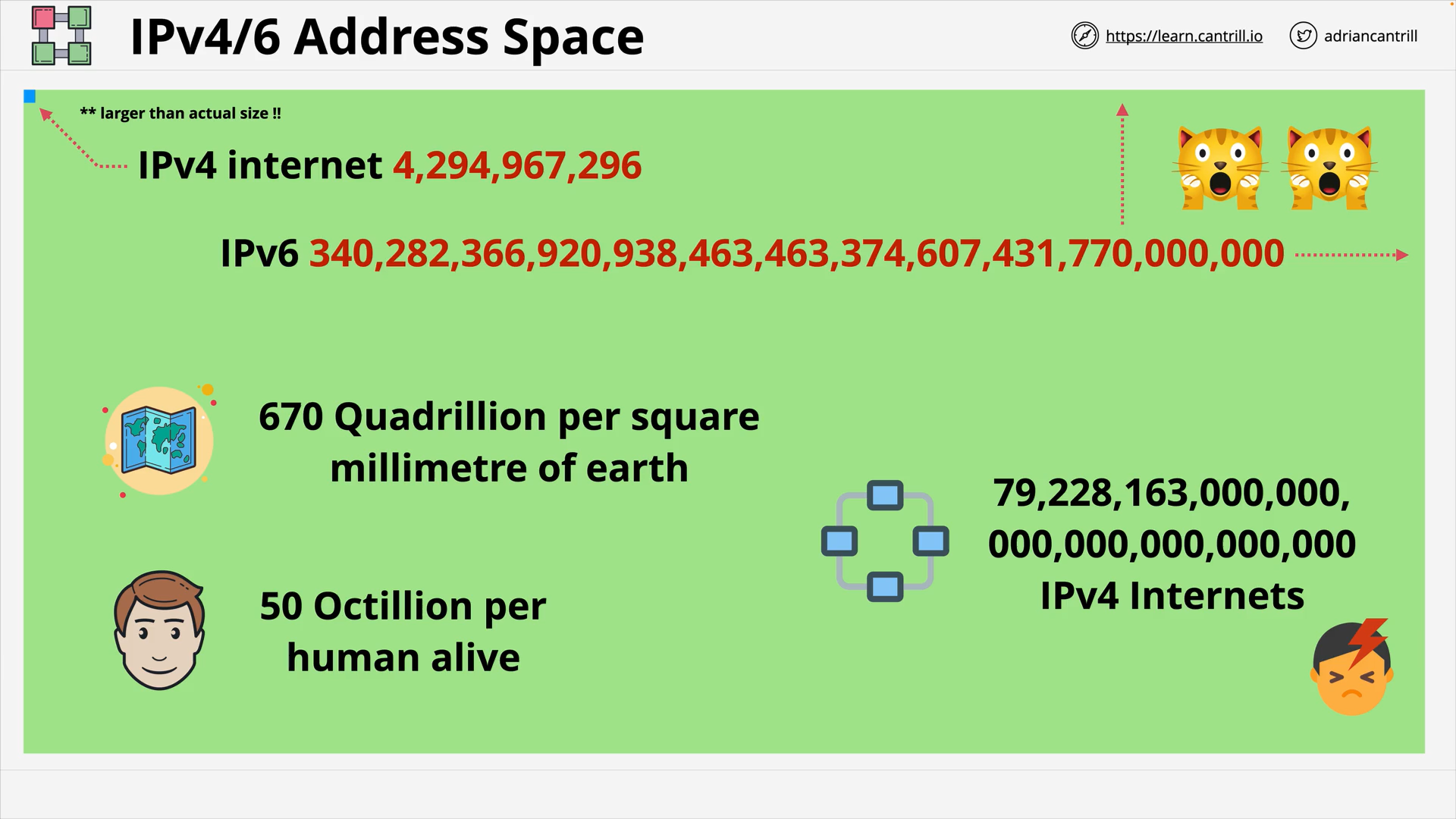 IPv4 vs IPv6 Address Space
IPv4 vs IPv6 Address Space
classless inter-domain routing (cidr)
A method for allocating IP addresses and for IP routing.
CIDR is introduced in 1993 to replace the previous classful network addressing architecture
subnetting
The process of spitting a larger network into more smaller subnets
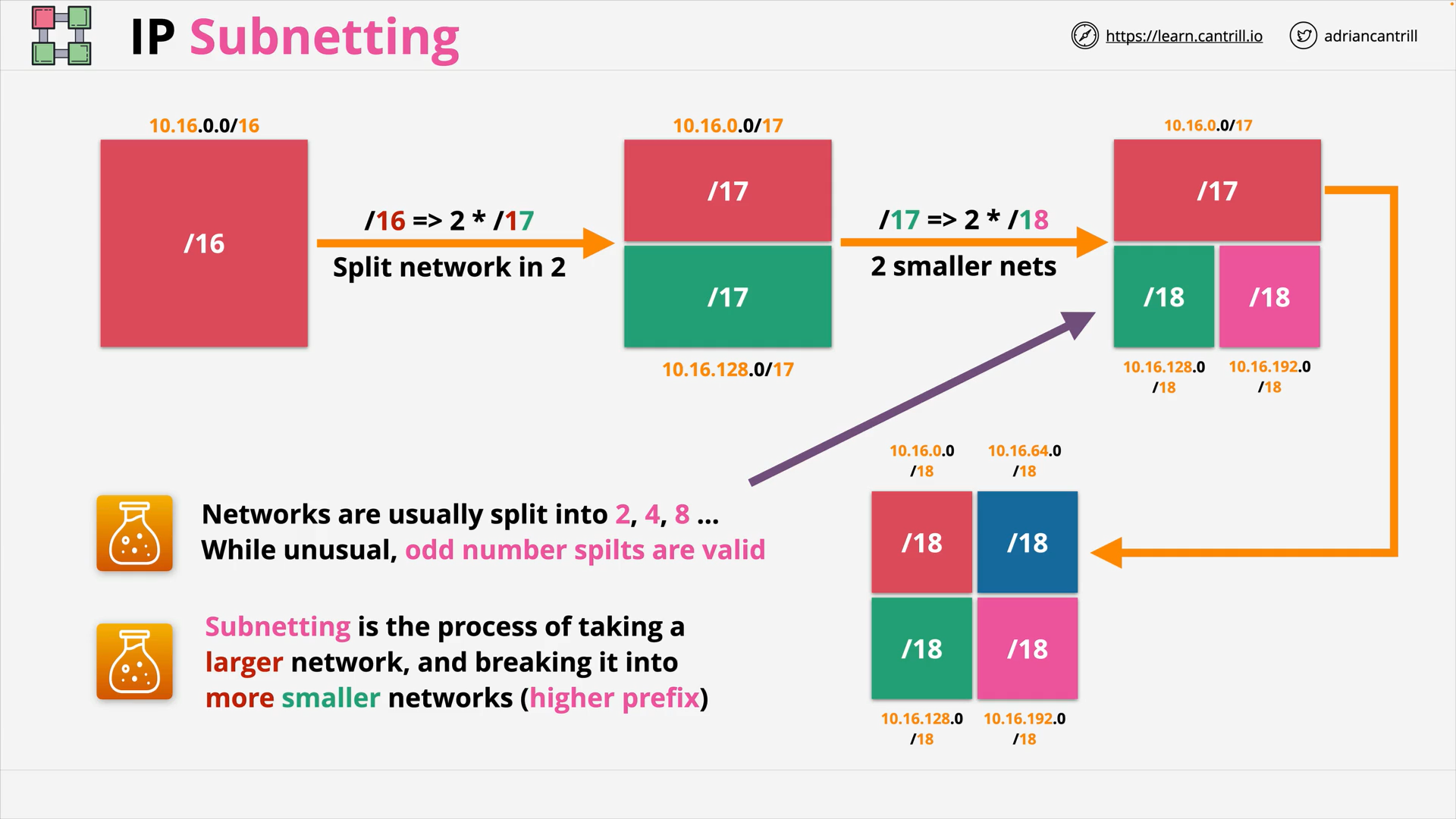 Subnetting and CIDR
Subnetting and CIDR
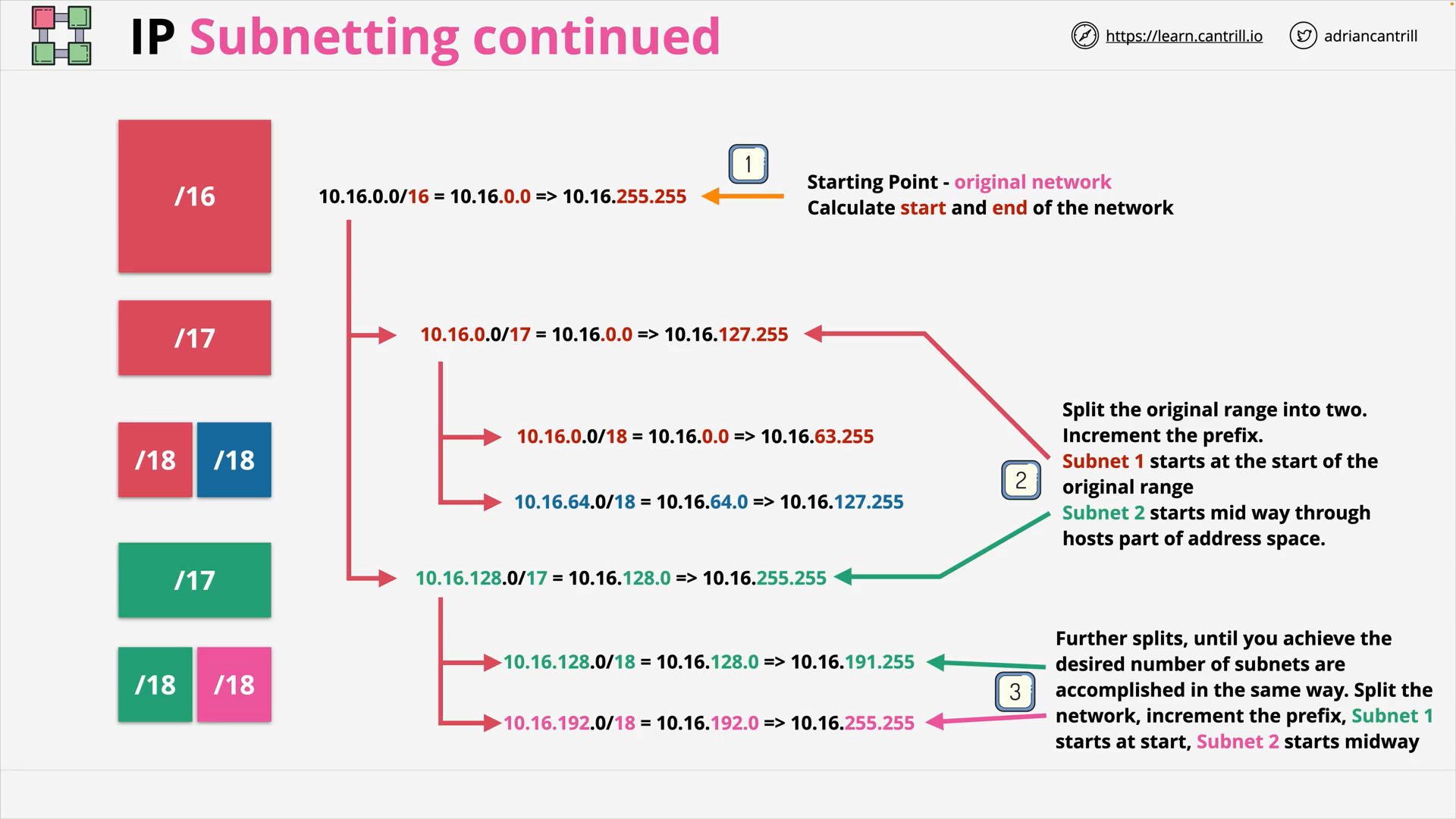 Subnetting - Start and end calculation
Subnetting - Start and end calculation
Distributed Denial of Service (DDOS) Attacks (14:35)
_Attacks__lear.png) DDOS - Overview
DDOS - Overview
ddos types:
- Layer 7:
- HTTP Flood
- DNS Fllod
- Layer 4:
- (TCP) SYN Flood
_Attacks__lear.png) Without DDOS - Normal App
Without DDOS - Normal App
_Attacks__lear.png) DDOS - Application Layer Attack (HTTP Flood)
DDOS - Application Layer Attack (HTTP Flood)
_Attacks__lear.png) DDOS - Protocol Attack (SYN Flood)
DDOS - Protocol Attack (SYN Flood)
_Attacks__lear.png) DDOS - Volumetric / Amplification Attack
DDOS - Volumetric / Amplification Attack
what is a ddos attack?
https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
VLANs, TRUNKS & QinQ (16:14)
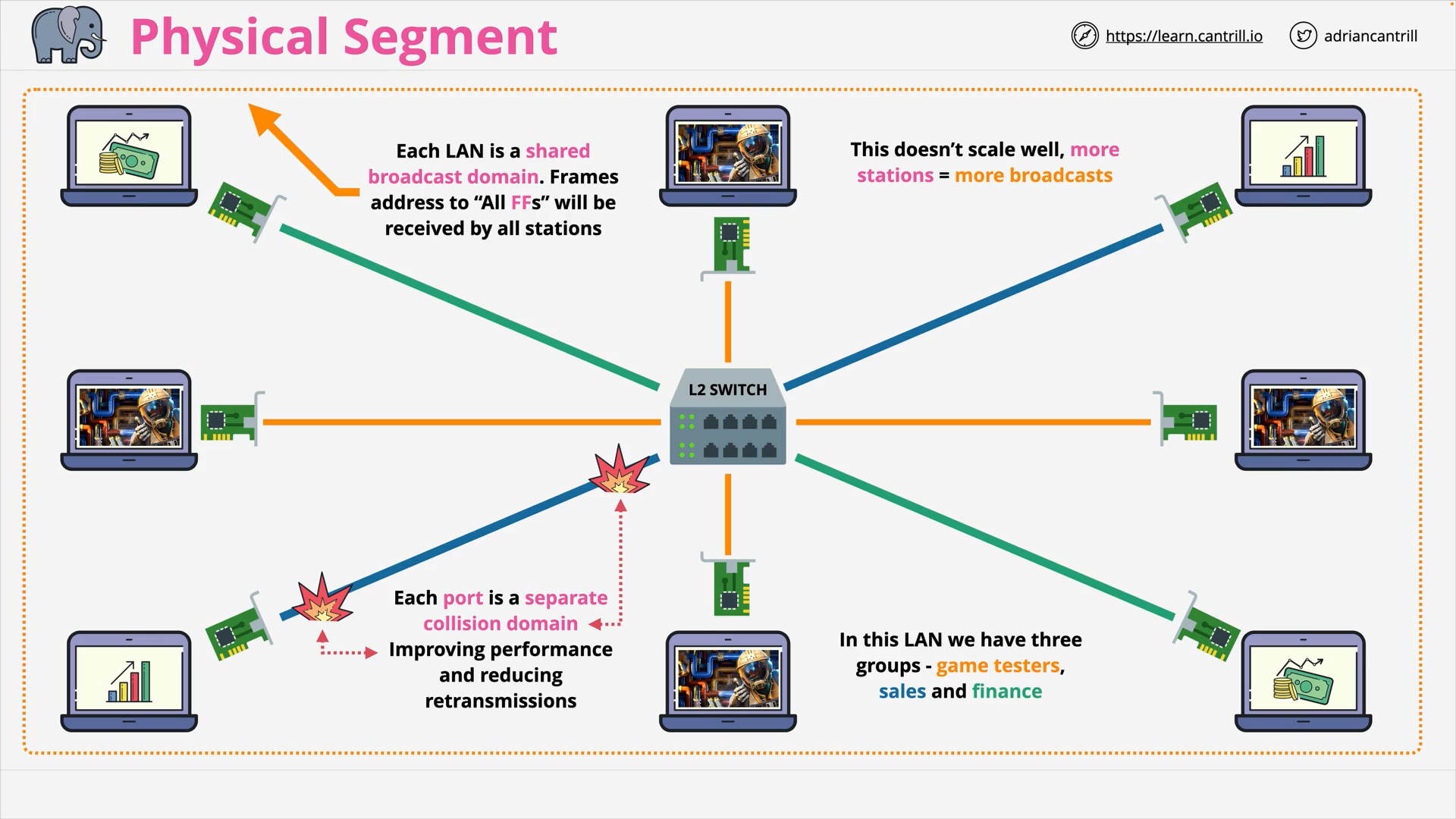 Physical Segment - 1 Switch
Physical Segment - 1 Switch
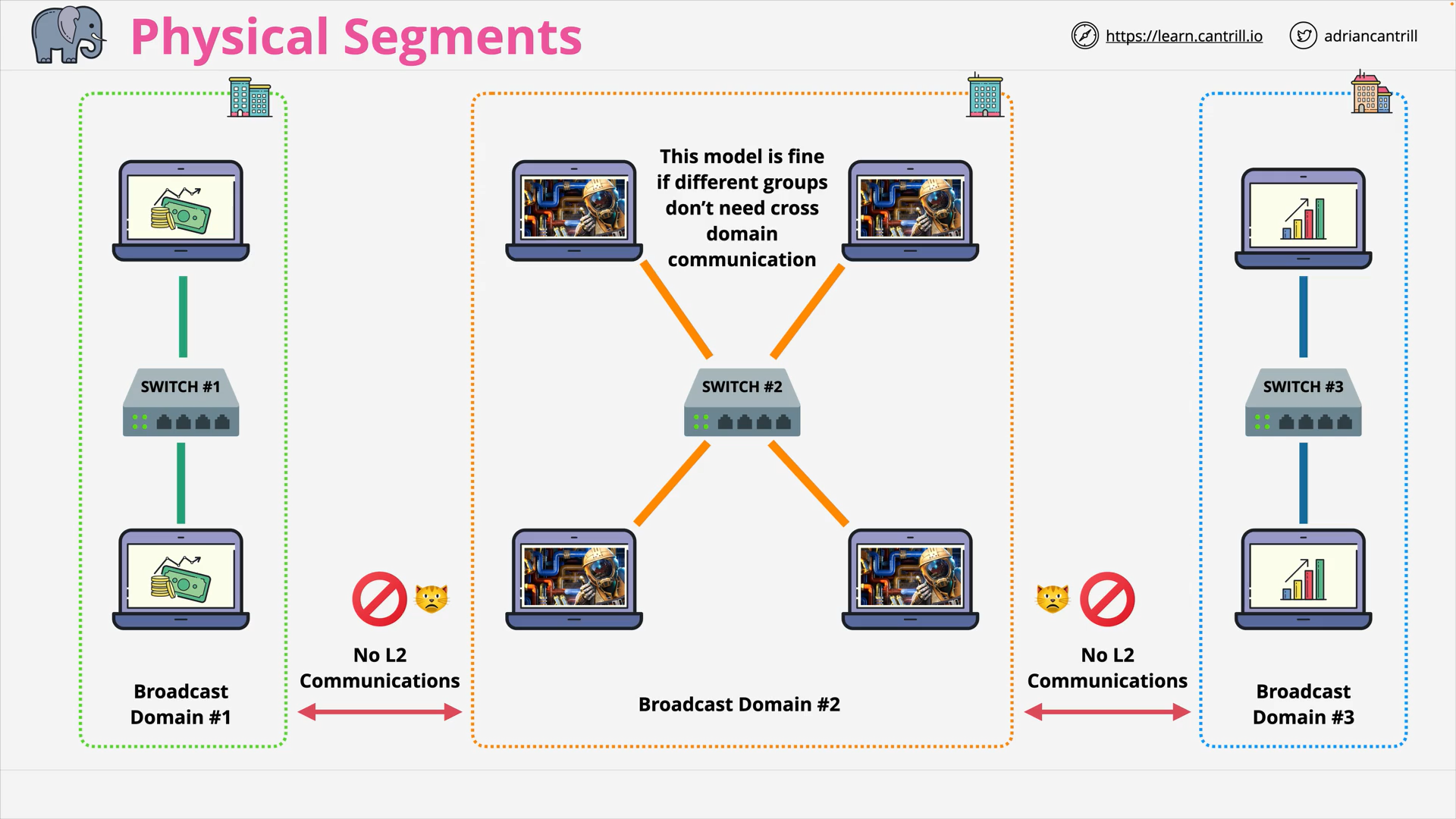 Physical Segment - Multi Switches
Physical Segment - Multi Switches
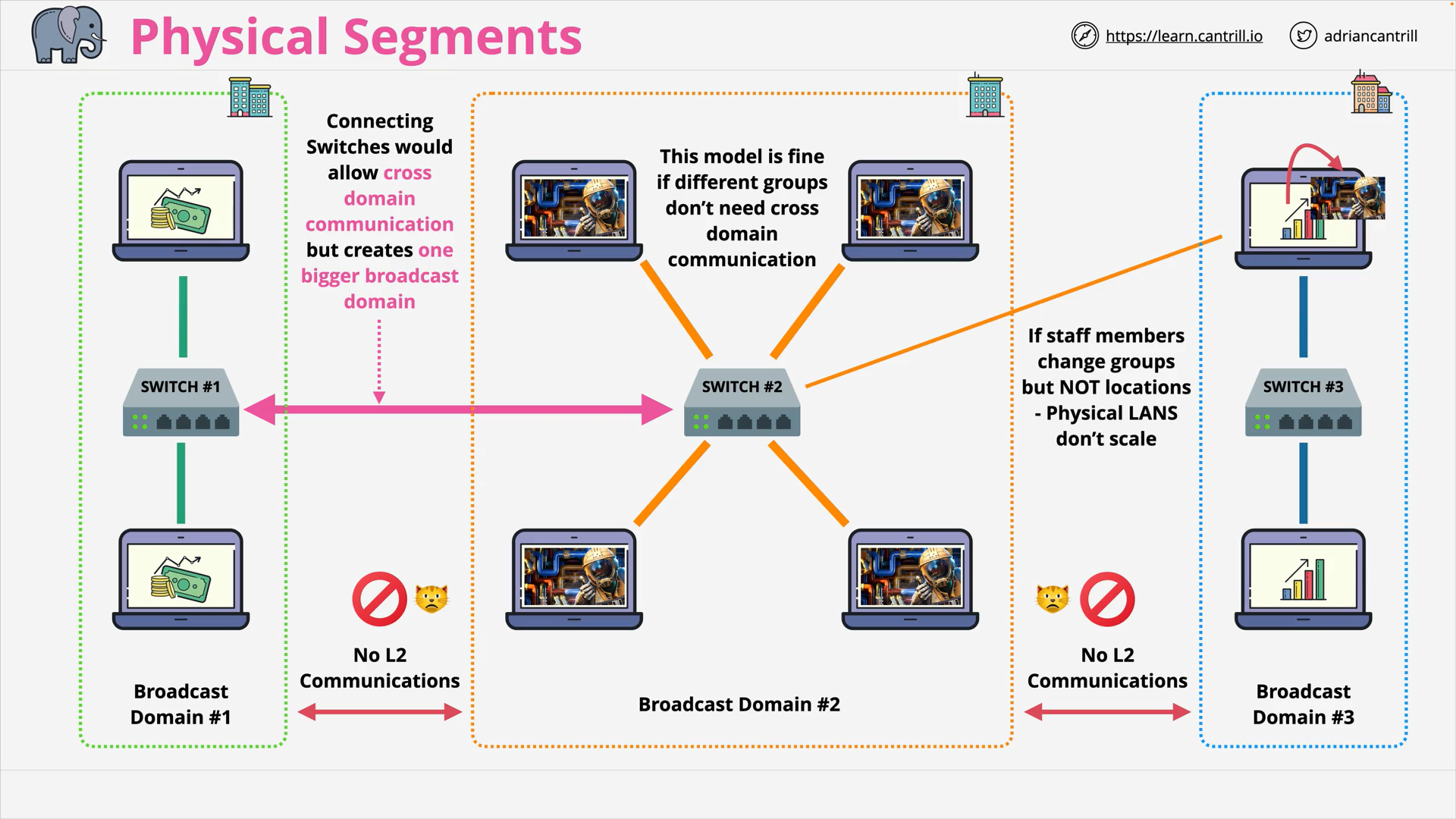 Physical Segment - Connecting Switches
Physical Segment - Connecting Switches
what is vlan?
A way to divide a single physical network into multiple logical networks.
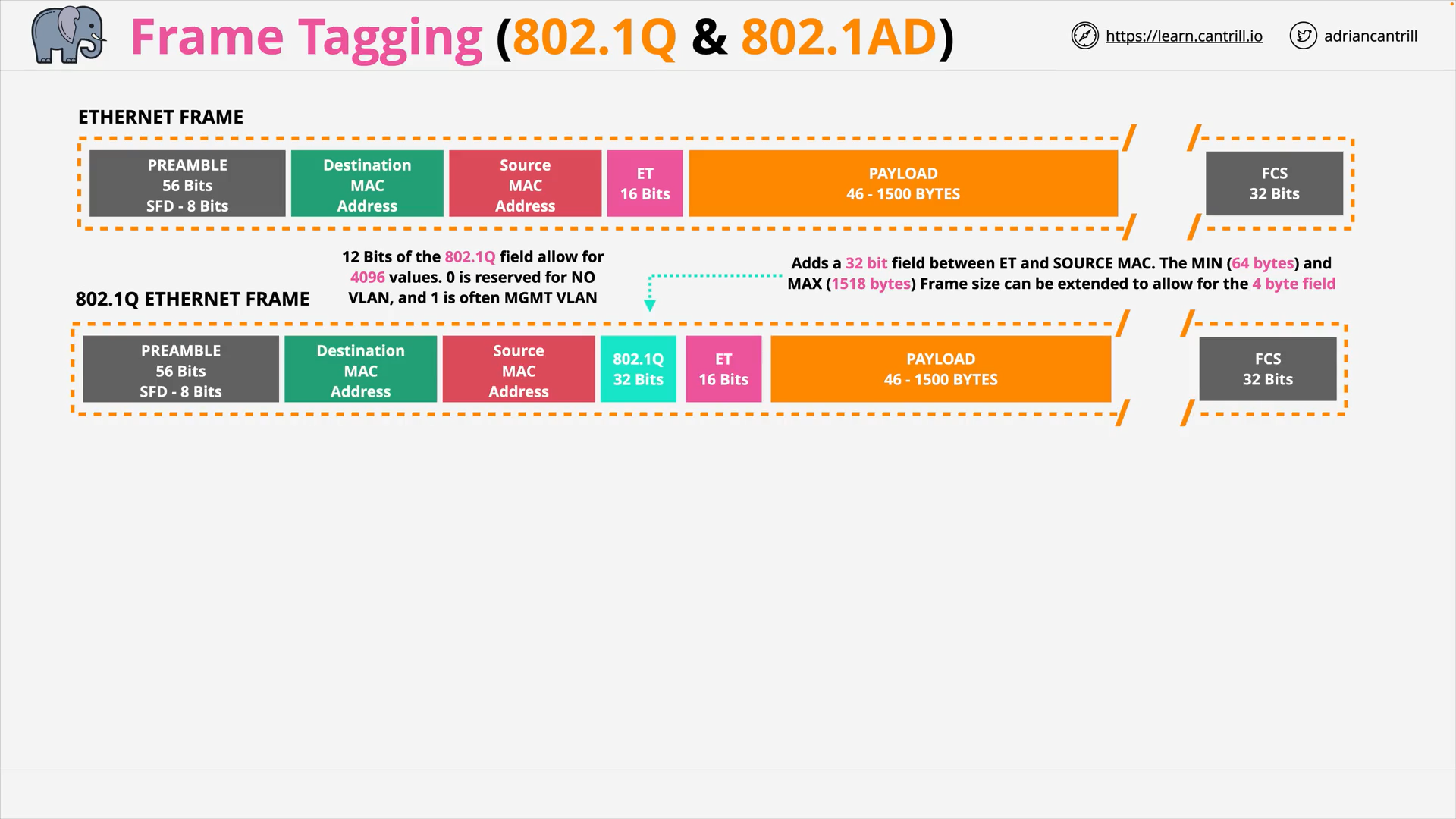 Frame Tagging - 802.1Q
Frame Tagging - 802.1Q
what does 802.1q do?
802.1Q allows multiple “VIRTUAL LANS (VLANS)” to operate over the same L2 physical network.
Each has a separate broadcast domain and is isolated from all others
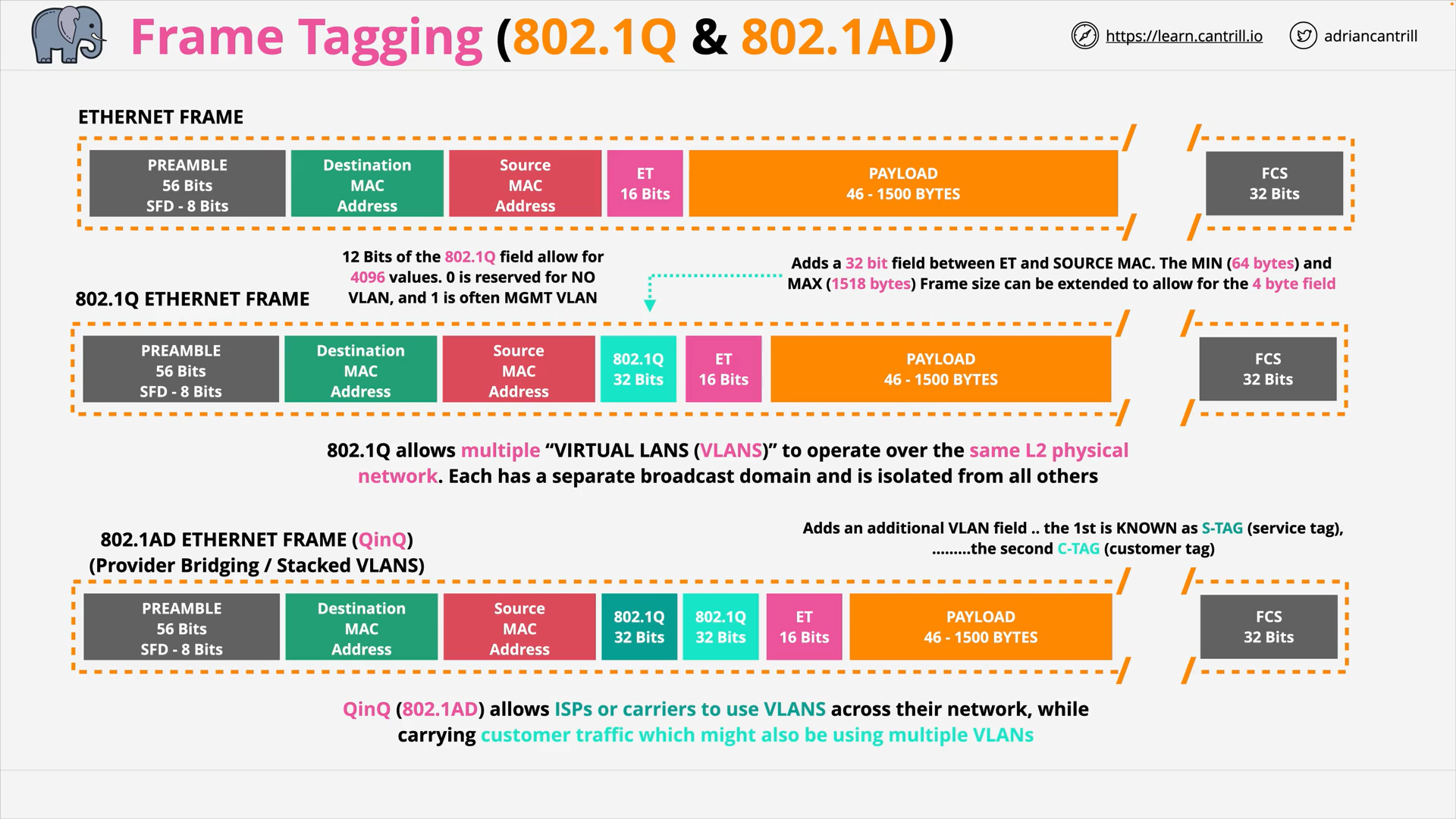 OSI Layer 2 - Frame Tagging - 802.1AD - QinQ
OSI Layer 2 - Frame Tagging - 802.1AD - QinQ
what does 802.1ad do?
802.1AD (QinQ) allows ISPs or carriers to use VLANS across their network, while carrying customer traffic which might also be using multiple VLANs
how does 802.1ad (qinq) work?
It allows multiple VLAN tags to be added to a single Ethernet frame.
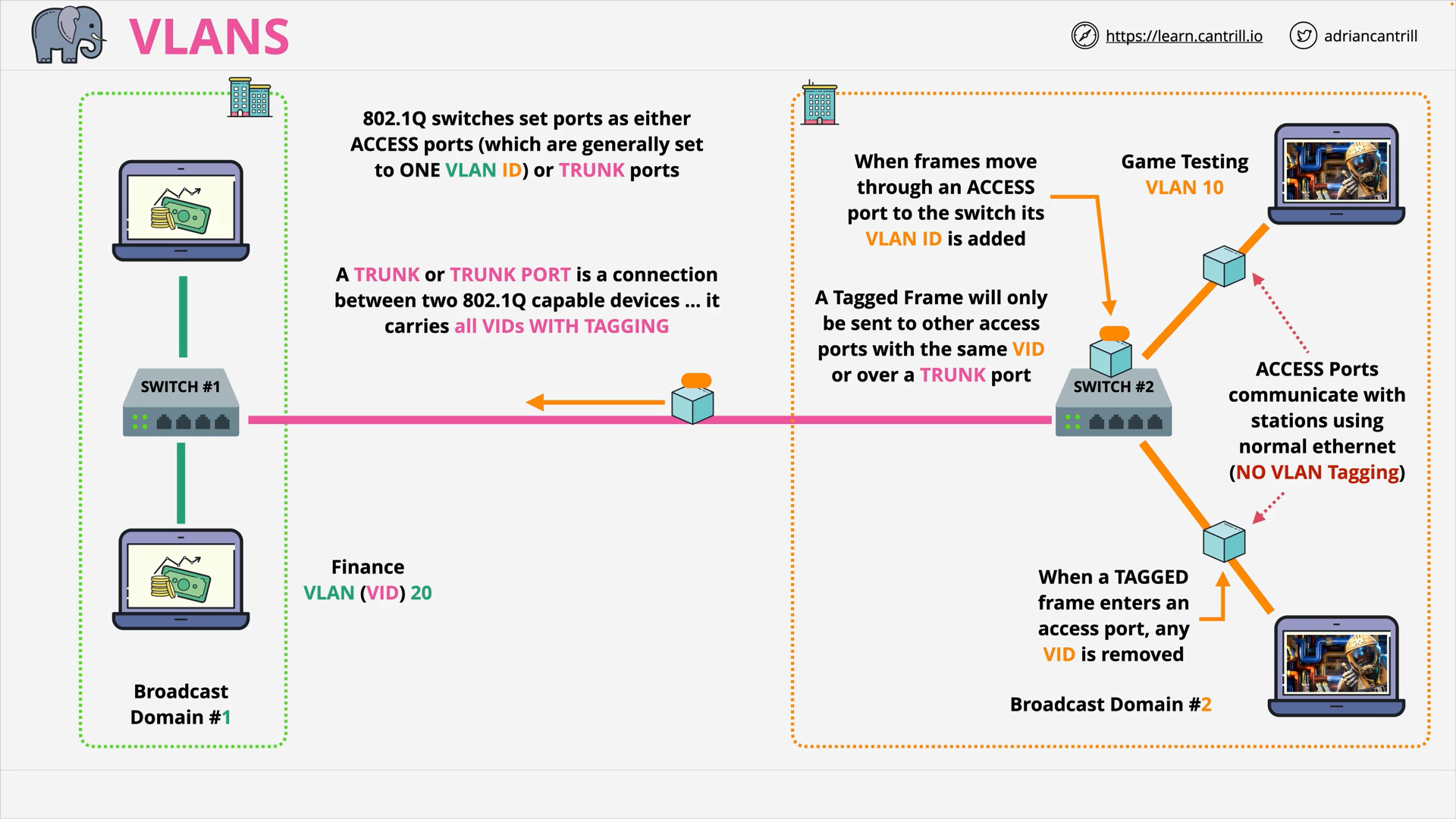 VLAN - Trunk Port vs Access Port
VLAN - Trunk Port vs Access Port
what are trunk port?
Trunk ports are a way to carry VLAN traffic between network switches
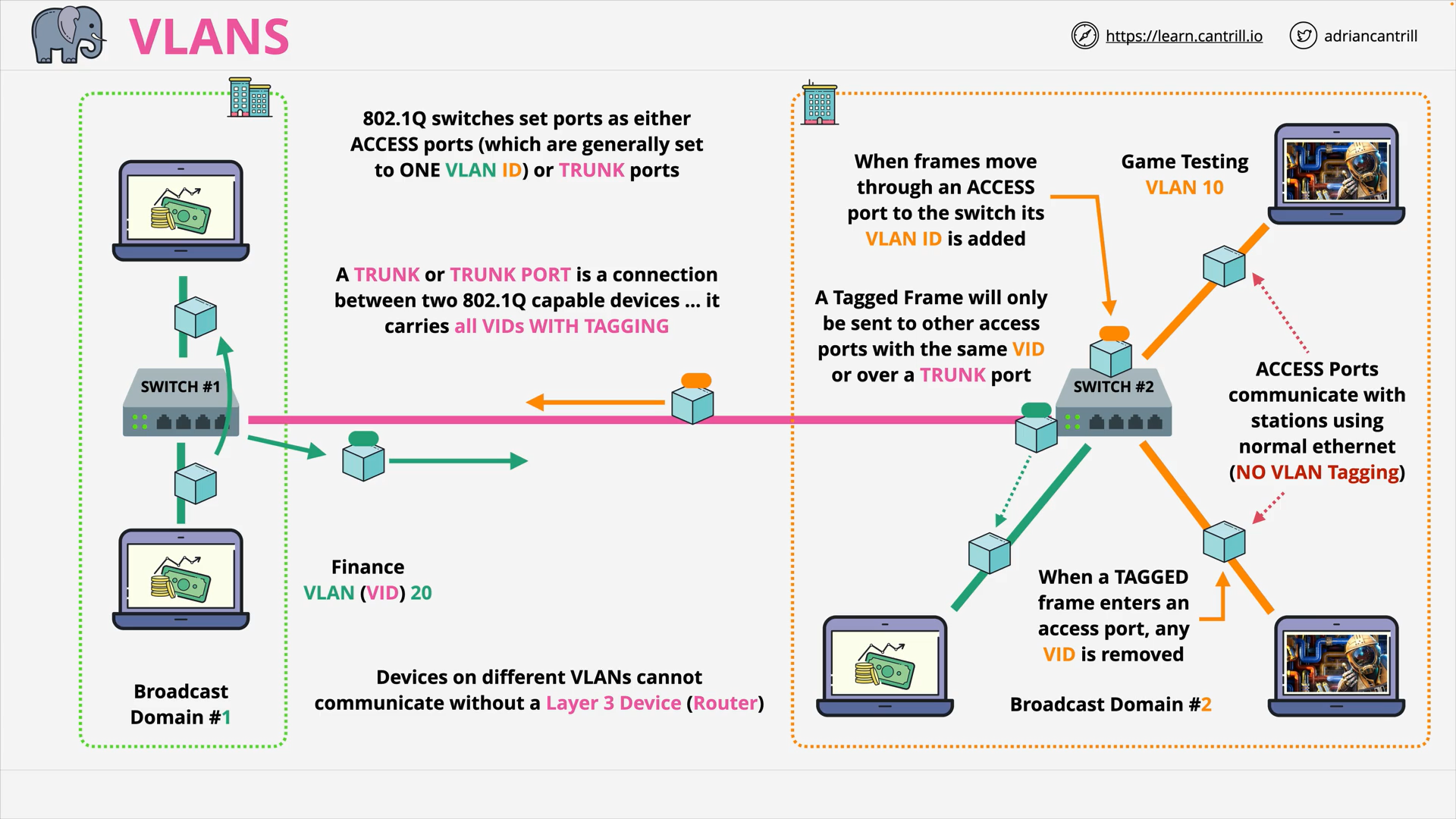 Devices on different VLANs cannot communicate without a Layer 3 Device (Router)
Devices on different VLANs cannot communicate without a Layer 3 Device (Router)
 VLAN - Summary
VLAN - Summary
Decimal to Binary Conversion (IP Addressing) (17:12)
__lear.png)
__lear.png)
__lear.png)
SSL & TLS (11:19)
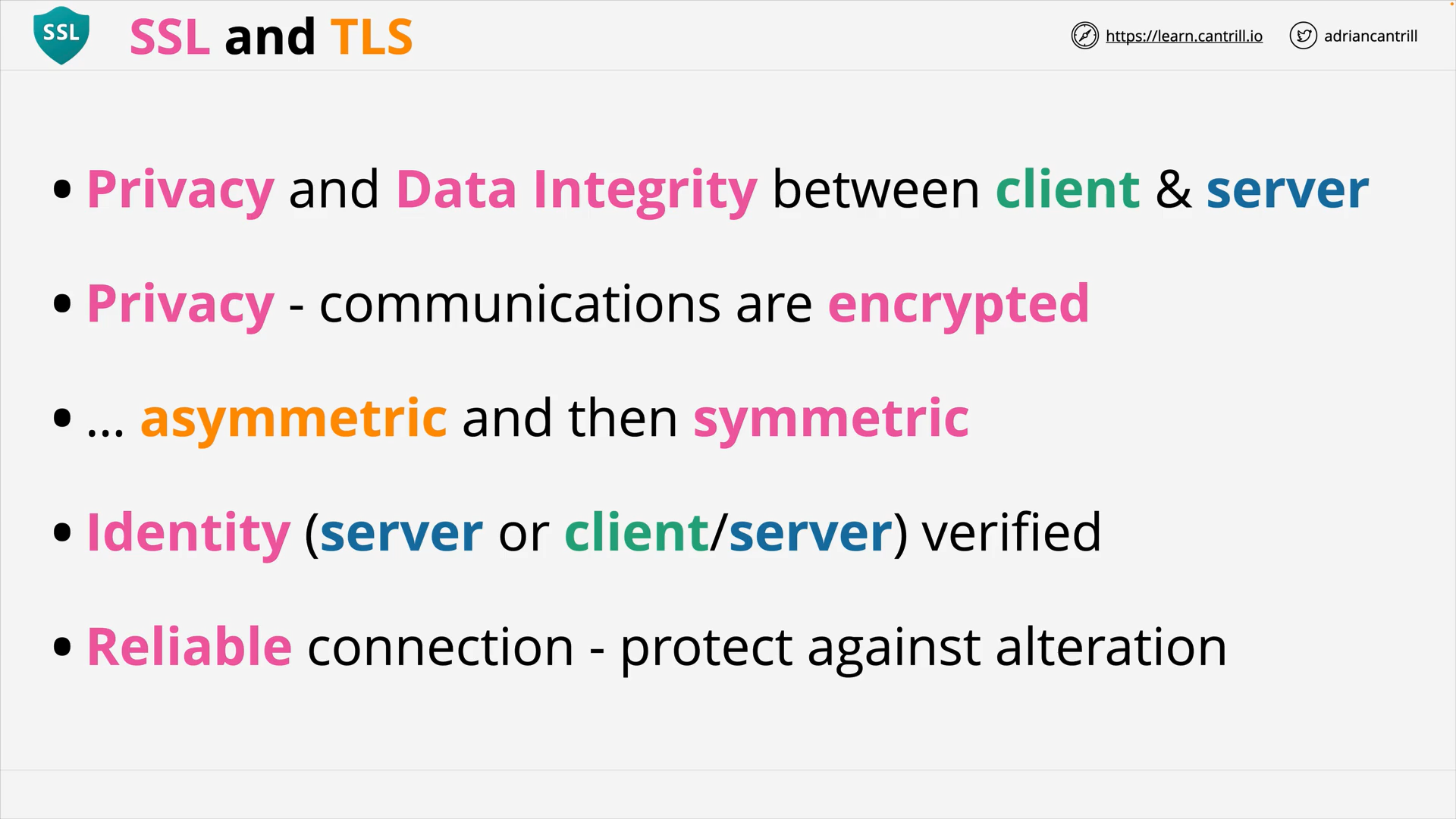
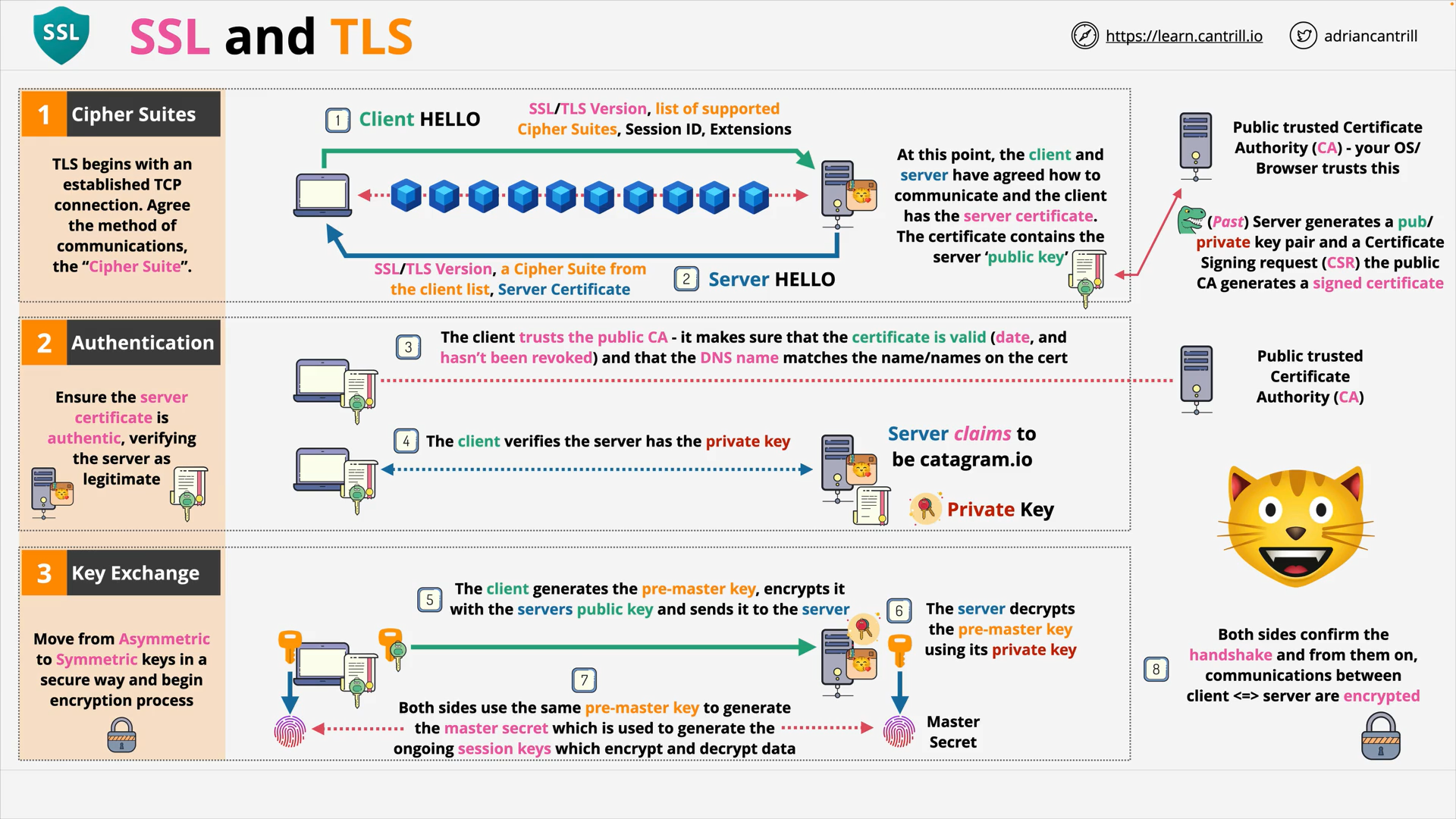
See The First Few Milliseconds of an HTTPS Connection
Border Gateway Protocol (BGP) 101 (17:03)
_101__learn.cantrill..png) BGP: Exchange the best path (ASPATH) to a destination
BGP: Exchange the best path (ASPATH) to a destination
_101__learn.cantrill..png) BGP: AS will advertise all the shortest paths its known to all its peers (and prepends its own ASN onto the path)
BGP: AS will advertise all the shortest paths its known to all its peers (and prepends its own ASN onto the path)
aspath prepending: make a path longer
Stateful vs Stateless Firewalls (14:04)
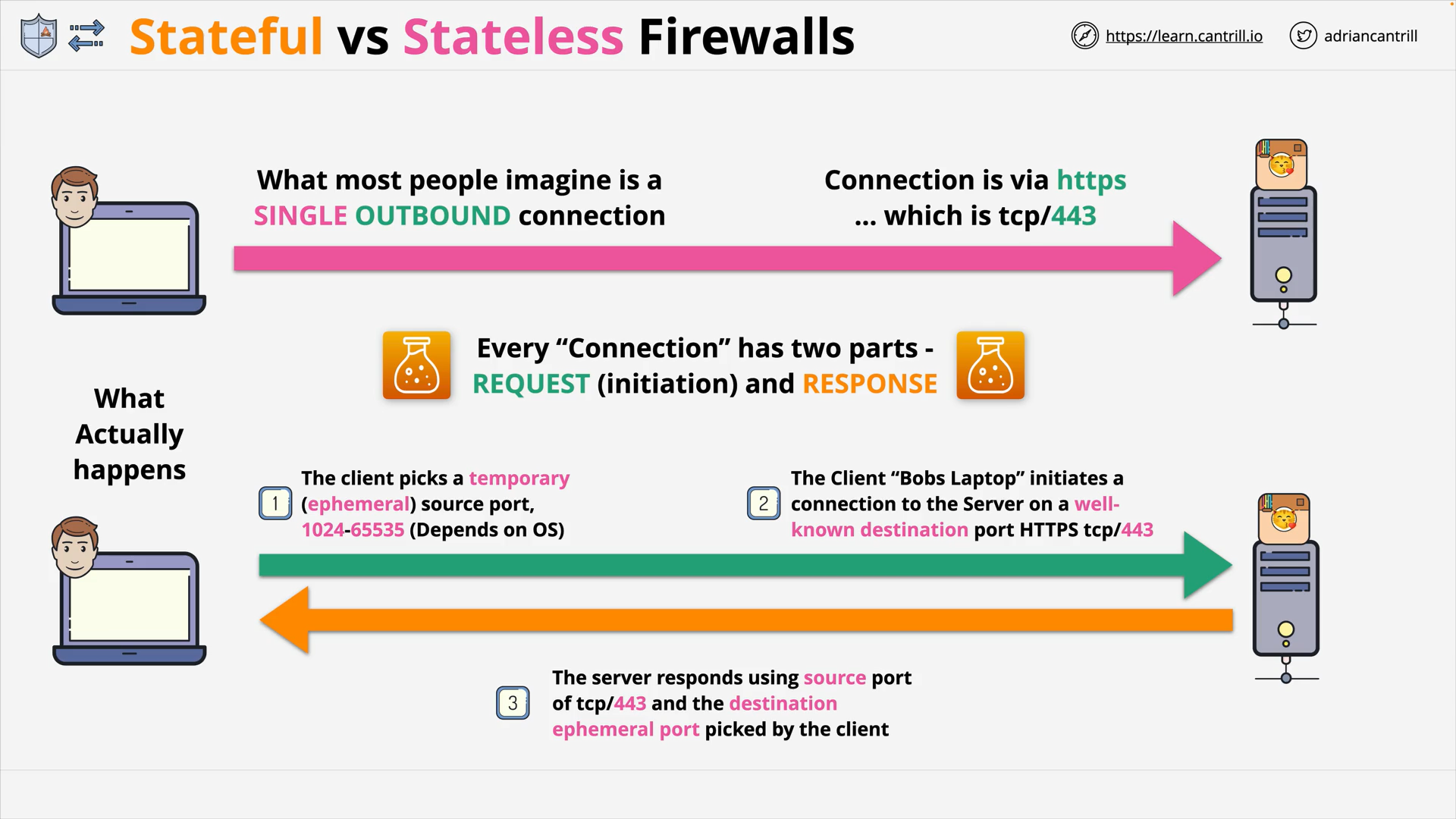 Connection’s Inbound and Outbound
Connection’s Inbound and Outbound
connection and port
A connection has 2 parts:
- Request: From an ephemeral port - chosen by the client - (to a well-known port)
- Response: From the well-known port (to that ephemeral port)
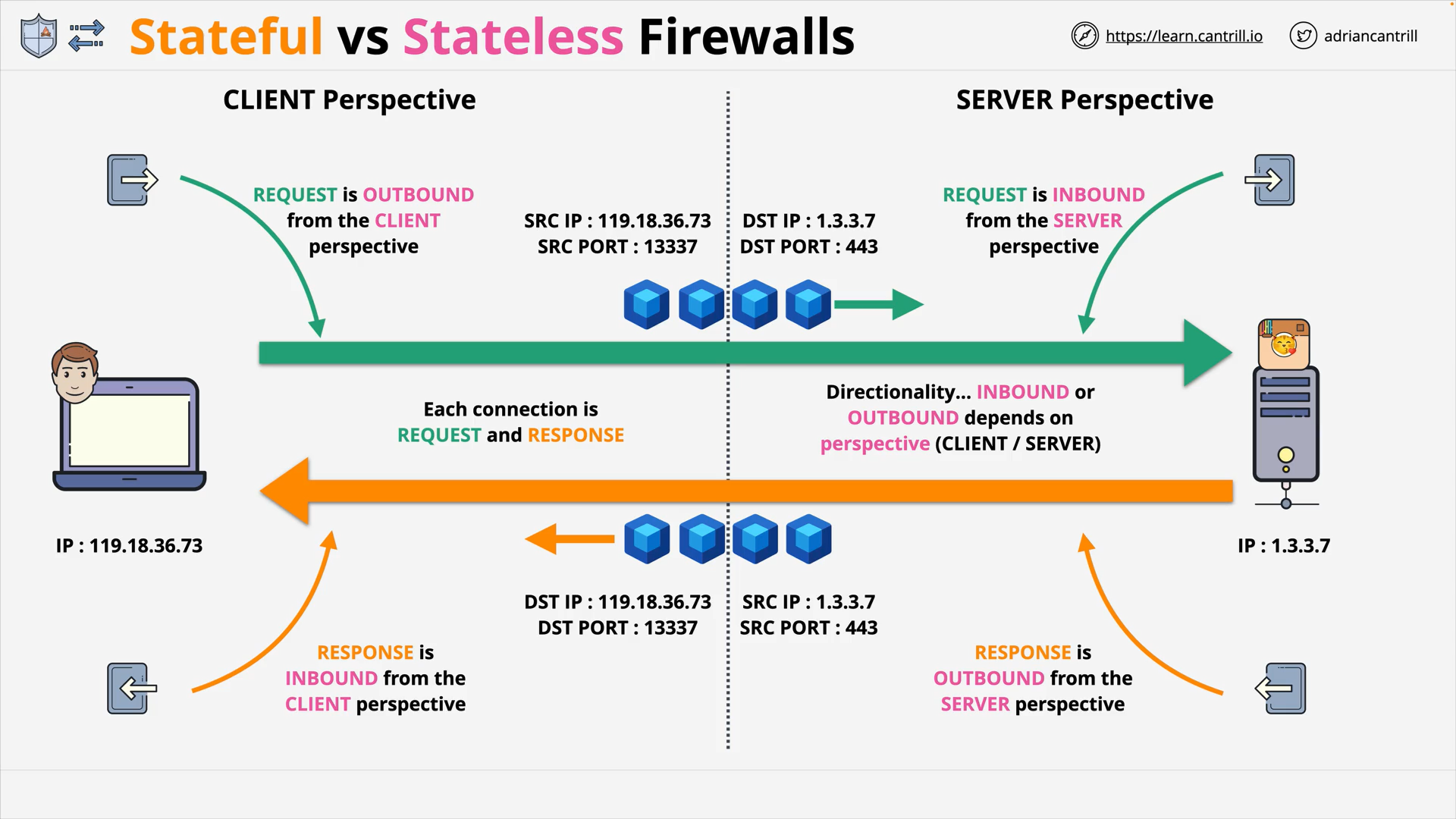 Inbound and Outbound are depend on perspective
Inbound and Outbound are depend on perspective
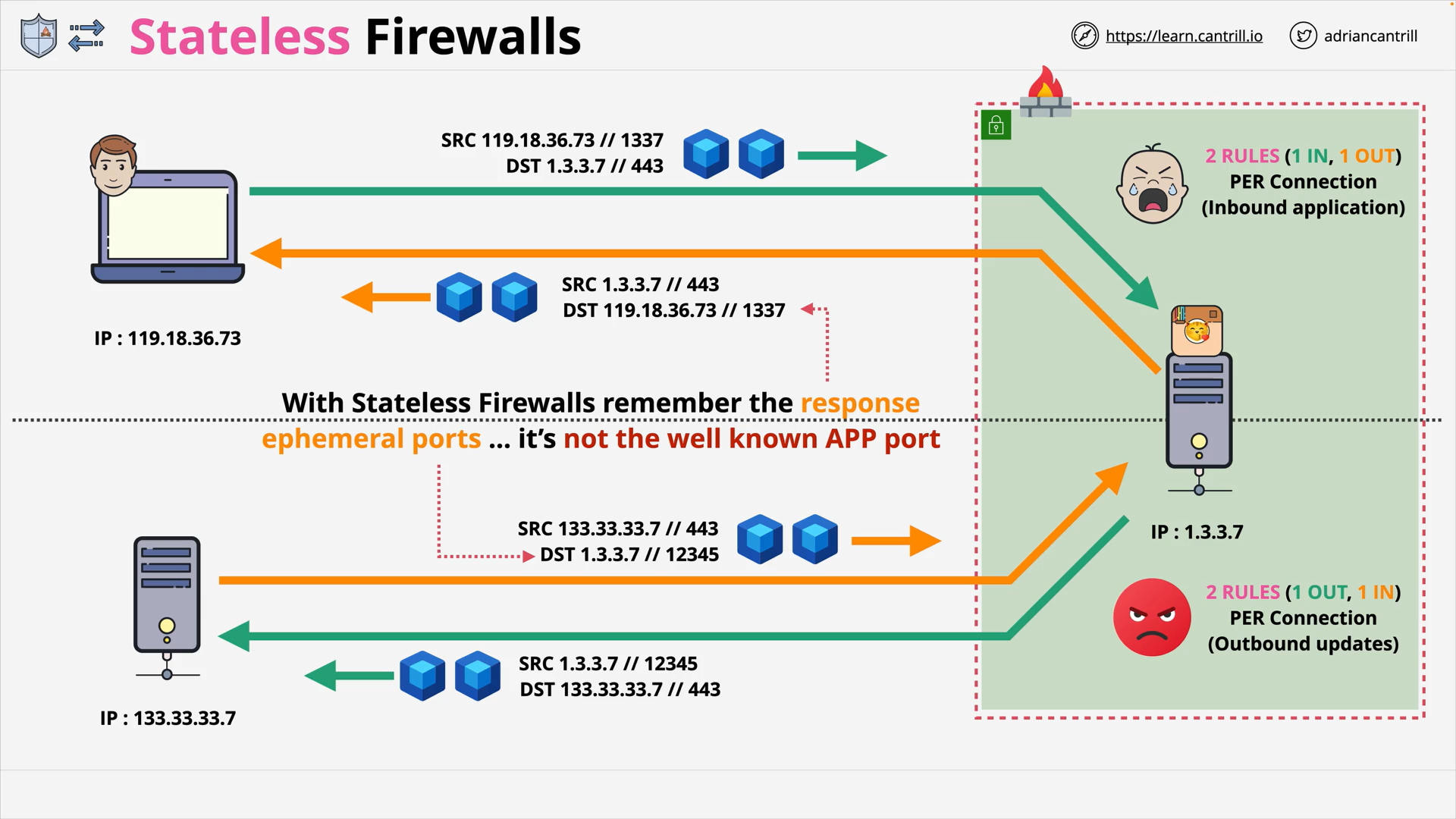 Stateless Firewall
Stateless Firewall
stateless firewall
A Stateless Firewall
- examines each individual network packet in isolation
- makes decisions
- based on predetermined rules
- without any awareness of the state of the network connection
stateless firewall and server
When using stateless firewall with a server, you need to:
- Allow inbound traffic to well-known port, e.g.
443 - Allow outbound traffic to all ephemeral ports, e.g.
1024,65535(randomly chosen by the client)
e.g. AWS Network ACL
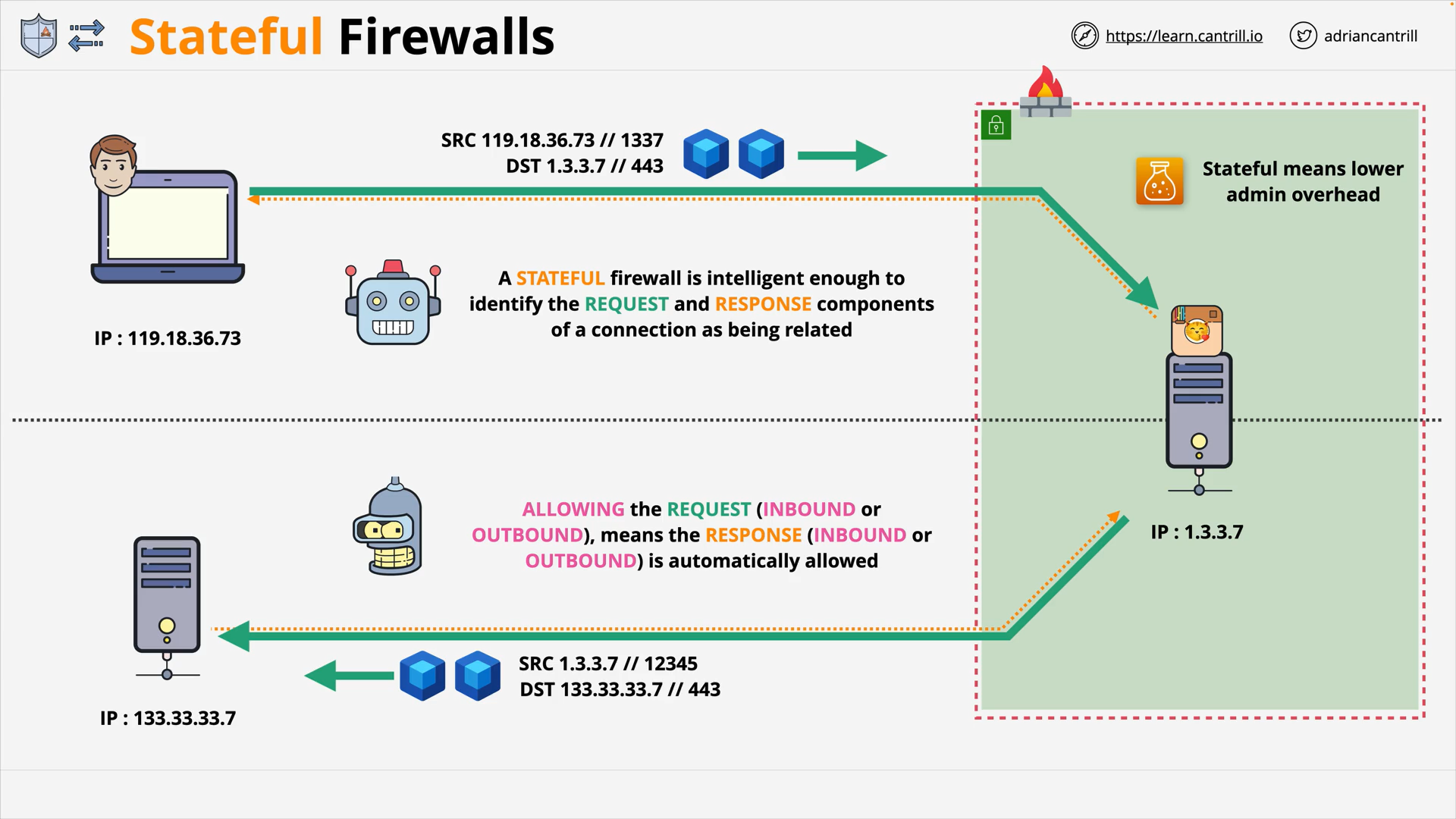 Stateful Firewall
Stateful Firewall
stateful firewall
A stateful firewall
- tracks the state of the network connections:
- knows a response corresponding to which request
- make decisions based on these knowledge:
- do some of the works for you
👉 If
- the request (no matter whether it’s inbound or outbound traffic) is allowed
- the response will be automatically allowed too
e.g. AWS security group
tip
Usually:
- A stateful firewall is called “firewall”.
- A stateless firewall is called ACL.
When something is called firewall, it usually means it’s a stateful firewall.
JumboFrames (4:35)
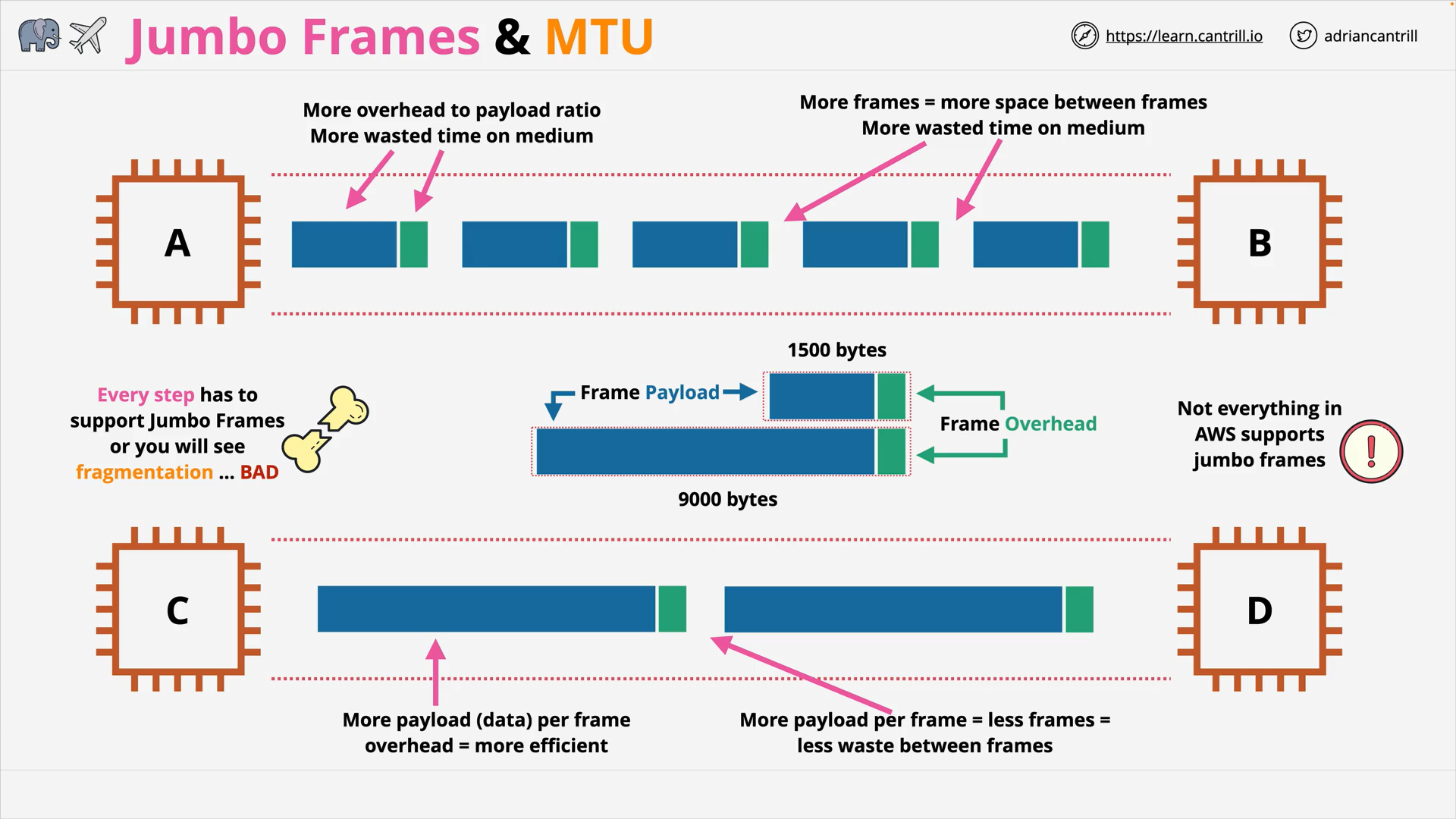 JumboFrame vs normal frame (OSI Layer 2)
JumboFrame vs normal frame (OSI Layer 2)
maximum transmission unit (mtu)
- Traditional Ethernet frames have a MTU of 1500 bytes.
- Jumbo Frames can allow for frames up to 9000 bytes.
why use jumbo frames
- Reduce frame overhead
- Reduce wasted time on medium (between frames)
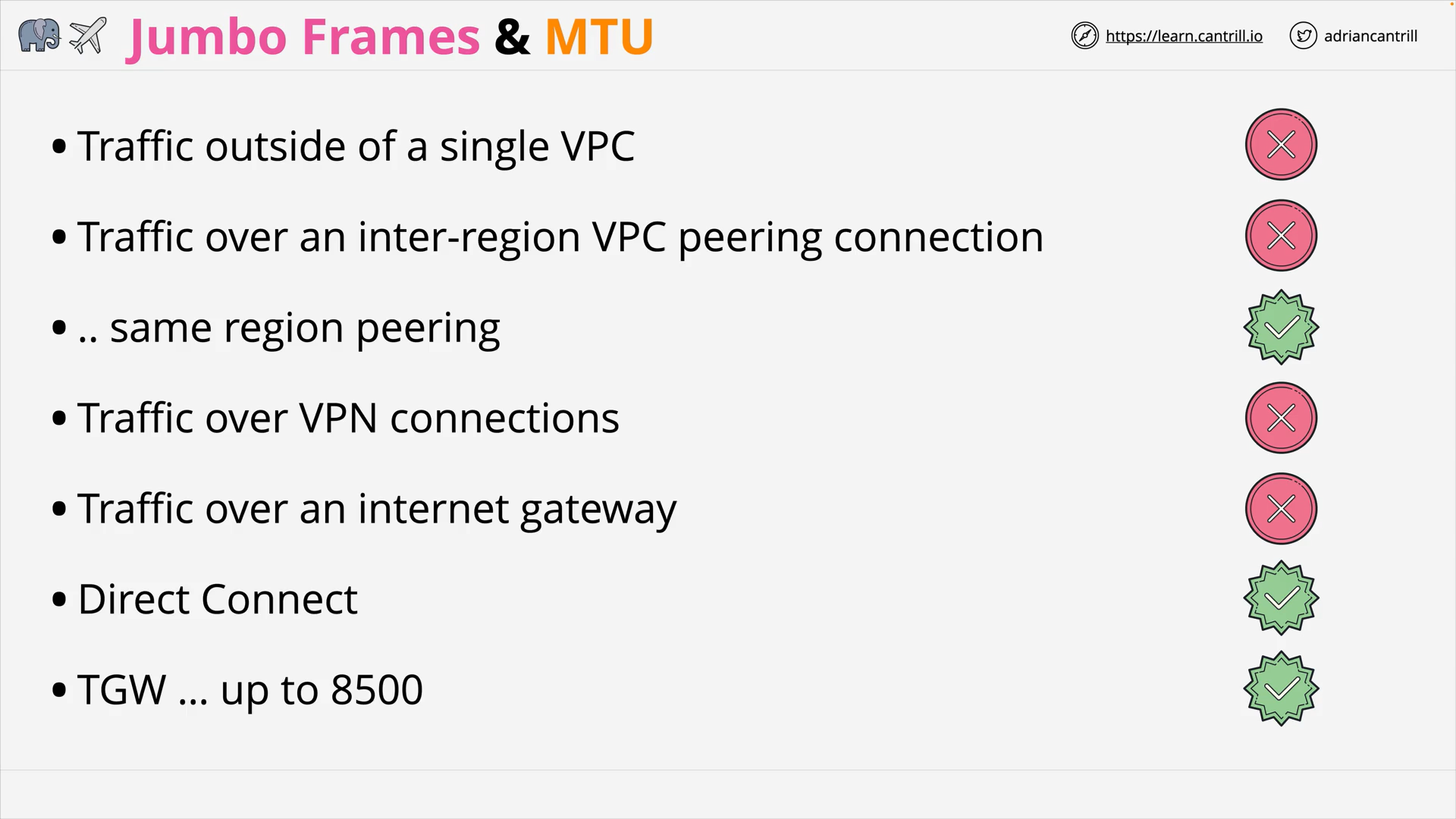 Not everything in AWS supports JumboFrames
Not everything in AWS supports JumboFrames
in aws, which traffic supports jumbo frames?
- VPC Peering in same region
- Direct Connect
- TGW (up to 8500 bytes)
Layer 7 Firewalls (7:44)
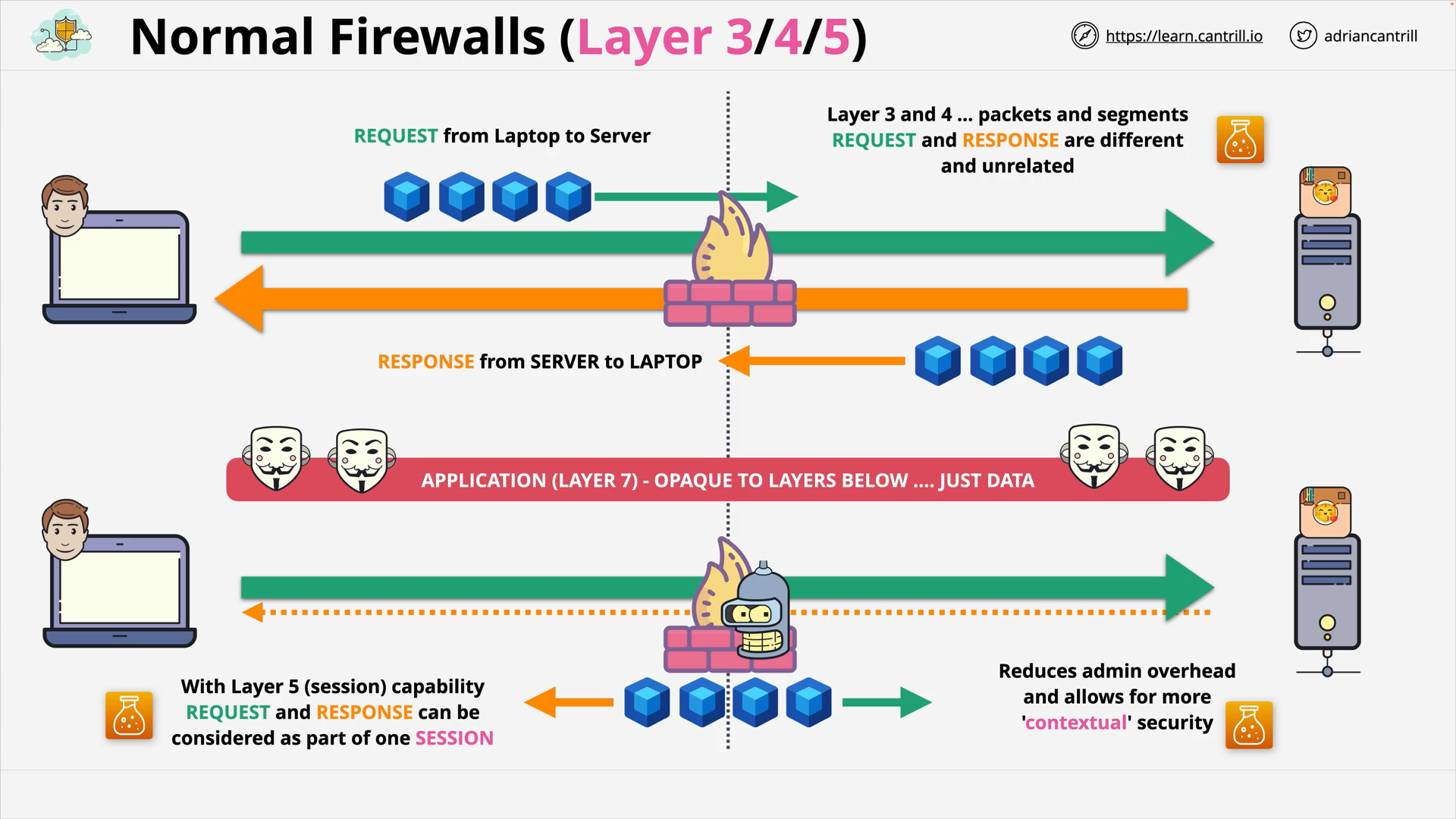 Traditional firewalls, such as packet filtering or stateful inspection firewalls, operate at the network and transport layers and are only capable of filtering traffic based on IP addresses, port numbers, and protocol types.
Traditional firewalls, such as packet filtering or stateful inspection firewalls, operate at the network and transport layers and are only capable of filtering traffic based on IP addresses, port numbers, and protocol types.
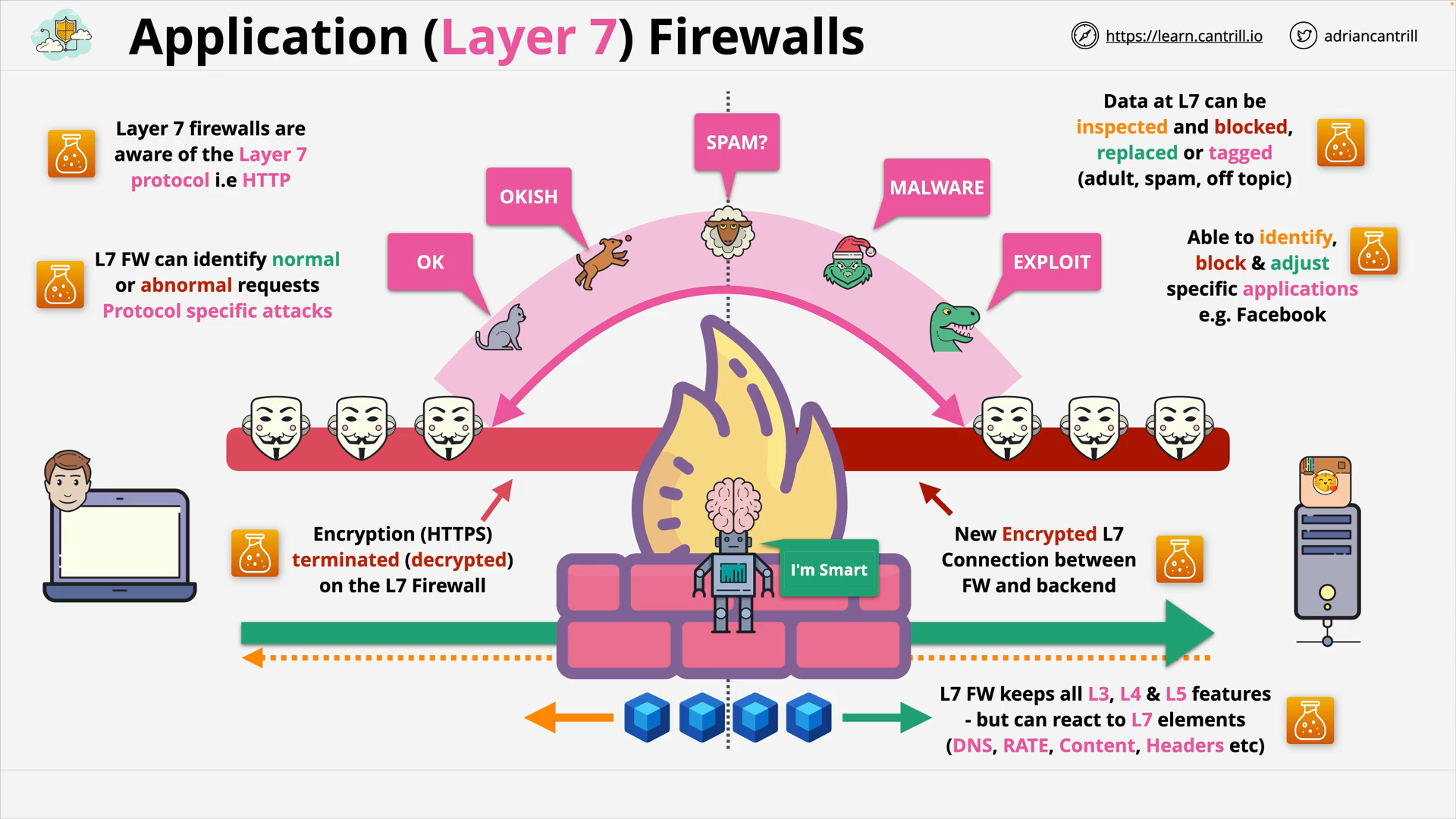 In contrast, layer 7 firewalls have the ability to analyze the content of network traffic, including application protocols such as HTTP, FTP, and SMTP, and can make more granular decisions about which traffic should be allowed or blocked.
In contrast, layer 7 firewalls have the ability to analyze the content of network traffic, including application protocols such as HTTP, FTP, and SMTP, and can make more granular decisions about which traffic should be allowed or blocked.
layer 7 firewall
| Feature | Traditional Firewalls (Packet Filtering/Stateful Inspection) | Layer 7 Firewalls (Application Firewalls) |
|---|---|---|
| Layer of Operation | Network and Transport Layers (Layer 3 & 4) | Application Layer (Layer 7) |
| Filtering Criteria | IP addresses, Port numbers, Protocol types | Application data, HTTP/FTP/SMTP, user inputs |
| Traffic Inspection | Basic packet-level inspection | Deep packet inspection of application data |
| Granularity | Coarse-grained (limited to IP, port, protocol) | Fine-grained (based on application content) |
| Protection against | Basic network attacks (IP spoofing, SYN floods) | Advanced threats (SQL injection, XSS, malware) |
| Policy Control | Limited to low-level network policies | Application-specific policies (e.g., block specific URLs) |
| Performance | Higher throughput due to simpler inspection | Potentially slower due to deep inspection |
| Complexity | Simpler to configure and manage | More complex, requires detailed understanding of applications |
| Use Case | Basic security for network and transport layers | Protection of web and application services |
| Examples of Applications | Firewall rules based on IP, Port, and Protocol | Web Application Firewall (WAF), API Gateways |
See Nord Security - Learning Center
IP Sec VPN Fundamentals (14:48)
 IPSec
IPSec
what does ip sec do?
IP Sec sets up secure tunnel across insecure networks.
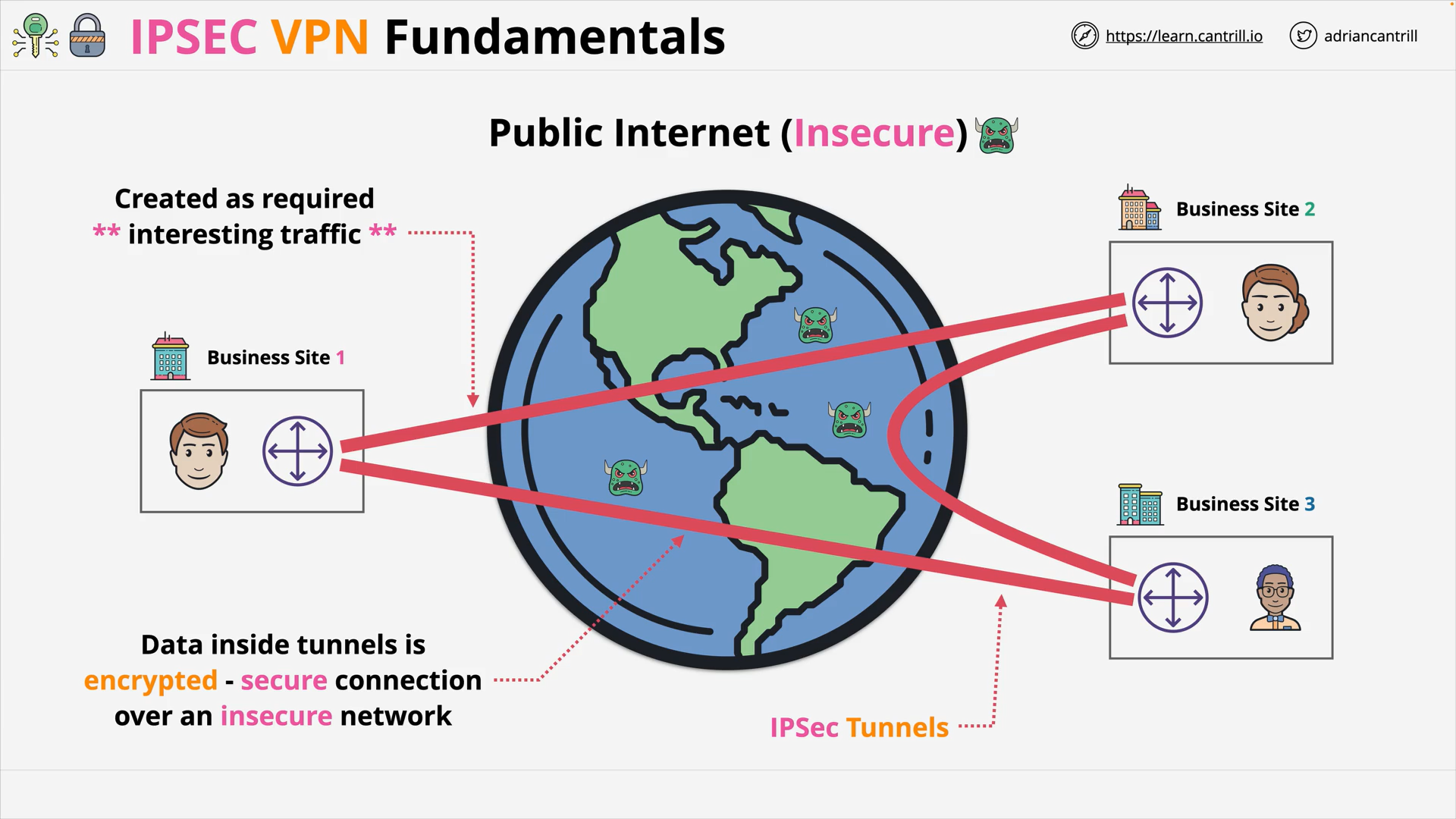 IP Sec Tunnel
IP Sec Tunnel
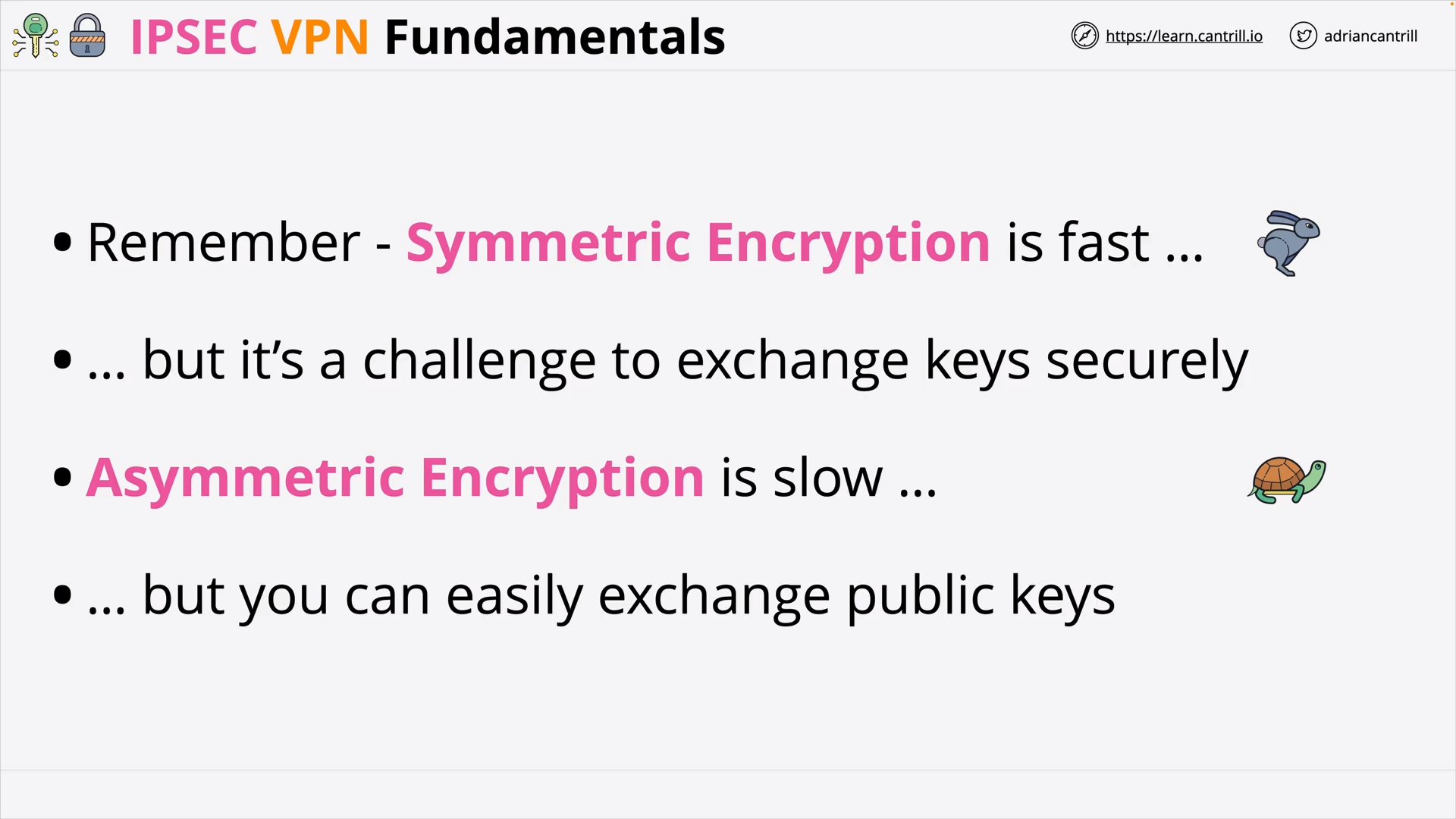 Asymmetric/Symmetric Encryption
Asymmetric/Symmetric Encryption
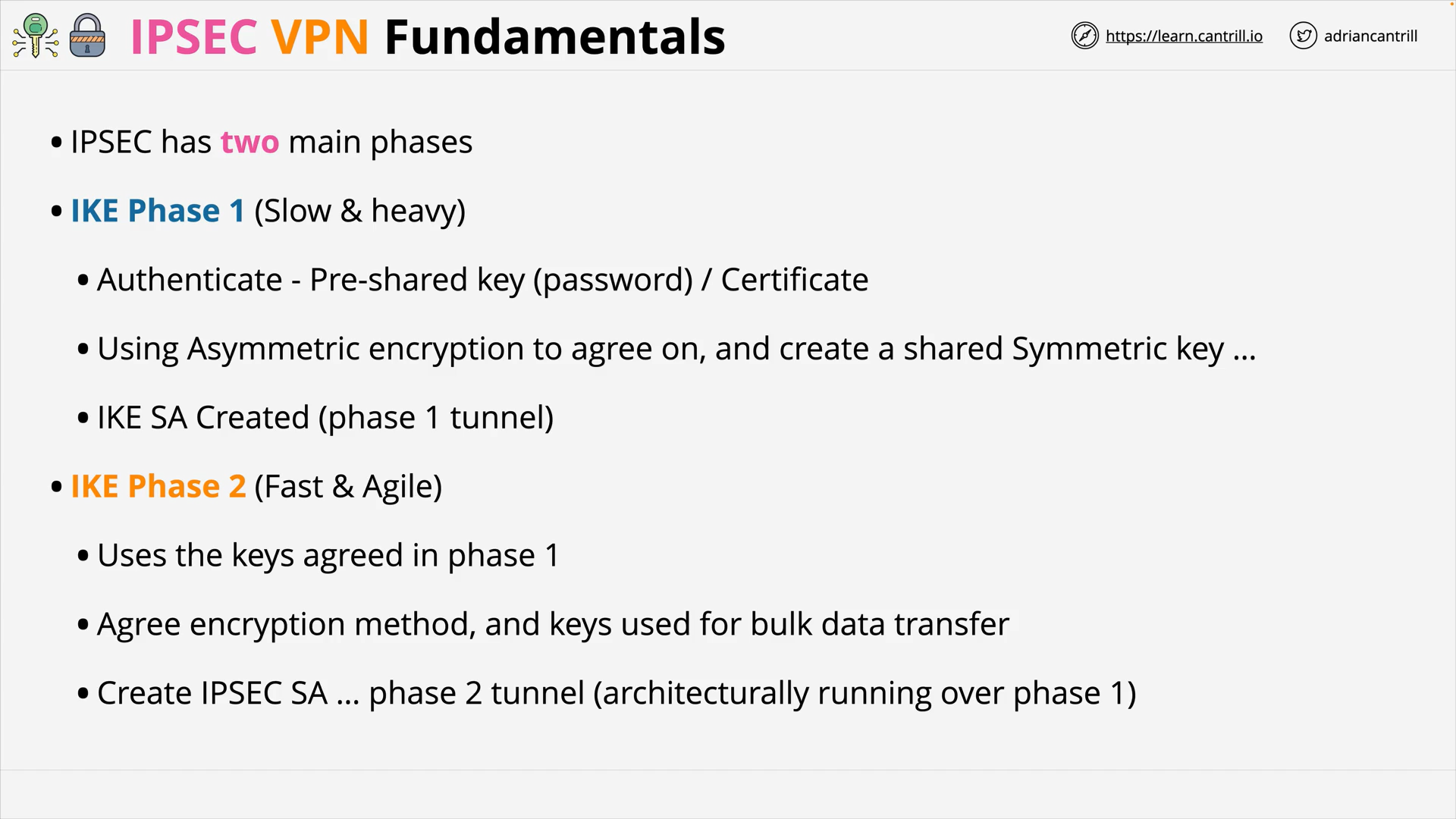 IP Sec’s 2 main phases
IP Sec’s 2 main phases
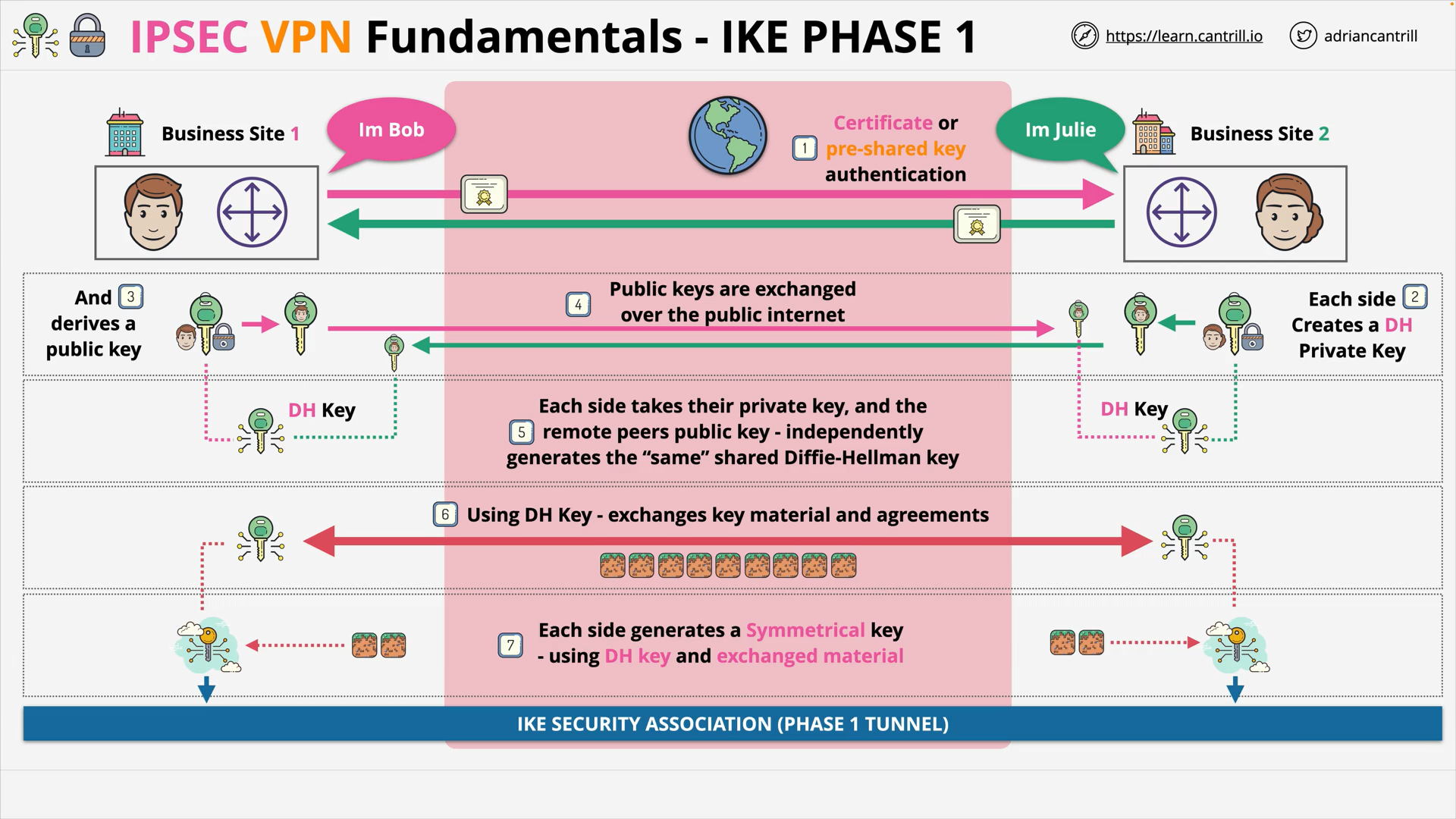 IP Sec - IKE Phase 1
IP Sec - IKE Phase 1
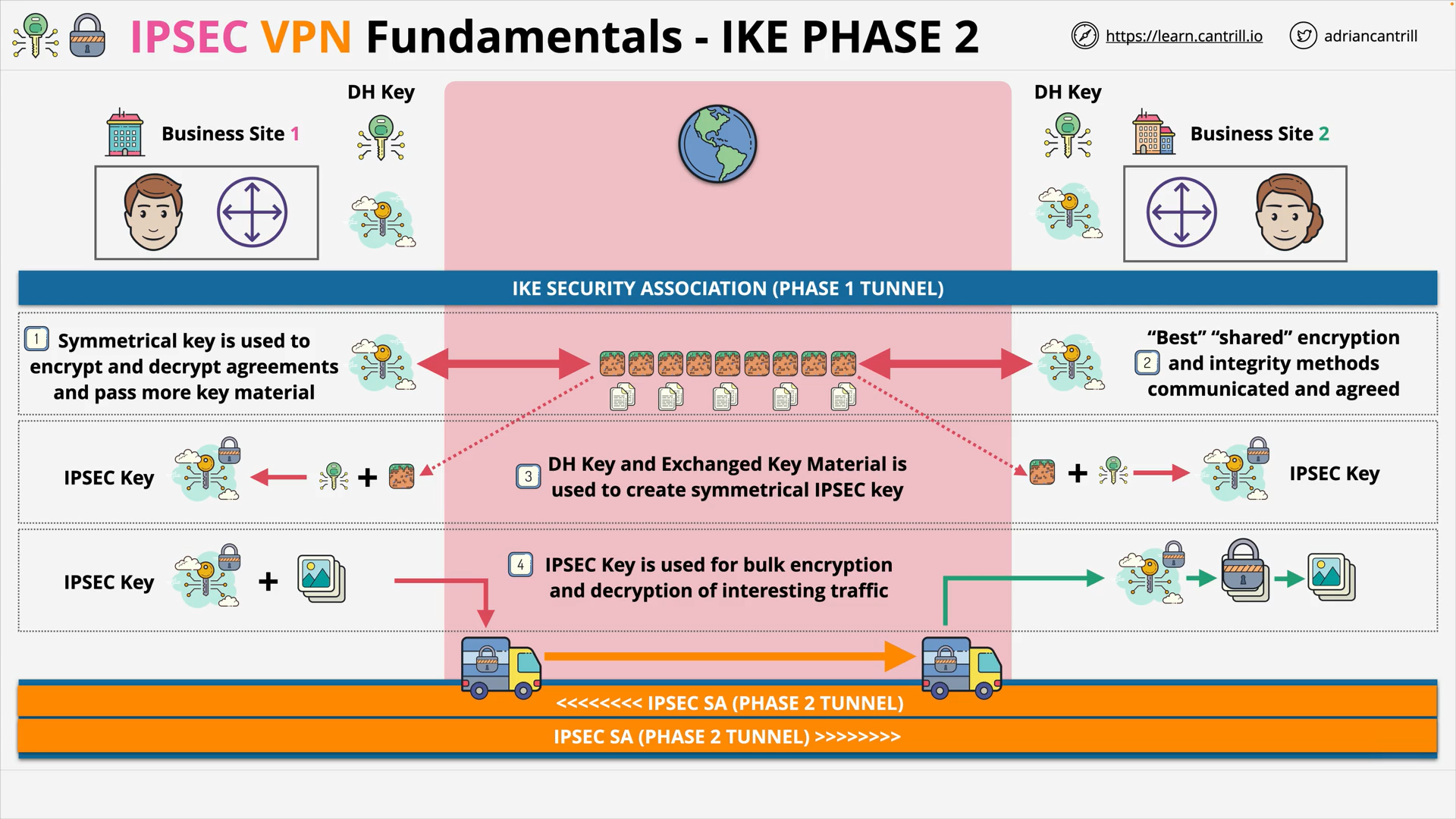 IP Sec - IKE Phase 2
IP Sec - IKE Phase 2
 Route-based VPN / Policy-based VPN
Route-based VPN / Policy-based VPN
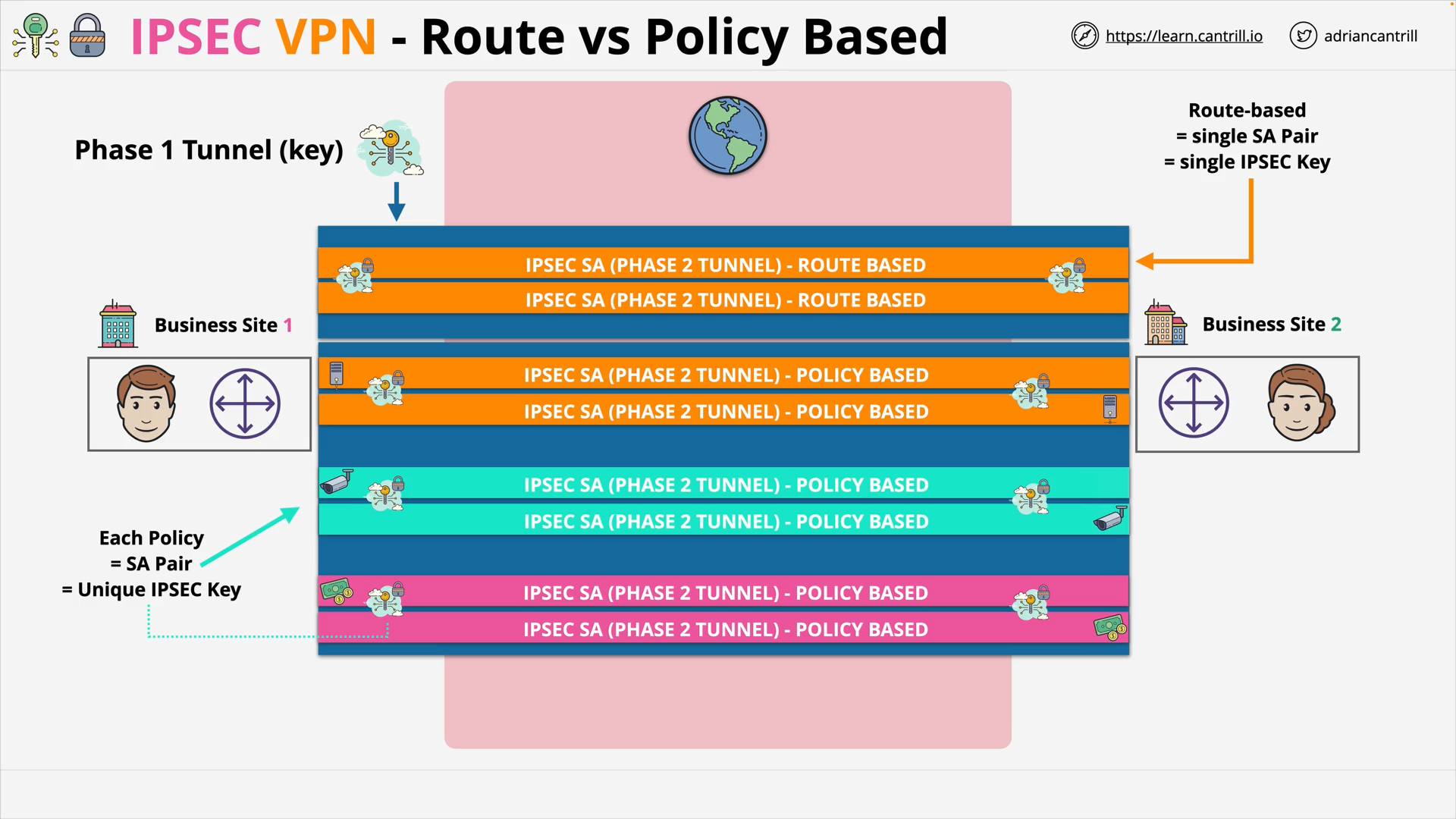 Route-based VPN / Policy-based VPN examples
Route-based VPN / Policy-based VPN examples
Fibre Optic Cable 101 (11:21)
 Fibre Optic Cables
Fibre Optic Cables
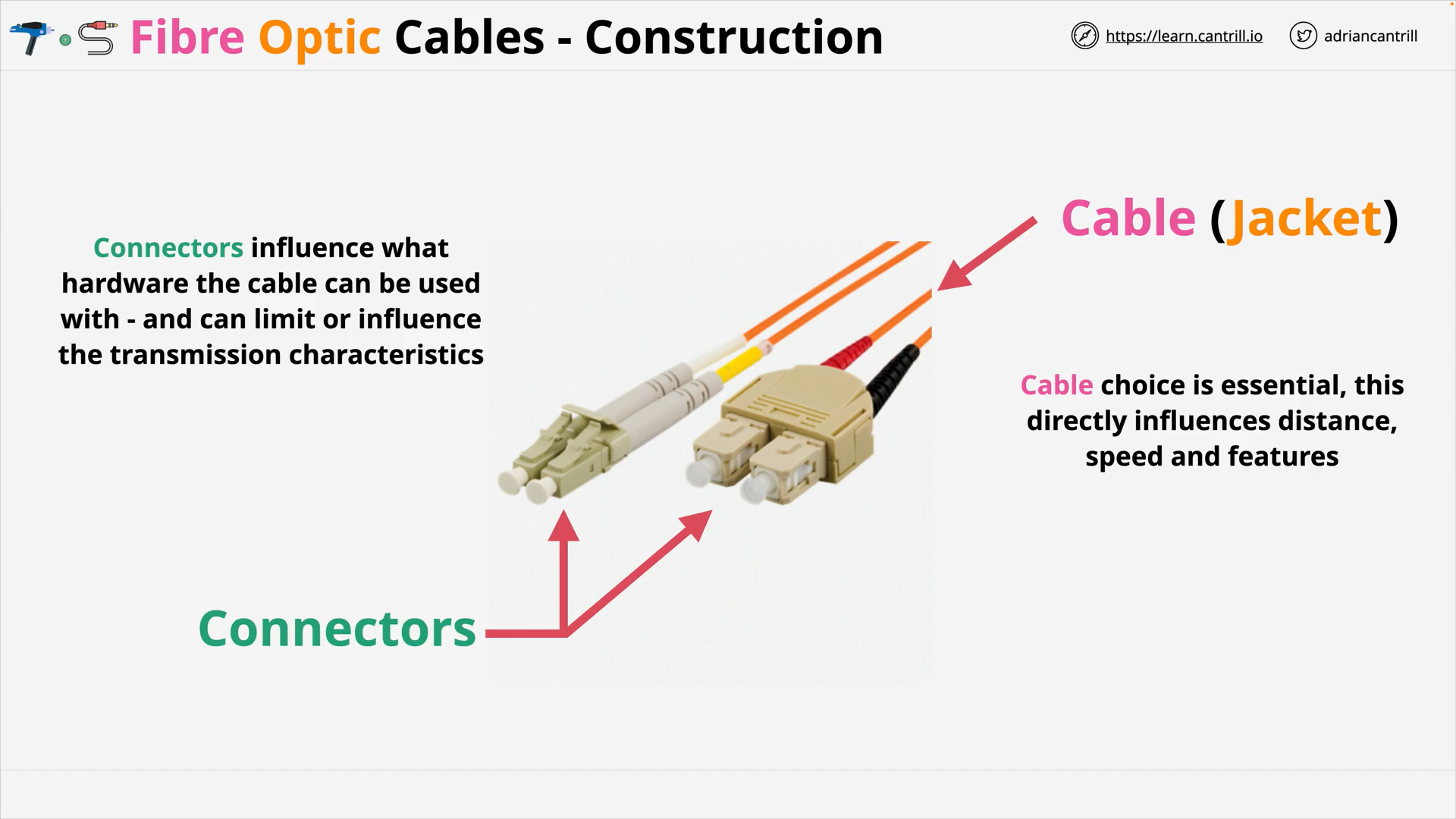 Fibre Optic Cables - Connectors
Fibre Optic Cables - Connectors
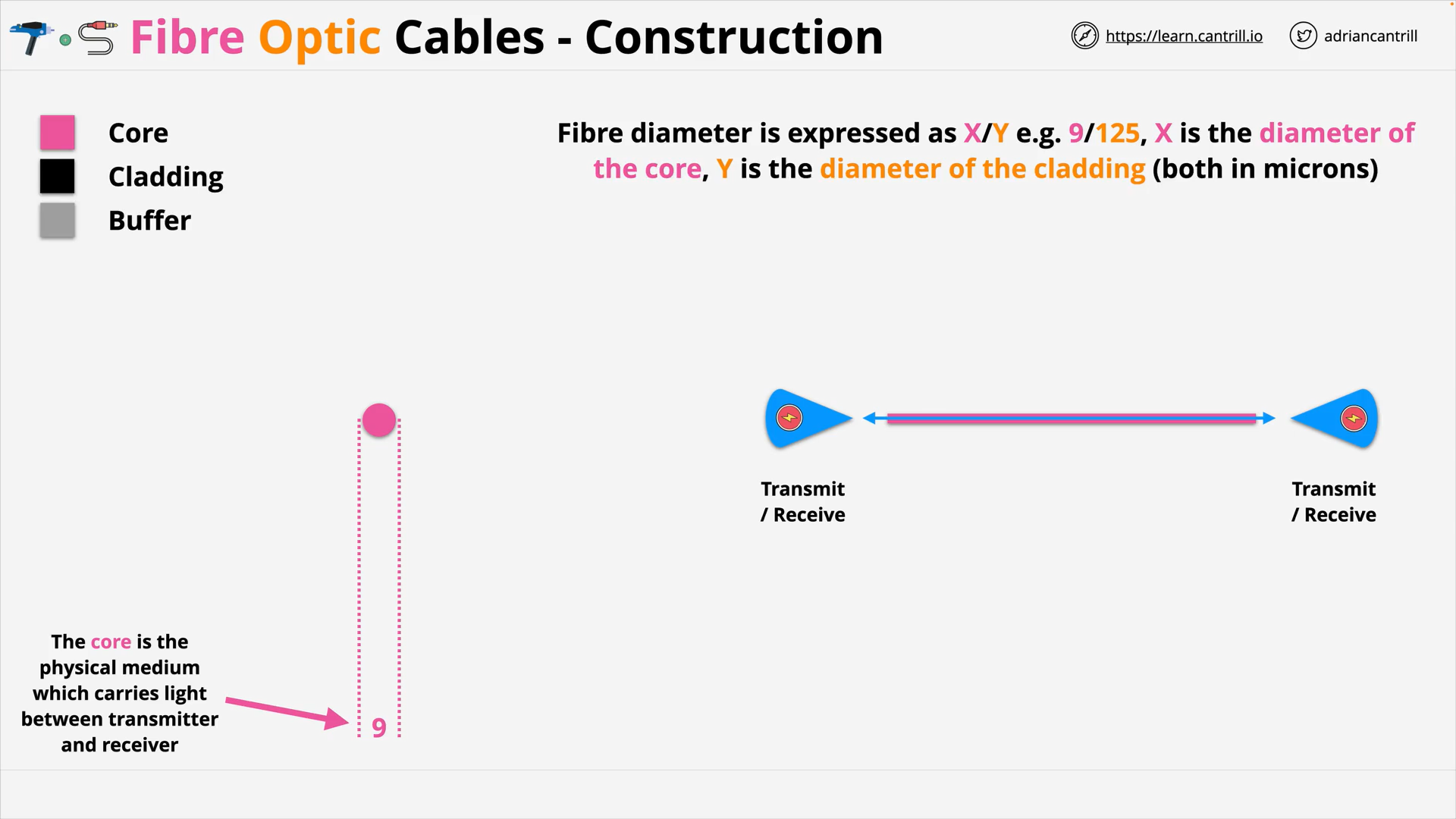 Fibre Optic Cables - Core
Fibre Optic Cables - Core
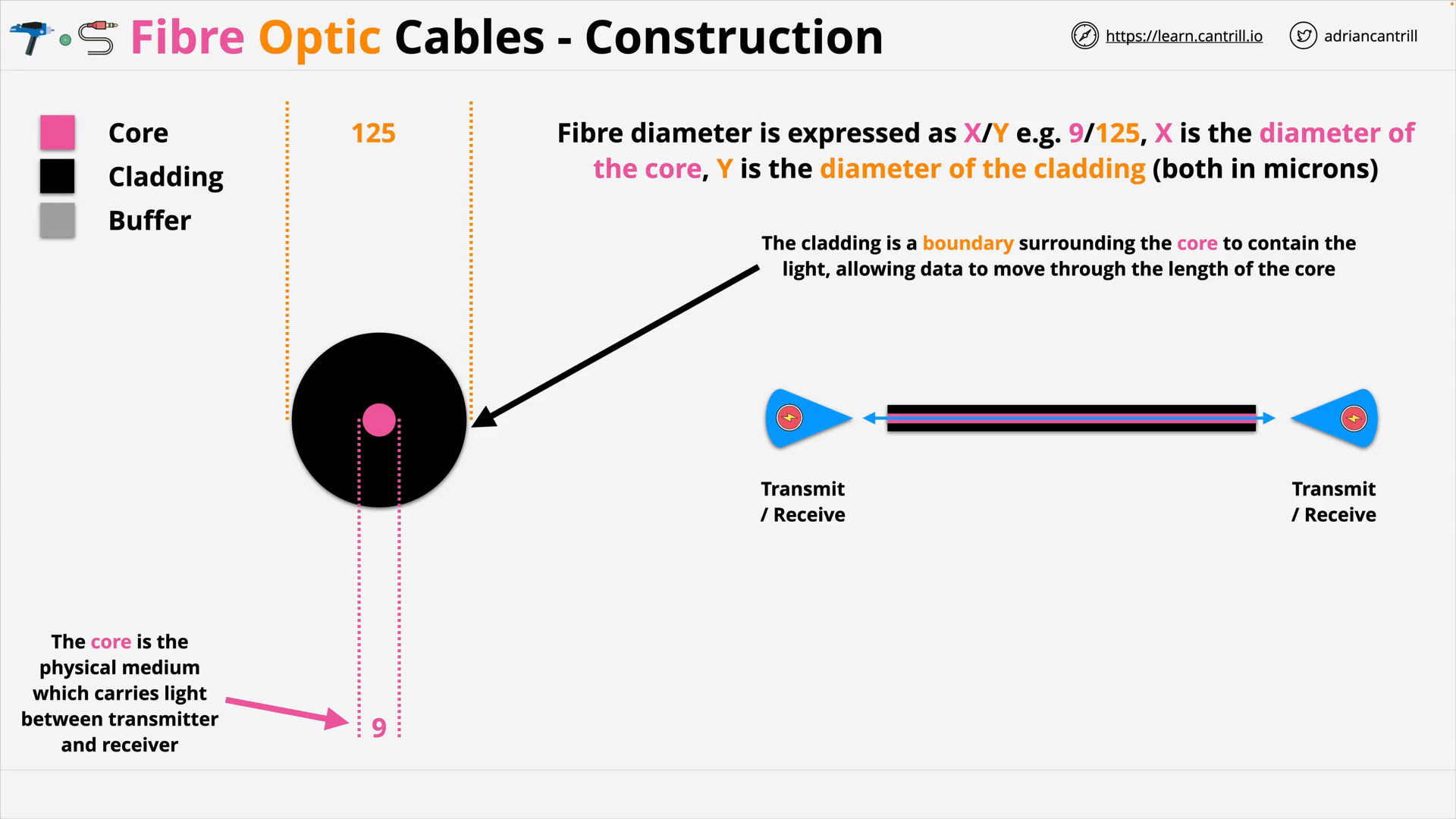 Fibre Optic Cables - Cladding
Fibre Optic Cables - Cladding
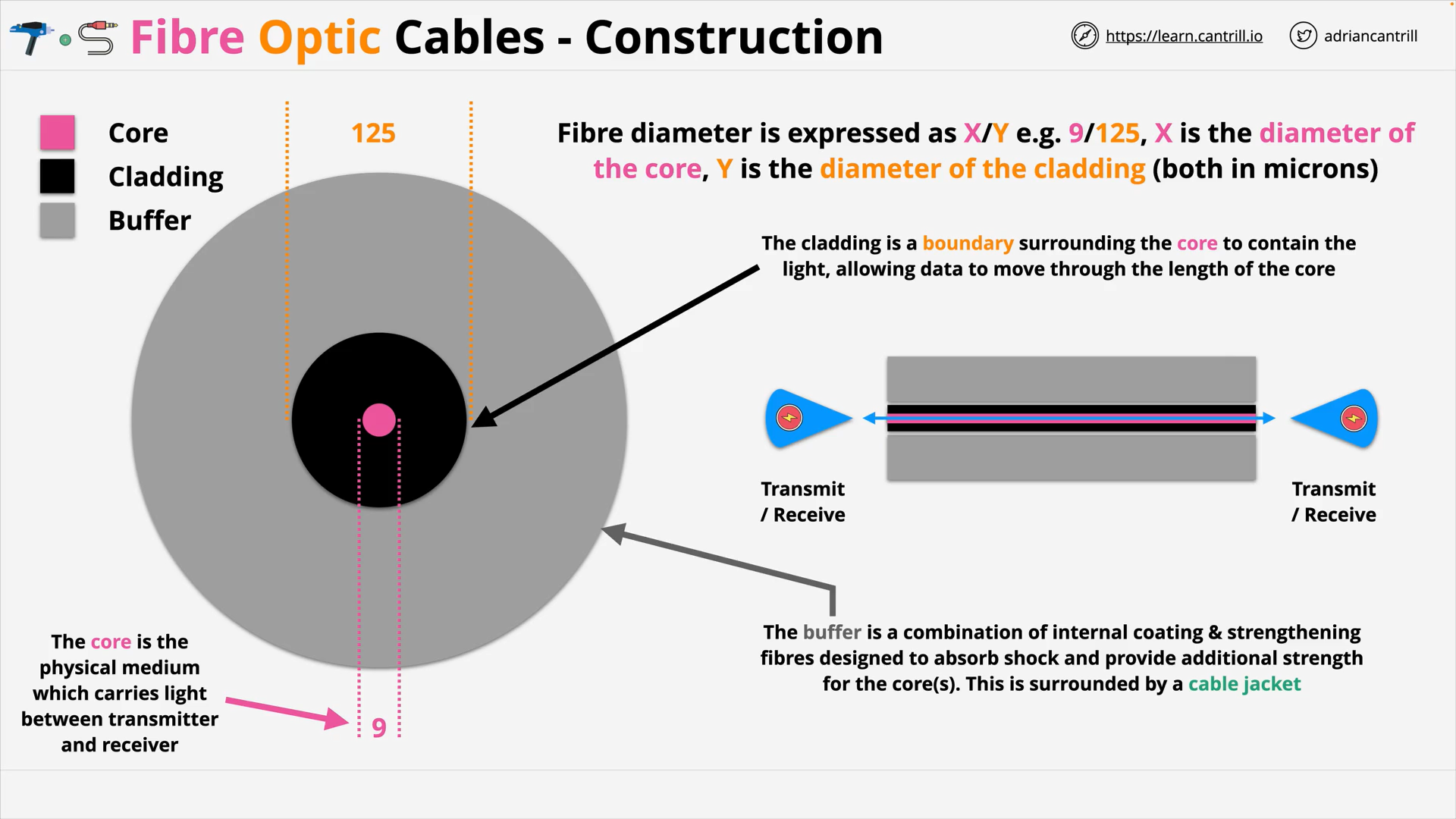 Fibre Optic Cables - Buffer
Fibre Optic Cables - Buffer
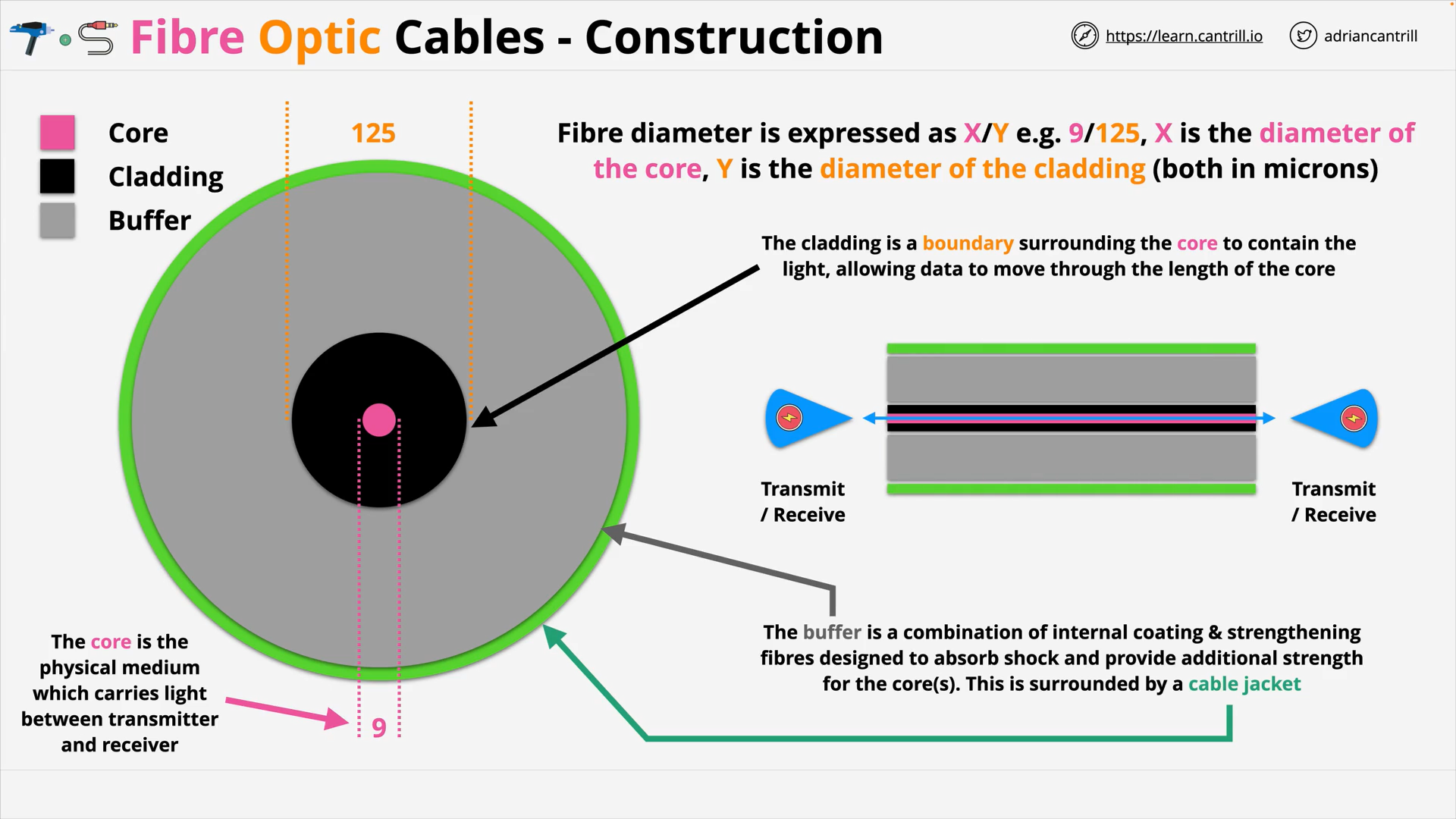 Fibre Optic Cables - Jacket
Fibre Optic Cables - Jacket
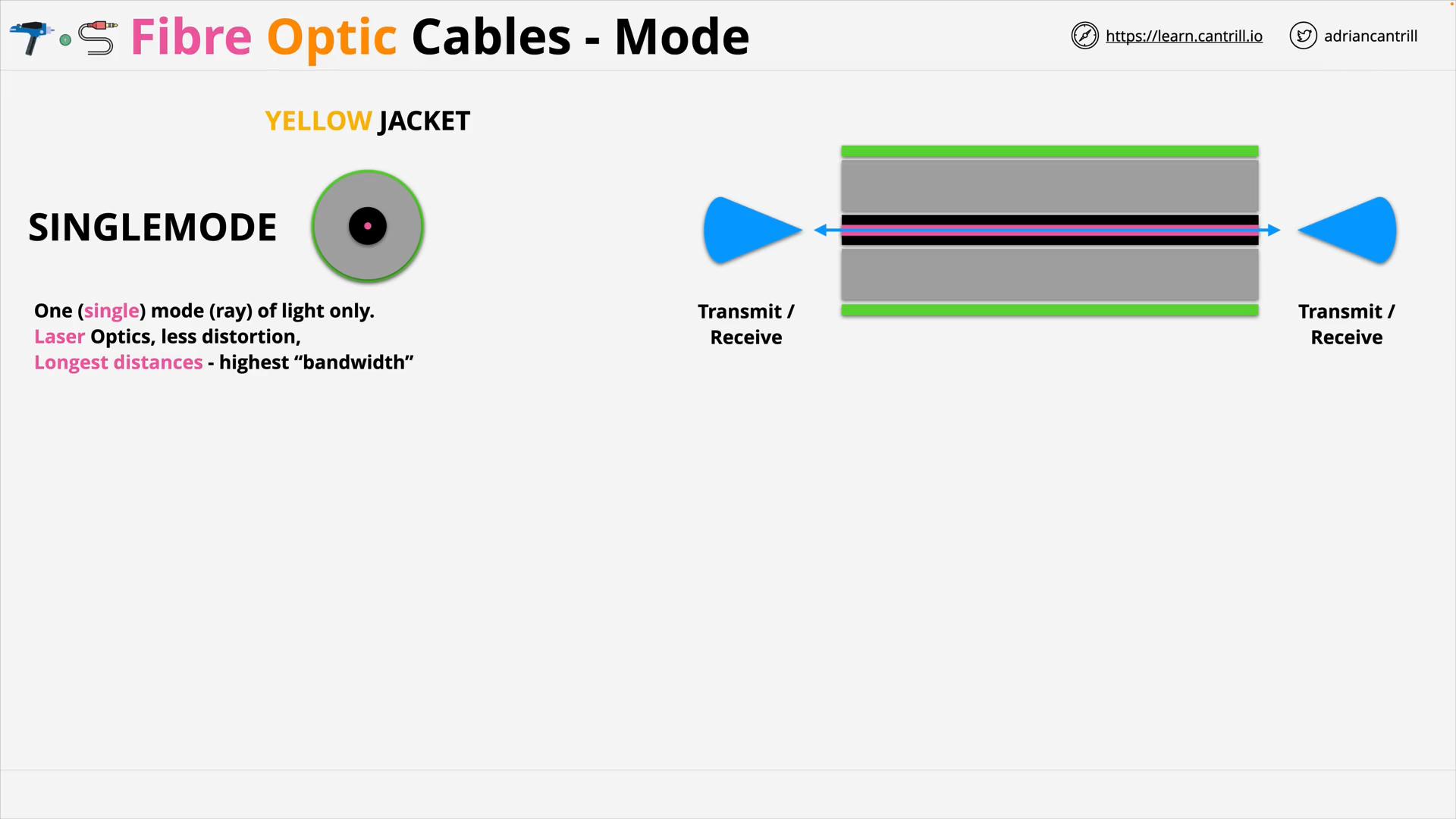 Fibre Optic Cables - Single Mode
Fibre Optic Cables - Single Mode
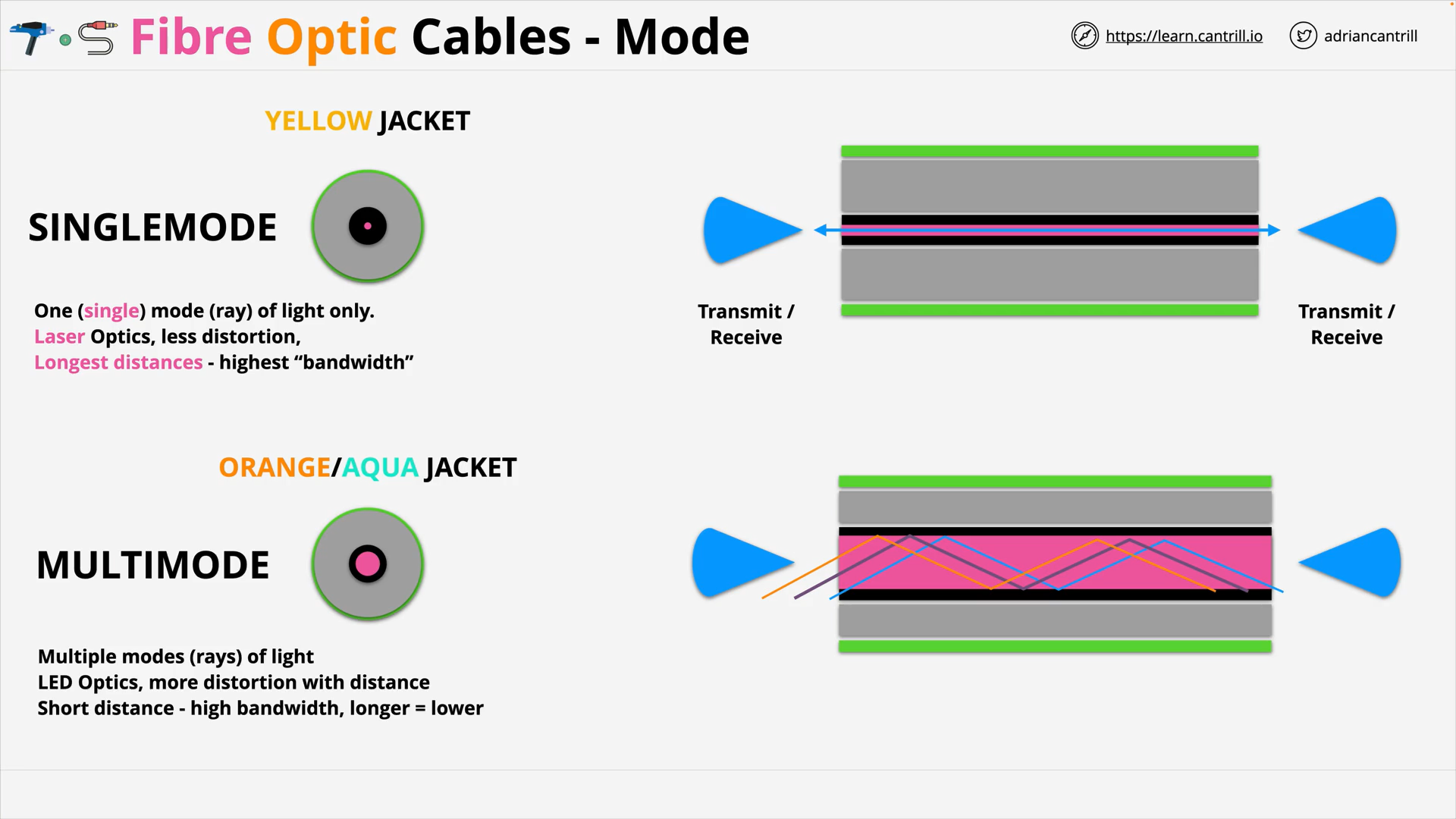 Fibre Optic Cables - Multi Mode
Fibre Optic Cables - Multi Mode
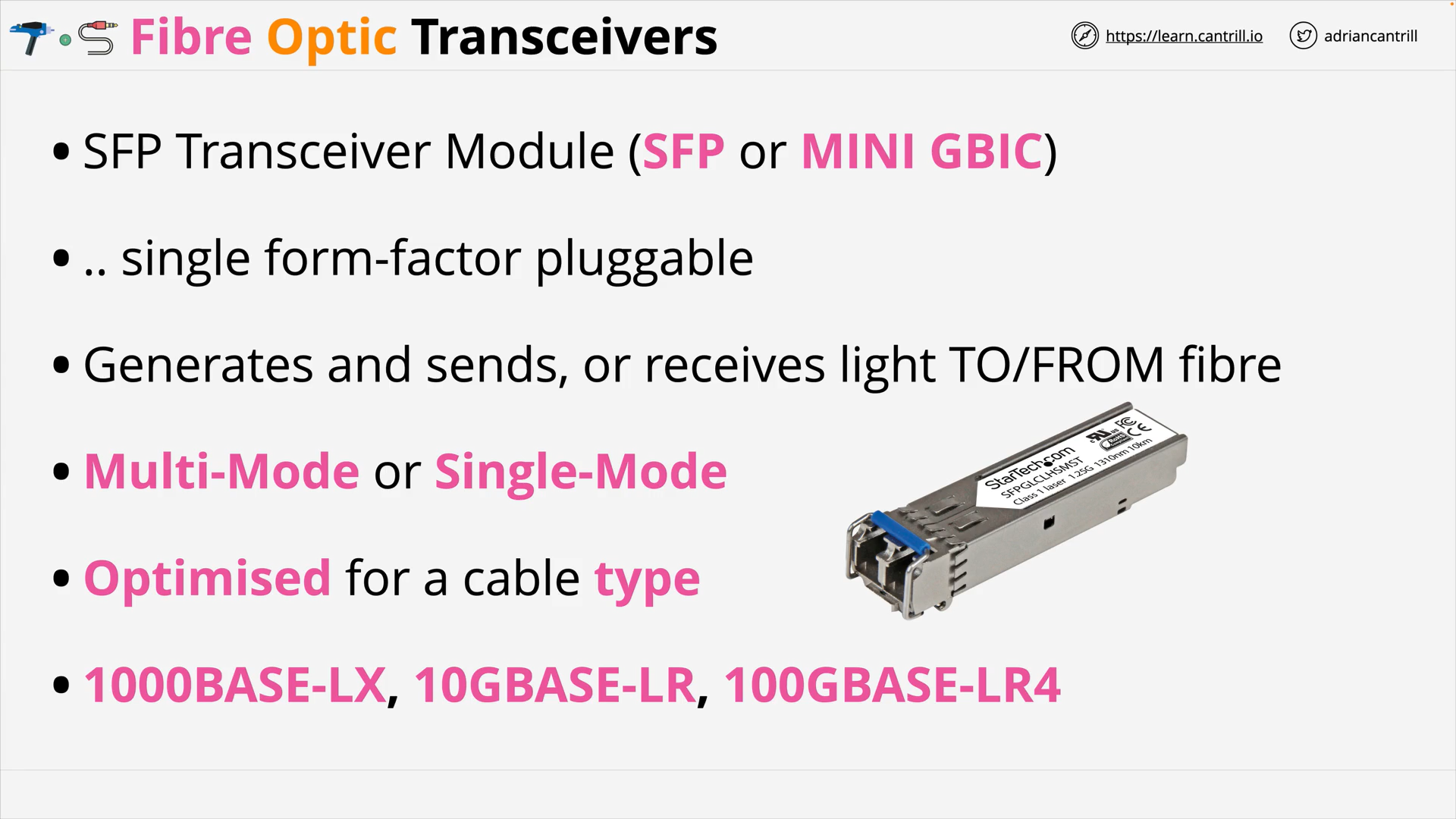 Fibre Optic Transceivers
Fibre Optic Transceivers
Security (MORE COMING SOON)
Encryption 101 - PART1 (13:56)
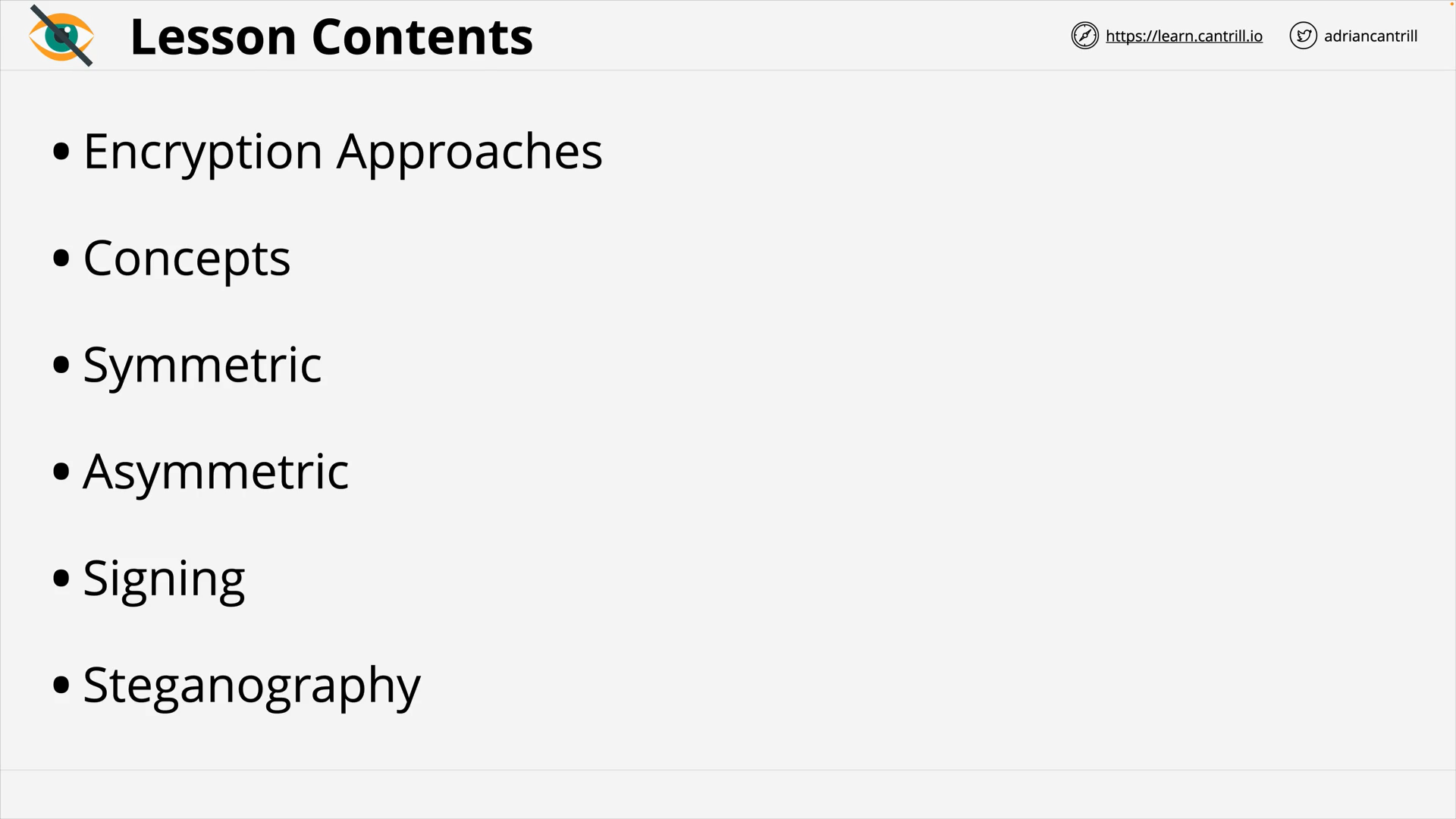 Encryption 101
Encryption 101
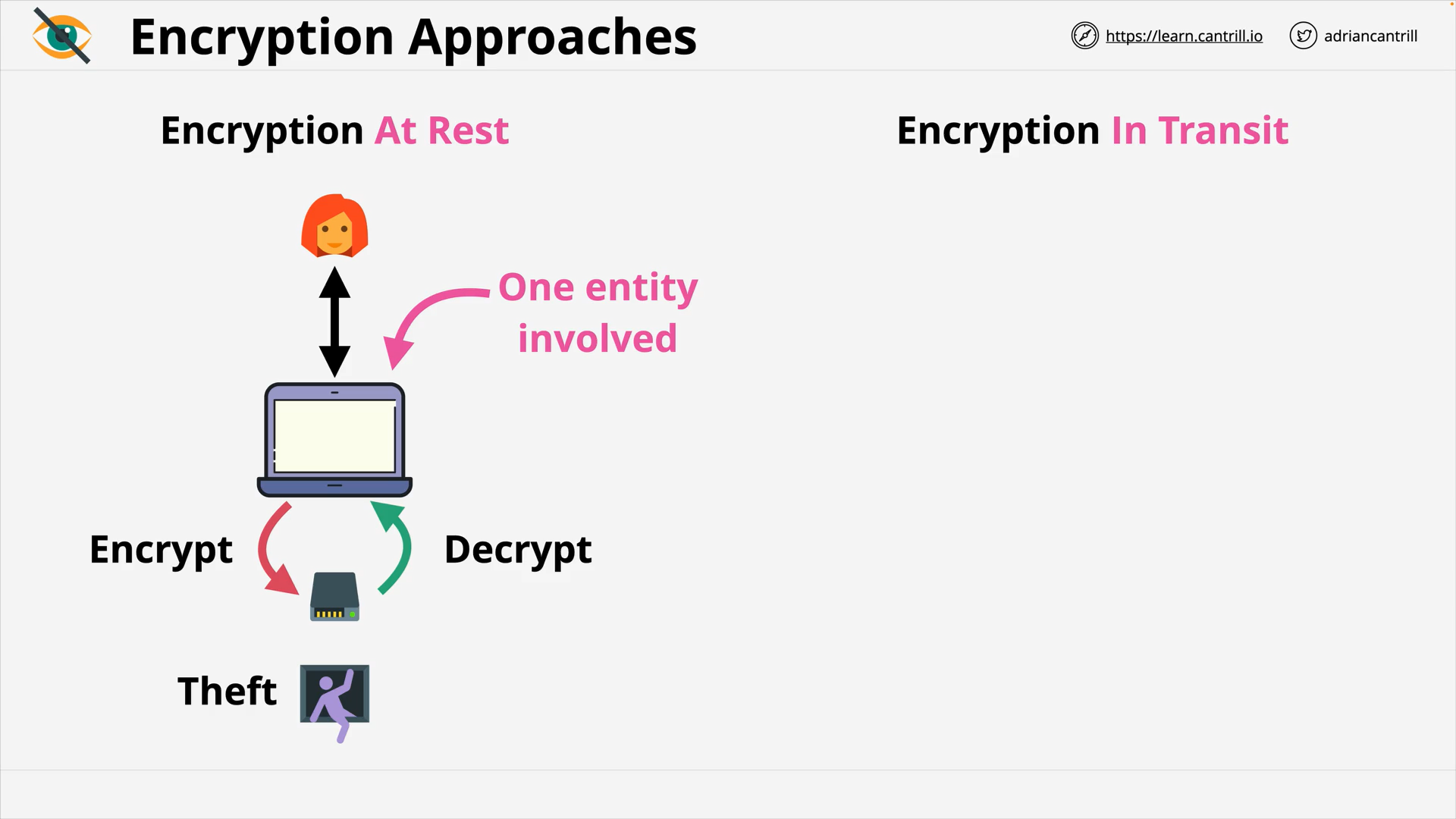 Encryption at Rest
Encryption at Rest
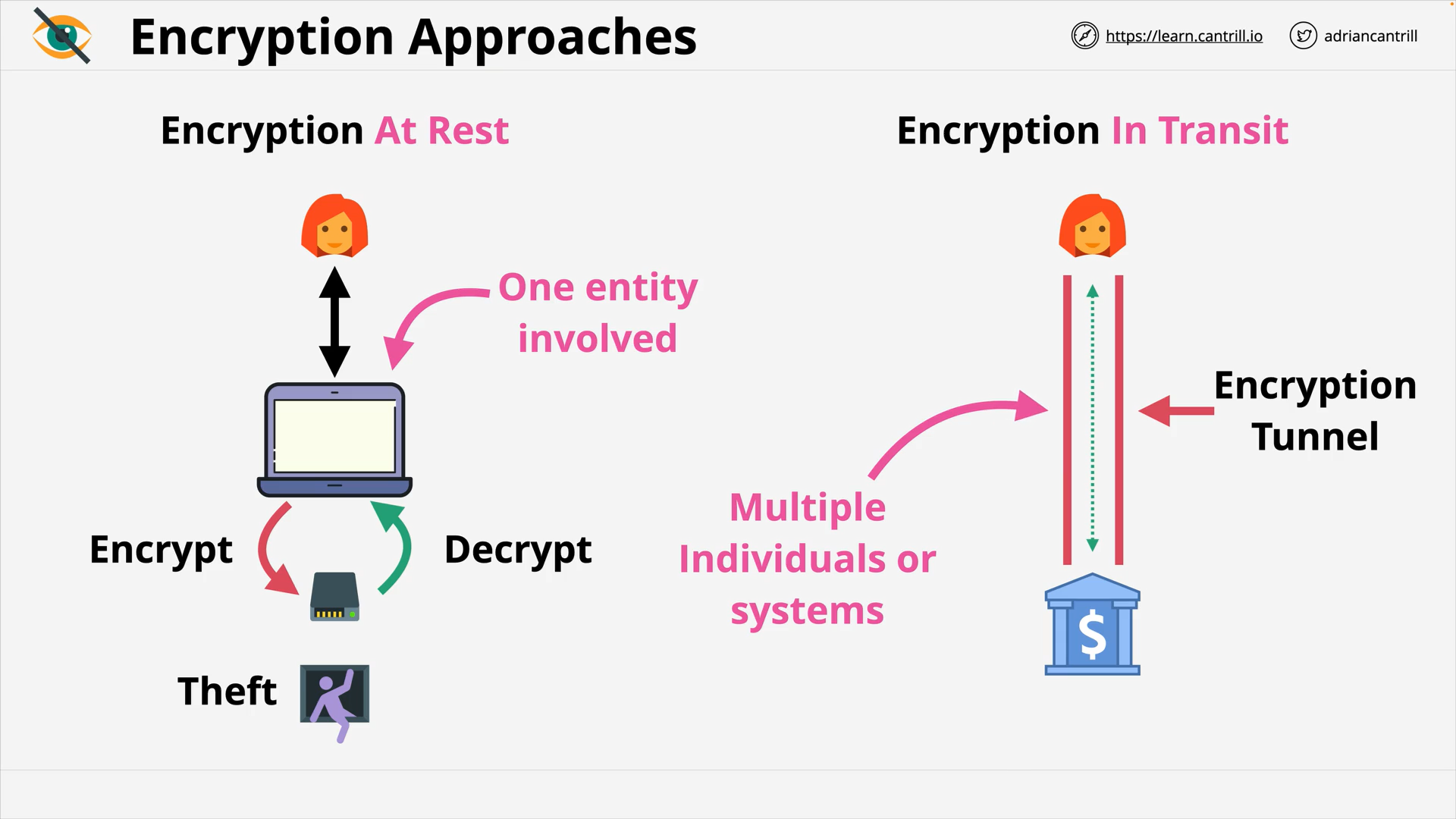 Encryption in Transit
Encryption in Transit
 Encryption Concepts: Plaintext, Algorithm, Key and Ciphertext
Encryption Concepts: Plaintext, Algorithm, Key and Ciphertext
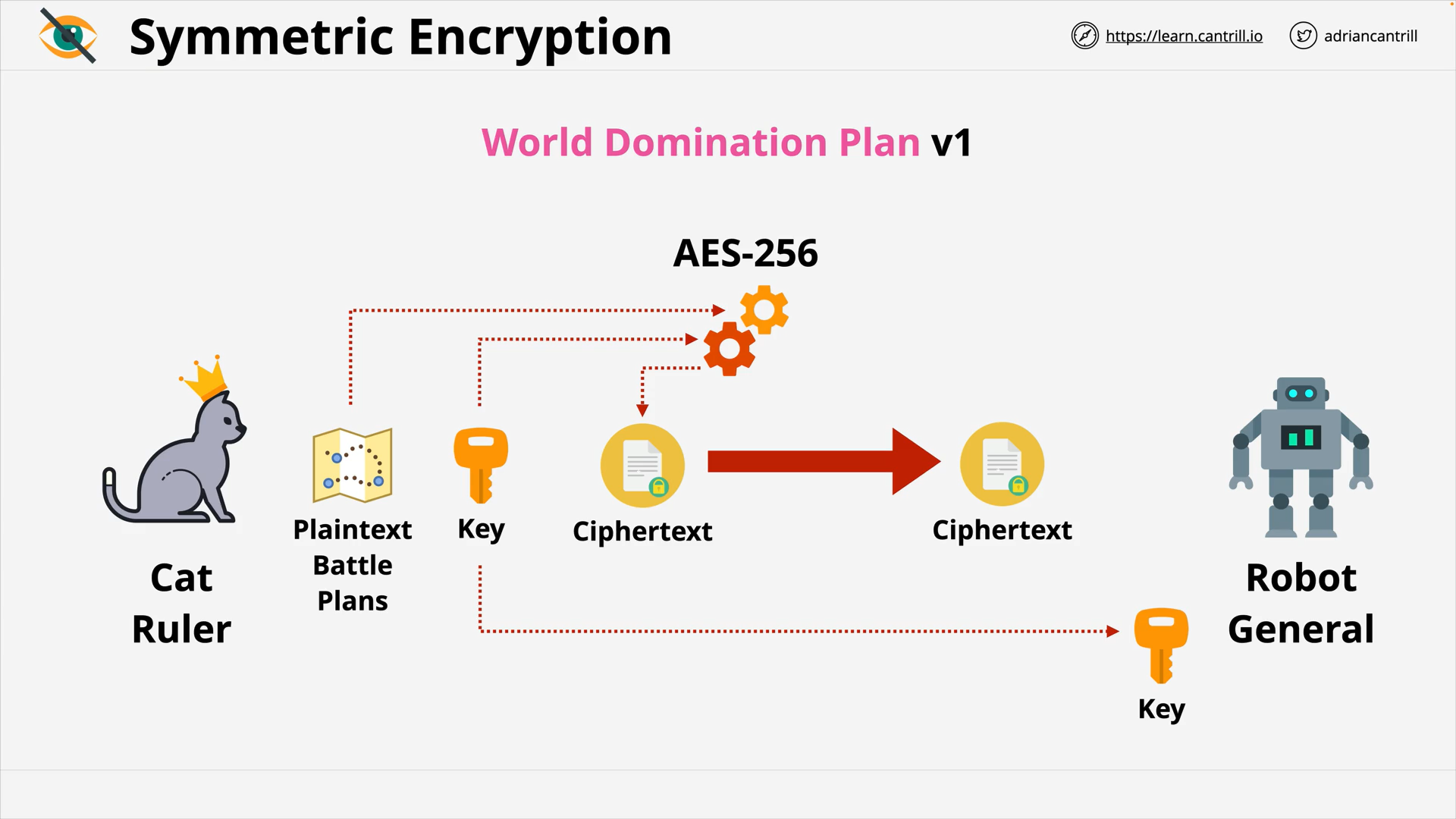 Symmetric Encryption
Symmetric Encryption
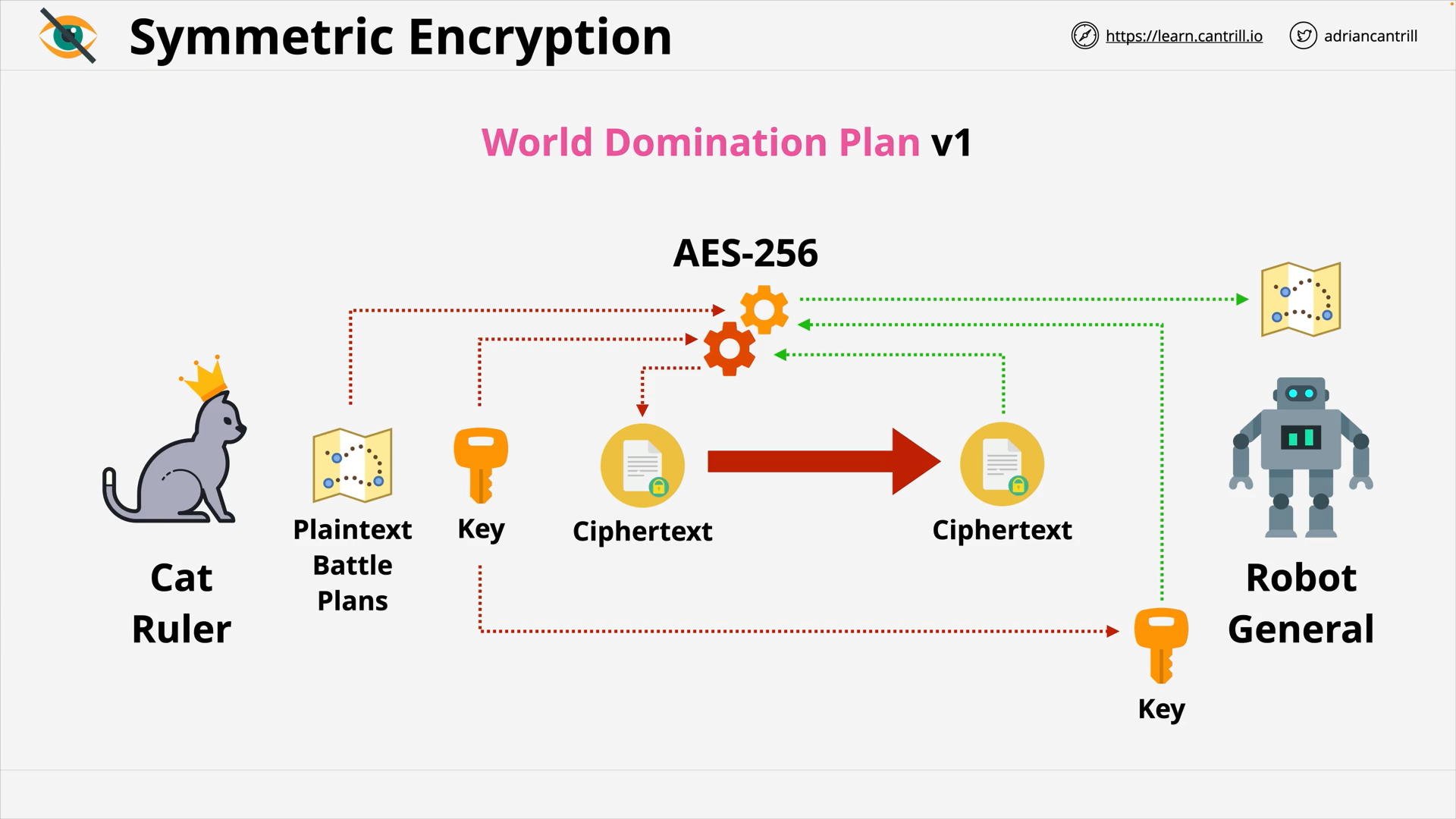 Symmetric Encryption - The same key is used for decryption
Symmetric Encryption - The same key is used for decryption
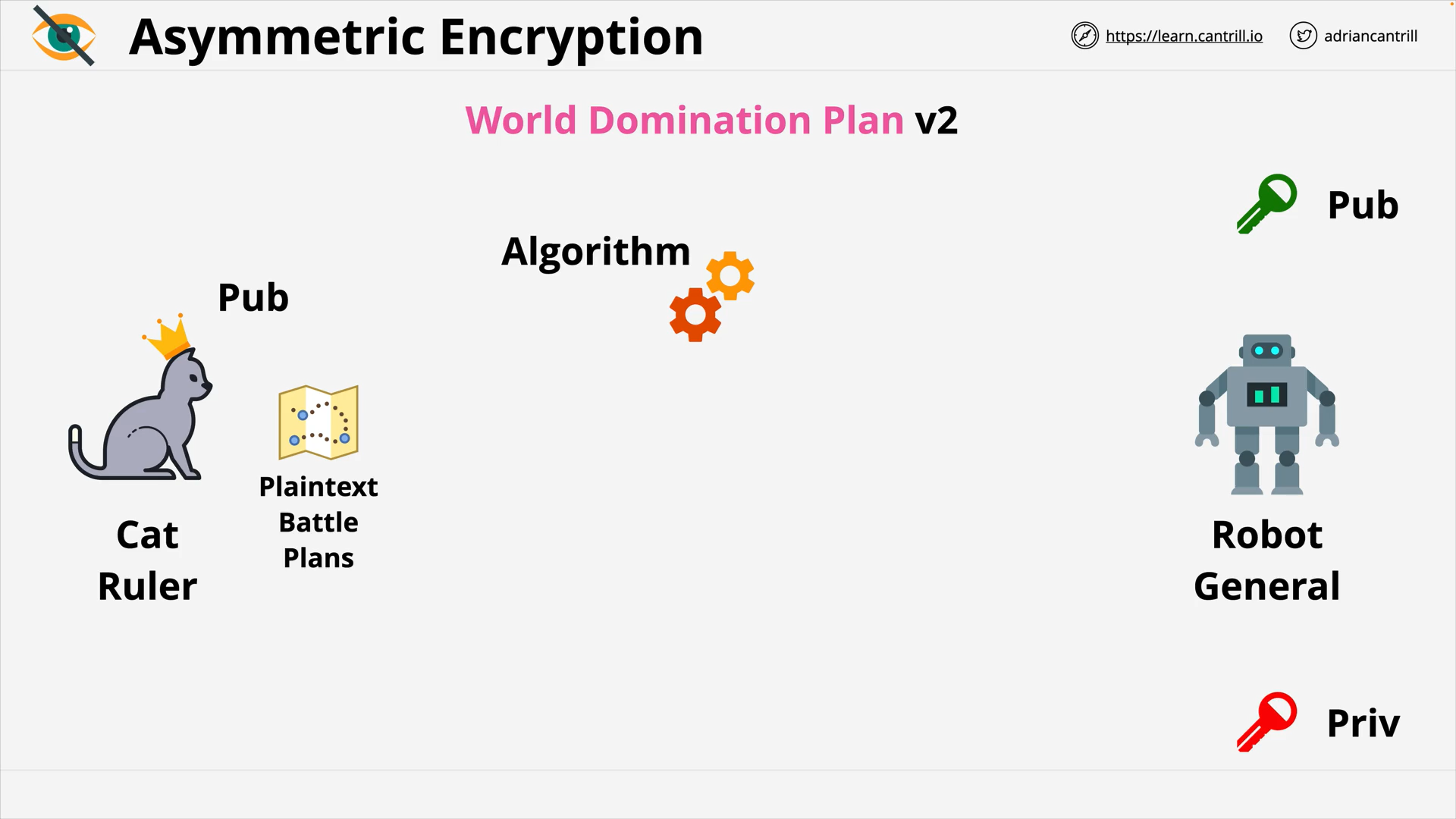 Asymmetric Encryption - Public and Private Key
Asymmetric Encryption - Public and Private Key
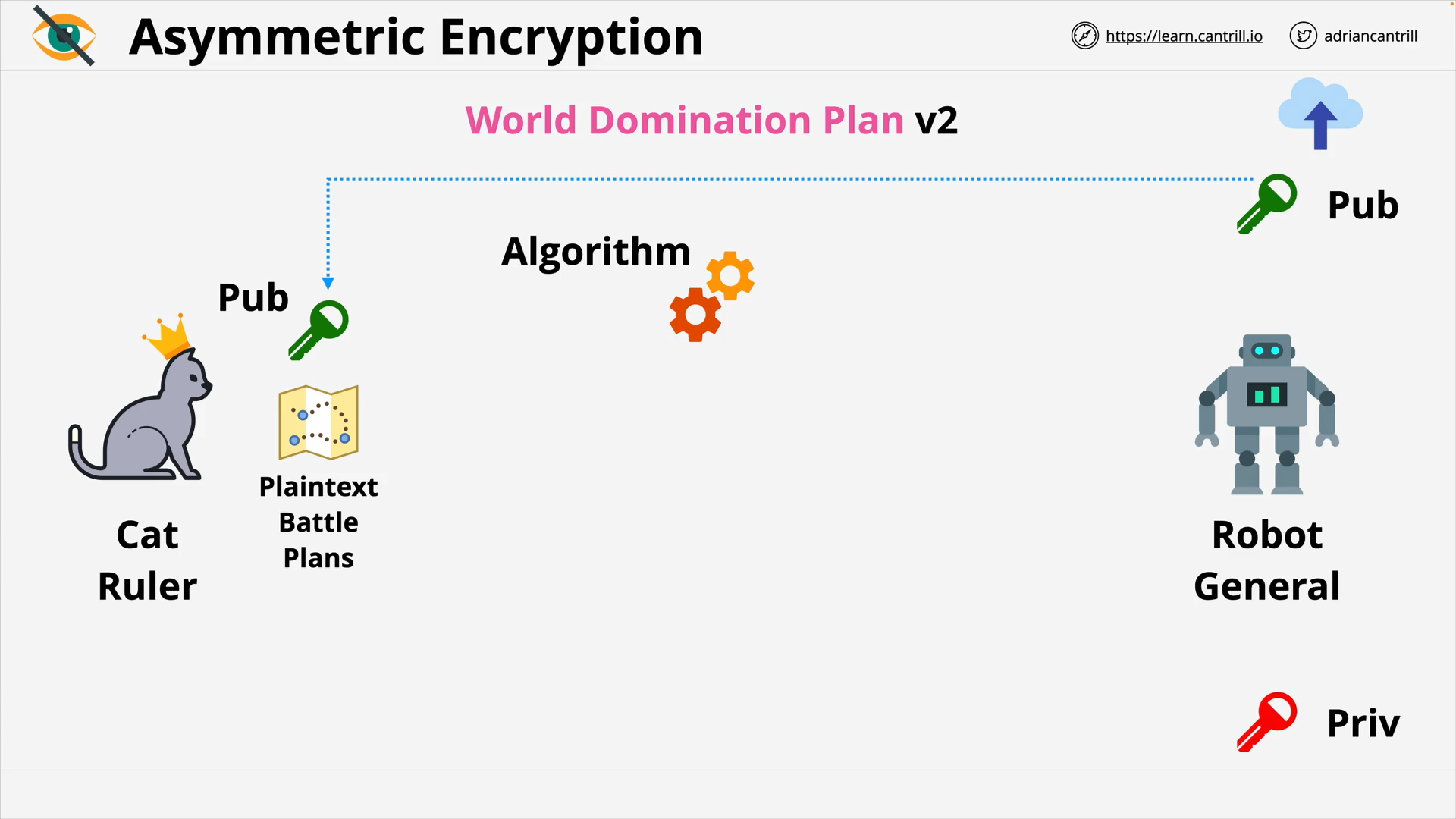 Asymmetric Encryption - Key Exchange
Asymmetric Encryption - Key Exchange
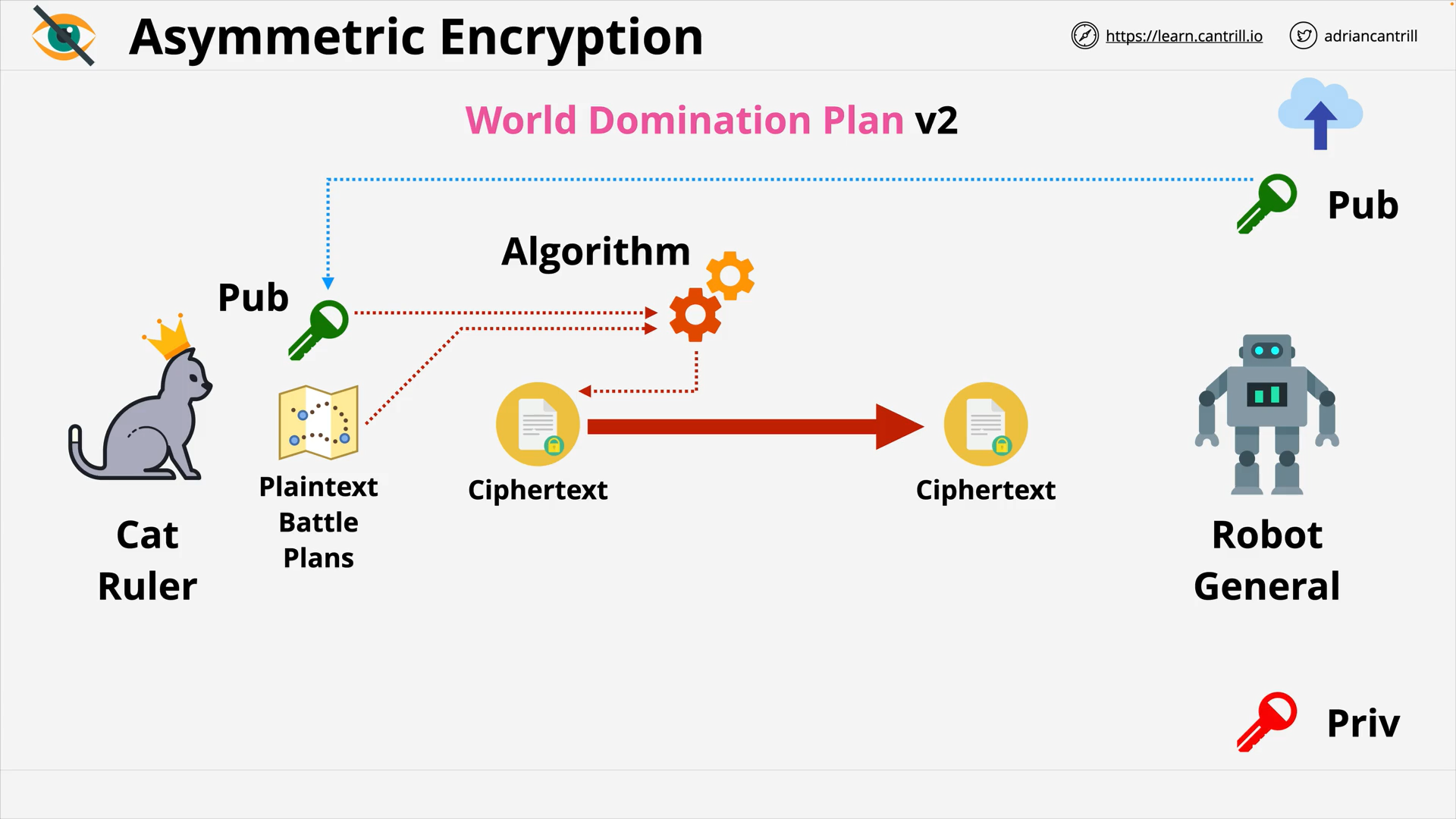 Asymmetric Encryption - Encryption
Asymmetric Encryption - Encryption
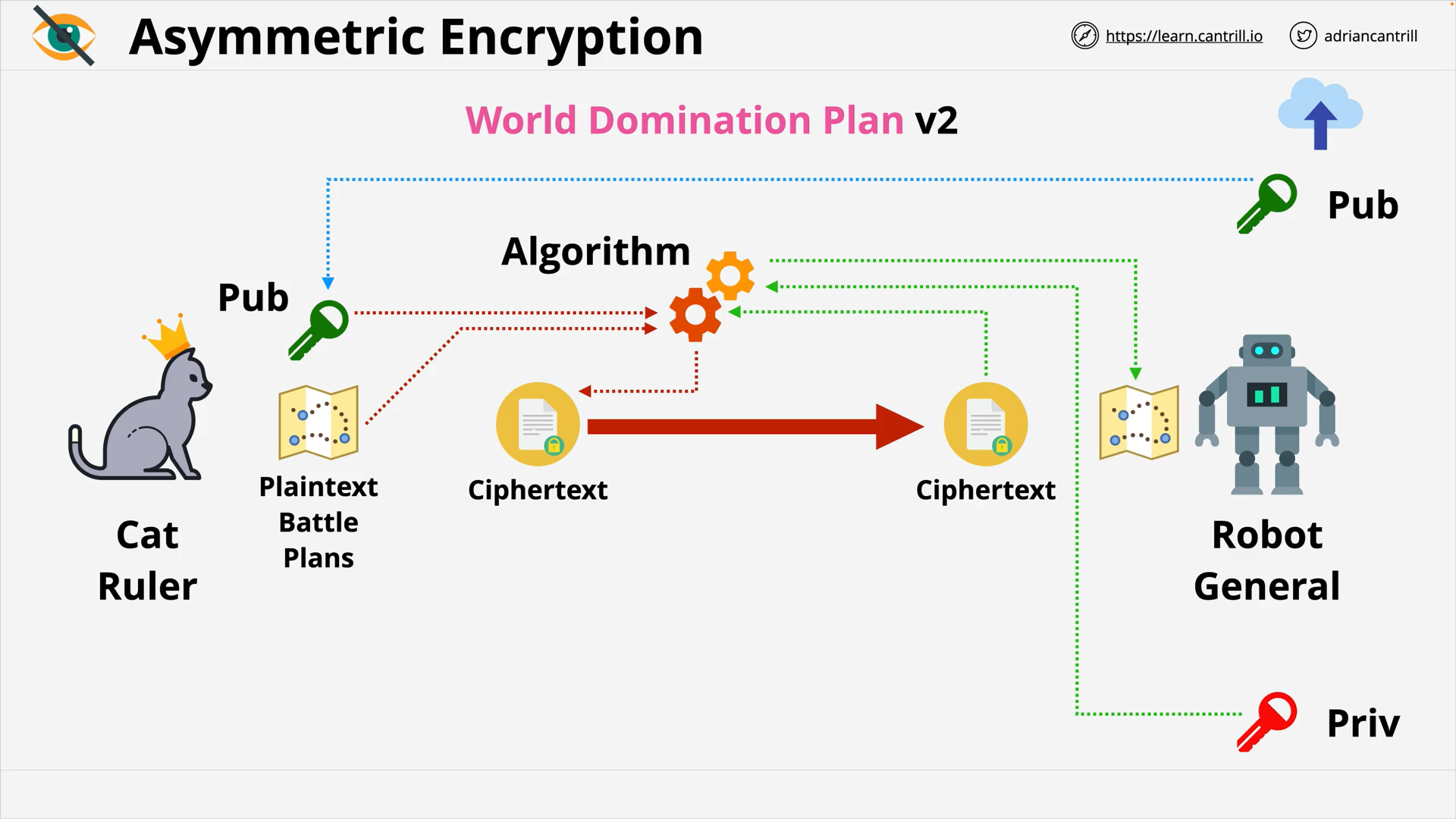 Asymmetric Encryption - Decryption
Asymmetric Encryption - Decryption
Encryption 101 - PART2 (6:42)
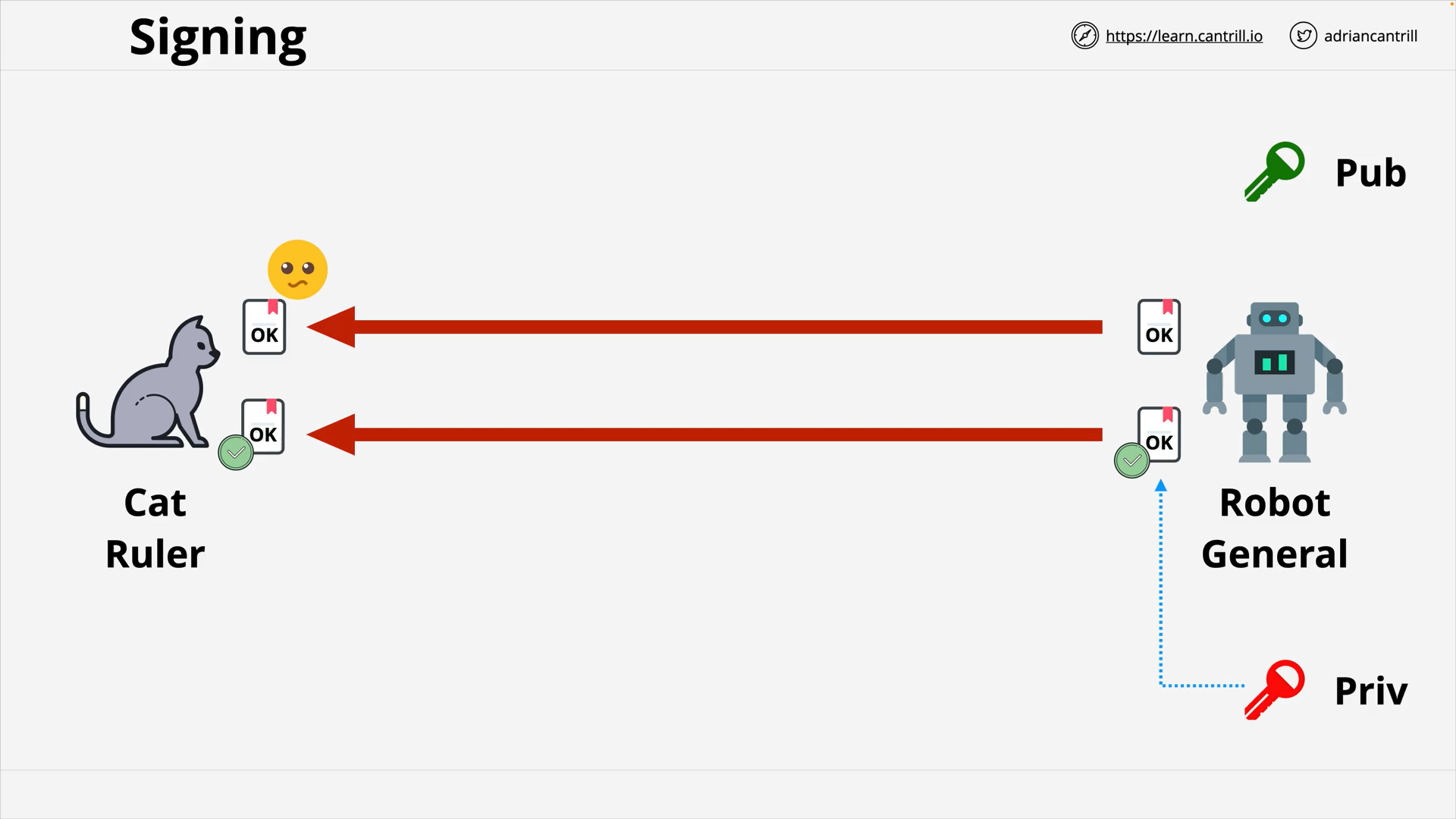
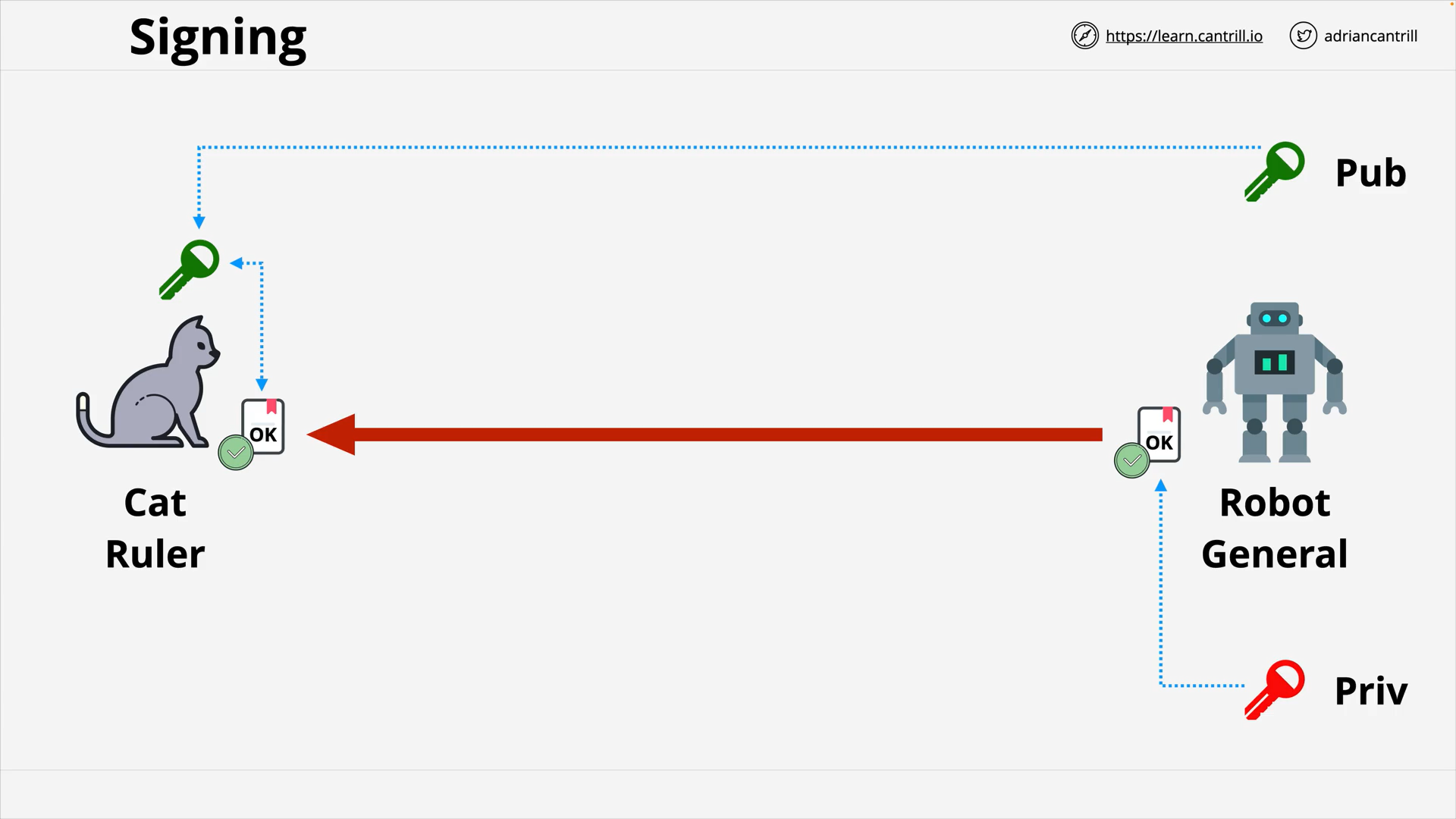 Signing
Signing
signing
The practice of using asymmetric keys to verify the authenticity and integrity of data.
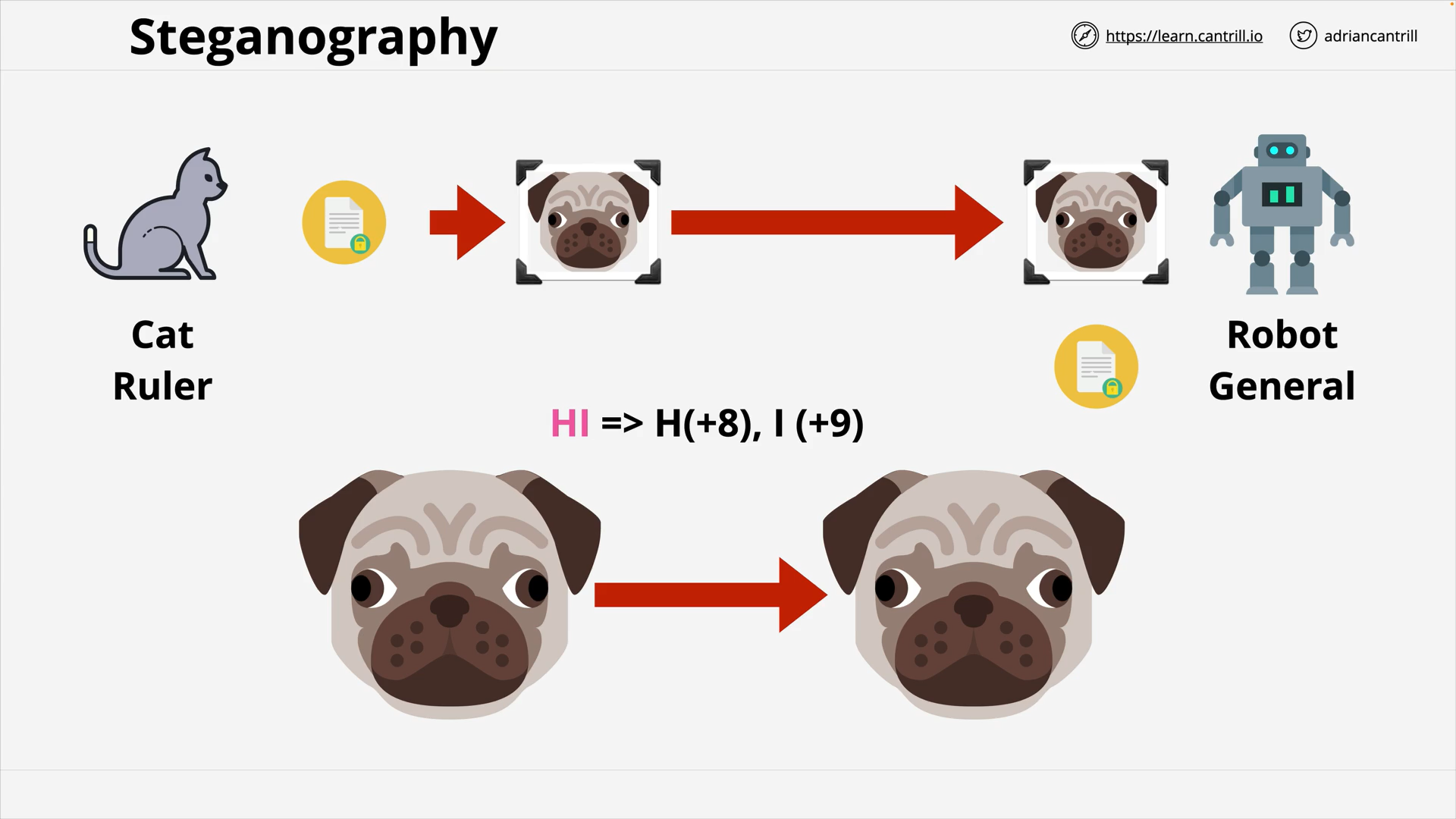
 Steganography
Steganography
steganography
The practice of concealing information within another message or physical object to avoid detection.
Envelope Encryption (8:06)
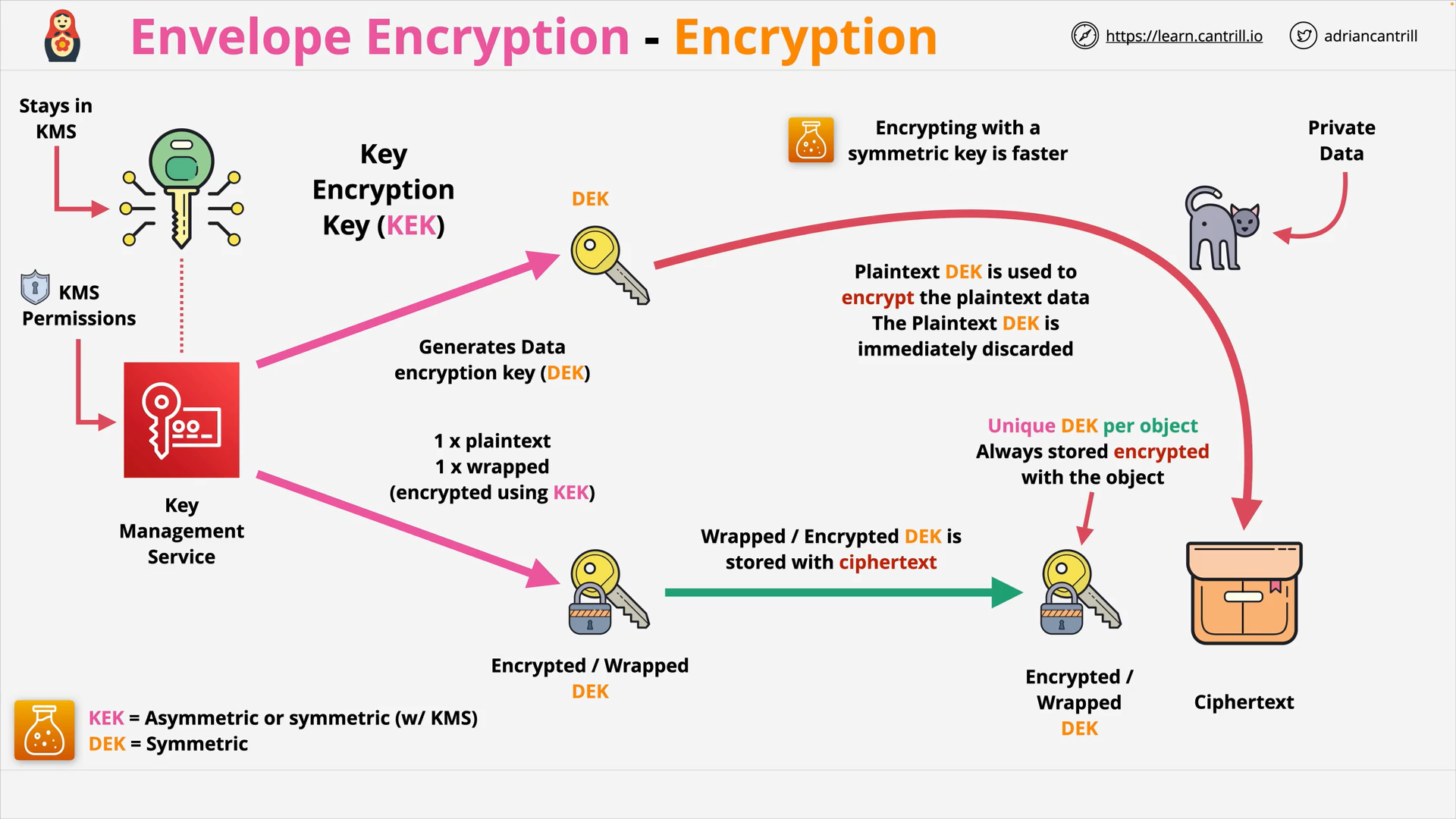 Enveloper Encryption: KEK, DEKs
Enveloper Encryption: KEK, DEKs
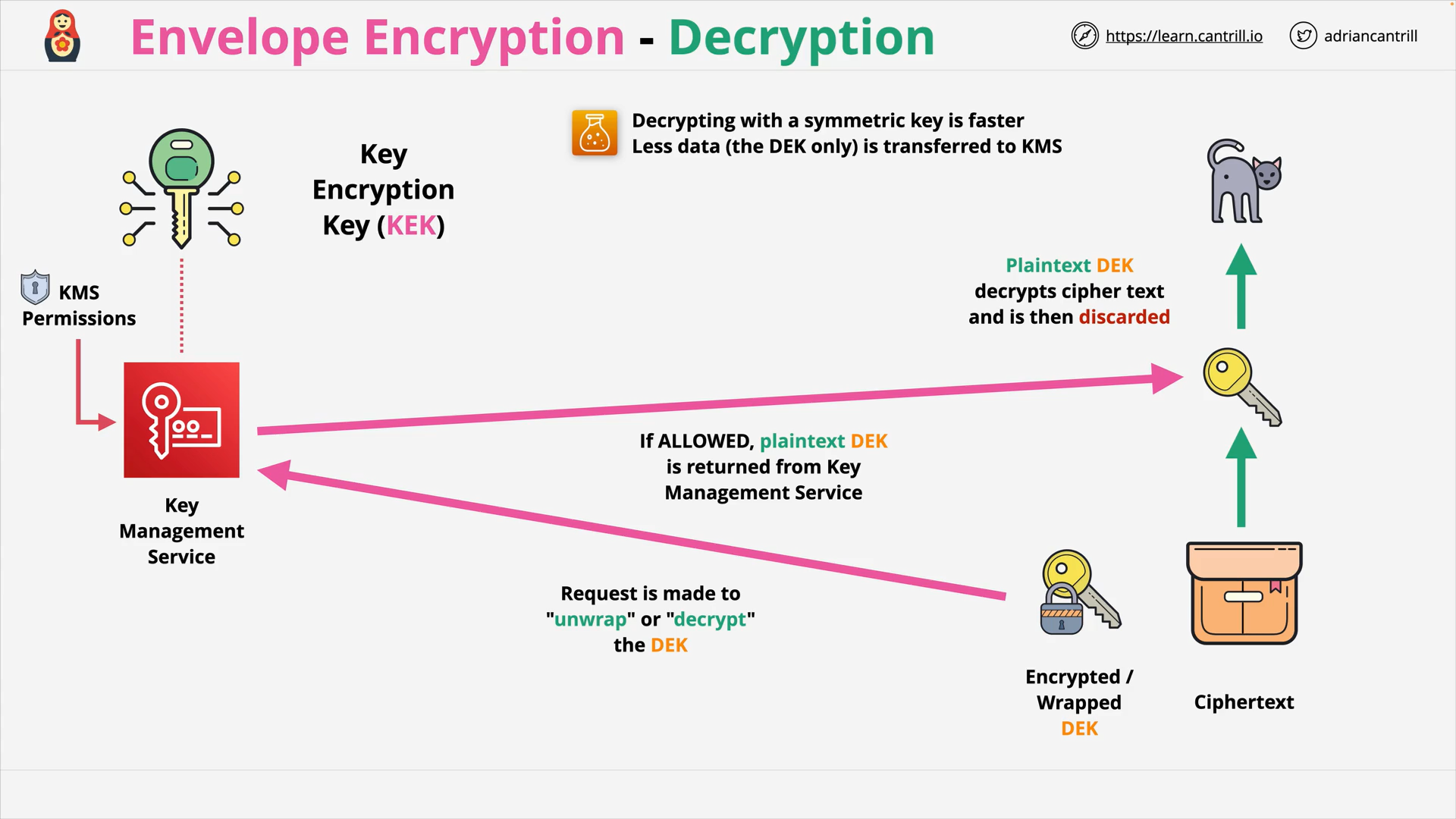 Enveloper Encryption - Decryption
Enveloper Encryption - Decryption
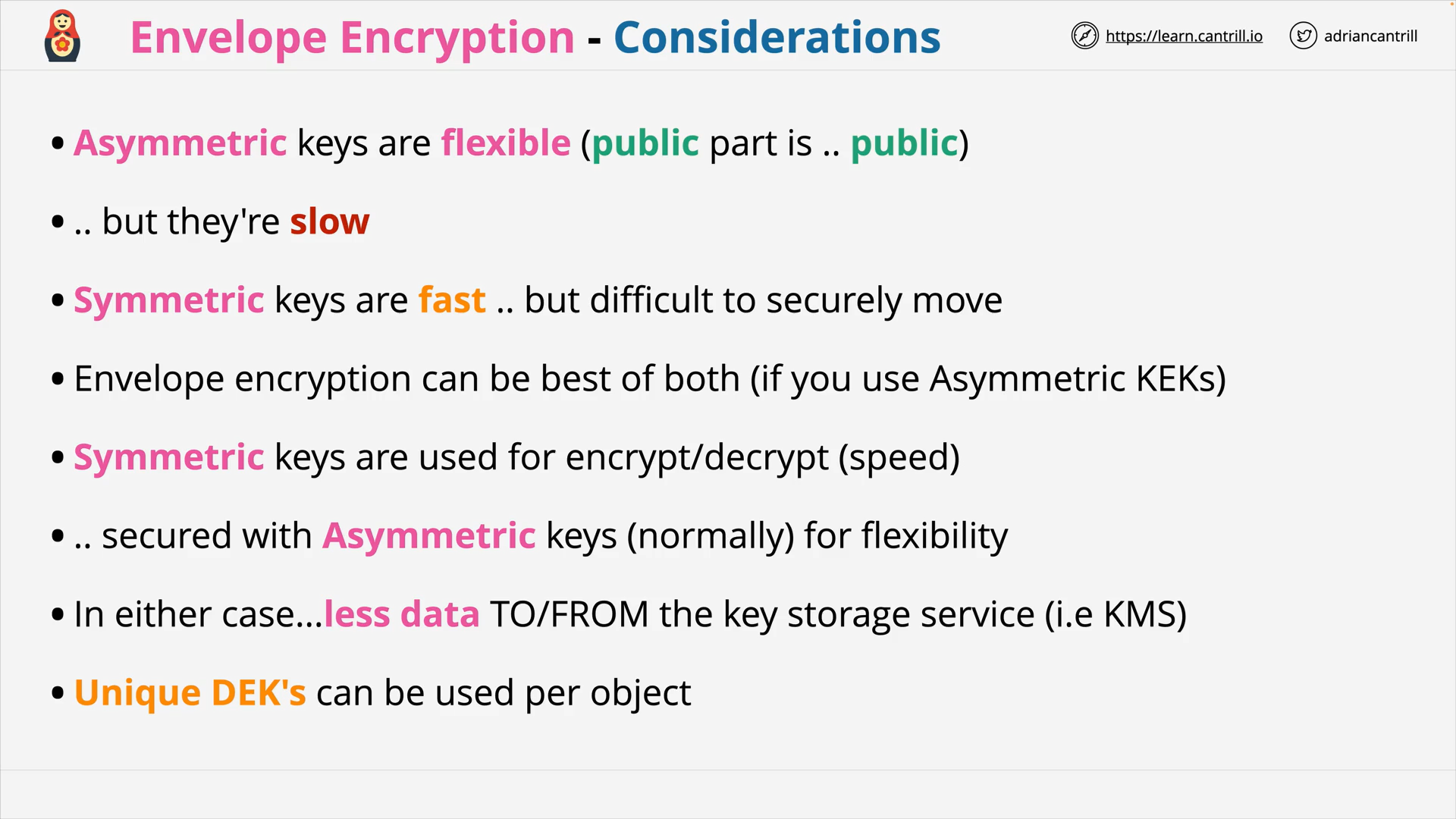 Enveloper Encryption - Considerations
Enveloper Encryption - Considerations
Hardware Security Modules (HSMs) (6:40)
__learn.cantrill.i.png) HSM - Without HSM
HSM - Without HSM
__learn.cantrill.i.png) HSM - With HSM
HSM - With HSM
__learn.cantrill.i.png) HSM - Keys are stored securely inside the HSM
HSM - Keys are stored securely inside the HSM
__learn.cantrill.i.png) HSM - Authenticate takes place inside the HSM
HSM - Authenticate takes place inside the HSM
__learn.cantrill.i.png) HSM - HSMs are tamper proof & hardened against physical logical attacks
HSM - HSMs are tamper proof & hardened against physical logical attacks
__learn.cantrill.i.png) HSM - Accessed via tightly controlled, industry standard APIs
HSM - Accessed via tightly controlled, industry standard APIs
__learn.cantrill.i.png) HSM - Role Separation: HSM admins can update & maintain but don’t always have full access
HSM - Role Separation: HSM admins can update & maintain but don’t always have full access
__learn.cantrill.i.png) HSM - HSM can be used to processing SSL/TLS or PKI Signing certificate
HSM - HSM can be used to processing SSL/TLS or PKI Signing certificate
Hash Functions & Hashing (13:19)
 Hashing
Hashing
hashing
The process of applying a hash function to data to produce a unique and irreversible representation of the original data.
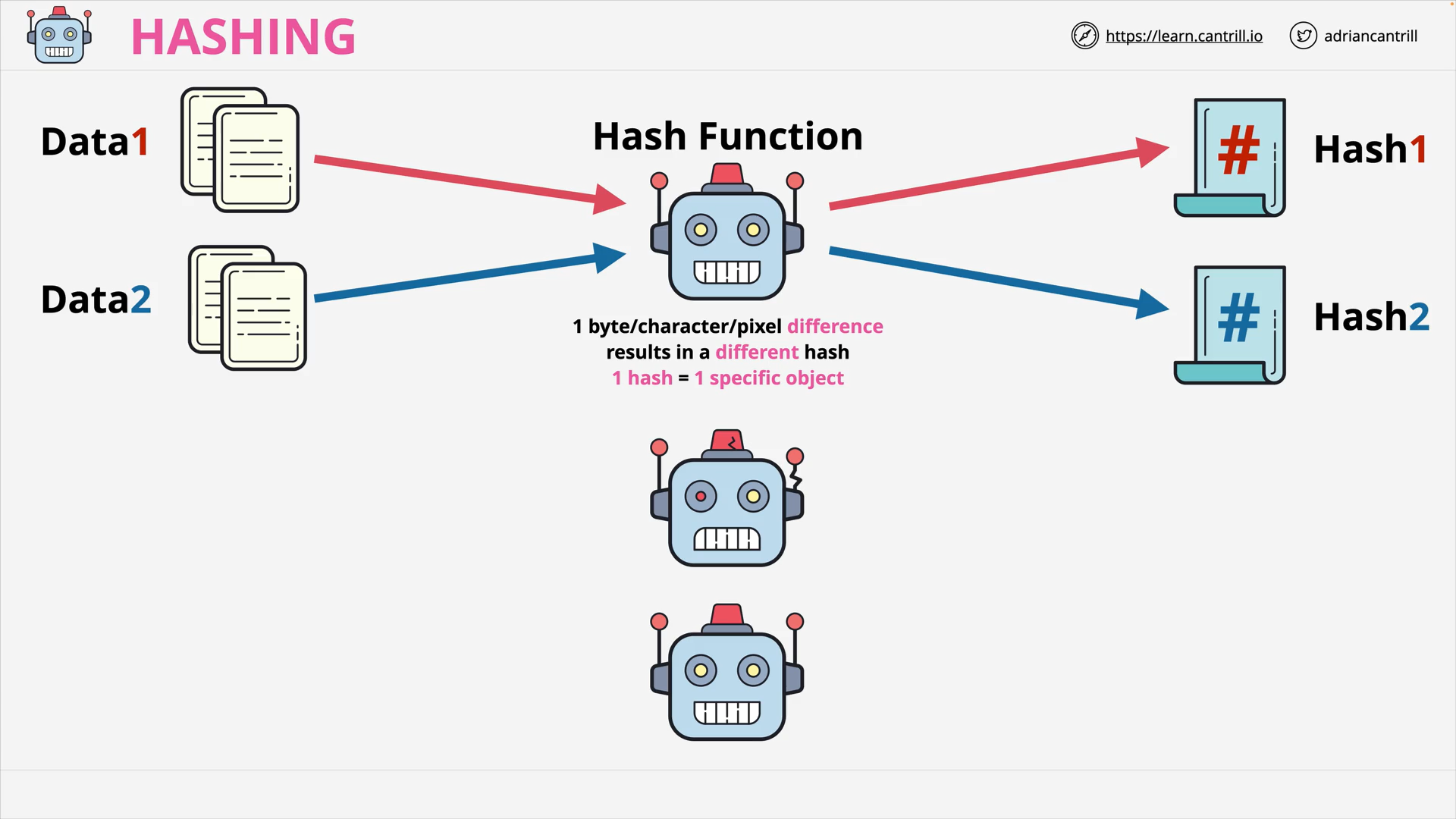 Hash Function
Hash Function
hash function
Mathematical algorithms that transform input data into a fixed-length string of characters, called a hash or message digest.
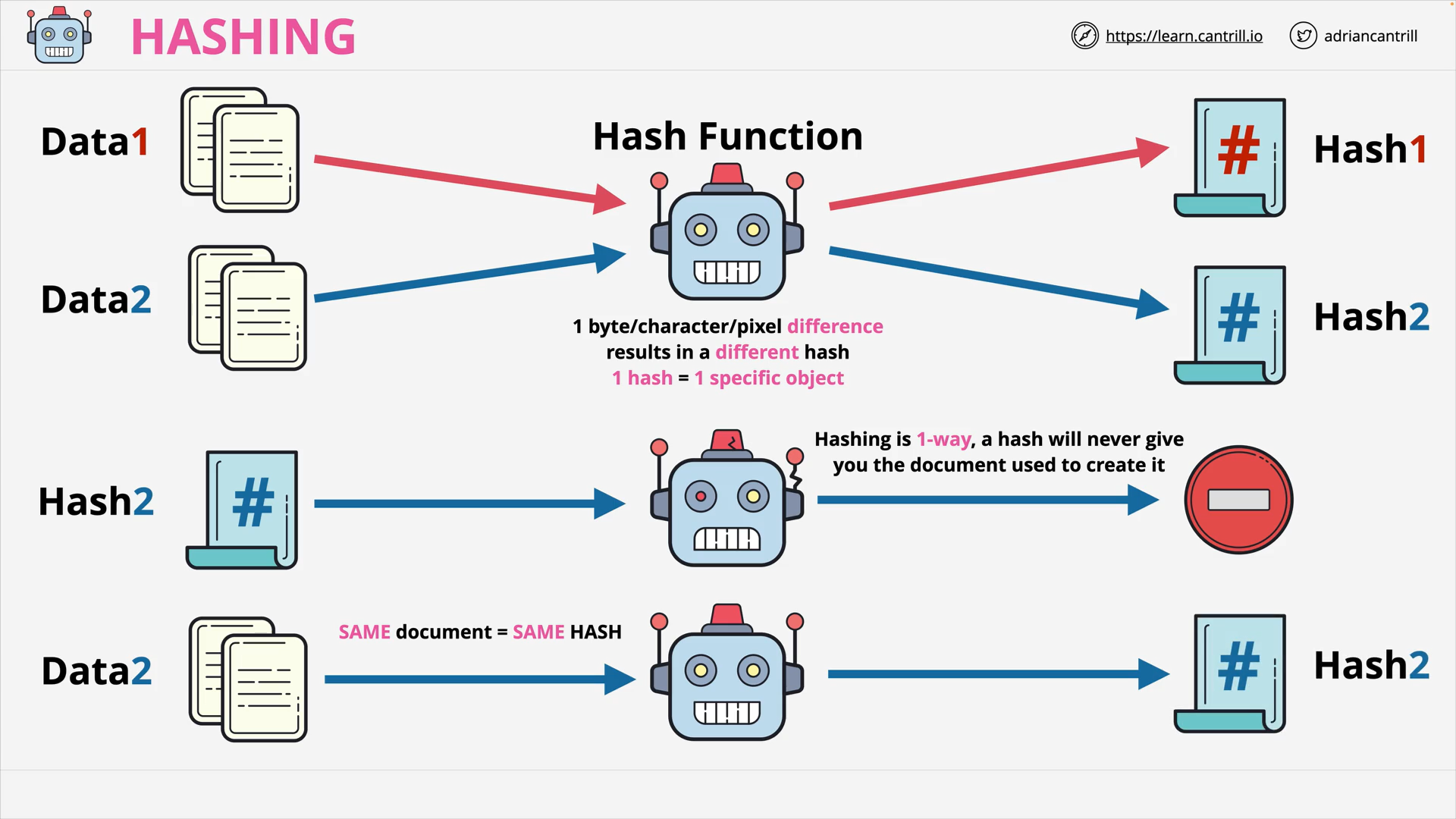 Hashing is 1 way.
Hashing is 1 way.
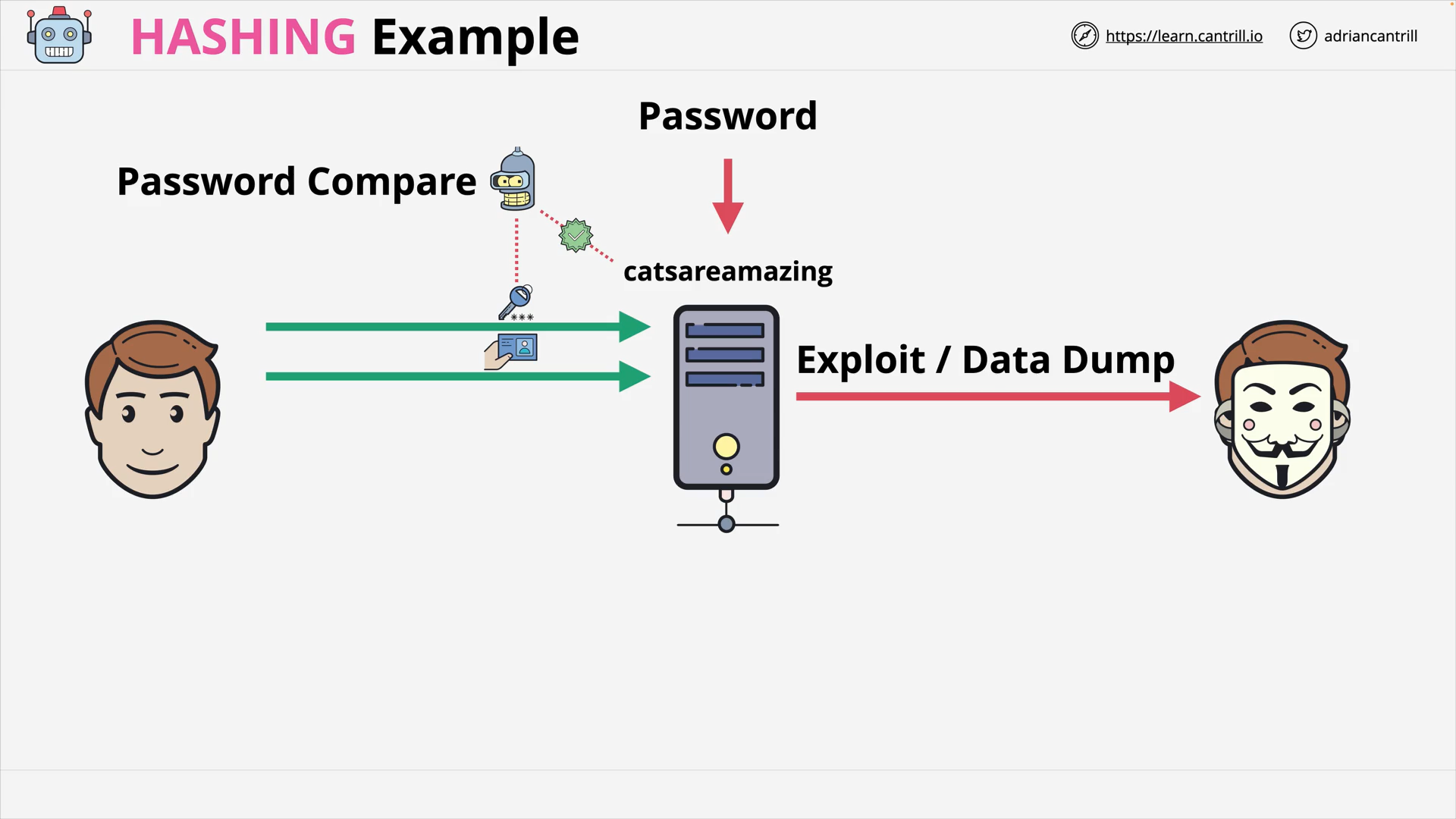 Hashing Example - Raw Password
Hashing Example - Raw Password
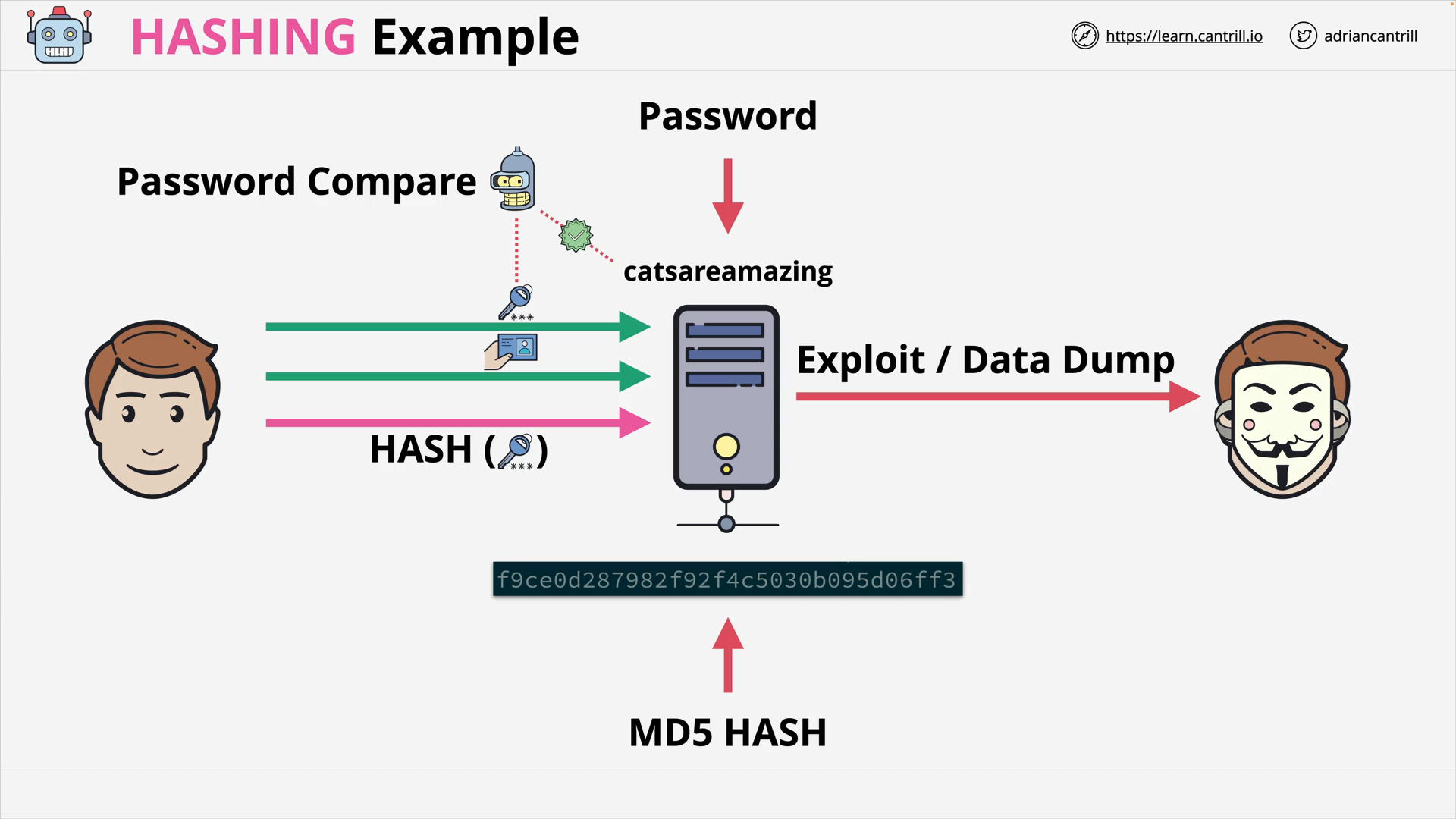 Hashing Example - Hashed Password
Hashing Example - Hashed Password
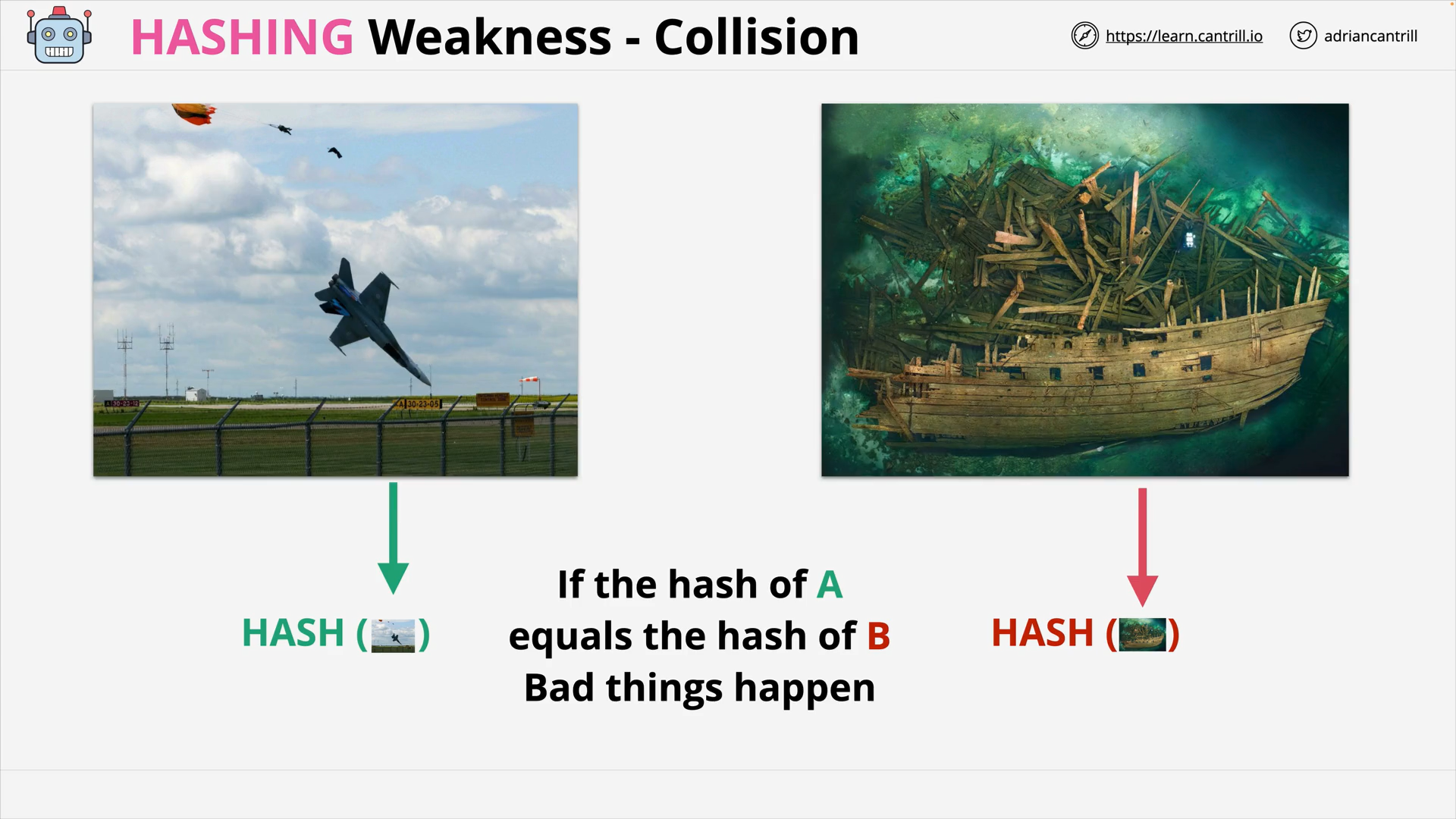 Hashing Collision
Hashing Collision
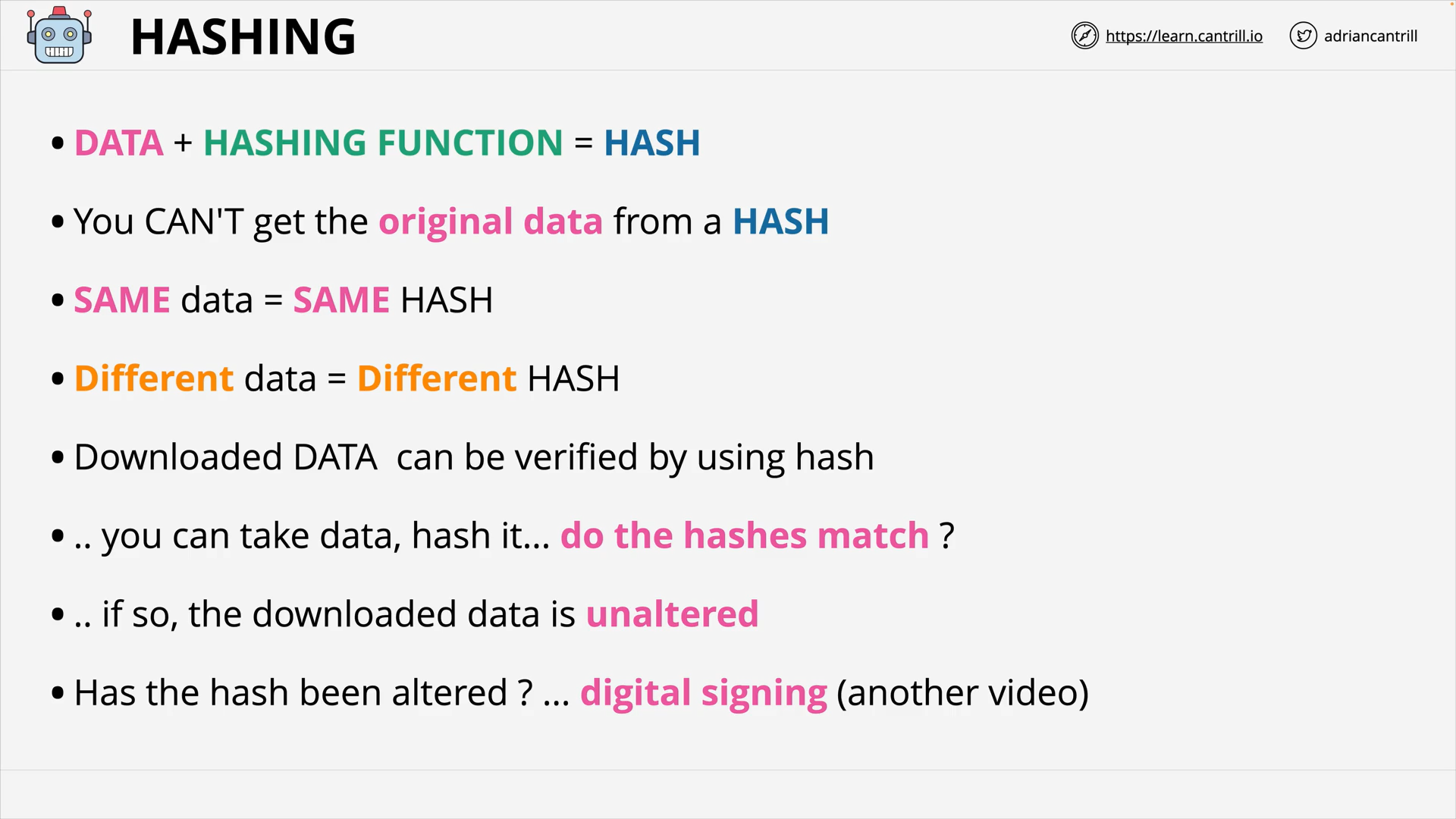 Hashing Summary
Hashing Summary
Digital Signatures (9:26)
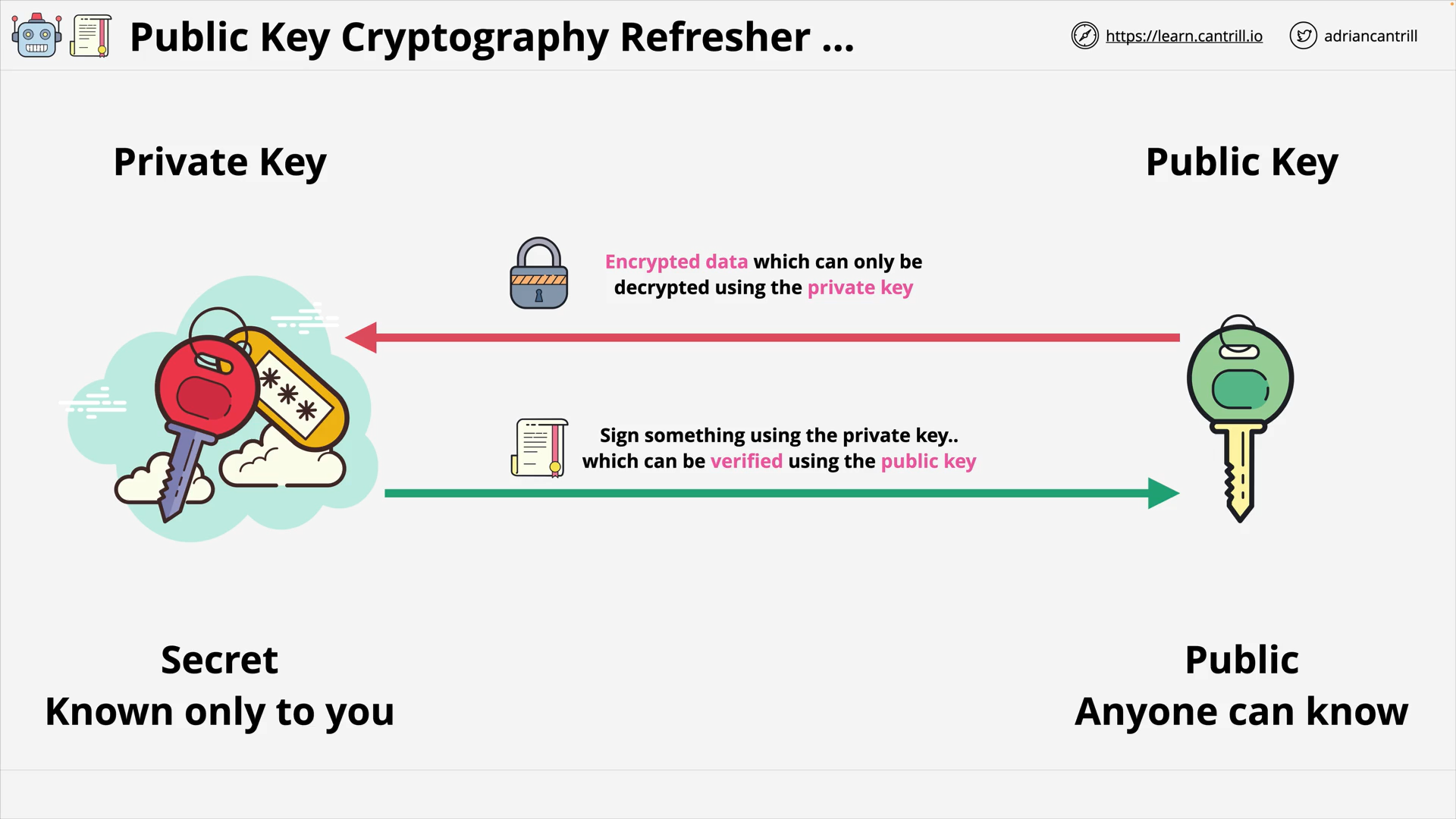 Public Key Cryptography
Public Key Cryptography
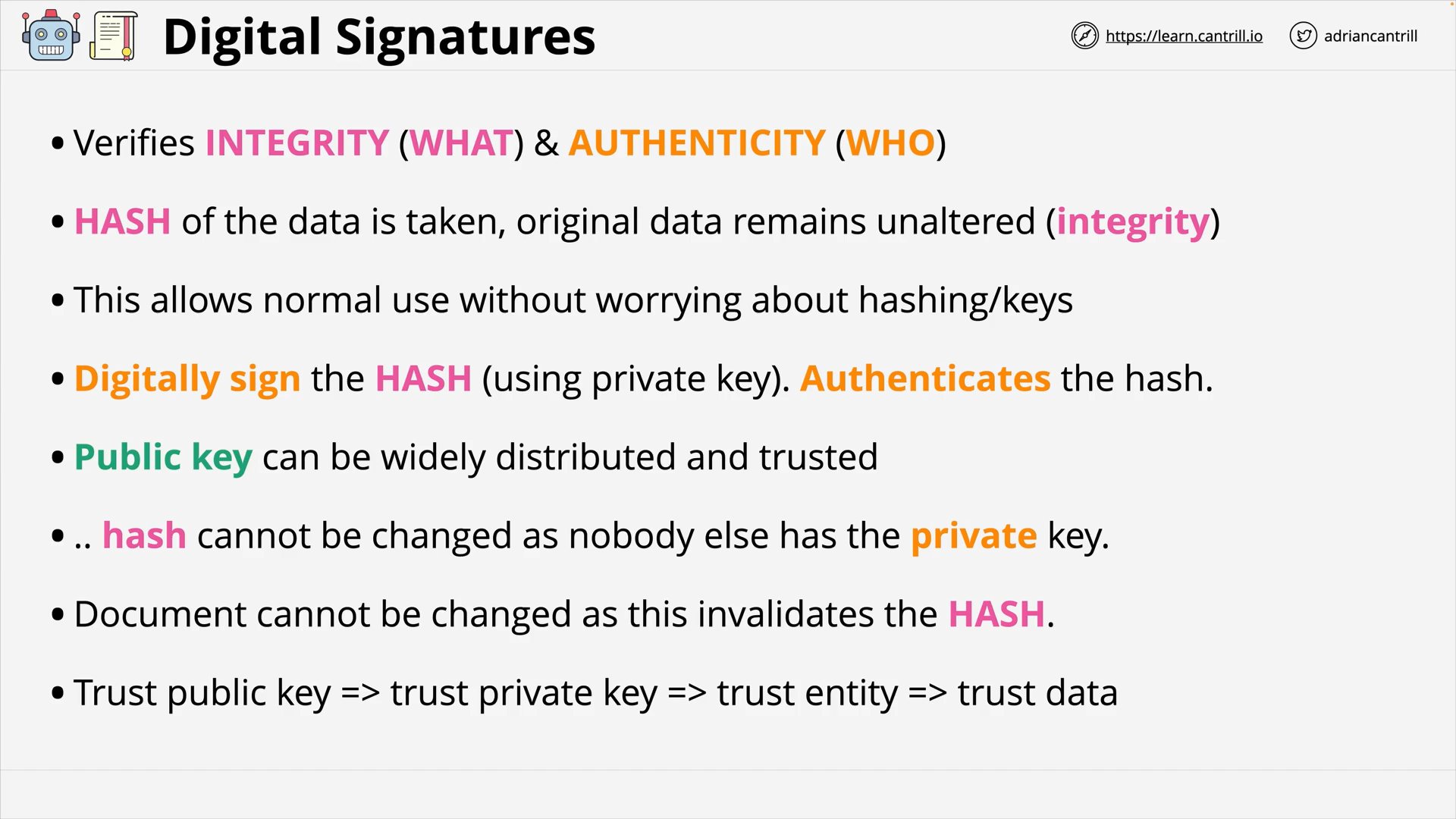 Digital Signatures verifies:
Digital Signatures verifies:
- Integrity (WHAT is sent) 👈 by compare the hash of data
- Authenticity (WHO sent it) 👈 by using the public key to very the signature
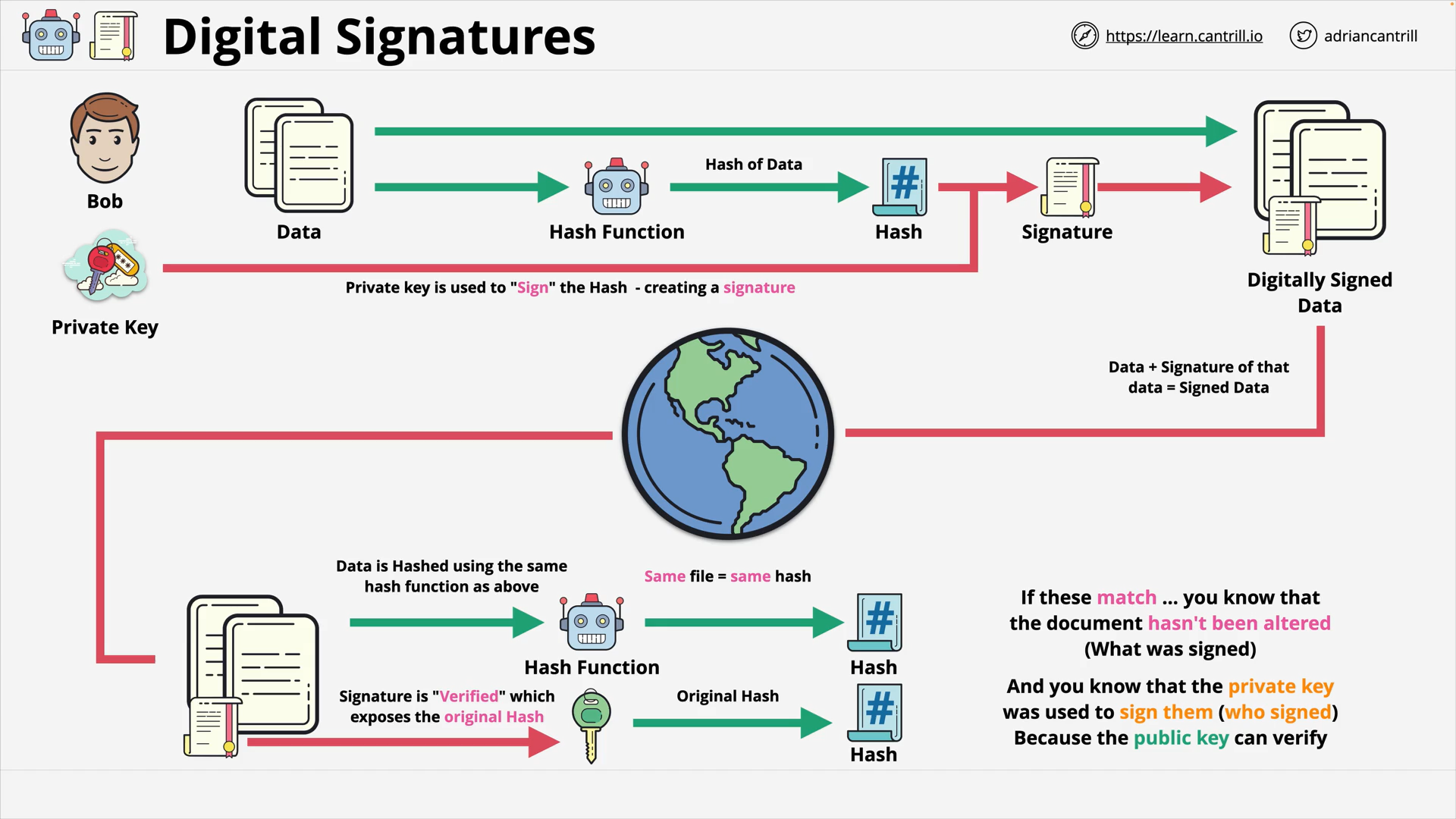
DNS & DNSSEC
DNS #1 - What does DNS do (2:56)
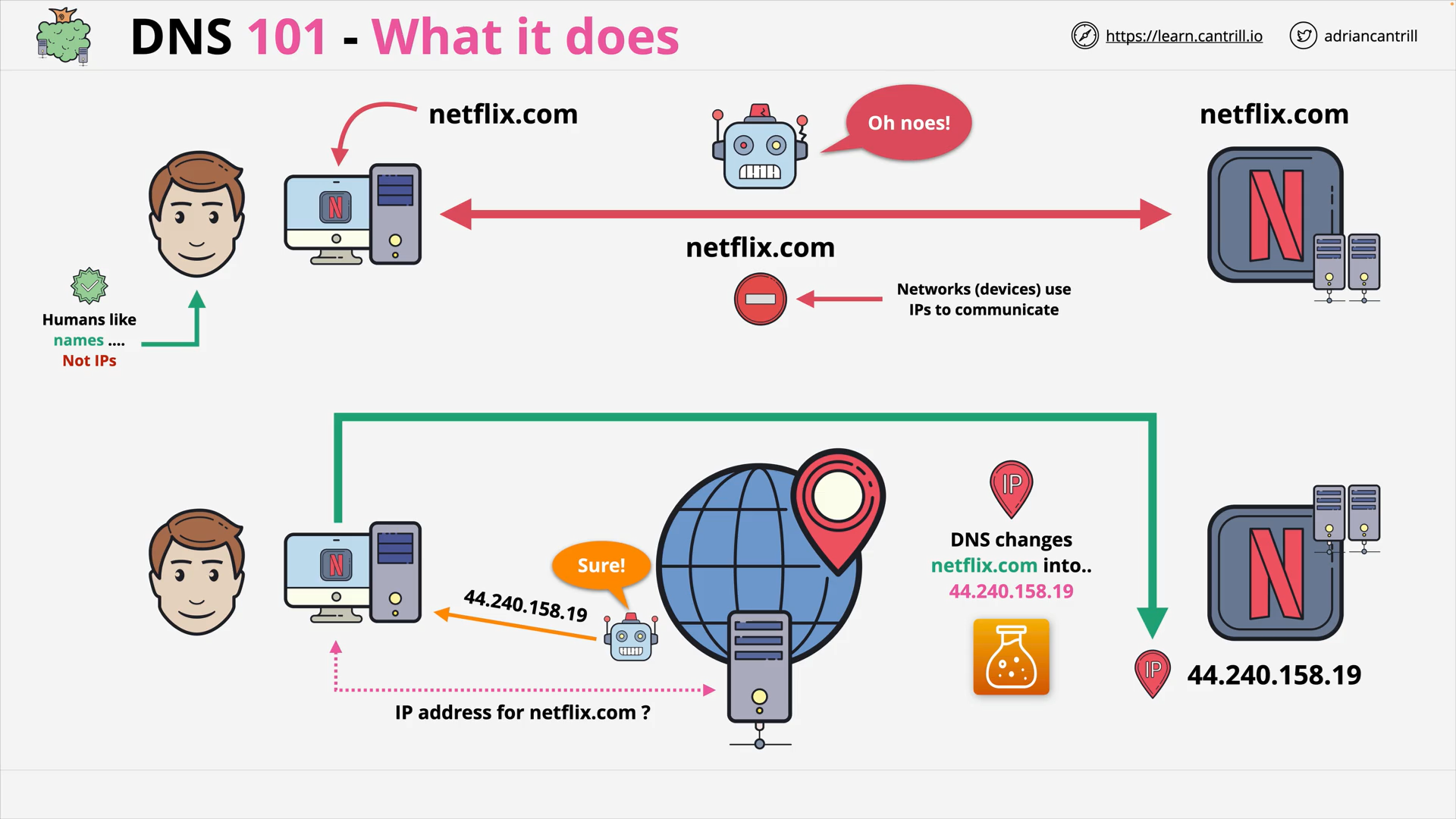 DNS translates human readable domain names (e.g. www.amazon.com) to machine readable IP addresses (e.g. 192.0.2.44)
DNS translates human readable domain names (e.g. www.amazon.com) to machine readable IP addresses (e.g. 192.0.2.44)
DNS #2 - Why does DNS need a complex architecture (13:19)
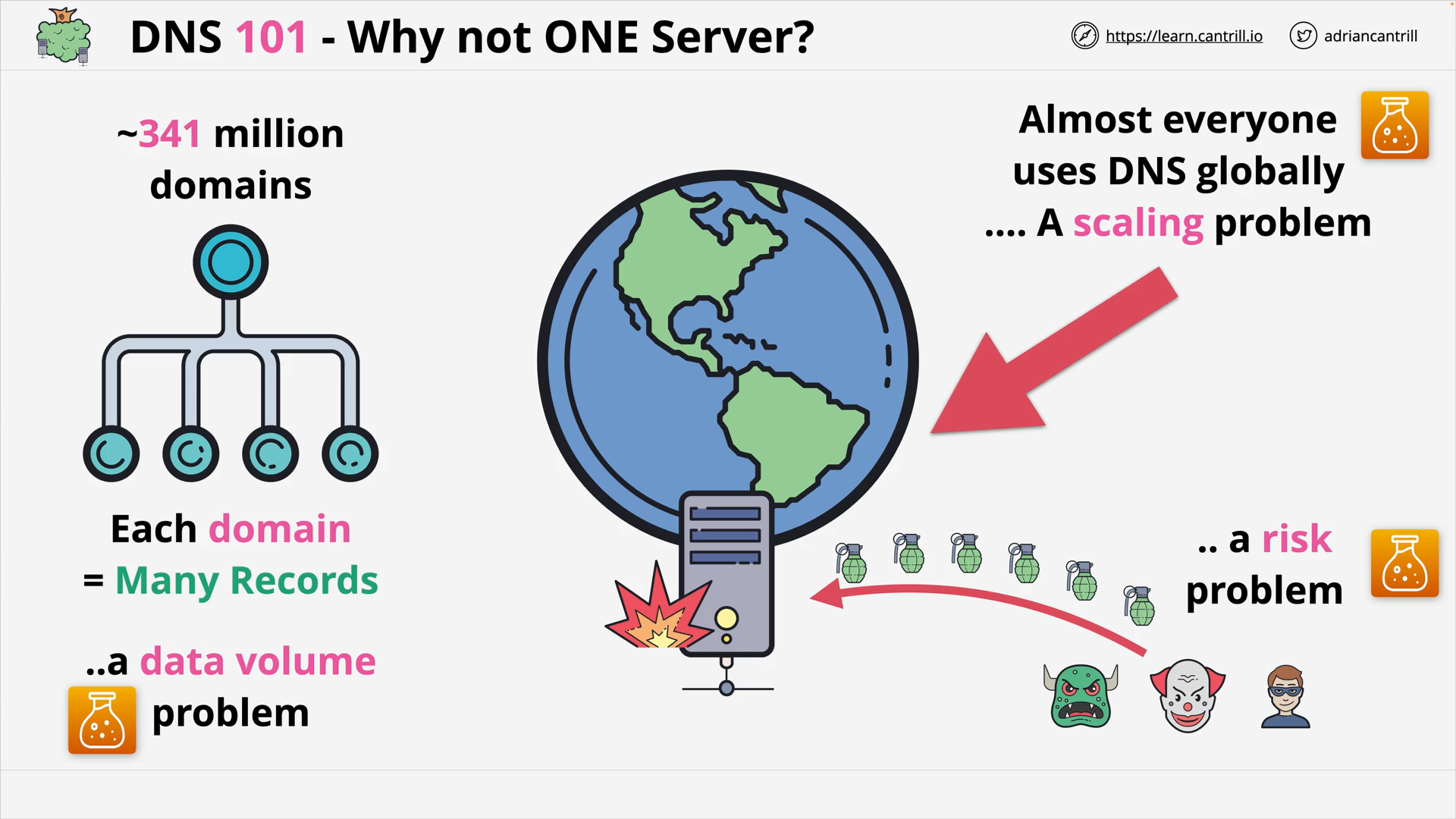 Why not ONE server?
Why not ONE server?
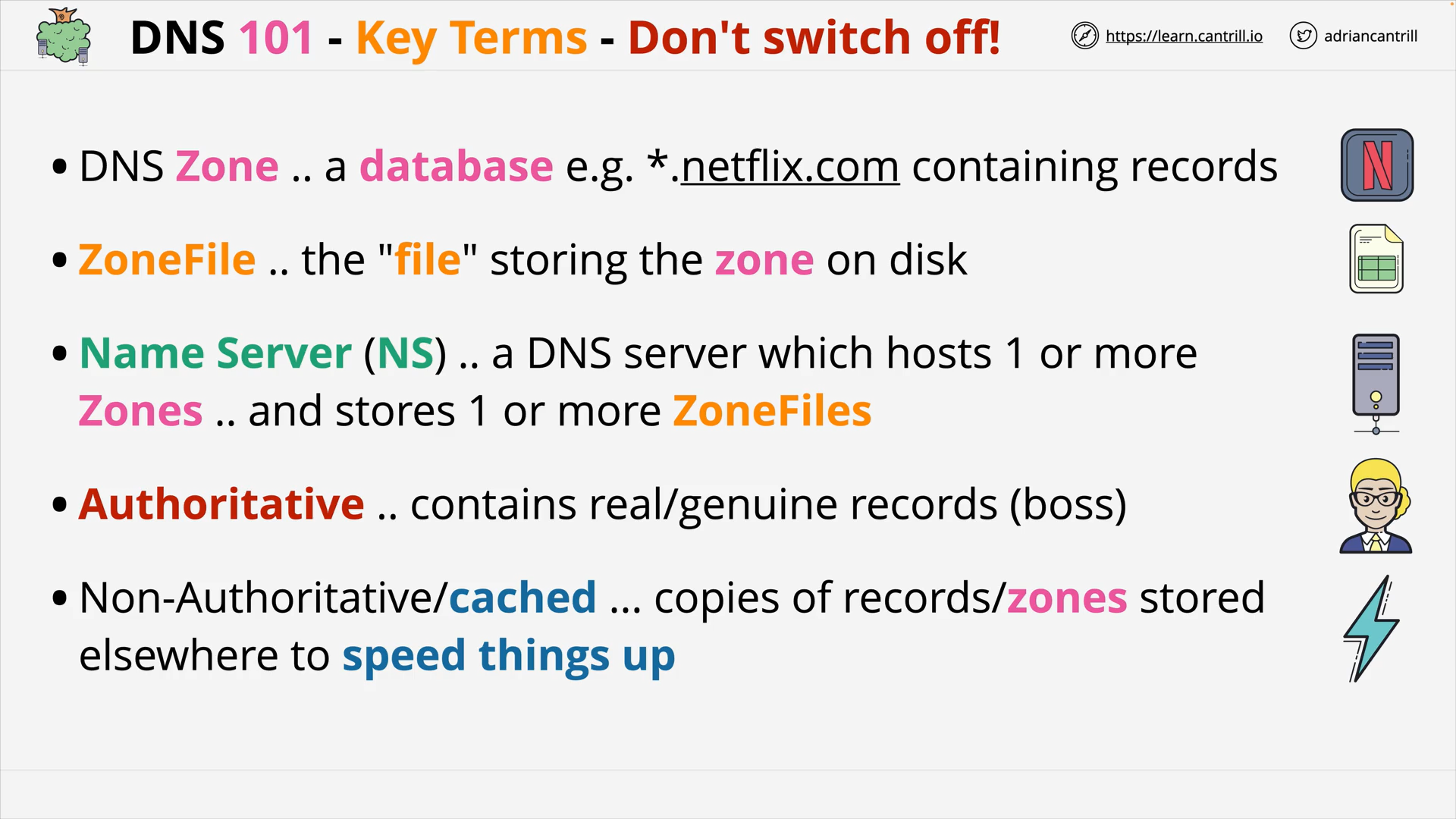 DNS Terms
DNS Terms
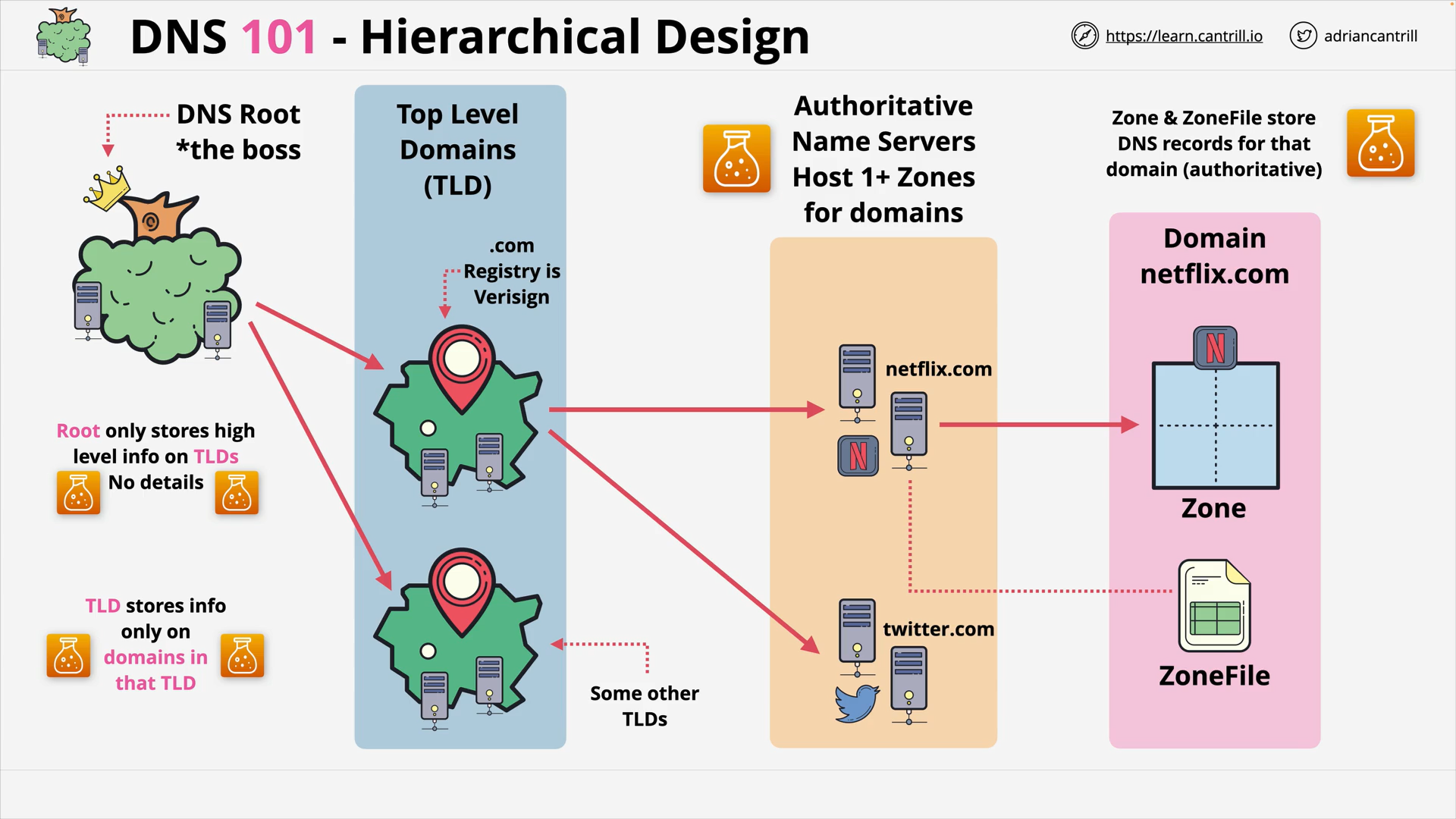 DNS Hierarchical Design
DNS Hierarchical Design
DNS #3 - How DNS actually works … walking the tree (8:46)
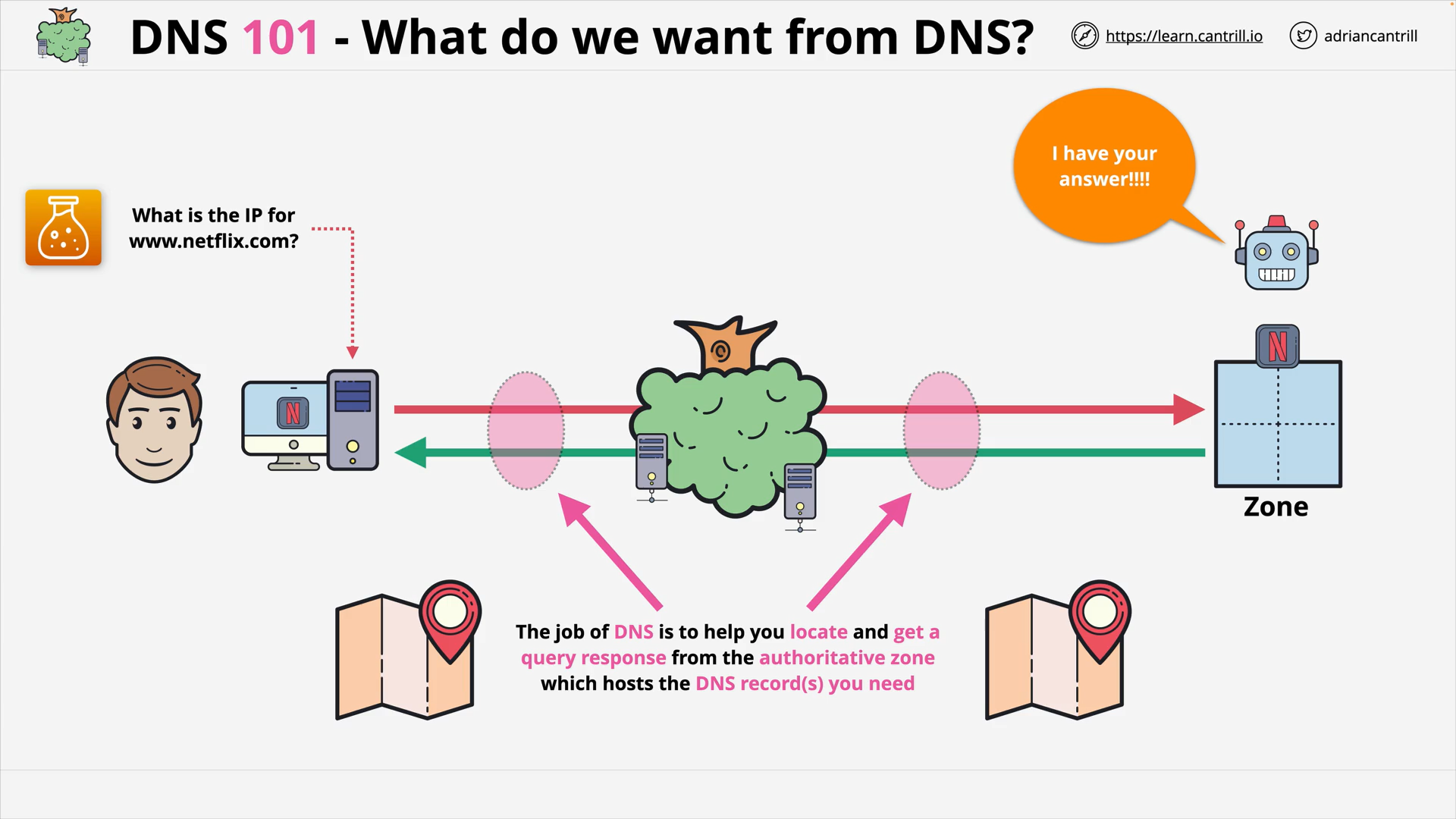 The job of DNS is help us get the DNS records we need.
The job of DNS is help us get the DNS records we need.
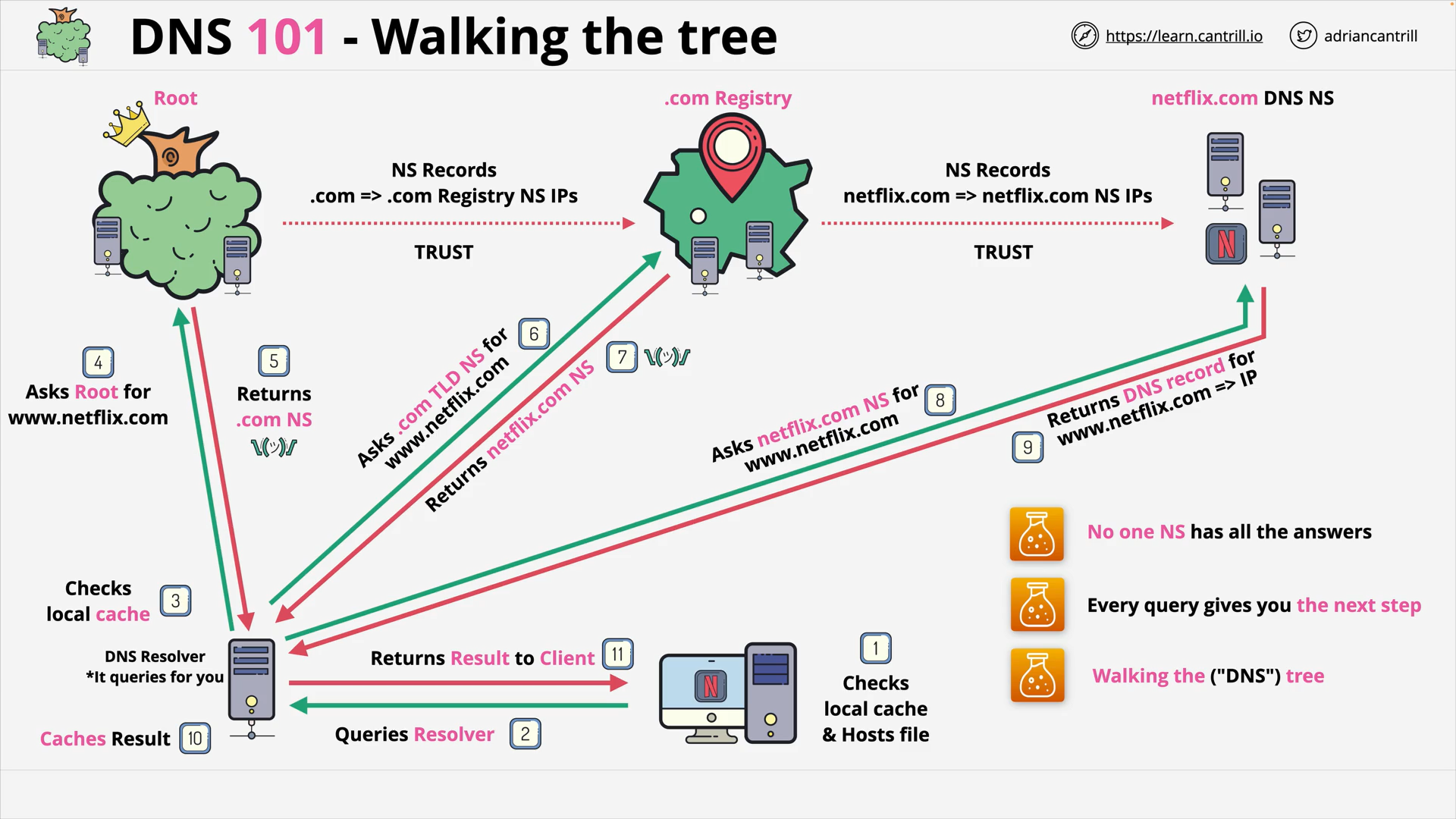 DNS - Walking the tree
DNS - Walking the tree
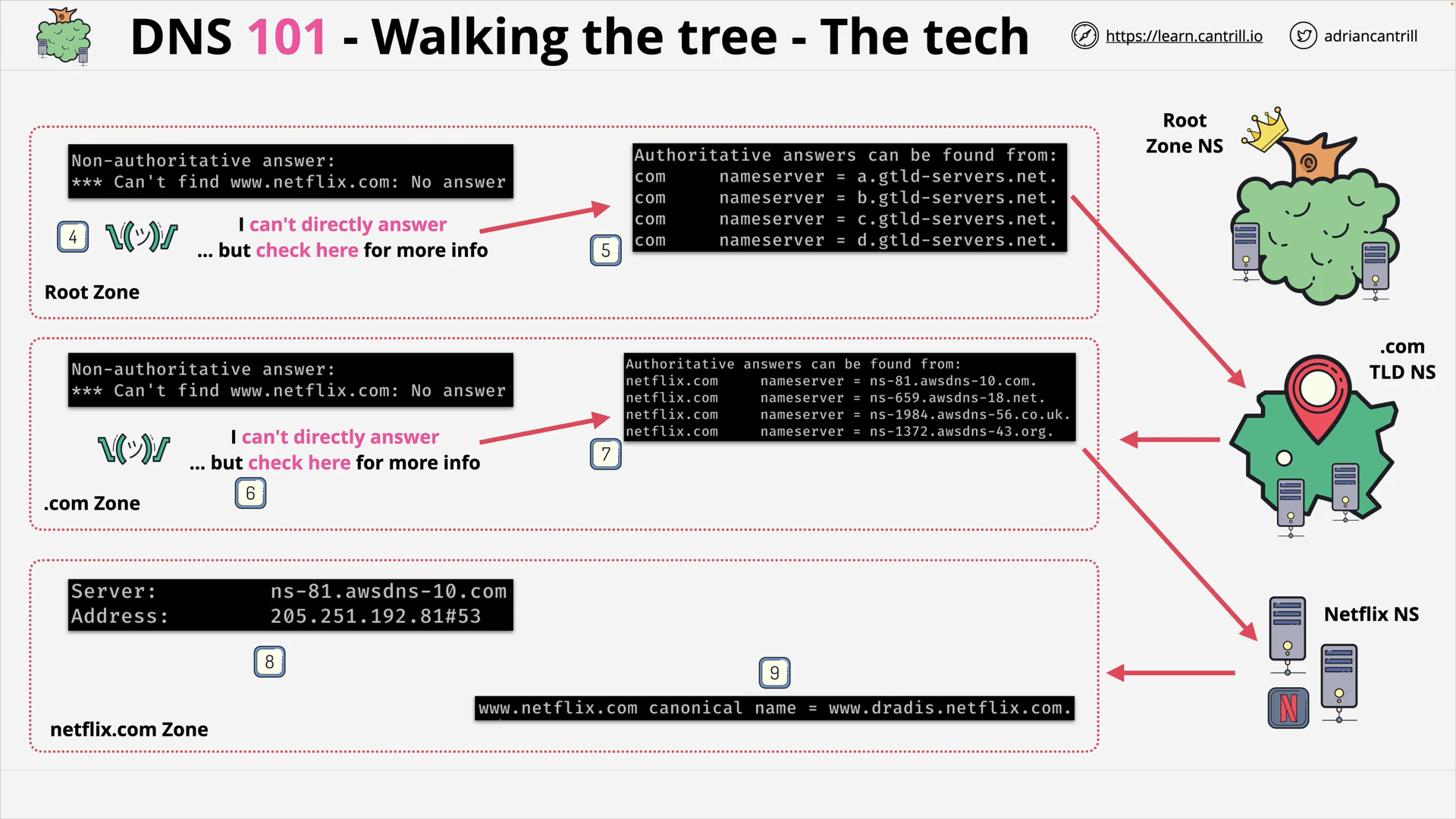 DNS - Walking the tree - Behind the scene
DNS - Walking the tree - Behind the scene
DNS #4 - What happens when a domain is registered? (4:27)
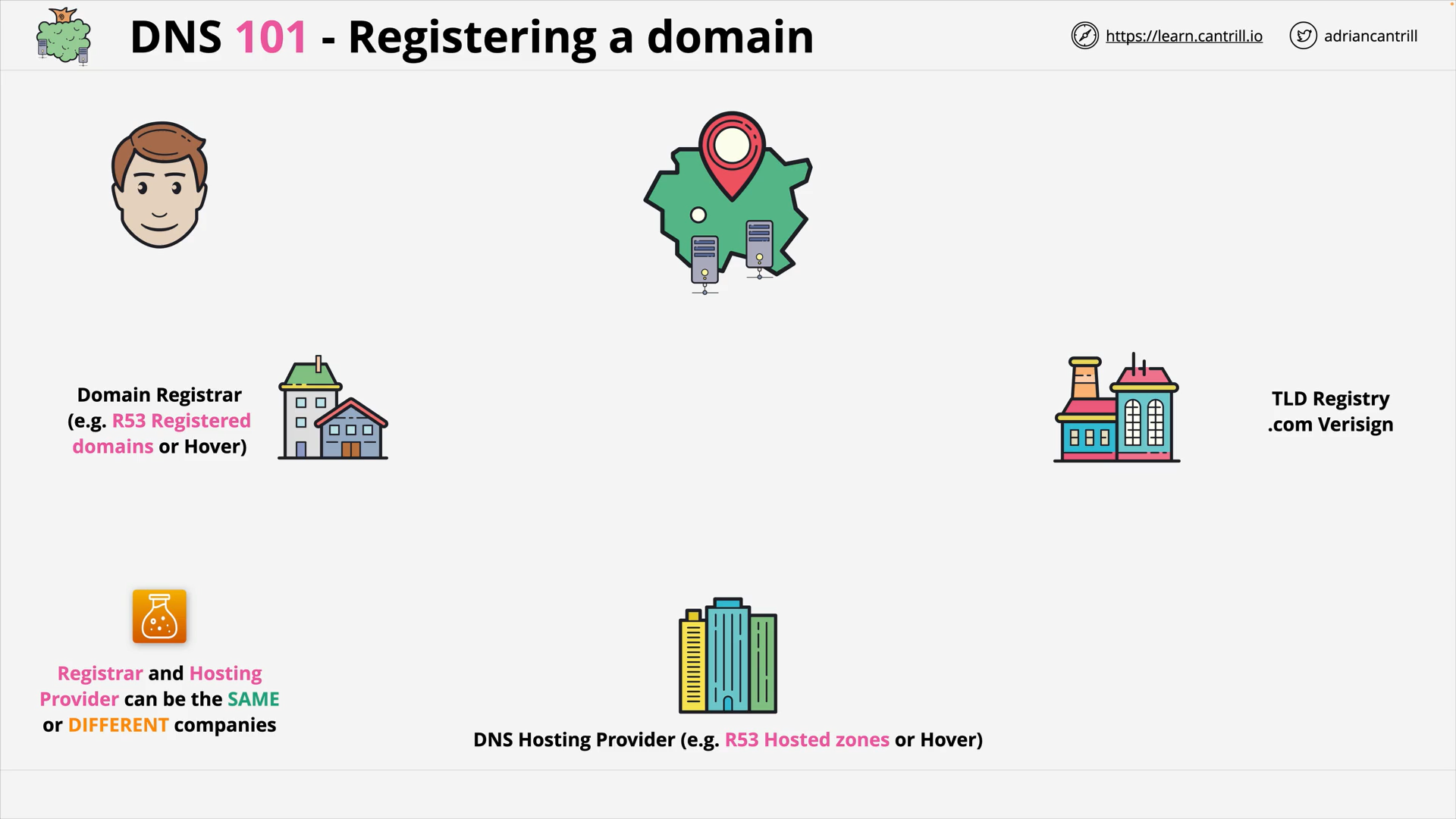 Domain Registrar - DNS Hosting Provider - TLD Registry
Domain Registrar - DNS Hosting Provider - TLD Registry
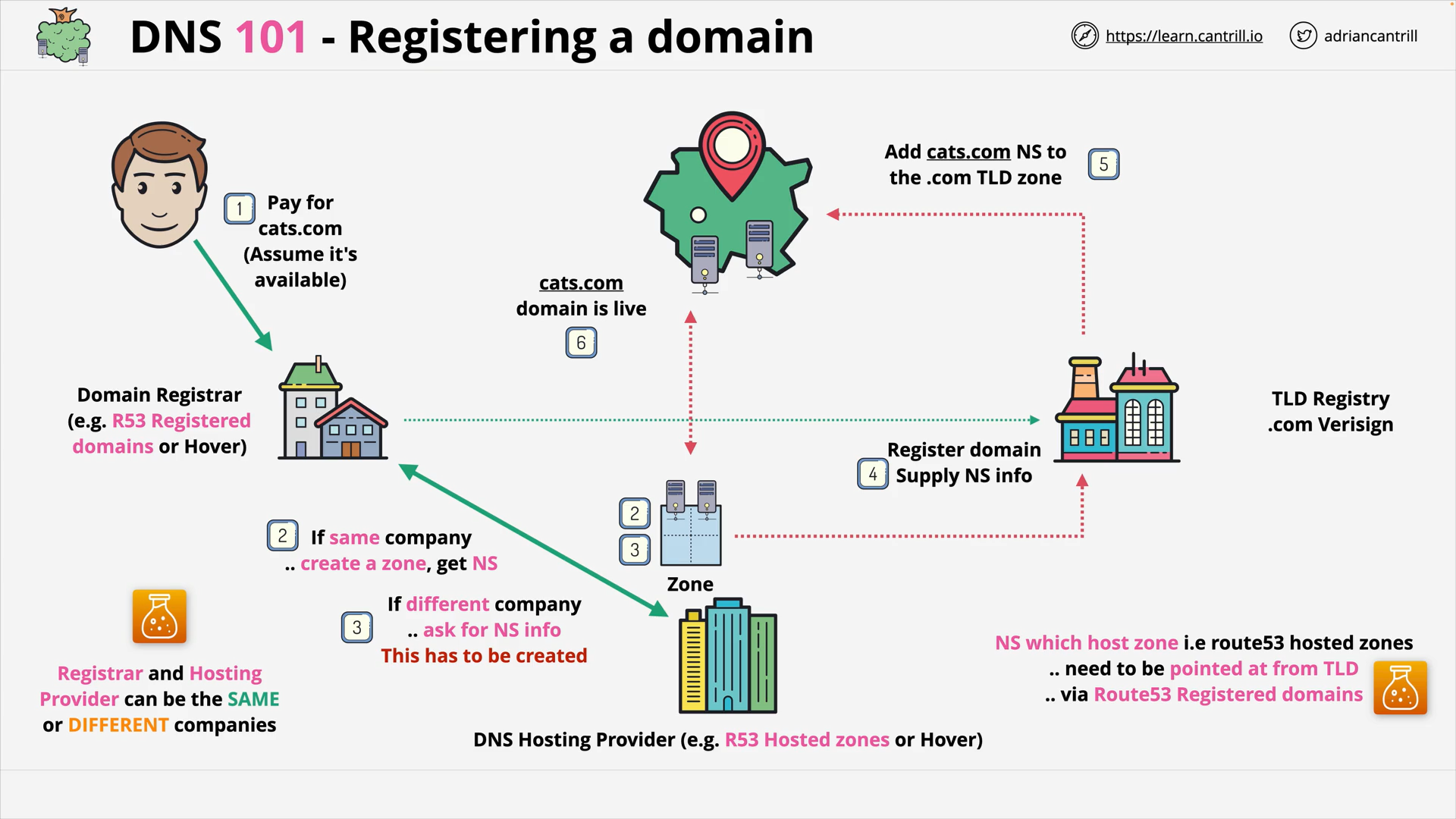 Registering a domain
Registering a domain
DNSSEC #1 - Why do we need DNSSEC (11:08)
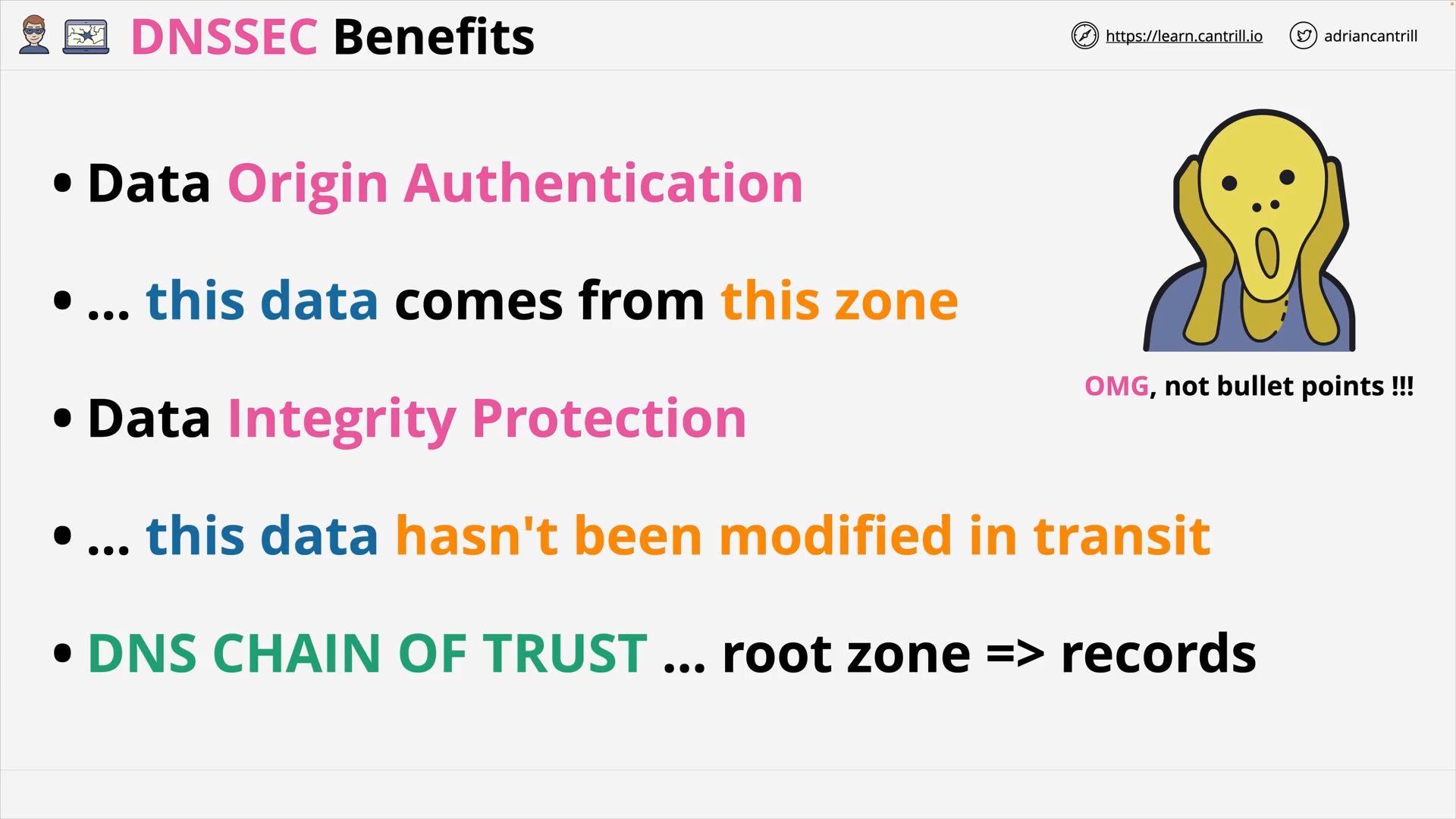 DNSSEC Benefits ~ Digital Signature for DNS Records
DNSSEC Benefits ~ Digital Signature for DNS Records
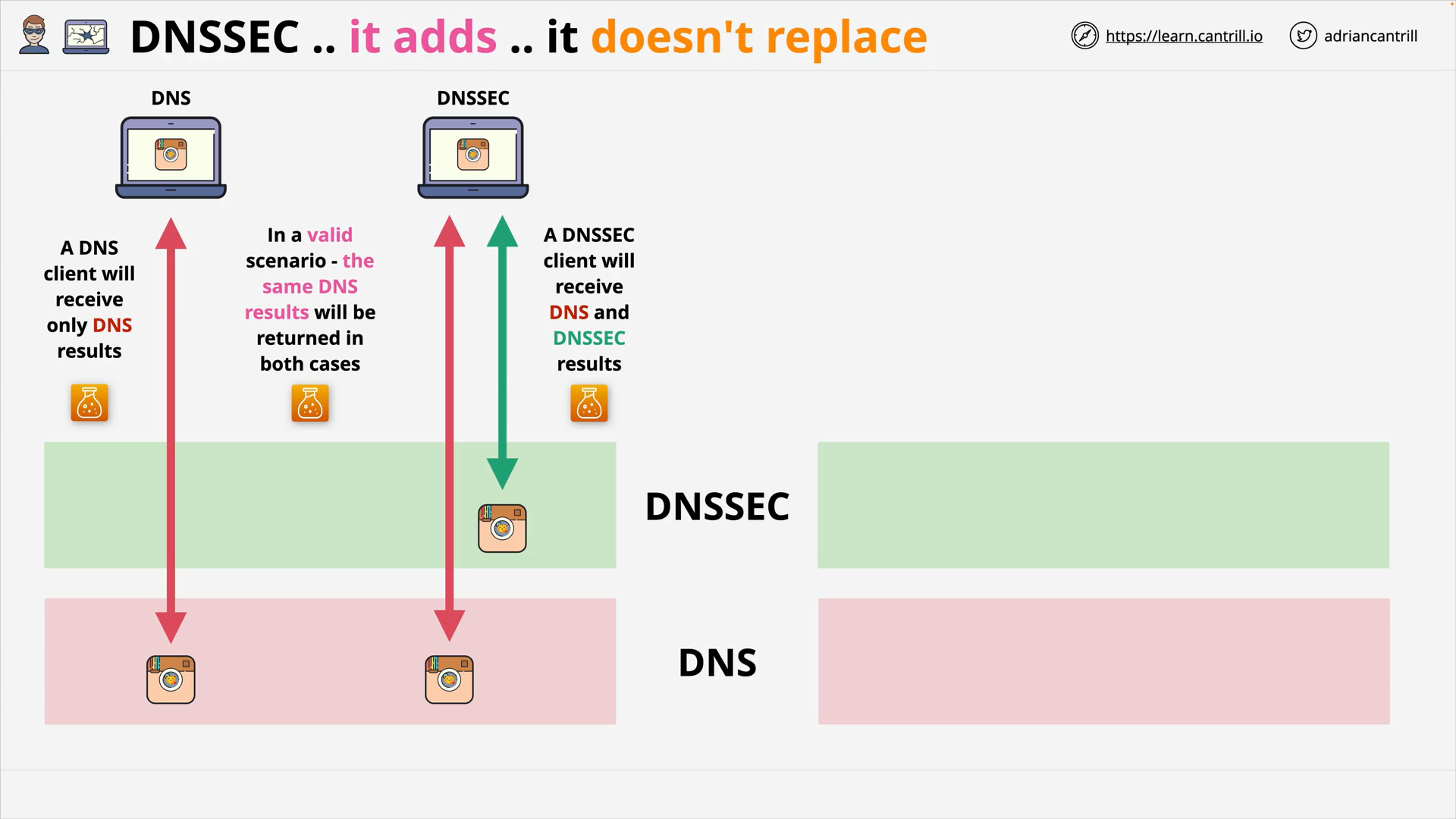 DNSSEC is an extension to DNS. It adds, and doesn’t replace DNS.
DNSSEC is an extension to DNS. It adds, and doesn’t replace DNS.
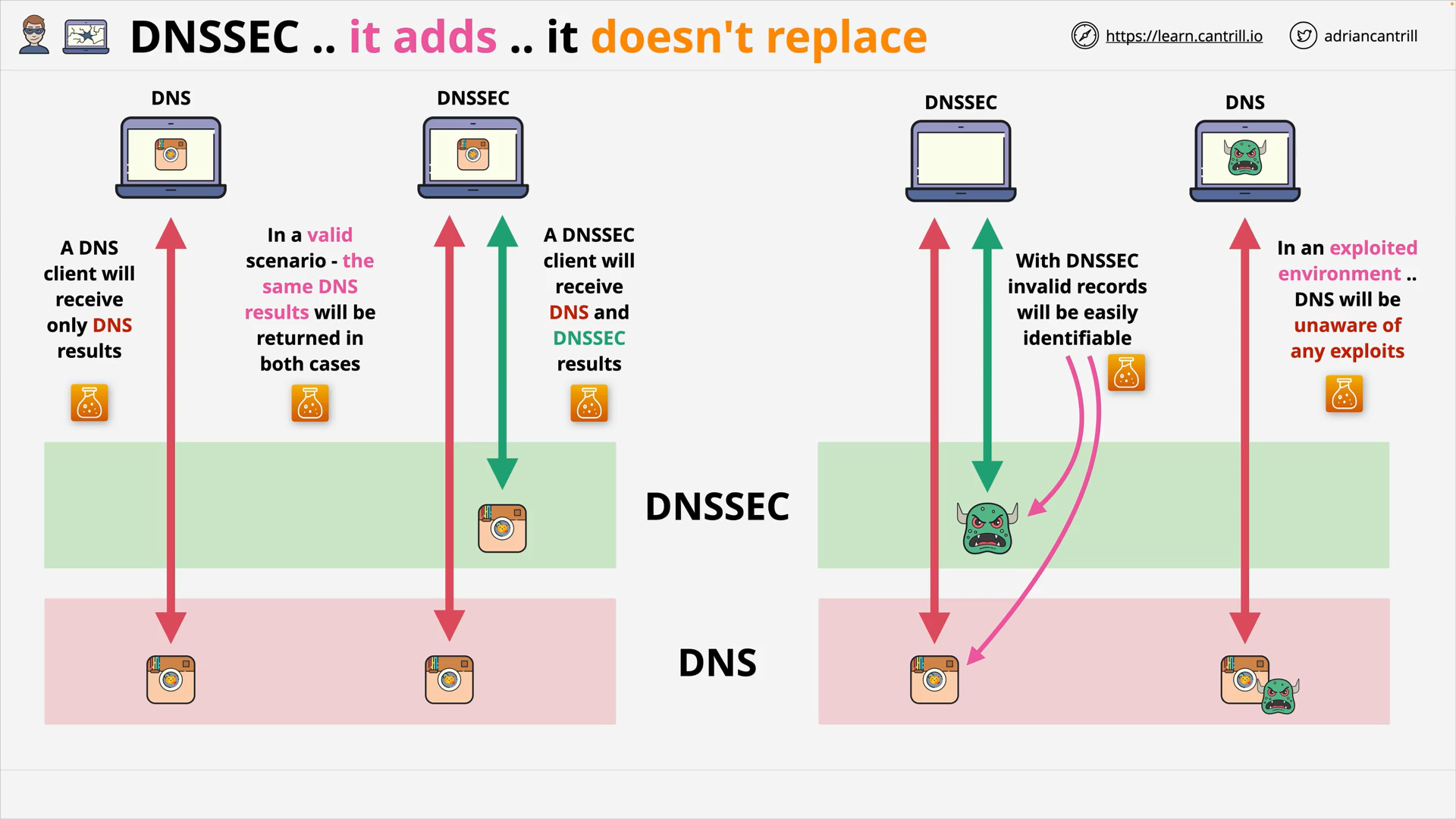 DNSSEC Benefit Example
DNSSEC Benefit Example
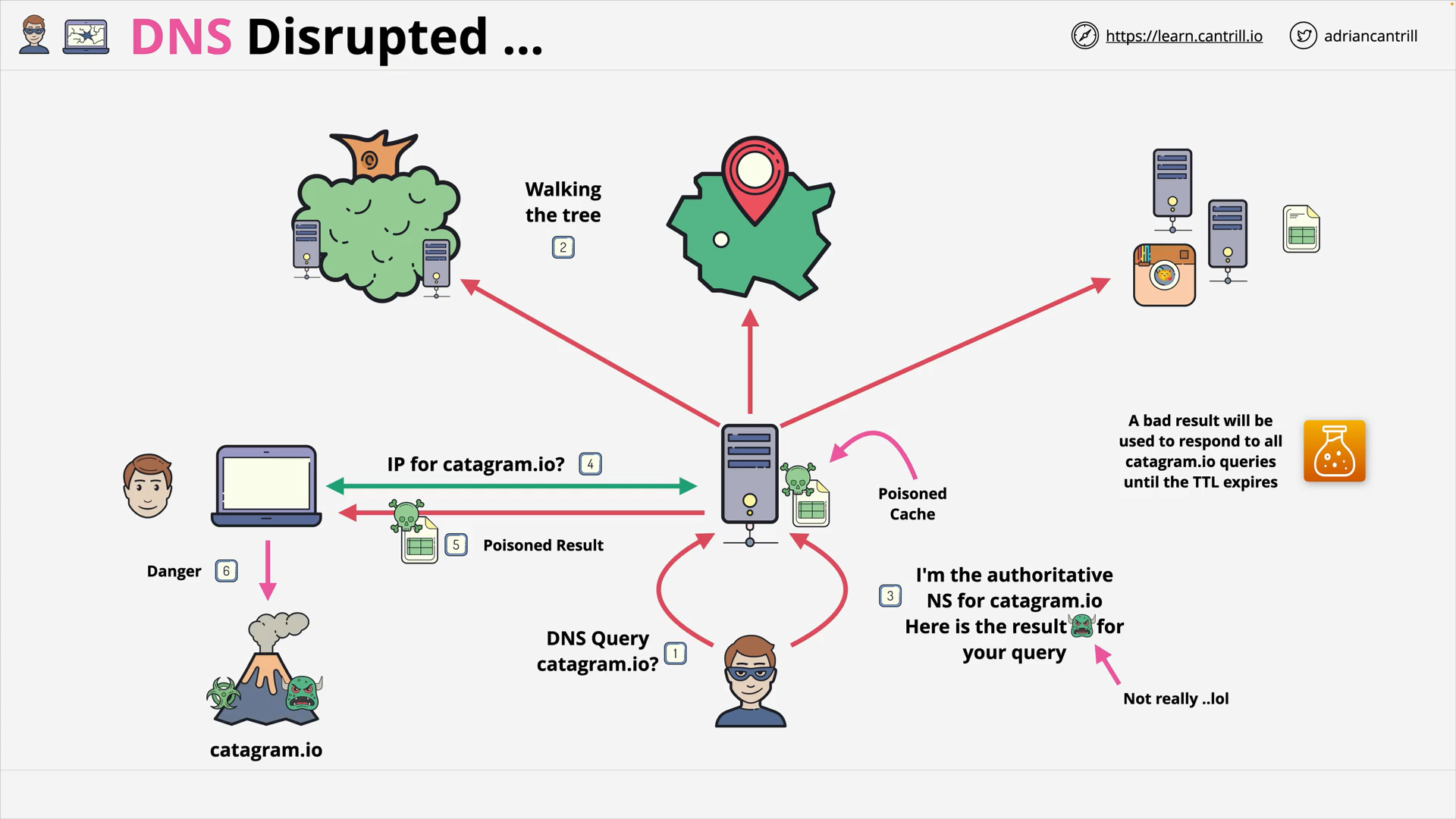 DNS Disrupted
DNS Disrupted
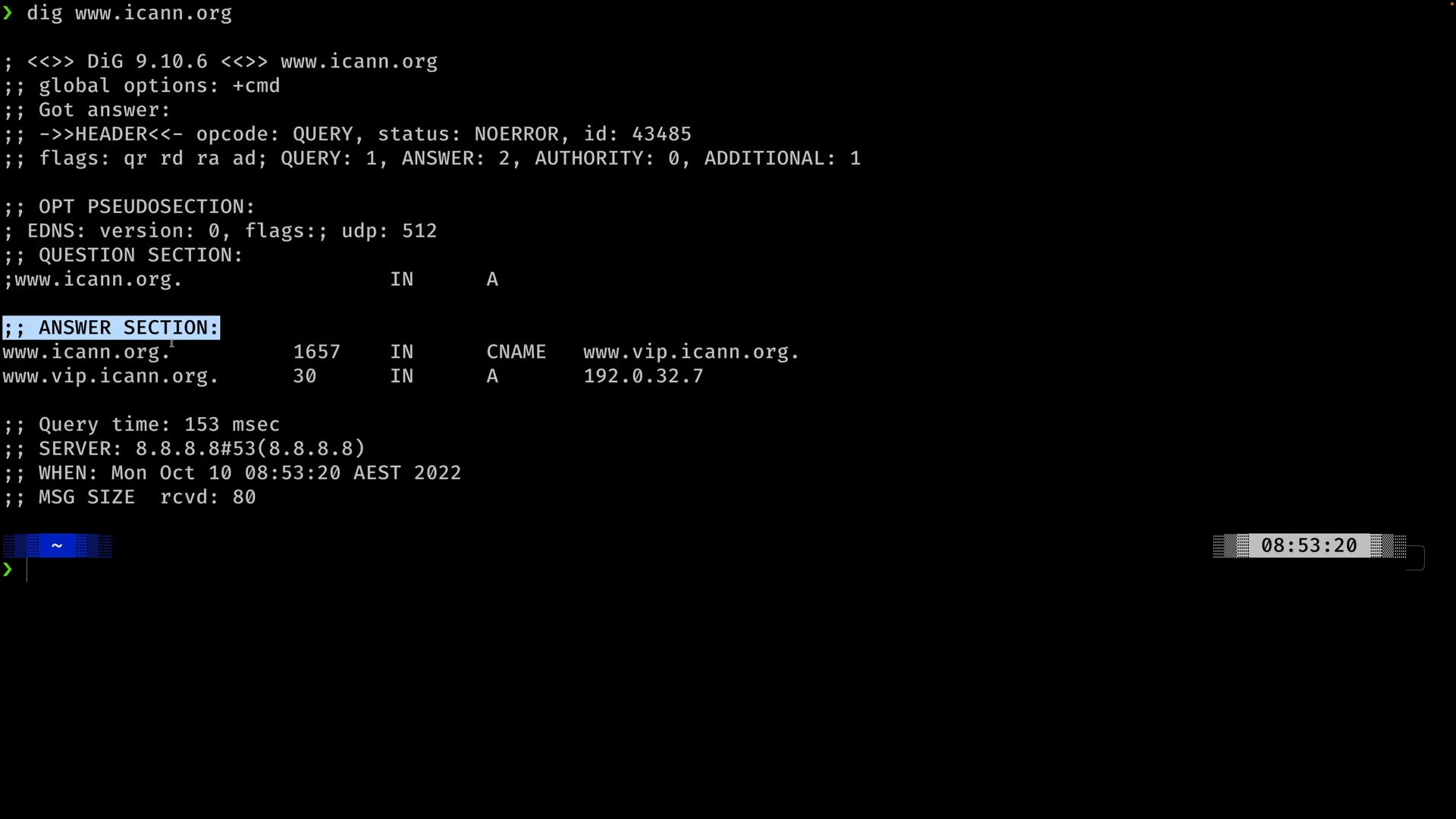 Example: Use dig to query A record for example.com
Example: Use dig to query A record for example.com
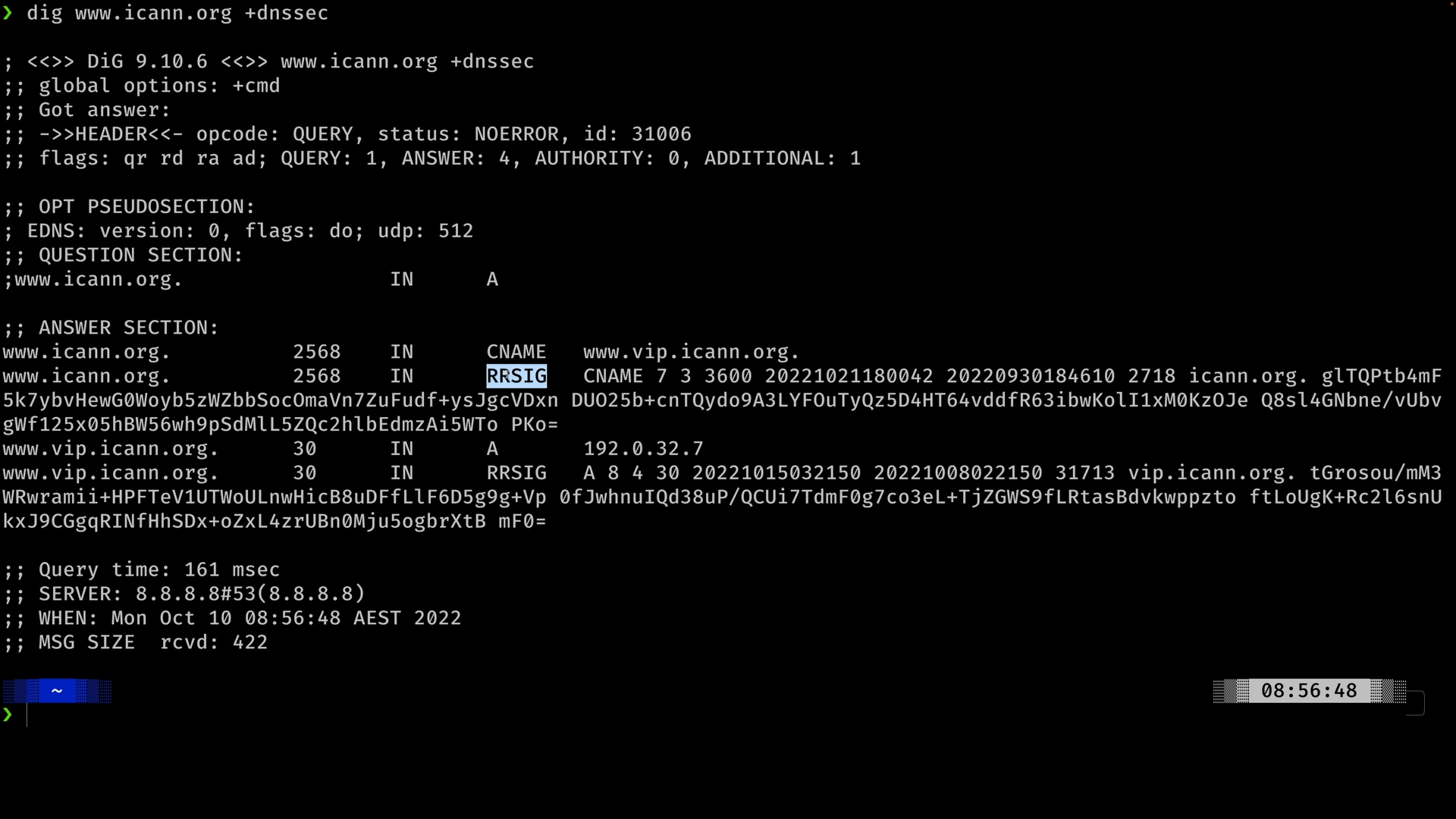 Example: Use dig to query A record and DNSSEC for example.com
Example: Use dig to query A record and DNSSEC for example.com
note
To verify DNSSEC of a domain, you can use:
- dig: if there’s the flag
ad - delv
- Web Tools: DNS Viz, DNSSEC Debugger
See
DNSSEC #2 - How DNSSEC Works within a Zone (17:34)
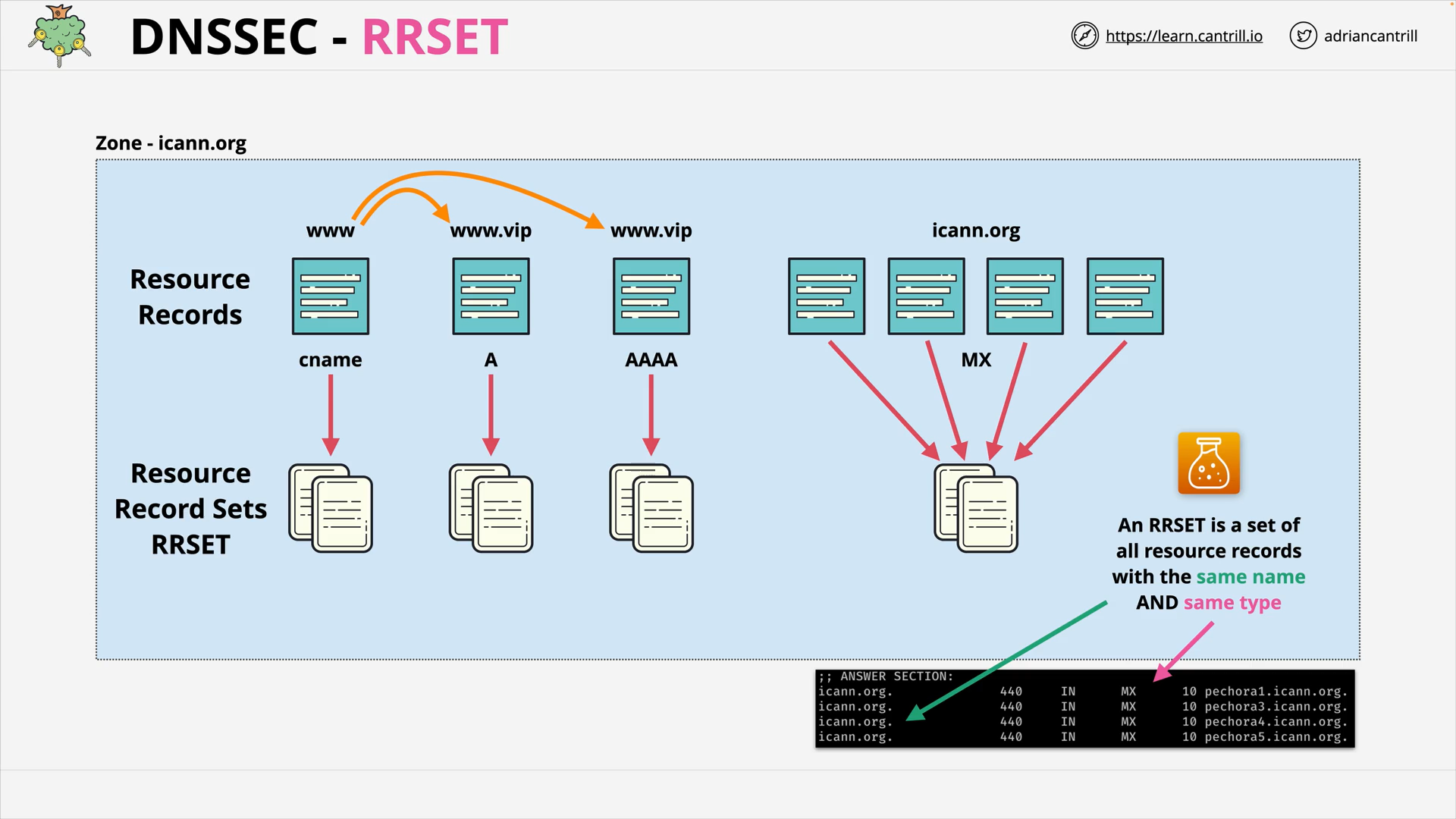 DNSSEC - RRSET
DNSSEC - RRSET
what is a rrset?
A group of all the records with the same type ad same name
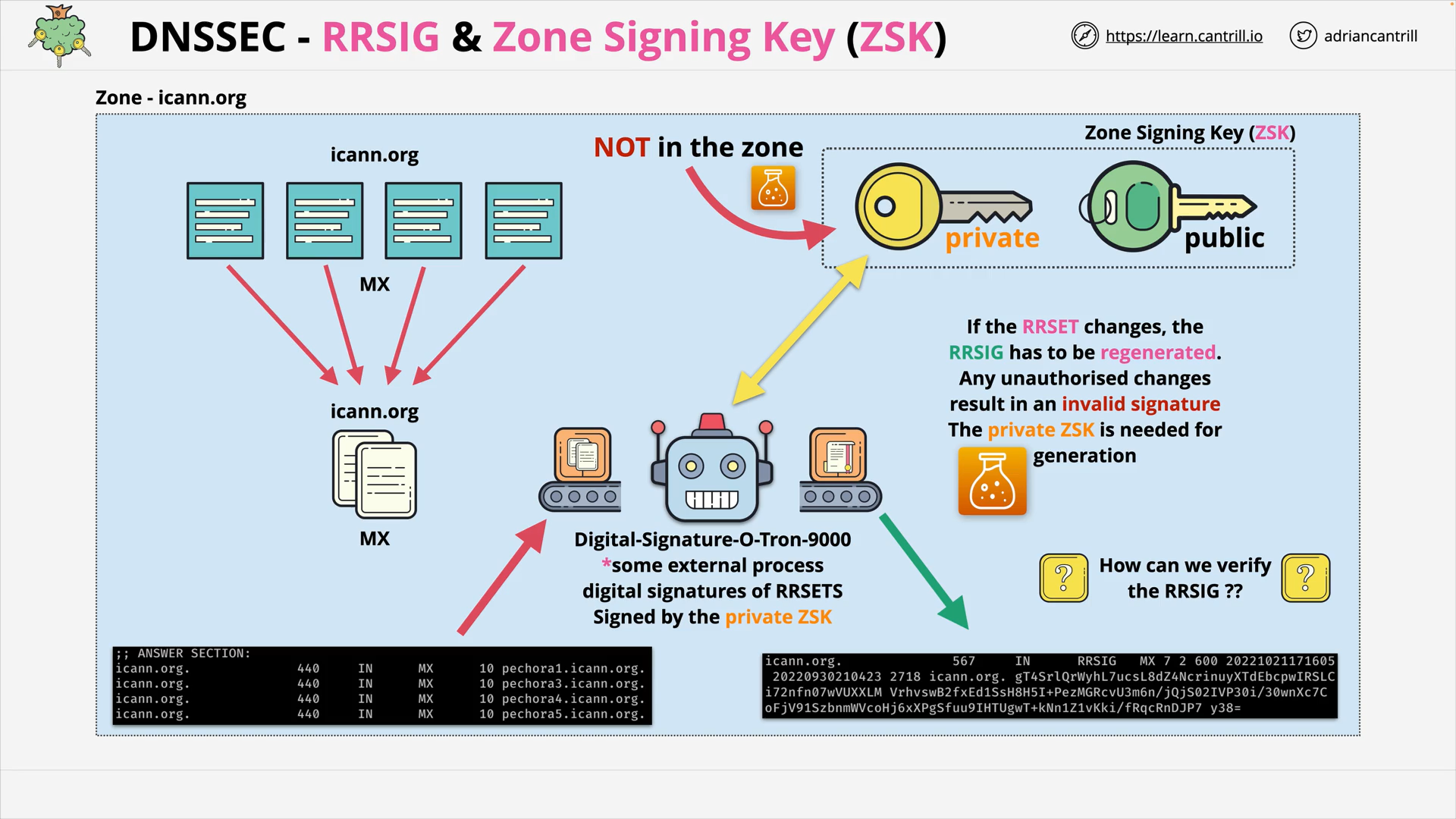 DNSSEC - RRSIG & Zone Signing Key (ZSK)
DNSSEC - RRSIG & Zone Signing Key (ZSK)
what is a rrsig?
A digital signature for a RRSET, signed by the private Zone Signing Key (ZSK).
what is zone signing key (zsk)?
Each zone has a ZSK, which is used to:
- sign 👈 the private ZSK
- verify 👈 the public ZSK
the RRSETs.
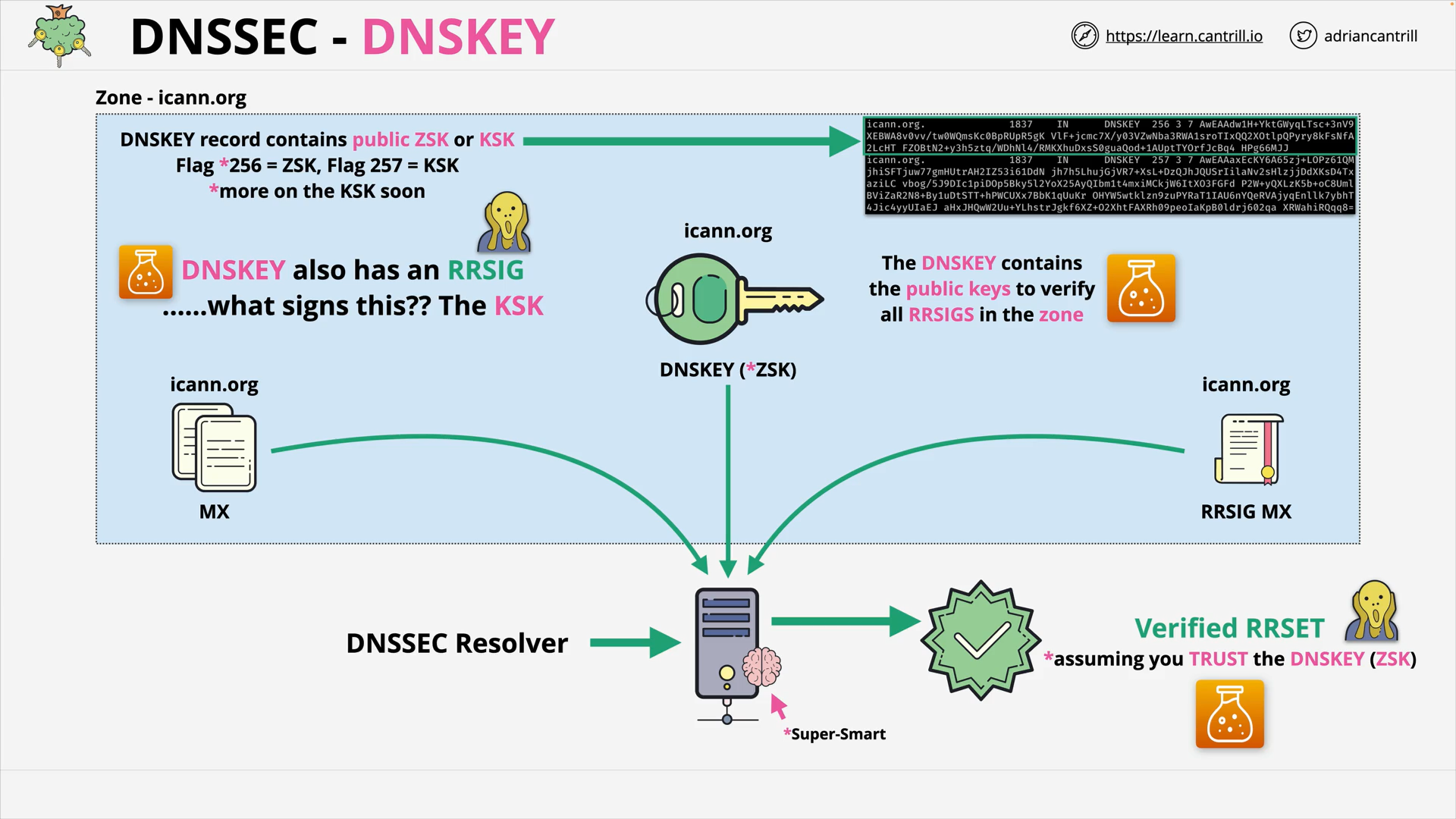 DNSSEC - DNSKEY contains public ZSK to verify all RRSIGs in the zone
DNSSEC - DNSKEY contains public ZSK to verify all RRSIGs in the zone
why the dnskey also has an rrsig?
Because someone can fake the DNSKEY too. 🤯
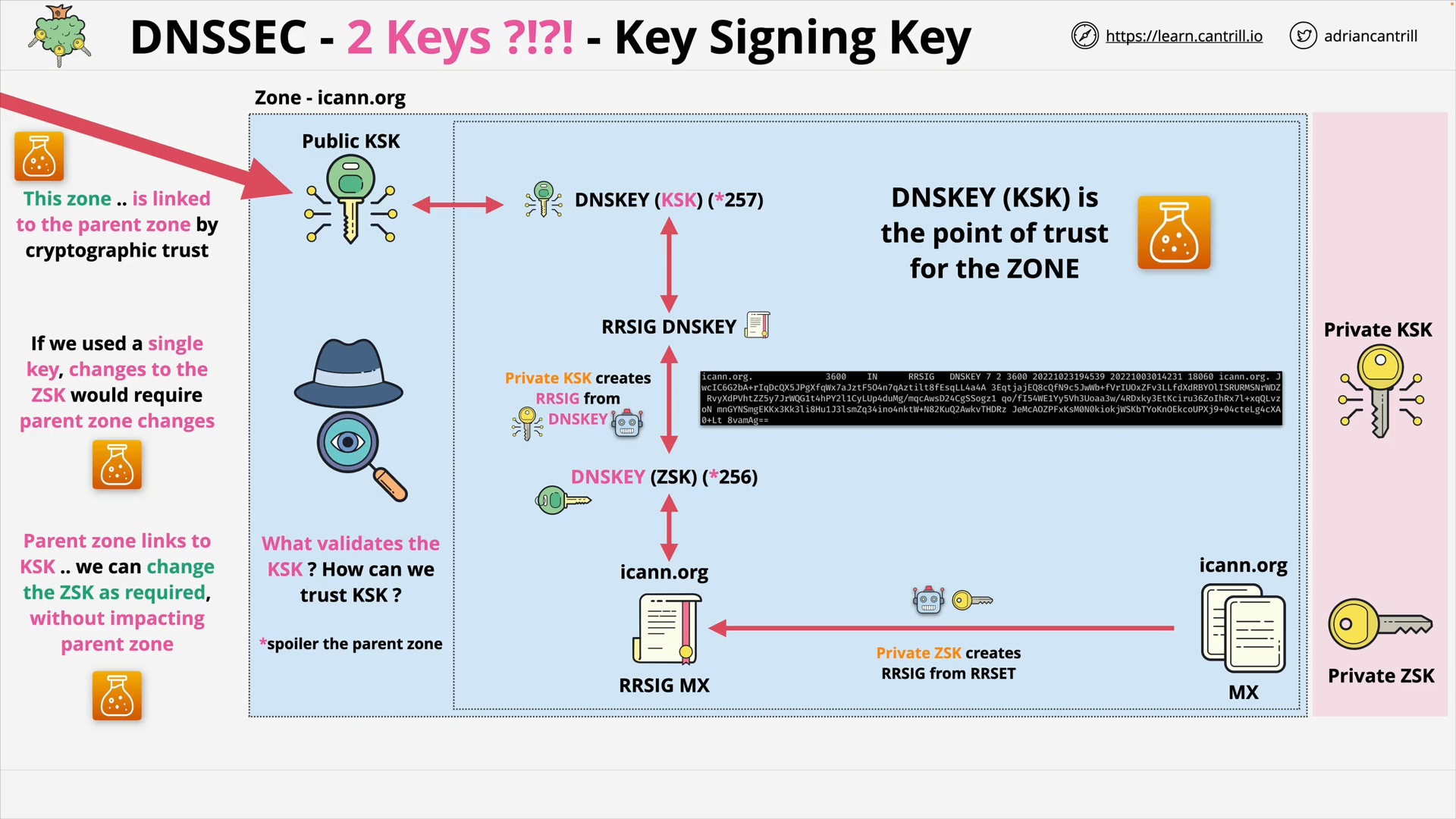 DNSSEC - 2 Keys - Key Signing Key
DNSSEC - 2 Keys - Key Signing Key
what is a ksk?
KSK is used to sign and verify the ZSK
why do we use separate zone-signing keys and key-signing keys?
The KSK is linked to the parent zone.
If we use a single key, changes to the ZSK would requires parent zone changes. 🐌🆘
By using 2 keys, we can change the ZSK as quired, without impacting parent zone. 🤳
 DNSSEC - Summary
DNSSEC - Summary
DNSSEC #3 - DNSSEC Chain of Trust (8:16)
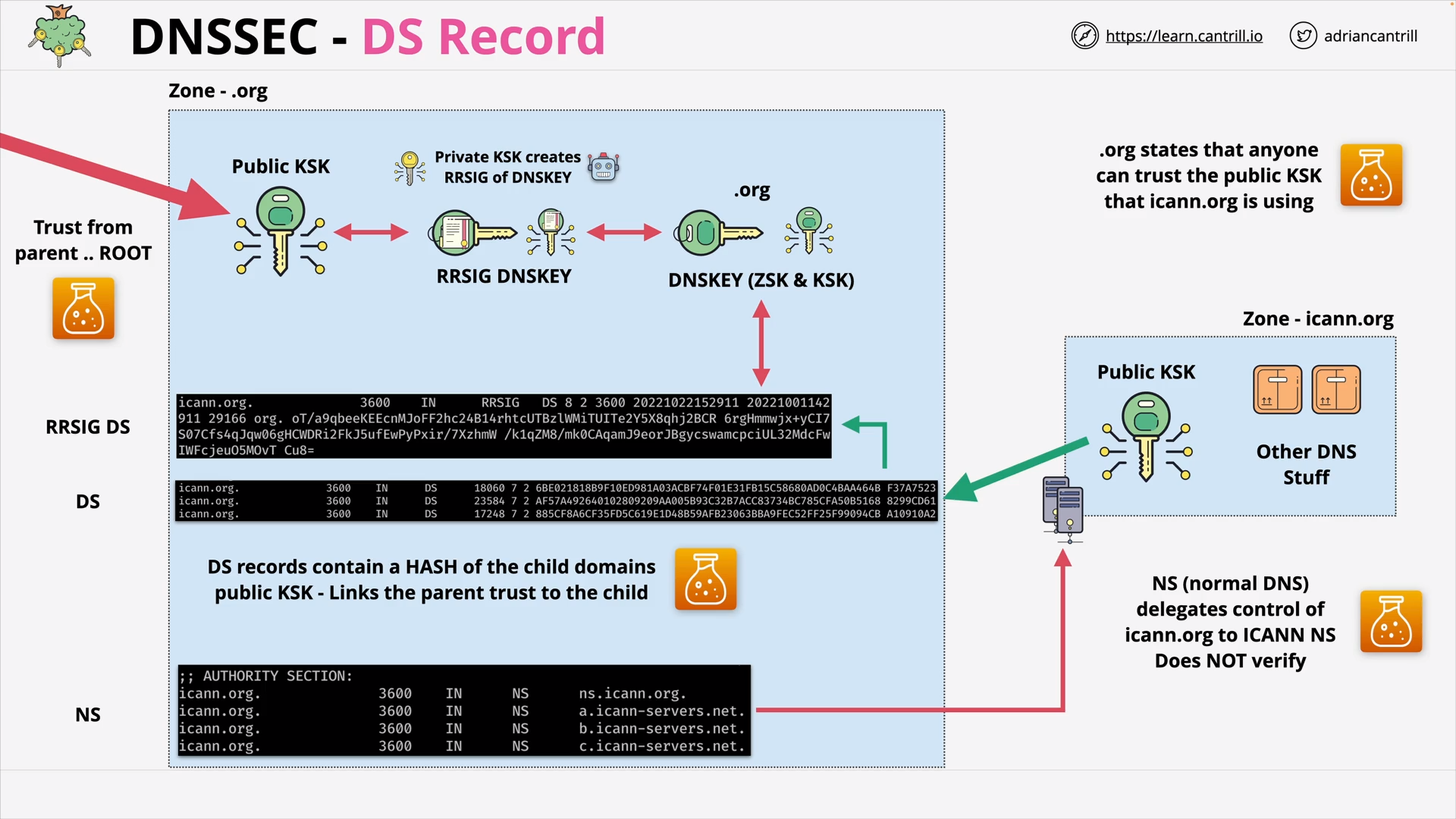 DNSSEC - DS Record
DNSSEC - DS Record
what is ds record?
DS (Delegation Signer) Record, on a parent zone, contains a hash of the KSK in a child zone.
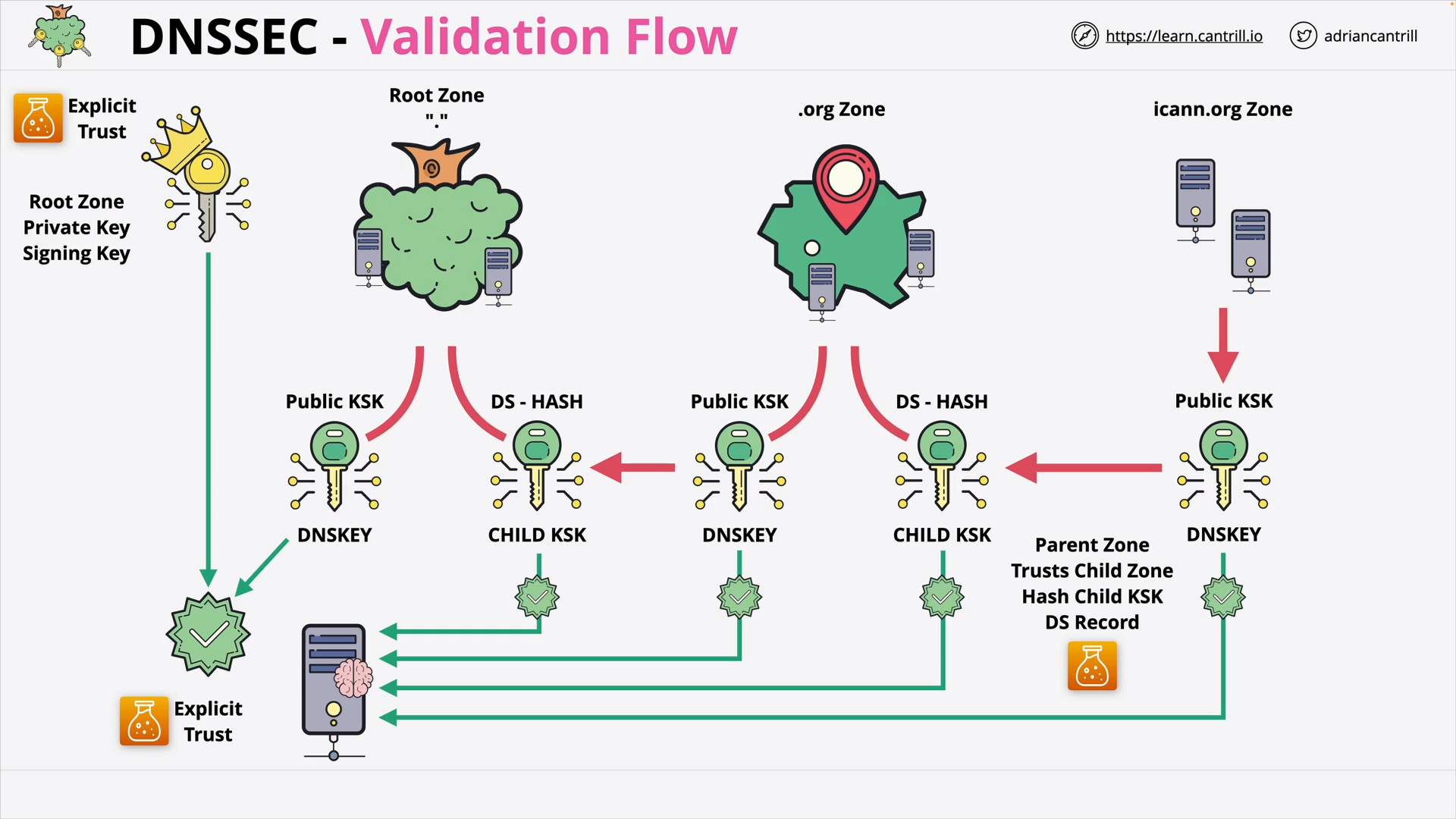 DNSSEC - Validation Flow
DNSSEC - Validation Flow
DNSSEC #4 - DNSSEC Root Signing Ceremony (7:53)
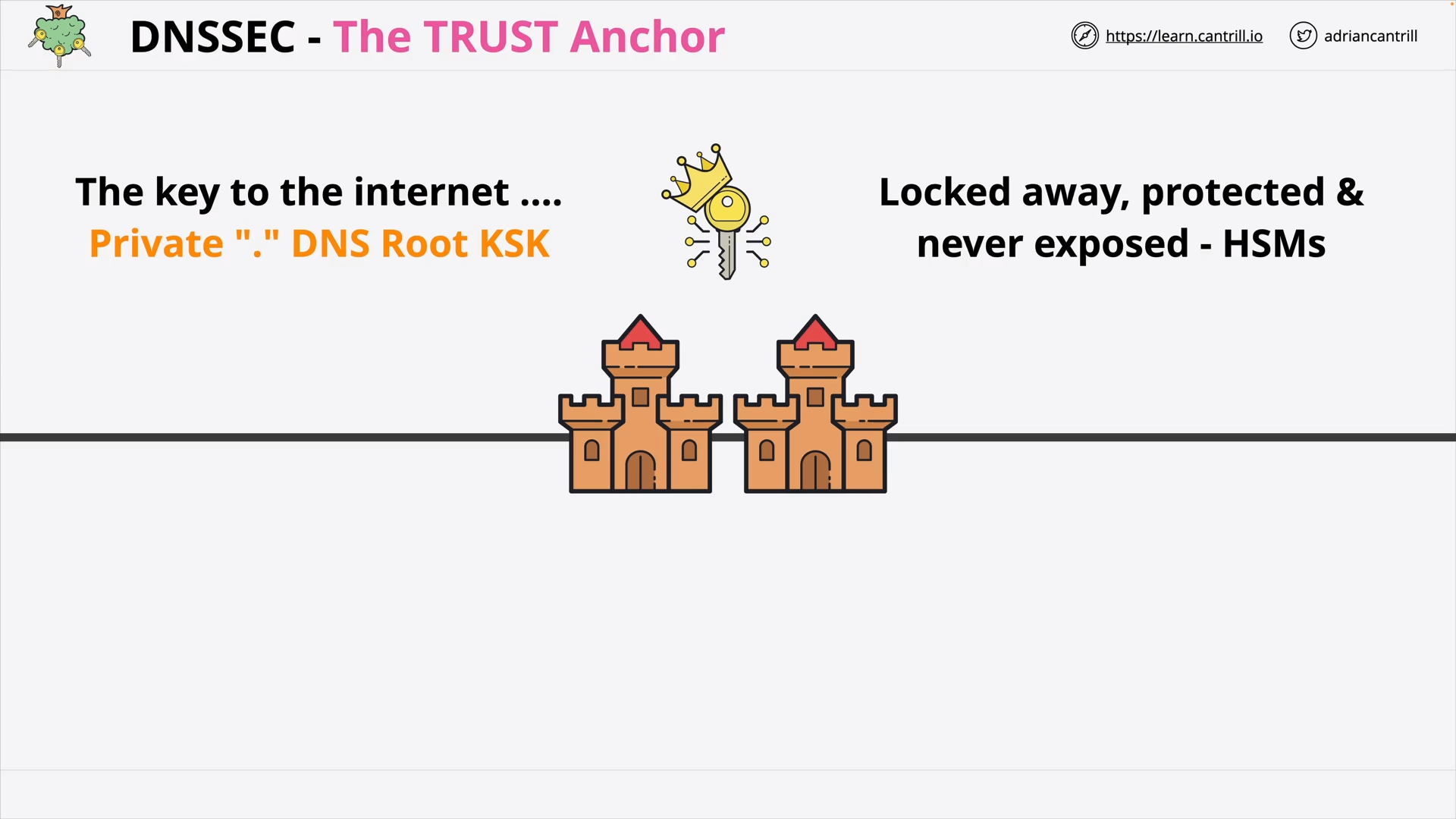 DNSSEC - Root KSK Private
DNSSEC - Root KSK Private
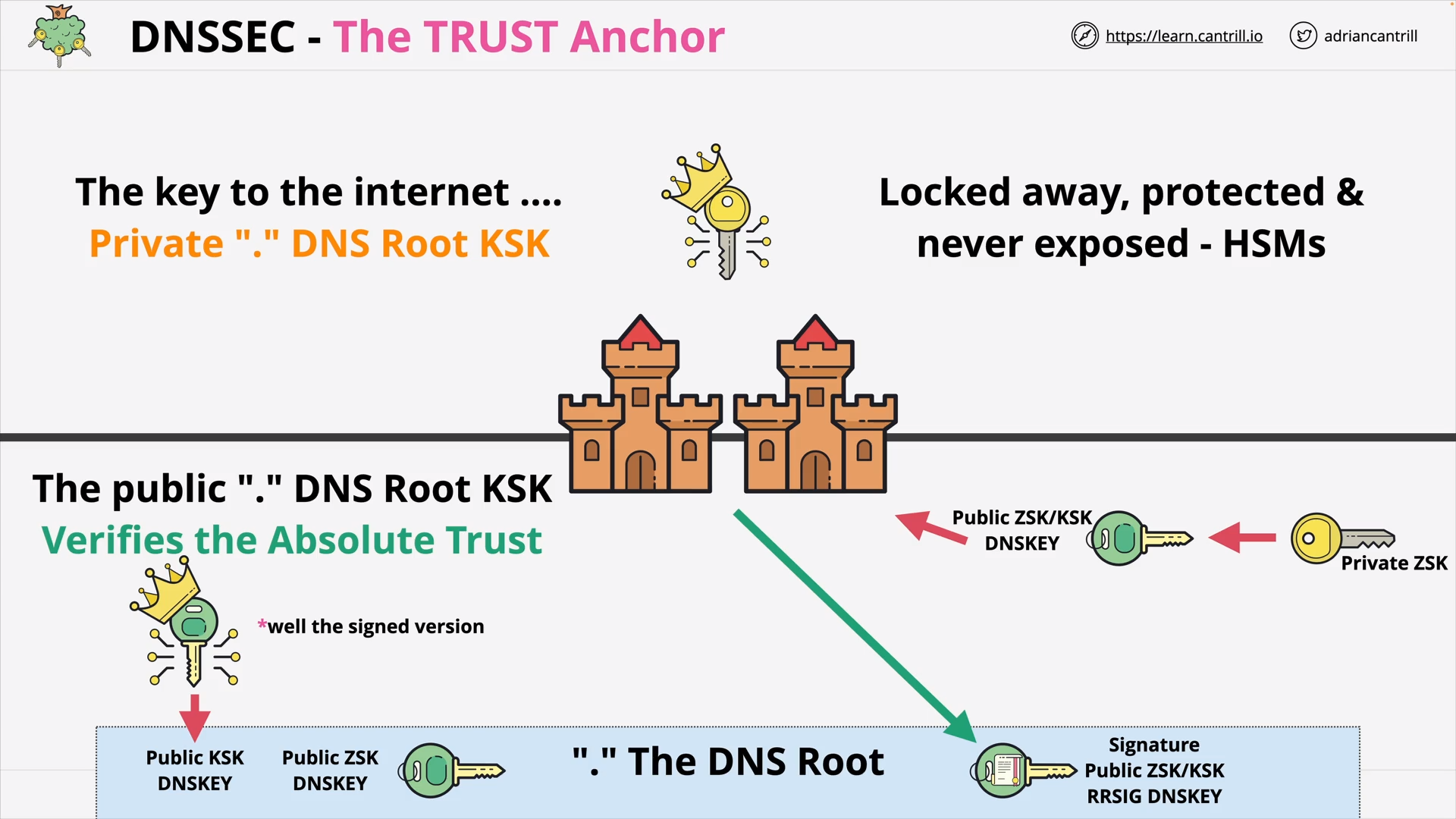 DNSSEC - Root KSK Public
DNSSEC - Root KSK Public
 DNSSEC - The TRUST Anchor (Root KSK)
DNSSEC - The TRUST Anchor (Root KSK)
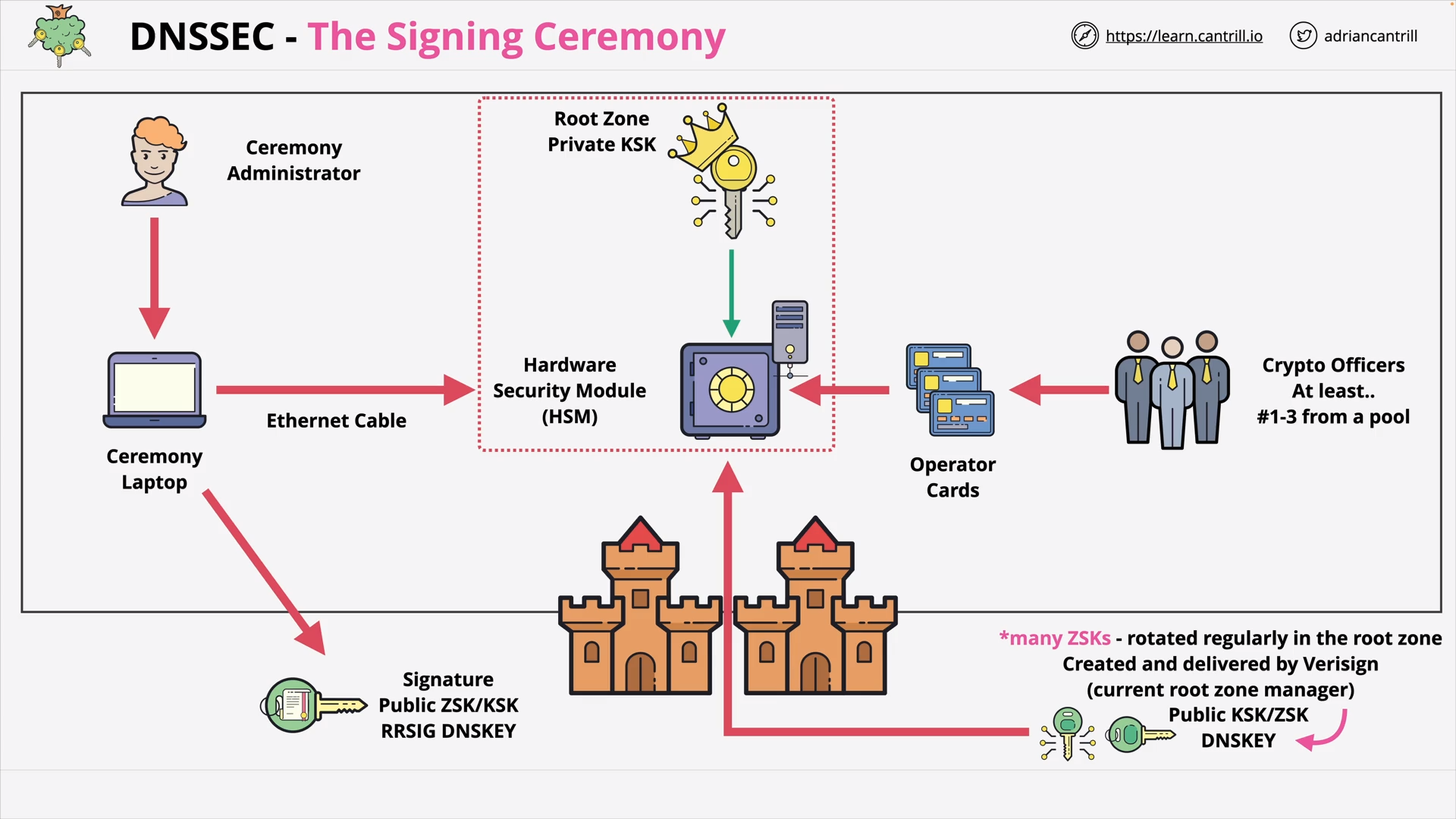 DNSSEC - The Signing Ceremony
DNSSEC - The Signing Ceremony
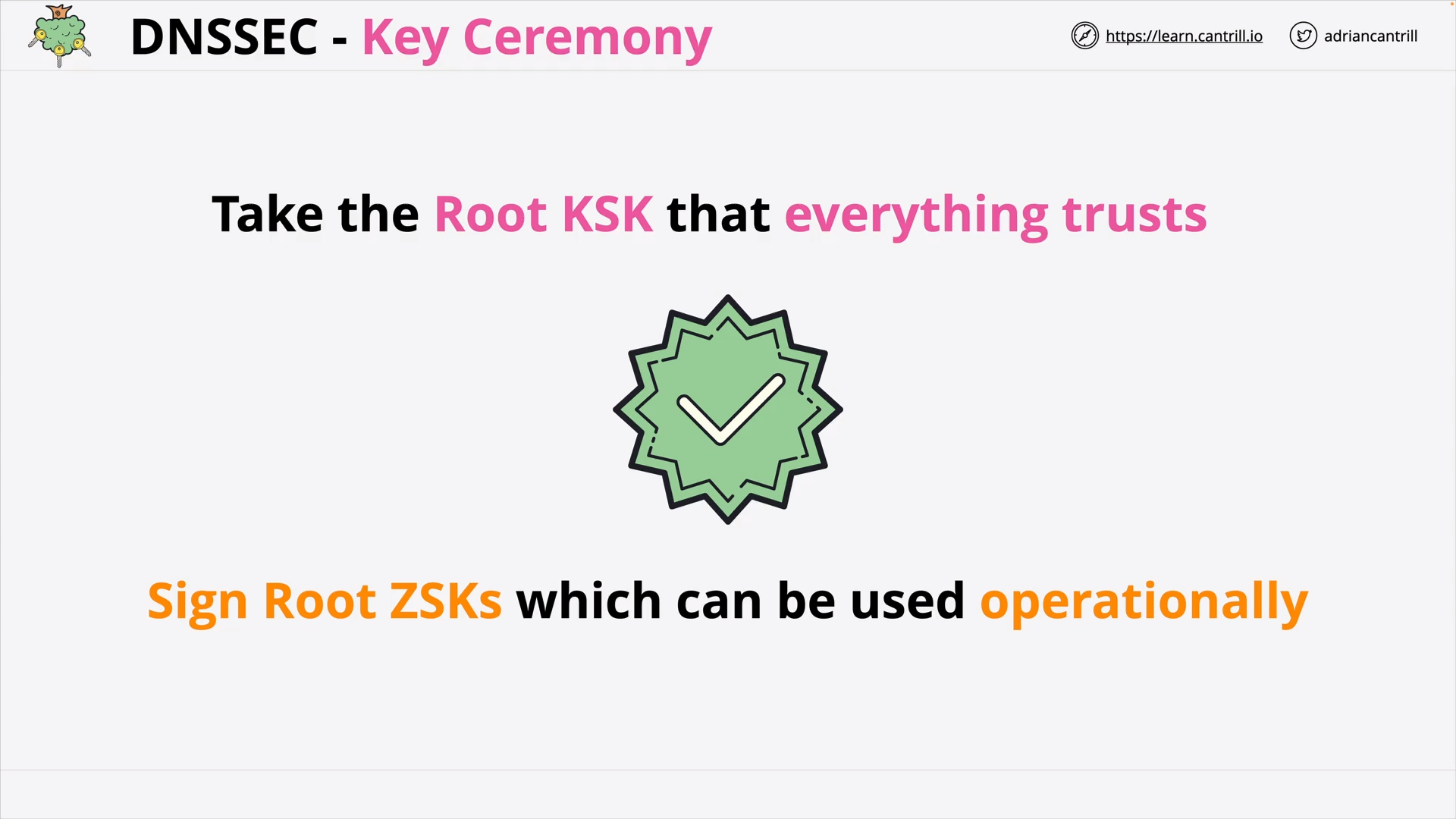 DNSSEC - Key Ceremony
DNSSEC - Key Ceremony
See The Key to the Internet and Key Ceremonies: An Explainer | ICANN
Containers & Virtualization (MORE COMING SOON)
Kubernetes 101 (11:27)
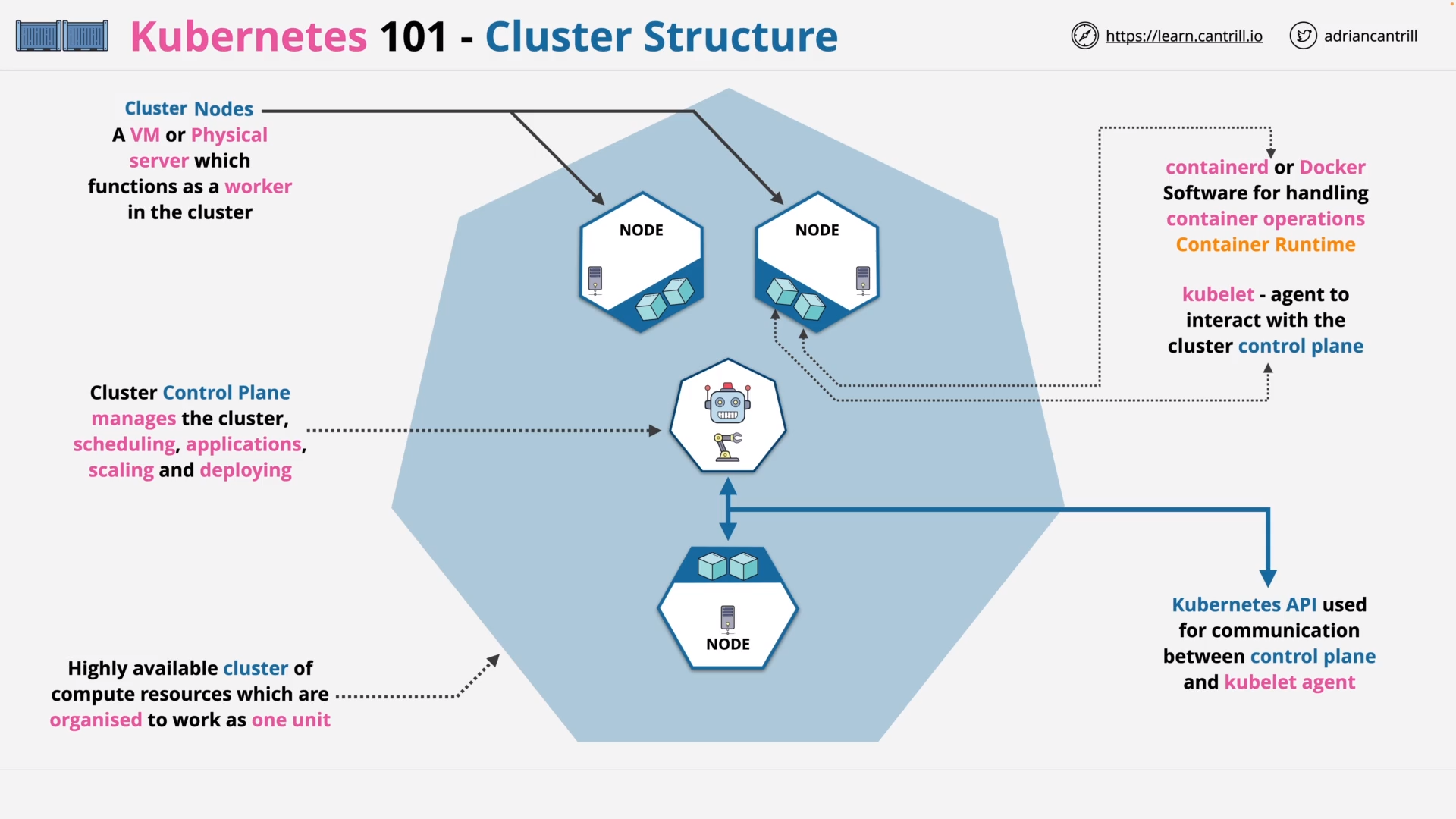 K8s - Cluster Structure
K8s - Cluster Structure
what is the basic structure of a k8s cluster?
A K8s cluster contains:
- Control Plane
- Worker Nodes
what is the control plane in k8s?
The control plane manages the overall state of the cluster
what is a worker node in k8s?
A worker node is the machine that actually run the containers
what are the core components of a worker node?
-
kubelet- Ensures that Pods are running, including their containers.
-
Container runtime
- Software responsible for running containers.
-
kube-proxy(optional)- Maintains network rules on nodes to implement Services.
what is the core component of control plane?
The core of Kubernetes’ control plane is
- the API server
- the HTTP API that it exposes, which is known as the Kubernetes API.
what does the kubernetes api do?
The Kubernetes API
- lets end users, different parts of your cluster, and external components communicate with one another.
- let you query and manipulate the state of API objects in Kubernetes (for example: Pods, Namespaces, ConfigMaps, and Events).
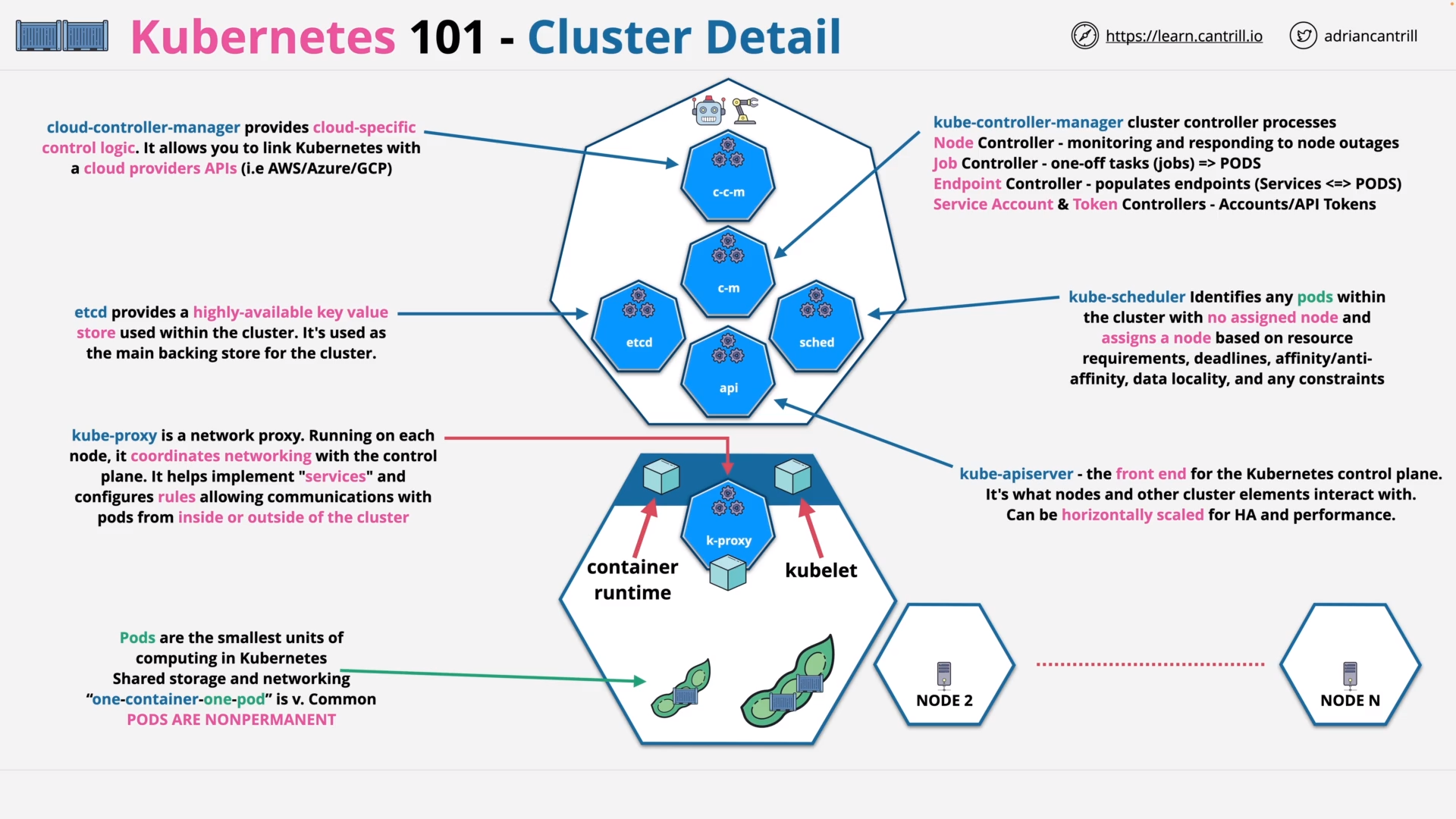 K8s - Cluster Detail
K8s - Cluster Detail
what is a `pod` in k8s?
In Kubernetes, a pod is the smallest unit of computing.
- In Docker, it’s the container.
what are the components of the control plane in k8s?
kube-apiserver: The core component server that exposes the Kubernetes HTTP APIetcd: Consistent and highly-available key value store for all API server datakube-scheduler: Looks for Pods not yet bound to a node, and assigns each Pod to a suitable node.kube-controller-manager: Core control loops of K8s: Runs controllers to implement Kubernetes API behavior.cloud-controller-manager(Optional): Integrates with underlying cloud provider(s).(AWS, Azure, GCP)
what is `kube-controller-manager`?
kube-controller-manager is the core control loops of K8s
- Watches the shared state of the cluster through the
apiserver - Makes changes attempting to move the current state towards the desired state
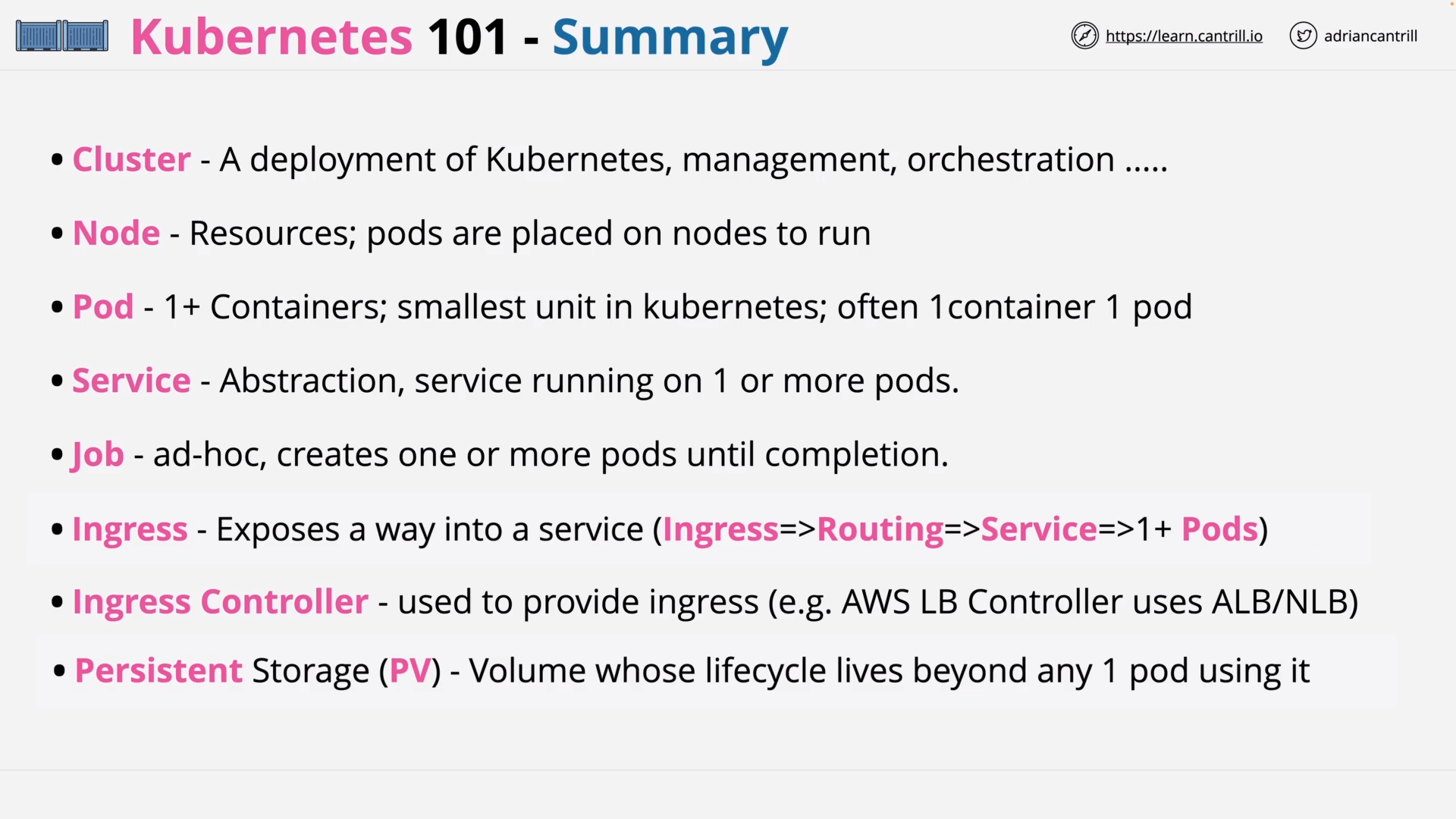 K8s - Summary
K8s - Summary
See Kubernetes Components | Kubernetes Documentation
Backups & DR (MORE COMING SOON)
Recovery Point Objective (RPO) & Recovery Time Objective (RTO) (16:54)
_&_Recovery_Time_Obj.png) Recovery Point Objective (RPO)
Recovery Point Objective (RPO)
what is rpo?
Recovery Point Objective (RPO) is the maximum (amount of) data (in time) can be lost.
_&_Recovery_Time_Obj.png) Recovery Time Objective (RTO)
Recovery Time Objective (RTO)
what is rto?
Recovery Time Objective (RTO) is the maximum of time that the system can be down.
when does rto begin and end?
RTO
- begins at at momne of failure
- ends when the system is operational (and handled back to business)
what need to be cautious about rto?
- How long until we know there is an issue?
- What is the issue?
- Do we need to restore a backup? How to restore the backup?
_&_Recovery_Time_Obj.png) RPO & RTO - Summary
RPO & RTO - Summary
Data Formats & Configuration Formats (MORE COMING SOON)
YAML aint markup language (YAML) 101 (6:12)
_101__learn.cantri.png) A YAML document is an “unordered list” of key:value pairs.
A YAML document is an “unordered list” of key:value pairs.
tip
In YAML, an “unordered list” is called a dictionary
_101__learn.cantri.png) YAML - Ordered list
YAML - Ordered list
tip
In YAML, an “ordered list” is called sequence, which can contains values of different types.
_101__learn.cantri.png) YAML - Structure
YAML - Structure
Javascript Object Notation (JSON) 101 (4:25)
_101__learn.cantr.png) JSON - Introduction
JSON - Introduction
_101__learn.cantr.png) JSON - Object & List
JSON - Object & List
_101__learn.cantr.png) JSON - Nested Object
JSON - Nested Object
OSI Model
| OSI Layer | OSI Layer Name | Protocol data unit (PDU) | PDU | TCP/IP Protocols | Misc examples | Software | Hardware | Function | Note | ||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Host layers | 7 | Application | Data | HTTP/S | DNS, WebSocket | Browser, curl | 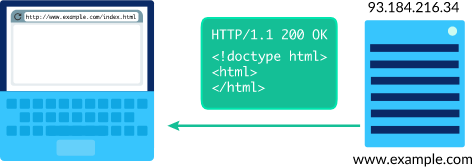 | High-level protocols such as for resource sharing or remote file access, e.g. HTTP. | |||
| 6 | Presentation | SSL/TLS | 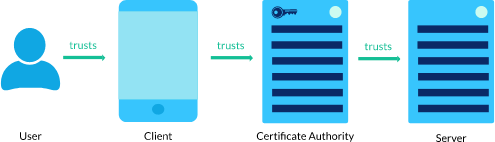 | Translation of data between a networking service and an application; including character encoding, data compression and encryption/decryption | |||||||
| 5 | Session | Sockets | NFS | Managing communication sessions, i.e., continuous exchange of information in the form of multiple back-and-forth transmissions between two nodes | |||||||
| 4 | Transport | Segment, Datagram | 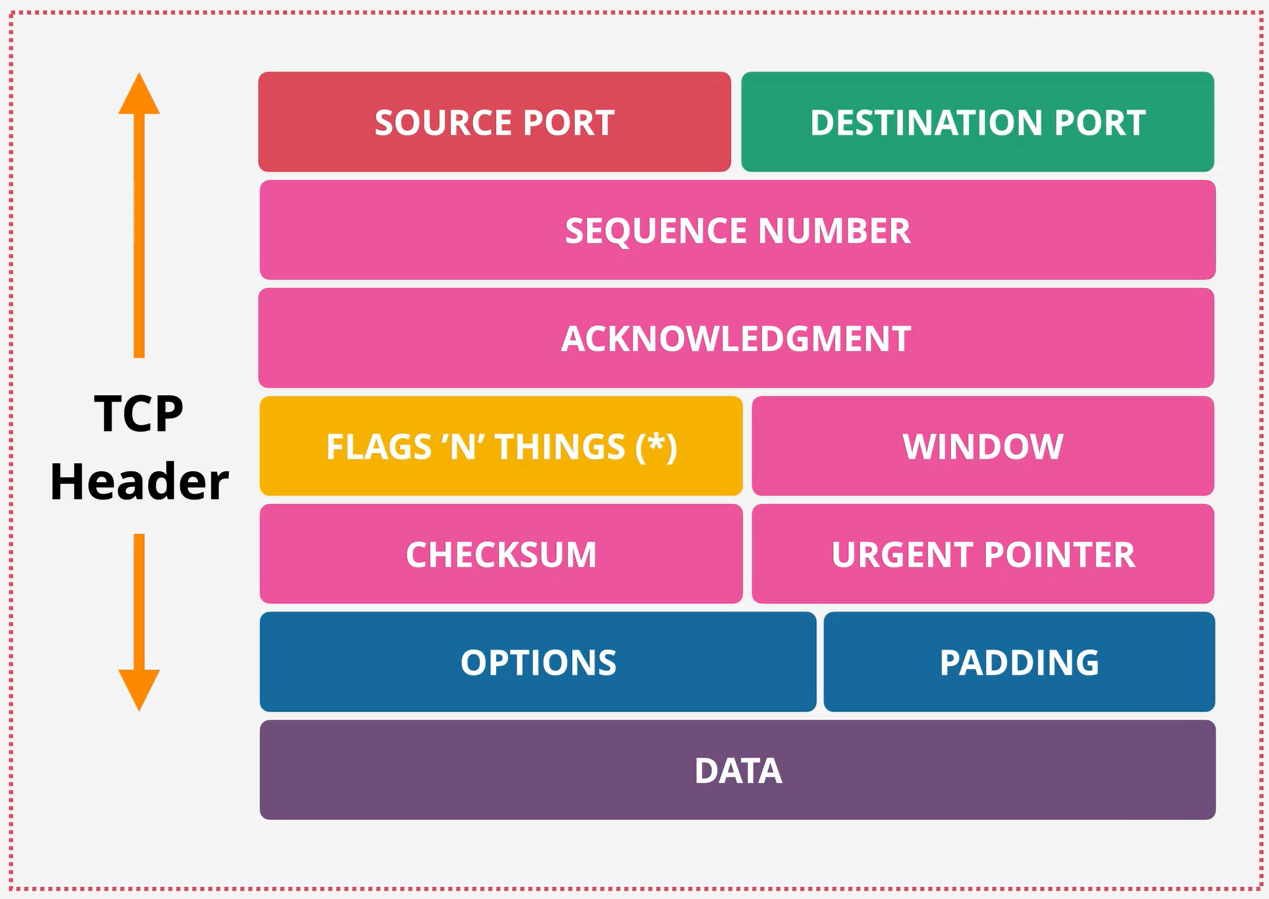 | TCP, UDP | QUIC | Internet Socket 1 (OS) |  | Reliable transmission of data segments between points on a network, including segmentation, acknowledgement and multiplexing | Where will the data goes? | ||
| Media layers | 3 | Network | Packet | 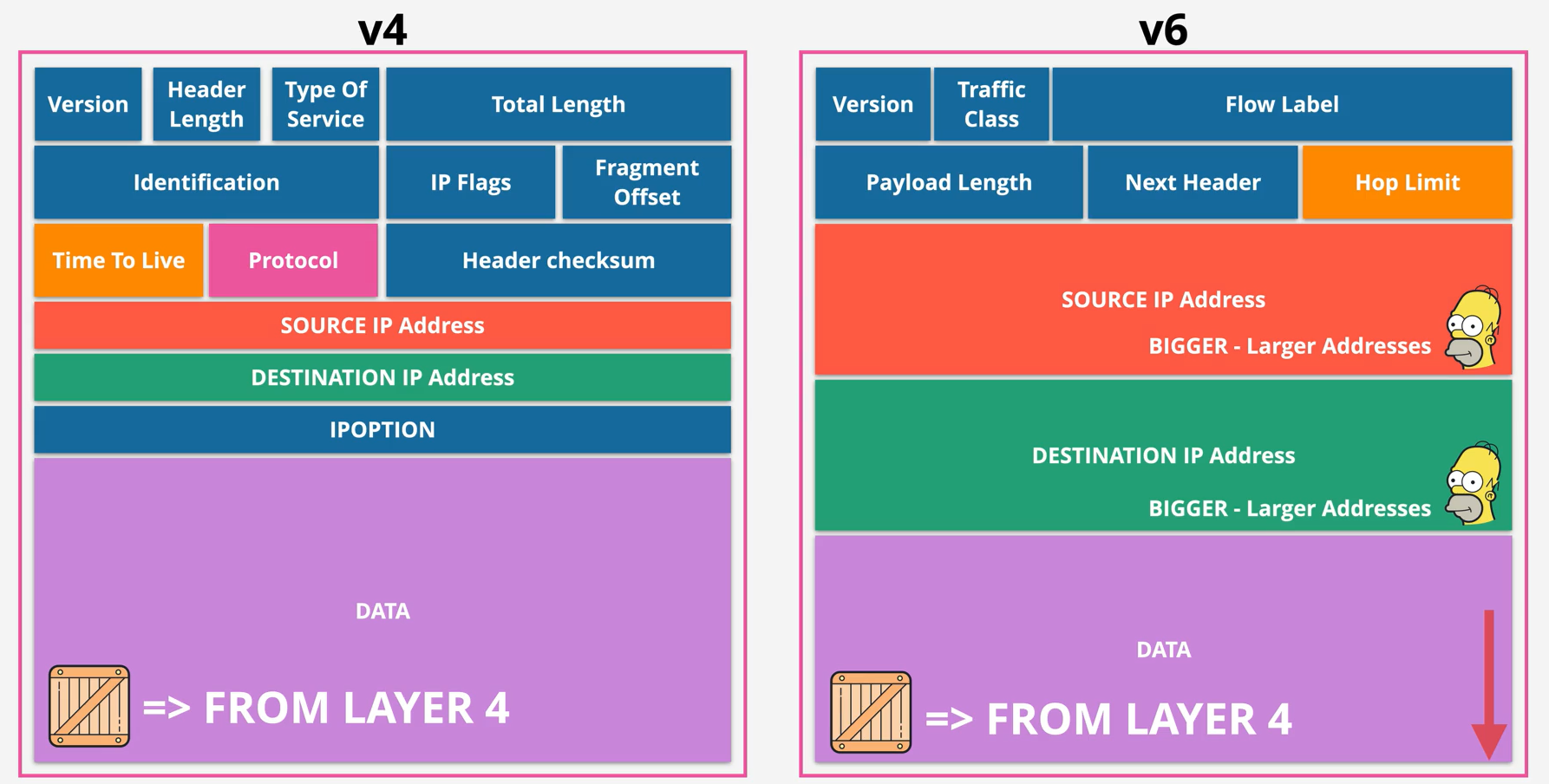 | IP, IPv6, IPSec, ICMP | Router | 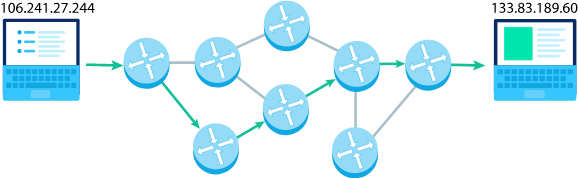 | Structuring and managing a multi-node network, including addressing, routing and traffic control | How the data goes to the final network? Which physical path the data will take? | ||
| 2 | Data link | Frame | 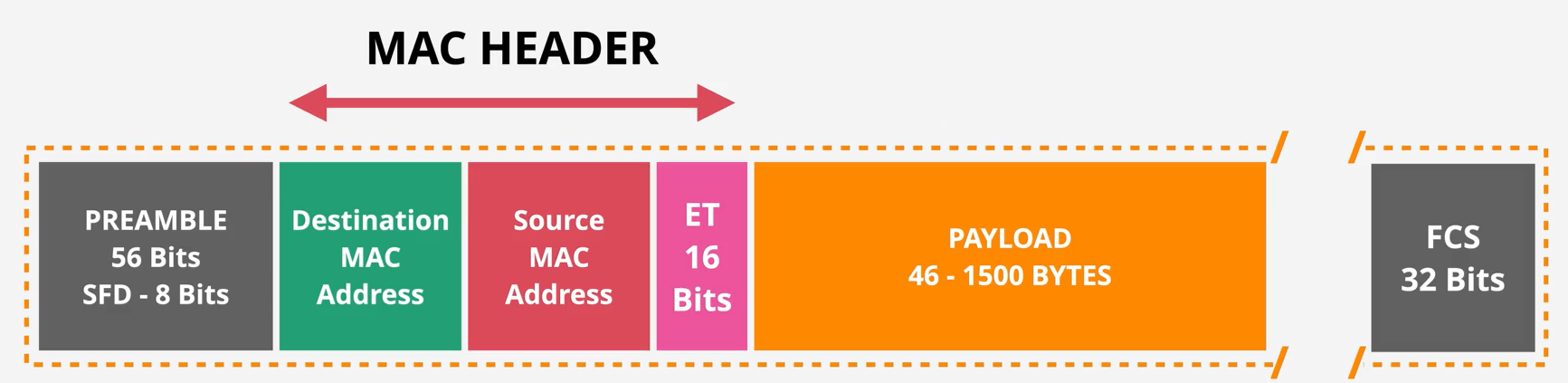 | PPP | MAC, Ethernet, Wifi, ARP, IEEE 802.1Q, 802.1AD (QinQ) (VLAN) | Switch | Transmission of data frames between two nodes connected by a physical layer | How the data goes inside local network? Two devices on the same network. | |||
| 1 | Physical | Bit | 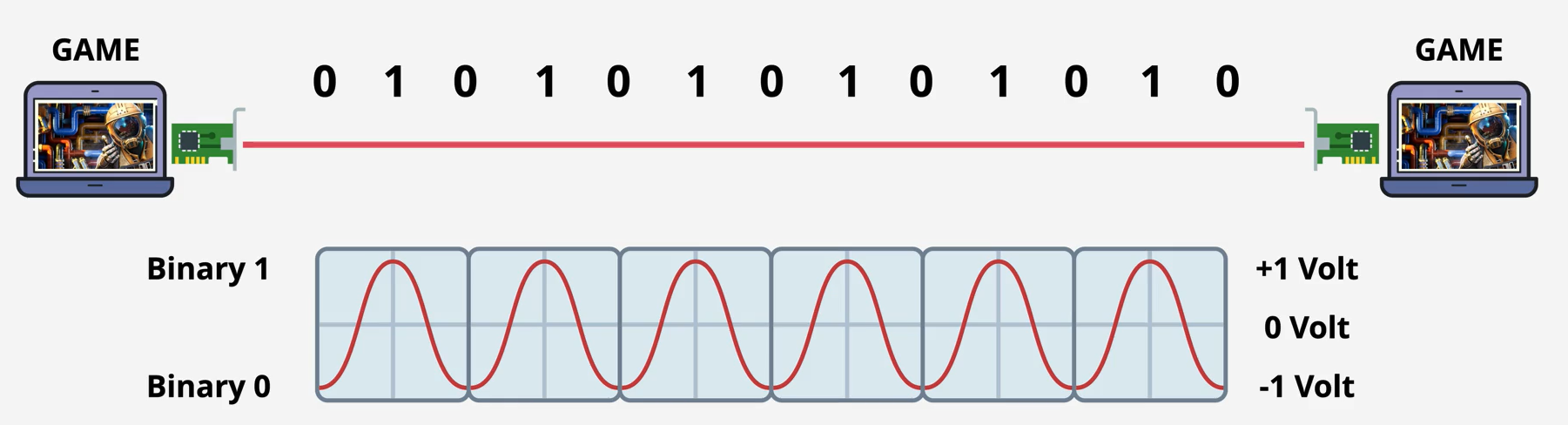 | RS232, Bluetooth | NIC, Hub |  | Transmission and reception of raw bit streams over a physical medium | How the bits goes? Raw bit stream over ethernet cable, optical fibre, Wifi… | |||
| OSI Layer | OSI Layer Name | Protocol data unit (PDU) | PDU | TCP/IP Protocols |
|---|---|---|---|---|
| 7 | Application | Data | HTTP/S | |
| 6 | Presentation | SSL/TLS | ||
| 5 | Session | Sockets | ||
| 4 | Transport | Segment, Datagram |  | TCP, UDP |
| 3 | Network | Packet |  | IP, ICMP |
| 2 | Data link | Frame |  | PPP |
| 1 | Physical | Bit |  |
| OSI Layer | OSI Layer Name | TCP/IP Layer | TCP/IP Protocols | Note | |
|---|---|---|---|---|---|
| 7 | Application | Application | HTTP/S |  | |
| 6 | Presentation | (as above) | SSL/TLS |  | |
| 5 | Session | (as above) | Sockets | ||
| 4 | Transport | Transport | TCP, UDP |  | |
| 3 | Network | Internet | IP, ICMP |  | Which physical path the data will take? |
| 2 | Data link | Link | PPP | Two devices on the same network. | |
| 1 | Physical |  | Raw bit stream over ethernet cable, optical fibre, Wifi… |
| Please | Do | Not | Throw | Sausage | Pizza | Away |
|---|---|---|---|---|---|---|
| Physical | Data Link | Network | Transport | Session | Presentation | Application |
| All | People | Seem | To | Need | Data | Processing |
|---|---|---|---|---|---|---|
| Application | Presentation | Session | Transport | Network | Data | Physical |
OSI Model Debugging Tools
OSI Layer 7
OSI Layer 7 - HTTP/s:
Using browser network debugging tool
Using CLI tools: httpie, curl
❯ http -v httpbin.org/headers
# Request Header
GET /headers HTTP/1.1
Accept: */*
Accept-Encoding: gzip, deflate
Connection: keep-alive
Host: httpbin.org
User-Agent: HTTPie/3.2.2
# Response Header
HTTP/1.1 200 OK
Access-Control-Allow-Credentials: true
Access-Control-Allow-Origin: *
Connection: keep-alive
Content-Length: 215
Content-Type: application/json
Date: Sun, 29 Oct 2023 09:02:09 GMT
Server: gunicorn/19.9.0
# Response Body
{
"headers": {
"Accept": "*/*",
"Accept-Encoding": "gzip, deflate",
"Host": "httpbin.org",
"User-Agent": "HTTPie/3.2.2",
"X-Amzn-Trace-Id": "Root=1-653e1f91-460f926d6dd9a7fa0b2ffadc"
}
}
OSI Layer 7 - DNS: dig +trace
OSI Layer 6 - Presentation Layer
OSI Layer 5 - Session Layer
Using browsers’s Dev Tools > Storage > Cookies > URL
OSI Layer 4: netcat
Example:
-
Connect to
example.comon TCP port 80❯ netcat -vz example.com 80 Connection to example.com (93.184.216.34) 80 port [tcp/http] succeeded! -
Connect to
example.comon TCP port 443❯ netcat -vz example.com 443 Connection to example.com (93.184.216.34) 443 port [tcp/https] succeeded!
OSI Layer 3
OSI Layer 3 - IP: traceroute
❯ traceroute example.com
traceroute to example.com (93.184.216.34), 30 hops max, 60 byte packets
1 _gateway (172.21.64.1) 4.980 ms 4.832 ms 5.207 ms
2 adsl.hnpt.com.vn (203.210.144.237) 13.331 ms 18.460 ms 18.355 ms
3 172.17.5.57 (172.17.5.57) 18.256 ms 172.17.5.61 (172.17.5.61) 18.521 ms 18.434 ms
4 static.vnpt.vn (113.171.48.157) 18.334 ms static.vnpt.vn (113.171.49.73) 18.248 ms static.vnpt.vn (113.171.48.113) 18.171 ms
5 * * *
6 static.vnpt.vn (113.171.31.80) 56.974 ms * *
7 * static.vnpt.vn (113.171.36.53) 54.805 ms 47.859 ms
8 * 203.22.177.41 (203.22.177.41) 130.841 ms 121.59.128.33 (121.59.128.33) 65.246 ms
9 static.vnpt.vn (113.171.36.85) 57.070 ms 203.22.177.41 (203.22.177.41) 134.357 ms 131.765 ms
10 * * 38.142.247.66 (38.142.247.66) 227.320 ms
11 * 38.142.247.66 (38.142.247.66) 227.136 ms *
12 * * *
13 * 38.142.247.66 (38.142.247.66) 211.344 ms *
14 93.184.216.34 (93.184.216.34) 250.968 ms 251.868 ms 251.738 ms
OSI Layer 3 - ICMP: ping
❯ ping -c 10 example.com
PING example.com (93.184.216.34) 56(84) bytes of data.
64 bytes from 93.184.216.34: icmp_seq=1 ttl=53 time=253 ms
64 bytes from 93.184.216.34: icmp_seq=2 ttl=53 time=286 ms
64 bytes from 93.184.216.34: icmp_seq=3 ttl=53 time=277 ms
64 bytes from 93.184.216.34: icmp_seq=4 ttl=53 time=269 ms
64 bytes from 93.184.216.34: icmp_seq=5 ttl=53 time=260 ms
64 bytes from 93.184.216.34: icmp_seq=6 ttl=53 time=254 ms
64 bytes from 93.184.216.34: icmp_seq=7 ttl=53 time=242 ms
64 bytes from 93.184.216.34: icmp_seq=8 ttl=53 time=235 ms
64 bytes from 93.184.216.34: icmp_seq=9 ttl=53 time=225 ms
64 bytes from 93.184.216.34: icmp_seq=10 ttl=53 time=235 ms
--- example.com ping statistics ---
10 packets transmitted, 10 received, 0% packet loss, time 15605ms
rtt min/avg/max/mdev = 225.020/253.679/285.941/18.837 ms
DNSSEC
.org
# 6️⃣ DS: Hash of icann.org's public KSK 5️⃣
icann.com. 86400 IN DS 50731 8 2 6912A467DC432811BD2B1C7E5C01B20E2C60049EB57833E8308FAD0F DE779511
# 7️⃣ RRSIG DS: Digital Signature of RRSET DS (signed with .org private ZSK) 👈 Use .org public ZSK to verify
icann.com. 86400 IN RRSIG DS 8 2 86400 20231004041827 20230927030827 4459 com. HzxBlHRtCbsrYi2gSs/bndqPM+CudLaCpHQQtZAxMgtdCnVaizDYPan2 2y90Xs6SEXtUqgoZqq7UUGsR+R/z3dB3WSp7x803l6YReF8yEl798JVb LqVZTHzxCkGI1epGgG7RRQh6guewsjIglLMn10F8DYYVwA/ciIM0MFVn PoGJ7jFVXCV94wbDjR/hGhmBnMs915qCQrXORsLoj3hNVA==
icann.org
# 1️⃣ A
icann.com. 21600 IN A 192.0.43.22
# 👉 2️⃣ RRSET A
# 3️⃣ RRSIG: Digital Signature of RRSET A (signed with icann.org private ZSK) 👈 Use icann.org public ZSK to verify
icann.com. 21171 IN RRSIG A 8 2 172800 20231013151215 20230922222304 19948 icann.com. kdlvu99UkZSgLwUm5kRLOh3uwPEDdrw8AGTA0GmVmHWVS+2DirvCvv5W cygWGaAJEgWv1vIrO7xxwhPSZgRFgGExsflJEweFeUhah4kvyu6ccWkH 7vKmB7FDllDk1jiOVTQxlMq6NMEiWEjdXV9kpWSz3W0zPUkZbfP0+LSU vF8=
# 4️⃣ DNSKEY 256 👈 Public ZSK
icann.com. 3600 IN DNSKEY 256 3 8 AwEAAZH9MYCAnL3ScBITGA/aqPHOWf06ggtfDNW2keGvZdI931UtwHqn yt7GxDReDChSBuKD4s61NqrNsLaYafAhJ2e0QoOMHdKerd0B/UXAr2Sg VjA1yhLicBivgmnF/+a1lfiMV8MuRLwQococw855FQe0+u7B+KfkSmna U+yl865p
# 5️⃣ DNSKEY 257 👈 Public KSK
icann.com. 3600 IN DNSKEY 257 3 8 AwEAAa7hPkfzWnWAMcvA+AYuFltjQRrwSitlgoq5rBZJw/rRS88g2jDK R9iM+8E4shyH97qElzKKWtmB9zo1Ch4+7hL7nX1Fb5yxPmuzIvsCgktj YWKe+5xzXn7k0SX4HtRZlkZEMSRZU0FU0nnuVo1uKqCfirLBwA1pS56c ocw/nBlLz+6+GIsJ8+Ru6gsoMJDsM/um6lRsaIpRsgJZE1MD9L+iIVm7 SQTuJ/A9fBALcDP709YAW2Km4AMpr858kMW9dFwotKhkTDdrR4w4DGvC YuM8mmjrVcWkGNXuJa1dIbDRnTYuklxQhl8q79l2afUpMHpJN2Clmgqk 2SCQx4Pidz0=
icann.com. 3600 IN RRSIG DNSKEY 8 2 3600 20231015134910 20230924084215 33307 icann.com. ecdISSPgwKvgW6LIwtalMSIwlp9uJr36EJ6DdAKcVERLJ4Qj3GL9Nzki VMbVnKAvSRxHvDTvI7C6lxwKw0IZRxbcyFHTj/FM7wZhXDZEeL/4XVNJ Zctbz61e+TQgsLaOsGtw3/6xiDBkMaVdSzXS+dGmcOZoLtnR3snd/lHb GRtTLI/MPICnCrJNV0r1L6Ka+sLAOVeci7qmB6VrG4oQ9z5/IIpXe0dW njPXRhETbgVIClV/lOXxOLcEot3txwBCYyT714Cmpr6tqNaK++MGKlrt SE5c5q4MgHn18TZapcwgbCXaQqcgl1Q4hm1UY0kqnf0arBVgtOrJHTPO LOainw==
icann.com. 3600 IN RRSIG DNSKEY 8 2 3600 20231015134910 20230924084215 50731 icann.com. SMh9VLTzhdBtZFvkiCrcbPKv0o4EtcyRH/HqOfNz5nF3A1NtA2OB9ygp jwCipXMCPP4exBdZWTYz+wcnTom2kSGADa7RfTolAvY5/ttoNlyIMDs0 TaHY9YlHG+24jgA/O3i00CHCT1cT9/Pi+A5mVkD+L+89/5bA1+b35Ee3 Nf3Ub6krykr817WXuvb5EqVpPxHdKFqbwxNfhLRhlAgidPWY/JxeXm+m jF30A25QE0XiS+FrBv6yi/0adCUiFnoIbd8mORuE+Lj/j++5EBOvUBQY a5fc100gJmn8M2hfbH7K9pGPjiG8WjDmJn7htj9DAOeU/WGmOz5bDSfG JO+mhA==
Cloud Computing 101
What is Cloud Computing? (13:30)
 Cloud Computing Characteristic #1 - On-demand Self-Service 🏧
Cloud Computing Characteristic #1 - On-demand Self-Service 🏧
 Cloud Computing Characteristic #2 - Broad Network Access 🌐
Cloud Computing Characteristic #2 - Broad Network Access 🌐
 Cloud Computing Characteristic #3 - Resource Pooling ⛲
Cloud Computing Characteristic #3 - Resource Pooling ⛲
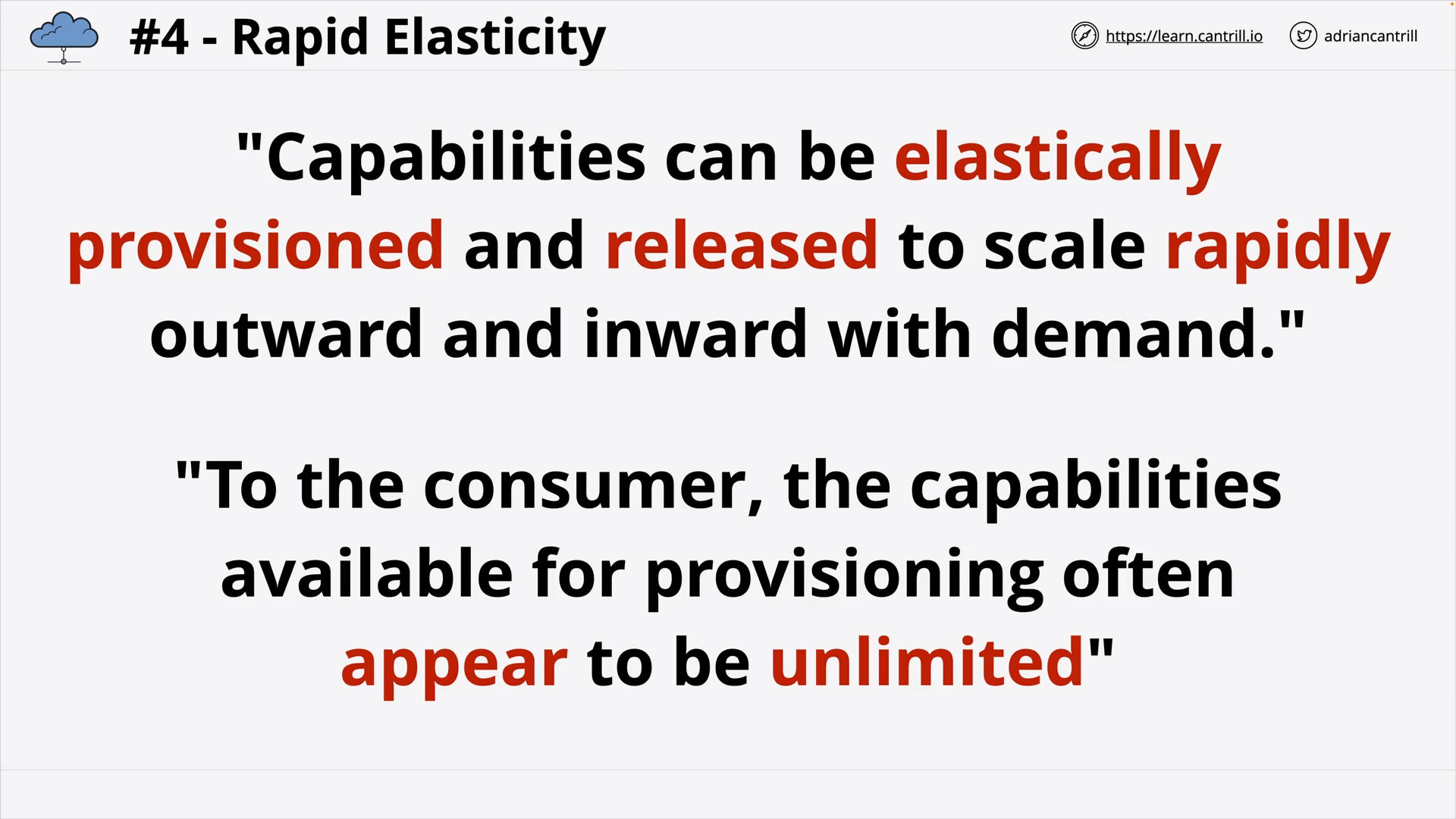 Cloud Computing Characteristic #4 - Rapid Elasticity ↕️
Cloud Computing Characteristic #4 - Rapid Elasticity ↕️
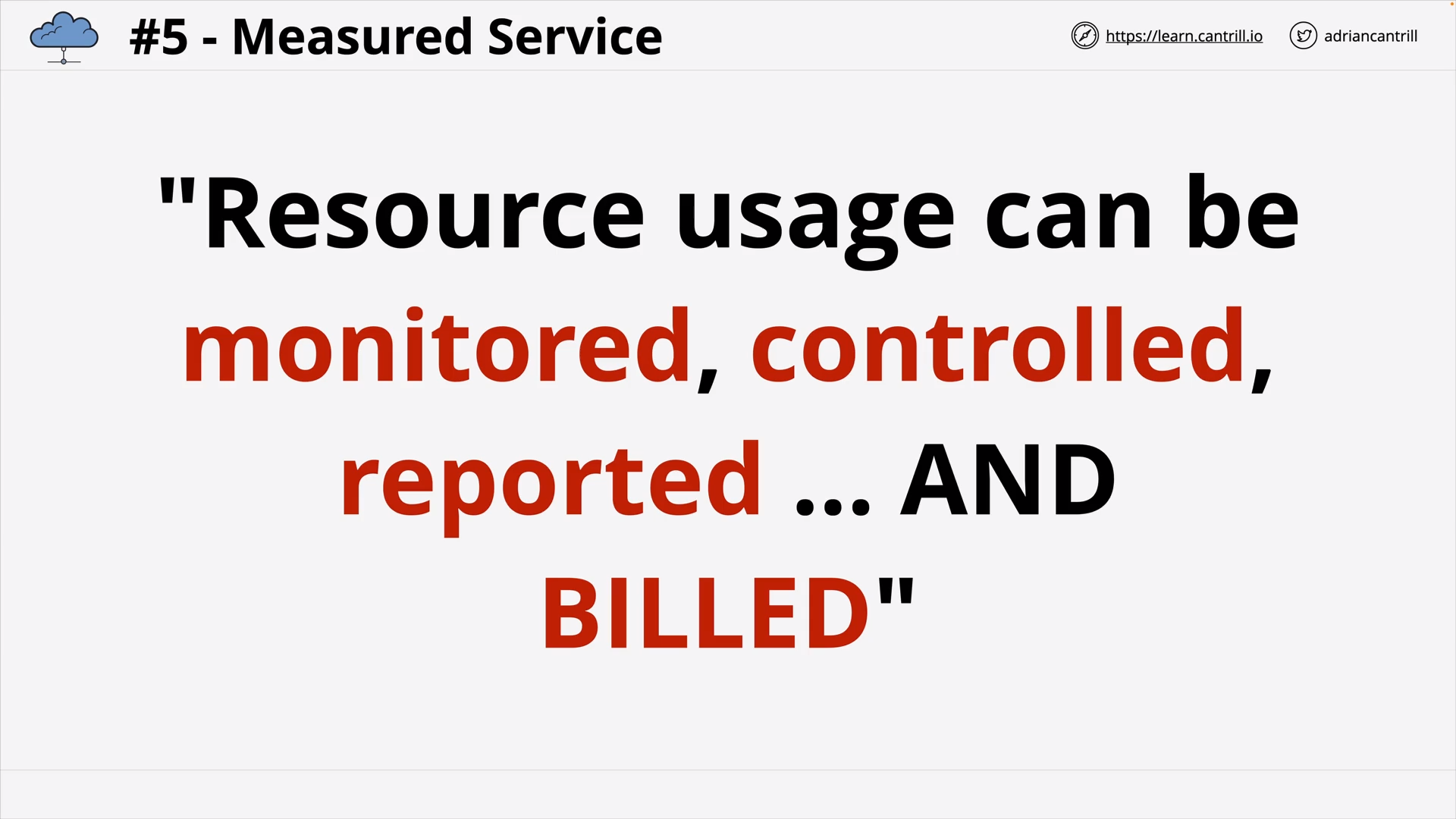 Cloud Computing Characteristic #5 - Measured Service 📏
Cloud Computing Characteristic #5 - Measured Service 📏
what are 5 characteristics of cloud computing?
- On-demand Self-Service 🏧
- Broad Network Access 🌐
- Resource Pooling ⛲
- Rapid Elasticity ↕️
- Measured Service 📏
Public vs Private vs Multi vs Hybrid Cloud .. (8:38)
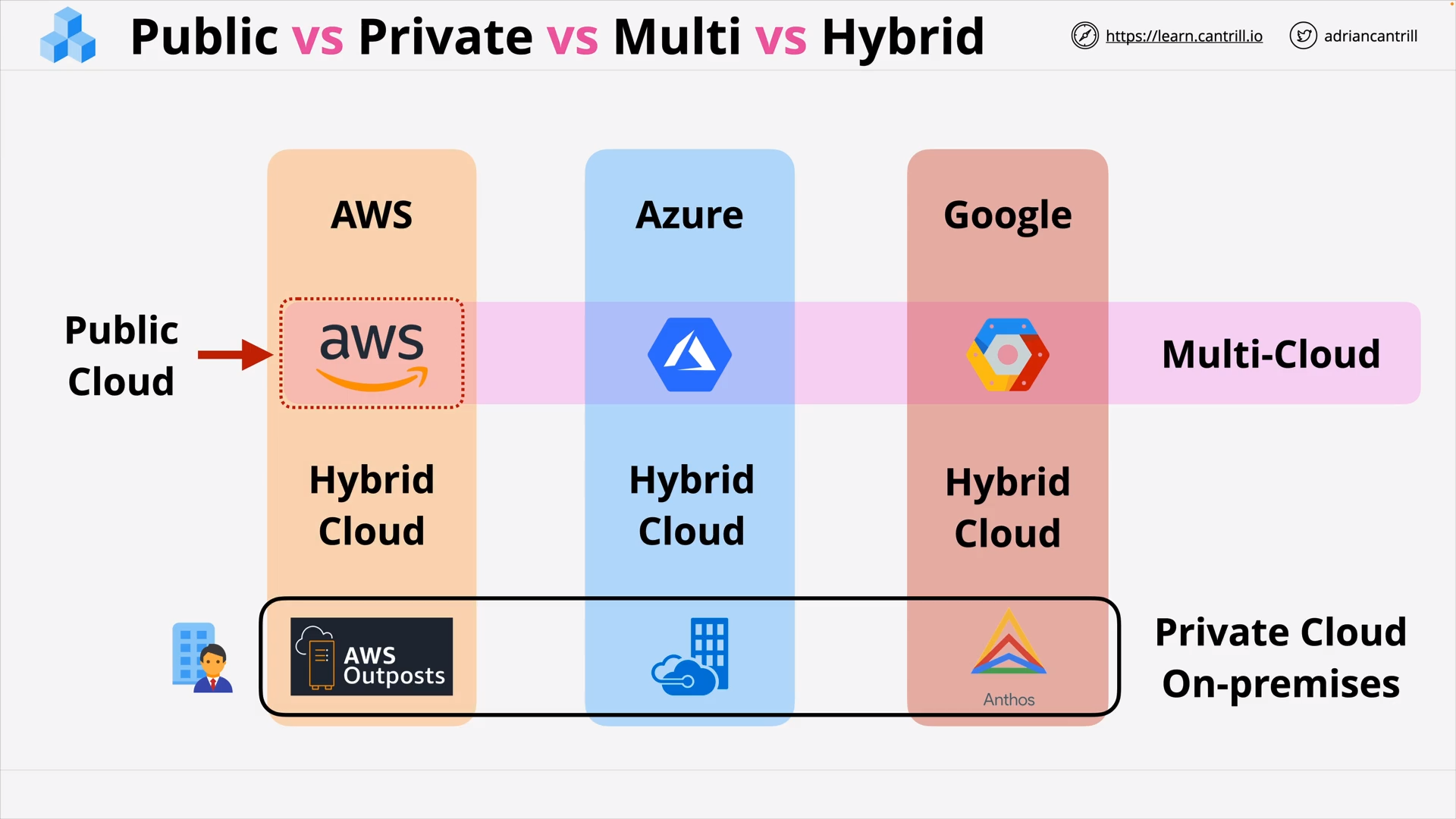 Cloud Computing - Deployment Models
Cloud Computing - Deployment Models
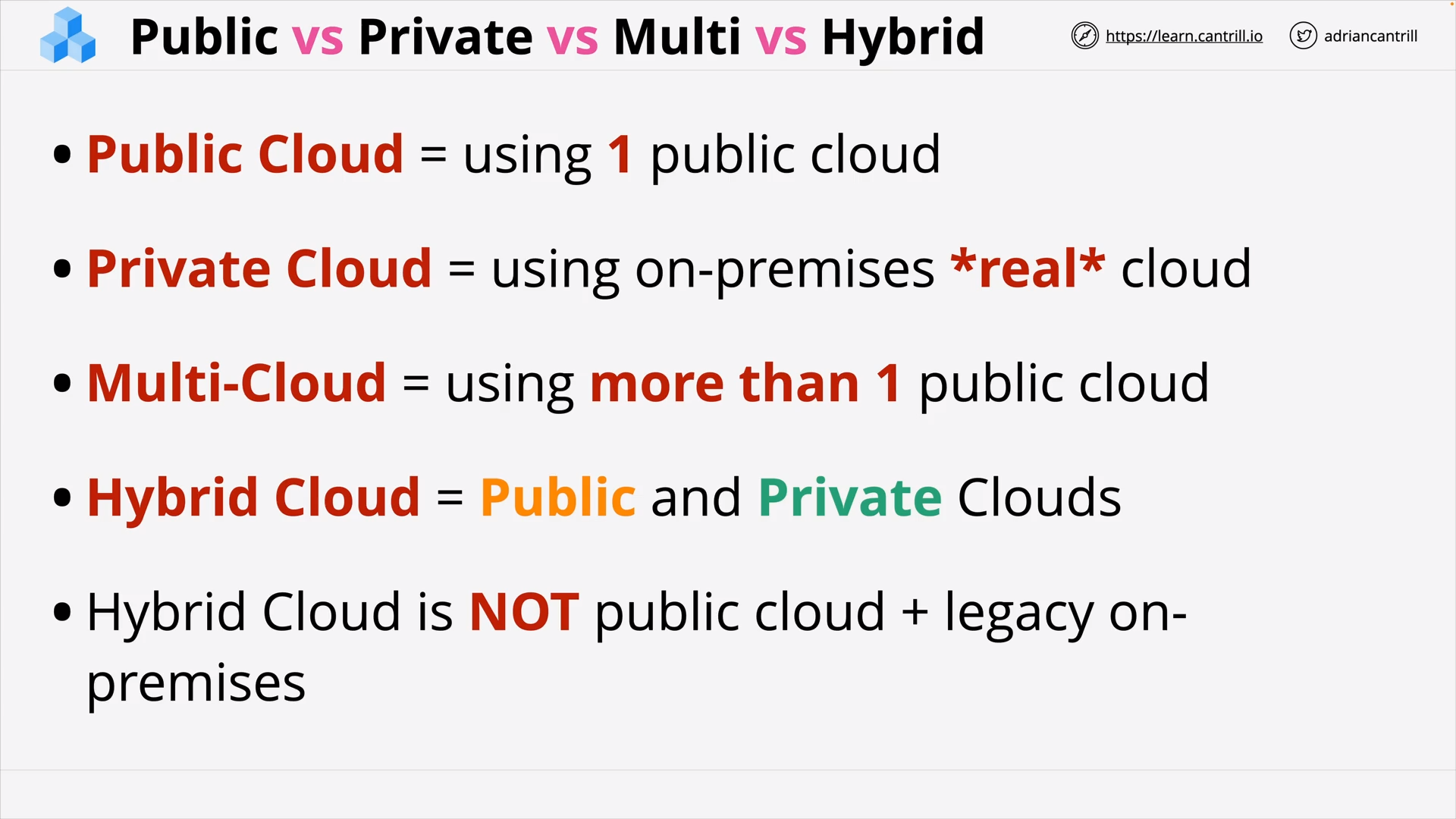 Cloud Computing - Hybrid Cloud is NOT Public Cloud + Legacy on-premises
Cloud Computing - Hybrid Cloud is NOT Public Cloud + Legacy on-premises
Cloud Service Models (IAAS, PAAS, SAAS) (10:25)
__learn.can.png) Infrastructure Stack
Infrastructure Stack
__learn.can.png) On-Premises vs Data Center Hosted
On-Premises vs Data Center Hosted
__learn.can.png) IaaS vs PasS vs SaaS
IaaS vs PasS vs SaaS
| APPLICATION | Data Center Hosted | IaaS | PaaS | SaaS | |
|---|---|---|---|---|---|
| DATA | 🔟🔟 | ⬆️ | |||
| RUNTIME | 🛣️ | ⬆️ | 💲 | ||
| CONTAINER | 🐋 | 💲 | 💲 | ||
| OS | 🪟🐧 | ⬆️ | 💲 | 💲 | |
| VIRTUALIZATION | 📦 | 💲 | 💲 | 💲 | |
| SERVERS | 🖥️ | 💲 | 💲 | 💲 | |
| INFRASTRUCTURE | ⚡🌐 | 💲 | 💲 | 💲 | |
| FACILITIES | 🏠 | 💲 | 💲 | 💲 | 💲 |
AWS FUNDAMENTALS
AWS Public vs Private Services (7:04)
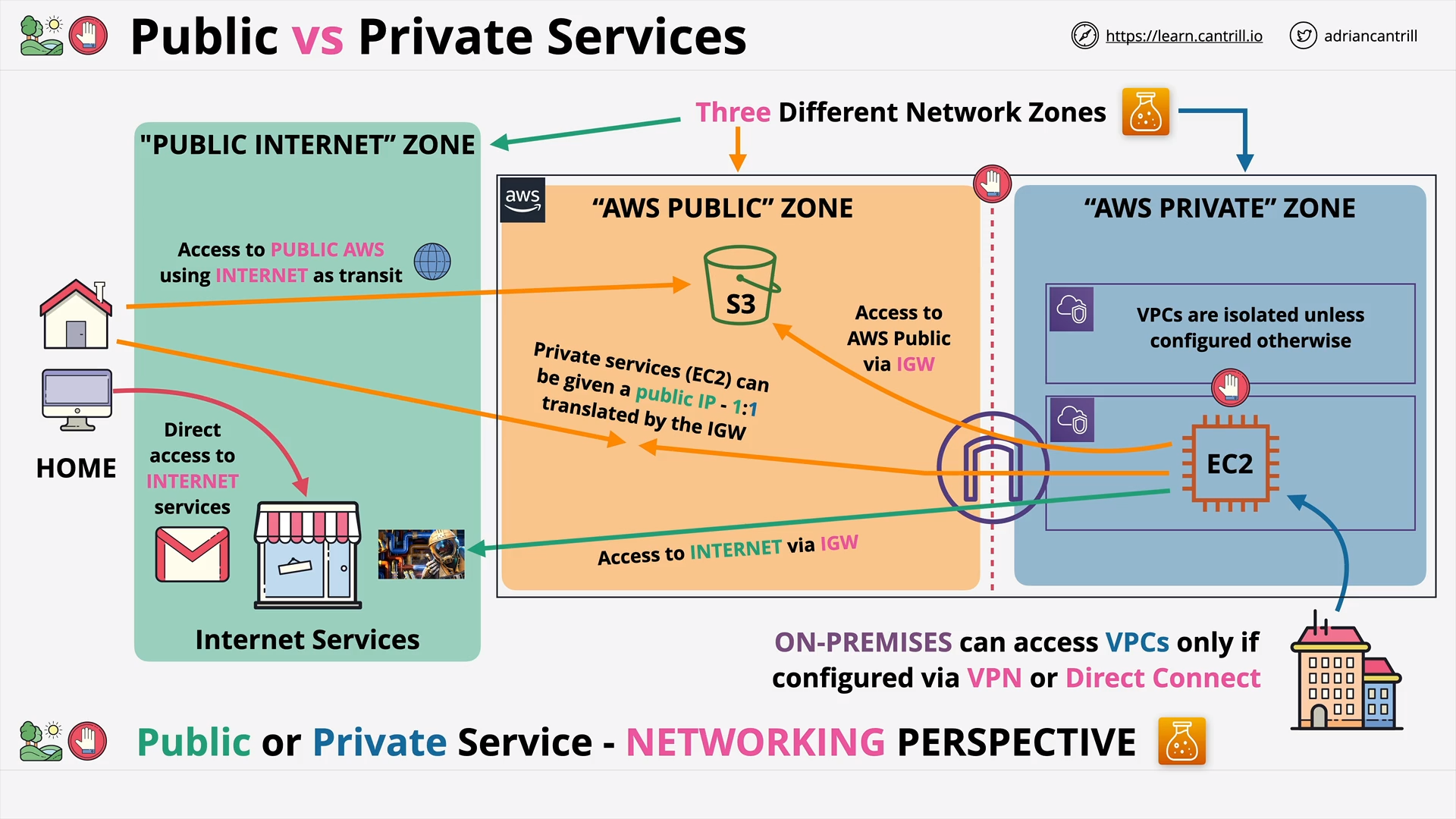
how many network zones are there in aws?
2:
- ‘AWS Public’ Zone
- ‘AWS Private’ Zone
and the “Public Internet” Zone
what is "public internet" zone?
what is "aws public" zone?
what is "aws private" zone?
how to access services in "aws private" zone?
how aws private services access services in "aws public" zone?
how can on-premise access "aws private" zone?
AWS Global Infrastructure (14:53)
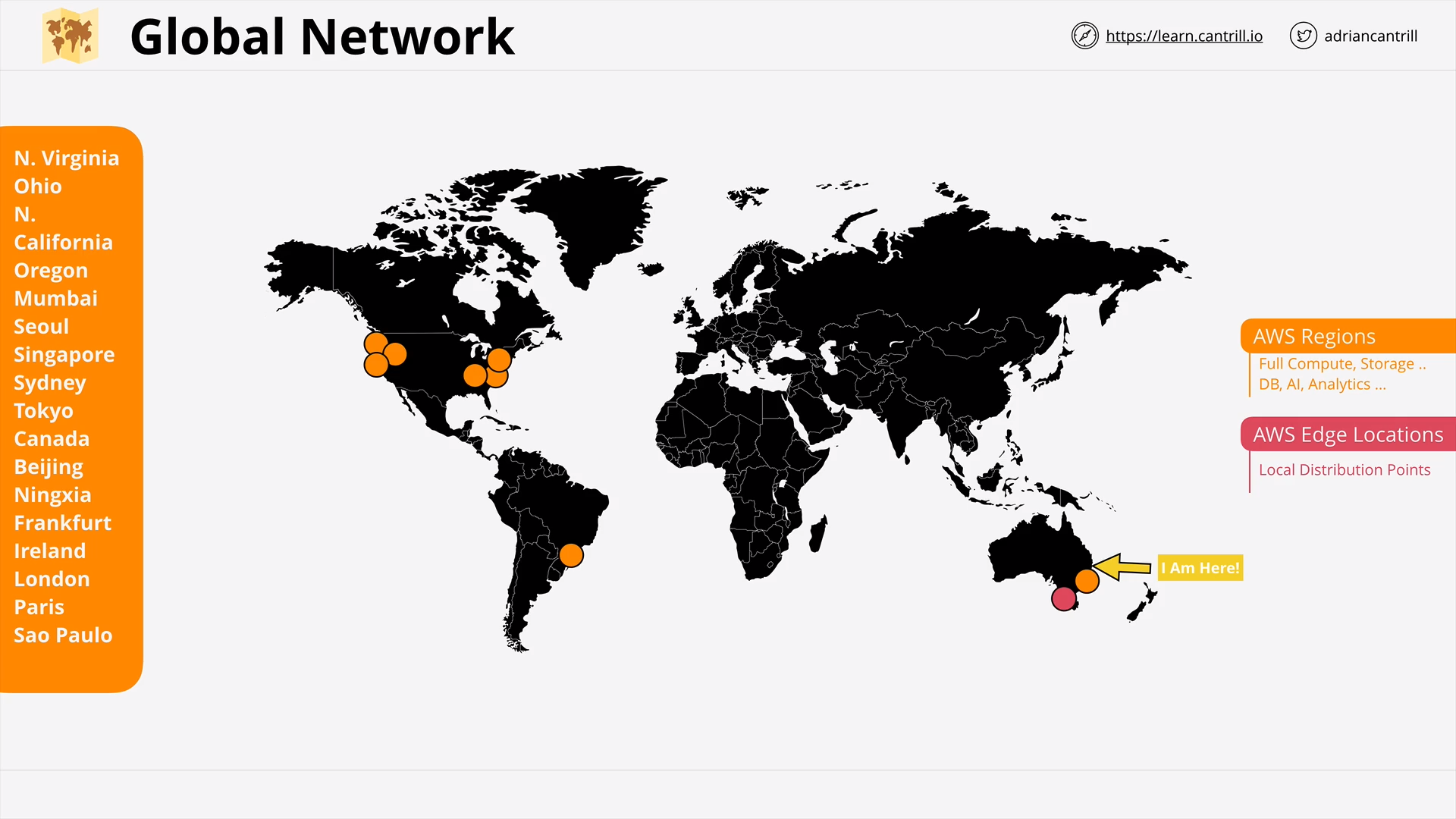 AWS Regions vs Edge Locations
AWS Regions vs Edge Locations
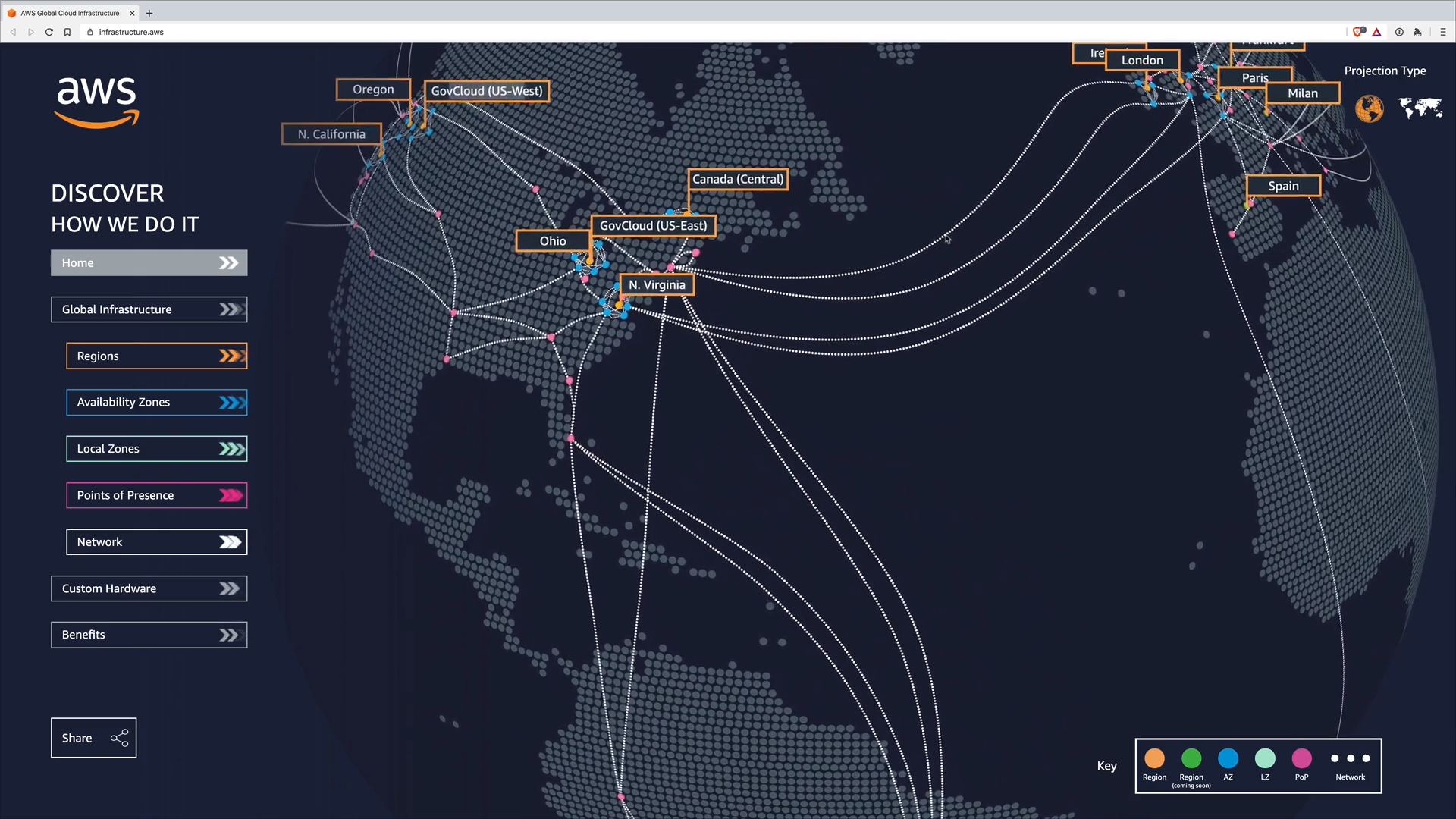
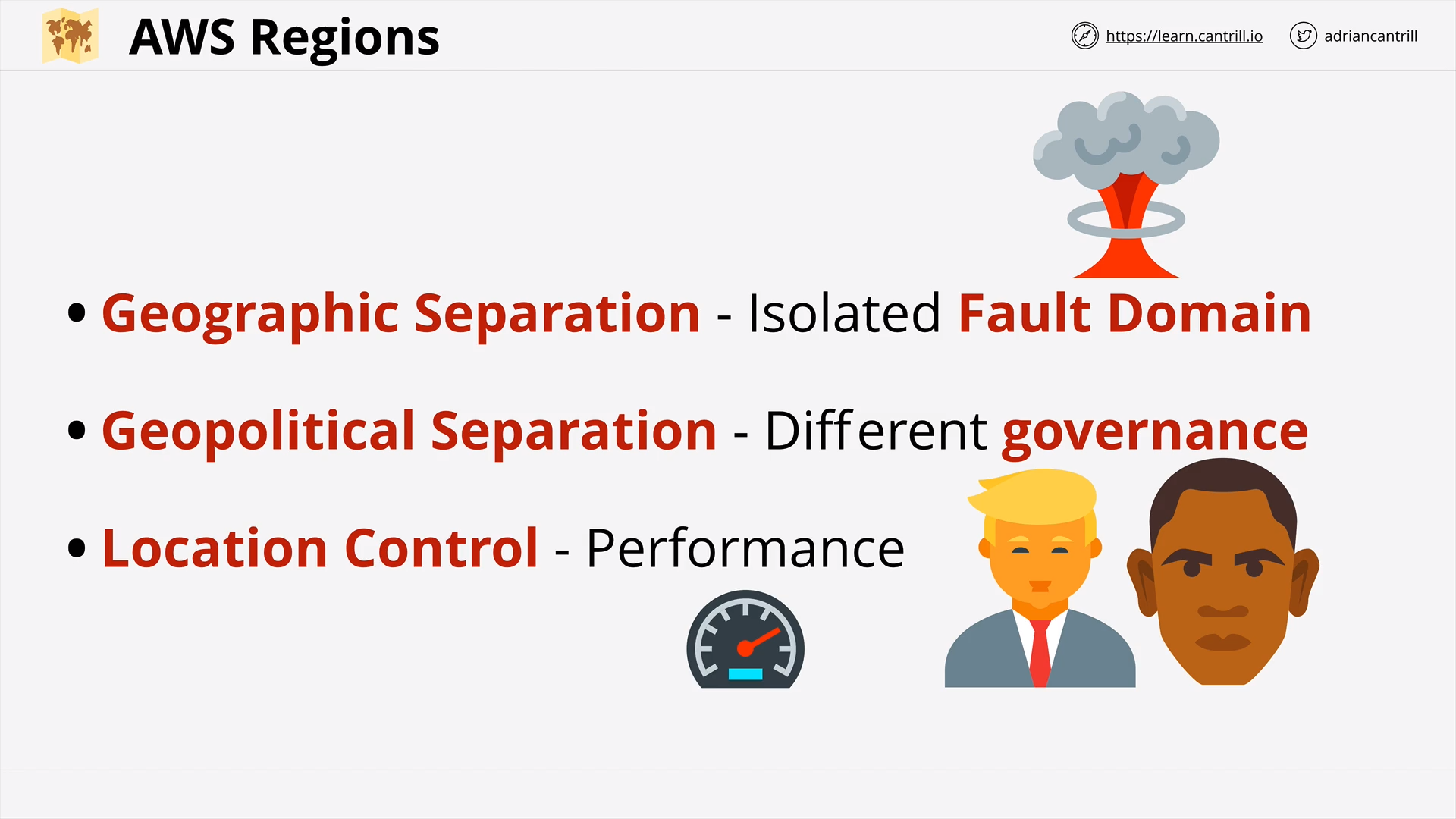 AWS Regions - Benefits
AWS Regions - Benefits
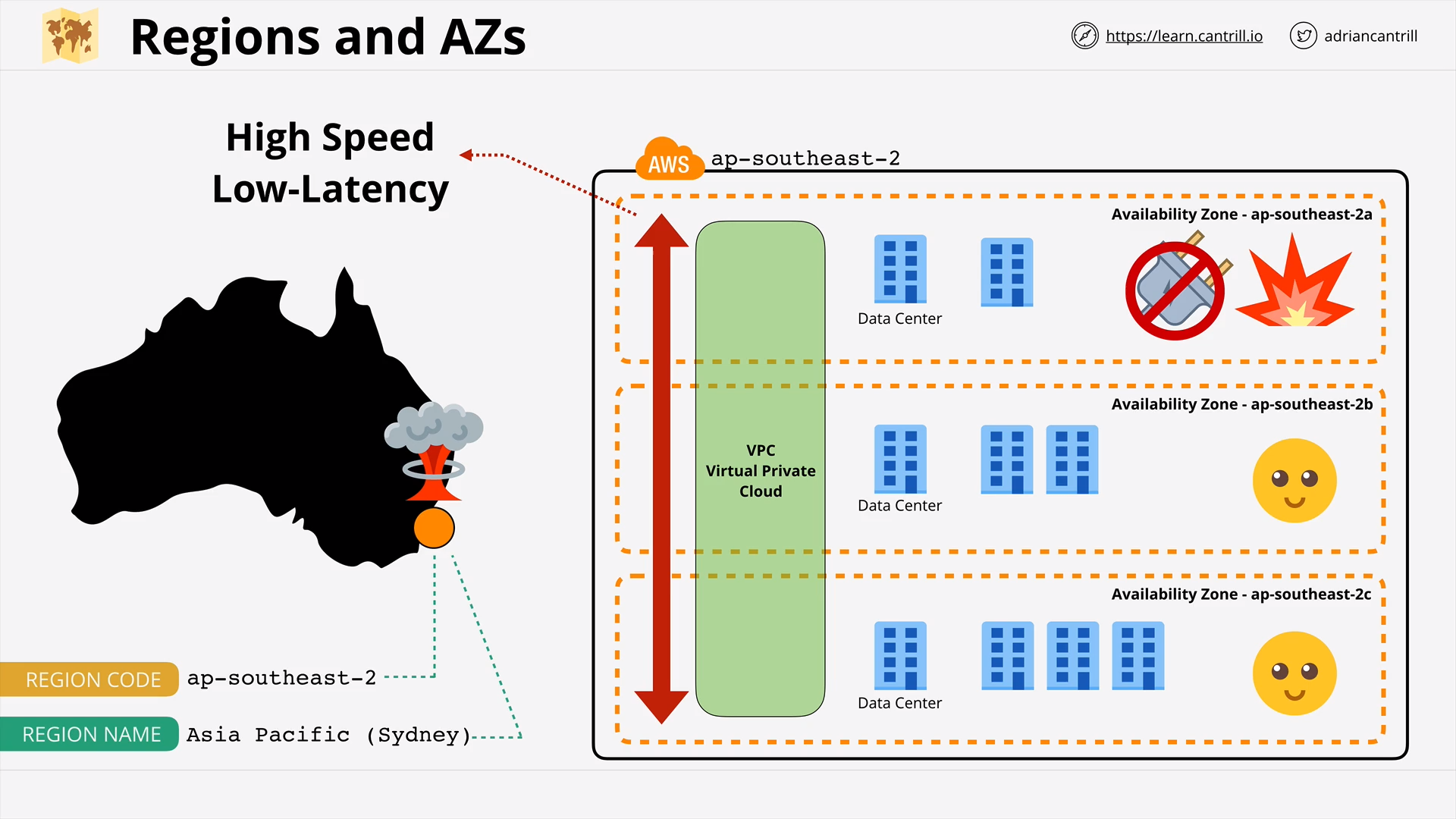 AWS Regions vs Availability Zones (AZs)
AWS Regions vs Availability Zones (AZs)
aws region code vs region name
| Region Code | Region Name |
|---|---|
| US East (N. Virginia) | us-east-1 |
| Asia Pacific (Singapore) | ap-southeast-1 |
how many data centers can be in a az?
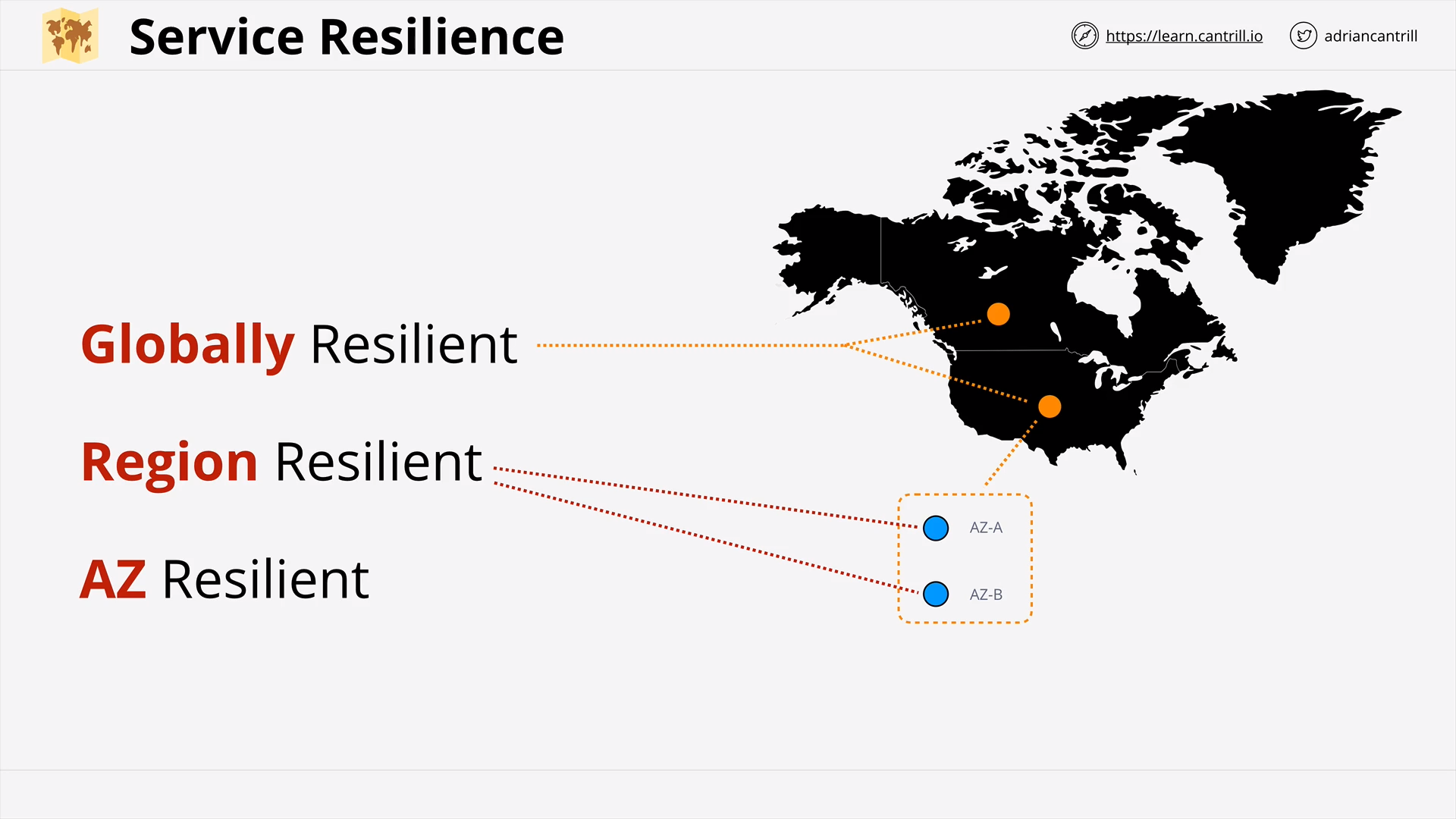 Service Resilient
Service Resilient
| Resilient | Example |
|---|---|
| Global Resilient | IAM, Route 53 |
| Region Resilient | VPC, RDS Multi-AZ |
| AZ Resilient | EC2, RDS Single-AZ |
AWS Default Virtual Private Cloud (VPC) (15:19)
 VPC Basics
VPC Basics
what is a vpc?
Virtual Private Cloud (VPC) is a virtual network inside AWS.
How many types of VPC are there?
There are 2 types of VPC: default VPC & custom VPC.
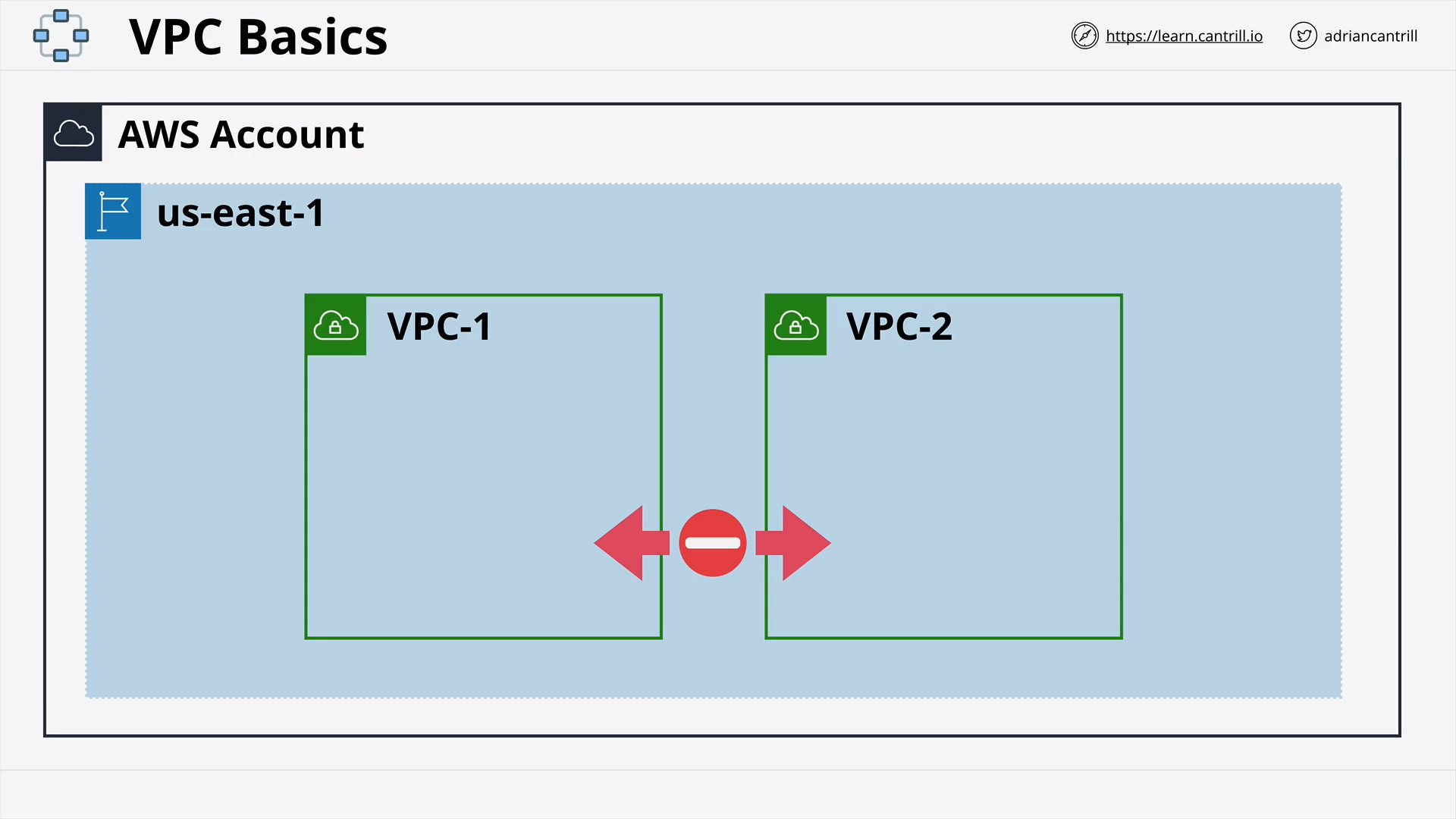
what is the default state of a vpc?
By default,a VPC is private and isolated
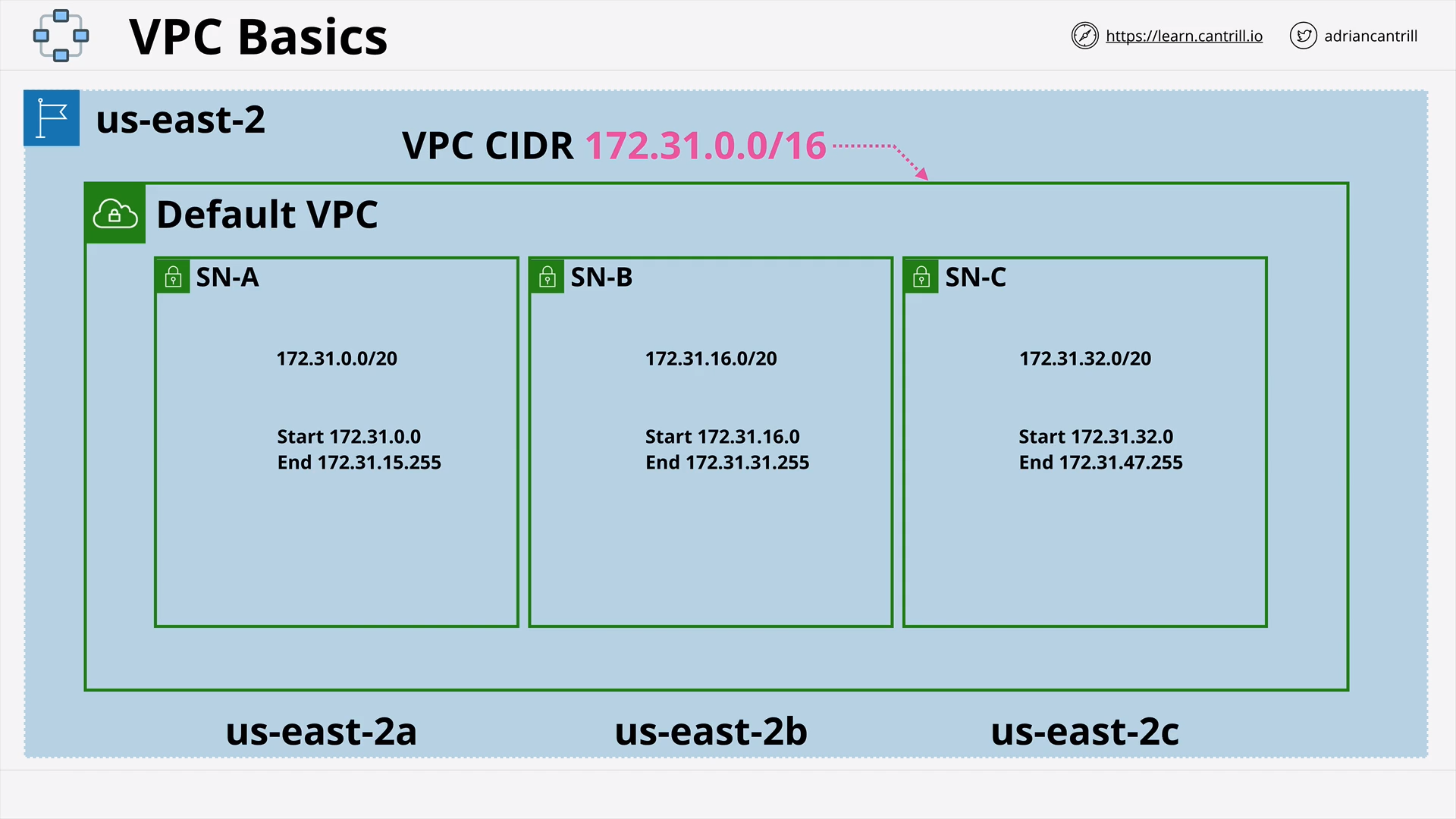
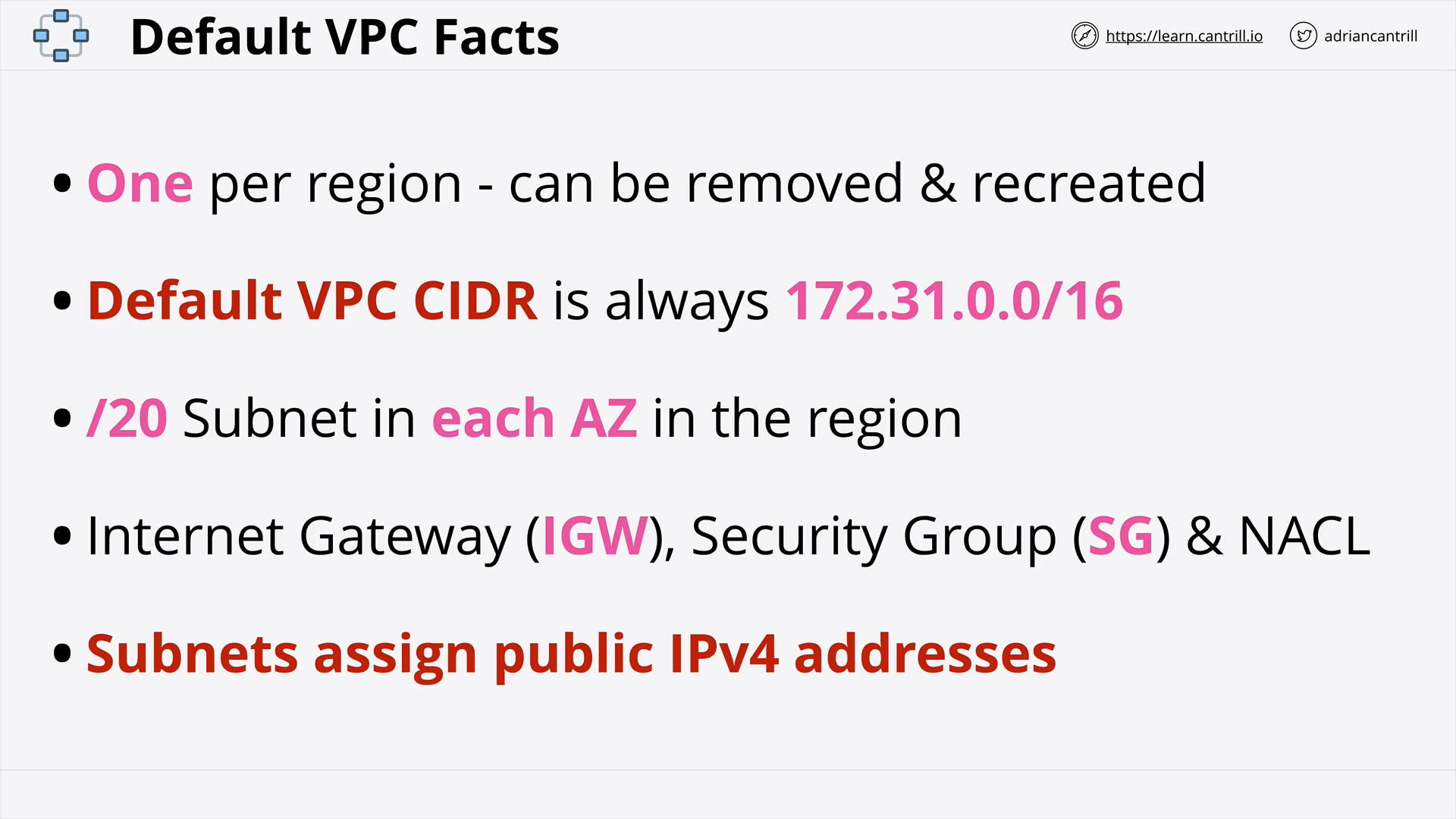
what is the default vpc?
The VPC that AWS created automatically for each region.
can we delete the default vpc?
We can delete the default VPC, and re-create in the Web Console.
what is the cidr of default vpc?
172.31.0.0/16 👉 65535 IPs 👉 16 subnets of /20
for the default vpc, how many subnets are there in each az in each region?
The default VPC has 1 subnet for each of its AZ.
They are /20 subnets - 4091 (2^12) available IPs
[x] TODO: DEMO - Delete and create default VPC
Elastic Compute Cloud (EC2) Basics (14:46)
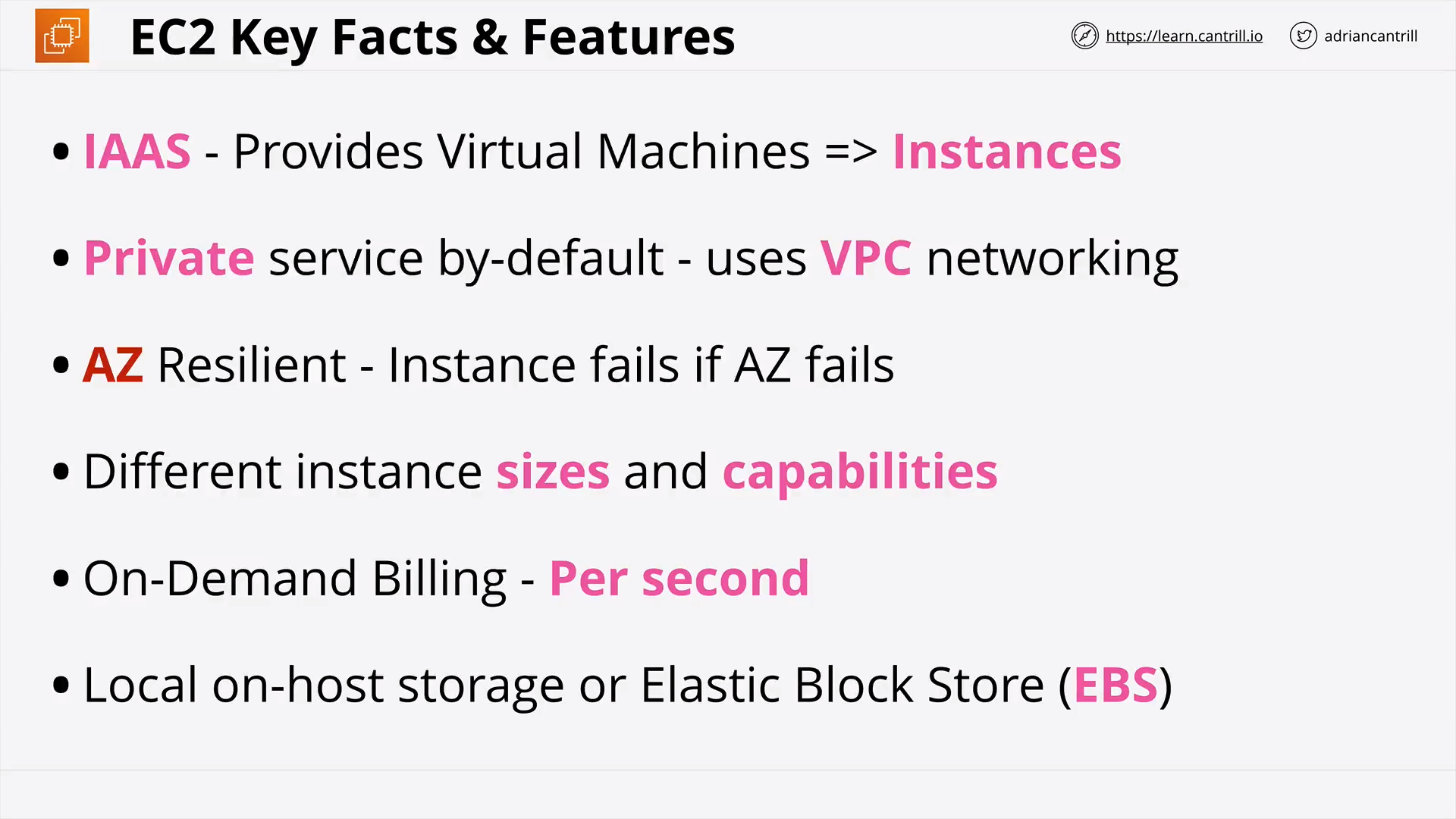 EC2 Features
EC2 Features
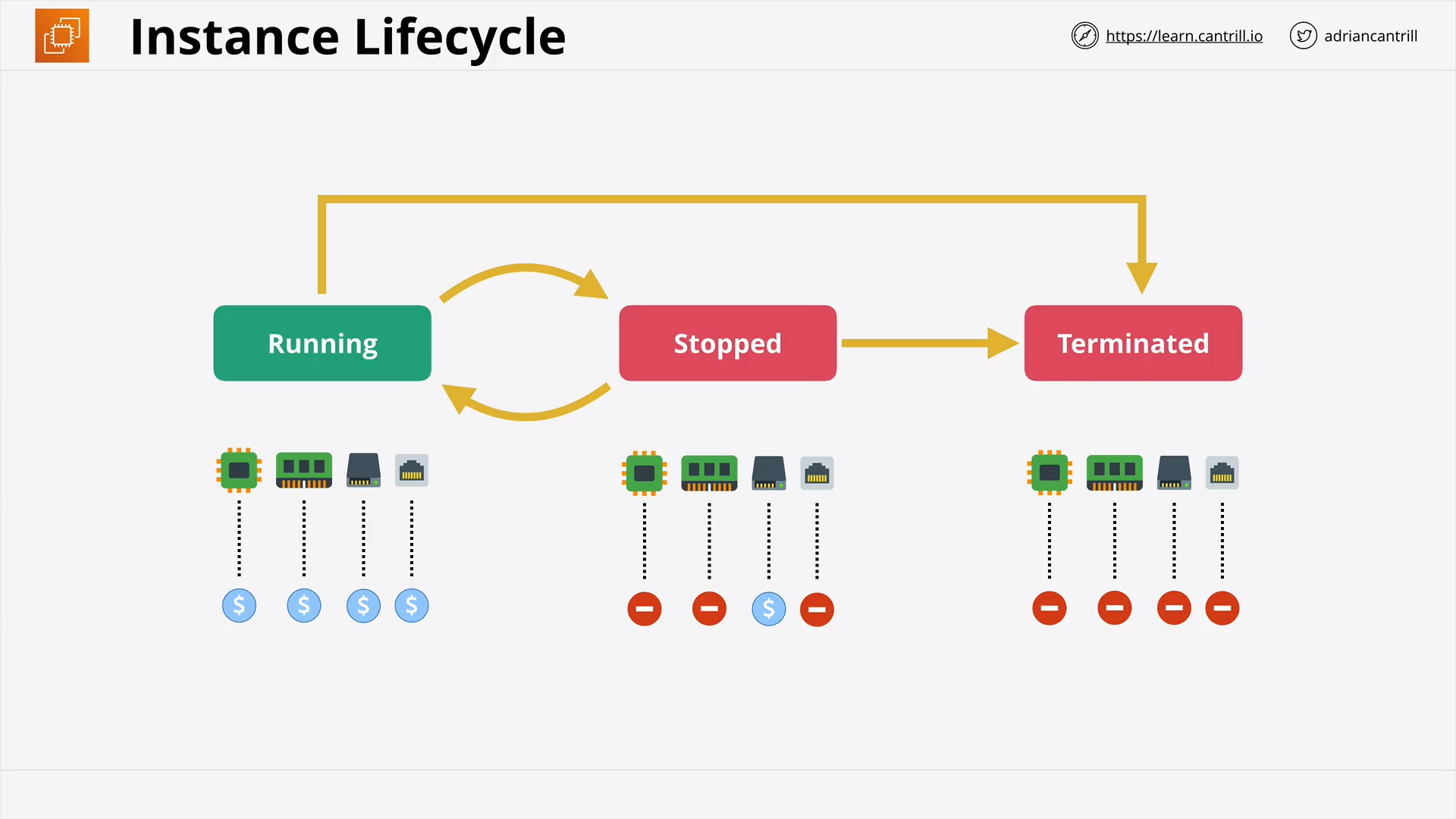 EC2 - Instance Lifecycle
EC2 - Instance Lifecycle
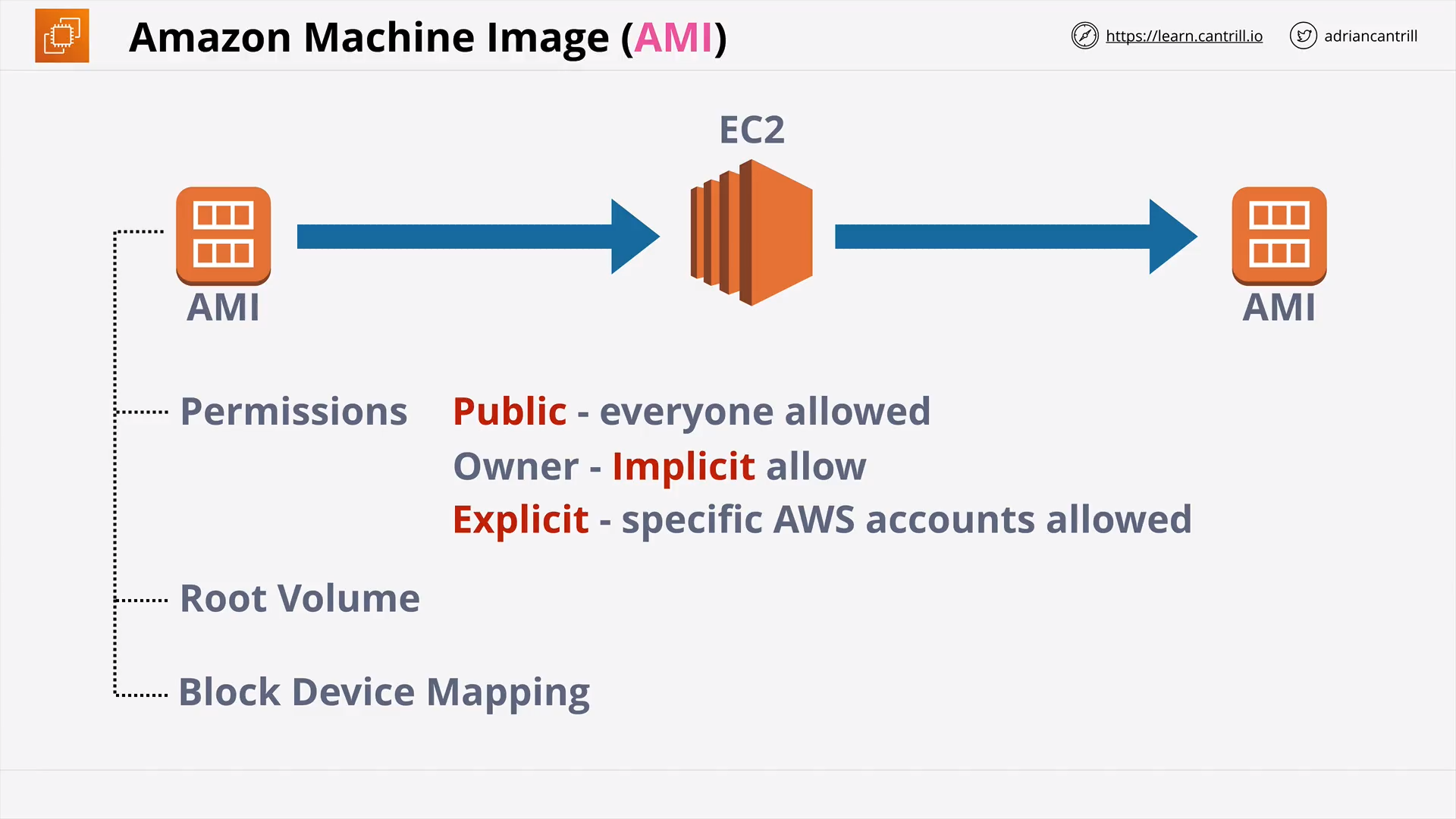 EC2 - AMI
EC2 - AMI
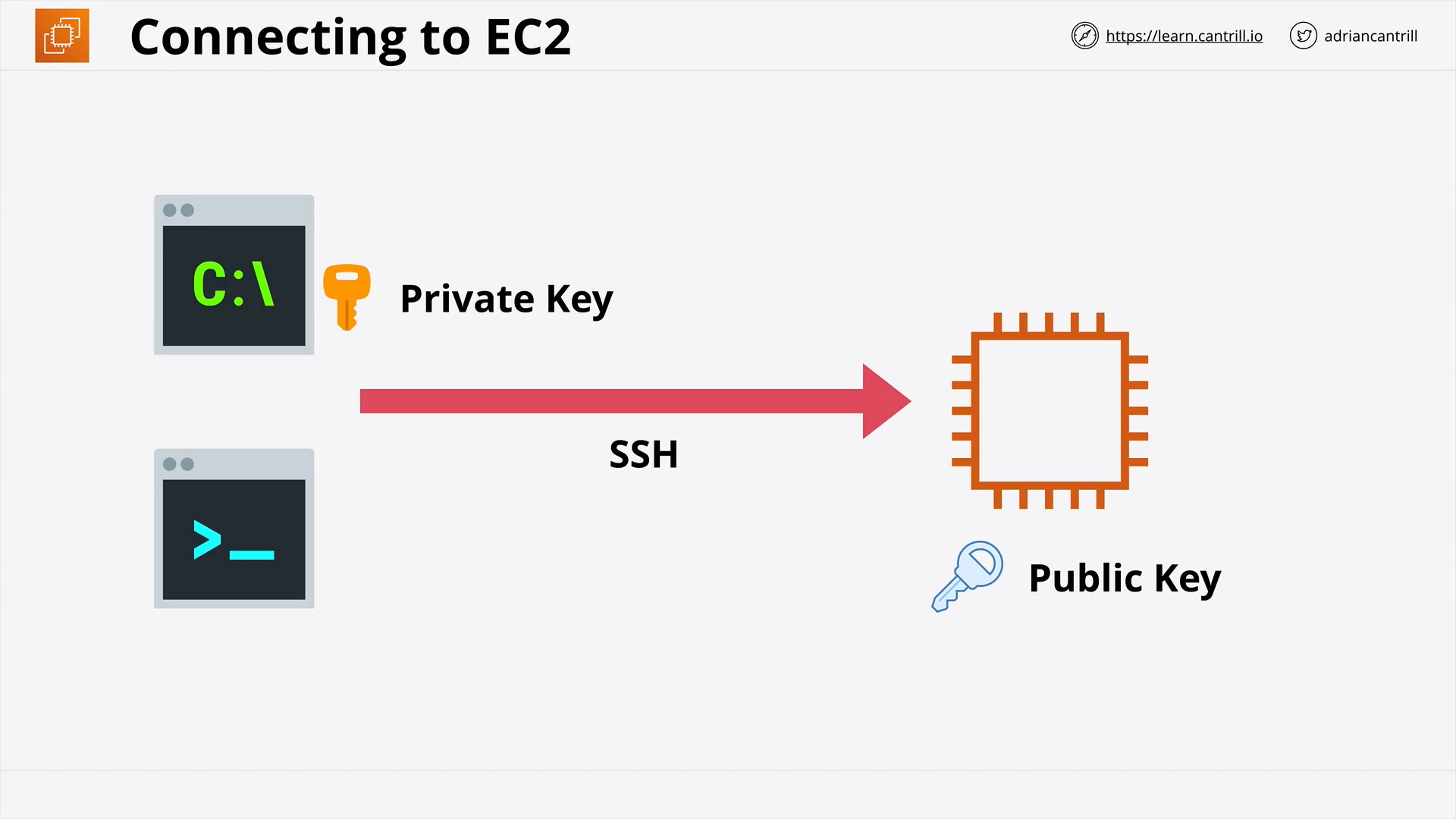 EC2 - Connecting to EC2
EC2 - Connecting to EC2
TODO: DEMO - Connect to an EC2 instance
[DEMO] My First EC2 Instance - PART1 (10:58)
[DEMO] My First EC2 Instance - PART2 (9:40)
Simple Storage Service (S3) Basics (15:48)
_Basic.png) S3 - 101
S3 - 101
what is the resilient of s3?
_Basic.png) S3 - Objects
S3 - Objects
what is s3 object?
_Basic.png) S3 - Buckets
S3 - Buckets
what is s3 bucket?
What is the structure of S3 bucket?
_Basic.png) S3 - Summary
S3 - Summary
what is the limit of s3 object?
What is the limit of S3 bucket?
_Basic.png) S3 - Pattern & Anti-pattern
S3 - Pattern & Anti-pattern
what is the type of s3 store?
[DEMO] My First S3 Bucket (18:34)
TODO: DEMO - S3
CloudFormation (CFN) Basics (12:28)
_Basics__lea.png) CFN - Template Format
CFN - Template Format
_Basics__lea.png) CFN Template - Resources
CFN Template - Resources
_Basics__lea.png) CFN Template - Descriptions
CFN Template - Descriptions
_Basics__lea.png) CFN Template - Metadata
CFN Template - Metadata
_Basics__lea.png) CFN Template - Parameters
CFN Template - Parameters
_Basics__lea.png) CFN Template - Mappings
CFN Template - Mappings
_Basics__lea.png) CFN Template - Conditions
CFN Template - Conditions
_Basics__lea.png) CFN Template - Outputs
CFN Template - Outputs
_Basics__lea.png) CFN - Stack, Logical Resource, Physical Resource
CFN - Stack, Logical Resource, Physical Resource
_Basics__lea.png) CFN - Create/Update/Delete Stack
CFN - Create/Update/Delete Stack
[DEMO] Simple Automation With CloudFormation (CFN) (15:52)
CloudWatch (CW) Basics (13:45)
 CloudWatch - Metrics, CloudWatch Logs/Events
CloudWatch - Metrics, CloudWatch Logs/Events
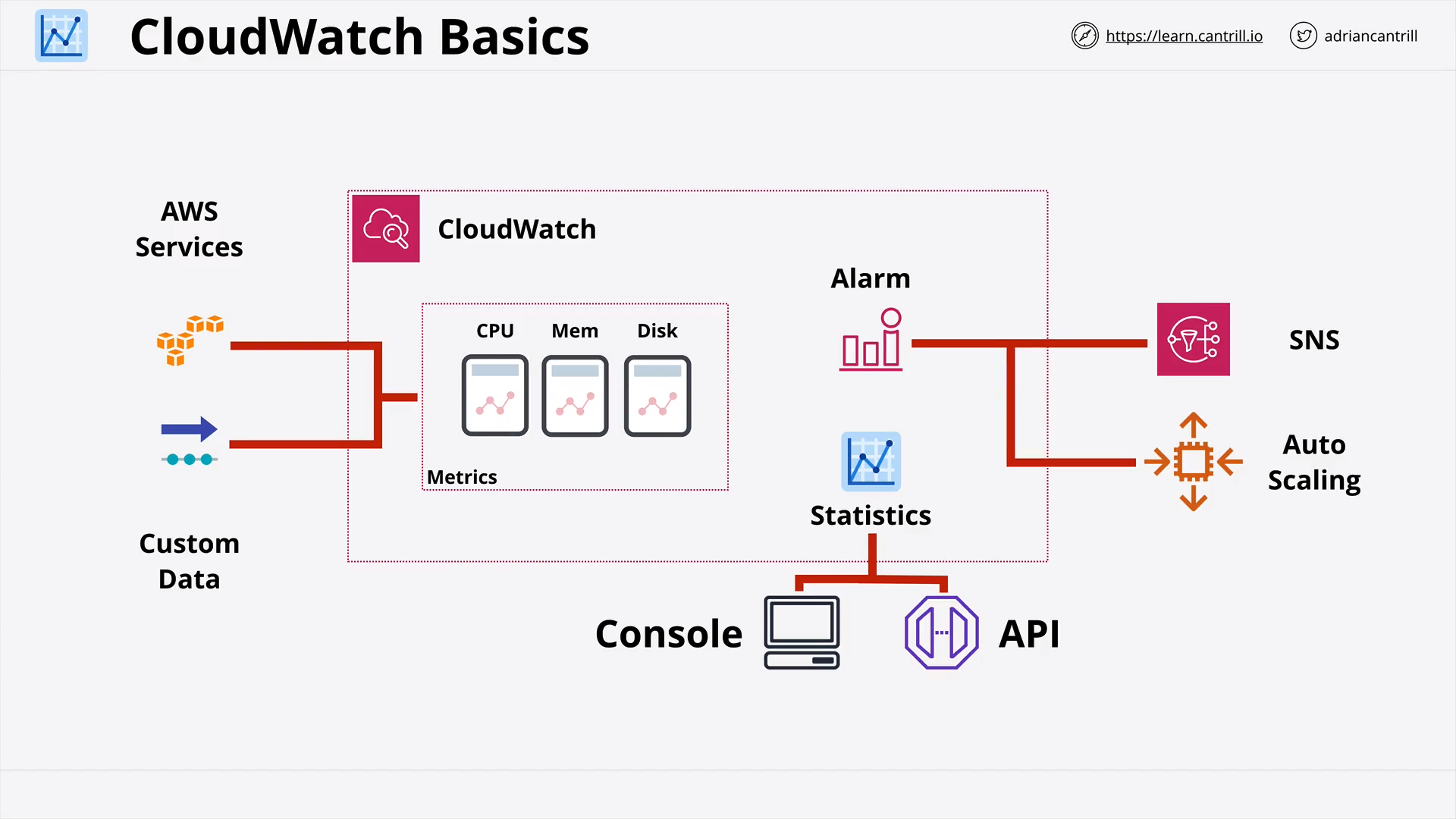 CloudWatch - Architecture
CloudWatch - Architecture
 CloudWatch - Namespace
CloudWatch - Namespace
 CloudWatch - Metric
CloudWatch - Metric
what is metric?
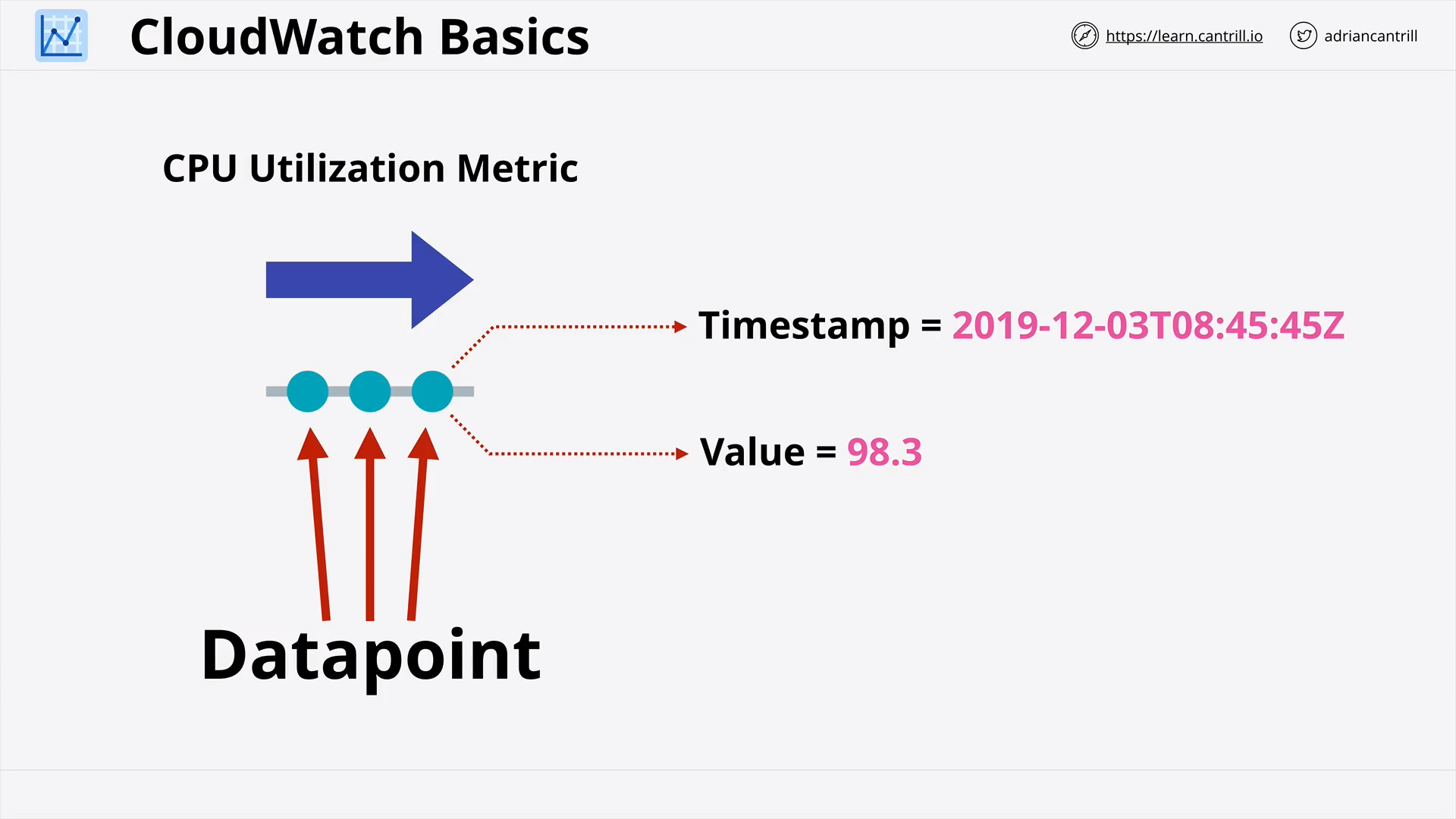 CloudWatch - Datapoint
CloudWatch - Datapoint
what is datapoint?
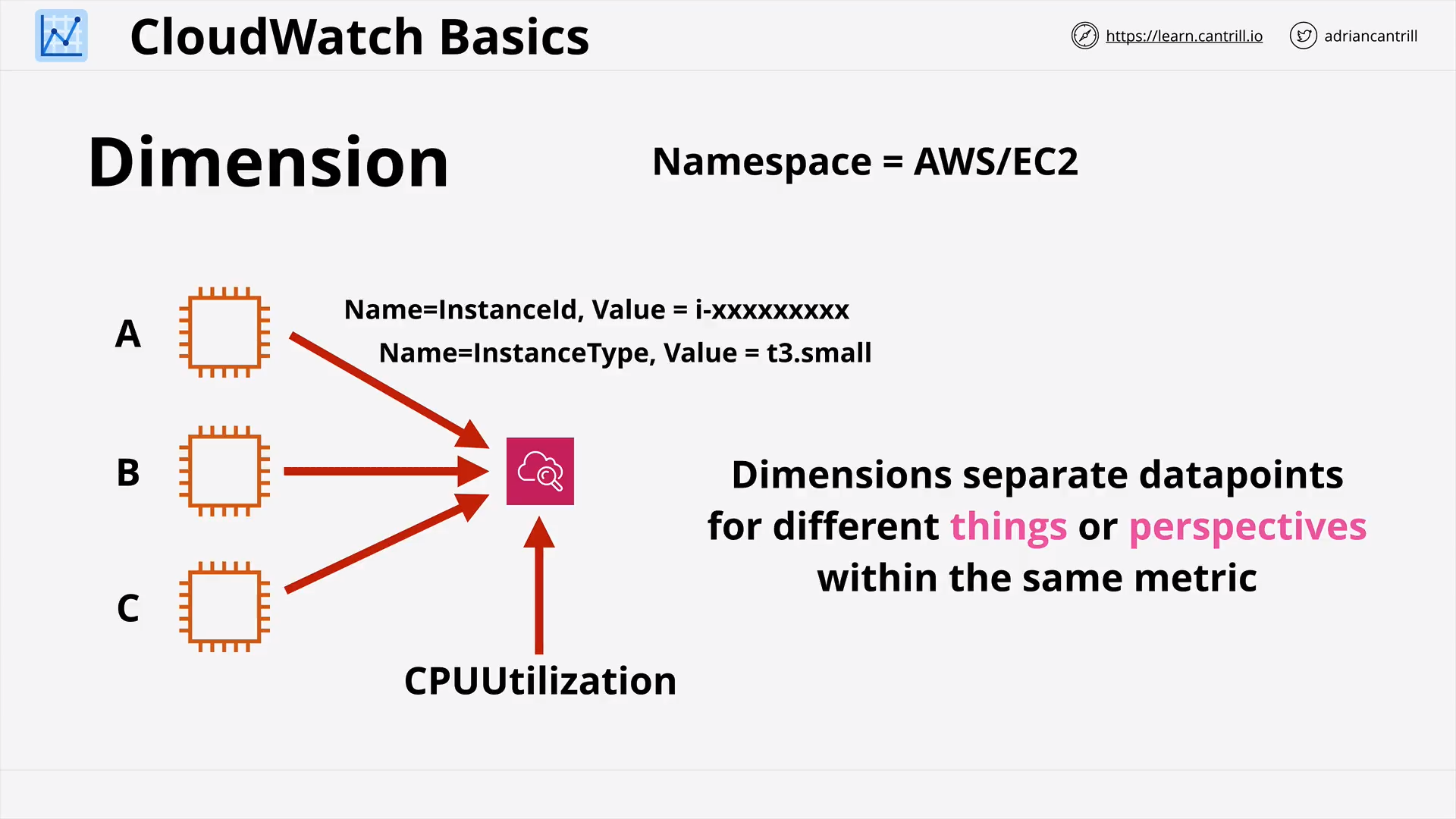 CloudWatch - Dimension
CloudWatch - Dimension
what is dimension?
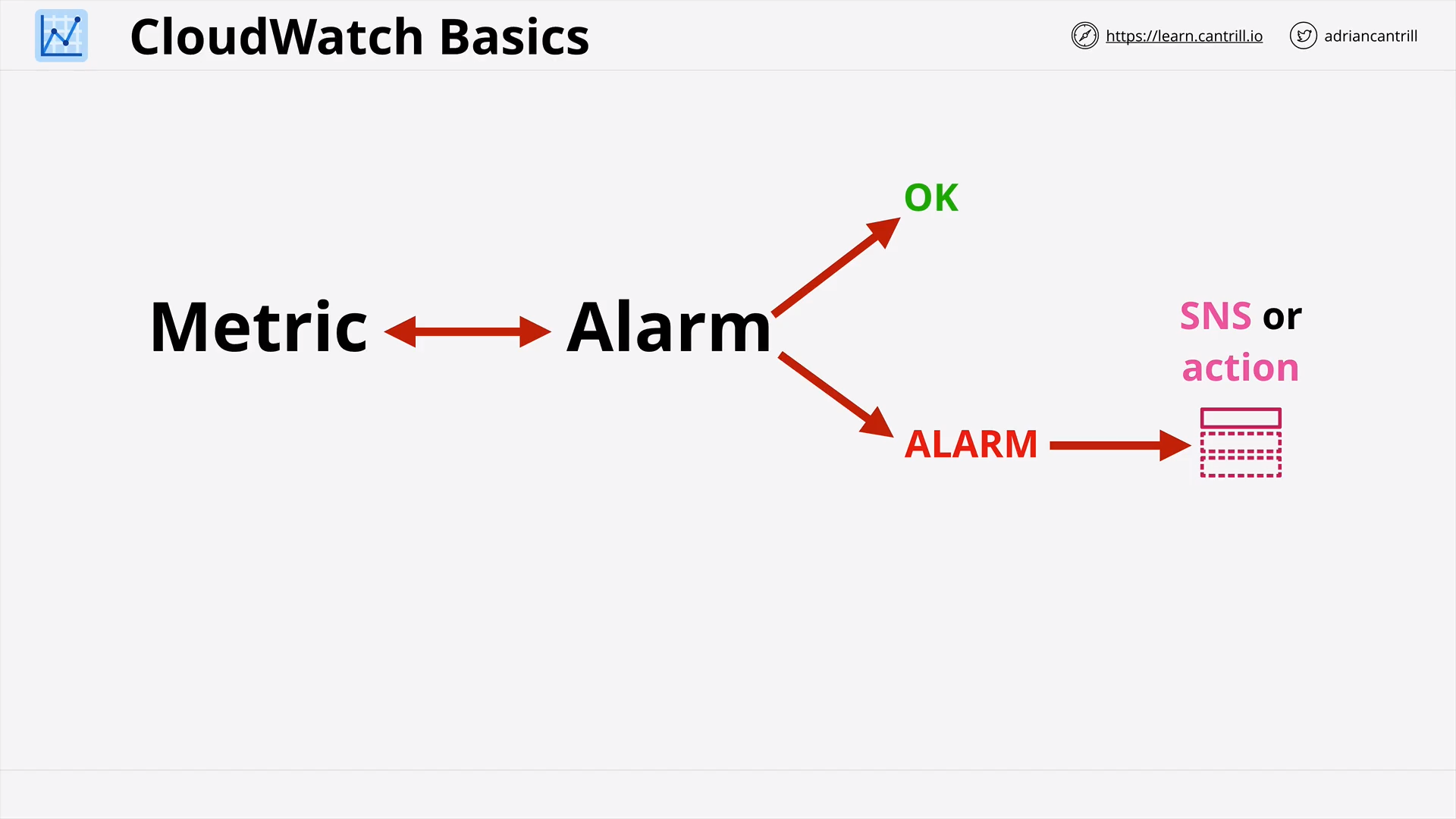 CloudWatch - Alarm
CloudWatch - Alarm
[Demo] Simple Monitoring with Cloudwatch (15:31)
Shared Responsibility Model (6:20)
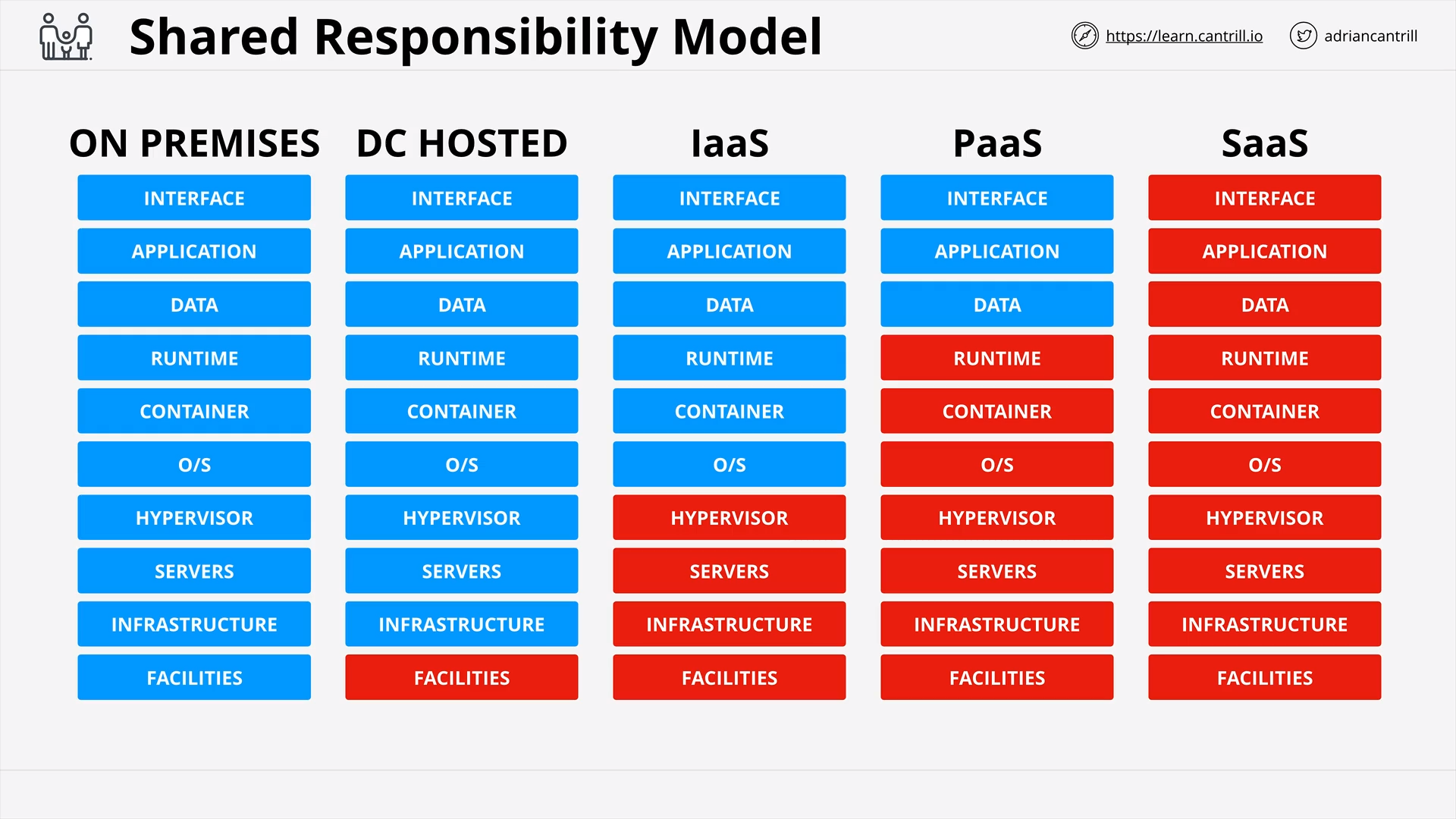 Infrastructure Stack
Infrastructure Stack
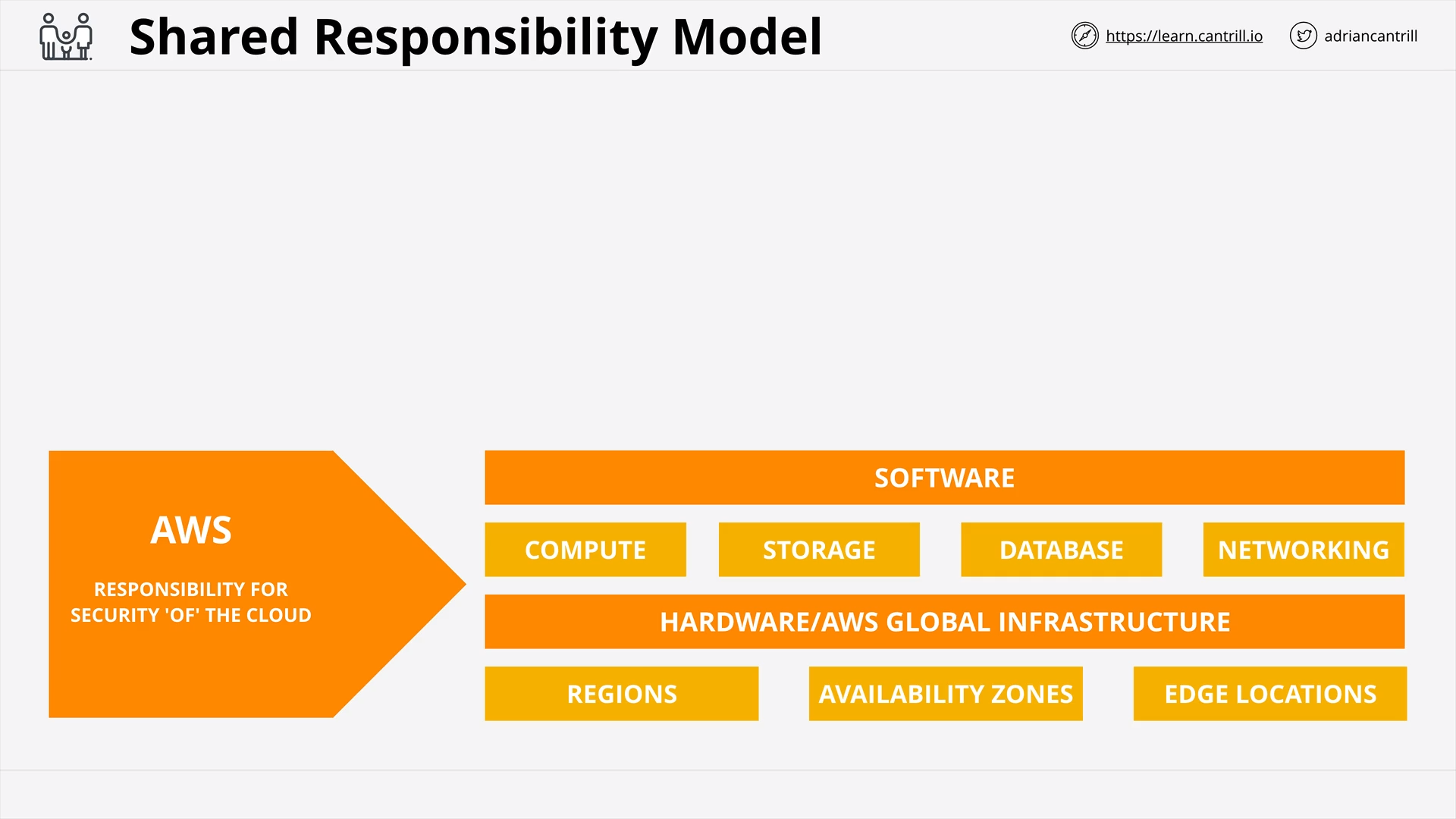 AWS: responsibility for security OF the cloud
AWS: responsibility for security OF the cloud
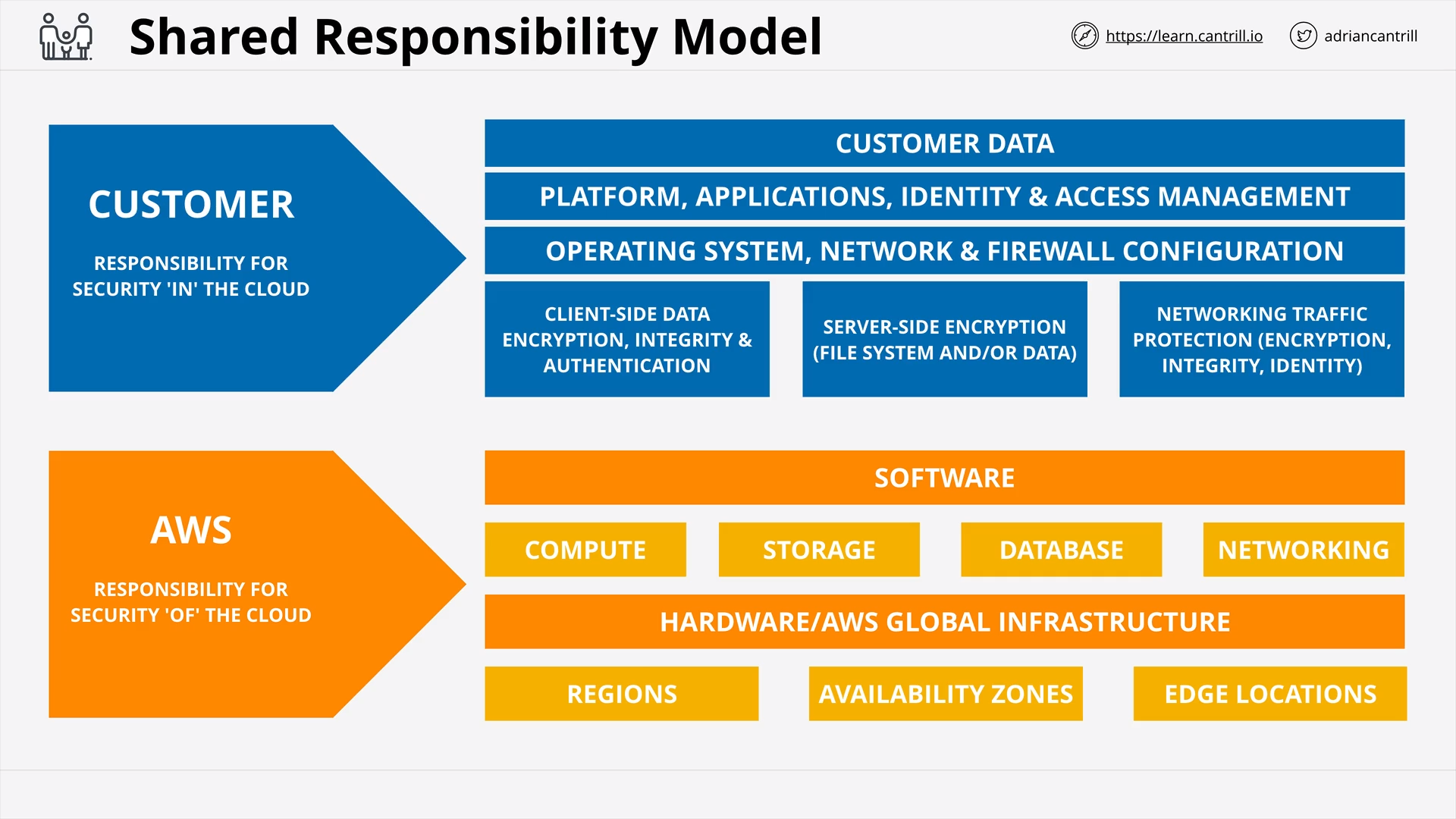 CUSTOMER: responsibility for security IN the cloud
CUSTOMER: responsibility for security IN the cloud
High-Availability vs Fault-Tolerance vs Disaster Recovery (17:21)
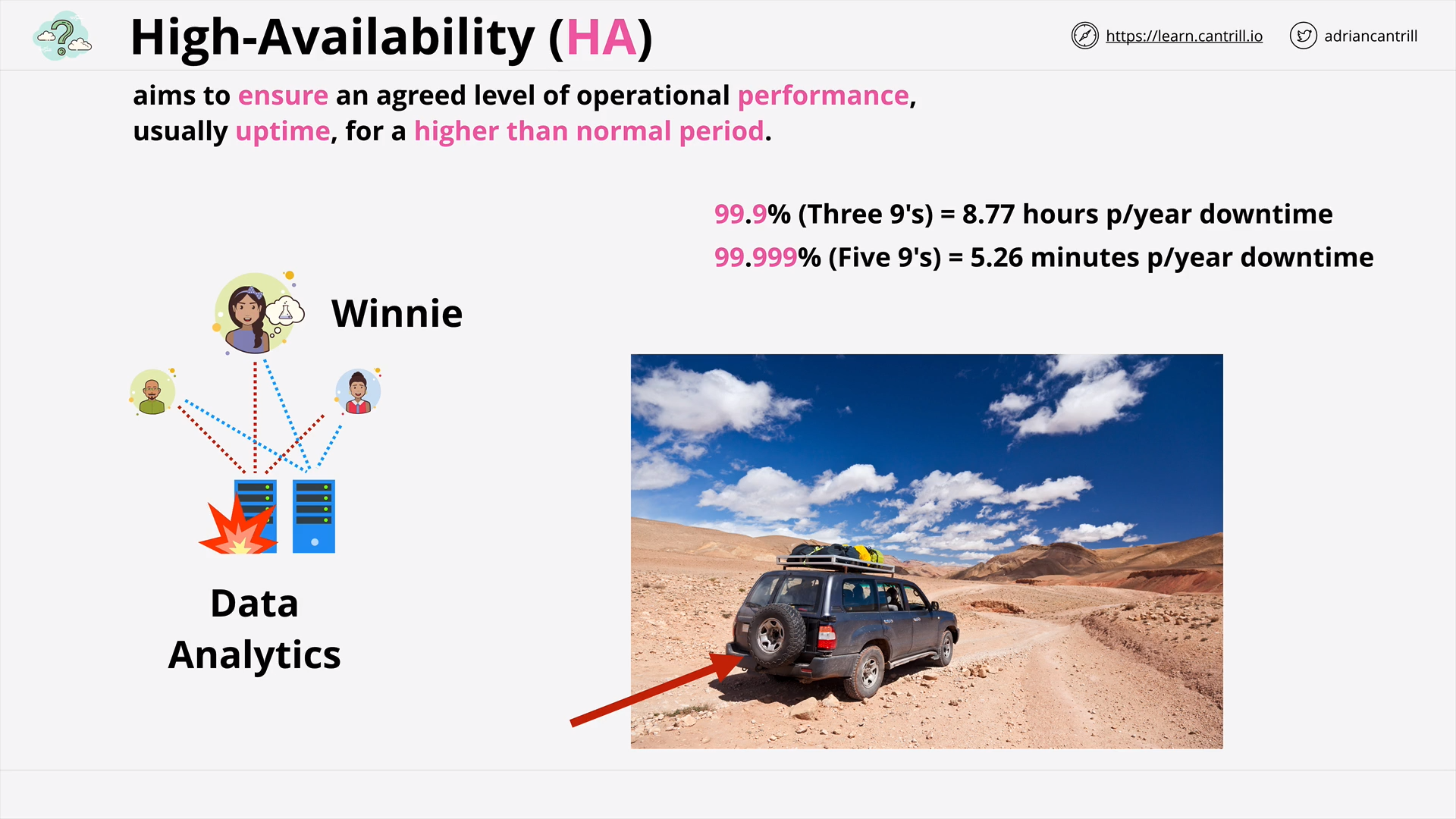 High-Availability (HA)
High-Availability (HA)
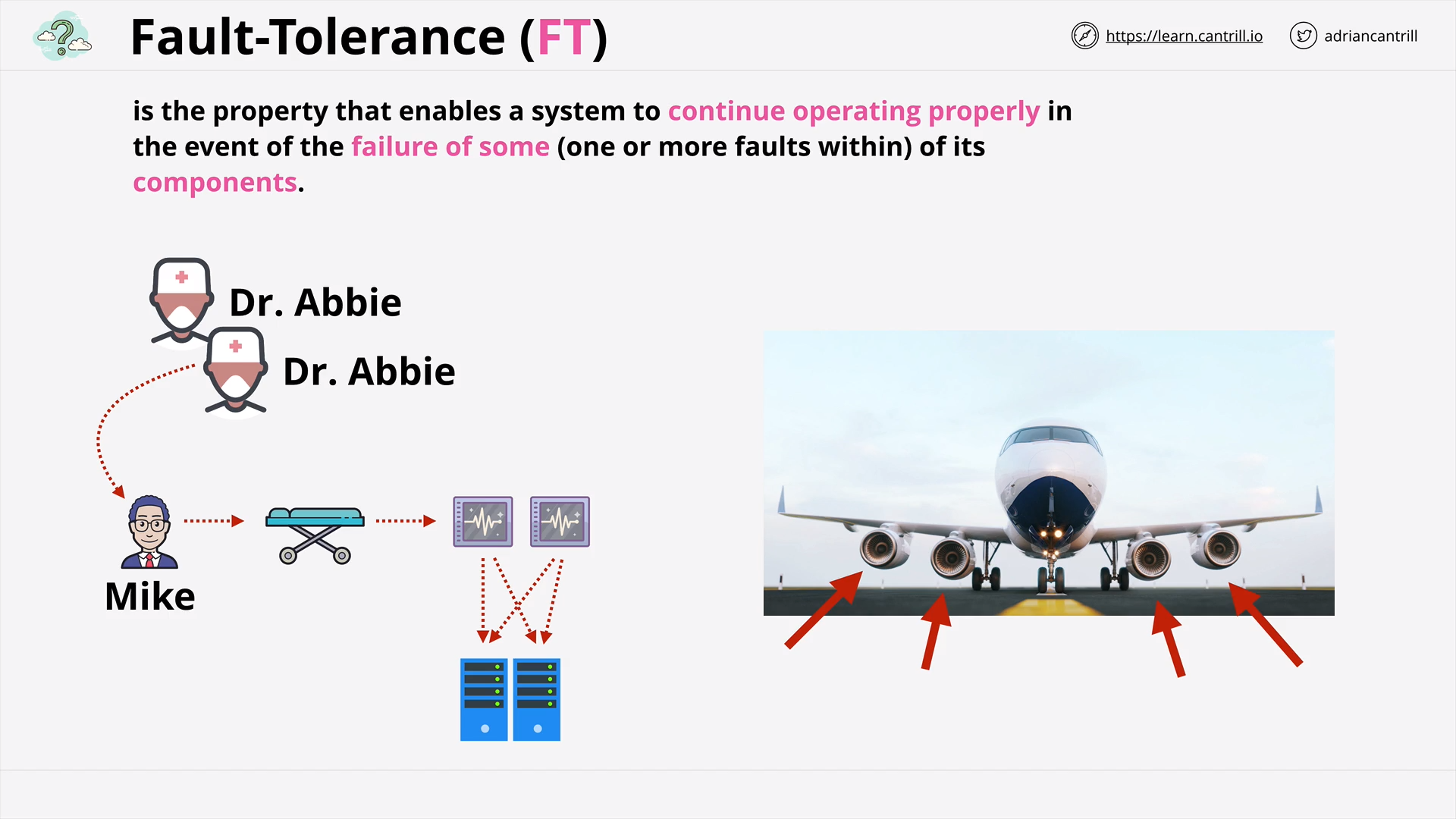 Fault-Tolerance (FT)
Fault-Tolerance (FT)
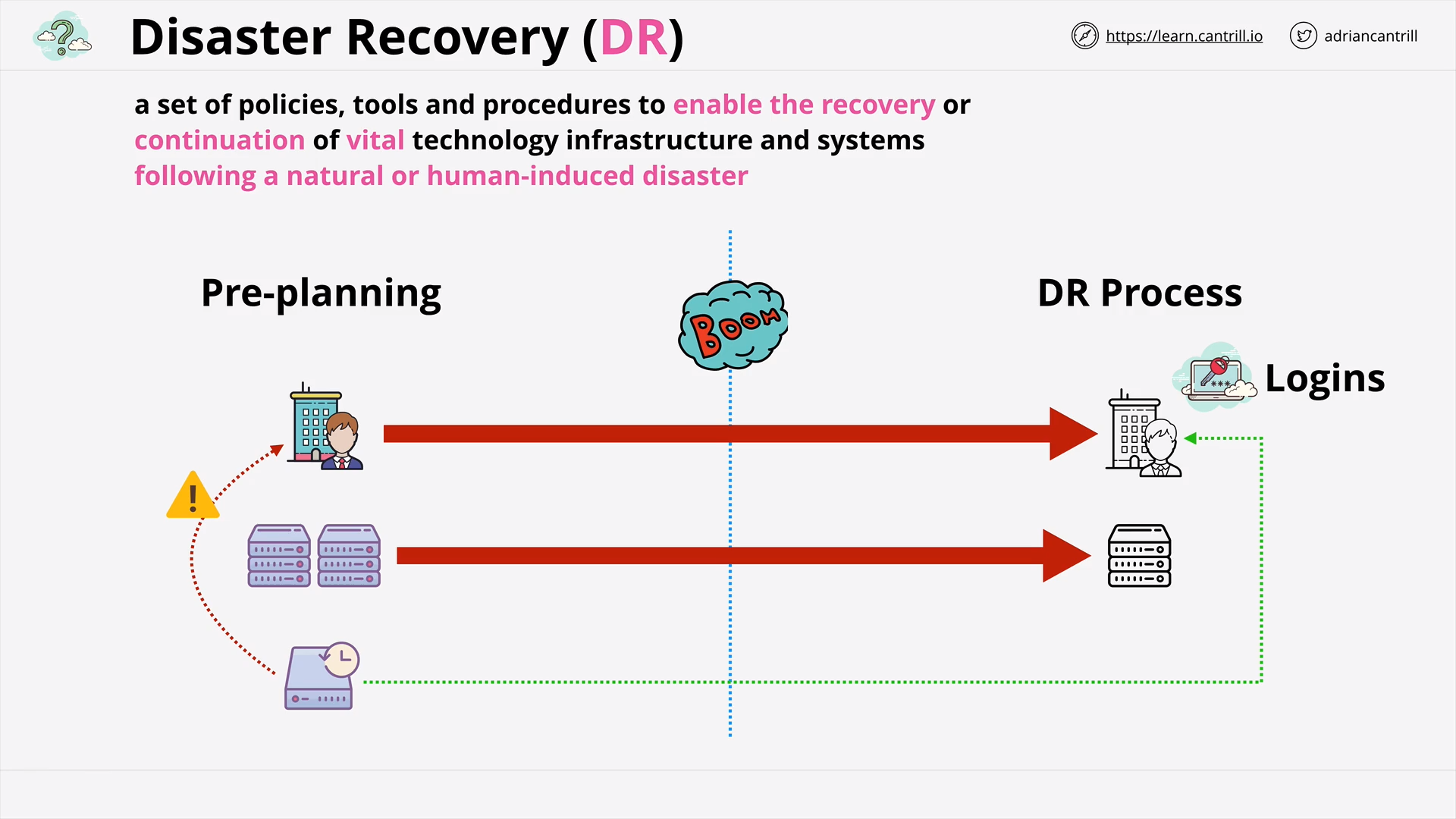 Disaster-Recovery (DR)
Disaster-Recovery (DR)
 HA - FT - DR
HA - FT - DR
ha: ha environment has a minimal service interruption.
FT: FT environment has no service interruption but a significantly higher cost.
Route53 (R53) Fundamentals (6:29)
_Fundamentals__lear.png) Route 53 - Features
Route 53 - Features
_Fundamentals__lear.png) Route 53 - Register Domains
Route 53 - Register Domains
_Fundamentals__lear.png) Route 53 - Hosted Zones
Route 53 - Hosted Zones
[DEMO] Registering a Domain with route53 (9:49)
DNS Record Types (13:25)
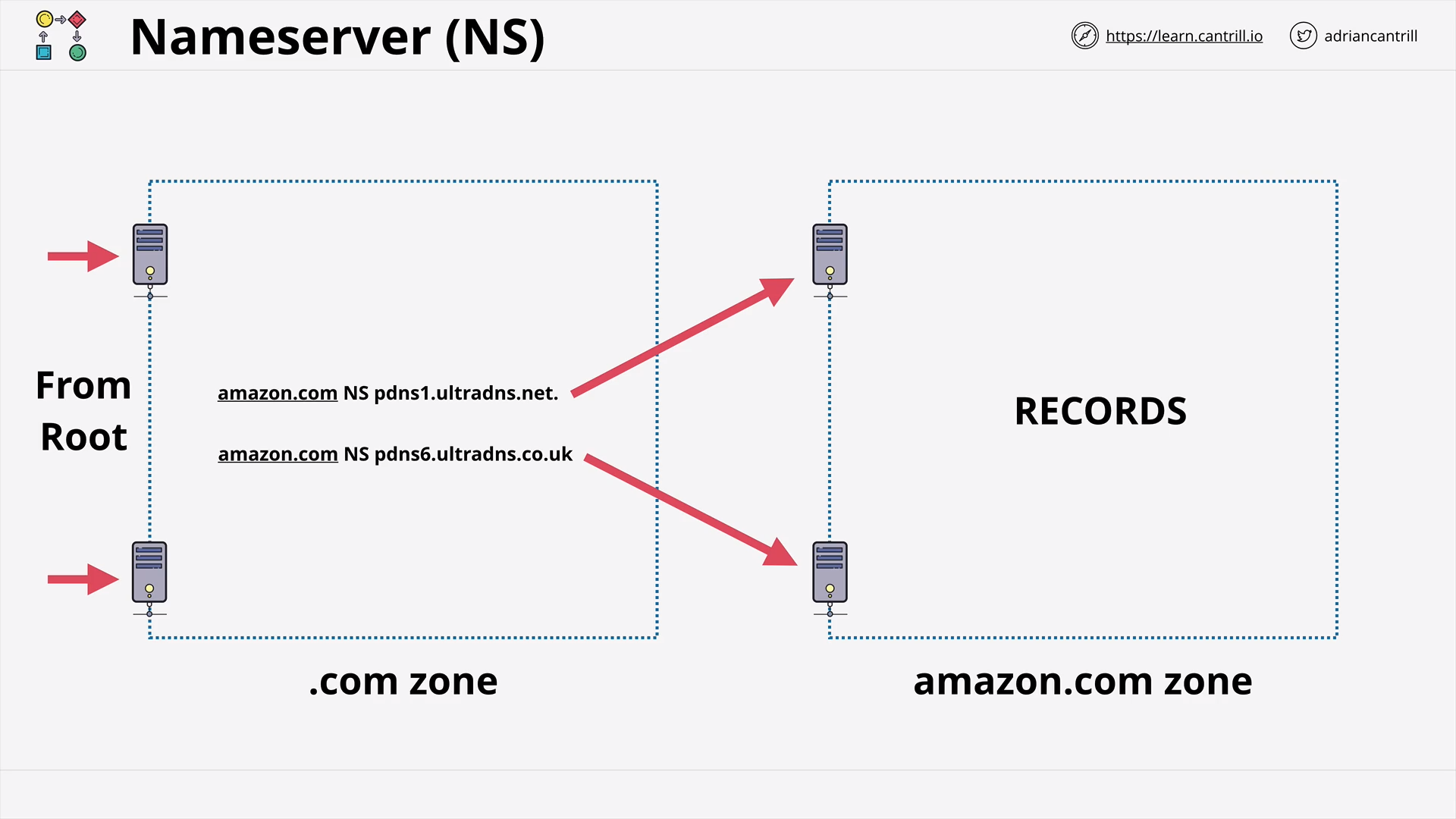 DNS Record - Nameserver (NS) Record
DNS Record - Nameserver (NS) Record
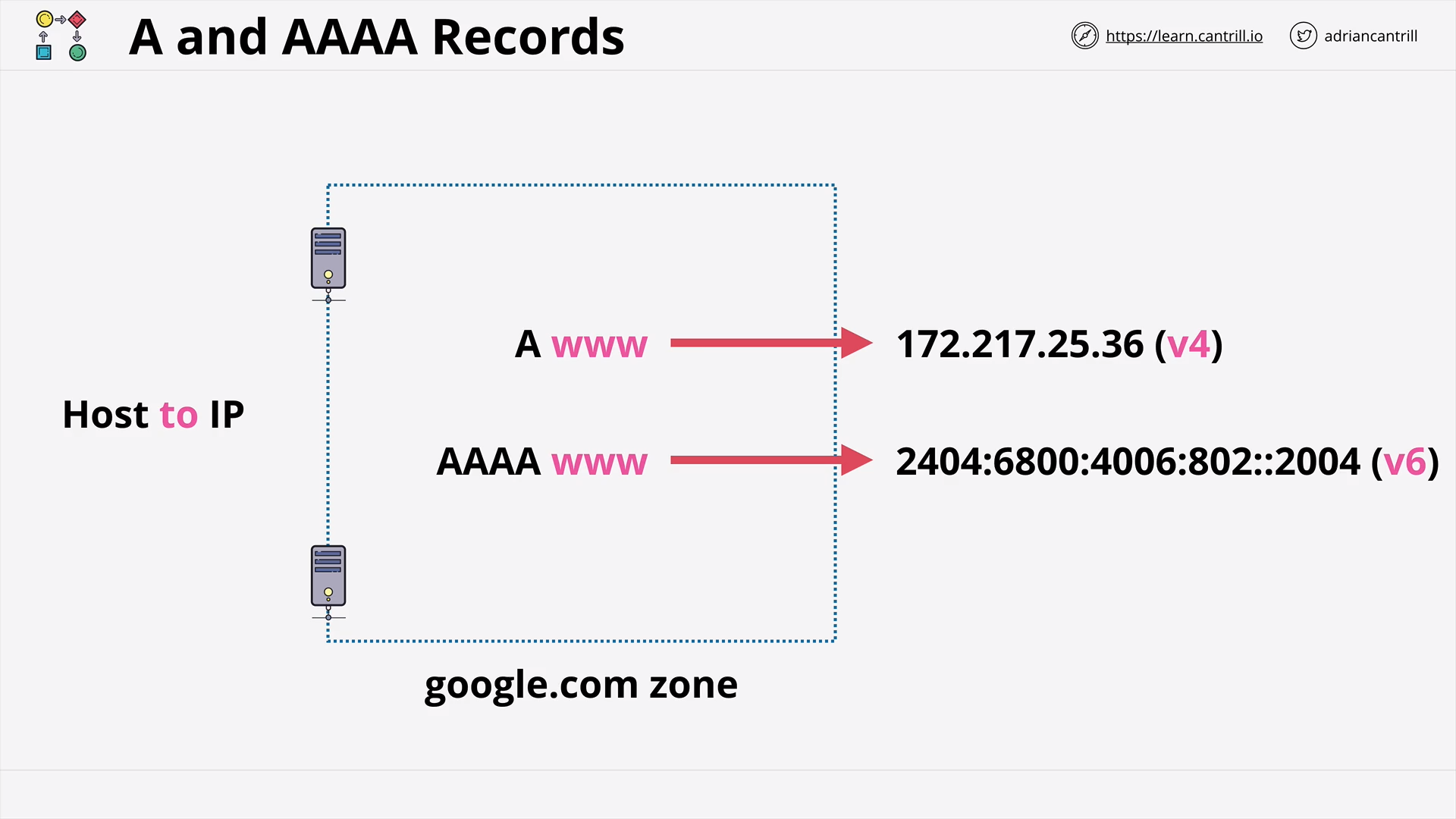 DNS Record - A and AAAA Record
DNS Record - A and AAAA Record
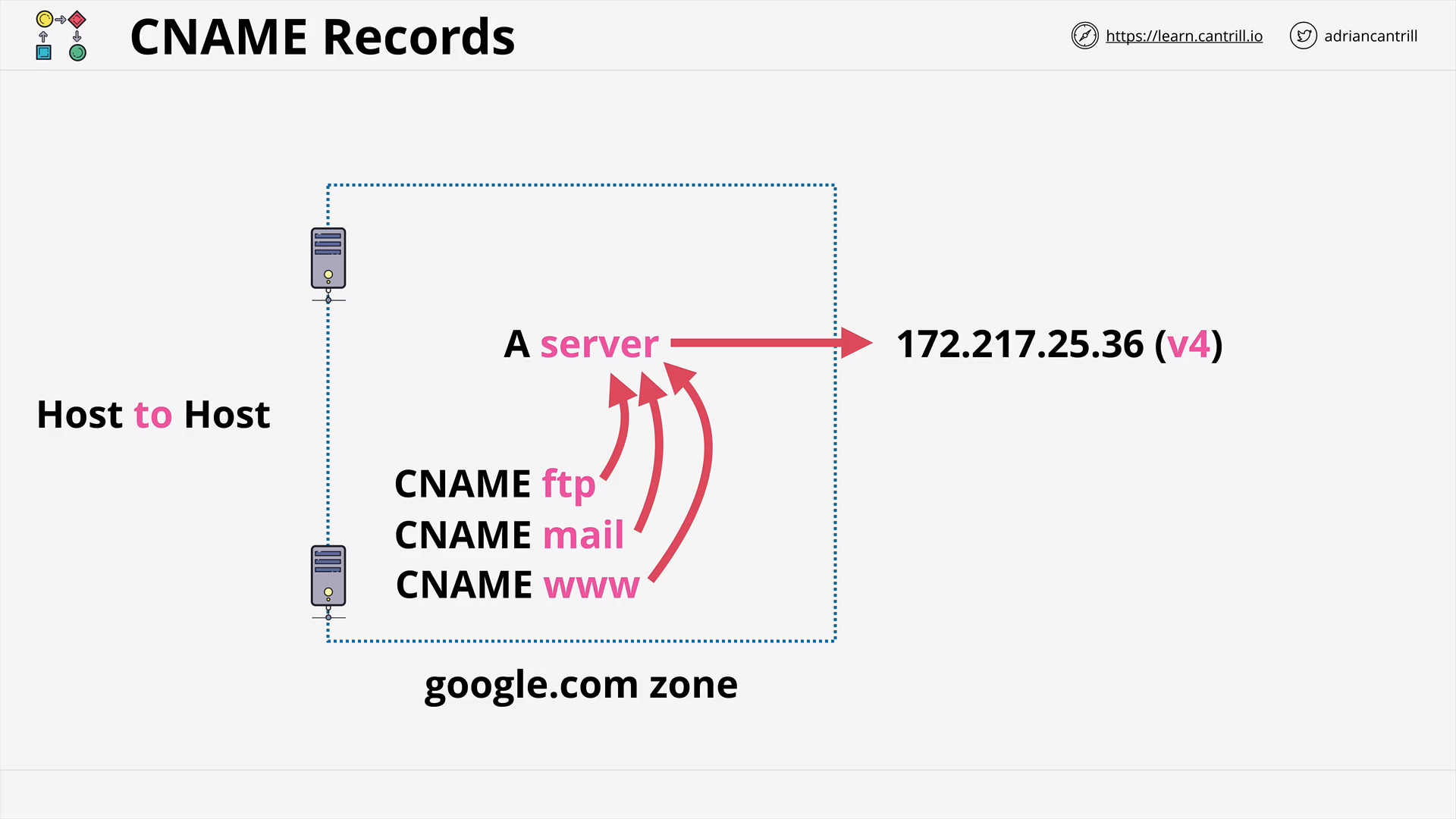 DNS Record - CNAME Record
DNS Record - CNAME Record
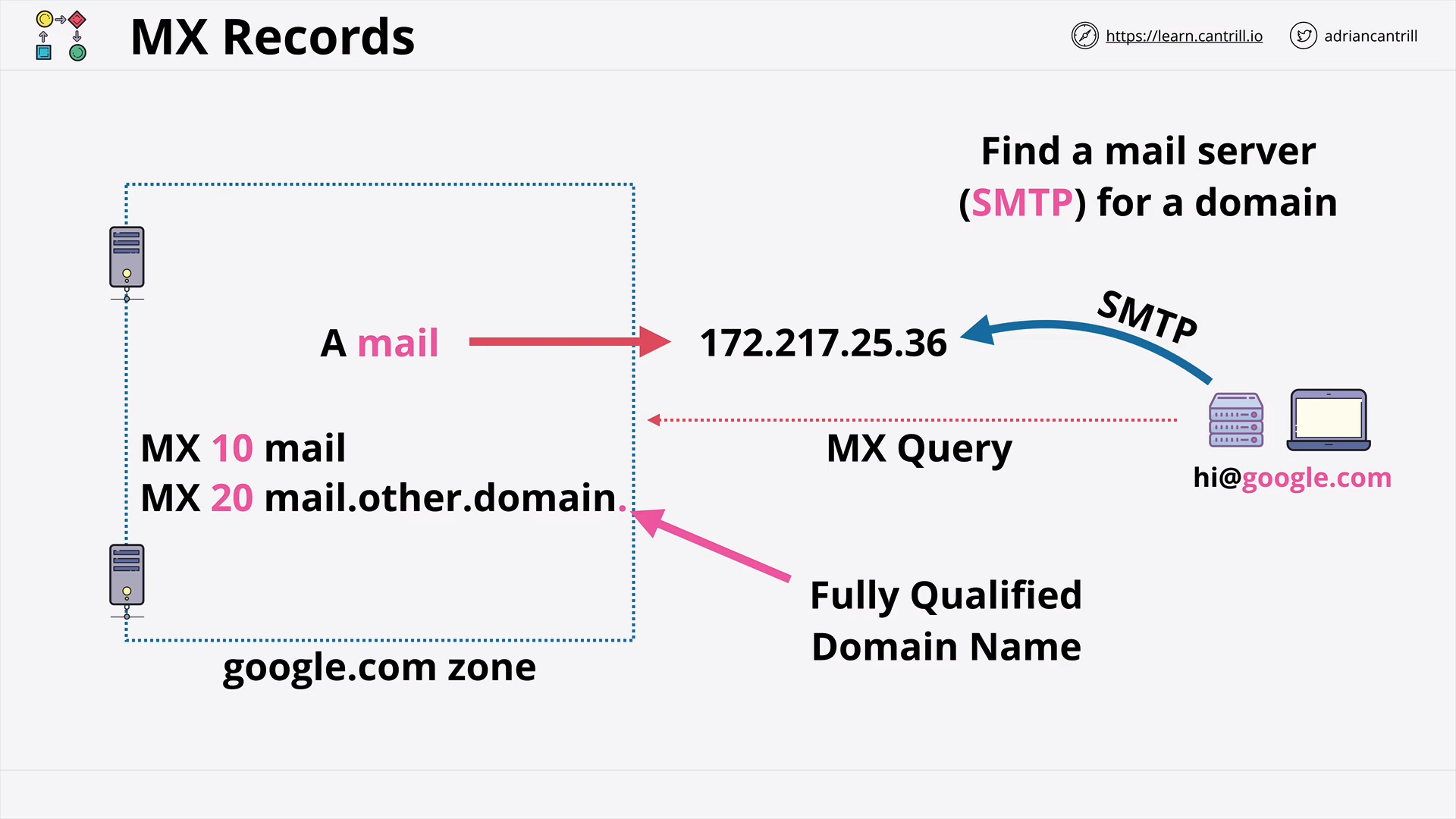 DNS Record - MX Record
DNS Record - MX Record
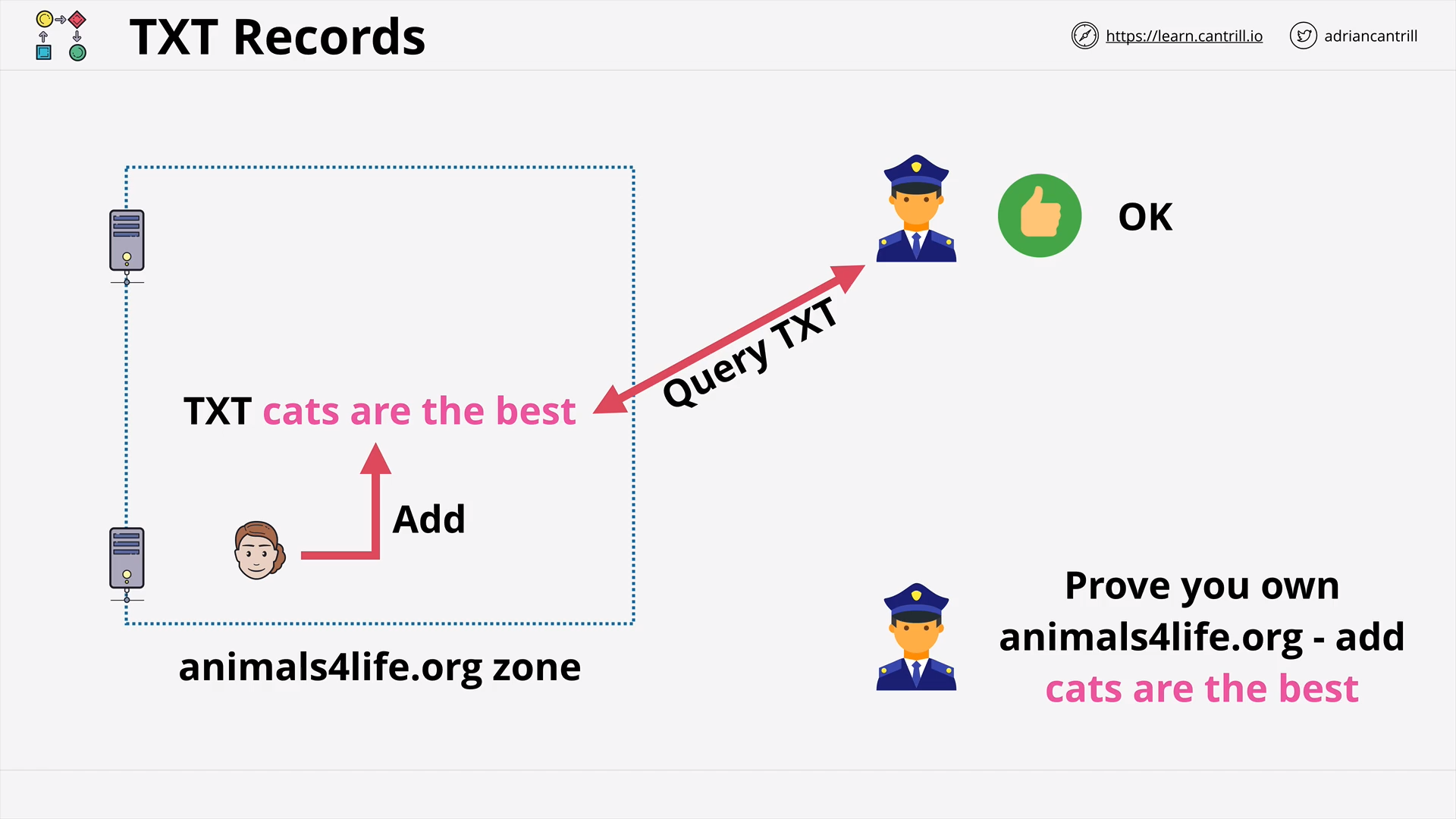 DNS Record - TXT Record
DNS Record - TXT Record
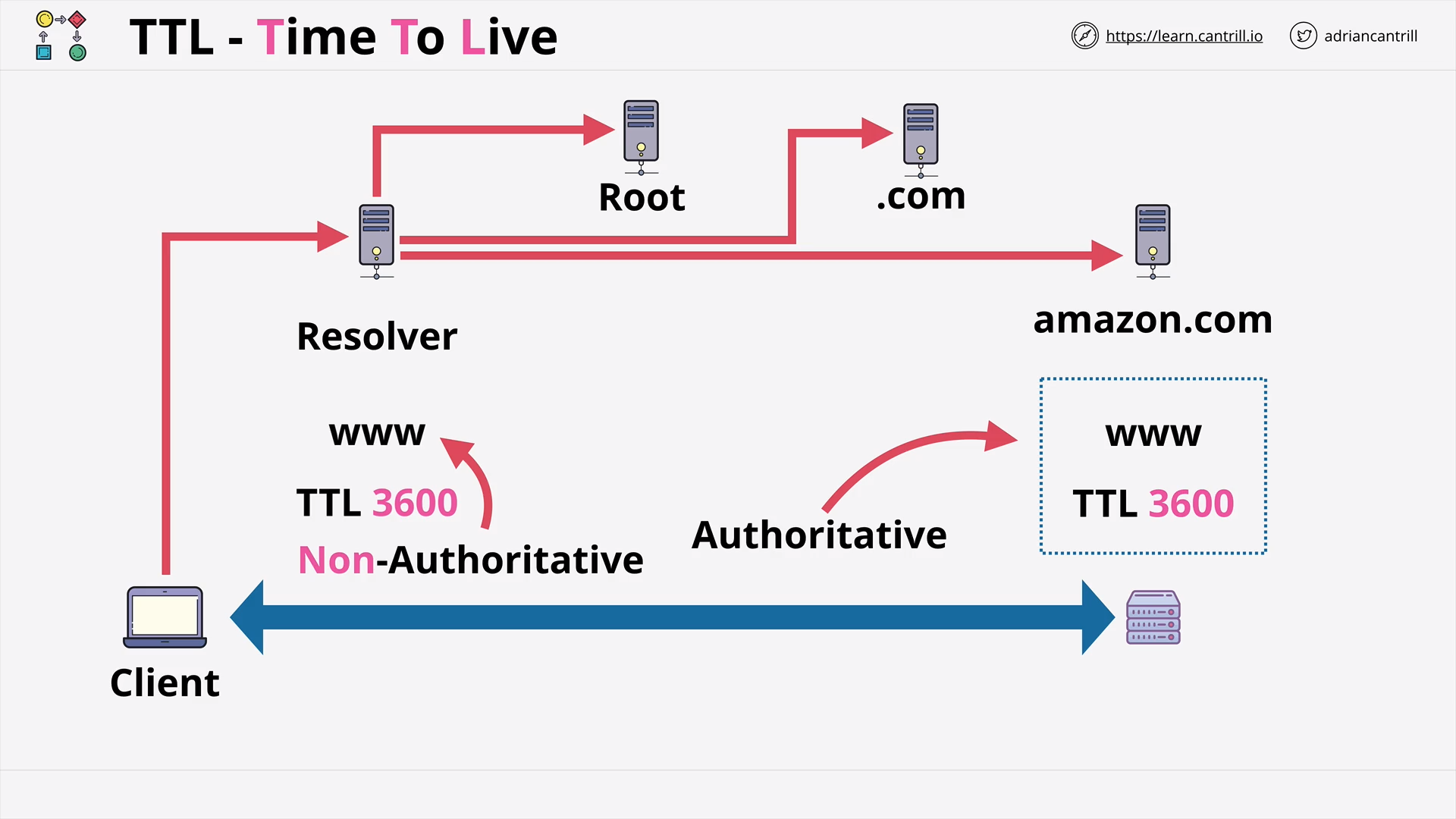 DNS Record - Time To Live (TTL)
DNS Record - Time To Live (TTL)
Fundamentals Section Quiz
IAM, ACCOUNTS AND AWS ORGANISATIONS
[ASSOCIATE] IAM Identity Policies (15:52)
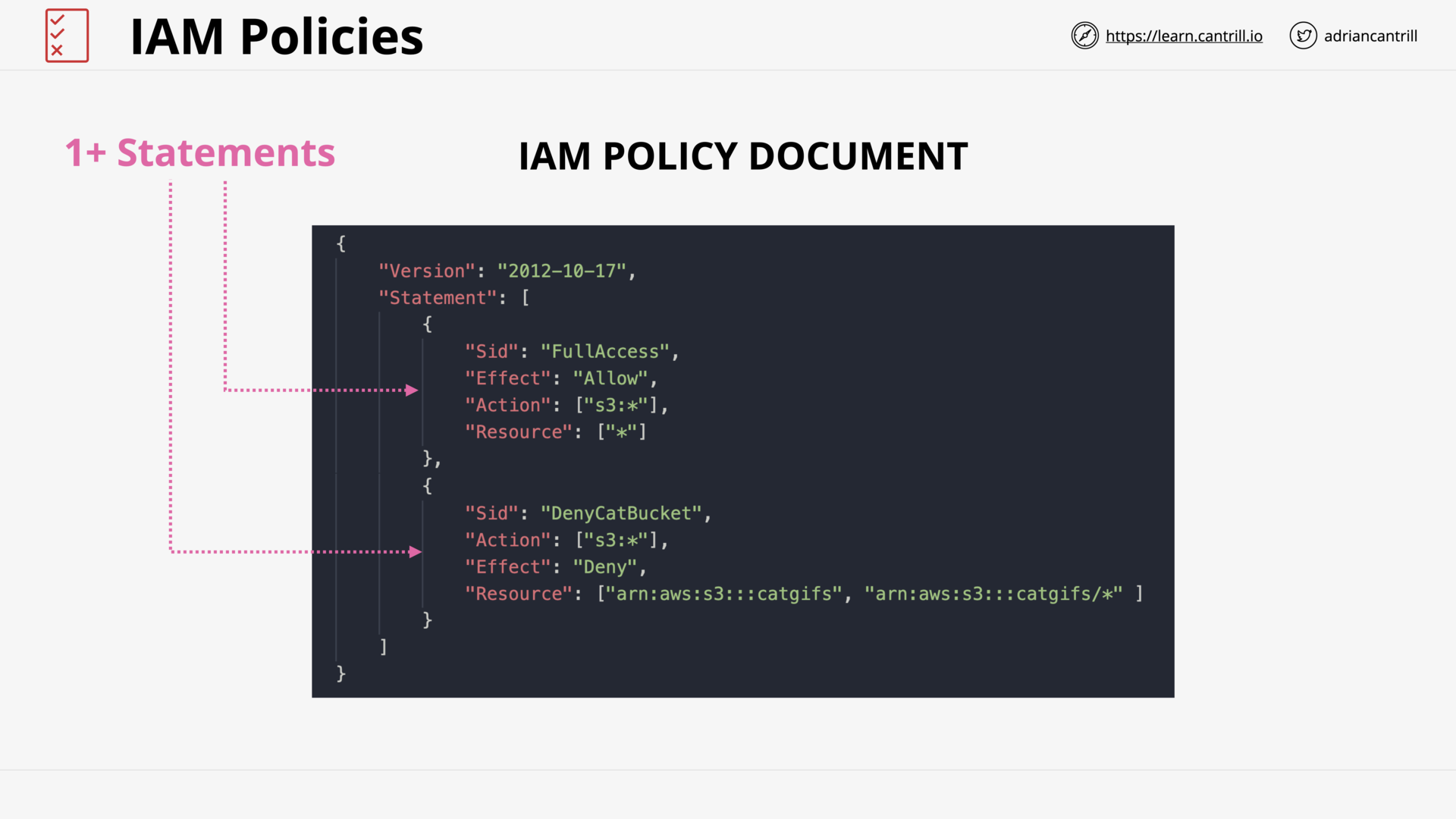 IAM Policy Document
IAM Policy Document
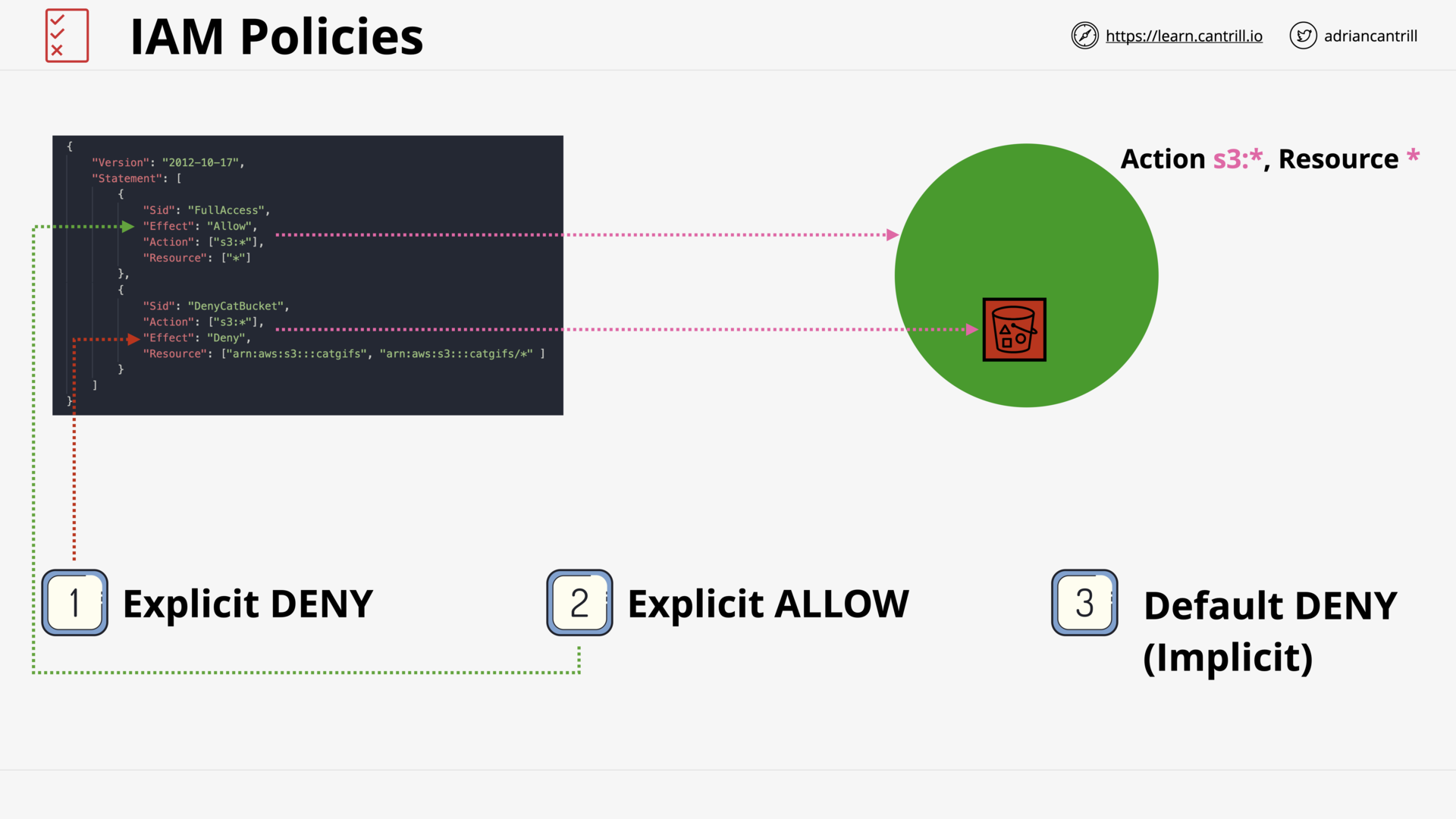 DENY - ALLOW - DENY
DENY - ALLOW - DENY
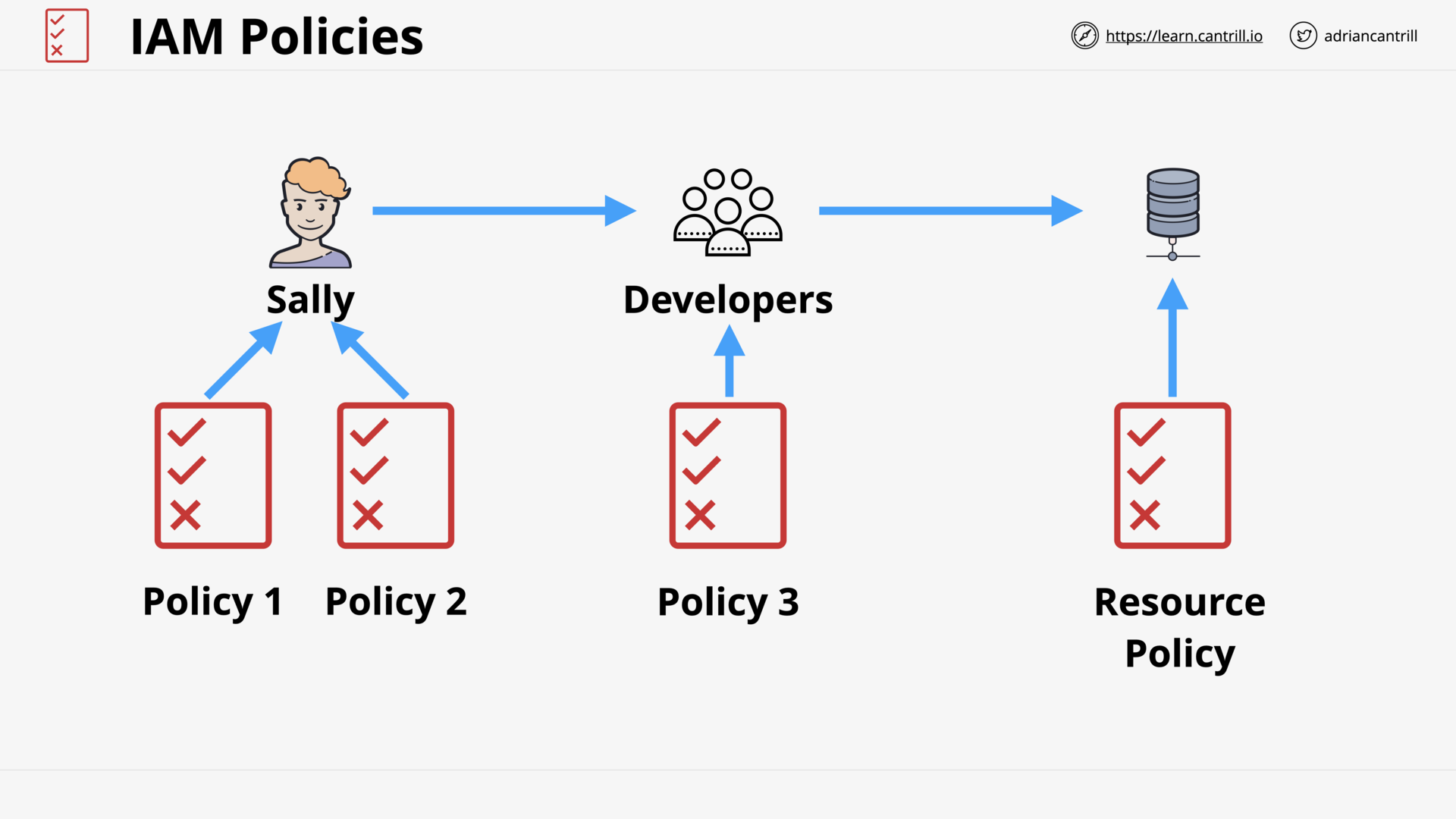 All policies for IAM Identities (User, Role, Group) & AWS Resources are evaluated at the same time.
All policies for IAM Identities (User, Role, Group) & AWS Resources are evaluated at the same time.
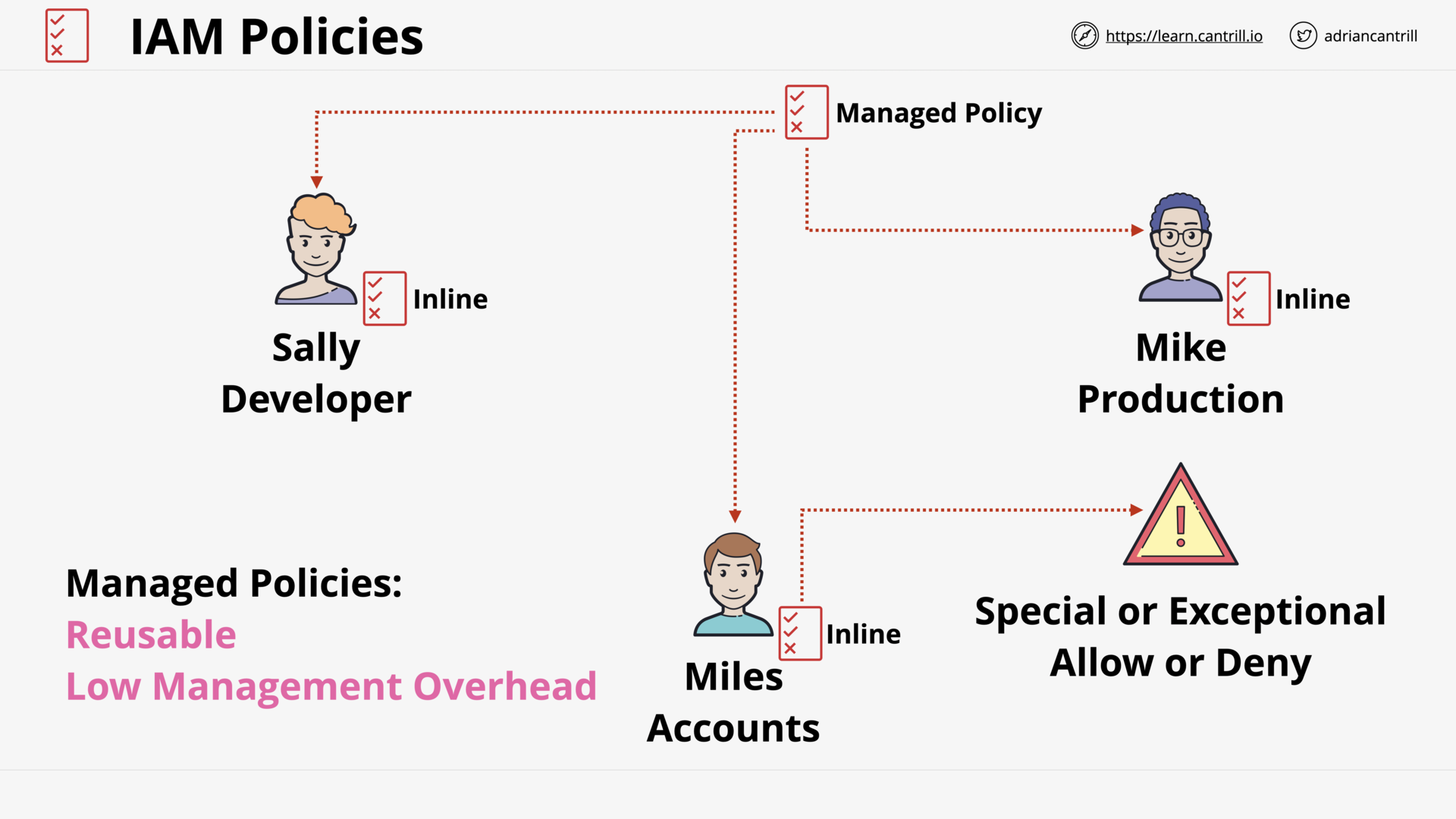 Inline Policy vs Managed Policy
Inline Policy vs Managed Policy
[ASSOCIATE] IAM Users and ARNs (13:49)
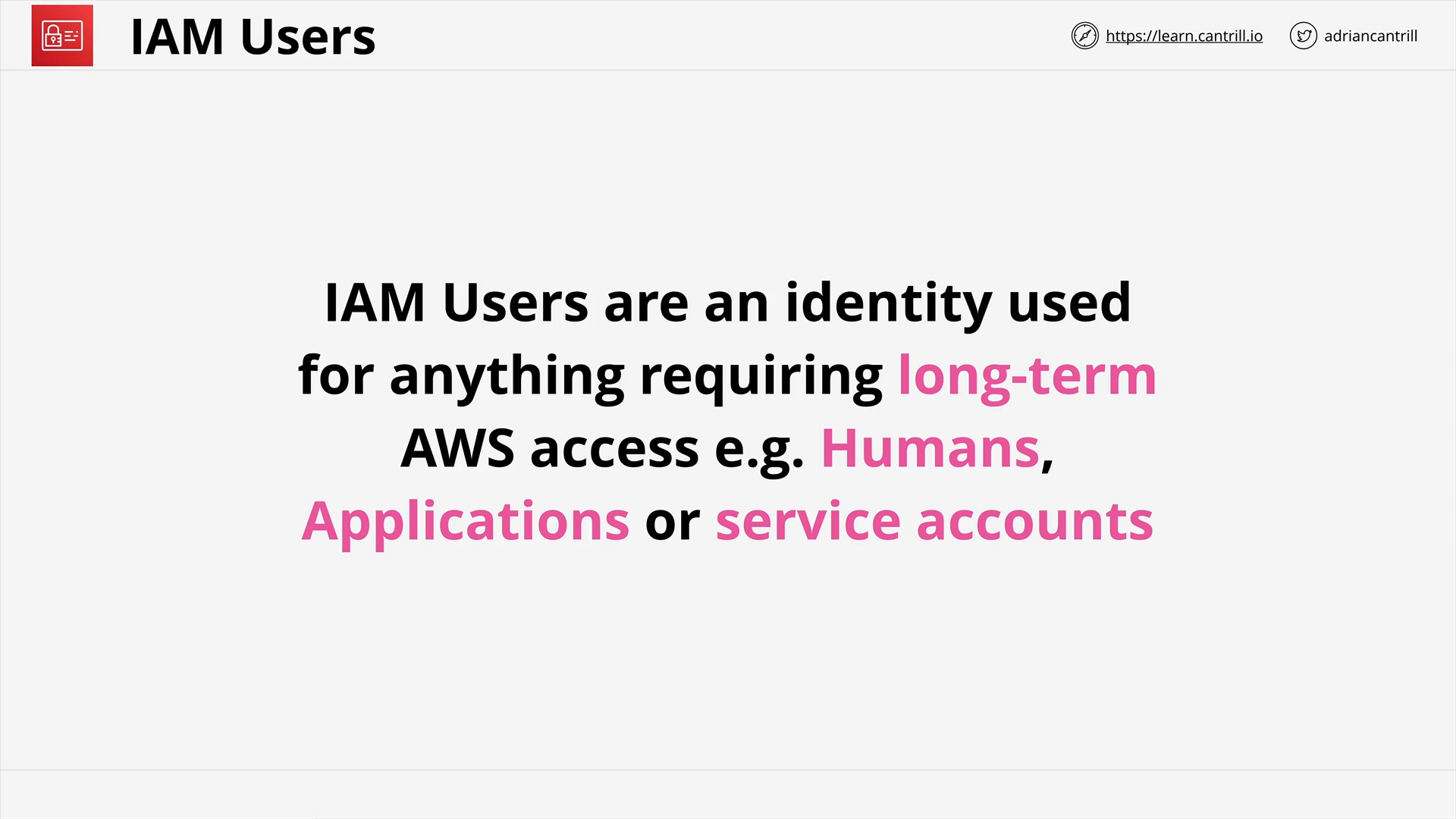 IAM User - What is it?
IAM User - What is it?
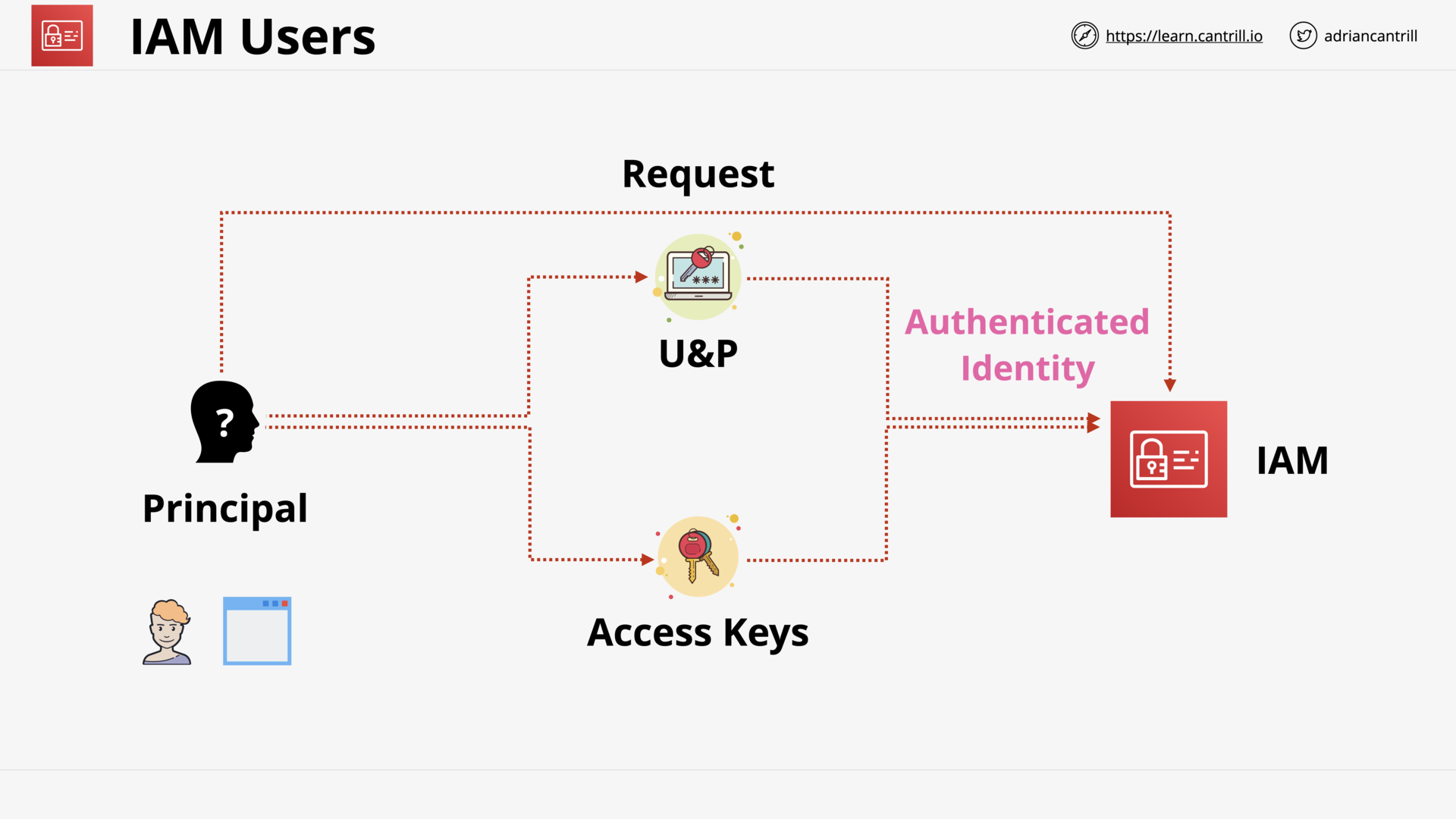 IAM - Principal and Authenticated Identity
IAM - Principal and Authenticated Identity
what is a principal?
Principal is an entity in AWS that can perform actions and access resources.
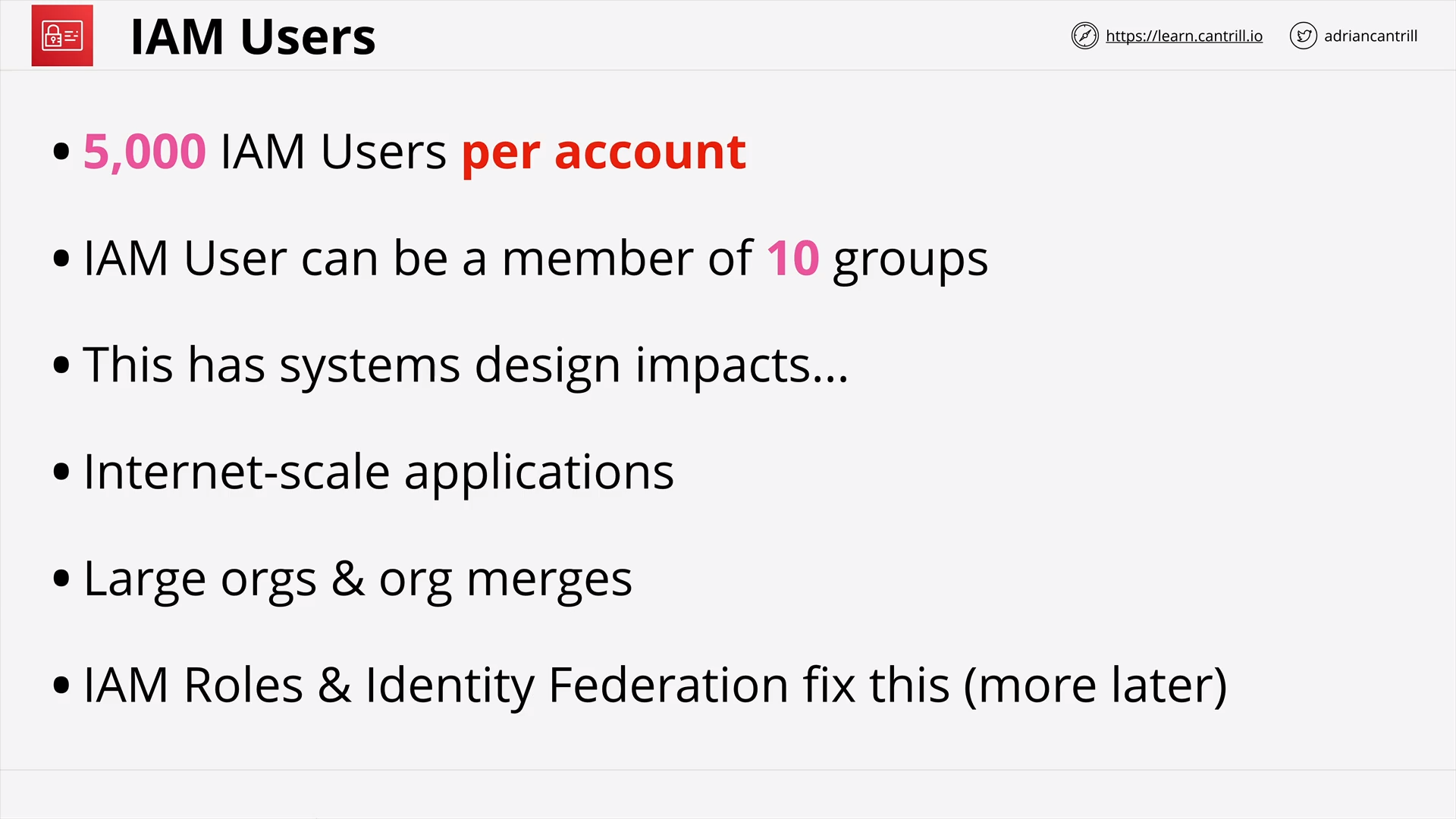 IAM Users - Limitation
IAM Users - Limitation
what is the limit iam users per account?
5.000 IAM Users per AWS account
how many iam groups a iam user can be a member of?
10 IAM groups per IAM User
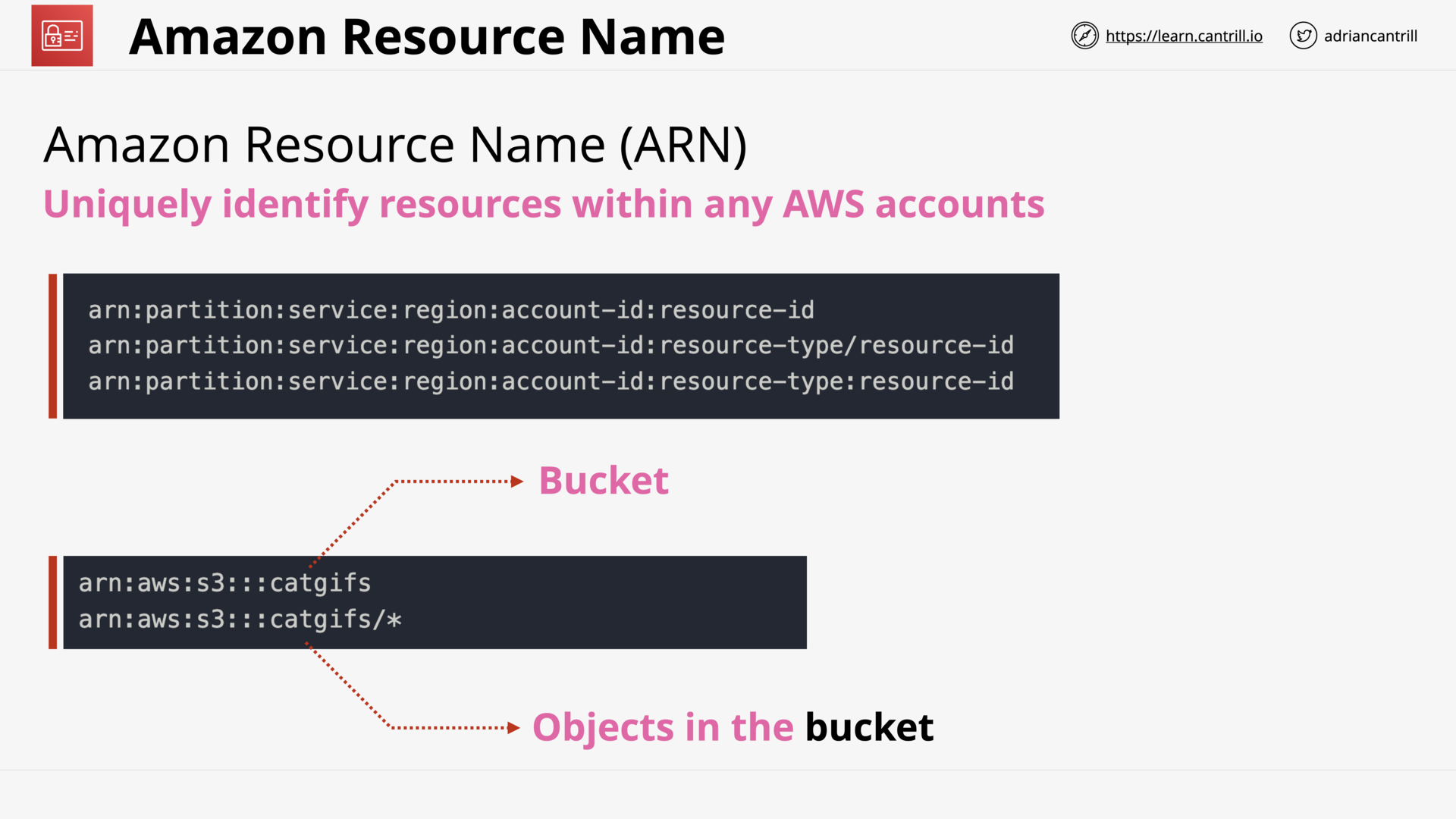 ARNs
ARNs
what is the format of arn?
- arn:partition:service:region:account-id:resource-id
- arn:partition:service:region:account-id:resource-type/resource-id
- arn:partition:service:region:account-id:resource-type:resource-id
👉
- 5 to 6 colon
: - region or/and account-id can be omitted.
| arn | partition | service | region | account-id | resource-type | resource-id |
|---|---|---|---|---|---|---|
awsaws-cnaws-us-gov | iams3ec2… | us-east-1ap-southest-1… | user |
[ASSOCIATE, DEMO] Simple Identity Permissions in AWS (16:06)
[ASSOCIATE] IAM Groups (7:48)
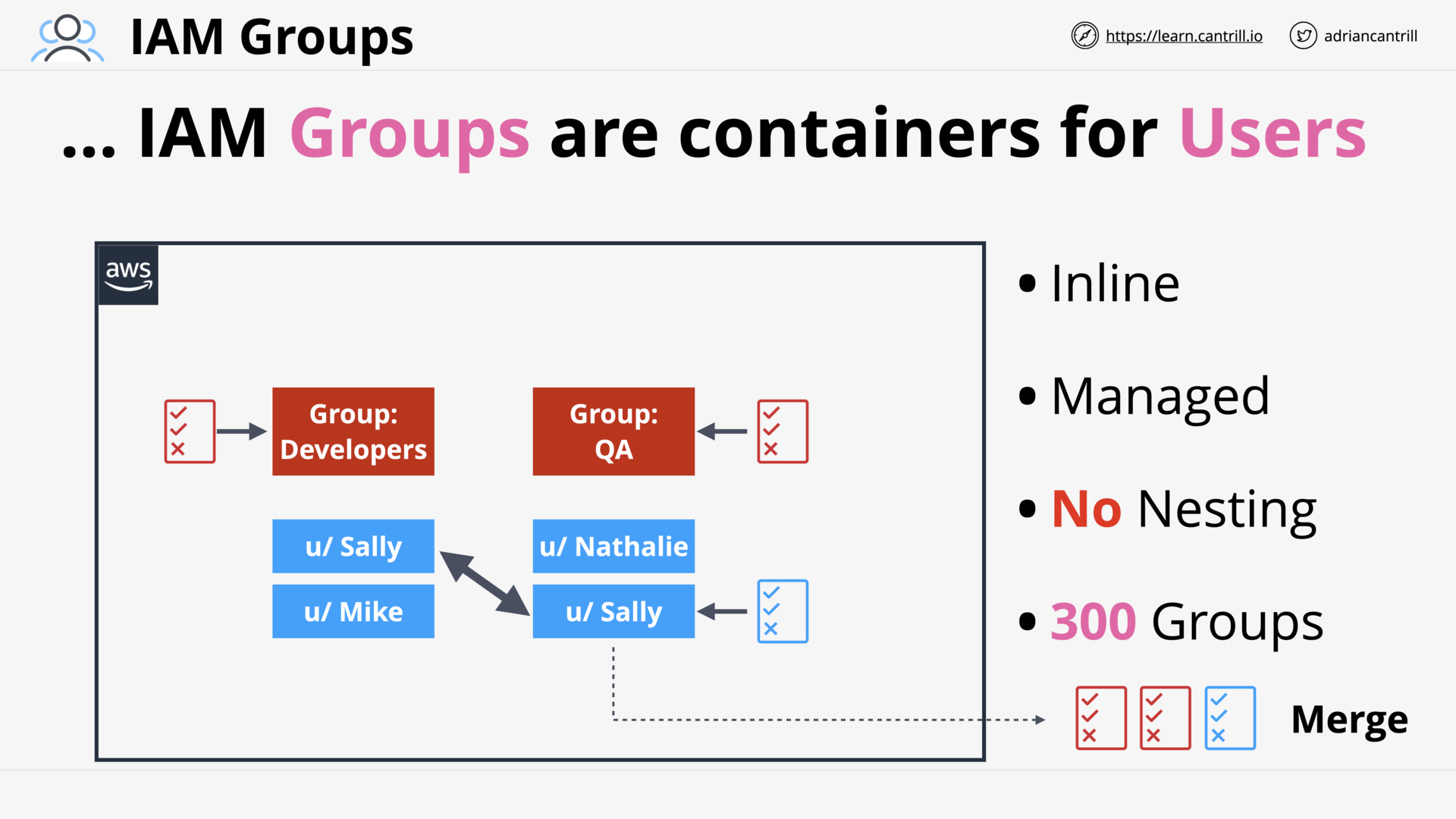 IAM Groups
IAM Groups
what is iam group?
Containers for IAM Users.
what are the limits of iam group?
- No Nesting.
- Limit of 300 Groups.
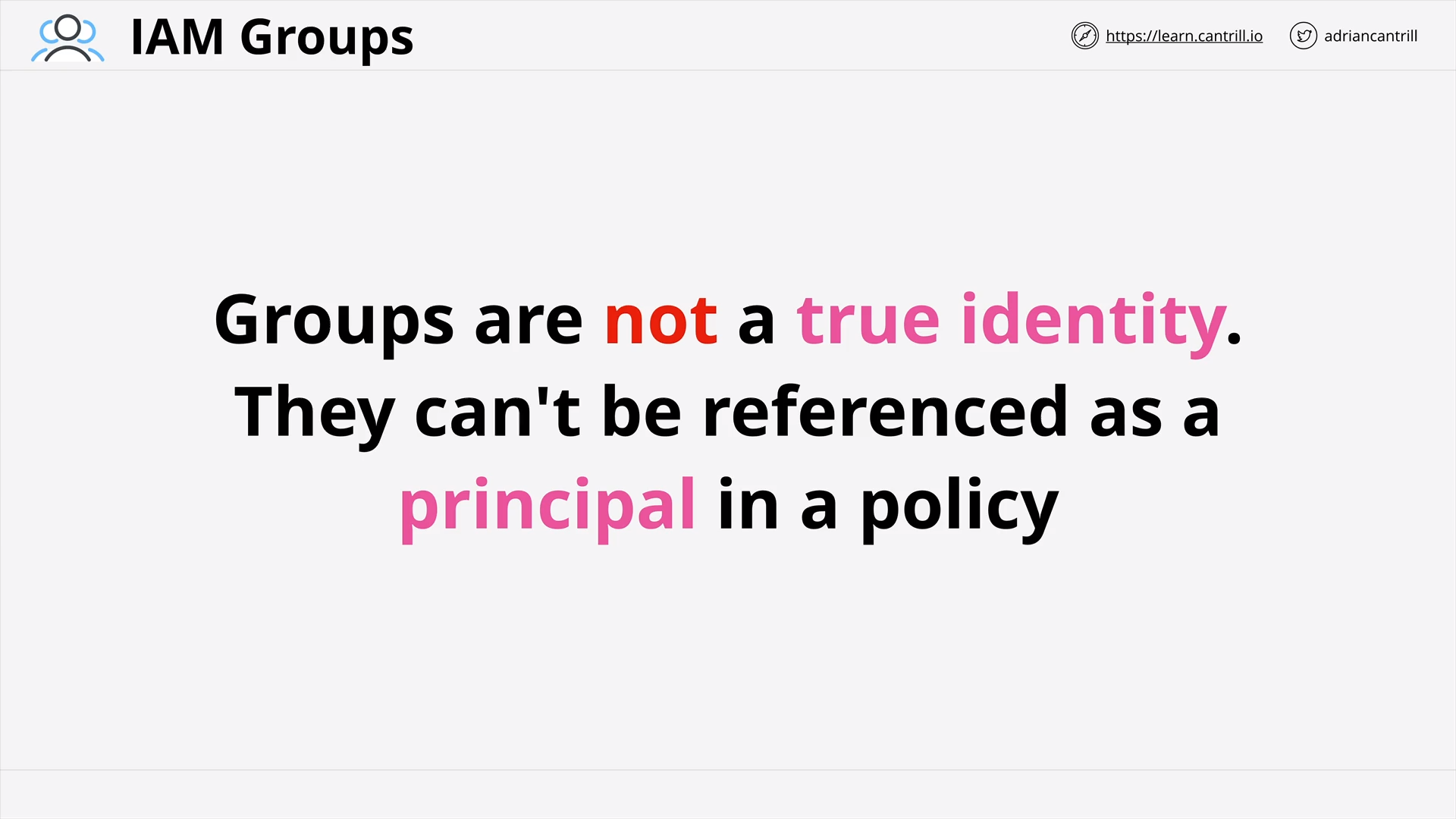 IAM Group is not a true identity
IAM Group is not a true identity
can an iam group be used as a principle in a policy?
IAM Group is NOT a true identity, that
- can NOT be used as a Principle in a policy.
- don’t have credential to login with
[ASSOCIATE, DEMO] Permissions control using IAM Groups (9:24)
[ASSOCIATE] IAM Roles - The Tech (8:13)
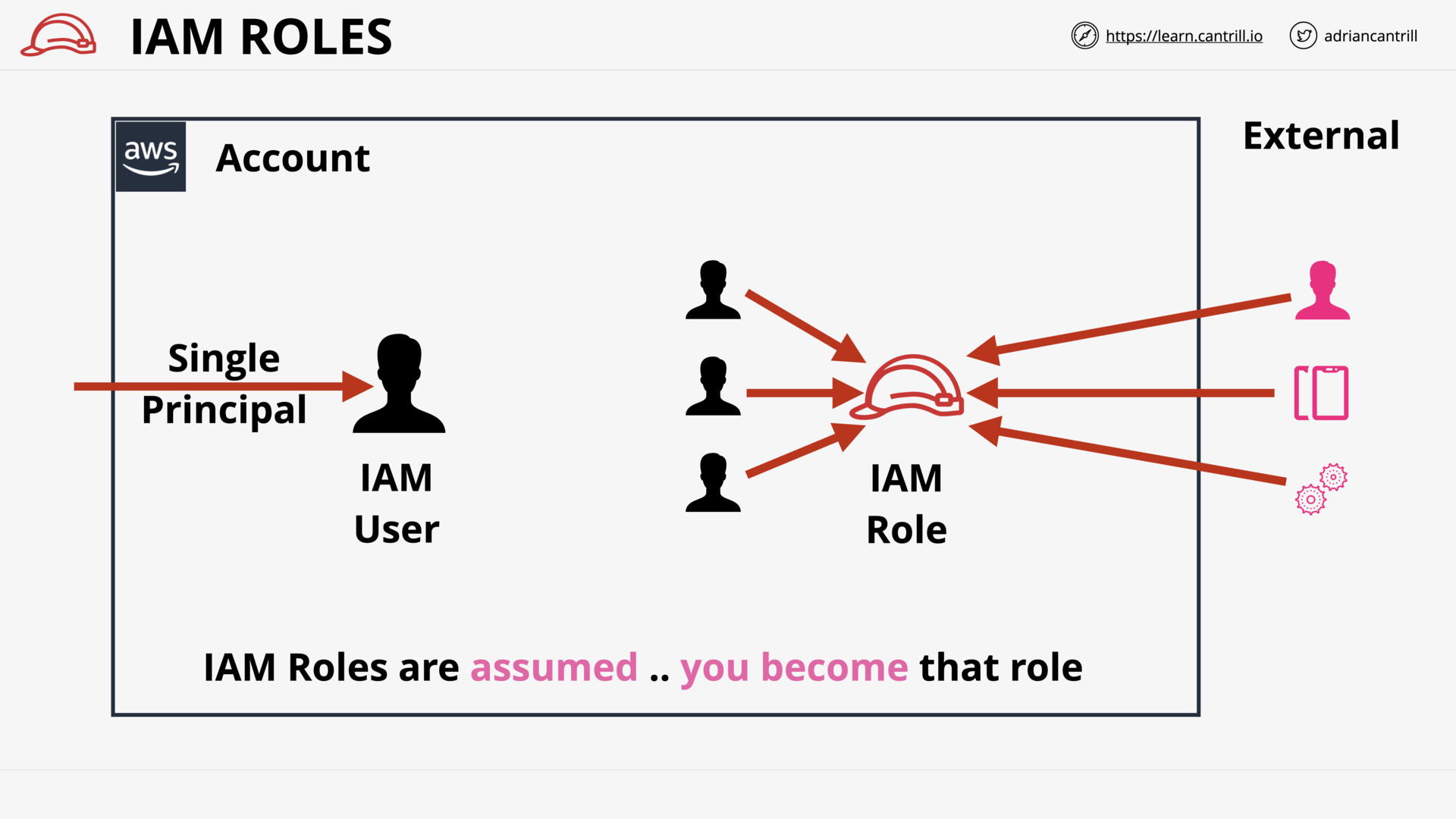 IAM Role and Assuming an IAM Role
IAM Role and Assuming an IAM Role
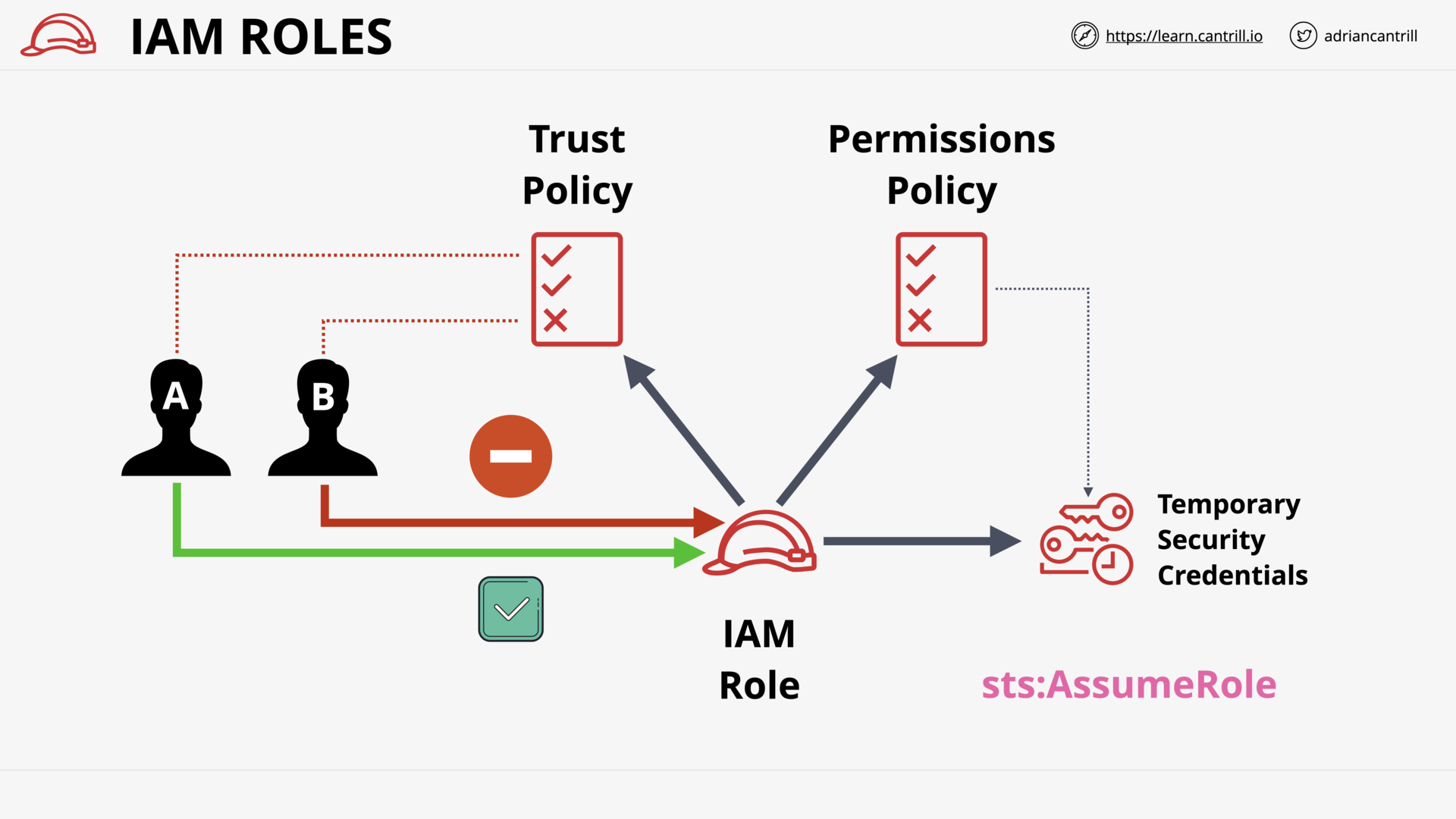 Trust Policy vs Permission Policy
Trust Policy vs Permission Policy
what is trust policy in iam?
The trust policy defines
- which principals can assume the role, and
- under which conditions
See How to use trust policies with IAM roles | AWS Security Blog
[ASSOCIATE] When to use IAM Roles (15:27)
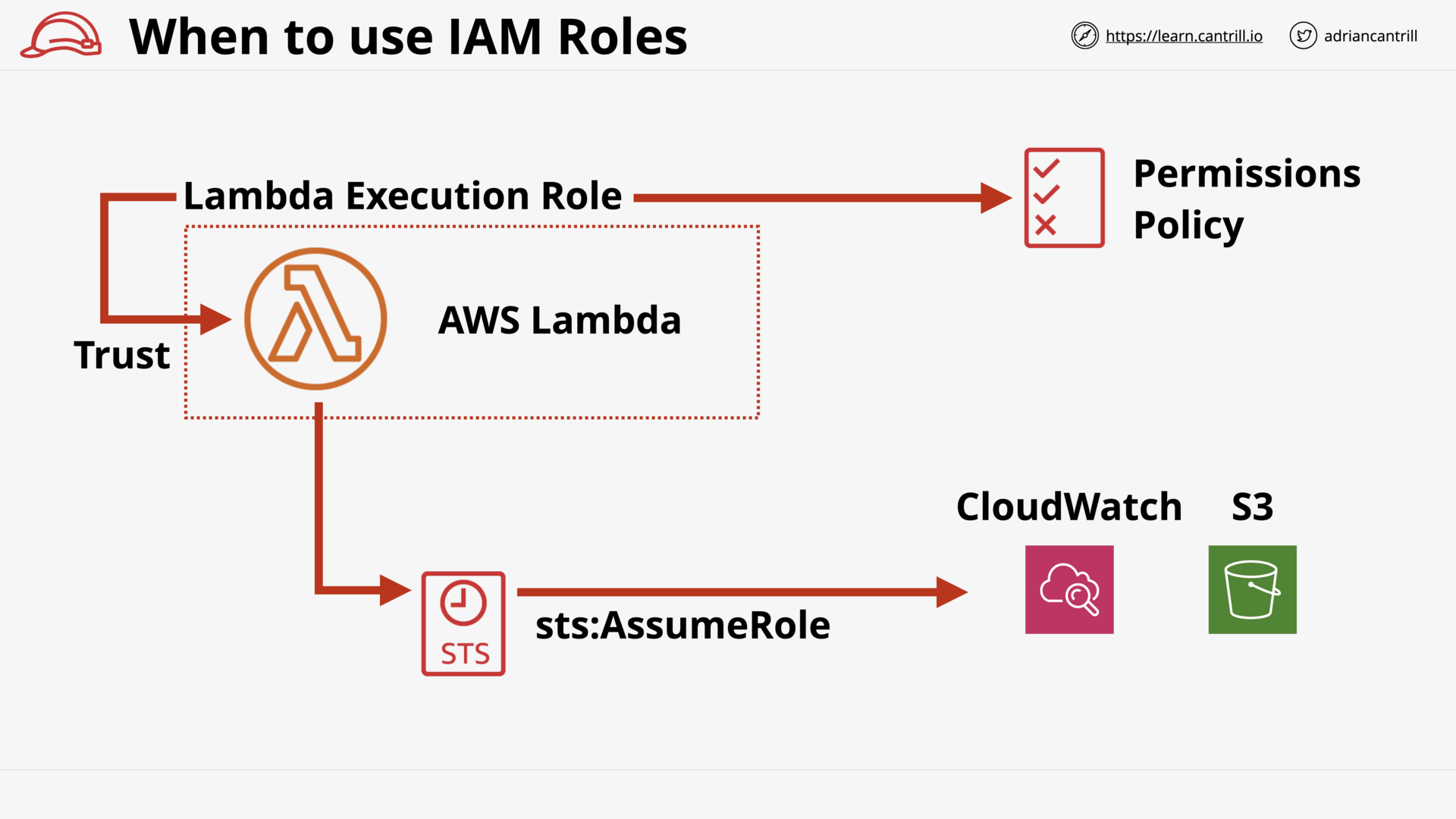 Lambda Execute Role
Lambda Execute Role
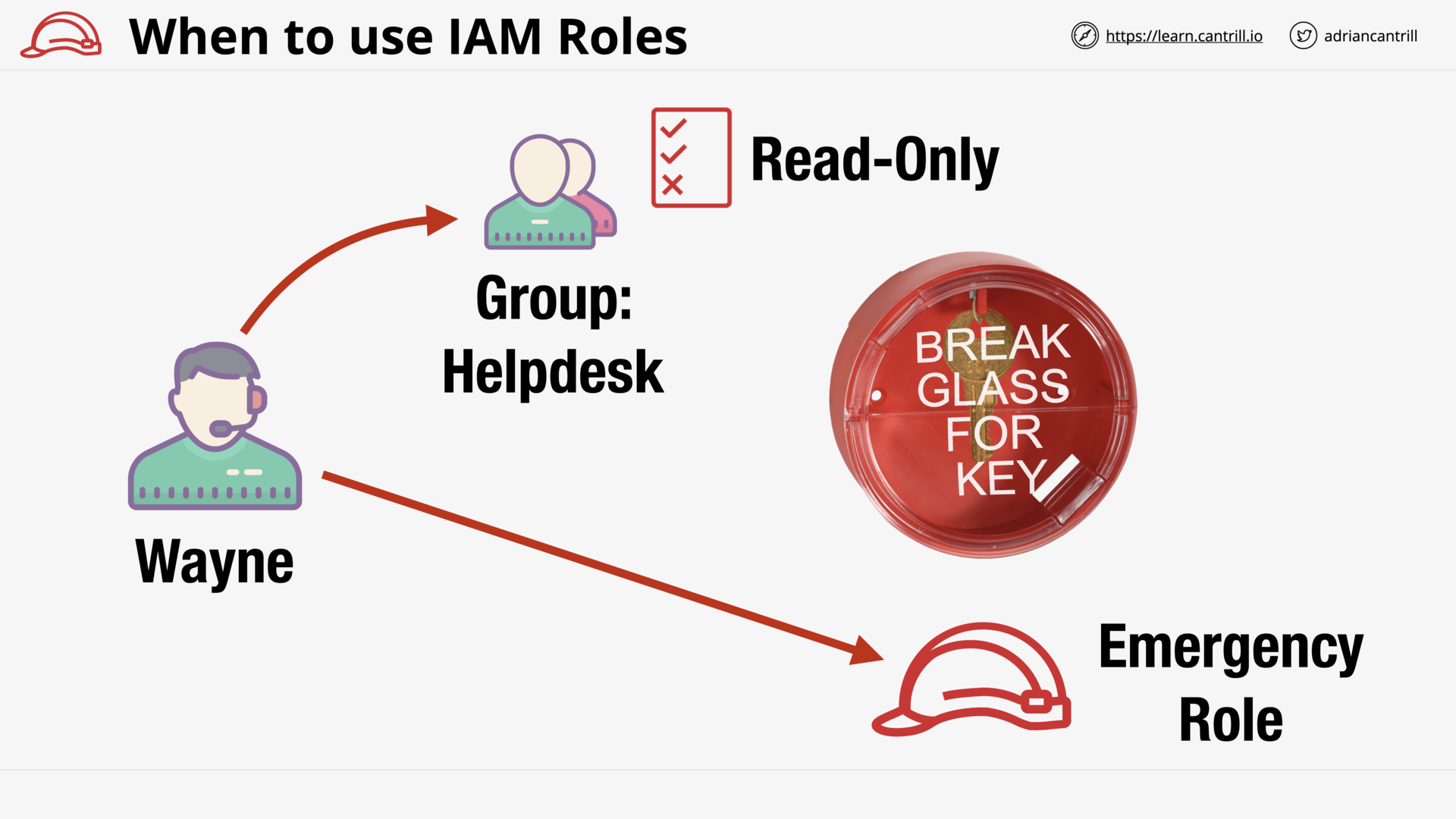 Emergency Role
Emergency Role
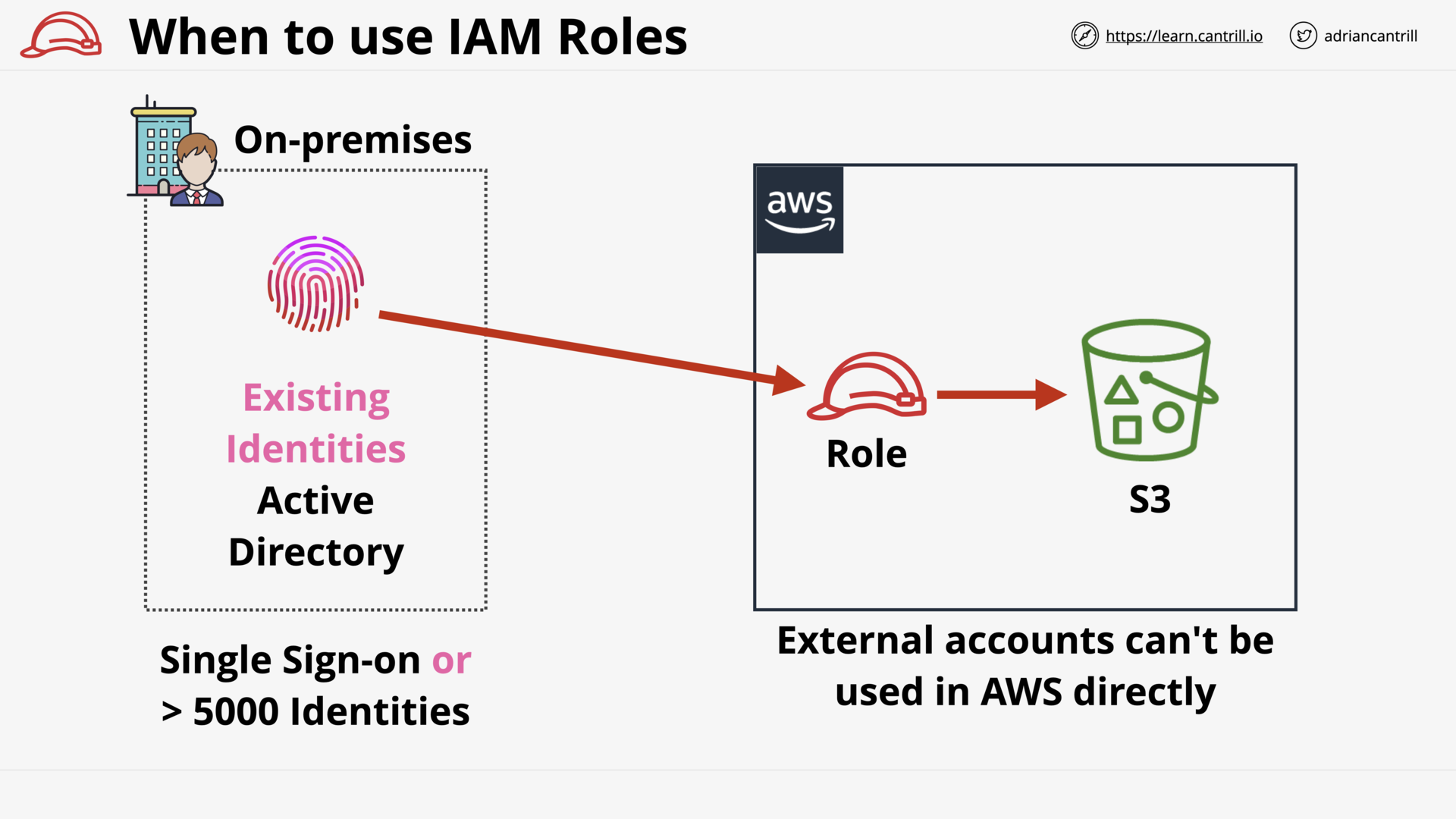 Existing Identities (e.g. Active Directory)
Existing Identities (e.g. Active Directory)
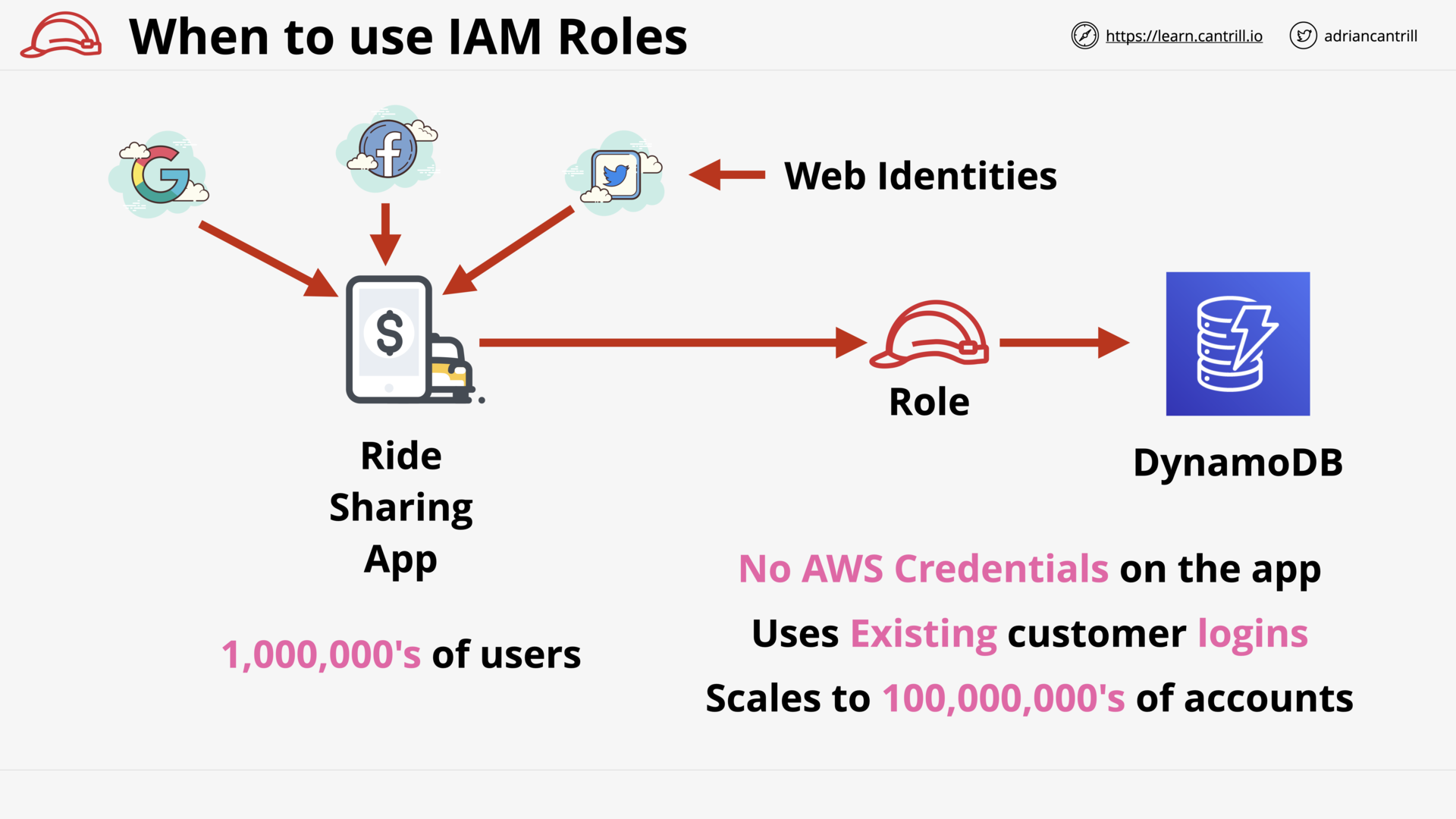 Web Identities (e.g. Google, Facebook)
Web Identities (e.g. Google, Facebook)
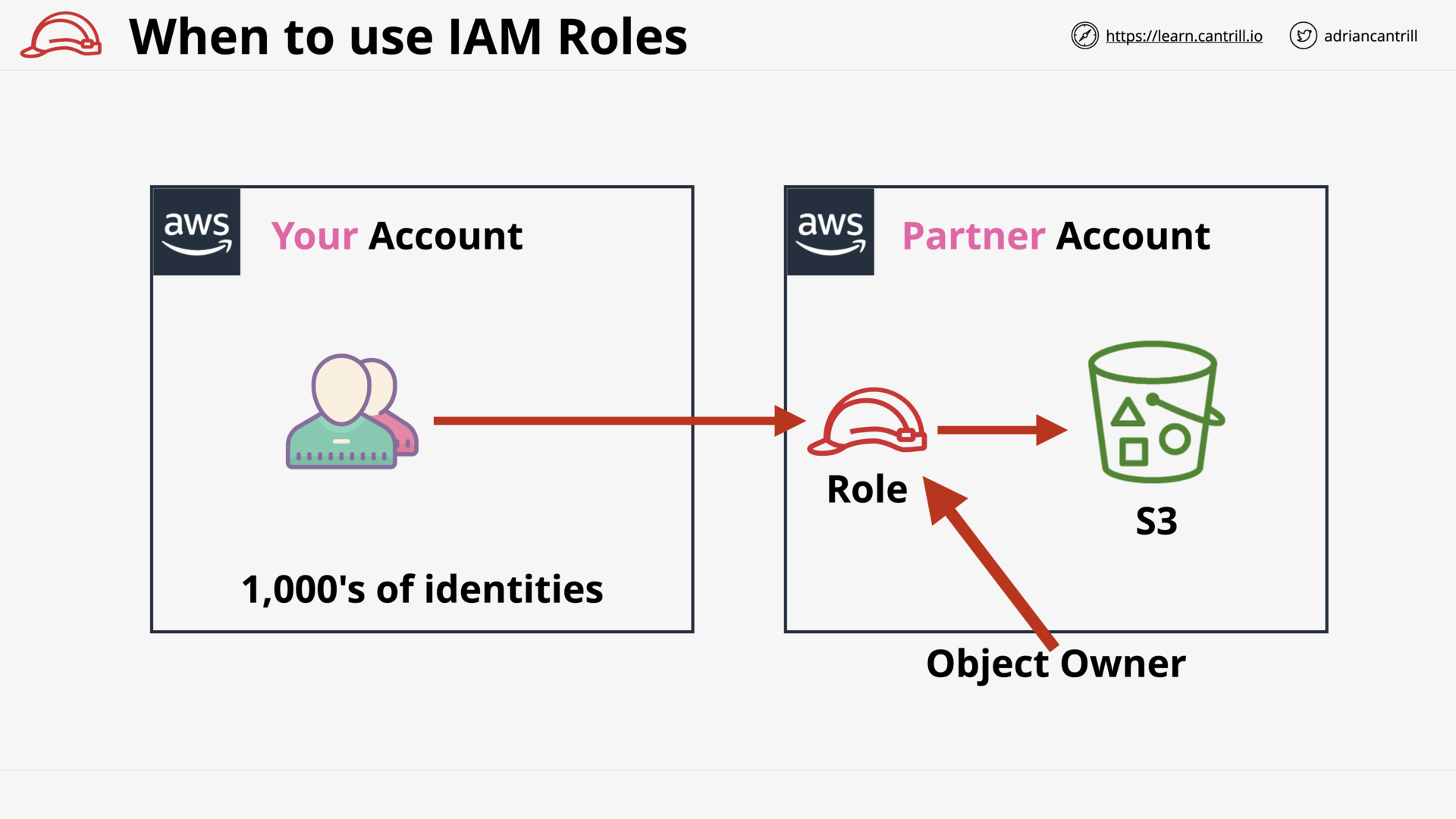 AWS Partner Accounts
AWS Partner Accounts
Service-linked Roles & PassRole (5:16)
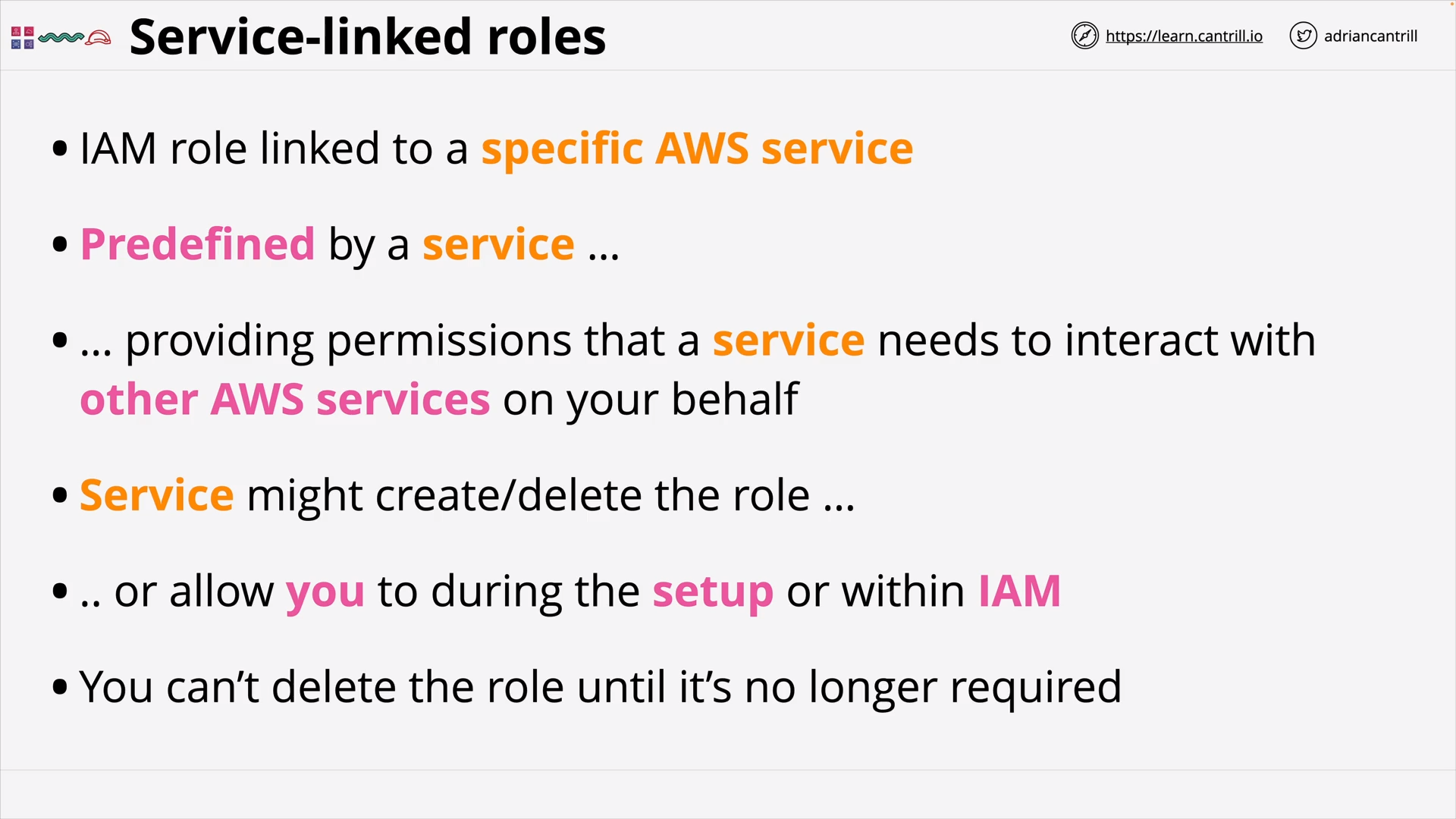 Service-linked Roles
Service-linked Roles
what is service-linked role?
A service-linked role is
- a unique type of IAM role that is linked directly to an AWS service.
- predefined (by the service) to include all the permissions that the service requires (to call other AWS services on your behalf).
why use service-linked role?
A service-linked Role
-
simplify the process of setting up a service because
- you don’t have to manually add permissions for the service to complete actions on your behalf
-
may be created
- automatically (by the service)
- manually using a wizard in the console
- manually using IAM
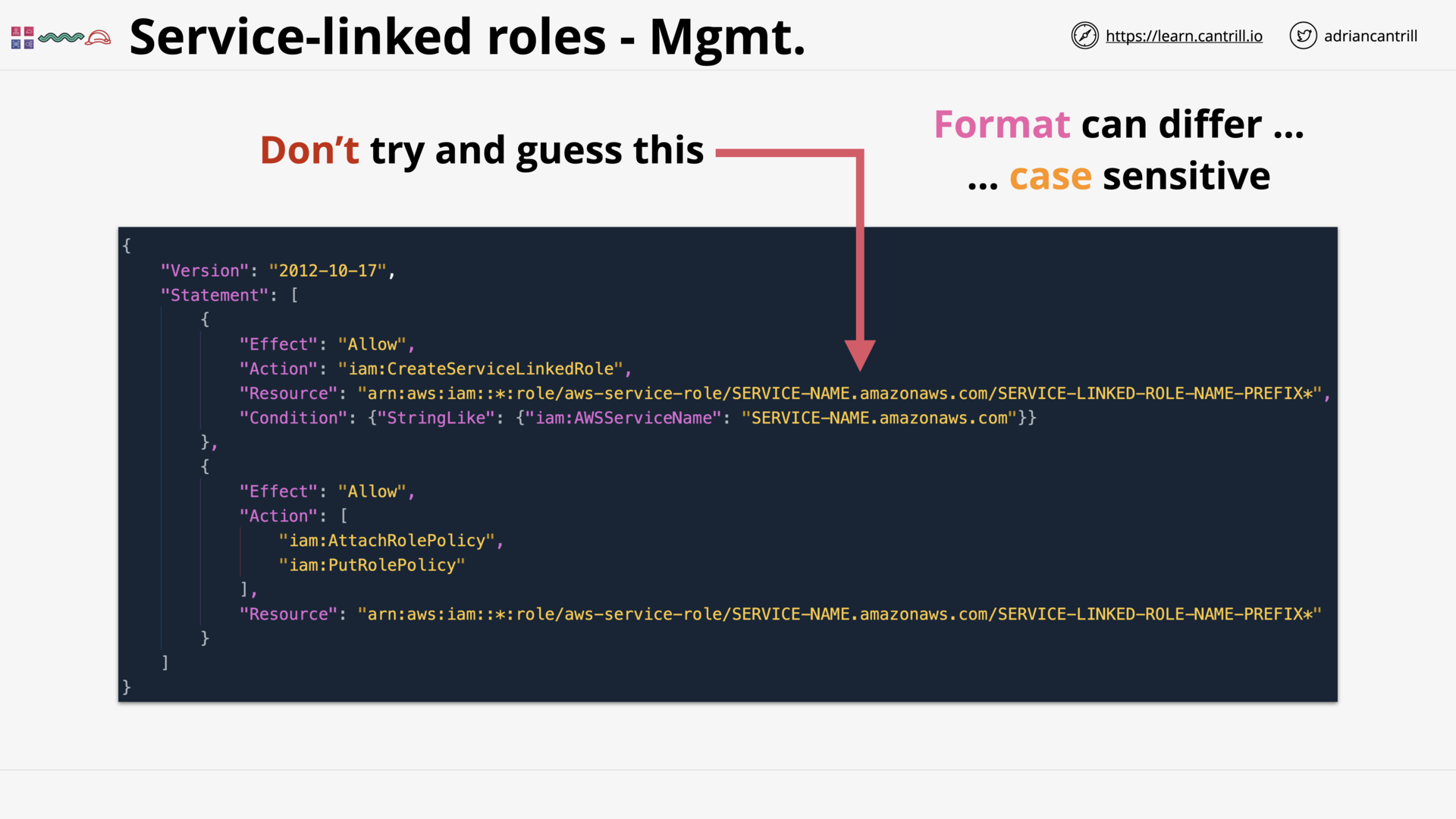 Permissions to allow create/edit the service-linked role
Permissions to allow create/edit the service-linked role
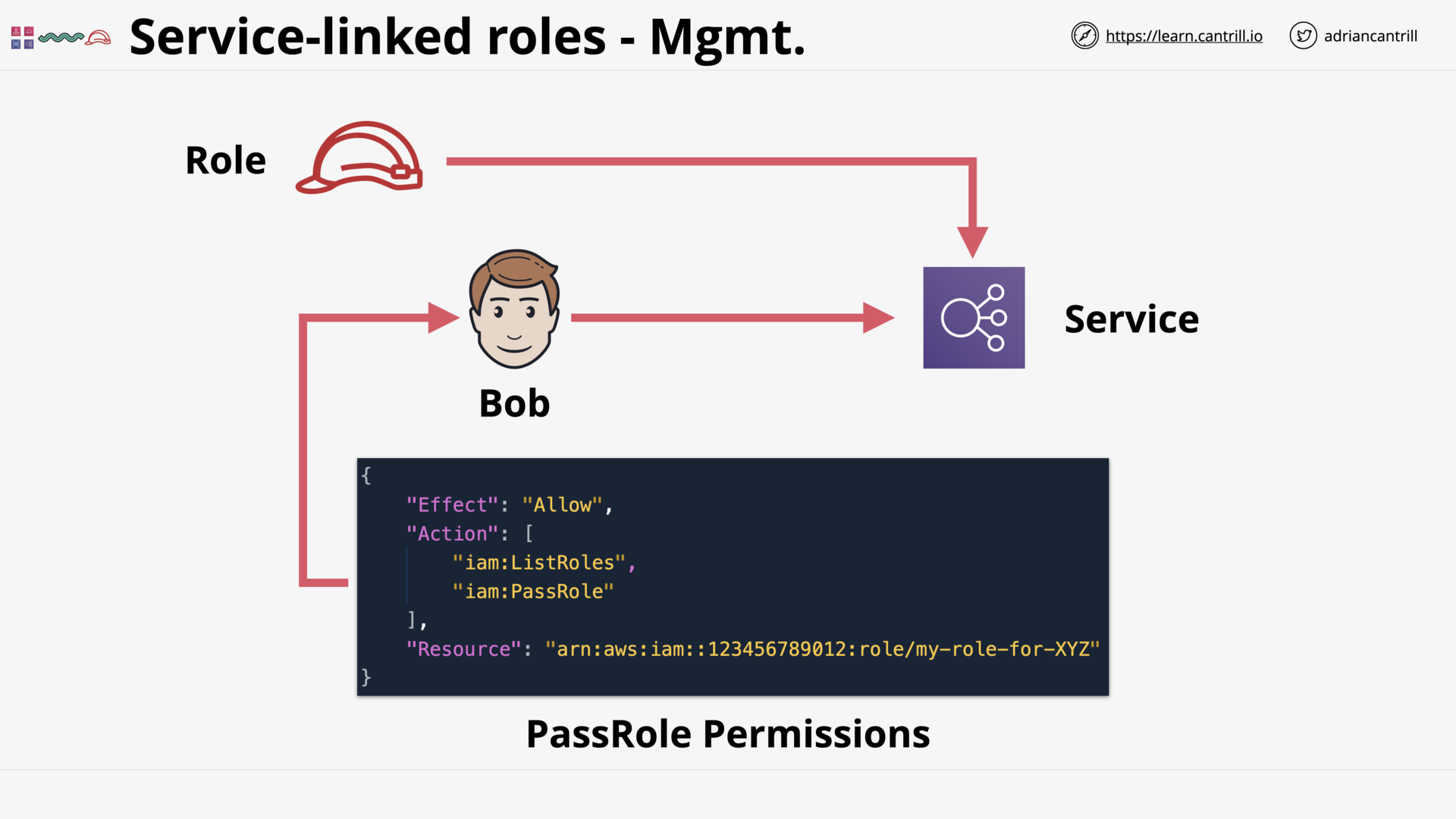 Pass an existing role to the service
Pass an existing role to the service
[ASSOCIATE] AWS Organizations (12:56)
 “Standard” AWS Account
“Standard” AWS Account
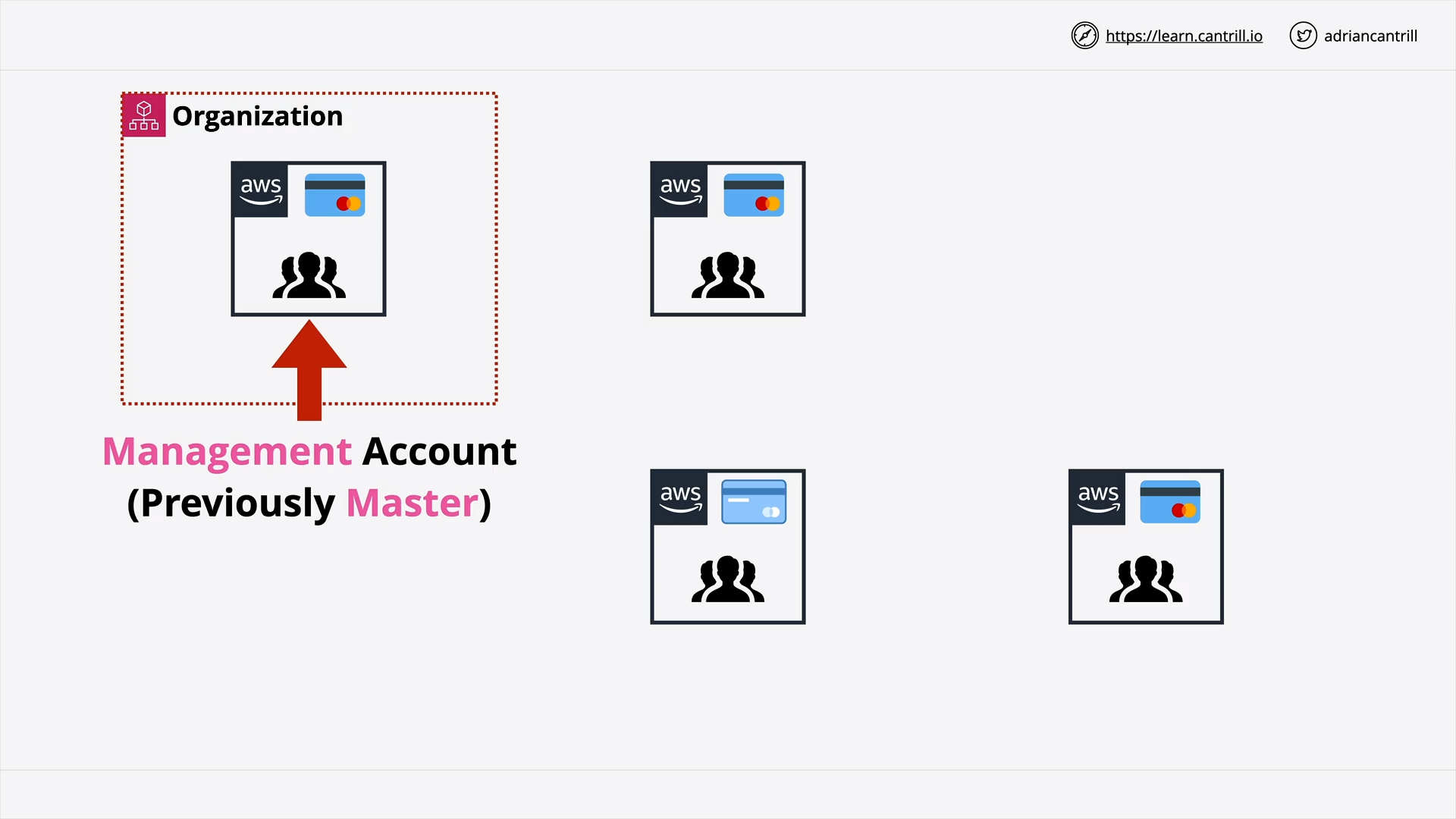 Management/Master Account
Management/Master Account
aws organization and management account, which come first?
- First, you use a standard account to create an AWS Organization
- Then that standard account become the management account of the AWS Organization.
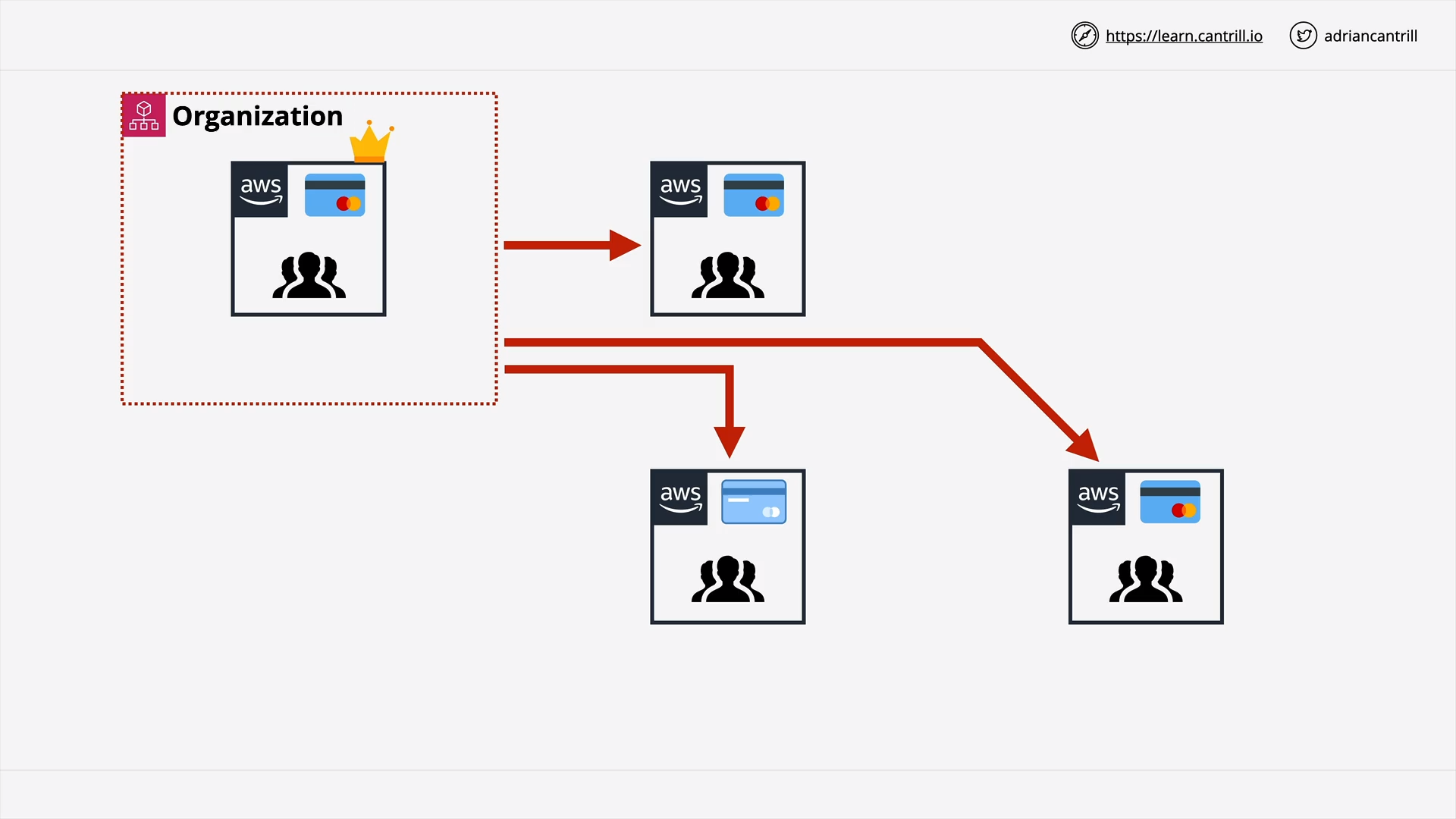 Invite existed standard accounts to an AWS Organization
Invite existed standard accounts to an AWS Organization
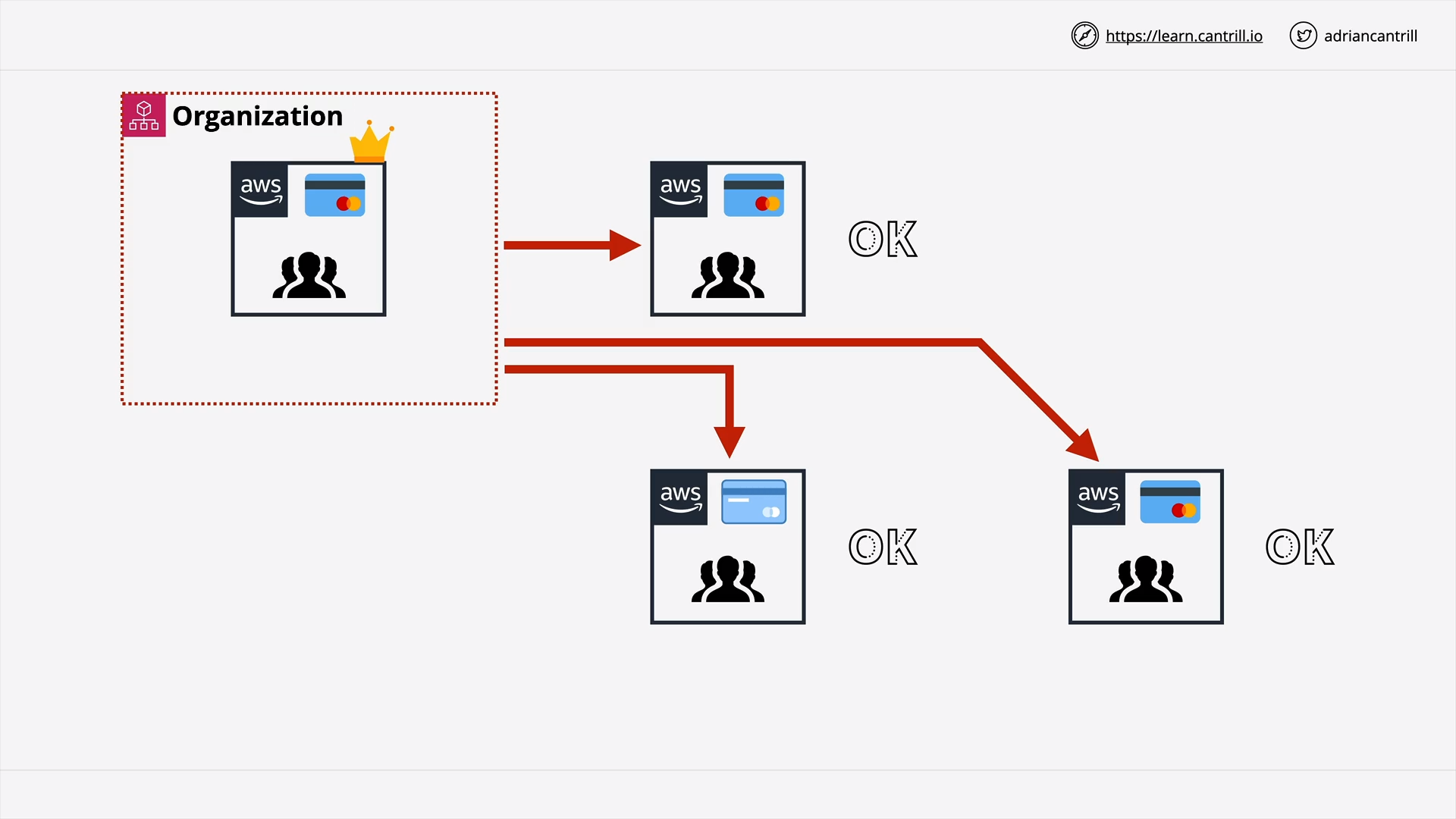 Accepting invitations to become member of an AWS Organization
Accepting invitations to become member of an AWS Organization
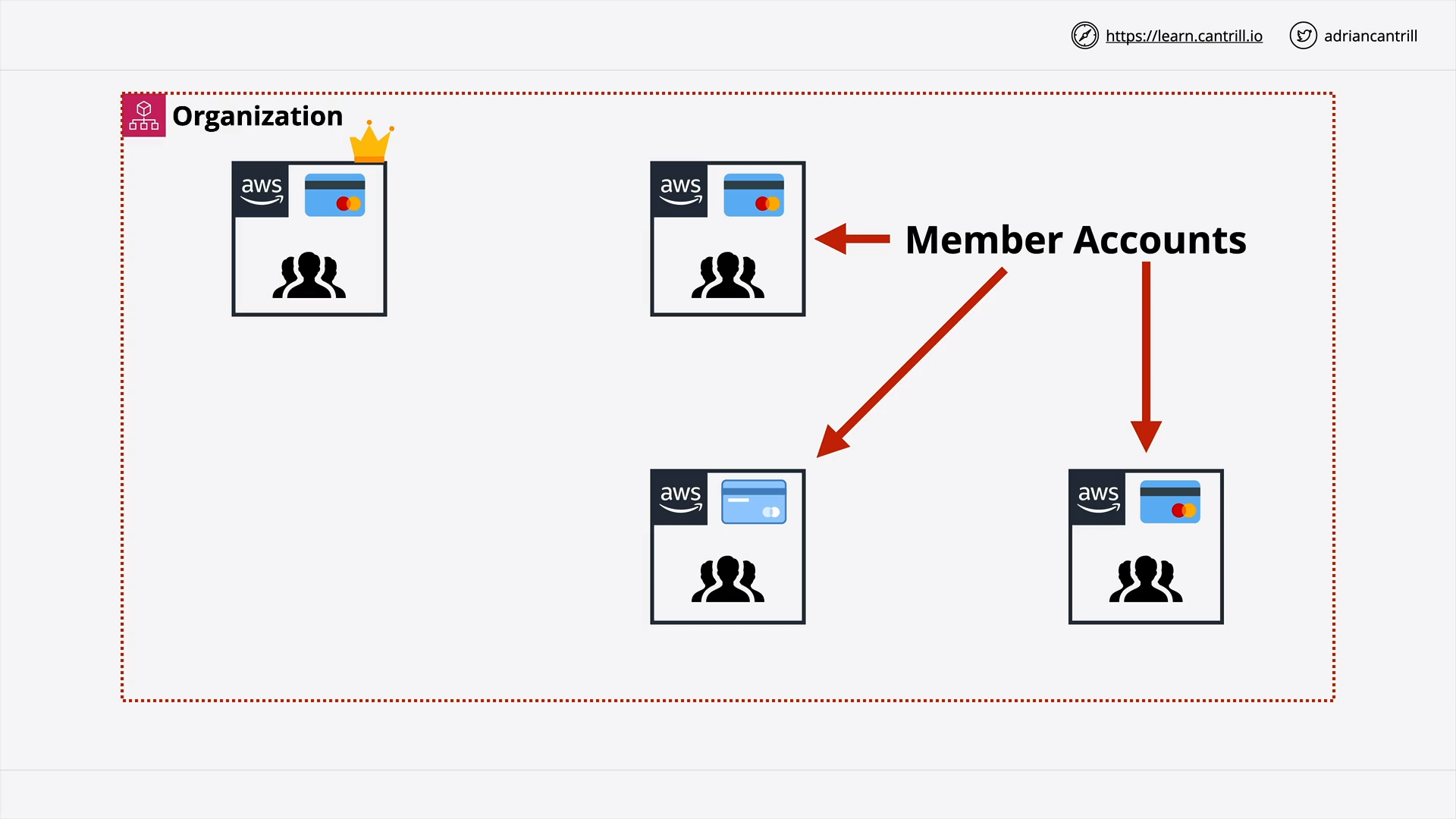 Member Accounts
Member Accounts
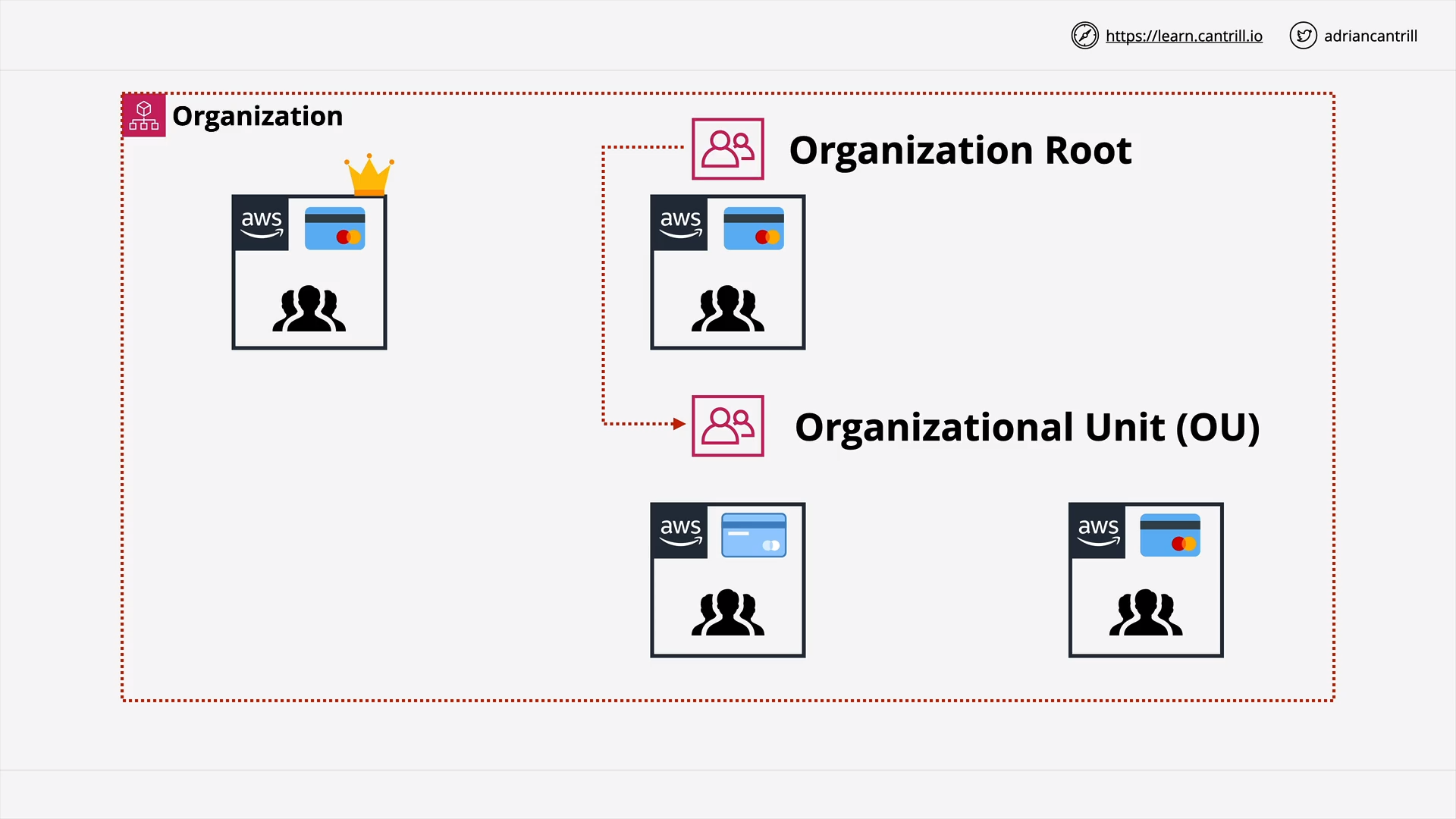 Organization Root & Organization Unit (OU)
Organization Root & Organization Unit (OU)
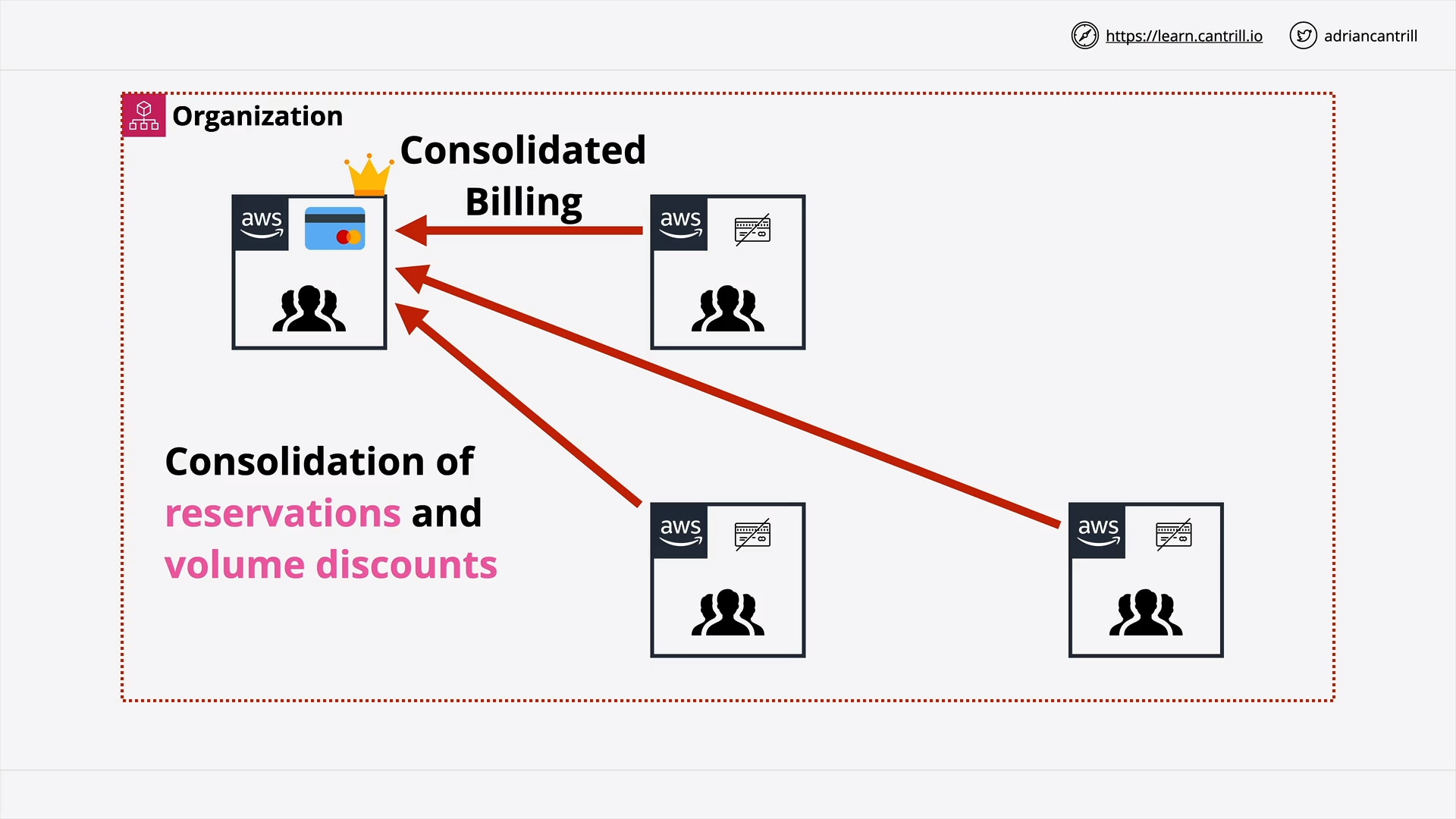 Consolidated Billing
Consolidated Billing
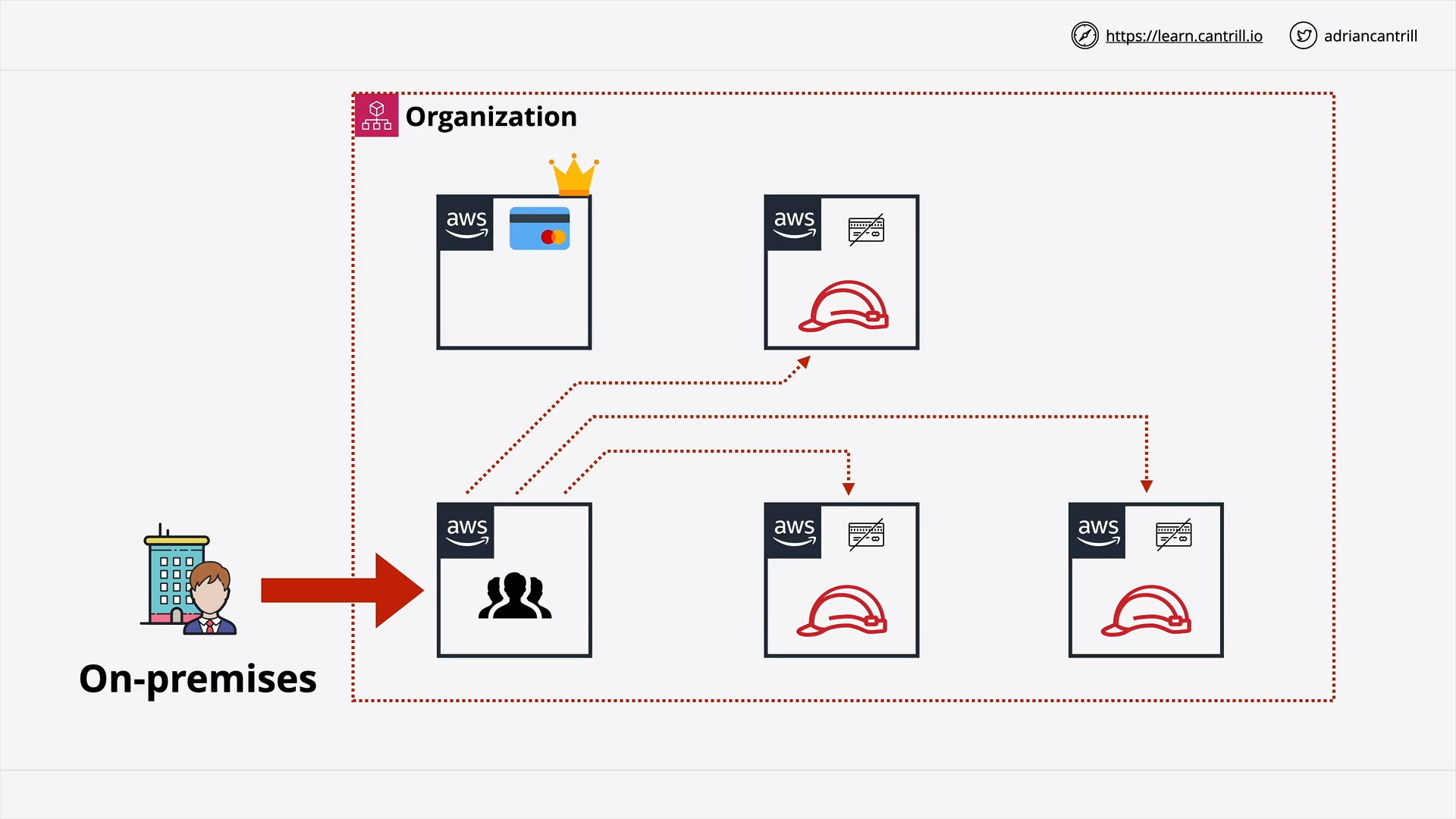 Role Switching
Role Switching
[ALL, DEMO] AWS Organizations (19:48)
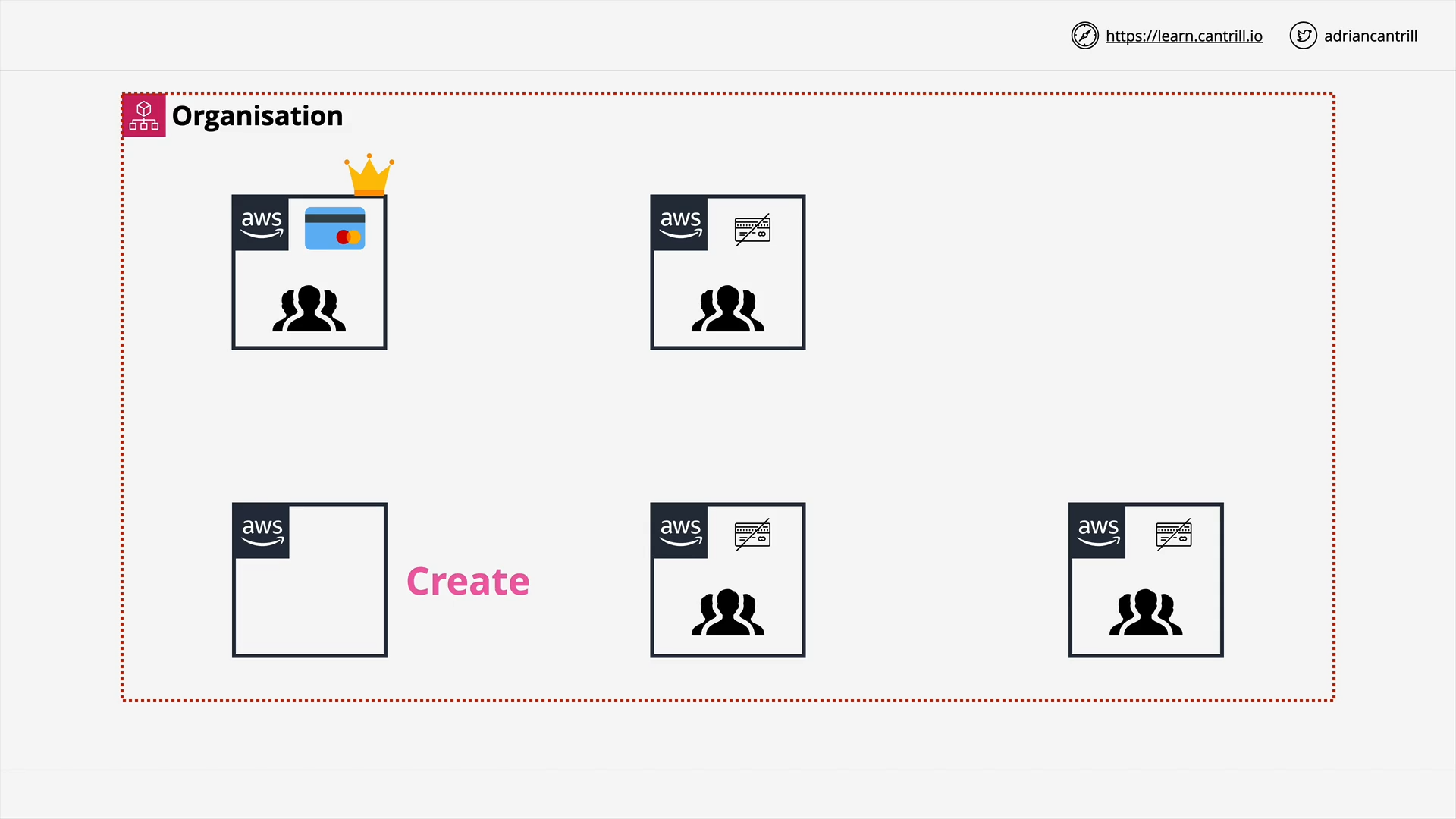 Create an account in your organization
Create an account in your organization
how to access an aws account in an aws organization?
- Using username/password of that AWS account to access that AWS account using its root user
- Using another account to switch role to that account’s IAM role
OrganizationAccountAccessRole - Using the AWS access portal with corporation credentials (Google, Facebook…)
[ASSOCIATE] Service Control Policies (SCPs) (12:44)
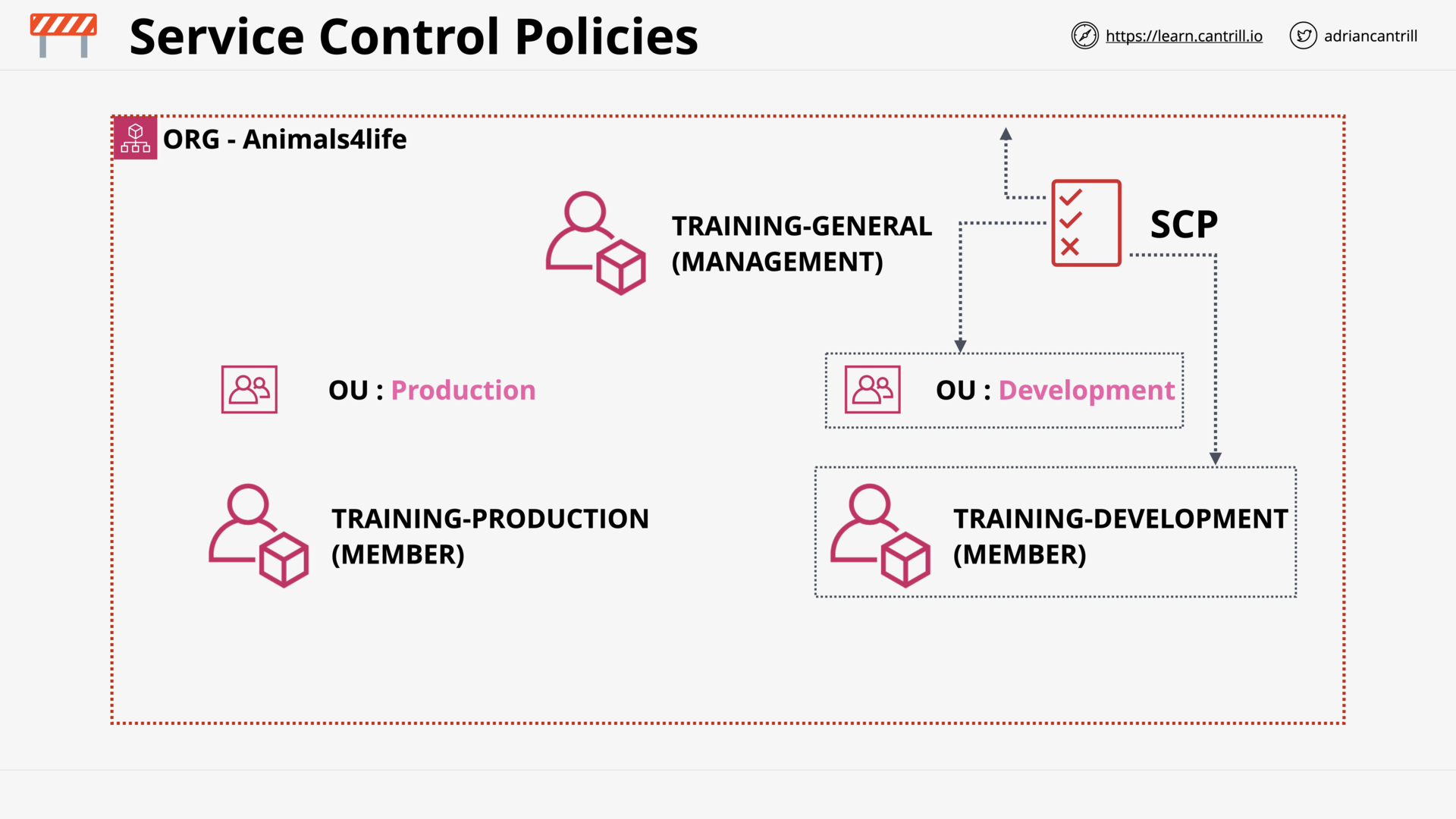 Service Control Policies (SCP)
Service Control Policies (SCP)
_.png) SCP controls account permissions in an organization
SCP controls account permissions in an organization
what does service control policies (scp) do?
SCP
-
restricts permissions for
- IAM users
- IAM roles
- including root user
in member accounts.
-
(do NOT grant permissions)
_.png) SCP - Deny List
SCP - Deny List
sgp - deny list strategy
With deny list strategy, all permissions are allowed unless explicitly denied.
This is the default behavior of AWS Organizations.
- By default, AWS Organizations attaches an AWS managed policy called
FullAWSAccessto all roots, OUs, and accounts. - You
- leave the default
FullAWSAccesspolicy in place (that allow “all”). - then attach additional policies that explicitly deny access to the unwanted services and actions.
- leave the default
_.png) SCP - Allow List
SCP - Allow List
sgp - allow list strategy
With allow list strategy, all permissions are denied unless explicitly allowed.
- By default, AWS Organizations attaches an AWS managed policy called
FullAWSAccessto all roots, OUs, and accounts. - You
- remove the default
FullAWSAccesspolicy - then attach additional policies that explicitly allow access to the wanted services and actions
- remove the default
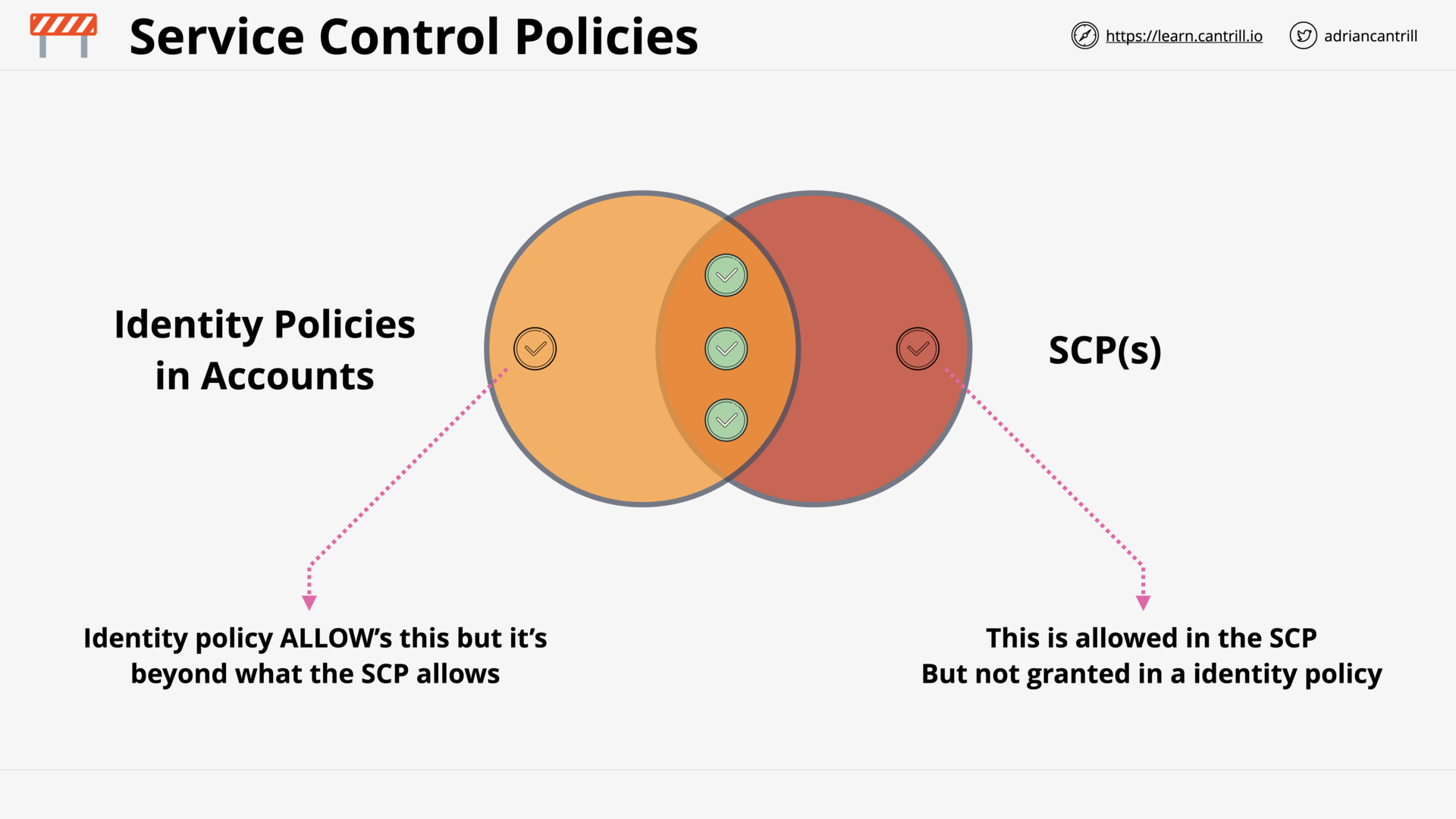 Identity Policies and SCPs
Identity Policies and SCPs
can scp restrict management account?
SCPs don’t affect users or roles in the management account. They affect only the member accounts in your organization.
can scp restrict root user?
SCP can un-directly control the member account’s root user (by control the account’s permission)
[ALL, DEMO] Using Service Control Policies (16:45)
[ASSOCIATE] CloudWatch Logs (7:16)
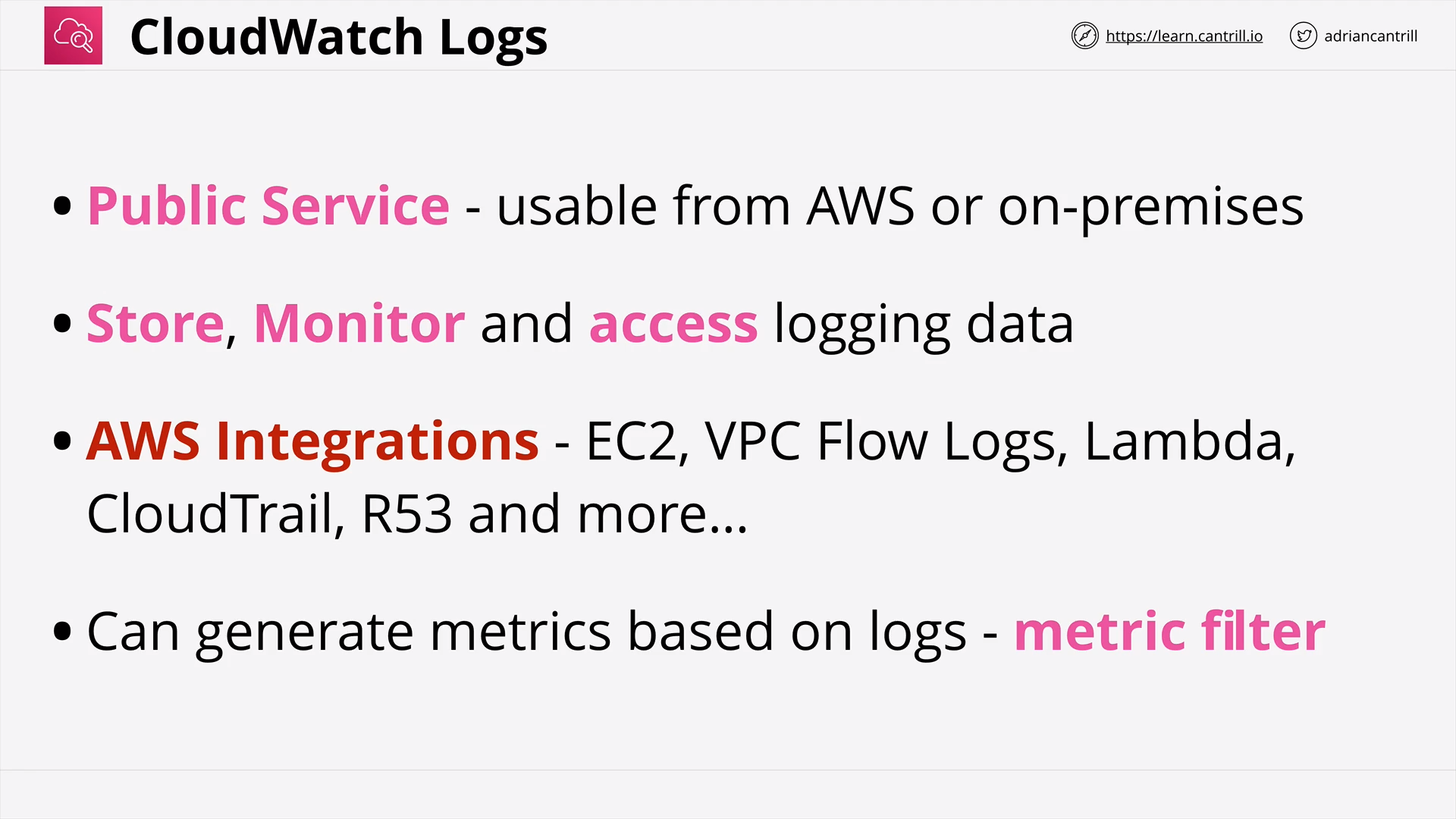 CloudWatch Logs - Basic
CloudWatch Logs - Basic
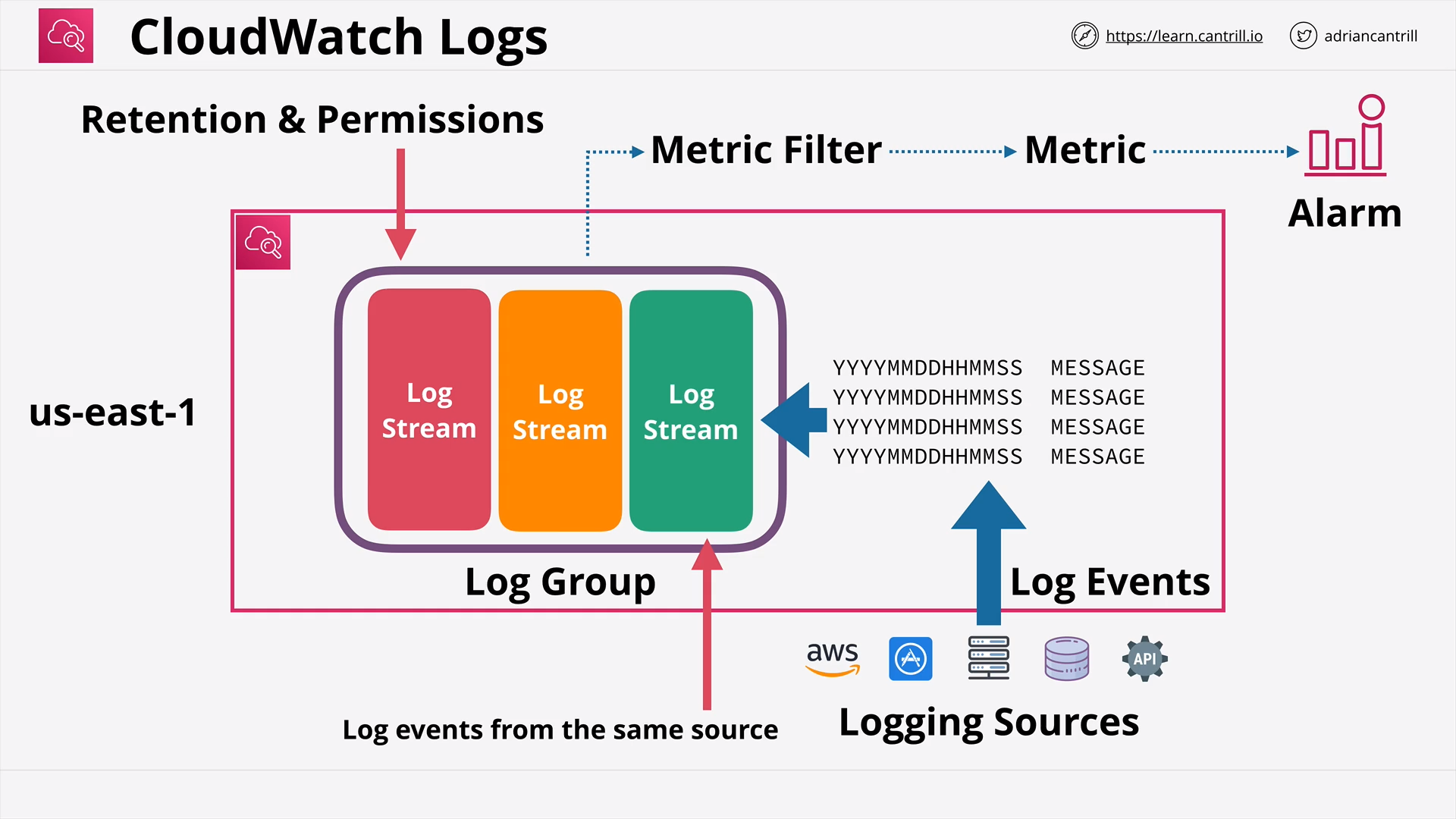
CloudWatch Logs - Architecture
what is log event?
what is log stream?
what is log group?
[ASSOCIATE] CloudTrail (11:40)
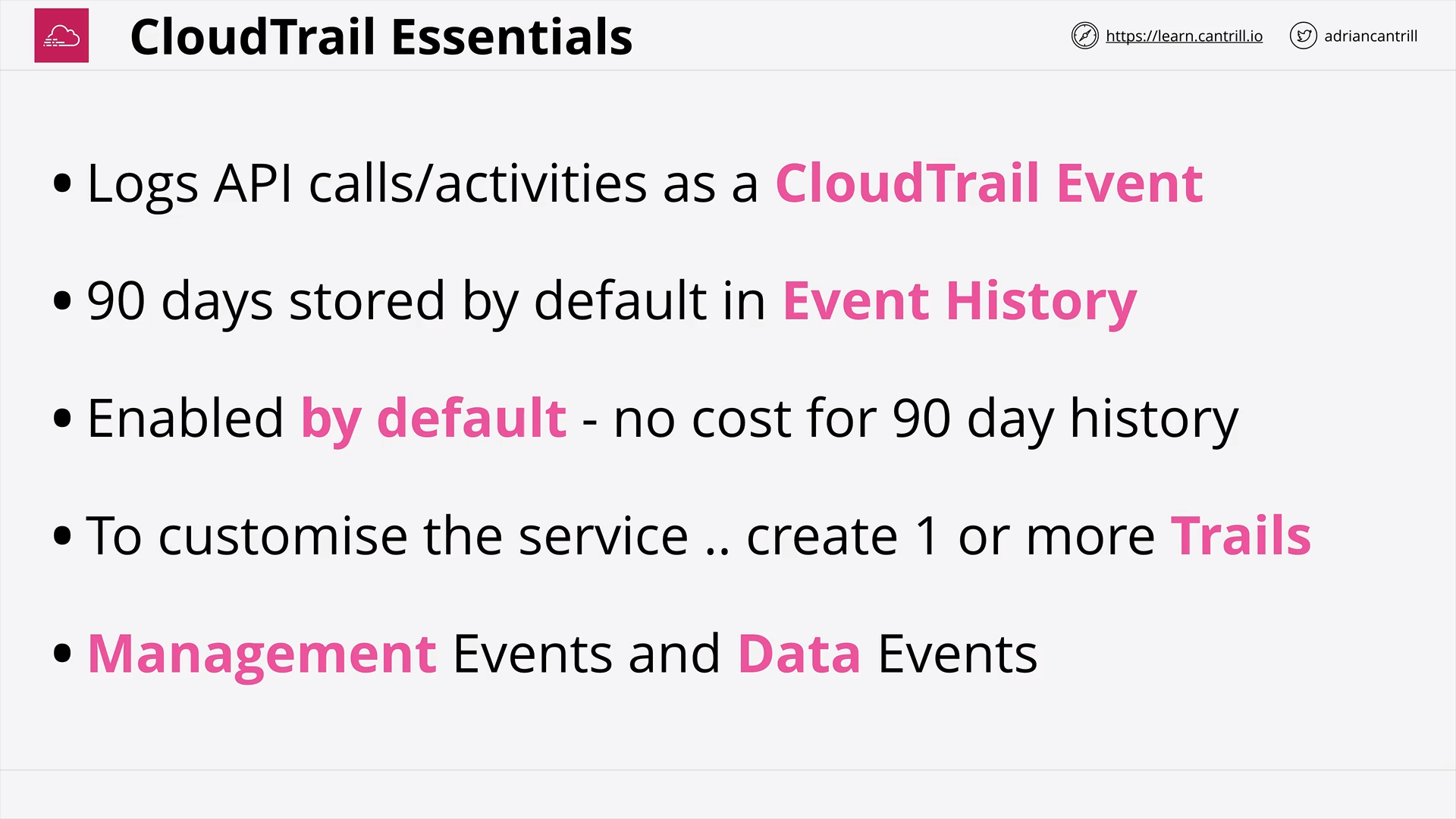
what is cloudtrail event/trail?
how long is the default cloudtrail history?
in cloudtrail, what are management events / data events?
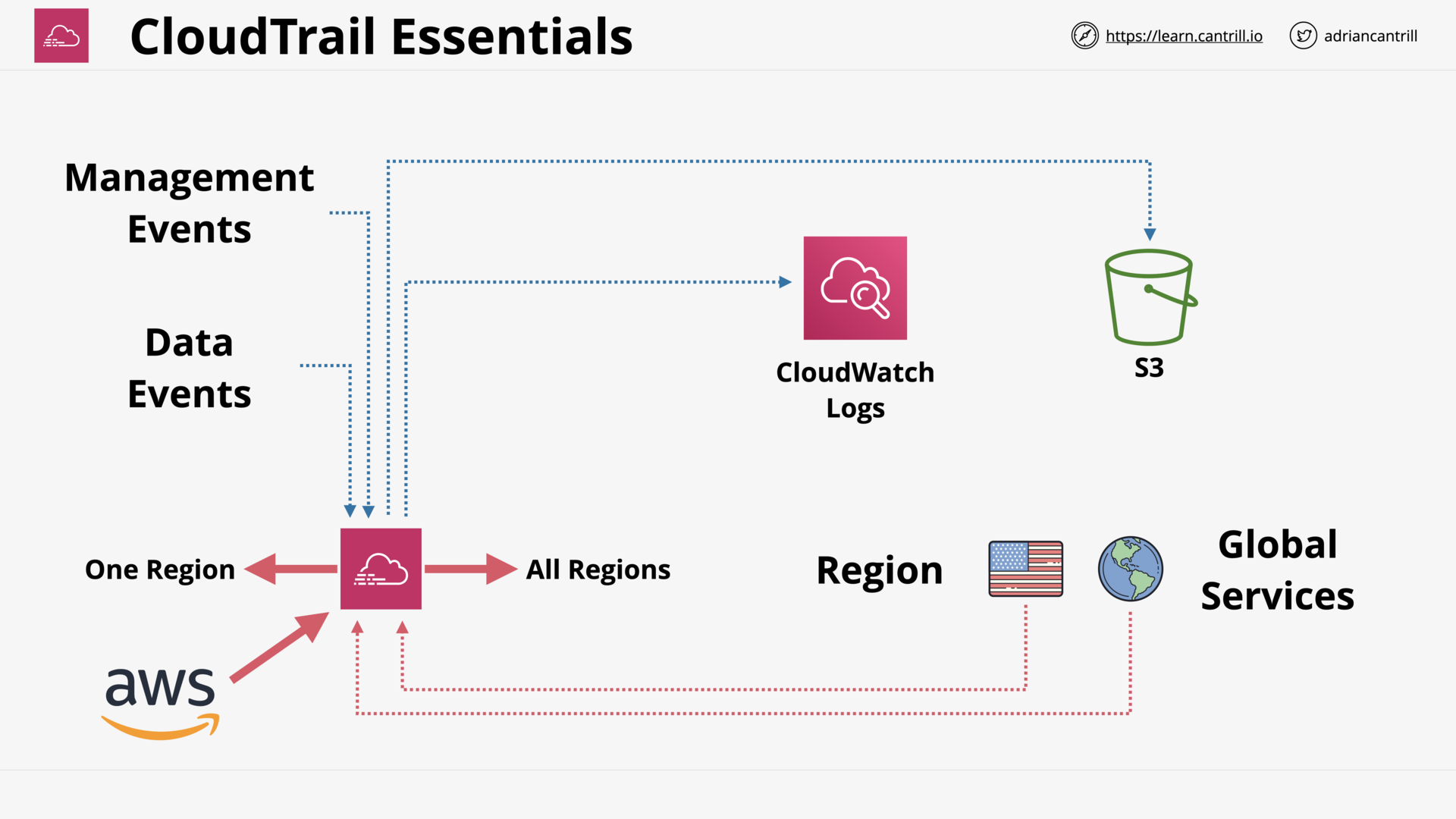
how to implement a central log store for aws organization?
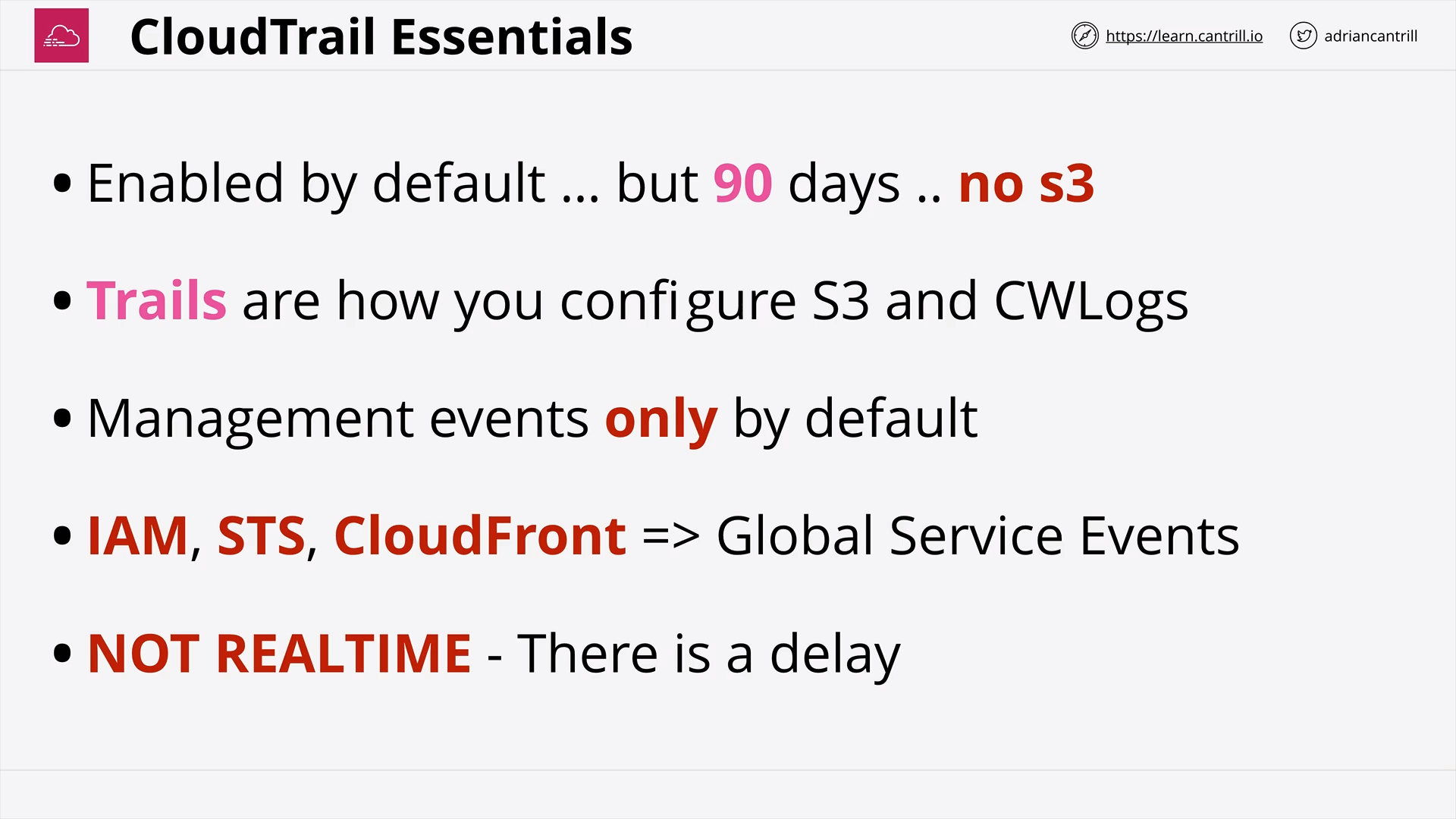
is cloudtrail realtime?
[ALL, DEMO] Implementing an Organizational Trail (18:23)
AWS Control Tower 101 (15:42)
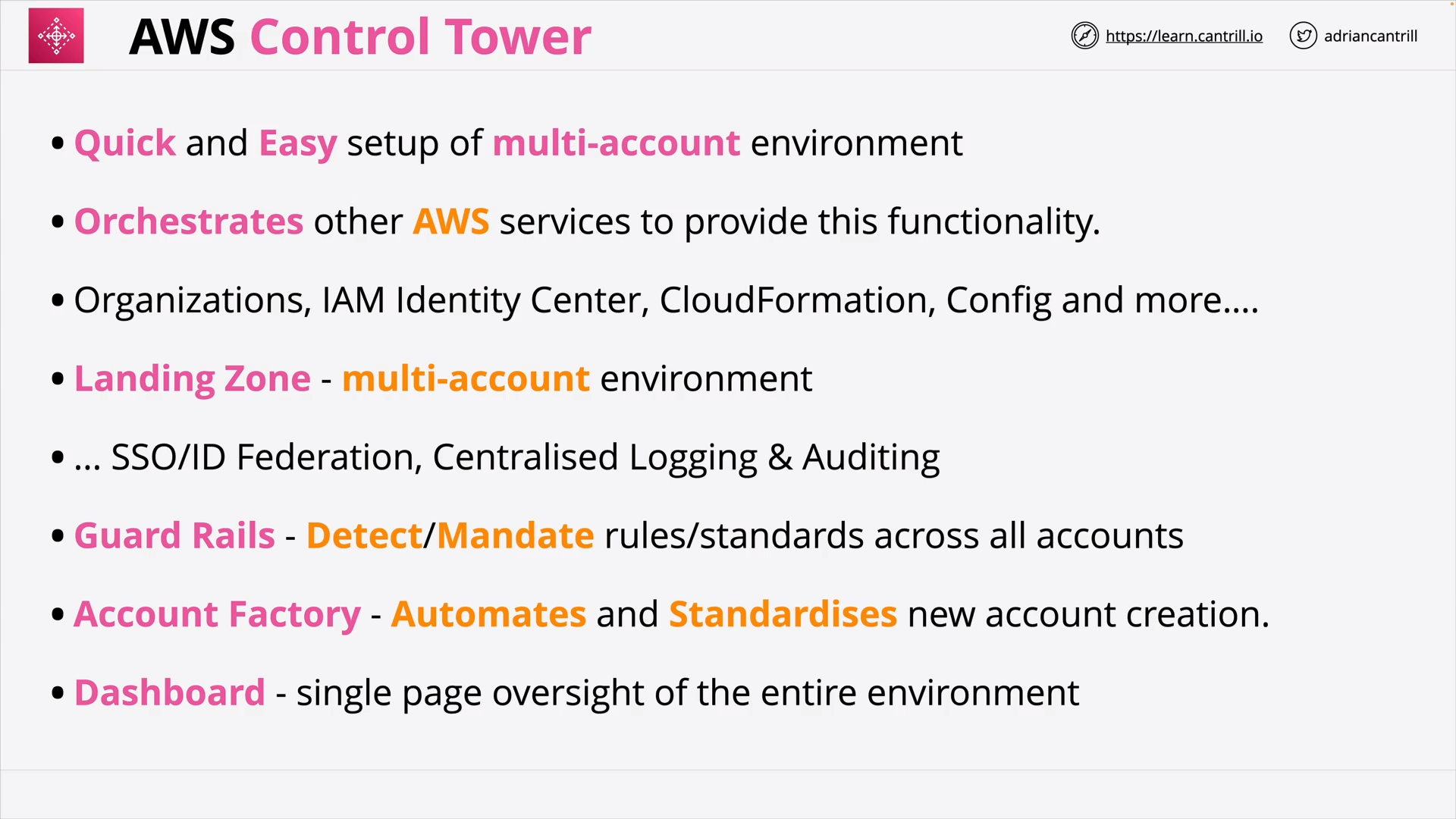
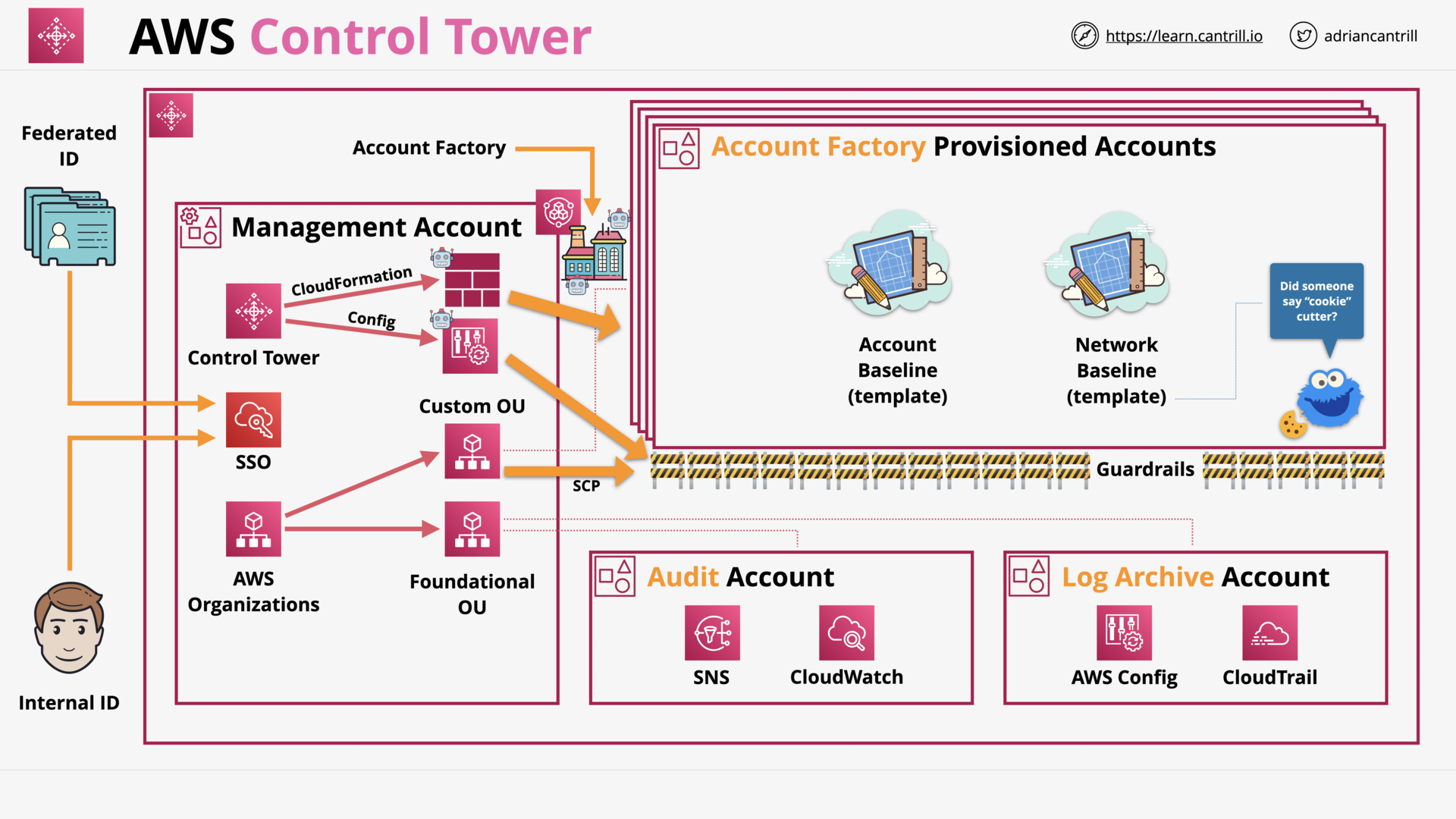
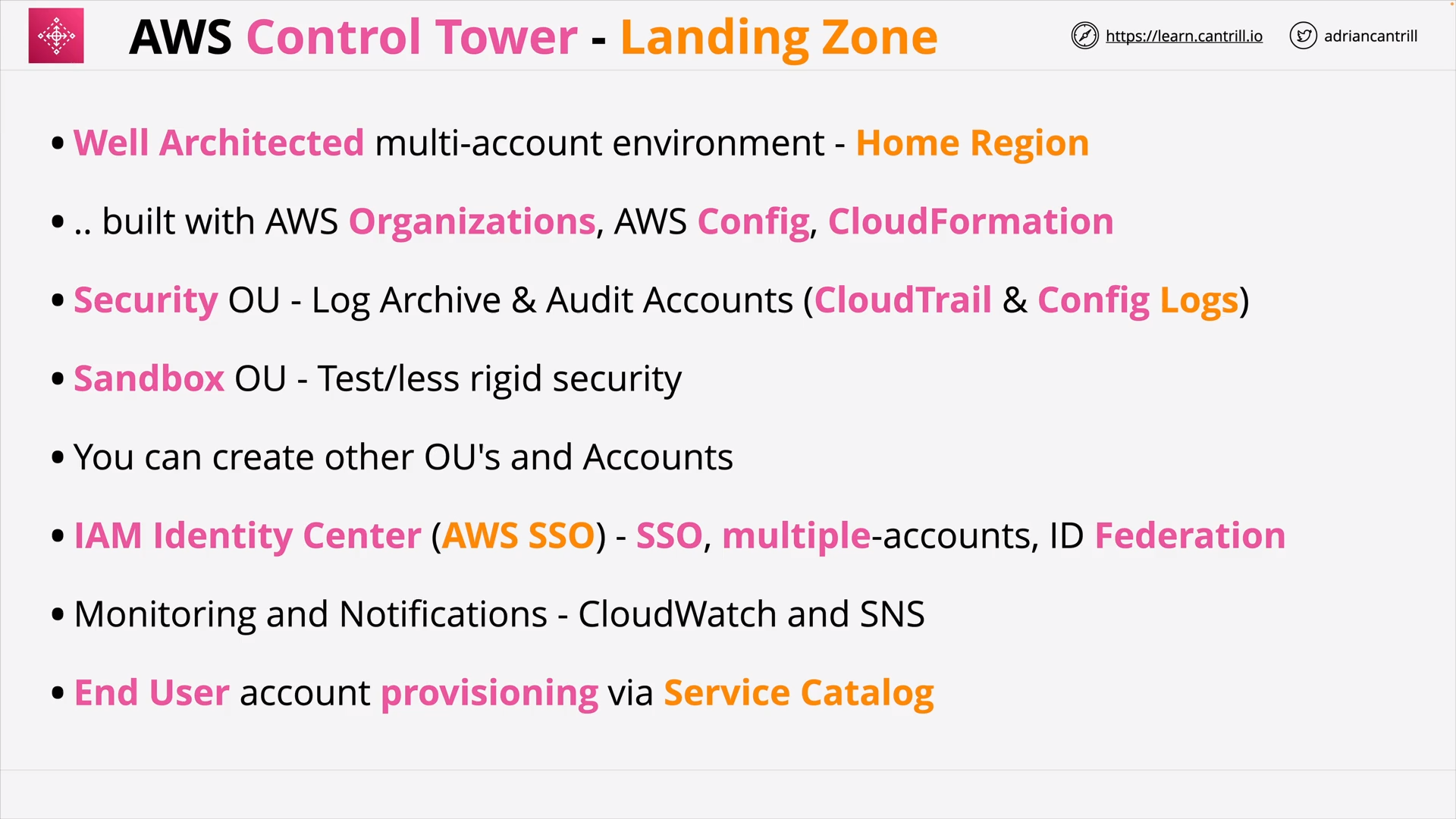
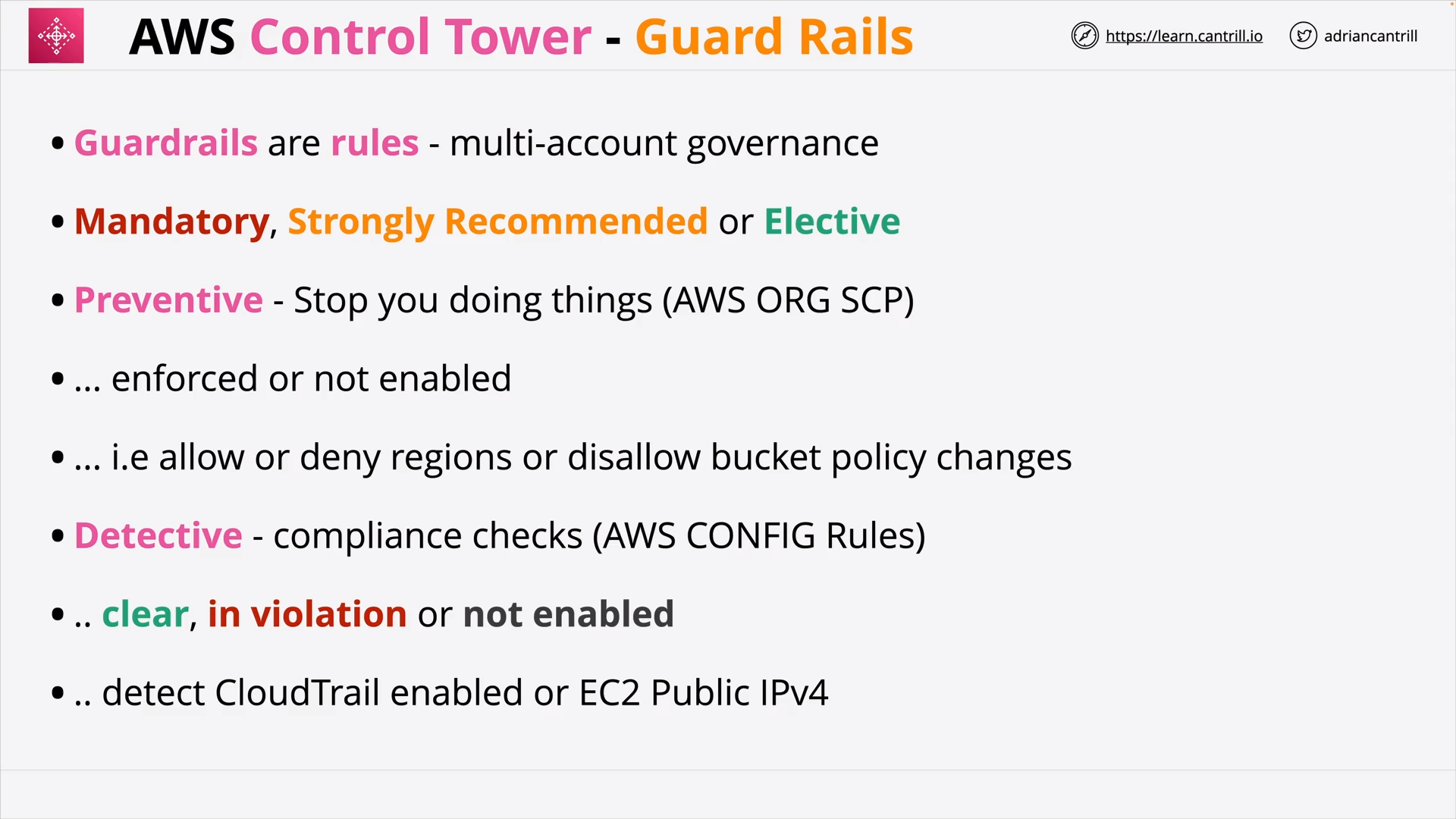
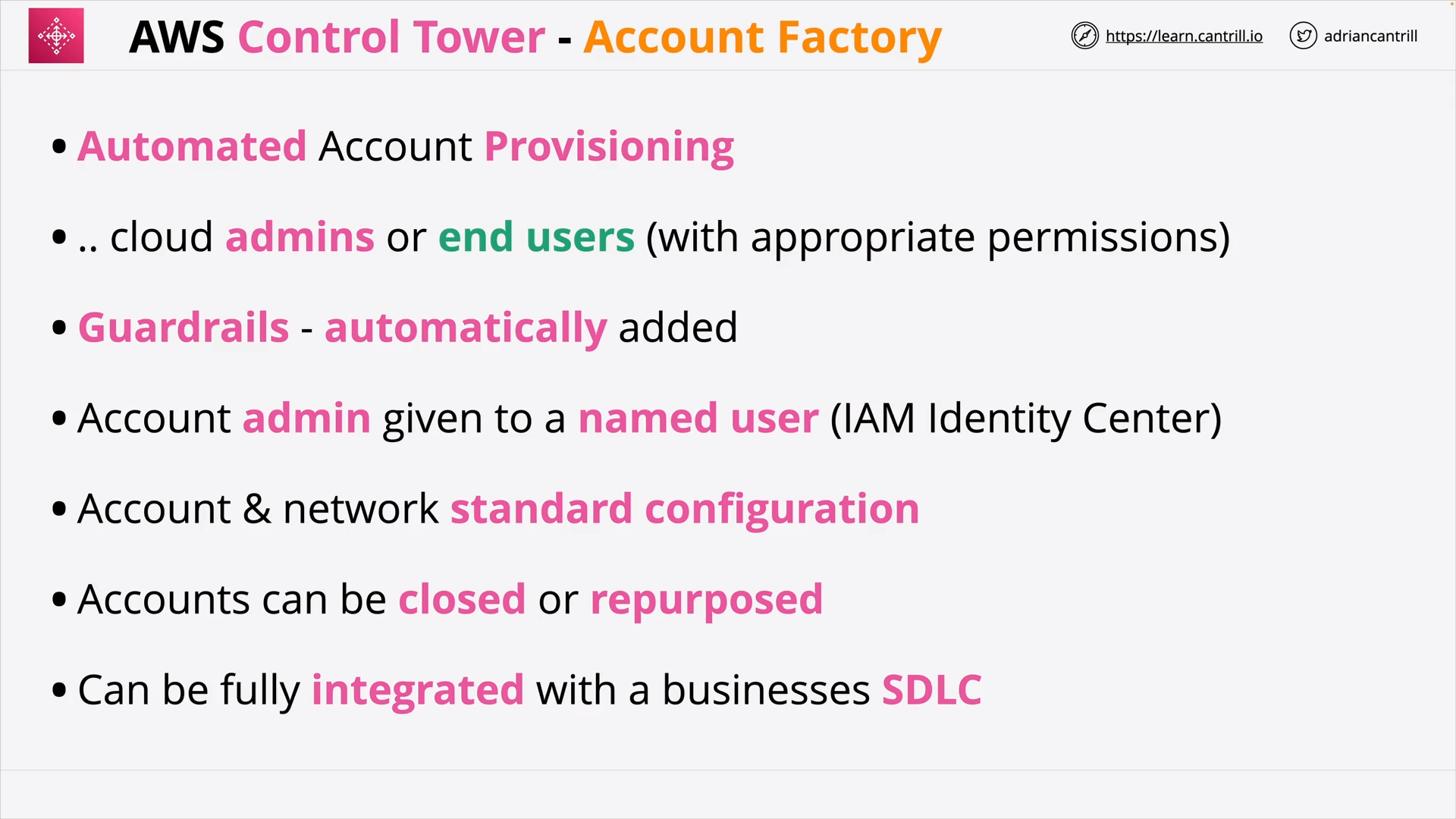
IAM & Orgs Section Quiz
SIMPLE STORAGE SERVICE (S3)
S3 Security (Resource Policies & ACLs) (18:19)
 S3 is private by default
S3 is private by default
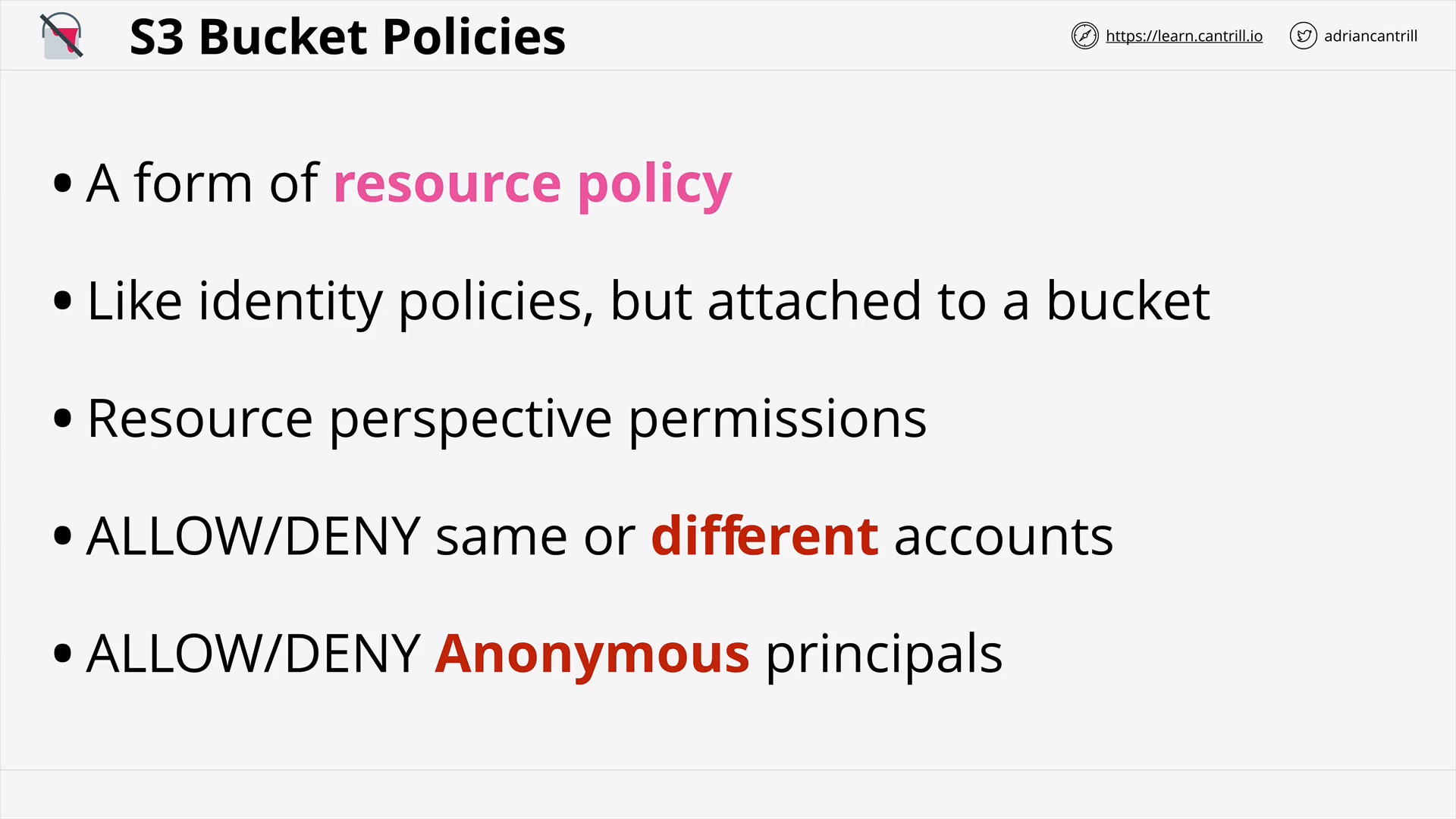 S3 Bucket Policies
S3 Bucket Policies
/00_LEARNINGAIDS/S3Security-1.png) S3 Bucket Polices support different accounts & anonymous principles
S3 Bucket Polices support different accounts & anonymous principles
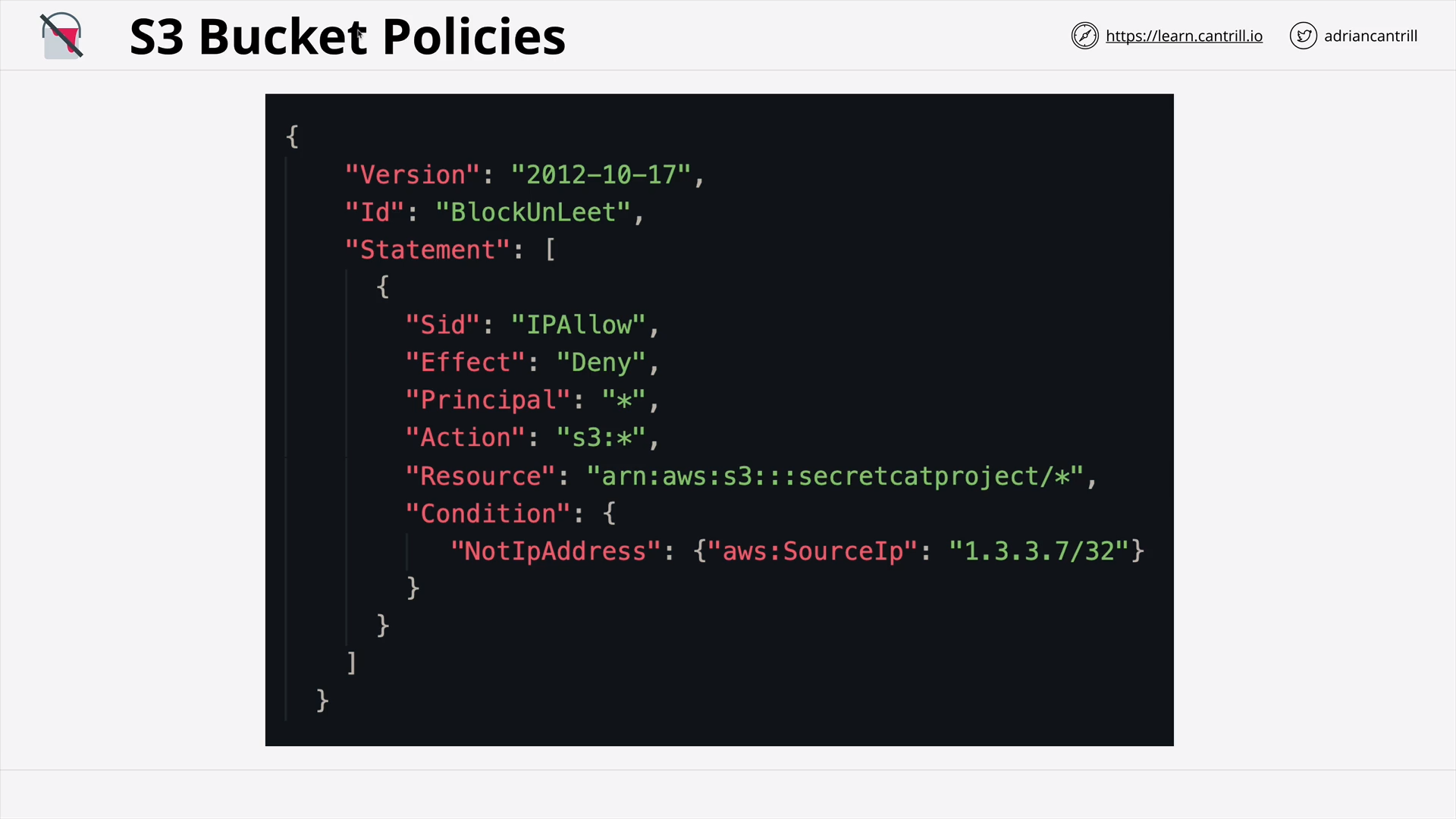 S3 Bucket Polices - Condition
S3 Bucket Polices - Condition
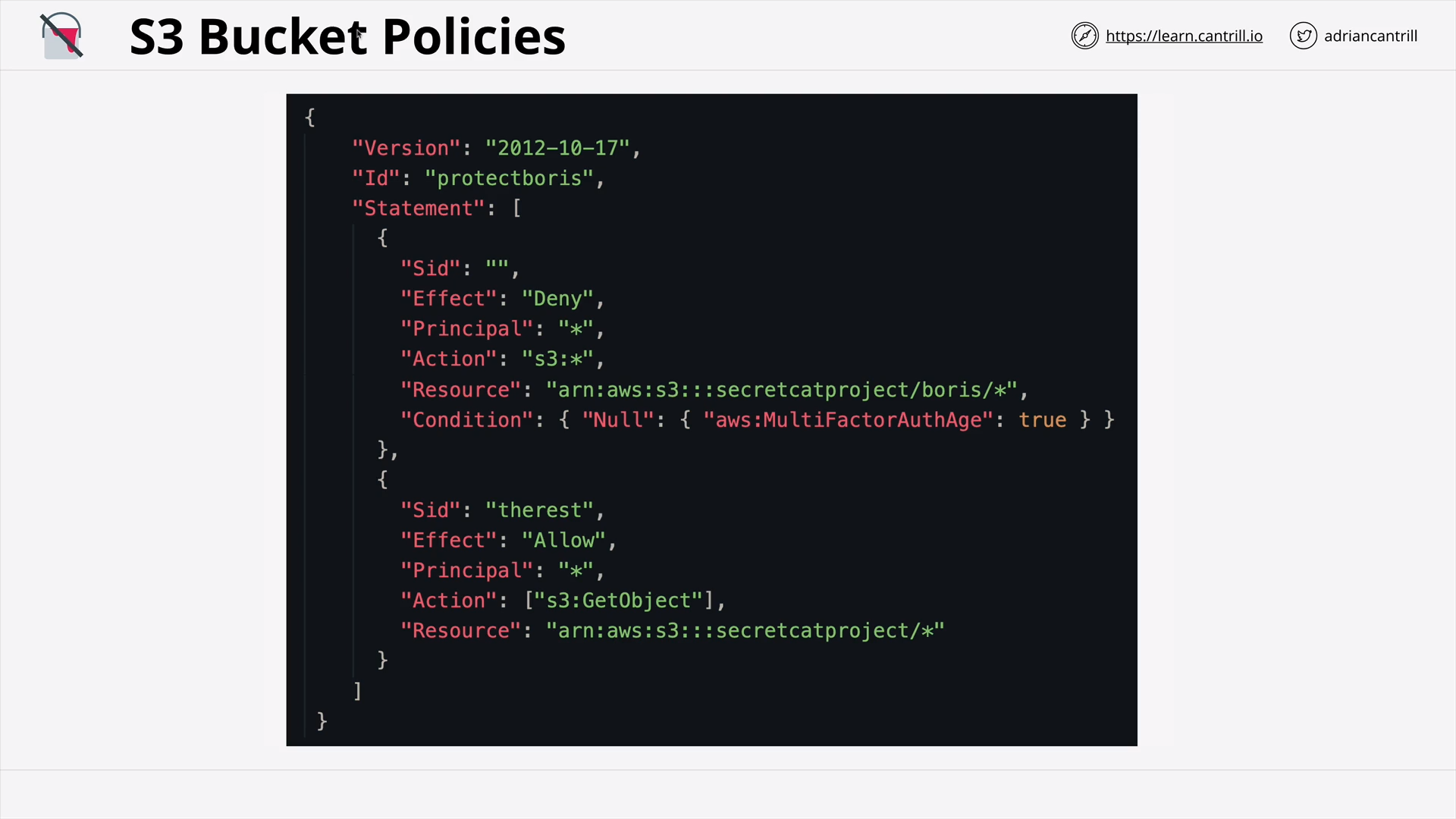 S3 Bucket Polices - Deny - Allow - Deny
S3 Bucket Polices - Deny - Allow - Deny
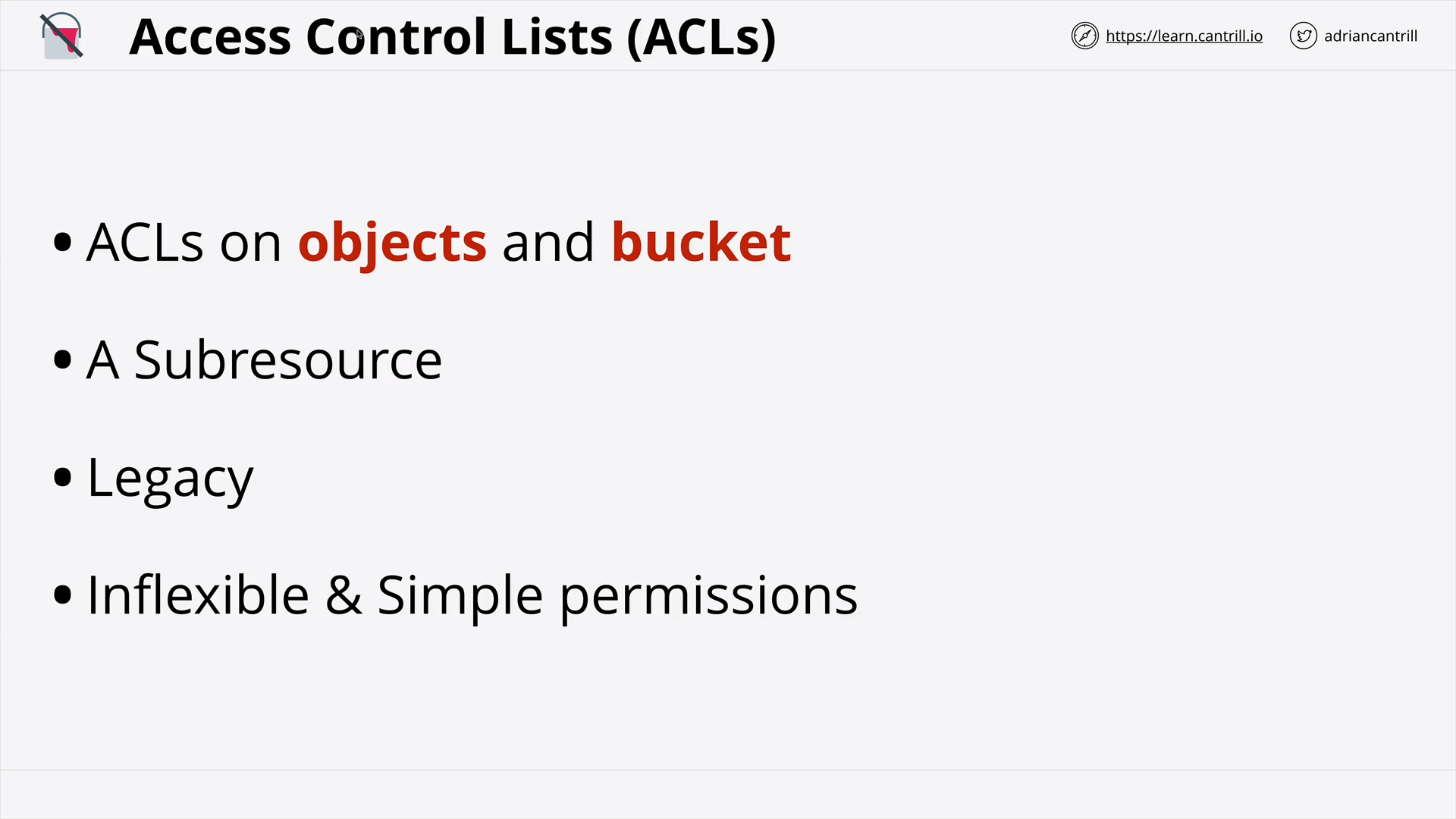 [Legacy] Access Control Lists (ACLS)
[Legacy] Access Control Lists (ACLS)
/00_LEARNINGAIDS/S3Security-2.png) Block Public Access
Block Public Access
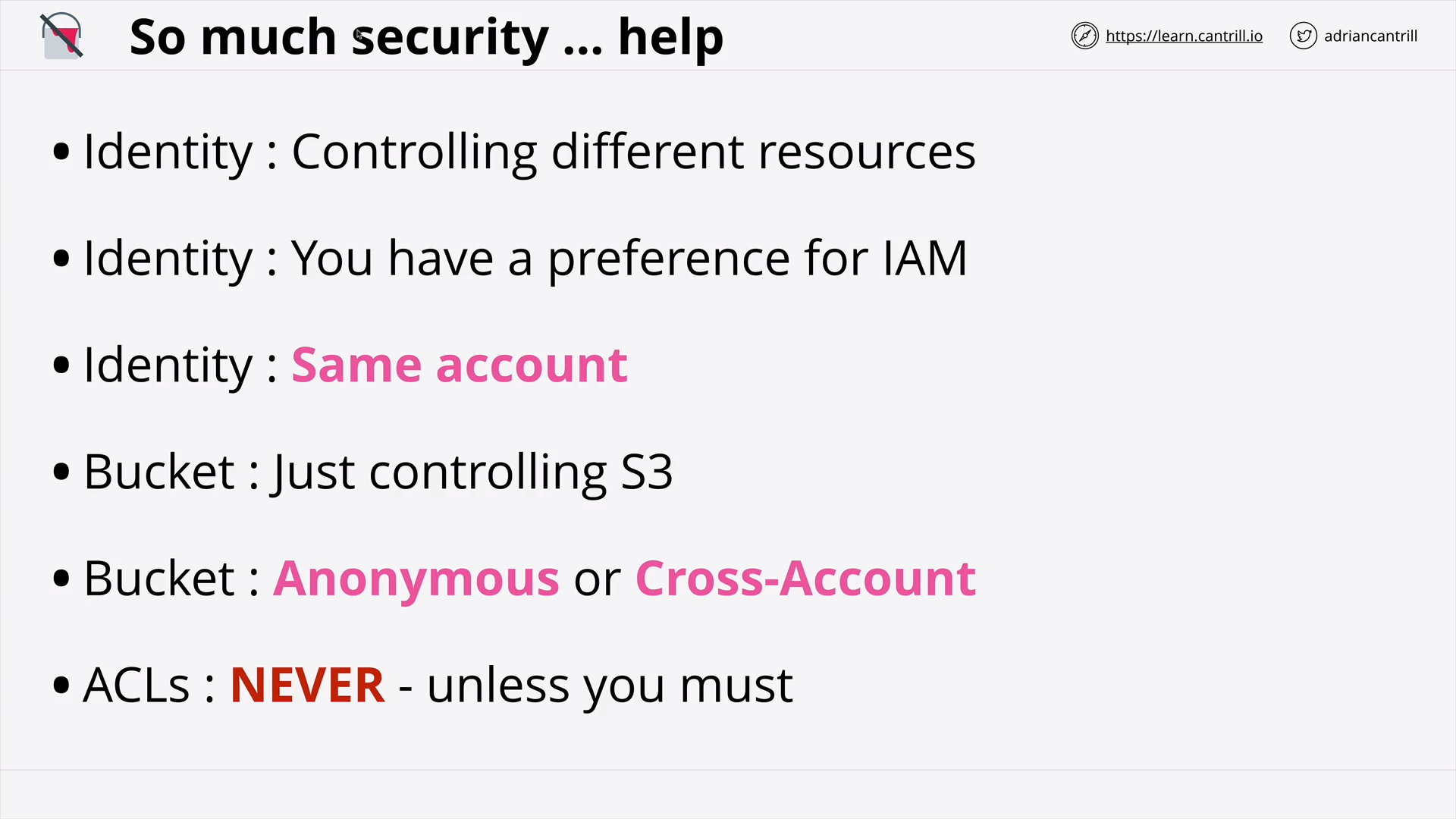 Identity Policies - Bucket Polices - ACLs
Identity Policies - Bucket Polices - ACLs
S3 Static Hosting (10:36)
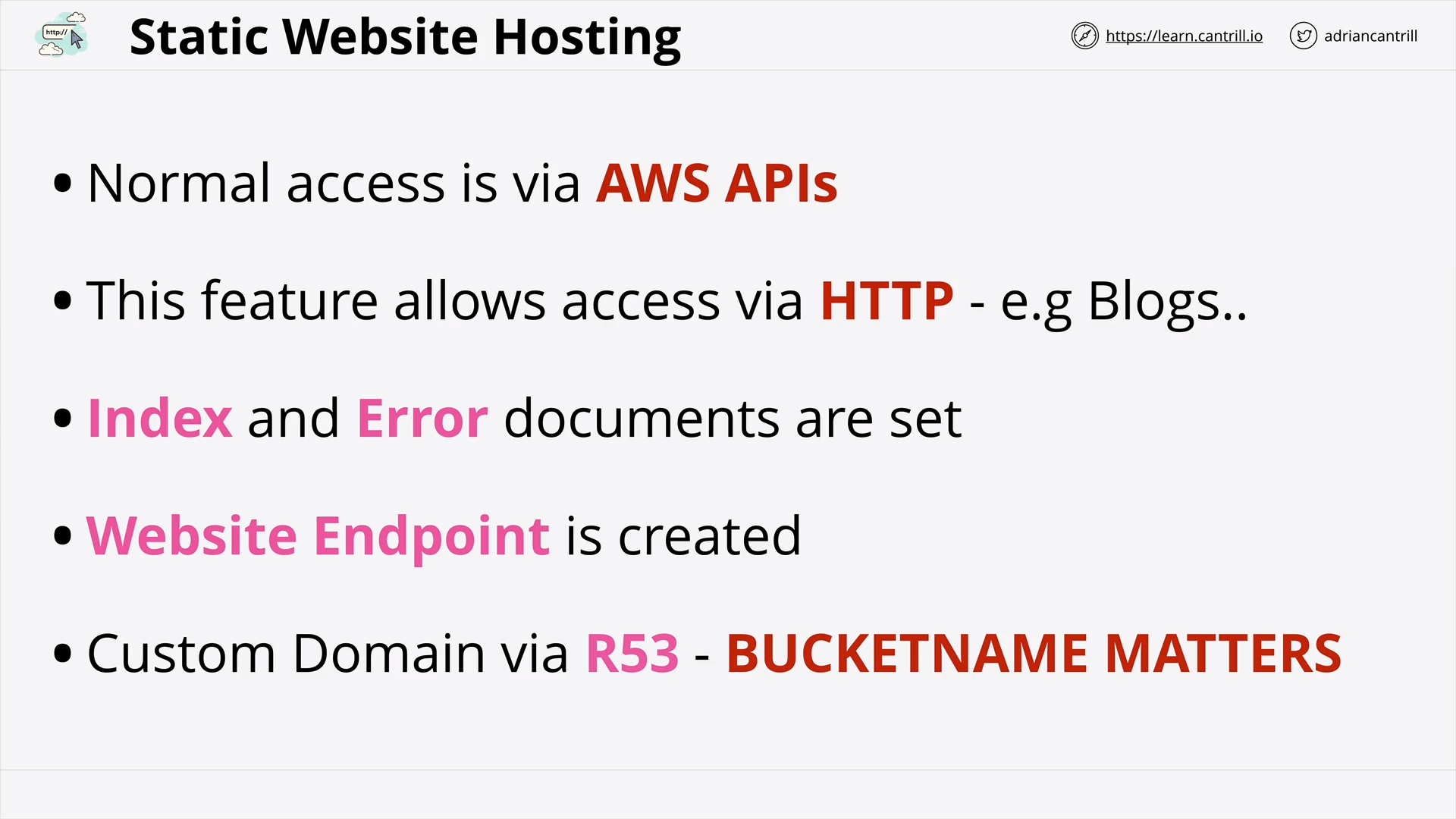
what is the normal access to s3 object?
Via AWS APIs.
what is s3 website endpoint?
The endpoint to access the S3 bucket via HTTP.
/00_LEARNINGAIDS/S3StaticHosting-1.png) Out-of-band pages
Out-of-band pages
[DEMO] Creating a static website with S3 (17:55)
Object Versioning & MFA Delete (7:41)
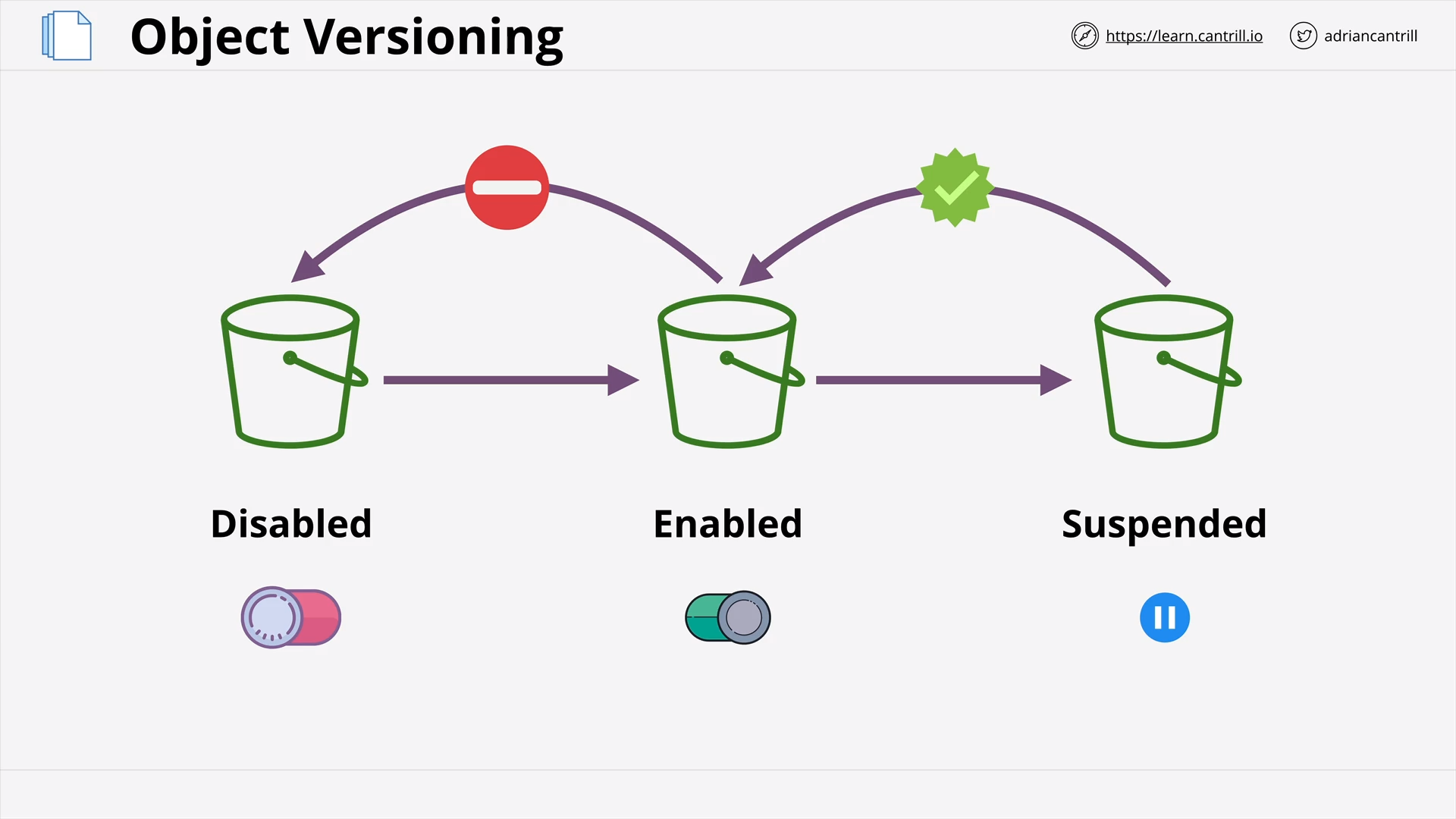 Object Versioning cannot be switched off
Object Versioning cannot be switched off
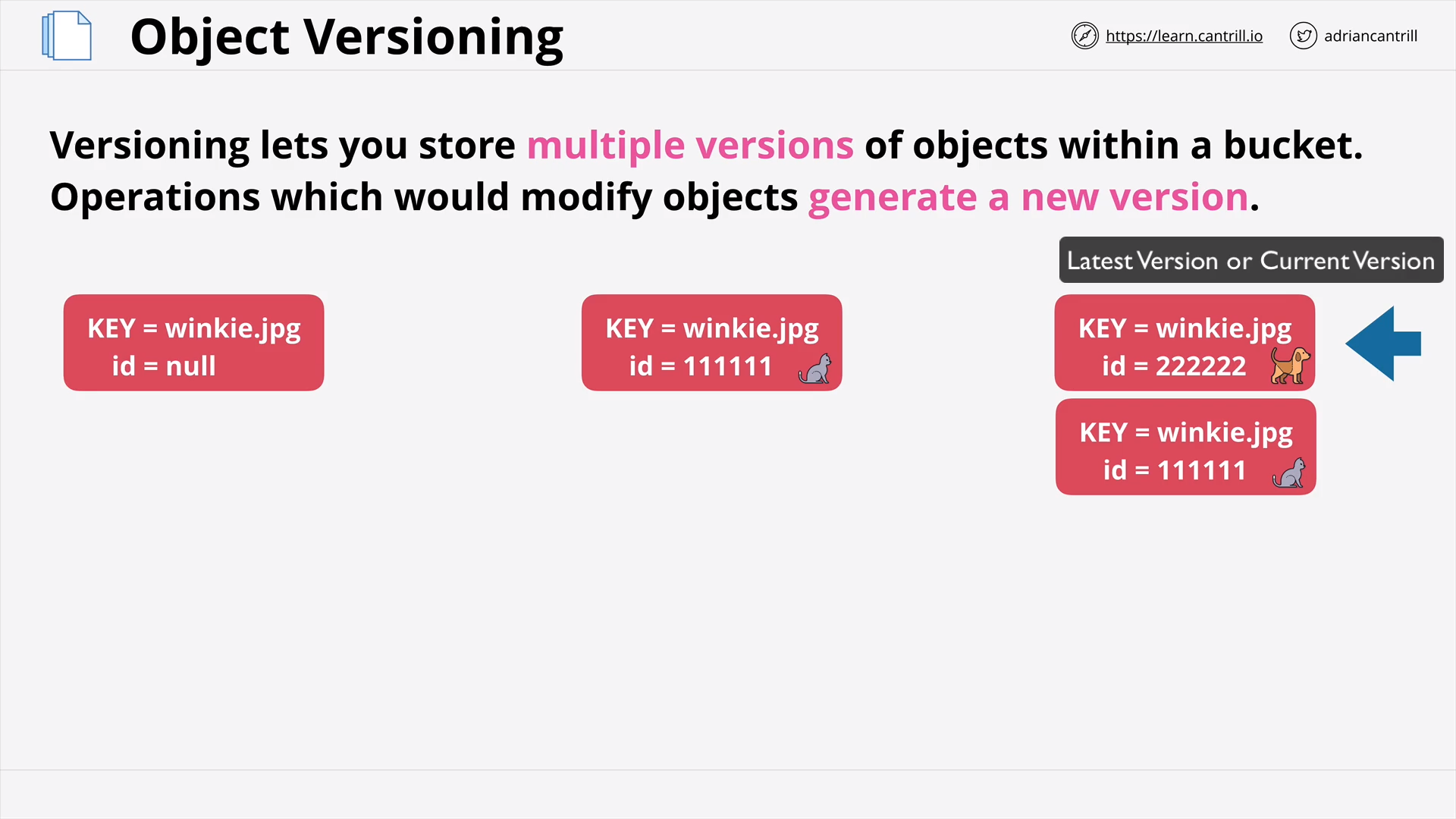 Object Versioning: store multiple versions of objects
Object Versioning: store multiple versions of objects
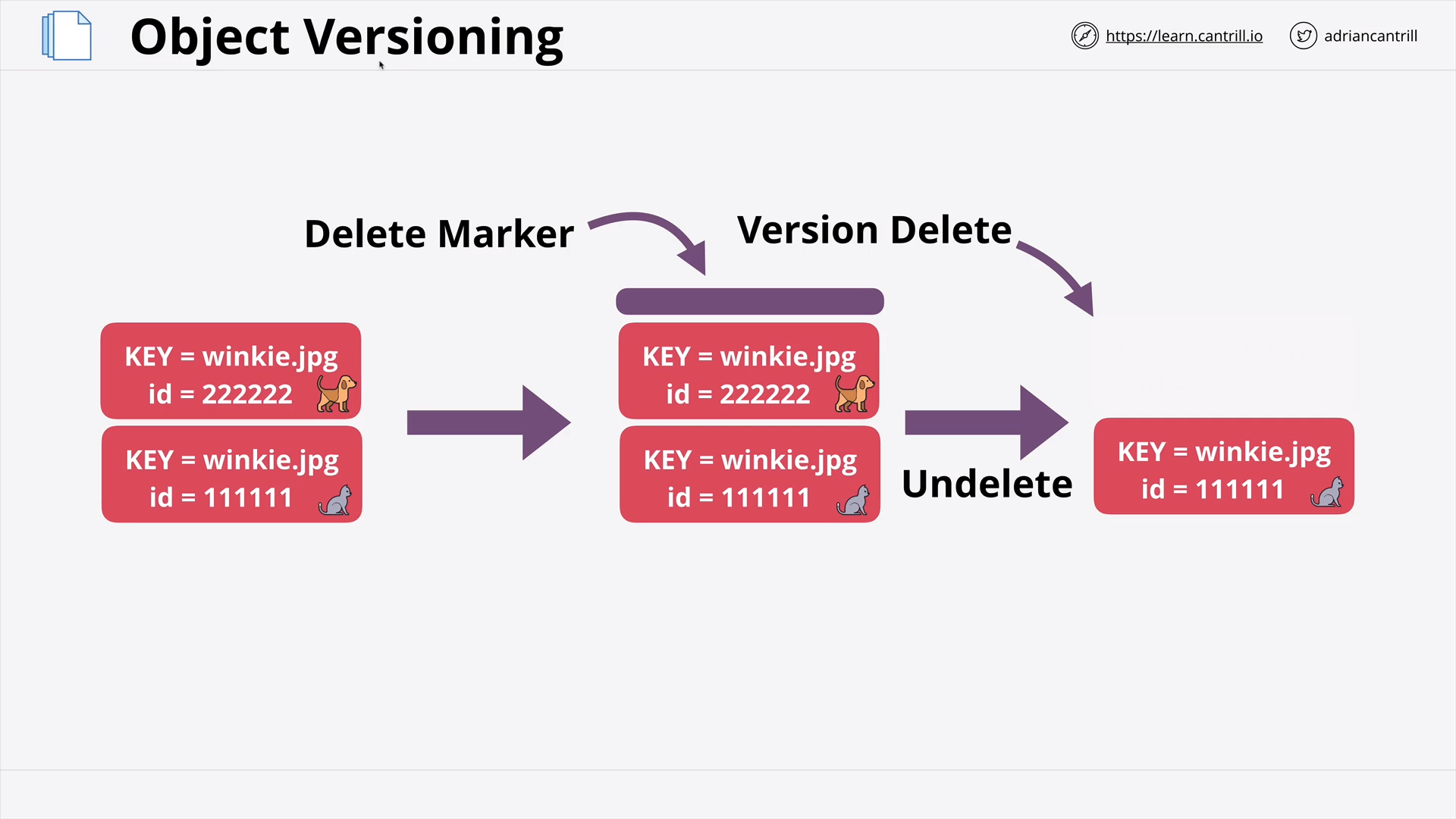 Object Versioning: DeleteMaker & Version delete
Object Versioning: DeleteMaker & Version delete
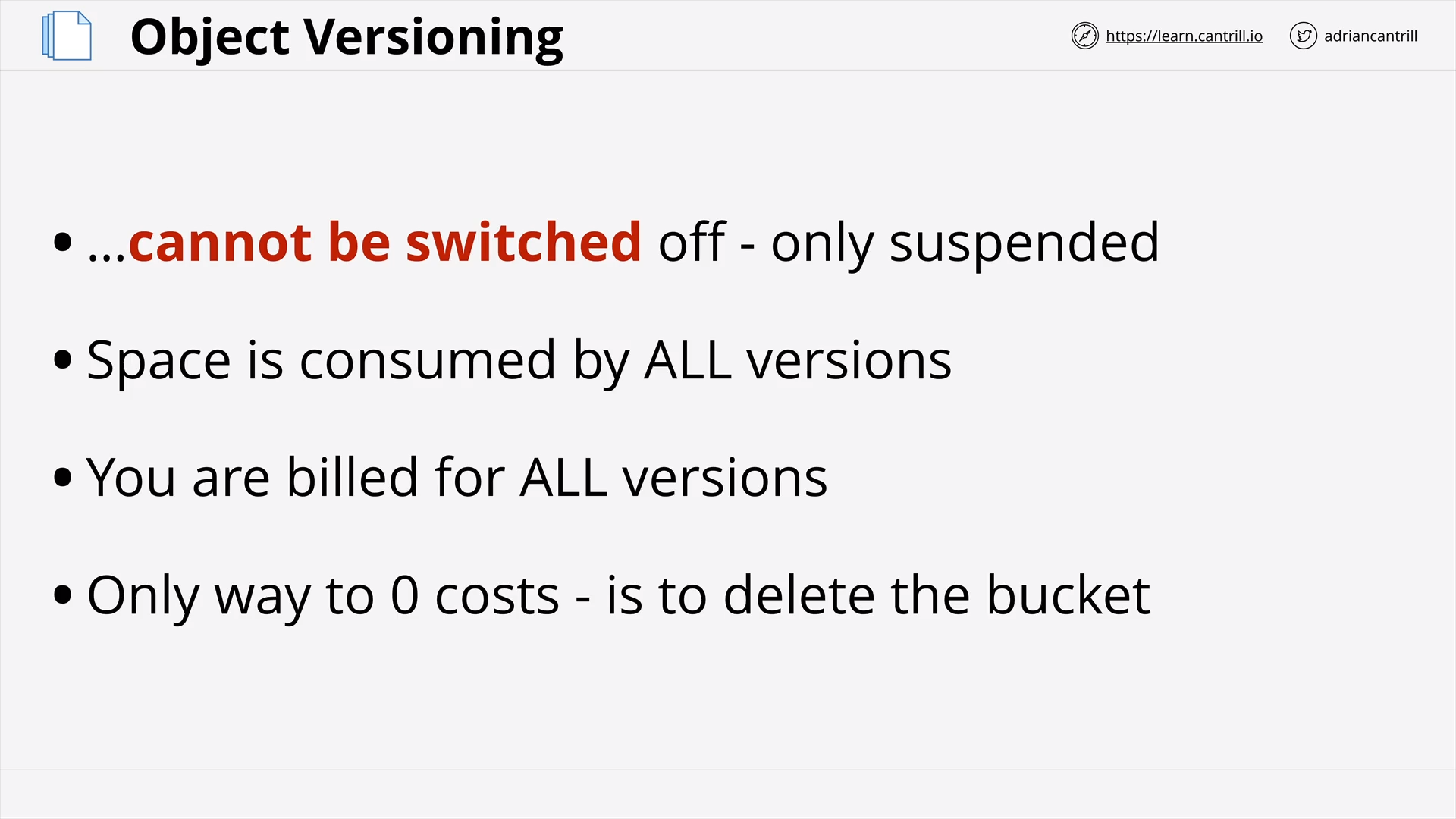 Object Versioning: All versions will be billed
Object Versioning: All versions will be billed
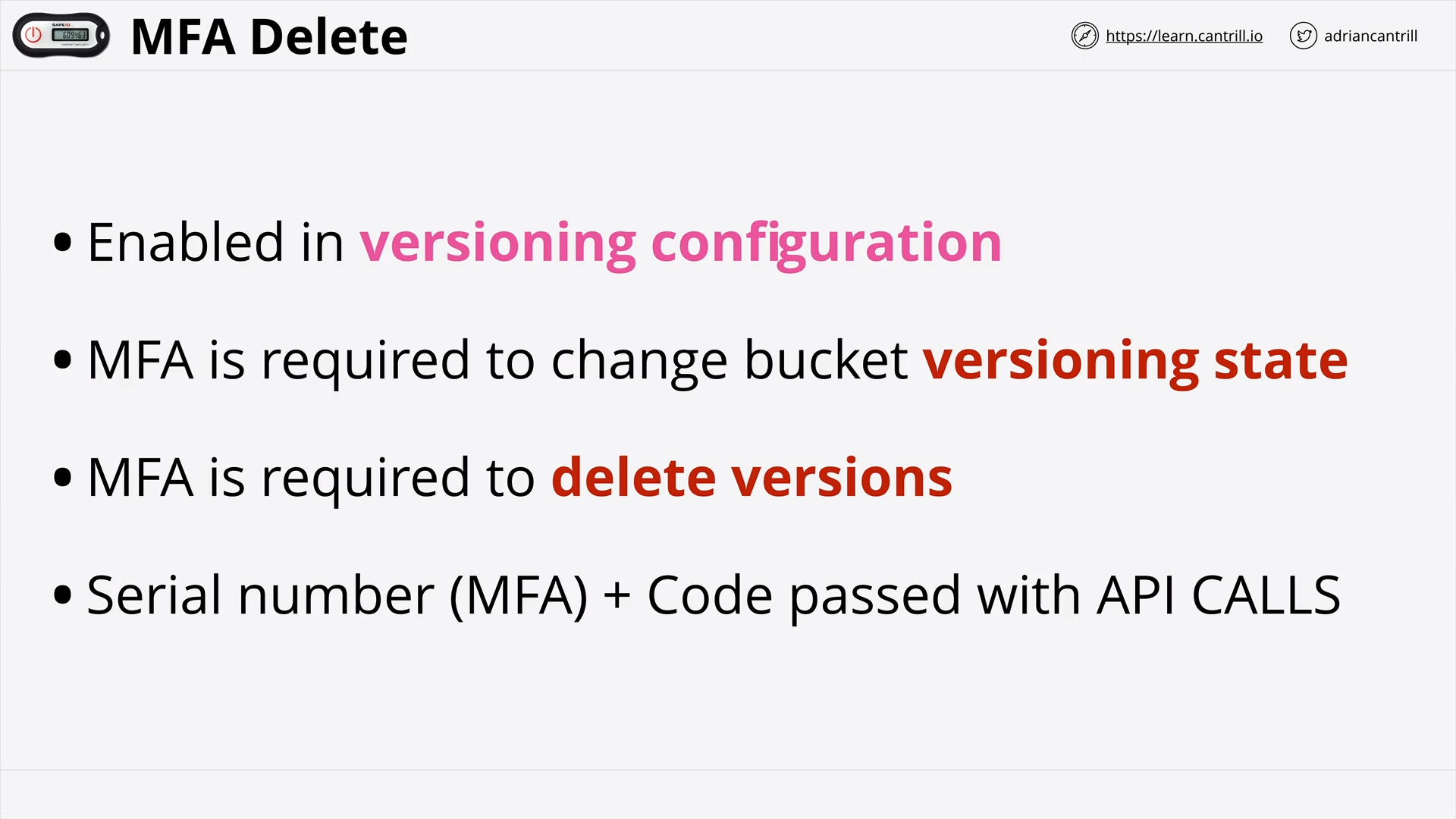 Object Versioning: MFA for suspending bucket versioning and deleting object versions
Object Versioning: MFA for suspending bucket versioning and deleting object versions
[DEMO] - S3 Versioning (15:45)
S3 Performance Optimization (11:42)
/00_LEARNINGAIDS/S3Performance-1.png) Global Architecture
Global Architecture
/00_LEARNINGAIDS/S3Performance-2.png) Single PUT Upload
Single PUT Upload
/00_LEARNINGAIDS/S3Performance-3.png) Multipart Upload
Multipart Upload
/00_LEARNINGAIDS/S3Performance-4.png) S3 Transfer Acceleration
S3 Transfer Acceleration
what is s3 transfer acceleration?
[DEMO] - S3 Performance (5:06)
Key Management Service (KMS) (18:38)
__le.png) Key Management Service (KMS)
Key Management Service (KMS)
__le.png) KMS Keys
KMS Keys
__le.png) CreateKey & Encrypt using KMS
CreateKey & Encrypt using KMS
__le.png) Decrypt using KMS
Decrypt using KMS
__le.png) Data Encryption Keys (DEKs)
Data Encryption Keys (DEKs)
__le.png) KMS Keys - Key Concepts
KMS Keys - Key Concepts
/00_LEARNINGAIDS/KMS-3.png) Key Policies and Security
Key Policies and Security
[DEMO] KMS - Encrypting the battleplans with KMS (12:43)
S3 Object Encryption CSE/SSE (23:31)
 S3 Bucket aren’t encrypted
S3 Bucket aren’t encrypted
/00_LEARNINGAIDS/S3Encryption-1.png) CSE vs SSE
CSE vs SSE
 SSE-C / SSE-S3 / SS3-KMS
SSE-C / SSE-S3 / SS3-KMS
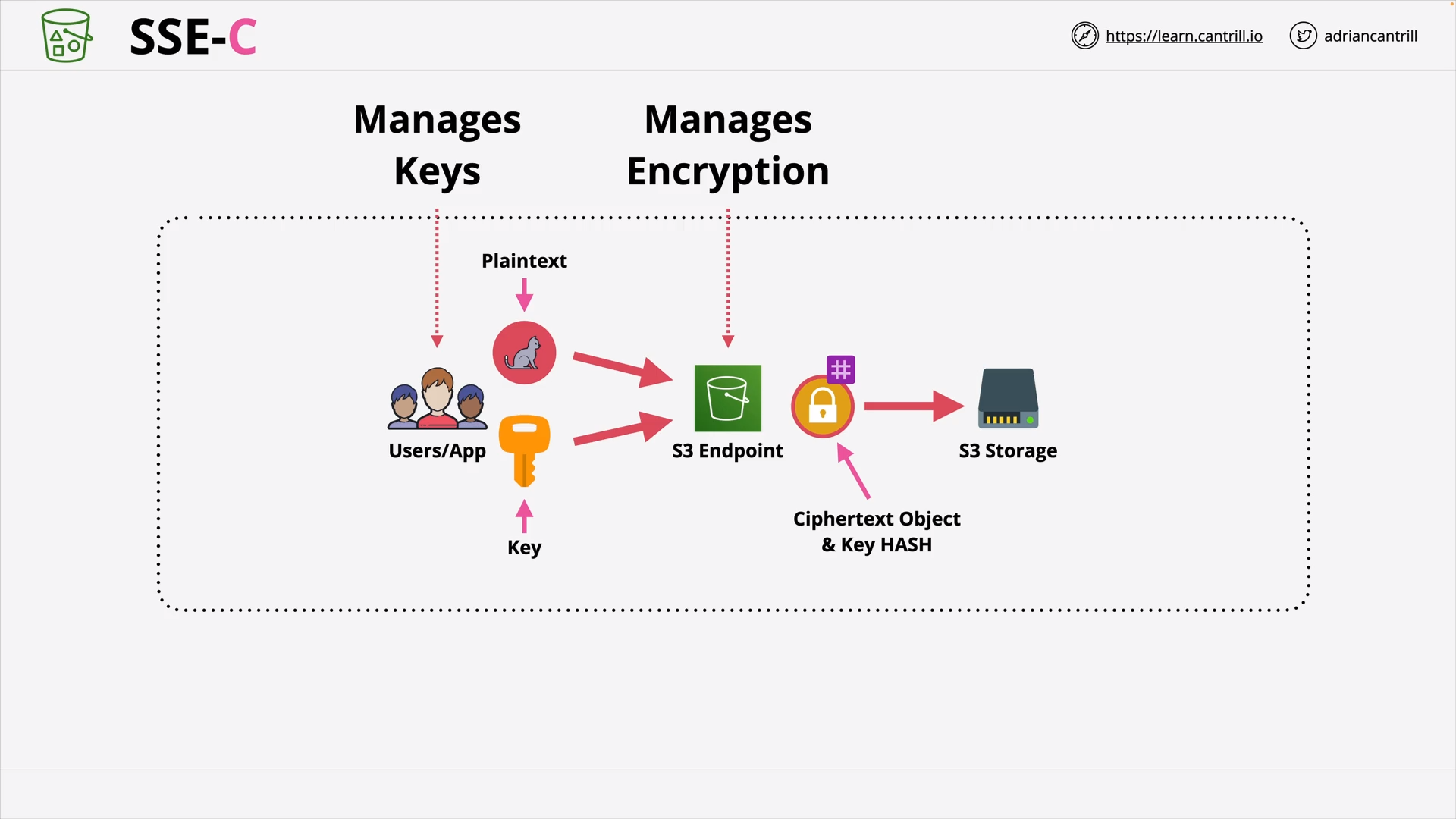 SSE-C
SSE-C
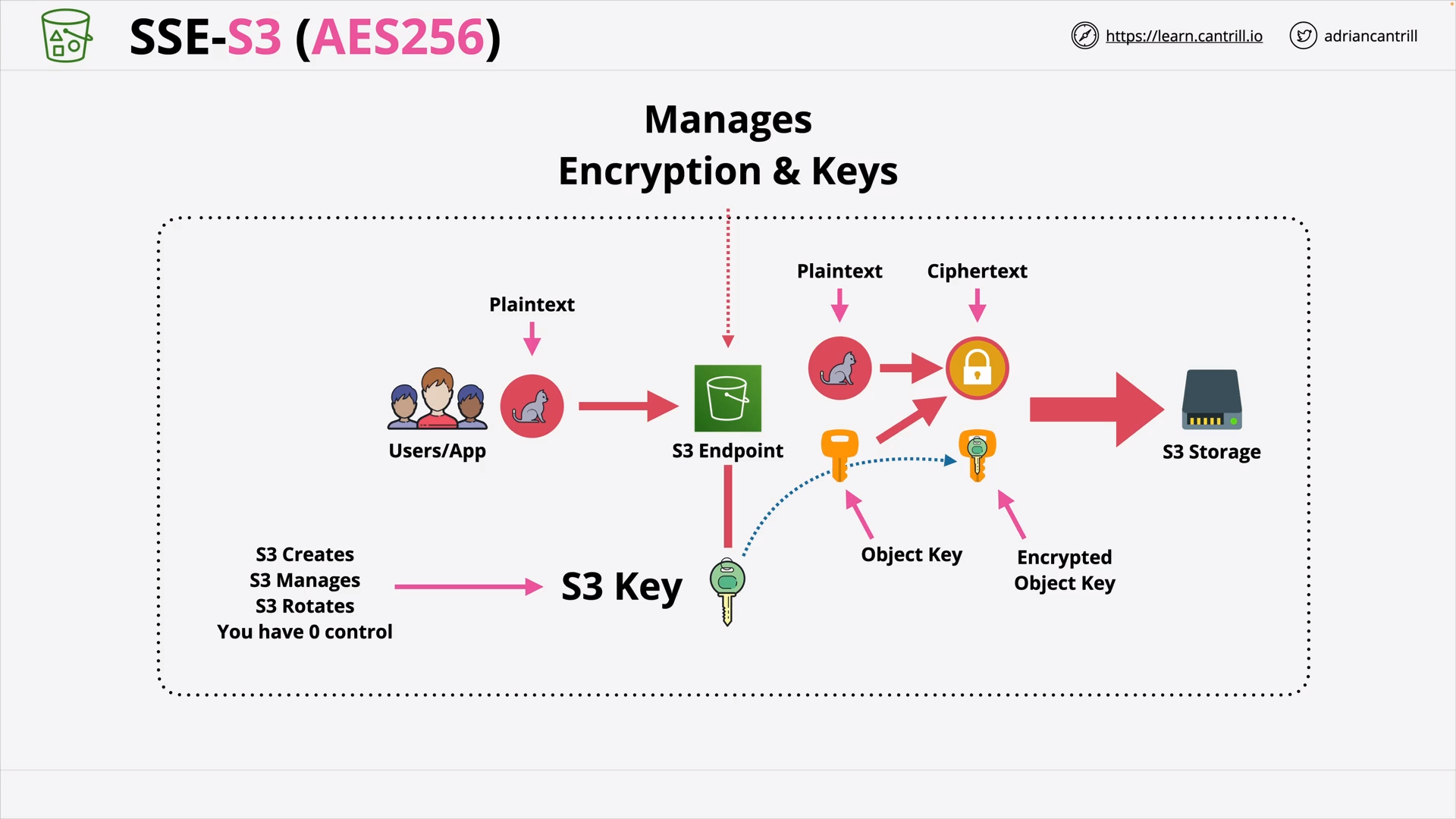 SSE-S3 👈 Default
SSE-S3 👈 Default
what is the biggest drawback of ss3-s3?
The admin can see the content.
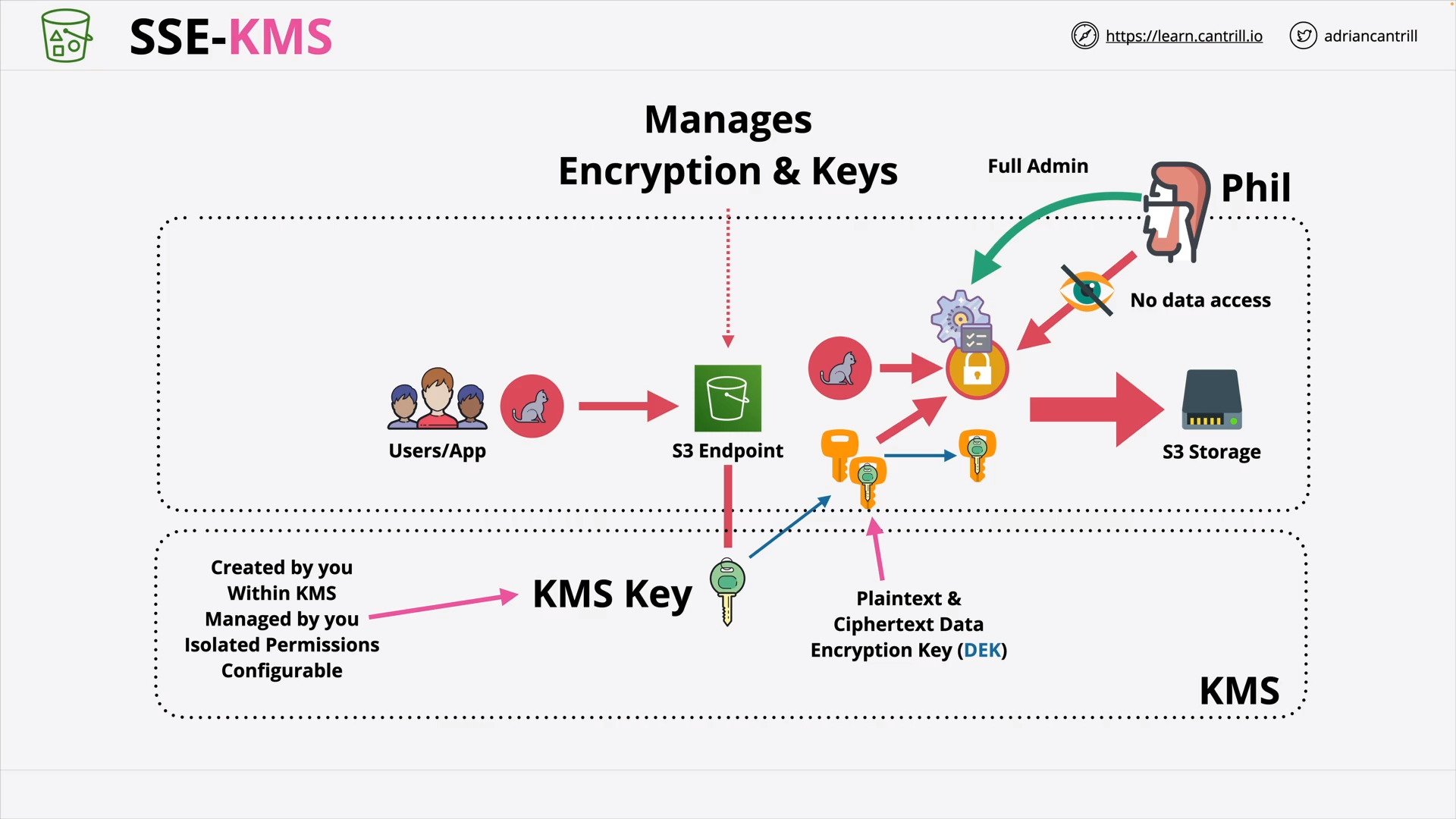 SSE-KMS
SSE-KMS
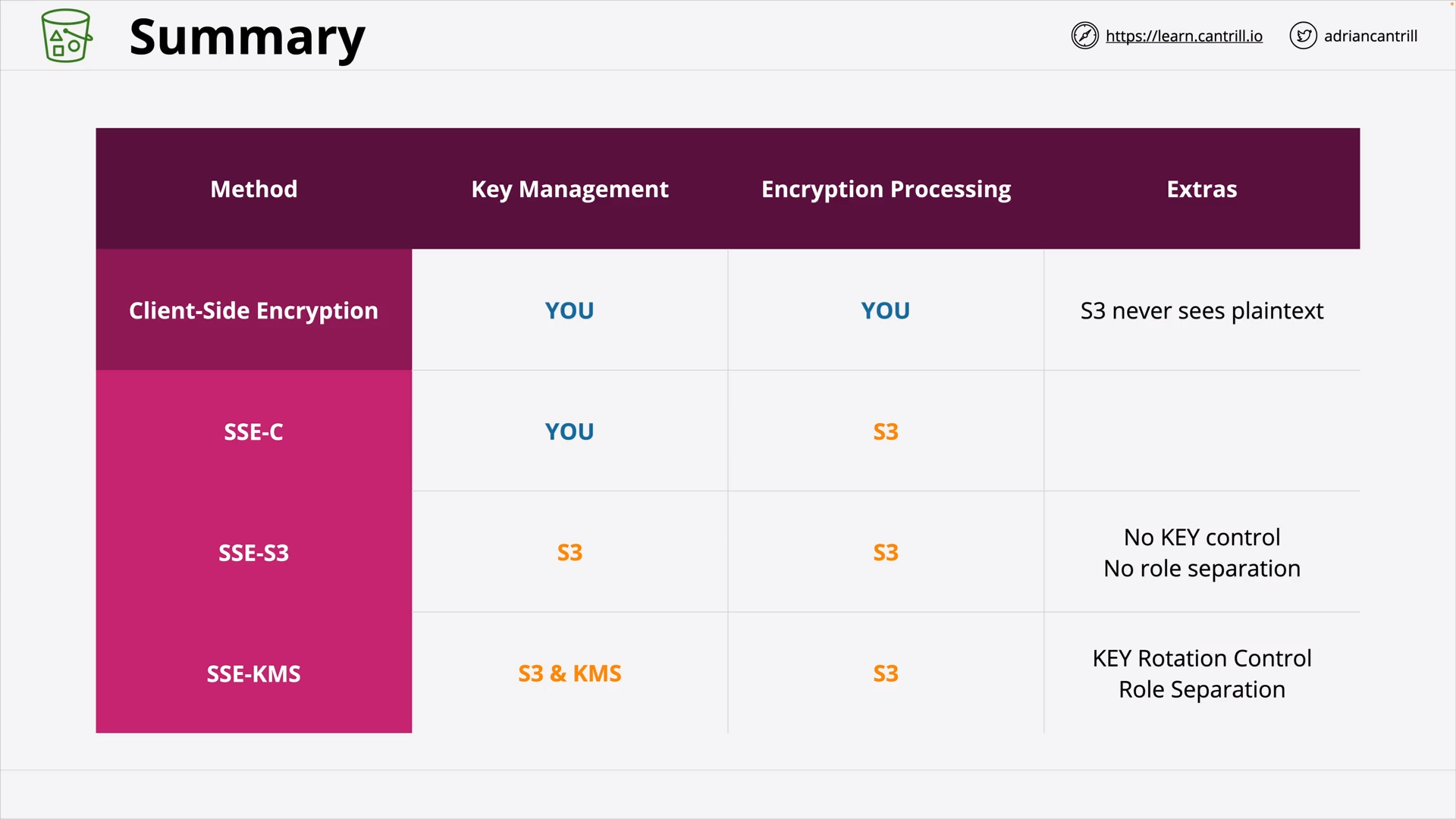 S3 Object Encryption - Summary
S3 Object Encryption - Summary
[DEMO] Object Encryption and Role Separation (14:50)
S3 Bucket Keys (5:59)
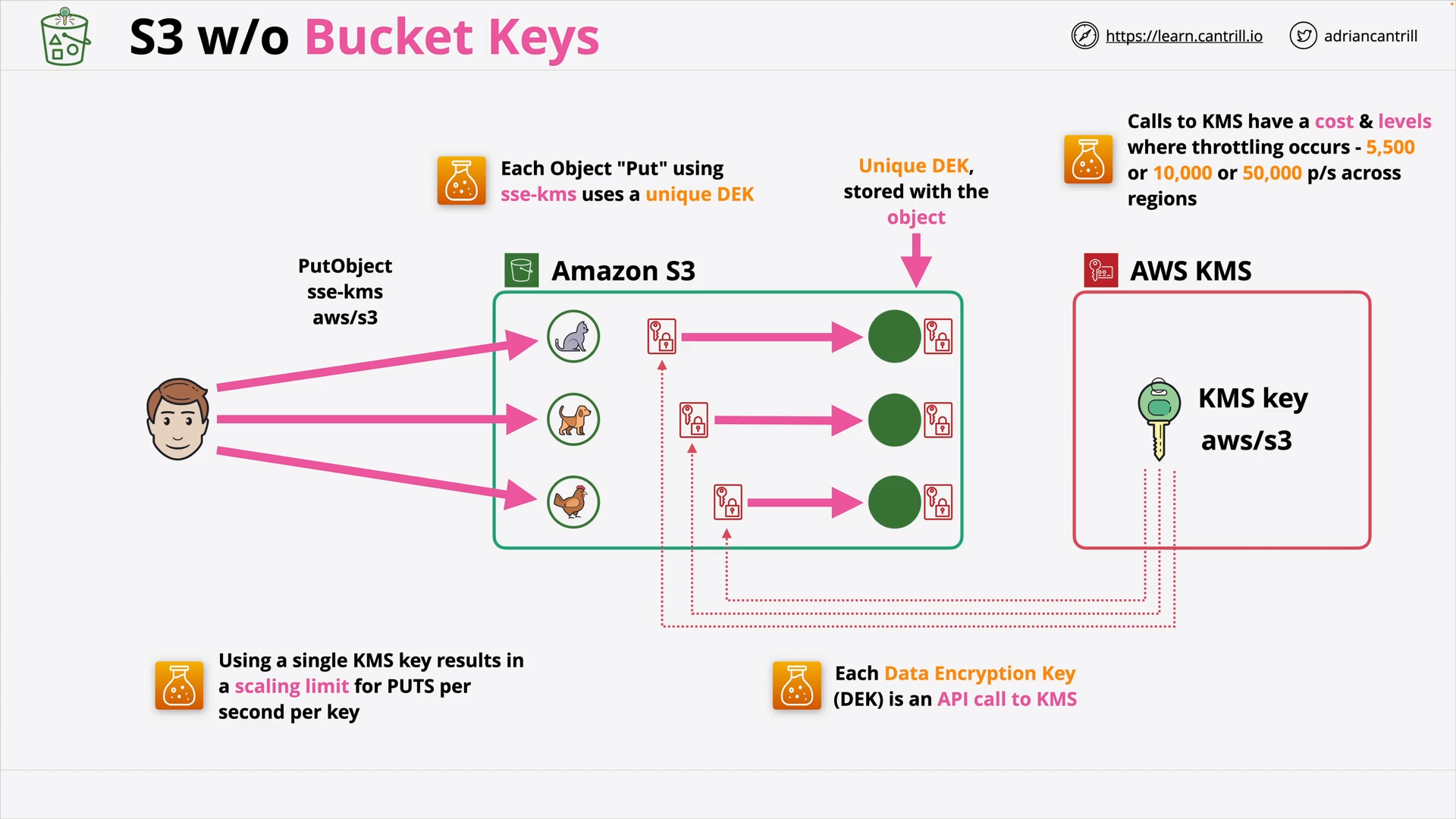 S3 without Bucket Keys
S3 without Bucket Keys
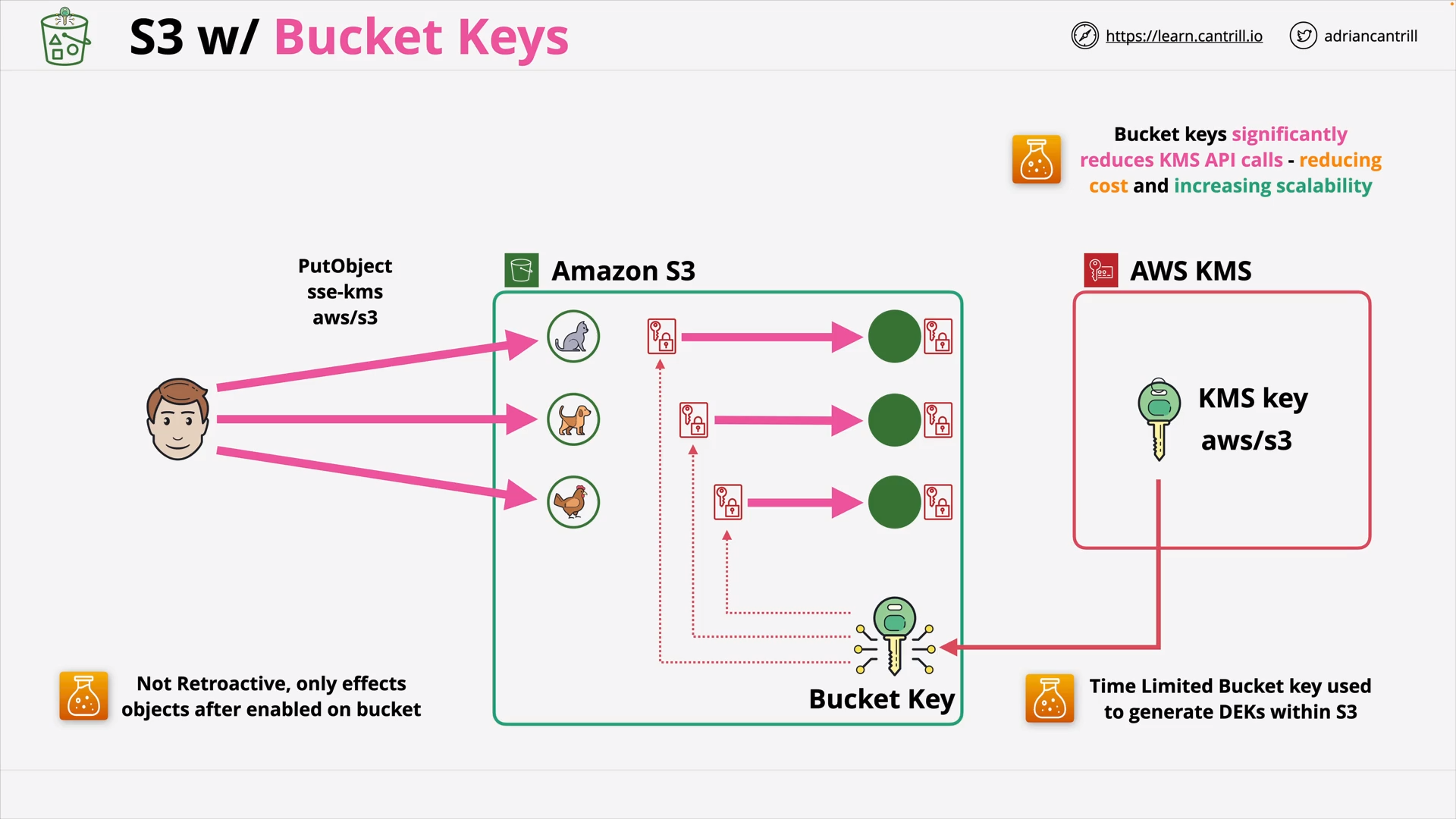 S3 with Bucket Keys
S3 with Bucket Keys
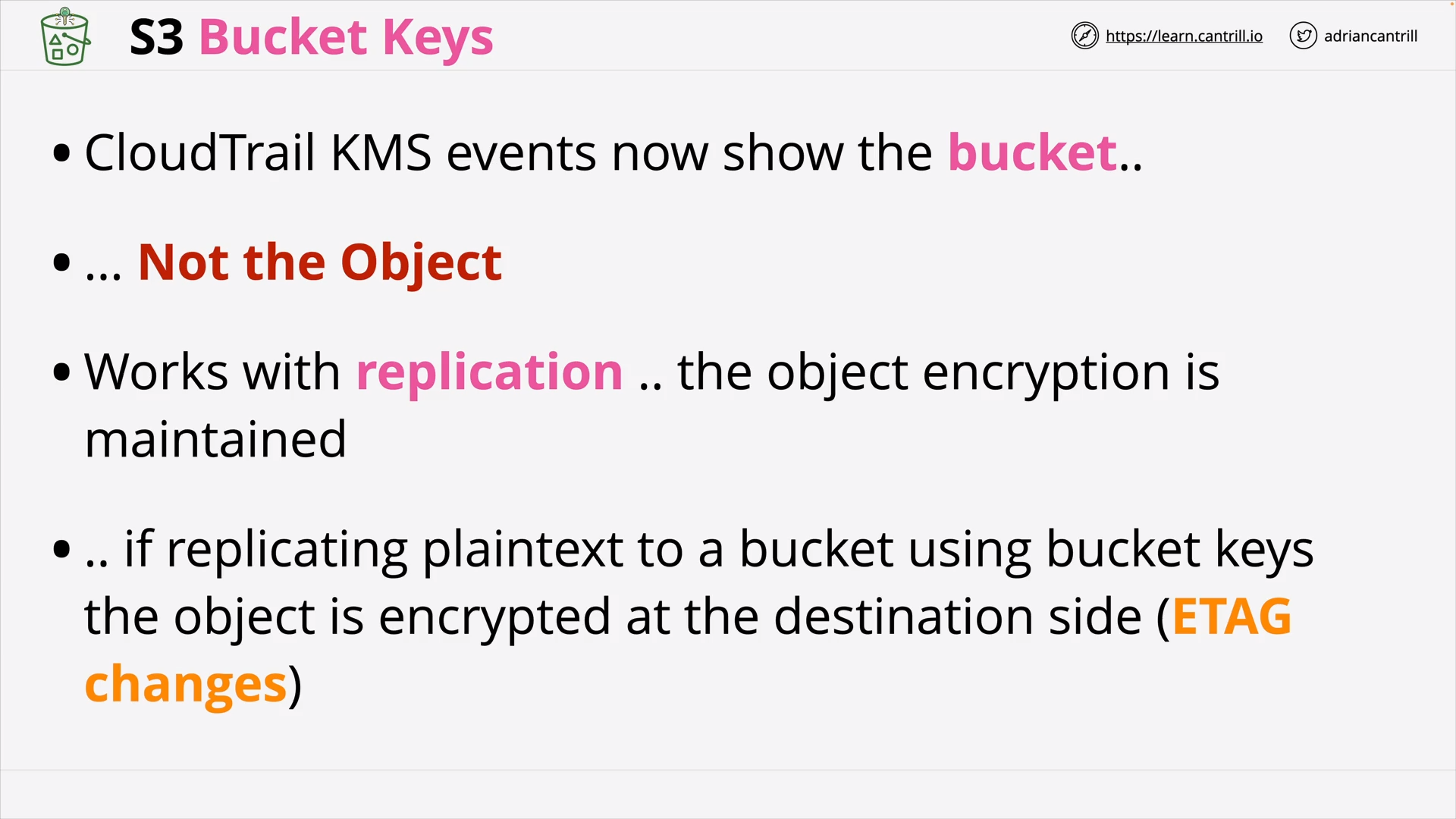 S3 Bucket Keys - Notes
S3 Bucket Keys - Notes
S3 Object Storage Classes - PART1 (9:23)
/00_LEARNINGAIDS/S3StorageClasses-1.png) S3 Storage Classes - S3 Standard
S3 Storage Classes - S3 Standard
/00_LEARNINGAIDS/S3StorageClasses-2.png) S3 Storage Classes - S3 Standard - IA
S3 Storage Classes - S3 Standard - IA
/00_LEARNINGAIDS/S3StorageClasses-3.png) S3 Storage Classes - S3 One Zone - IA
S3 Storage Classes - S3 One Zone - IA
S3 Object Storage Classes - PART2 (11:41)
/00_LEARNINGAIDS/S3StorageClasses-4.png) S3 Storage Classes - S3 Glacier - Instant
S3 Storage Classes - S3 Glacier - Instant
/00_LEARNINGAIDS/S3StorageClasses-5.png) S3 Storage Classes - S3 Glacier - Flexible
S3 Storage Classes - S3 Glacier - Flexible
/00_LEARNINGAIDS/S3StorageClasses-6.png) S3 Storage Classes - S3 Glacier - Deep Archive
S3 Storage Classes - S3 Glacier - Deep Archive
/00_LEARNINGAIDS/S3IntelligentTiering.png) S3 Storage Classes - S3 Intelligent-Tiering
S3 Storage Classes - S3 Intelligent-Tiering
S3 Lifecycle Configuration (8:13)
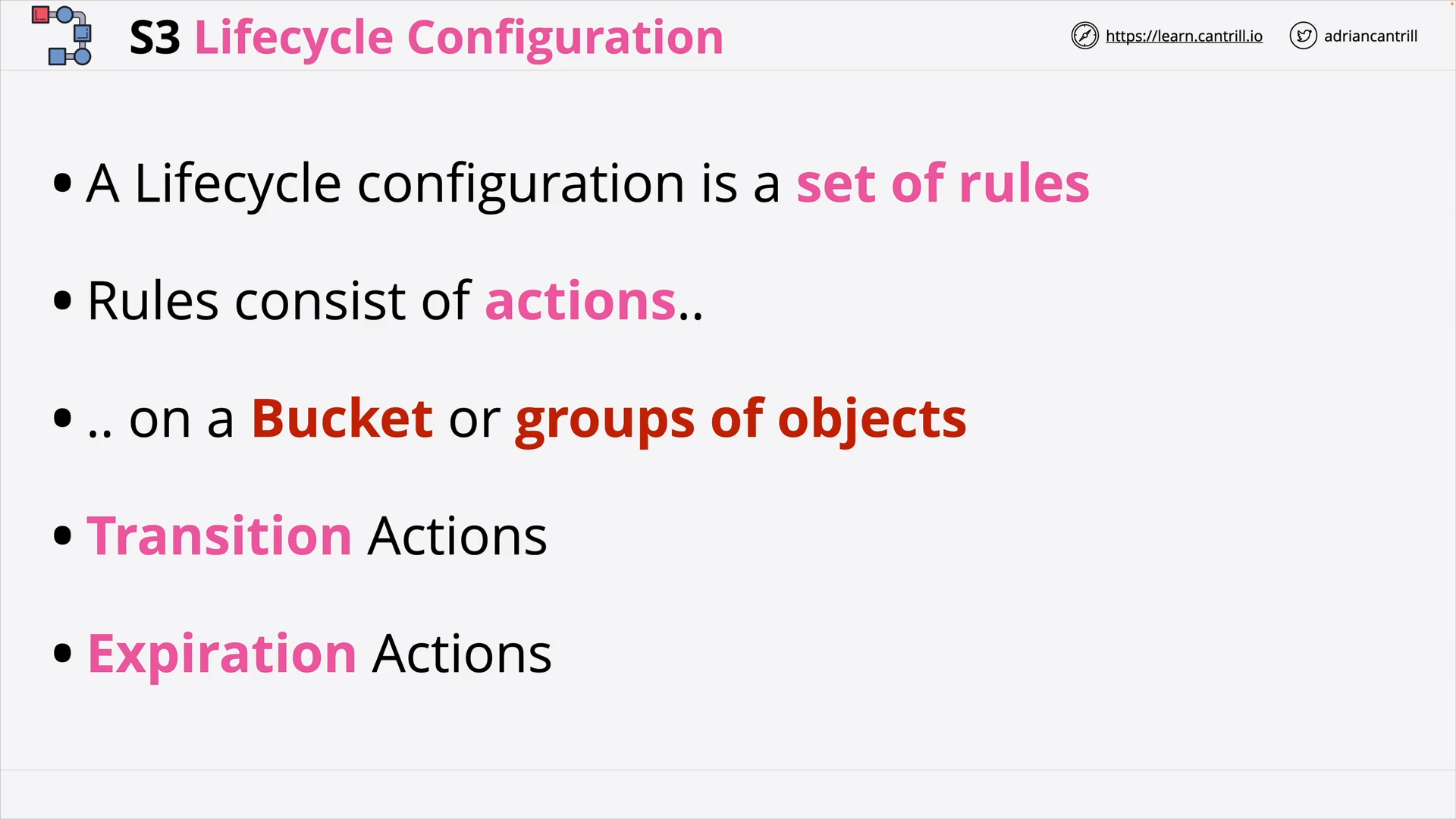 S3 Lifecycle Configuration
S3 Lifecycle Configuration
/00_LEARNINGAIDS/S3LifeCycle.png) S3 Lifecycle Configuration - Transition
S3 Lifecycle Configuration - Transition
S3 Replication (13:59)
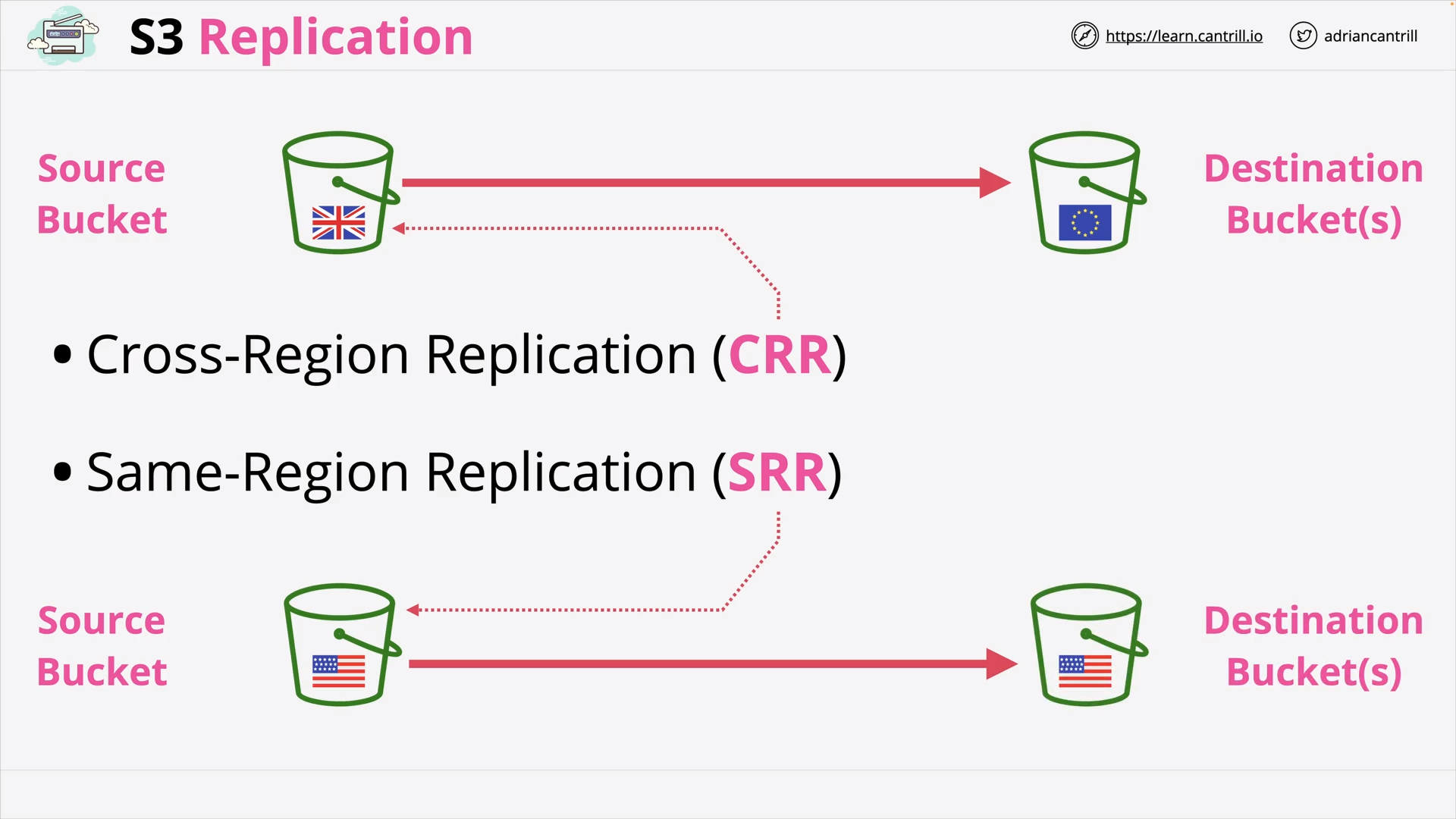 Cross-Region Replication (CRR) & Same-Region Replication (SRR)
Cross-Region Replication (CRR) & Same-Region Replication (SRR)
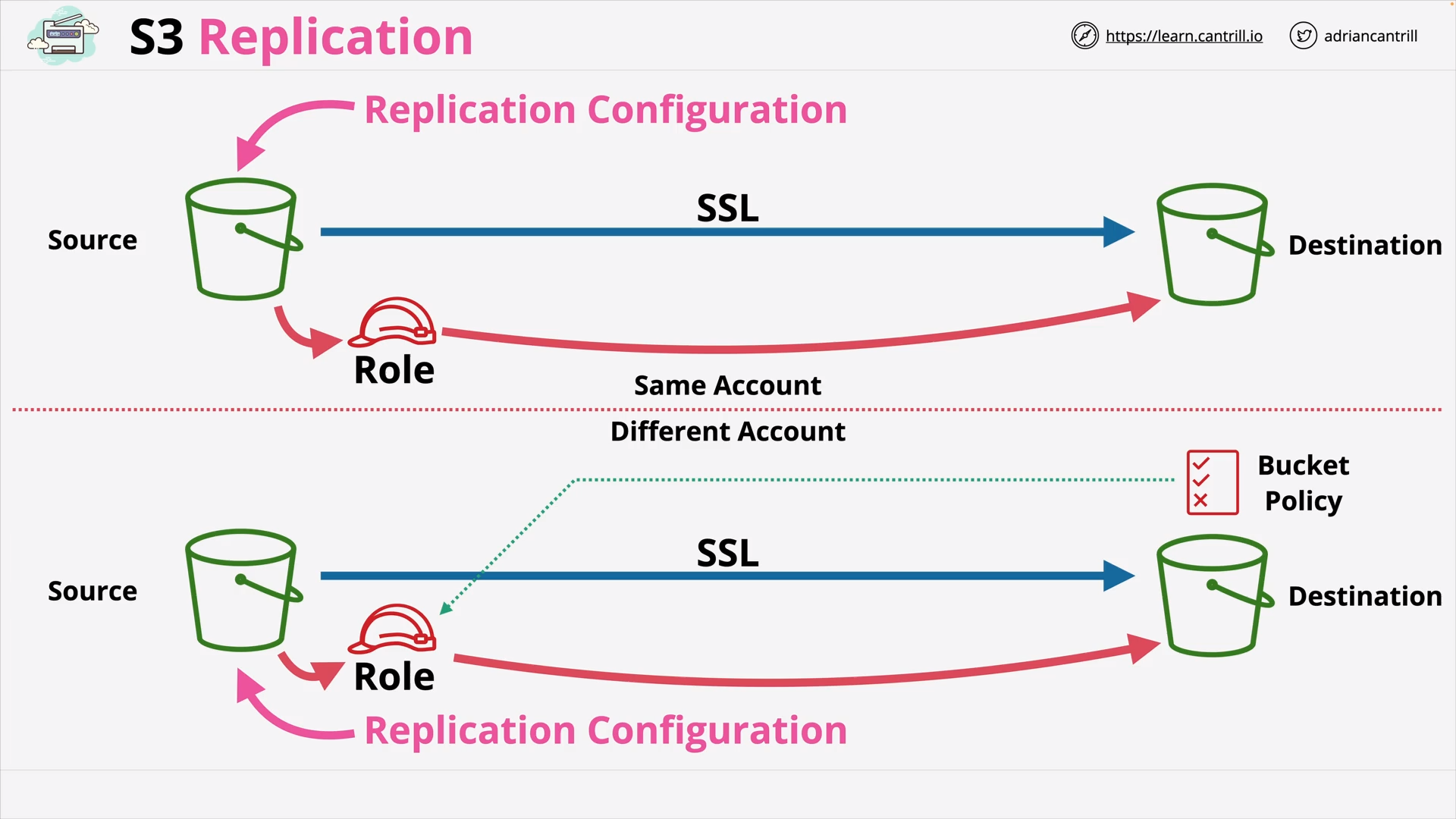 Replication can be between different accounts
Replication can be between different accounts
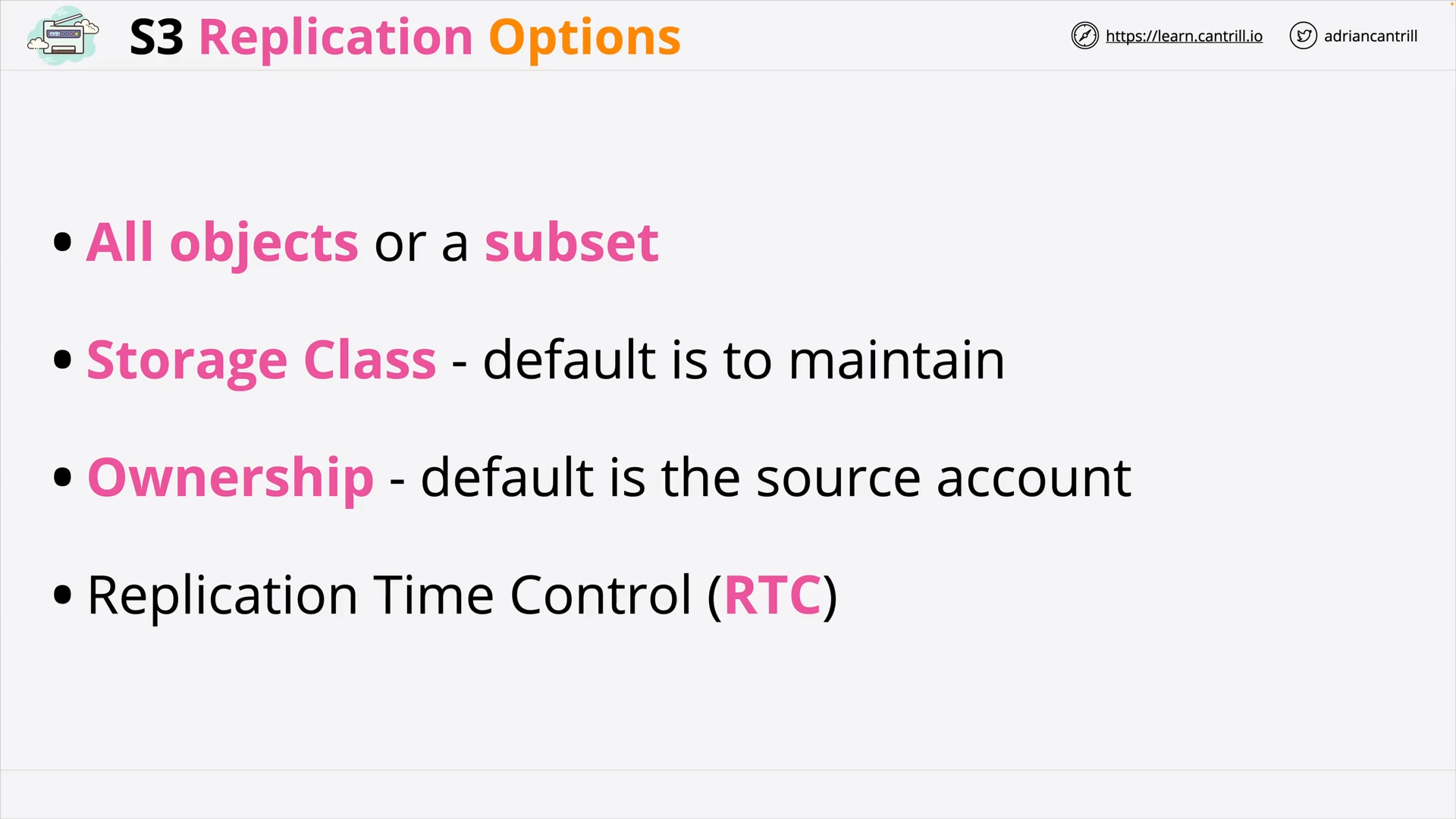 S3 Replication Options - RTC
S3 Replication Options - RTC
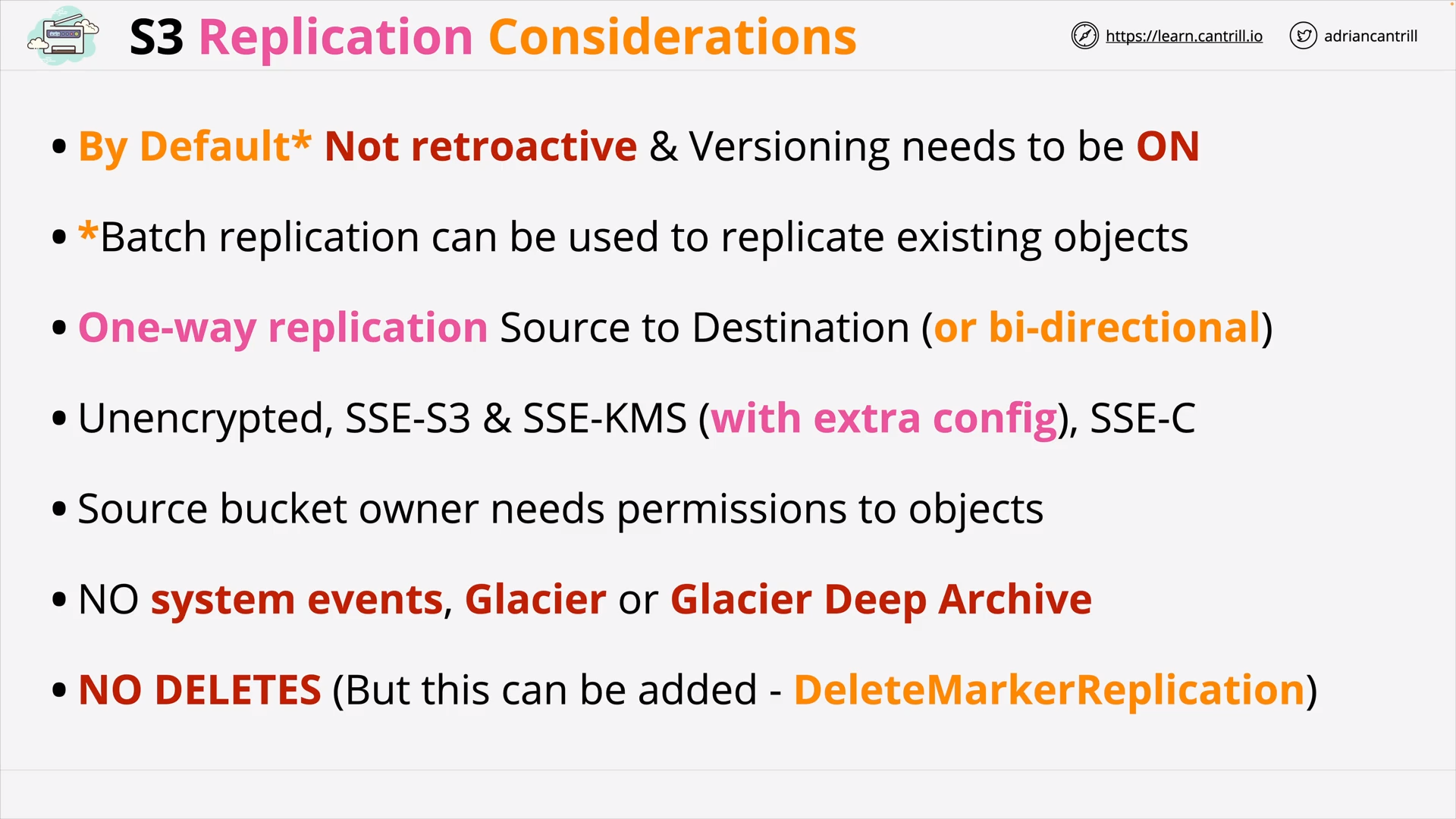 S3 Replication - Considerations
S3 Replication - Considerations
 Why use S3 replication?
Why use S3 replication?
[DEMO] Cross-Region Replication of an S3 Static Website (19:52)
S3 PreSigned URLs (11:11)
/00_LEARNINGAIDS/S3PresignedURL-1.png) Why use Presigned URL?
Why use Presigned URL?
/00_LEARNINGAIDS/S3PresignedURL-2.png) Presigned URL works with both Upload and Download
Presigned URL works with both Upload and Download
/00_LEARNINGAIDS/S3PresignedURL-3.png) Apps can use Presigned URL to provide access to Media Bucket
Apps can use Presigned URL to provide access to Media Bucket
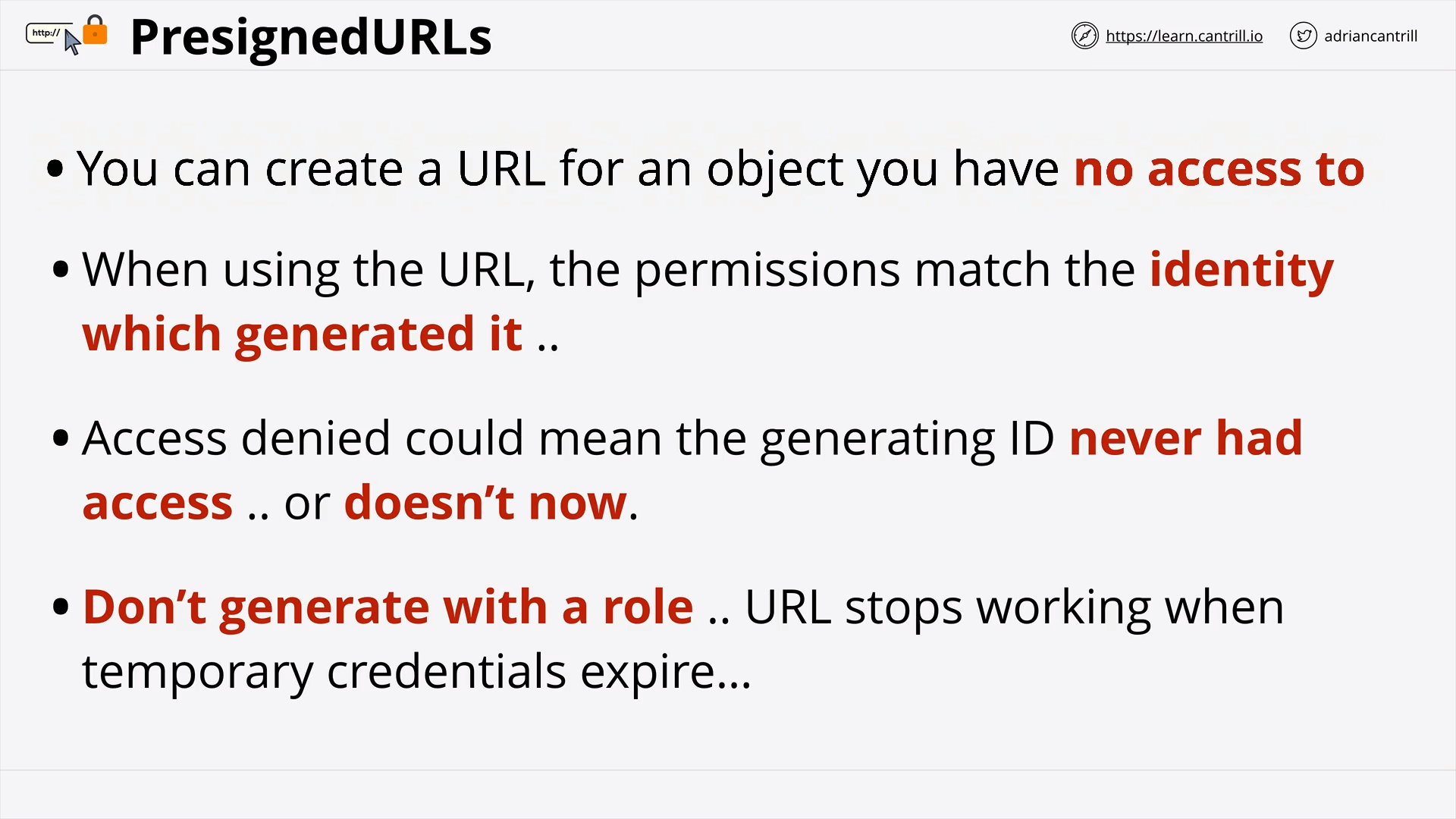 Presigned URL - Gotchas
Presigned URL - Gotchas
[DEMO] Creating and using PresignedURLs (18:23)
S3 Select and Glacier Select (5:32)
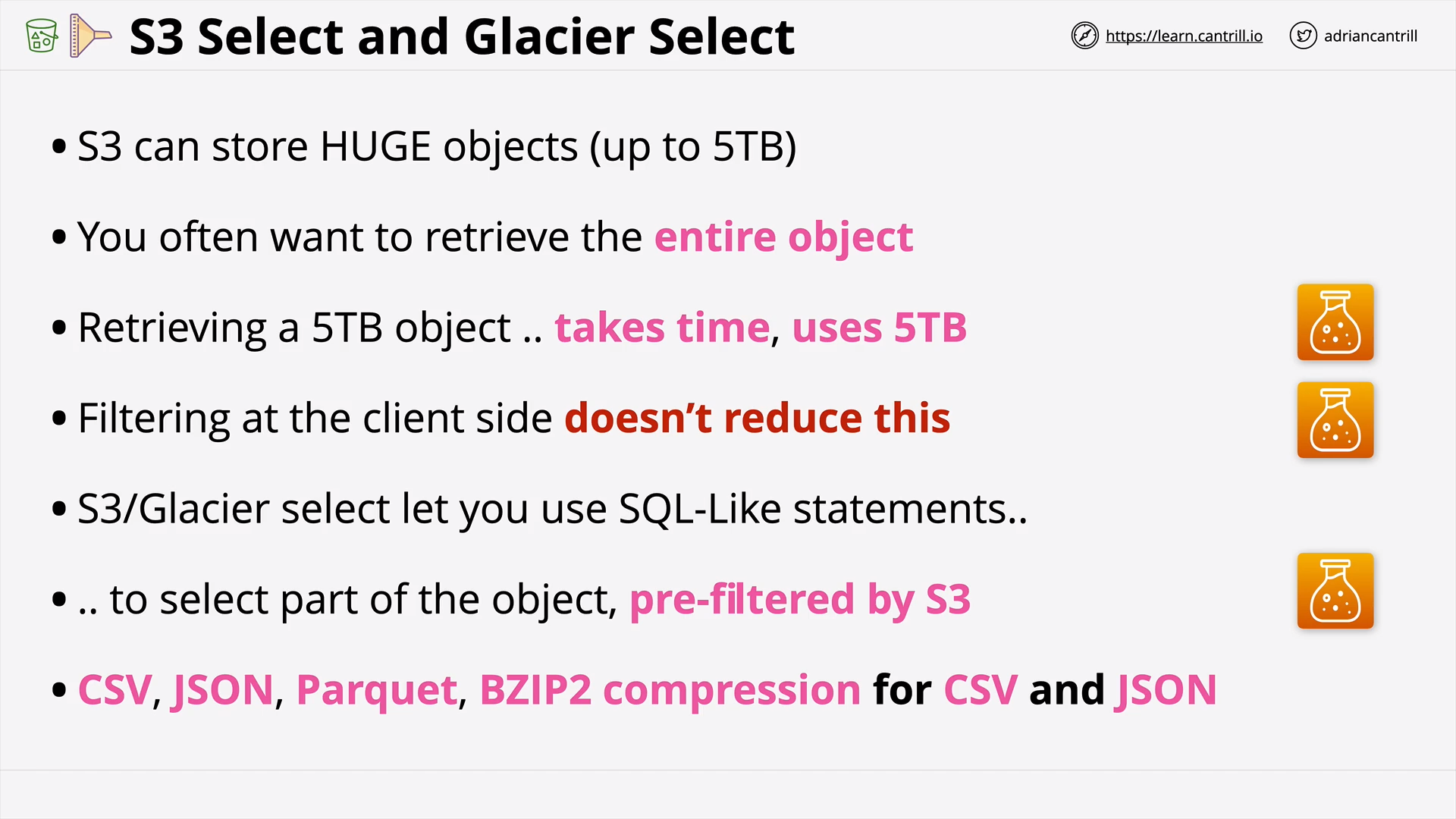
/00_LEARNINGAIDS/S3andGlacierSelect.png)
S3 Events (4:32)
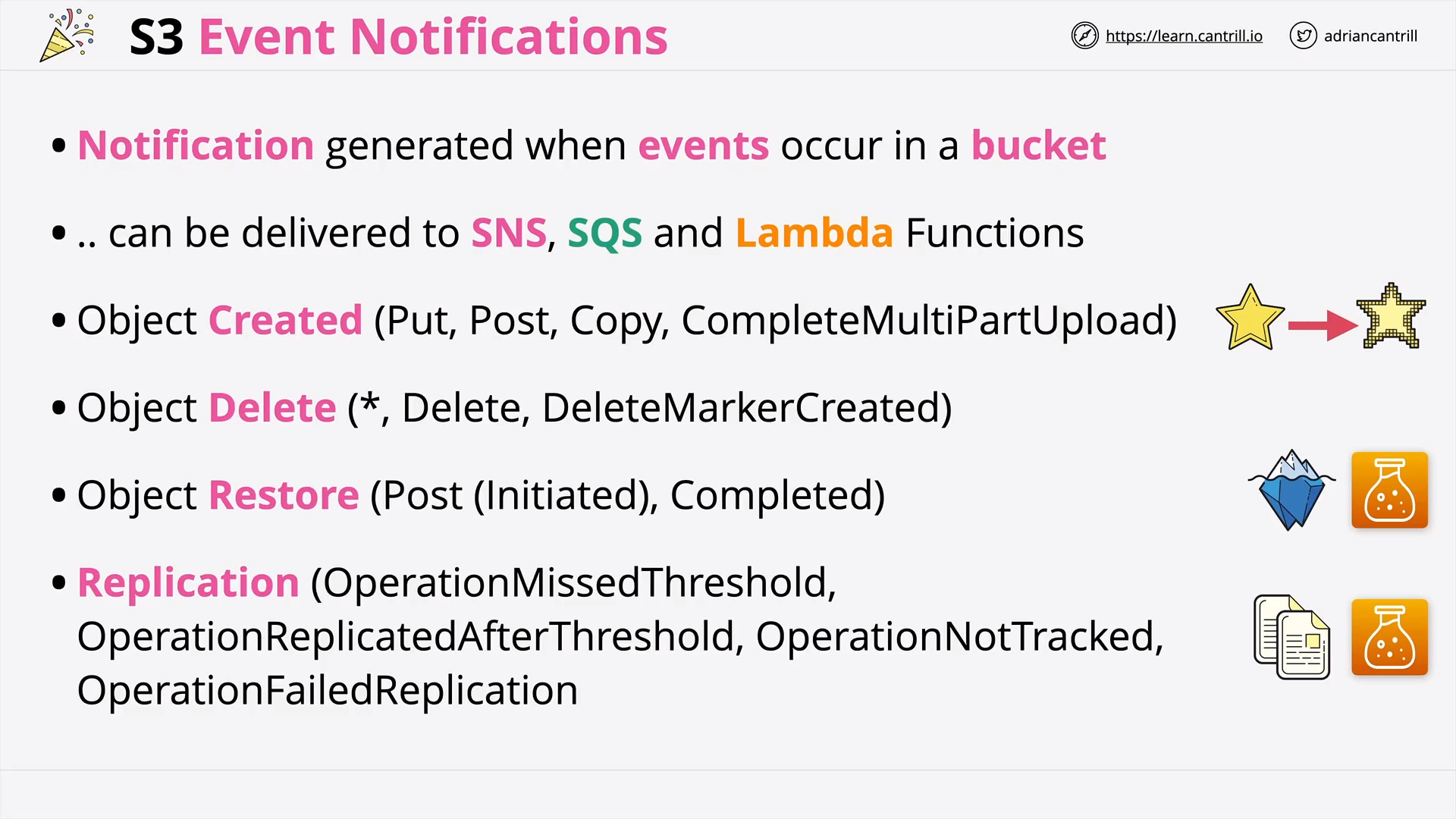
/00_LEARNINGAIDS/S3EventNotifications.png)
S3 Access Logs (3:05)
/00_LEARNINGAIDS/S3AccessLogs.png) S3 Access Logs
S3 Access Logs
S3 Object Lock (9:52)
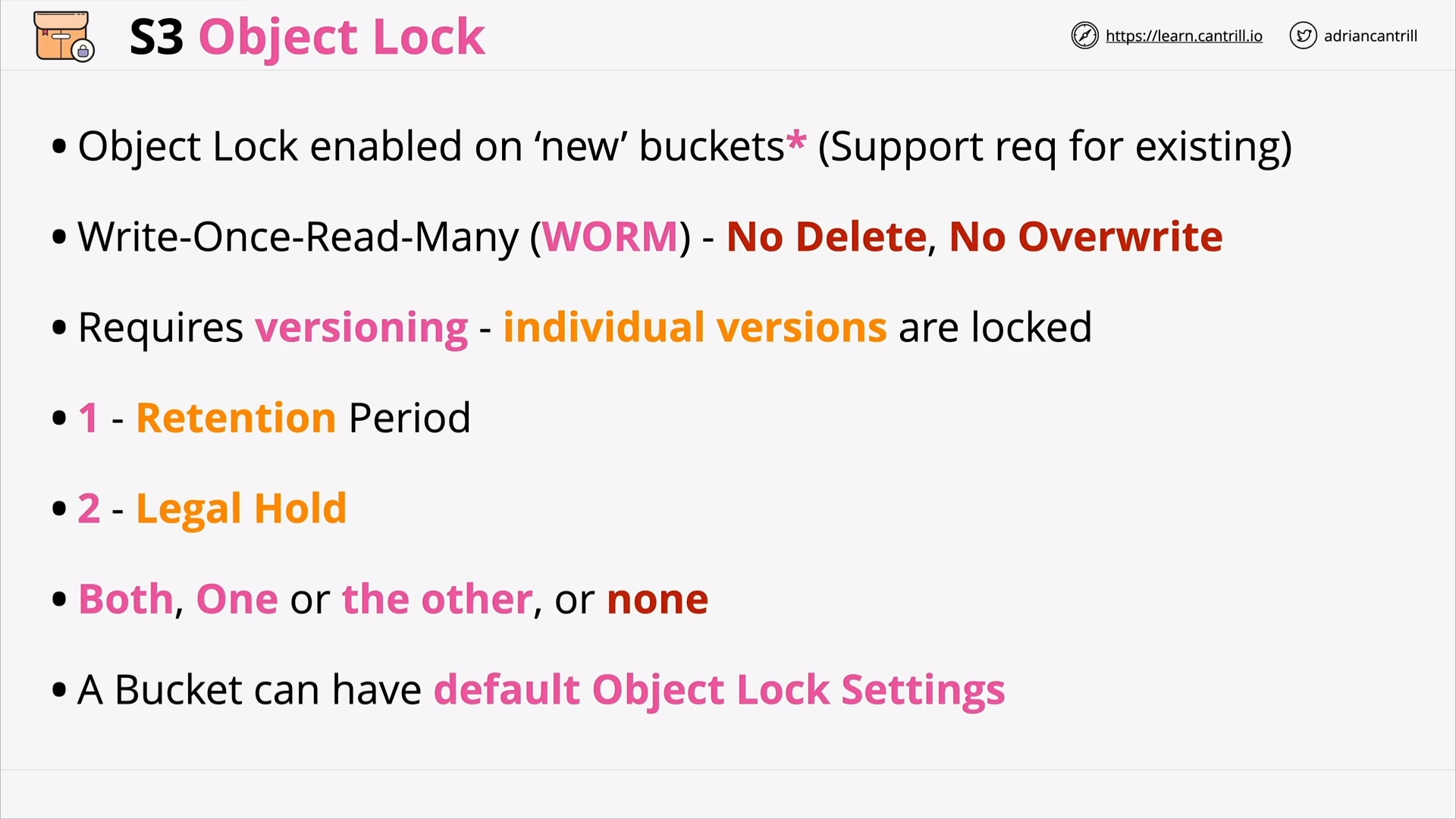 S3 Object Lock - Write-Once-Read-Many (WORM)
S3 Object Lock - Write-Once-Read-Many (WORM)
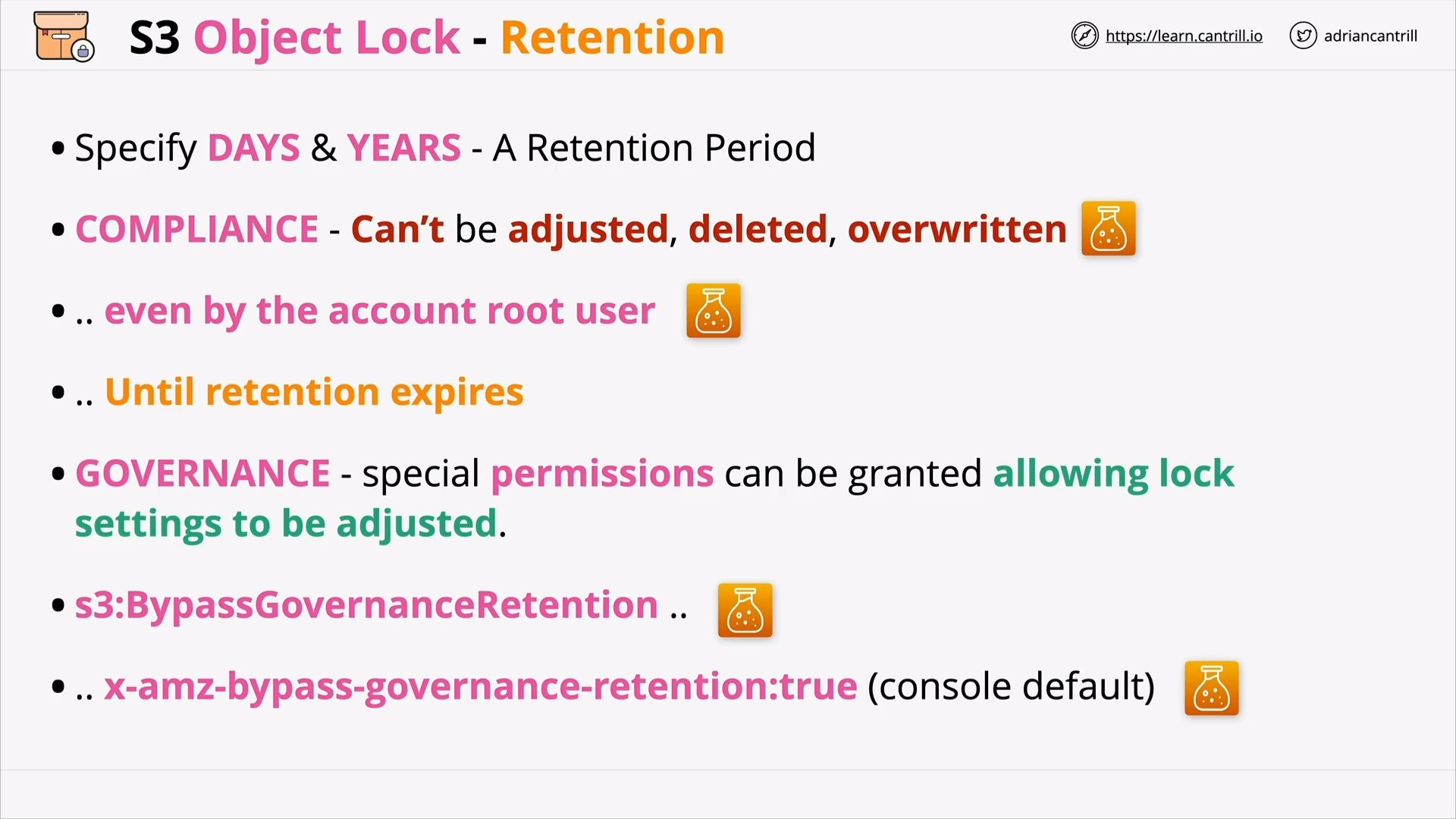 S3 Object Lock - Retention (Compliance / Governance)
S3 Object Lock - Retention (Compliance / Governance)
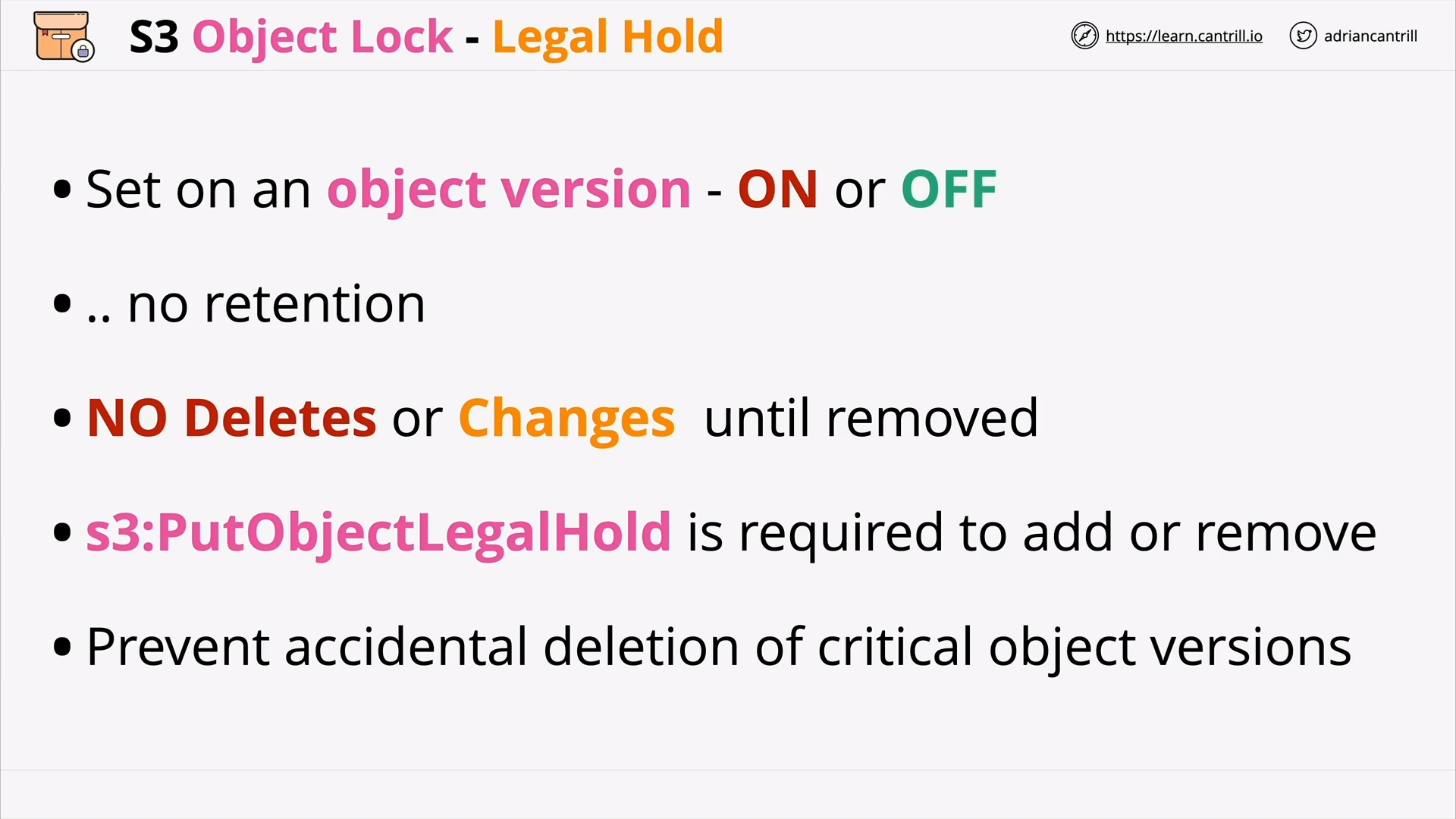 S3 Object Lock - Legal Hold
S3 Object Lock - Legal Hold
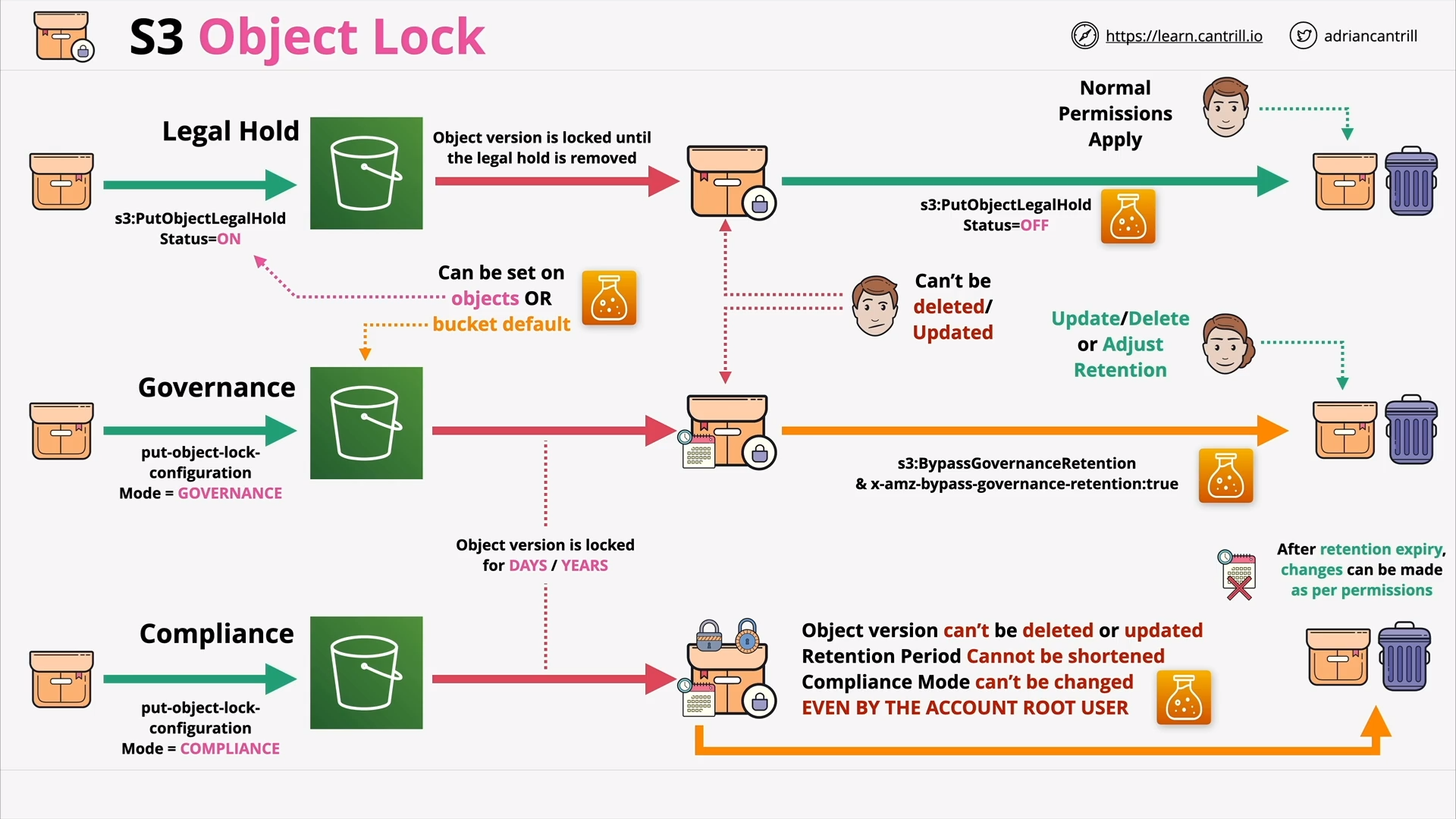 S3 Object Lock - Summary
S3 Object Lock - Summary
S3 Access Points (5:52)
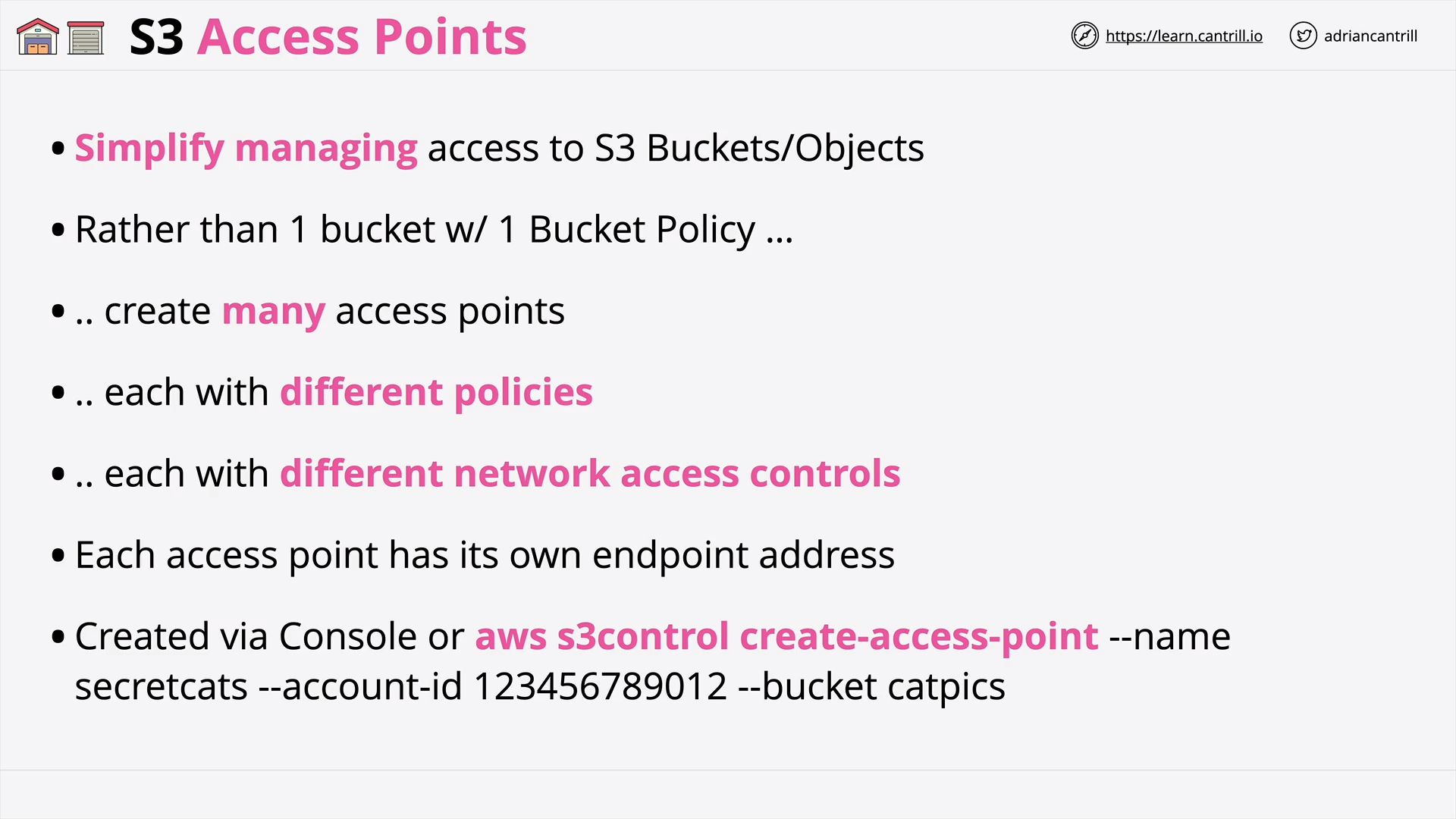 Each S3 Access Points is a “mini S3 bucket”
Each S3 Access Points is a “mini S3 bucket”
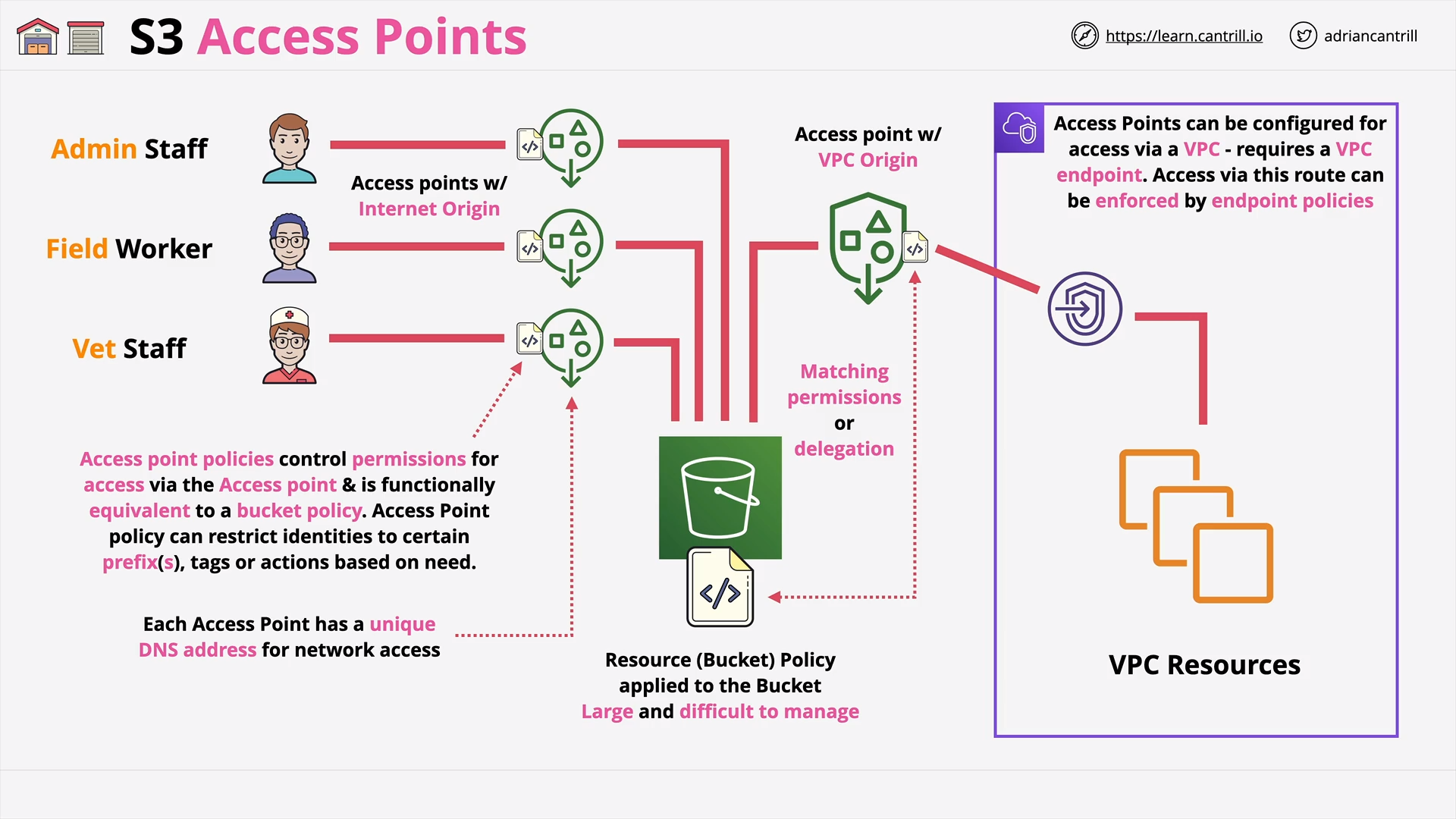 S3 Access Points’ DNS, policies & endpoint polices
S3 Access Points’ DNS, policies & endpoint polices
[DEMO] Multi-Region Access Points (MRAP) (20:25)
S3 Section Quiz
VIRTUAL PRIVATE CLOUD (VPC) BASICS
VPC Sizing and Structure - PART1 (11:48)
 VPC Considerations
VPC Considerations
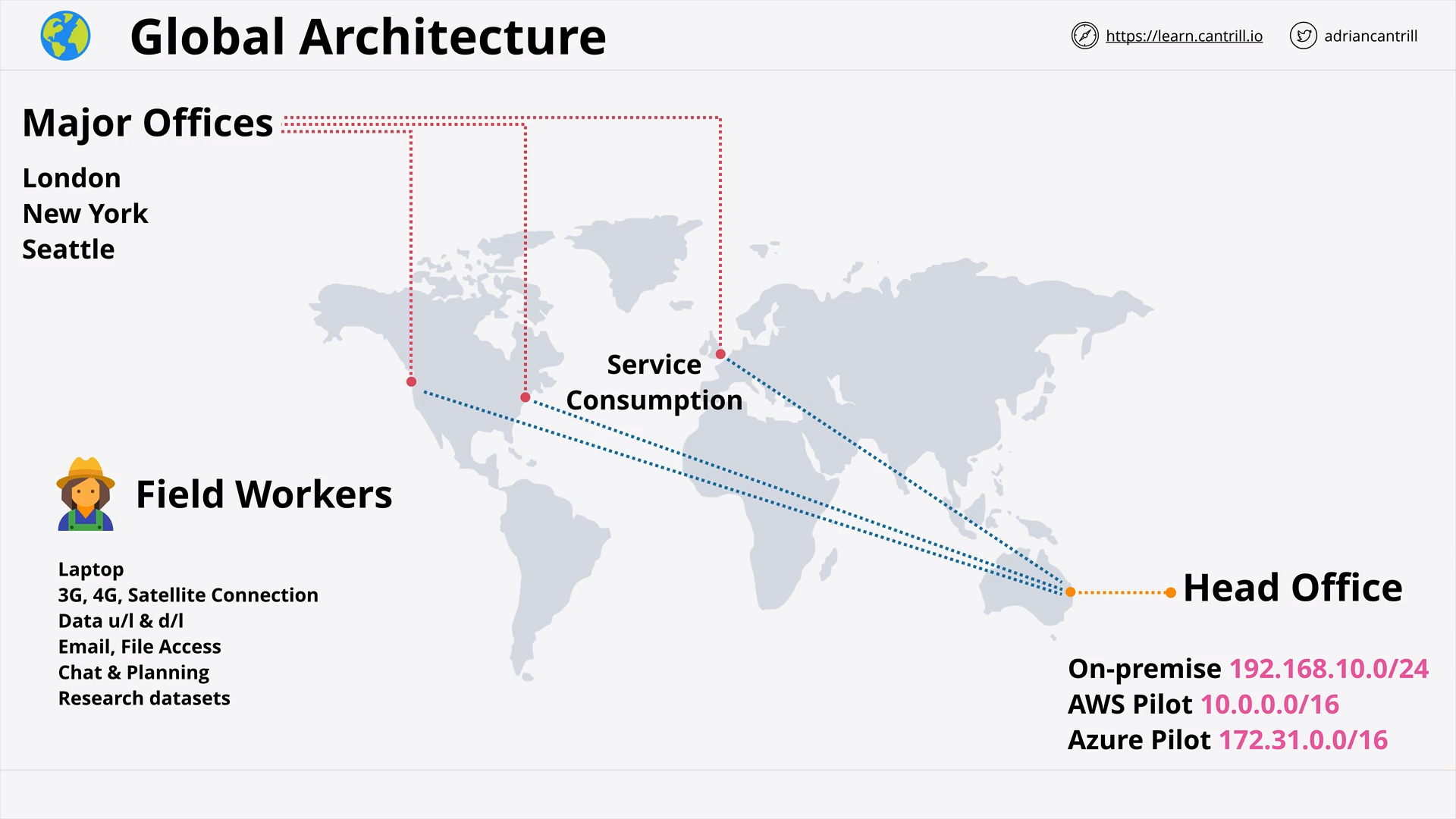 Global Architecture
Global Architecture
 IP Ranges to Avoid
IP Ranges to Avoid
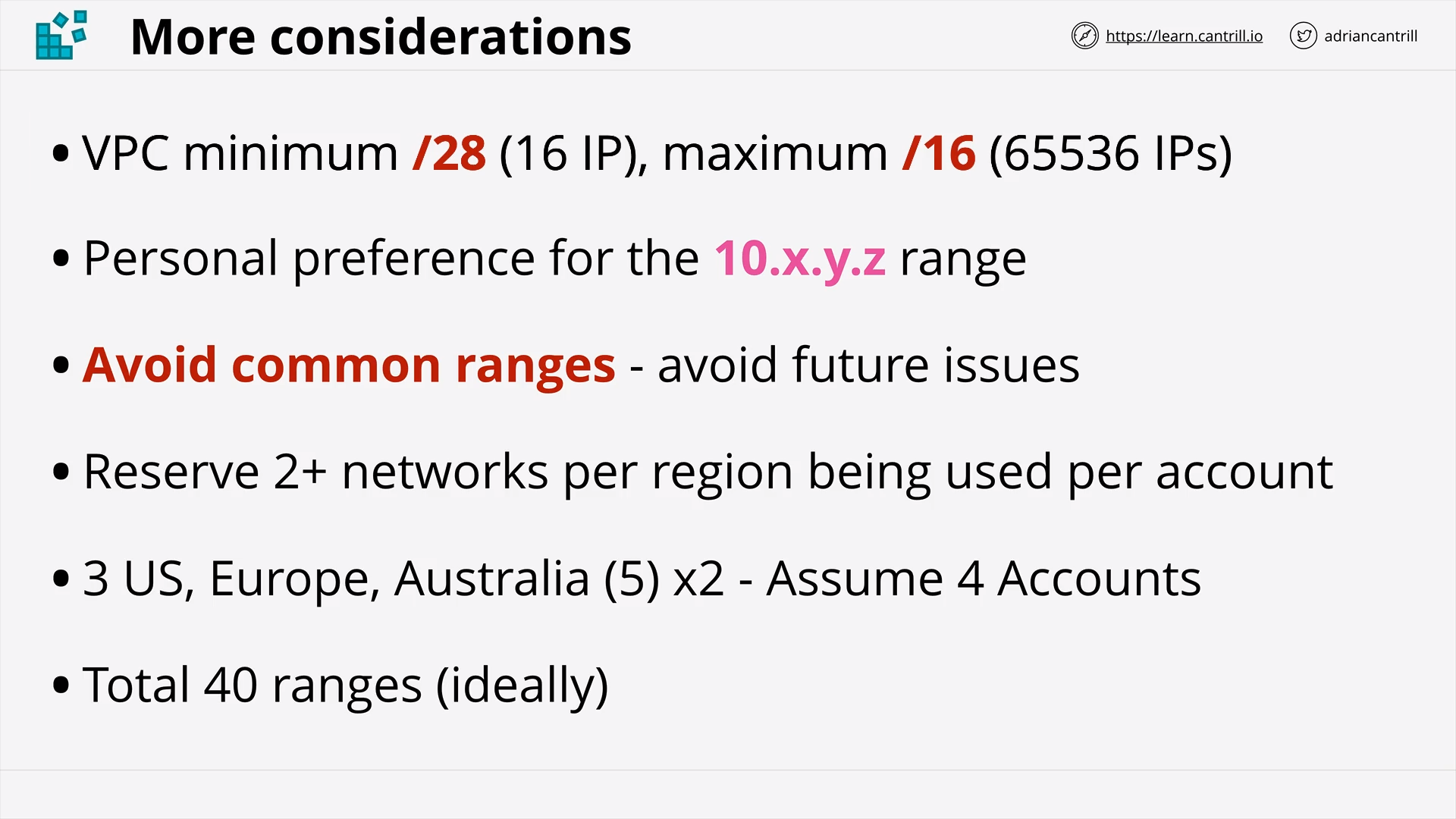 VPC - More Considerations
VPC - More Considerations
/00_LEARNINGAIDS/VPCSizing-1.png) VPC Sizing
VPC Sizing
/00_LEARNINGAIDS/VPCSizing-2.png) VPC Structure
VPC Structure
VPC Sizing and Structure - PART2 (11:16)
/00_LEARNINGAIDS/VPCStucture-1.png) VPC Design - End State
VPC Design - End State
Custom VPCs - PART1 - THEORY (10:10)
/00_LEARNINGAIDS/CustomVPC.png) VPC Design - Basic
VPC Design - Basic
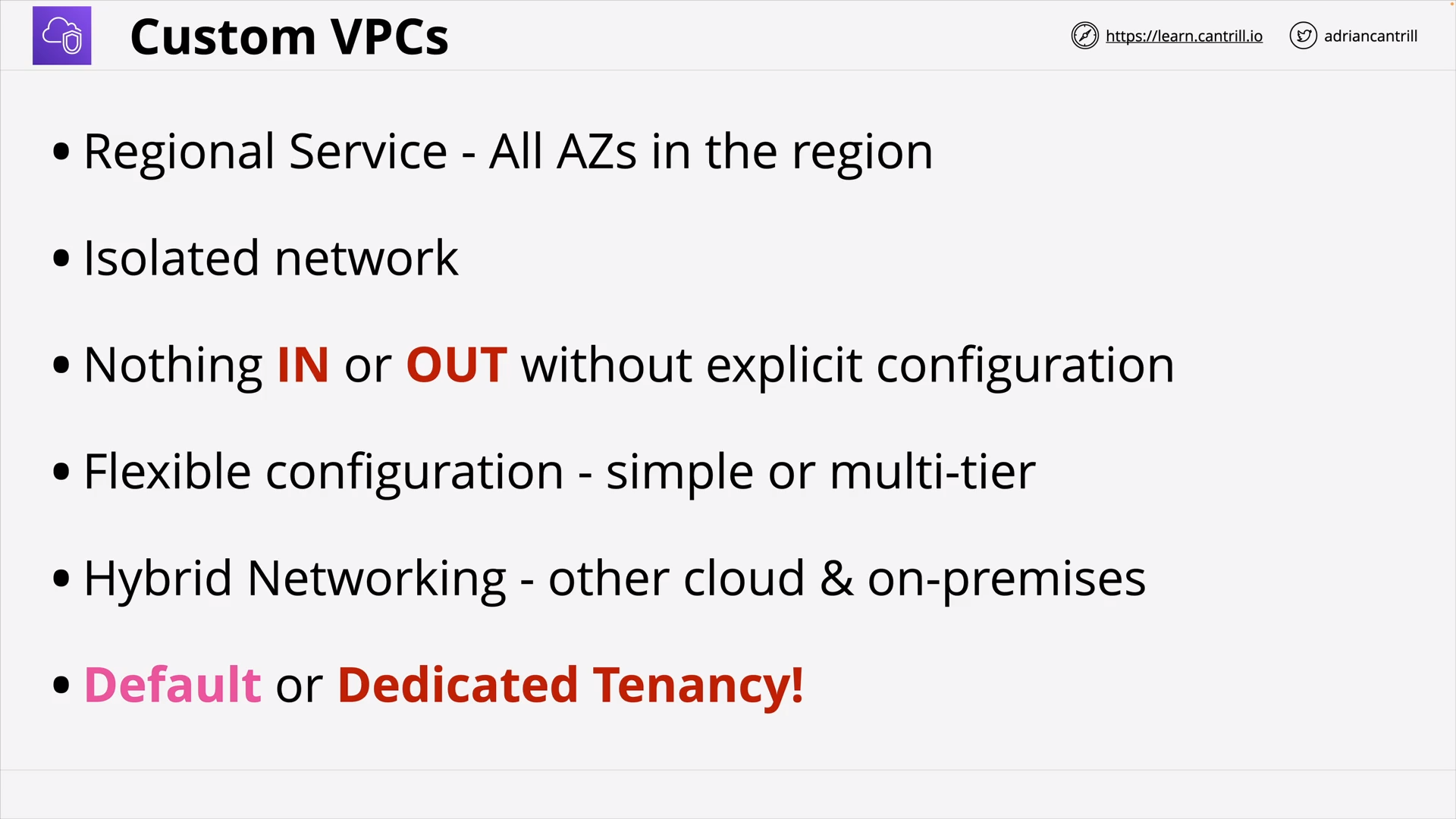 Custom VPC: Overview
Custom VPC: Overview
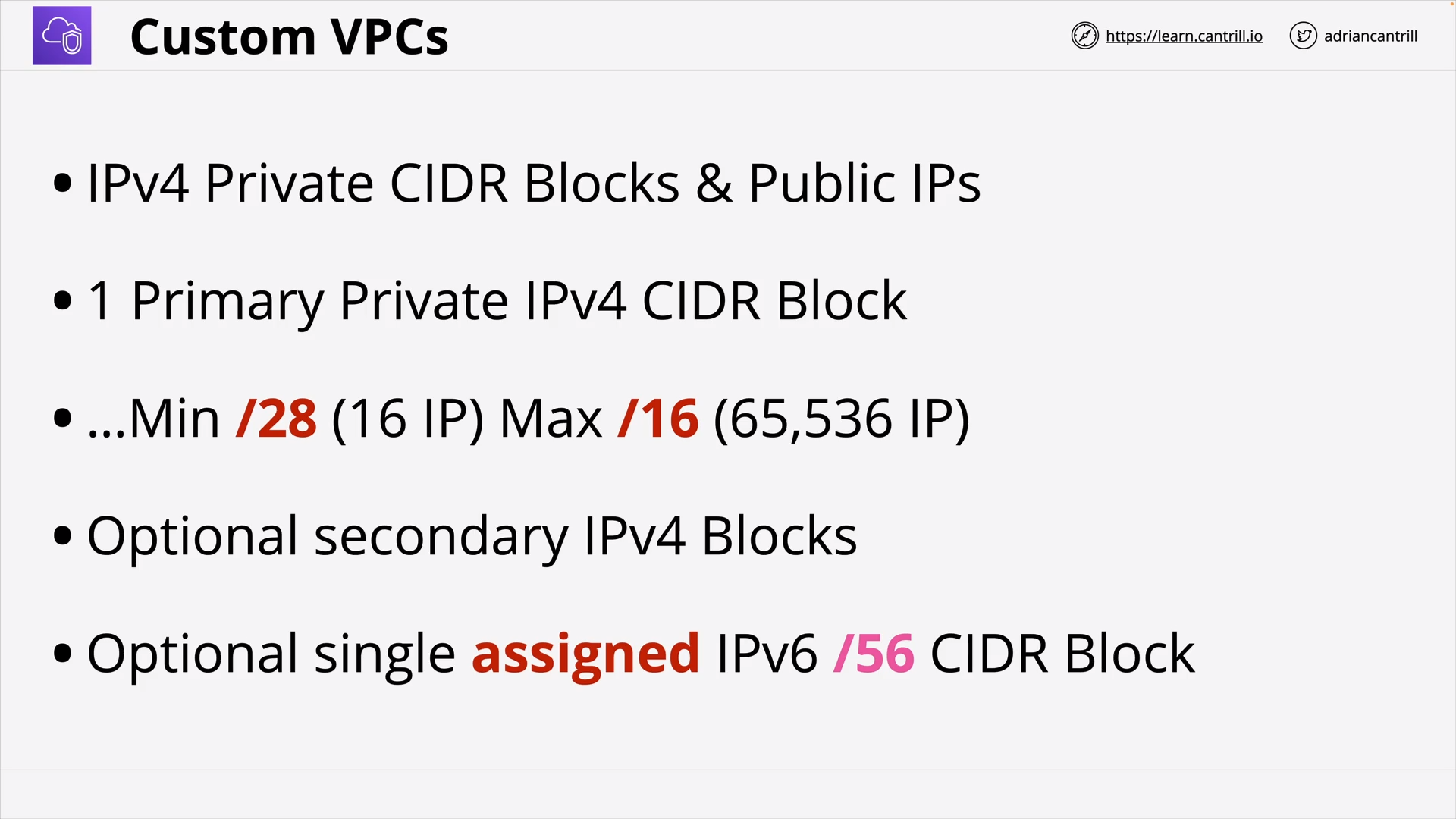 Custom VPC: IP address
Custom VPC: IP address
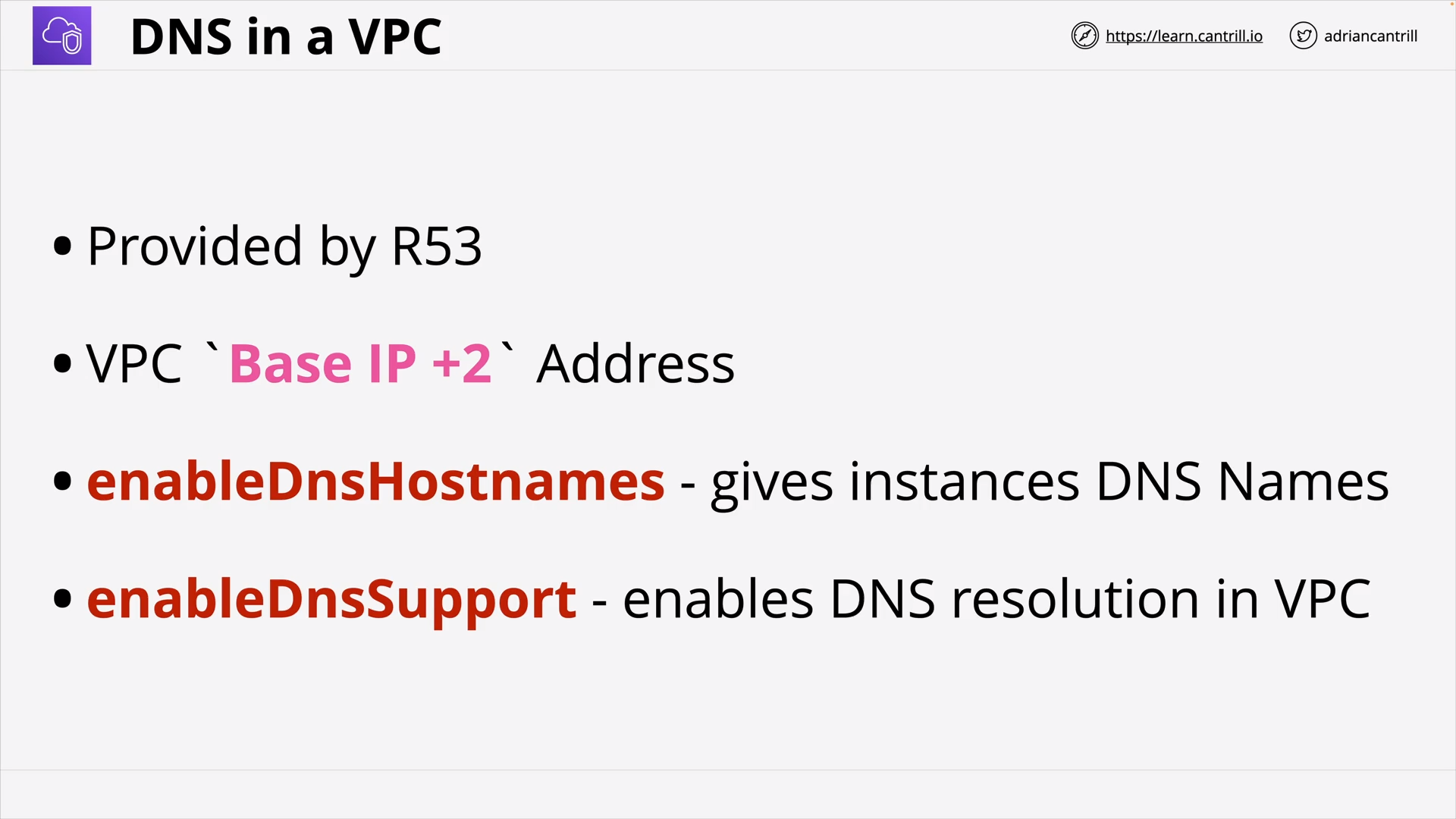 Custom VPC: DNS in the VPC
Custom VPC: DNS in the VPC
[DEMO] Custom VPCs - PART2 - DEMO (5:40)
VPC Subnets (10:42)
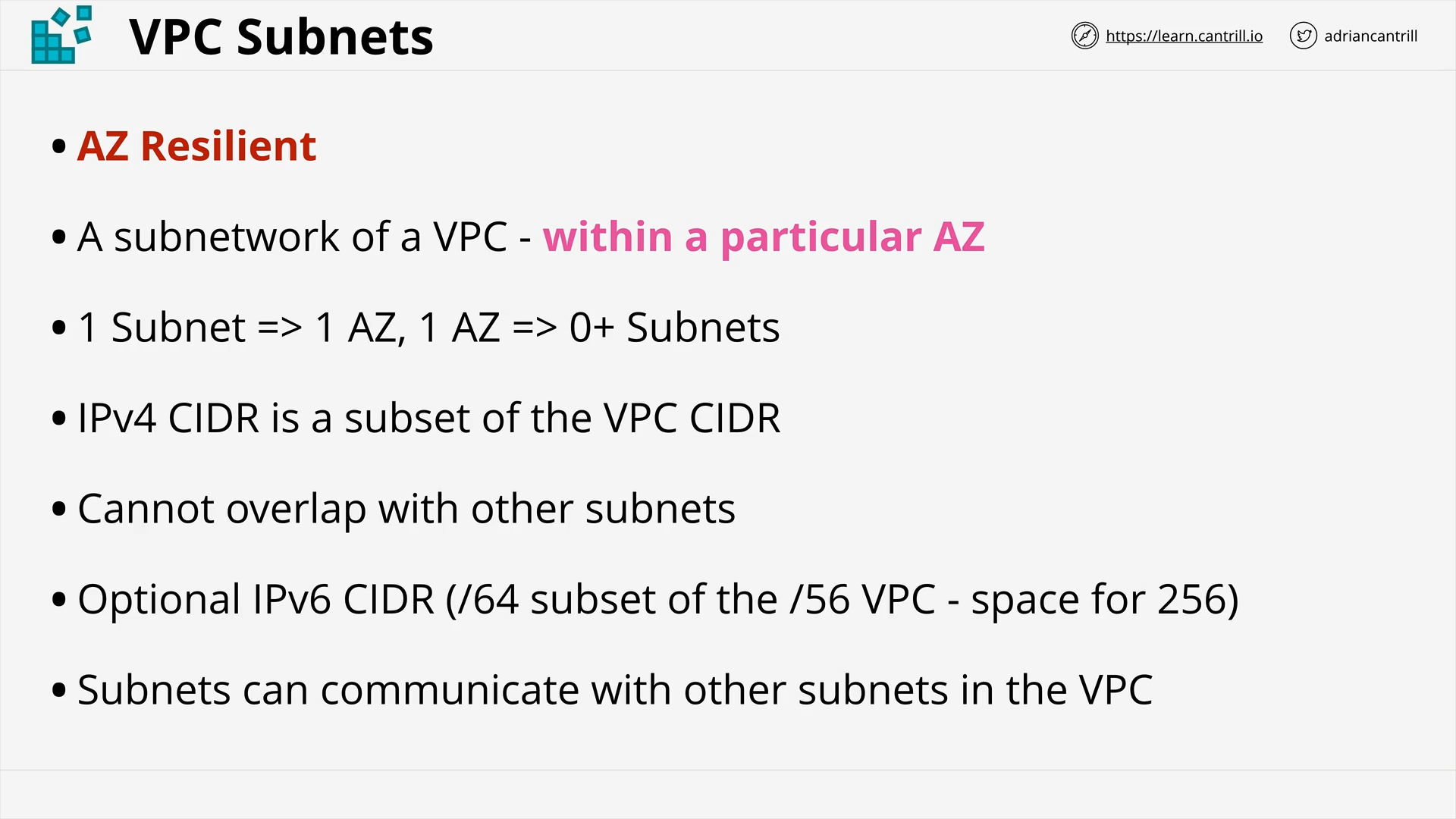 VPC Subnets
VPC Subnets
how many subnets an az can have?
An AZ can have many subnets.
how many azs a subnet can have?
A subnet can only be in an AZ.
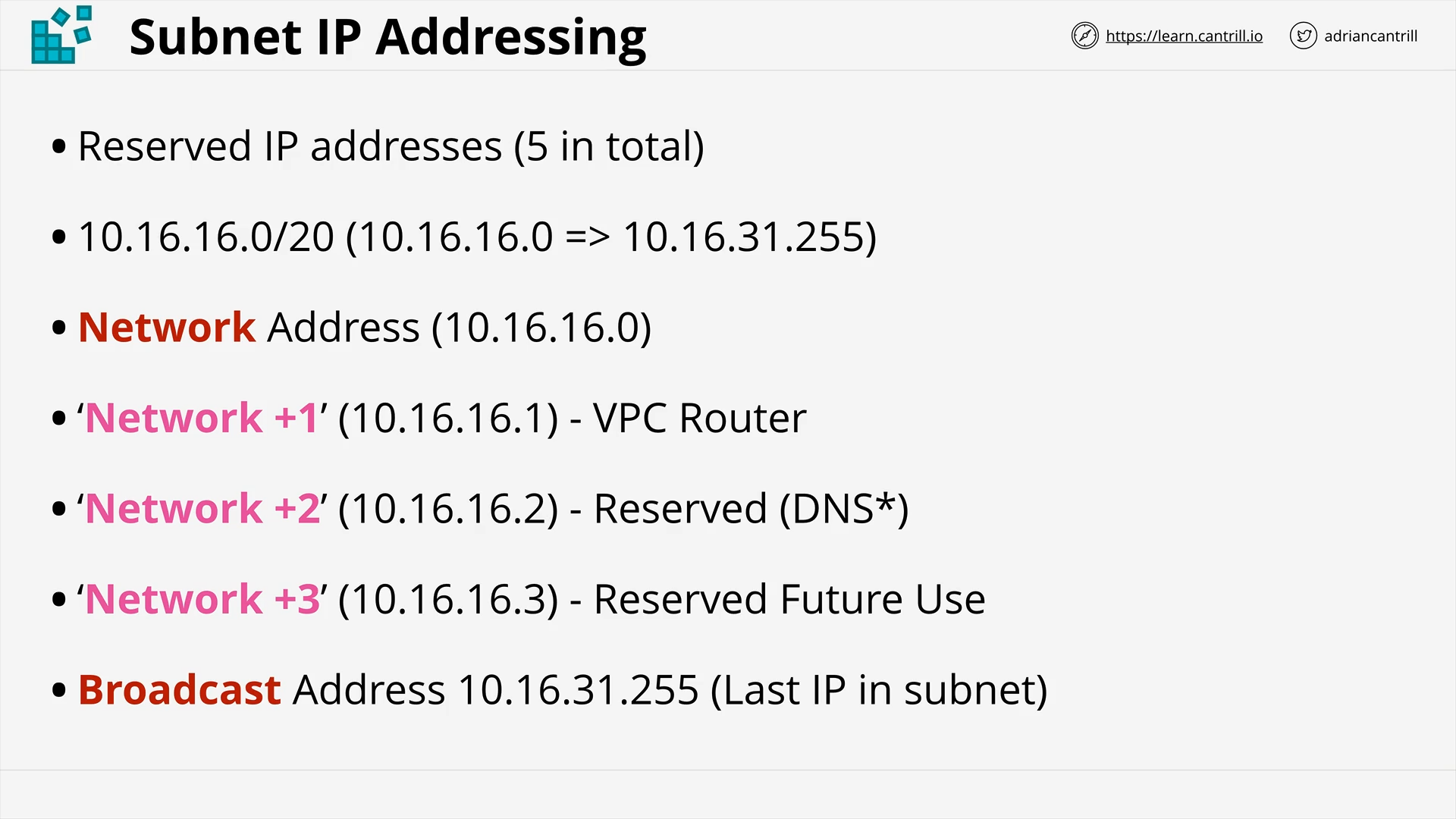 Subnet IP Addressing
Subnet IP Addressing
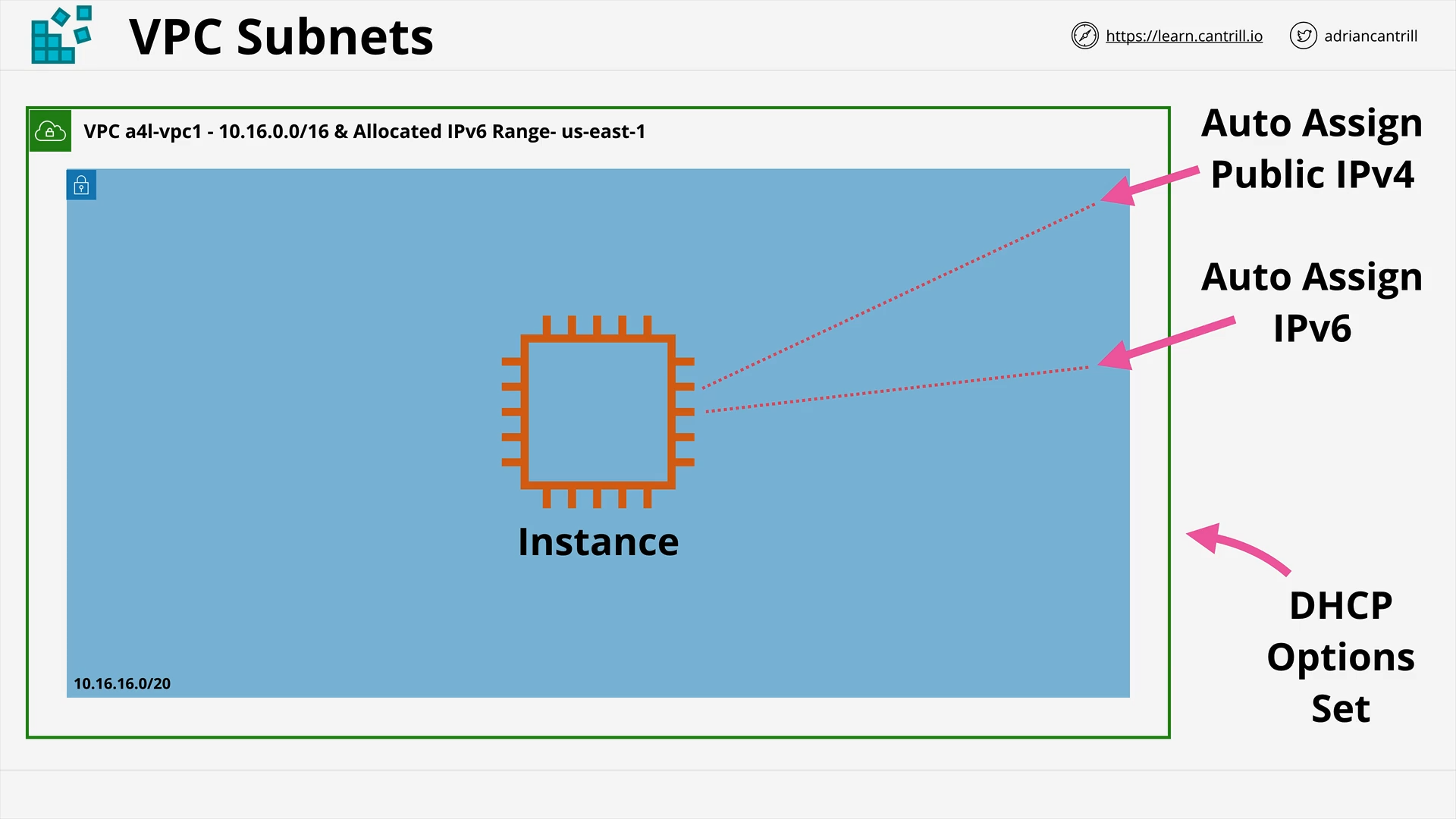 VPC Subnets - Auto Assign IP & DHCP
VPC Subnets - Auto Assign IP & DHCP
[DEMO] Implement multi-tier VPC subnets (15:24)
| No. | Subnet Name | Subnet Address | CIDR | AZ | IPv6 | Host Address Range | Broadcast Address |
|---|---|---|---|---|---|---|---|
| 1 | sb-reserved-A | 10.16.0.0 | 10.16.0.0/20 | AZ-A | 00 | 10.16.0.1 - 10.16.15.254 | 10.16.15.255 |
| 2 | sb-db-A | 10.16.16.0 | 10.16.16.0/20 | AZ-A | 01 | 10.16.16.1 - 10.16.31.254 | 10.16.31.255 |
| 3 | sb-app-A | 10.16.32.0 | 10.16.32.0/20 | AZ-A | 02 | 10.16.32.1 - 10.16.47.254 | 10.16.47.255 |
| 4 | sb-web-A | 10.16.48.0 | 10.16.48.0/20 | AZ-A | 03 | 10.16.48.1 - 10.16.63.254 | 10.16.63.255 |
| 5 | sb-reserved-B | 10.16.64.0 | 10.16.64.0/20 | AZ-B | 04 | 10.16.64.1 - 10.16.79.254 | 10.16.79.255 |
| 6 | sb-db-B | 10.16.80.0 | 10.16.80.0/20 | AZ-B | 05 | 10.16.80.1 - 10.16.95.254 | 10.16.95.255 |
| 7 | sb-app-B | 10.16.96.0 | 10.16.96.0/20 | AZ-B | 06 | 10.16.96.1 - 10.16.111.254 | 10.16.111.255 |
| 8 | sb-web-B | 10.16.112.0 | 10.16.112.0/20 | AZ-B | 07 | 10.16.112.1 - 10.16.127.254 | 10.16.127.255 |
| 9 | sb-reserved-C | 10.16.128.0 | 10.16.128.0/20 | AZ-C | 08 | 10.16.128.1 - 10.16.143.254 | 10.16.143.255 |
| 10 | sb-db-C | 10.16.144.0 | 10.16.144.0/20 | AZ-C | 09 | 10.16.144.1 - 10.16.159.254 | 10.16.159.255 |
| 11 | sb-app-C | 10.16.160.0 | 10.16.160.0/20 | AZ-C | 0A | 10.16.160.1 - 10.16.175.254 | 10.16.175.255 |
| 12 | sb-web-C | 10.16.176.0 | 10.16.176.0/20 | AZ-C | 0B | 10.16.176.1 - 10.16.191.254 | 10.16.191.255 |
| 13 | 10.16.192.0 | 10.16.192.0/20 | 10.16.192.1 - 10.16.207.254 | 10.16.207.255 | |||
| 14 | 10.16.208.0 | 10.16.208.0/20 | 10.16.208.1 - 10.16.223.254 | 10.16.223.255 | |||
| 15 | 10.16.224.0 | 10.16.224.0/20 | 10.16.224.1 - 10.16.239.254 | 10.16.239.255 | |||
| 16 | 10.16.240.0 | 10.16.240.0/20 | 10.16.240.1 - 10.16.255.254 | 10.16.255.255 |
VPC Routing, Internet Gateway & Bastion Hosts (17:35)
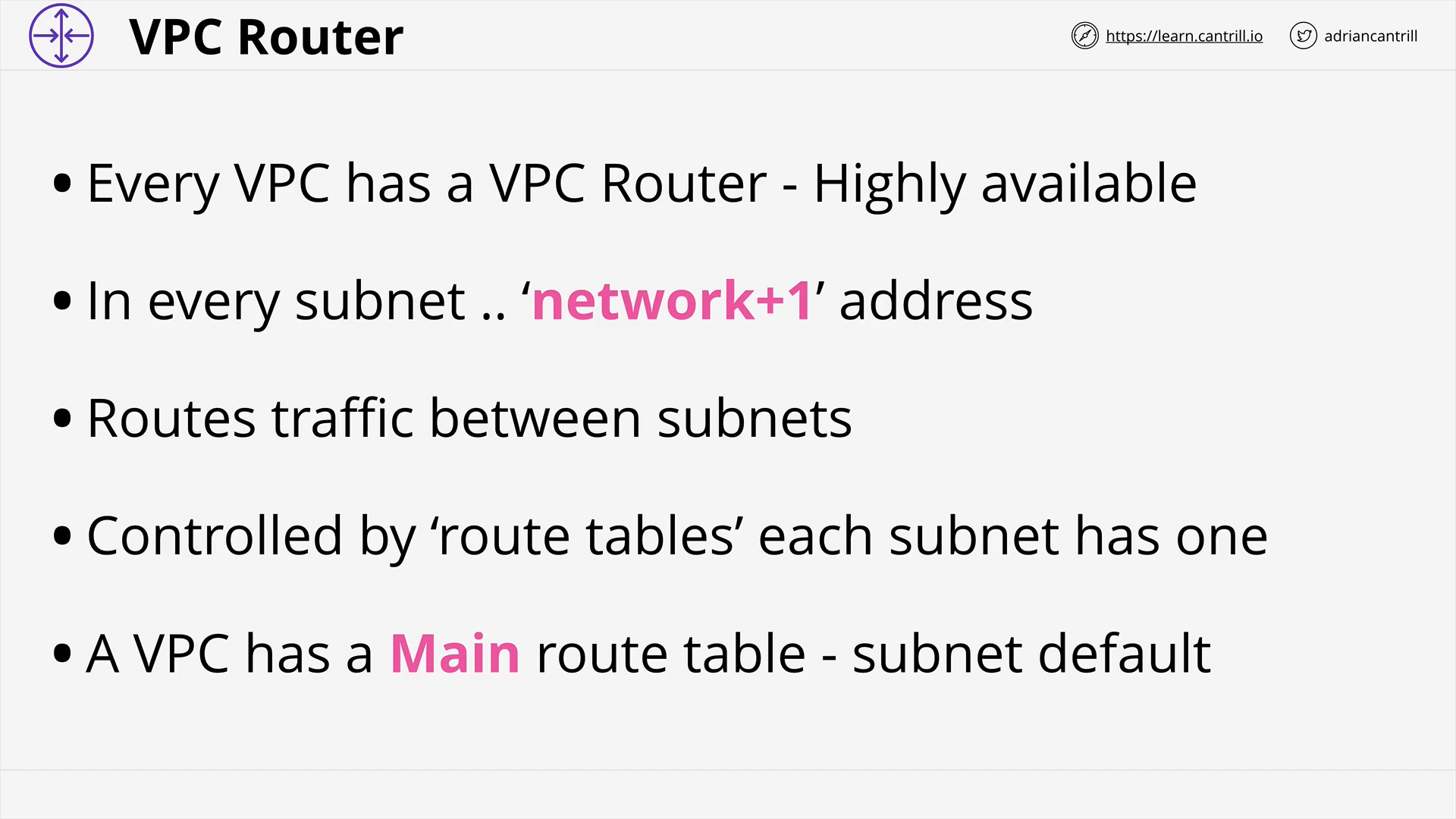 VPC Router
VPC Router
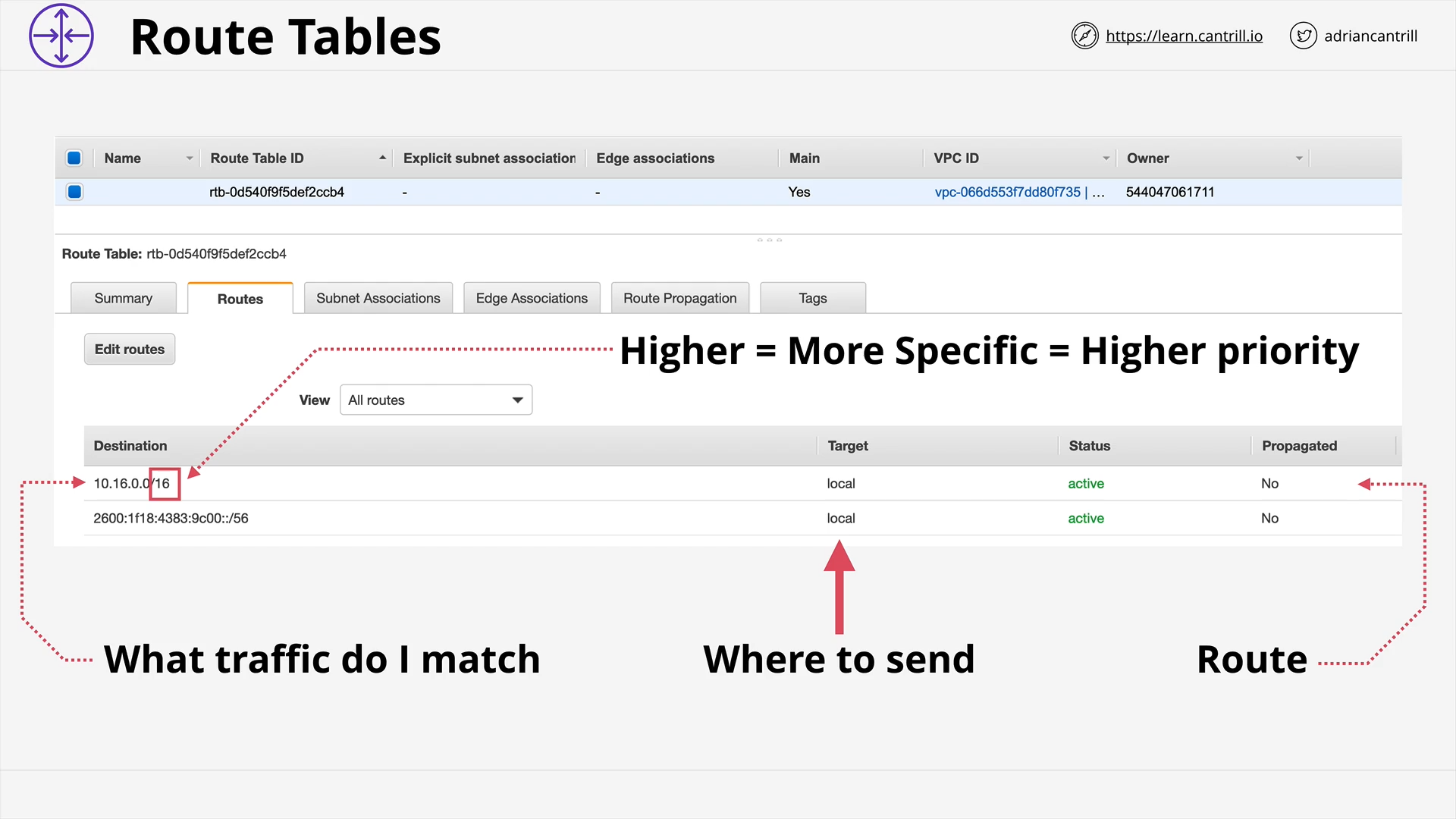 Route Tables
Route Tables
how many subnets a route table can be associated with?
A Route Table can be associated with many subnets.
how many route tables a subnet can be associated with?
A subnet can be attached with only ONE Route Table.
 Internat Gateway (IGW)
Internat Gateway (IGW)
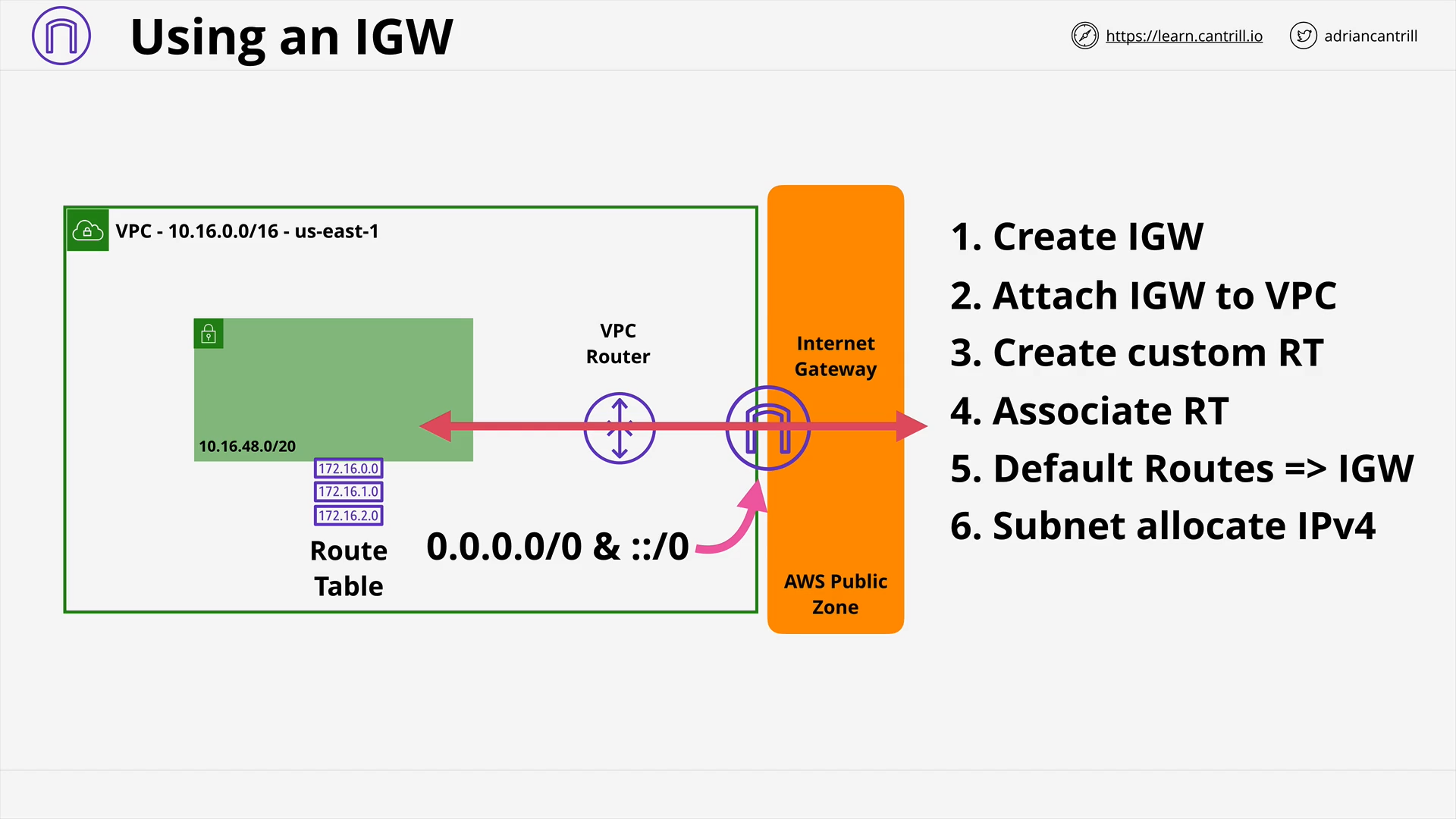 Using an IGW
Using an IGW
/00_LEARNINGAIDS/IGW.png) IPv4 Addresses with an IGW - Outbound Traffic
IPv4 Addresses with an IGW - Outbound Traffic
/00_LEARNINGAIDS/IGW-2.png) IPv4 Addresses with an IGW - Inbound Traffic
IPv4 Addresses with an IGW - Inbound Traffic
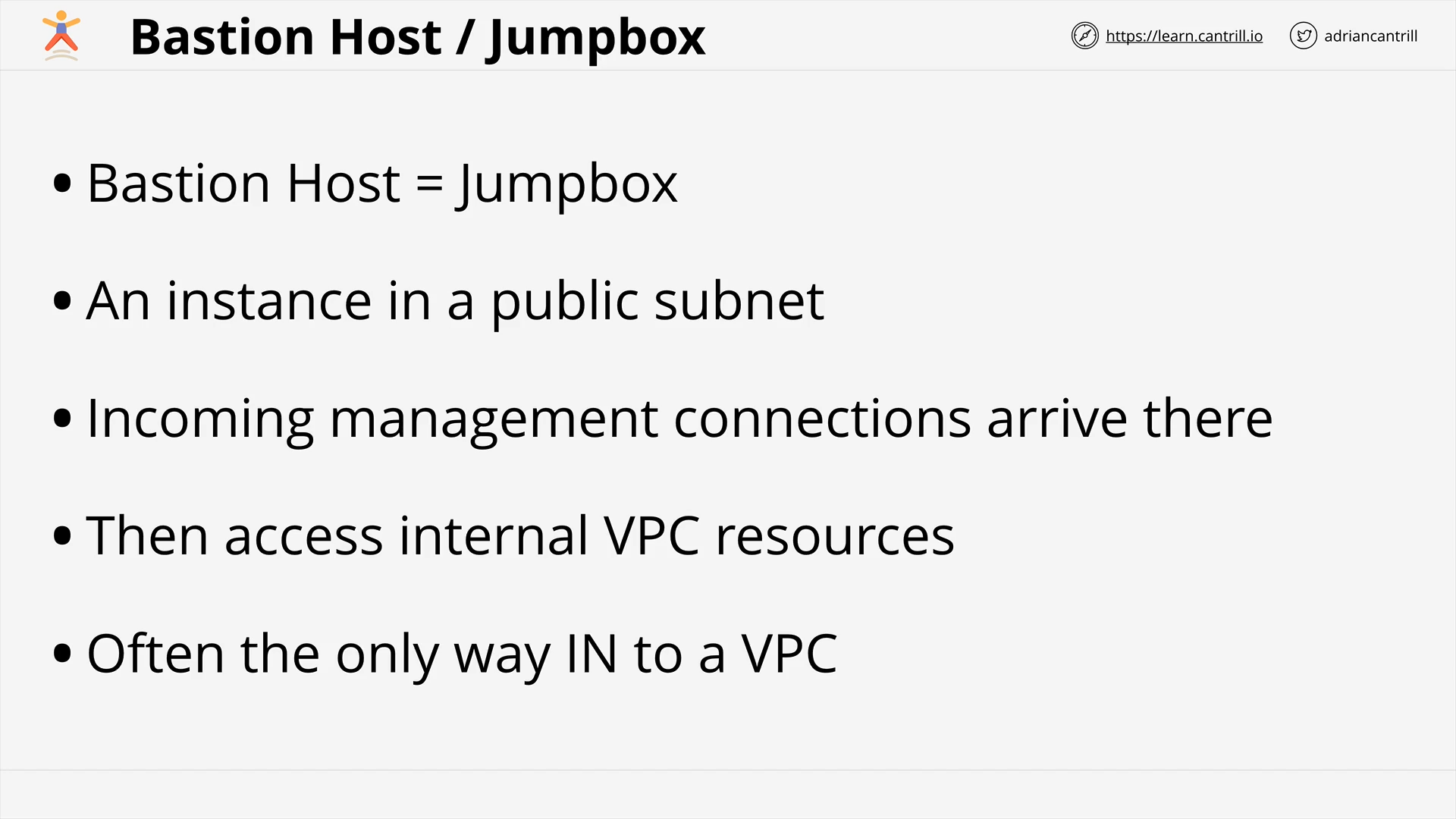 Bastion Host / Jumpbox
Bastion Host / Jumpbox
[DEMO] Configuring A4l public subnets and Jumpbox - PART1 (13:45)
[DEMO] Configuring A4l public subnets and Jumpbox - PART2 (11:45)
Stateful vs Stateless Firewalls (14:04)
/00_LEARNINGAIDS/StatefulvsStateless-1.png) TCP
TCP
/00_LEARNINGAIDS/StatefulvsStateless-2.png) Every “Connection” has 2 parts: REQUEST & RESPONSE
Every “Connection” has 2 parts: REQUEST & RESPONSE
/00_LEARNINGAIDS/StatefulvsStateless-3.png) Directionality (Inbound or Outbound) depends on perspective (Client/Server)
Directionality (Inbound or Outbound) depends on perspective (Client/Server)
/00_LEARNINGAIDS/StatefulvsStateless-4.png) With Stateless Firewall, a connection needs 2 rules (1 IN, 1 OUT) to go through
With Stateless Firewall, a connection needs 2 rules (1 IN, 1 OUT) to go through
with stateless firewall, ephemeral port is not the well known port (e.g. 443, 80)
/00_LEARNINGAIDS/StatefulvsStateless-5.png) Stateful firewall is intelligent enough to identify the REQUEST and RESPONSE components of a connection as being related
Stateful firewall is intelligent enough to identify the REQUEST and RESPONSE components of a connection as being related
/00_LEARNINGAIDS/StatefulvsStateless-6.png)
Network Access Control Lists (NACLs) (12:38)
/00_LEARNINGAIDS/NACL-1.png) NACLs filter traffic across the subnet’s boundary
NACLs filter traffic across the subnet’s boundary
what is nacl?
A set of rules grouped into:
- INBOUND rules 👉 match traffic ENTERING the subnet
- OUTBOUND rules 👉 match traffic LEAVING the subnet
what does nacl do?
NACLs filter traffic across the subnet’s boundary.
how are nacl's rules processed?
NACL’s rules are process in order:
- Lowest rule number first. 🤏1️⃣
- Once a match occurs, processing STOPS. 🛑
- If nothing else matched,
*is process 👈 implicit DENY ❌
/00_LEARNINGAIDS/NACL-2.png) NACLs are stateless firewall
NACLs are stateless firewall
/00_LEARNINGAIDS/NACL-3.png) Rule-pairs (
Rule-pairs (app port & ephemeral port) are needed on each NACL for each communication type which occurs:
- 🔄️ within a VPC
- ➡️ to a VPC
- ⬅️ from a VPC
/00_LEARNINGAIDS/NACL-4.png) Default NACL - The NACL created with a VPC
Default NACL - The NACL created with a VPC
what does default nacl do?
Default NACL does NOTHING. It has an ALLOW ALL rule.
/00_LEARNINGAIDS/NACL-5.png) Custom NACL DENIED ALL traffic after created
Custom NACL DENIED ALL traffic after created
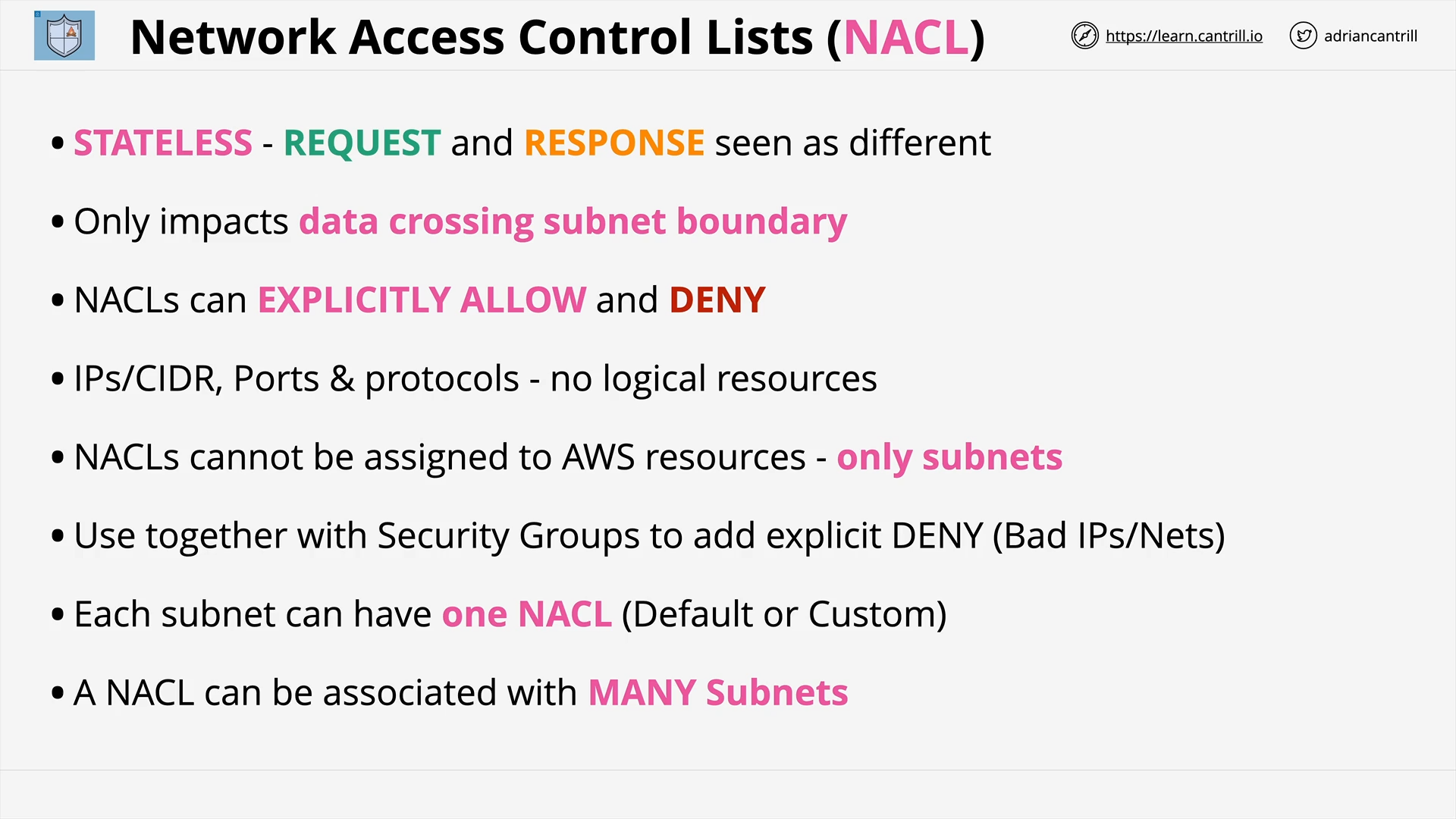 NACL - Summary
NACL - Summary
which aws resources can be use with nacls?
NACLS can only be used with subnets.
how many subnets a nacl can be associated with?
A NACL can be associated with MANY subnets.
how many nacls a subnet can have?
A subnet can only have ONE (1) NACL.
Security Groups (SG) (11:48)
__learn.cant.png) Security Group (SG) is STATEFUL firewall
Security Group (SG) is STATEFUL firewall
which type of rules a sg can have?
SG can only have ALLOW rule.
👉 SG can’t block specific bad actors 😈
can sg deny a traffic?
No. SG can’t deny traffic. It can’t block bad actors.
Because SG only support ALLOW rules.
which kind of sources does sg rules support?
SG rules supports:
- CIDR blocks
- Many AWS logical resources:
- Other SGs
- Itself 🤯
- Prefix Lists 📃
to which, the sgs are attached to?
SGs are attached to ENI, not the instances.
/00_LEARNINGAIDS/SG-1.png) SG is applied to all traffic entering or leaving the ENI
SG is applied to all traffic entering or leaving the ENI
/00_LEARNINGAIDS/SG-2.png) An SG reference applies to anything which has the SG attached
An SG reference applies to anything which has the SG attached
/00_LEARNINGAIDS/SG-3.png) With SG reference, any new instances uses a SG has that SG reference ALLOW rule
With SG reference, any new instances uses a SG has that SG reference ALLOW rule
/00_LEARNINGAIDS/SG-4.png) With SG Self reference, the instances can scale easily
With SG Self reference, the instances can scale easily
Network Address Translation (NAT) & NAT Gateway - PART1 (13:43)
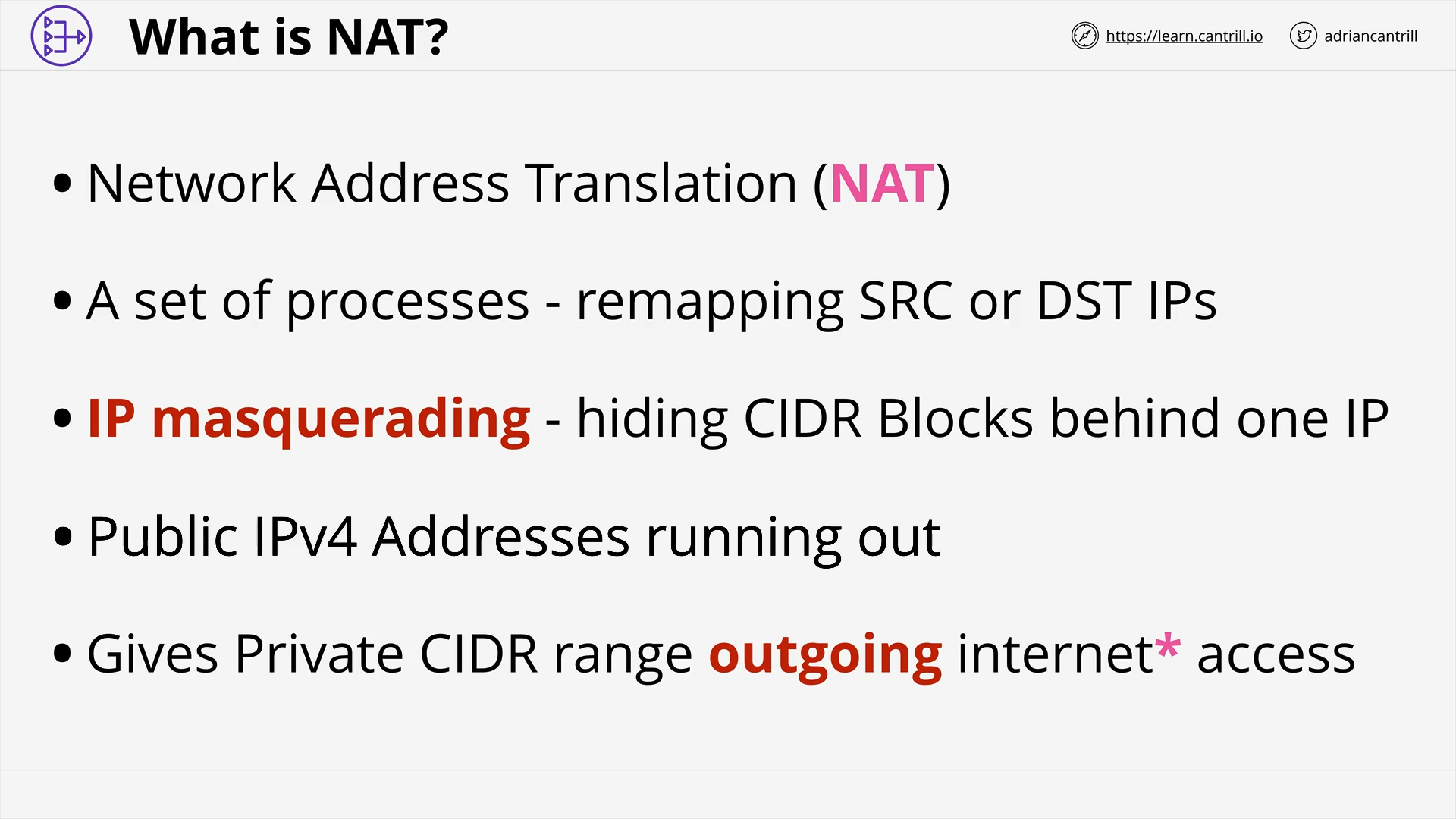
aws internet gateway (aws igw) is a nat (static nat)
what can nat can be used for?
- IP masquerading 👺: hiding CIDR blocks behind one IP.
- Gives Private CIDR block outgoing internet access.
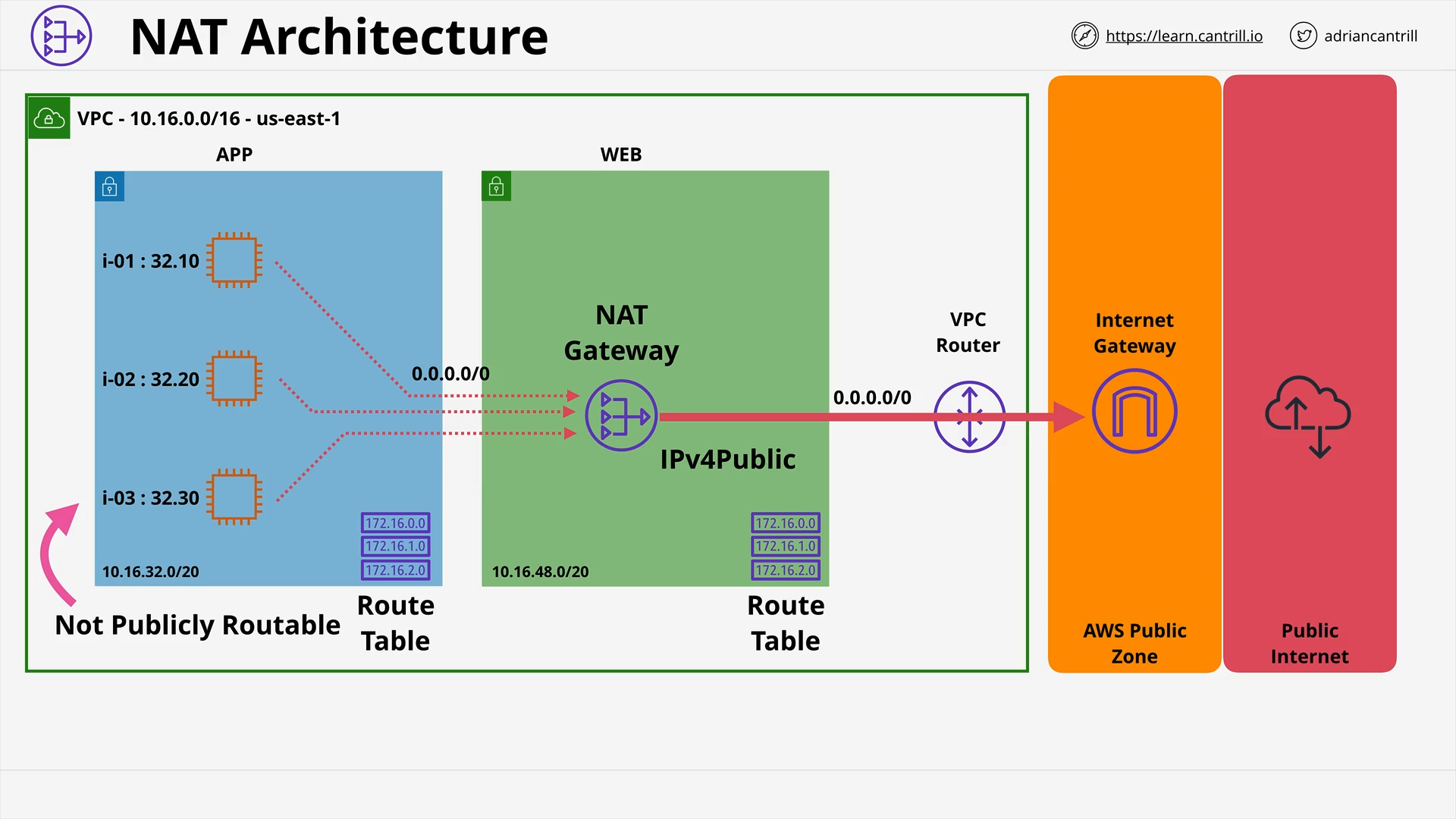 NAT Architecture - Example
NAT Architecture - Example
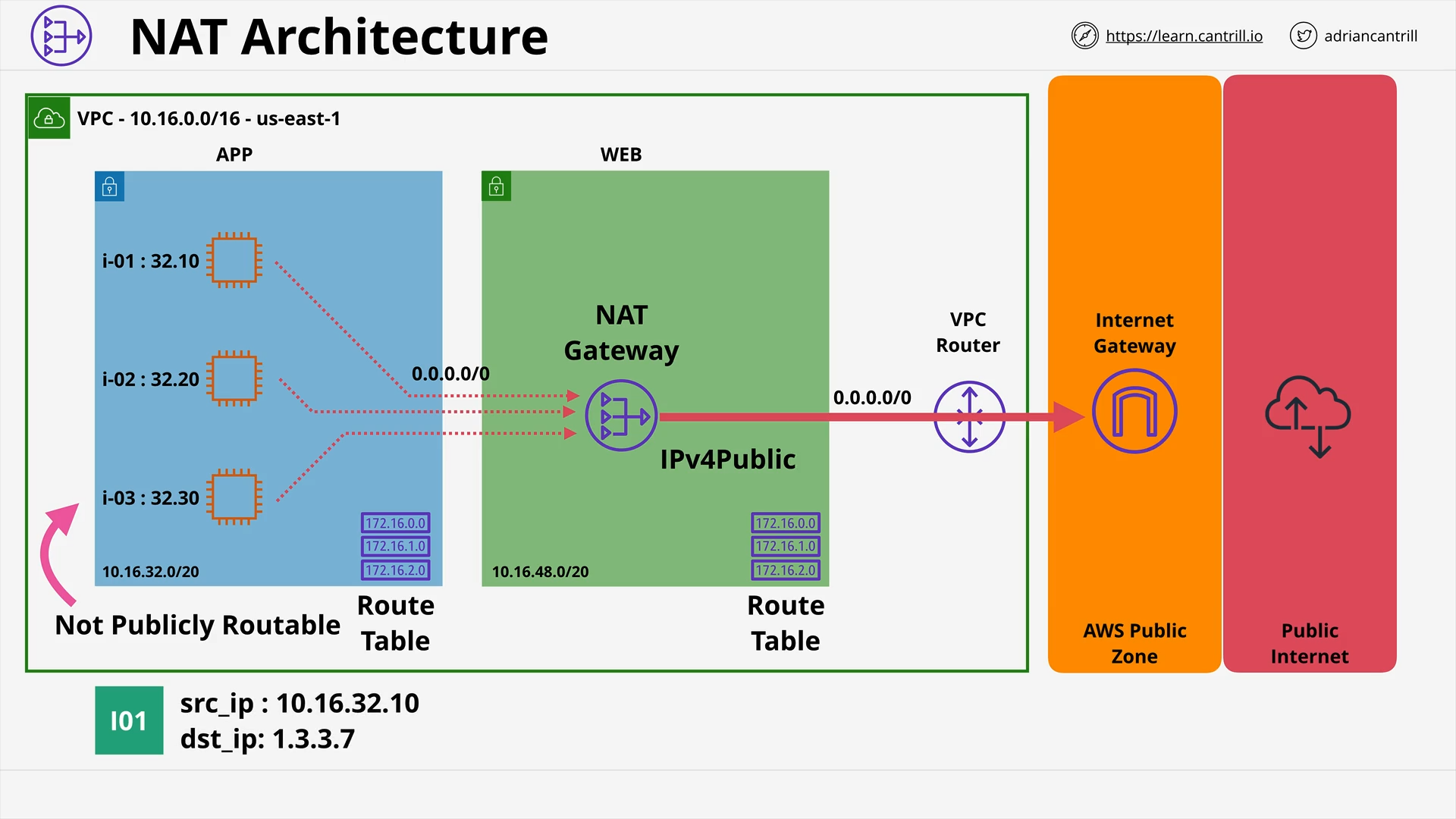 Routing a package from an instance in a private subnet …
Routing a package from an instance in a private subnet …
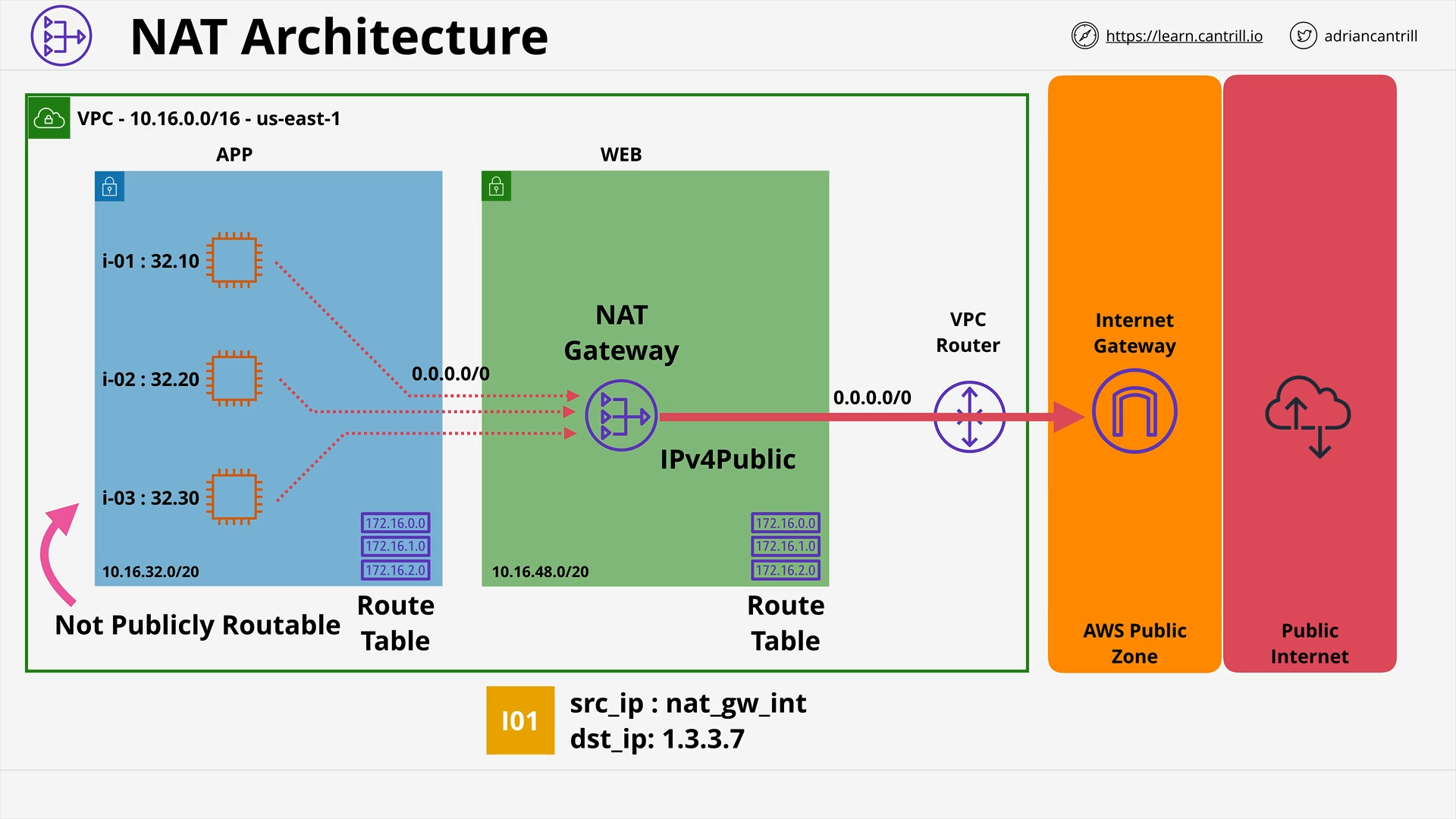 … through the NAT Gateway (in a public subnet) …
… through the NAT Gateway (in a public subnet) …
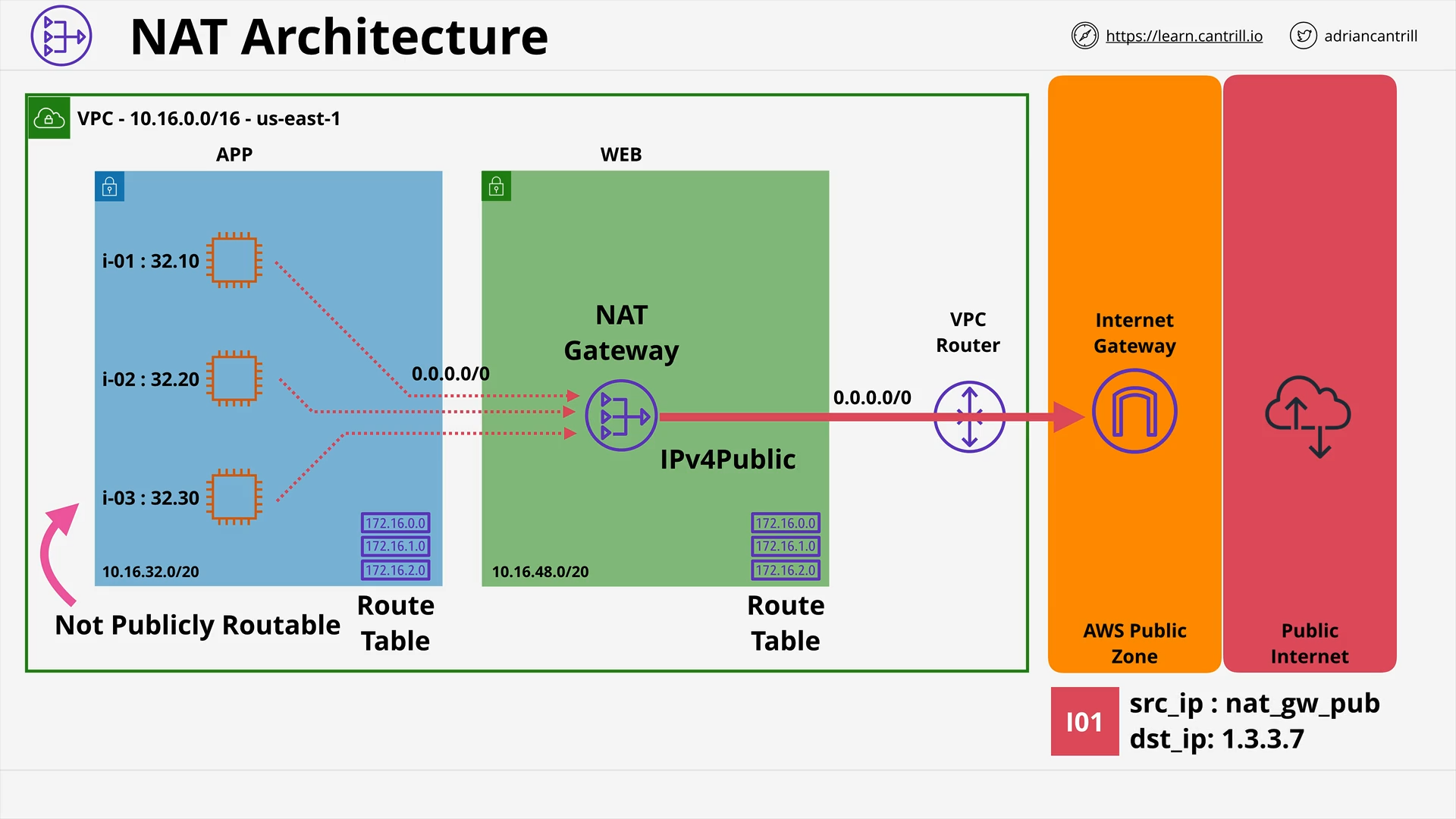 … through the Internet Gateway, then to the Public Internet.
… through the Internet Gateway, then to the Public Internet.
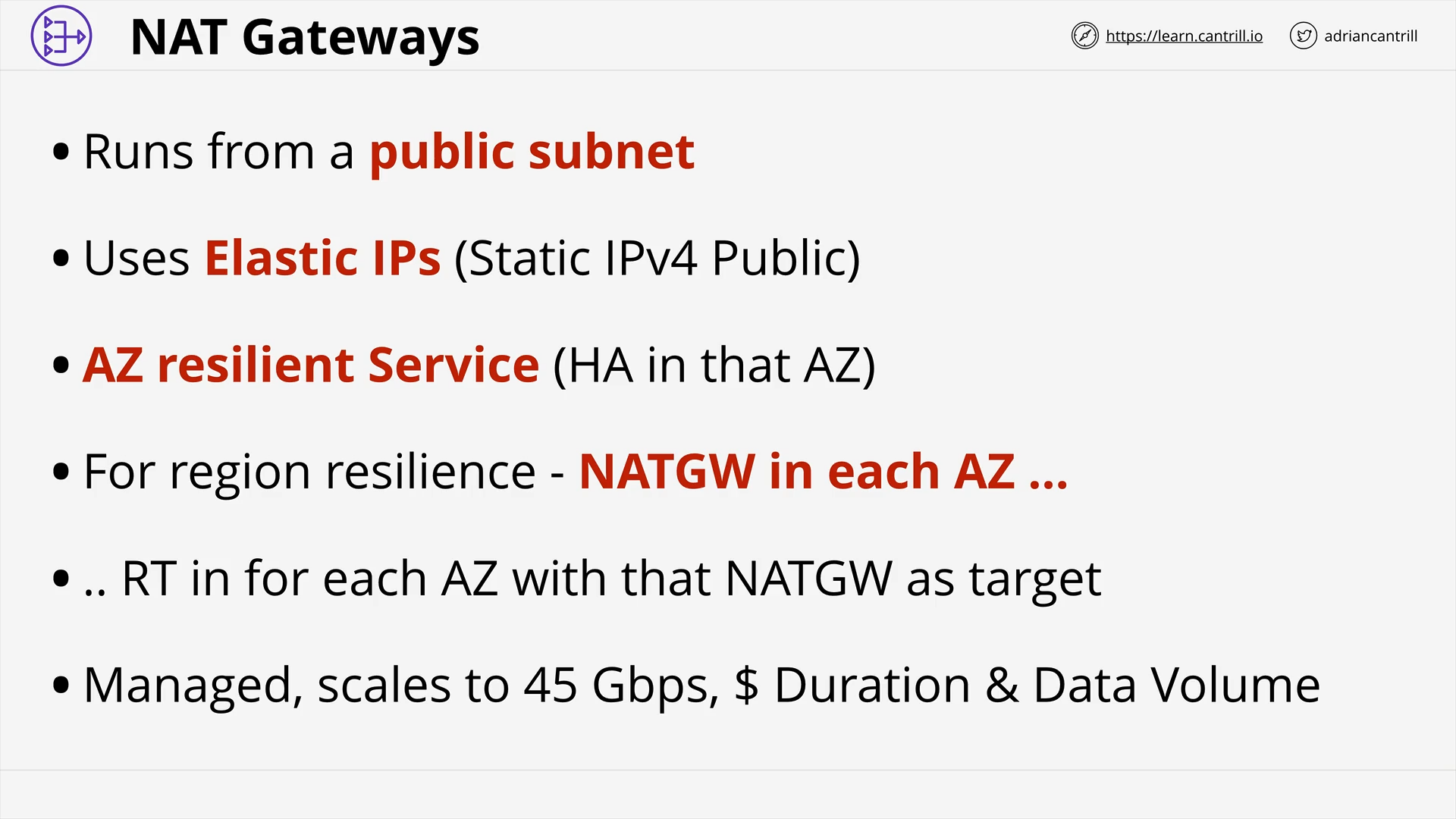 NAT Gateways run from a public subnet, uses Elastic IPs
NAT Gateways run from a public subnet, uses Elastic IPs
what level of resilient nat gateway is?
NAT Gateway is an AZ resilient service.
how to have the region resilience for nat gateways?
NATGW in each AZ, and Route Tables in each AZ targets that NATGW.
Network Address Translation (NAT) & NAT Gateway - PART2 (11:08)
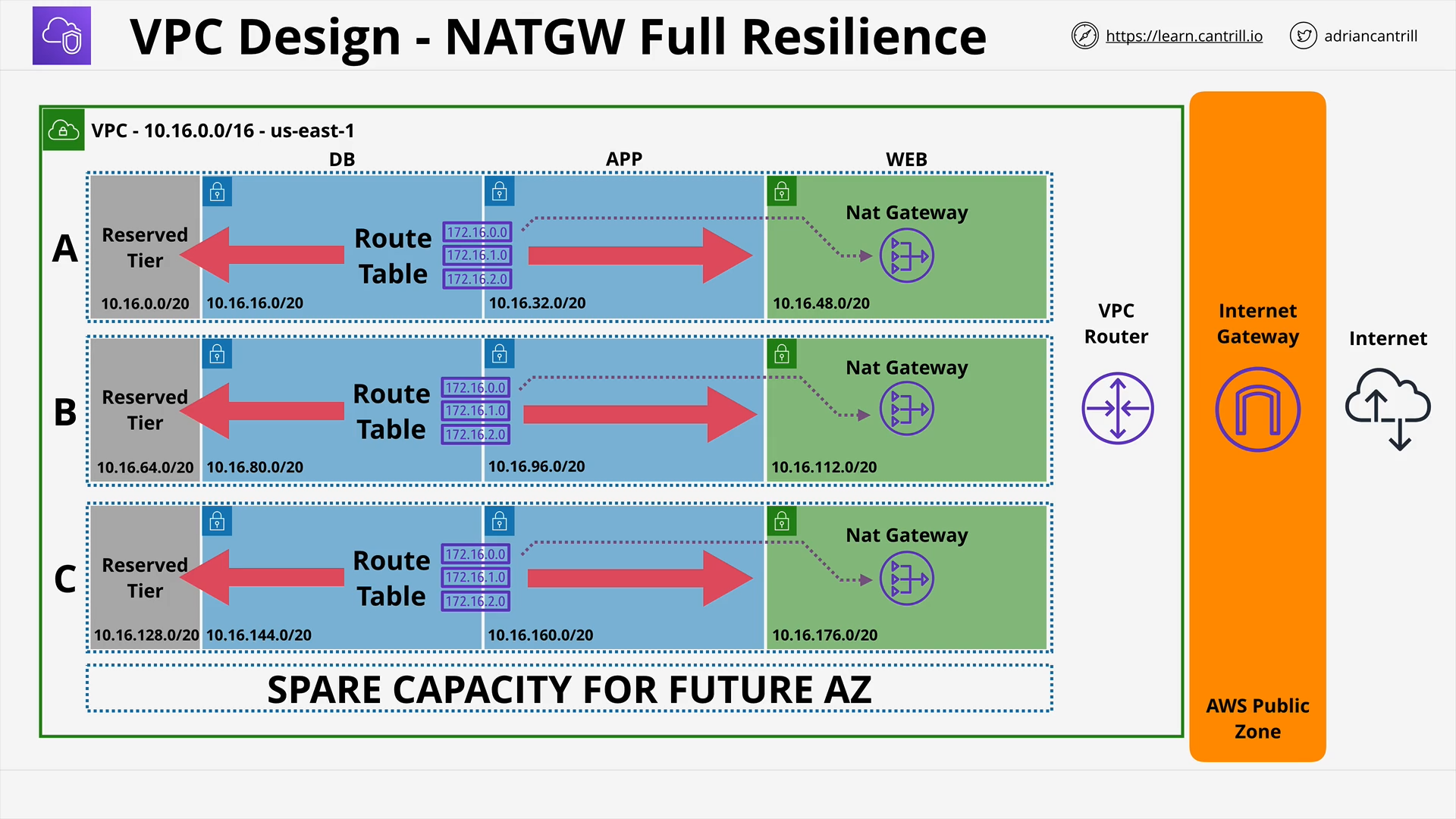 VPC Design - NATGW Full Resilience
VPC Design - NATGW Full Resilience
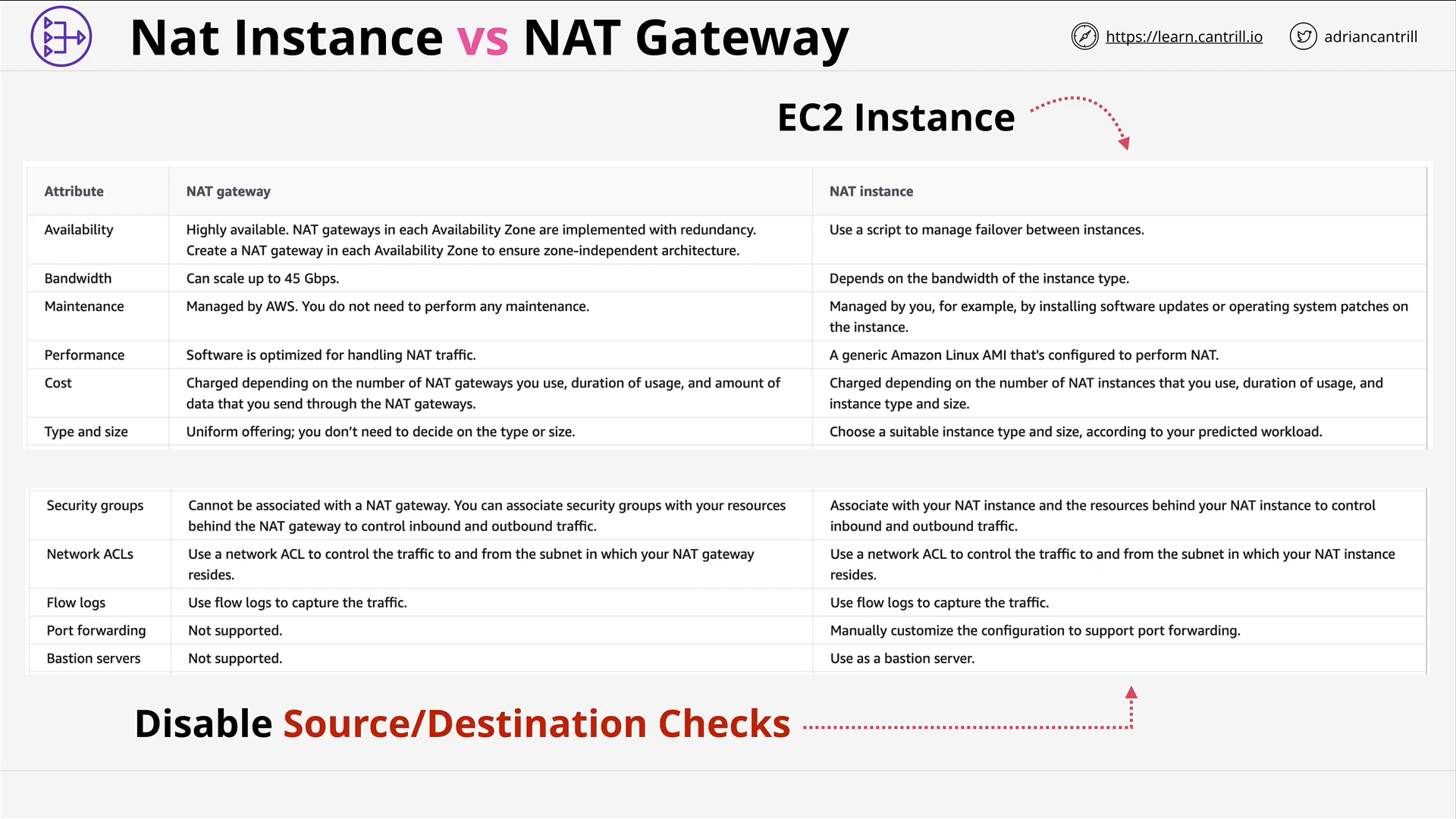 NAT Instance vs NAT Gateway
NAT Instance vs NAT Gateway
what is nat instance?
 NAT Gateway and IPv6
NAT Gateway and IPv6
which kind of ip version can nat gateway work with?
NAT Gateway only works with IPv4, it doesn’t work with IPv6.
All IPv6 addresses in AWS are publicly routable. The IGW works with IPv6 directly without the NAT Gateway.
[DEMO] Implementing private internet access using NAT Gateways (19:25)
VPC Basics Section Quiz
ELASTIC COMPUTE CLOUD (EC2) BASICS
Virtualization 101 (12:27)
/00_LEARNINGAIDS/Virtualization101-1.png) Privileged Mode / User Mode - Kernel - System Call
Privileged Mode / User Mode - Kernel - System Call
/00_LEARNINGAIDS/Virtualization101-2.png) How to run multiple OSes with a single piece of hardware?
How to run multiple OSes with a single piece of hardware?
/00_LEARNINGAIDS/Virtualization101-3.png) Emulated Virtualization
Emulated Virtualization
/00_LEARNINGAIDS/Virtualization101-4.png) Para-virtualization
Para-virtualization
/00_LEARNINGAIDS/Virtualization101-5.png) Hardware Assisted Virtualization
Hardware Assisted Virtualization
/00_LEARNINGAIDS/Virtualization101-6.png) SR-IOV
SR-IOV
EC2 Architecture and Resilience (12:36)
 EC2 - Overview
EC2 - Overview
/00_LEARNINGAIDS/EC2Architecture-1.png) EC2 - Architecture
EC2 - Architecture
what is the level of resilience of ec2 service?
EC2 has AZ-level resilience
 What’s EC2 Good for?
What’s EC2 Good for?
EC2 Instance Types - PART1 (11:52)
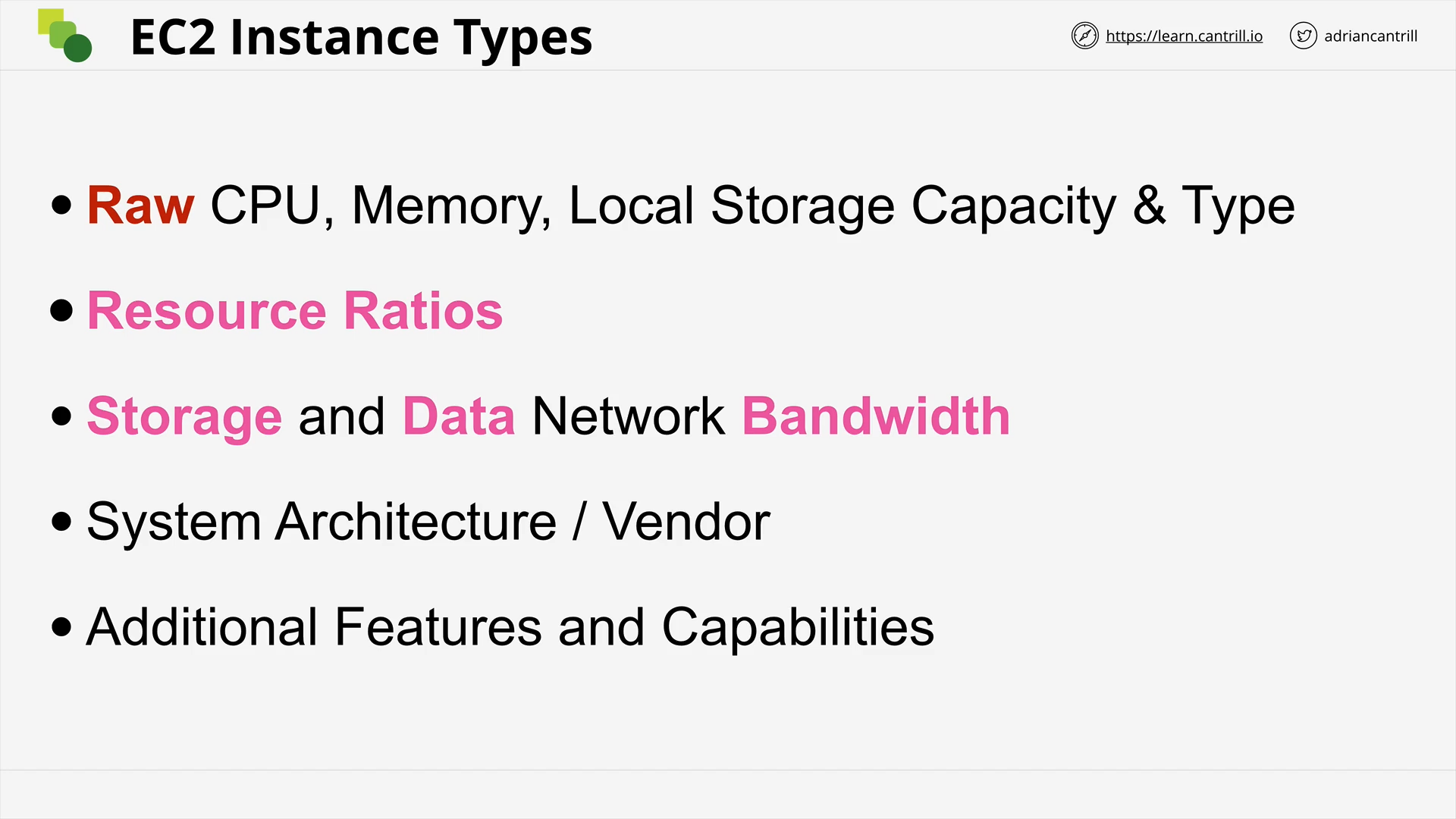
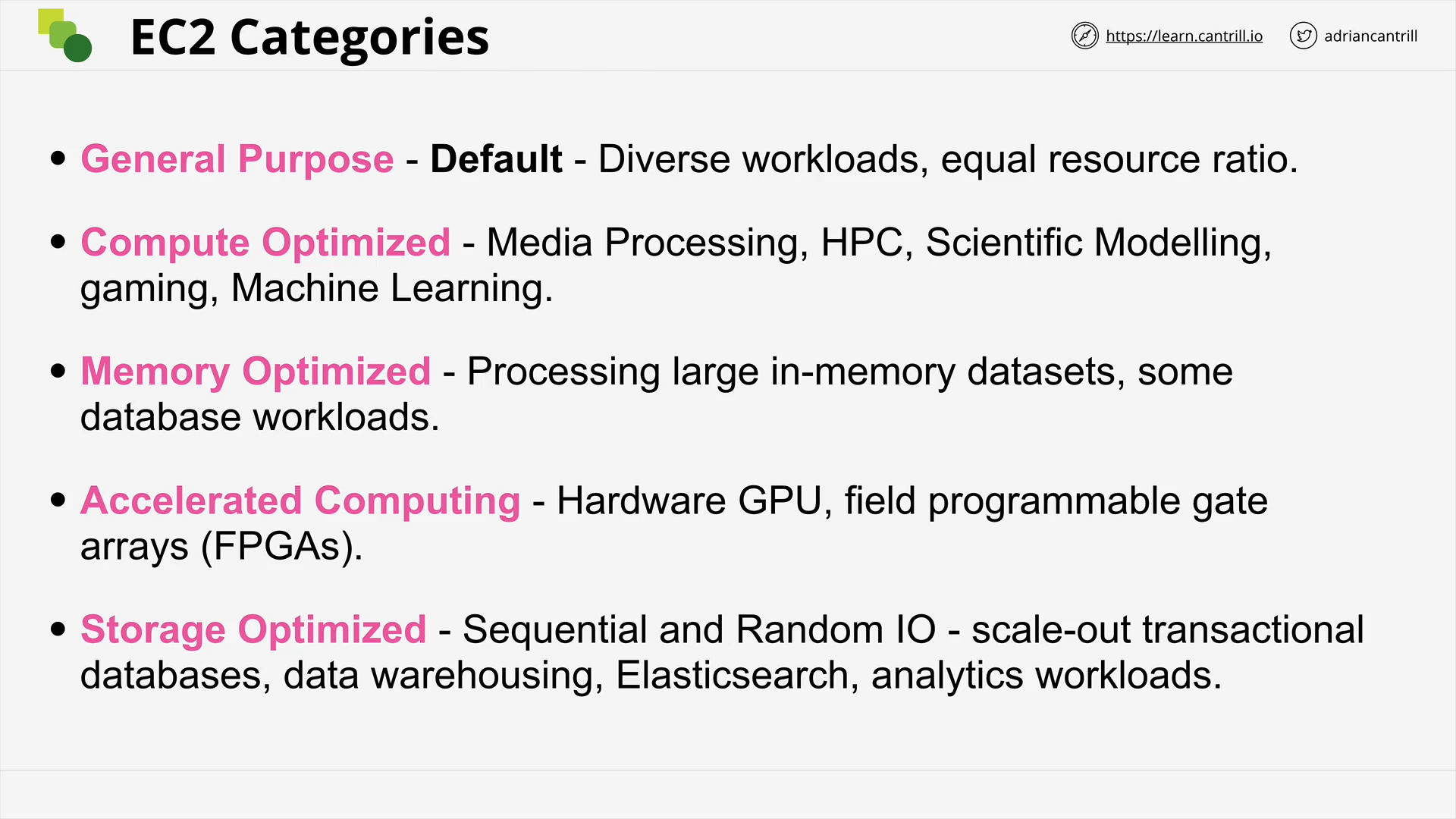
/00_LEARNINGAIDS/EC2InstanceTypes.png)
EC2 Instance Types - PART2 (8:13)
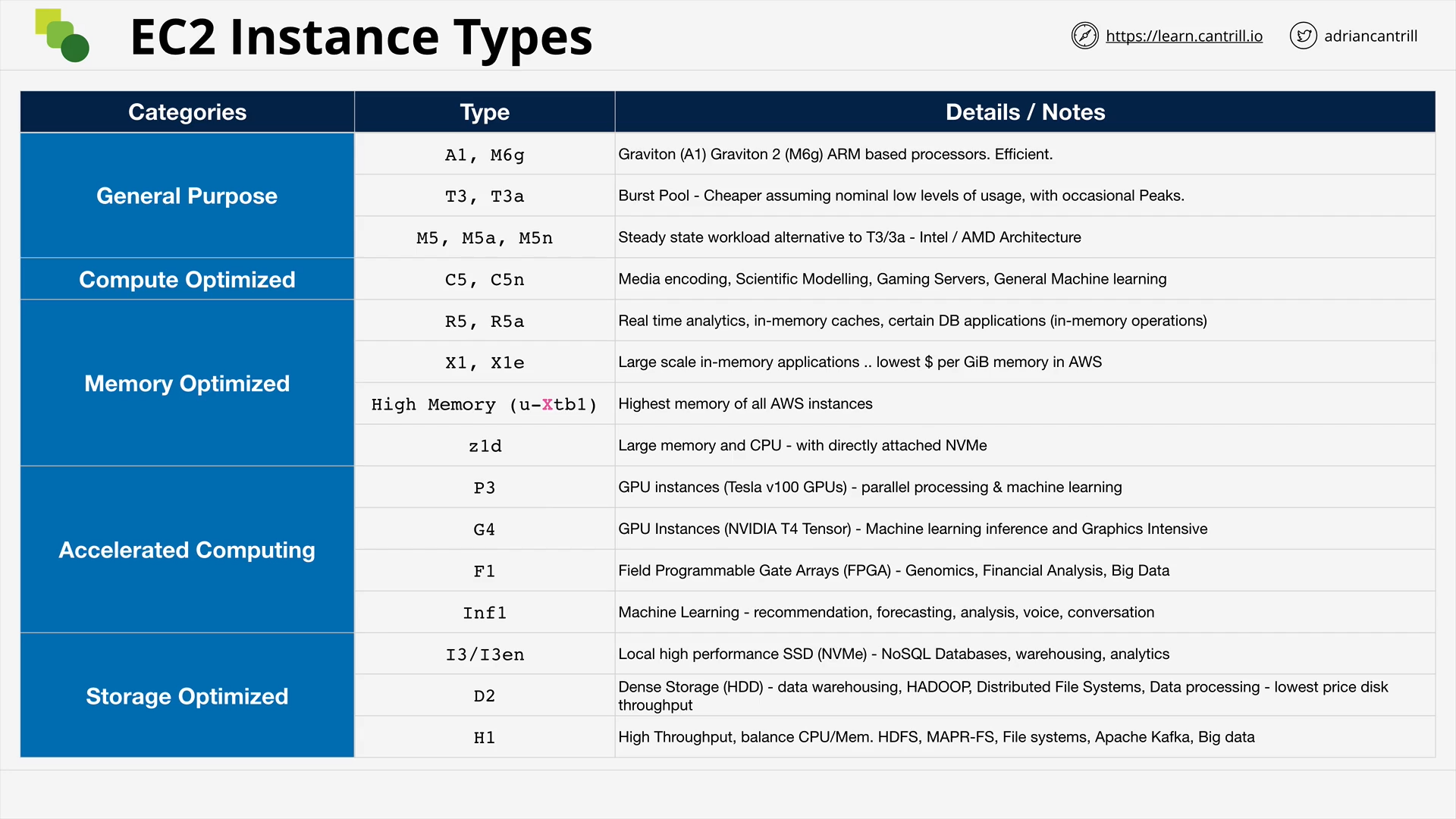
[DEMO] EC2 SSH vs EC2 Instance Connect (17:06)
Storage Refresher (14:16)
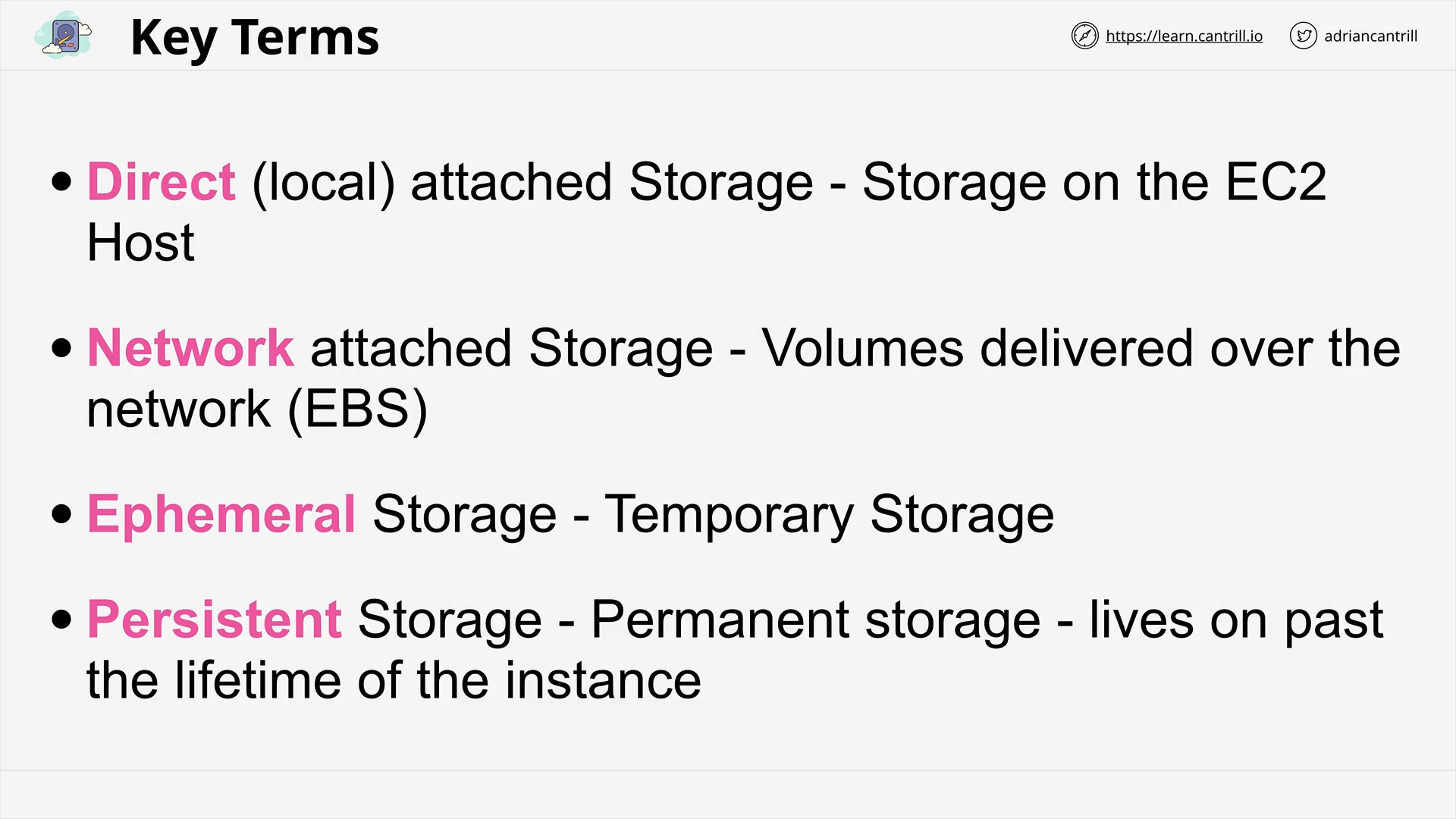 Direct / Network Storage, Ephemeral / Persistent Storage
Direct / Network Storage, Ephemeral / Persistent Storage
/00_LEARNINGAIDS/StorageRefresher-1.png) Block / File / Object Storage
Block / File / Object Storage
/00_LEARNINGAIDS/StorageRefresher-2.png) IO Block Size - IOPS - Throughput
IO Block Size - IOPS - Throughput
Elastic Block Store (EBS) Service Architecture (8:43)
_Servic.png) EBS Architecture
EBS Architecture
_Servic.png) EBS Snapshot
EBS Snapshot
EBS Volume Types - General Purpose (9:23)
/00_LEARNINGAIDS/EBSVolumes-1.png) EBS - GP2
EBS - GP2
/00_LEARNINGAIDS/EBSVolumes-2.png) EBS - GP3
EBS - GP3
EBS Volume Types - Provisioned IOPS (6:15)
/00_LEARNINGAIDS/EBSVolumes-3.png)
EBS Volume Types - HDD-Based (4:32)
/00_LEARNINGAIDS/EBSVolumes-4.png)
Instance Store Volumes - Architecture (9:00)
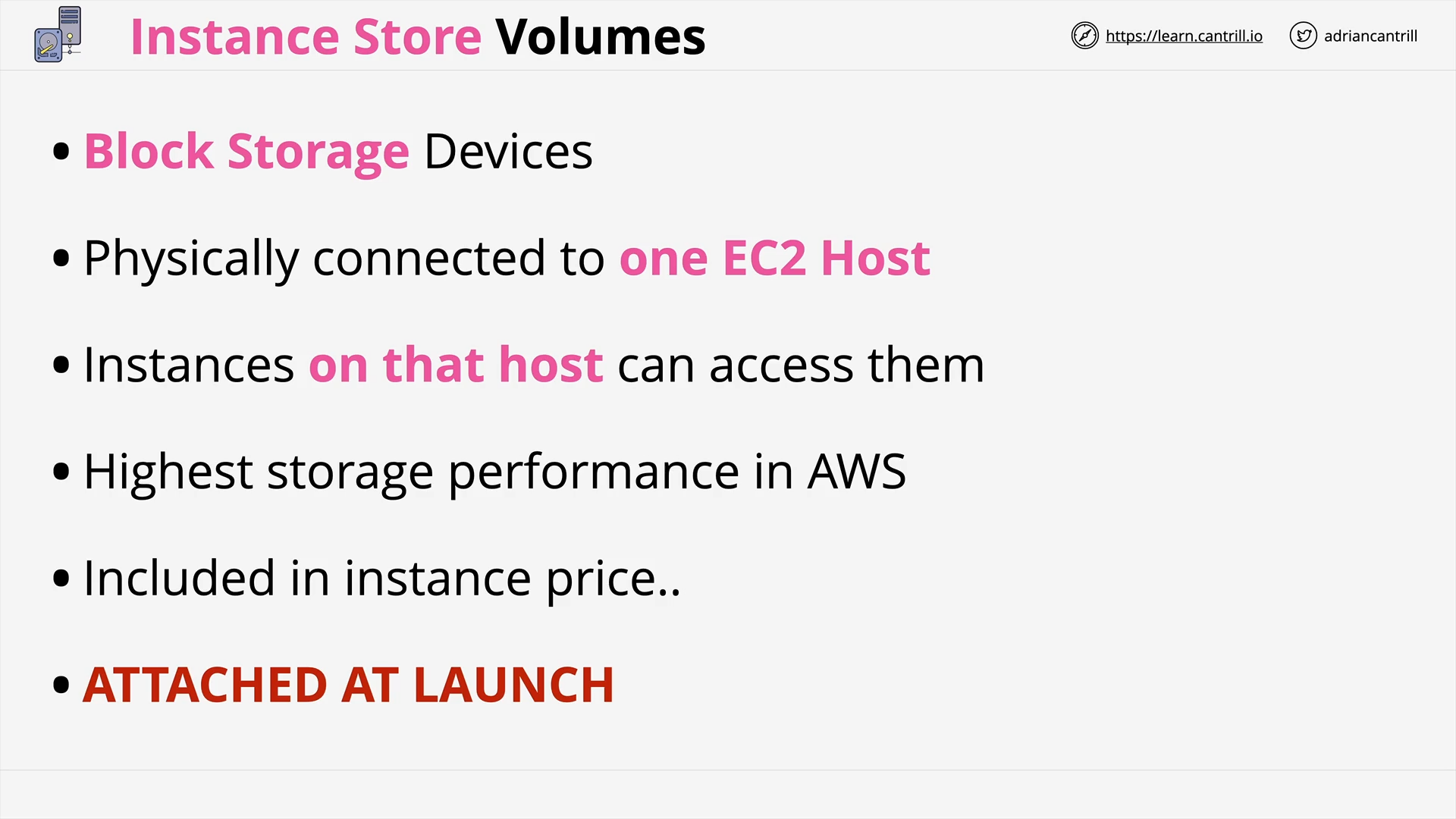 Instance Store is local storage on the EC2 host
Instance Store is local storage on the EC2 host
what kind of storage has the highest performance for ec2?
Instance Store
what is the price model of ec2 instance store?
Instance Store is include in instance price.
what is the lifecycle of instance store?
It’s can only be attached at instance launch.
/00_LEARNINGAIDS/InstanceStoreVolumes.png) Instance Store is ephemeral storage, attached with an EC2 host
Instance Store is ephemeral storage, attached with an EC2 host
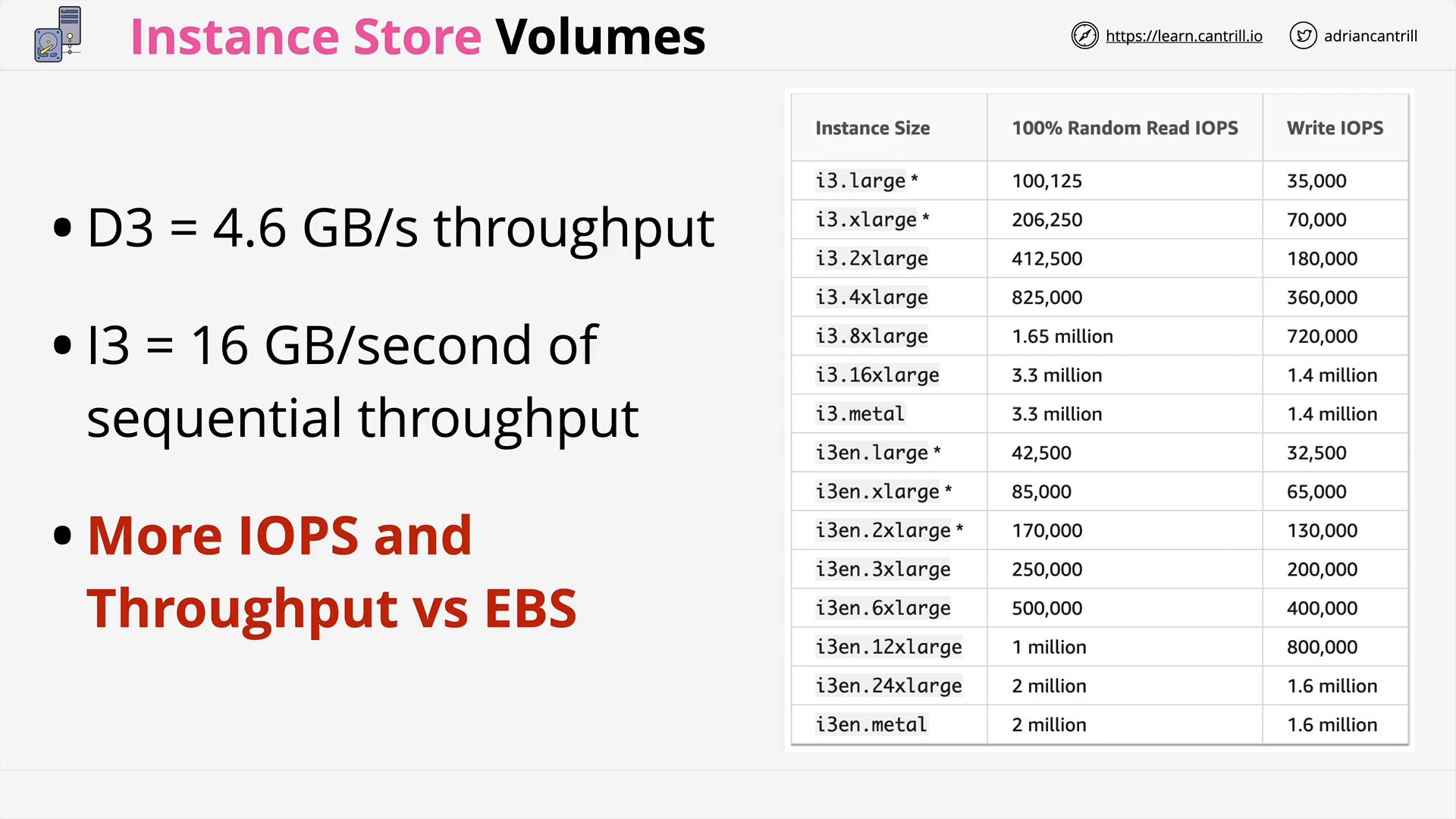 Instance Store - Throughput
Instance Store - Throughput
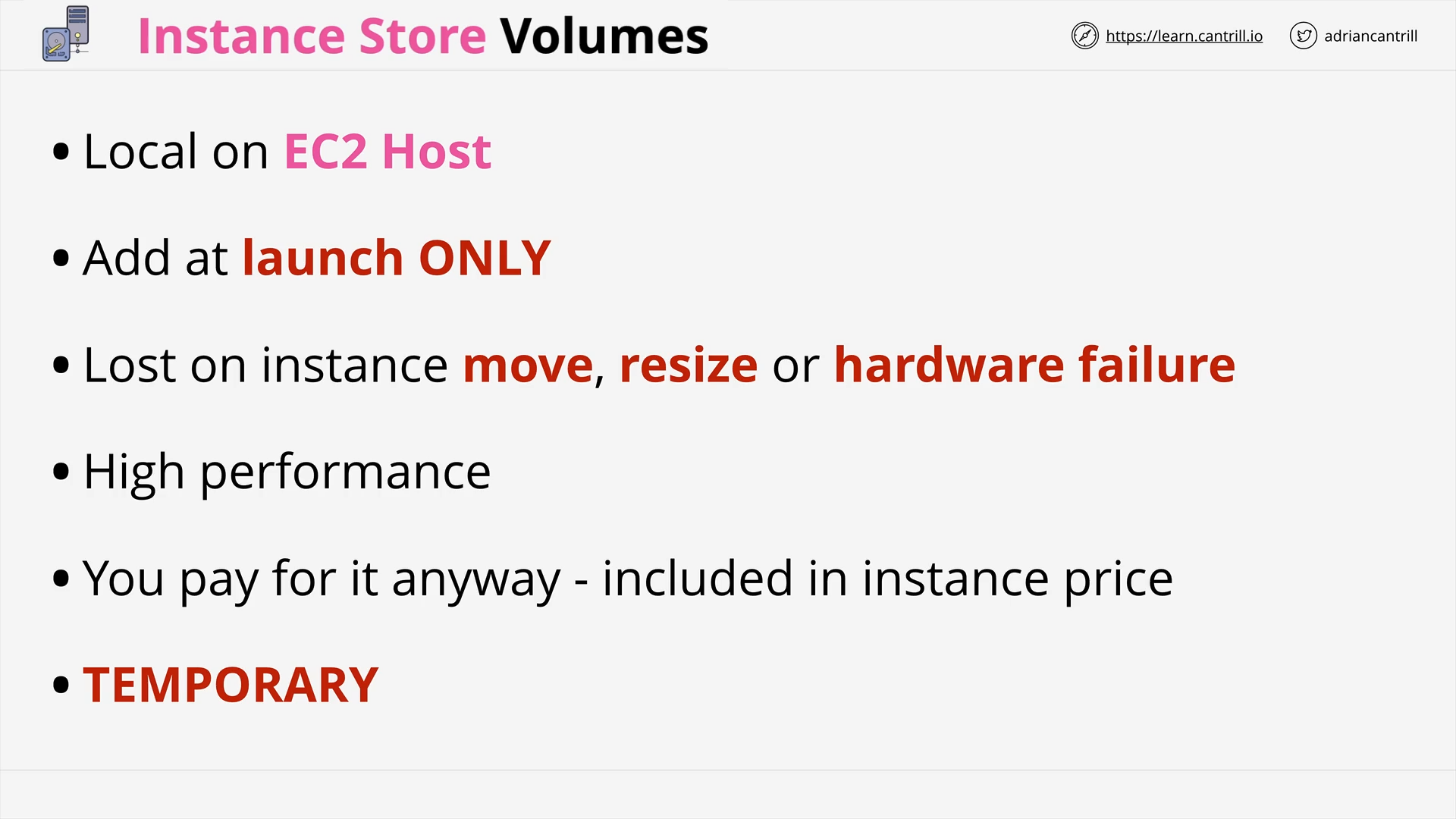 Instance Store - Recap
Instance Store - Recap
Choosing between the EC2 Instance Store and EBS (8:49)
/00_LEARNINGAIDS/InstanceStorevsEBS-1.png)
/00_LEARNINGAIDS/InstanceStorevsEBS-2.png)
Snapshots, Restore & Fast Snapshot Restore (FSR) (10:55)
 EBS Snapshots
EBS Snapshots
/00_LEARNINGAIDS/EBSSnapshots-1.png) EBS Snapshots - Architecture
EBS Snapshots - Architecture
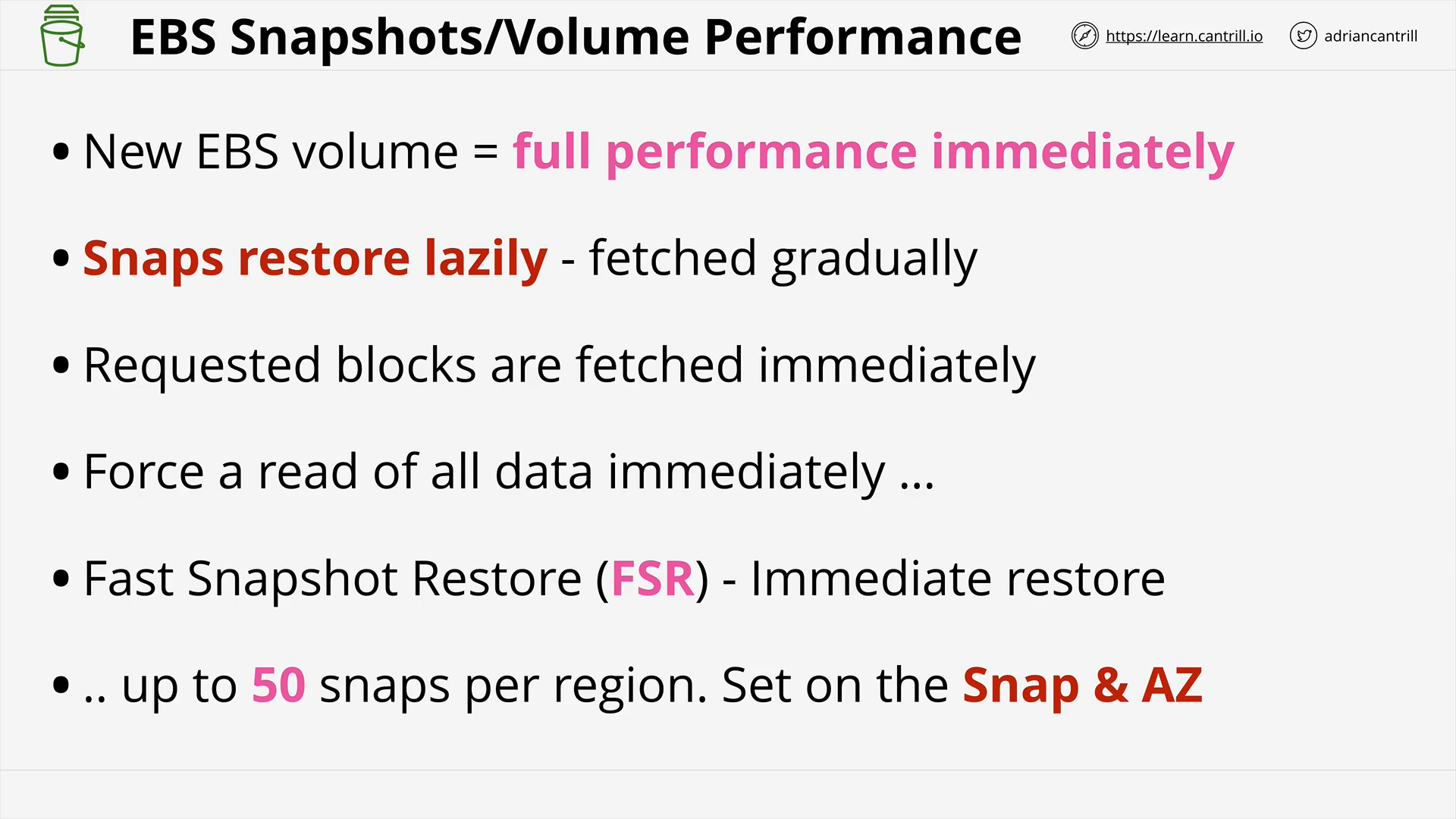 EBS Snapshots - Performance - Fast Snapshot Restore (FSR)
EBS Snapshots - Performance - Fast Snapshot Restore (FSR)
/00_LEARNINGAIDS/EBSSnapshots-2.png) EBS Snapshot - Consumption & Billing
EBS Snapshot - Consumption & Billing
[DEMO] EBS Volumes - PART1 (15:16)
[DEMO] EBS Volumes - PART2 (14:13)
[DEMO] EBS Volumes - PART3 (14:27)
EBS Encryption (8:22)
/00_LEARNINGAIDS/EBSEncryption-1.png) Flow of EBS Encryption
Flow of EBS Encryption
/00_LEARNINGAIDS/EBSEncryption-2.png) Encryption of EBS Snapshot
Encryption of EBS Snapshot
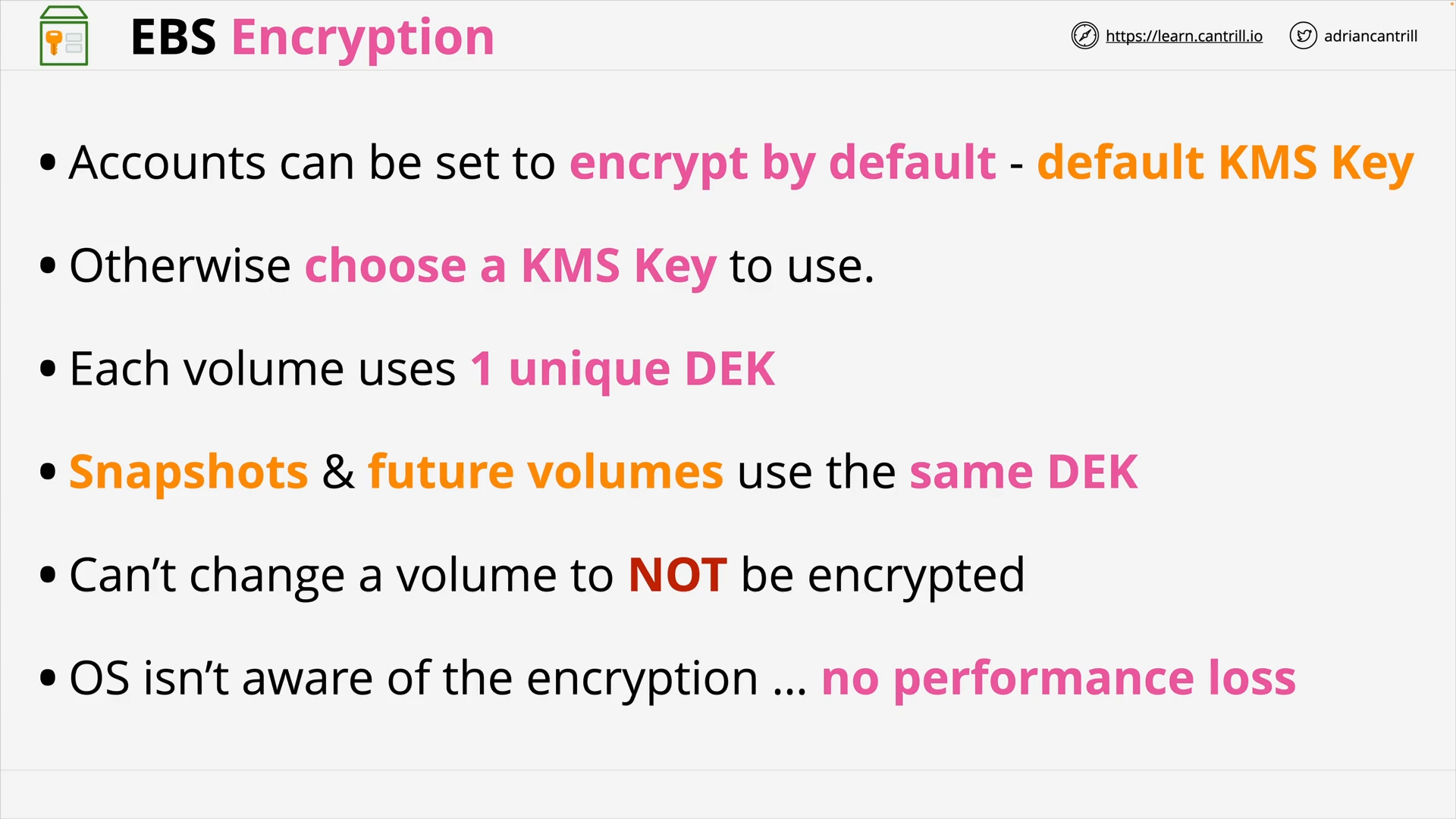 EBS Encryption - Summary
EBS Encryption - Summary
Network Interfaces, Instance IPs and DNS (15:58)
/00_LEARNINGAIDS/EC2networking-1.png) Elastic Network Interface (ENI) & EC2 Network
Elastic Network Interface (ENI) & EC2 Network
/00_LEARNINGAIDS/EC2networking-2.png) EC2 Network & DNS Architecture
EC2 Network & DNS Architecture
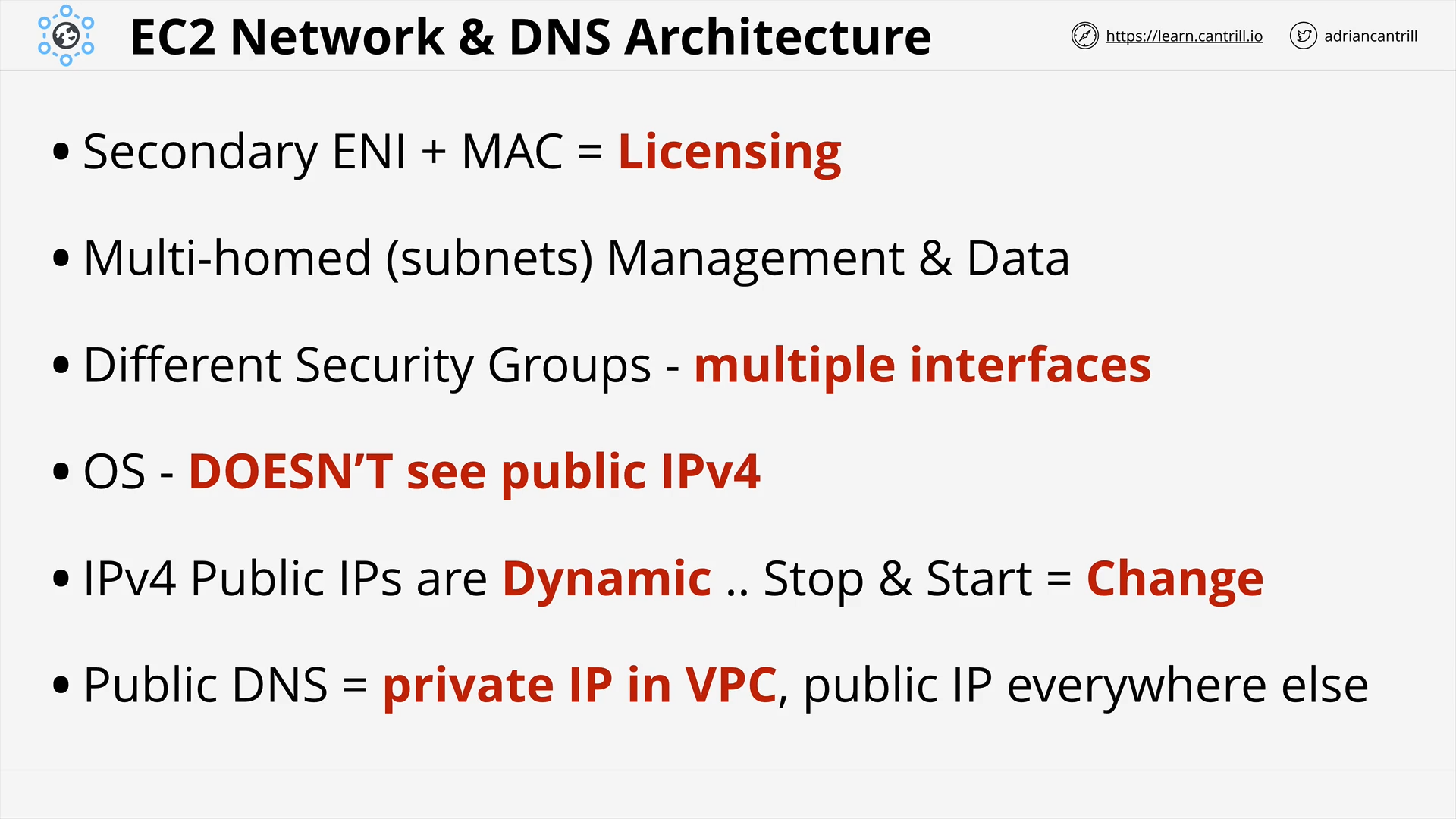 EC2 Network & DNS Architecture - Summary
EC2 Network & DNS Architecture - Summary
[DEMO] Manual Install of Wordpress on EC2 - PART1 (12:27)
[DEMO] Manual Install of Wordpress on EC2 - PART2 (12:36)
Amazon Machine Images (AMI) (13:58)
__lea.png) AMI
AMI
/00_LEARNINGAIDS/AMILifecycle.png) AMI Lifecycle
AMI Lifecycle
__lea.png) AMI - Tips
AMI - Tips
[DEMO] Creating an Animals4life AMI - PART1 (9:38)
[DEMO] Creating an Animals4life AMI - PART2 (10:57)
[DEMO] Copying & Sharing an AMI (8:35)
EC2 Purchase Options - PART1 (9:22)
/00_LEARNINGAIDS/EC2PurchaseOptions-1.png) EC2 Purchase Options - On-Demand
EC2 Purchase Options - On-Demand
/00_LEARNINGAIDS/EC2PurchaseOptions-2.png) EC2 Purchase Options - Spot
EC2 Purchase Options - Spot
EC2 Purchase Options - PART2 (11:56)
/00_LEARNINGAIDS/EC2PurchaseOptions-3.png) EC2 Purchase Options - Reserved
EC2 Purchase Options - Reserved
/00_LEARNINGAIDS/EC2PurchaseOptions-4.png) EC2 Purchase Options - Dedicated Hosts
EC2 Purchase Options - Dedicated Hosts
/00_LEARNINGAIDS/EC2PurchaseOptions-5.png) EC2 Purchase Options - Dedicated Instances
EC2 Purchase Options - Dedicated Instances
Reserved Instances - the rest (11:58)
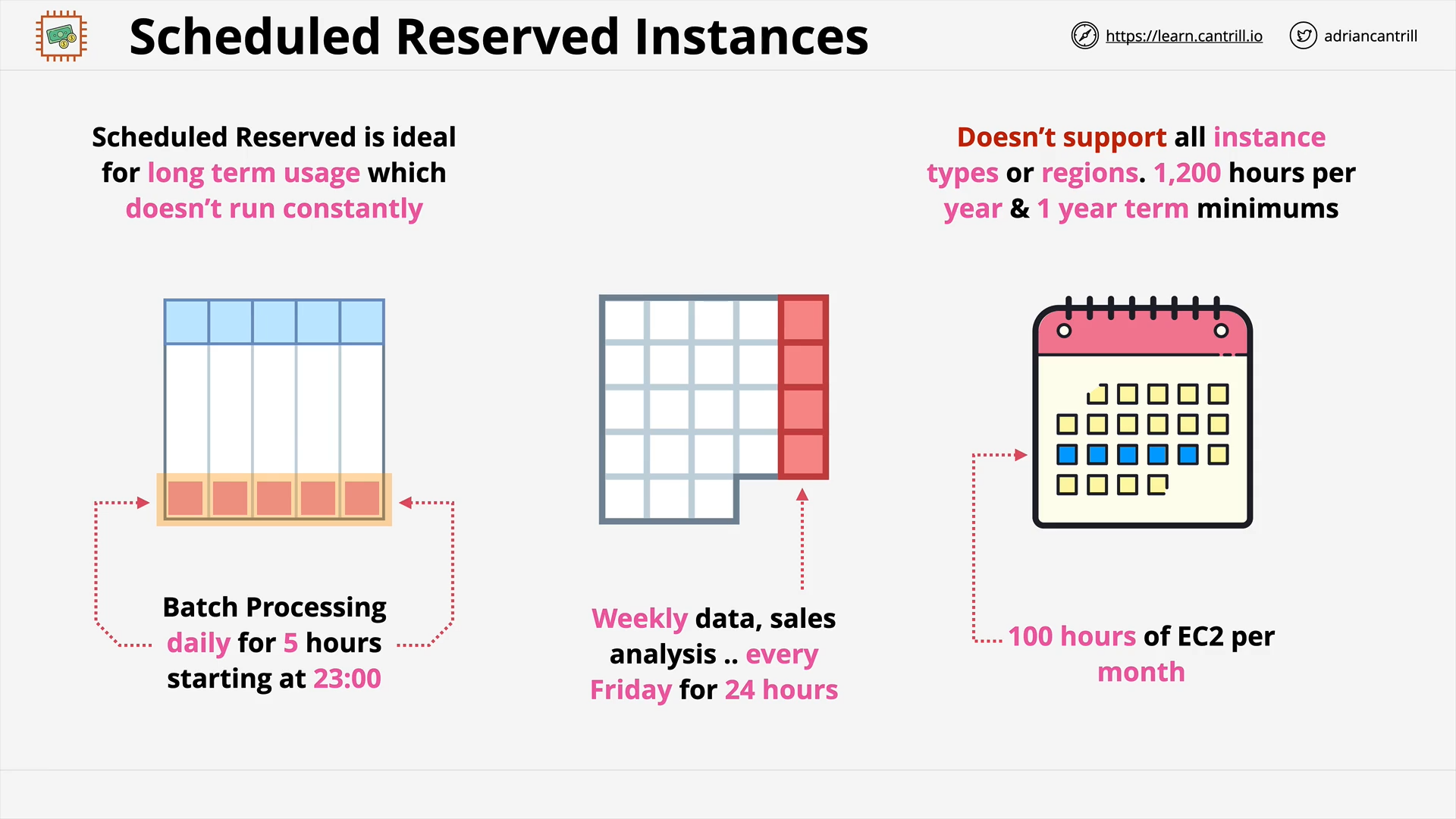 Scheduled Reserved Instances
Scheduled Reserved Instances
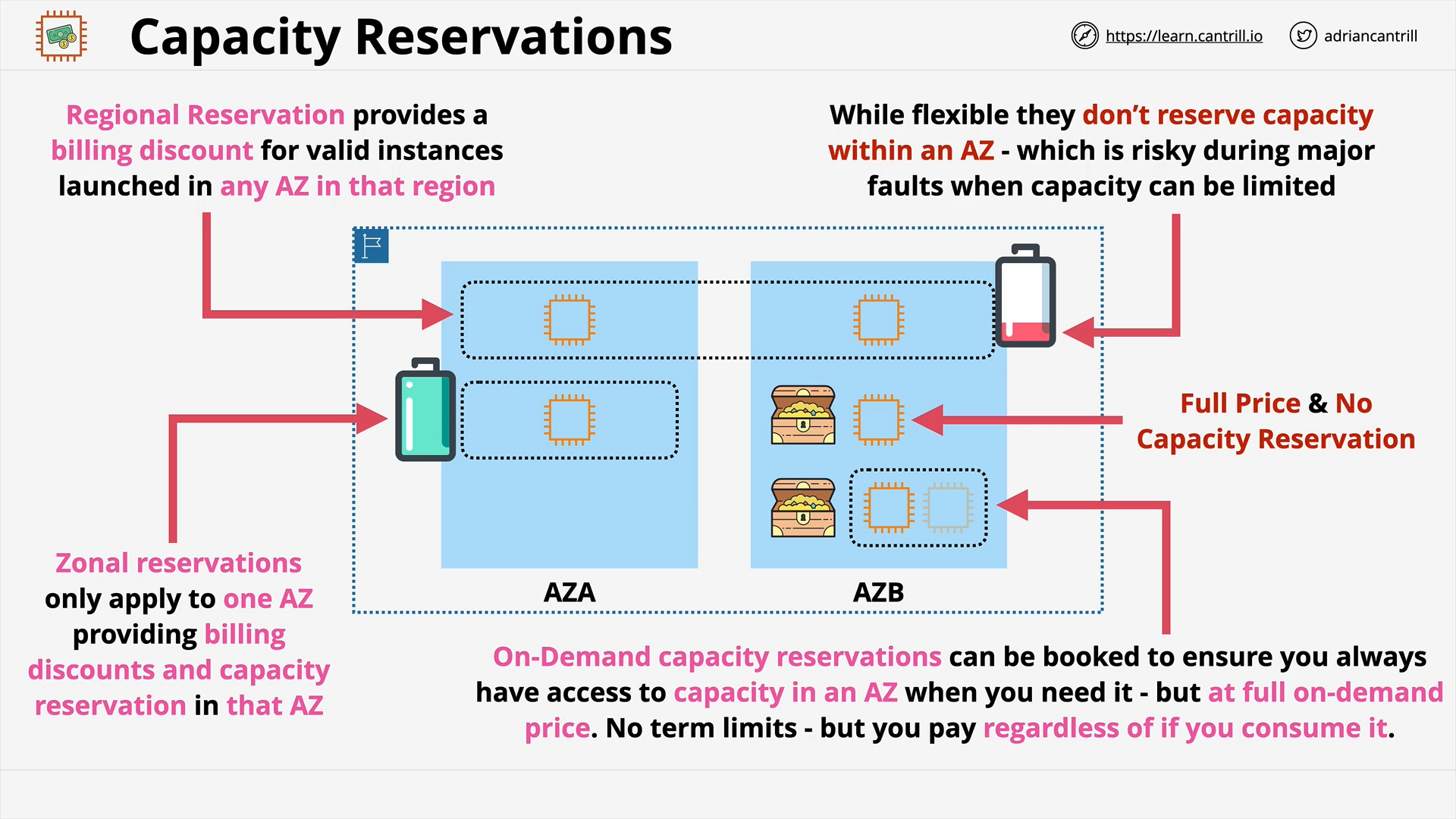 Capacity Reservations
Capacity Reservations
 EC2 Saving Plan
EC2 Saving Plan
Instance Status Checks & Auto Recovery (7:42)
/00_LEARNINGAIDS/InstanceStatusChecks.png) Instance Status Checks & Auto Recovery
Instance Status Checks & Auto Recovery
[DEMO] Shutdown, Terminate & Termination Protection (5:40)
Horizontal & Vertical Scaling (11:23)
/00_LEARNINGAIDS/EC2Scaling-1.png)
/00_LEARNINGAIDS/EC2Scaling-2.png)
/00_LEARNINGAIDS/EC2Scaling-3.png)
Instance Metadata [THEORY & DEMO] (15:46)
/00_LEARNINGAIDS/EC2InstanceMetadata.png)
EC2 Basics Section Quiz
EBS Volume Types
SSD-based
| Volume Type | gp2 | gp3 | io1 | io2 | io2 Block Express ‡ |
|---|---|---|---|---|---|
| Durability | 99.8% - 99.9% durability | - | 99.8% - 99.9% durability | 99.999% durability | - |
| (0.1% - 0.2% annual failure rate) | - | (0.1% - 0.2% annual failure rate) | (0.001% annual failure rate) | - | |
| Use Cases | Transactional workloads | - | Workloads that require | - | Workloads that require |
| Virtual desktops | - | - | - Sub-millisecond latency | ||
| Medium-sized, single-instance databases, | - | - sustained IOPS performance | - | - Sustained IOPS performance | |
| Low-latency interactive applications | - | - more than 16,000 IOPS | - | - More than 64,000 IOPS or 1,000 MiB/s of throughput | |
| Boot volumes | - | I/O-intensive database workloads | - | ||
| Development and test environments | - | - | |||
| Volume Size | 1 GiB - 16 TiB | - | 4 GiB - 16 TiB | - | 4 GiB - 64 TiB |
| Max IOPS per Volume (16KB IO) | 16,000 | 64,000 † | - | 256,000 | |
| Max Throughput per Volume | Up to 250 MiB/s | 1,000 MiB/s | 1,000 MiB/s † | - | 4,000 MiB/s |
| Amazon EBS Multi-attach | Not supported | - | Supported | - | - |
| Max IOPS per Instance | Not supported | - | 350,000 | 160,000 | 350.000 |
| Max Throughput per Instance | Not supported | - | 10,000 MB/s | 4,750 MB/s | 10,000 MB/s |
| Boot Volume | Supported | - | - | - | - |
gp3 volume performance
gp3 IOPS performance
- Baseline IOPS: 3,000 IOPS
- Additional IOPS cost: 500 IOPS / GiB of volume size
- Maximum IOPS can be provisioned for volumes 32 GiB or larger (500 IOPS per GiB × 32 GiB = 16,000 IOPS).
gp3 throughput performance
- Baseline throughput: 125 MiB/s
- Additional throughput cost: 0.25 MiB/s per provisioned IOPS
- Maximum throughput can be provisioned at 4,000 IOPS or higher and 8 GiB or larger (4,000 IOPS × 0.25 MiB/s per IOPS = 1,000 MiB/s).
| gp3 Volume Size | 1GiB | … | 8GiB | …. | 32GiB | … | 16TiB |
|---|---|---|---|---|---|---|---|
| (Min Volume Size) | (Max Volume Size ) | ||||||
| IOPS performance | Baseline IOPS (3,000 IOPS) | Max IOPS (16,000 IOPS) | |||||
| Throughput performance | Baseline Throughput (125 MiB/s) | Max Throughput (1,000 MiB/s) | Max Throughput (1,000 MiB/s) |
gp3 pricing
- gp3 volume instance with min spec:
3,000 iops / 1 GB = 3,000.00 IOPS to GB ratio (gp3)
125 MBps / 3,000 iops = 0.04 IOPS to Throughput ratio
1 volumes x 730 instance hours = 730.00 total instance hours
730.00 instance hours / 730 hours in a month = 1.00 instance months
1 GB x 1.00 instance months x 0.08 USD = 0.08 USD (EBS Storage Cost)
EBS Storage Cost: 0.08 USD
3,000 iops - 3000 GP3 iops free = 0.00 billable gp3 iops
EBS IOPS Cost: 0.00 USD
125 MBps - 125 GP3 MBps free = 0.00 billable MBps
EBS Snapshot Cost: 0 USD
Amazon Elastic Block Storage (EBS) total cost (monthly): 0.08 USD
- gp3 volume instance with 32GB volume size and no provisional IOPS, throughput
3,000 iops / 32 GB = 93.75 IOPS to GB ratio (gp3)
125 MBps / 3,000 iops = 0.04 IOPS to Throughput ratio
1 volumes x 730 instance hours = 730.00 total instance hours
730.00 instance hours / 730 hours in a month = 1.00 instance months
32 GB x 1.00 instance months x 0.08 USD = 2.56 USD (EBS Storage Cost)
EBS Storage Cost: 2.56 USD
3,000 iops - 3000 GP3 iops free = 0.00 billable gp3 iops
EBS IOPS Cost: 0.00 USD
125 MBps - 125 GP3 MBps free = 0.00 billable MBps
EBS Snapshot Cost: 0 USD
Amazon Elastic Block Storage (EBS) total cost (monthly): 2.56 USD
- gp3 volume instance with max spec:
16,000 iops / 32 GB = 500.00 IOPS to GB ratio (gp3)
1,000 MBps / 16,000 iops = 0.06 IOPS to Throughput ratio
1 volumes x 730 instance hours = 730.00 total instance hours
730.00 instance hours / 730 hours in a month = 1.00 instance months
32 GB x 1.00 instance months x 0.08 USD = 2.56 USD (EBS Storage Cost)
EBS Storage Cost: 2.56 USD
16,000 iops - 3000 GP3 iops free = 13,000.00 billable gp3 iops
Max (13000.00 iops, 0 minimum billable iops) = 13,000.00 total billable gp3 iops
13,000.00 iops x 1.00 instance months x 0.005 USD = 65.00 USD (EBS IOPS gp3 Cost)
EBS IOPS Cost: 65.00 USD
1,000 MBps - 125 GP3 MBps free = 875.00 billable MBps
Max (875.00 MBps, 0 minimum mbps) = 875.00 billable throughput (MBps)
875.00 MBps / 1024 MB per GB = 0.8545 billable throughput (GBps)
0.8545 GBps x 1.00 instance months x 40.96 USD = 35.00 USD (EBS gp3 throughput Cost)
EBS Snapshot Cost: 0 USD
2.56 USD + 65.00 USD + 35.00 USD = 102.56 USD (Total EBS cost)
Amazon Elastic Block Storage (EBS) total cost (monthly): 102.56 USD
HDD-based
| Volume Type | st1 | sc1 |
|---|---|---|
| Durability | 99.8% - 99.9% durability | - |
| (0.1% - 0.2% annual failure rate) | - | |
| Use Cases | ||
| - Big data | - Throughput-oriented storage for data that is infrequently accessed | |
| - Data warehouses | - Scenarios where the lowest storage cost is important | |
| - Log processing | ||
| Volume Size | 125 GiB - 16 TiB | - |
| Max IOPS per volume (1 MiB I/O) | 500 | 250 |
| Max Throughput per volume | 500 MiB/s | 250 MiB/s |
| Baseline throughput | 40 MiB/s per TiB (Base) | 12 MiB/s per TiB (Base) |
| 250 MiB/s per TiB (Burst) | 80 MiB/s per TiB (Burst) | |
| Amazon EBS Multi-attach | Not supported | Not supported |
| Boot volume | Not supported | Not supported |
AWS EC2 Instance Lifecycle
| Instance state | Description | Instance usage billing |
|---|---|---|
| pending | The instance is preparing to enter the running state. An instance enters the pending state when it is launched or when it is started after being in the stopped state. | Not billed |
| running | The instance is running and ready for use. | Billed |
| stopping | The instance is preparing to be stopped. | Not billed |
| stopped | The instance is shut down and cannot be used. The instance can be started at any time. | Not billed |
| shutting-down | The instance is preparing to be terminated. | Not billed |
| terminated | The instance has been permanently deleted and cannot be started. | Not billed |
CONTAINERS & ECS
Introduction to Containers (17:13)
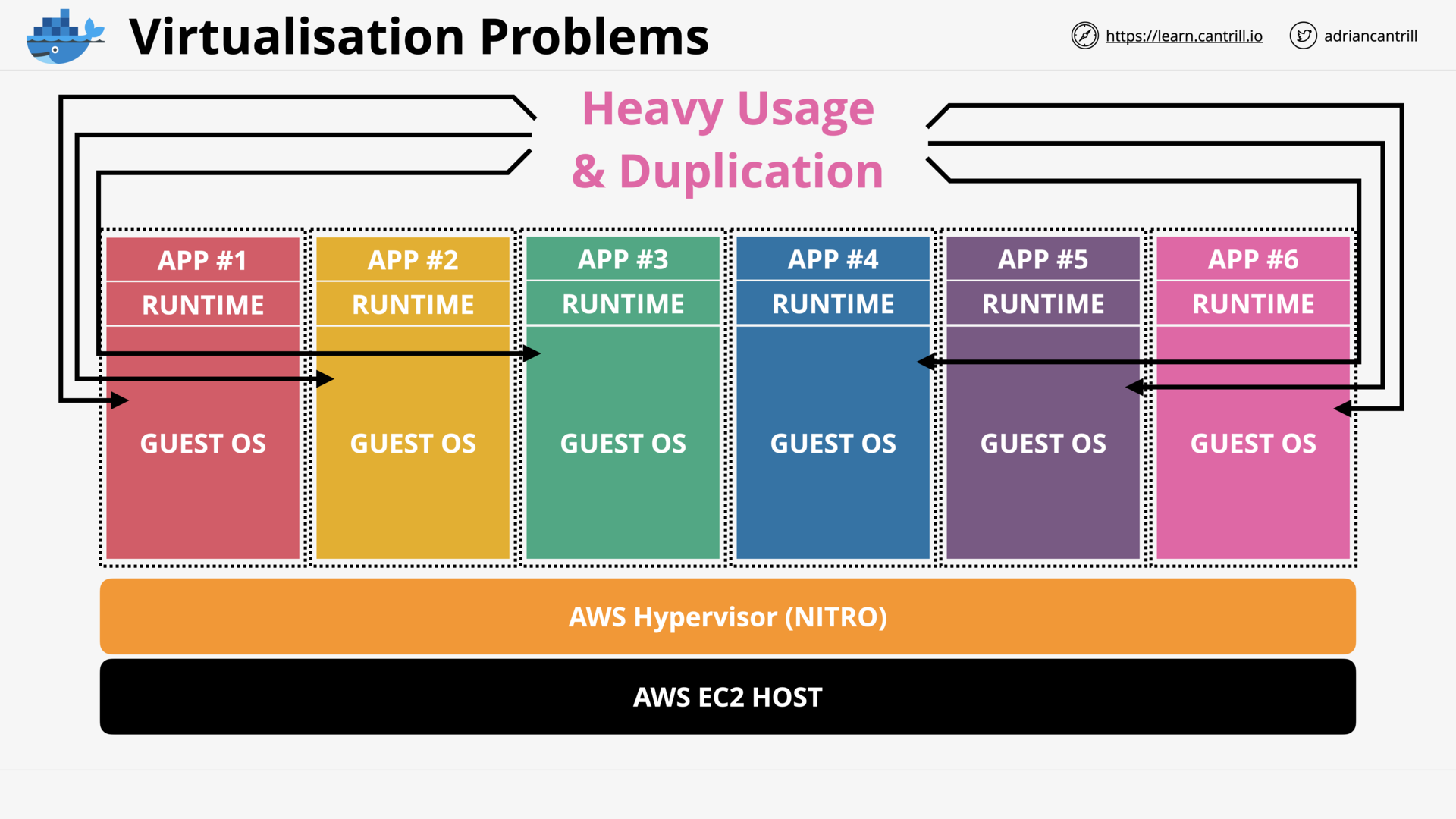 Virtualization Problems
Virtualization Problems
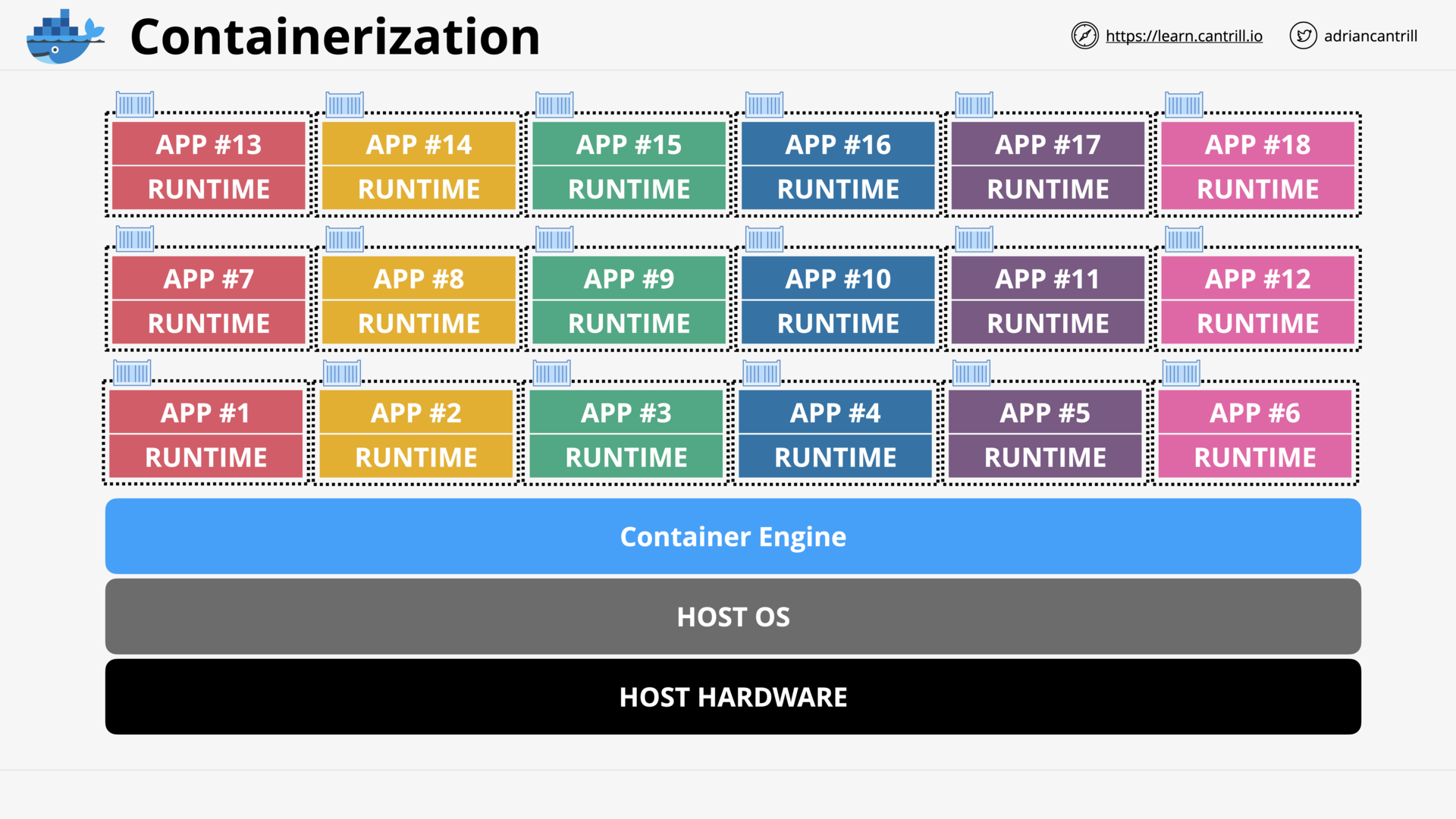 Containerization
Containerization
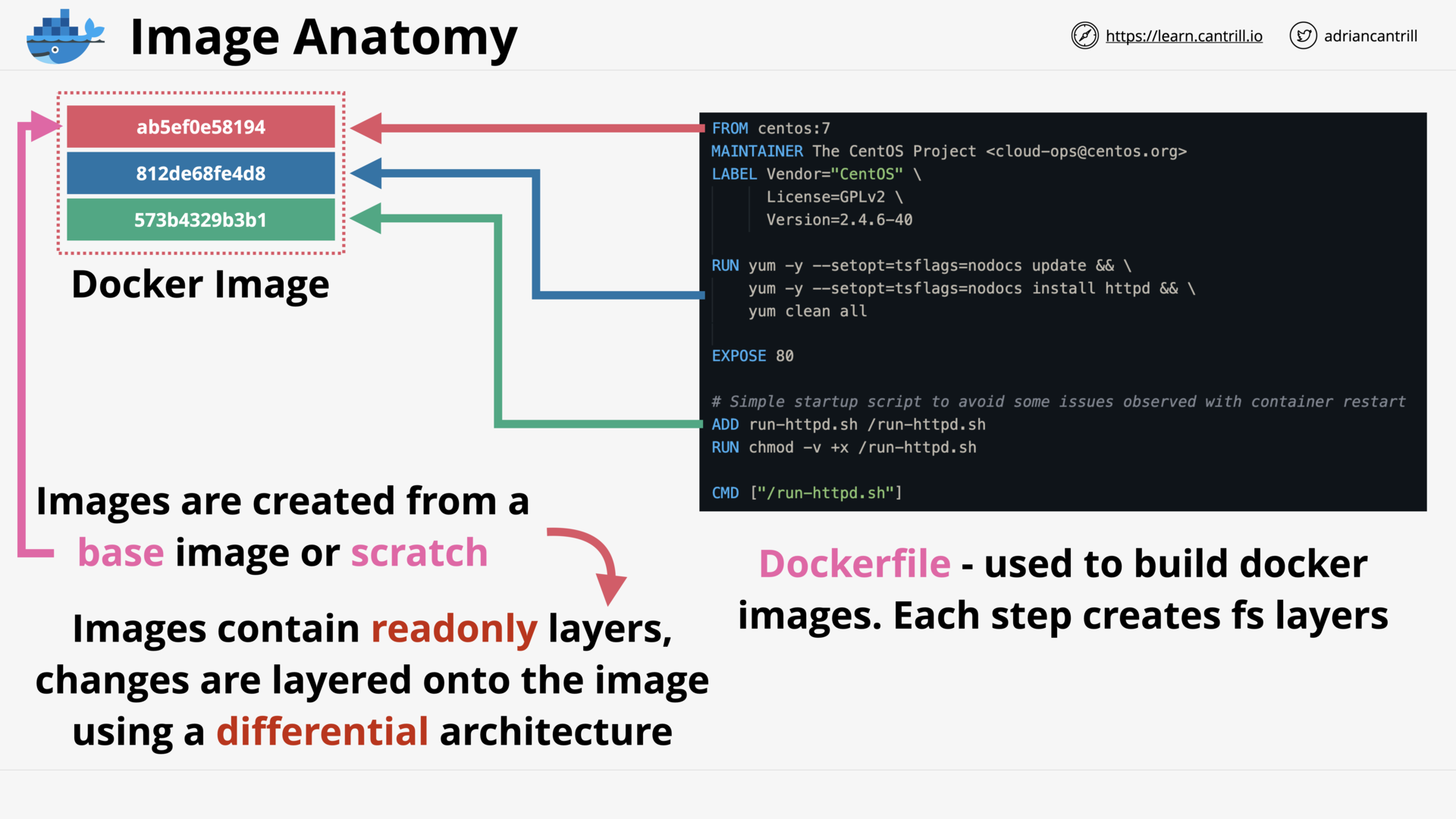 Image Anatomy
Image Anatomy
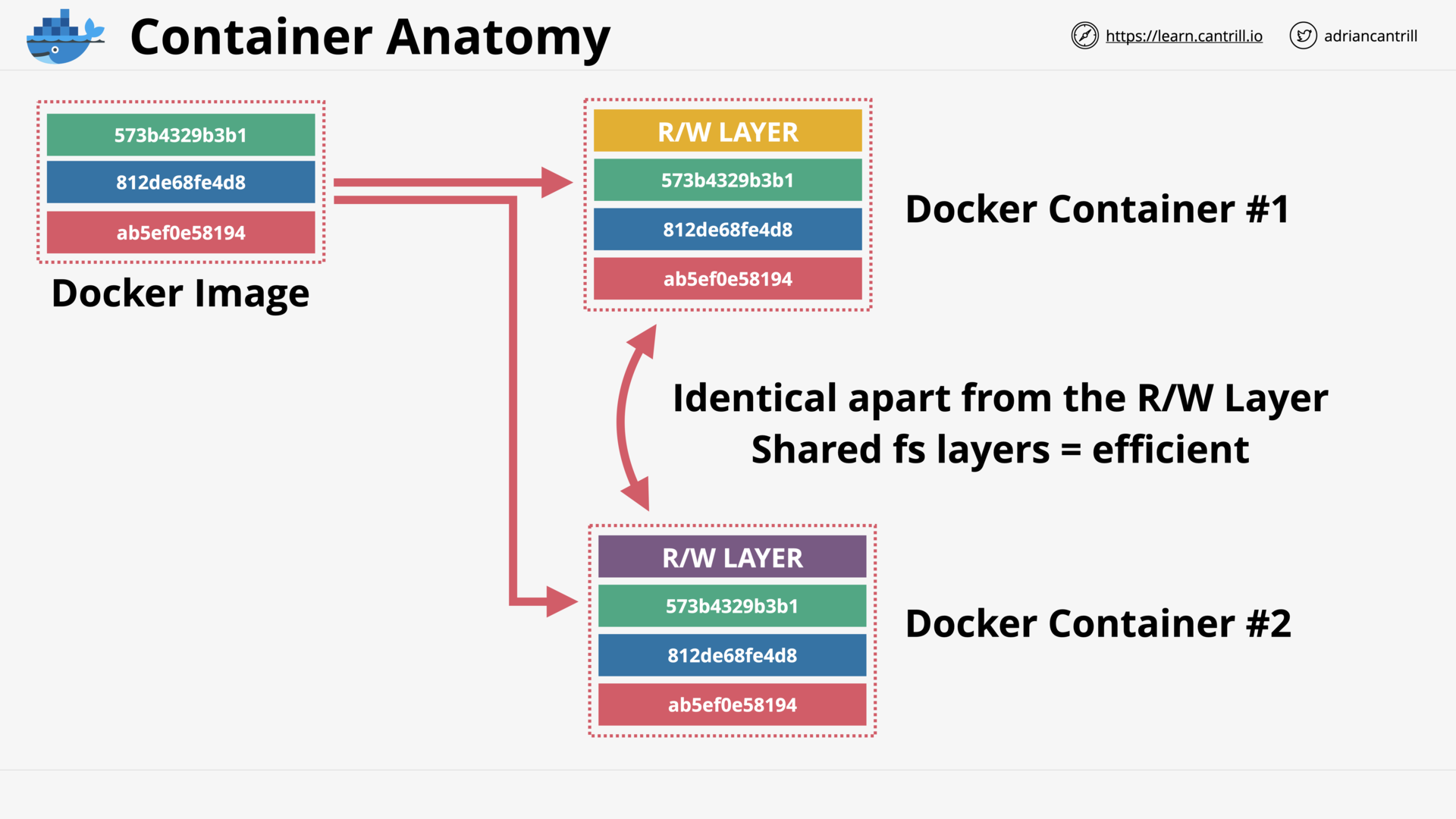 Container Anatomy
Container Anatomy
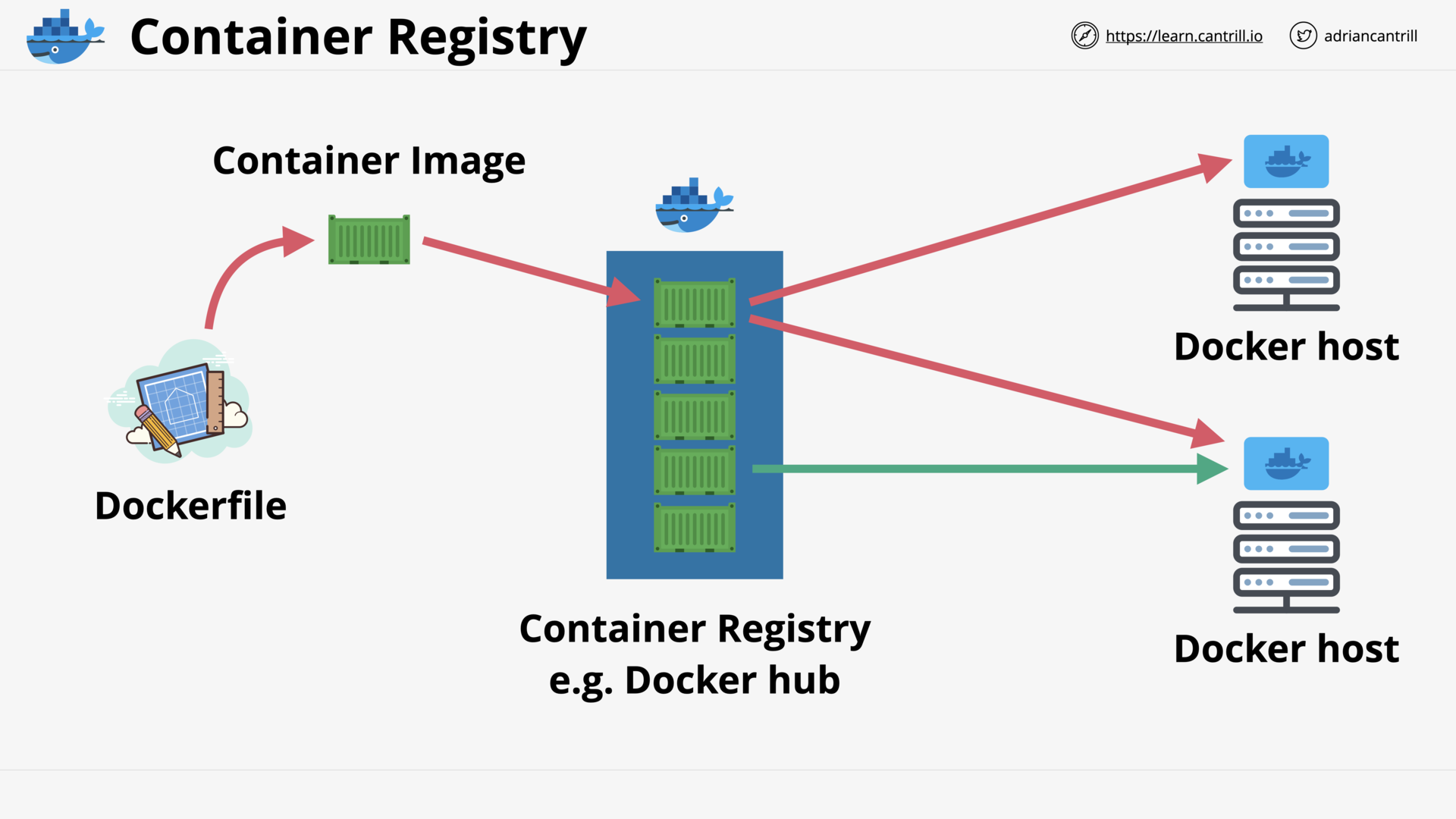 Container Registry
Container Registry
 Container Key Concepts
Container Key Concepts
[DEMO] Creating ‘container of cats’ Docker Image (18:15)
ECS - Concepts (10:25)
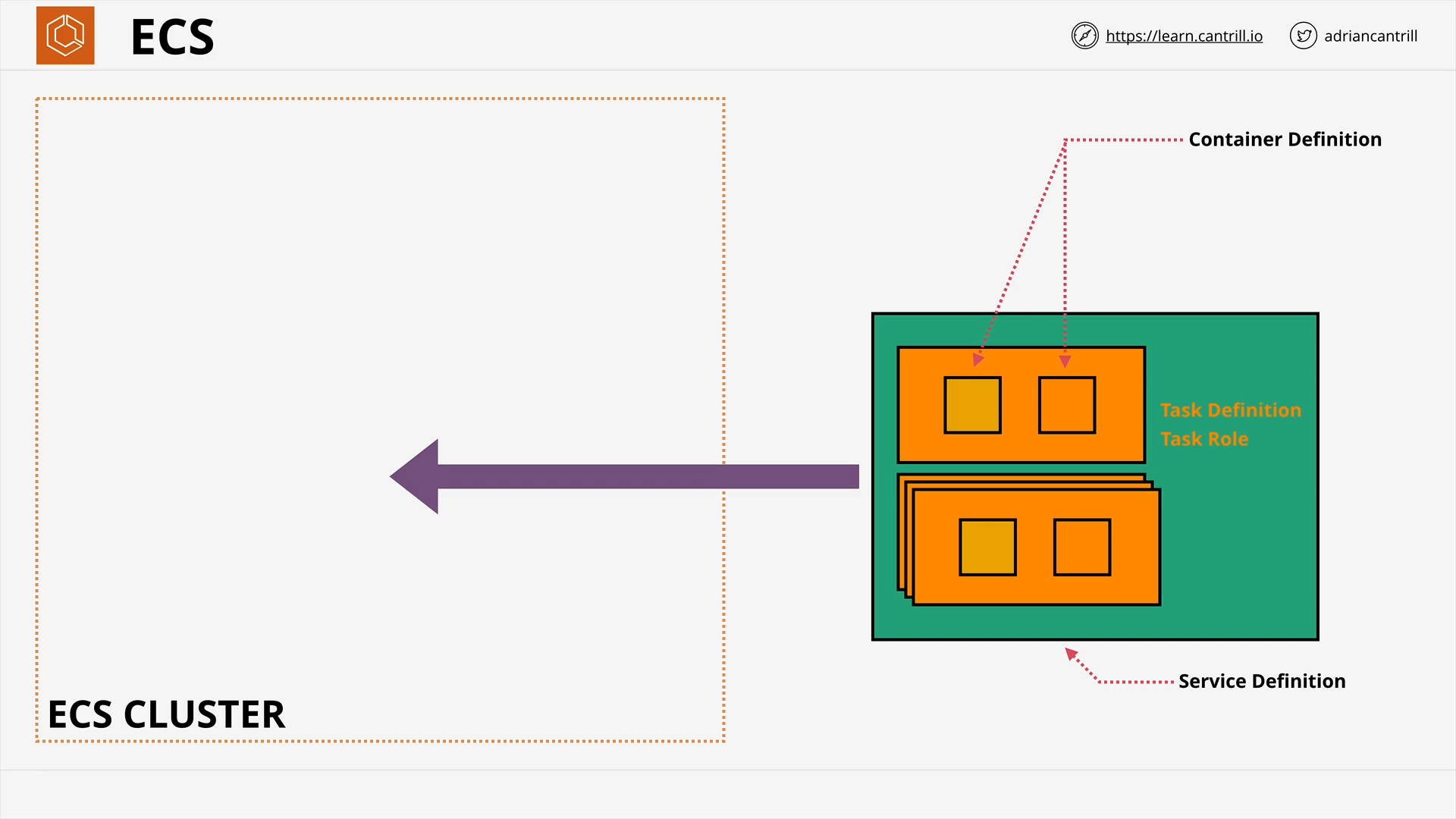
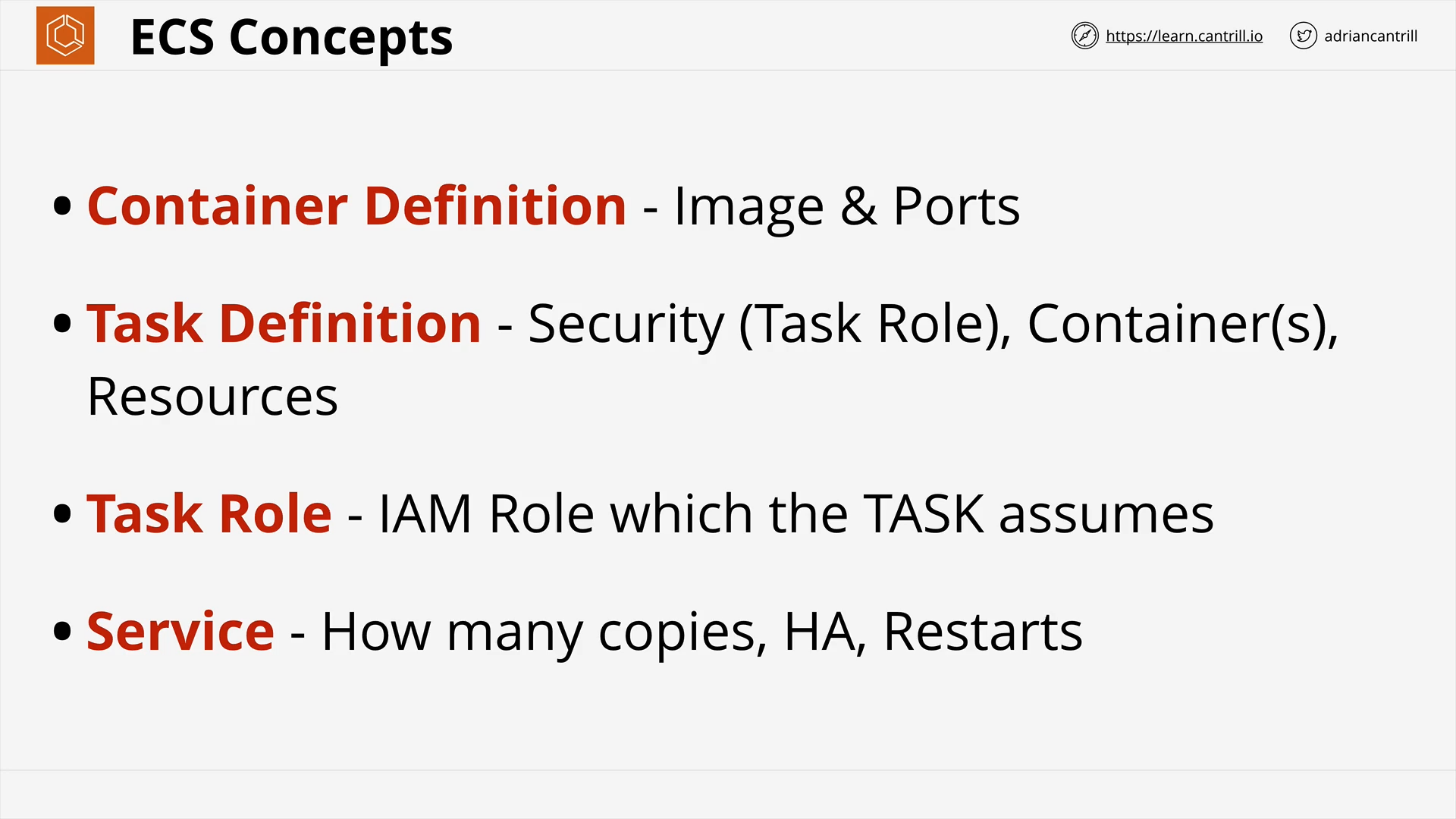
ECS - Cluster Mode (13:09)
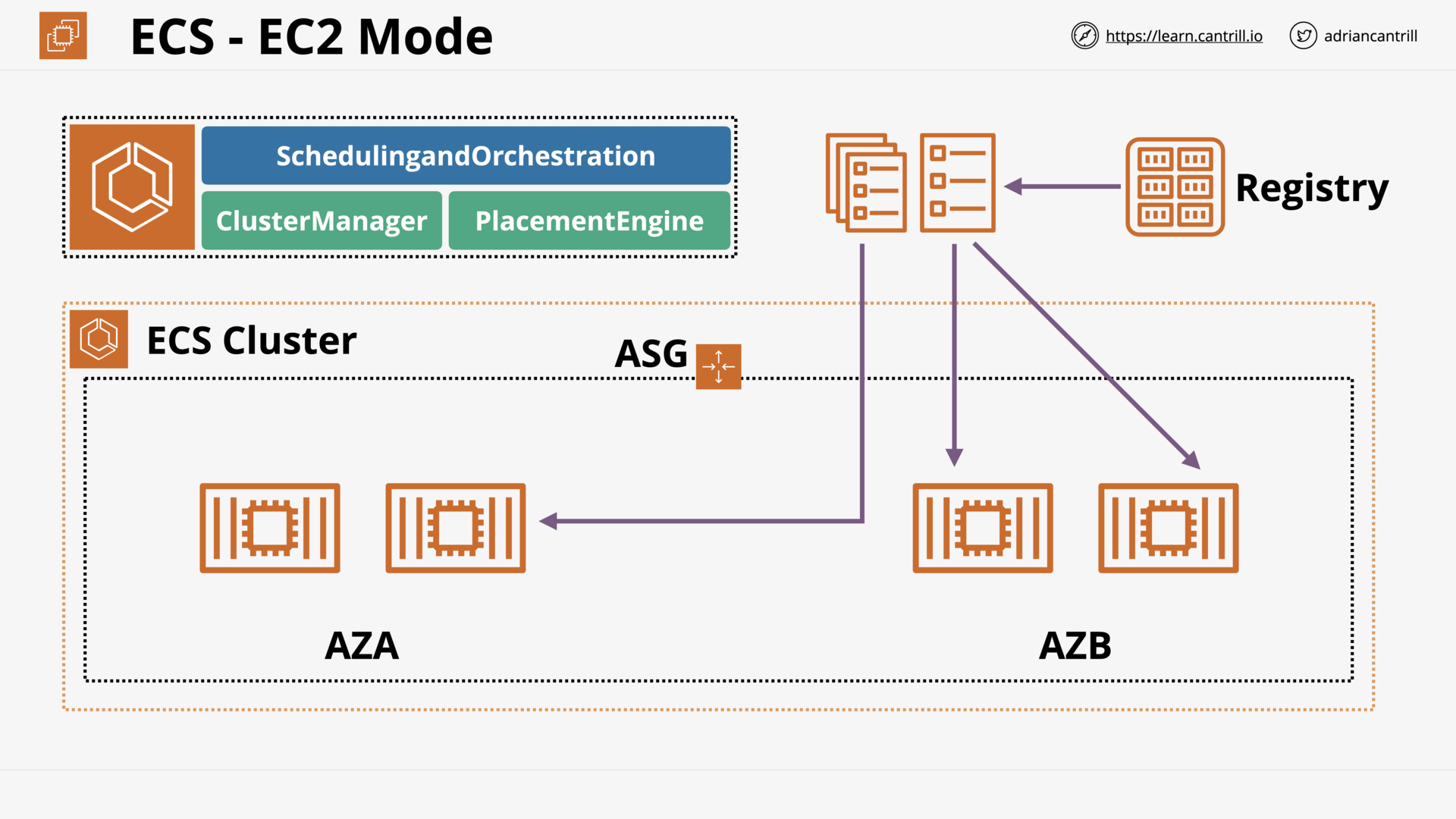 ECS - EC2 Mode
ECS - EC2 Mode
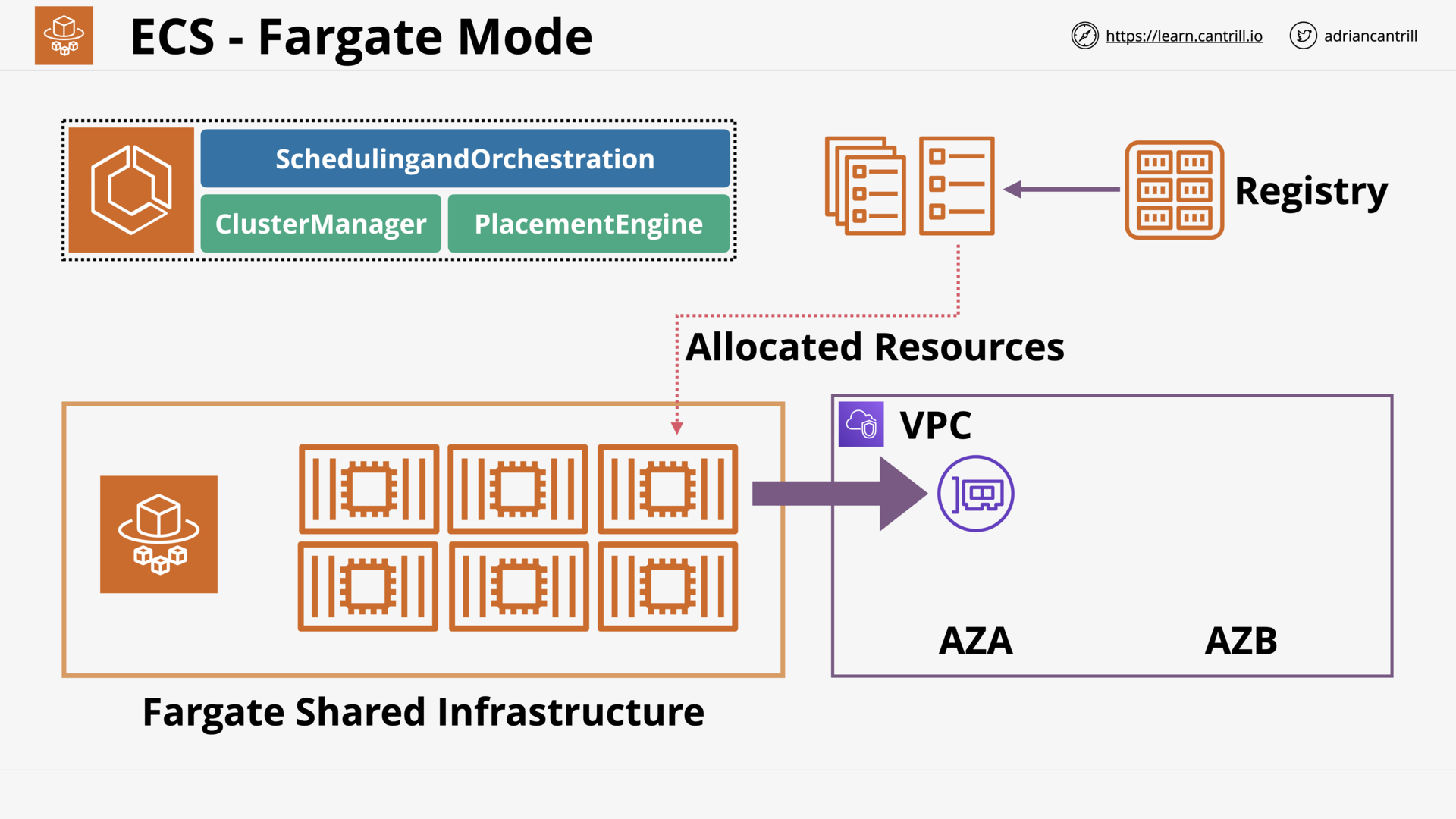 ECS - Fargate Mode
ECS - Fargate Mode
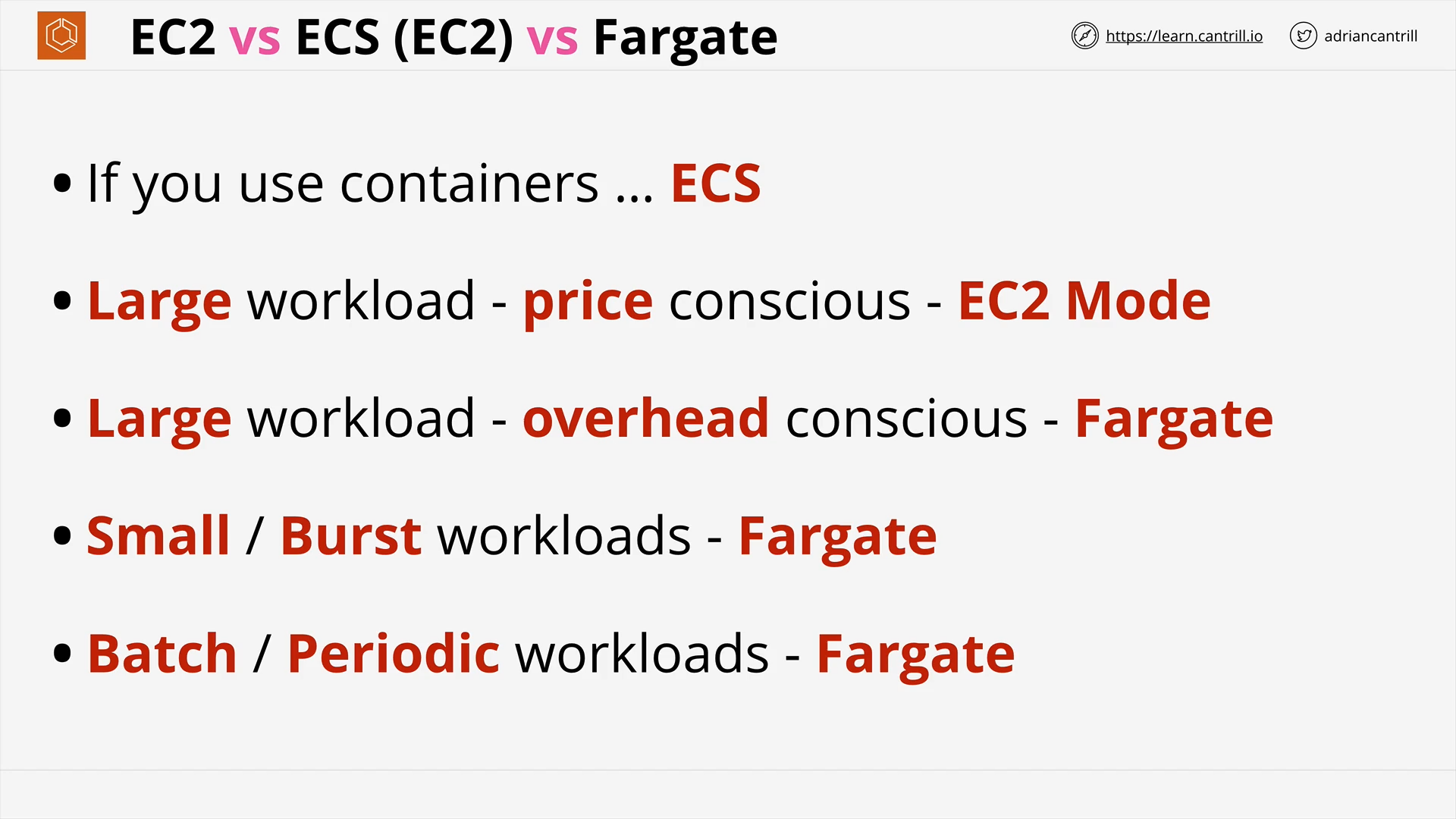 EC2 - ECS (EC2) - ECS (Fargate)
EC2 - ECS (EC2) - ECS (Fargate)
[DEMO] - Deploying ‘container of cats’ using Fargate (13:13)
Elastic Container Registry (ECR) (4:14)
__lea_%E2%80%94_Firefox_De.png) ECR - Public/Private Registry - Repo - Image - Tag
ECR - Public/Private Registry - Repo - Image - Tag
__lea_%E2%80%94_Firefox_De.png) ECR is integrated with many AWS services
ECR is integrated with many AWS services
Kubernetes 101 (11:27)
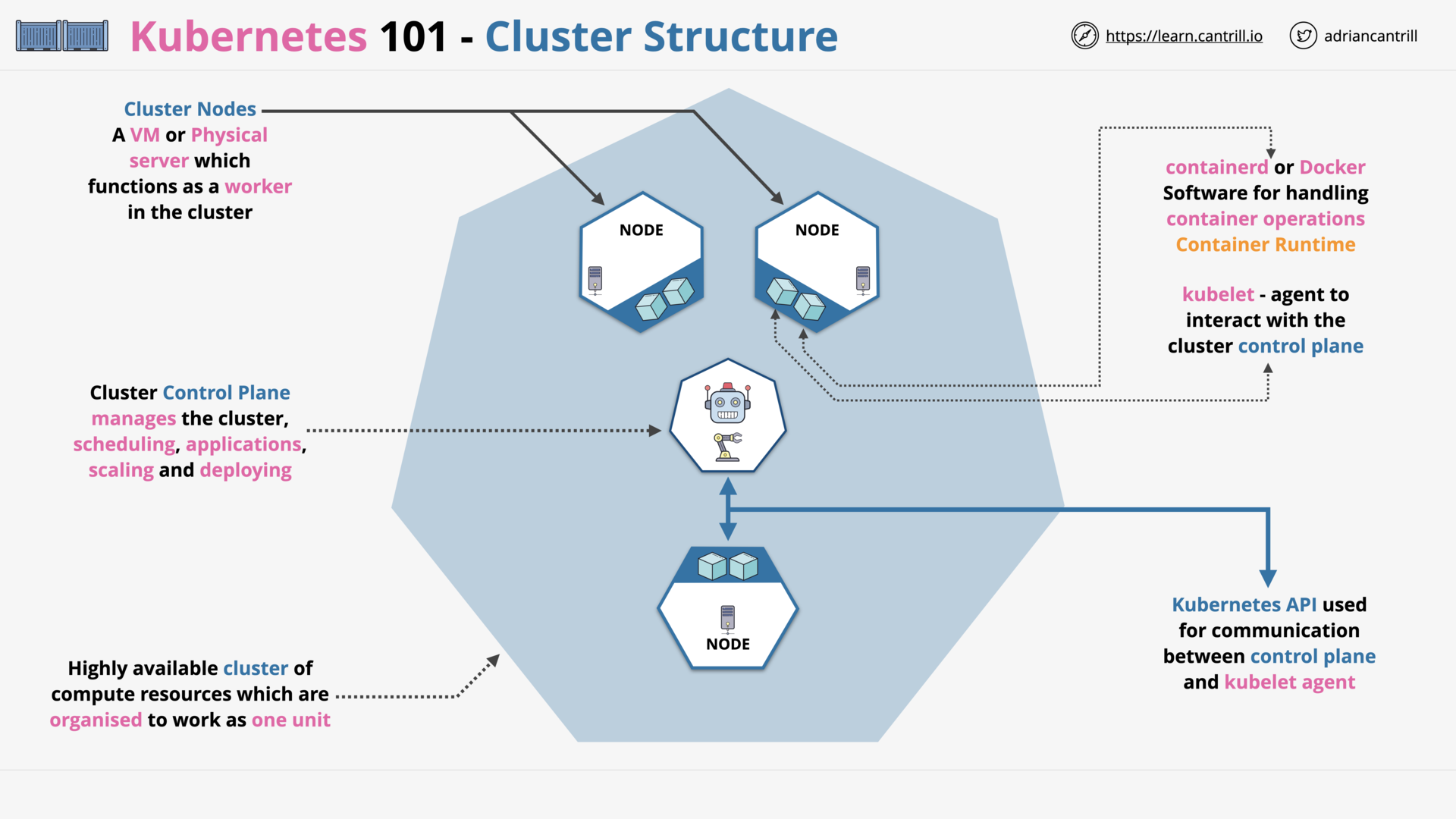 K8s - Cluster - Control Plane - Worker Nodes
K8s - Cluster - Control Plane - Worker Nodes
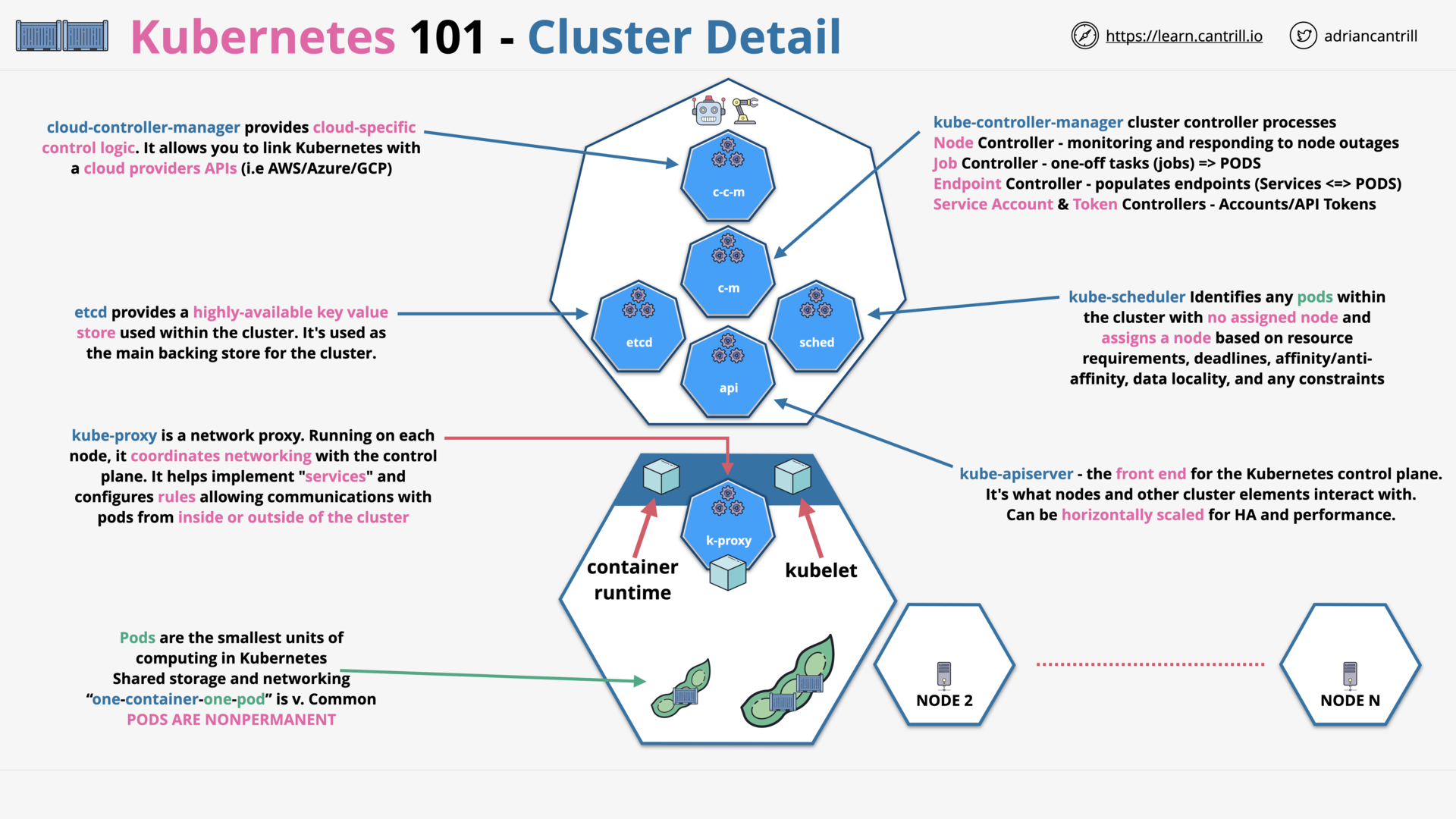 K8s - Architecture
K8s - Architecture
 K8s - Summary
K8s - Summary
Elastic Kubernetes Service (EKS) 101 (6:14)
_101__.png) EKS - AWS managed K8s
EKS - AWS managed K8s
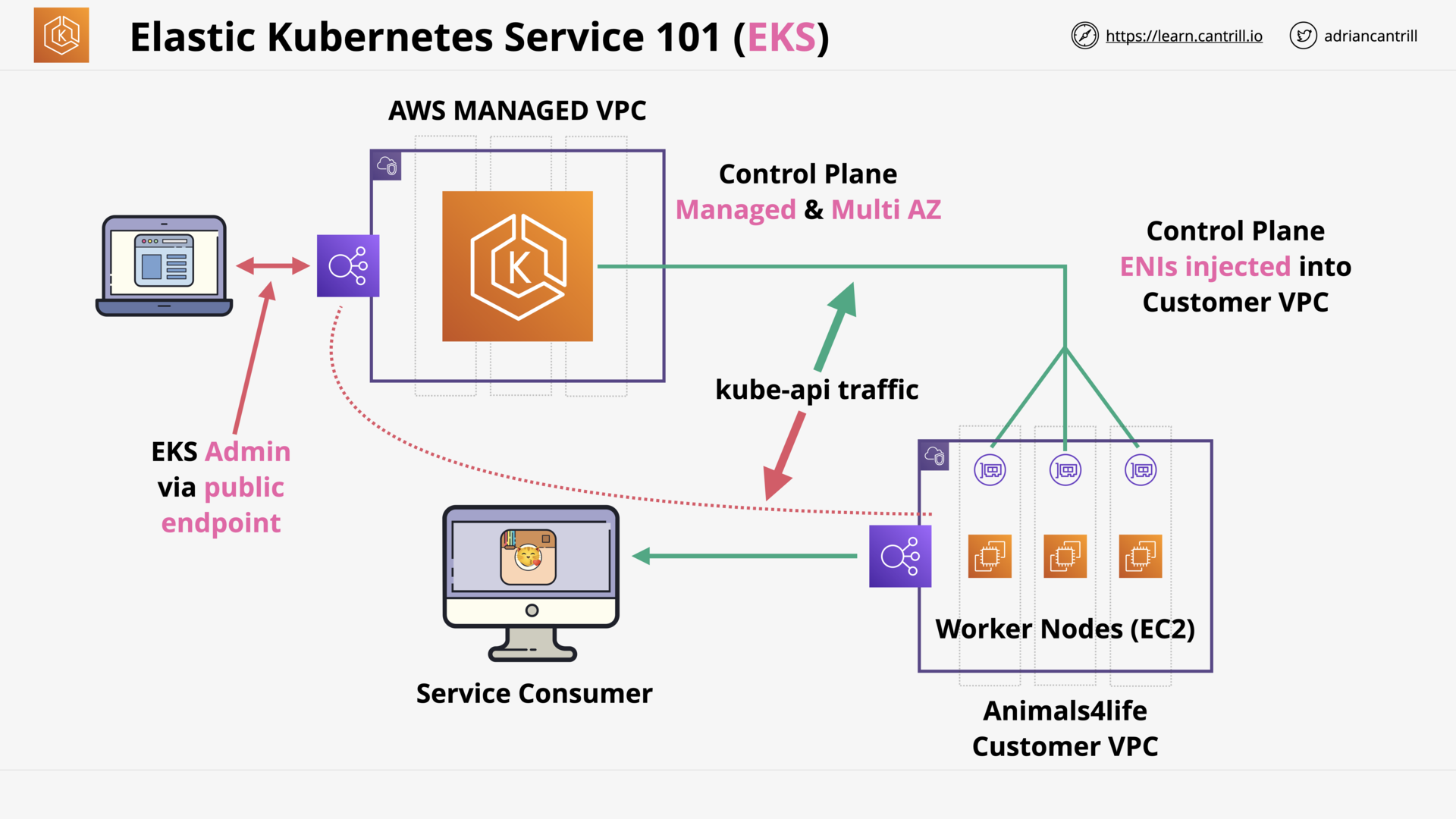 EKS - Architecture
EKS - Architecture
Containers Section Quiz
ADVANCED EC2
Bootstrapping EC2 using User Data (10:25)
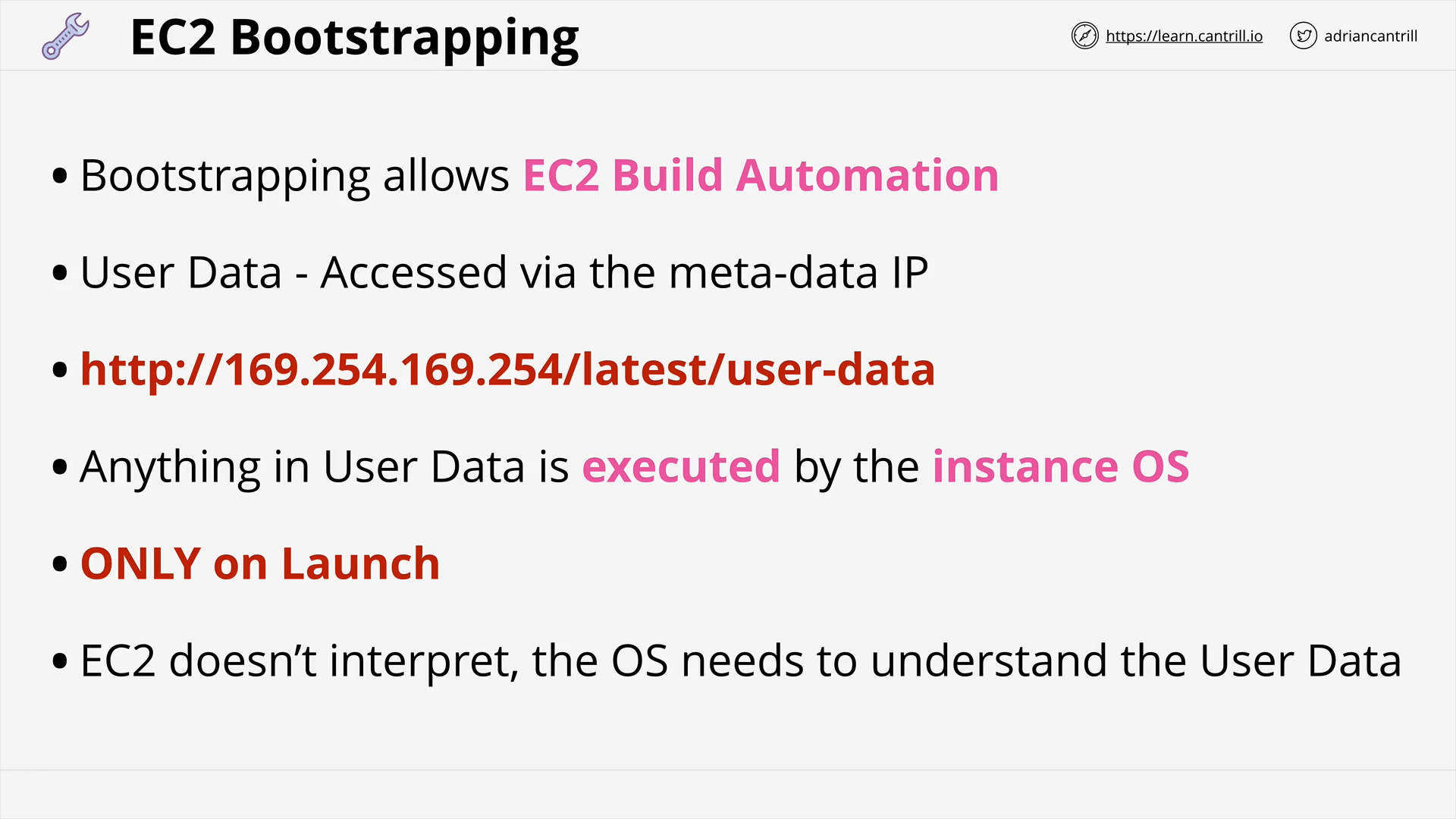 EC2 User Data
EC2 User Data
what is ec2 bootstrapping?
The process of configuring an EC2 instance to perform automated install & configuration steps ‘post launch’ before an instance is brought into service.
how to bootstrap an ec2 instance?
what is ec2 user data?
when does ec2 execute user data?
what exactly execute ec2 user data?
how many times does the ec2 user data be executed?
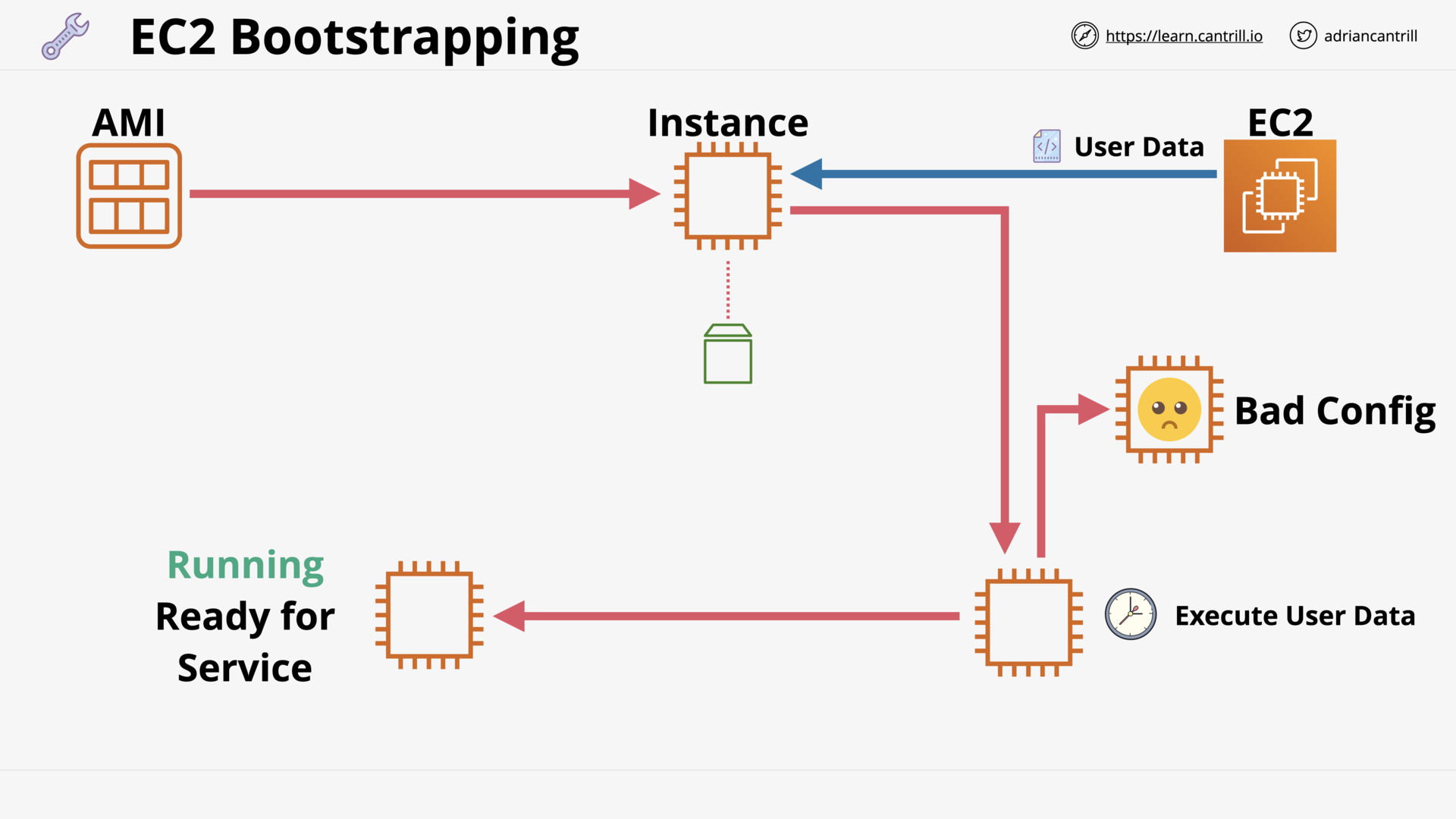 EC2 Bootstrapping
EC2 Bootstrapping
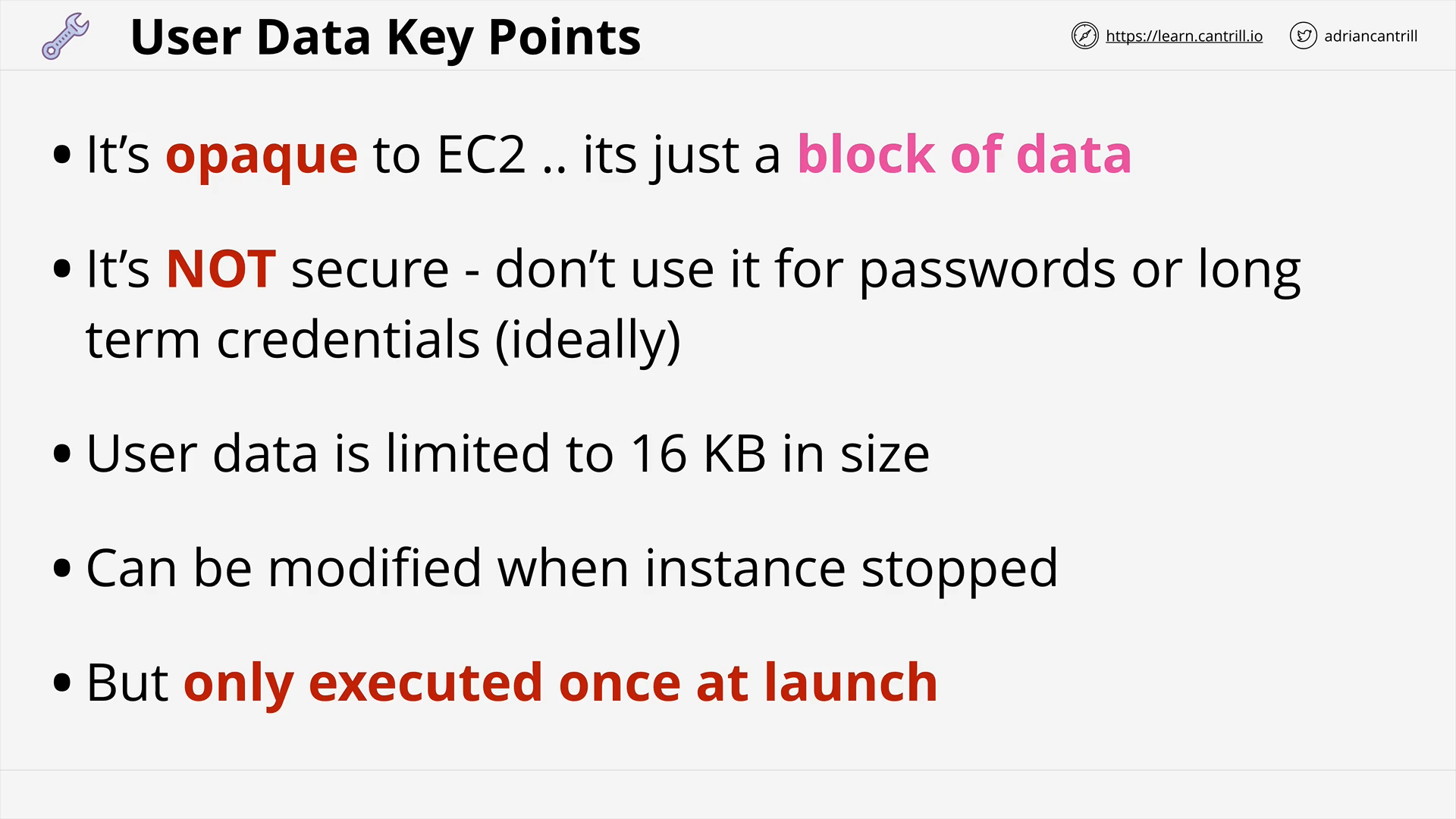 User Data - Key Points
User Data - Key Points
what are drawbacks of ec2 user data?
- It’s opaque to EC2.
- NOT secure.
- Limited to 16KB.
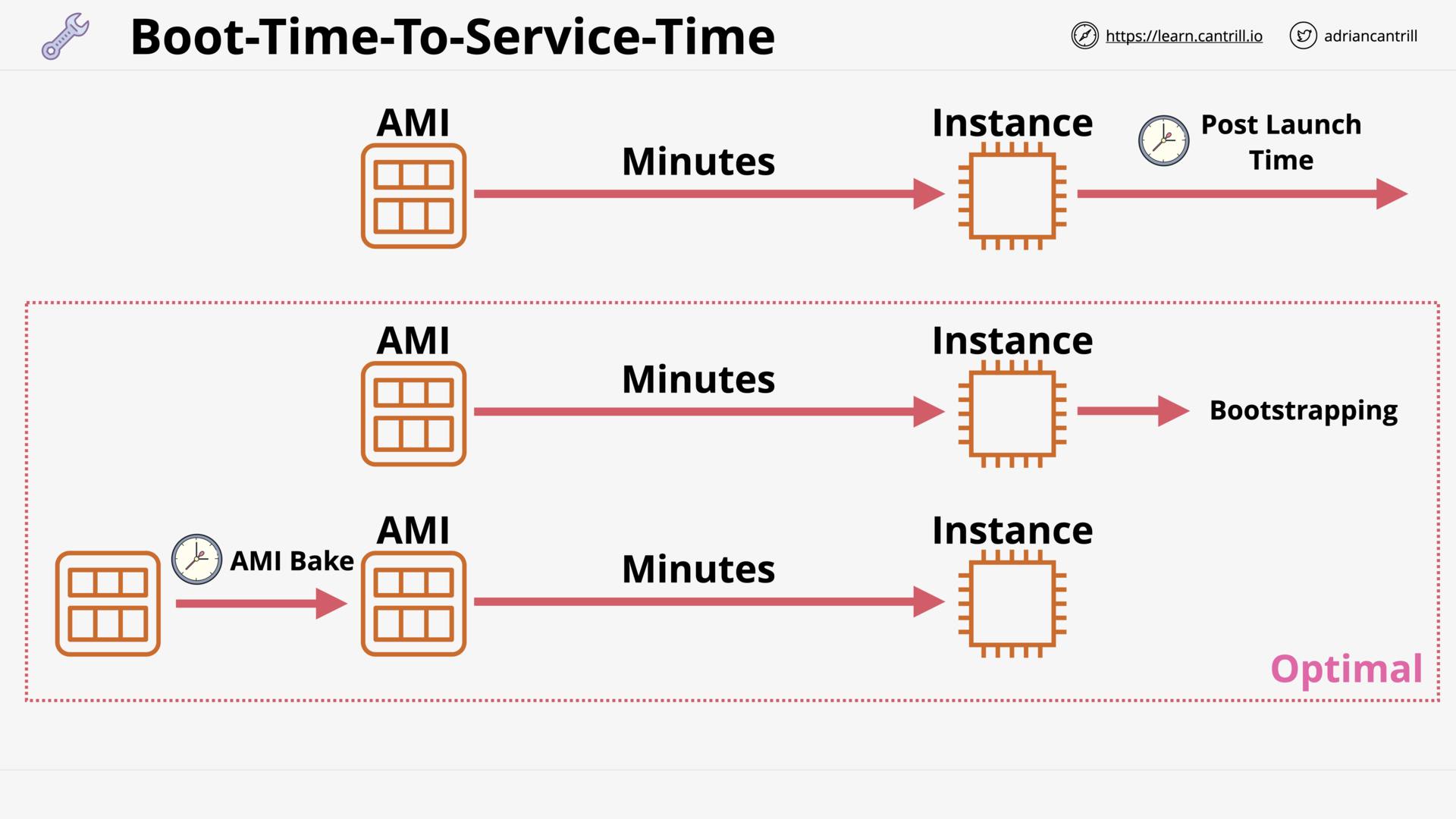 Boot-Time-To-Service-Time
Boot-Time-To-Service-Time
[DEMO] Bootstrapping Wordpress Installation - PART1 (15:00)
[DEMO] Bootstrapping Wordpress Installation - PART2 (6:45)
Enhanced Bootstrapping with CFN-INIT (11:52)
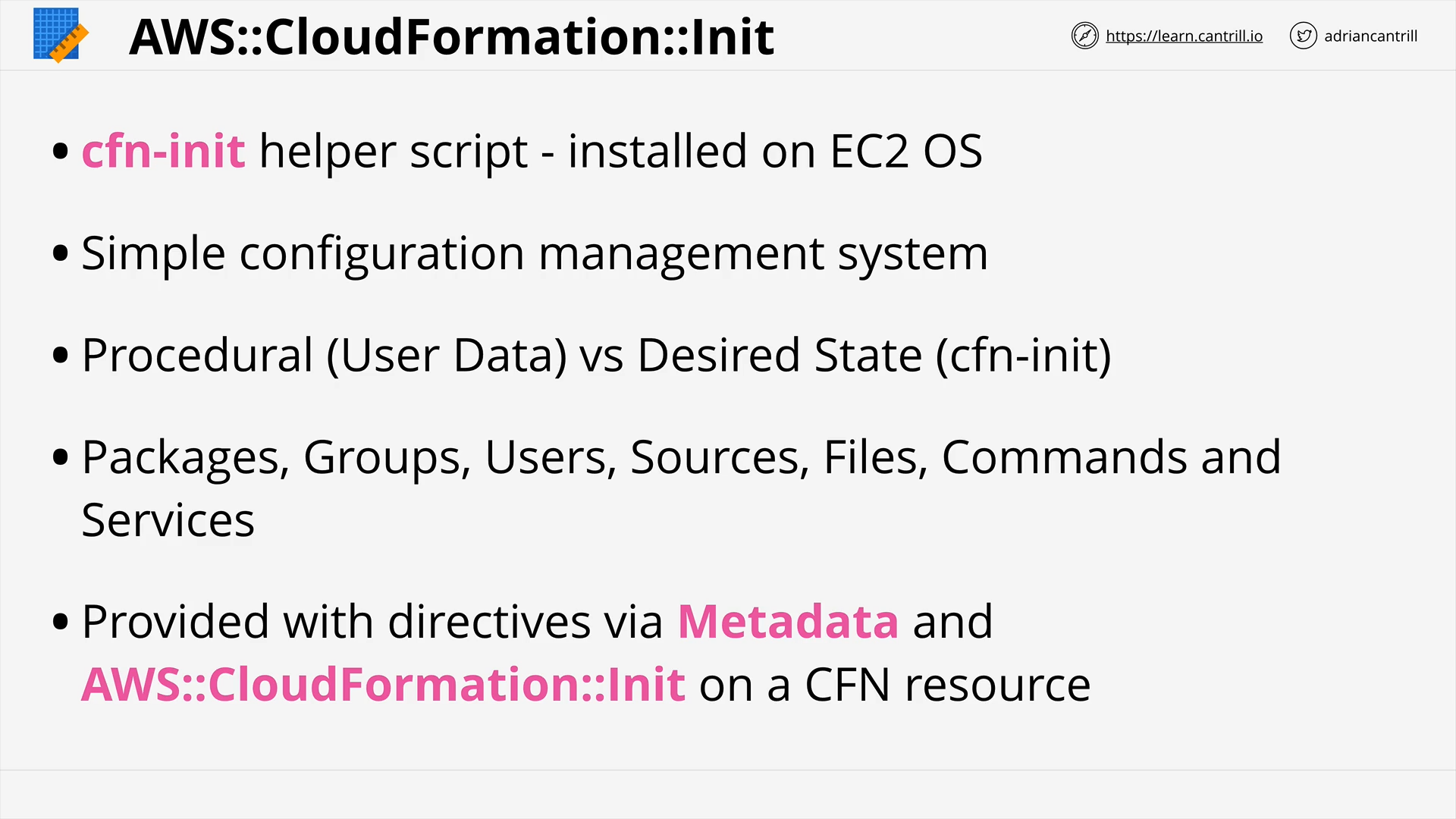 AWS::CloudFormation::Init
AWS::CloudFormation::Init
what is `cfn-init`?
A powerful desired-state-like configuration engine which is part of the CFN suite of products.
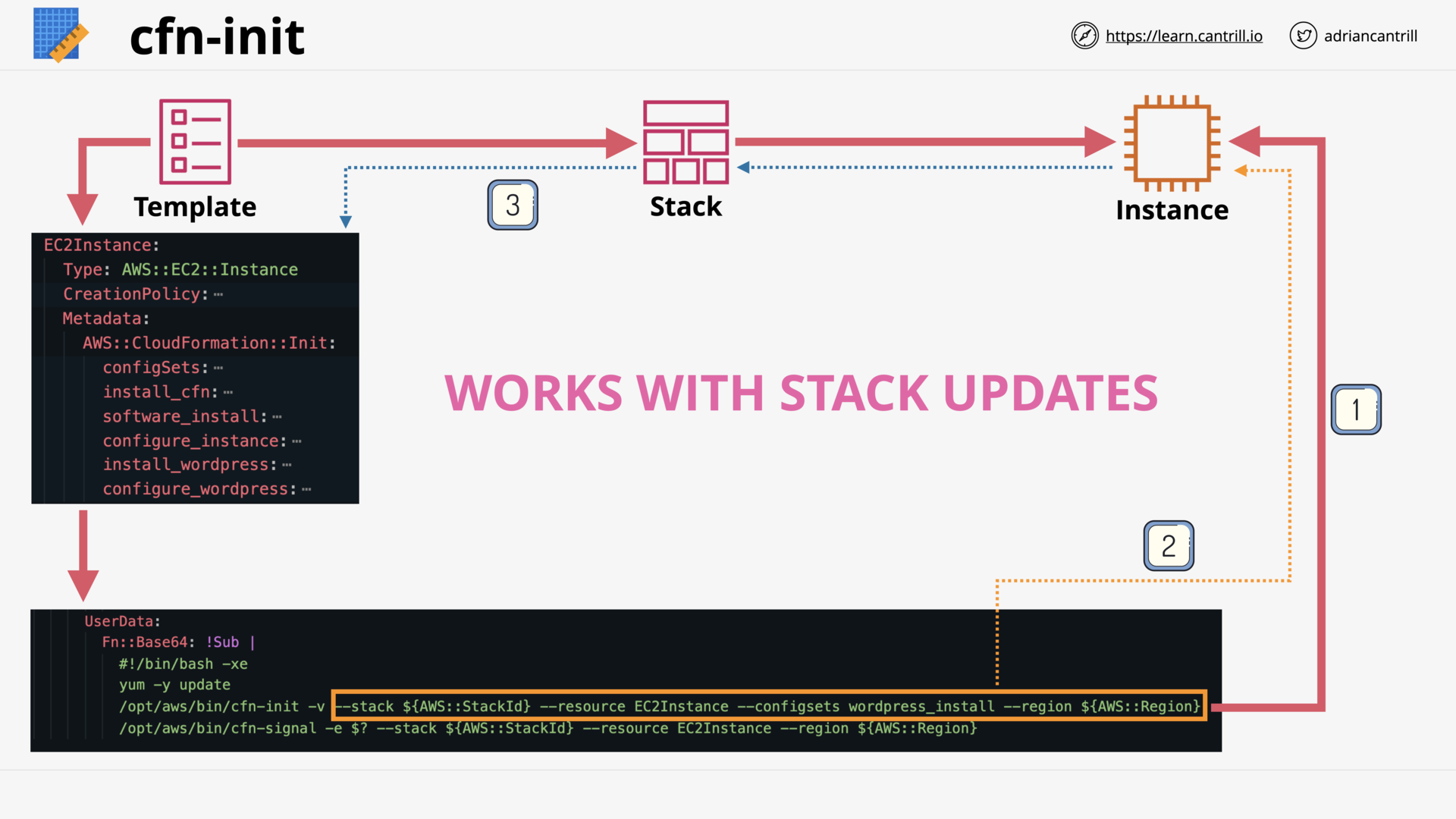
cfn-init works with stack updates
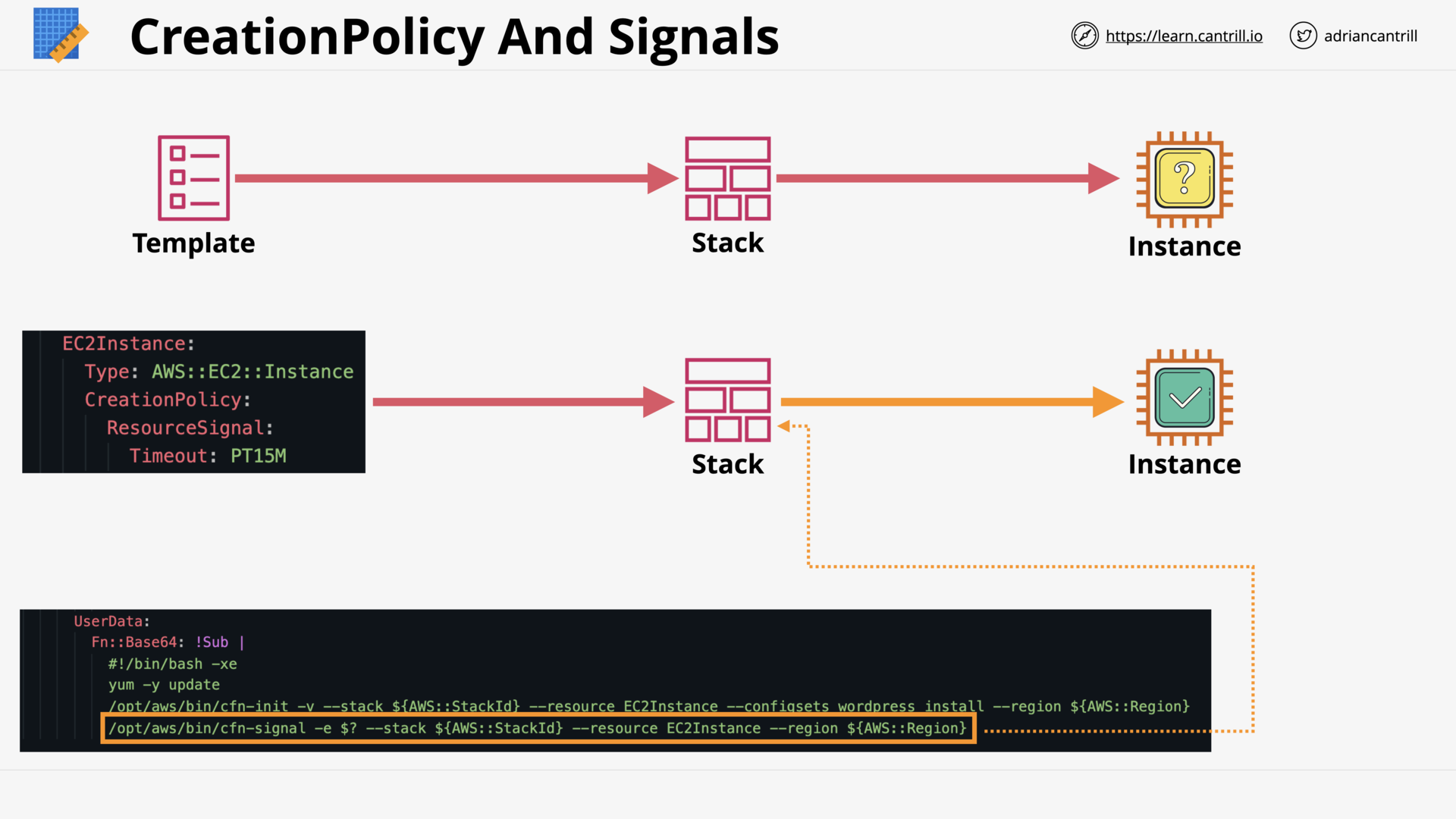 CreatePolicy & Signals
CreatePolicy & Signals
what does `cloudformation`'s `createpolicy` do?
Creation policies create a ‘WAIT STATE’ on resources .. not allowing the resource to move to CREATE_COMPLETE until signalled using the cfn-signal tool.
what does `cfn-signal` do?
cfn-signal tells CloudFormation that the stack’s resource is at the desired state (it’s created).
[DEMO] CFN-INIT and CFN Creation Policies (12:29)
EC2 Instance Roles & Profile (4:18)
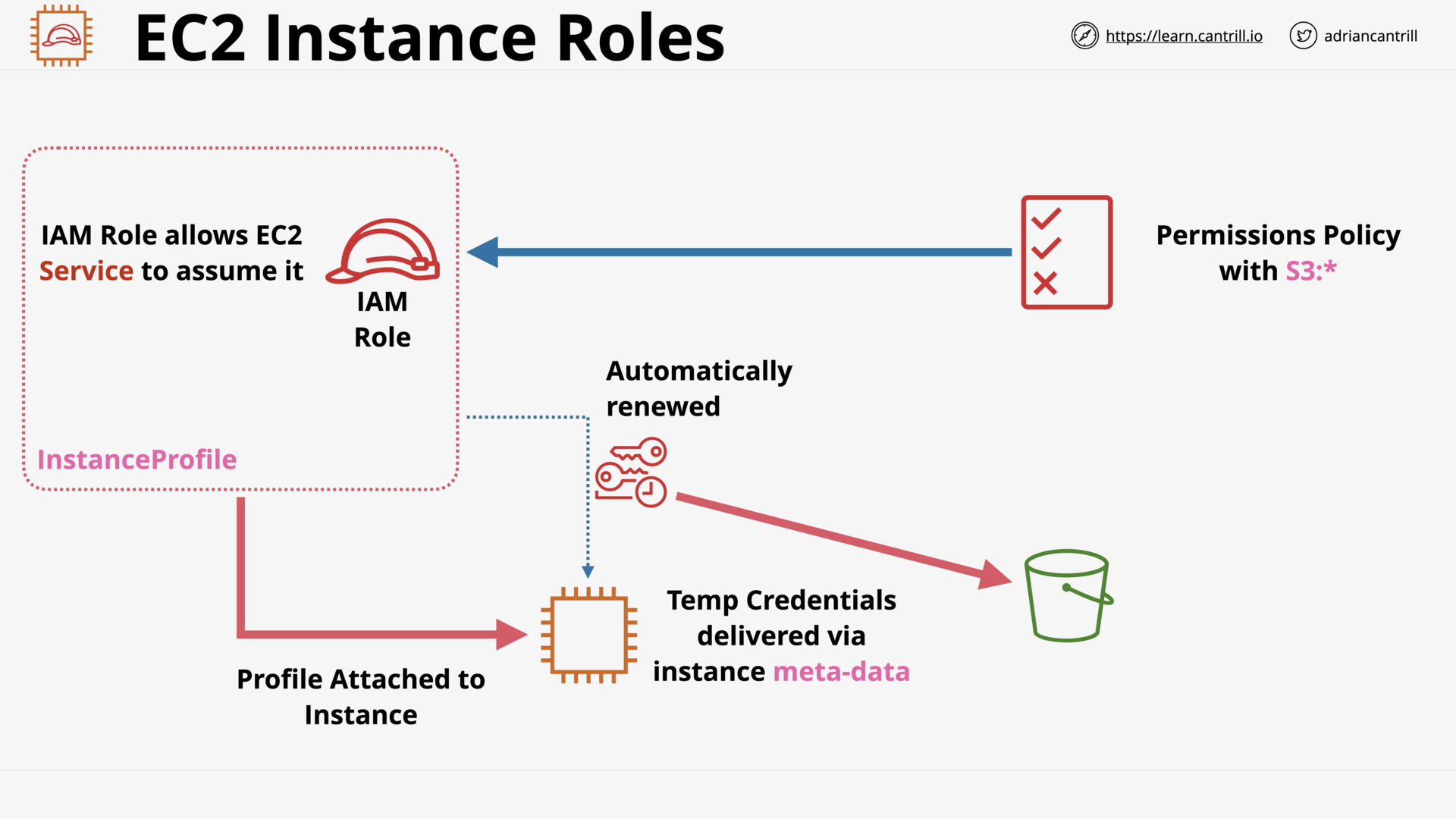 EC2 Instance Role & Instance Profile
EC2 Instance Role & Instance Profile
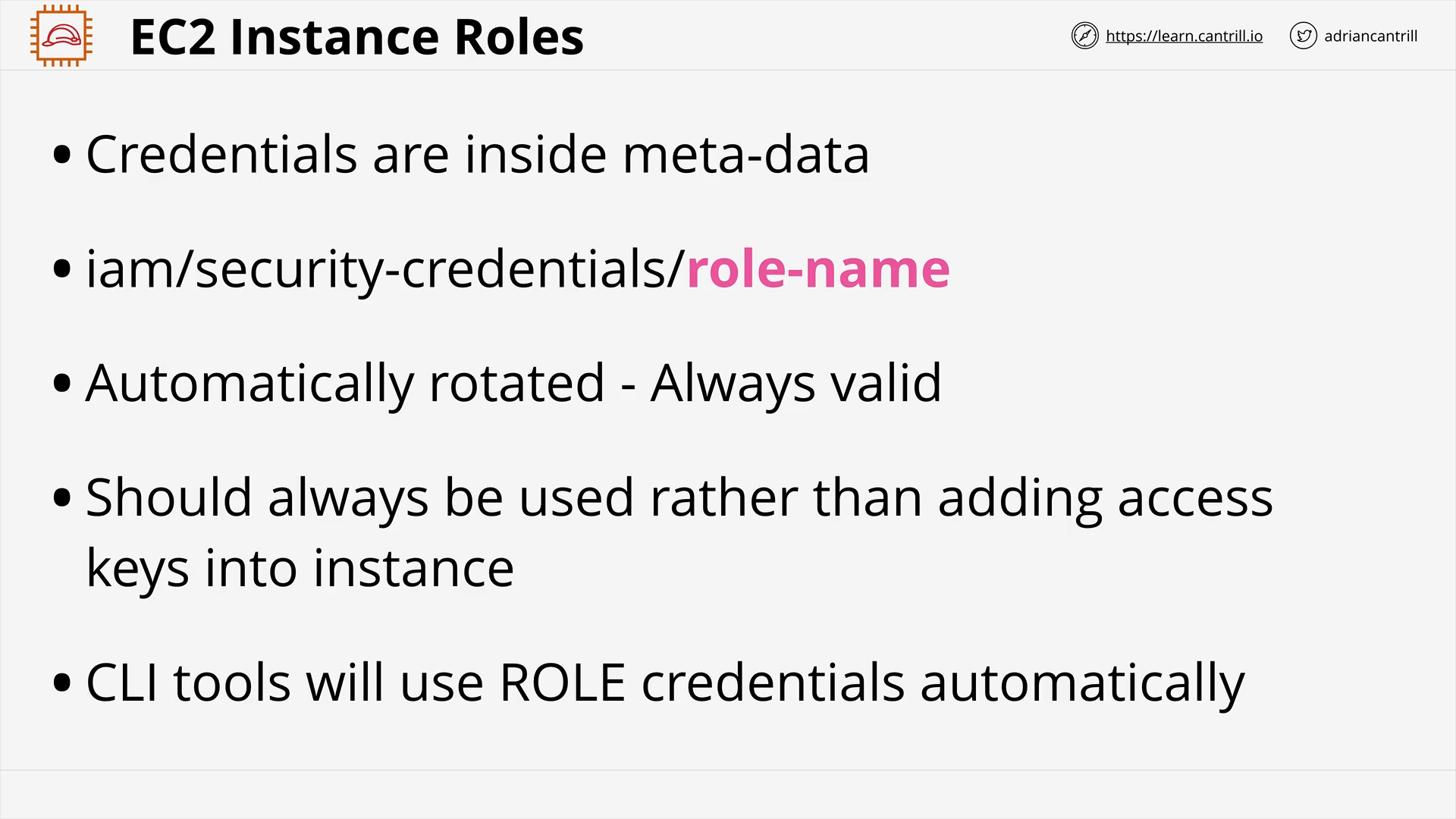 EC2 Instance Profile’s credential
EC2 Instance Profile’s credential
why use instance role/profile?
To grant permissions to applications running on Amazon EC2 instances via short-term credentials.
Using an IAM role to grant permissions to applications running on Amazon EC2 instances
[DEMO] Using EC2 Instance Roles (13:31)
SSM Parameter Store (6:16)
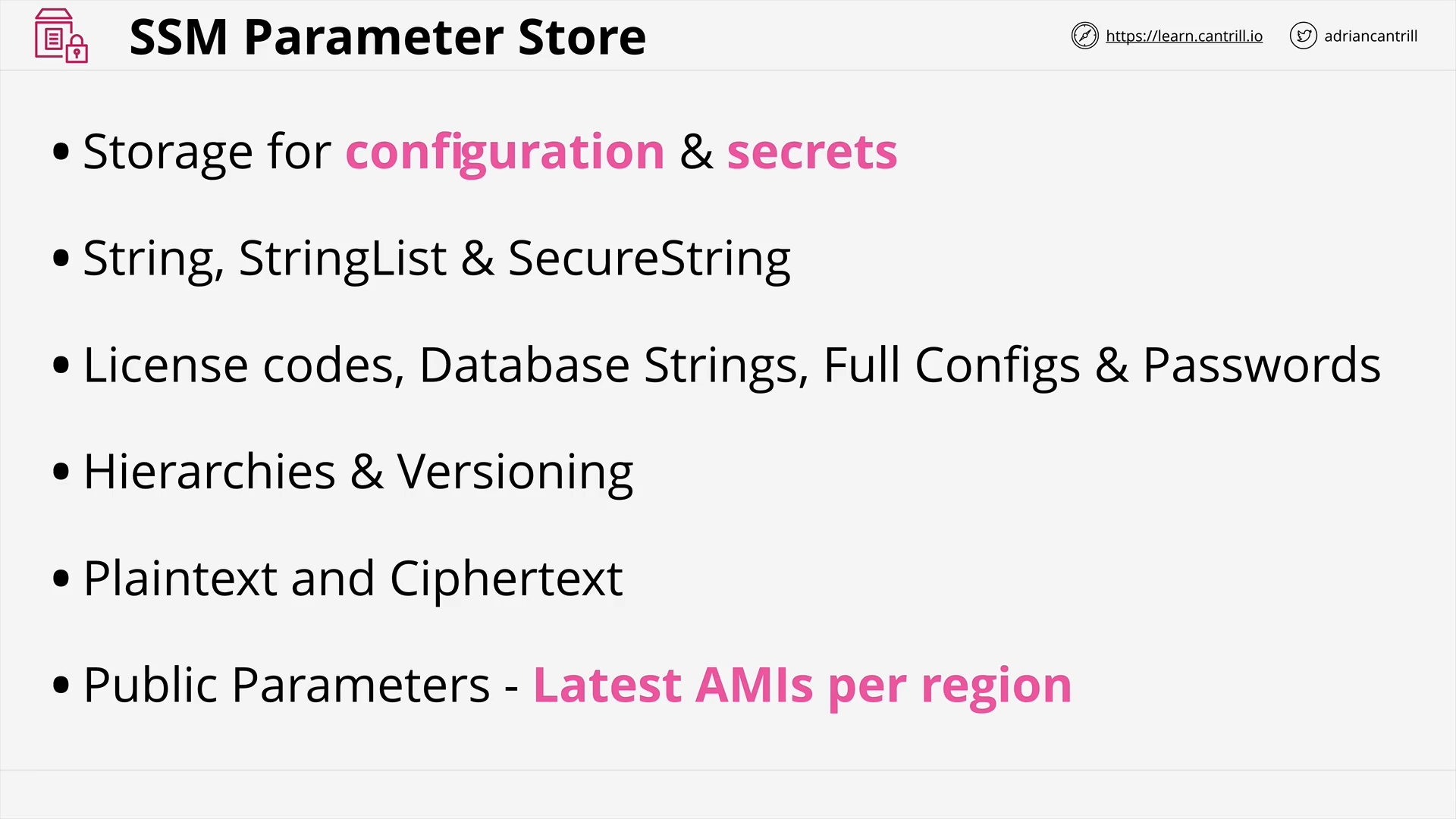 SSM Paremeter Store - Overview
SSM Paremeter Store - Overview
what is ssm parameter store?
Parameter Store, a capability of AWS Systems Manager, provides secure, hierarchical storage for configuration data management and secrets management.
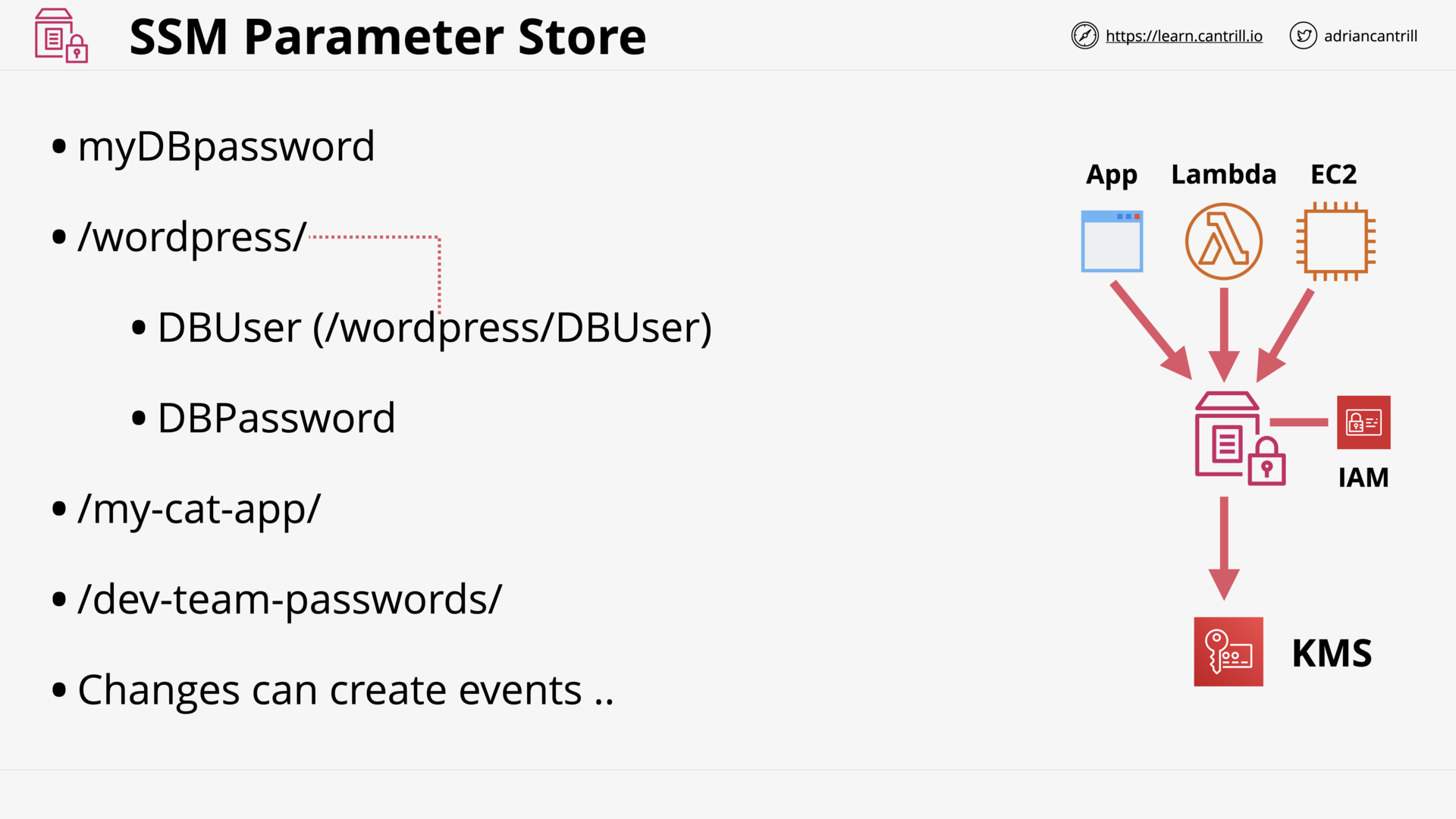 SSM Paremeter Store - Example
SSM Paremeter Store - Example
[DEMO] Parameter Store (16:11)
System and Application Logging on EC2 (6:15)
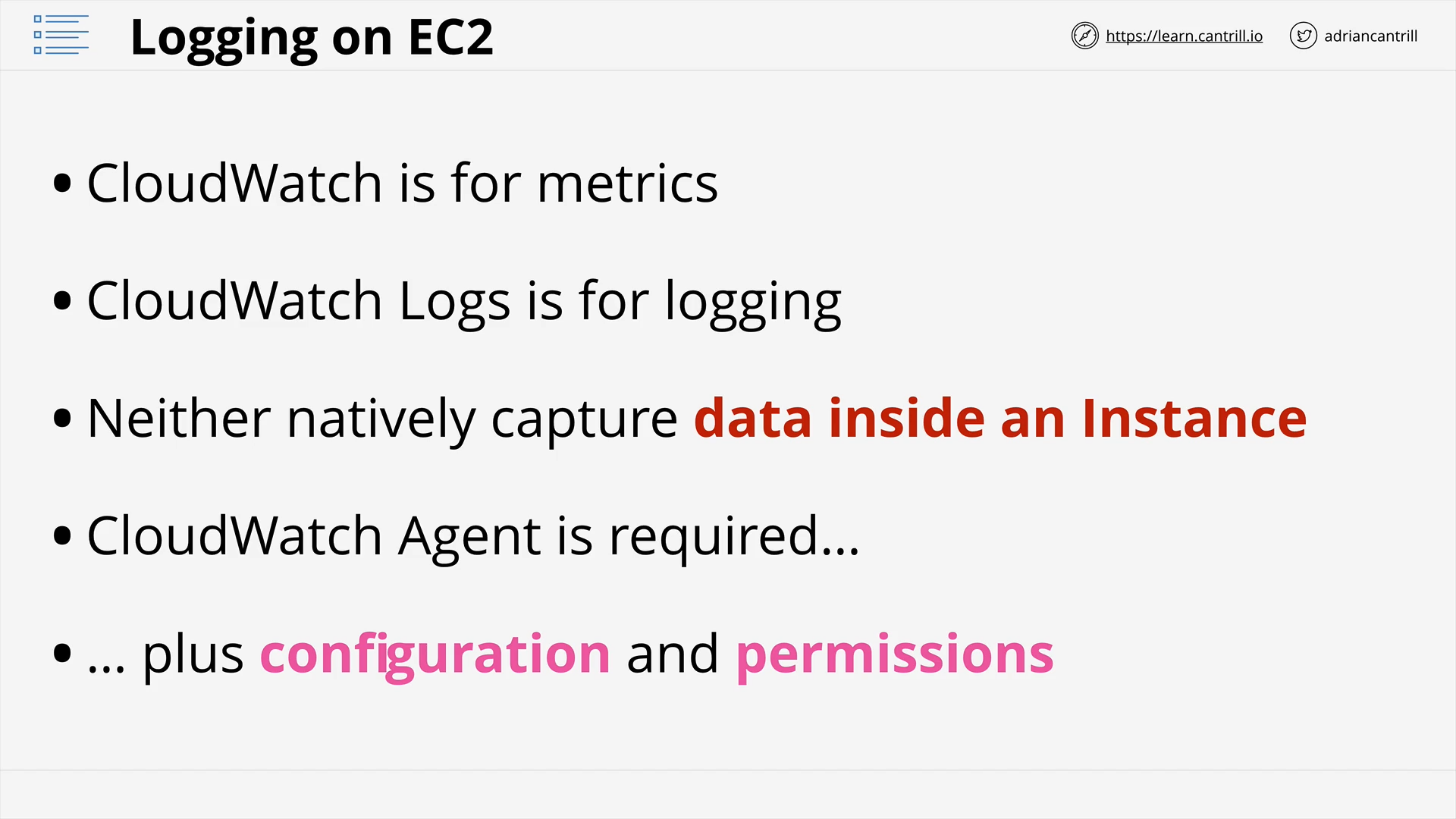 Logging on EC2
Logging on EC2
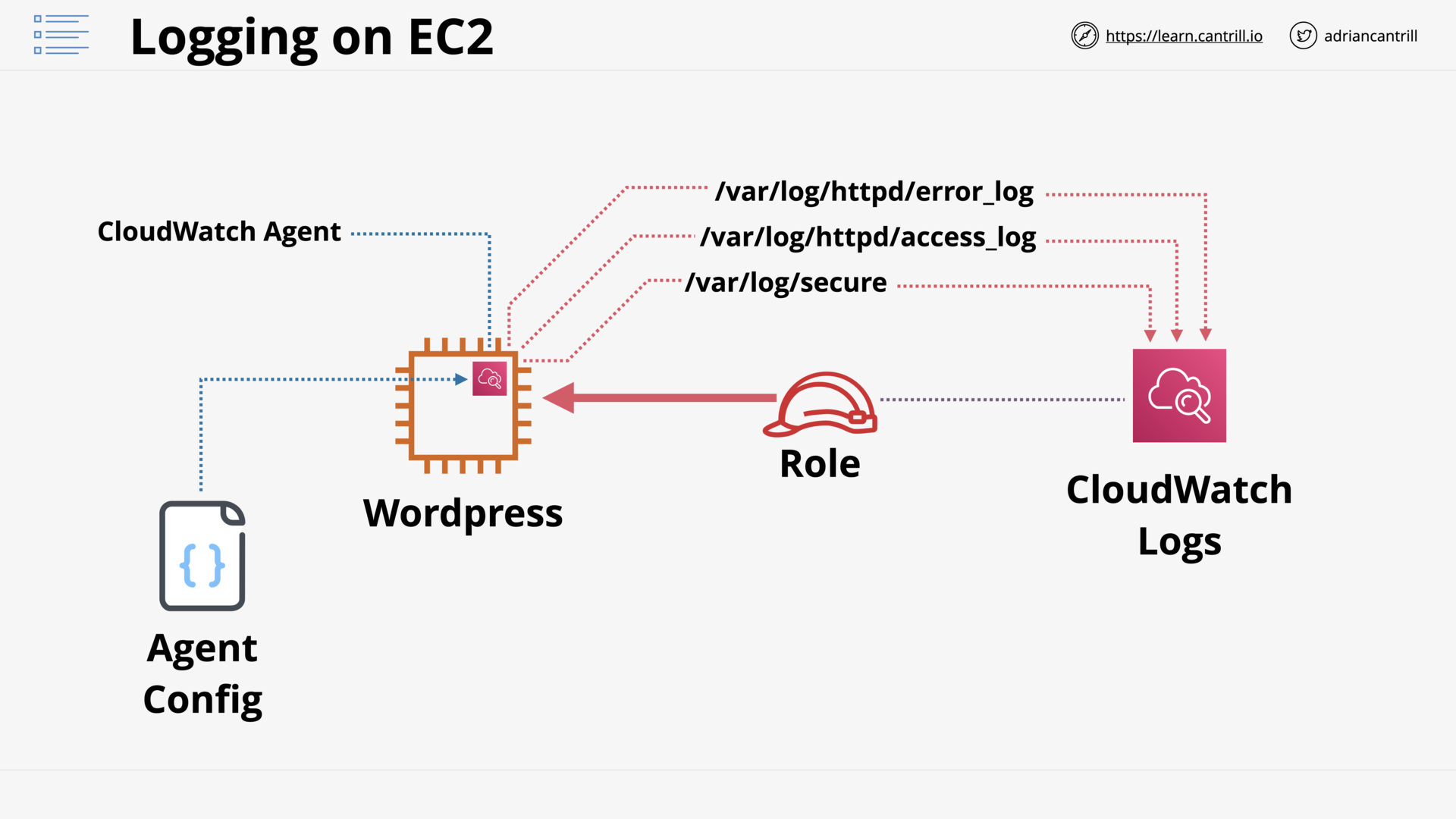 CloudWatch Agent - internal instance metrics and logging collection
CloudWatch Agent - internal instance metrics and logging collection
[DEMO] Logging and Metrics with CloudWatch Agent-PART1 (11:51)
[DEMO] Logging and Metrics with CloudWatch Agent-PART2 (8:08)
EC2 Placement Groups (14:29)
 EC2 Placement Groups - Placement strategies
EC2 Placement Groups - Placement strategies
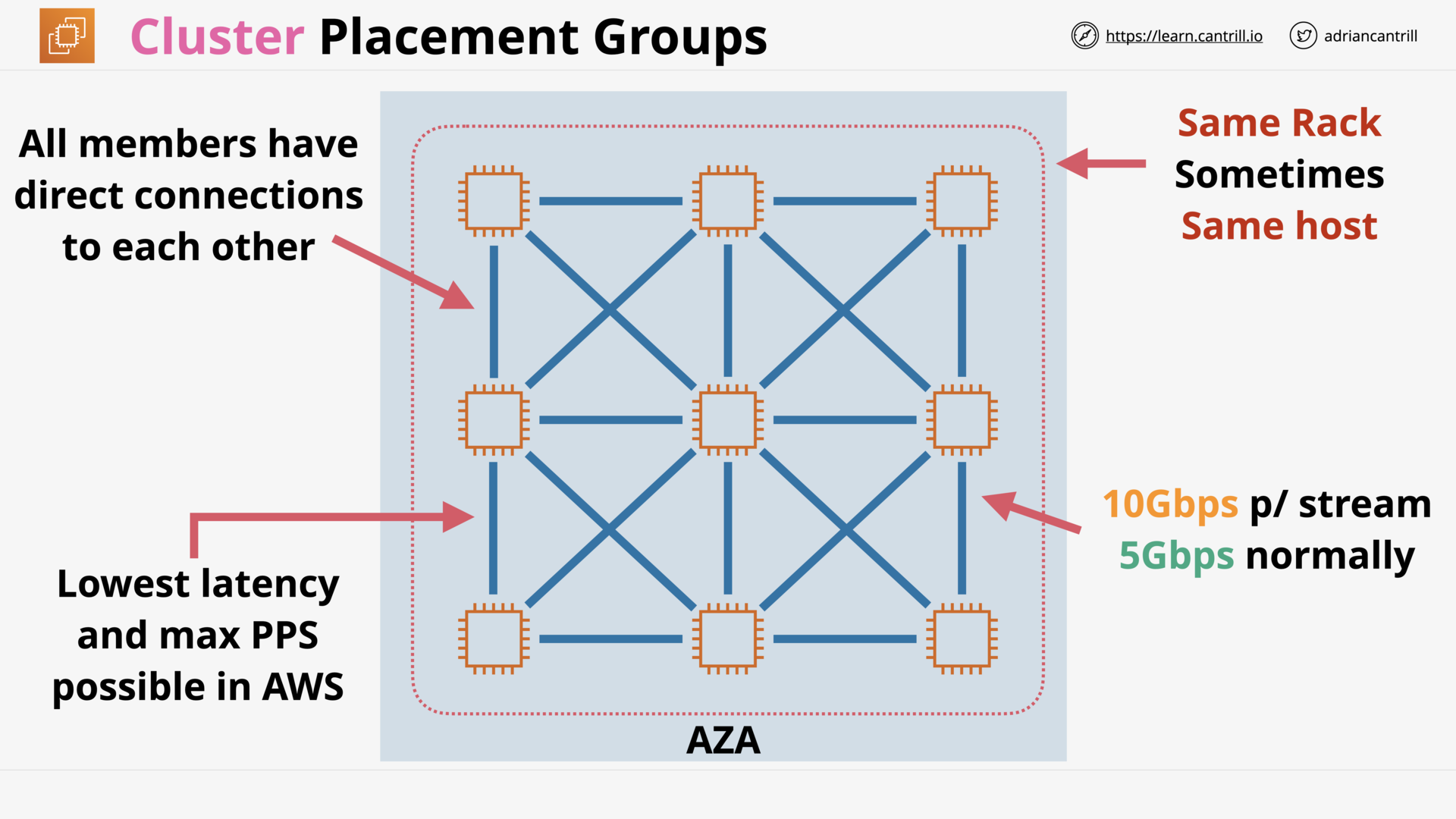 Cluster Placement Groups
Cluster Placement Groups
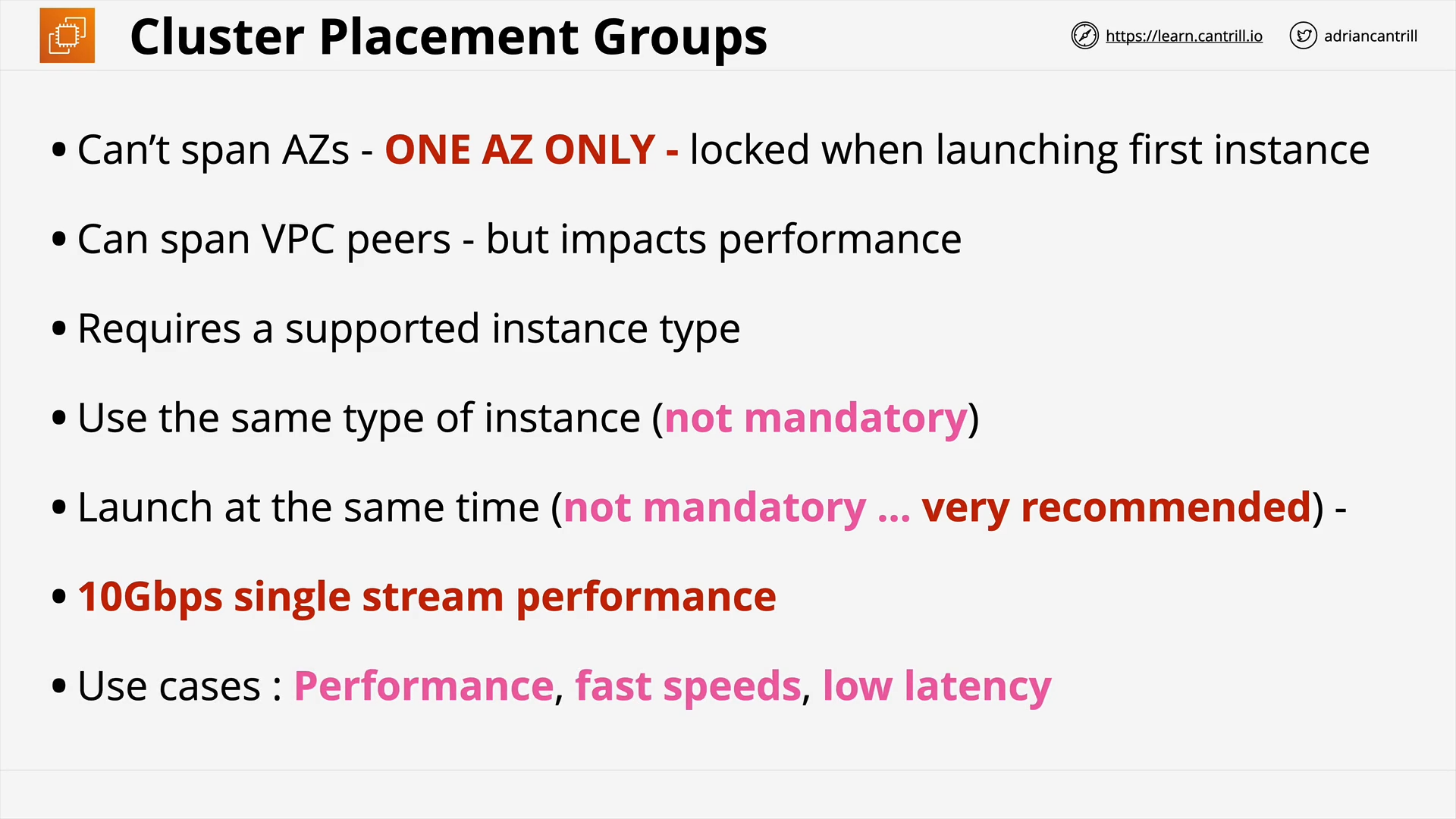 Cluster Placement Groups - Pros and Cons
Cluster Placement Groups - Pros and Cons
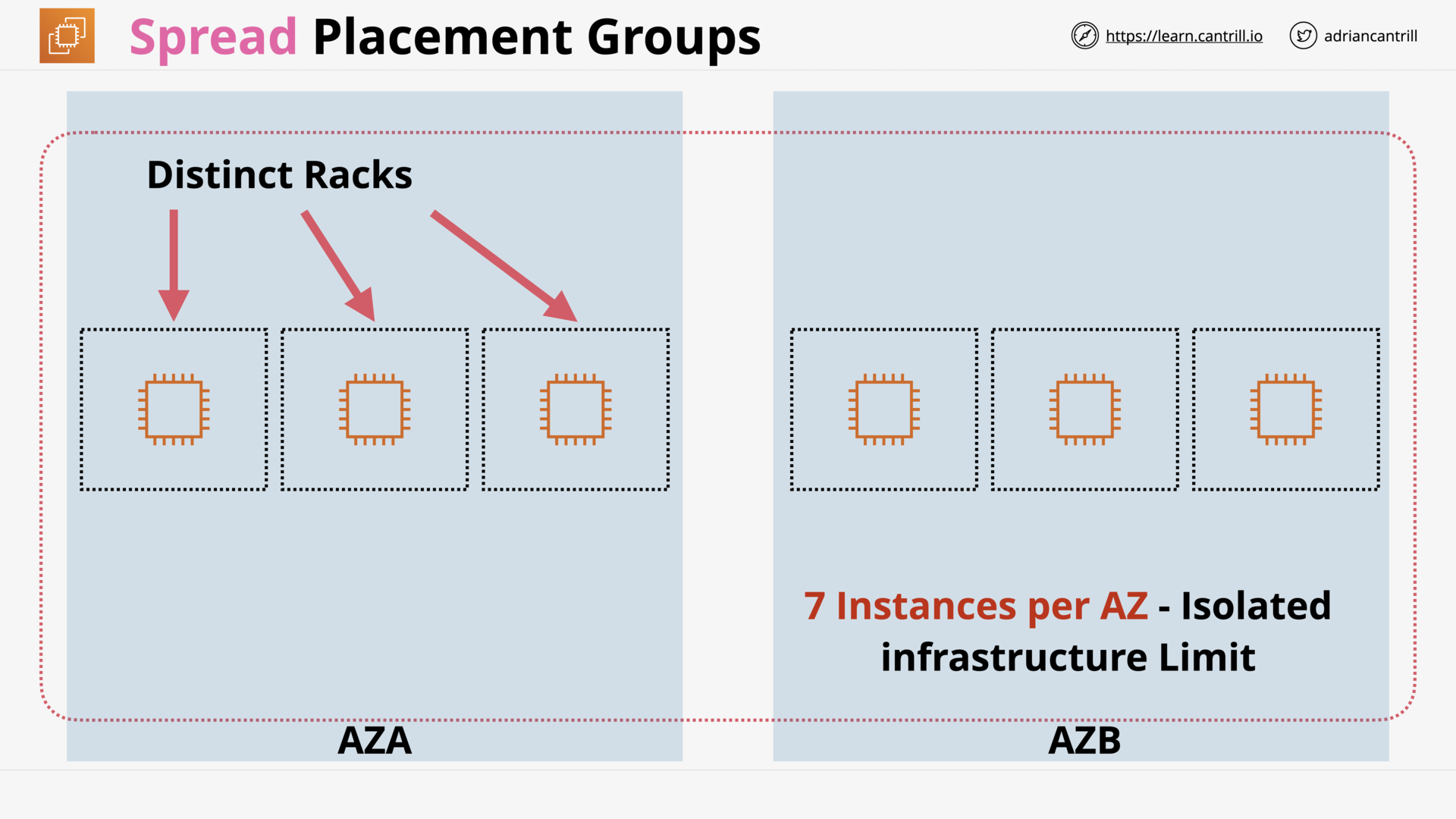 Spread Placement Groups
Spread Placement Groups
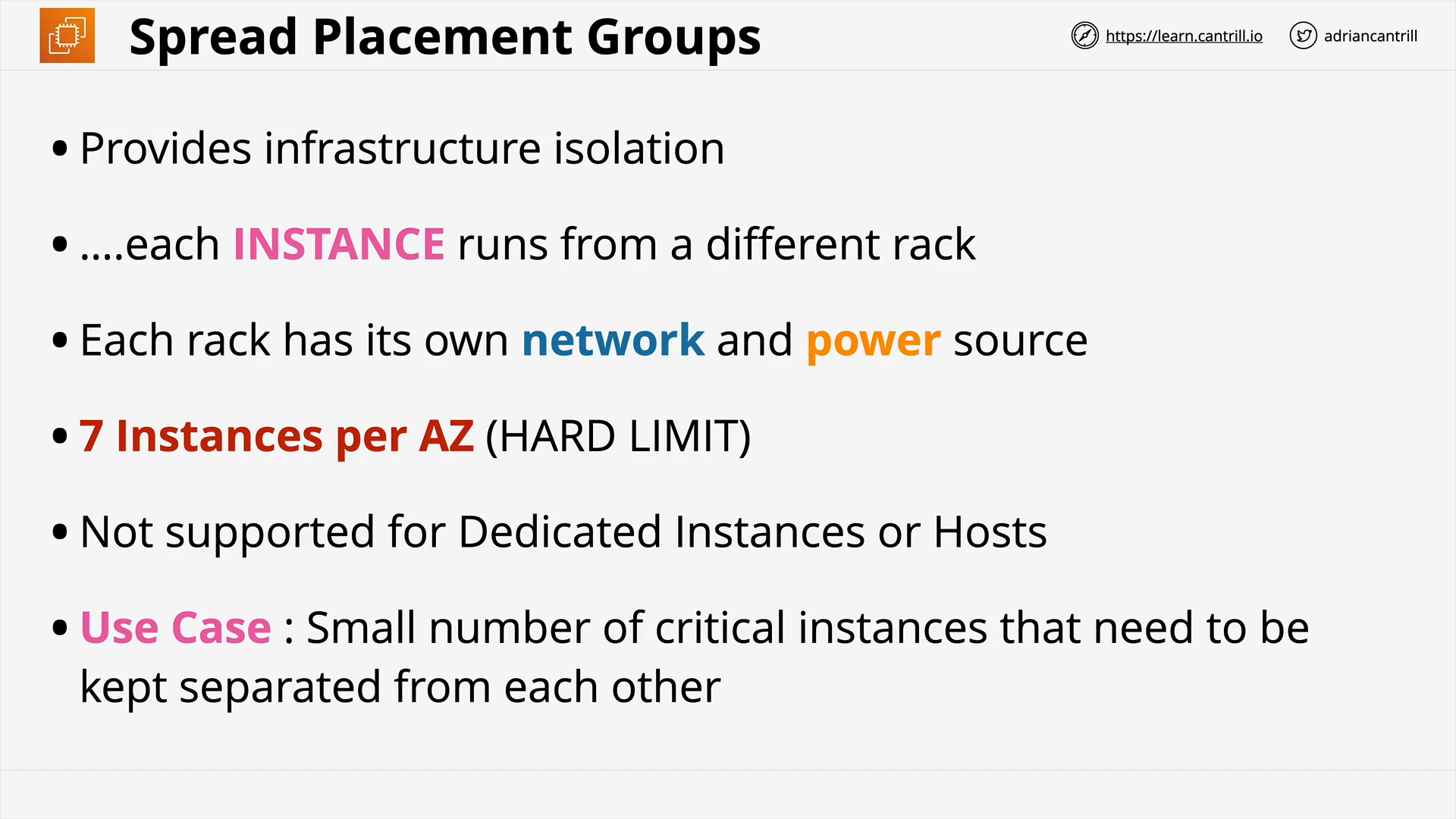 Spread Placement Groups - Pros and Cons
Spread Placement Groups - Pros and Cons
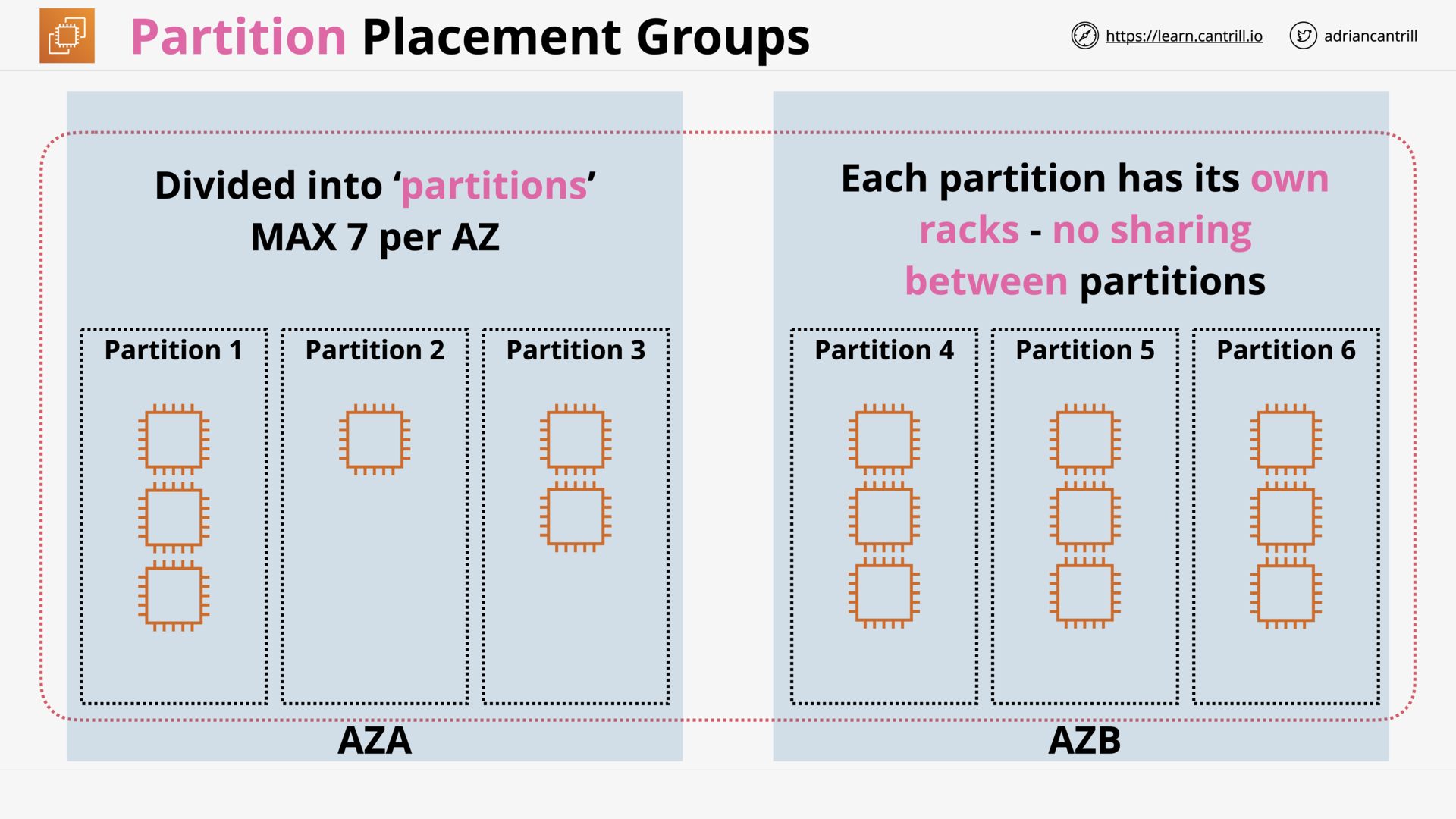 Partition Placement Groups
Partition Placement Groups
 Partition Placement Groups - Pros and Cons
Partition Placement Groups - Pros and Cons
Dedicated Hosts (8:56)
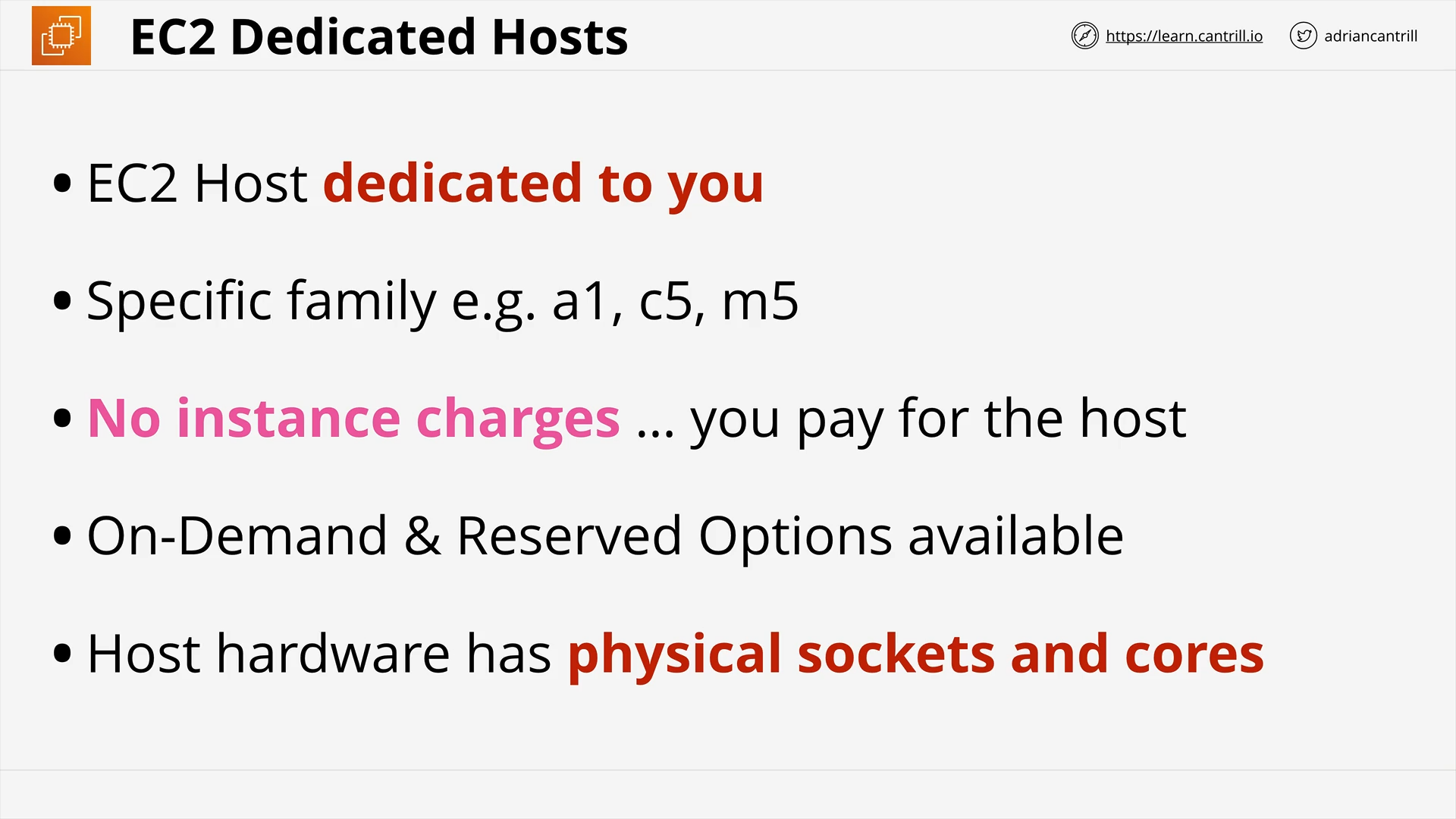 EC2 Dedicated Hosts
EC2 Dedicated Hosts
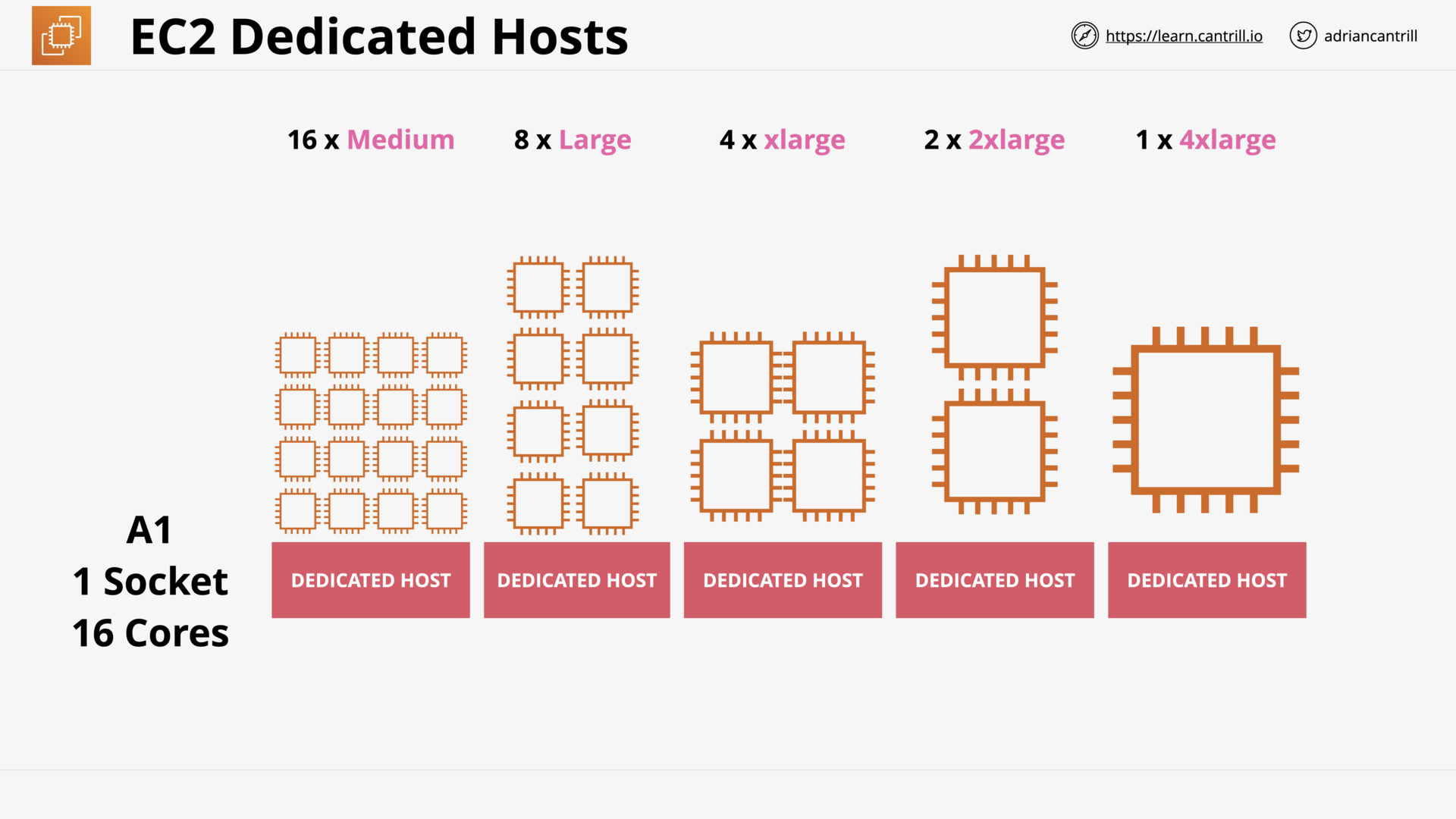 Instance capacity configurations - Single instance type support
Instance capacity configurations - Single instance type support
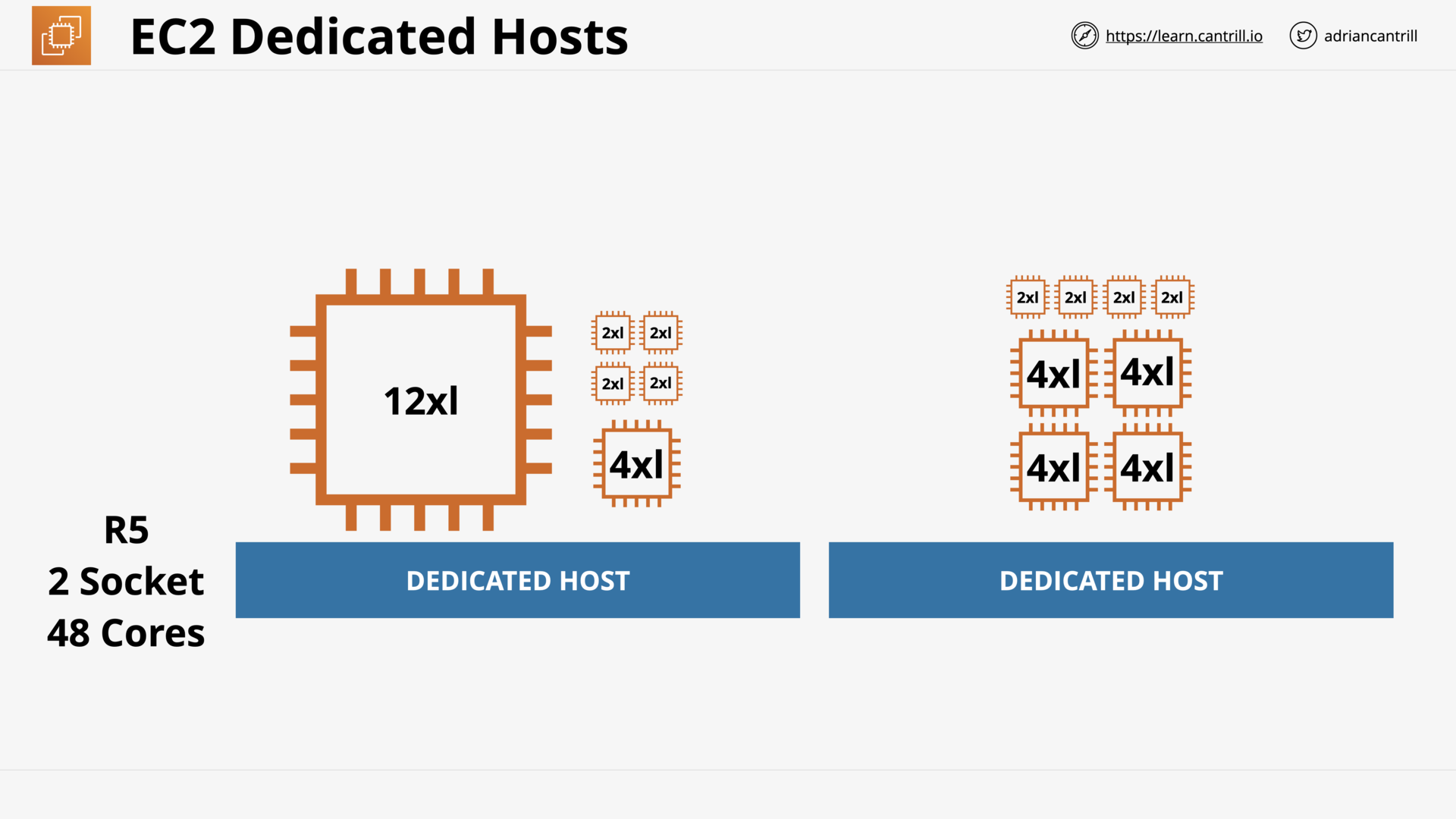 Instance capacity configurations - Multiple instance type support
Instance capacity configurations - Multiple instance type support
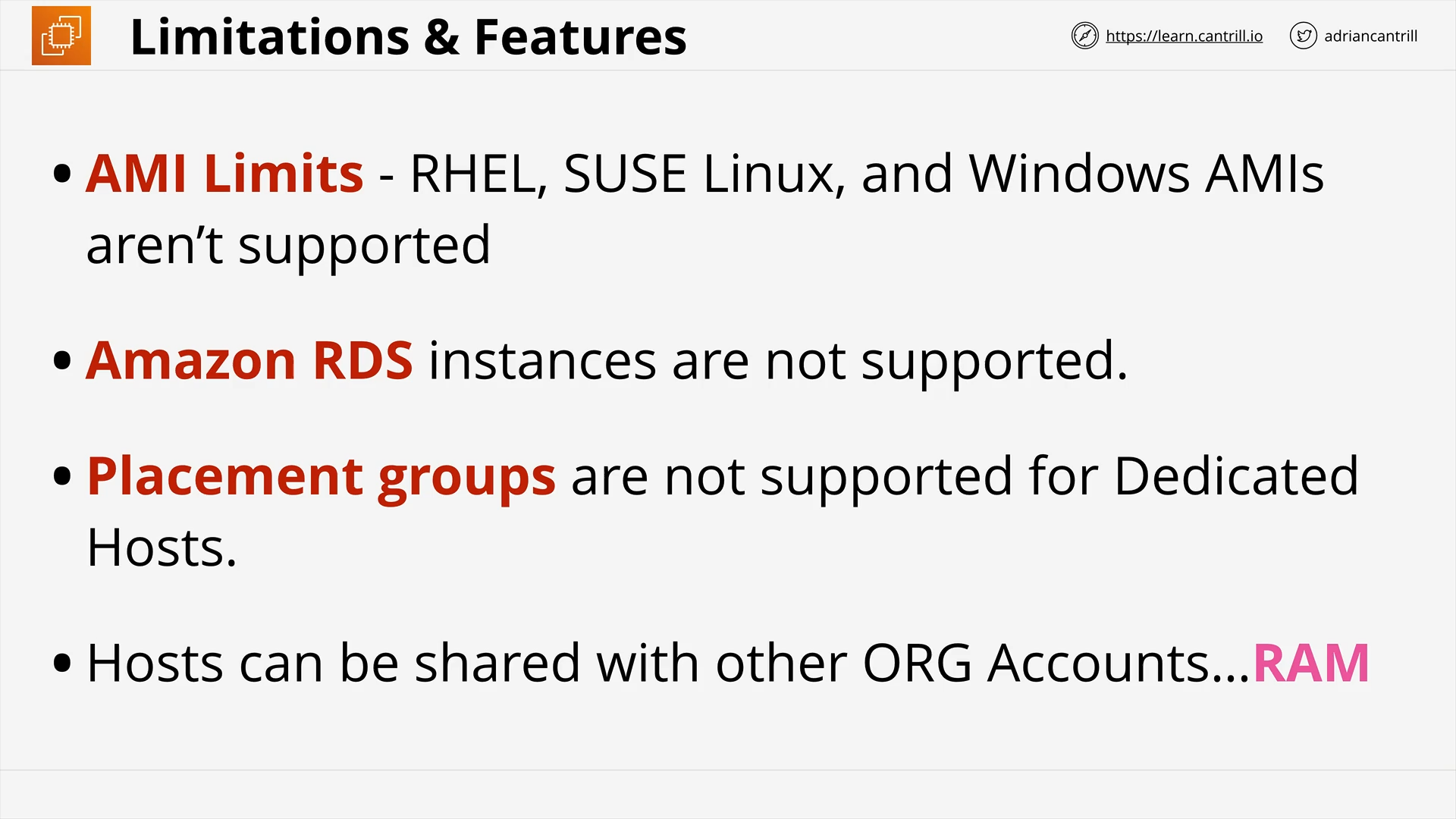 EC2 Dedicated Hosts - Limitations & Features
EC2 Dedicated Hosts - Limitations & Features
Enhanced Networking & EBS Optimized (6:57)
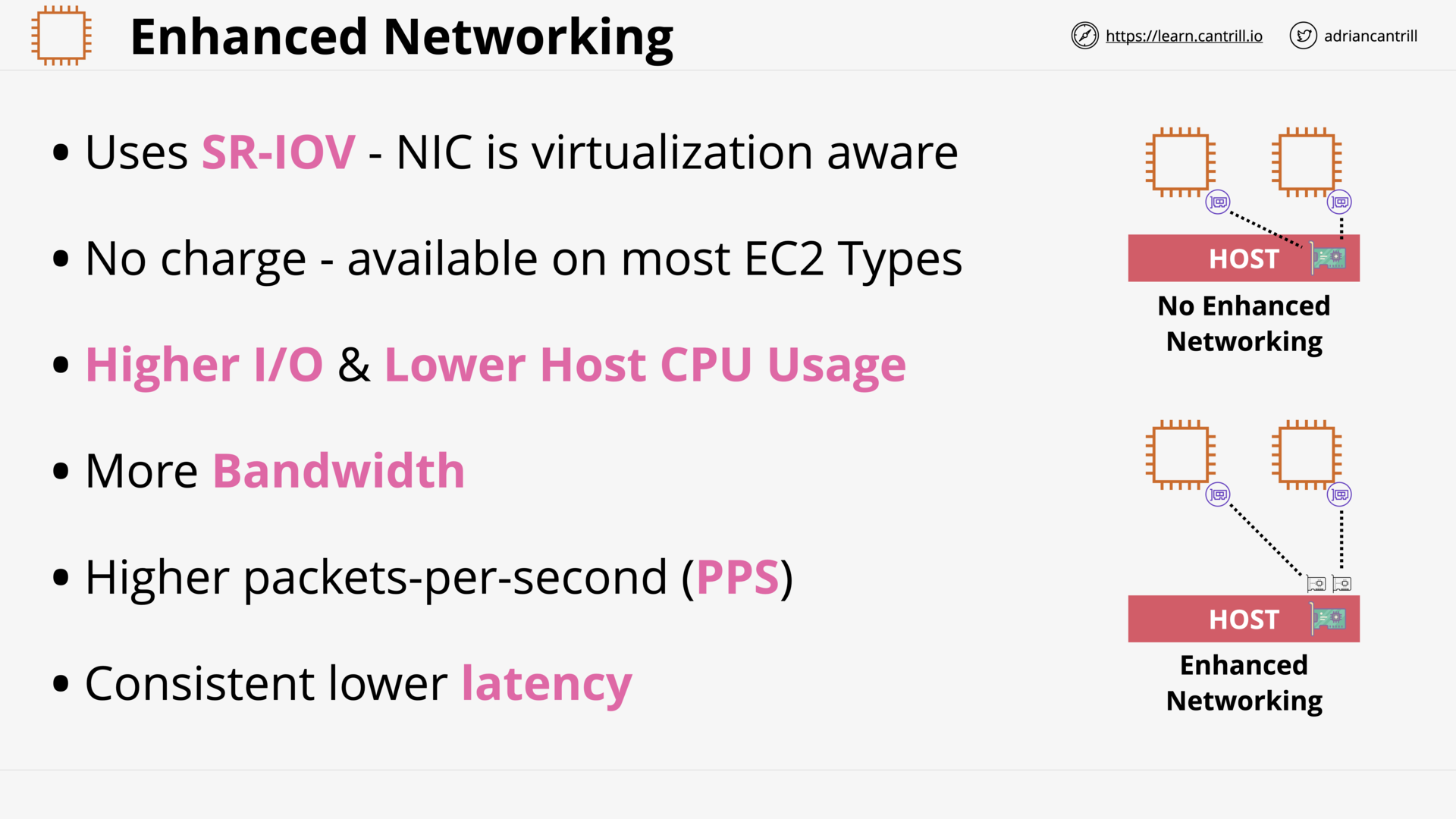
what is aws enhanced networking?
The AWS implementation of SR-IOV.
what is sr-iov?
A standard allowing a physical host network card to present many logical devices which can be directly utilized by instances.
what is the benefit of sr-iov?
Lower host CPU usage, better throughput, lower and consistent latency.
what is ebs optimized?
A dedicated bandwidth for storage networking - separate from data networking.
Advanced EC2 Section Quiz
ROUTE 53 - GLOBAL DNS
R53 Hosted Zones
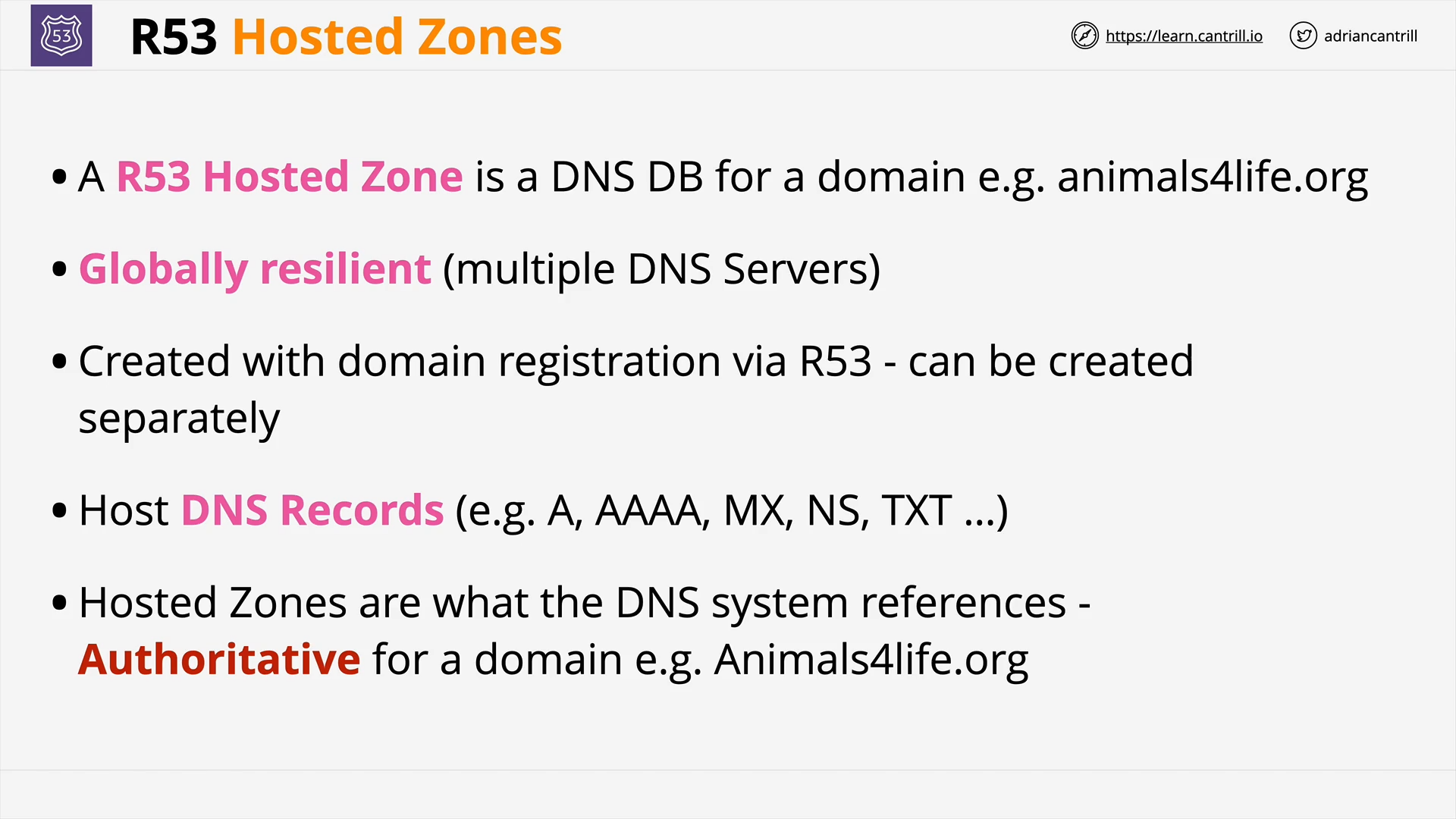
what is a route53 hosted zone?
A DNS database for a domain, e.g. animals4life.io
- It’s what the DNS system references for a domain.
- In other words, hosted zone is the Authoritative nameserver of a domain.
R53 Public Hosted Zones (6:28)
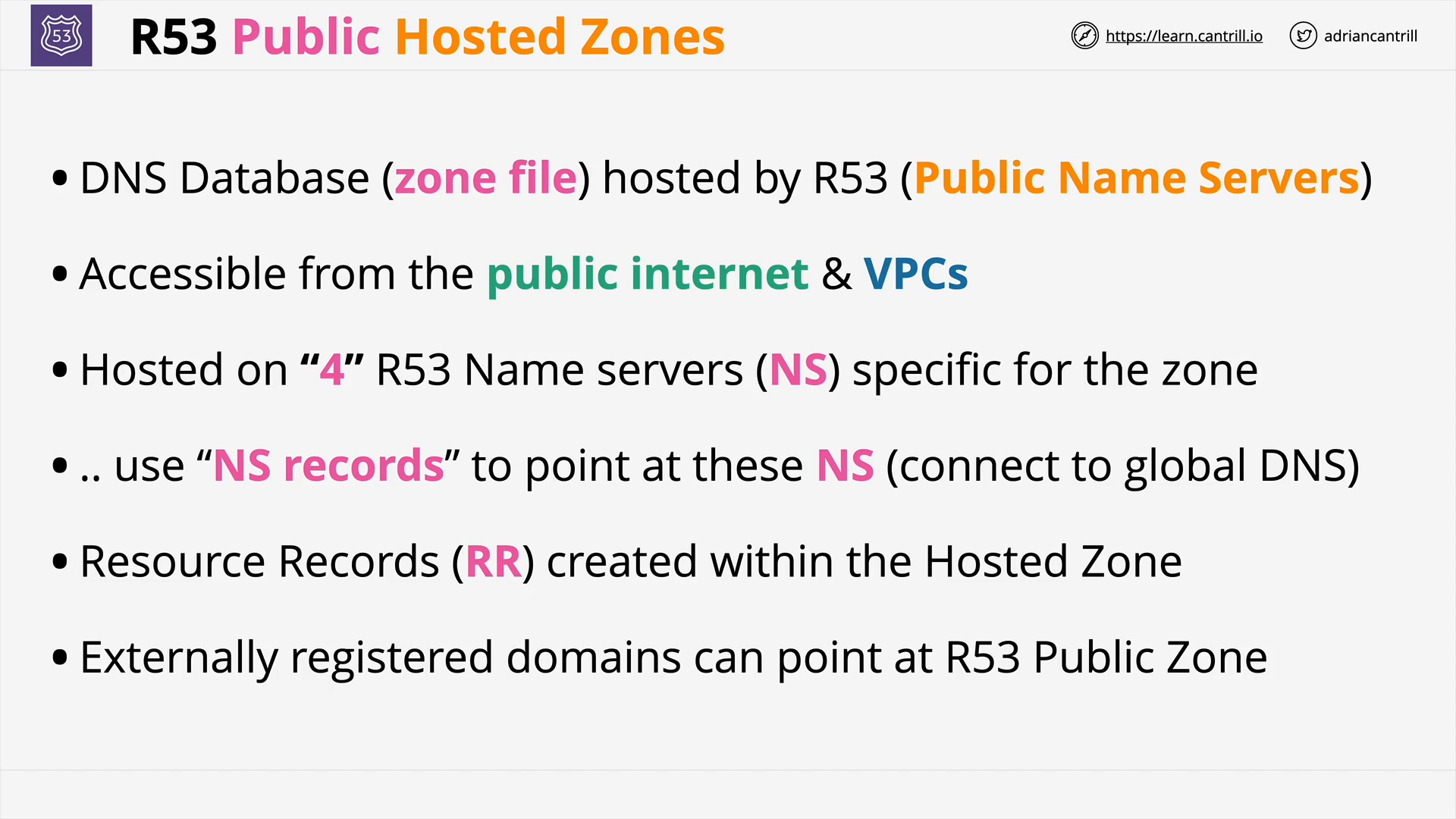 R53 Public Hosted Zones - Overview
R53 Public Hosted Zones - Overview
how many nameservers does a public hosted zone have?
4 Route53 nameservers
what is the accessibility of a r53 public zone?
A R53 Public Zone can be accessed from:
- the public internet
- AWS VPCs.
for a public hosted zone, what is the dns query process of the aws vpc?
- VPC Instances are configured with the VPC
+2 Address(R53 Resolver). - Any resources in the VPC can query public DNS and R53 Public Hosted Zones record.
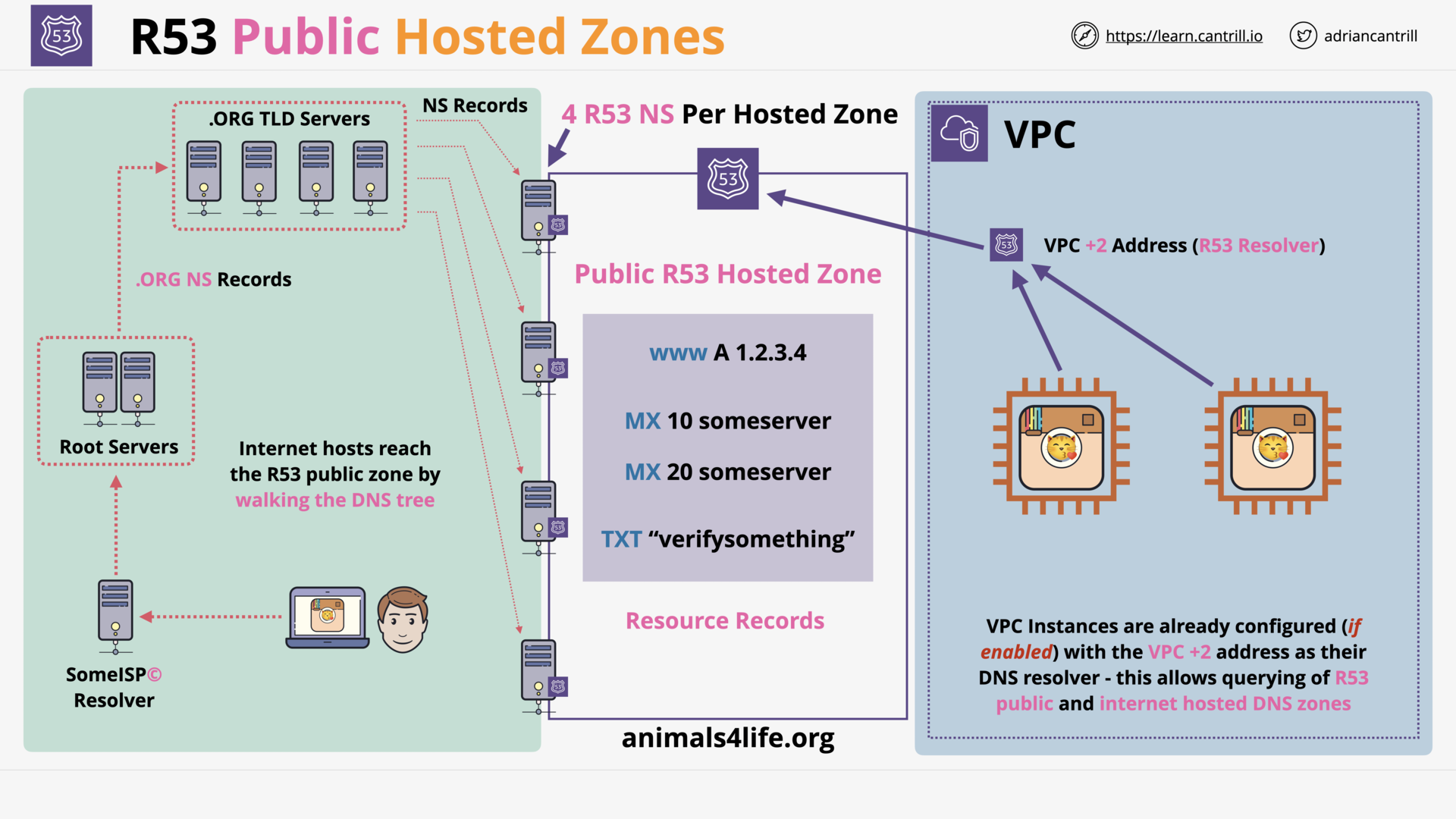 R53 Public Hosted Zones - Example
R53 Public Hosted Zones - Example
R53 Private Hosted Zones (5:10)
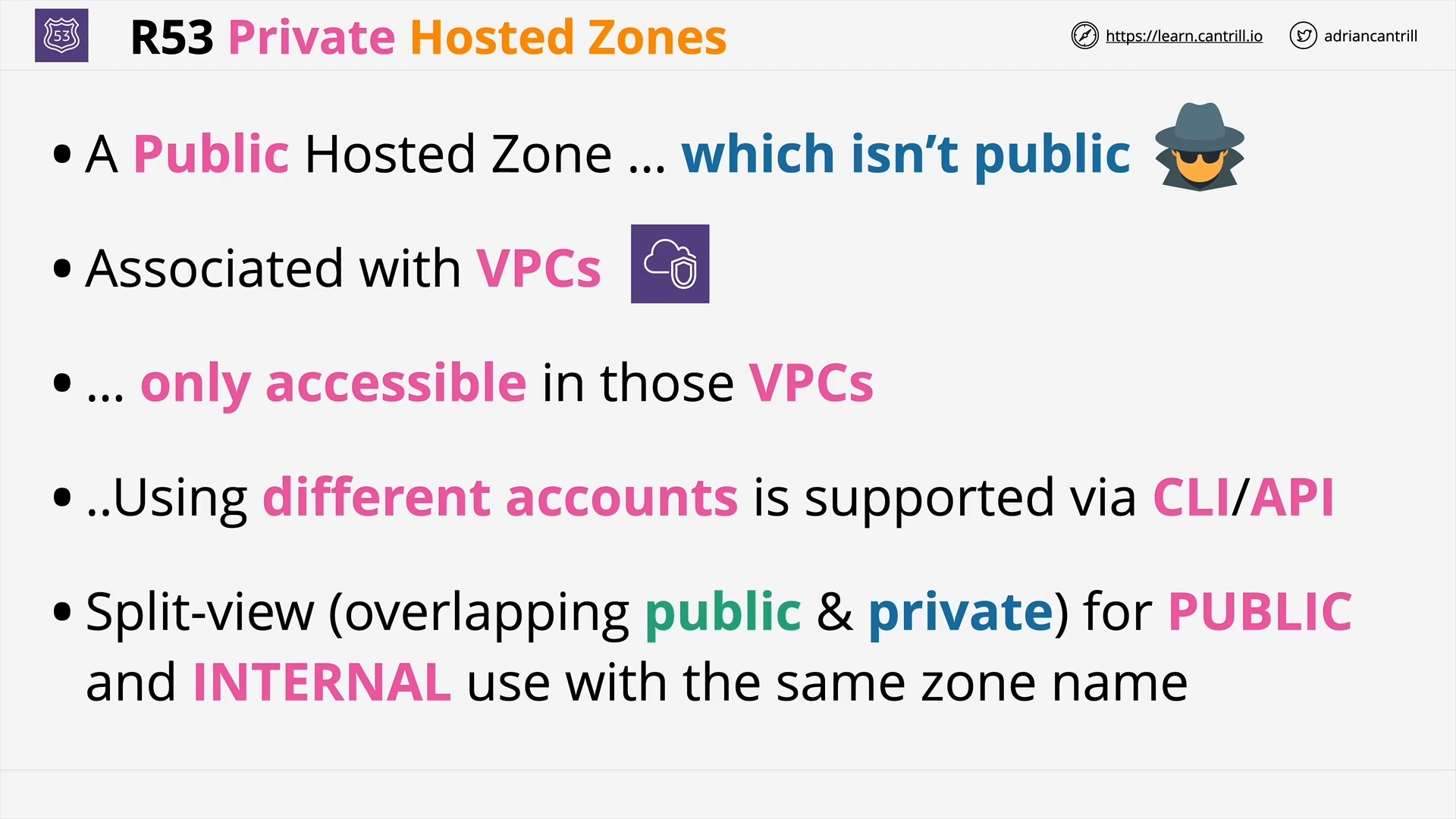 R53 Private Hosted Zones - Overview
R53 Private Hosted Zones - Overview
what is the accessibility of a r53 private hosted zone?
A R53 Private Hosted Zone can only be accessed by the VPCs (which with it is associated).
- These VPCs can be from the same account or different accounts.
- The public internet cannot access R53 Private Hosted Zones.
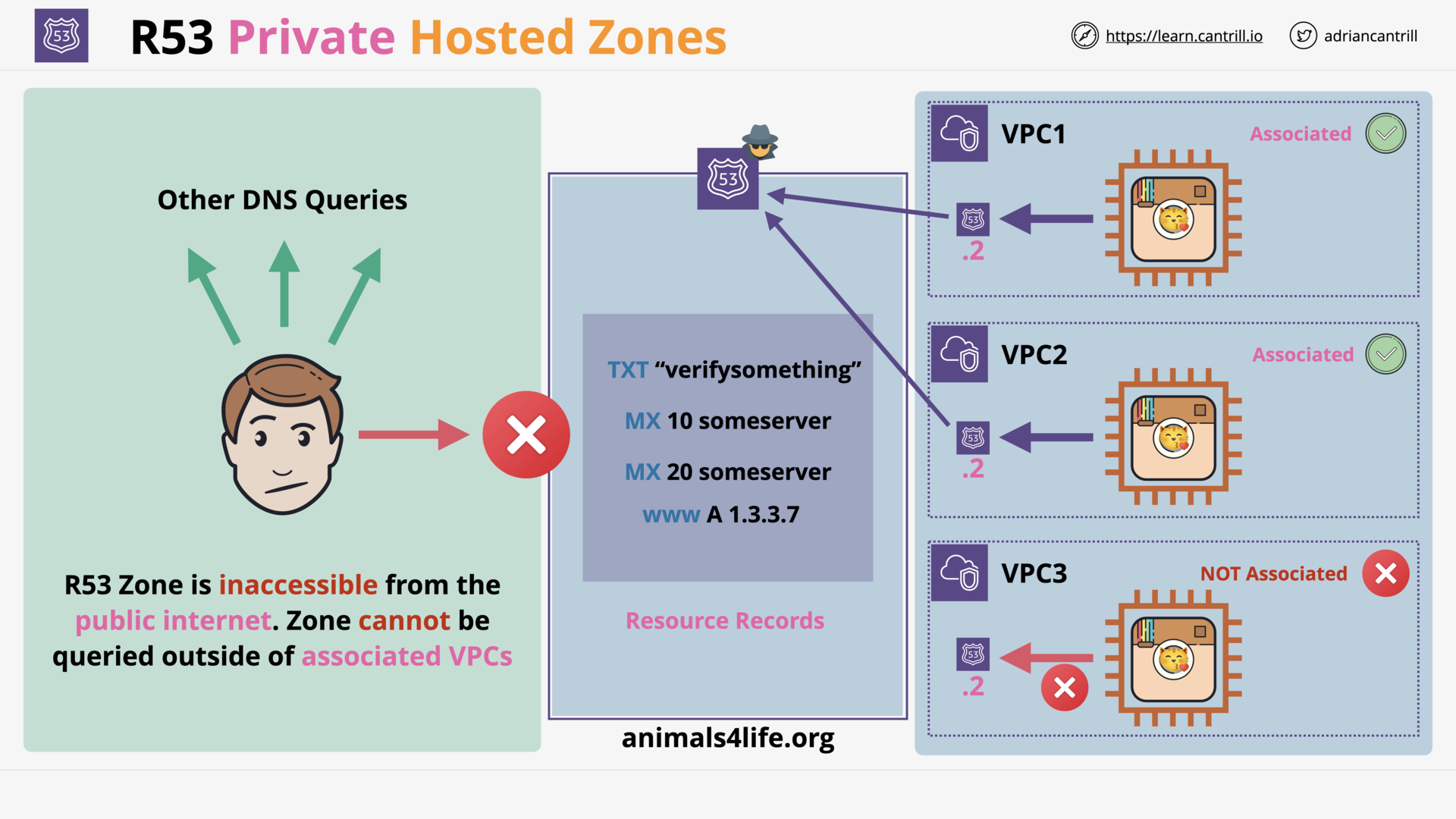 R53 Private Hosted Zones - Example
R53 Private Hosted Zones - Example
R53 Split View Hosted Zones
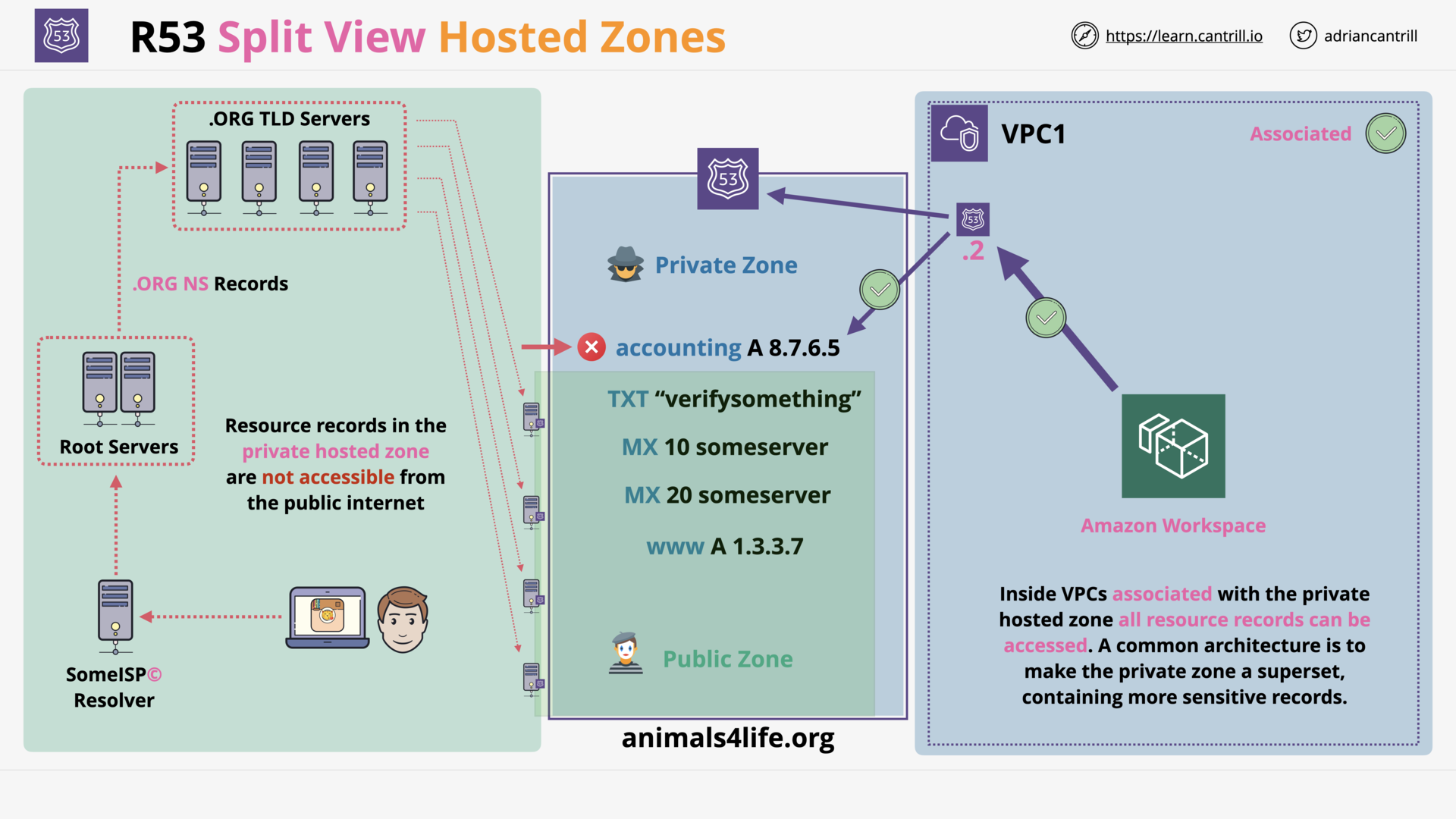 R53 Split View Hosted Zones
R53 Split View Hosted Zones
what is r53 split-view dns?
Using the same domain name (example.com) for
- internal uses (
accounting.example.com) - external uses, such as your public website (
www.example.com)
Or even using the same sub-domain for both public (external) and internal usage.
CNAME vs R53 Alias (5:19)
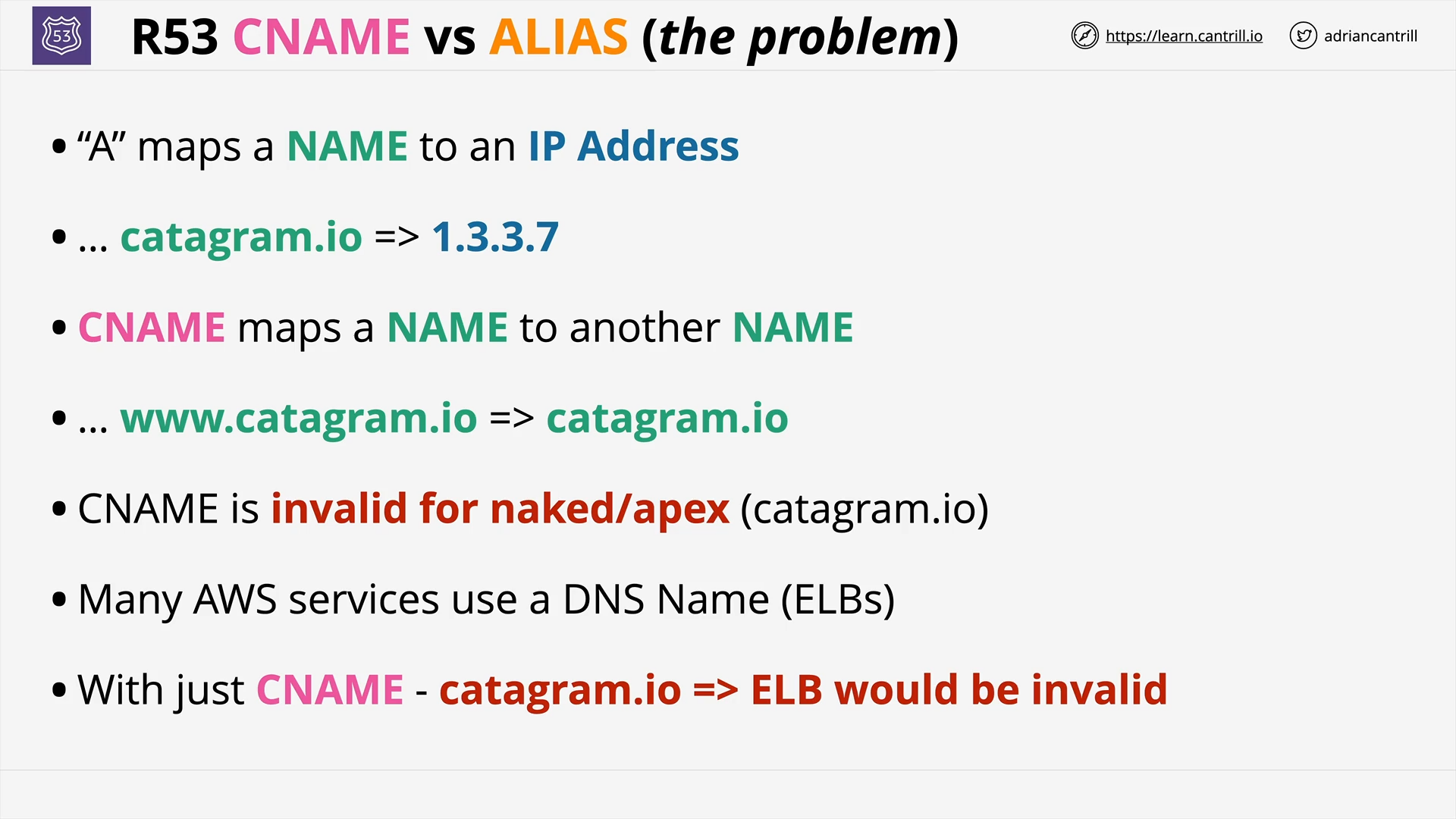
CNAME record - Problem
what is `cname` record?
A CNAME record:
- maps DNS queries for the name of the current record, such as
acme.example.com - to:
- another domain (
example.comorexample.net) - or subdomain (
acme.example.comorzenith.example.org).
- another domain (
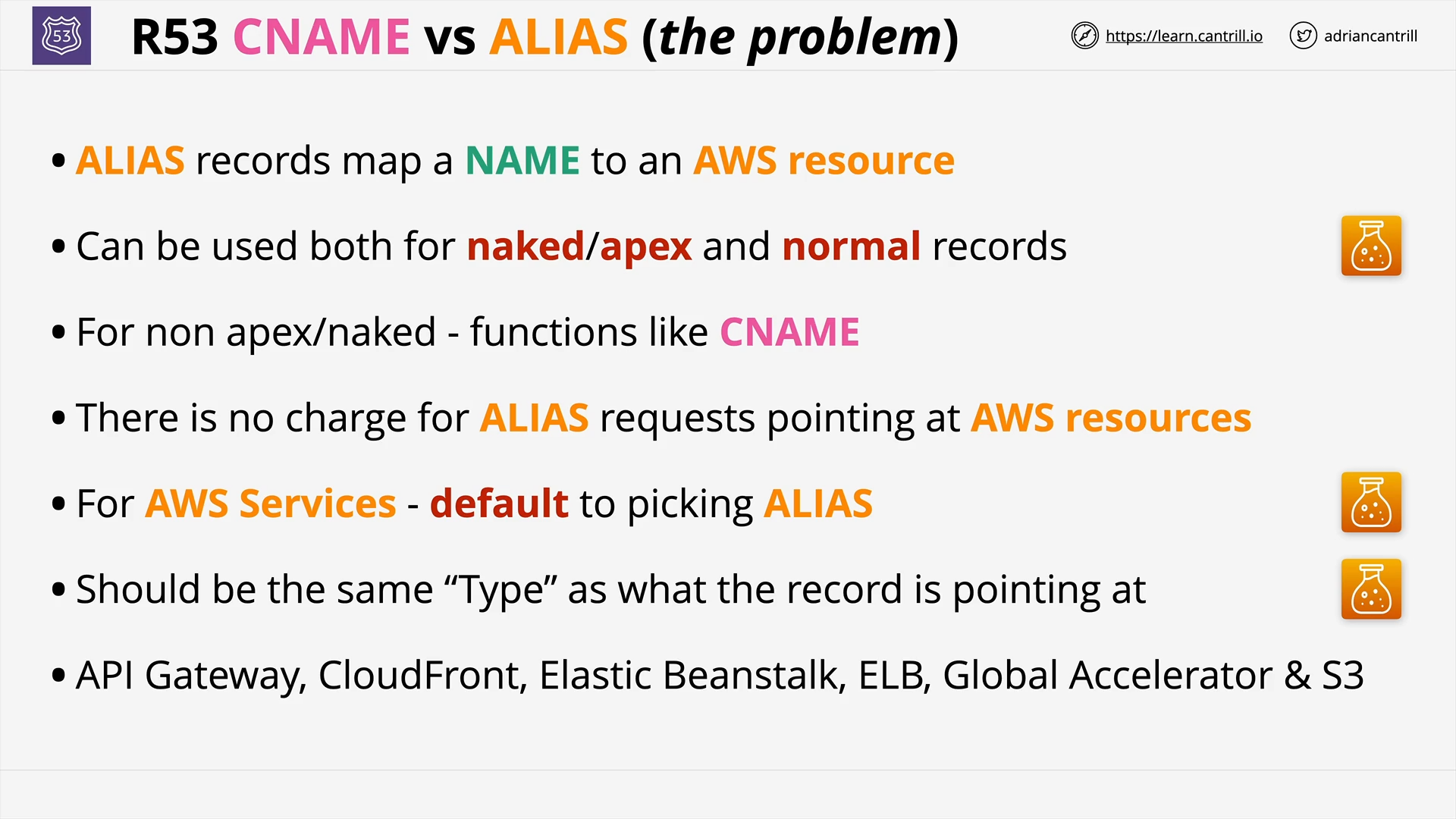 R53
R53 alias record
what is `alias` record?
Amazon Route 53 alias record is a Route 53–specific extension to DNS functionality.
what does r53 `alias` record do?
R53 alias record:
-
route traffic to selected AWS resources, such as
- CloudFront distributions
- Amazon S3 buckets.
-
route traffic from one record in a hosted zone to another record.
why use r53 `alias` record?
-
Unlike a CNAME record, we can create an R53
aliasrecord at the top node of a DNS namespace, also known as thezone apex.e.g. DNS name
example.com:- We can’t create a
CNAMErecord forexample.com - But we can create a R53
aliasrecord forexample.comthat routes traffic towww.example.com.
- We can’t create a
-
We can use a R53
aliasrecord to route traffic to many AWS resources.Many AWS resources don’t have a static IP address. They only have a DNS name, e.g.
lb1-1234.us-east-1.elb.amazonaws.comWith R53
aliasrecord, we can route directly traffic to these DNS name, without allocating an additional Elastic IP address.
Simple Routing (2:17)
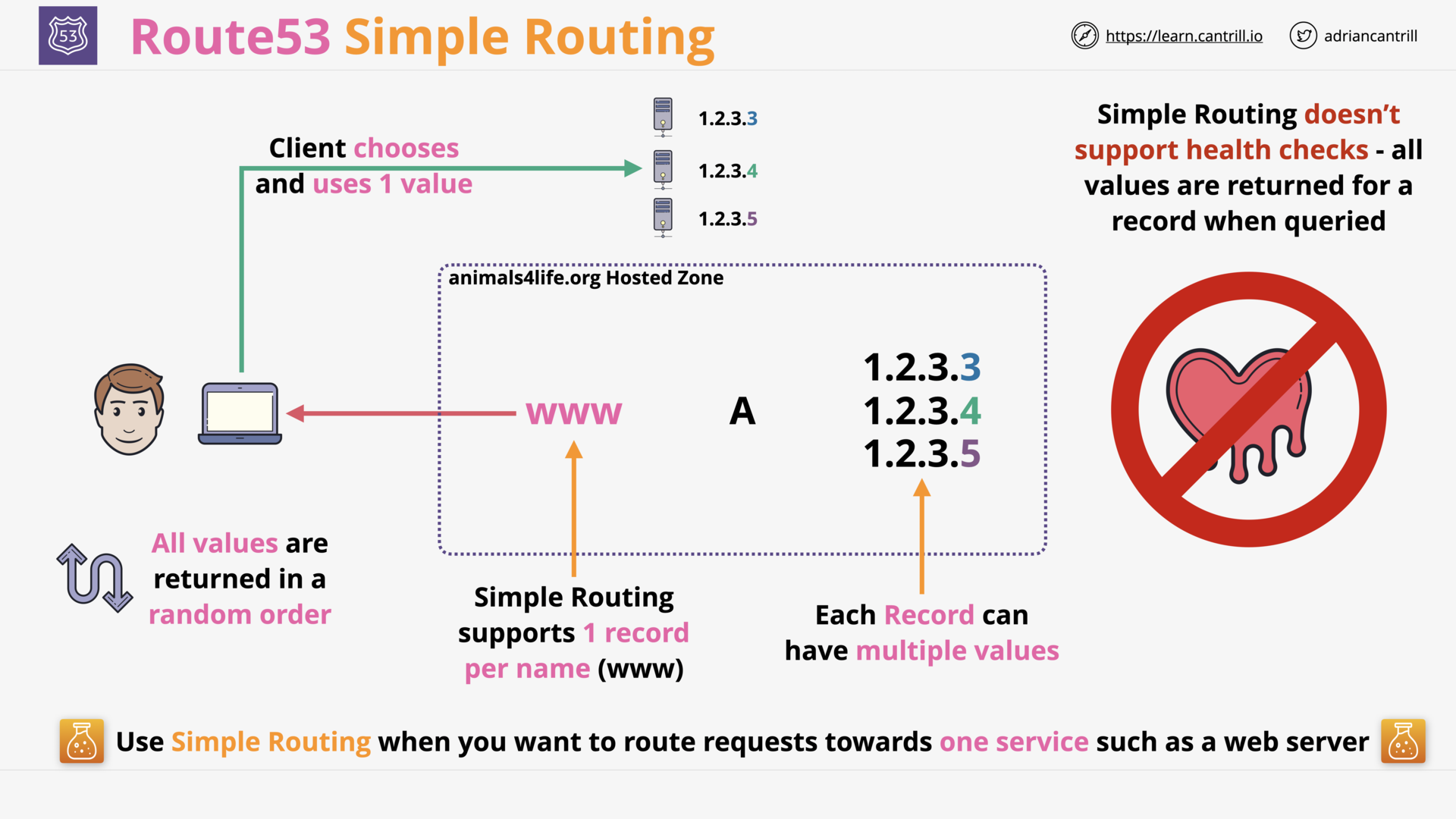
what is r53 `simple routing`?
Routing traffic to a single resource, for example, to a web server for your website.
what is the drawback of r53 `simple routing`?
Simple Routing doesn’t support health check.
R53 Health Checks (12:41)
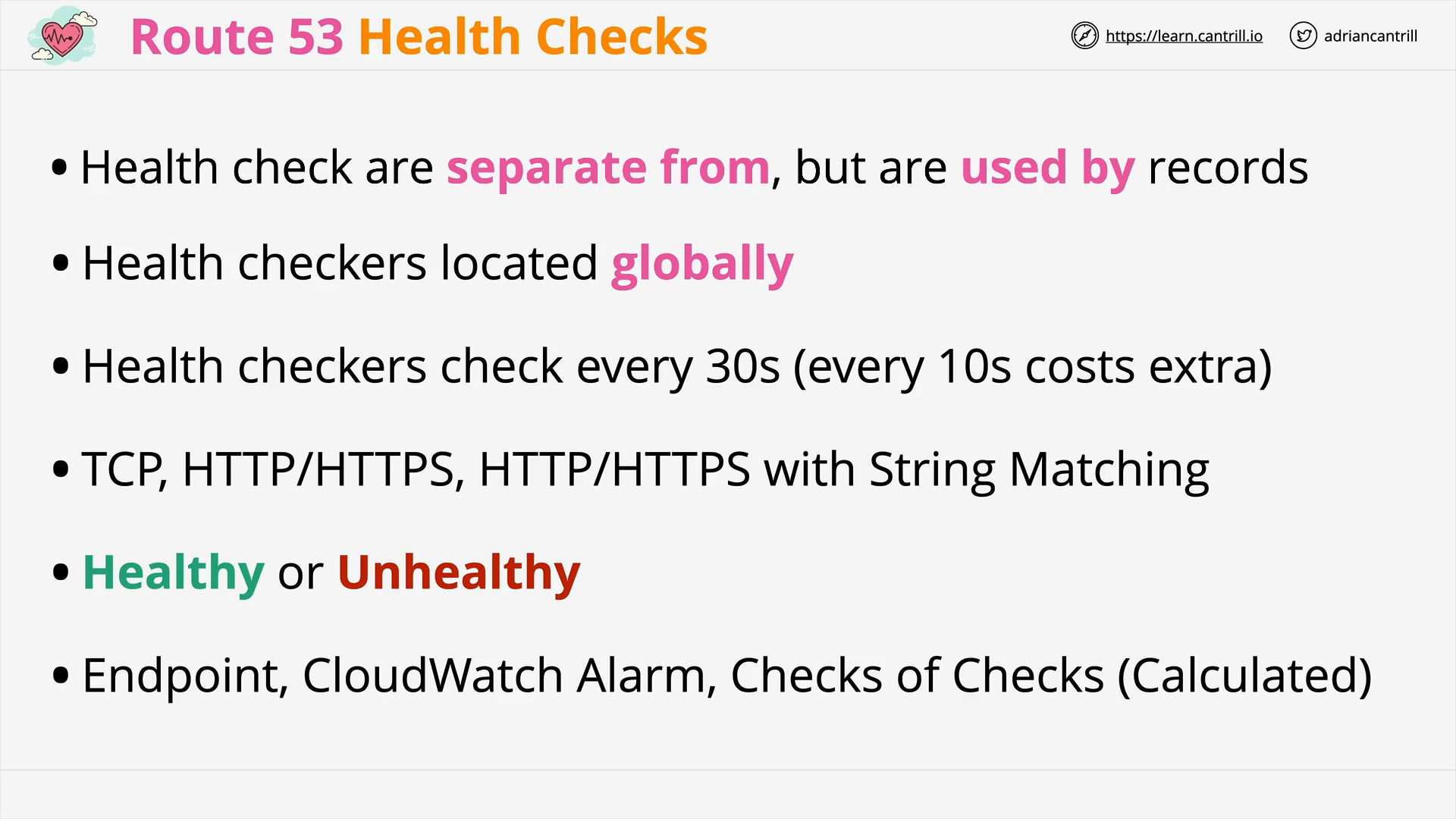 R53 Health Check - Overview
R53 Health Check - Overview
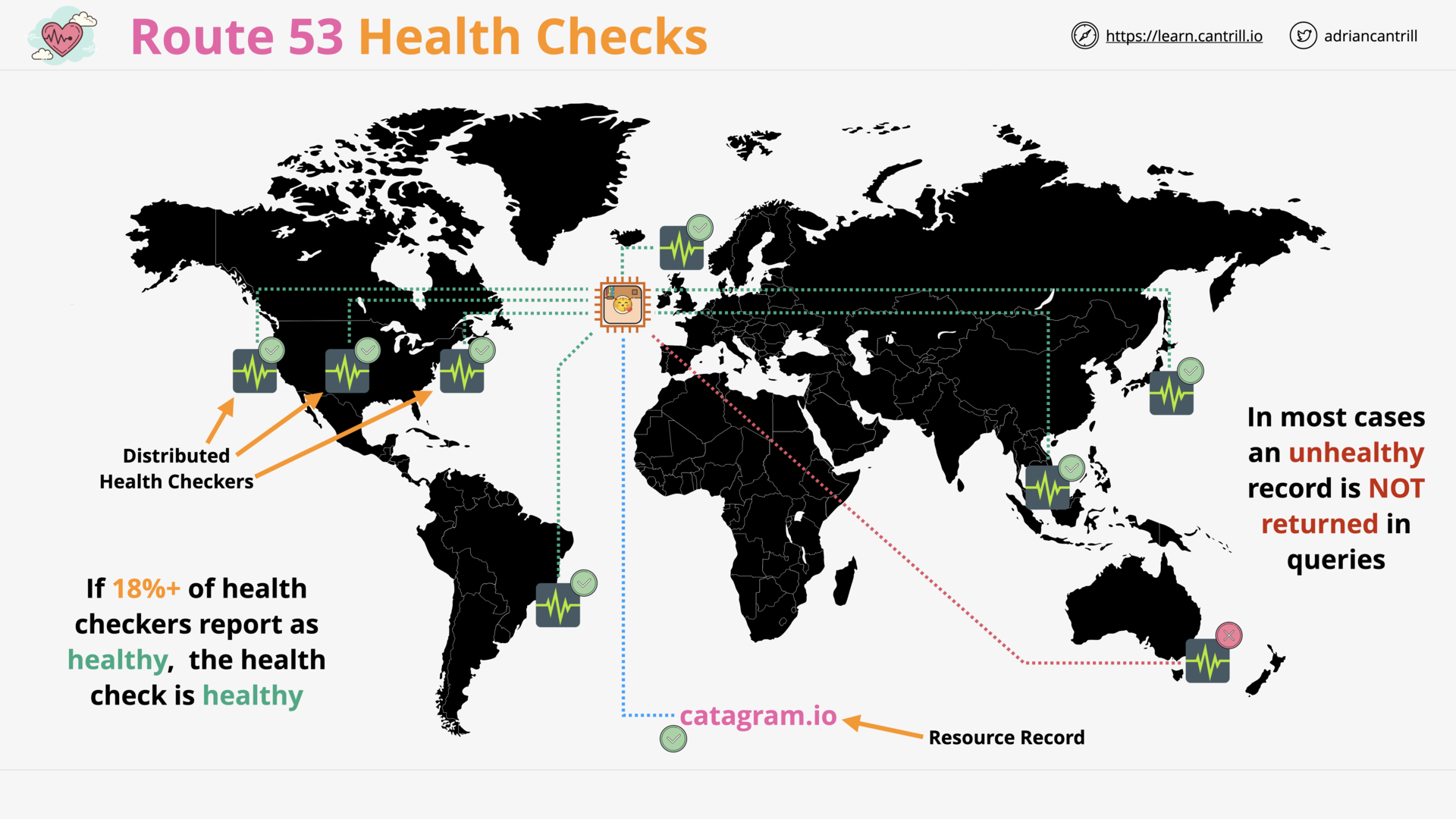 R53 Distributed Health Checkers
R53 Distributed Health Checkers
Failover Routing (1:53)
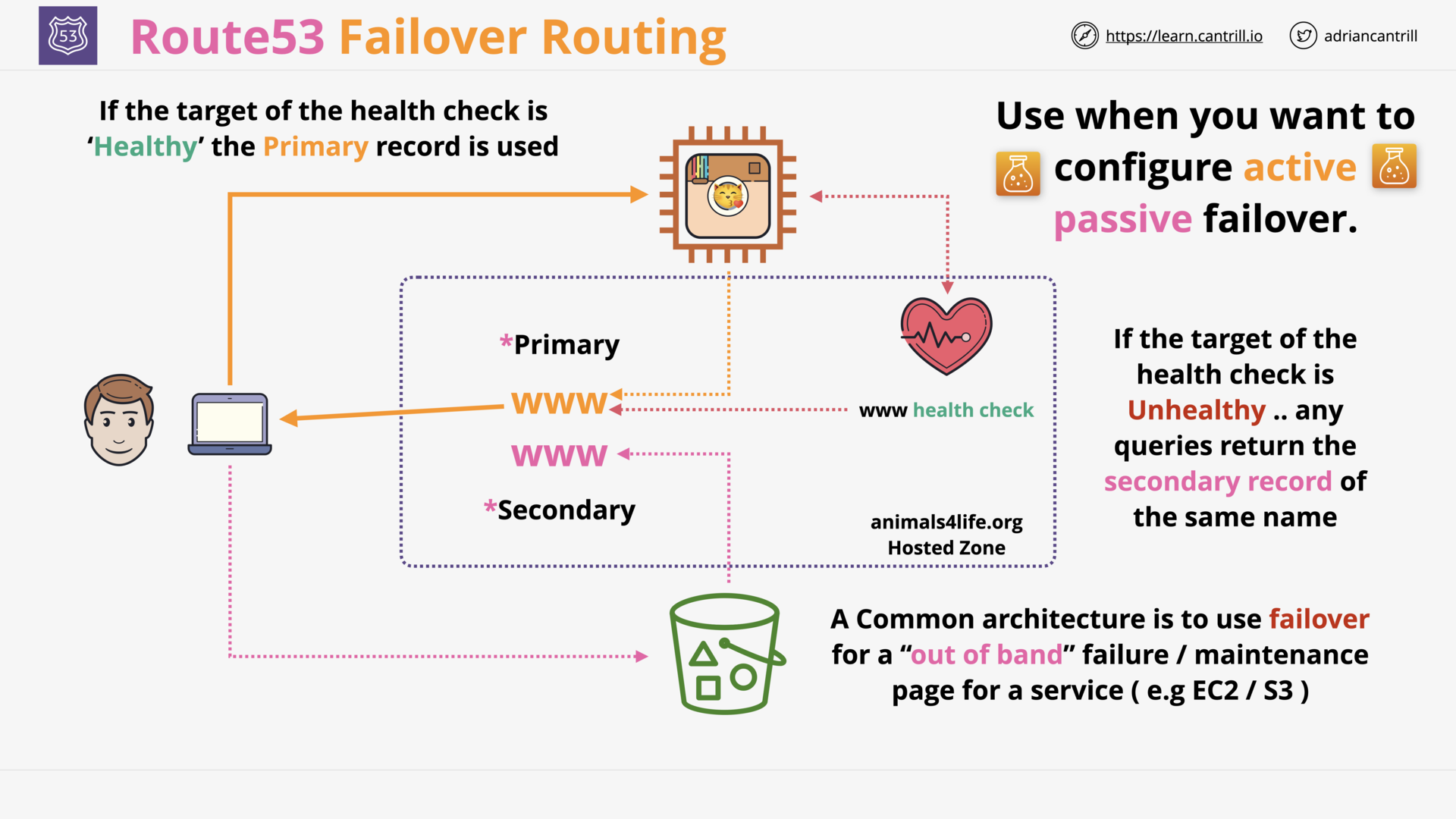 R53 Failover Routing
R53 Failover Routing
what is `failover routing`?
Routing traffic
- to a resource when the resource is healthy
- or to a different resource when the first resource is unhealthy
[DEMO] Using R53 and Failover Routing-PART1 (16:41)
[DEMO] Using R53 and Failover Routing-PART2 (6:28)
Multi Value Routing (2:32)
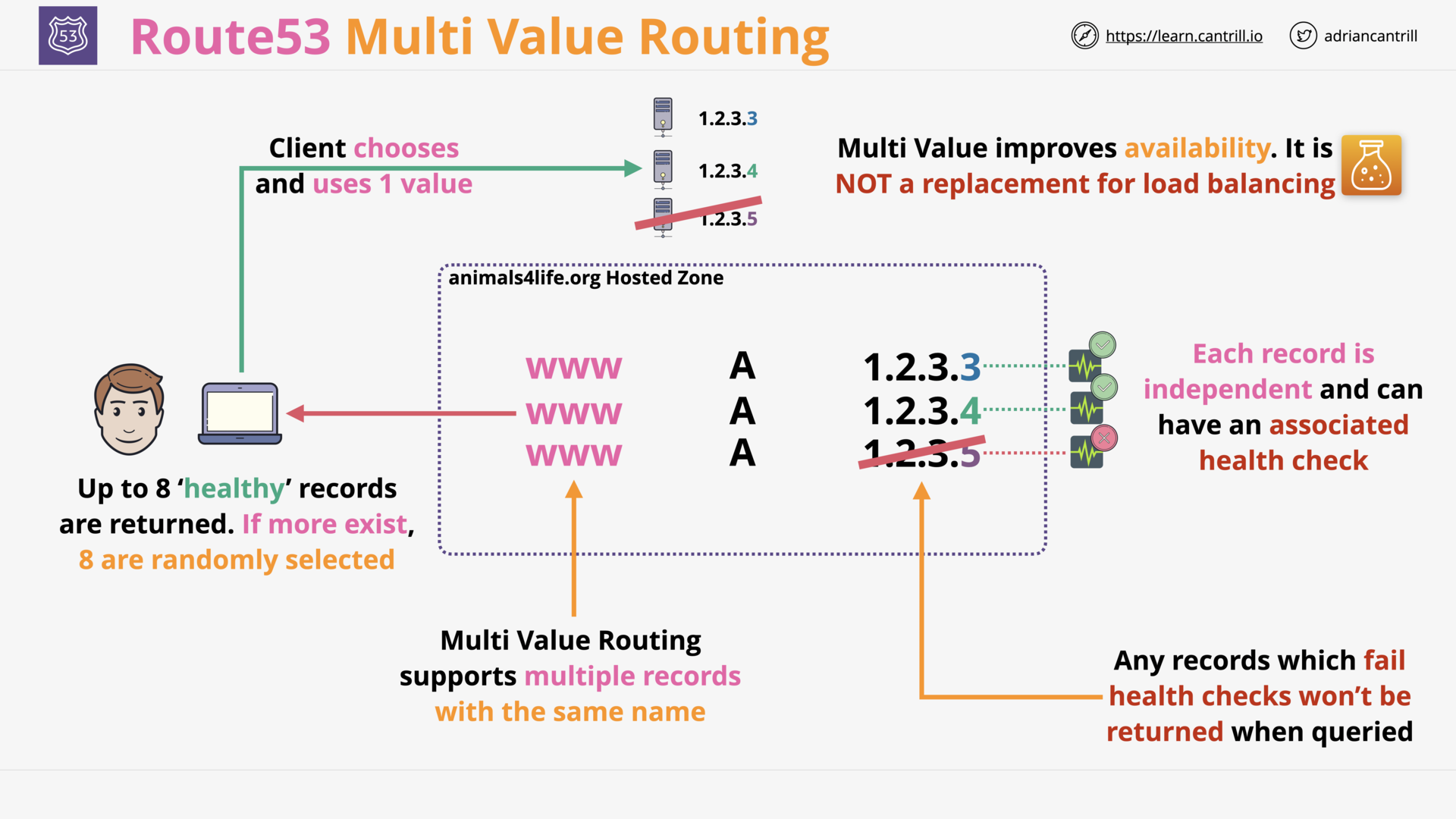 R53 Multi Value Routing
R53 Multi Value Routing
can r53 `simple routing` return multi values?
Yes.
what is the different between `simple routing` and `multi value routing`?
- With
Simple Routing, a hosted zone can have a record that have multi values. - With
Multi Value Routing, a hosted zone can have multiple records with the same name
Weighted Routing (3:24)
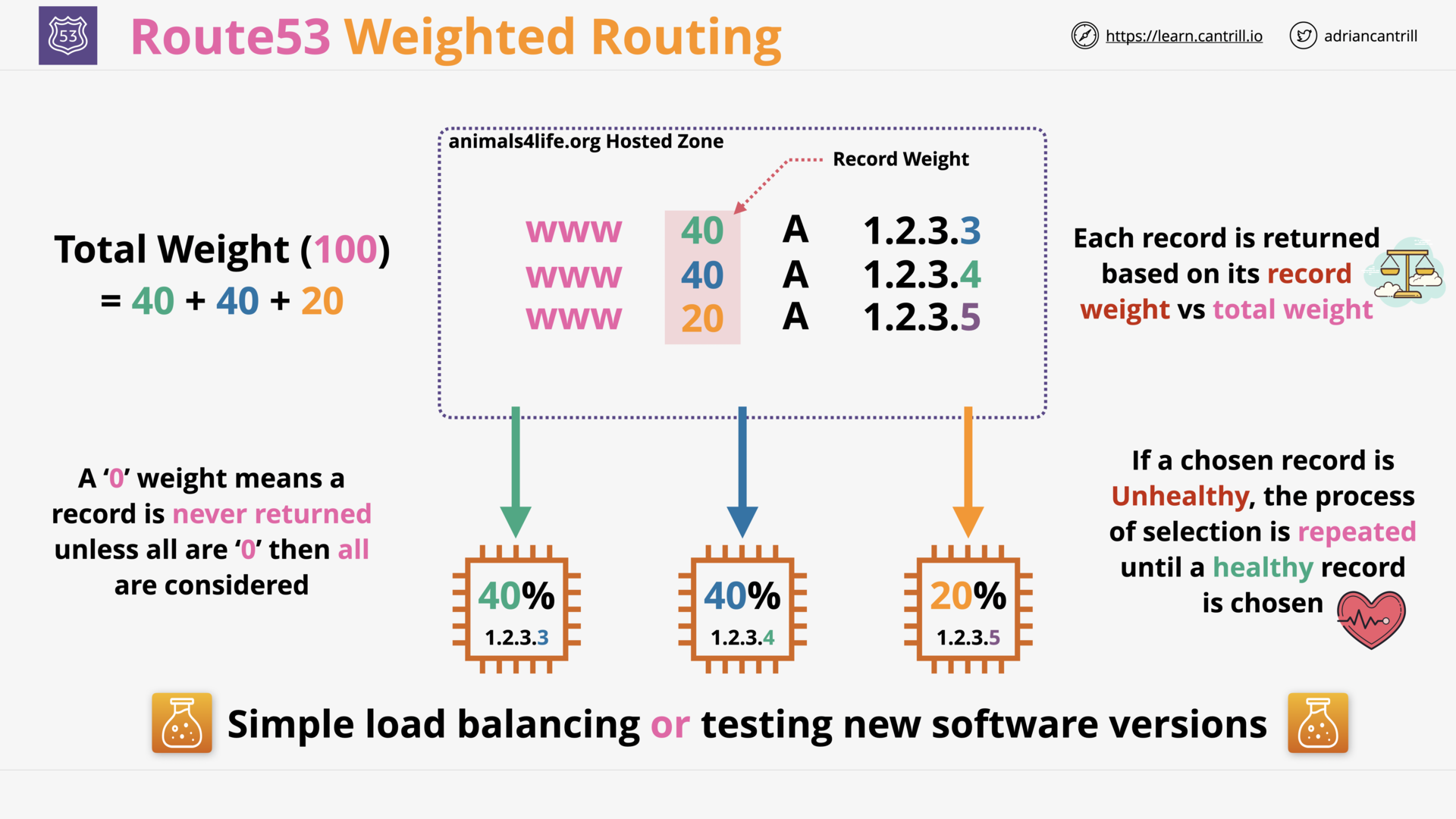 R53 Weighted Routing
R53 Weighted Routing
what is weighted routing?
Associating multiple resources with
- a single domain name (example.com)
- or subdomain name (acme.example.com) and
and choose how much traffic is routed to each resource.
Latency-based Routing (2:44)
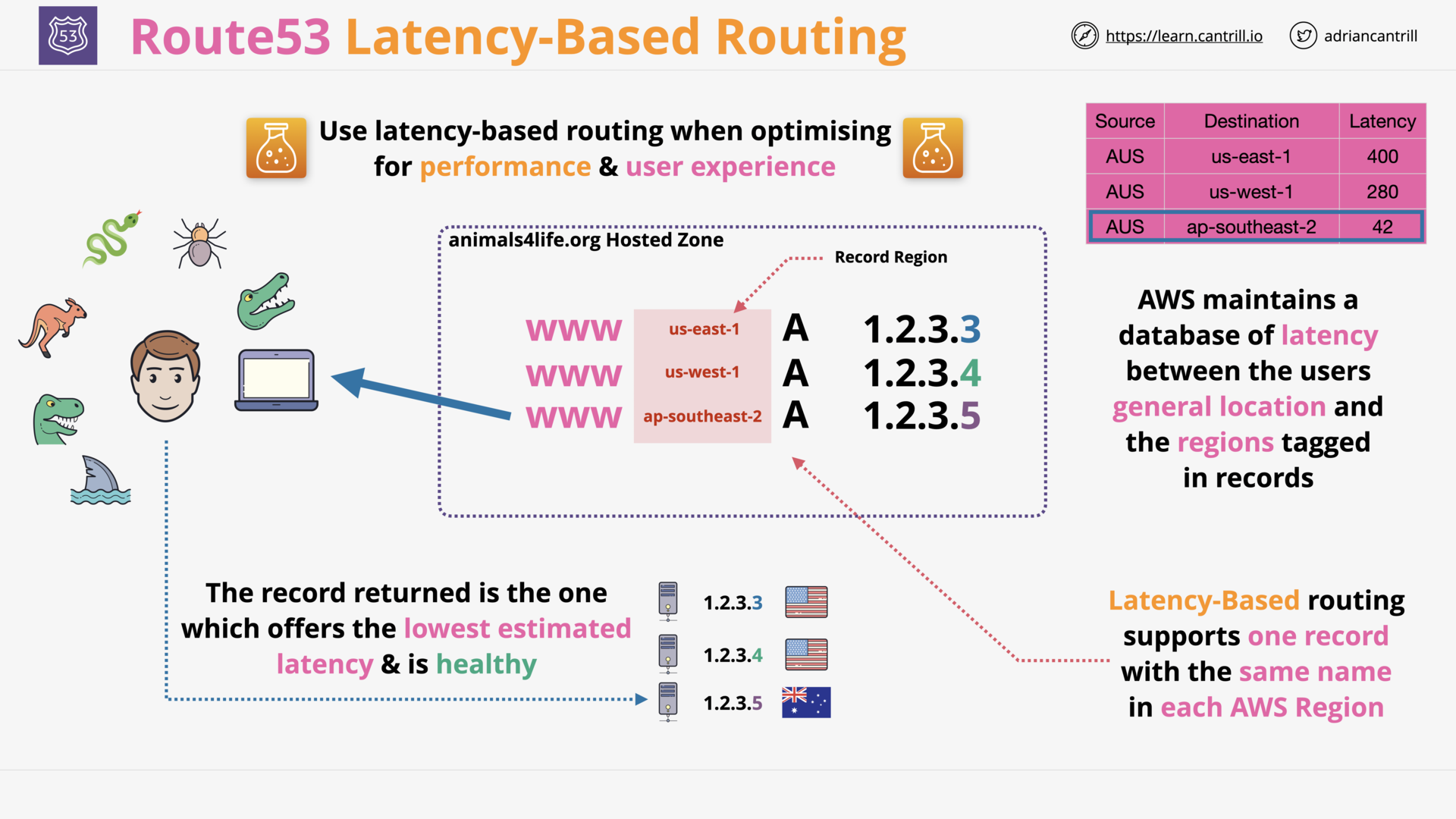
what is latency-based routing?
Routing traffic to the AWS Region that provides the lowest latency.
Geolocation Routing (5:02)
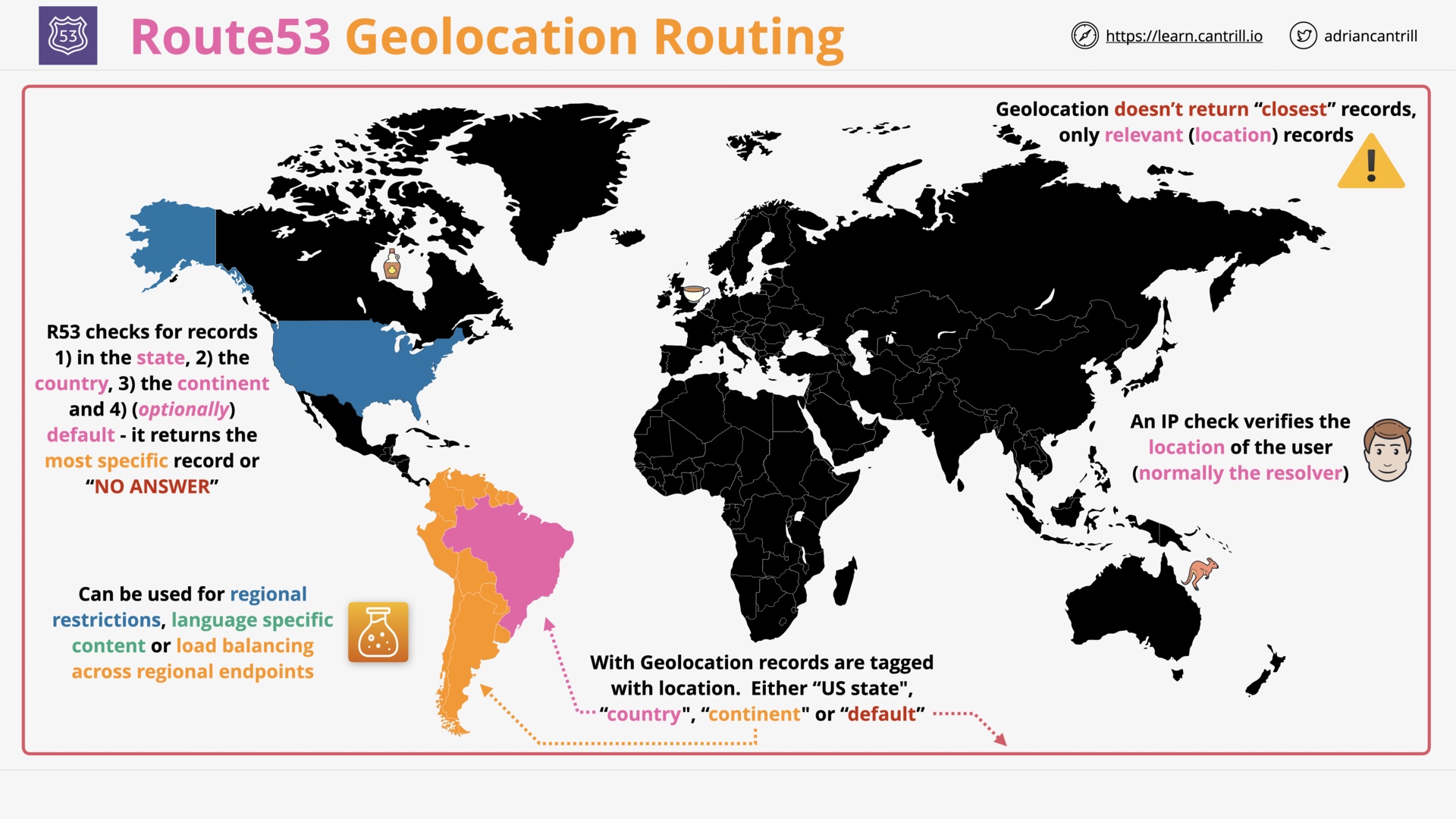
what is geolocation routing?
Routing traffic based on the geographic location of users:
- to localize content
- to restrict distribution of content
- …
Geoproximity Routing (4:50)
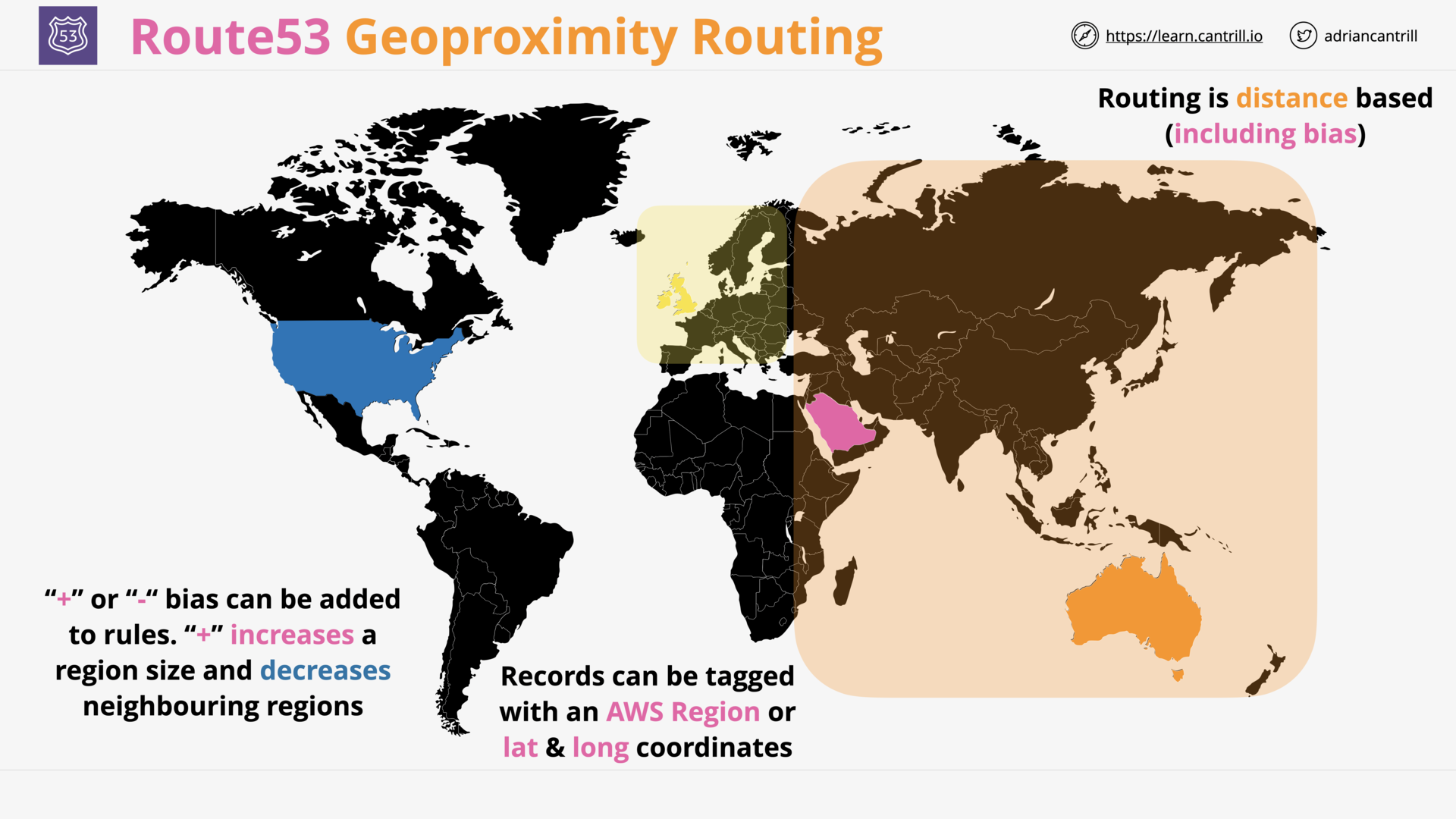
what is geoproximity routing?
Routing traffic based on the geographic location of users and our resources.
A ‘bias’ can be applied to expand/shrink the size of the geographic region.
compare `latency-based routing` - `geolocation routing` - `geoproximity routing`?
R53 Interoperability (11:50)
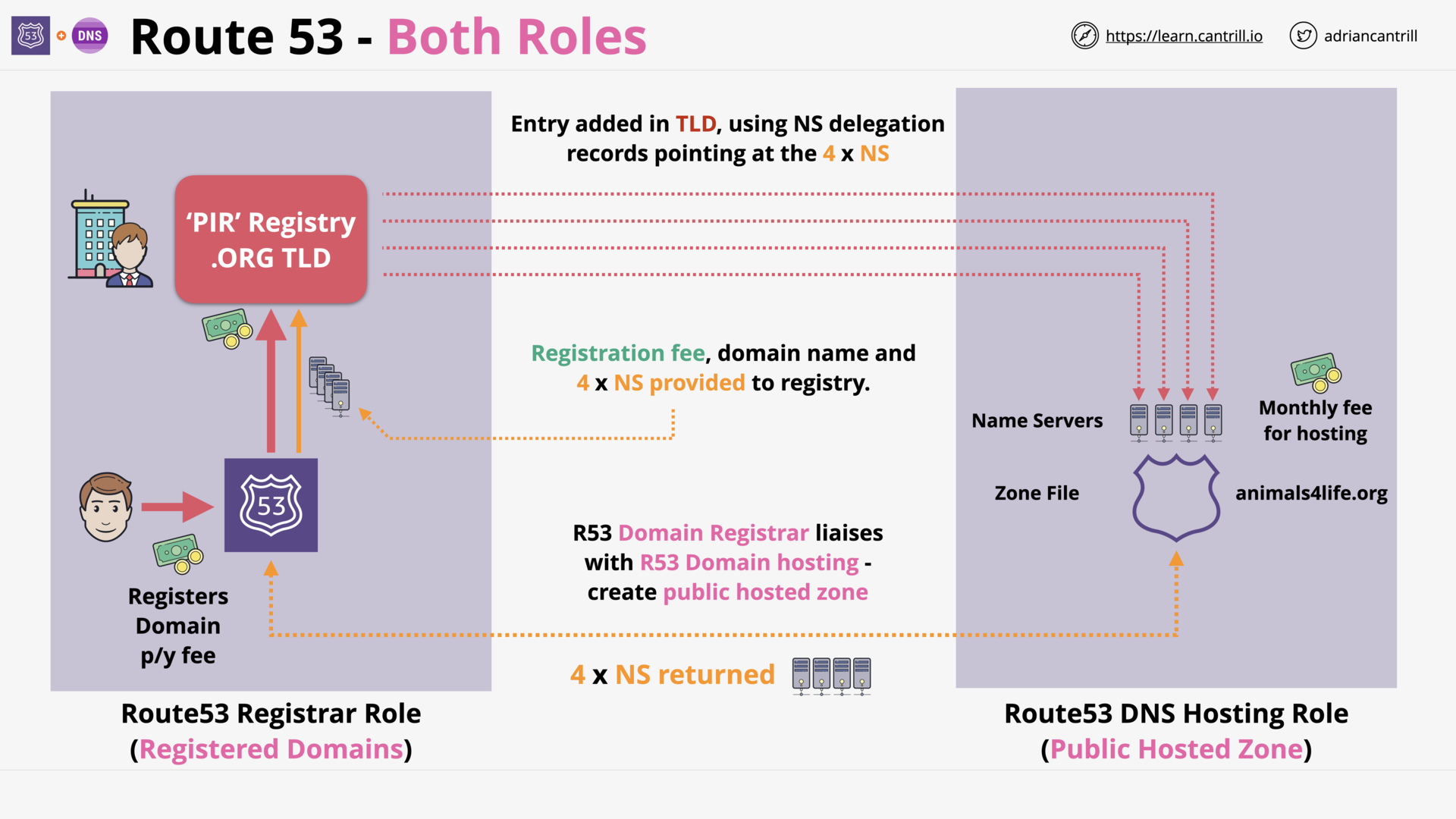 Route 53: Registrar + Hosting
Route 53: Registrar + Hosting
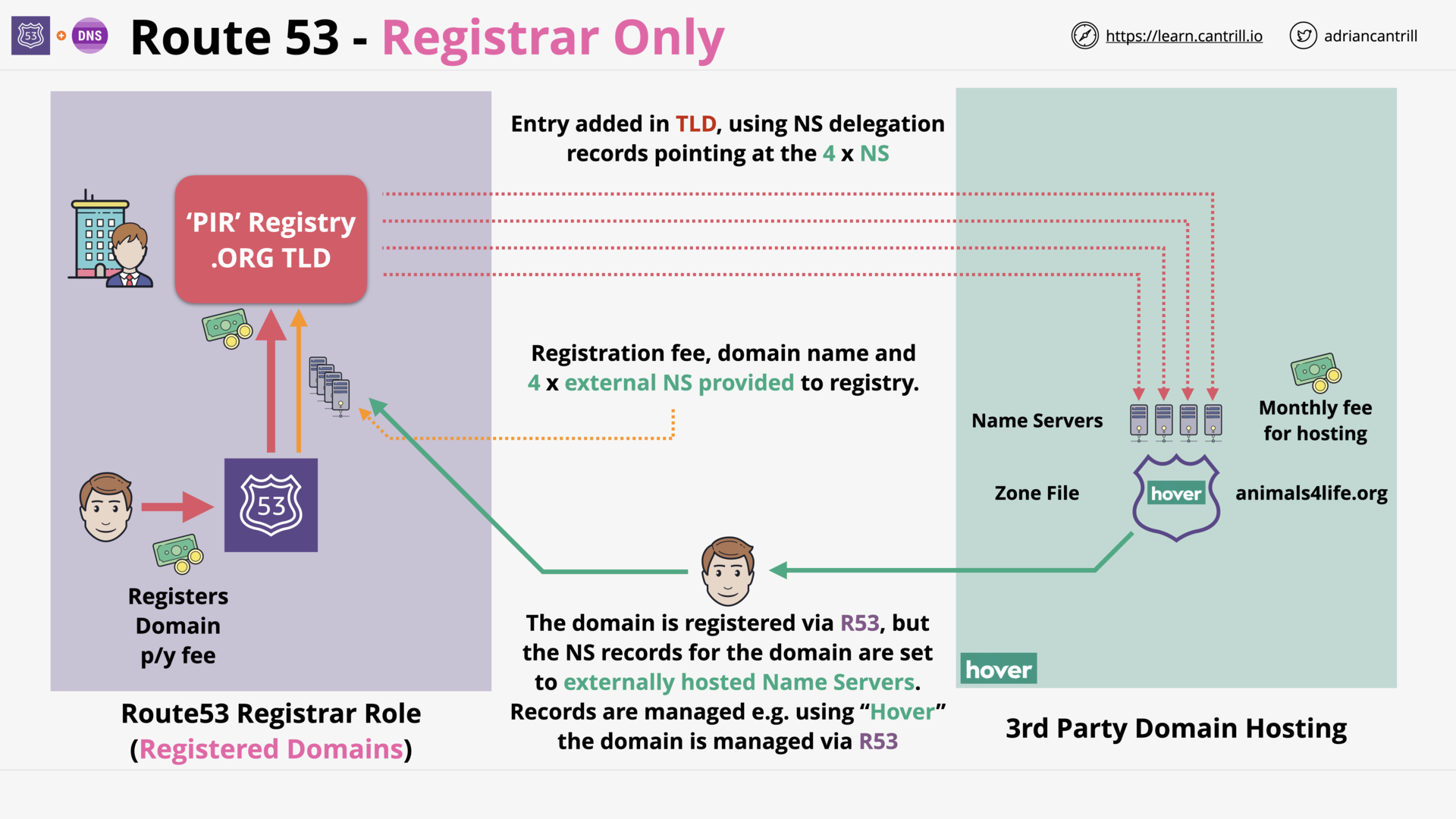 Route 53: Registrar Only
Route 53: Registrar Only
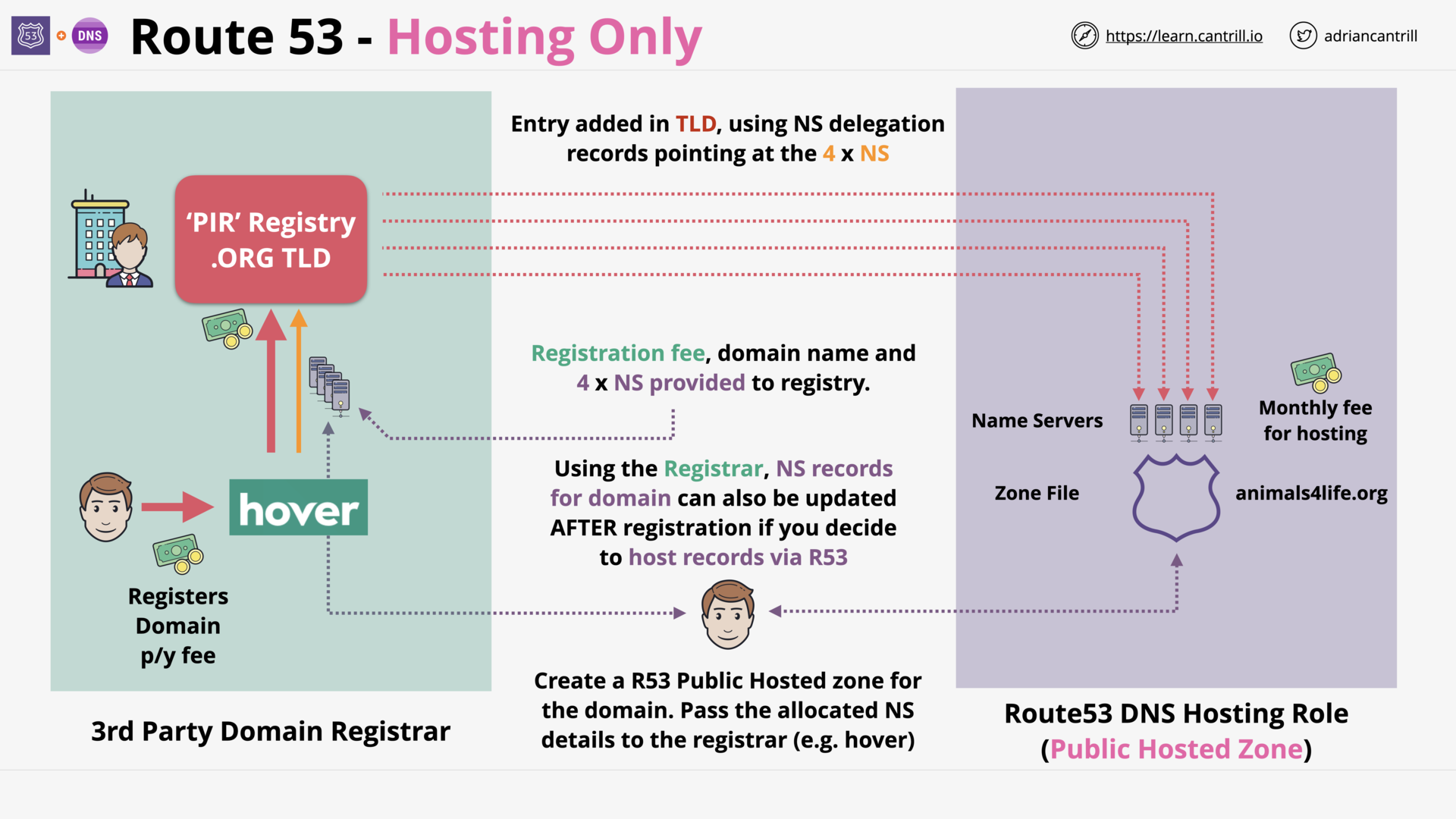 Route 53: Hosting Only
Route 53: Hosting Only
[DEMO] Implementing DNSSEC using Route53 (17:43)
Route53 Section Quiz
Domain Registration and Hosting
sequenceDiagram
actor Ryan
participant Sally
participant Ron
participant Henry
Ryan->>Sally: Buy ryan-corp.org
Sally->>Ron: Give me ryan-corp.org
Ron->>Sally: Here is your ryan-corp.org
Sally->>Henry: Can you host the zone for ryan-corp.org on your NS?
Henry->>Sally: OK. Here are the domains for the NS?
Sally->>Ron: This is the NS for my ryan-corp.org?
Ron->>Sally: OK. If someone want to go to ryan-corp.org. I'll give them these NS.
RELATIONAL DATABASE SERVICE (RDS)
Database Refresher & MODELS - PART1 (8:51), PART2 (14:45)
 SQL vs NoSQL
SQL vs NoSQL
what is sql?
what is nosql?
Relational (SQL) Database
 Relational Database, e.g. MySQL, Postgres
Relational Database, e.g. MySQL, Postgres
Non-Relational (NoSQL) Database
 Key-Value Database, e.g. Redis, Google Bigtable, Amazon DynamoDB
Key-Value Database, e.g. Redis, Google Bigtable, Amazon DynamoDB
 Wide Column Store, e.g. Google Bigtable, Amazon DynamoDB
Wide Column Store, e.g. Google Bigtable, Amazon DynamoDB
 Document Database, e.g. MongoDB, Amazon DocumentDB
Document Database, e.g. MongoDB, Amazon DocumentDB
 Column Database, e.g. BigQuery, Amazon Redshift
Column Database, e.g. BigQuery, Amazon Redshift
 Graph Database, e.g. neo4j, Amazon Neptune
Graph Database, e.g. neo4j, Amazon Neptune
ACID vs BASE (11:02)
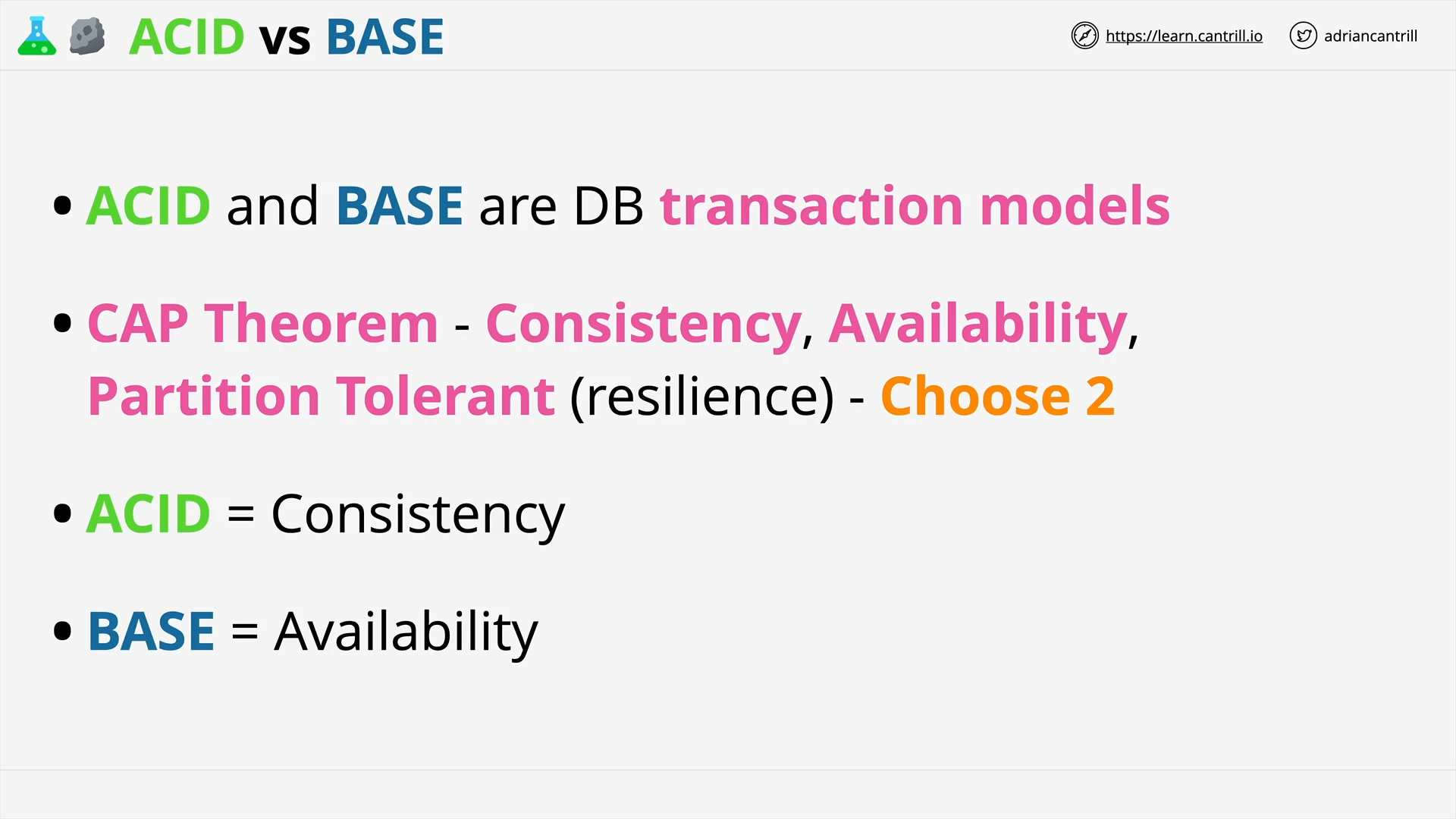 CAP Theorem
CAP Theorem
what is cap theorem?
The CAP theorem states that any networked shared-data system can have at most two of three desirable properties:
- consistency (C) equivalent to having a single up-to-date copy of the data (linearizable);
- high availability (A) of that data (system always accepts updates);
- and tolerance to network partitions (P)
Ref:
 ACID
ACID
 BASE
BASE
Databases on EC2 (13:08)
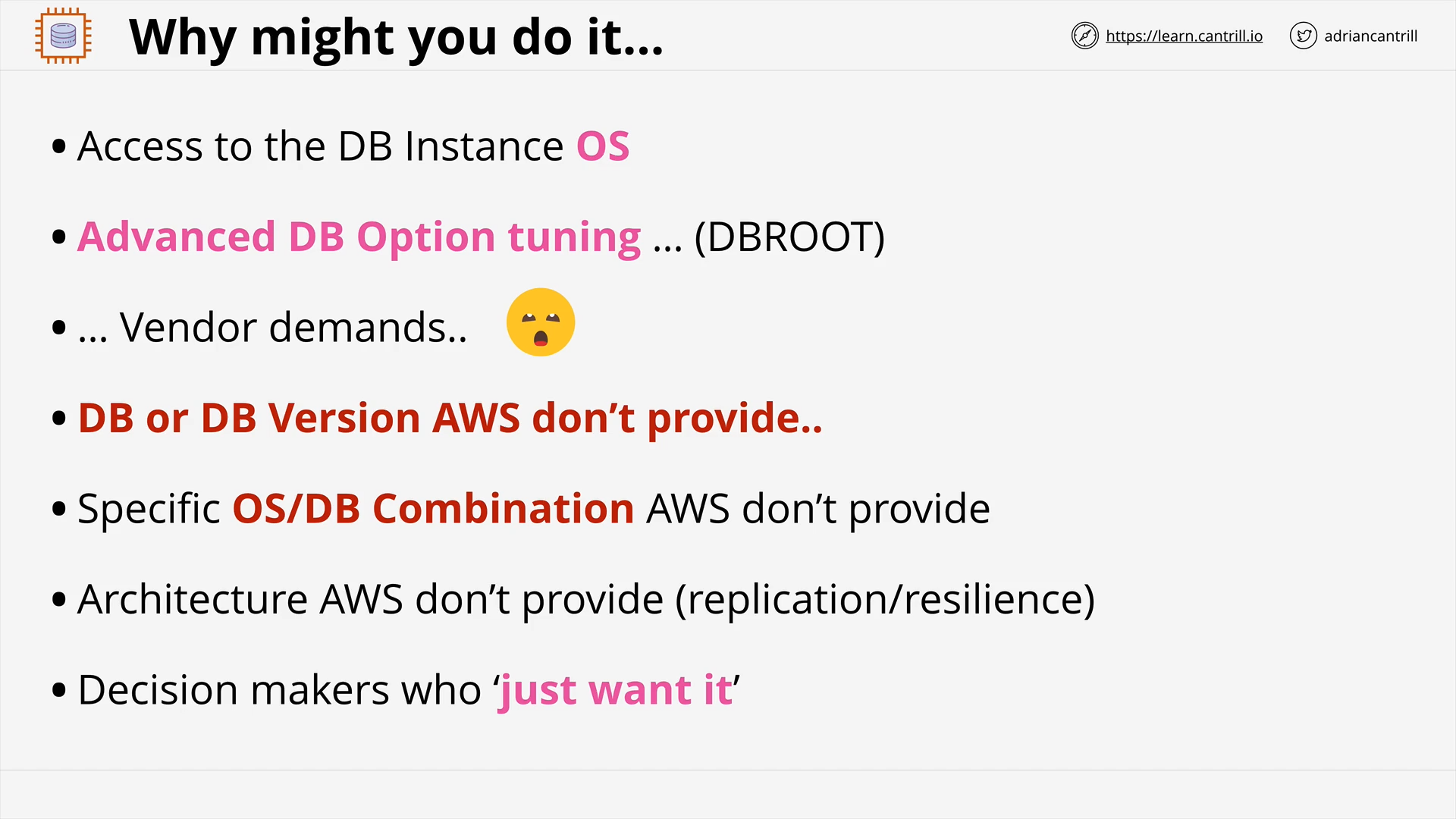 Why?
Why?
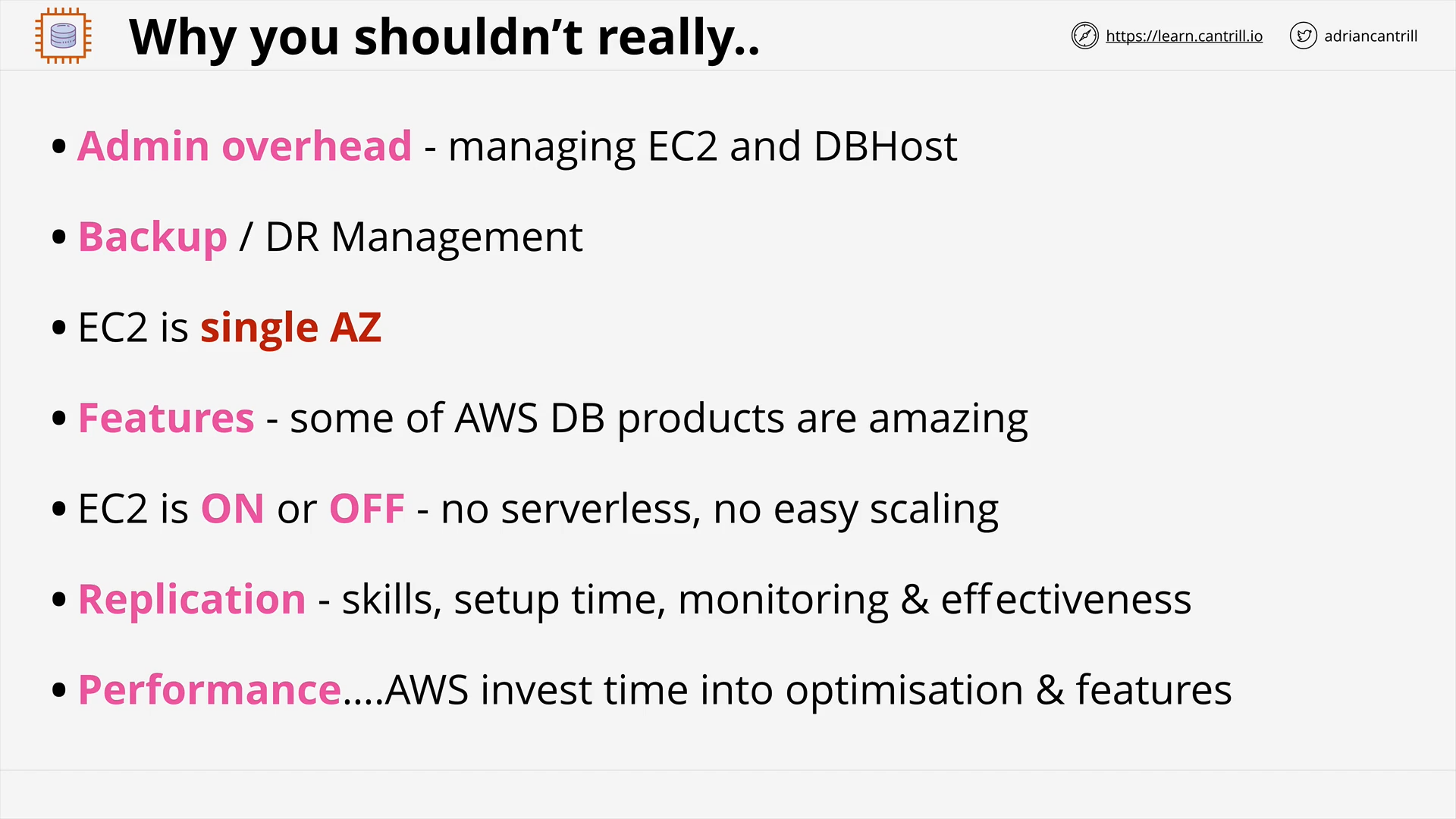 Why not?
Why not?
 Databases on EC2 - Example
Databases on EC2 - Example
[DEMO] Splitting Wordpress Monolith => APP & DB (18:01)
Relational Database Service (RDS) Architecture (11:39)
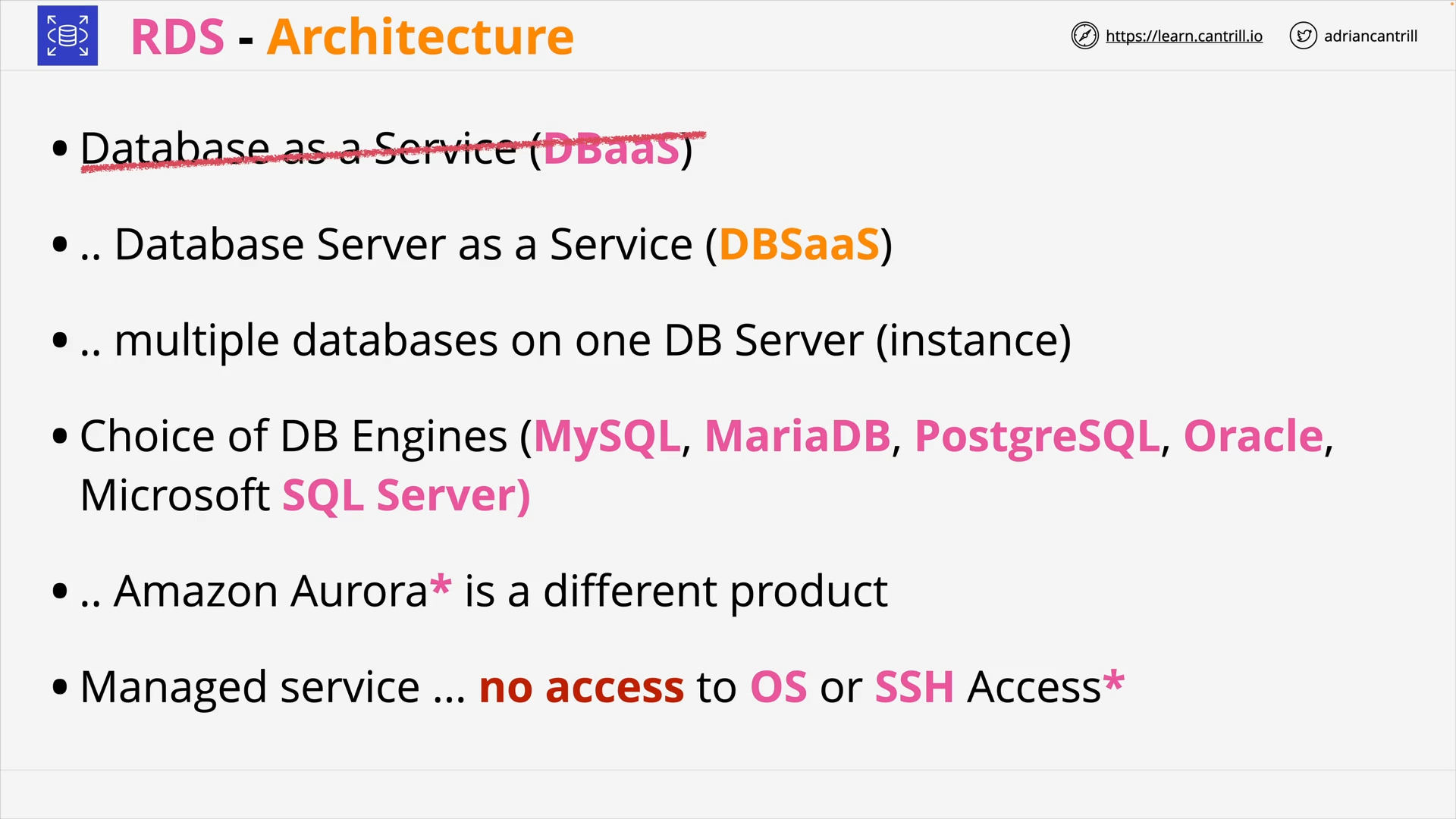 RDS - DBSaaS
RDS - DBSaaS
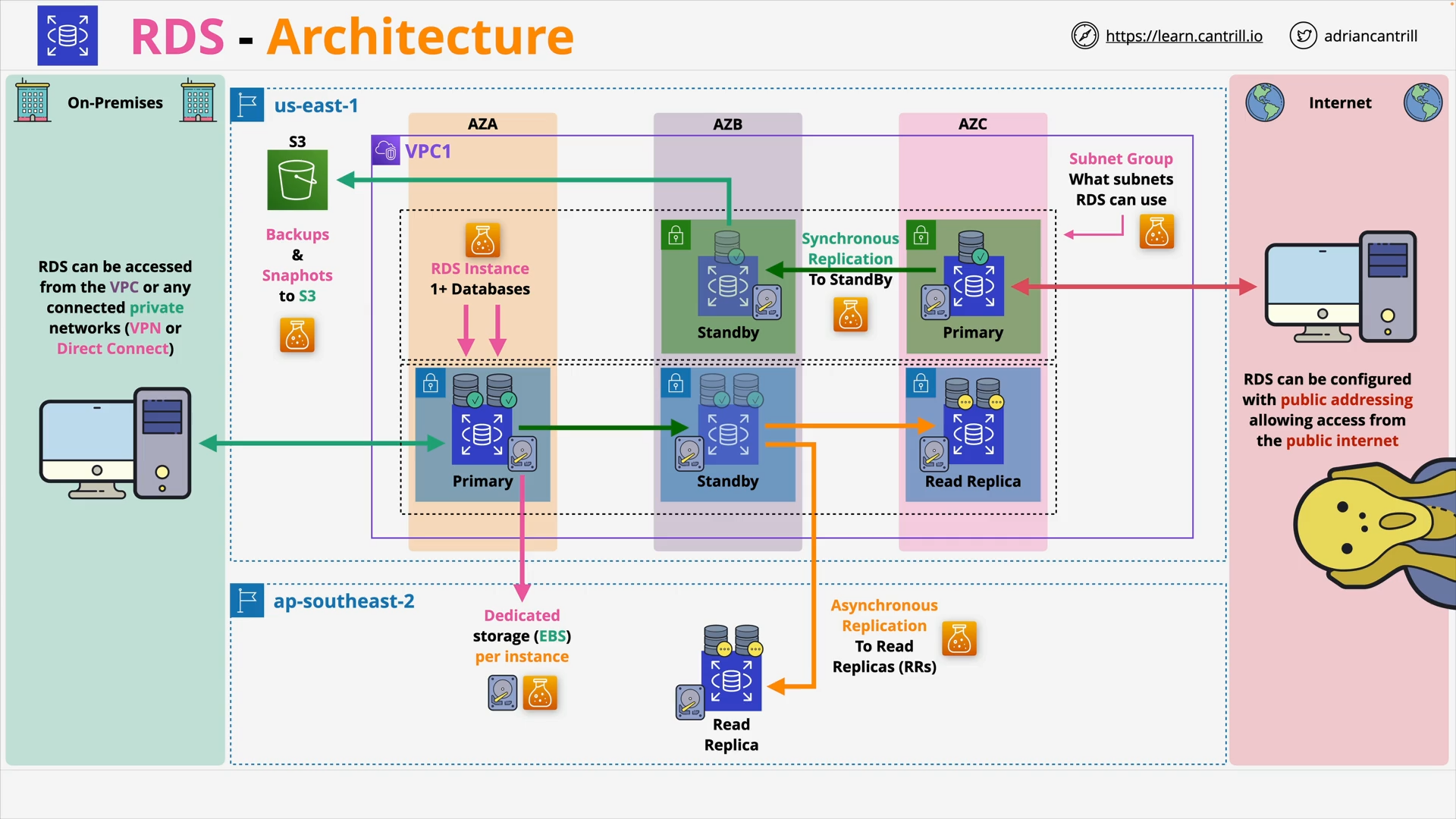 RDS - Architecture
RDS - Architecture
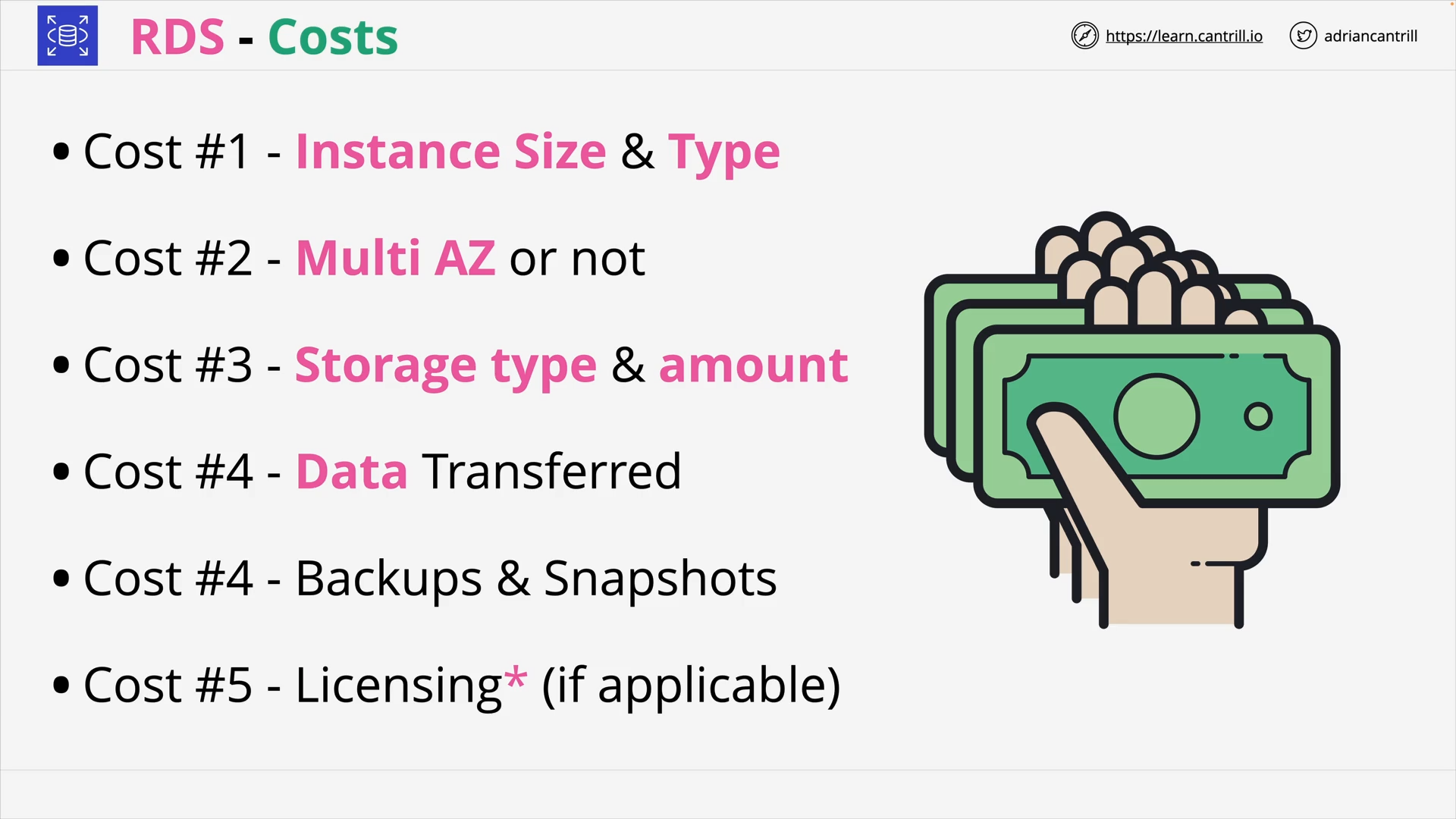 RDS - Costs
RDS - Costs
[DEMO] Migrating EC2 DB into RDS - PART1 (18:20)


[DEMO] Migrating EC2 DB into RDS - PART2 (12:58)
Relational Database Service (RDS) MultiAZ - Instance and Cluster (11:54)
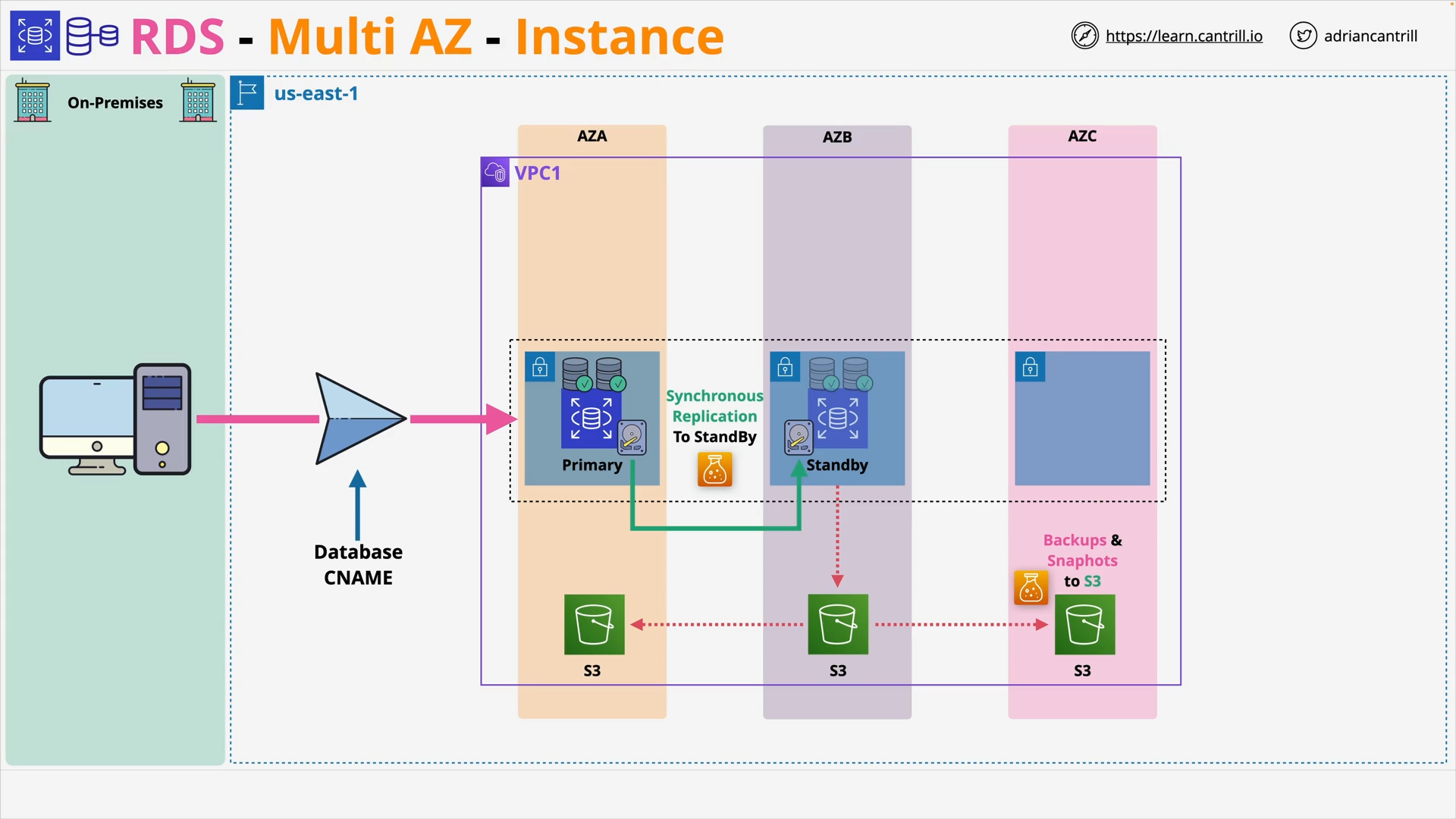 RDS - Multi AZ - Instance
RDS - Multi AZ - Instance
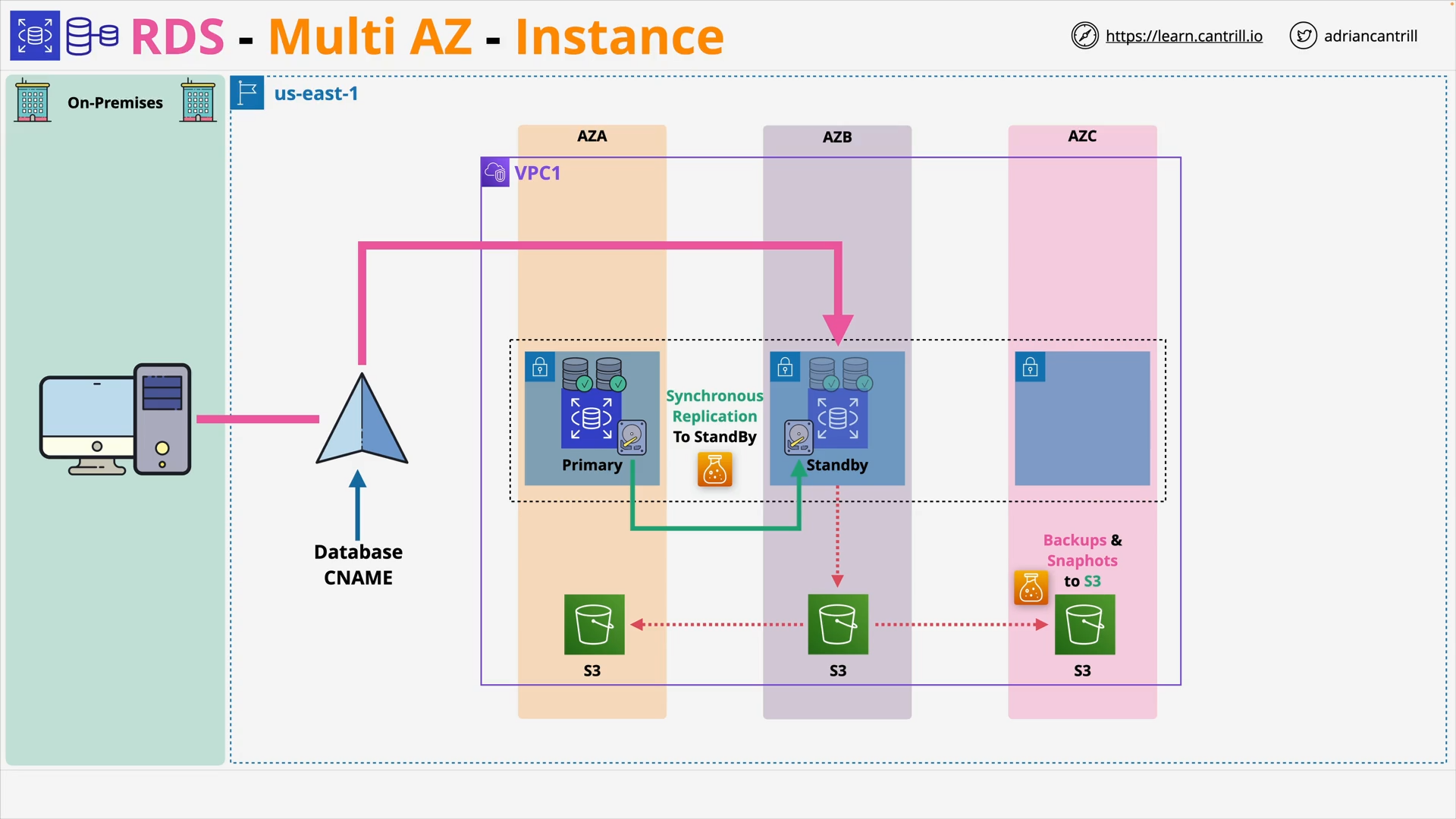 RDS - Multi AZ - Instance - Failover
RDS - Multi AZ - Instance - Failover
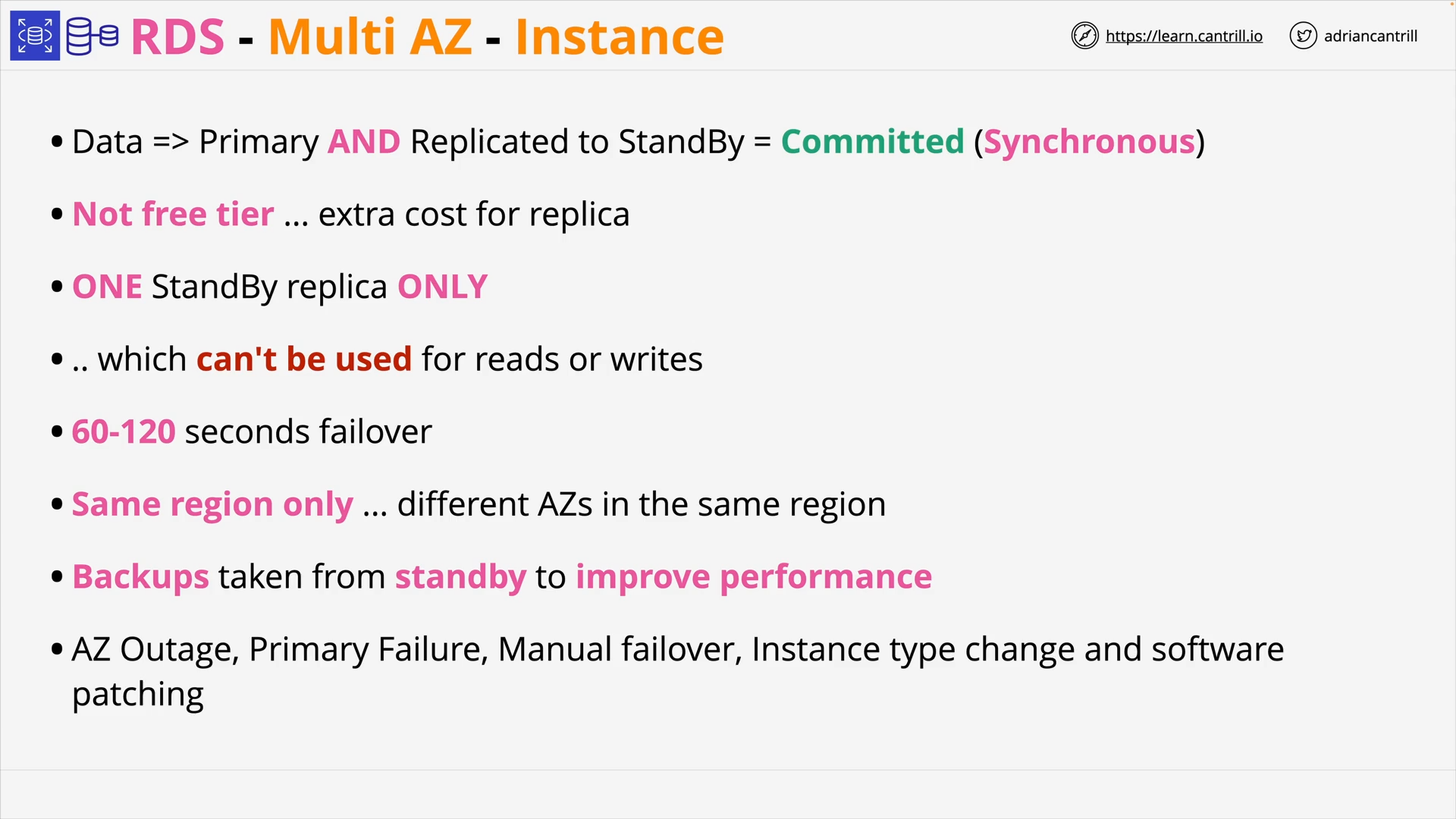 RDS - Multi AZ - Instance - Summary
RDS - Multi AZ - Instance - Summary
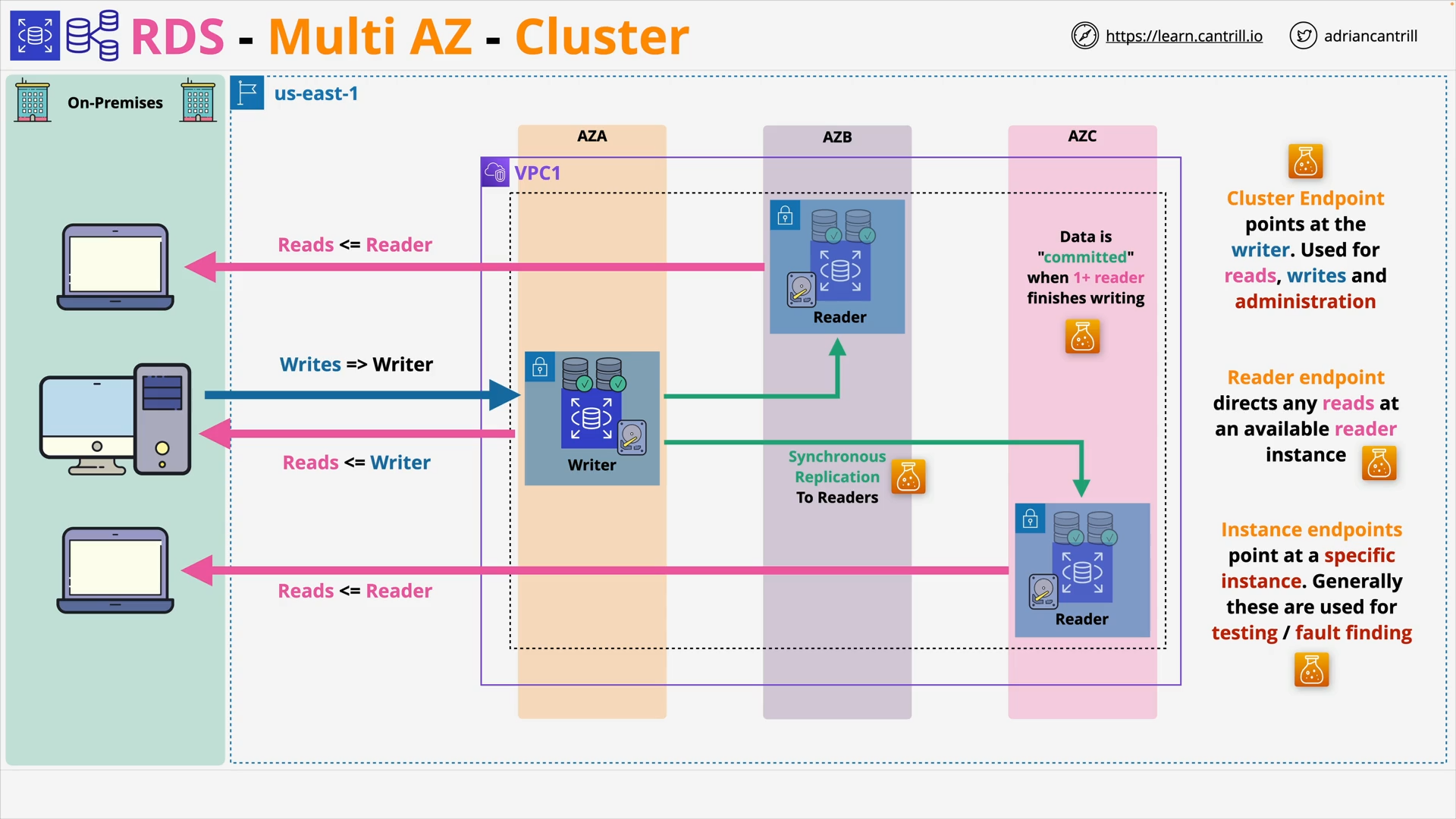 RDS - Multi AZ - Cluster - Architecture
RDS - Multi AZ - Cluster - Architecture
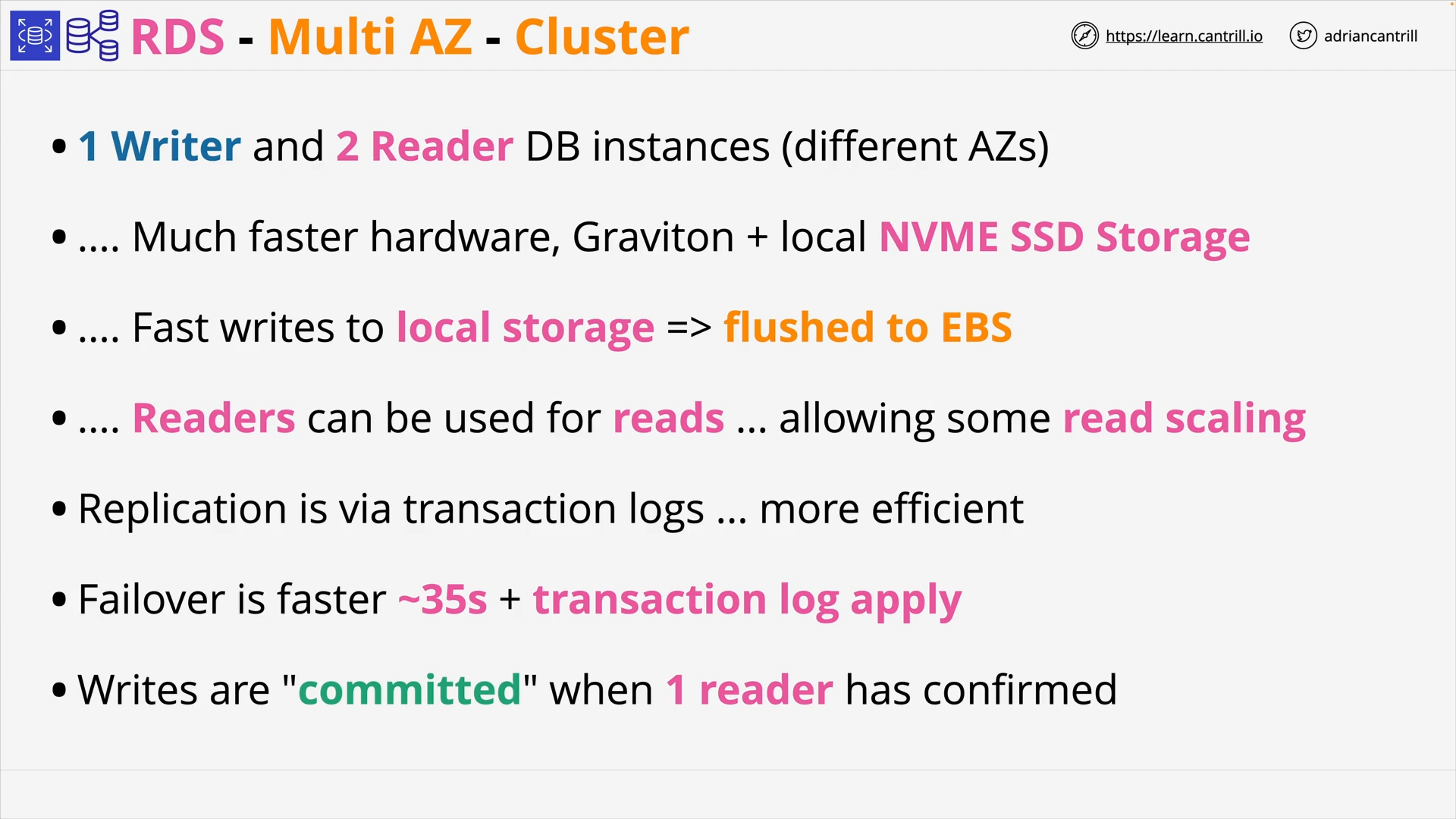 RDS - Multi AZ - Cluster - Summary
RDS - Multi AZ - Cluster - Summary
compare rds multi az instance and multi az cluster.
-
Multi AZ Instance:
- 1 Primary instance
- 1 Standby replica:
- can’t be used for reads / write 👈 not for performance scaling, only for availability
- kept in sync Synchronously with the primary instance
-
Multi AZ Cluster:
- 1 Writer DB instance
- 2 Reader DB instances:
- can be used for read 👈 limited read scaling
- kept in sync Asynchronously with the Writer instance 👈 replication lag (aka Replica lag)
RDS Automatic Backup, RDS Snapshots and Restore (8:52)
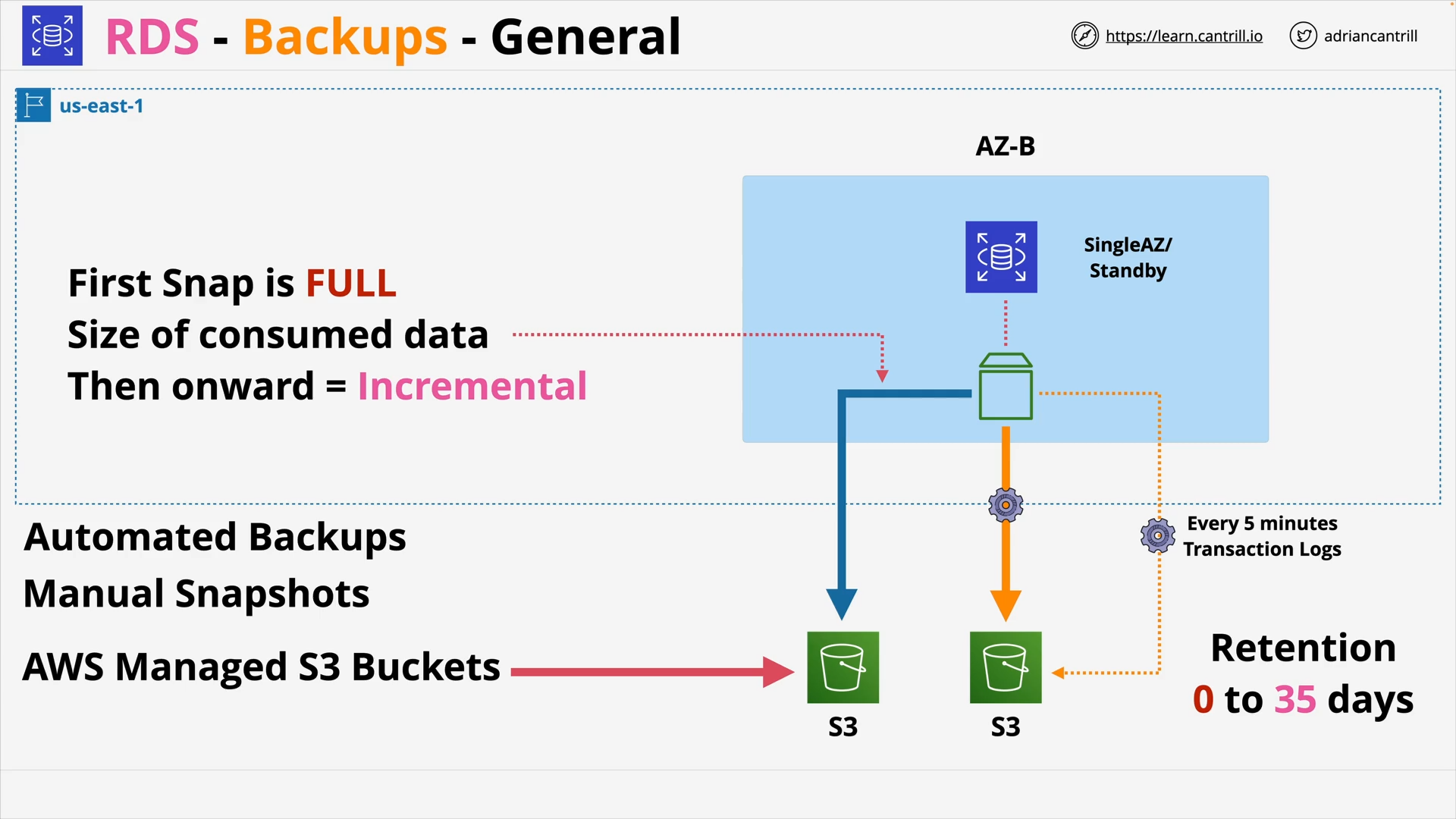 RDS Backups - General
RDS Backups - General
what kind of backups does rds support?
RDS support 2 kind of backup:
- Manually Snapshots
- Automated Backups
what is rds manually snapshot?
A backup performed manually and live past the termination of an RDS instance
what is rds automated backups?
Backups performed automatically by RDS:
- 0 to 35 days retention.
- RDS also use S3 to store transaction logs every 5 minutes.
👉 With RDS Automated Backups, RPO can be only 5 minutes. 💪
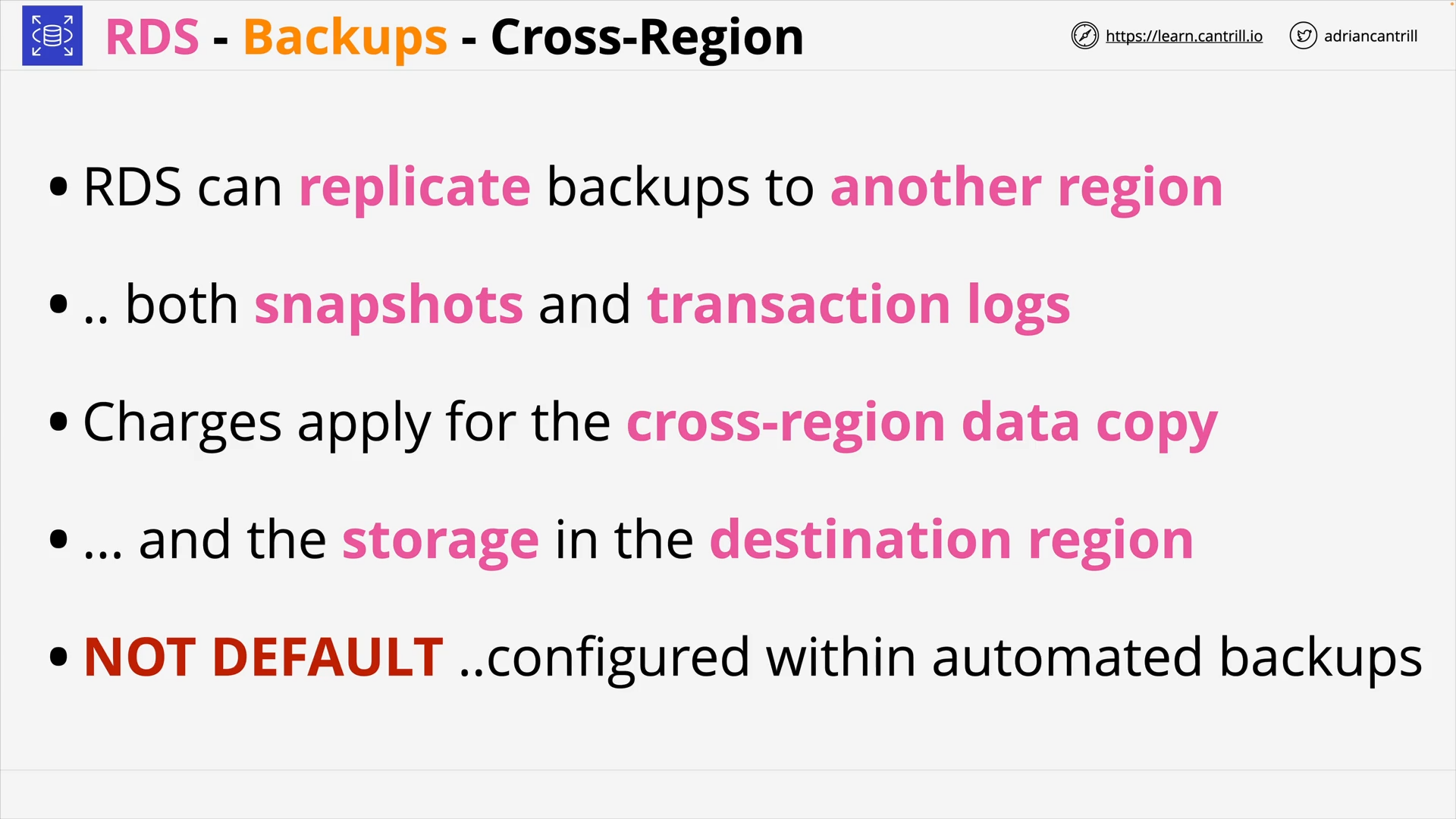 RDS Backups - Cross-Region
RDS Backups - Cross-Region
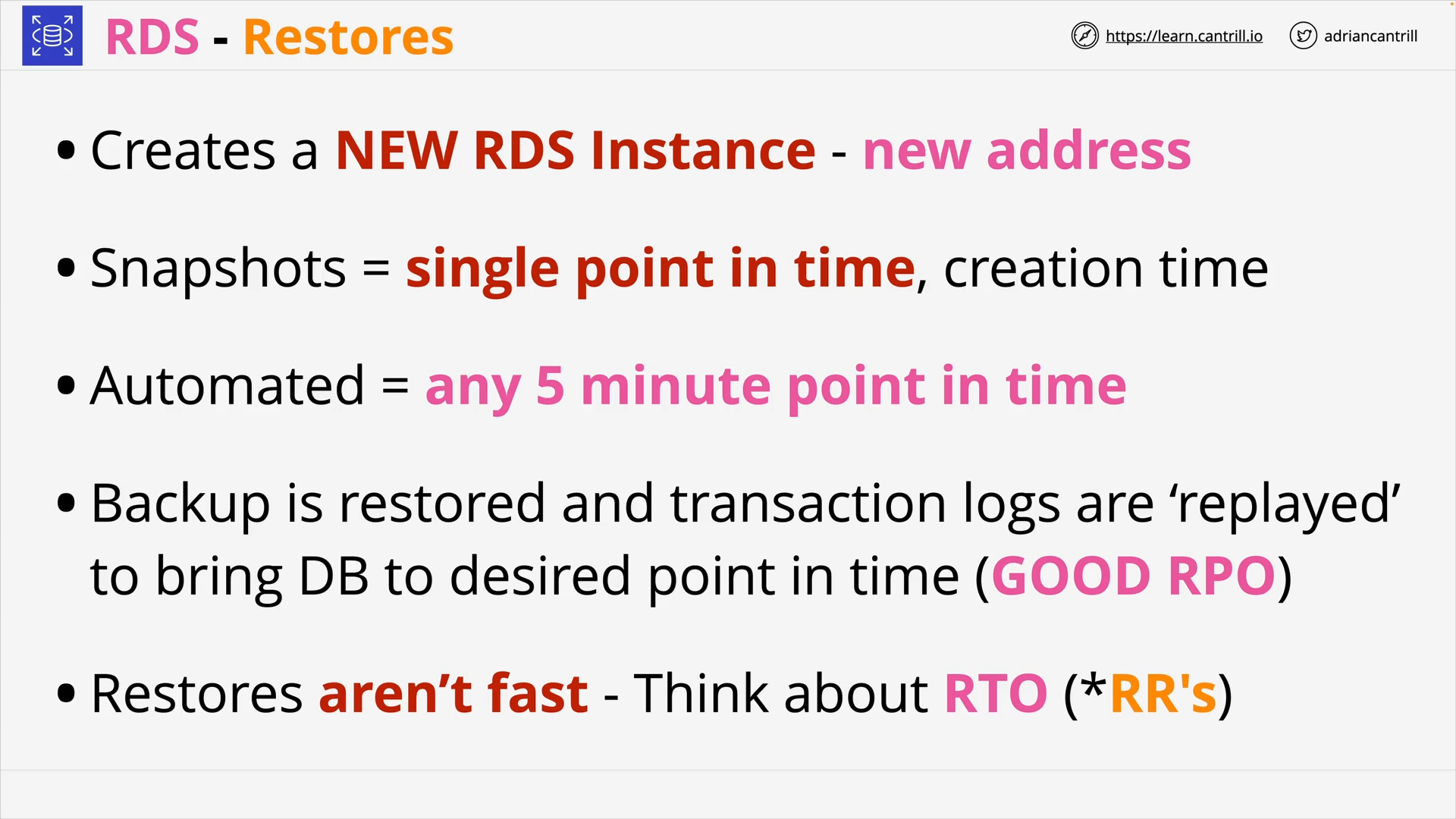 RDS Restores
RDS Restores
where is a rds snapshot restored to?
RDS Snapshot is restored to a new RDS instance, with new address.
how long is an rds restore?
RDS Restores aren’t fast. Be careful with RTO.
RDS Read-Replicas (6:36)
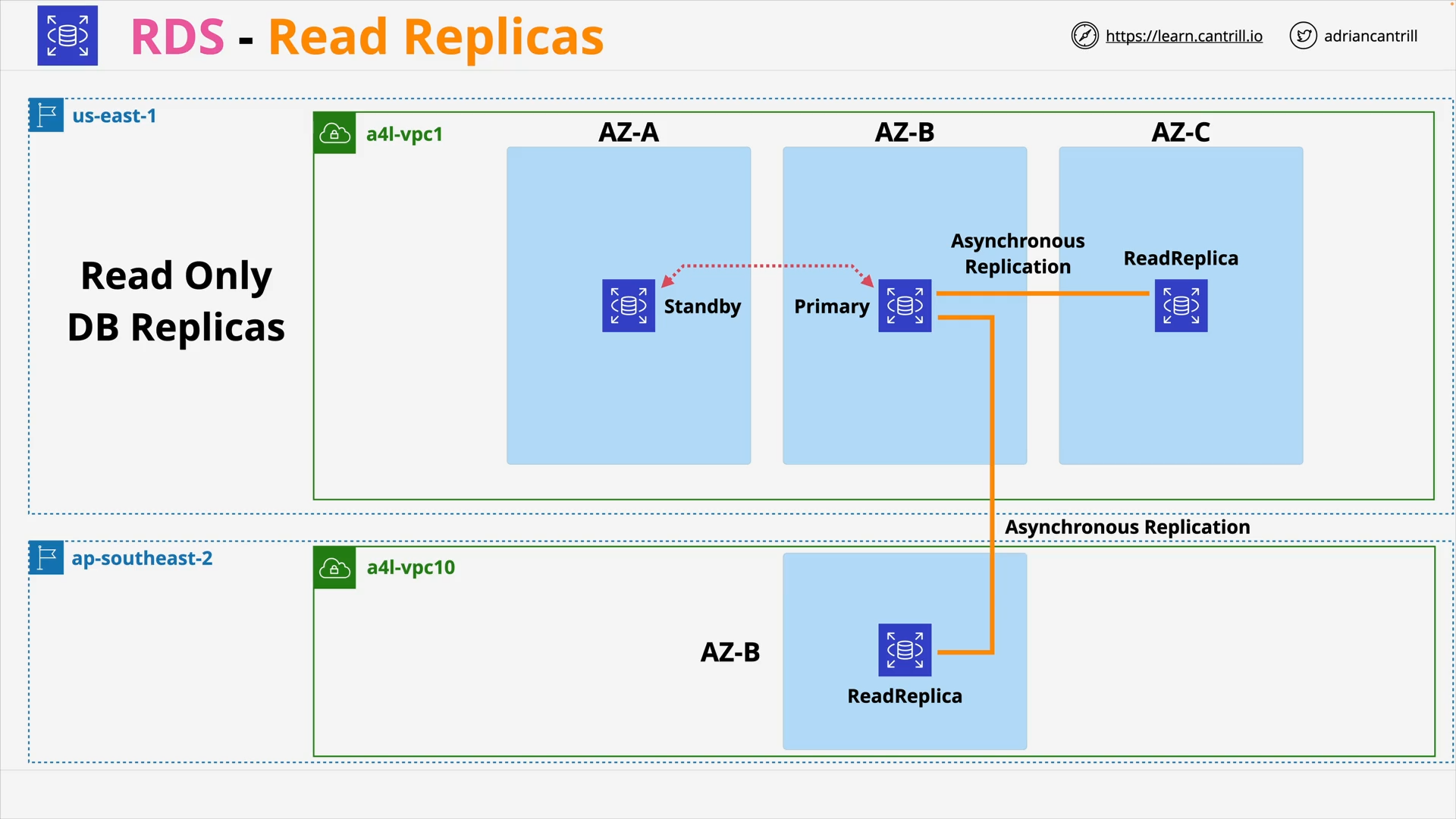 RDS Read-Replicas are kept in sync asynchronously with the primary instance
RDS Read-Replicas are kept in sync asynchronously with the primary instance
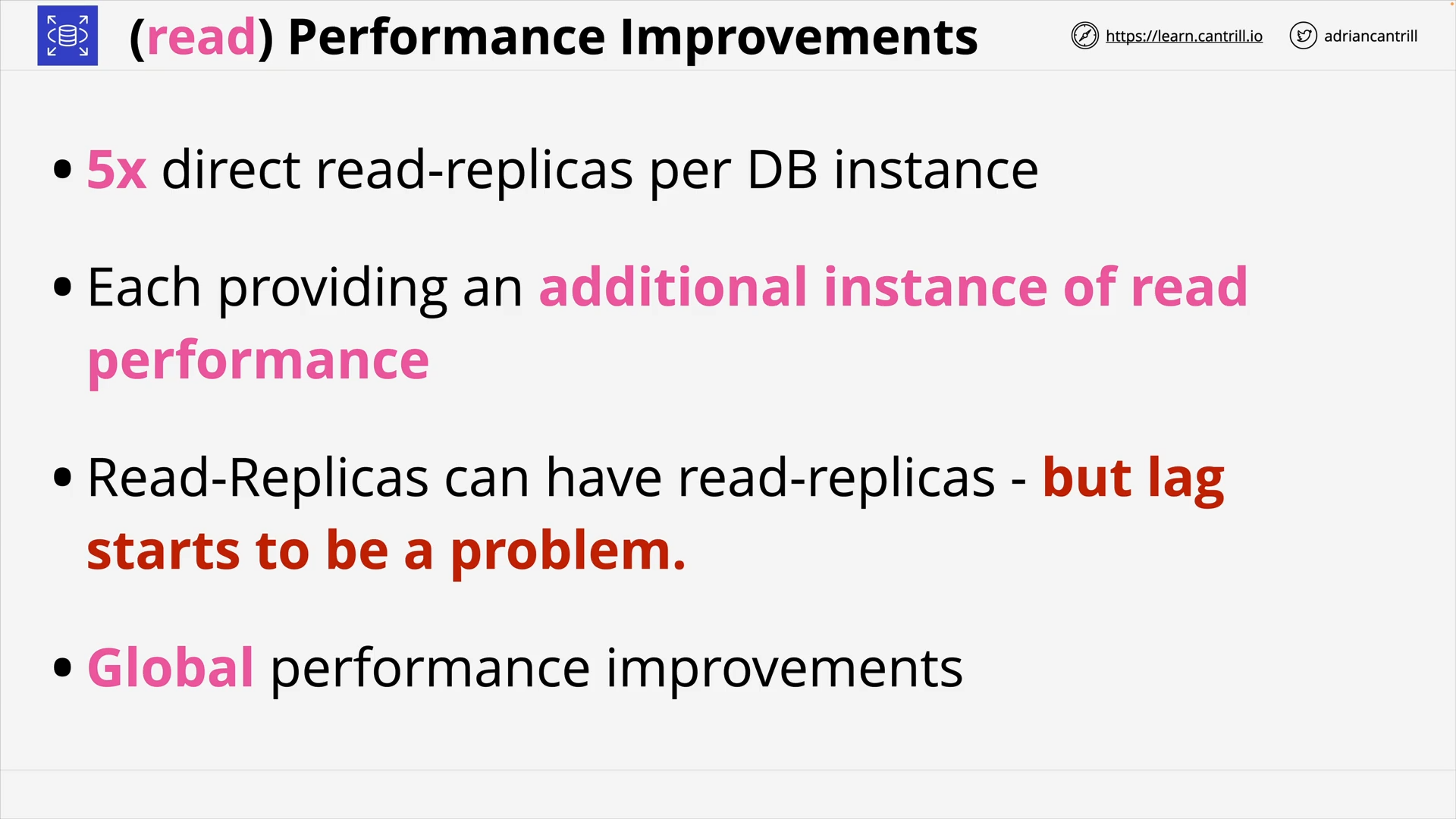 RDS Read-Replicas - Performance Improvement
RDS Read-Replicas - Performance Improvement
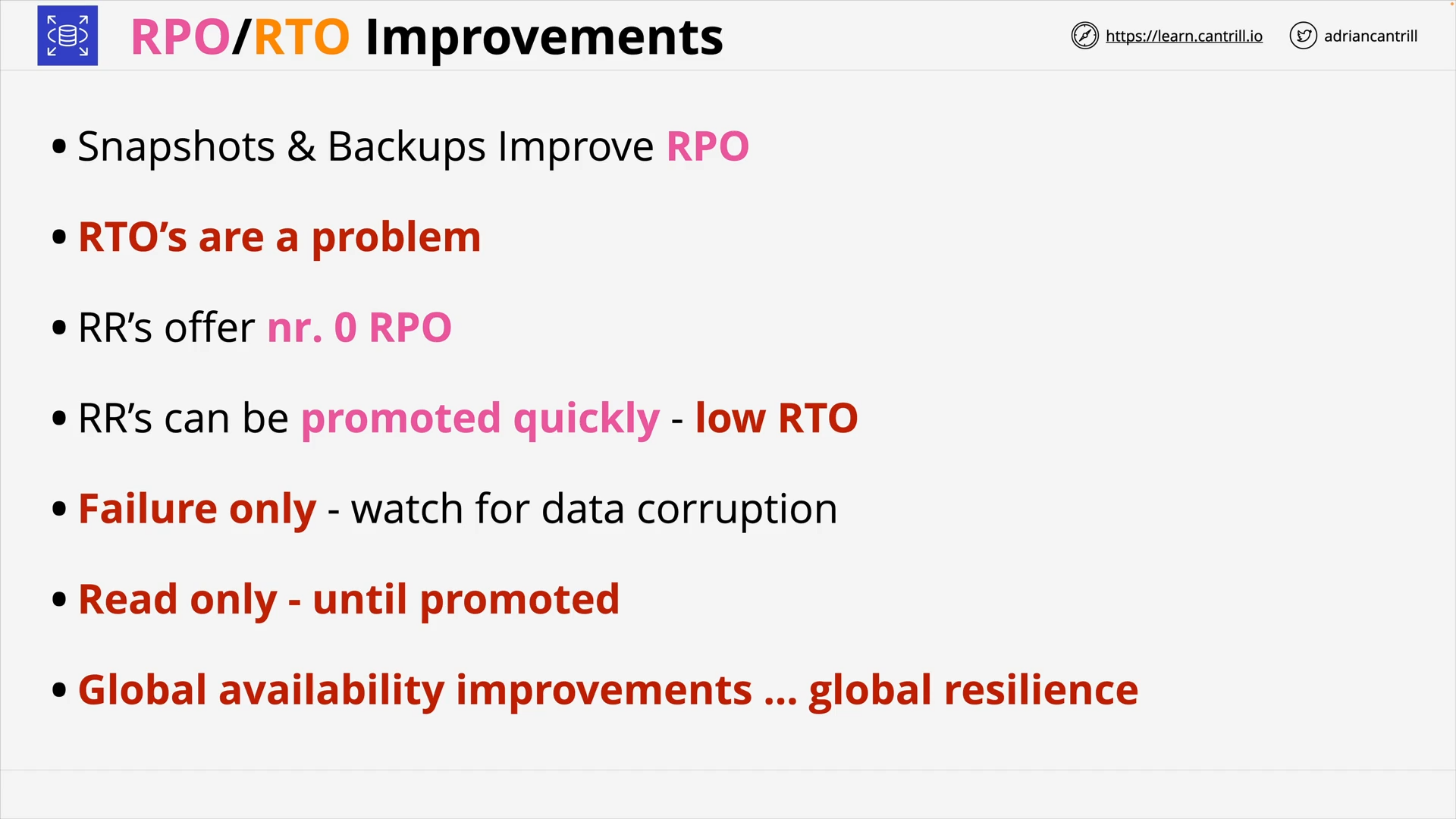 RDS Read-Replicas - RPO/RTO Improvement
RDS Read-Replicas - RPO/RTO Improvement
what is the impact of rds read-replicas to rpo/rto?
Read-Replicas offer:
- near 0 RPO.
- very low RTO 👈 RRs can be promoted quickly.
can read-replicas solve data corruption?
No. Data corruption will be replicated to RRs.
[DEMO] MultiAZ & Snapshot Restore with RDS - PART1 (14:05)
[DEMO] MultiAZ & Snapshot Restore with RDS - PART2 (12:07)
RDS Data Security (7:03)
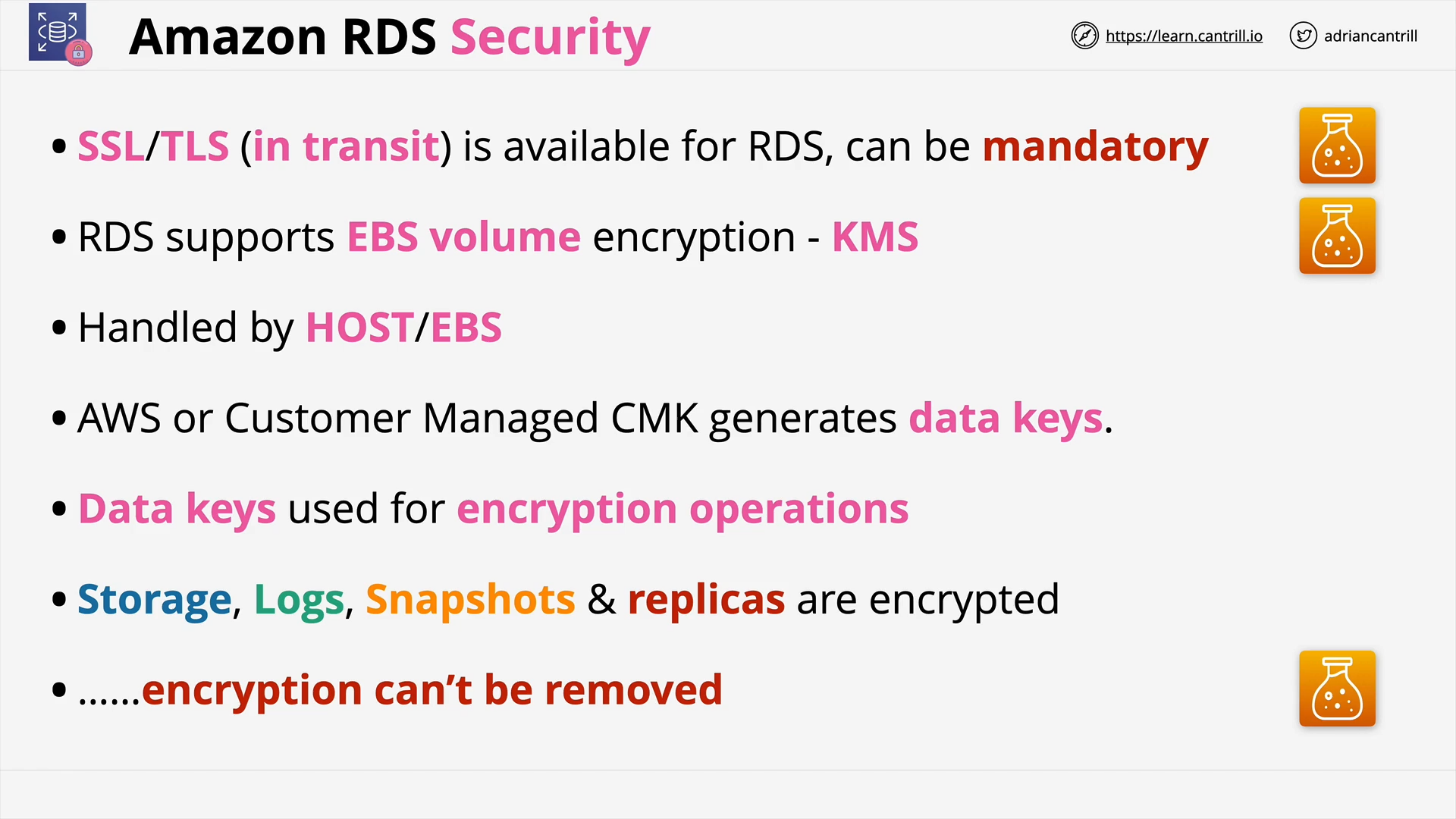 RDS Data Security
RDS Data Security
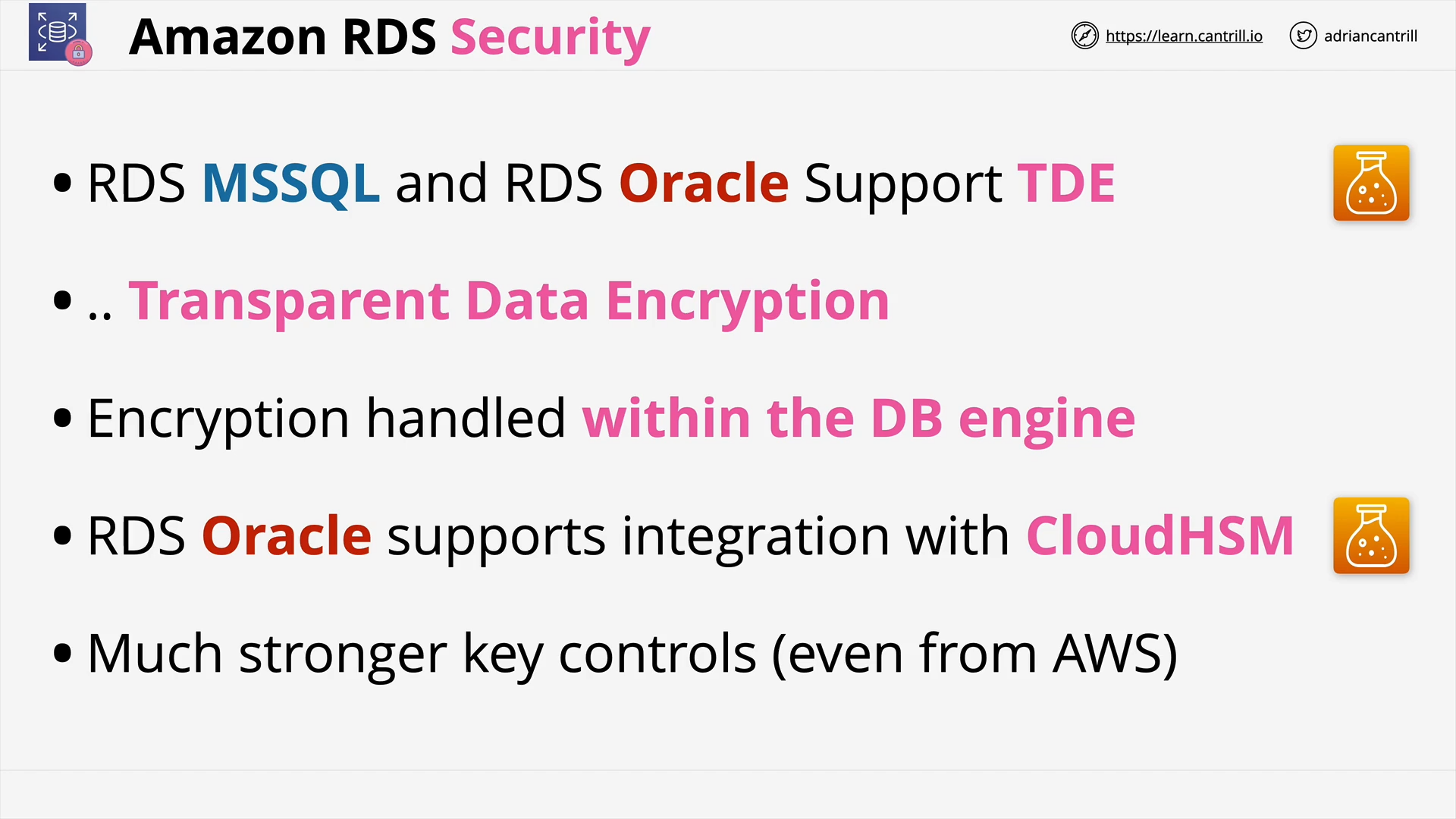 RDS Data Security - Extra Security
RDS Data Security - Extra Security
 RDS KMS Encryption & TDE
RDS KMS Encryption & TDE
 IAM Authentication RDS
IAM Authentication RDS
RDS Custom (5:22)
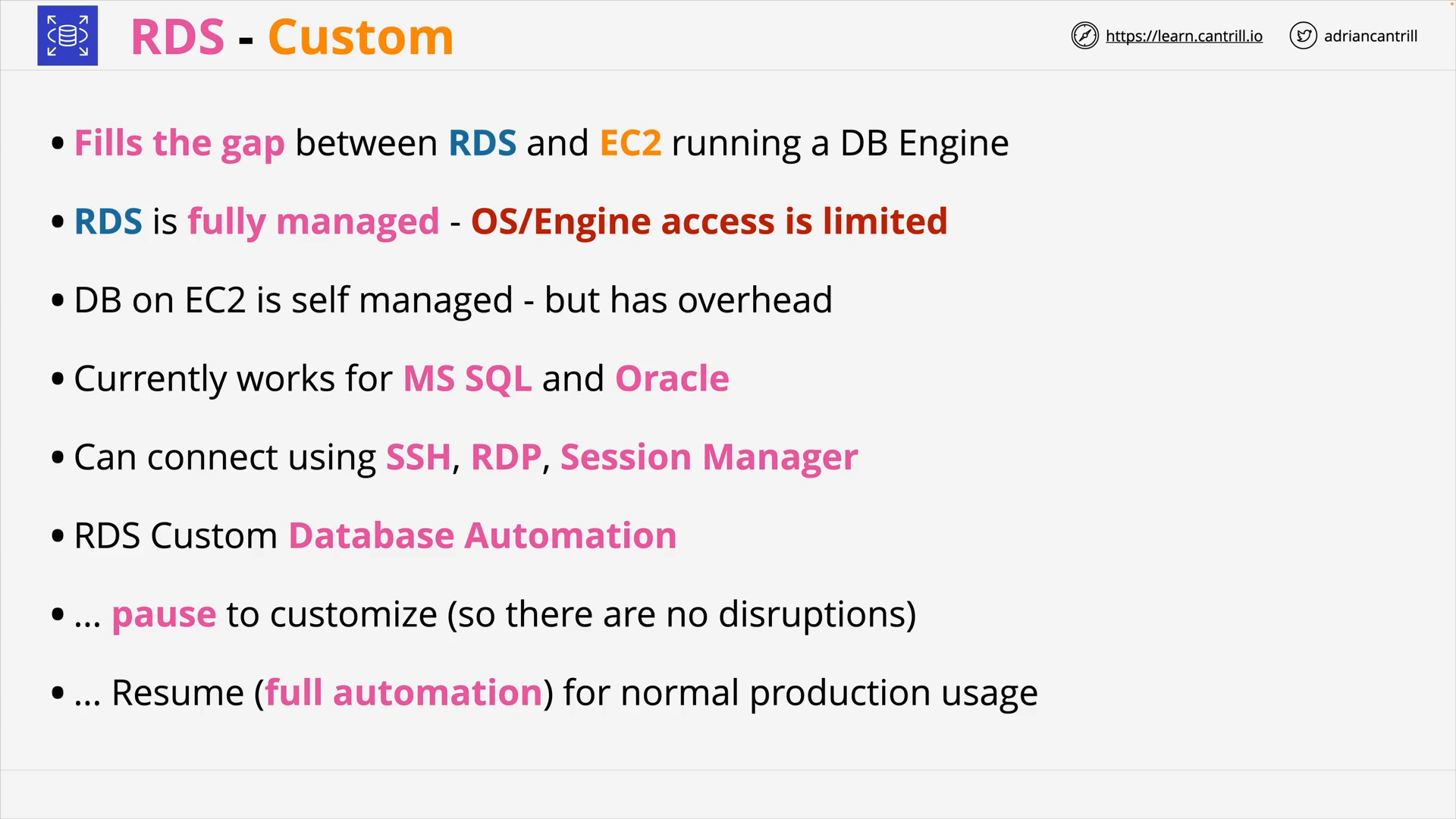 RDS Custom - Fill the gap between DB-on-EC2 and RDS.
RDS Custom - Fill the gap between DB-on-EC2 and RDS.
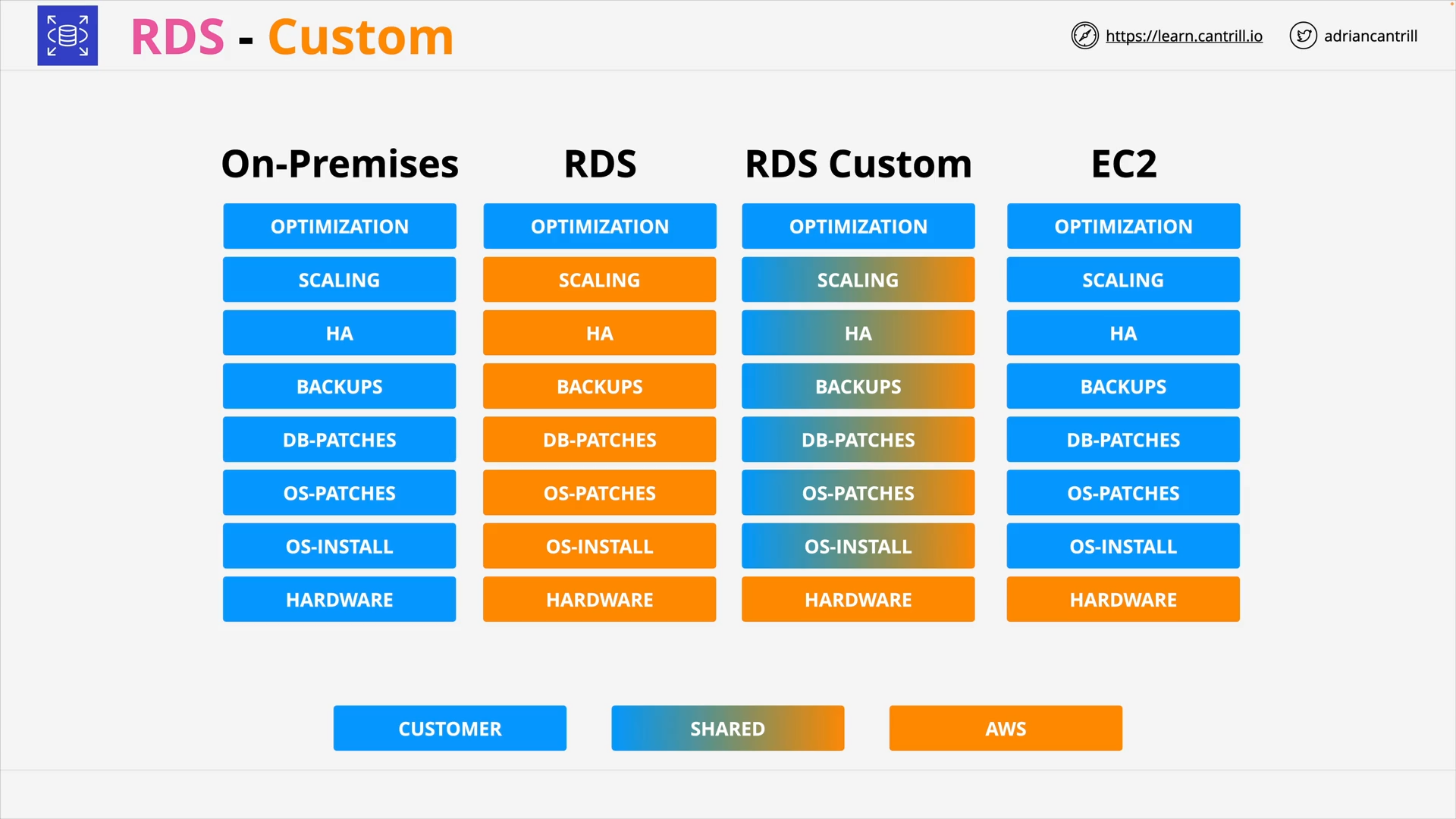 RDS Custom - Shared Responsibility
RDS Custom - Shared Responsibility
Aurora Architecture (13:44)
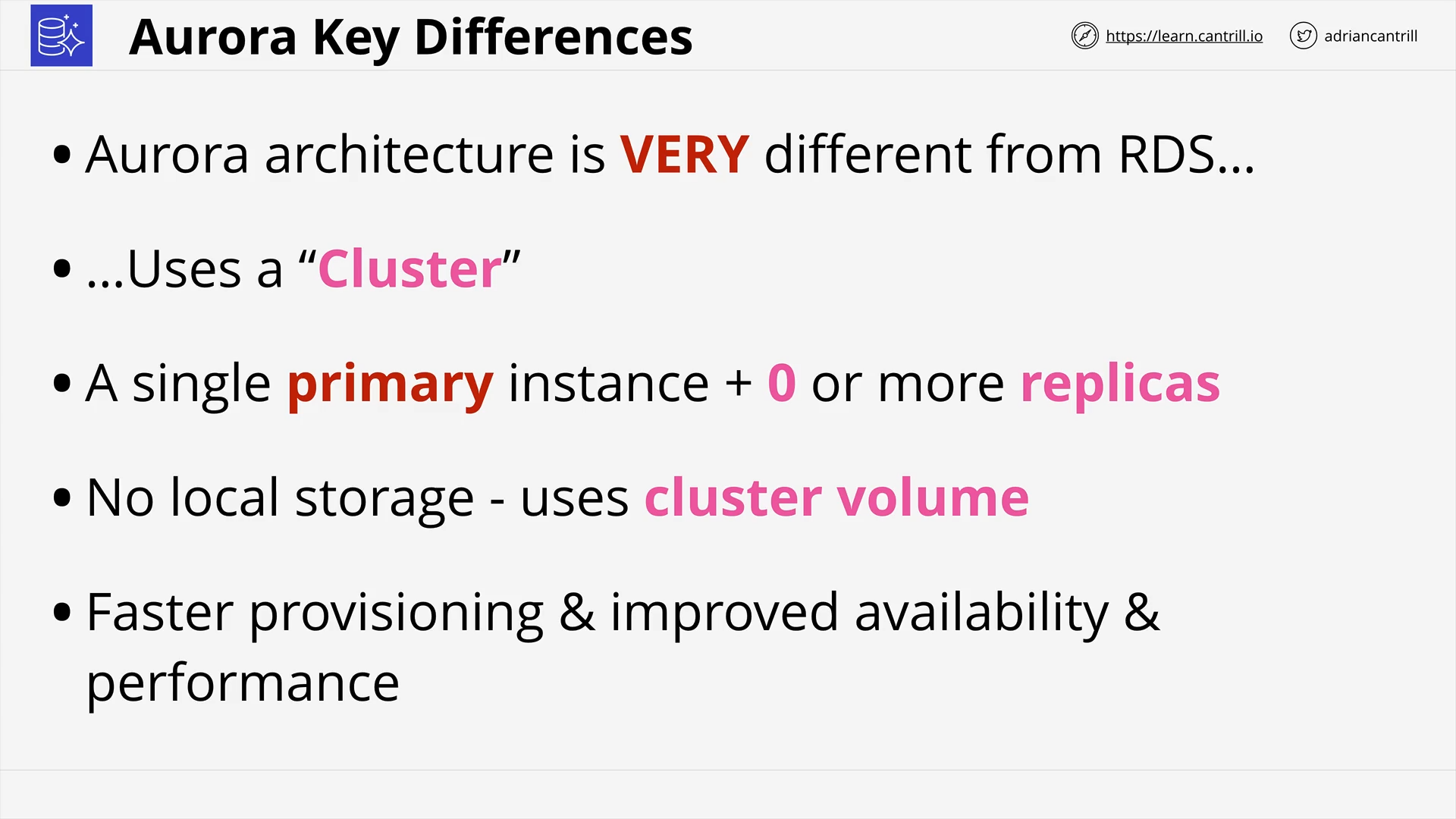 Aurora - Key Differences
Aurora - Key Differences
 Aurora - Storage Architecture - 6 replicas
Aurora - Storage Architecture - 6 replicas
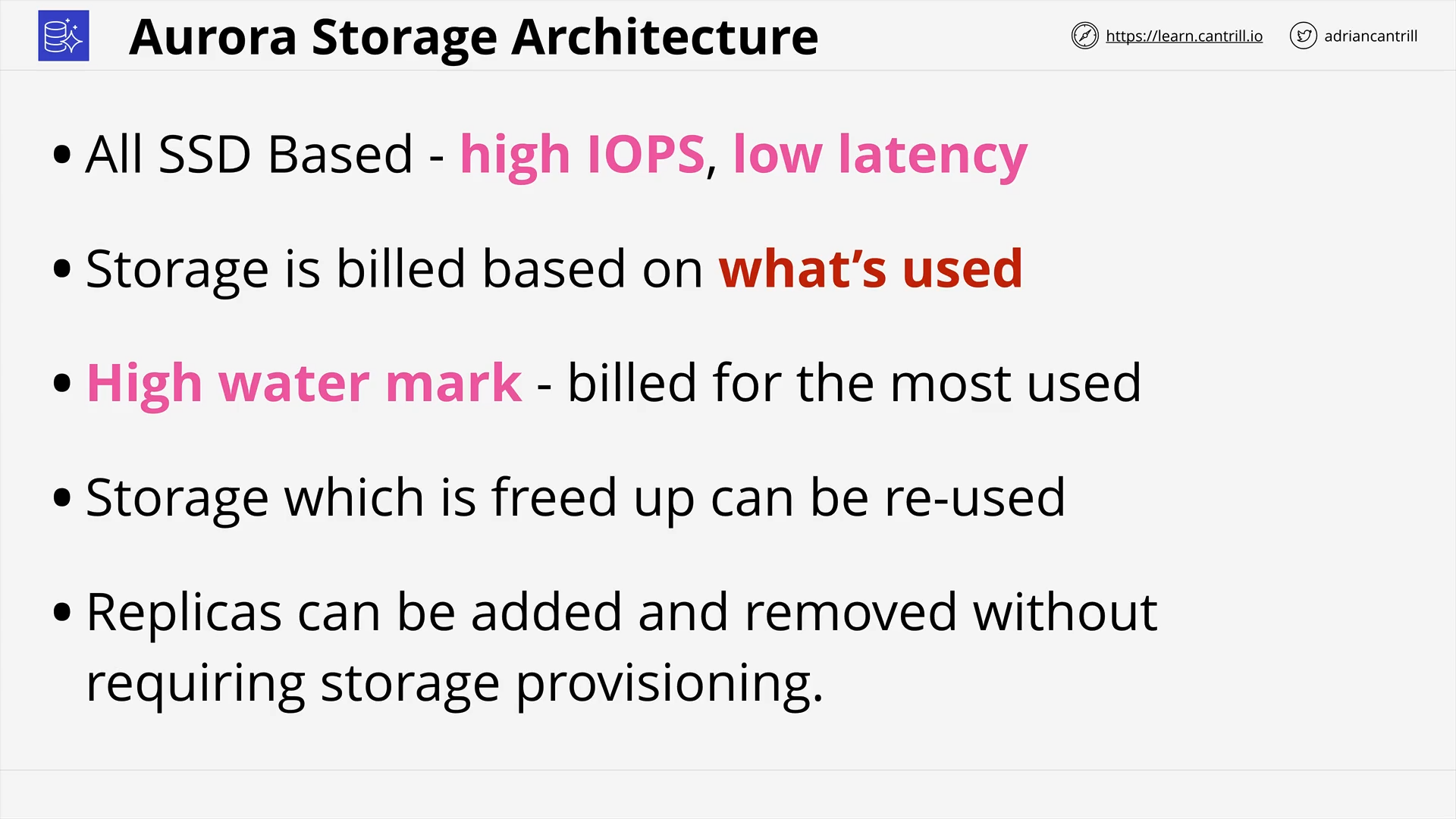 Aurora - Storage Architecture - Summary
Aurora - Storage Architecture - Summary
 Aurora - Endpoints
Aurora - Endpoints
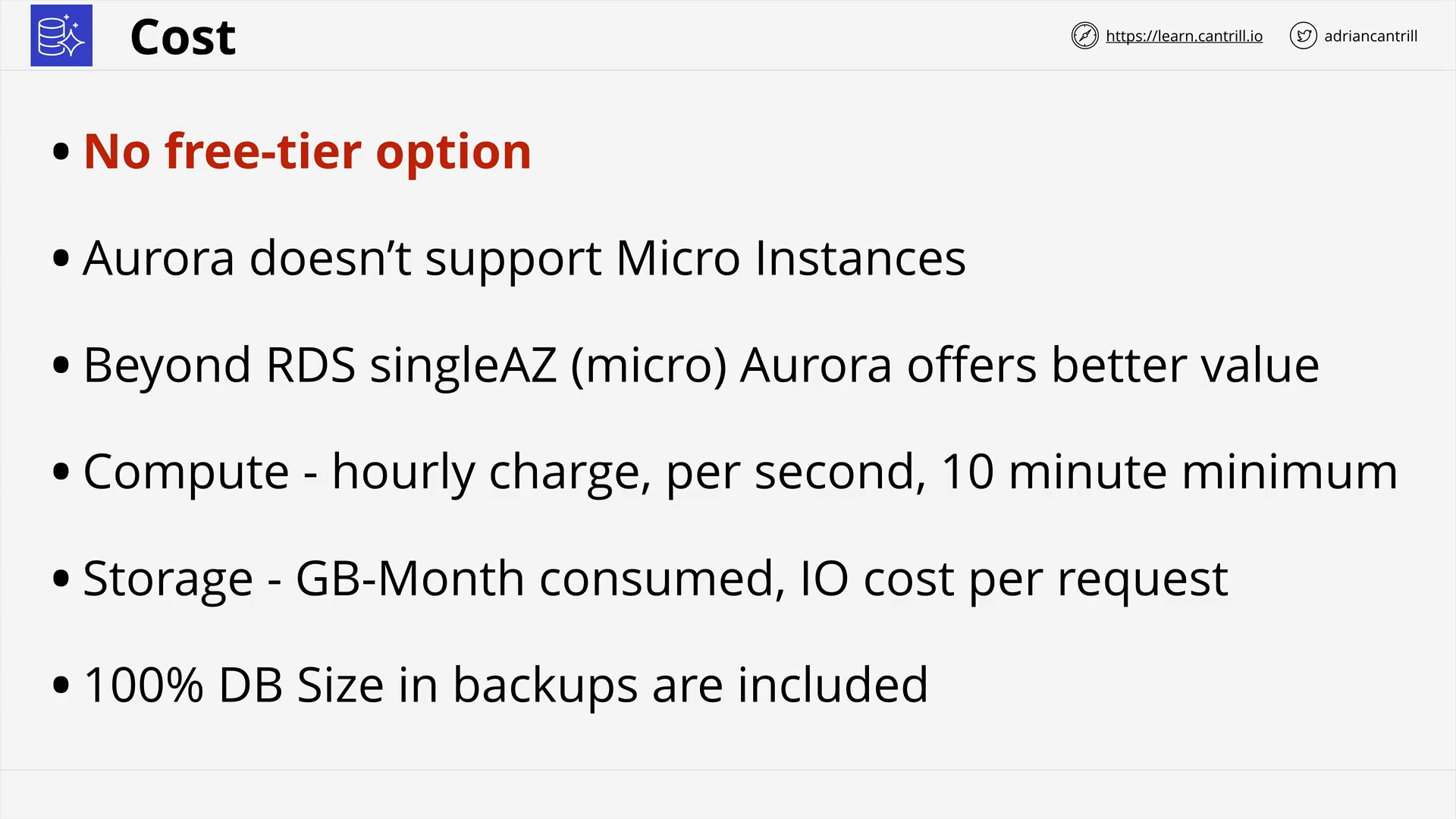 Aurora - Cost
Aurora - Cost
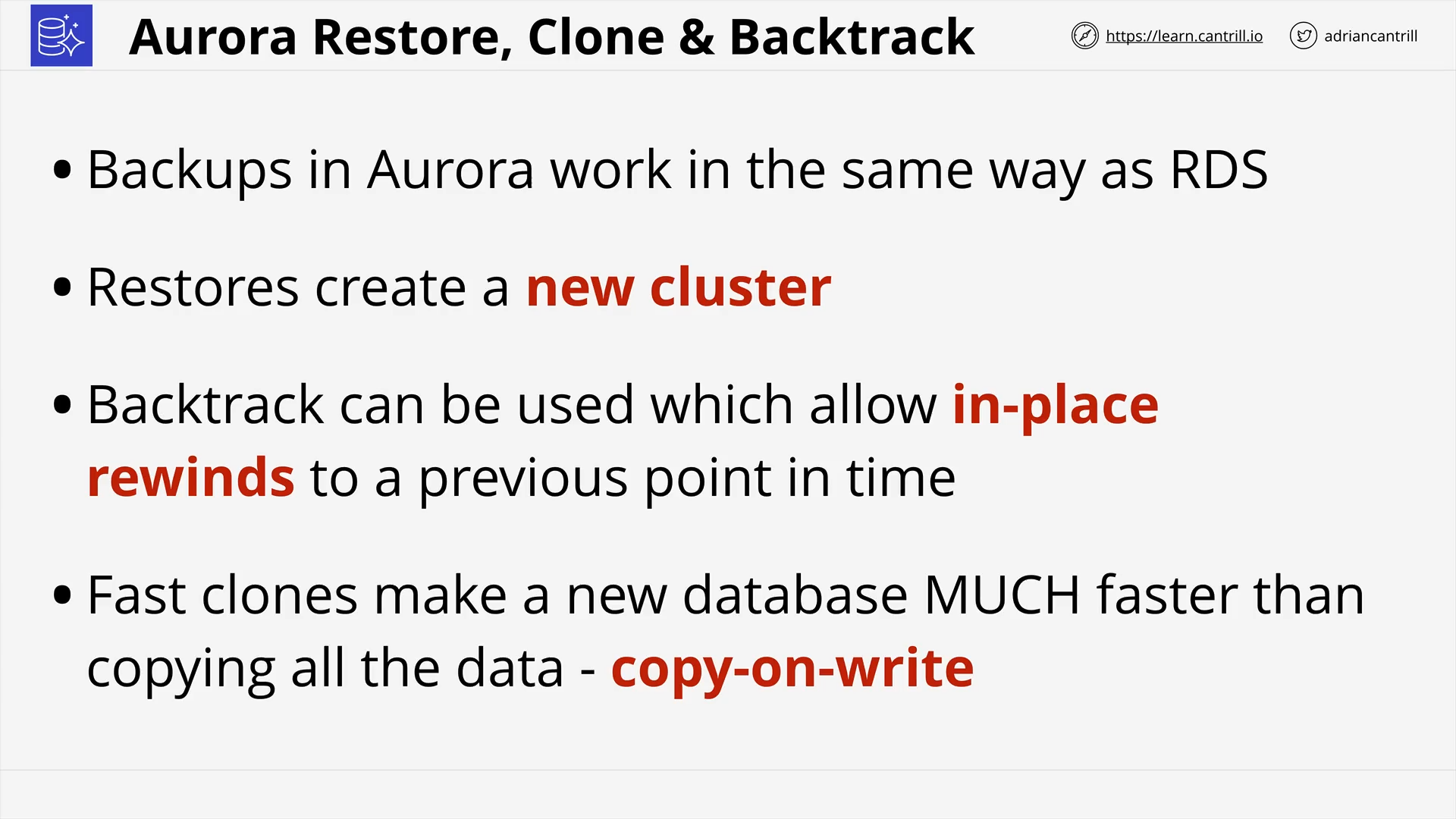 Aurora - Restore, Clone & Backtrack
Aurora - Restore, Clone & Backtrack
👉 Aurora implements a number of radical design changes which offer significant performance and feature improvements over other RDS database engines.
Aurora Serverless (9:52)
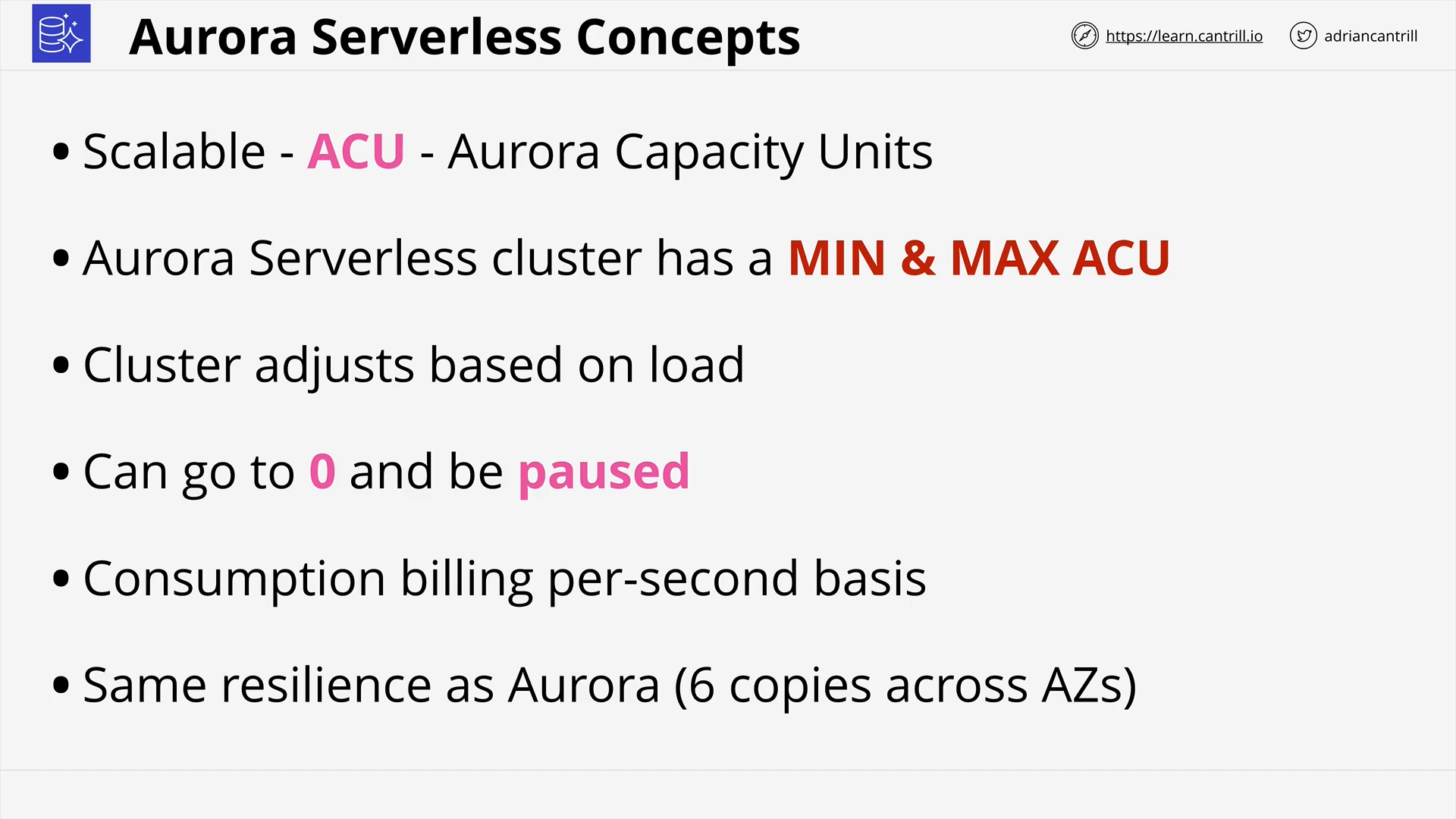 Aurora Serverless - Concepts
Aurora Serverless - Concepts
 Aurora Serverless - Architecture
Aurora Serverless - Architecture
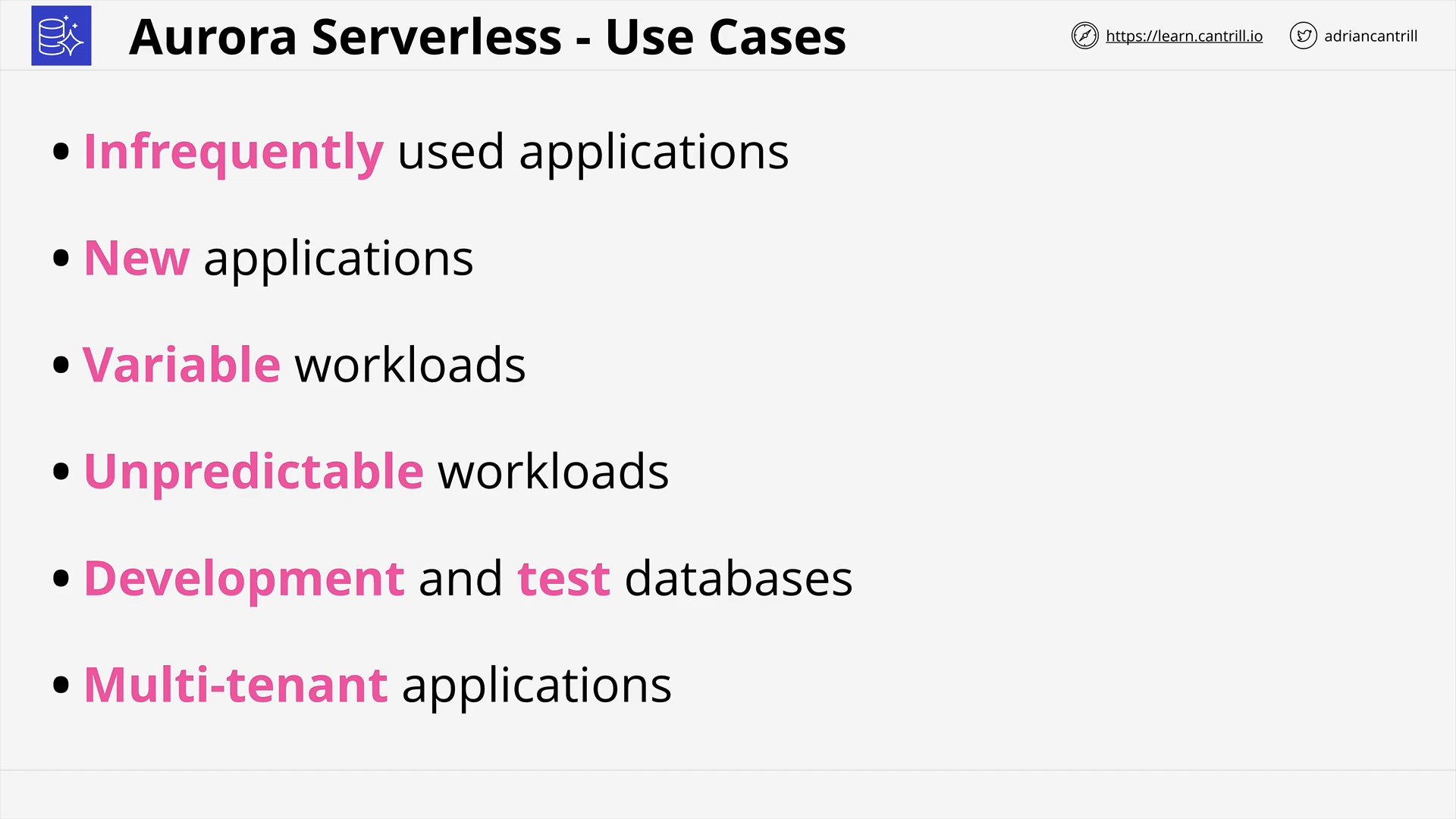 Aurora Serverless - Use Cases
Aurora Serverless - Use Cases
[DEMO] Migrating to Aurora Serverless [DENT DO THIS DEMO, IT WON’T WORK, UPDATING to SERVERLESSv2] (14:47)
Aurora Global Database (5:08)
 Aurora Global Database - Architecture
Aurora Global Database - Architecture
how long is aurora global database's replication between regions?
Less than or equal 1s
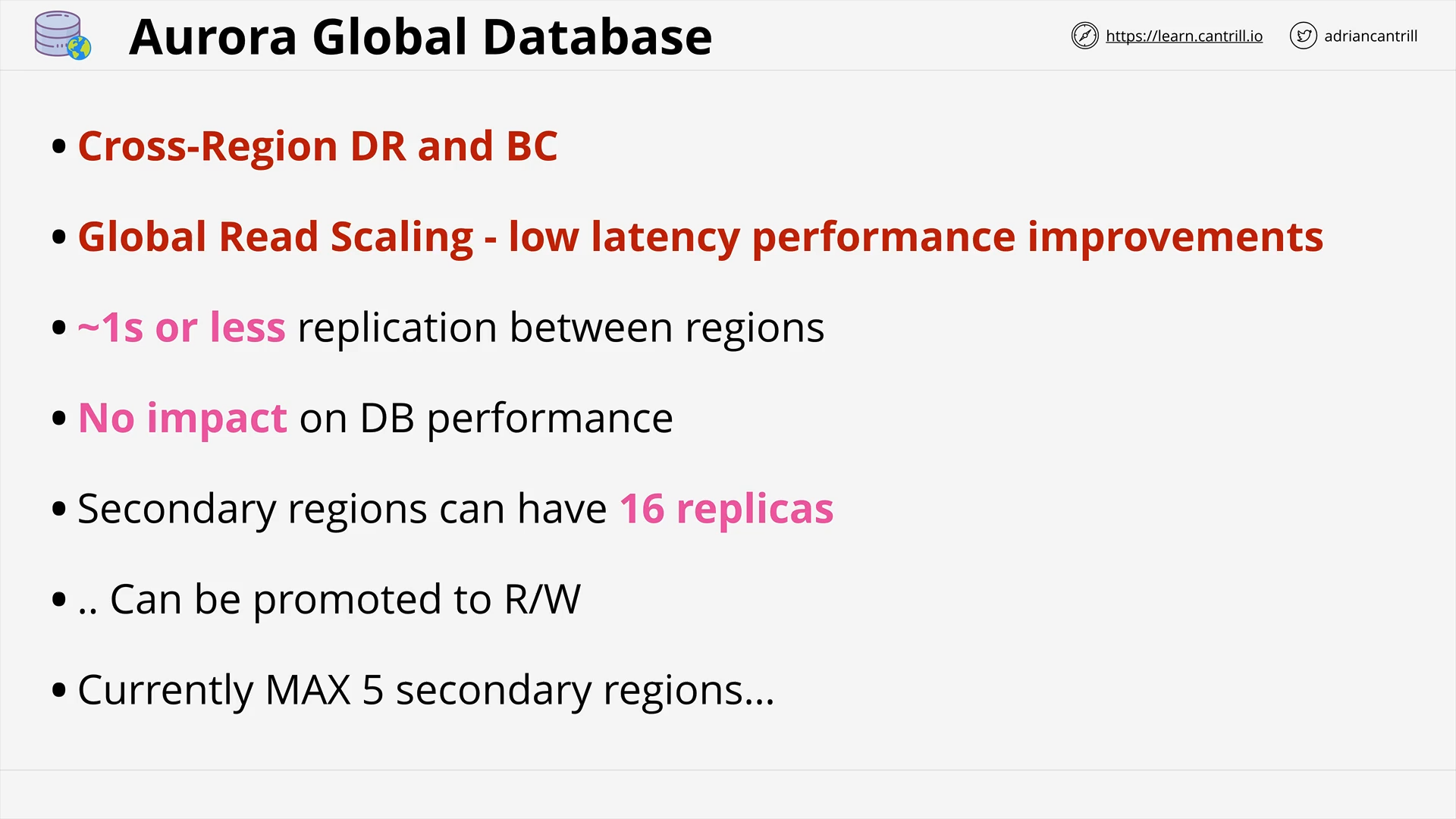 Aurora Global Database - 5 secondary regions - each regions can have 16 read-only replicas
Aurora Global Database - 5 secondary regions - each regions can have 16 read-only replicas
Aurora Multi-master writes (7:51)
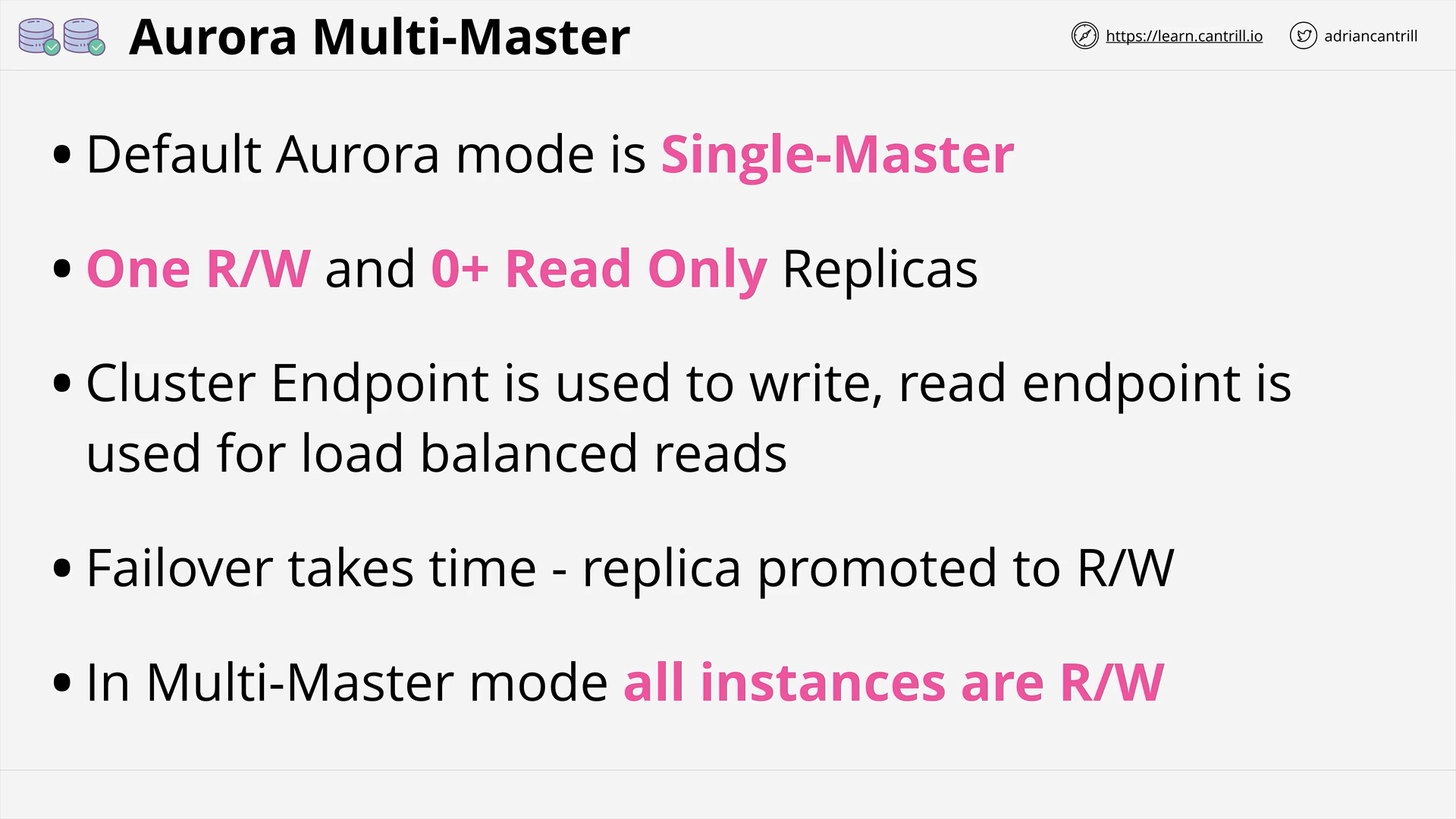 Aurora Multi-Master - All instances are R/W
Aurora Multi-Master - All instances are R/W
 Aurora Multi-Master - Architecture
Aurora Multi-Master - Architecture
 Aurora Single-Master - Failover
Aurora Single-Master - Failover
 Aurora Multi-Master - Failover
Aurora Multi-Master - Failover
Relational Database Service (RDS) - RDS Proxy (9:47)
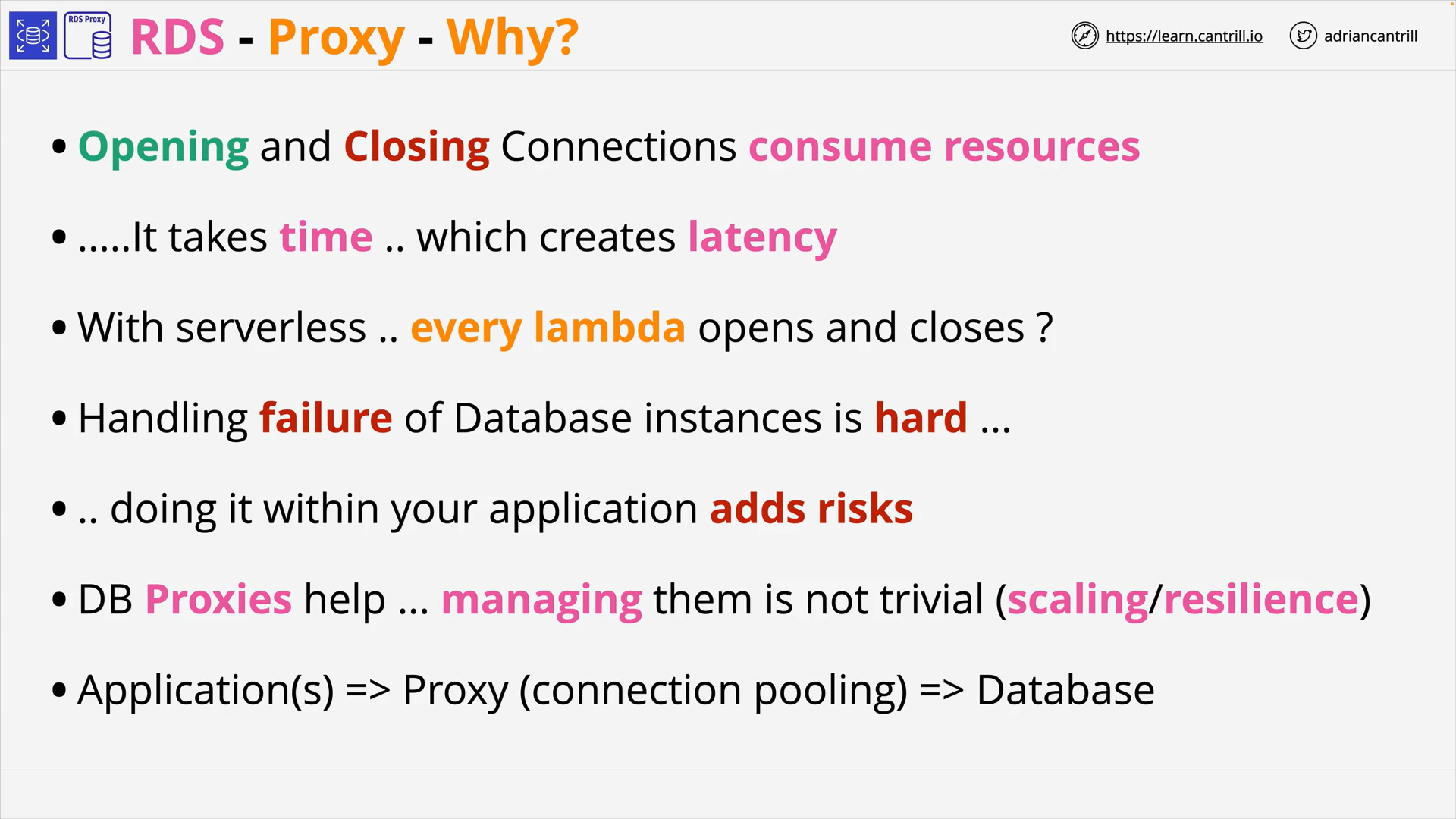 RDS Proxy - Why?
RDS Proxy - Why?
why use rds proxy?
-
Opening/Closing DB Connections consume resources.
- Increase latency.
- Especially with serverless architecture.
-
Handling failure of DB instance is hard:
- Doing it within application add risks
👉 RDS Proxy solves these problems.
how rds proxy works?
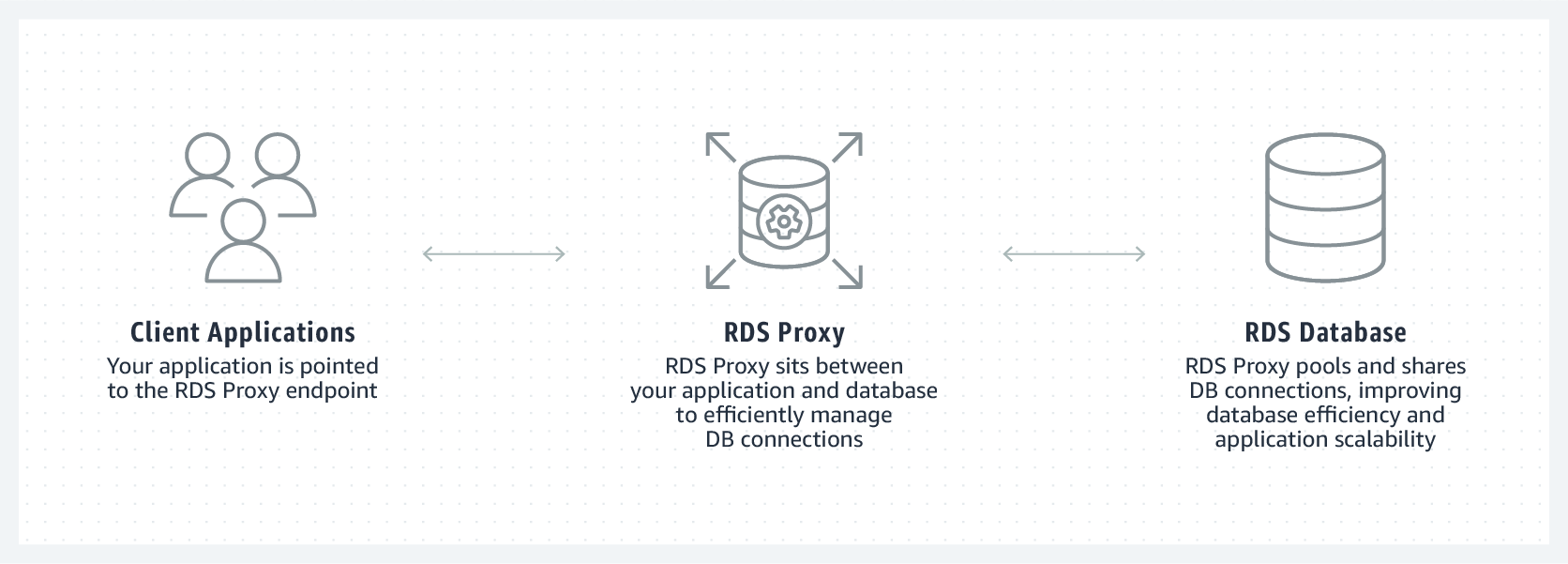
- sits between your application and your relational database
- to efficiently manage connections to the database
👉 improve scalability of the application.
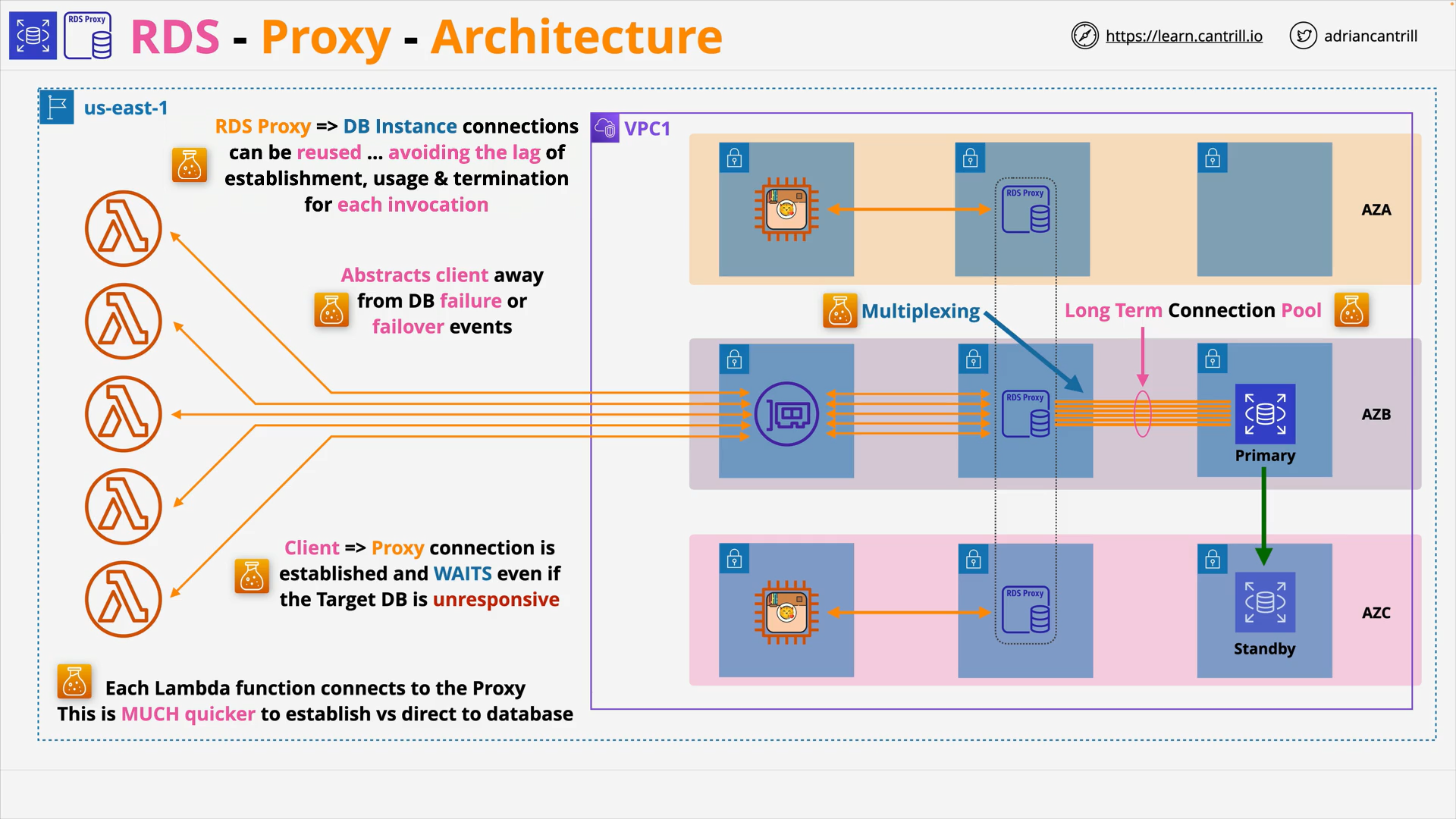 RDS Proxy - Architecture
RDS Proxy - Architecture
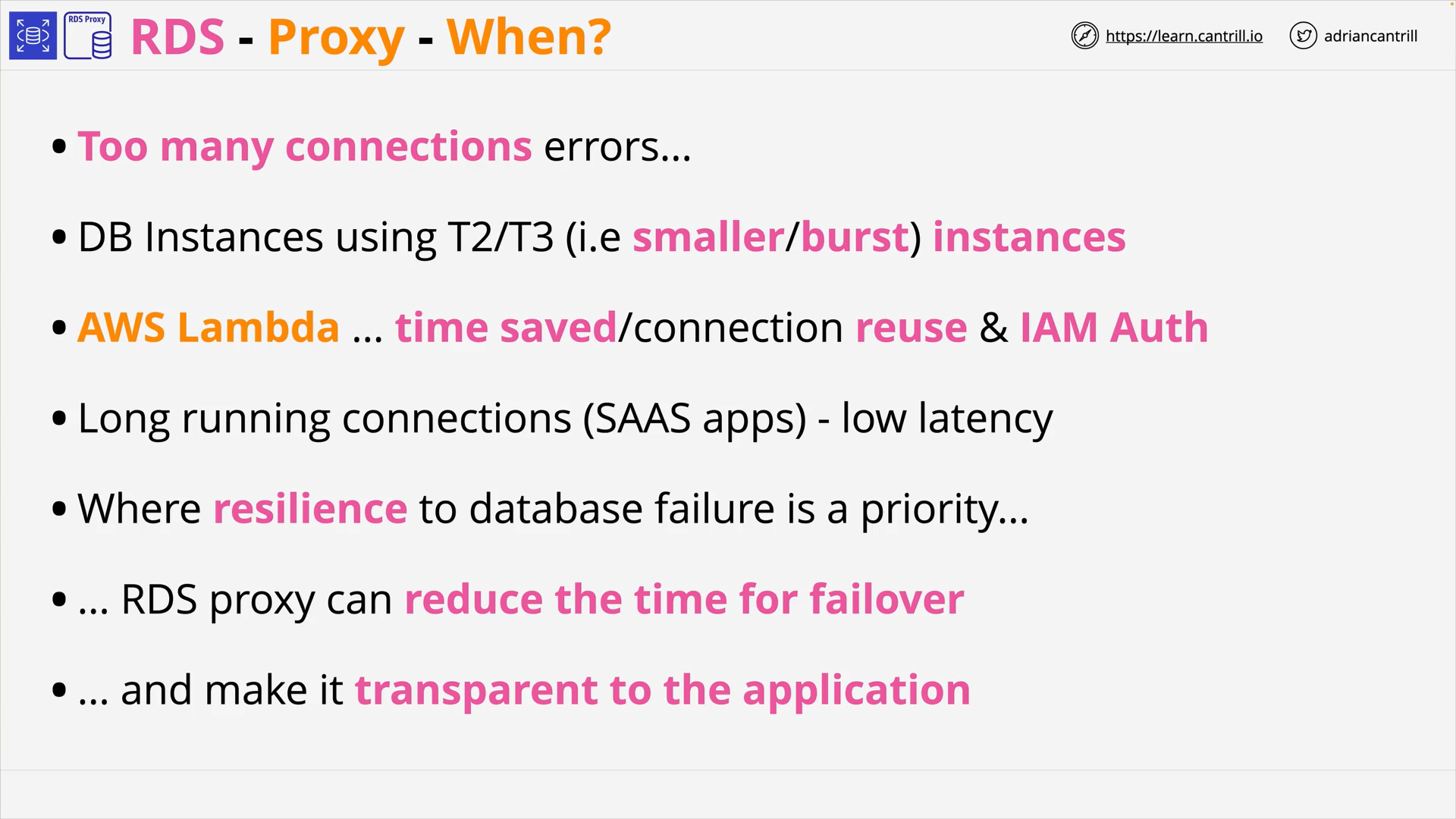 RDS Proxy - When?
RDS Proxy - When?
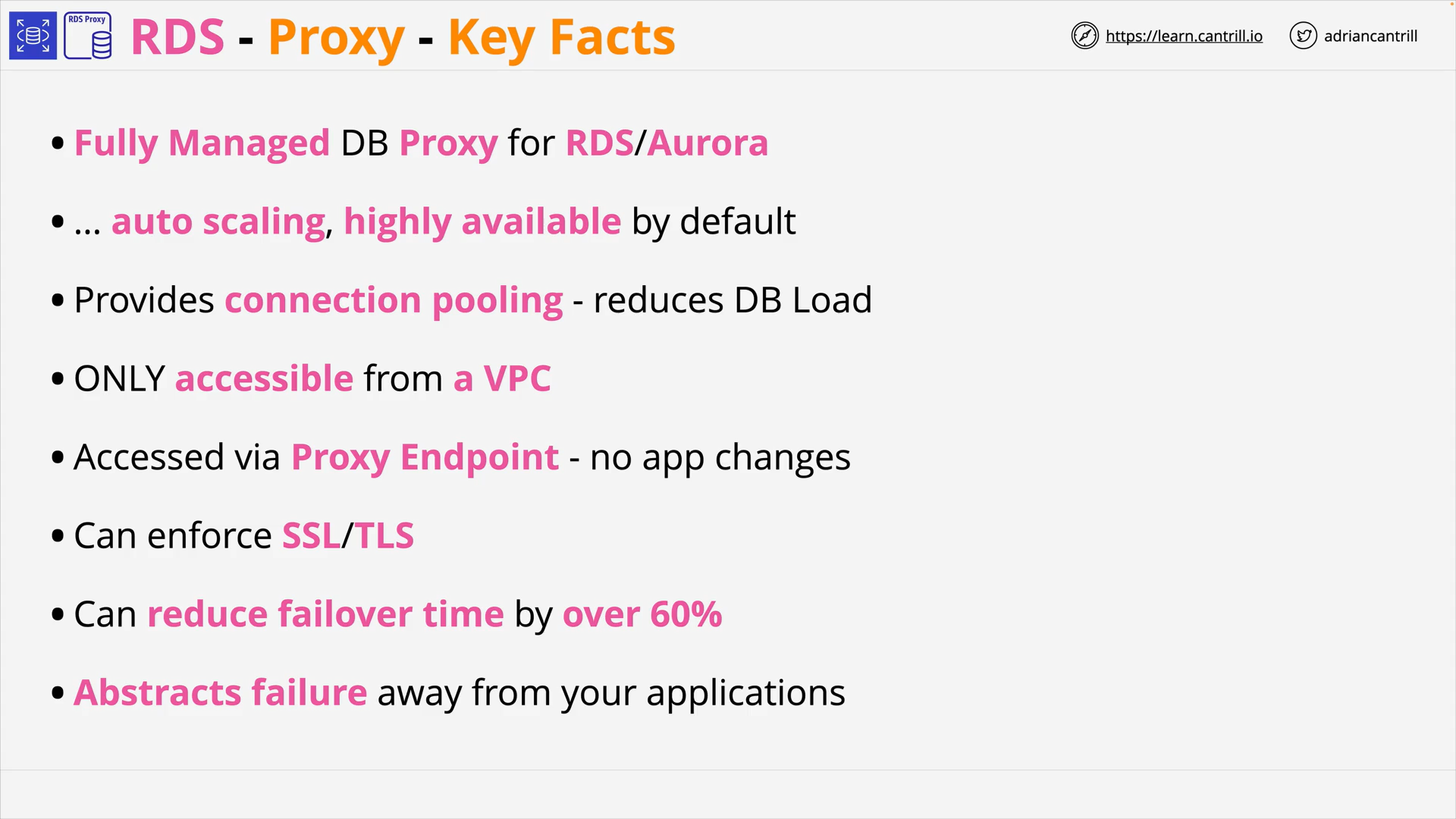 RDS Proxy - Key Facts
RDS Proxy - Key Facts
Database Migration Service (DMS) (11:03)
.png) Database Migration Service (DMS) - Summary
Database Migration Service (DMS) - Summary
can dms be used for on-premises db?
Yes and No.
- DMS can be used to migrate from/to on-premises DB if the other endpoint were on AWS.
- If both endpoints are on-premise, DMS can NOT be used.
 DMS - Architecture
DMS - Architecture
where is dms run?
On a replication instance (an EC2 instance).
which part of dms really run the migration?
DMS Task:
- Full load
- Full load + CDC
- CDC only
.png) Schema Conversion Tool (SCT)
Schema Conversion Tool (SCT)
aws schema conversion tool (sct) vs aws dms schema conversion?
-
AWS Schema Conversion Tool (SCT):
- convert your existing database schema from one database engine to another.
- used to convert data warehouse schemas, big data frameworks, application SQL code, and ETL processes.
-
AWS DMS Schema Conversion:
- a web-version of the AWS SCT. [1]
- supports less database platforms and provides more limited functionality compared
.png) DMS & Snowball ☃️
DMS & Snowball ☃️
RDS Section Quiz
Database - How to choose?
Ref:
| Database Family | When Would You Use It? | Use Case | Optimized For | AWS Related Database Engines or Services | 3rd-party |
|---|---|---|---|---|---|
| Relational | Migrating on-premises relational workloads, ad hoc query patterns | Traditional applications, enterprise resource planning (ERP), customer relationship management (CRM), e-commerce | Structured data in tables, rows, and columns, supports complex ad hoc queries through joins | Amazon Aurora, Amazon RDS | MySQL, Postgres |
| Amazon Redshift | Google BigQuery | ||||
| Key-value | Session stores, shopping carts, scalable for high volumes of state changes | High-traffic web applications, e-commerce systems, gaming applications | Fast access to large amounts of structured, semi-structured, or unstructured data with high read and write throughput | Amazon DynamoDB | Google Bigtable |
| Document | Storing JSON documents with rich querying abilities | Content management, catalogs, user profiles | Storing semi-structured data as JSON documents | Amazon DocumentDB (with MongoDB compatibility) | MongoDB |
| In-memory | Improving read performance through caching | Caching, session management, gaming leaderboards, geospatial applications | Applications requiring sub-millisecond data access | Amazon ElastiCache, Amazon MemoryDB for Redis | Redis |
| Wide column | Migrating on-premises Cassandra workloads, high-speed data processing | High-scale industrial apps for equipment maintenance, fleet management, and route optimization | Workloads requiring heavy reads/writes, high throughput, low latency, and linear scalability | Amazon Keyspaces | Apache Cassandra |
| Graph | Fraud detection, recommendation engines, airline networks | Fraud detection, social networking, recommendation engines | Storing and navigating relationships | Amazon Neptune | neo4j |
| Time series | Managing large amounts of time series data from various sources | Internet of Things (IoT) applications, DevOps, industrial telemetry | Storing and querying data that changes over time | Amazon Timestream | |
| Ledger | Communicating with other entities, maintaining verifiable history of database changes | Systems of record, supply chain, registrations, banking transactions | Maintaining a complete and verifiable history of database changes | Amazon Quantum Ledger Database (QLDB) |
Structured, semi-structured, and unstructured data
| Structured data | Semi-structured data | Unstructured data | |
|---|---|---|---|
| Data pie | 10 to 15 % | 5% to 10% | 80% to 90% |
| Example | RDS table, spreadsheet | HTML, JSON, XML | Multimedia (photo, audio, video), text document, scanned PDF |
Ref:
- https://www.mongodb.com/unstructured-data
- https://www.bisok.com/analytics-and-business-intelligence/unstructured-data/
Why RDS?
| Feature | On-premise database | Amazon EC2 management | Amazon RDS management |
|---|---|---|---|
| On-premises management | Customer | Customer | AWS |
| Application optimization | Customer | Customer | AWS |
| Scaling | Customer | Customer | AWS |
| High availability | Customer | Customer | AWS |
| Database backups | Customer | Customer | AWS |
| Database software patching | Customer | Customer | AWS |
| Database software install | Customer | Customer | AWS |
| Operating system (OS) patching | Customer | Customer | AWS |
| OS installation | Customer | Customer | AWS |
| Server maintenance | Customer | AWS | AWS |
| Hardware lifecycle | Customer | AWS | AWS |
| Power, network, and cooling | Customer | AWS | AWS |
NETWORK STORAGE & DATA LIFECYCLE
EFS Architecture (9:05)
 EFS - Overview
EFS - Overview
which os does aws efs support?
AWS EFS is an implement of NFSv4, which can only be mounted in Linux.
how to access an aws efs?
The EFS can be accessed:
- inside a VPC.
- from on-premises: via VPN or DX.
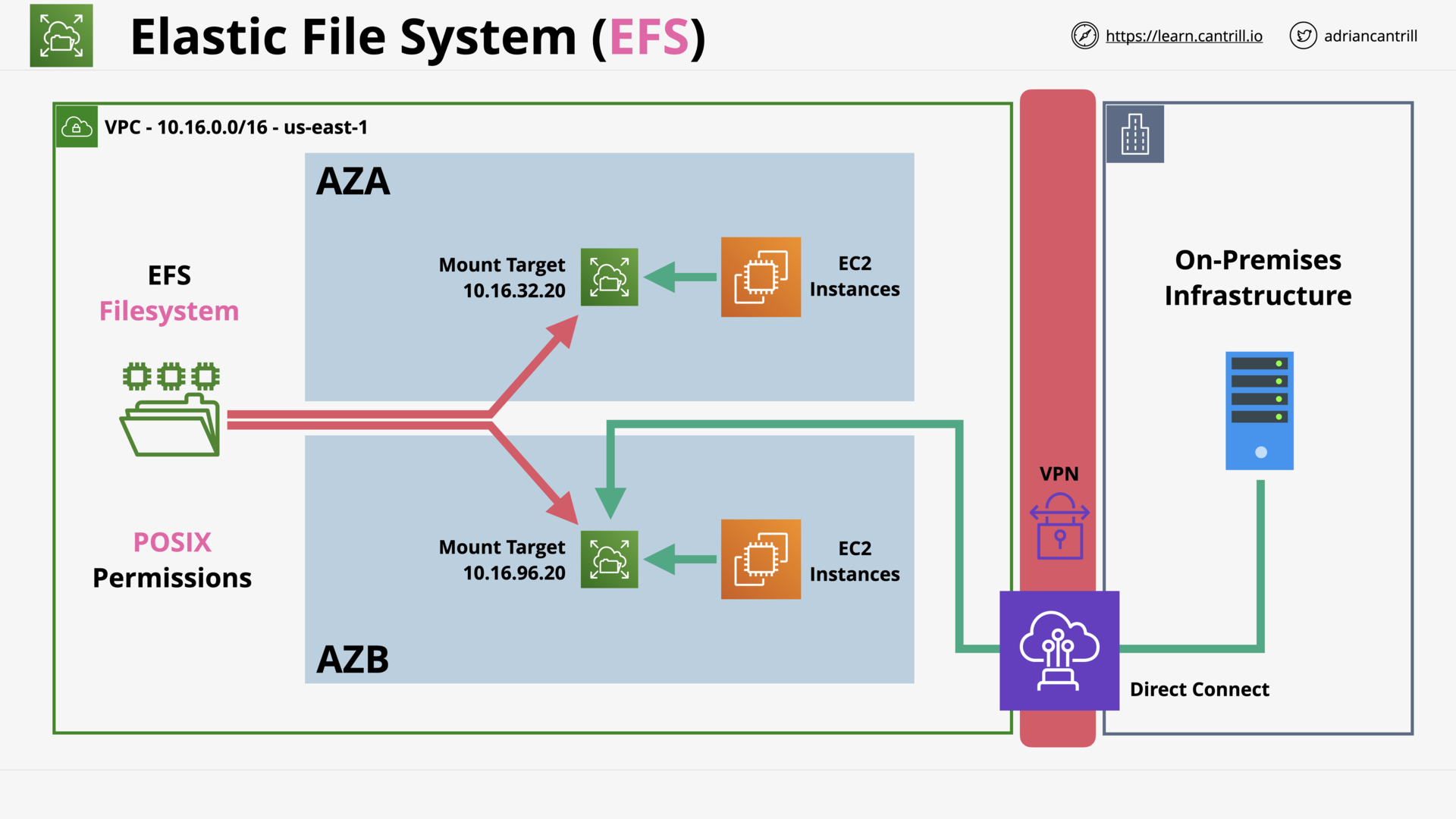 EFS - Architecture
EFS - Architecture
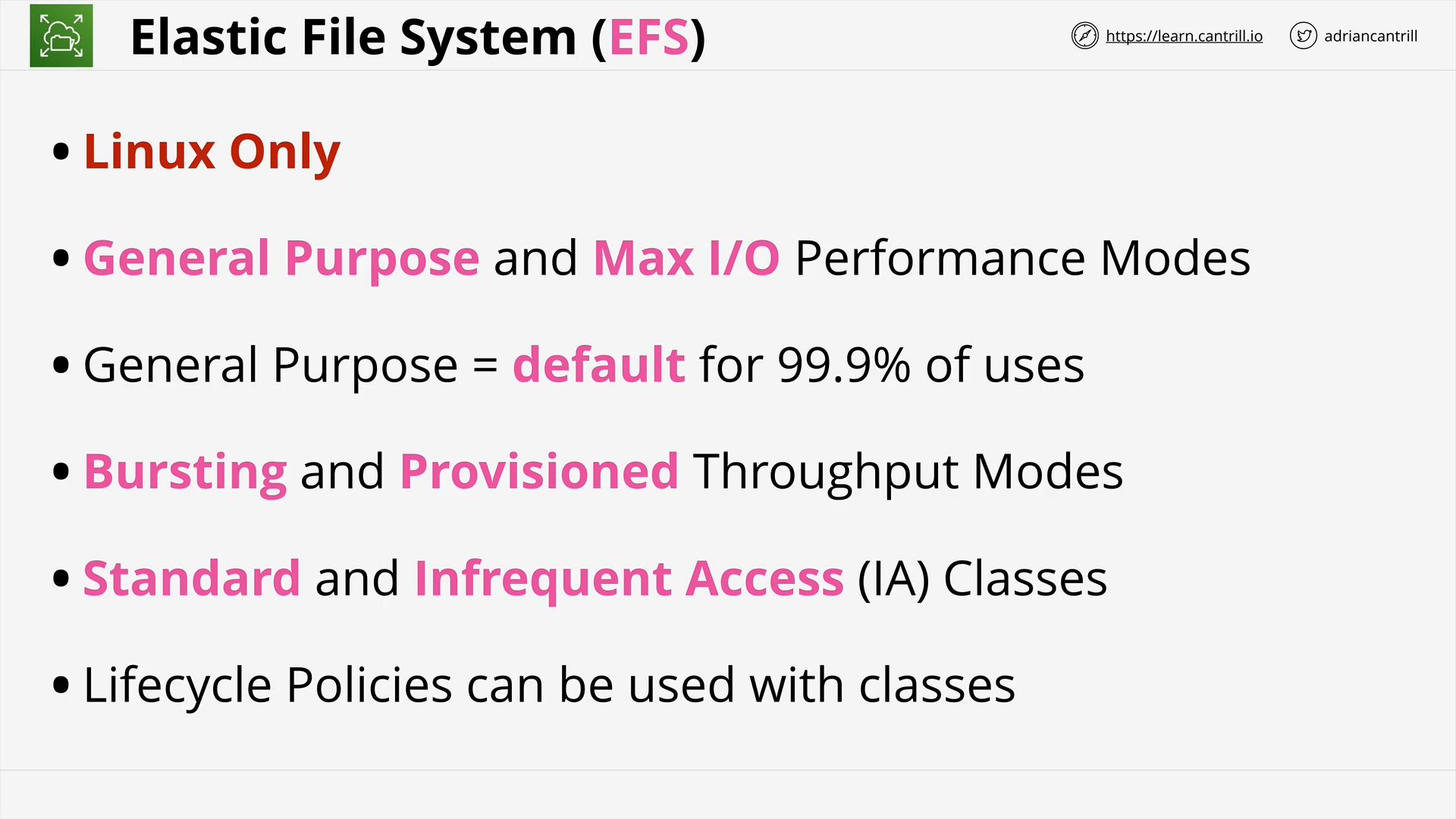 EFS - Performance
EFS - Performance
which configuration impact an [efs performance](https://docs.aws.amazon.com/efs/latest/ug/performance.html)?
-
Storage Class:
- EFS
One Zone/ One Zone-IA - EFS
Standard/ Standard-IA - EFS
Archive
- EFS
-
Performance Mode:
General Purposemode (default - 99.9% of uses): Lowest latencyMax I/Omode: Highly parallelized workloads that can tolerate higher latencies
-
Throughput Mode:
Burstingmode: Throughput scale with storage- Enhanced
Elasticmode (default - recommend): Spiky/unpredictable workloadsProvisionedmode: Known performace requirements; or throughput > 5% average-to-peak ratio
[DEMO] Implementing EFS - PART1 (8:51)
[DEMO] Implementing EFS - PART2 (11:32)
[DEMO] Using EFS with Wordpress (16:00)
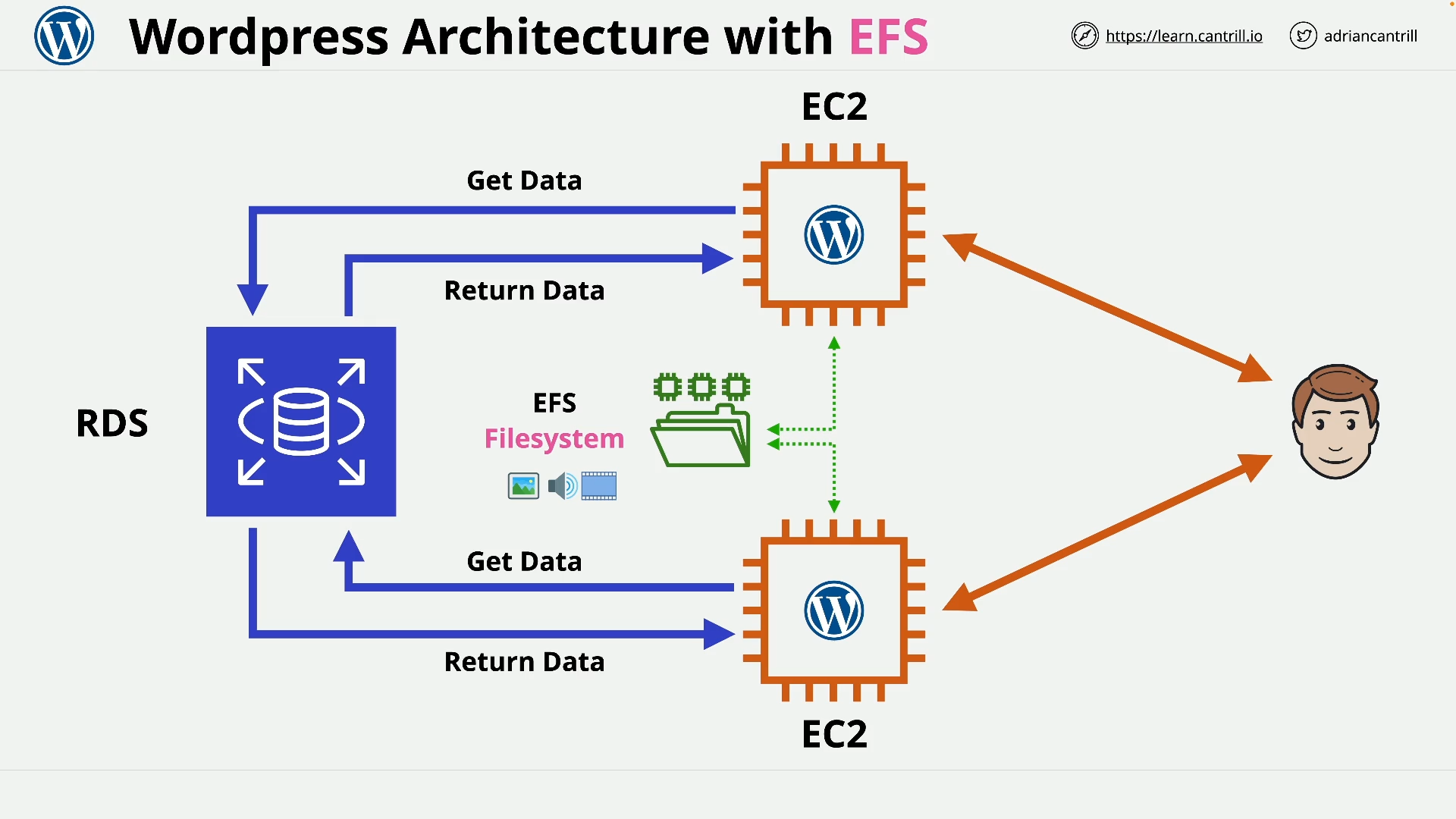
AWS Backup (6:36)
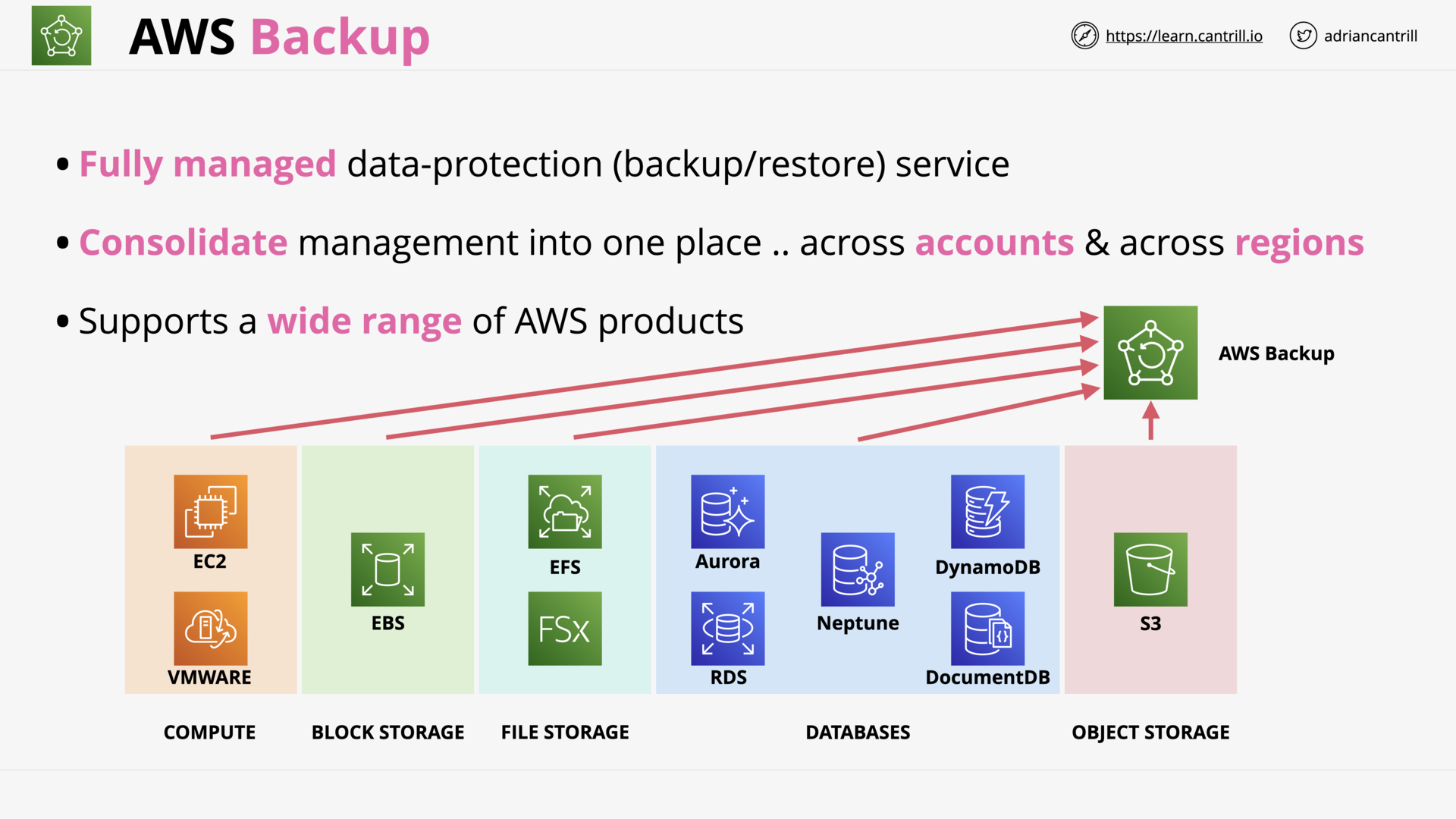 AWS Backup supports a wide range of AWS services
AWS Backup supports a wide range of AWS services
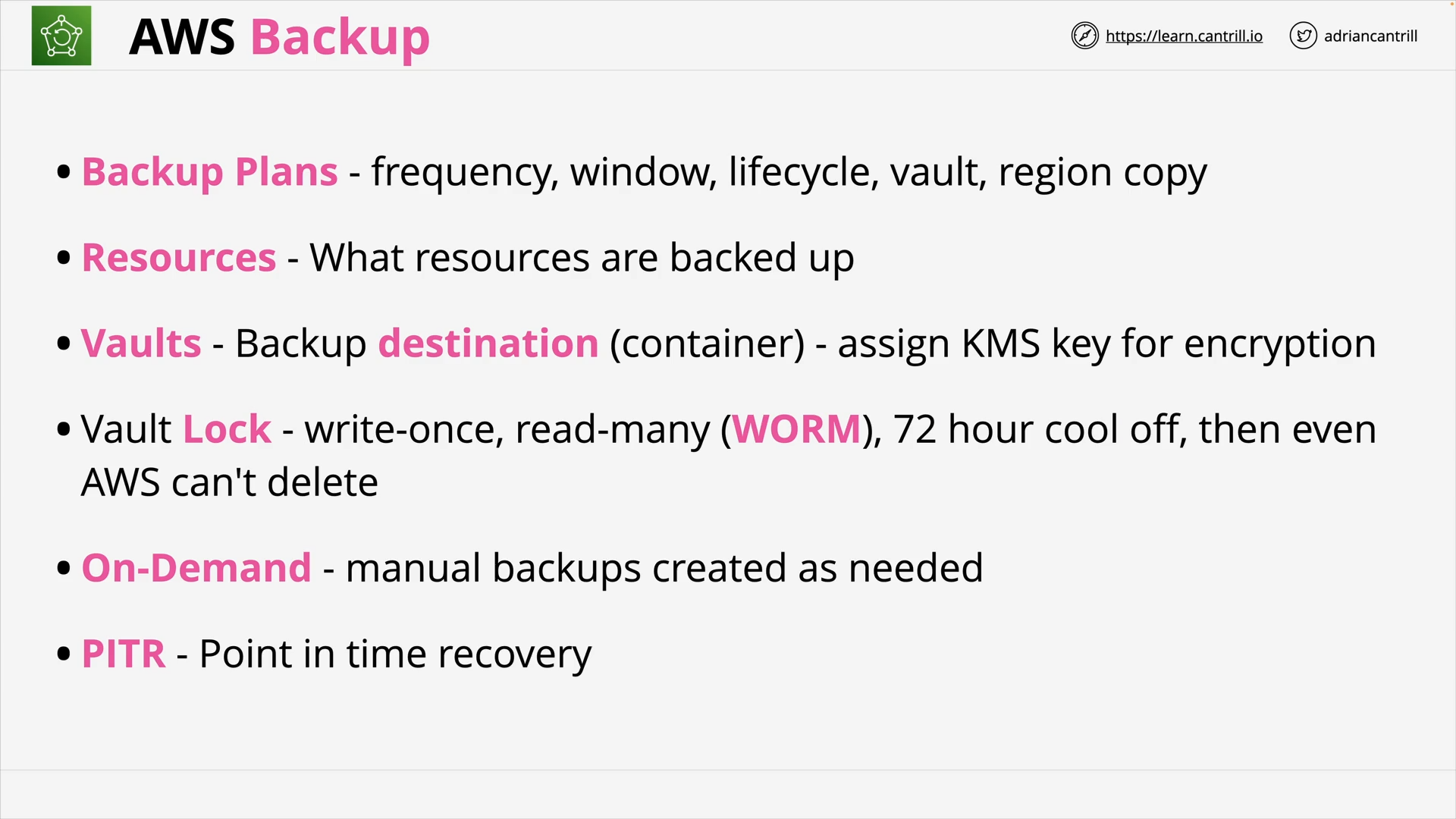 AWS Backup - Summary
AWS Backup - Summary
Network Storage Section Quiz
HA & SCALING
Regional and Global AWS Architecture (10:42)
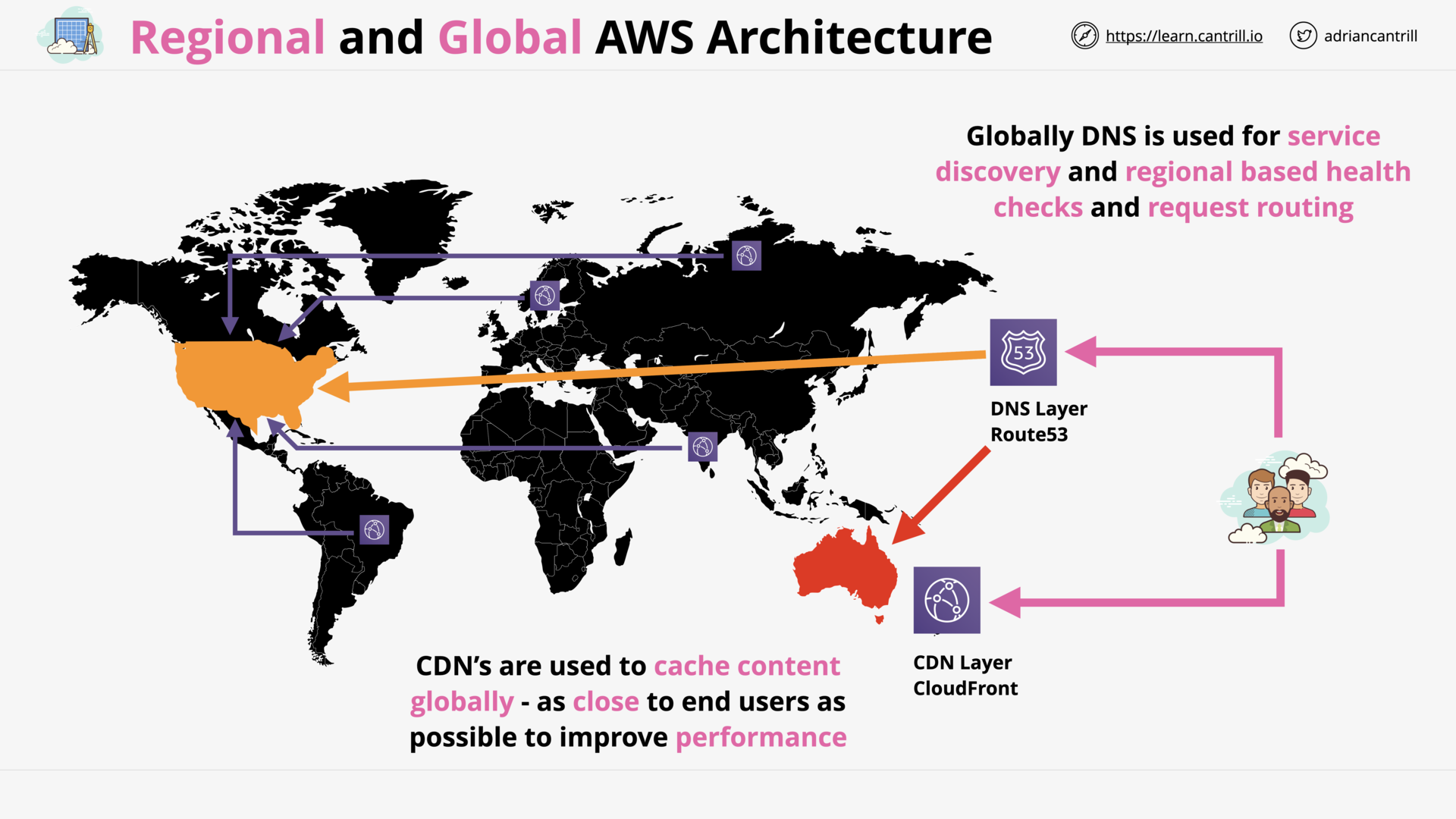 Regional & Global AWS Architecture
Regional & Global AWS Architecture
 Regional & Global Components
Regional & Global Components
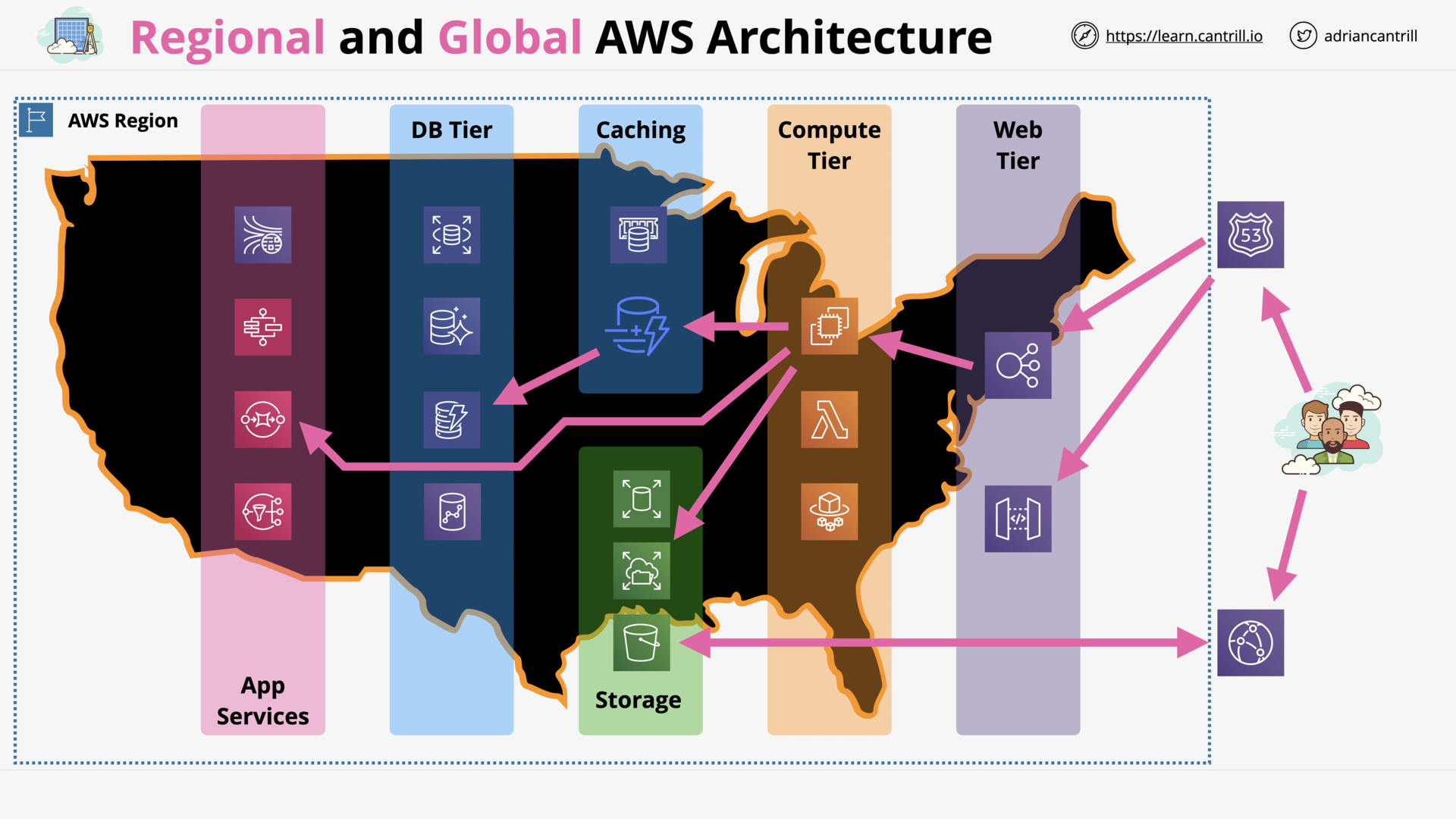 The tiers (components) of an application
The tiers (components) of an application
Evolution of the Elastic Load Balancer (4:10)
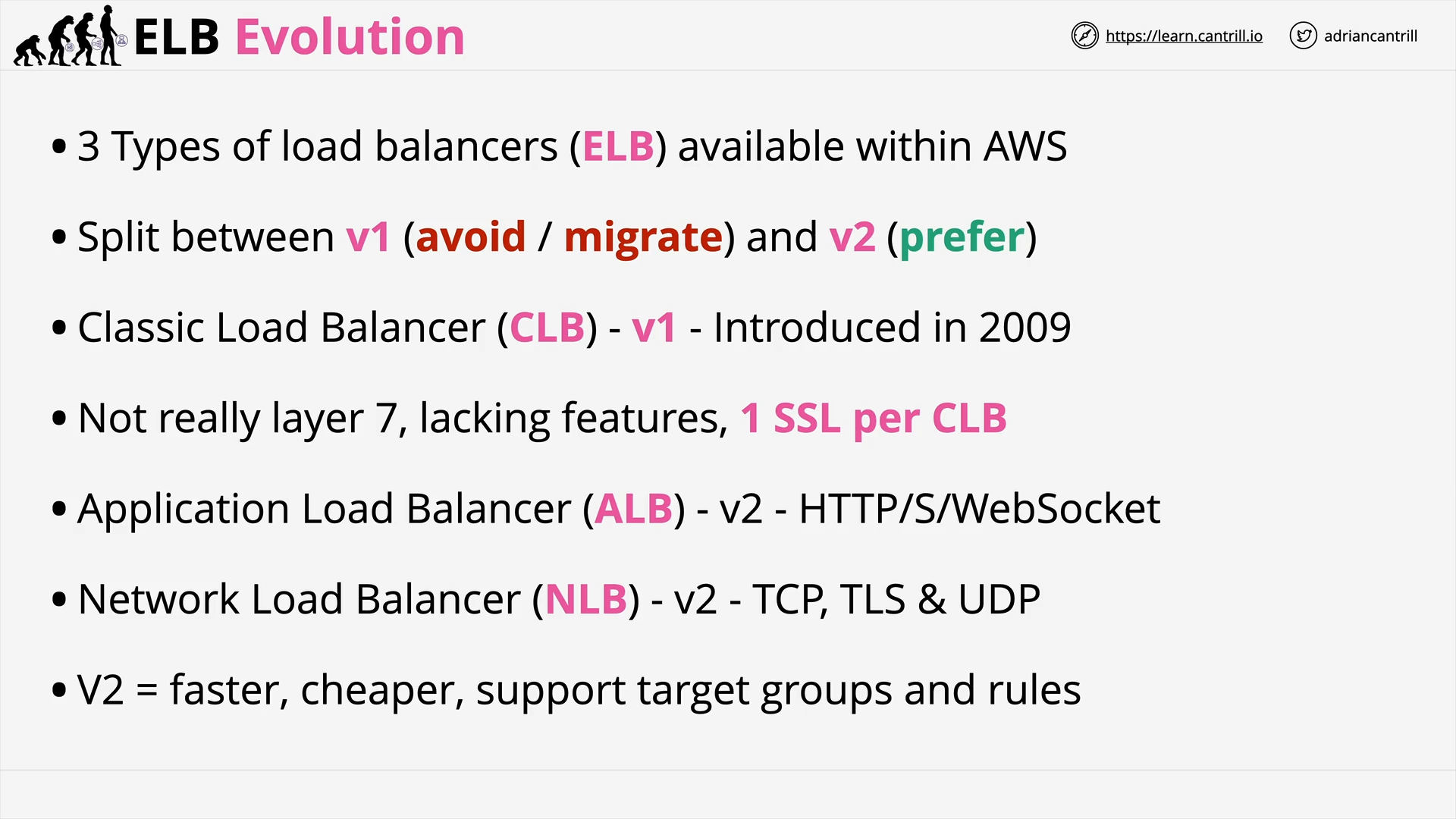 Elastic Load Balancer (ELB) - Evolution
Elastic Load Balancer (ELB) - Evolution
what are the 3 types of load balancers in aws?
- v1:
- Classic Load Balancer (CLB): 2009
- v2:
- Application Load Balancer (ALB): HTTP/s, gRPC 👈 Layer 4
- Network Load Balancer (NLB): TCP/UDP, TLS 👈 Layer 7
- Gateway LB (GWLB)
Elastic Load Balancer Architecture - PART1 (10:18)
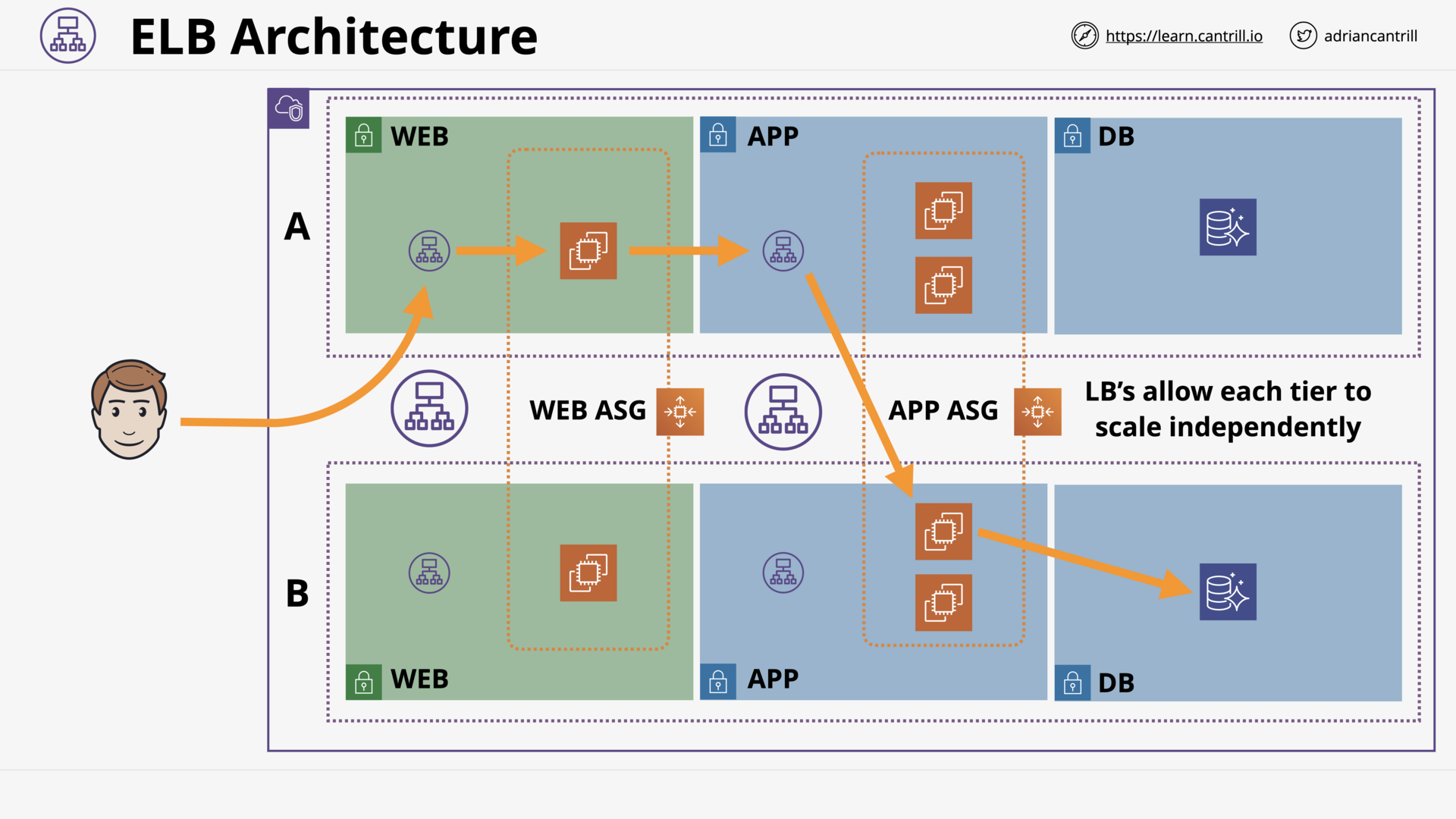 ELB - Architecture
ELB - Architecture
what is the benefits of load balancer?
- Distributing workloads across multiple compute resources 👉 HA & FT
- Decoupling application tiers 👉 ↕️ compute resources without disrupting the overall flow of our app.
- Or:
- Sending request only to healthy ones.
- Offloading encryption/decryption from computer resources to LB.
(Source)
Elastic Load Balancer Architecture - PART2 (12:32)
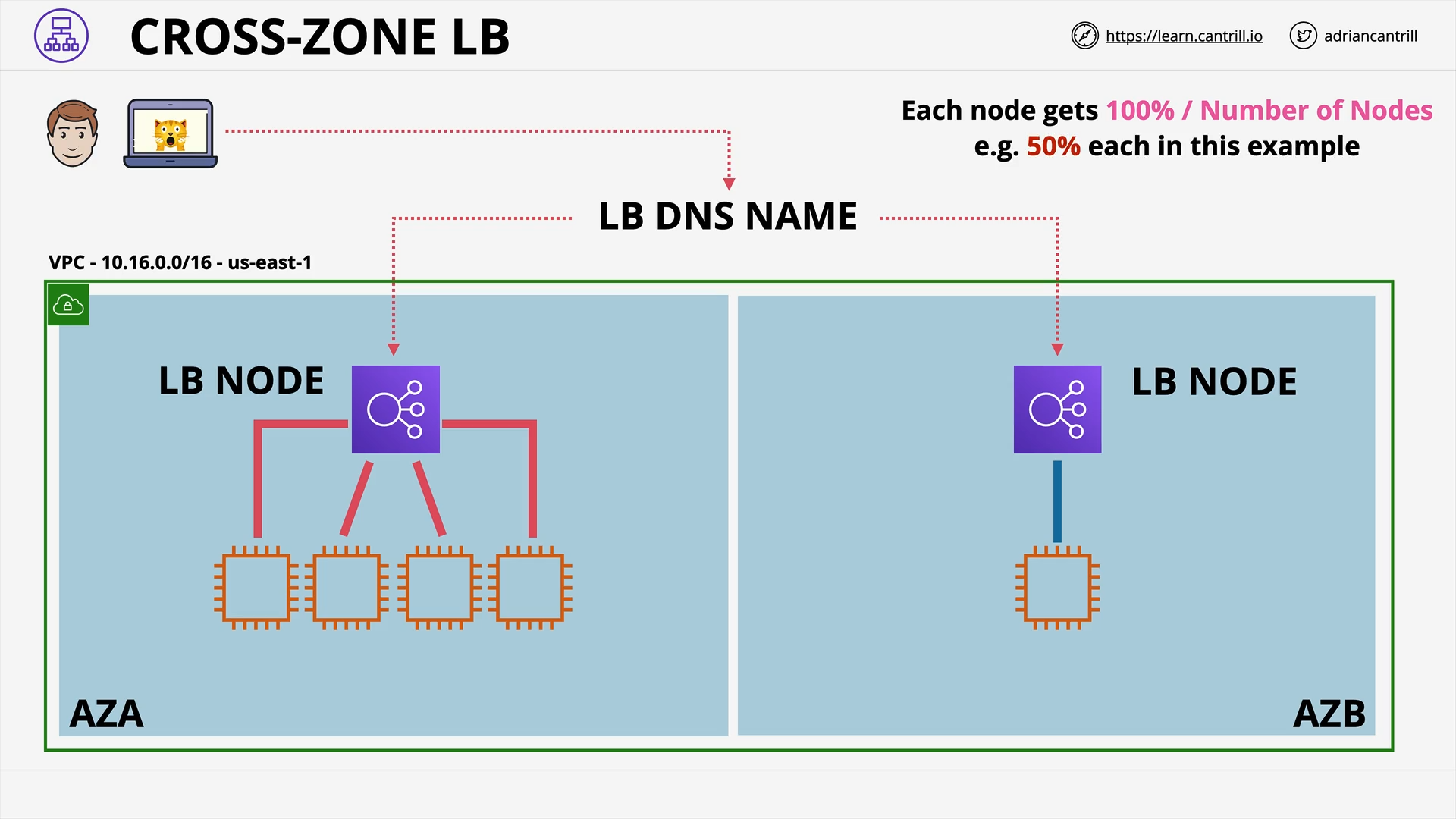 ELB - Without Cross-Zone LB
ELB - Without Cross-Zone LB
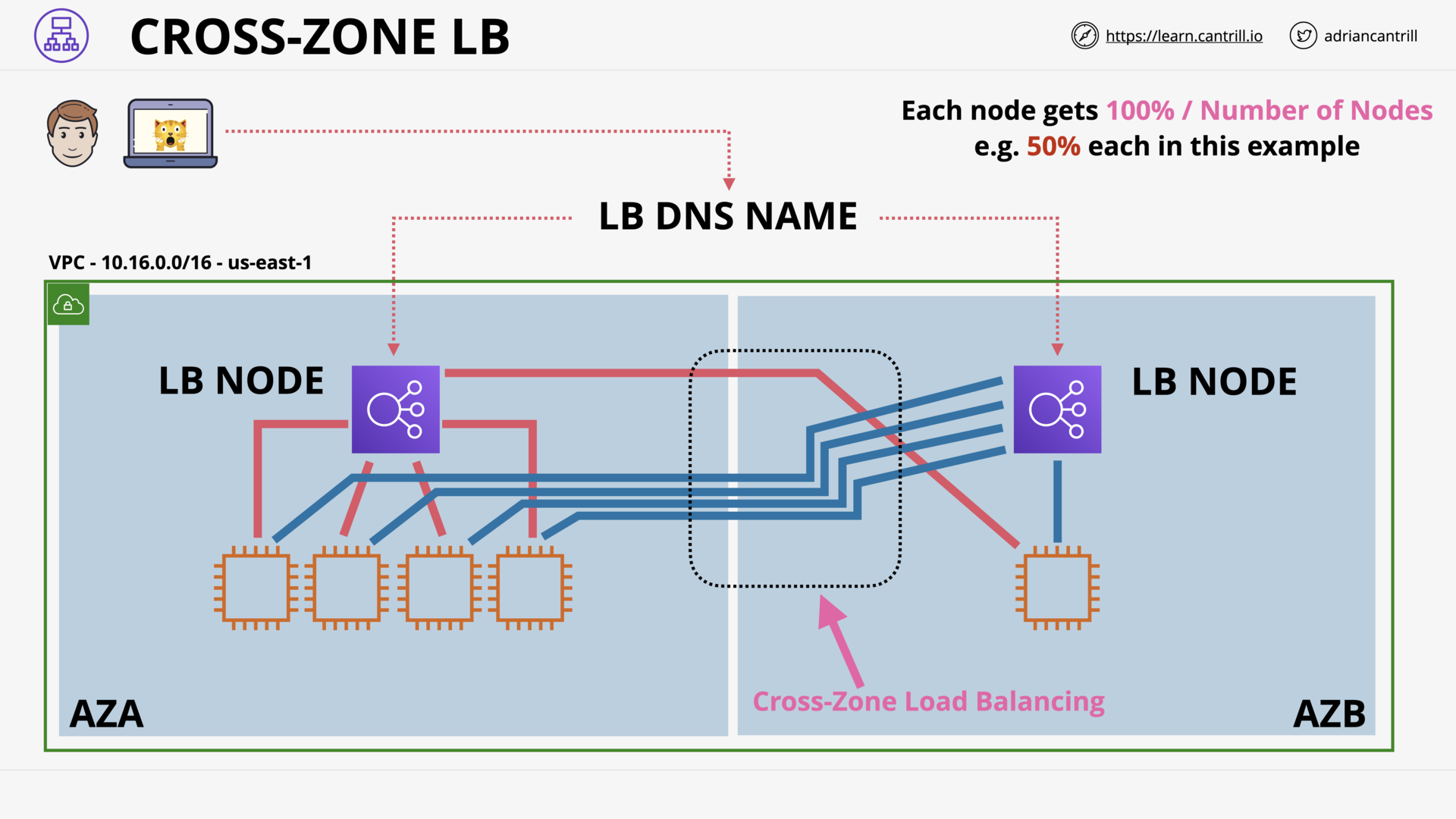 ELB - With Cross-Zone LB
ELB - With Cross-Zone LB
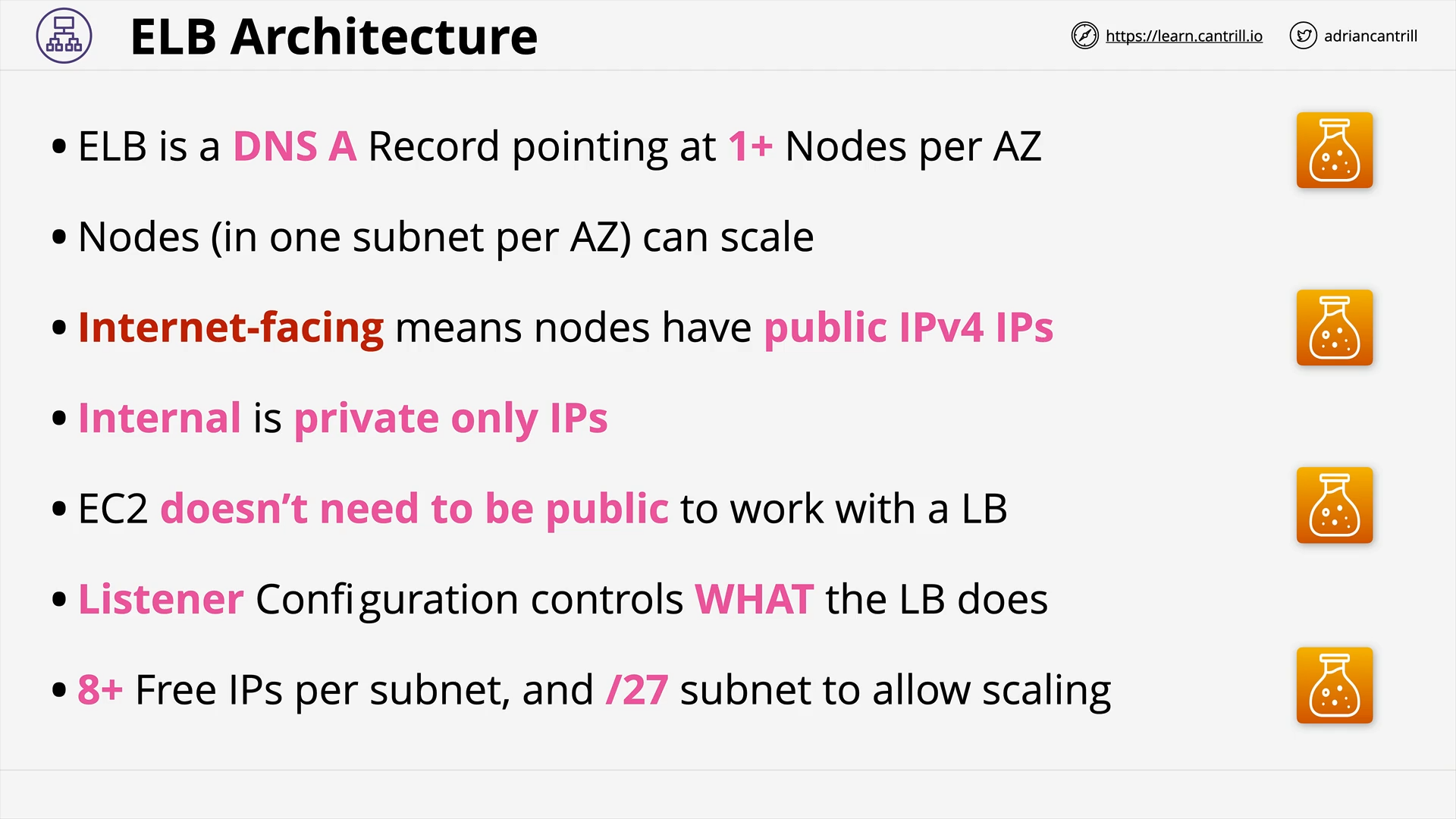 ELB - Summary
ELB - Summary
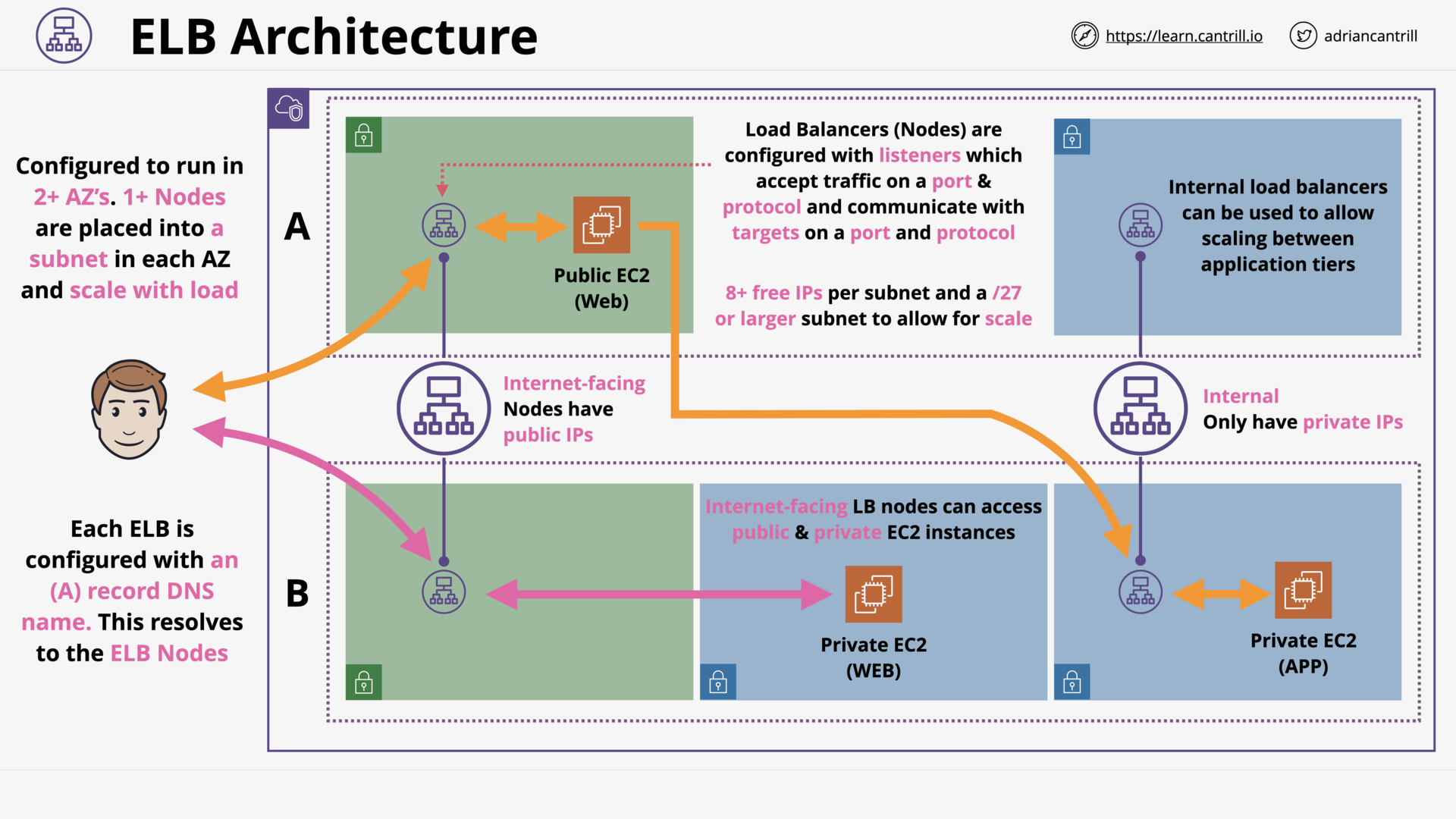 ELB - Internet-facing LB & Internal LB
ELB - Internet-facing LB & Internal LB
what are 2 types [scheme](https://docs.aws.amazon.com/elasticloadbalancing/latest/userguide/how-elastic-load-balancing-works.html#load-balancer-scheme) of aws elb?
- Internet-facing LB: the nodes have public IP addresses.
- Internal LB: the nodes have only private IP addresses.
Application Load balancing (ALB) vs Network Load Balancing (NLB) (16:20)
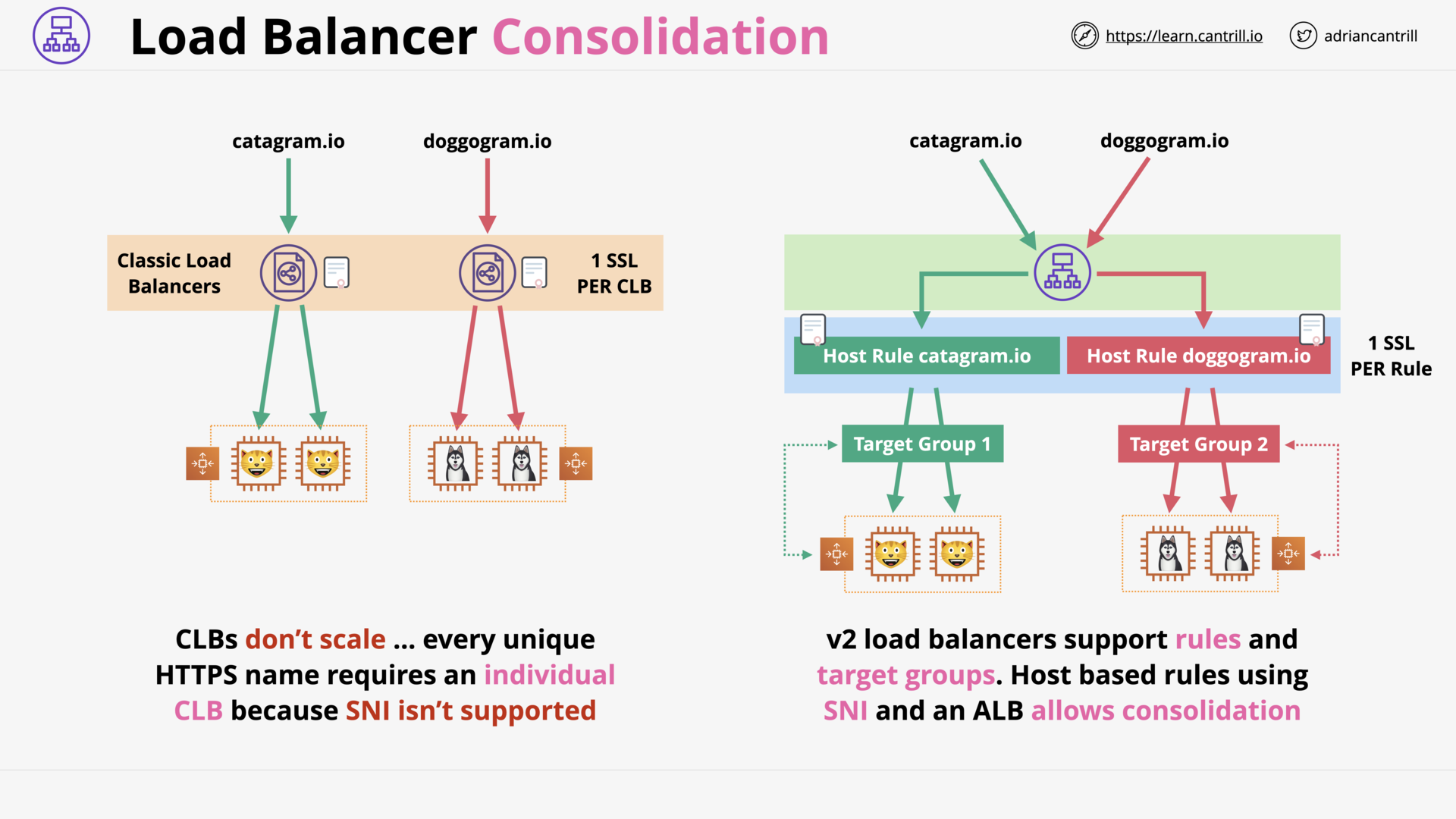 LB Consolidation 🏳️🌈
LB Consolidation 🏳️🌈
why aws classic load balancer don't scale?
CLB don’t support TLS Server Name Indicator (SNI).
😭 Every unique host name requires an individual CLB.
what is lb consolidation?
When multiple websites are hosted on one server (the LB) and share a single IP address.
how does aws v2 lbs allows consolidation?
AWS v2 ALB support rules and target groups.
Using an ALB and its rules based on TLS SNI allows consolidation.
_vs_Ne.png) ALB
ALB
_vs_Ne.png) ALB - Rules
ALB - Rules
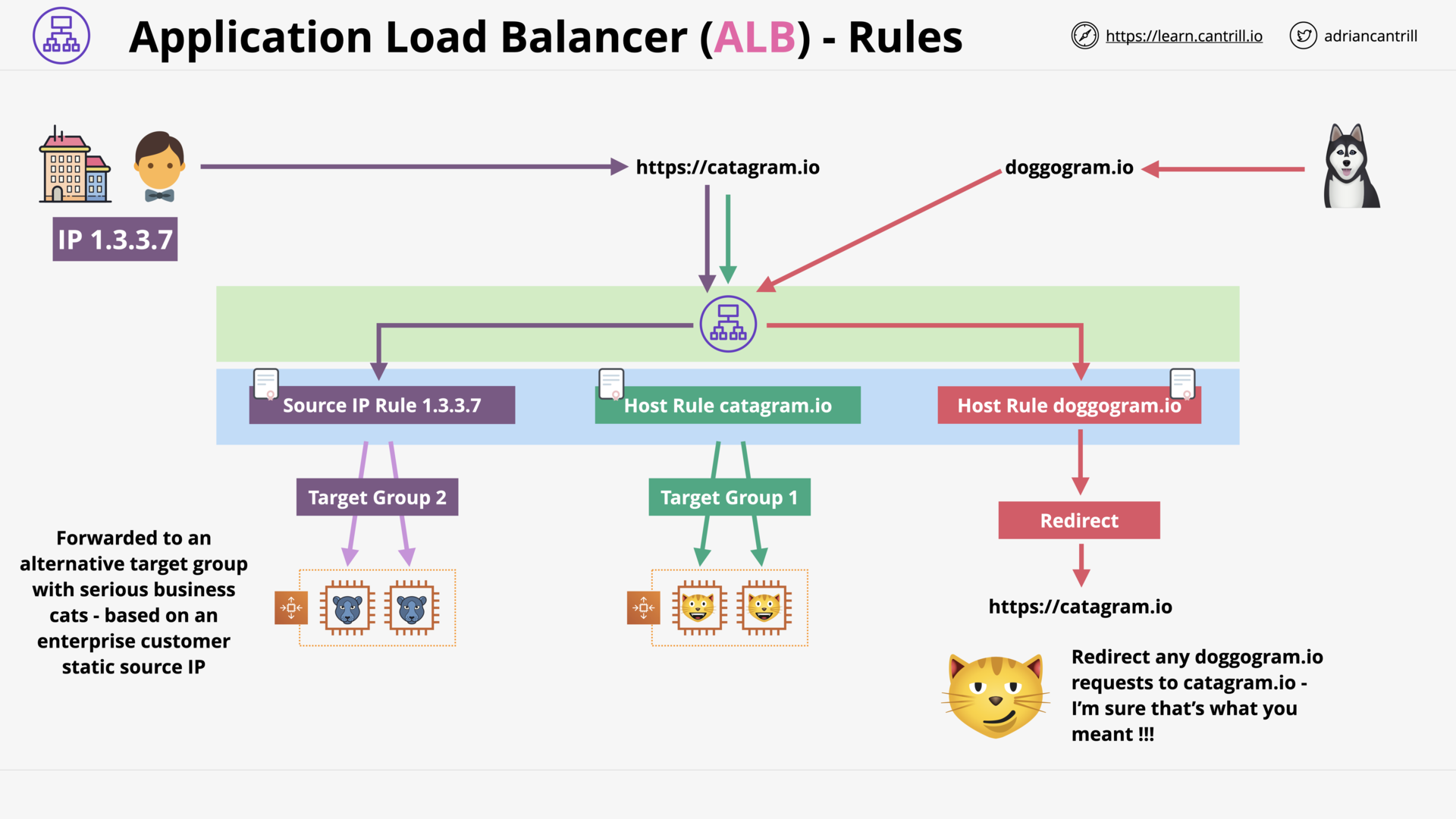 ALB - Rules Example
ALB - Rules Example
_vs_Ne.png) NLB
NLB
_vs_Ne.png) NLB vs ALB - Exam Tips
NLB vs ALB - Exam Tips
which type of elb can have a static ip?
Only NLB can have a static IP.
Launch Configuration and Templates (4:00)
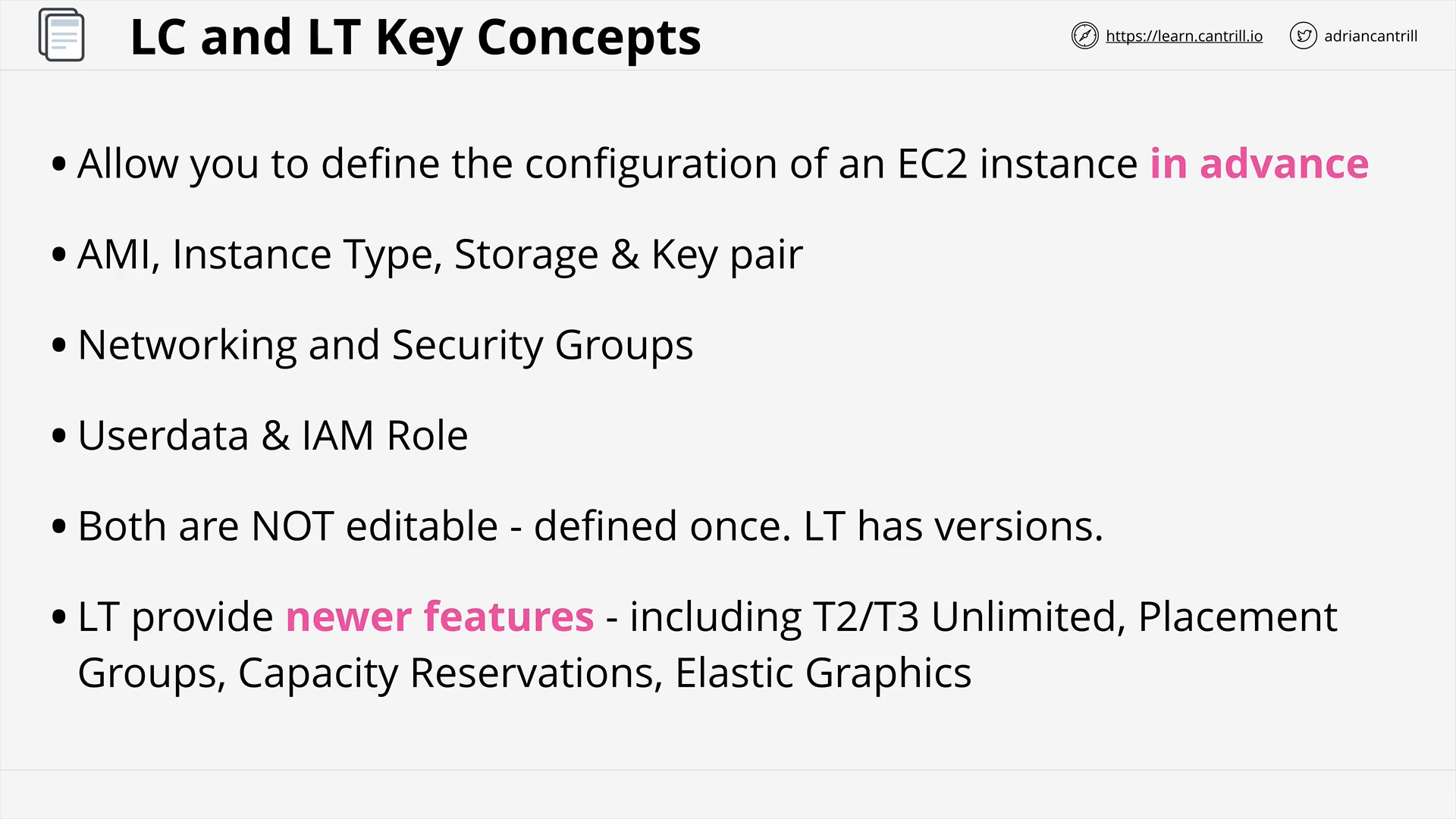 Launch Configuration (LC) & Launch Template (LT)
Launch Configuration (LC) & Launch Template (LT)
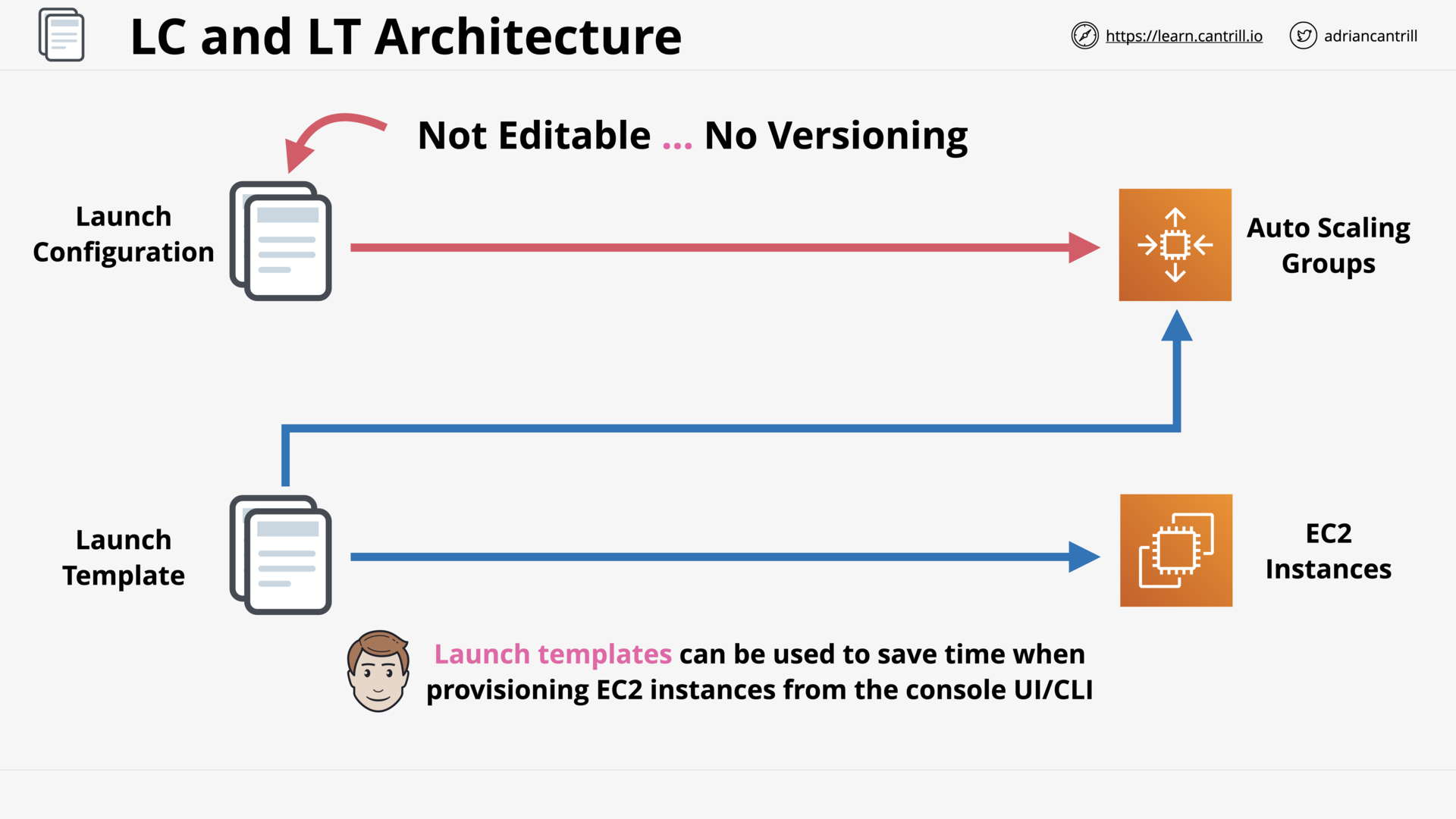 LC & LT - Architecture
LC & LT - Architecture
Auto-Scaling Groups (16:01)
 ASG - Automatic Scaling EC2 instances
ASG - Automatic Scaling EC2 instances
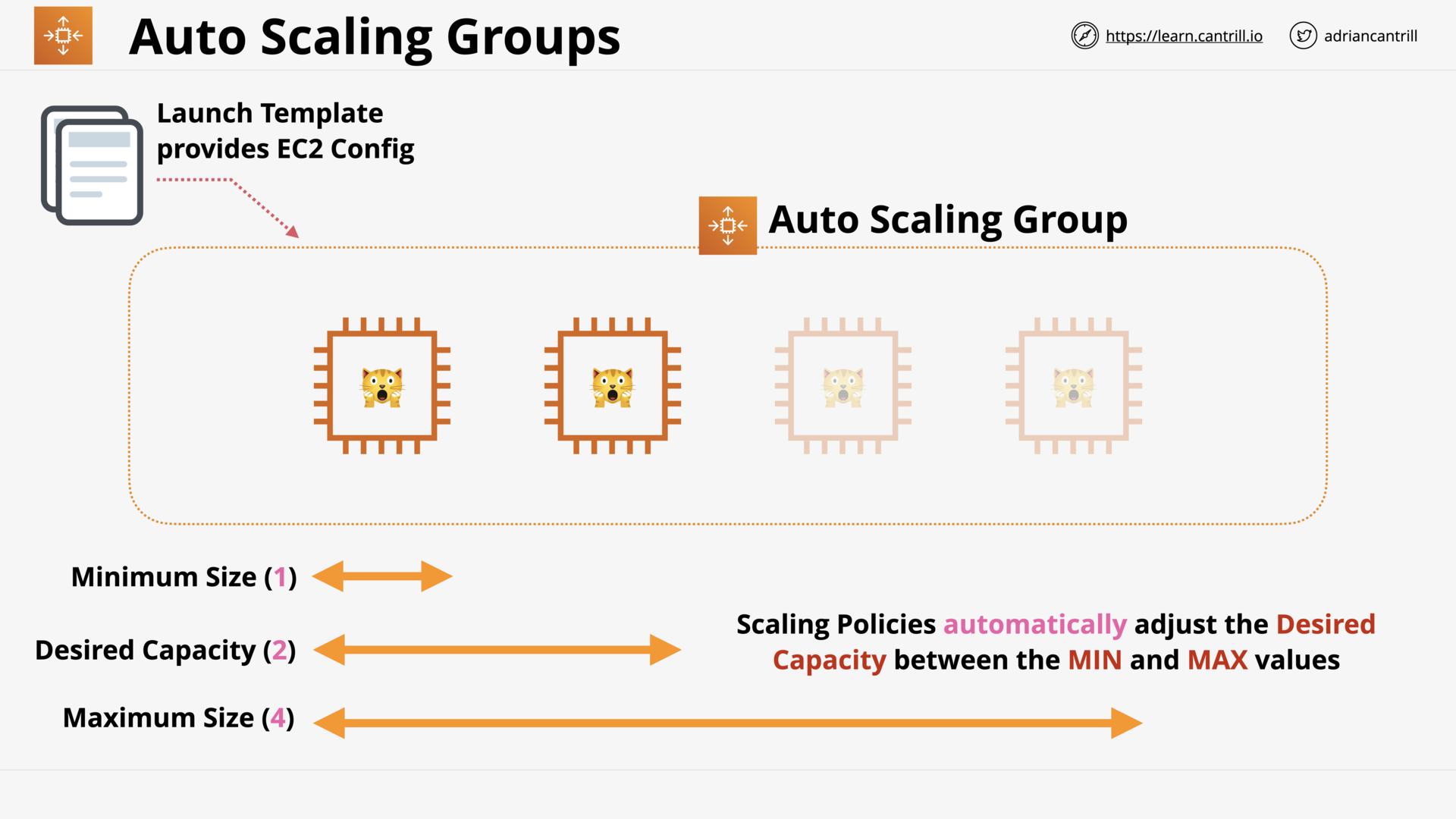 ASG - Scaling Polices automatically adjust the Desired Capacity
ASG - Scaling Polices automatically adjust the Desired Capacity
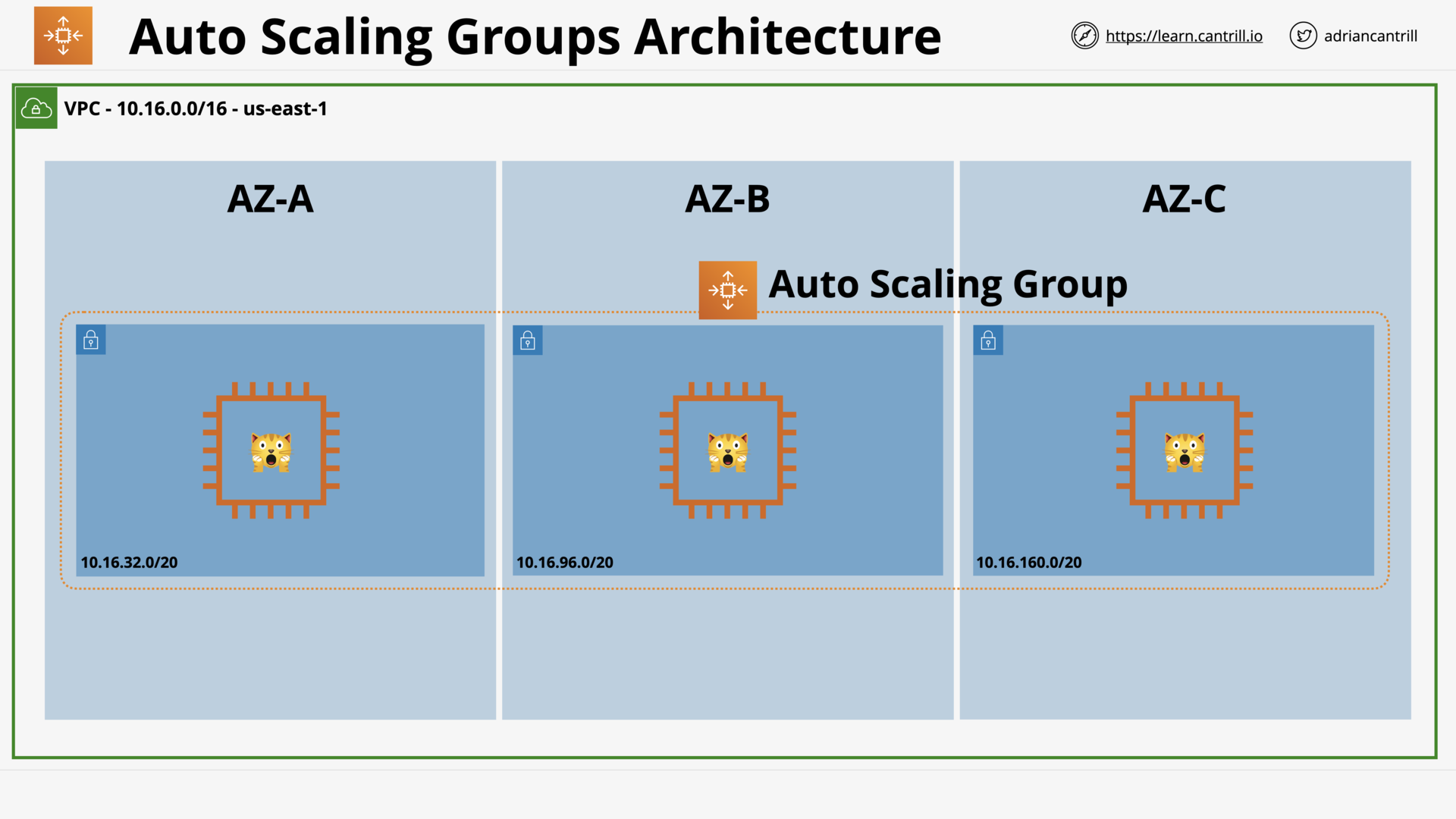 ASG - Architecture
ASG - Architecture
 ASG - Scaling Polices
ASG - Scaling Polices
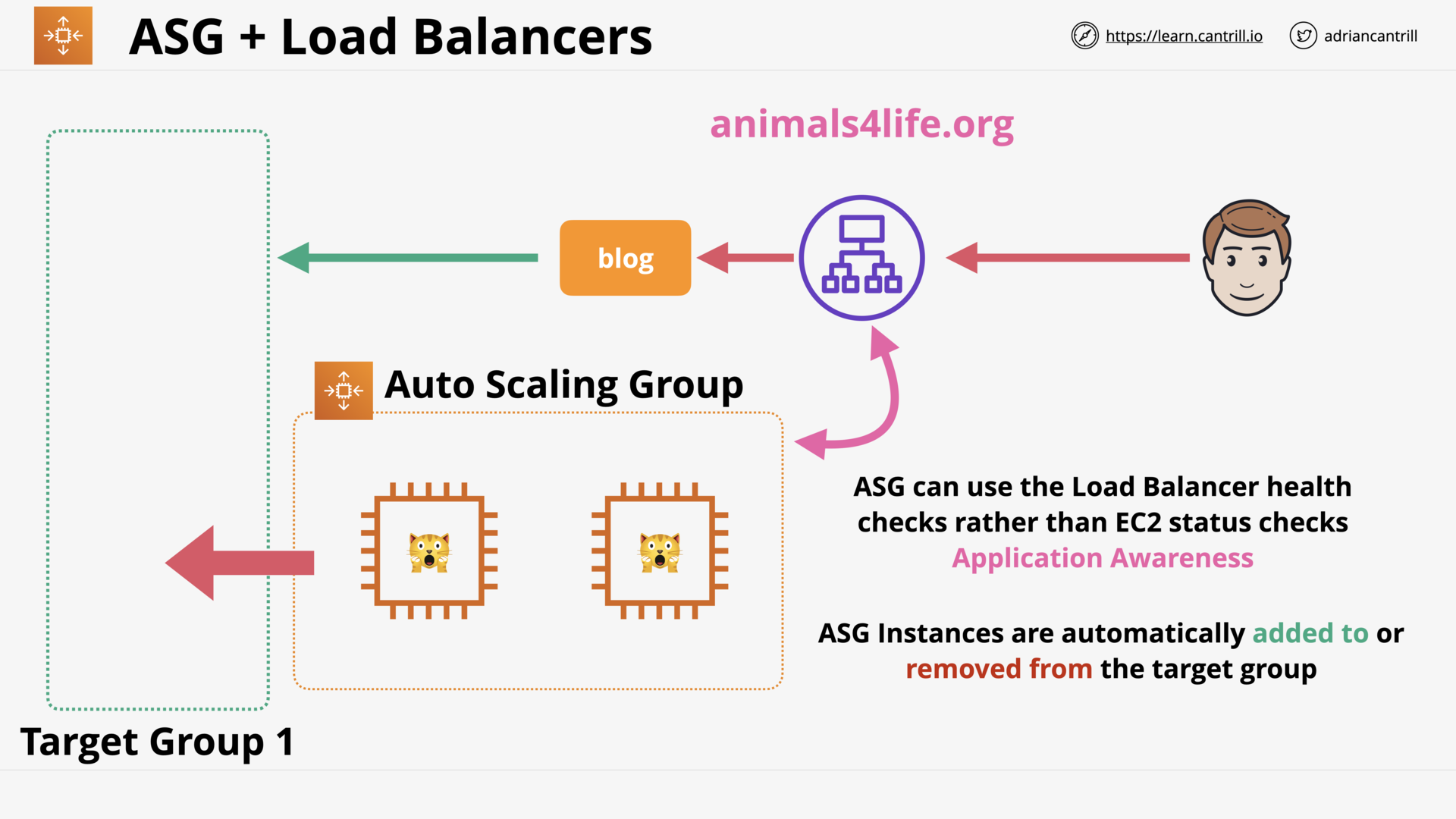 ASG + LBs
ASG + LBs
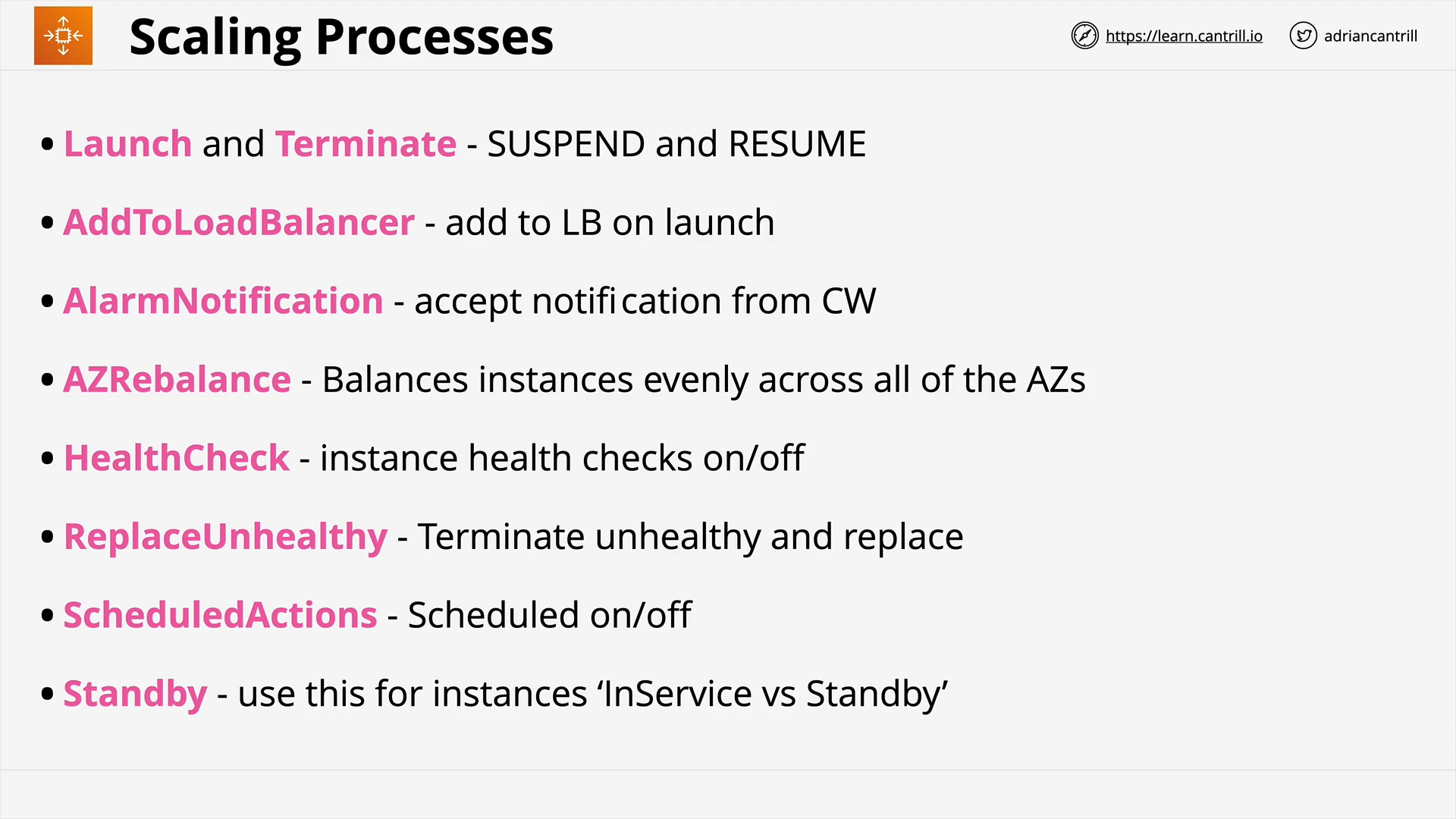 ASG - Scaling Processes
ASG - Scaling Processes
 ASG - Summary
ASG - Summary
ASG Scaling Policies (10:23)
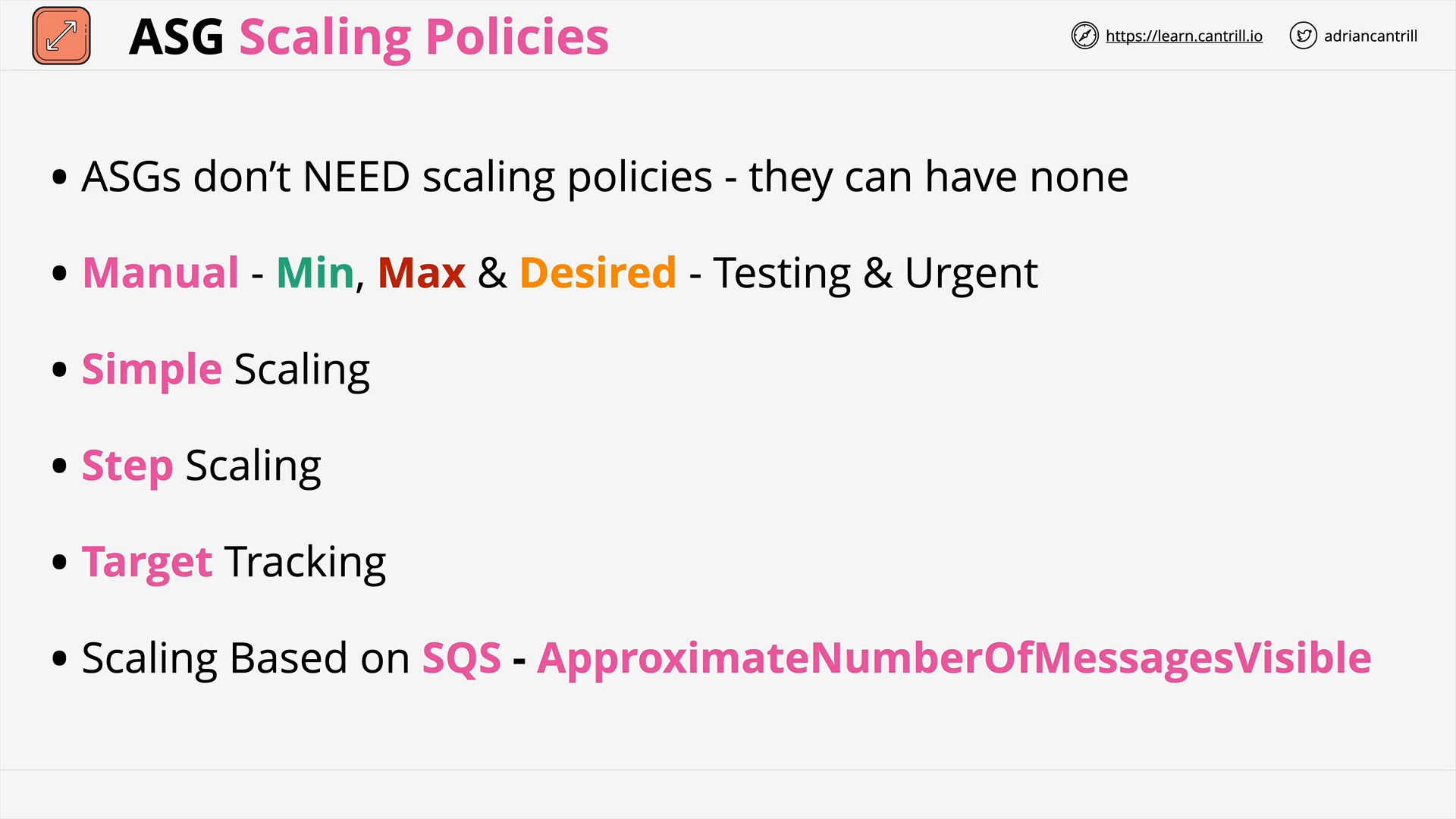 ASG Scaling Policies
ASG Scaling Policies
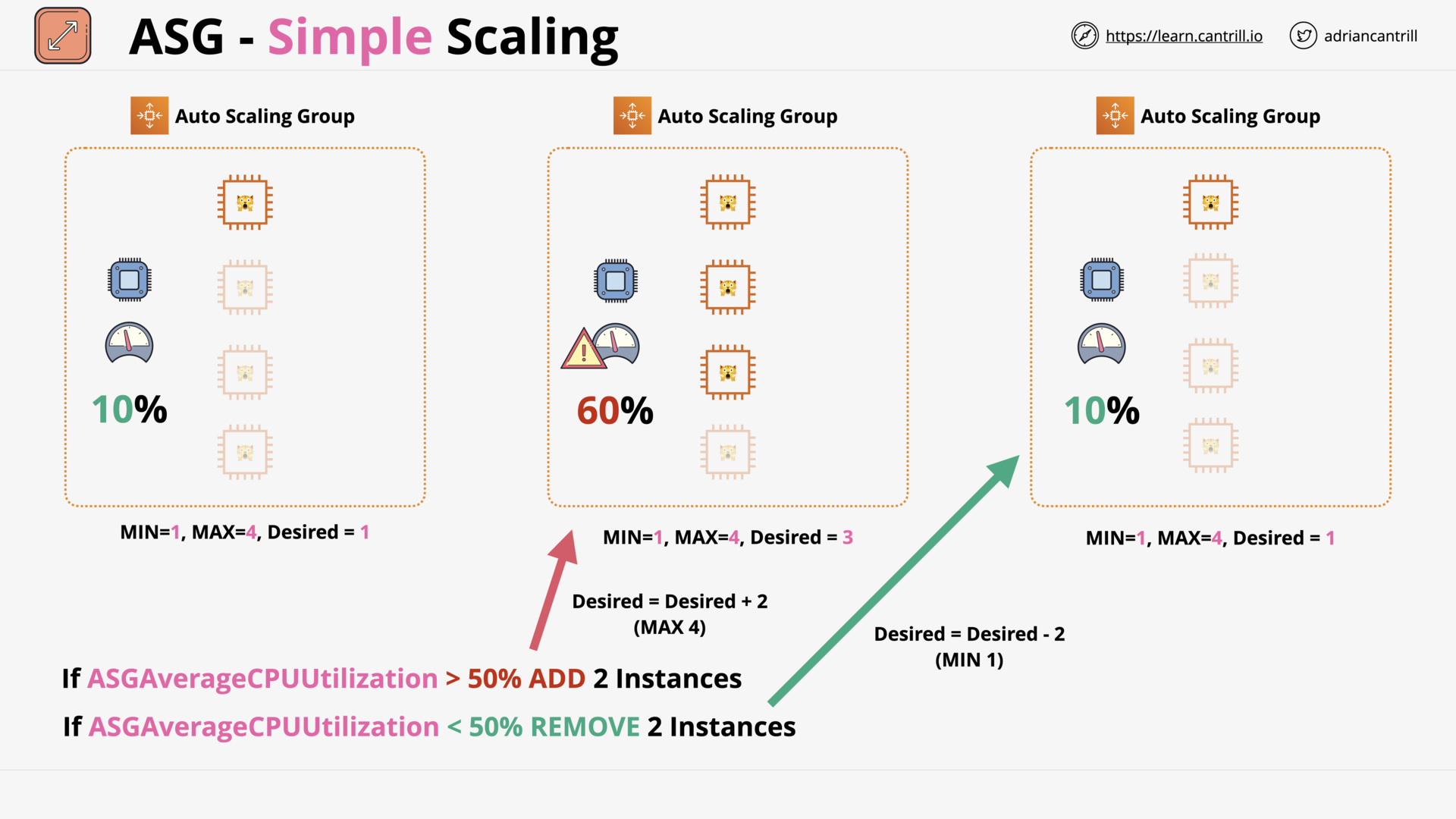 ASG Scaling Policies - Simple Scaling
ASG Scaling Policies - Simple Scaling
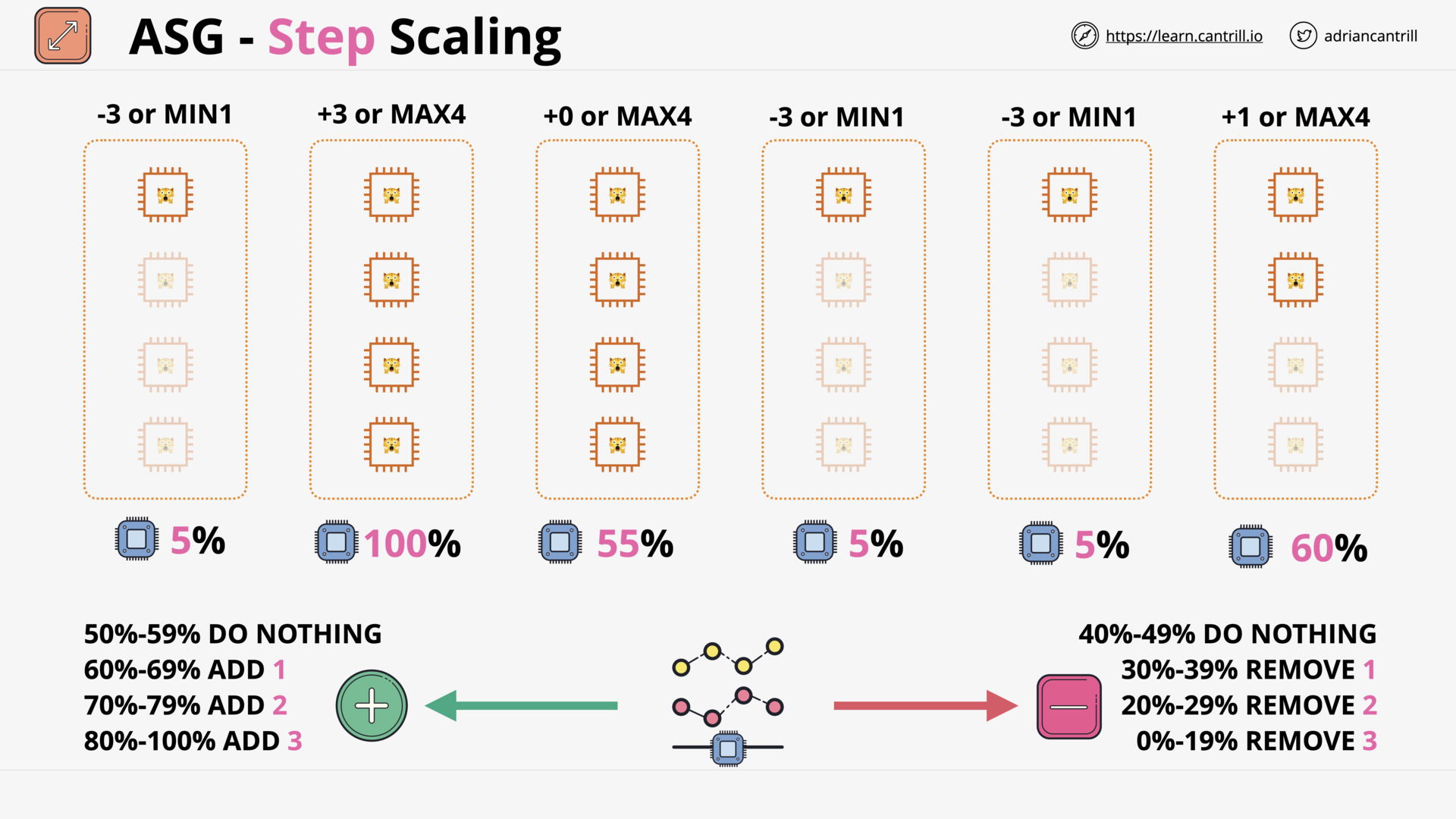 ASG Scaling Policies - Step Scaling
ASG Scaling Policies - Step Scaling
ASG Lifecycle Hooks (4:41)
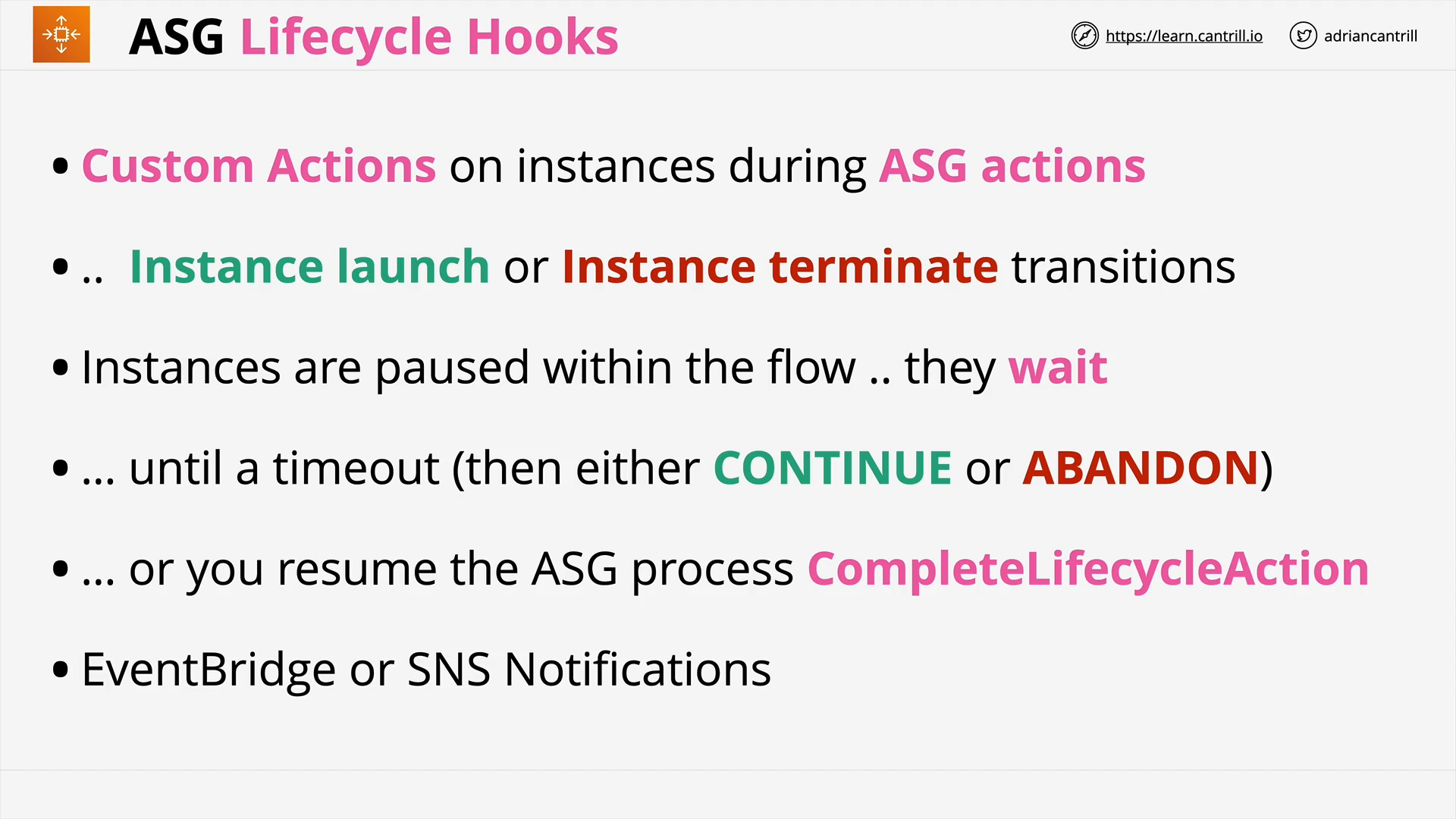 ASG Lifecycle Hooks
ASG Lifecycle Hooks
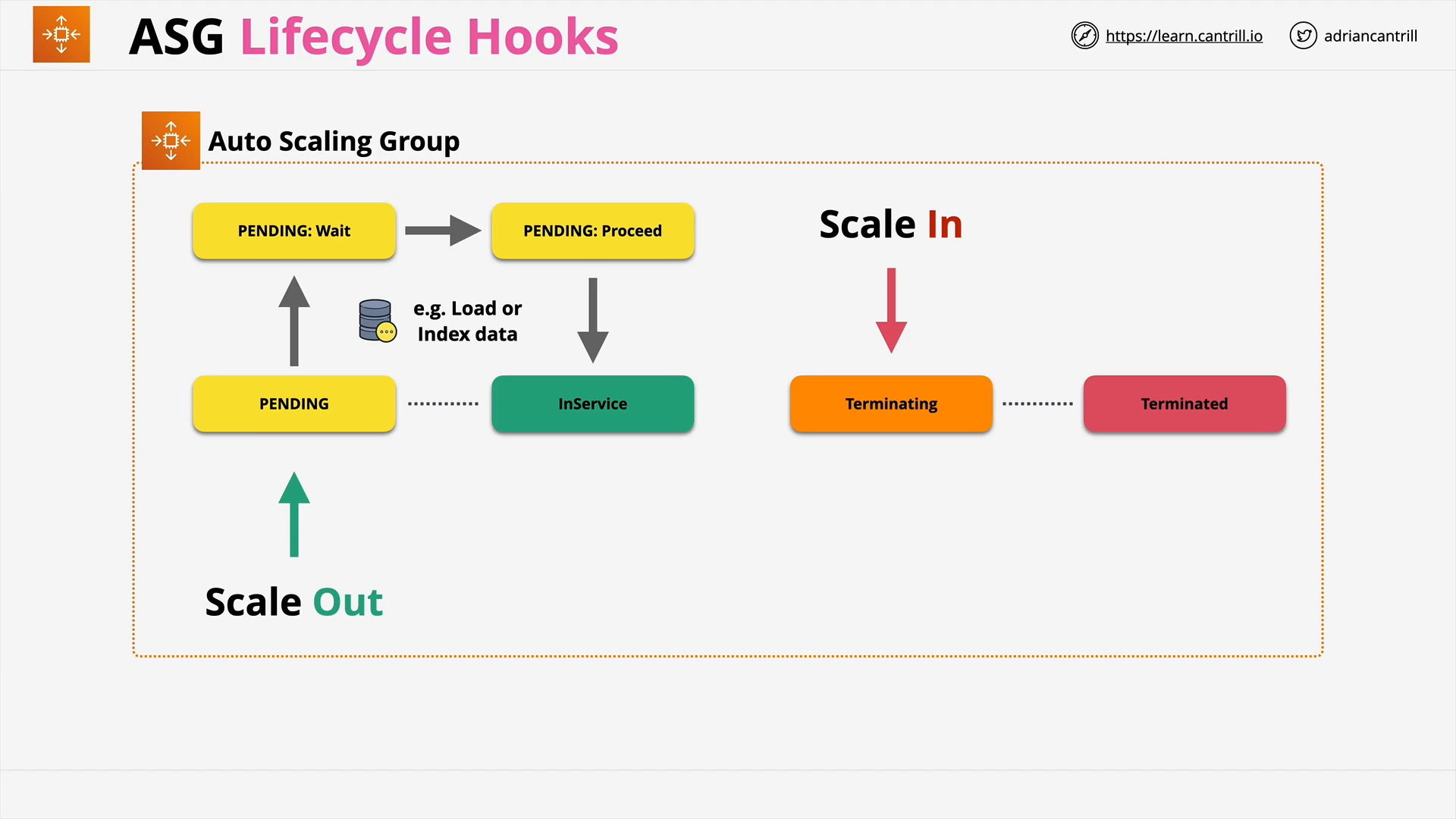 ASG - Without Lifecycle Hooks
ASG - Without Lifecycle Hooks
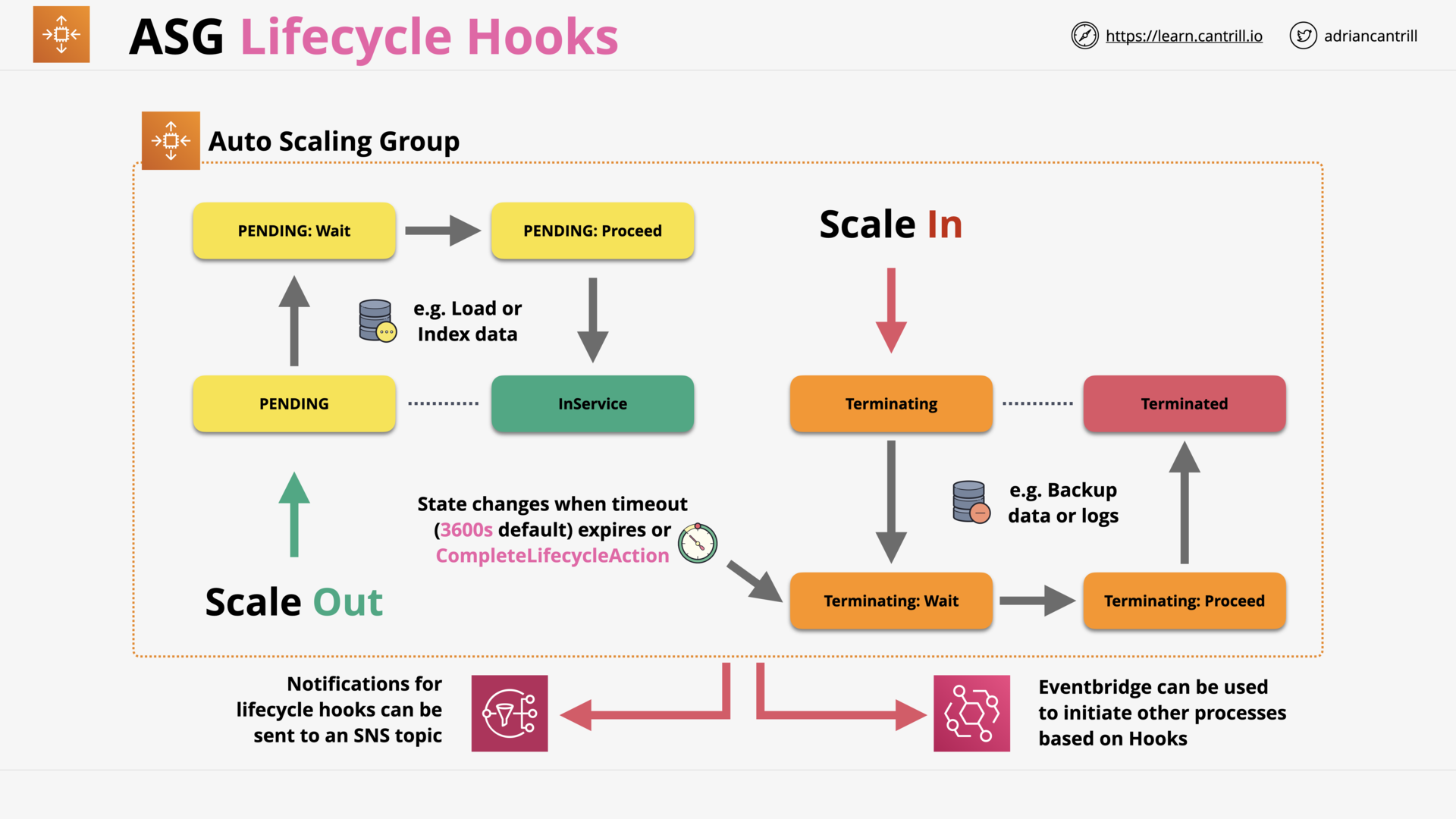 ASG - With Lifecycle Hooks
ASG - With Lifecycle Hooks
ASG HealthCheck Comparison - EC2 vs ELB (3:38)
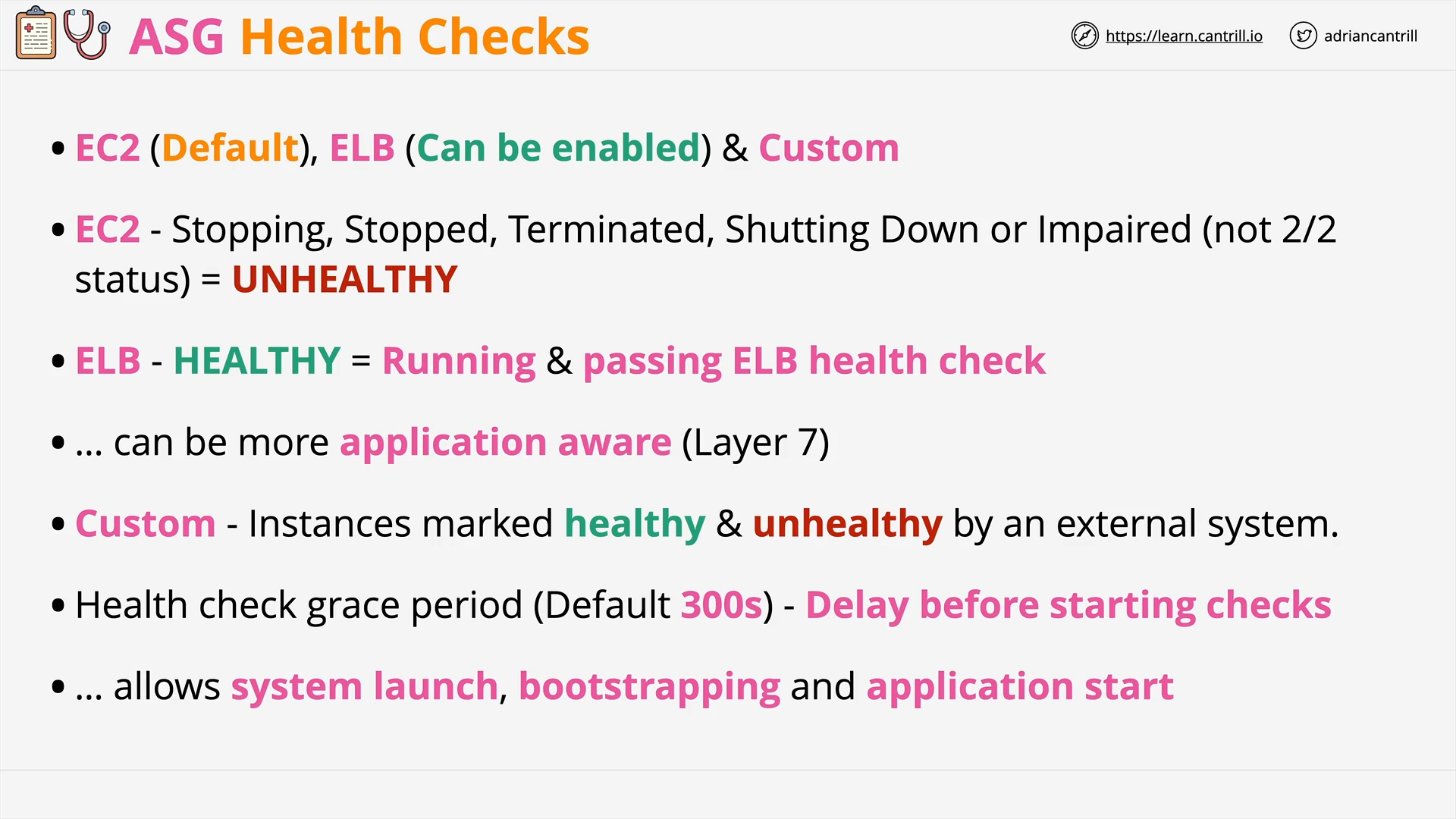 ASG - 3 types of HealthCheck
ASG - 3 types of HealthCheck
what are 3 types of asg healthcheck?
-
EC2 (Default)
- Hardware issue of EC2 host
- Software issue of EC2 instance
-
ELB
More application aware (Layer 7).
-
Custom
Instances mark healthy/unhealthy by an external system.s
SSL Offload & Session Stickiness (12:11)
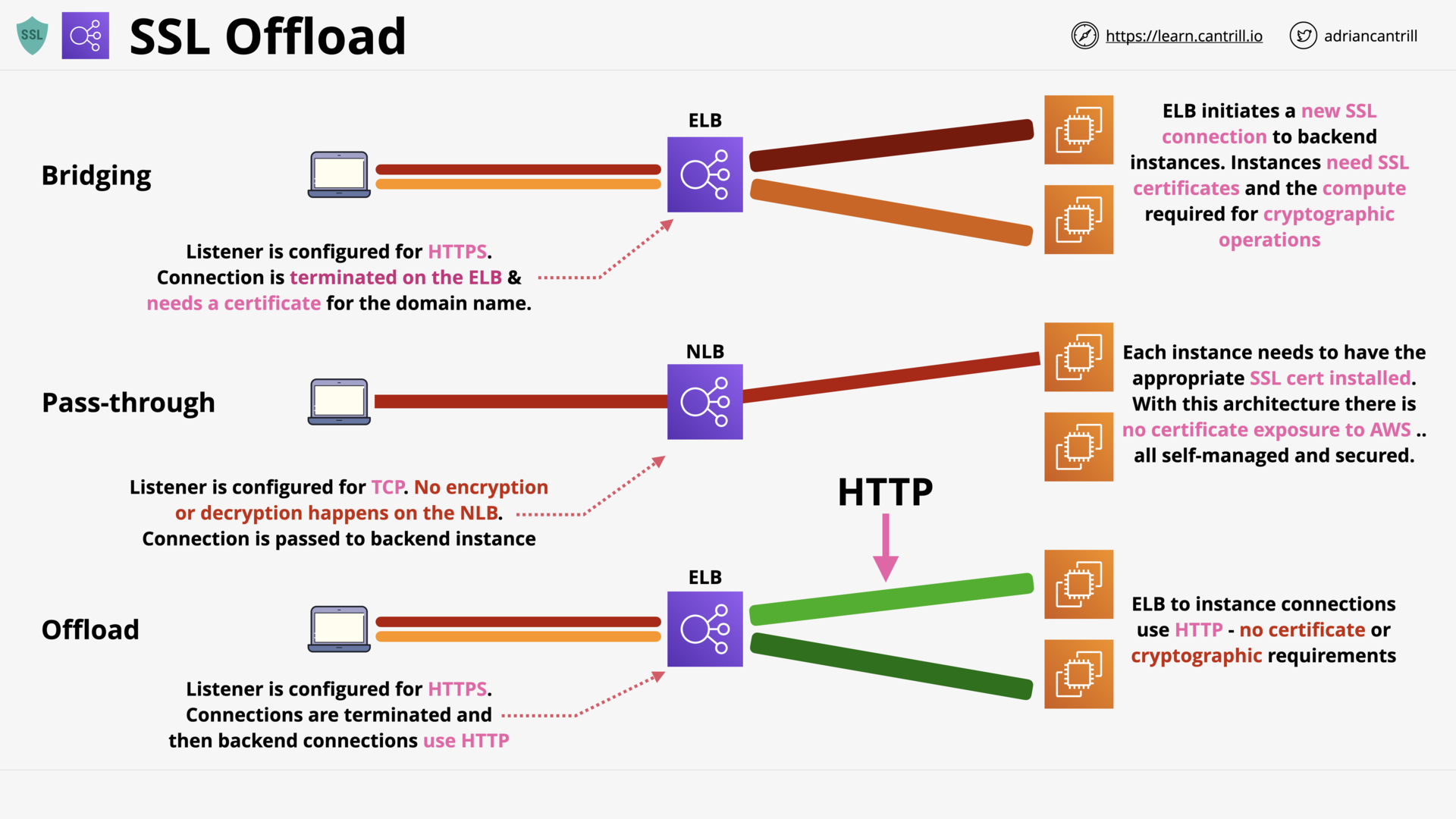 ELB - SSL Offload
ELB - SSL Offload
what are 3 ways that elb's can handle ssl?
- Bridging (Default): HTTPS <-> HTTPS
- Pass-through: TCP
- Offload: HTTPS <-> HTTP
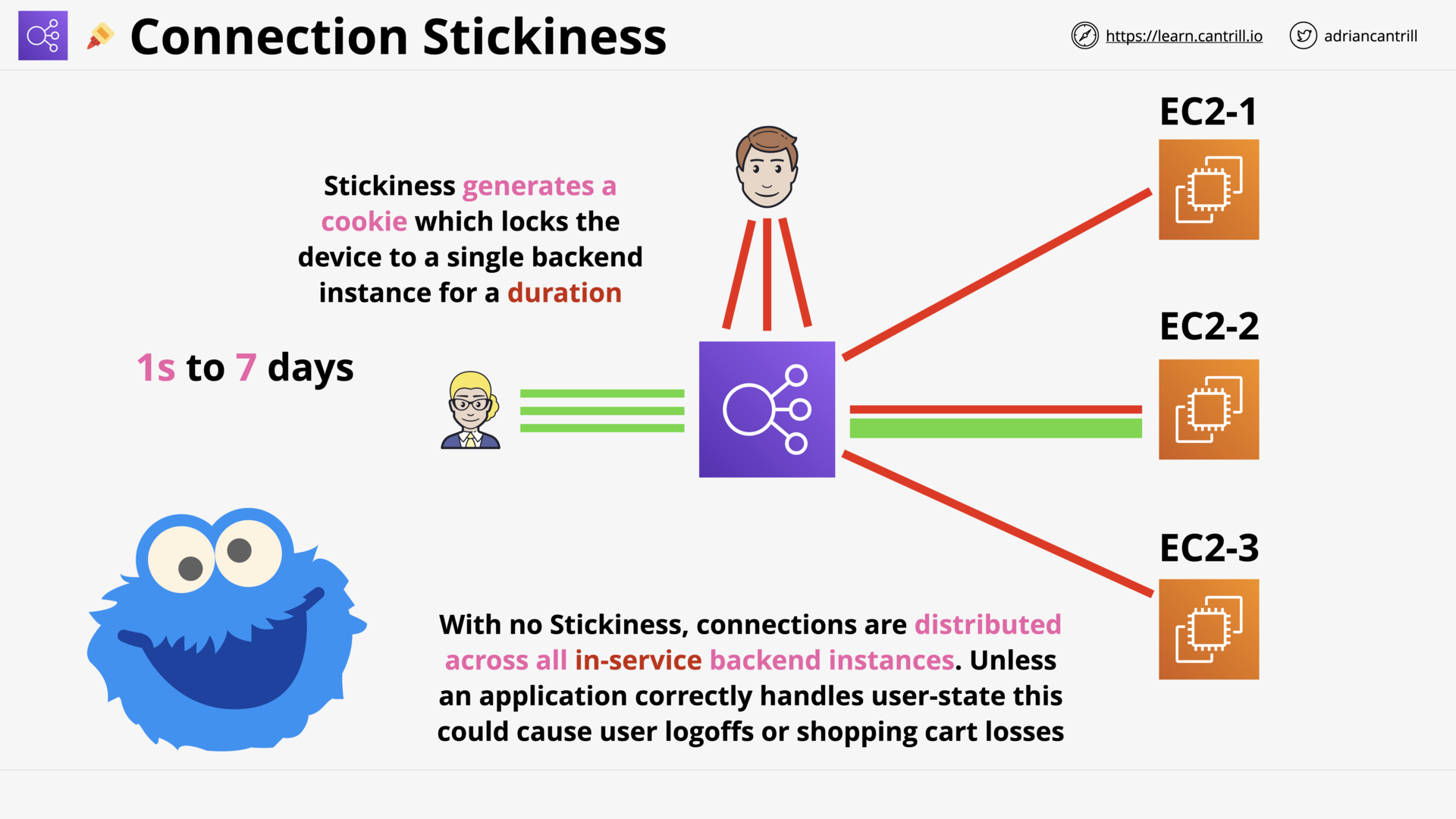 ELB - Connection Stickiness
ELB - Connection Stickiness
[DEMO] Seeing Session Stickiness in Action (12:57)
[ADVANCED_DEMO] Architecture Evolution - STAGE1 - PART1 (14:24)
[ADVANCED_DEMO] Architecture Evolution - STAGE1 - PART2 (10:43)
[ADVANCED_DEMO] Architecture Evolution - STAGE2 (12:58)
[ADVANCED_DEMO] Architecture Evolution - STAGE3 (19:30)
[ADVANCED_DEMO] Architecture Evolution - STAGE4 (18:04)
[ADVANCED_DEMO] Architecture Evolution - STAGE 5 - PART1 (11:31)
[ADVANCED_DEMO] Architecture Evolution - STAGE 5 - PART2 (14:56)
[ADVANCED_DEMO] Architecture Evolution - STAGE6 (5:48)
Gateway Load Balancer (13:40)
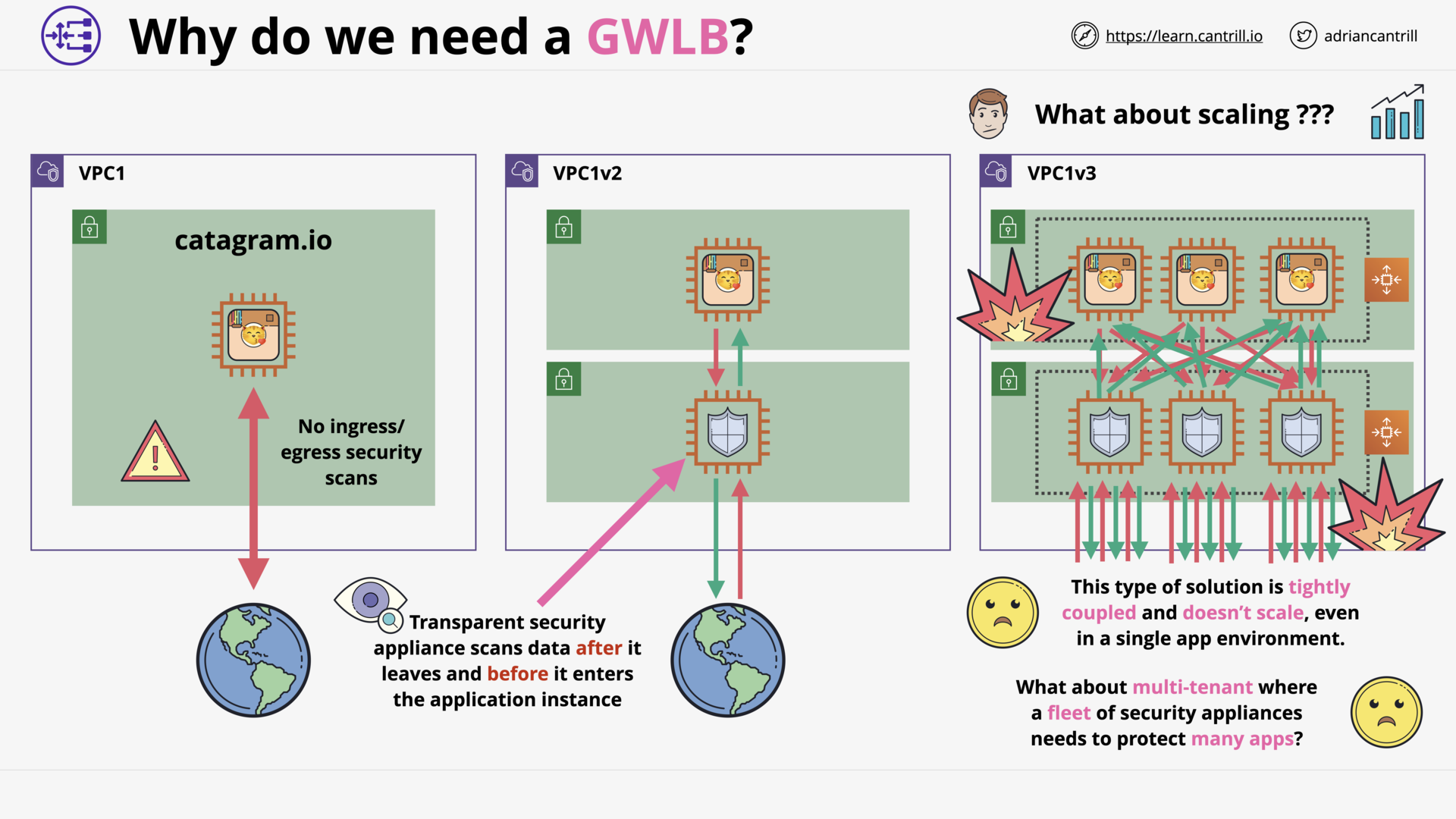 Why GWLB?
Why GWLB?
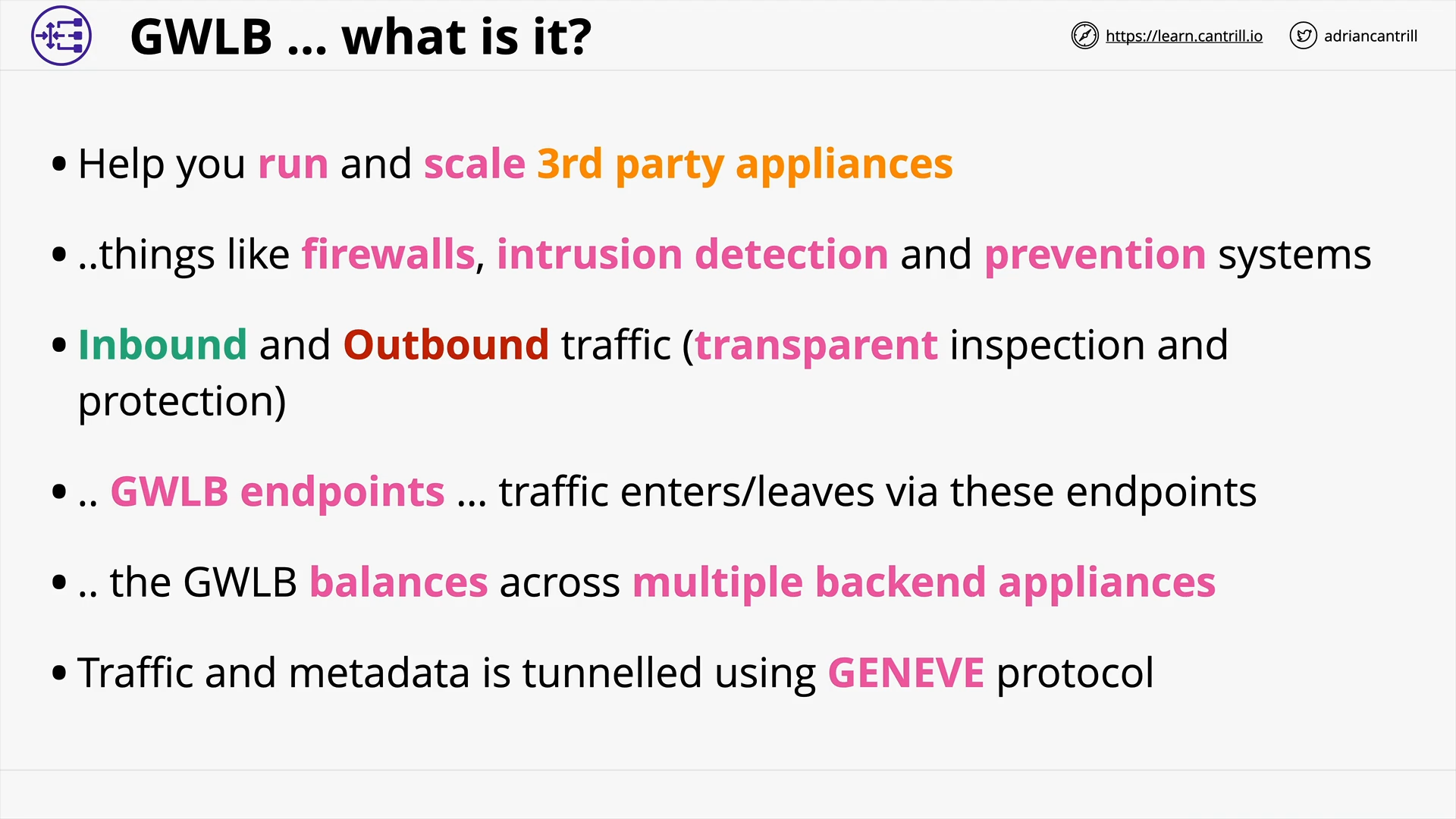 What is GWLB?
What is GWLB?
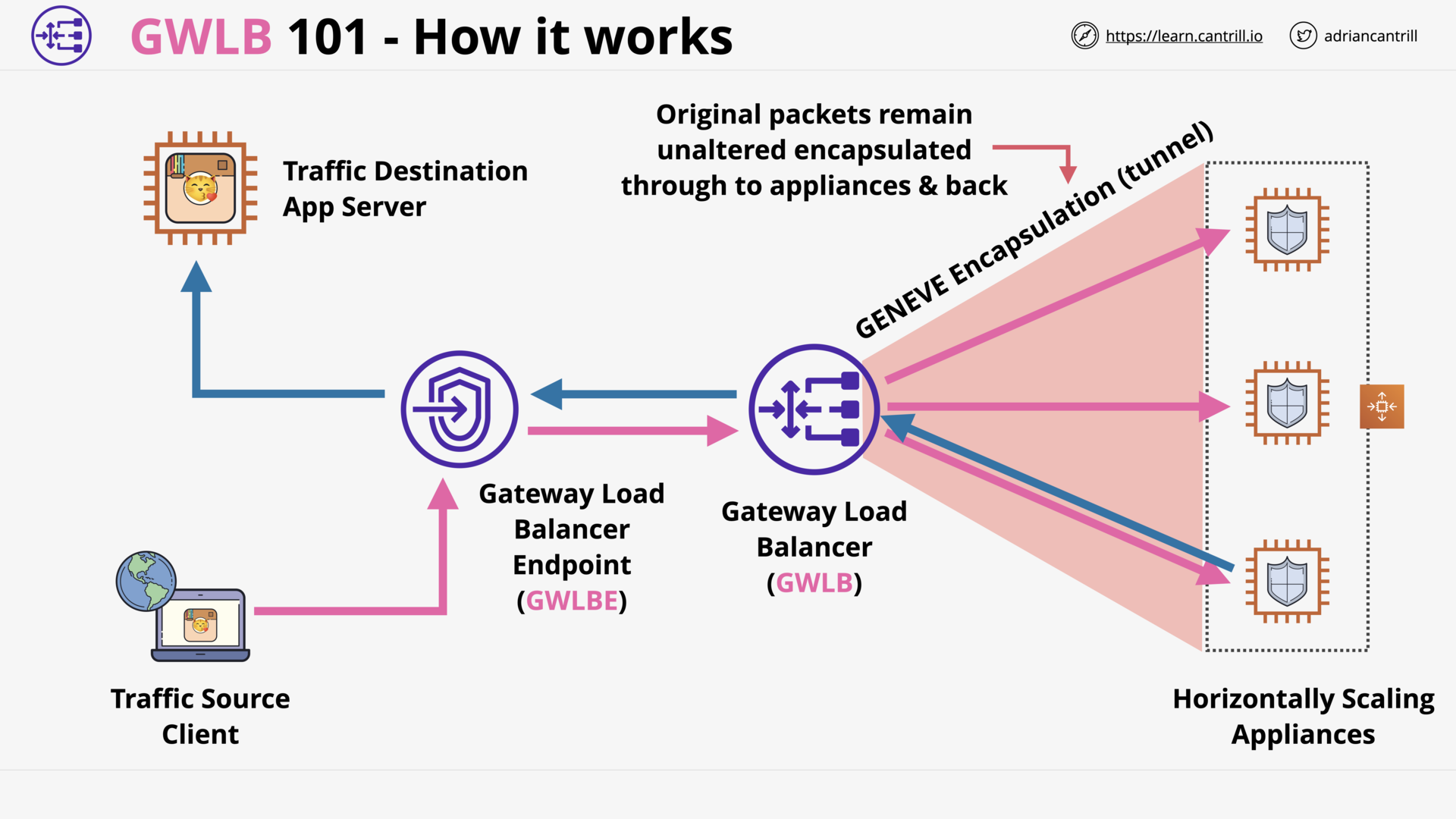 How GWLB works?
How GWLB works?
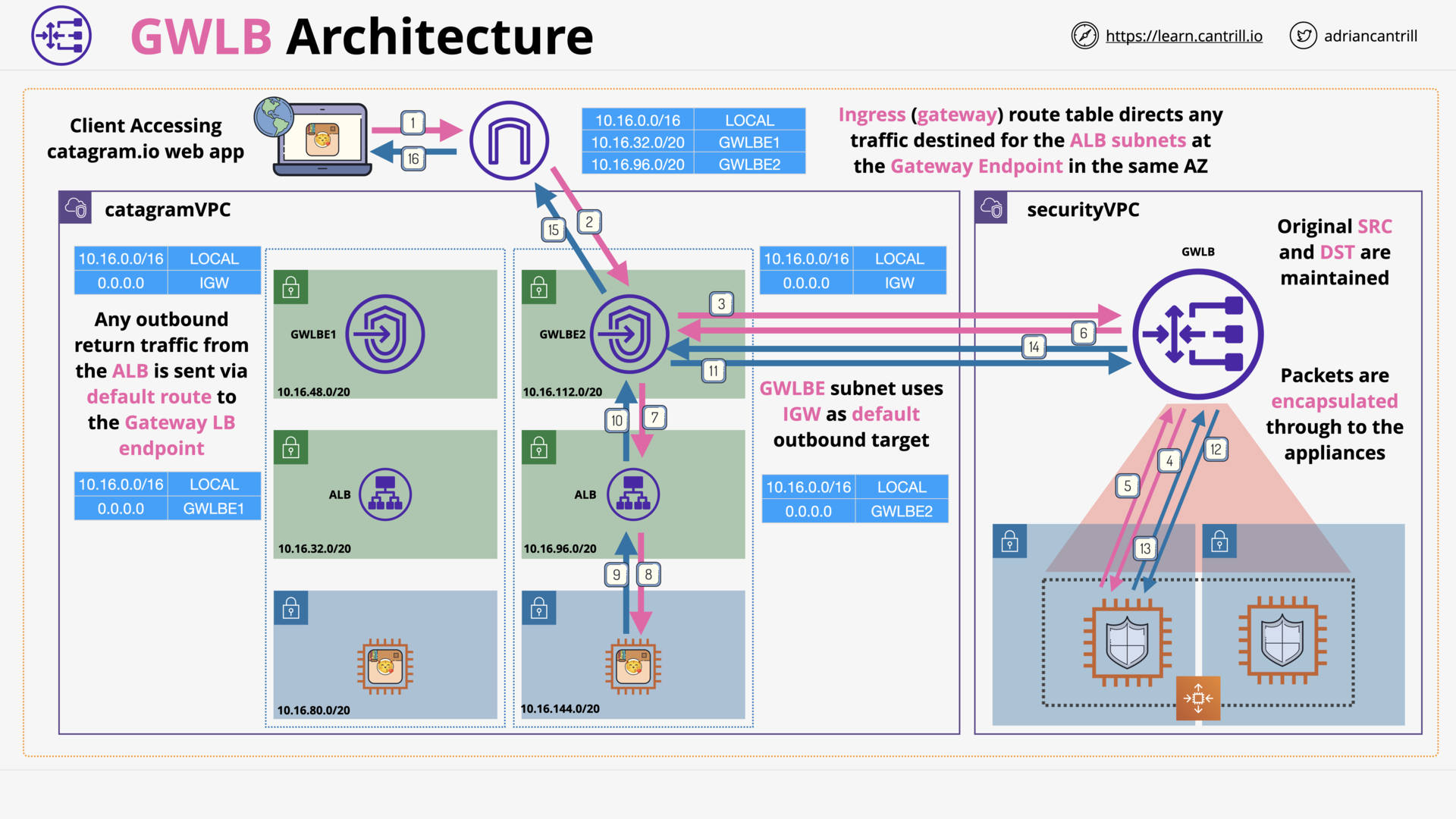 GWLB - Architecture
GWLB - Architecture
HA and Scaling Section Quiz
SERVERLESS AND APPLICATION SERVICES
Architecture Deep Dive - PART1 (8:52)
 CatTube - Monolithic Architecture
CatTube - Monolithic Architecture
 CatTube - Tiered Architecture
CatTube - Tiered Architecture
Architecture Deep Dive - PART2 (13:09)
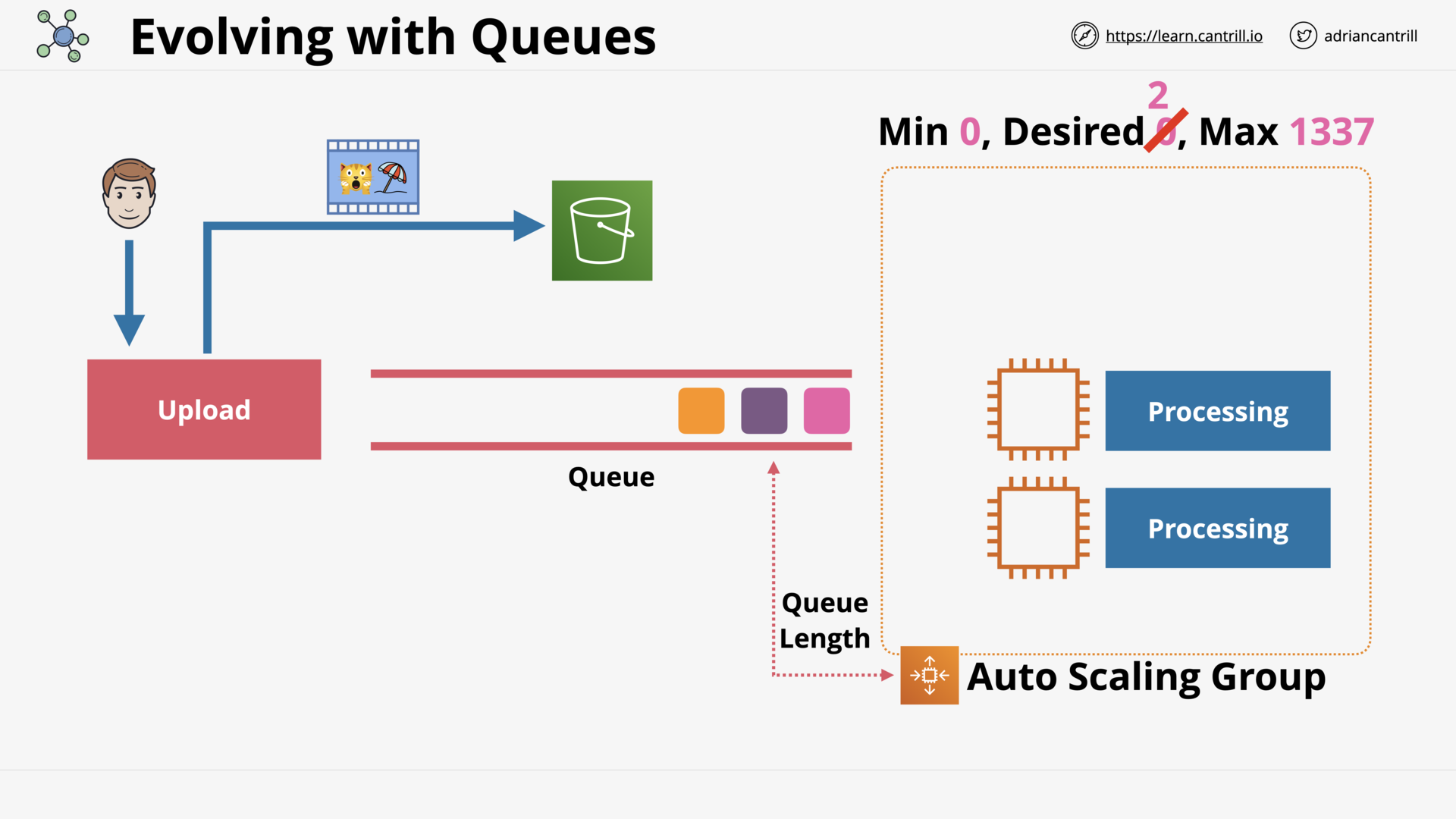 Evolving with Queues
Evolving with Queues
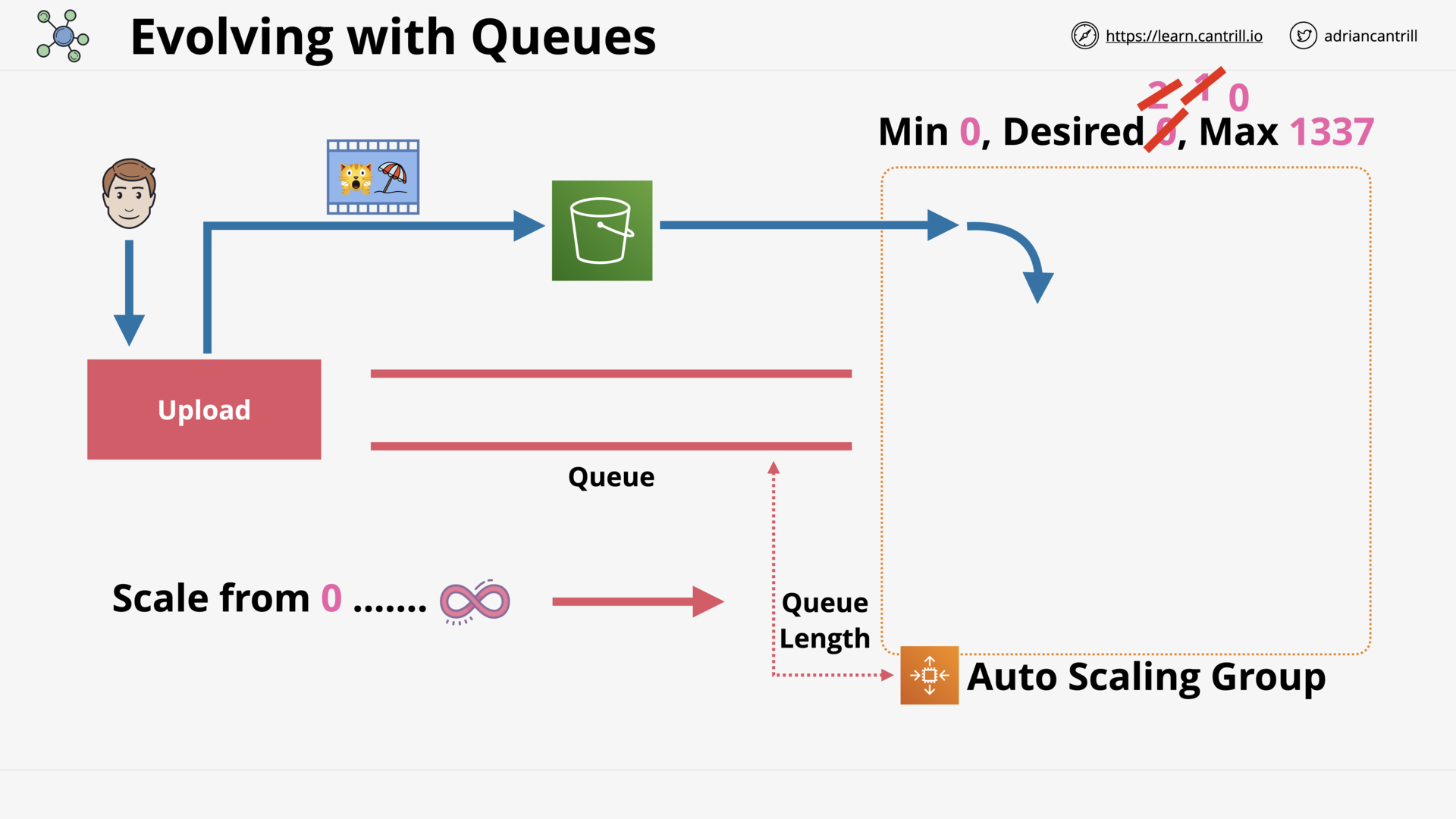 Evolving with Queues
Evolving with Queues
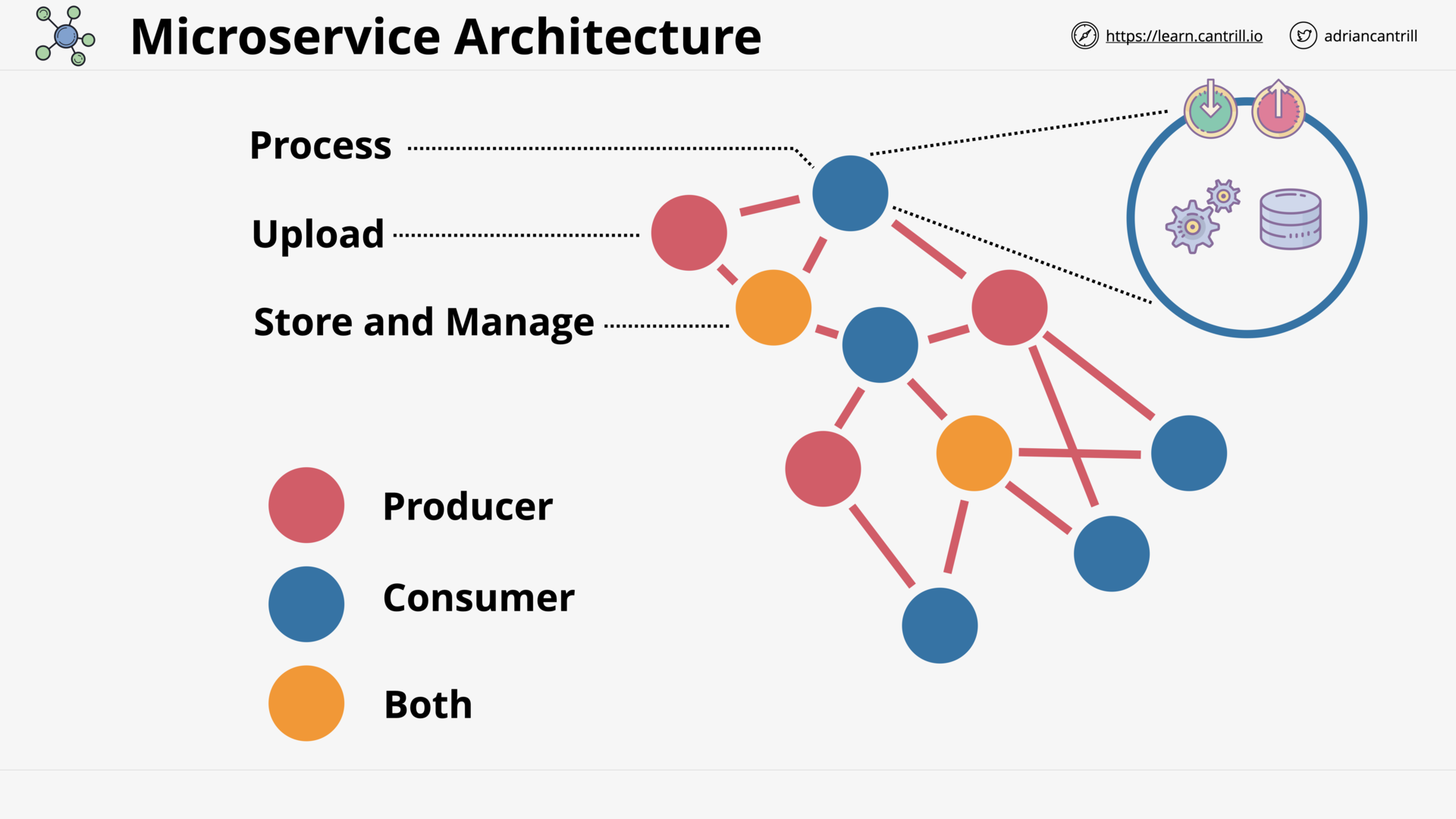 Microservices Architecture
Microservices Architecture
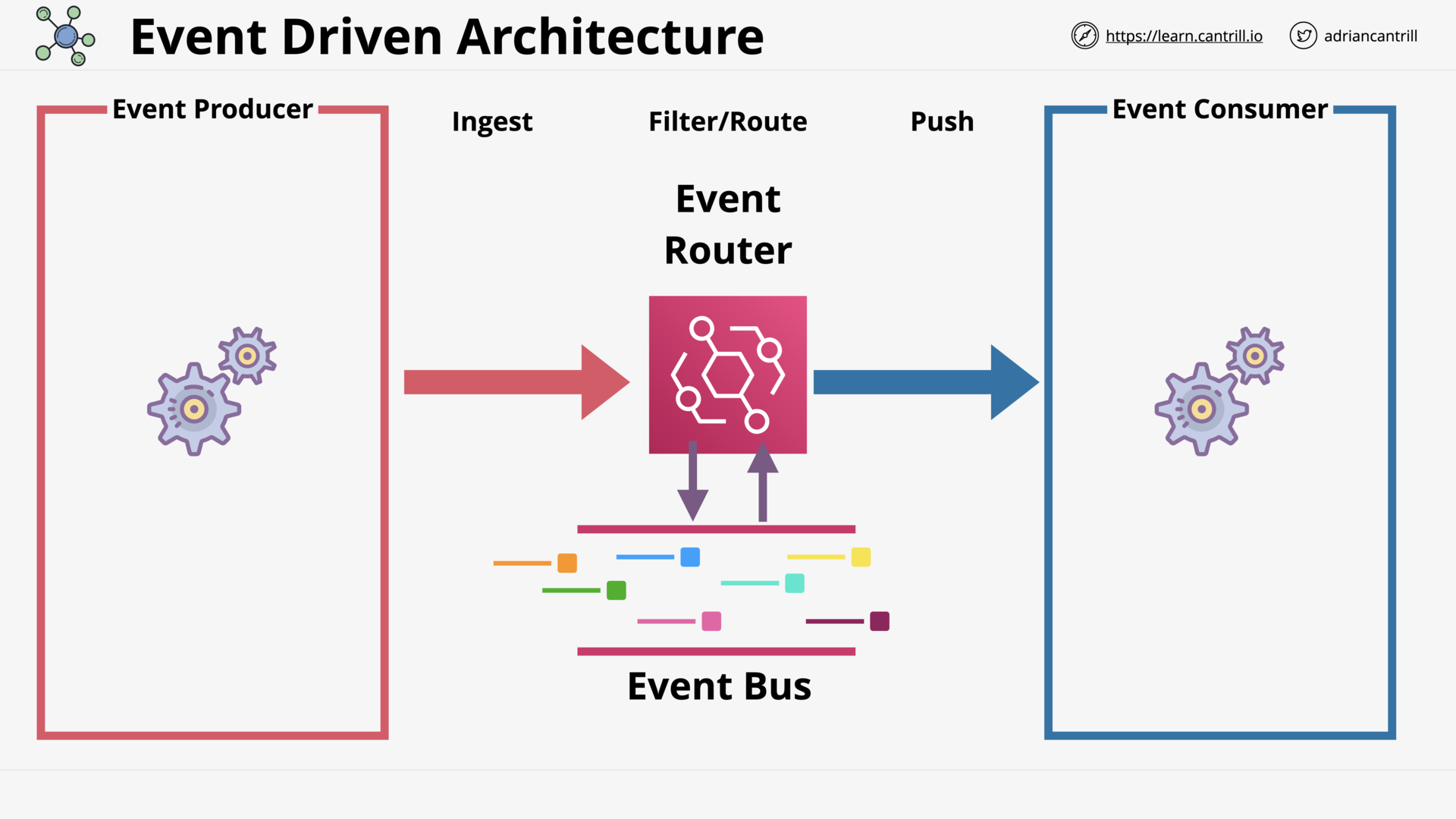 Event Driven Architecture - Event Producer / Event Consumer
Event Driven Architecture - Event Producer / Event Consumer
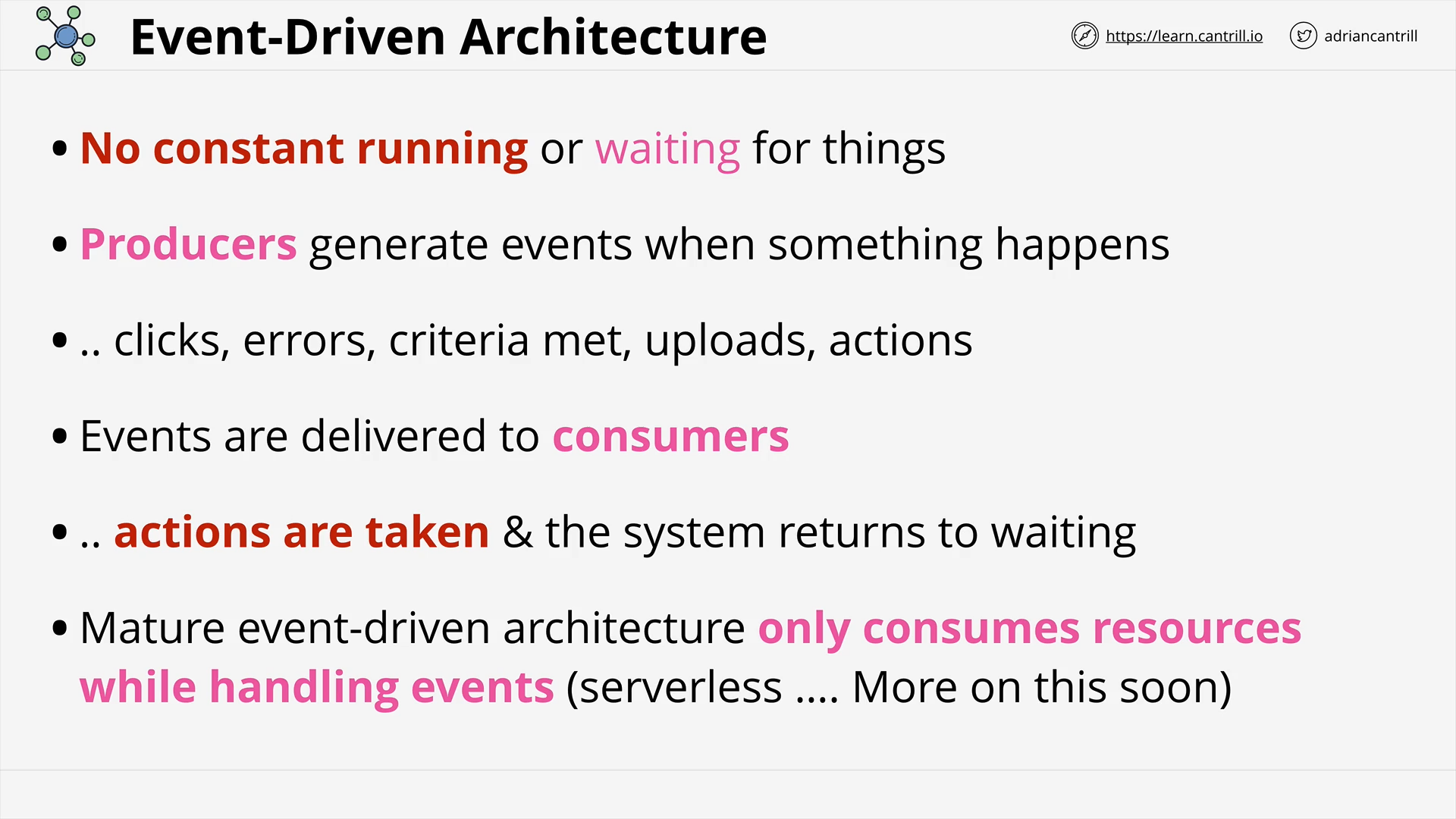 Event Driven Architecture - Only consumes resources while handling events
Event Driven Architecture - Only consumes resources while handling events
AWS Lambda - PART1 (11:25)
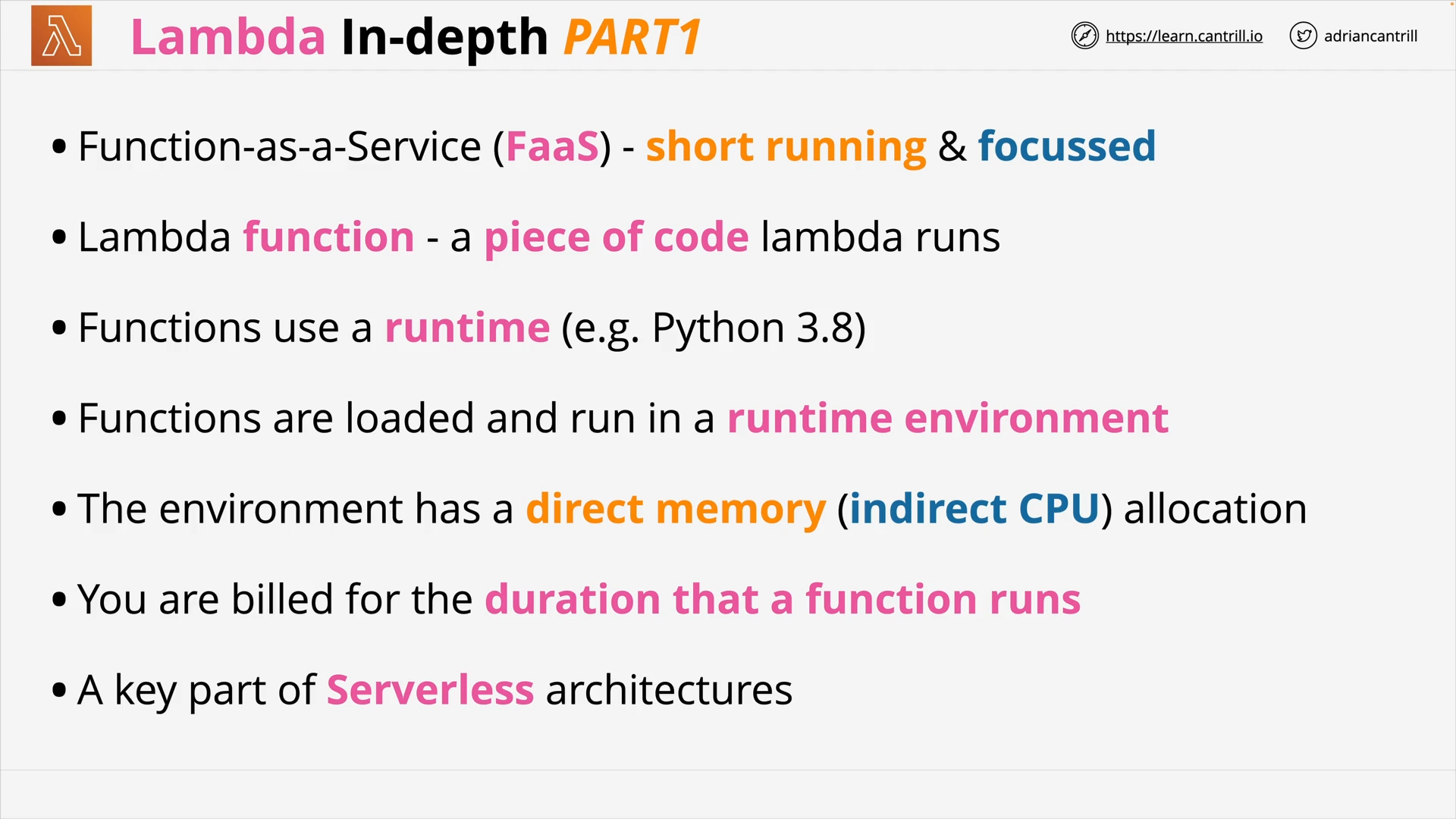 AWS Lambda - Overview
AWS Lambda - Overview
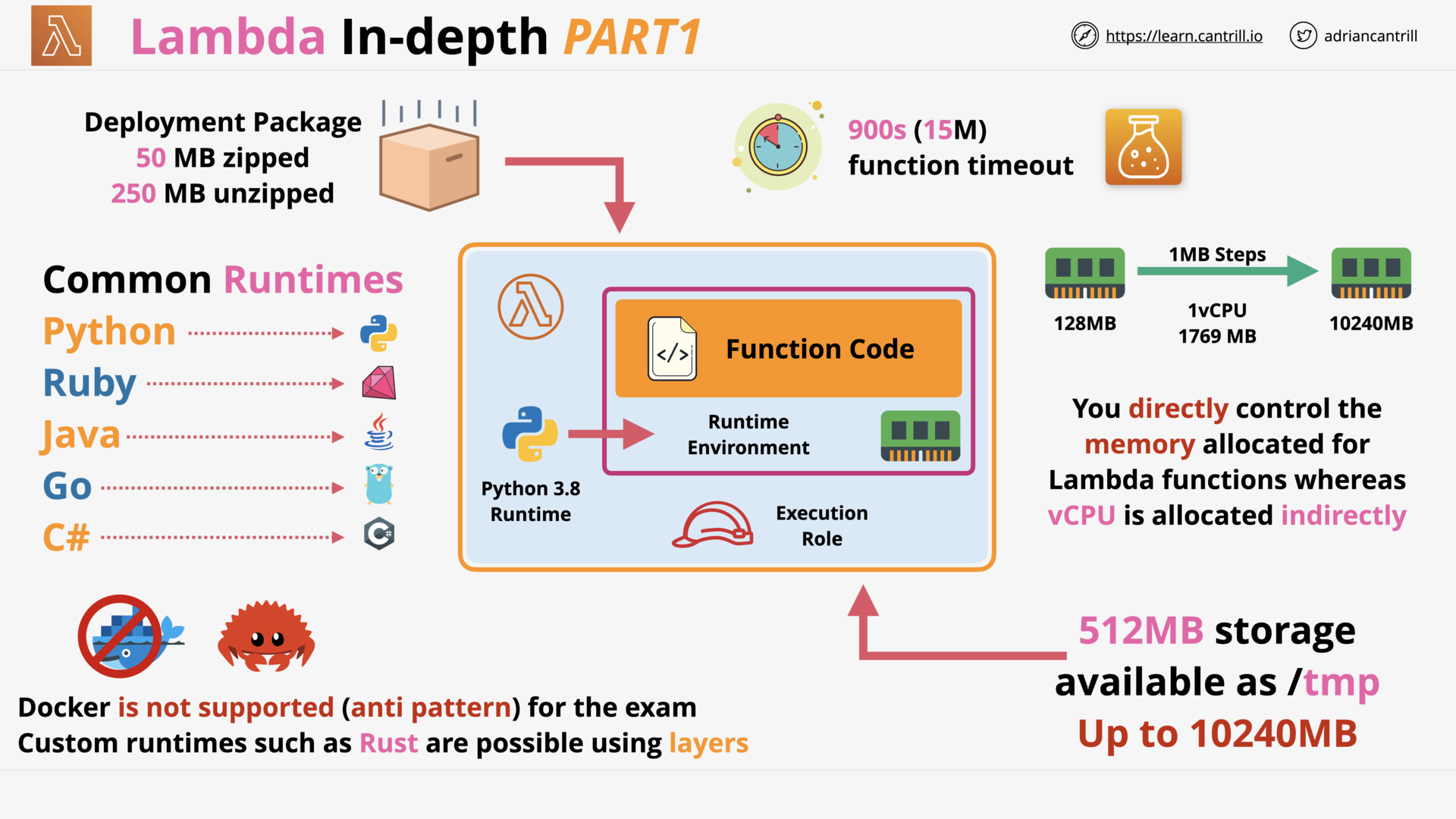 AWS Lambda - Architecture
AWS Lambda - Architecture
what is the maximum execution time of an aws lambda?
900s (15min)
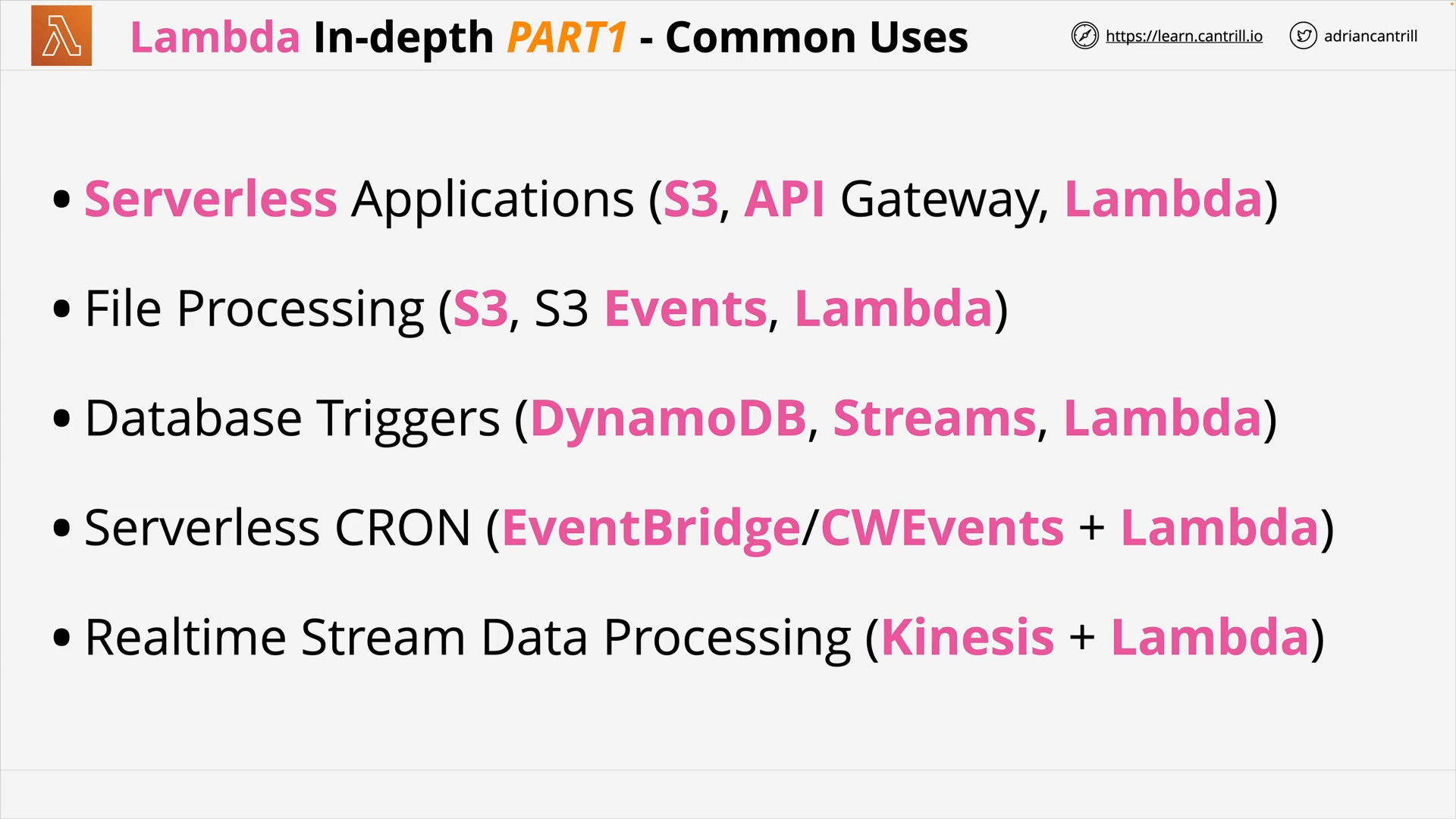 AWS Lambda - Common Uses
AWS Lambda - Common Uses
AWS Lambda - PART2 (13:59)
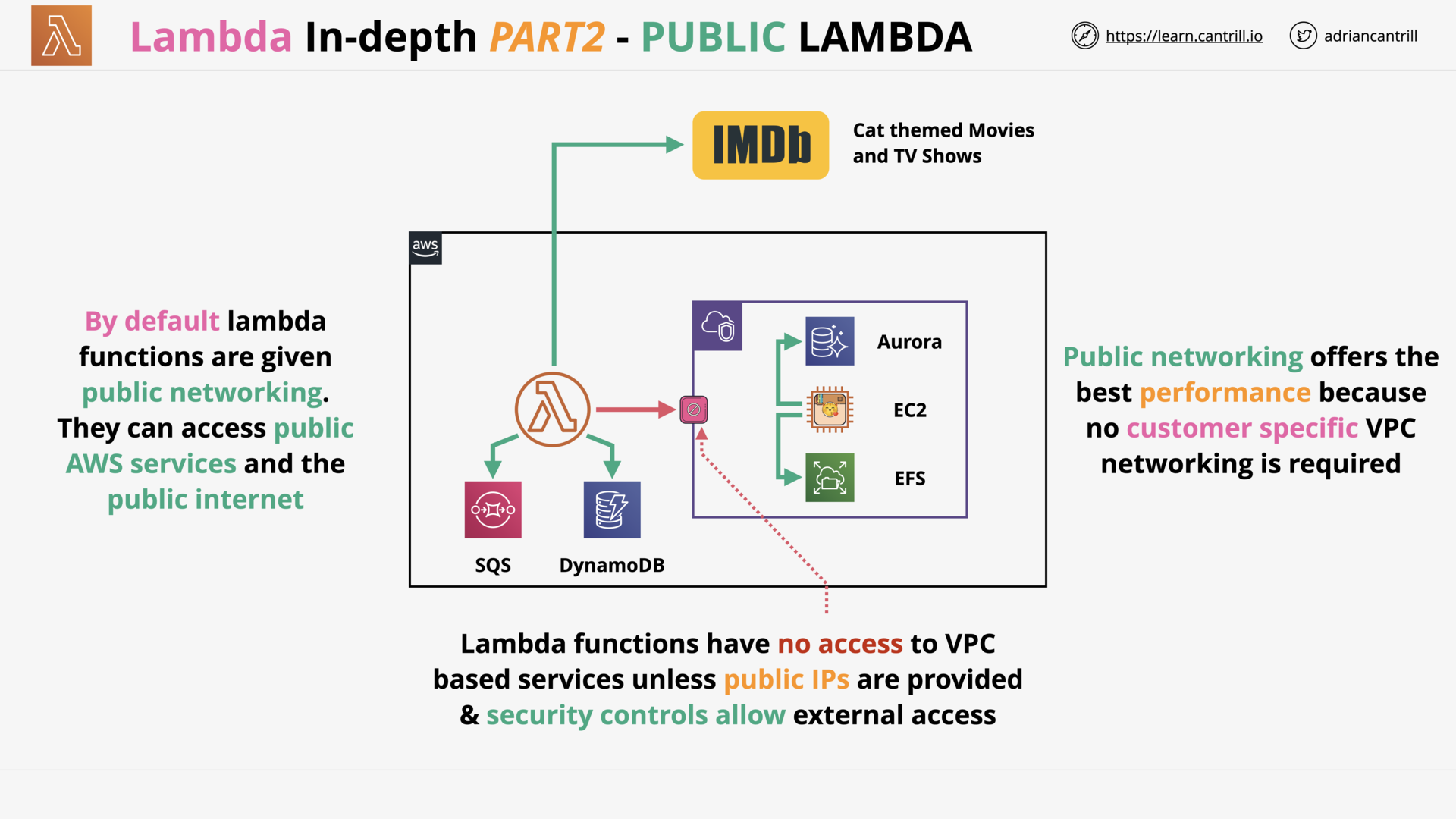 Public Lambda
Public Lambda
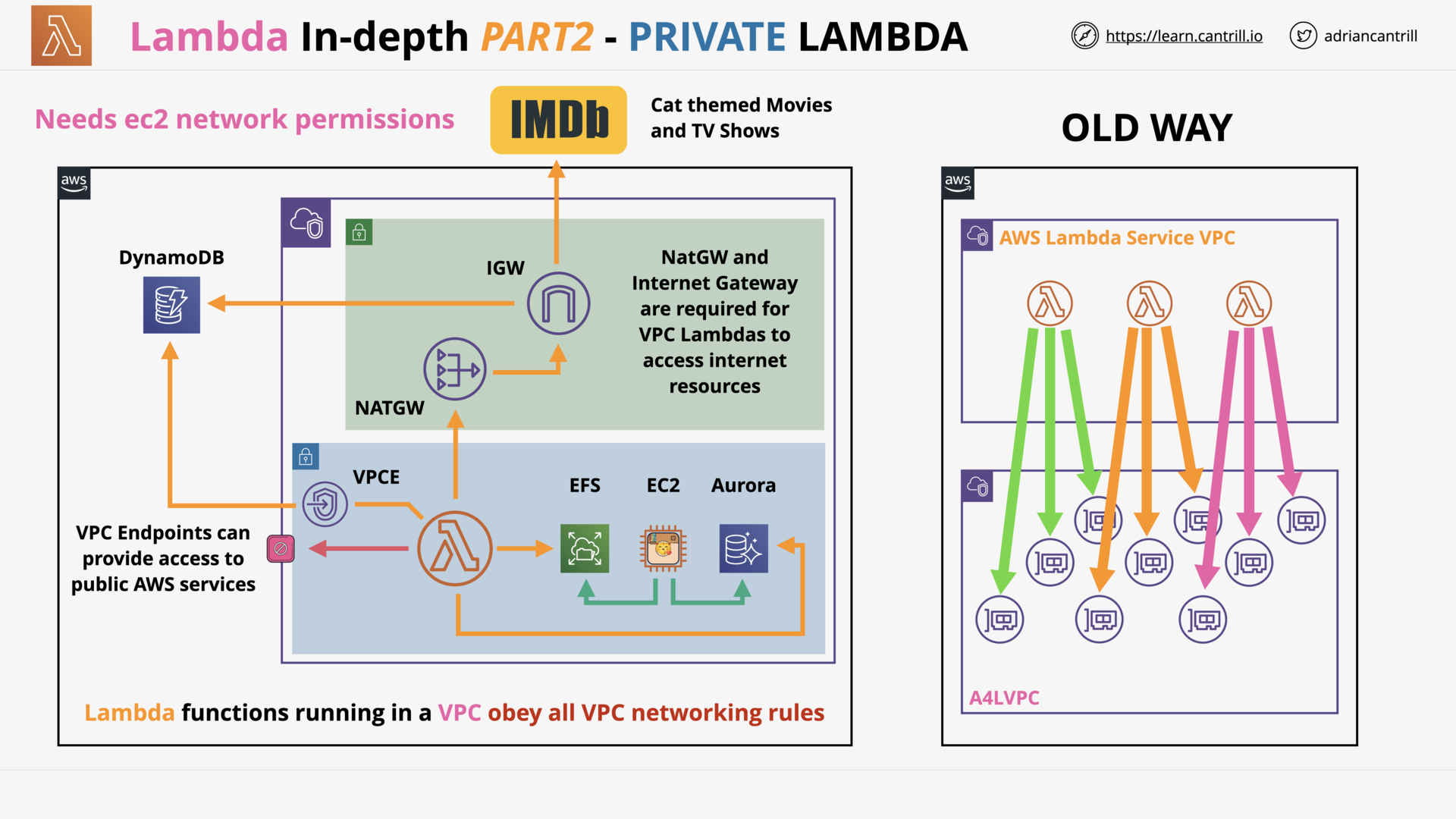 Private Lambda - Old Way
Private Lambda - Old Way
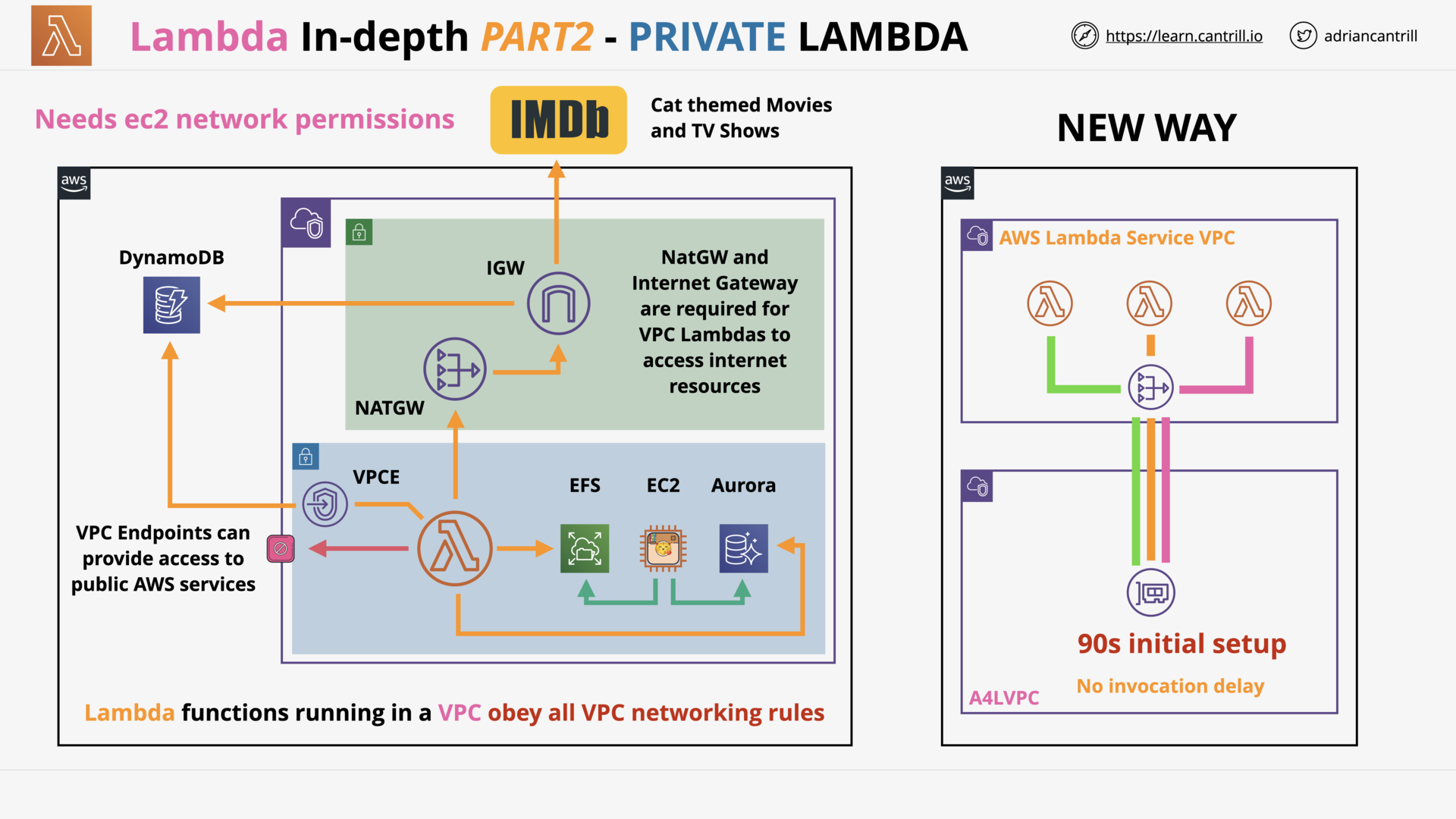 Private Lambda - New Way
Private Lambda - New Way
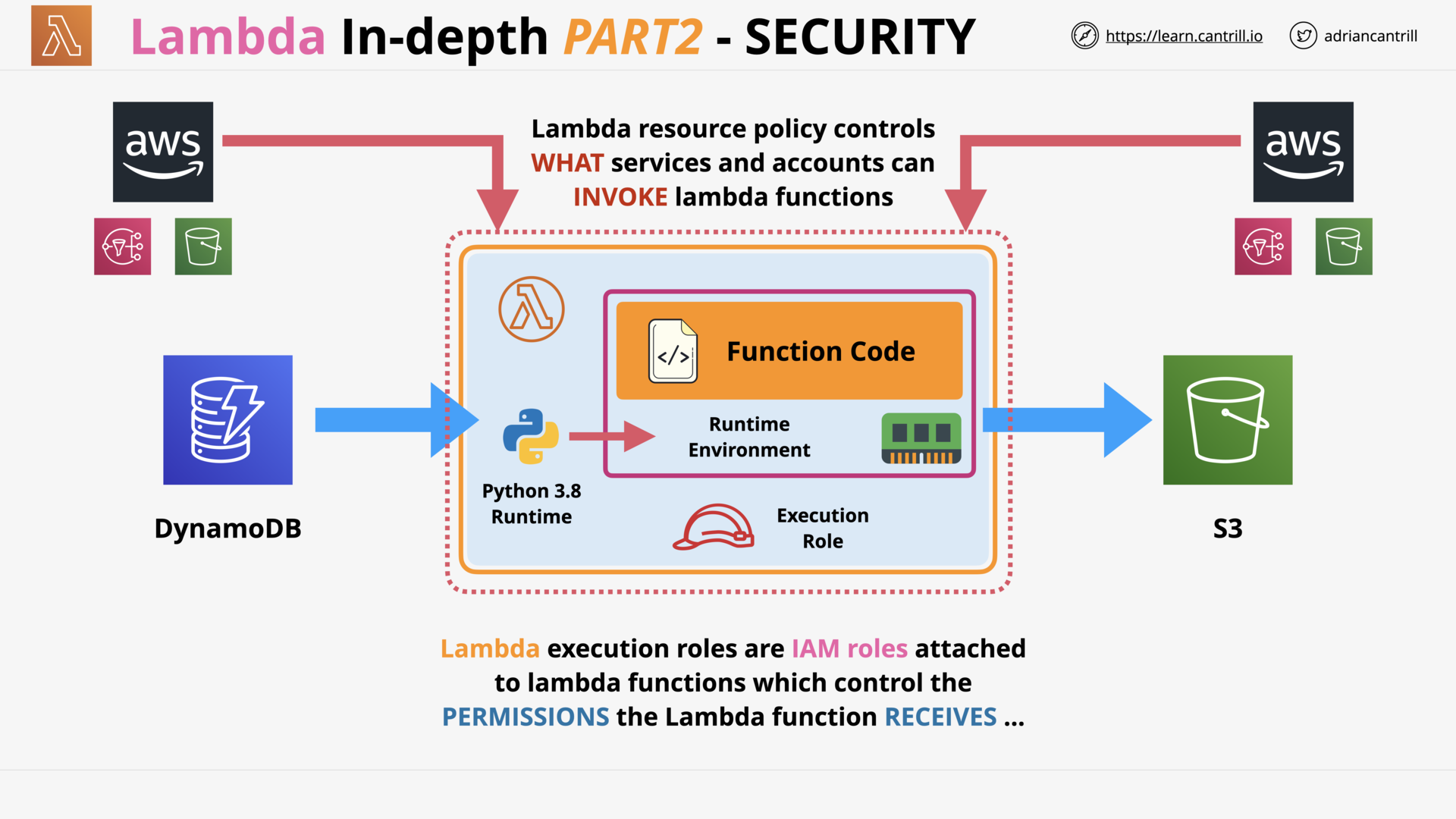 Lambda - Security
Lambda - Security
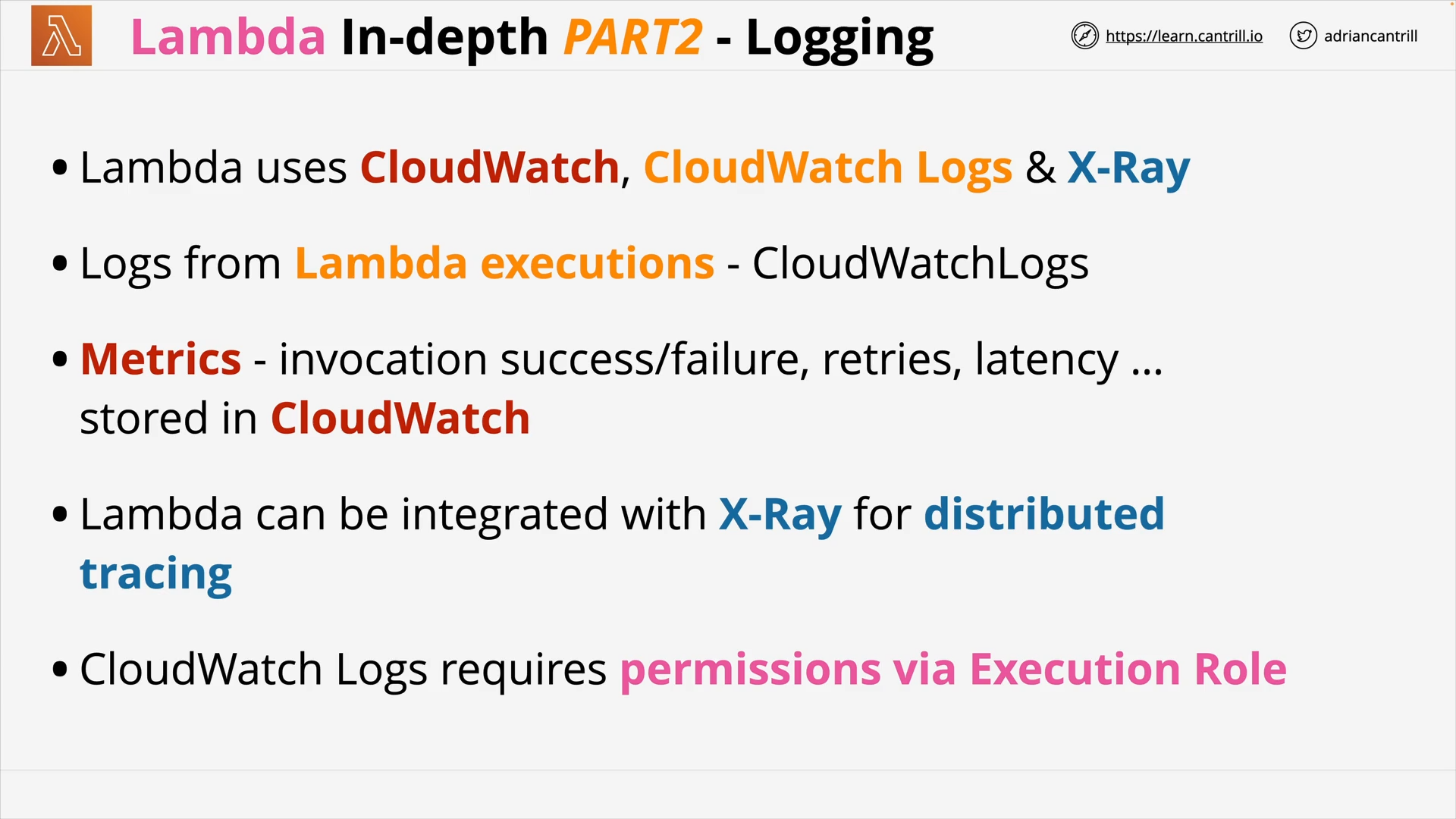 Lambda - Logging
Lambda - Logging
AWS Lambda - PART3 (17:03)
 Lambda - 3 Types of Invocation
Lambda - 3 Types of Invocation
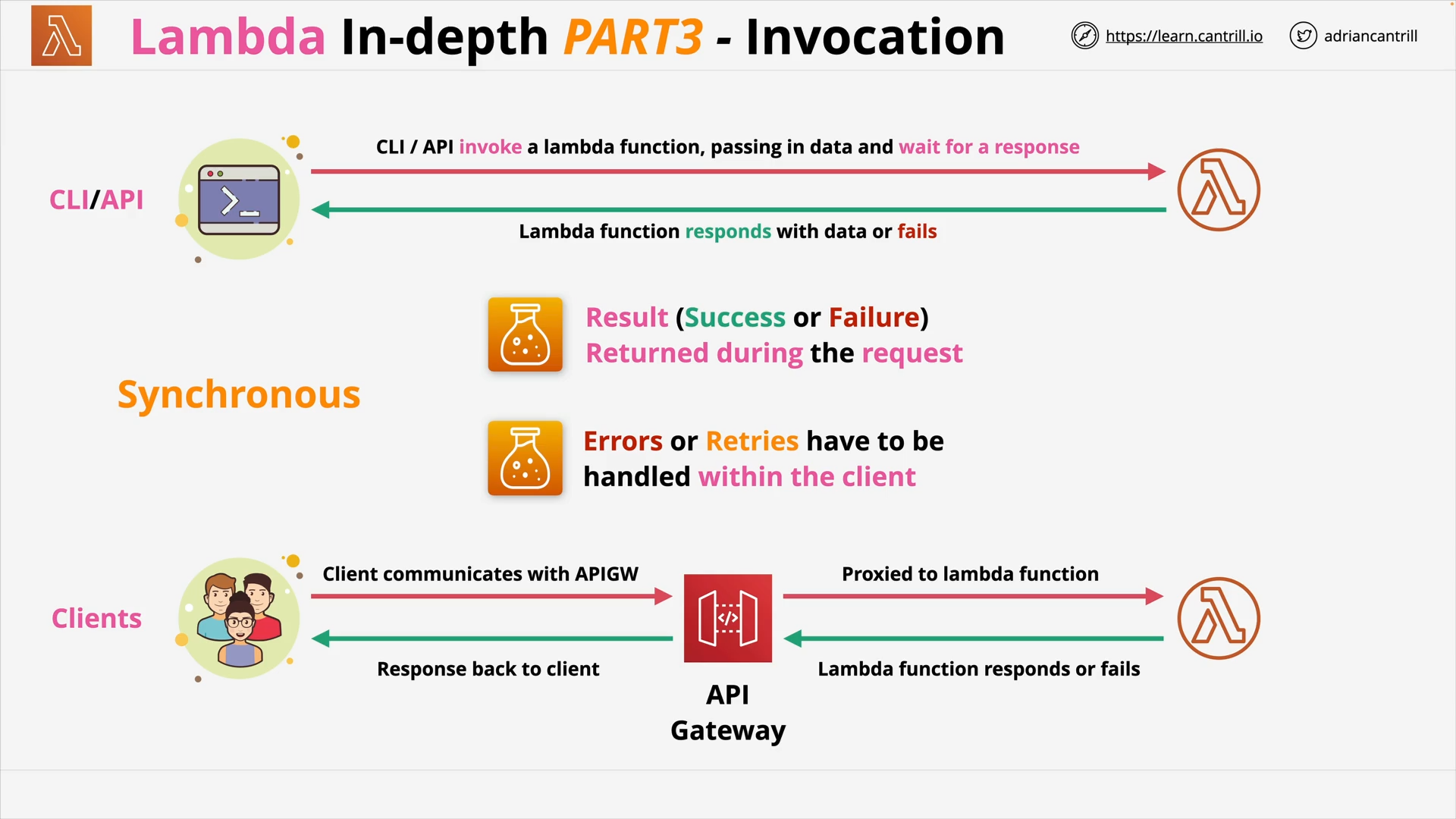 Lambda - Synchronous Invocation
Lambda - Synchronous Invocation
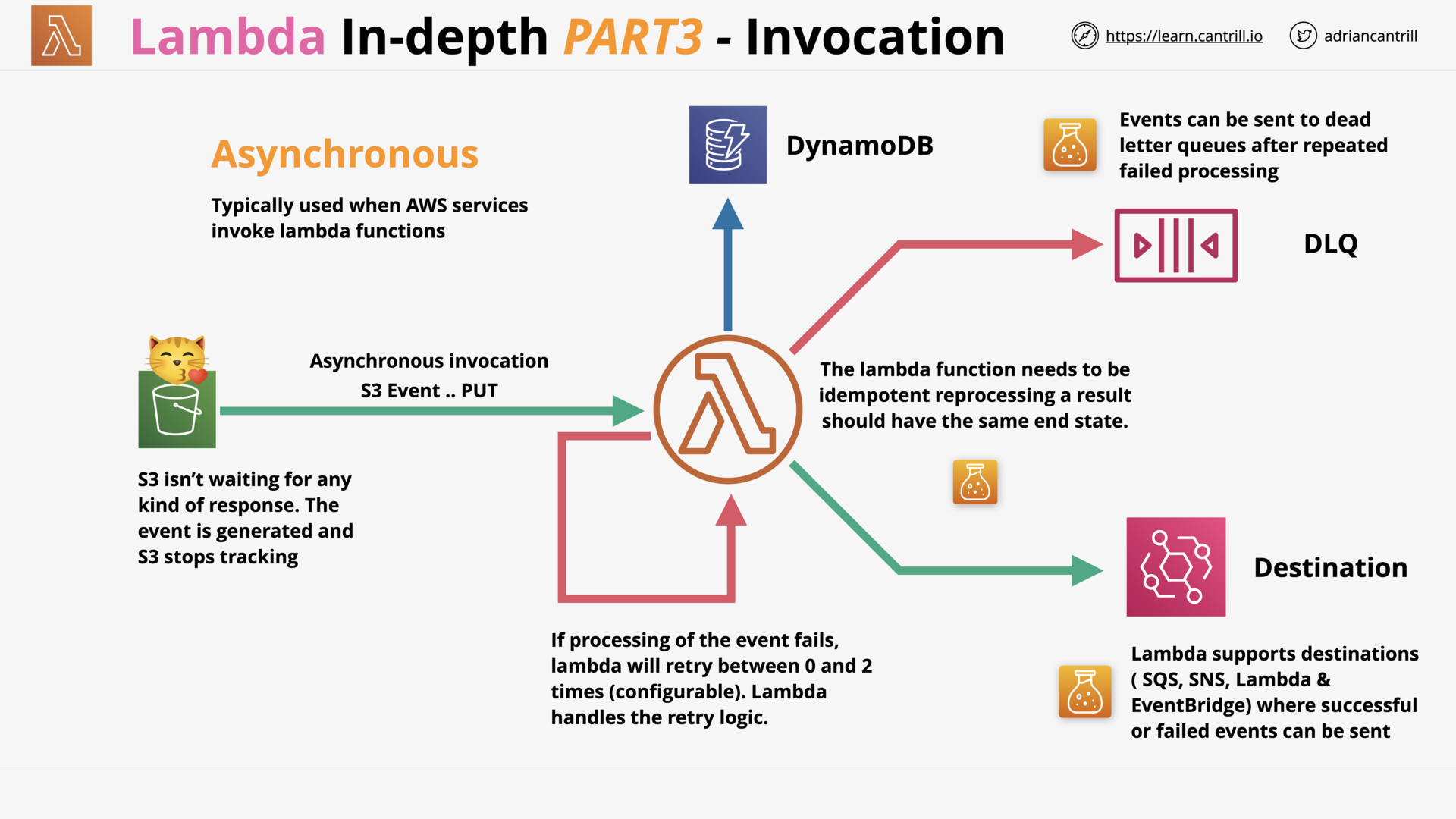 Lambda - Asynchronous Invocation
Lambda - Asynchronous Invocation
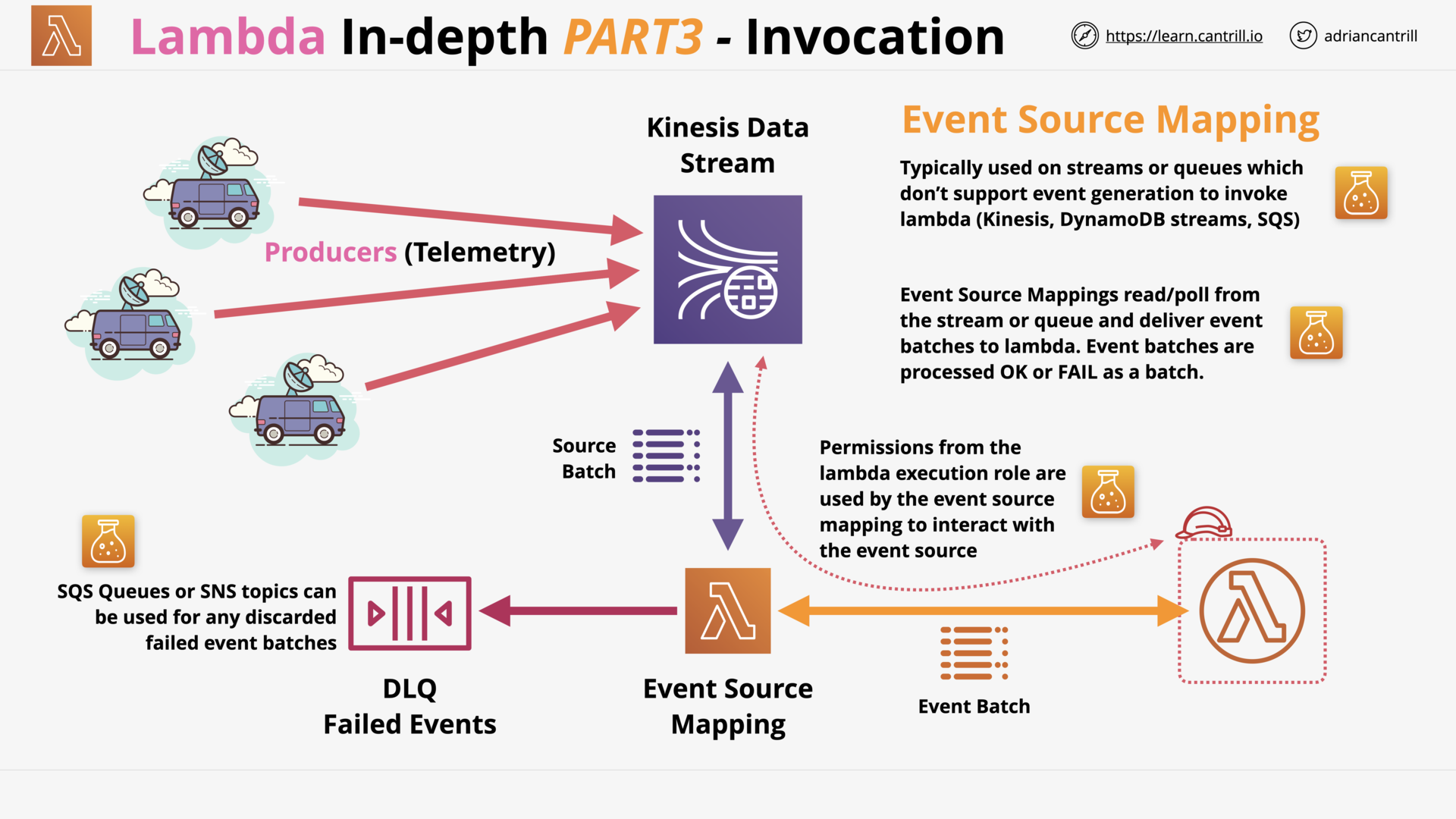 Lambda - Event Source Mapping
Lambda - Event Source Mapping
 Lambda - Versions
Lambda - Versions
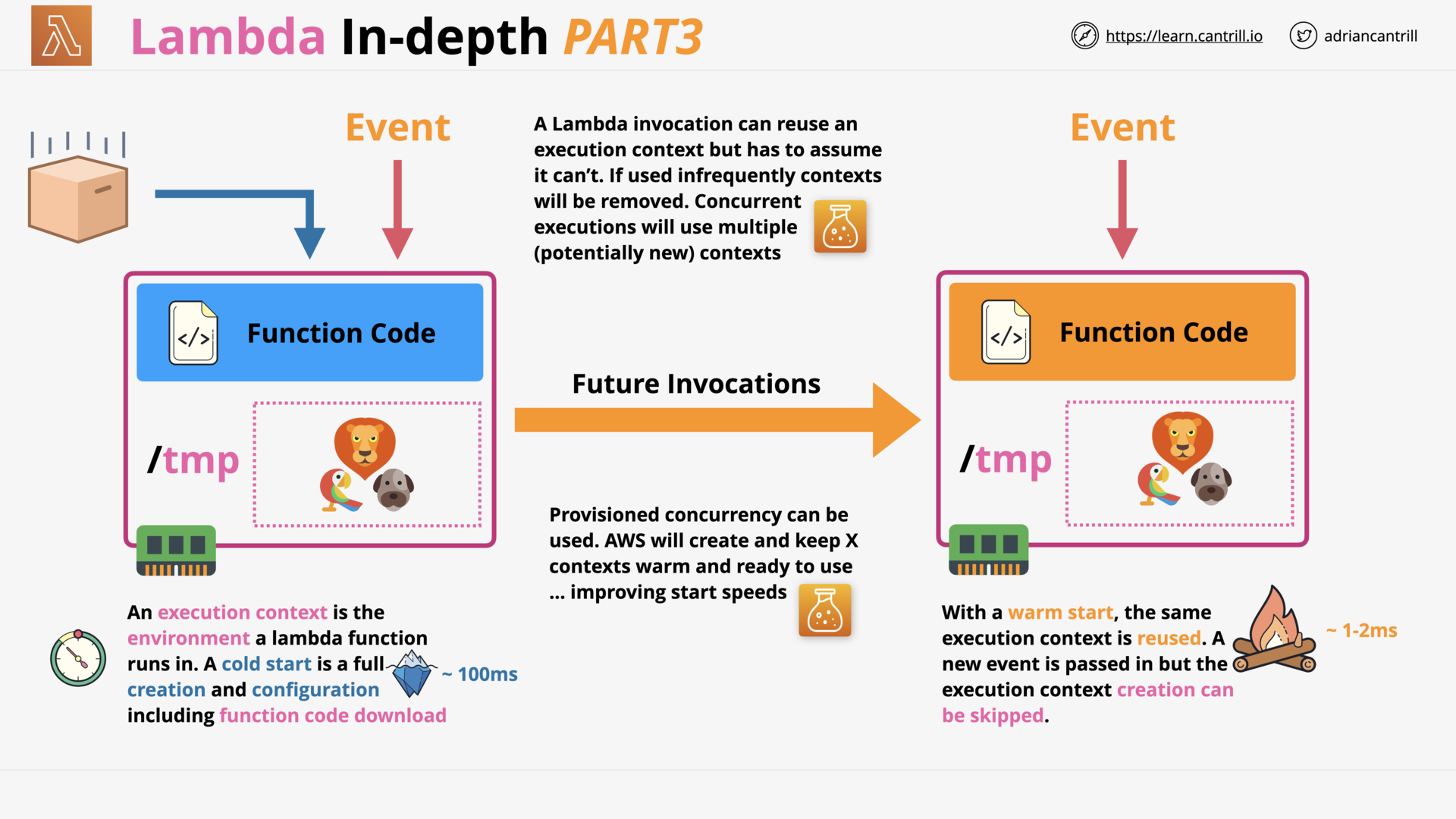 Lambda - Execution Context: Cold start ☃️ - Warm start 🌞
Lambda - Execution Context: Cold start ☃️ - Warm start 🌞
CloudWatch Events and EventBridge (6:54)
 EventBridge = CloudWatch Events v2
EventBridge = CloudWatch Events v2
which type of events do cloudwatch events and eventbridge process?
Events generated by supported AWS services within an account.
how many buses do cloudwatch events and eventbridge have?
-
Both have a default Event bus:
-
CloudWatch Events: 1
The default is the only bus CloudWatch Events has.
-
EventBridge: 1+
In additional to the defaut event bus, EventBridge can have other event buses.
-
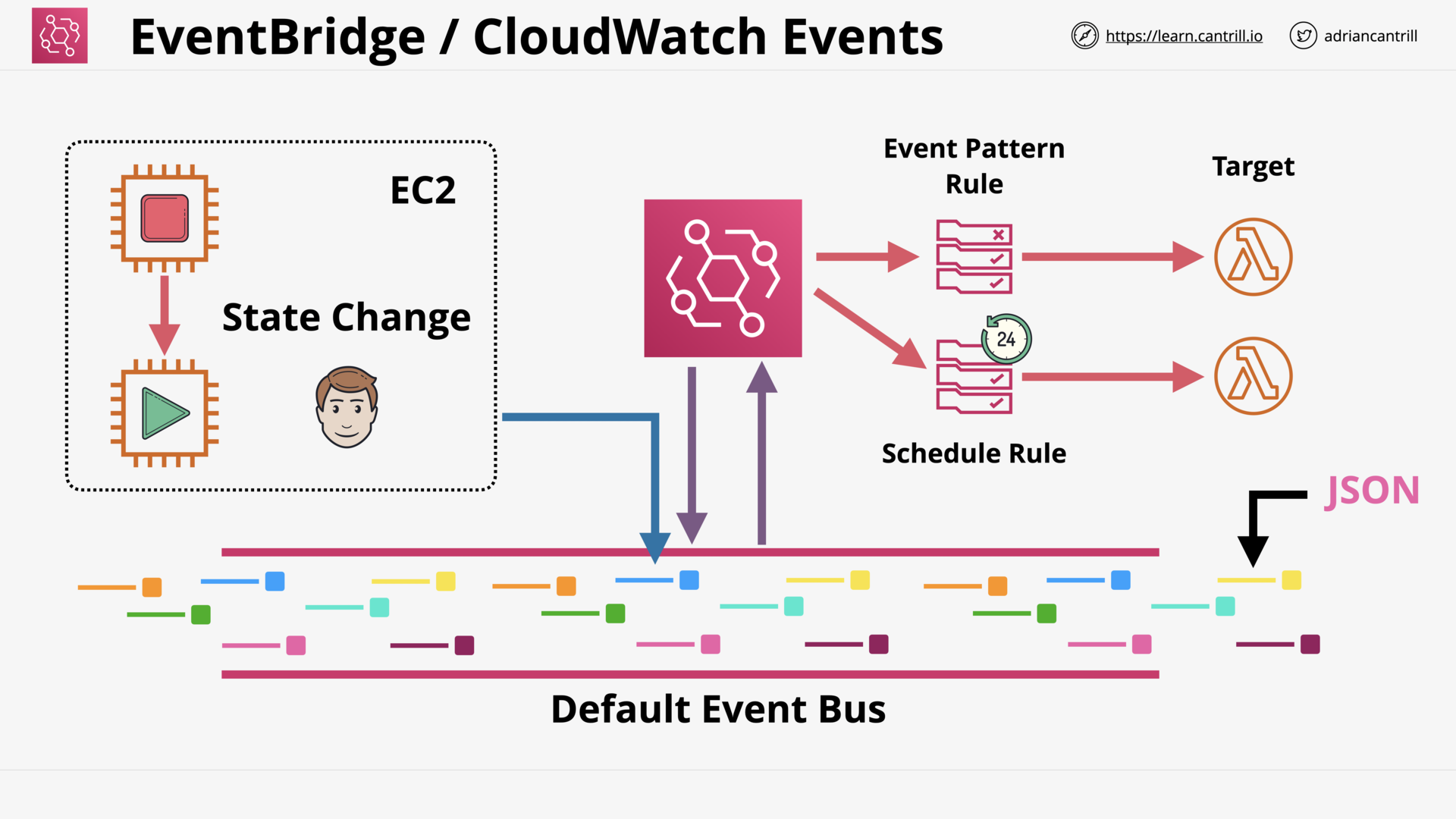 Rule & Target
Rule & Target
which types of rules do cloudwatch events and eventbridge support?
- Event Pattern Rule 👈 If
Xhappens doZ. - Schedule Rule👈 At
Ytime(s) doZ.
[DEMO] Automated EC2 Control using Lambda and Events - PART1 (13:44)
[DEMO] Automated EC2 Control using Lambda and Events - PART2 (18:49)
Serverless Architecture (12:56)
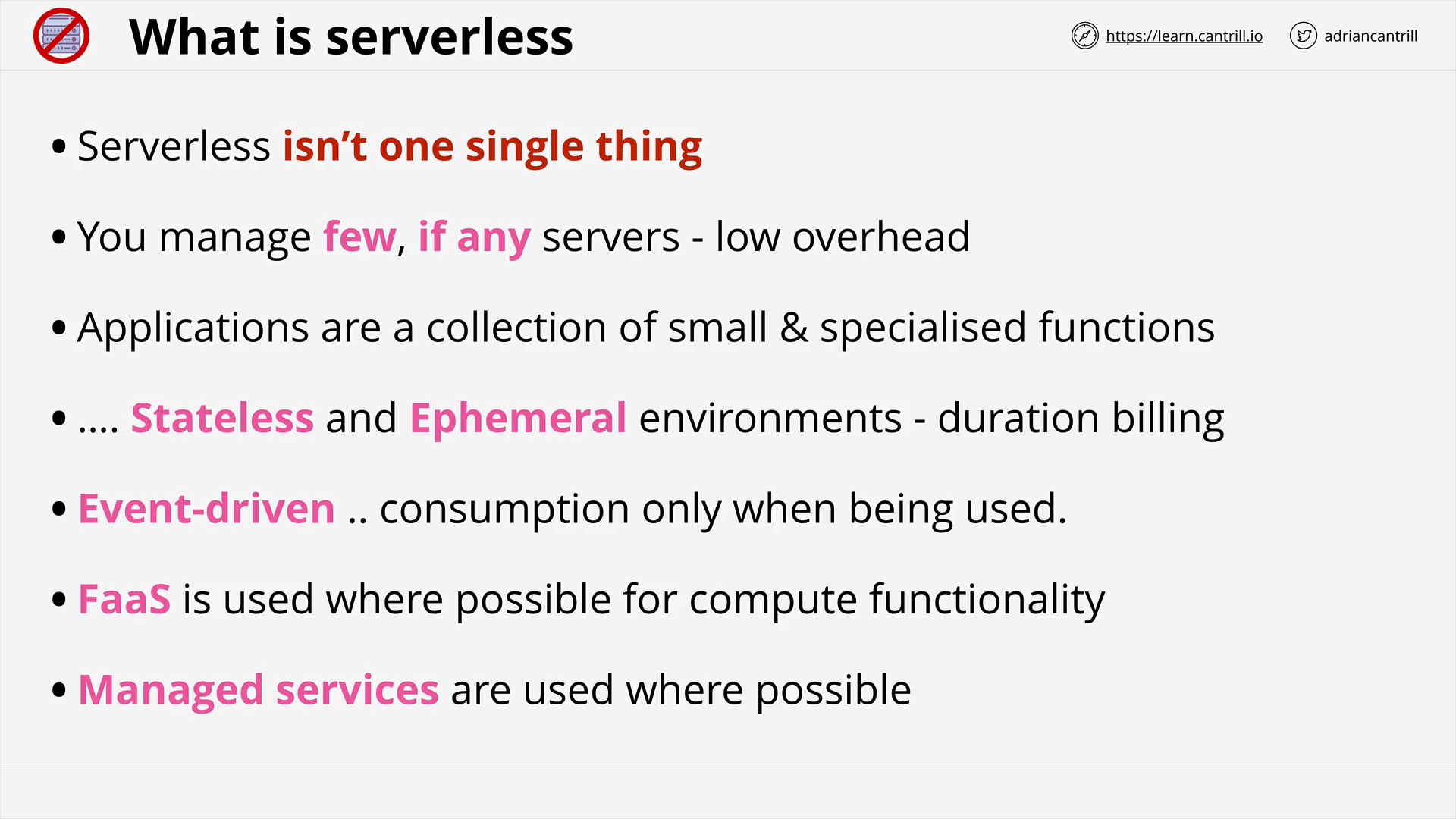 What is serverless?
What is serverless?
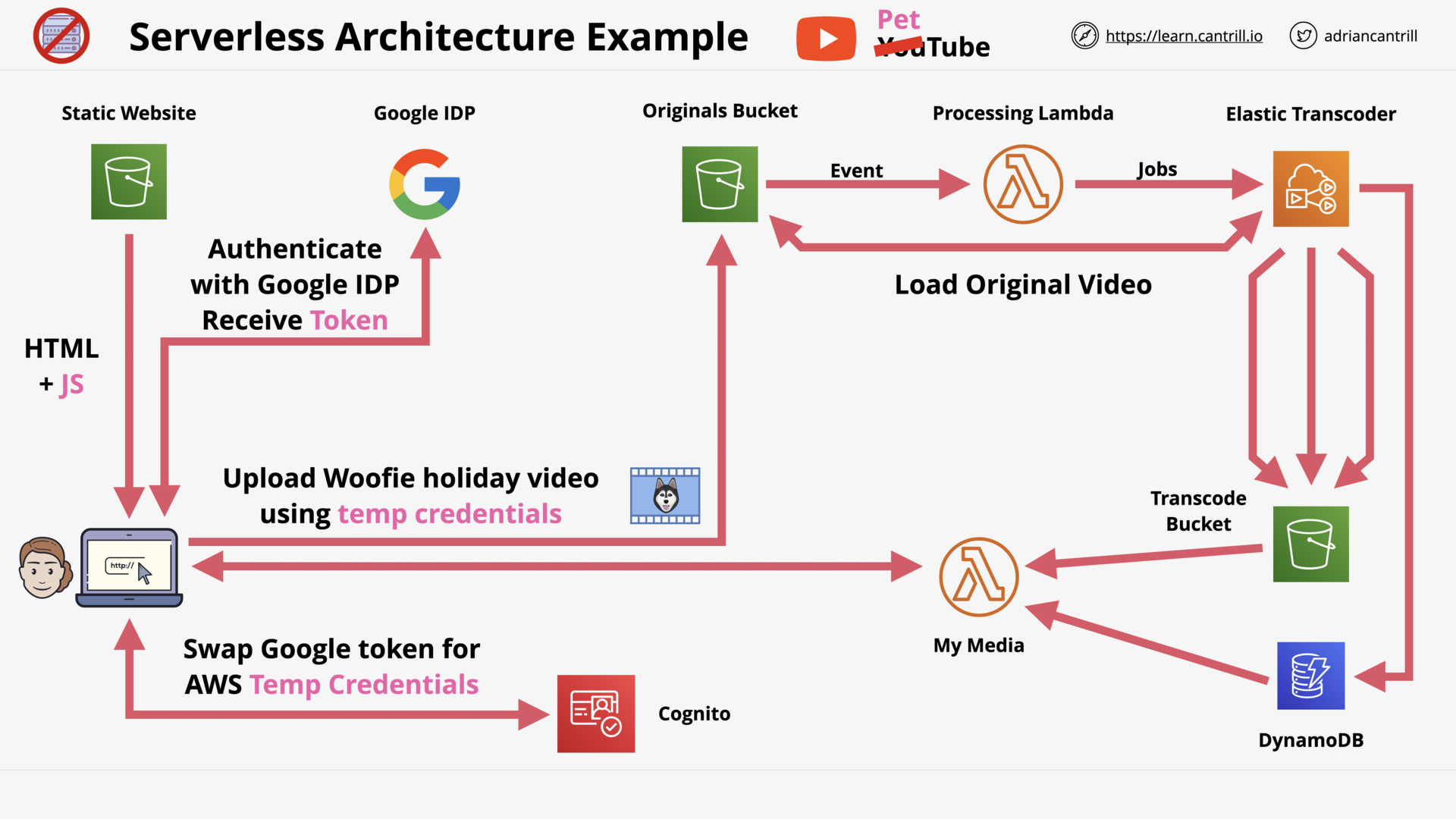 Serverless Architecture Example - PetTube
Serverless Architecture Example - PetTube
Simple Notification Service (7:49)
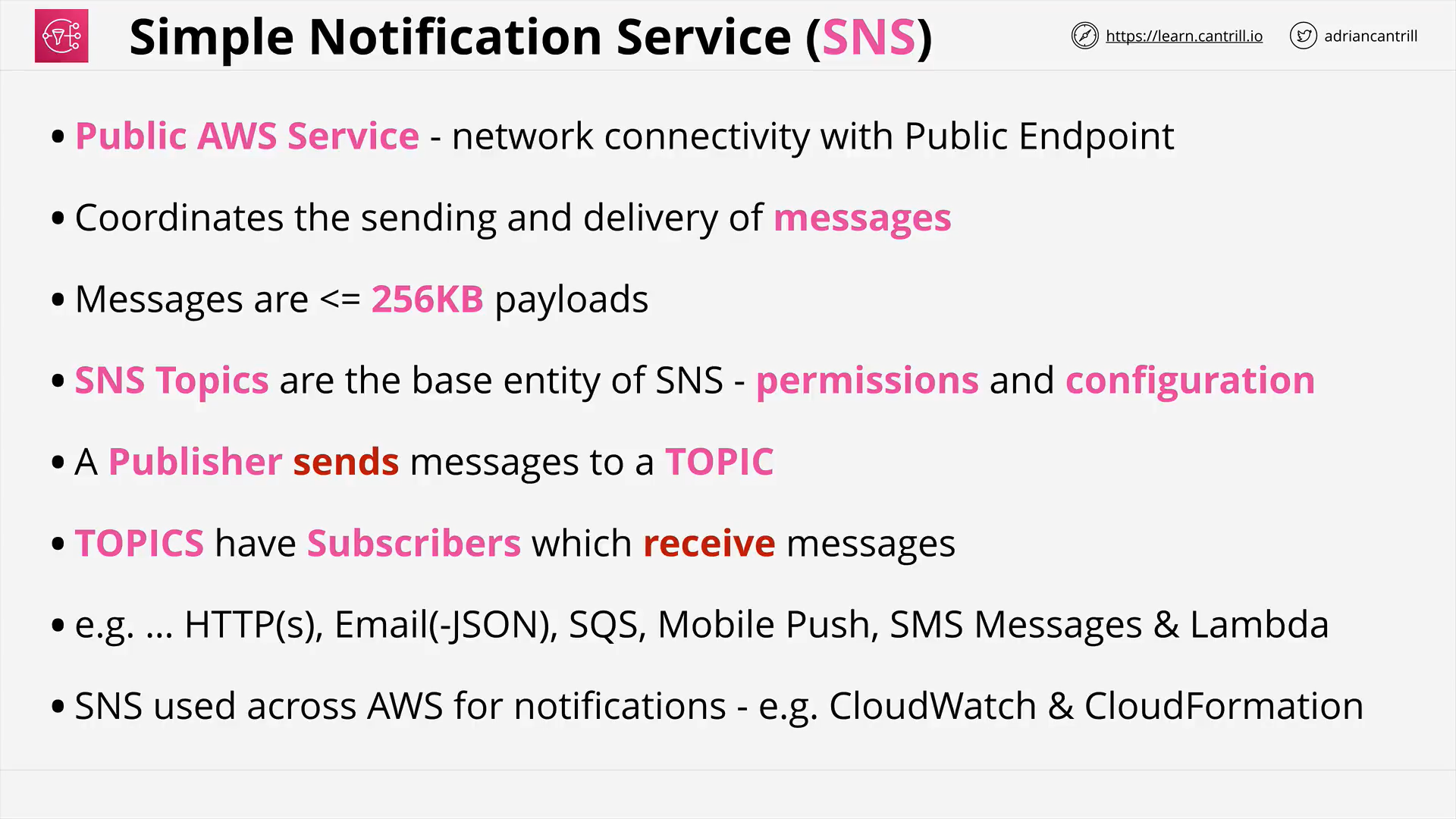 SNS - Pub-Sub Service
SNS - Pub-Sub Service
what is the maximum size of sns message?
256KB
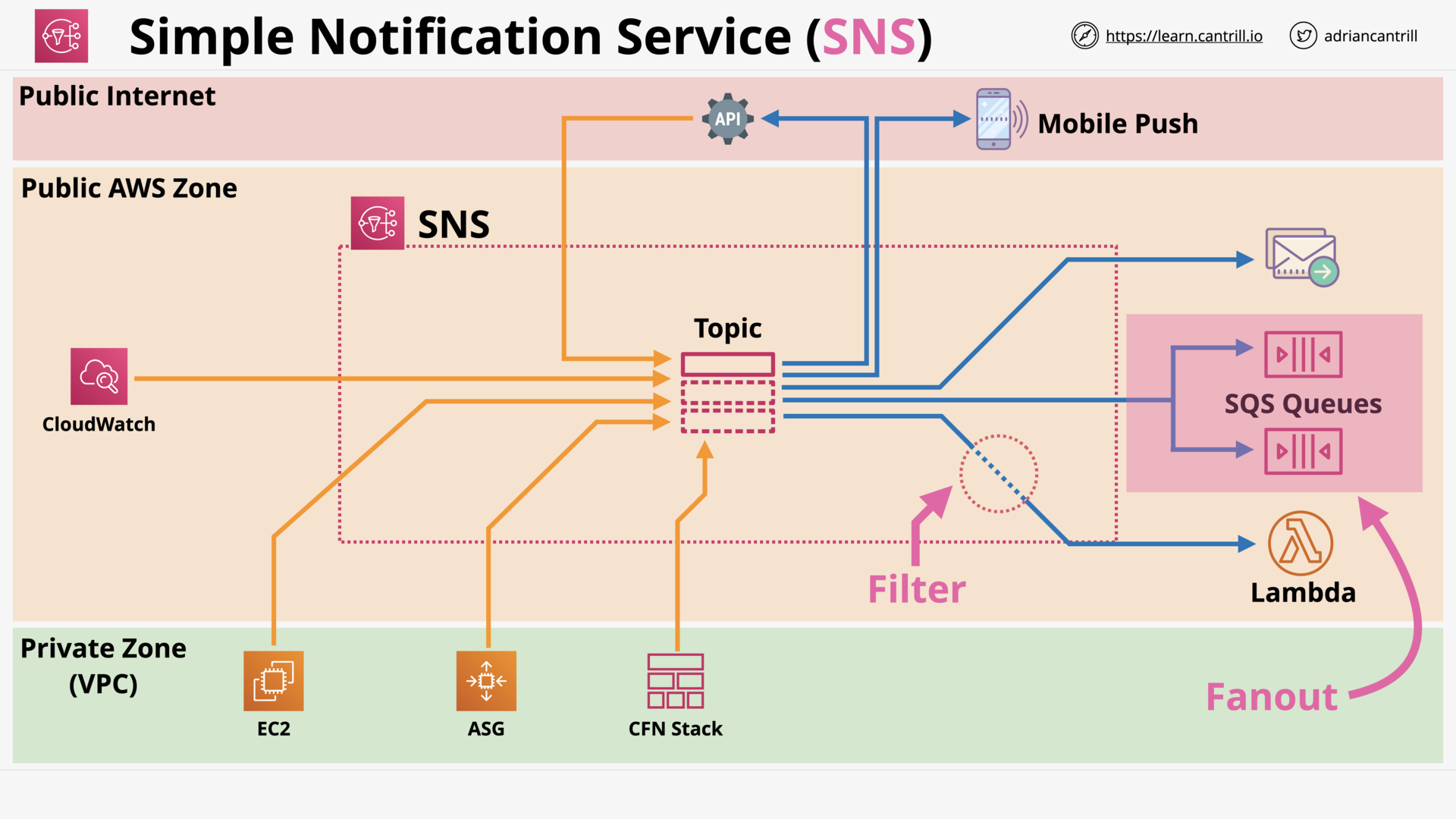 SNS - Architecture
SNS - Architecture
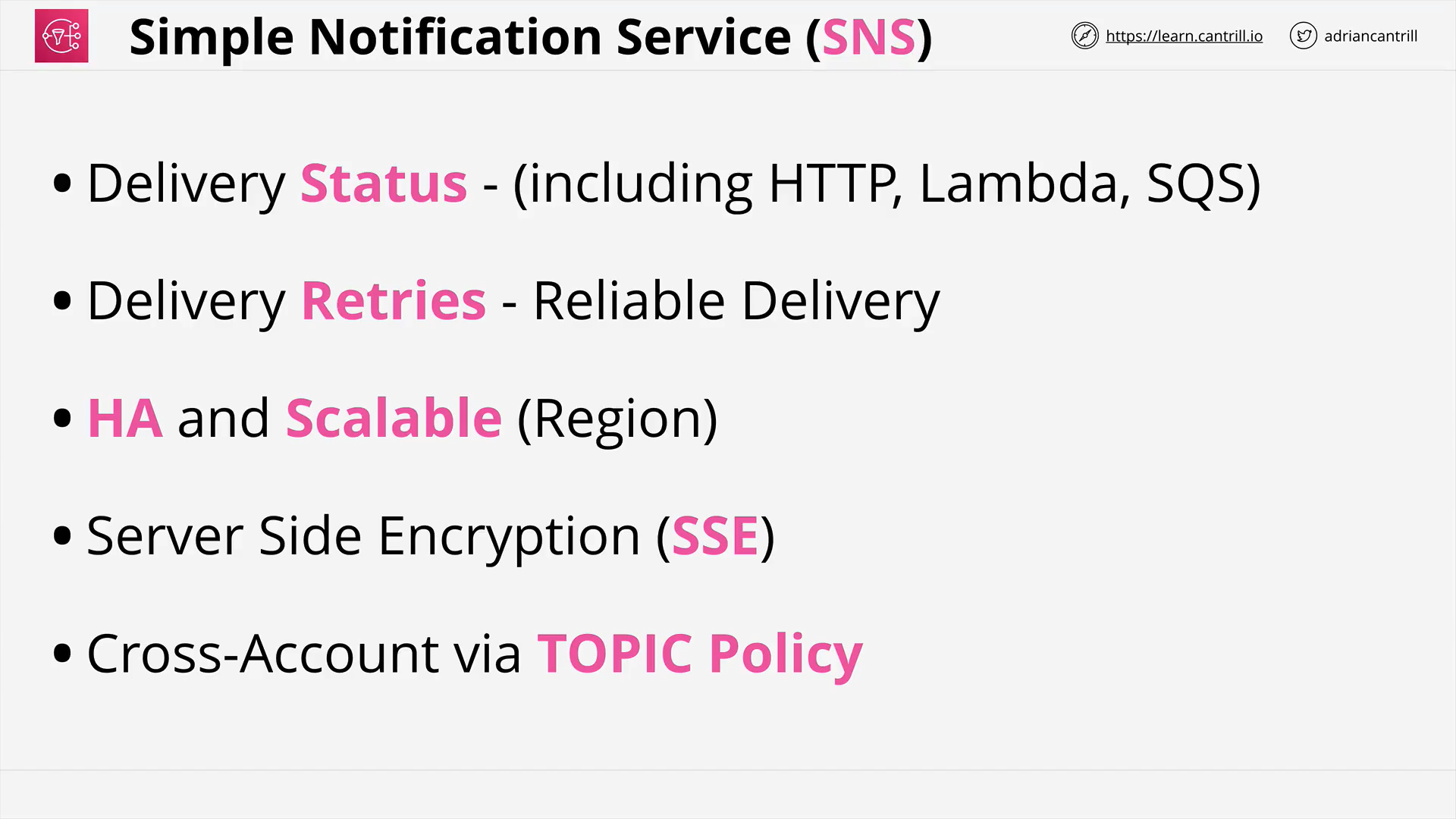 SNS - Delivery Status/Retries
SNS - Delivery Status/Retries
Step Functions (16:09)
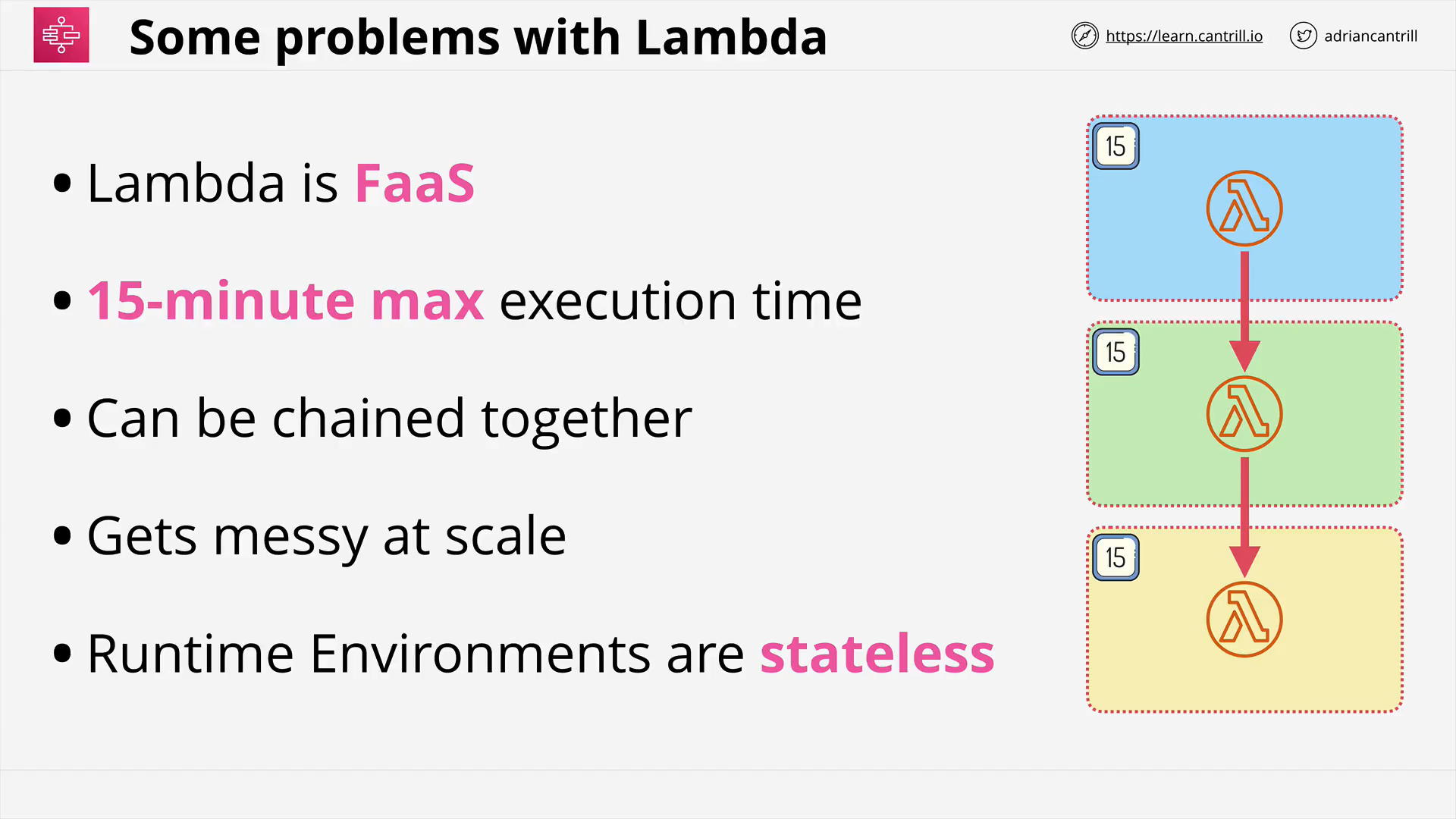 Lambda’s Problems
Lambda’s Problems
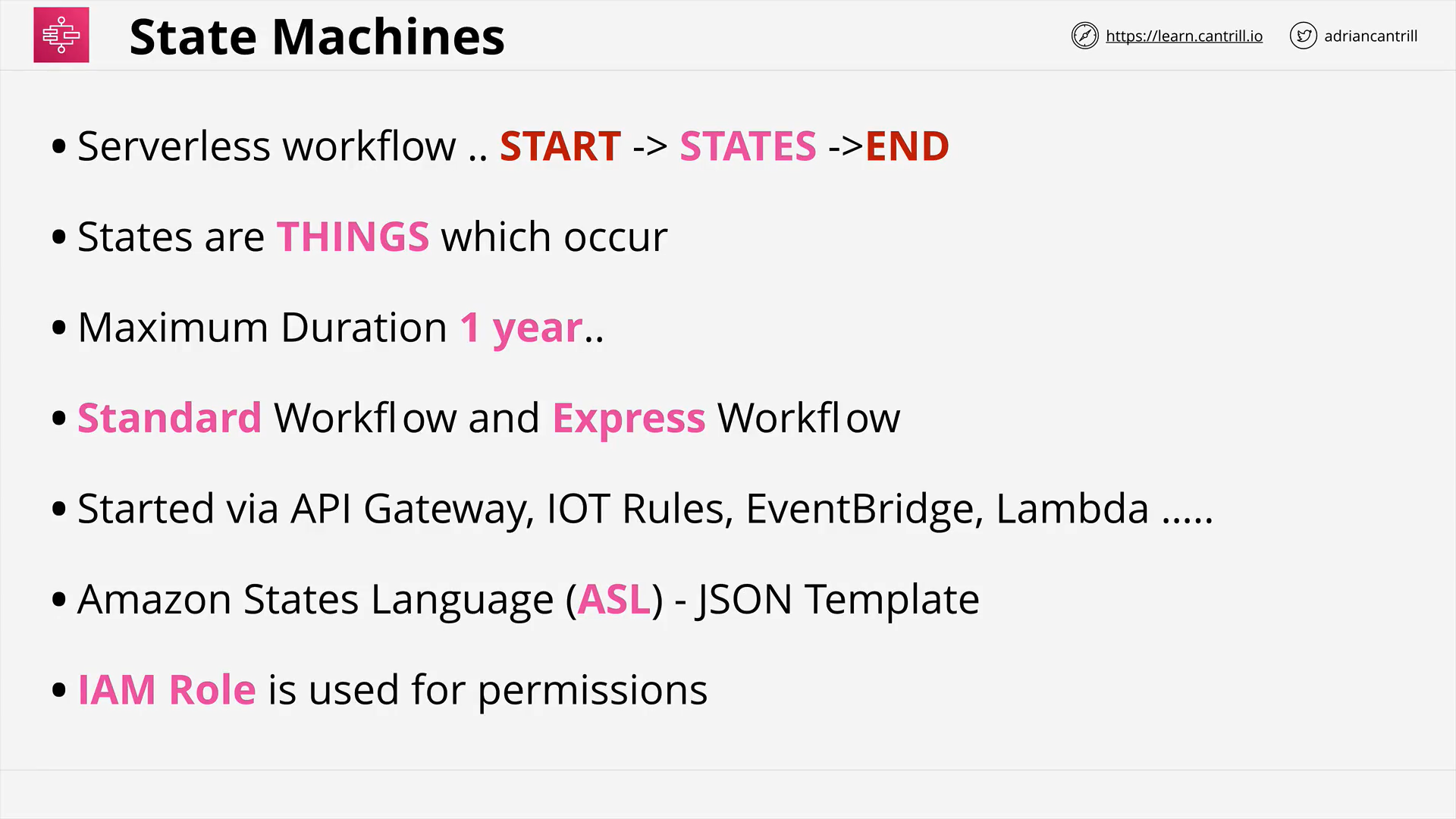 Step Functions - State Machines
Step Functions - State Machines
what are the main concepts of aws step functions?
-
AWS Step Functions lets we coordinate individual tasks into a visual workflow, so you can build and update apps quickly.
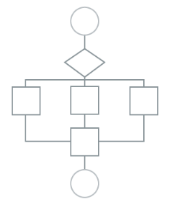
-
The workflows we build with Step Functions are called state machines.
-
Each step of your workflow is called a state.
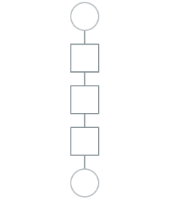
-
A Task (corresponding to a state) (a “Step Function”) represents a unit of work that another AWS service, such as AWS Lambda, performs.
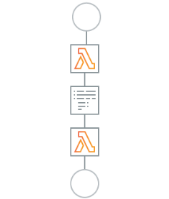
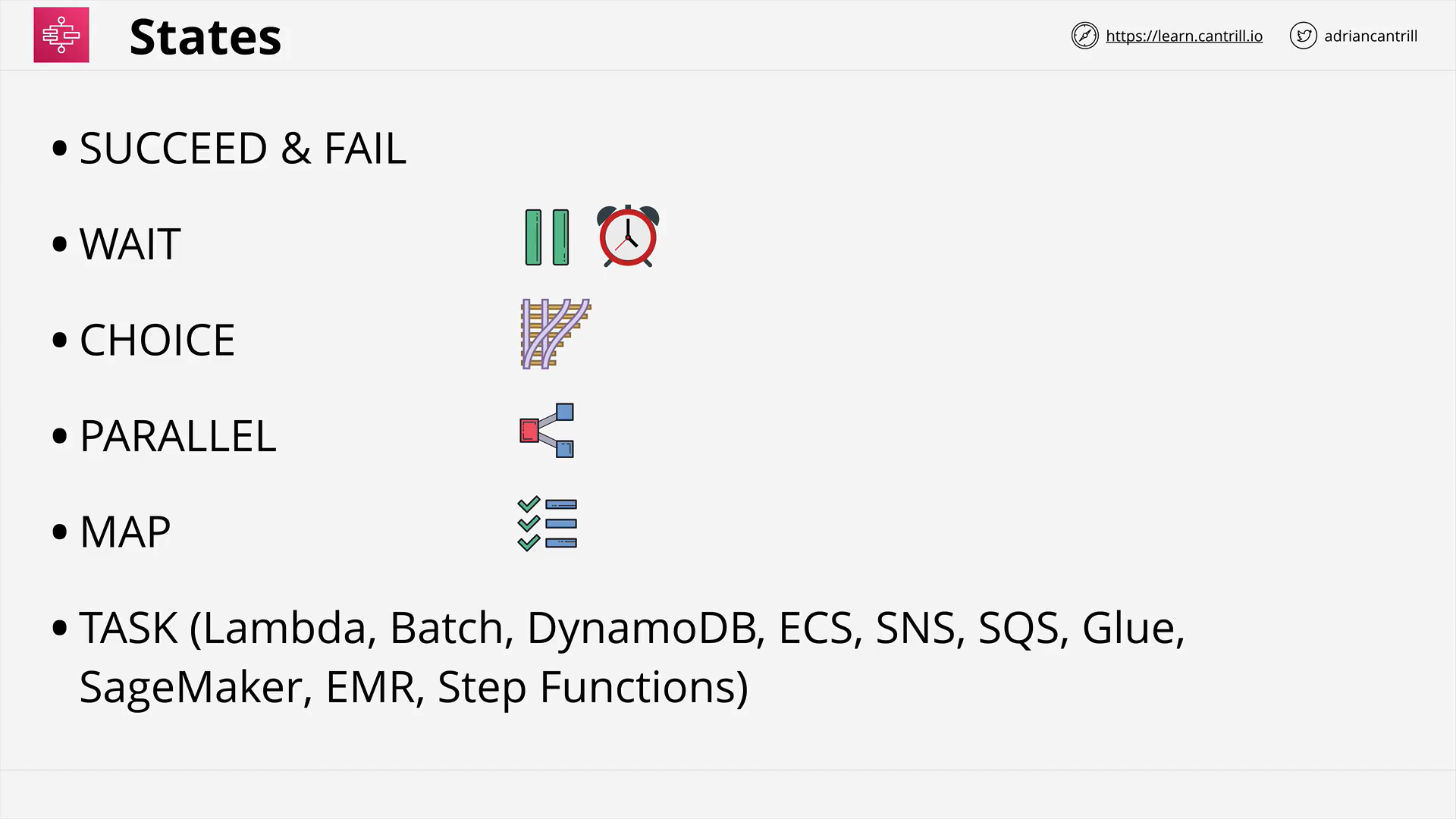 Step Functions - States
Step Functions - States
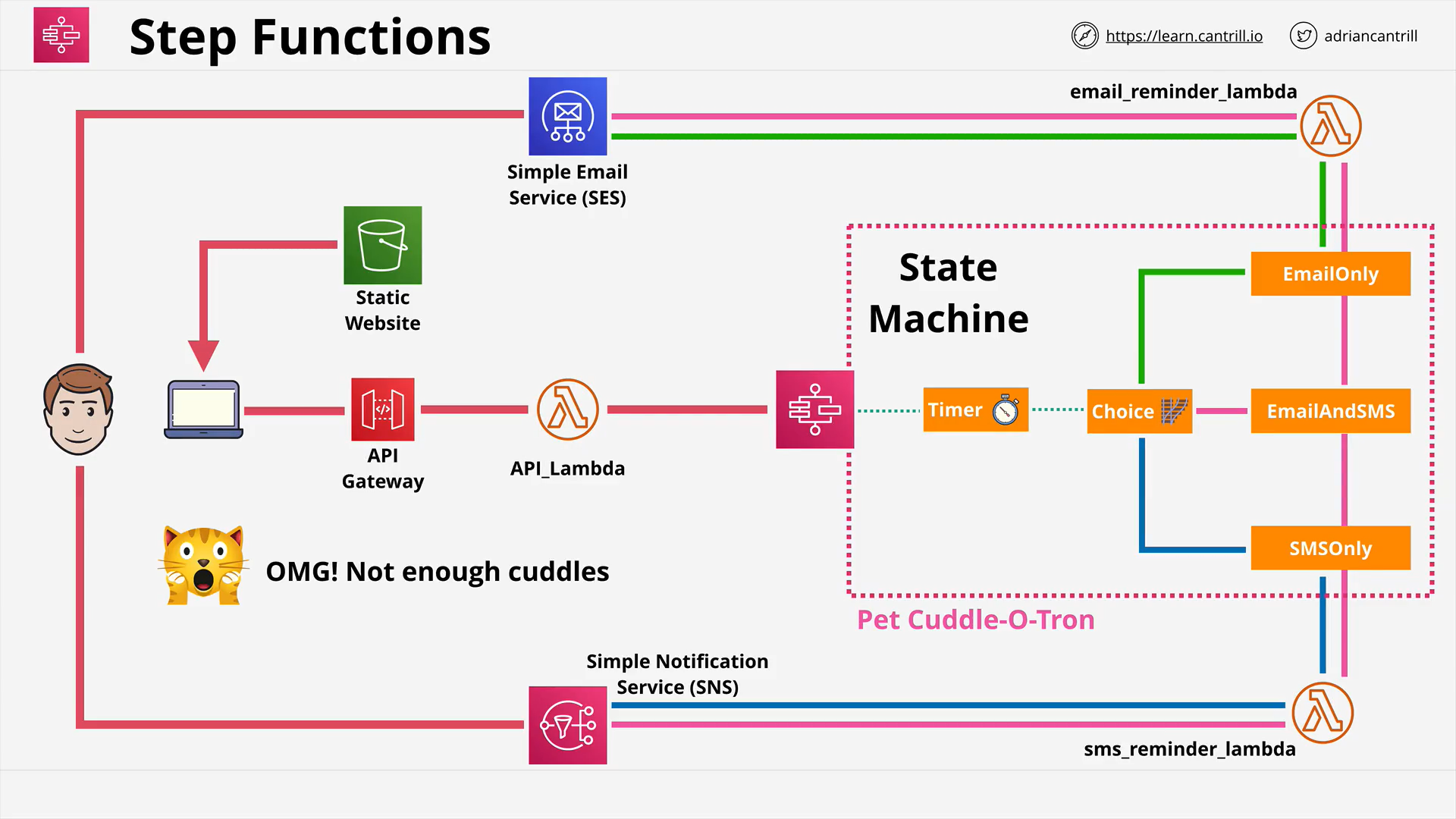 Step Functions - Example Architecture
Step Functions - Example Architecture
API Gateway 101 (16:27)
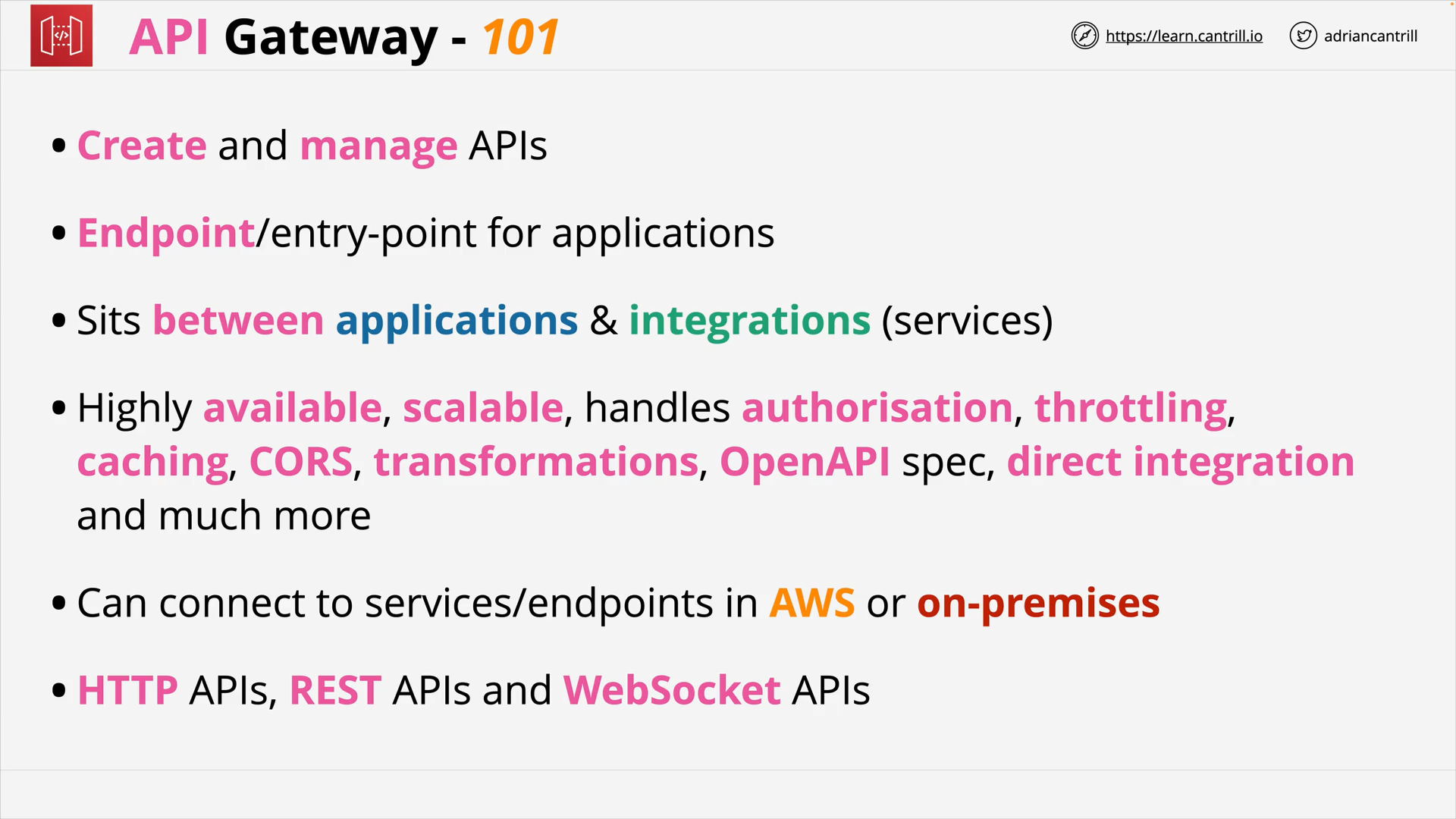 API Gateway - 101
API Gateway - 101
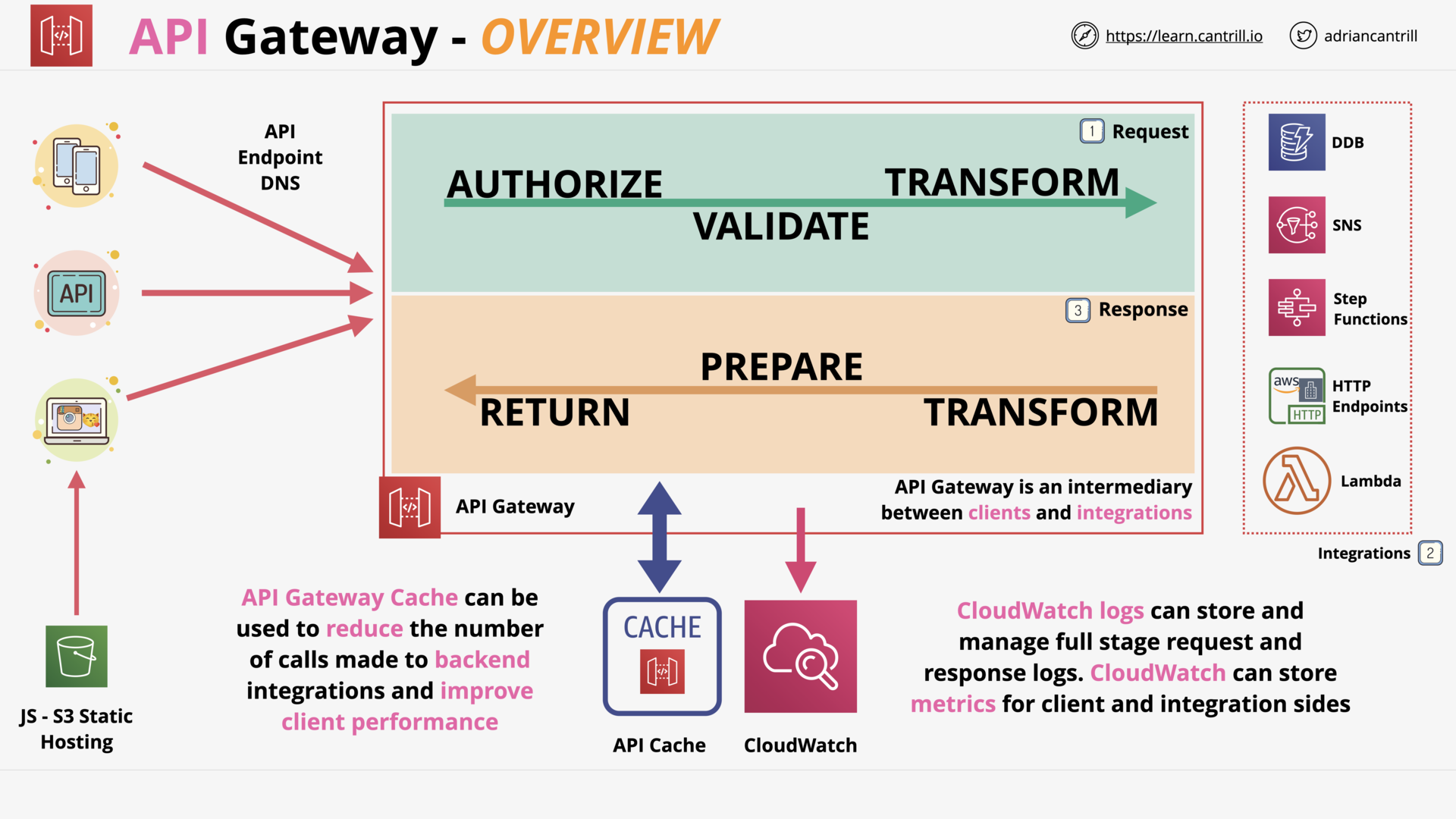 API Gateway - Overview
API Gateway - Overview
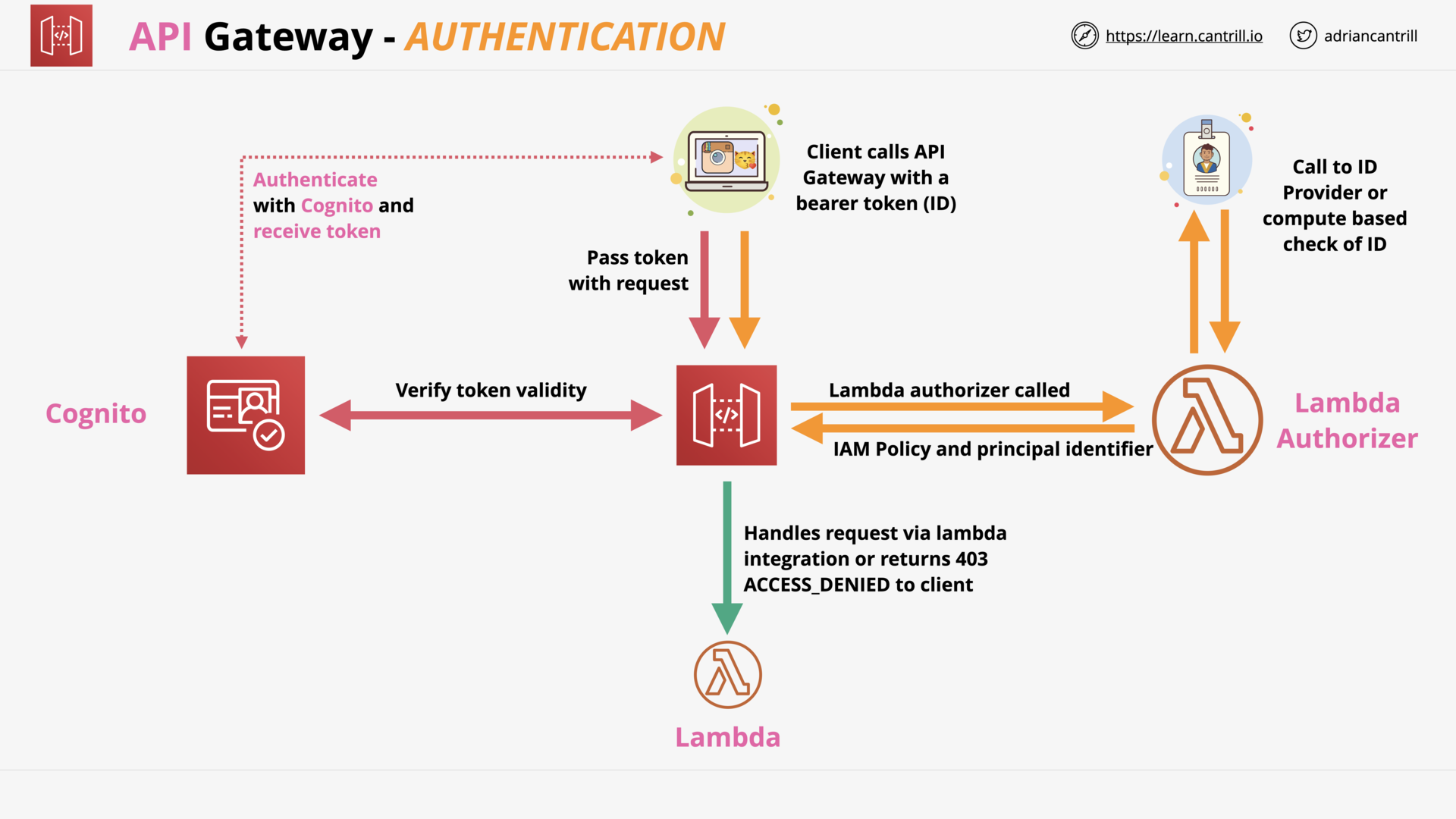 API Gateway - Authentication
API Gateway - Authentication
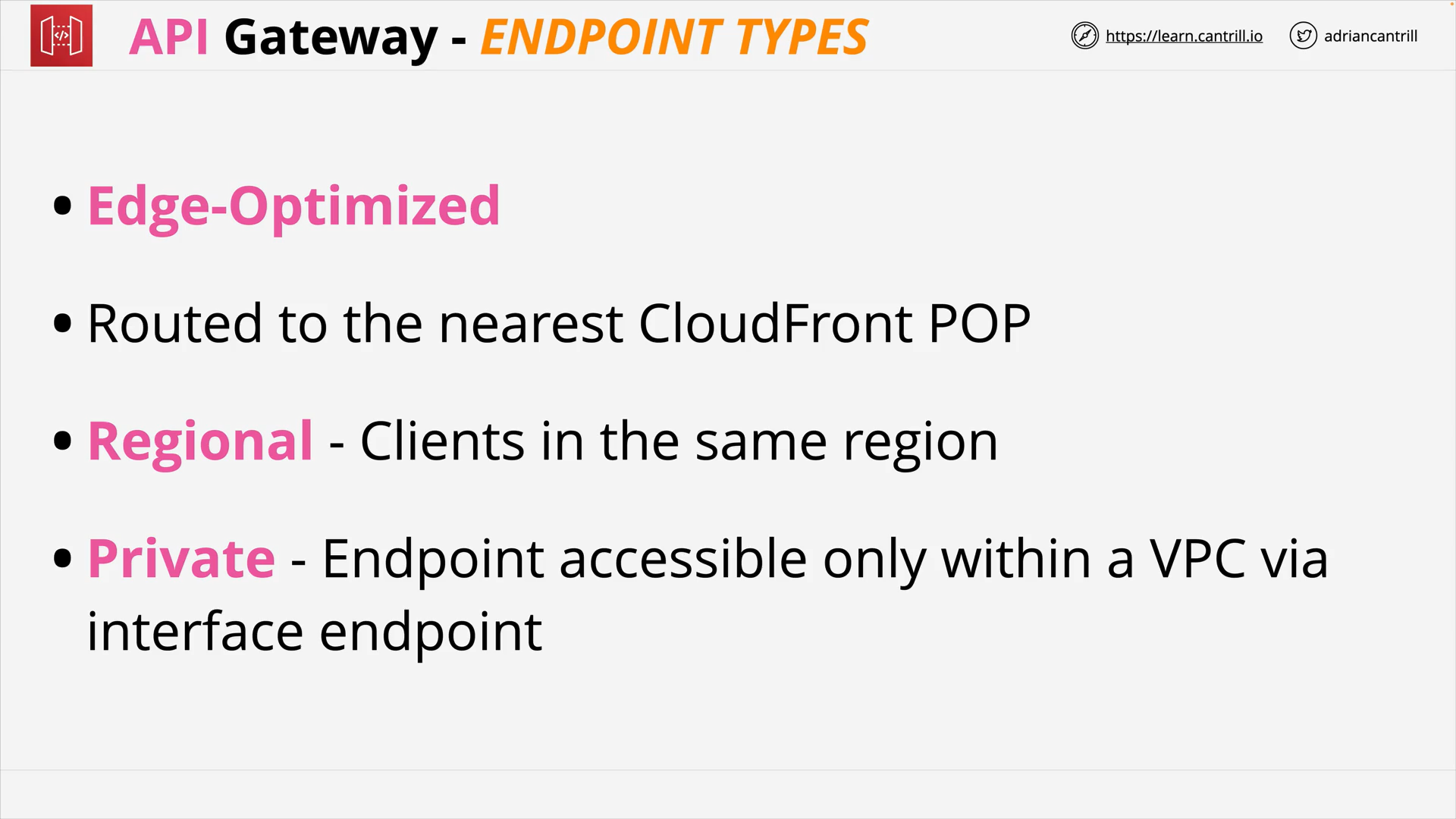 API Gateway - Endpoint Types
API Gateway - Endpoint Types
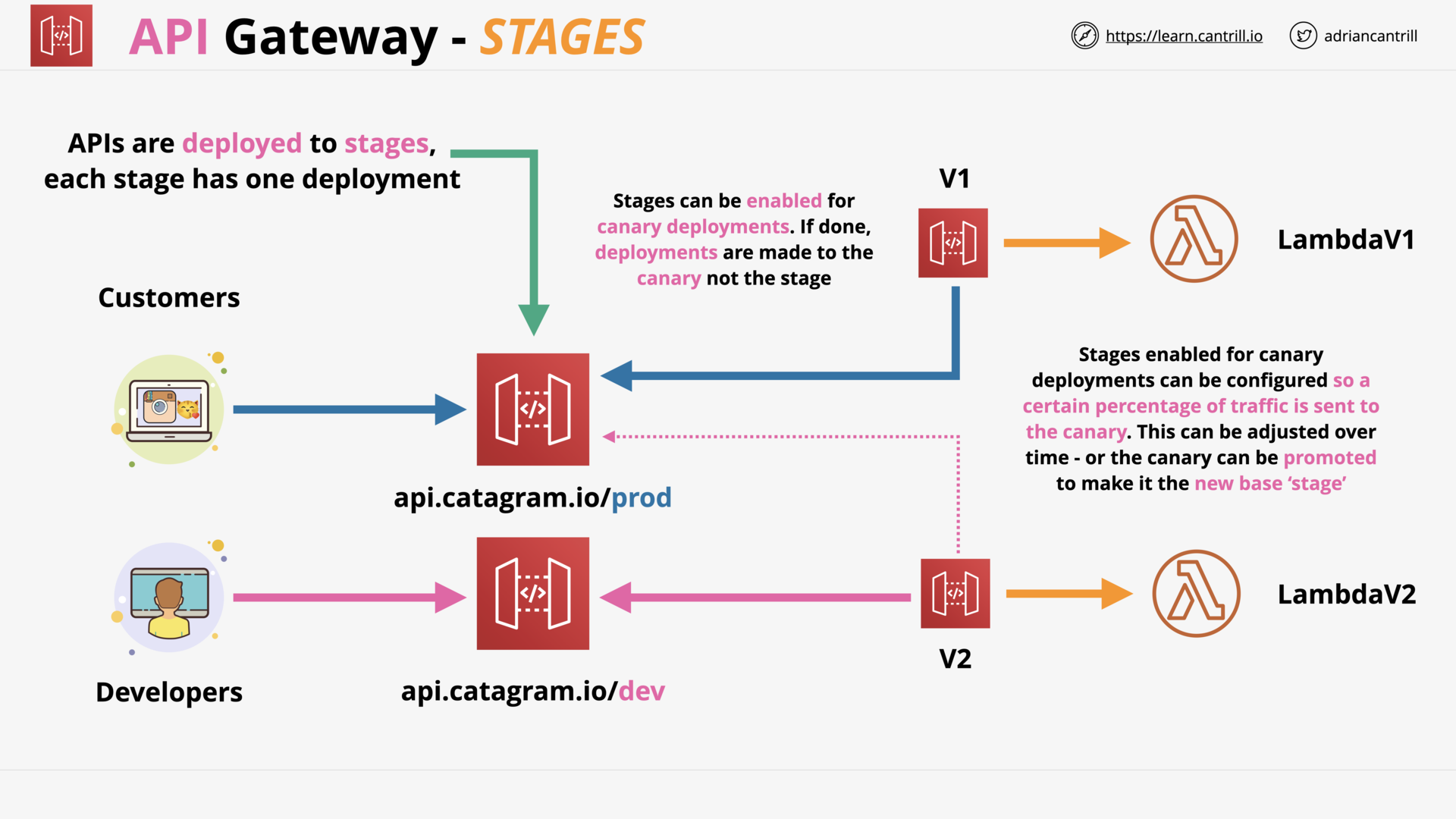 API Gateway - Stages
API Gateway - Stages
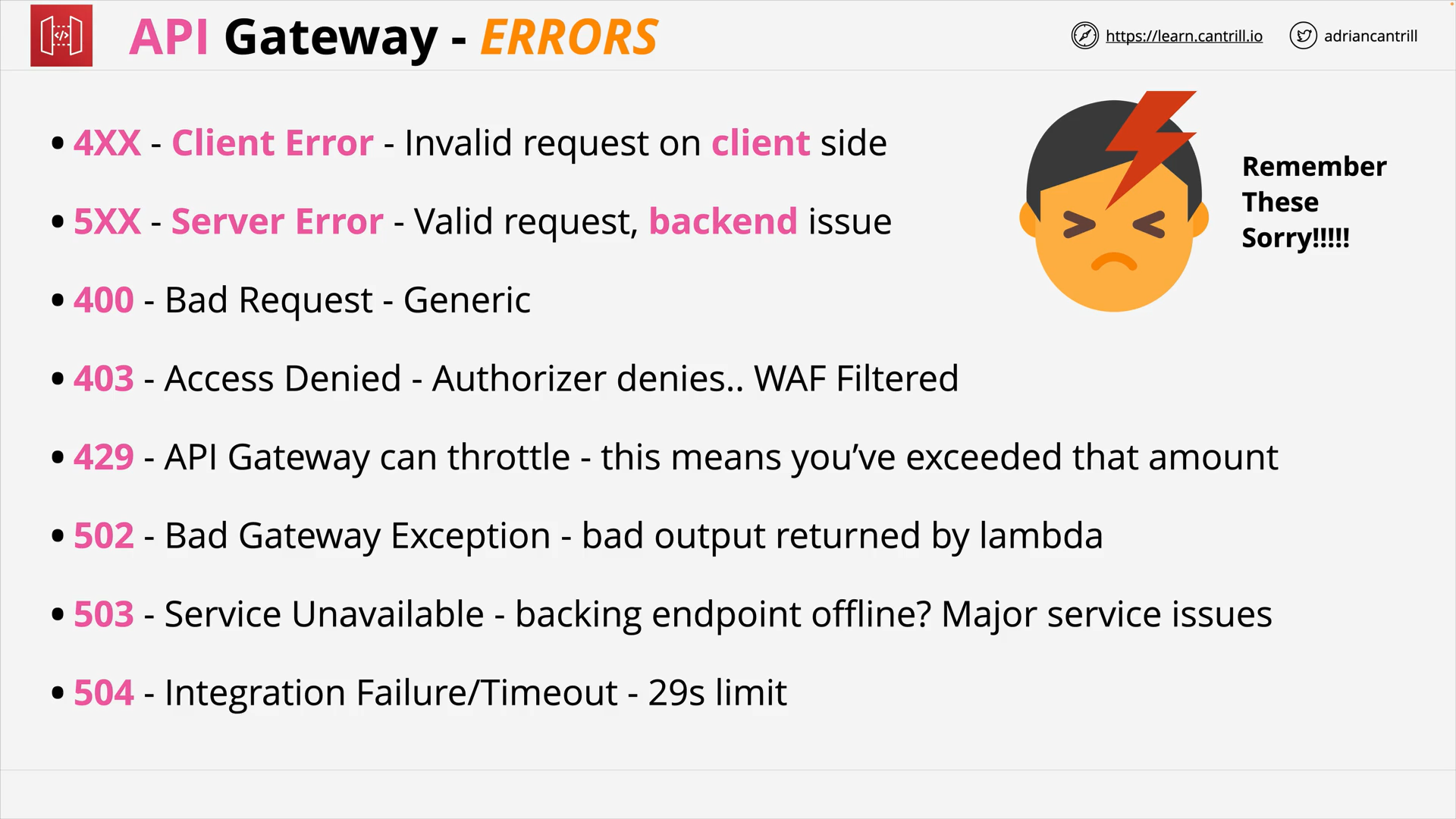 API Gateway - Errors
API Gateway - Errors
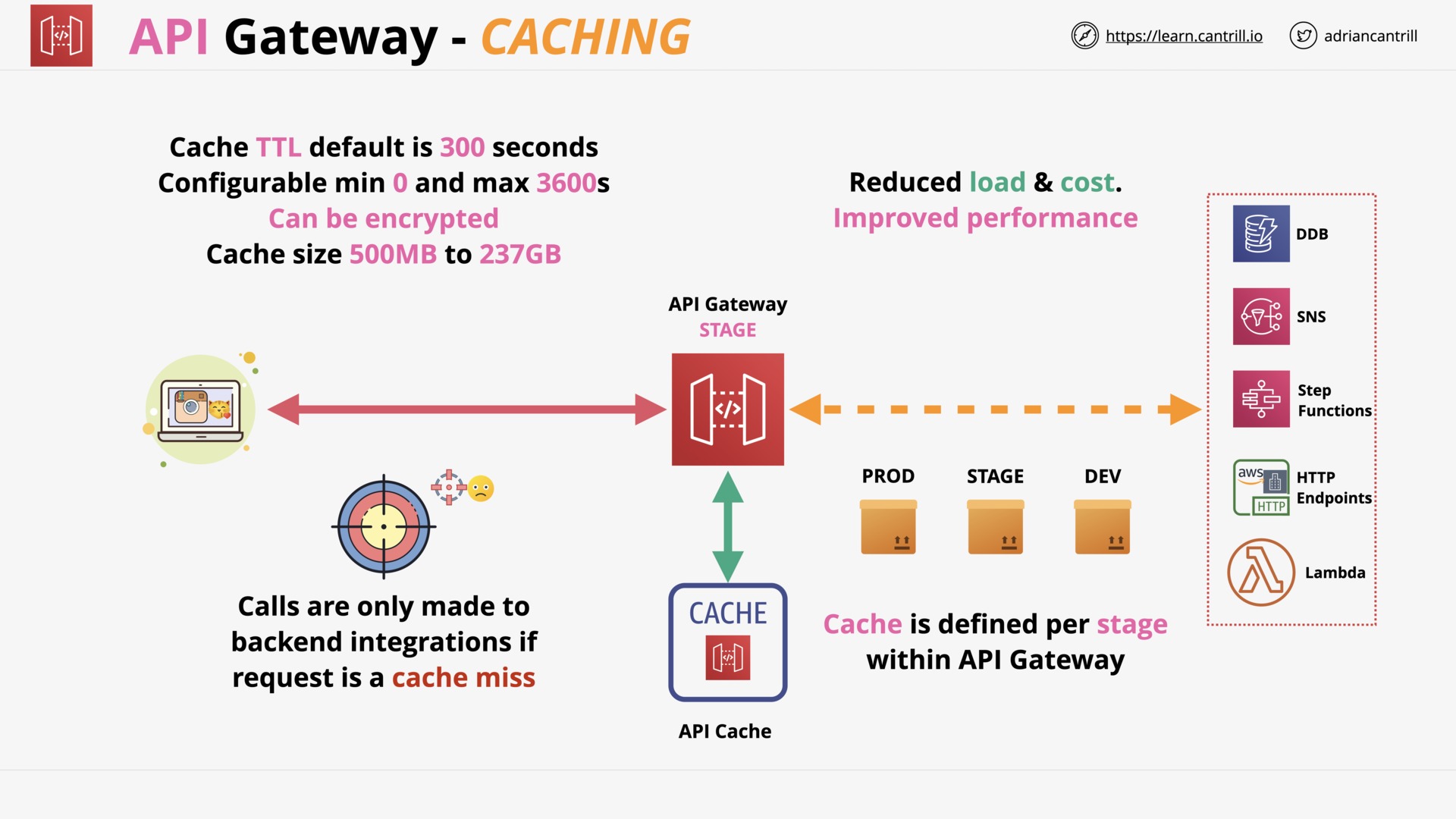 API Gateway - Caching
API Gateway - Caching
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART1 (5:01)
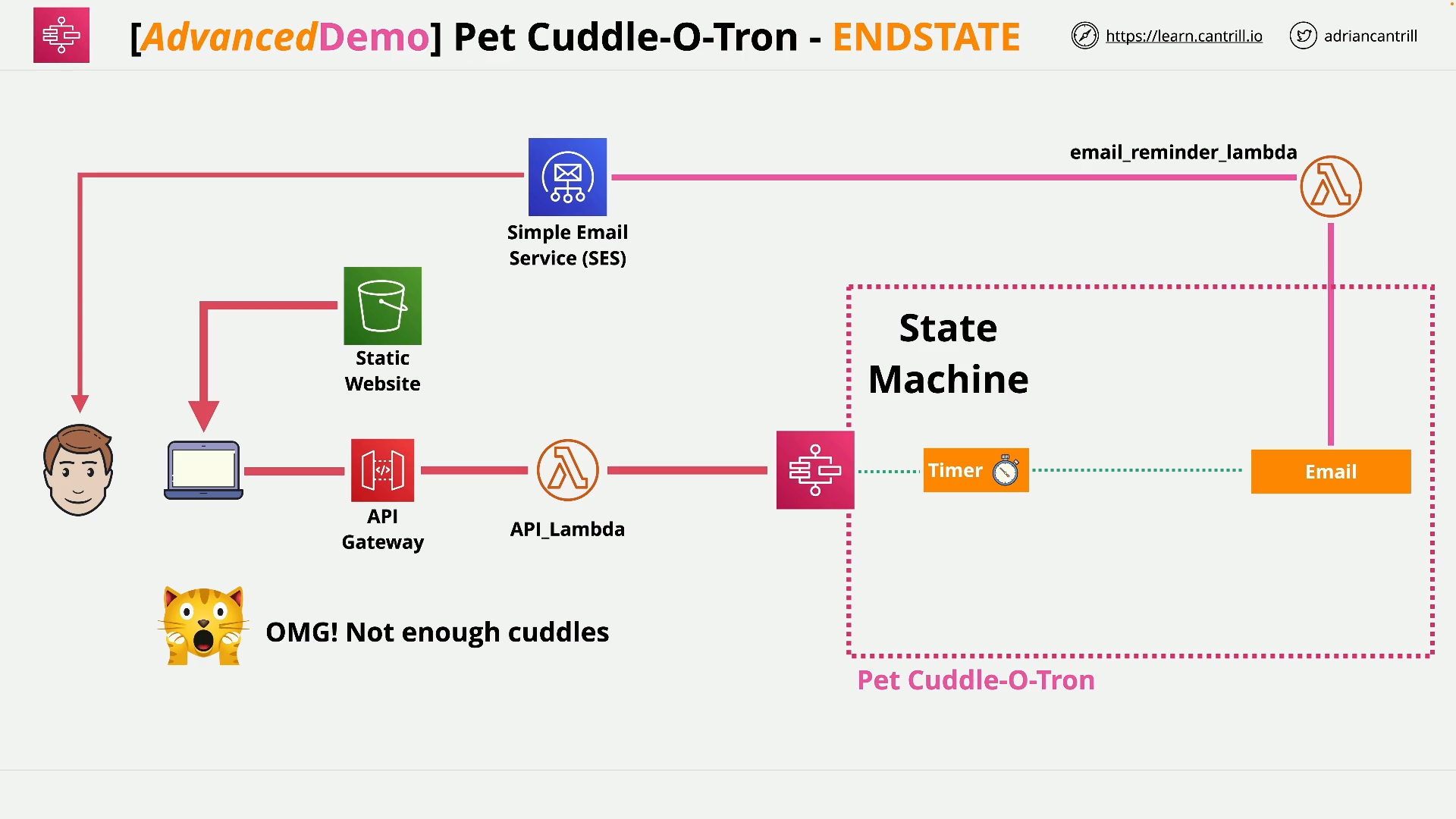
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART2 (8:24)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART3 (12:31)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART4 (13:31)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART5 (12:55)
[MINI_PROJECT] Build A Serverless App - Pet-Cuddle-o-Tron - PART6 (2:39)
Simple Queue Service (15:30)
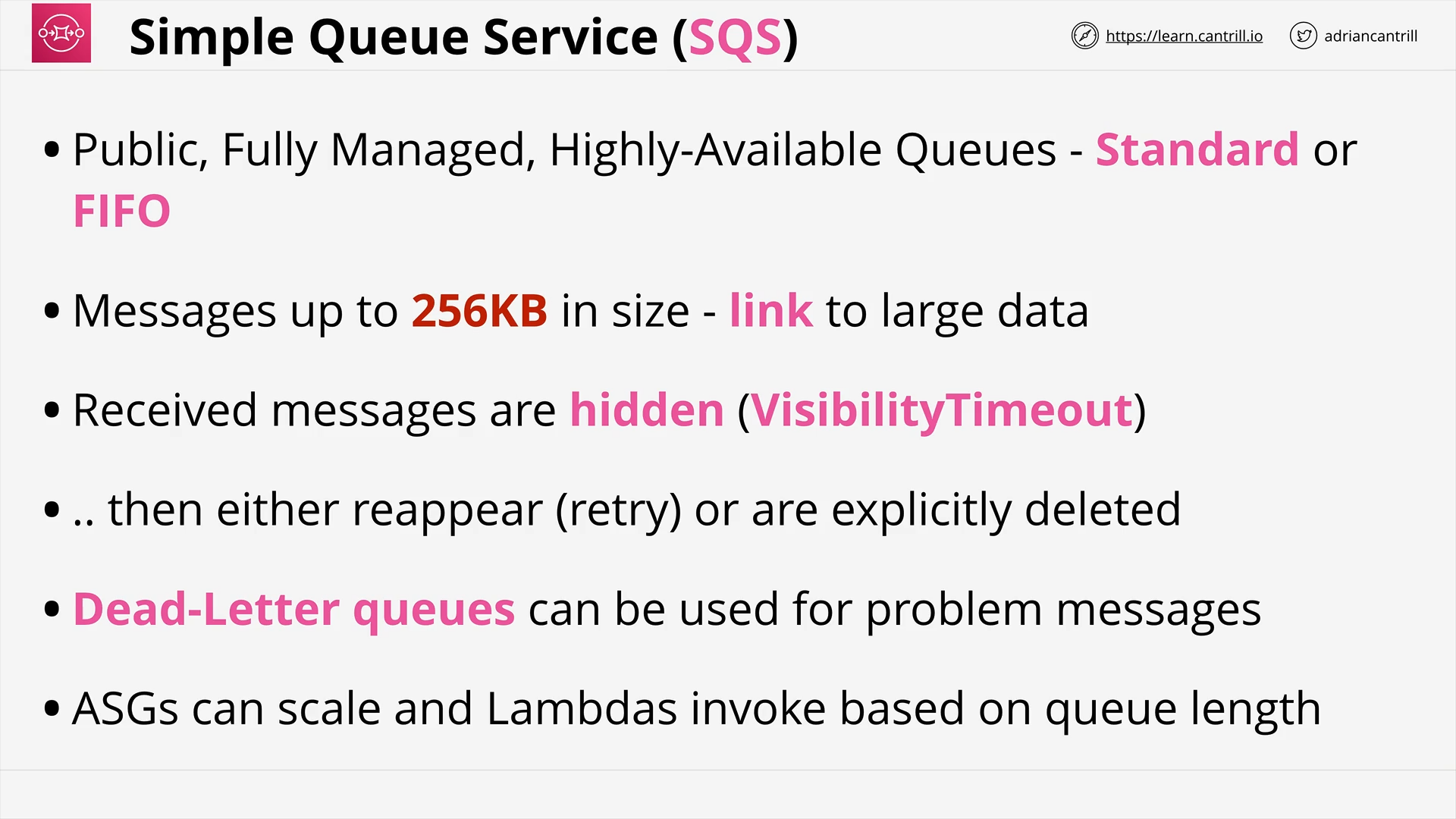 SQS - Overview
SQS - Overview
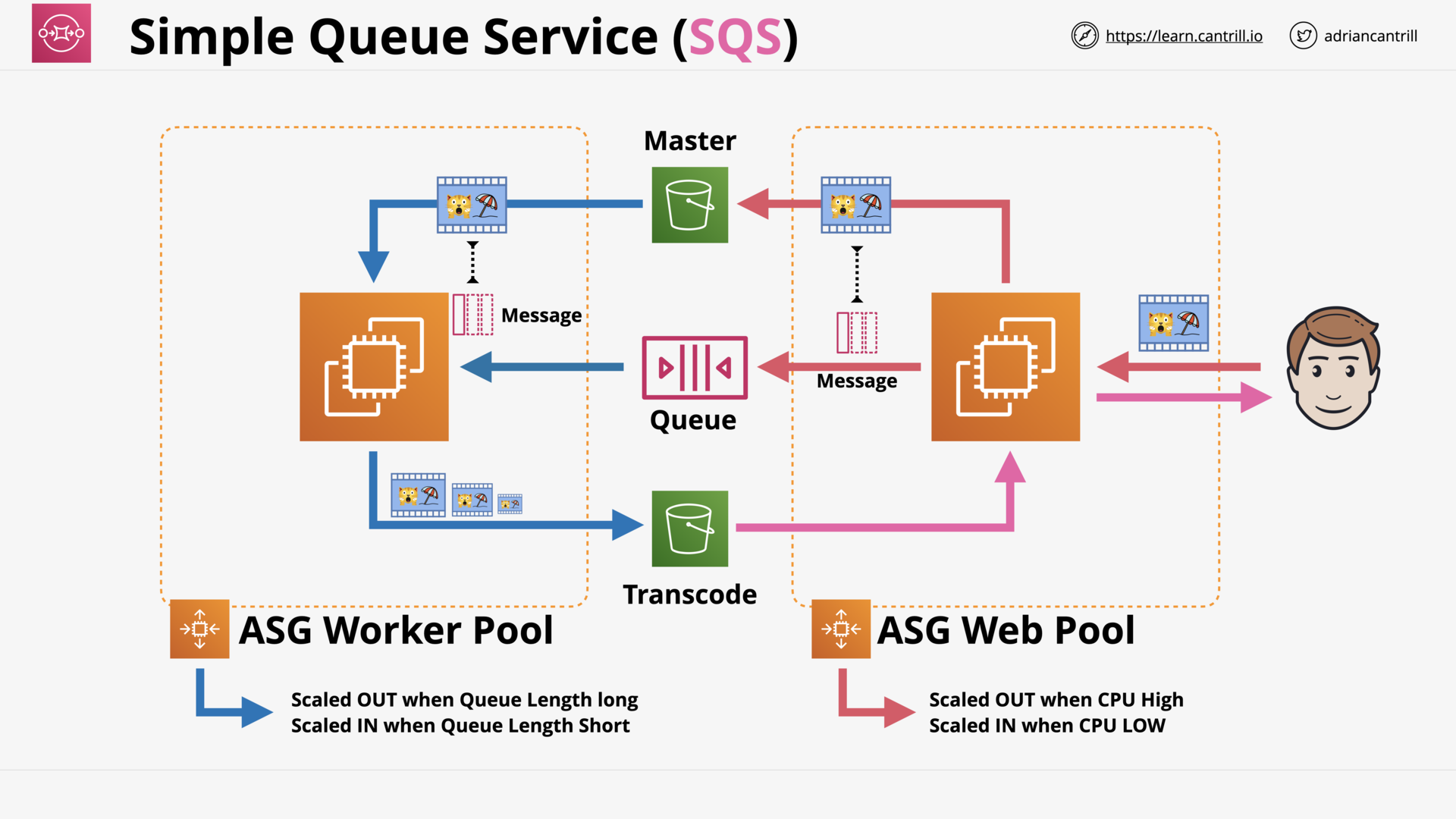 SQS - Architecture
SQS - Architecture
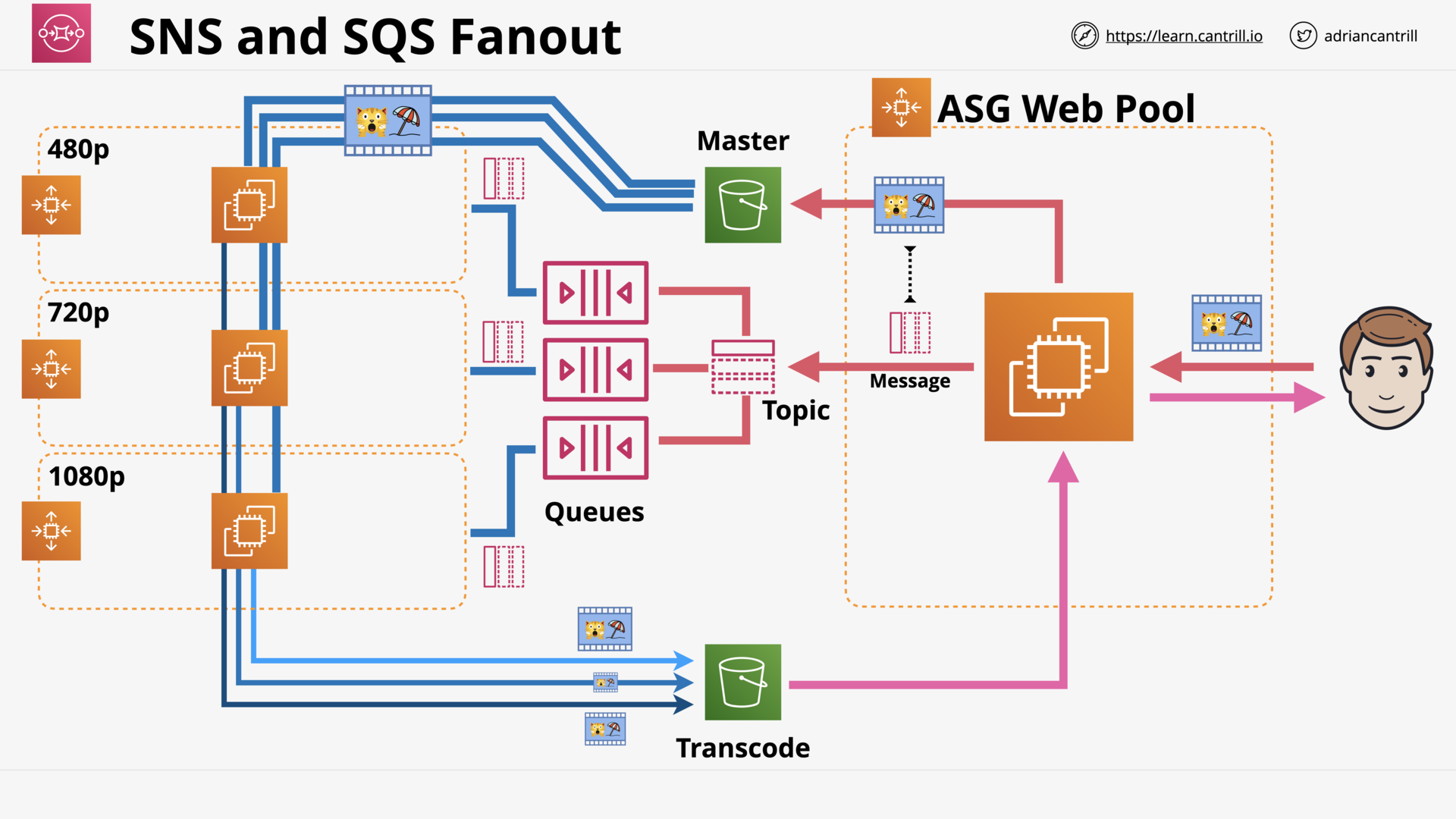 SQS & SNS - Architecture
SQS & SNS - Architecture
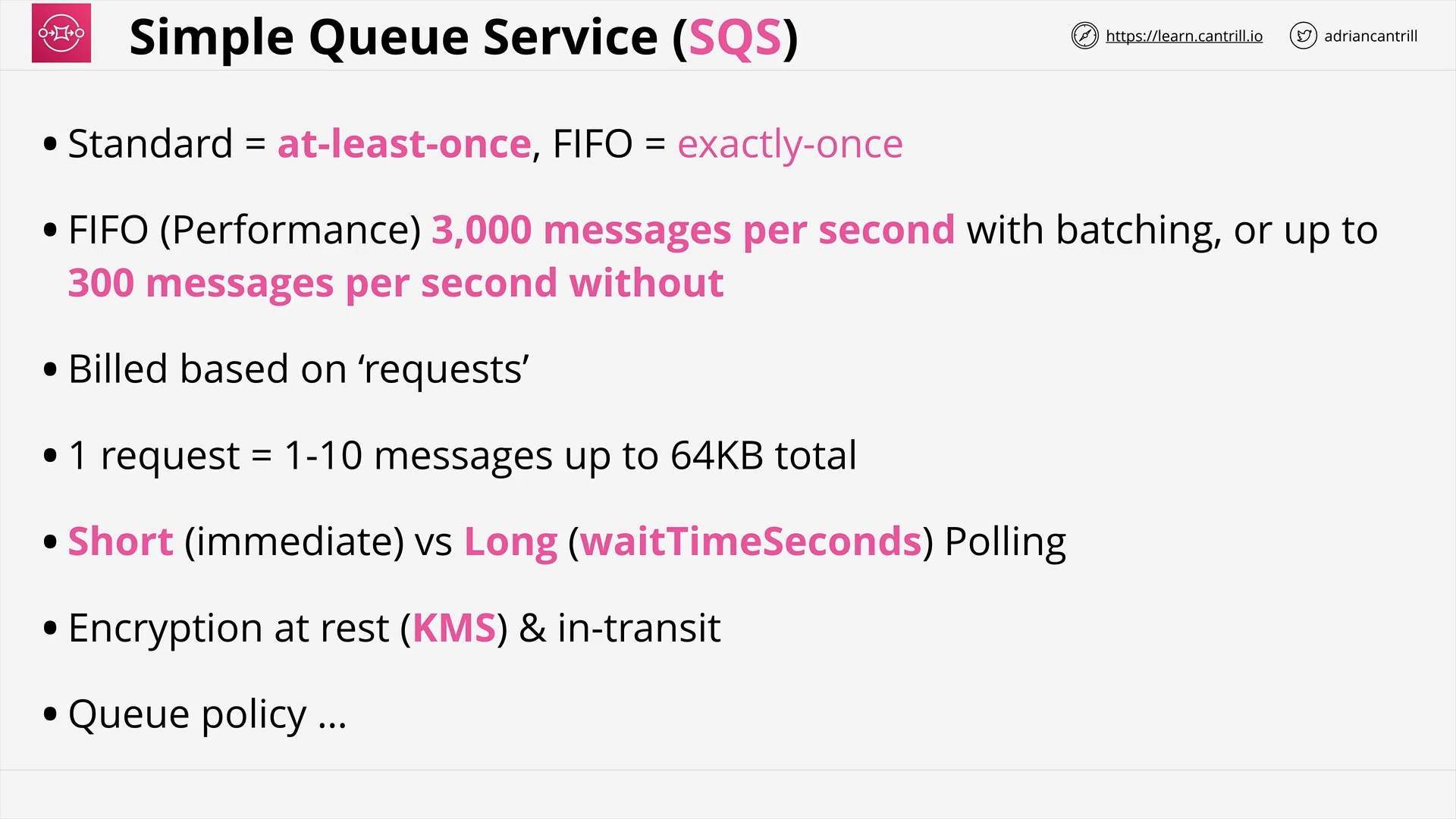 SQS - Recap
SQS - Recap
SQS Standard vs FIFO Queues (3:29)
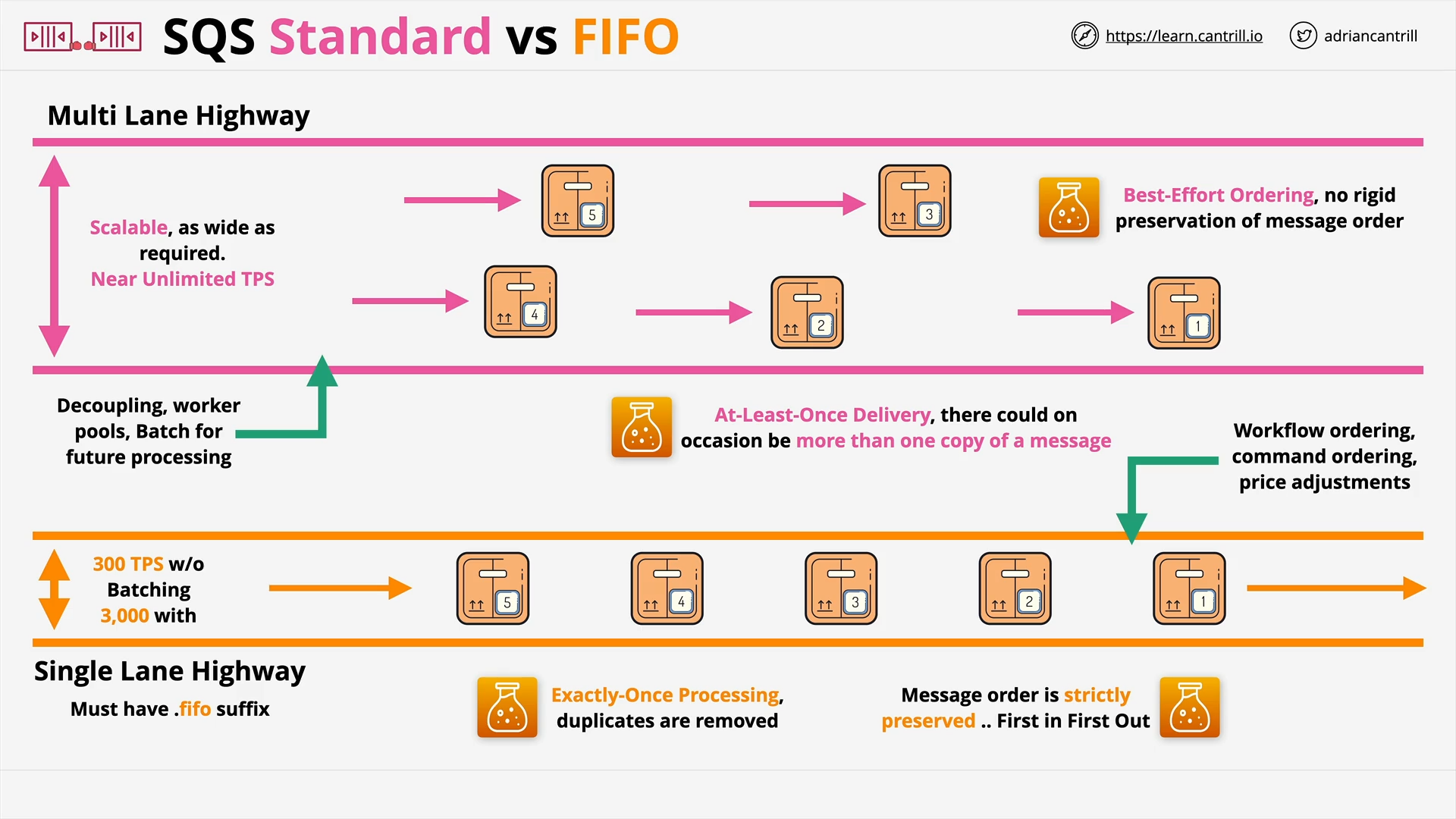 SQS - Standard vs FIFO Queues
SQS - Standard vs FIFO Queues
SQS Delay Queues (4:38)
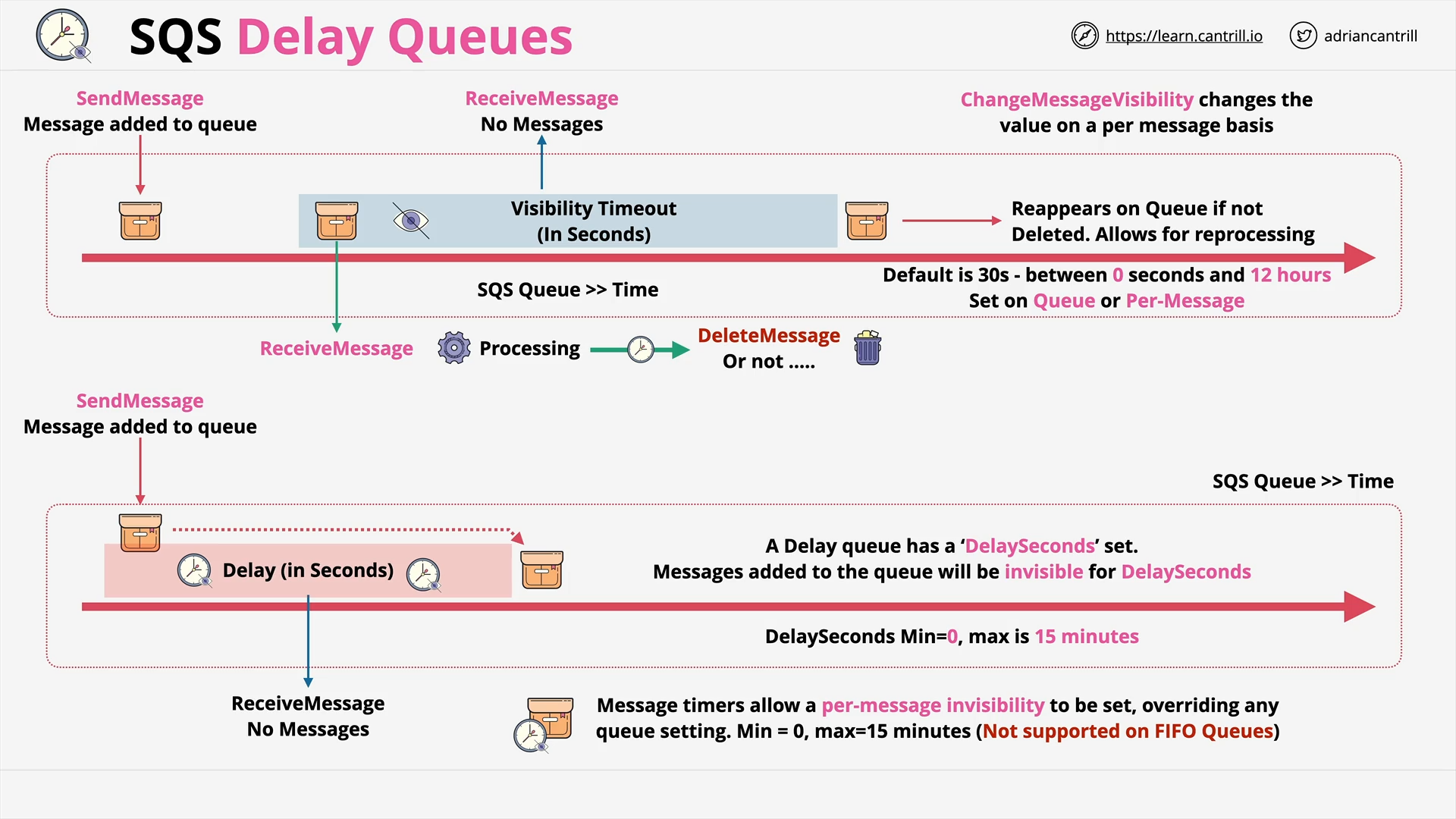 SQS Visibility Timeout vs SQS Delay Queues
SQS Visibility Timeout vs SQS Delay Queues
what is [sqs visibility timeout](https://docs.aws.amazon.com/awssimplequeueservice/latest/sqsdeveloperguide/sqs-delay-queues.html)?
- While a SQS message is processing, it won’t be visible in the SQS queue.
- After the message are processed,
- It needs to be explicitly delete from the queue
- or it will reappear on the queue after the
Visibility Timeout.
what is the default value of sqs visibility timeout?
30s.
It can be varied from 0s -> 12h.
what is [sqs delay queues](https://docs.aws.amazon.com/awssimplequeueservice/latest/sqsdeveloperguide/sqs-delay-queues.html)?
For an SQS queue which has DelaySeconds set, after the messages added to the queue, they will be invisible for DelaySeconds.
what is the limit of sqs `delayseconds`?
0s -> 15m
SQS Dead-Letter Queues (DLQ) (4:17)
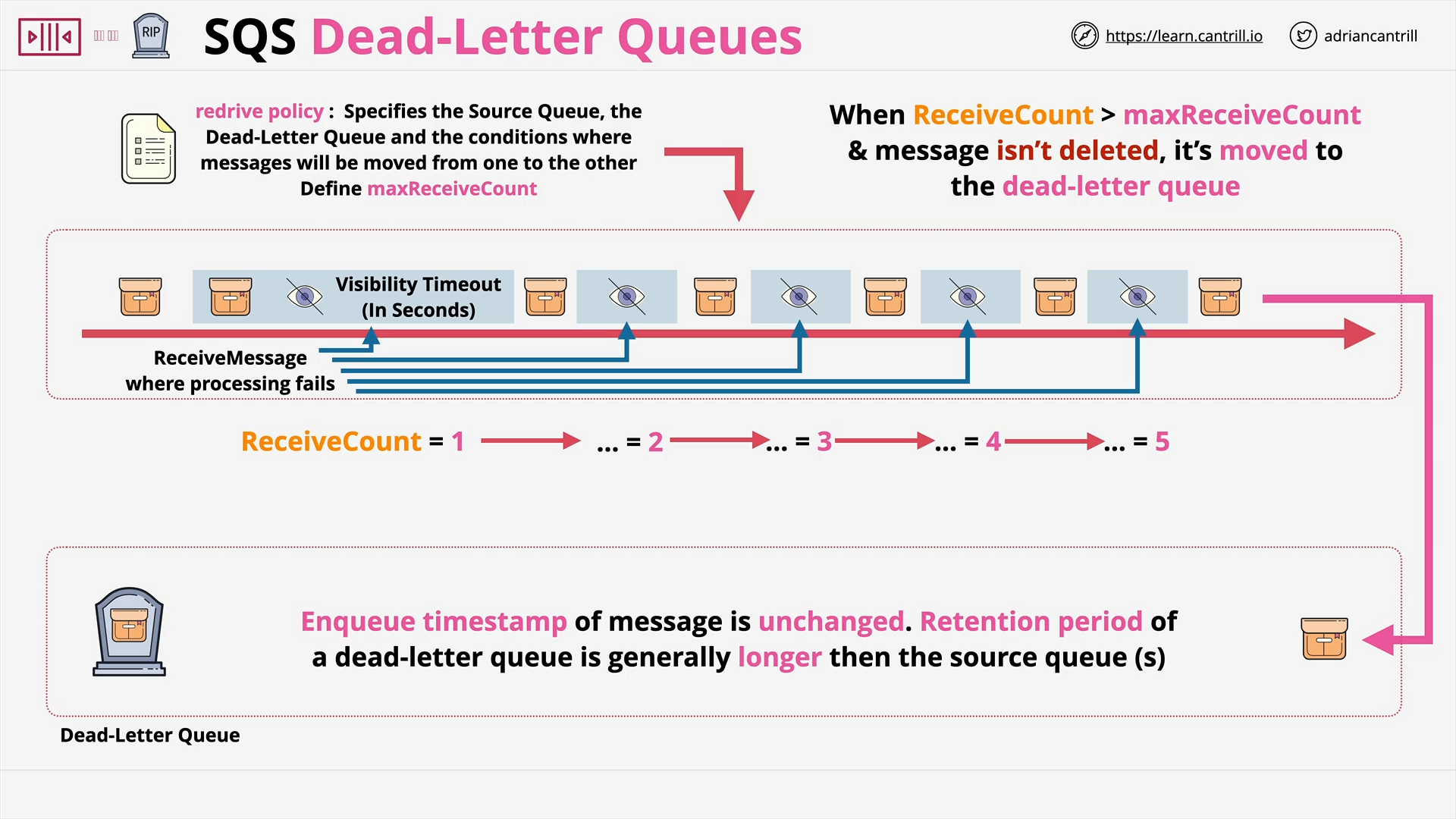 SQS Dead-Letter Queues
SQS Dead-Letter Queues
what is [sqs dlq](https://docs.aws.amazon.com/awssimplequeueservice/latest/sqsdeveloperguide/sqs-dead-letter-queues.html)?
The queue which stores messages that can’t be processed (consumed) successfully.
Kinesis Data Streams (7:52)
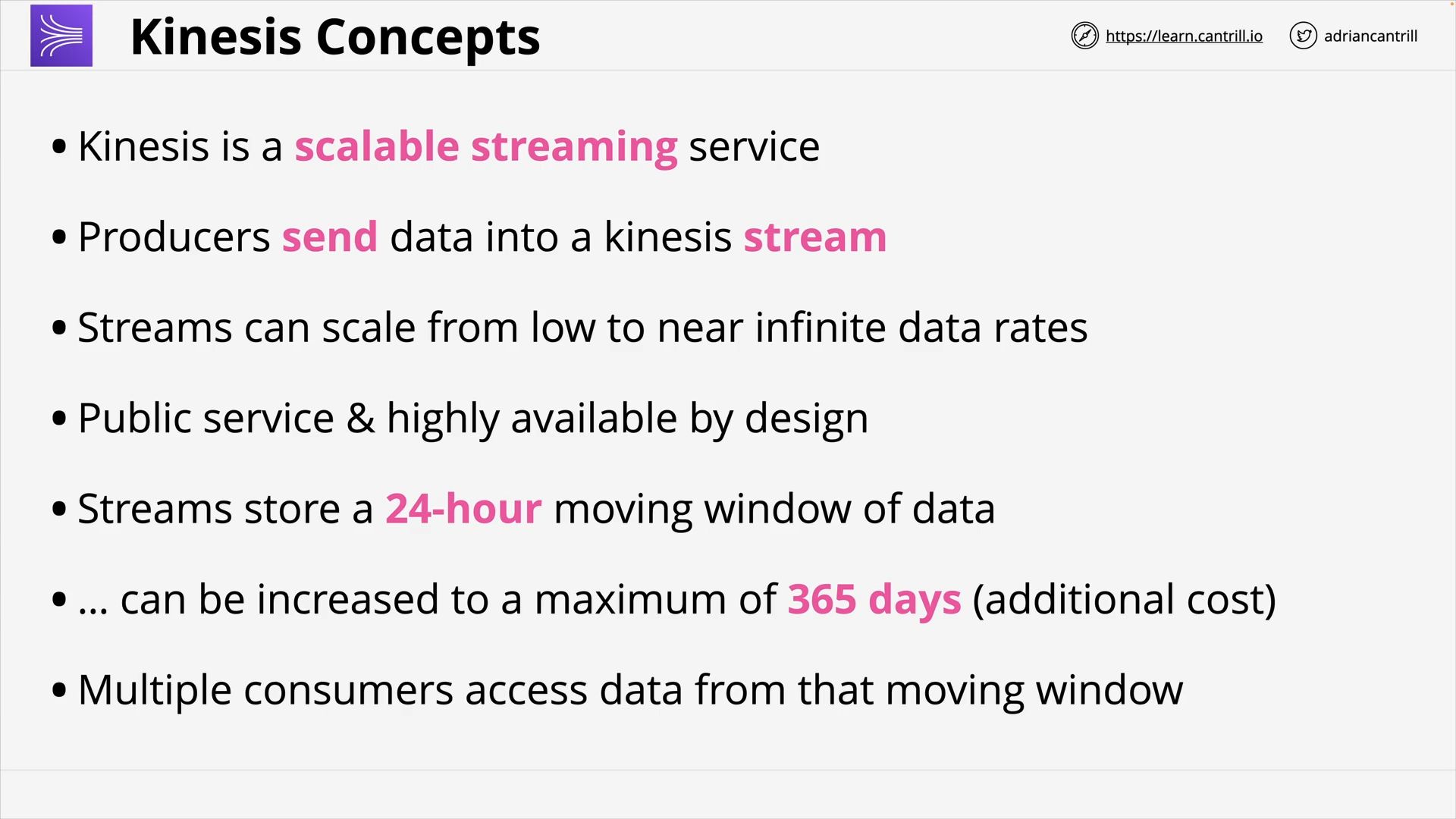 Kinesis - Concept
Kinesis - Concept
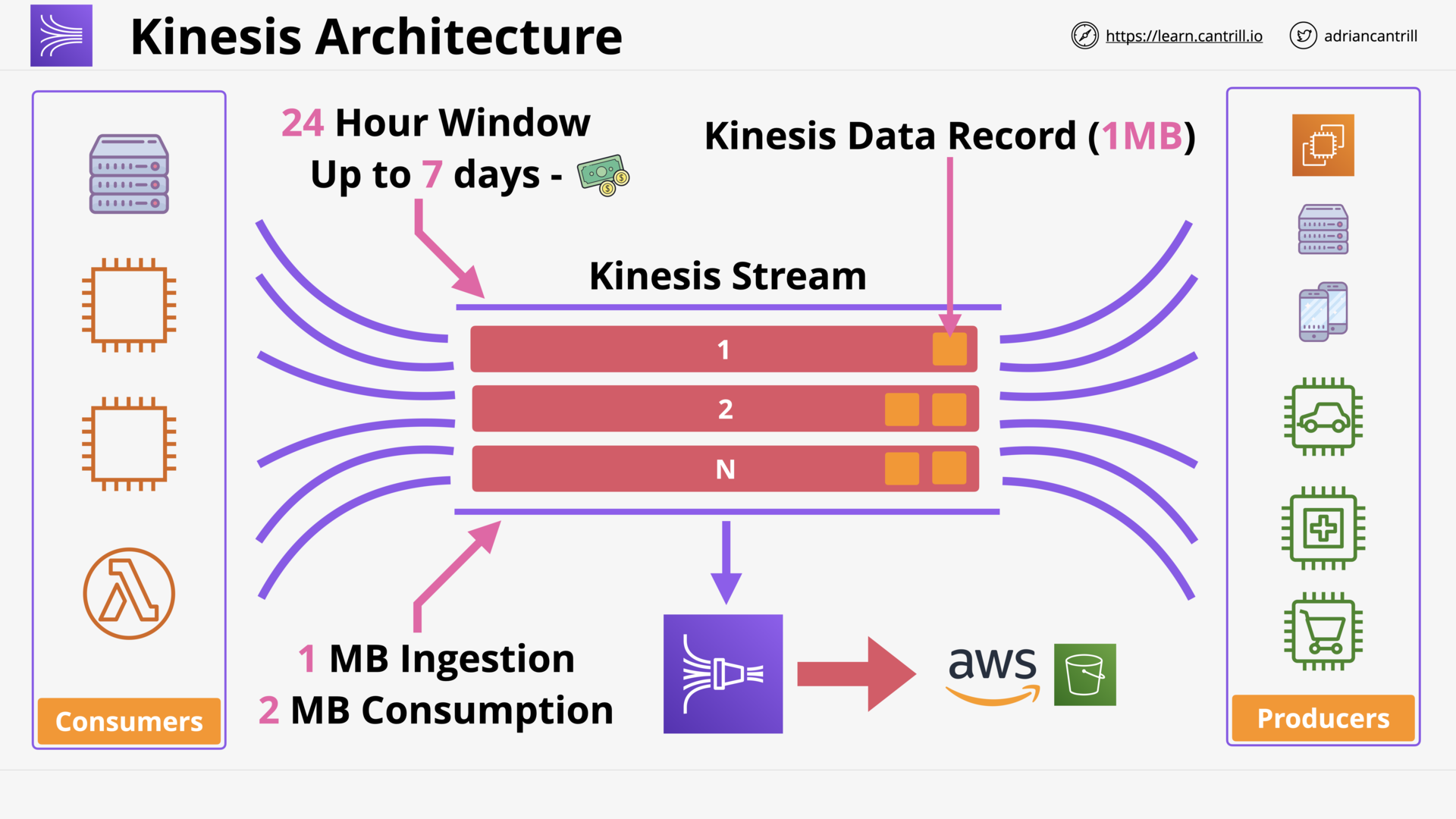 Kinesis - Architecture
Kinesis - Architecture
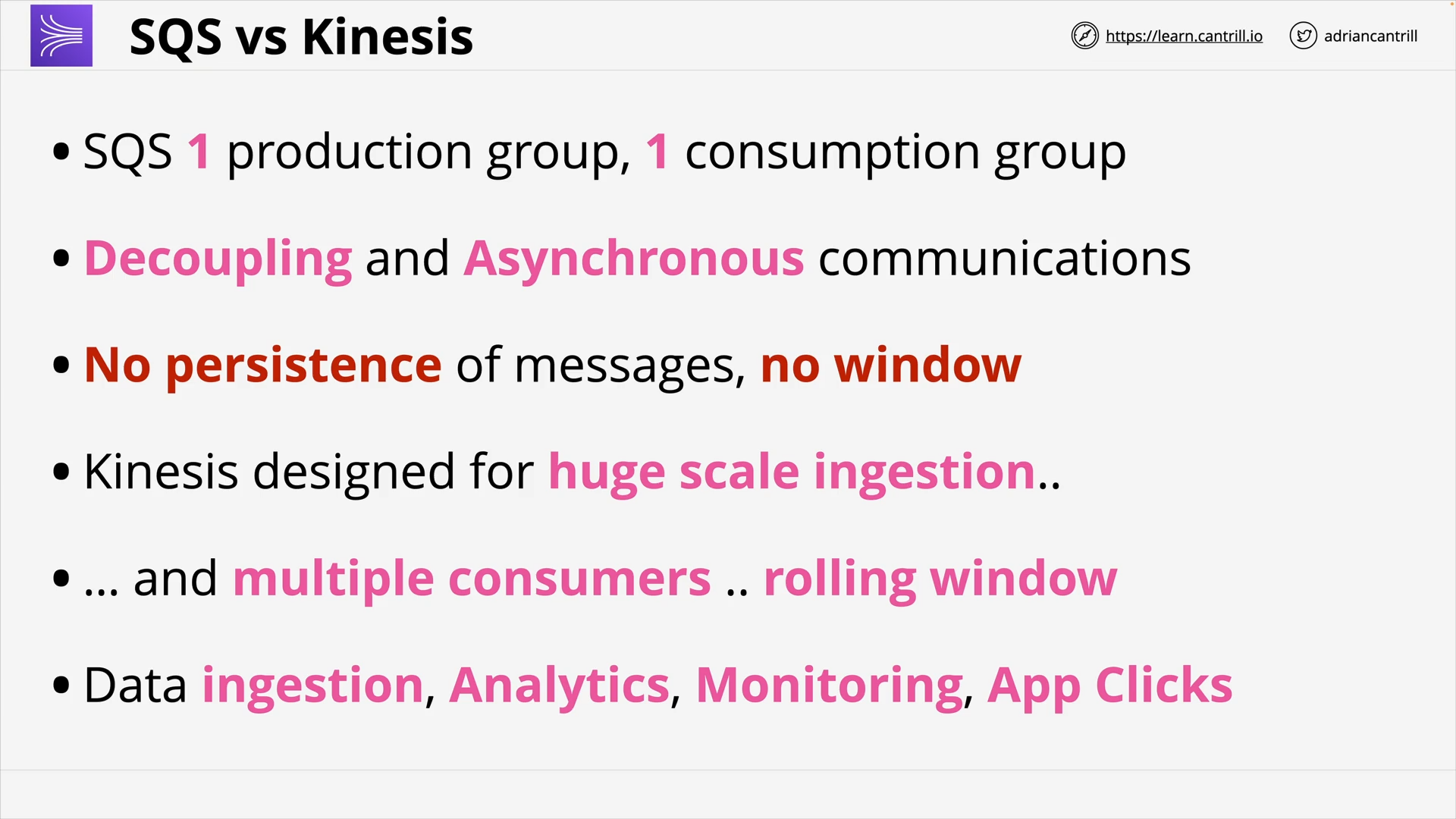 SQS vs Kinesis
SQS vs Kinesis
Kinesis Data Firehose (9:11)
 Kinesis Data Firehose - Overview
Kinesis Data Firehose - Overview
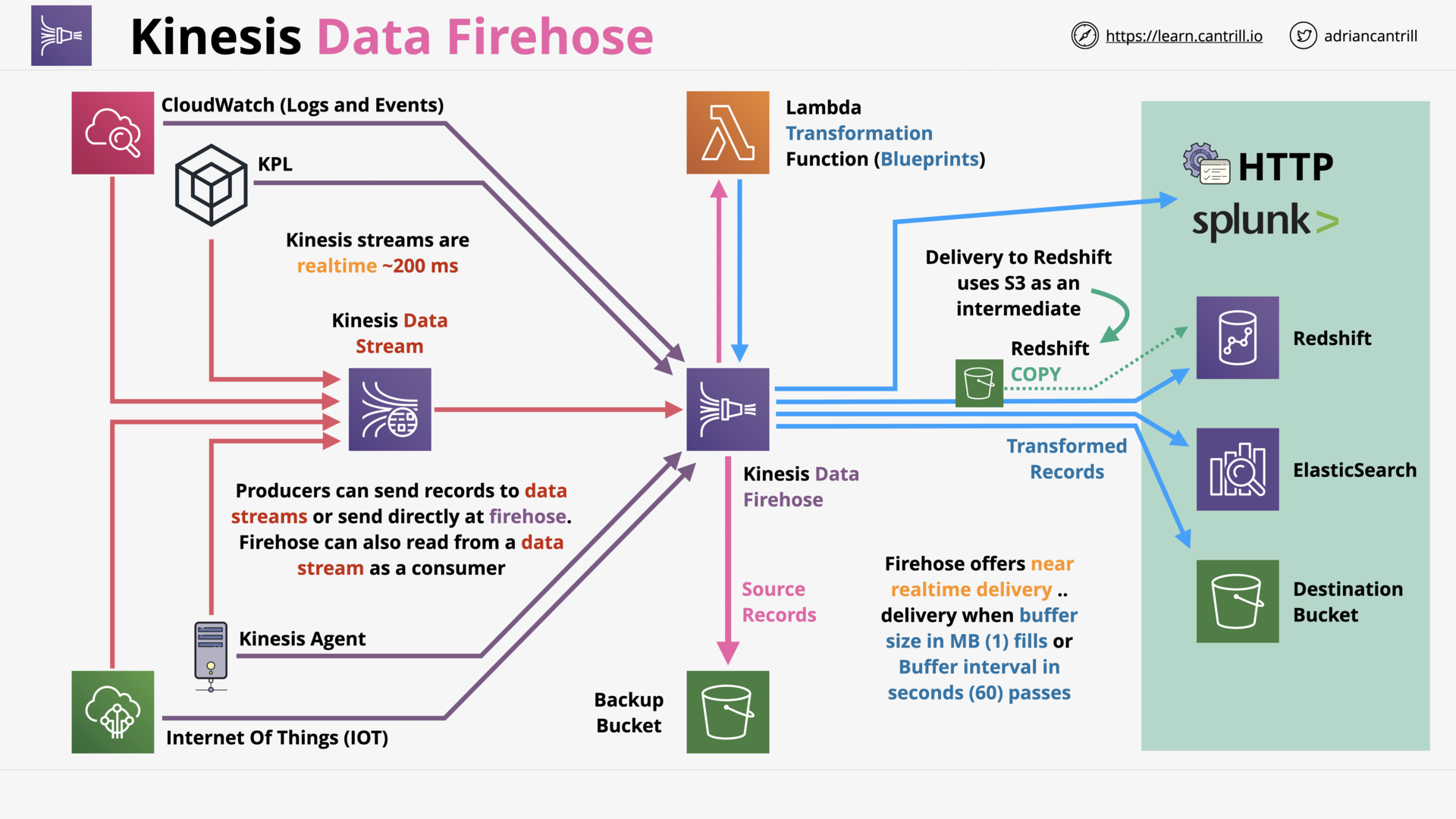 Kinesis Data Firehose - Architecture
Kinesis Data Firehose - Architecture
can kinesis data firehose offer real-time delivery?
No. Although Kinesis Data Firehose can receive data in realtime (200ms), it only delivery data in NEAR realtime.
The messages are delivered when:
- buffer is filled (1MB)
- buffer interval passed (60s)
Kinesis Data Analytics (8:51)
 Kinesis Data Analytics - Overview
Kinesis Data Analytics - Overview
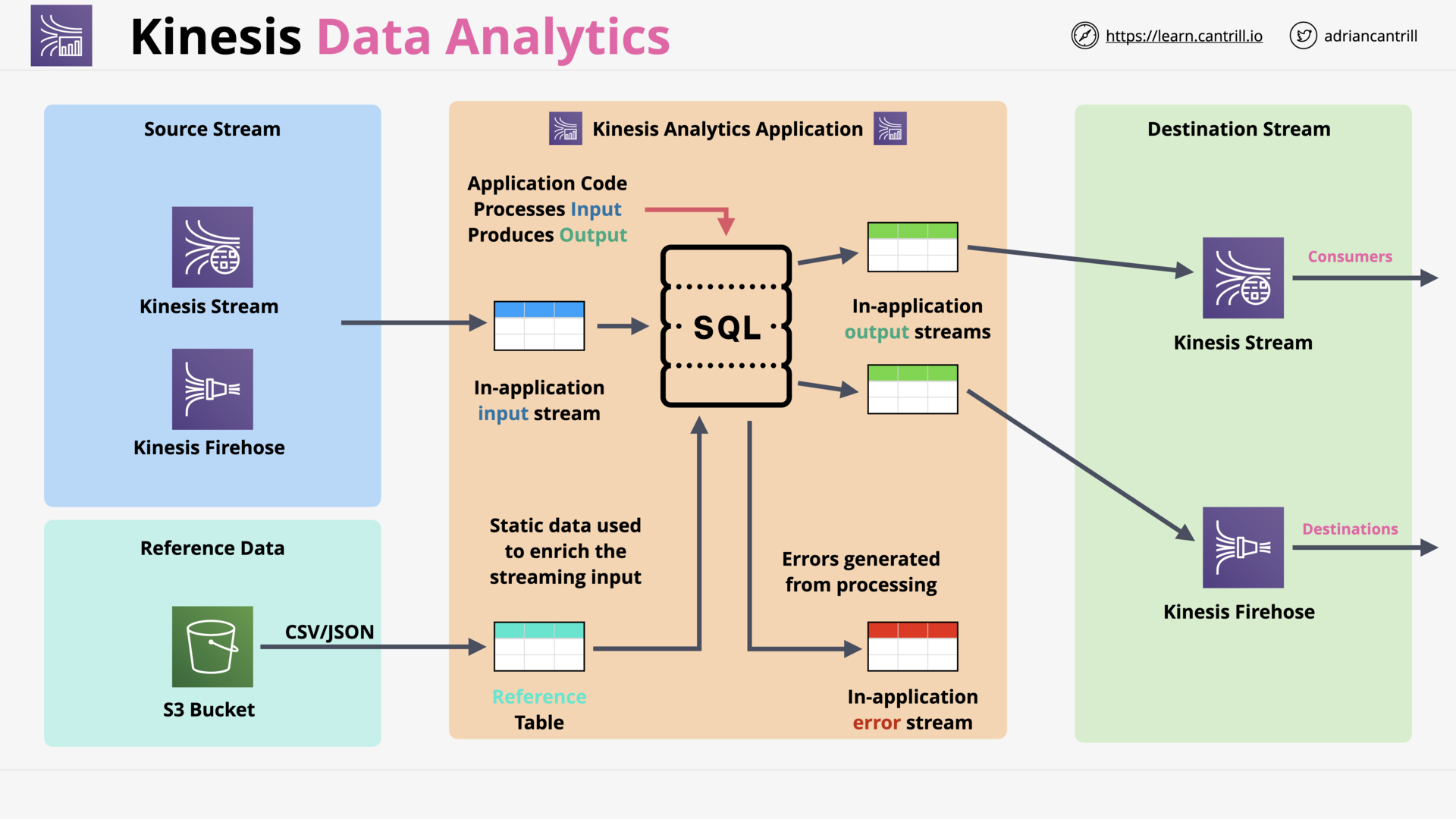 Kinesis Data Analytics - Architecture
Kinesis Data Analytics - Architecture
 Kinesis Data Analytics - When & Where?
Kinesis Data Analytics - When & Where?
Kinesis Video Streams (5:09)
 Kinesis Video Streams - Overview
Kinesis Video Streams - Overview
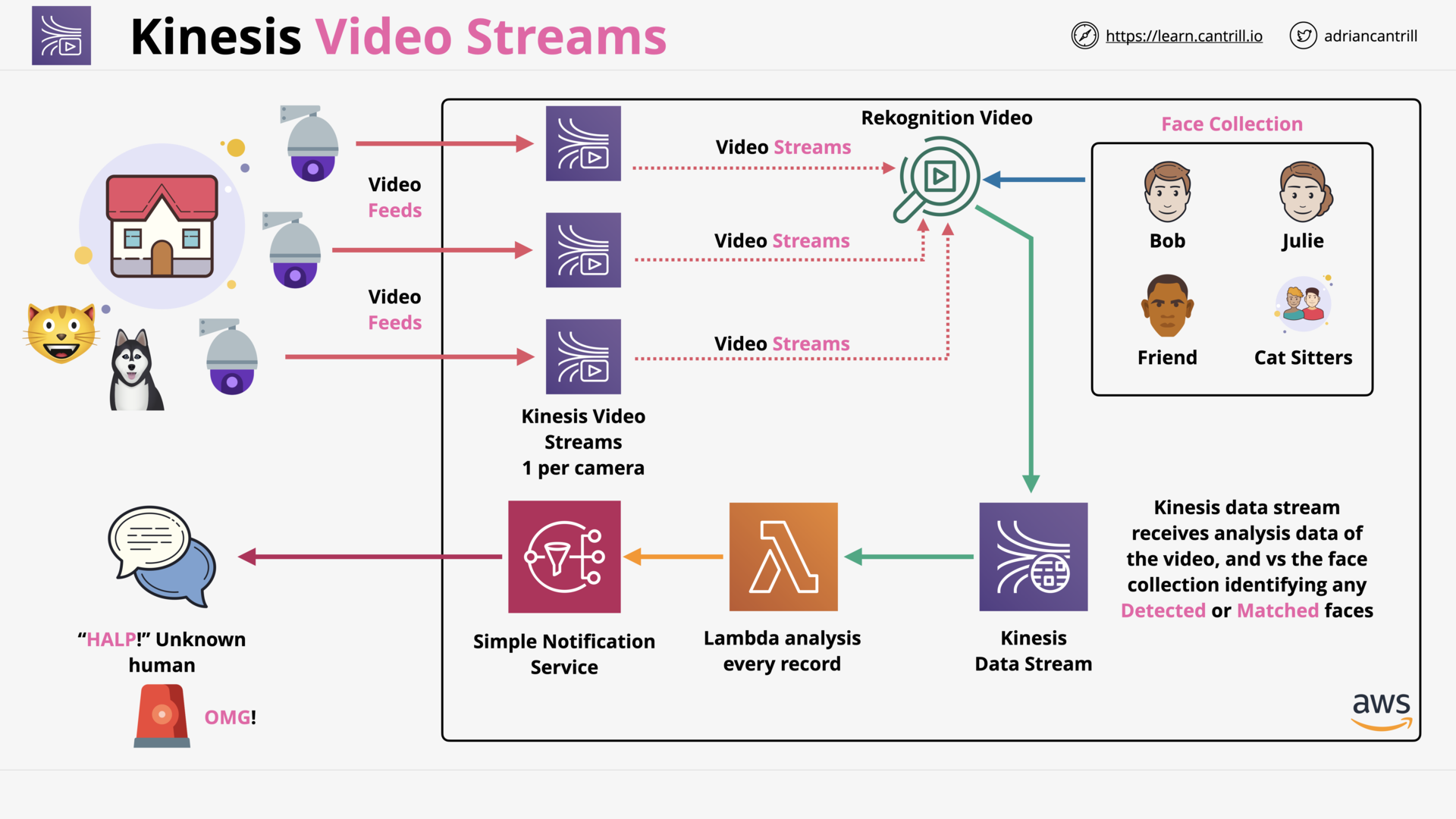 Kinesis Video Streams - Architecture
Kinesis Video Streams - Architecture
Amazon Cognito - User and Identity Pools (14:44)
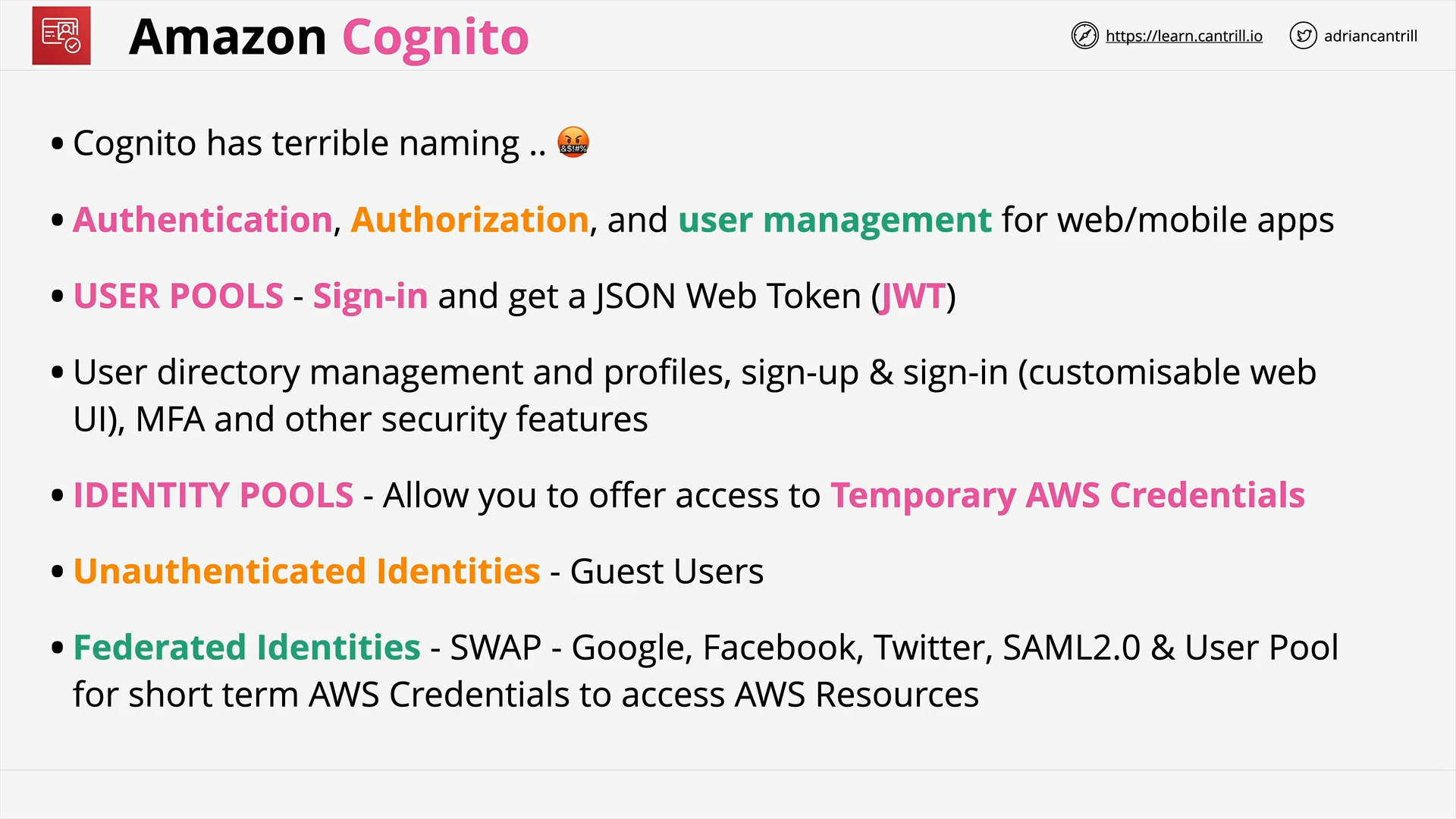 Cognito - Overview
Cognito - Overview
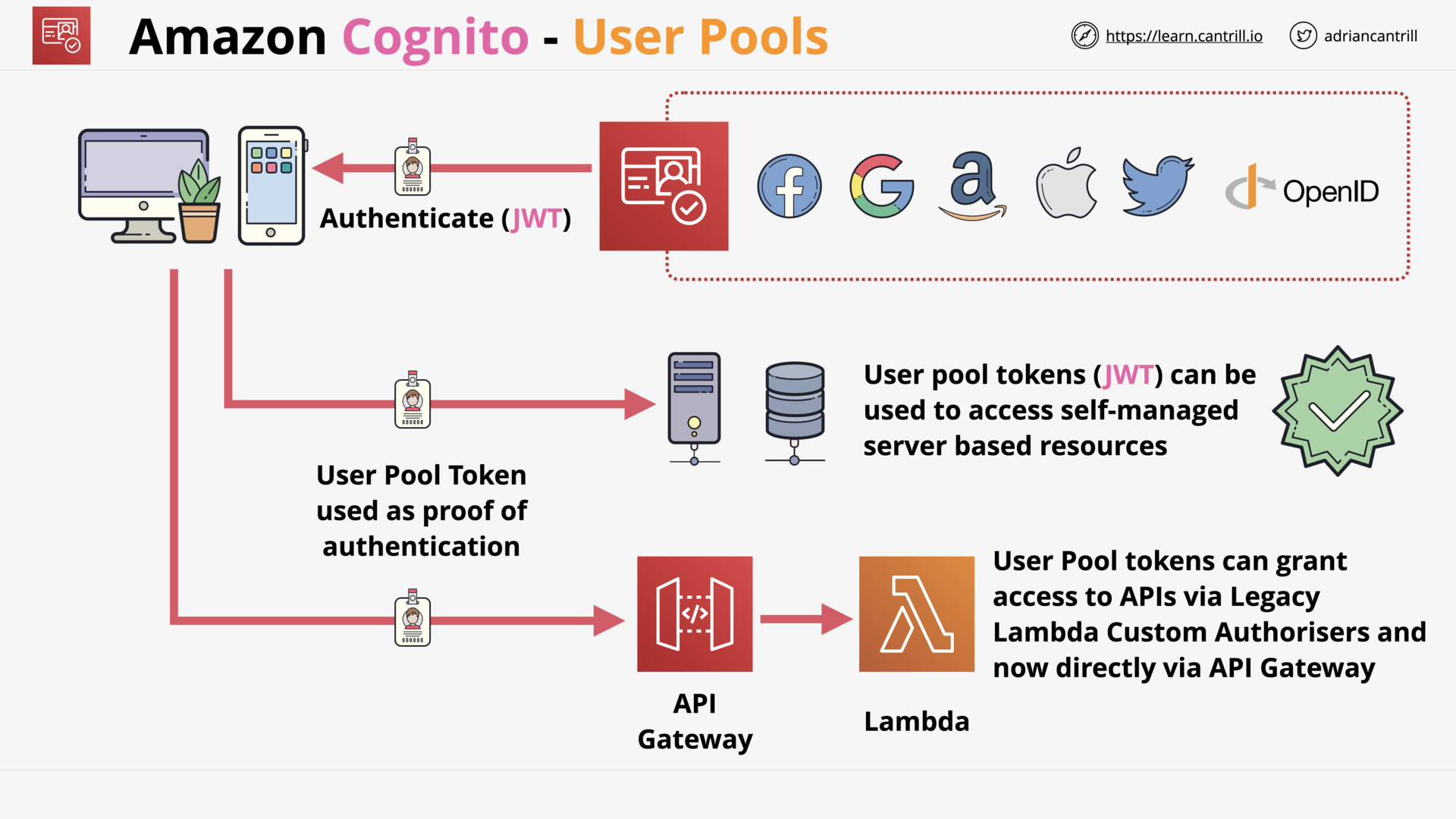 Cognito - User Pool (authenticate & authorize users to your app or API)
Cognito - User Pool (authenticate & authorize users to your app or API)
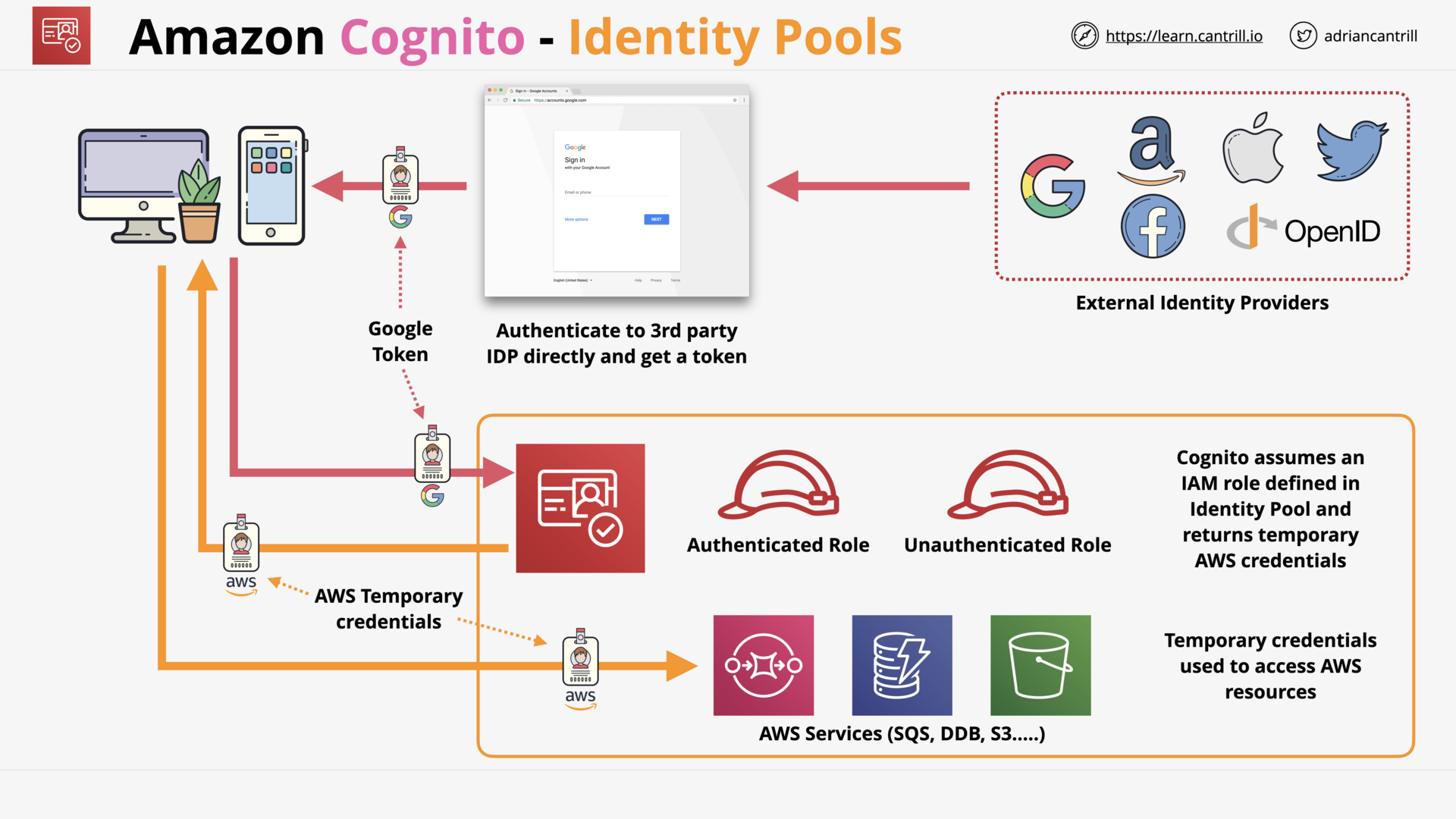 Cognito - Identity Pool (authorize authenticated/anonymous users to access your AWS resources)
Cognito - Identity Pool (authorize authenticated/anonymous users to access your AWS resources)
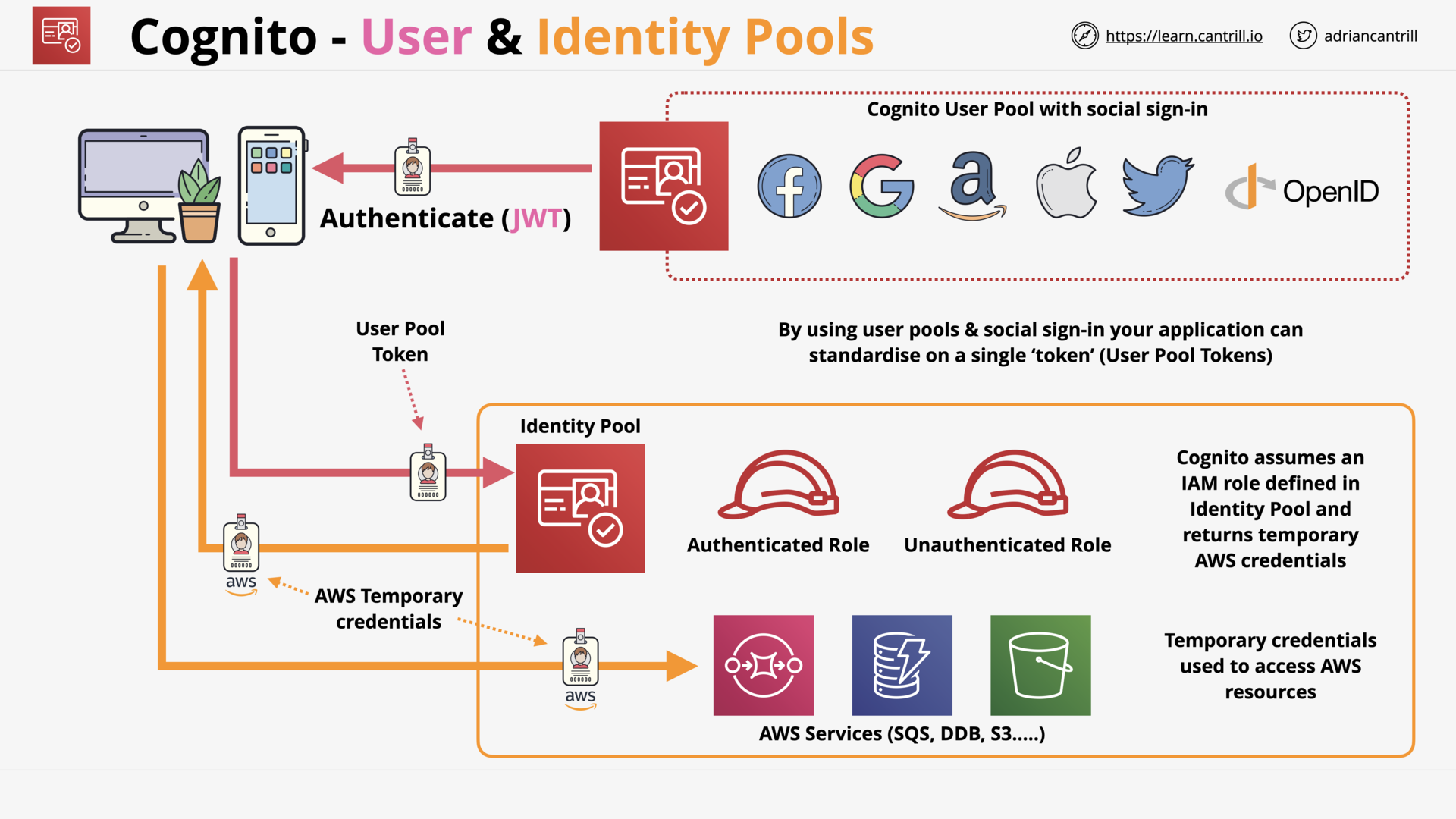 Cognito - User Pool & Identity Pool
Cognito - User Pool & Identity Pool
AWS Glue 101 (6:23)
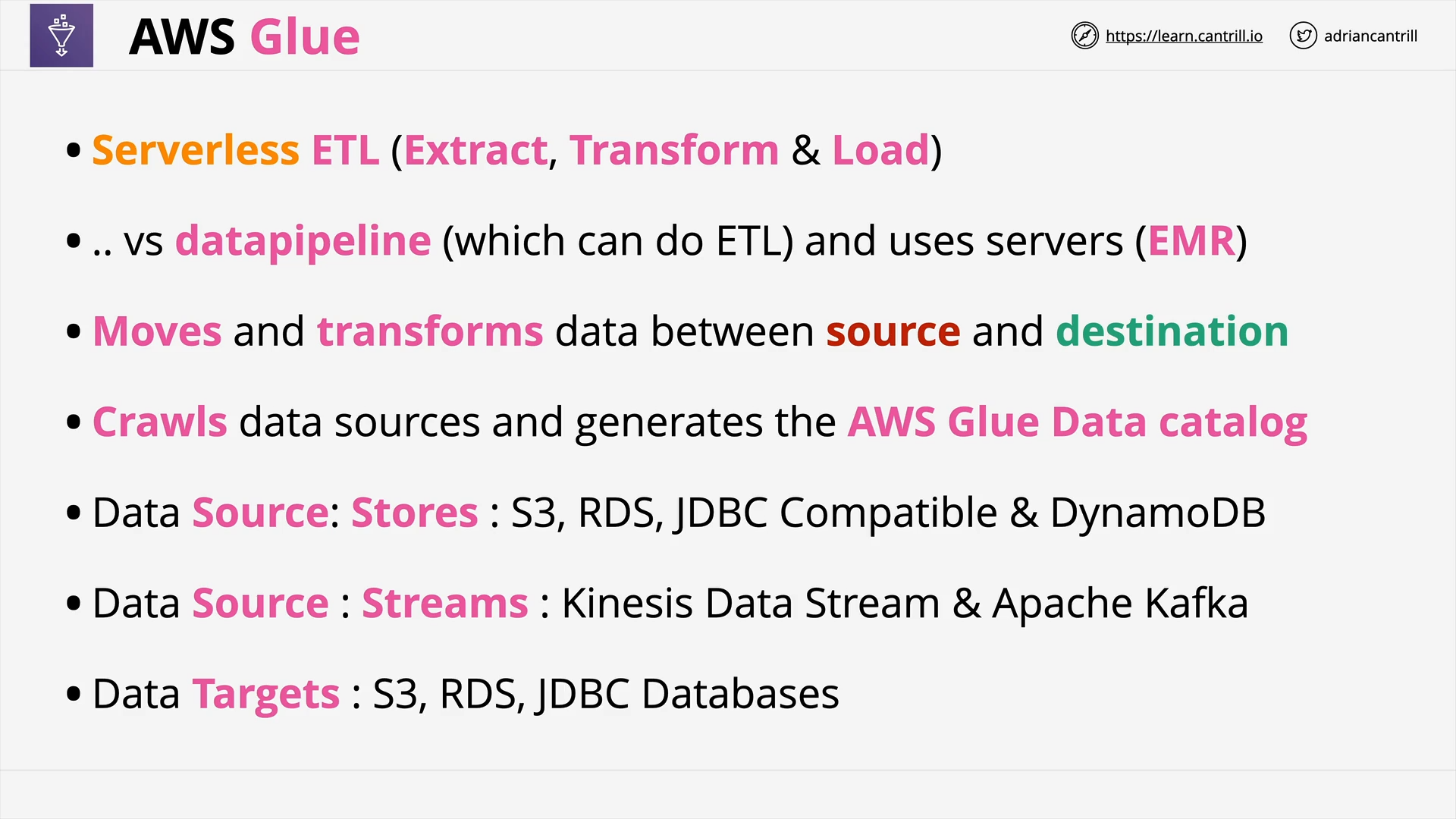 AWS Glue - Serverless ETL
AWS Glue - Serverless ETL
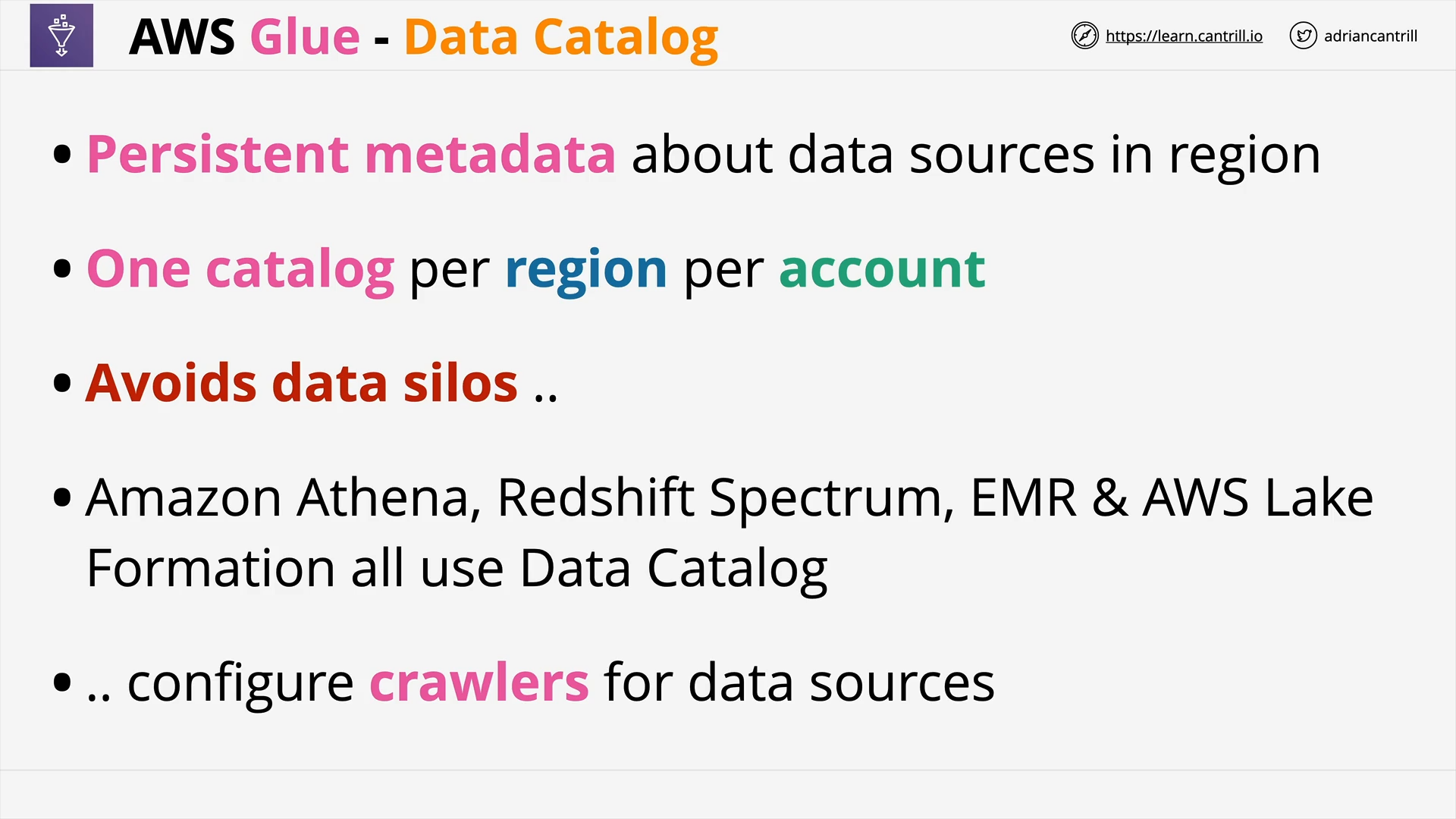 AWS Glue - Data Catalog
AWS Glue - Data Catalog
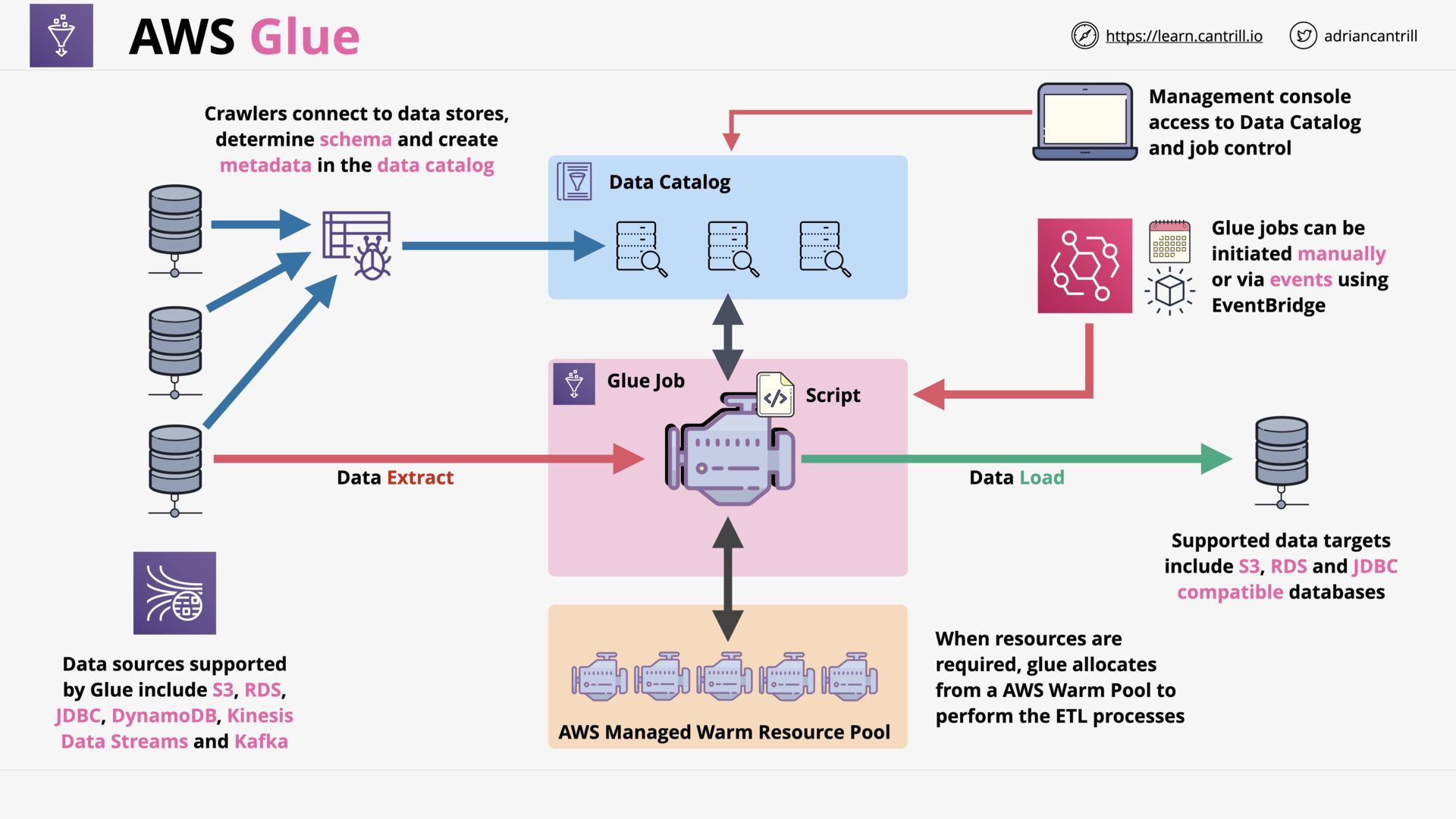 AWS Glue - Architecture
AWS Glue - Architecture
Amazon MQ 101 (8:15)
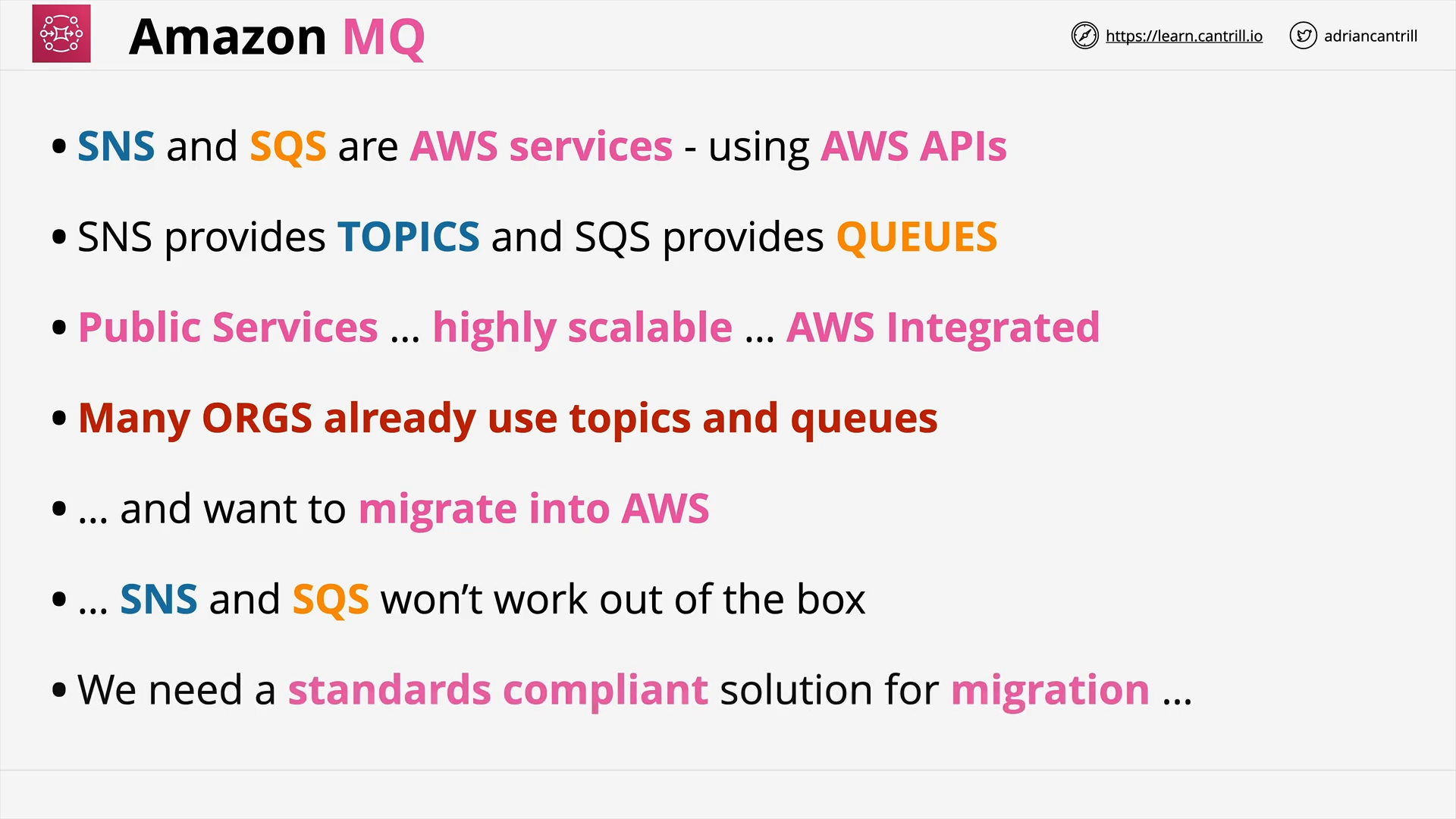 Amazon MQ - Why?
Amazon MQ - Why?
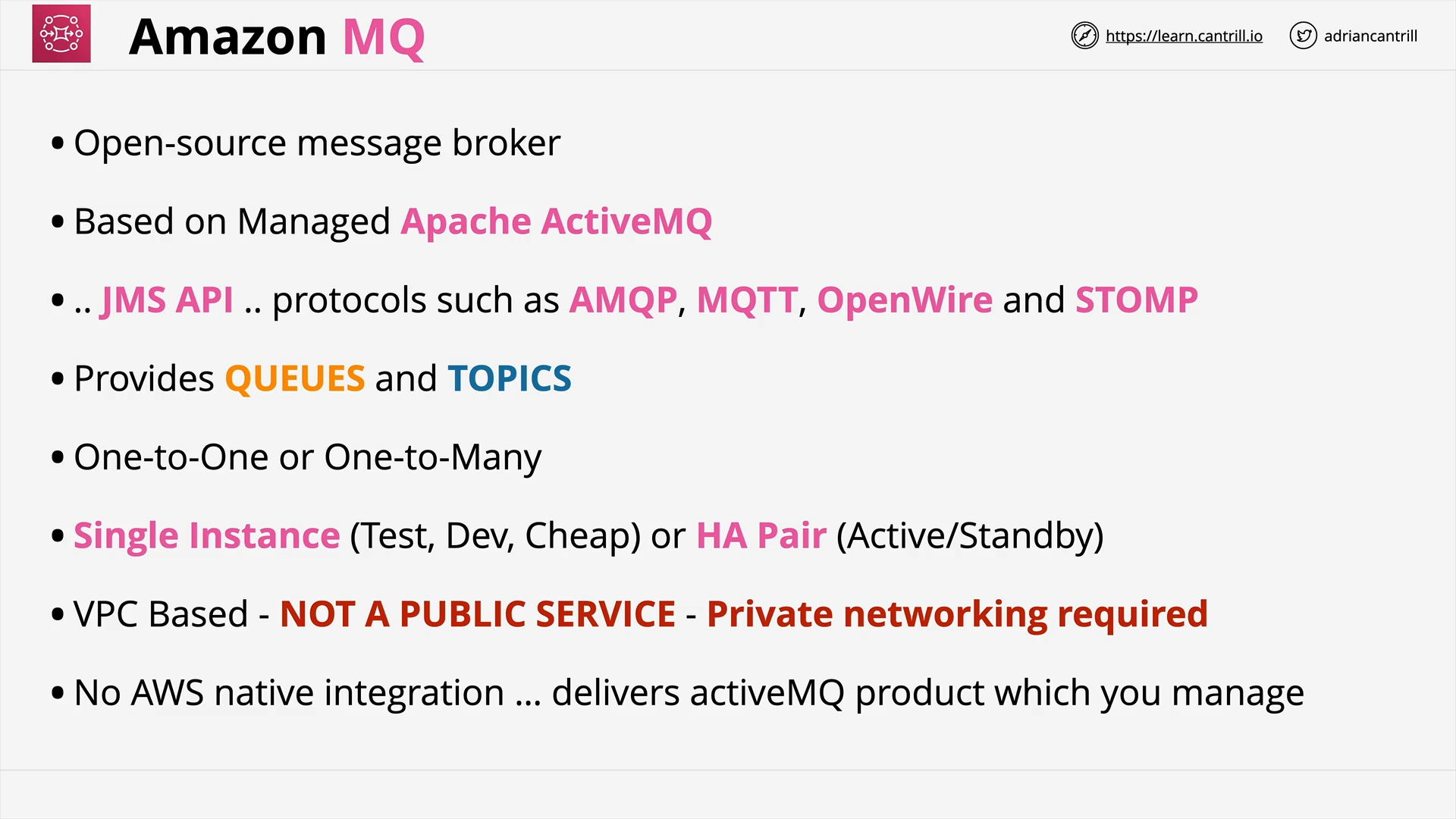 Amazon MQ - What?
Amazon MQ - What?
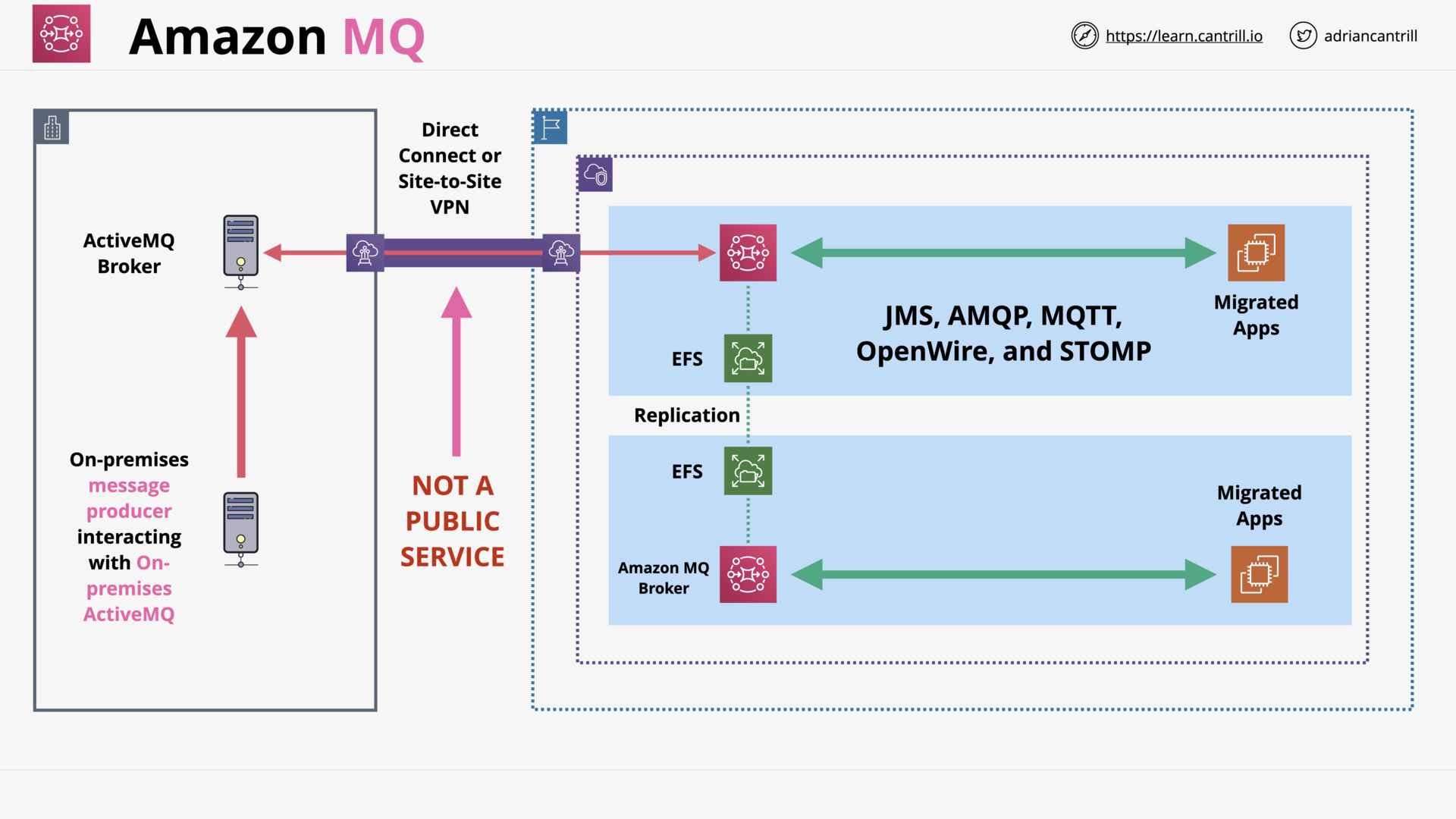 Amazon MQ - How?
Amazon MQ - How?
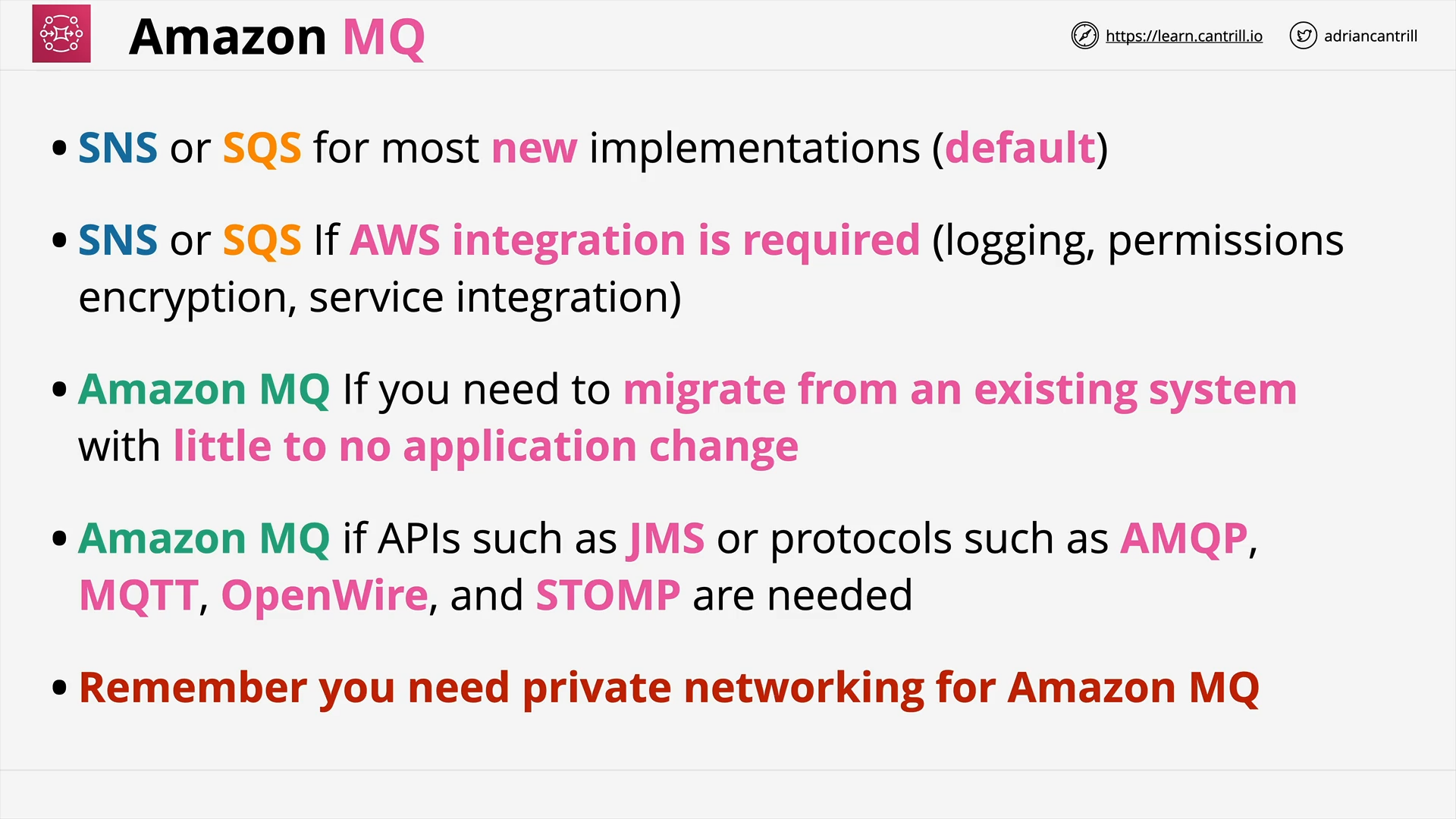 Amazon MQ - When?
Amazon MQ - When?
Amazon AppFlow (3:30)
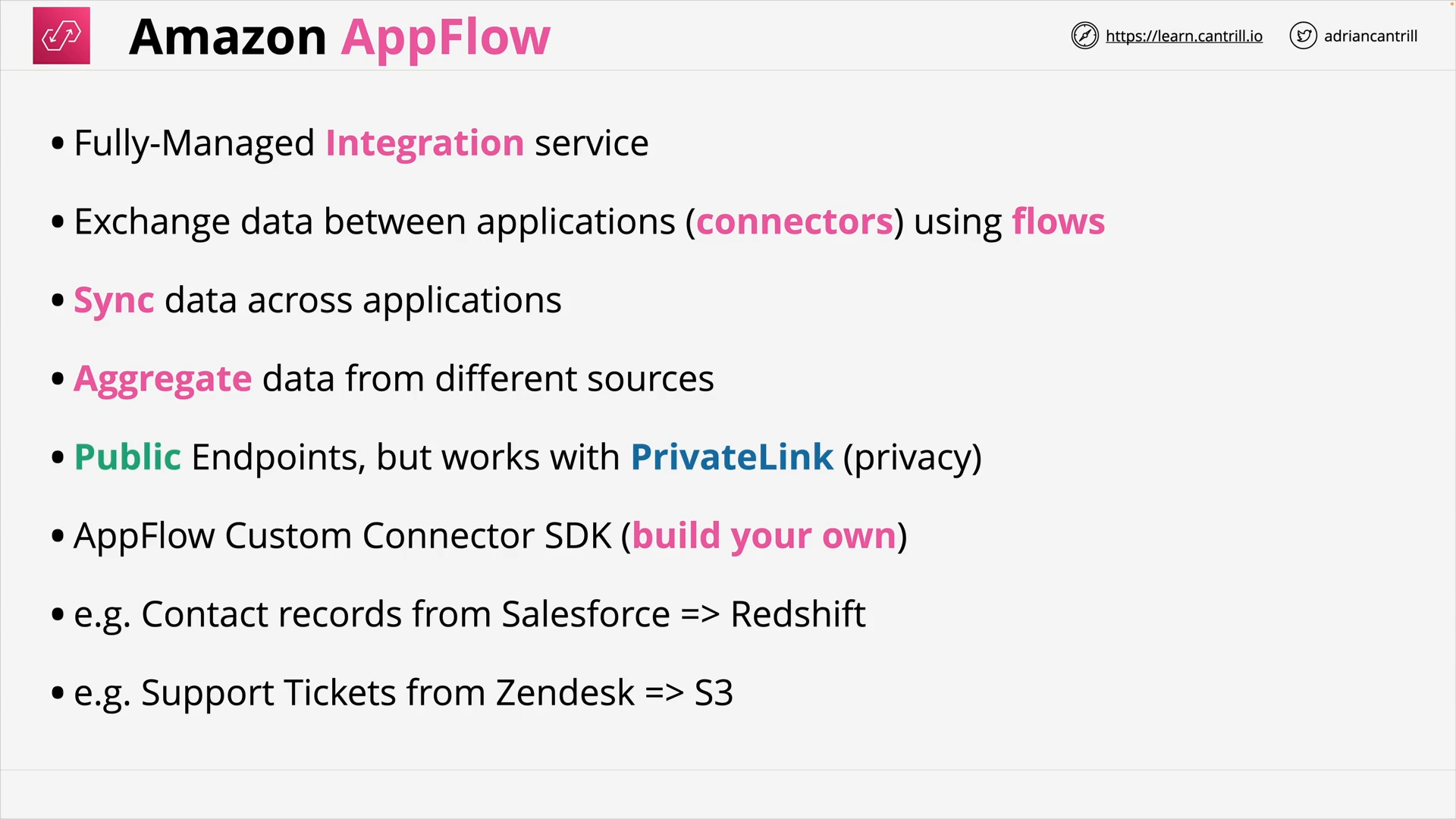 Amazon AppFlow - Overview
Amazon AppFlow - Overview
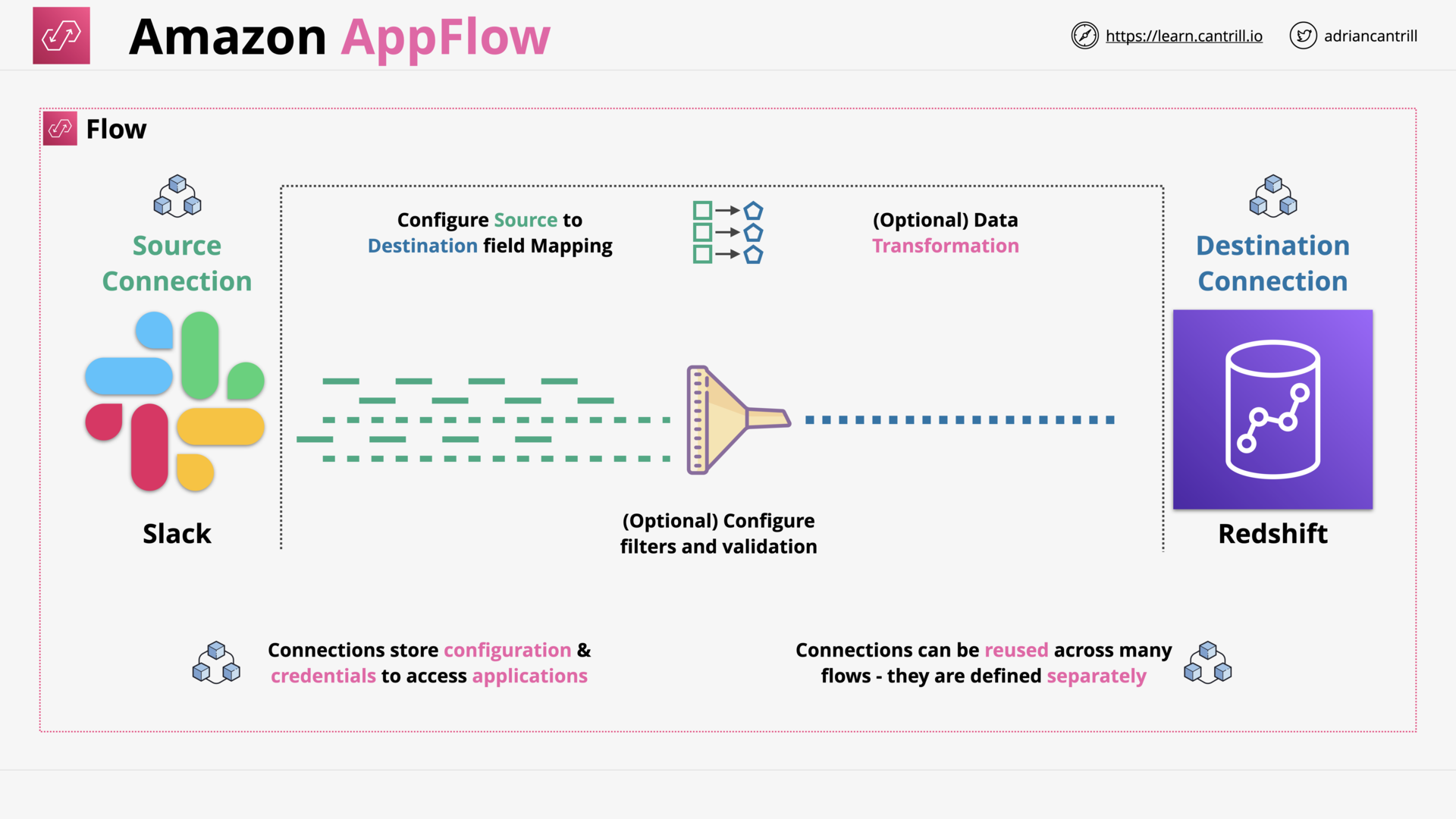 Amazon AppFlow - Architecture
Amazon AppFlow - Architecture
Serverless and App Services Section Quiz
GLOBAL CONTENT DELIVERY AND OPTIMIZATION
CloudFront Architecture (14:56)
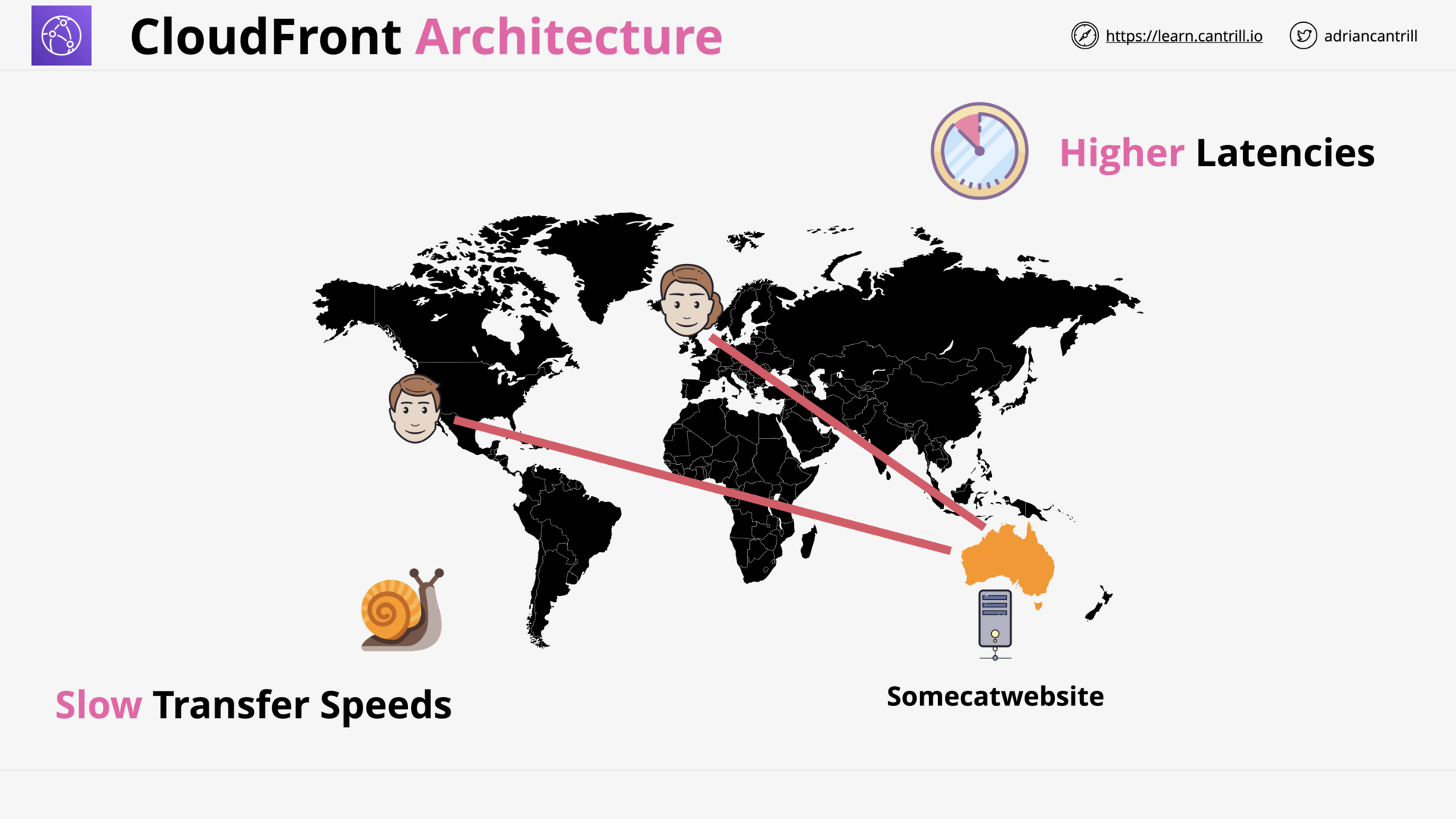 Which problems CloudFront solves?
Which problems CloudFront solves?
 CloudFront - Terms
CloudFront - Terms
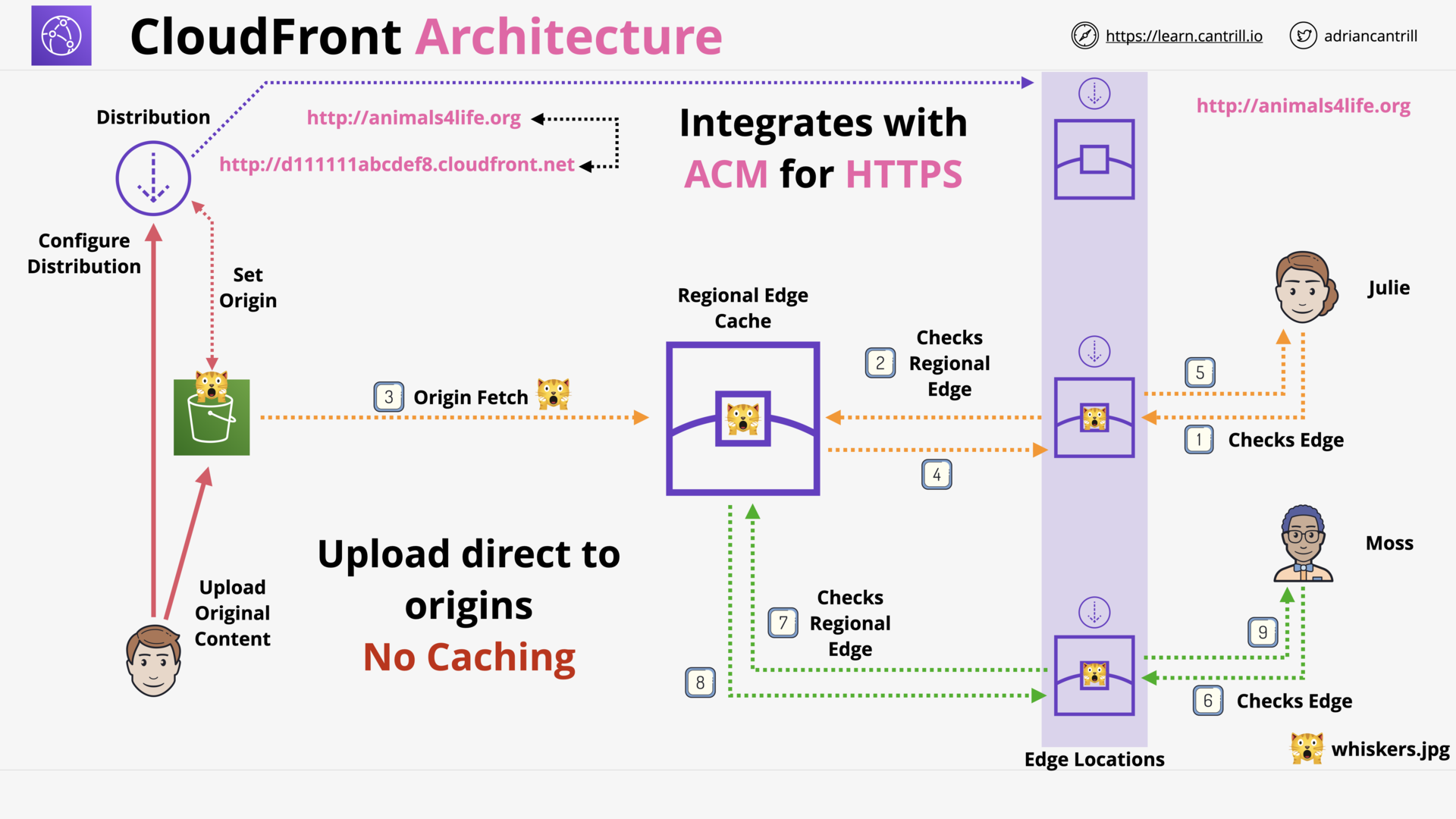 CloudFront - Regional Edge Cache & Edge Location
CloudFront - Regional Edge Cache & Edge Location
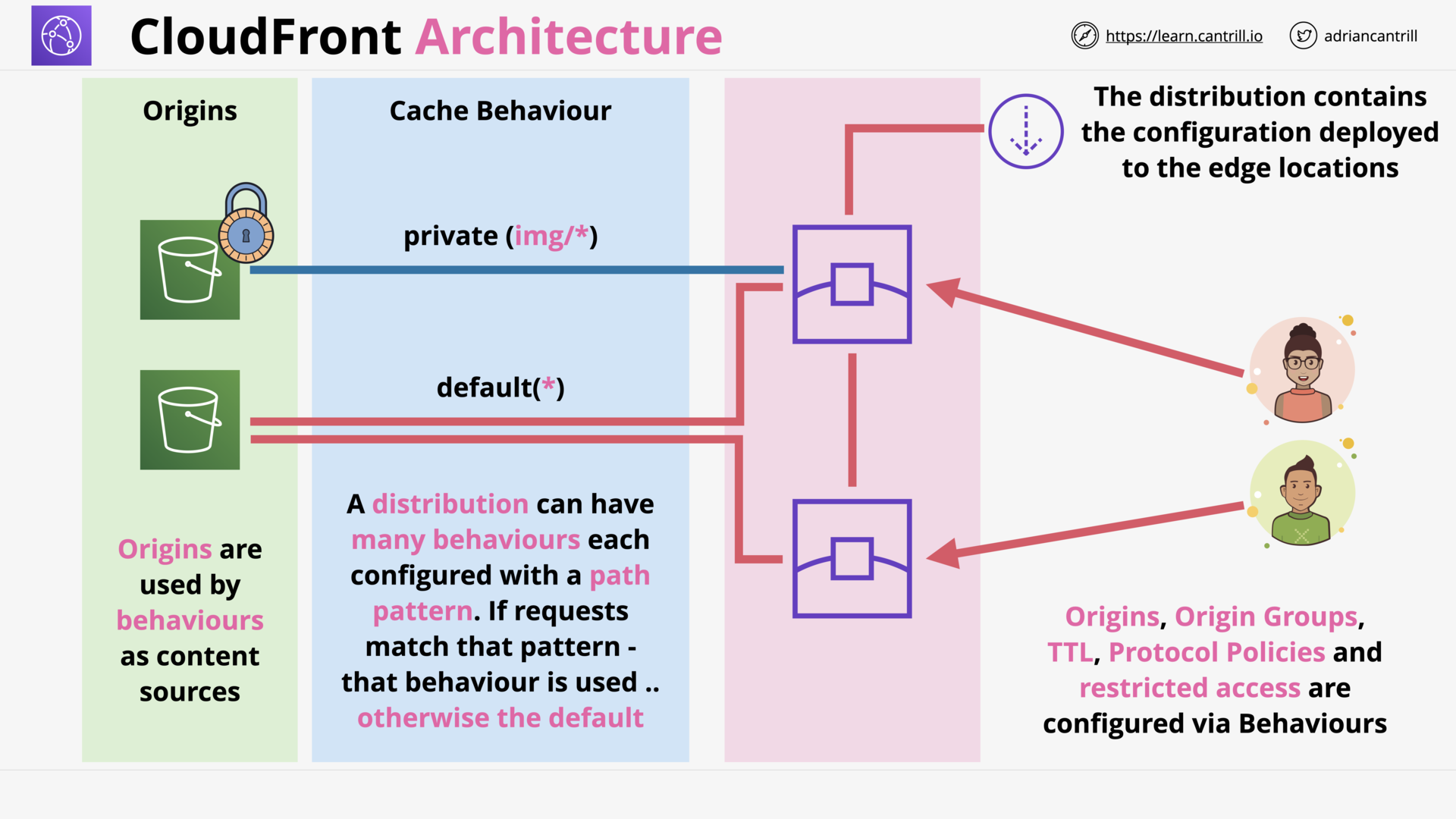 CloudFront - Distribution & Cache Behavior
CloudFront - Distribution & Cache Behavior
CloudFront (CF) - Behaviours (9:21)
CloudFront’s Cache behavior settings
CloudFront - TTL and Invalidations (13:48)
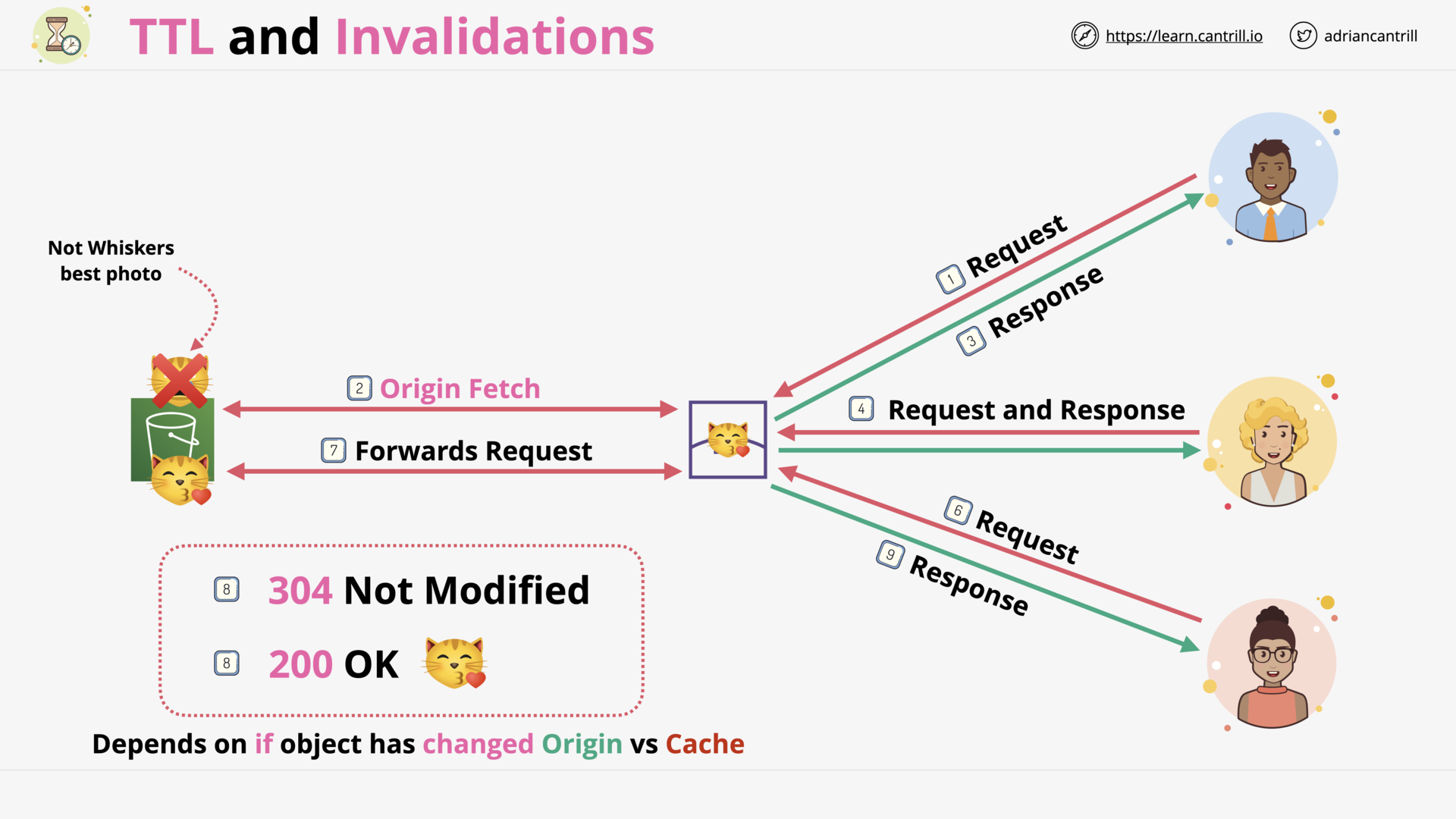 CloudFront - Cache Hit
CloudFront - Cache Hit
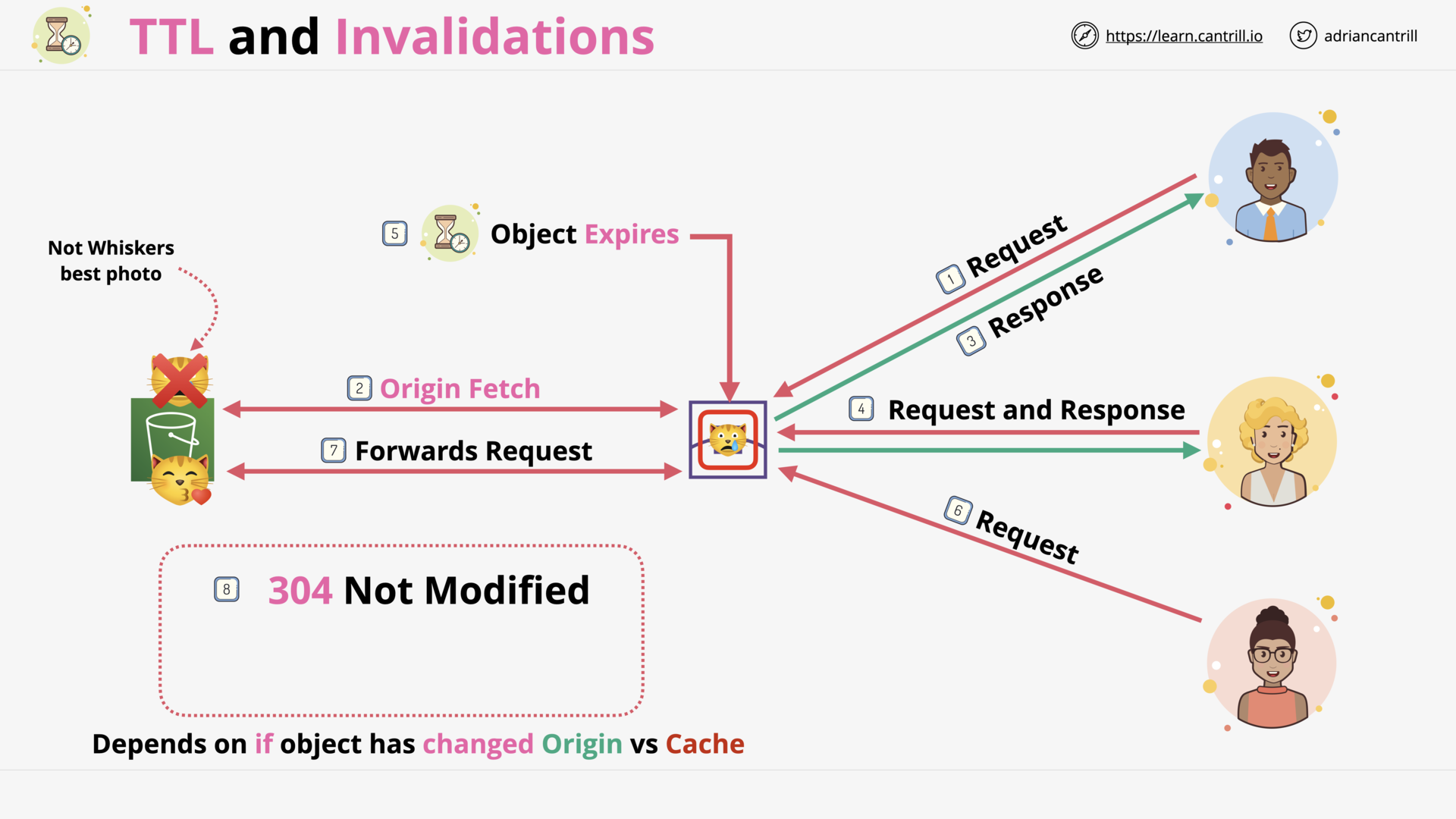 CloudFront - Stale Object
CloudFront - Stale Object
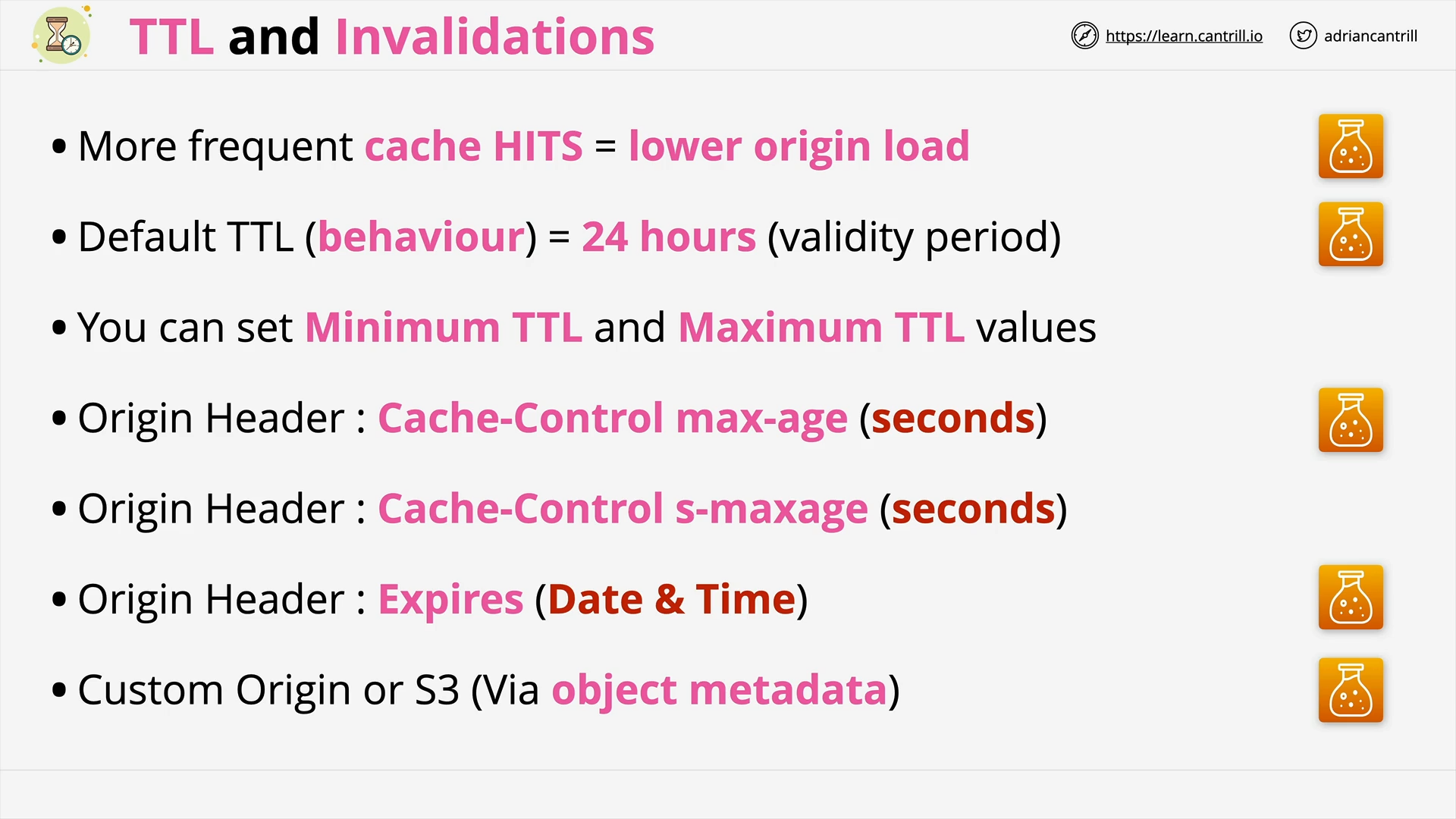 CloudFront - TTL
CloudFront - TTL
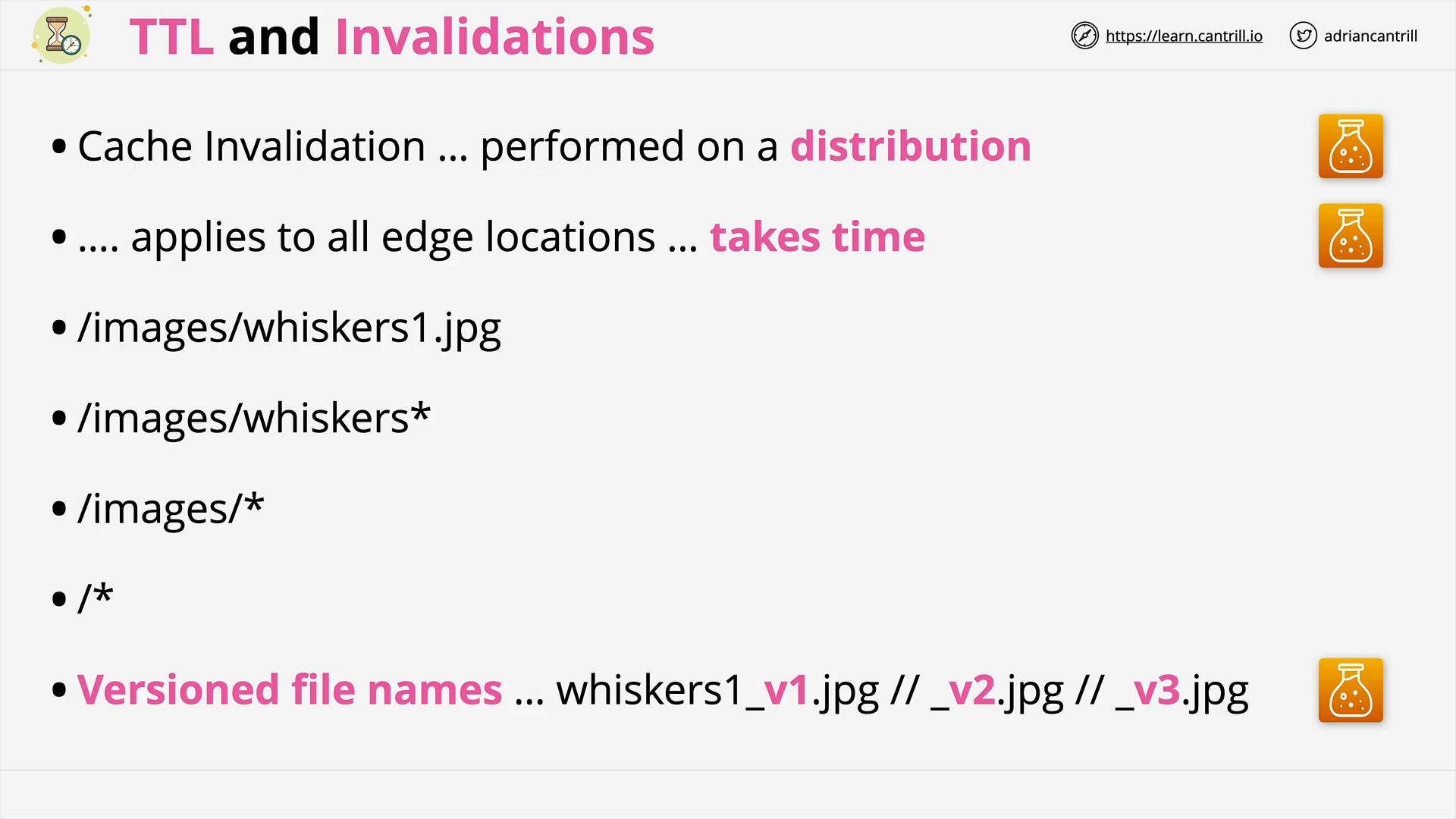 CloudFront - Invalidations
CloudFront - Invalidations
ACM (11:21)
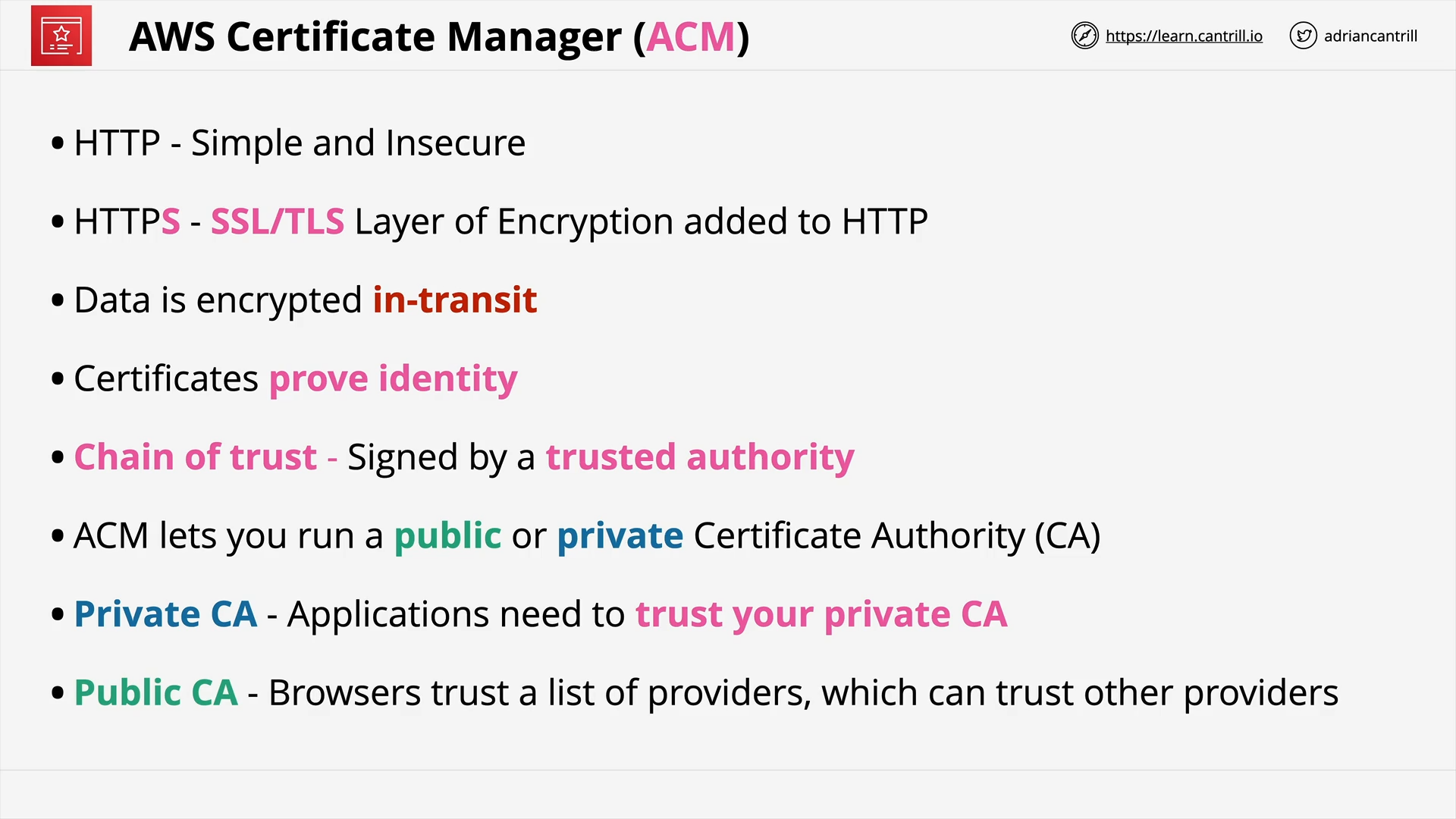 AWS Certificate Manager (ACM) - Overview
AWS Certificate Manager (ACM) - Overview
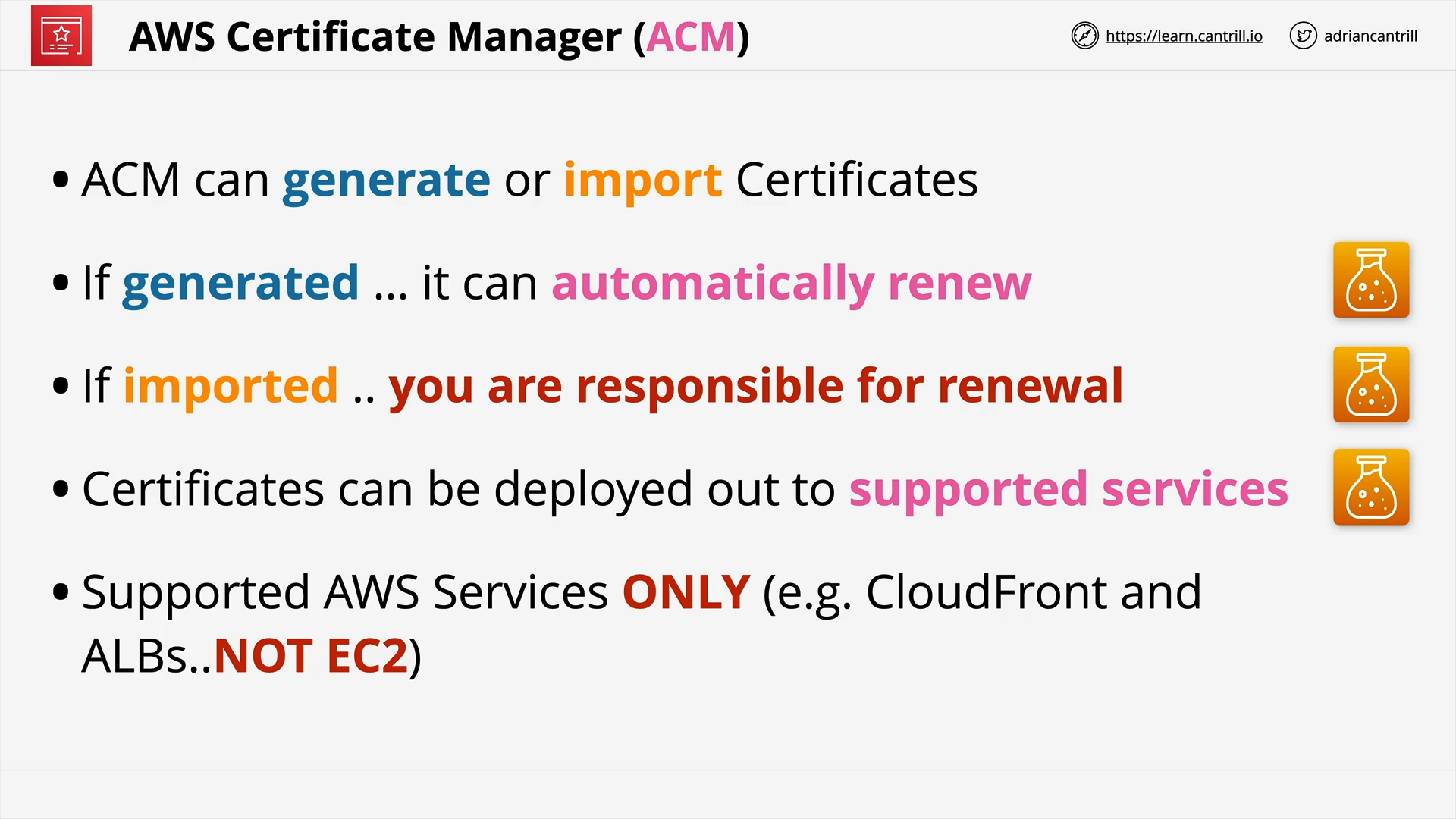 AWS Certificate Manager (ACM) - Certificates
AWS Certificate Manager (ACM) - Certificates
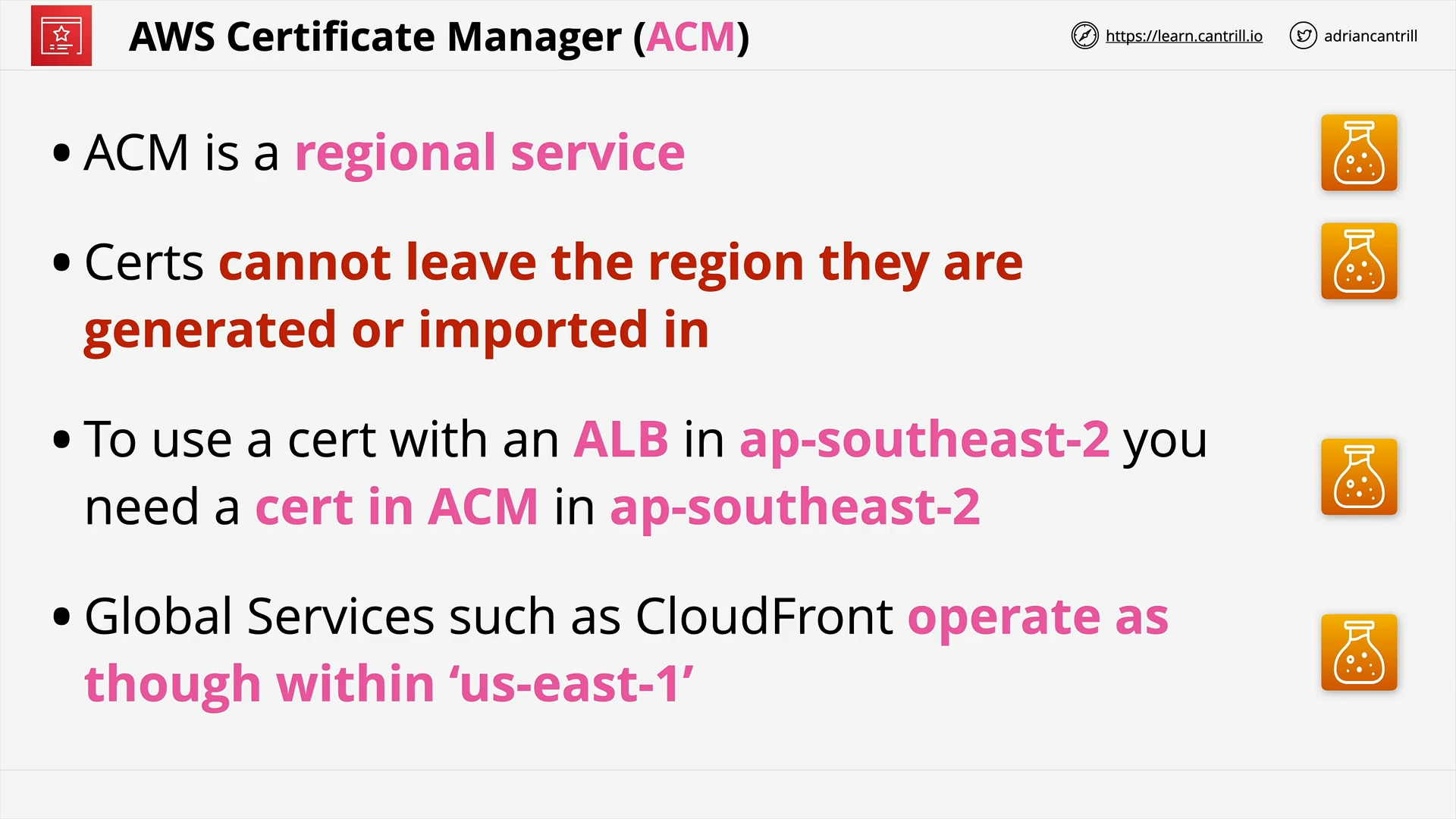 AWS Certificate Manager (ACM) - Regional Service
AWS Certificate Manager (ACM) - Regional Service
what types of services does acm support?
ACM supports: CloudFront, ALB.
ACM does NOT support: EC2.
which region an acm should be in?
The same with AWS resources:
- An ALB in
ap-southeast-1needs a cert in ACM inap-southeast-1. - CloudFront needs a cert in
us-east-1. 👈 Global services are implicitly inus-east-1.
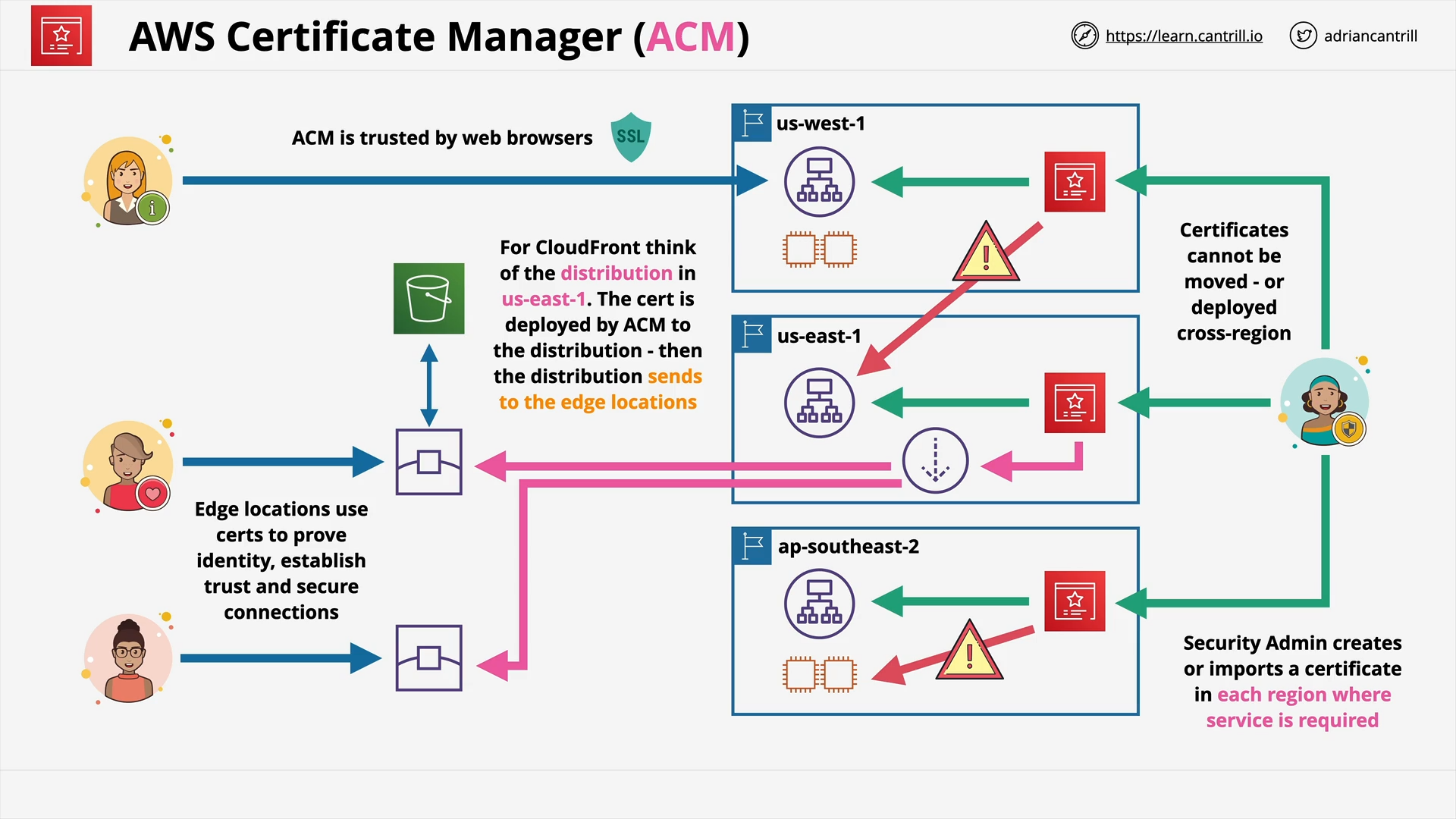 AWS Certificate Manager (ACM) - Architecture
AWS Certificate Manager (ACM) - Architecture
CloudFront and SSL/TLS (14:59)
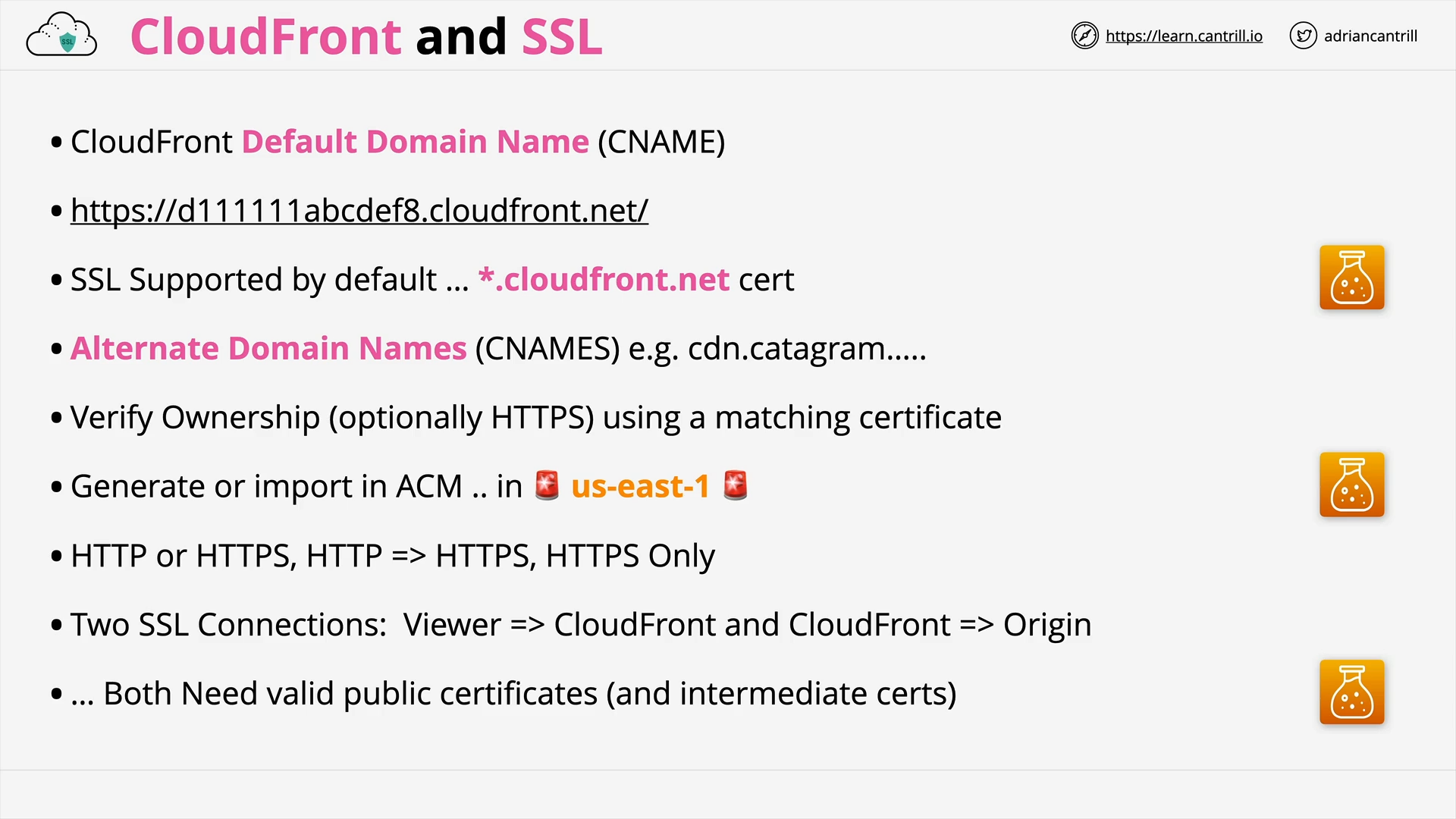 CloudFront & SSL
CloudFront & SSL
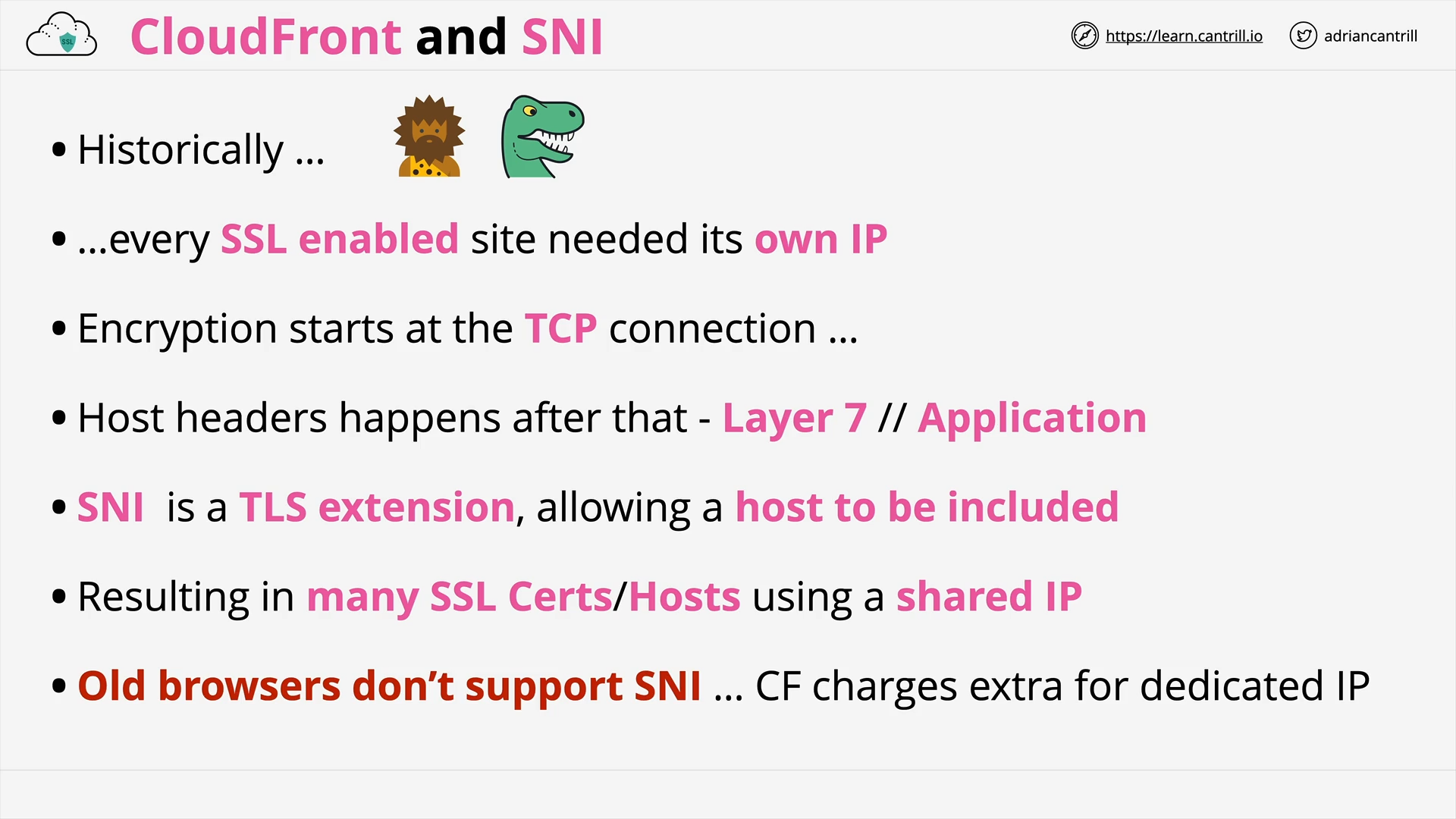 CloudFront & SNI
CloudFront & SNI
what is the problem between old browsers and ssl?
Old browsers don’t support SNI.
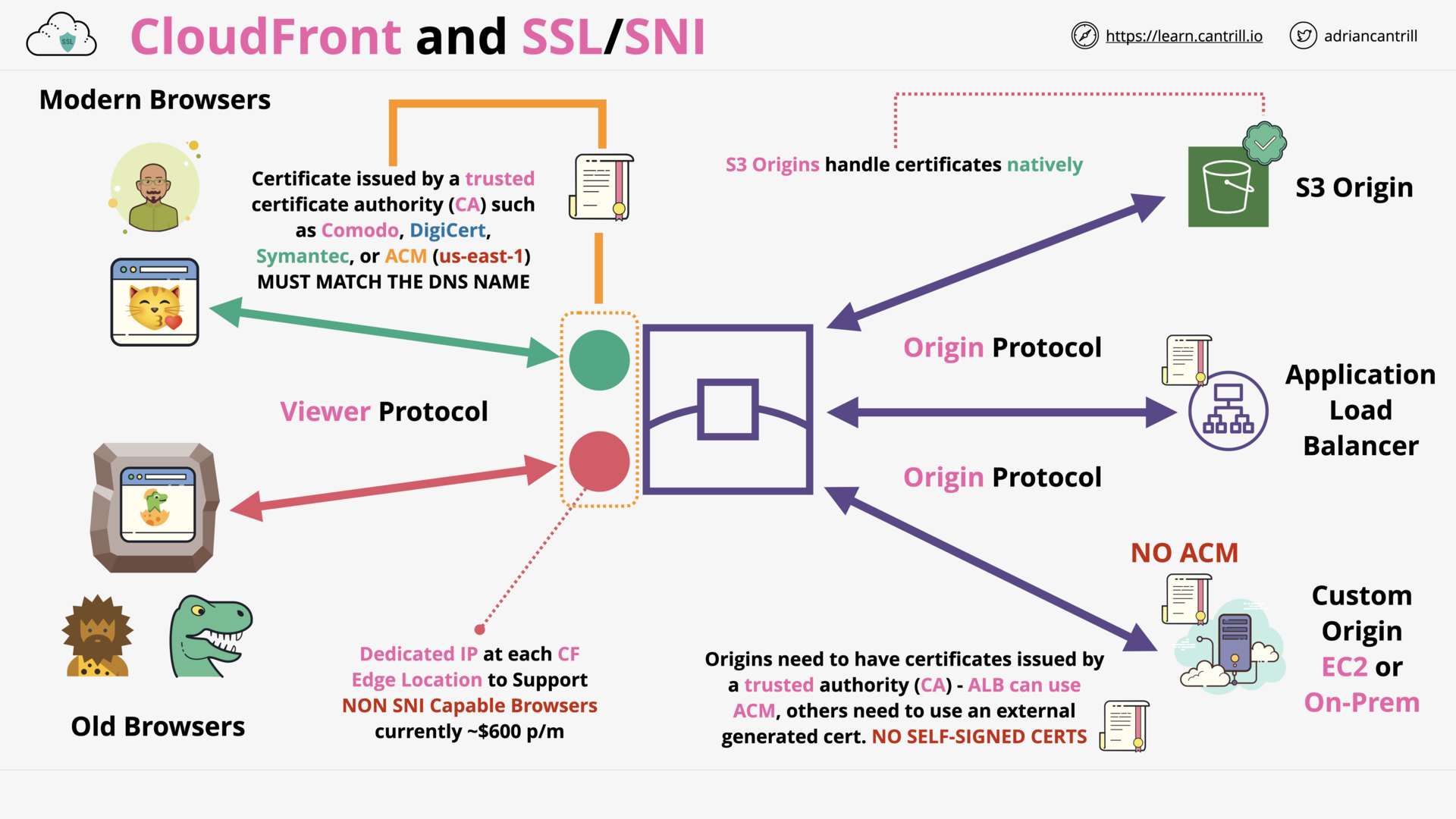 CloudFront & SSL/SNI
CloudFront & SSL/SNI
CloudFront (CF) - Origin Types & Origin Architecture (10:20)
CloudFront distributions supports various origins.
CloudFront Origin Settings
[DEMO] CloudFront (CF) - Adding a CDN to a static Website-PART1 (16:23)
[DEMO] CloudFront (CF) - Adding a CDN to a static Website-PART2 (12:24)
[DEMO] CloudFront (CF) - Adding an Alternate CNAME and SSL (11:12)
CloudFront - Security - OAI & Custom Origins (8:50)
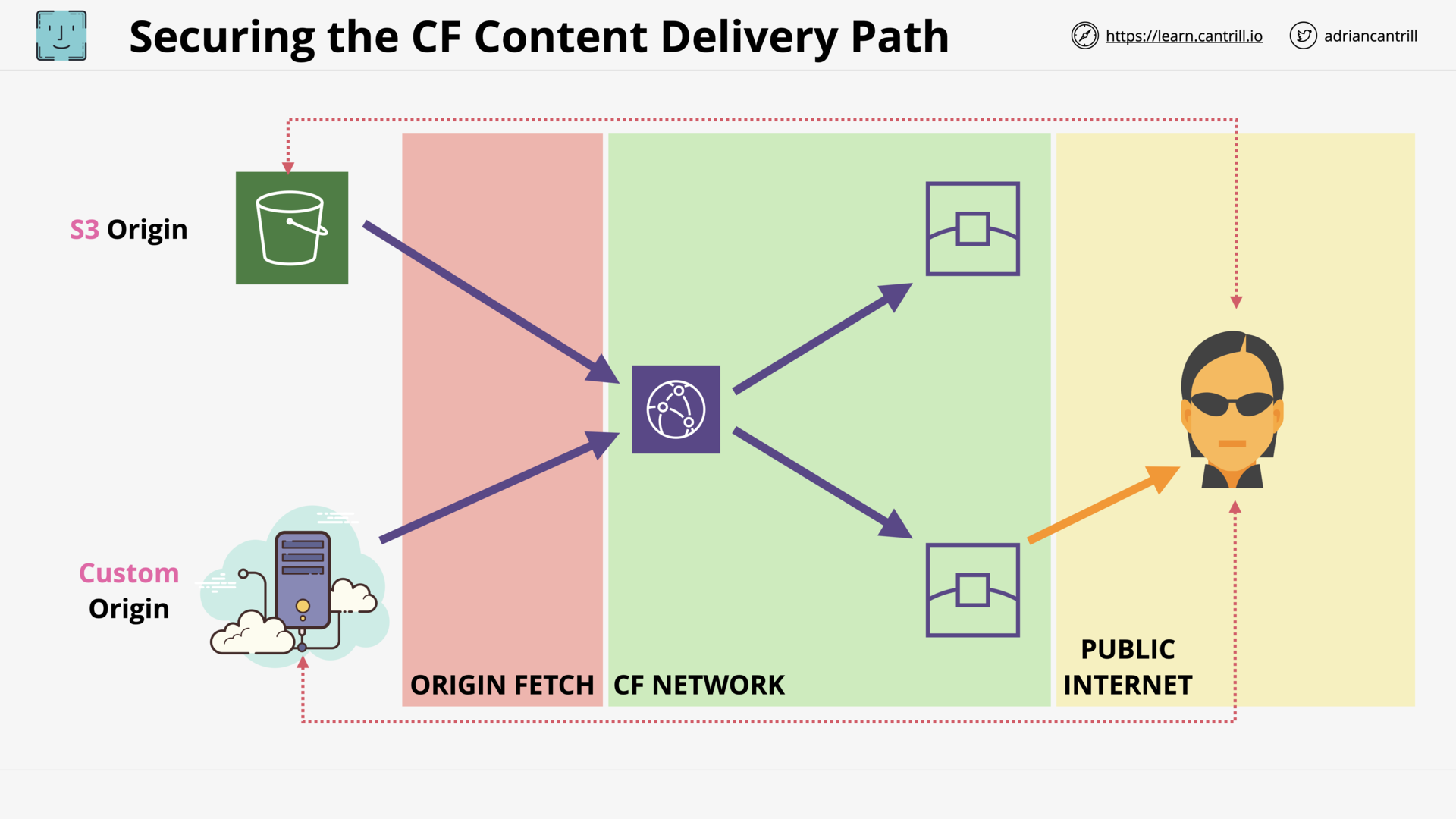 Securing CF Content Delivery Path
Securing CF Content Delivery Path
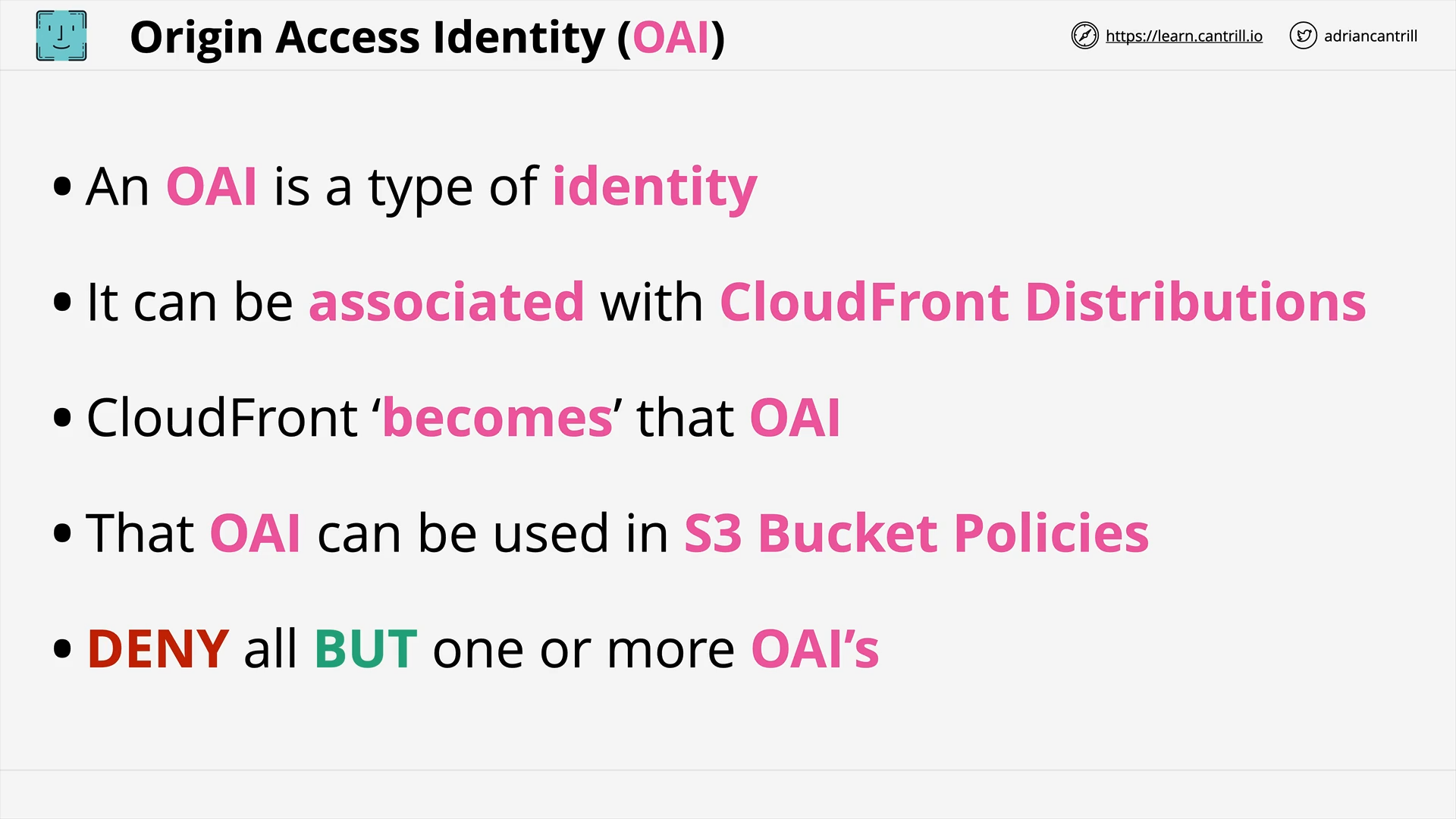 Origin Access Identity (OAI)
Origin Access Identity (OAI)
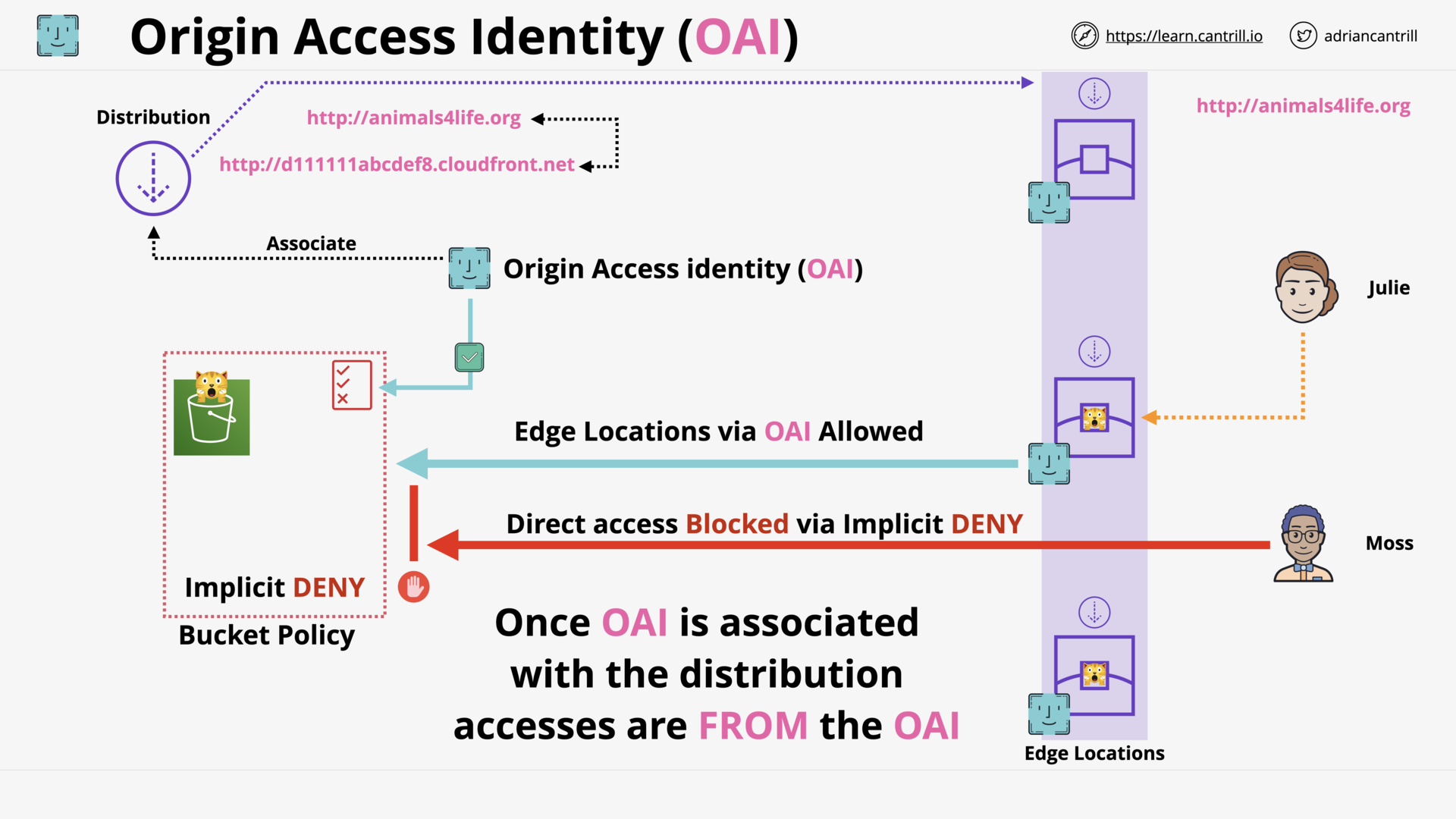 OAI - In Action
OAI - In Action
⚠️ aws has introduced [oac](https://aws.amazon.com/blogs/networking-and-content-delivery/amazon-cloudfront-introduces-origin-access-control-oac/) to replace oai.
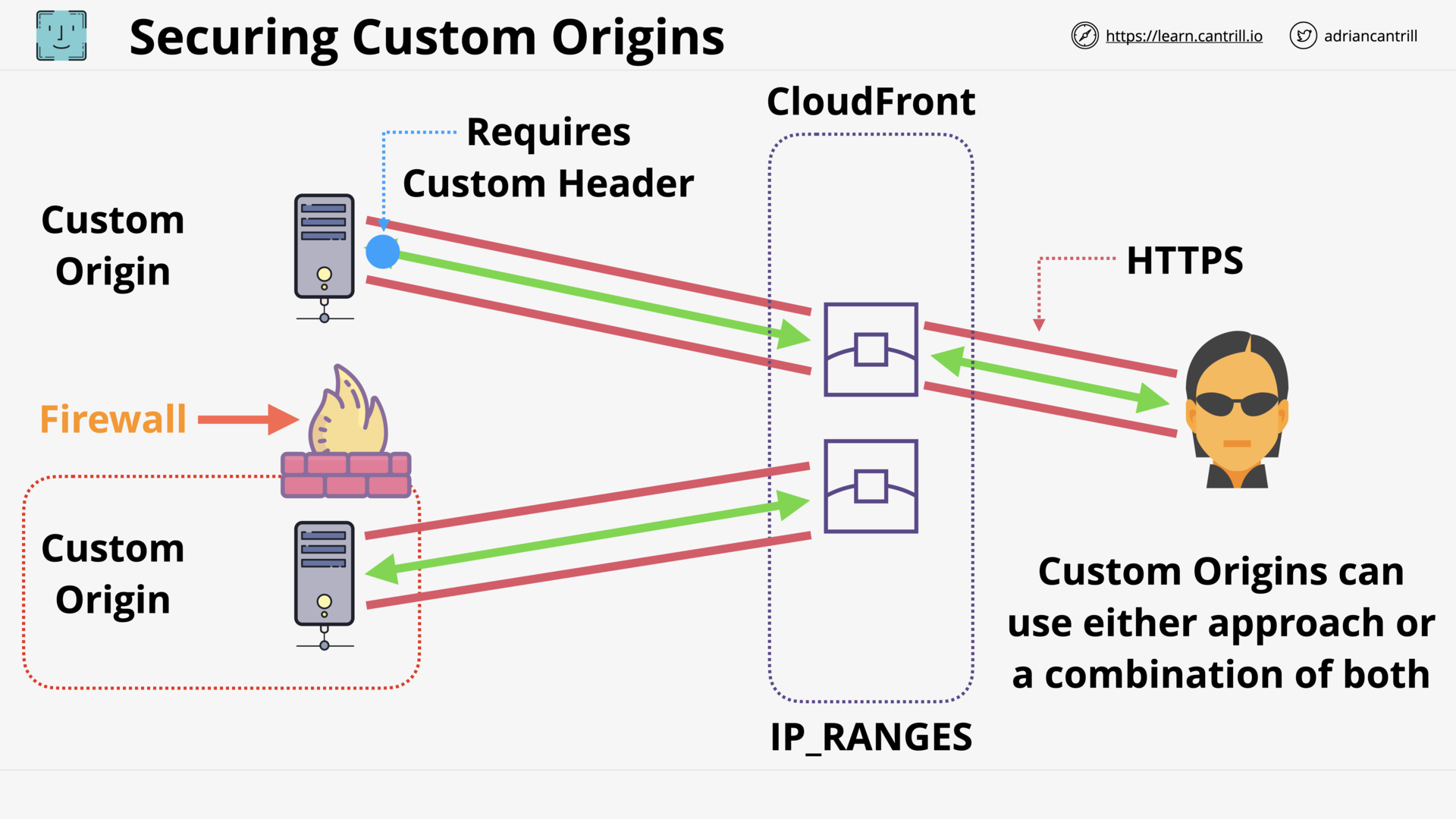 Securing Custom Origins
Securing Custom Origins
CloudFront - Private Distribution & Behaviours (7:49)
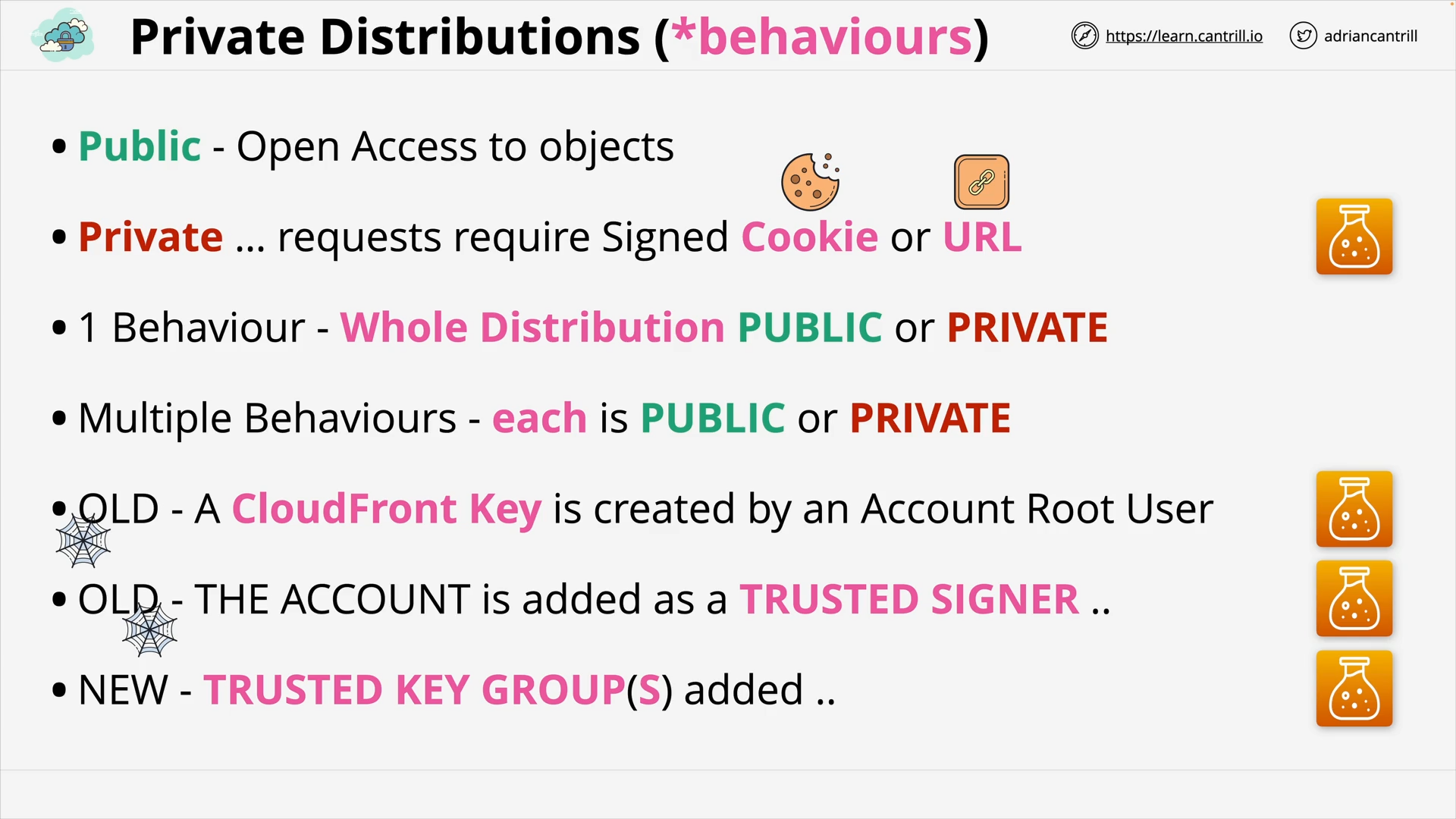 Private Distributions (*behaviours)
Private Distributions (*behaviours)
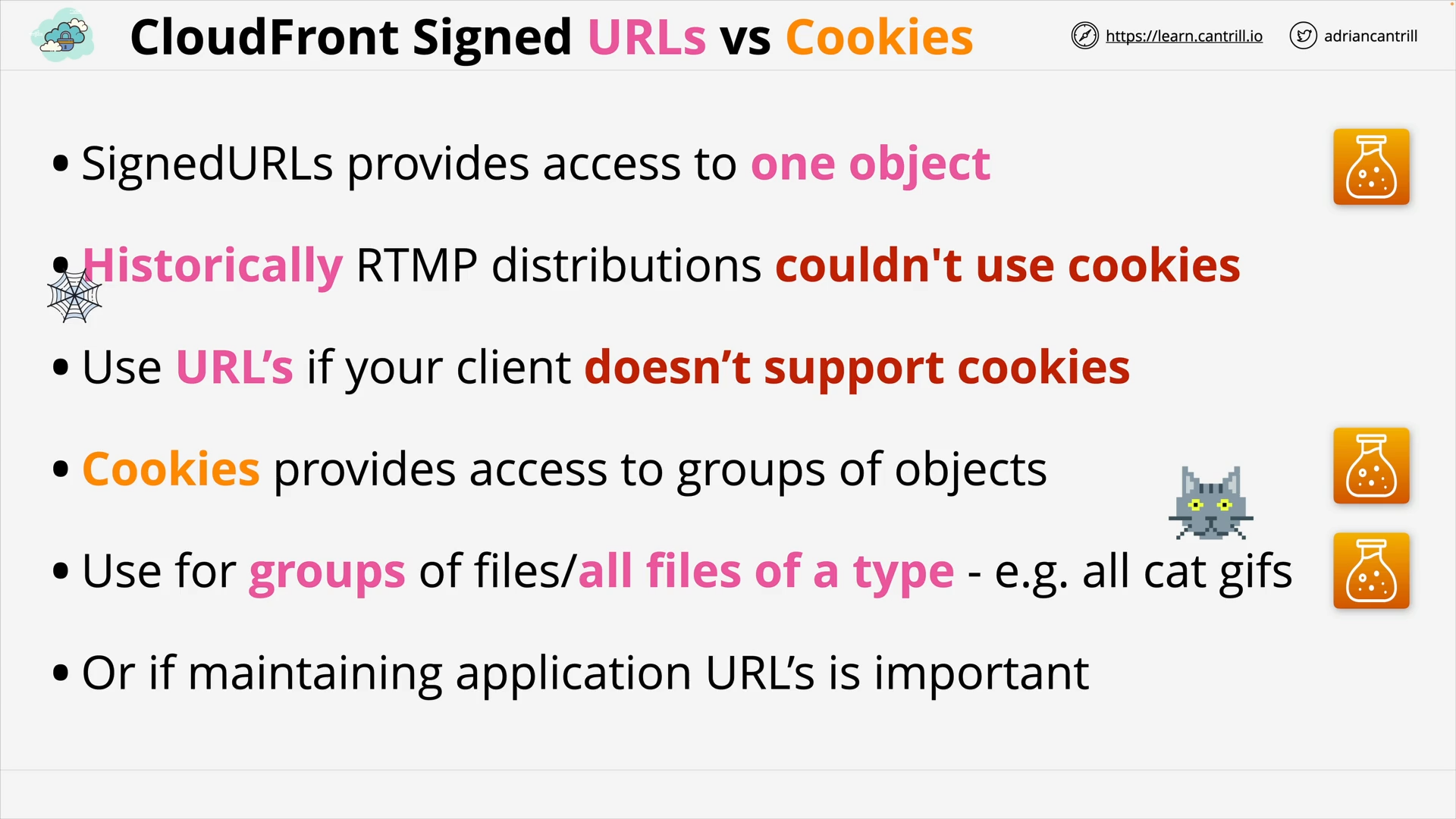 CloudFront Signed URLs 🔗 vs Cookies 🍪
CloudFront Signed URLs 🔗 vs Cookies 🍪
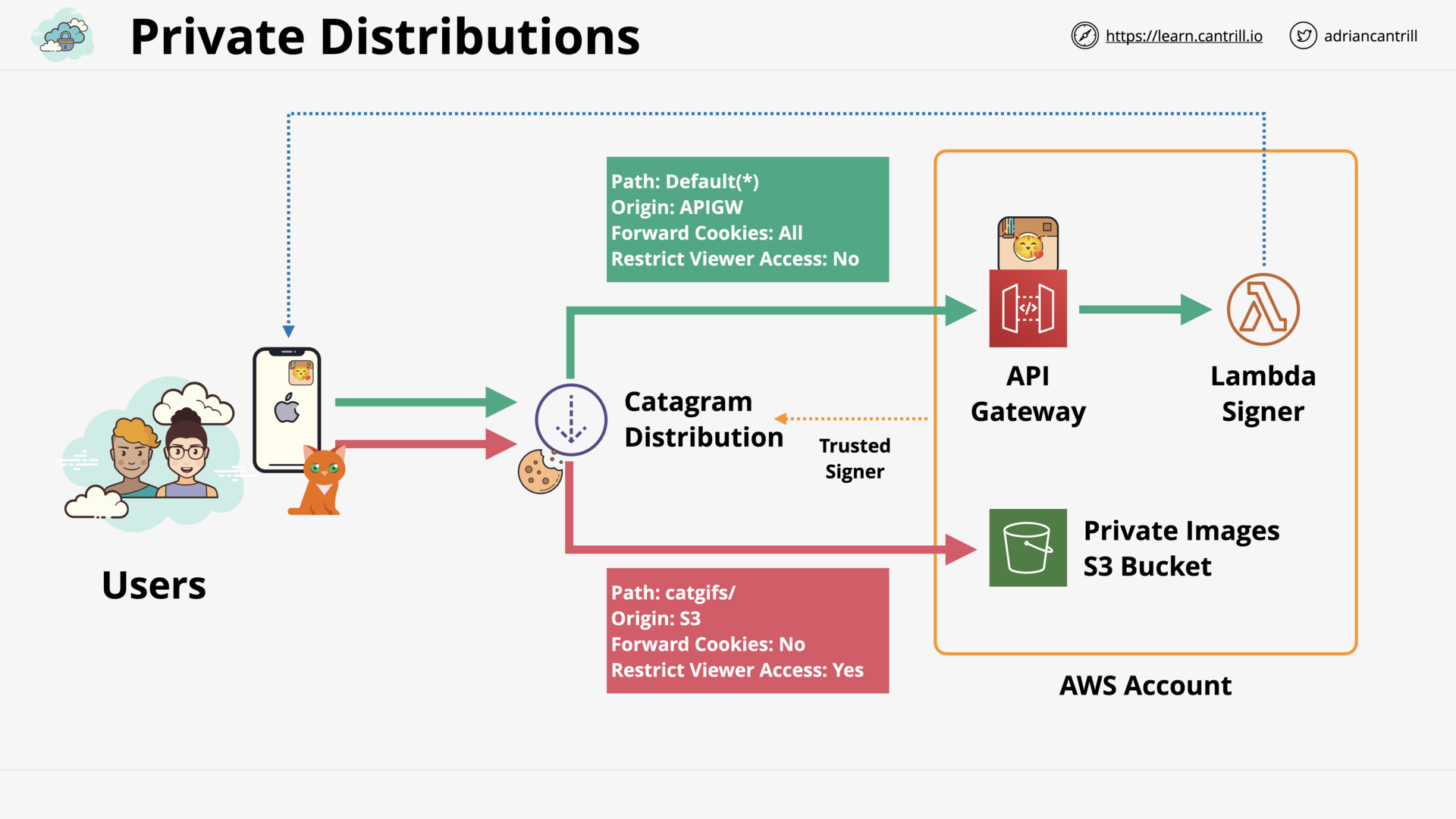 Private Distributions - Architecture
Private Distributions - Architecture
[DEMO] CloudFront (CF) - Using Origin Access Control (OAC) (new version of OAI) (11:21)
Lambda@Edge (8:03)
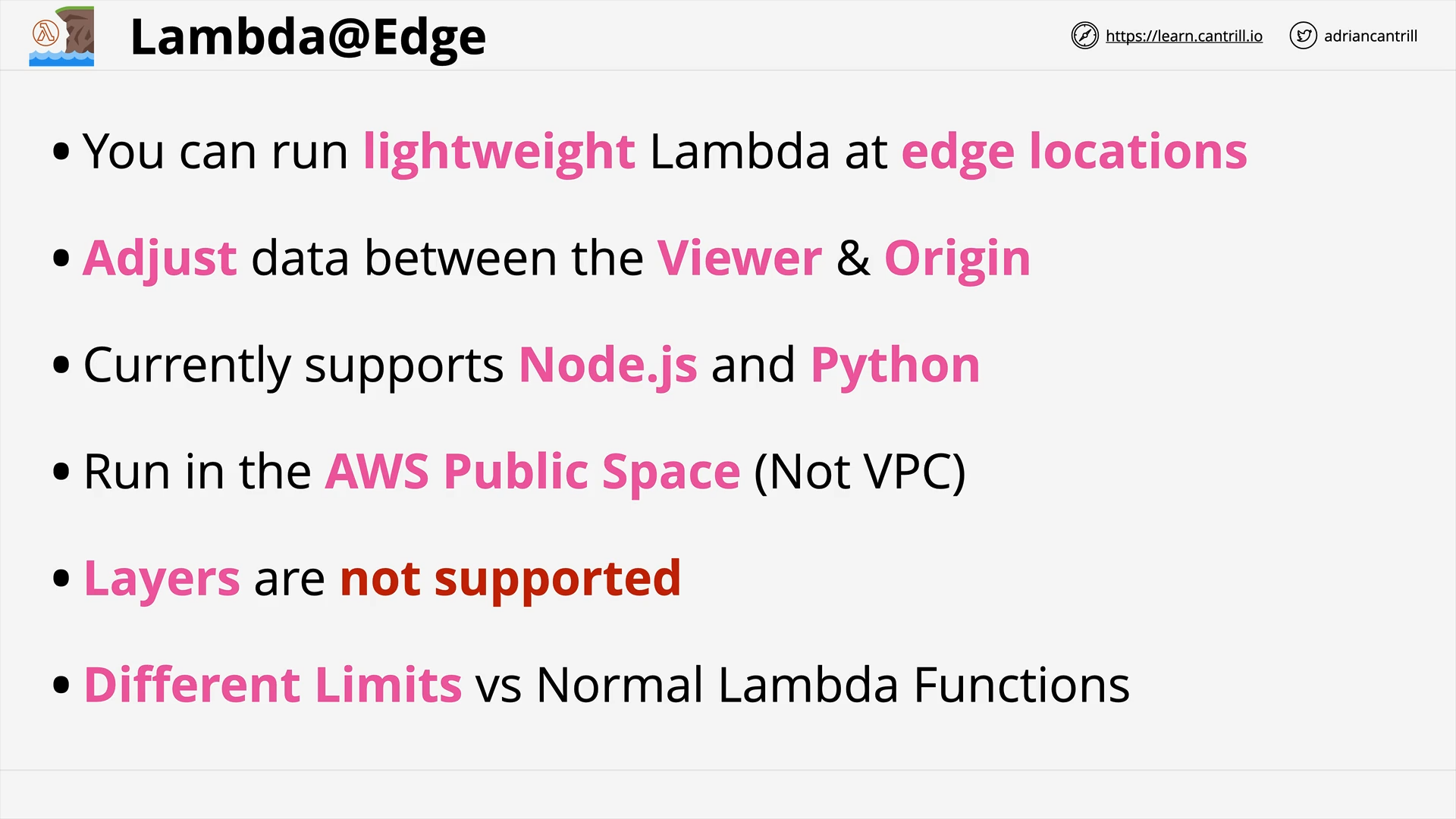 Lambda@Edge - Overview
Lambda@Edge - Overview
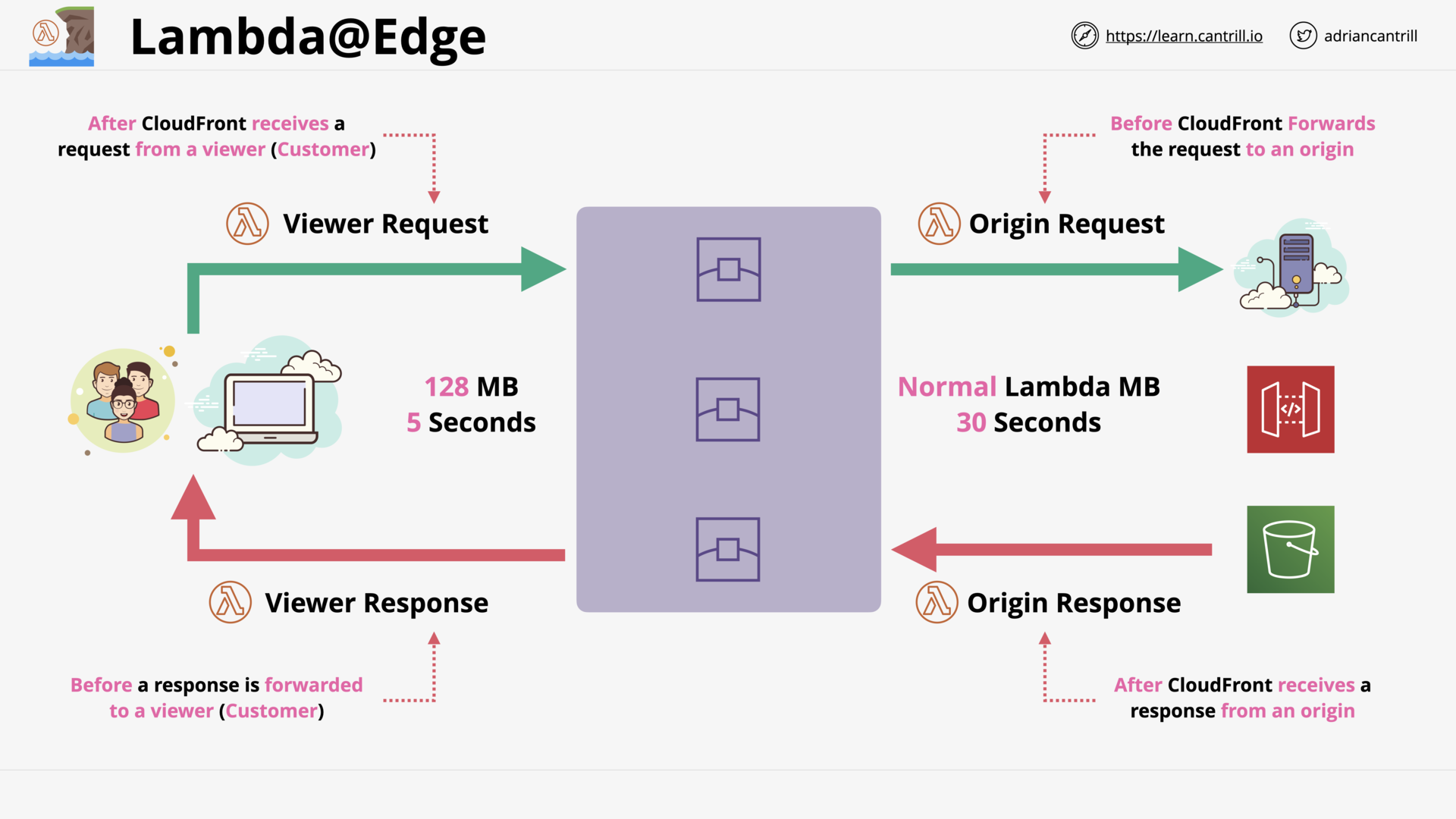 Lambda@Edge - Architecture
Lambda@Edge - Architecture
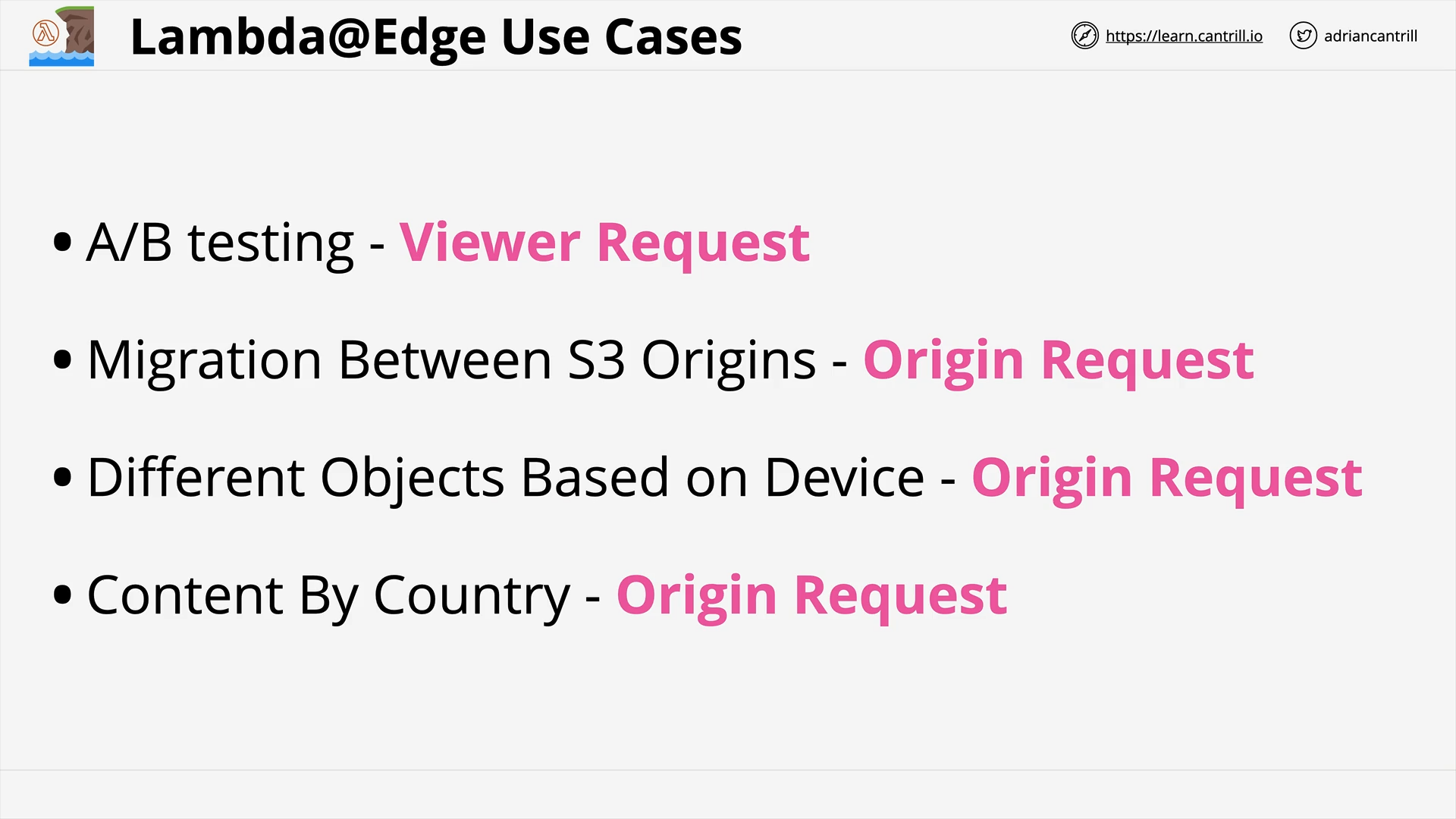 Lambda@Edge - Use Cases (More)
Lambda@Edge - Use Cases (More)
Global Accelerator (10:29)
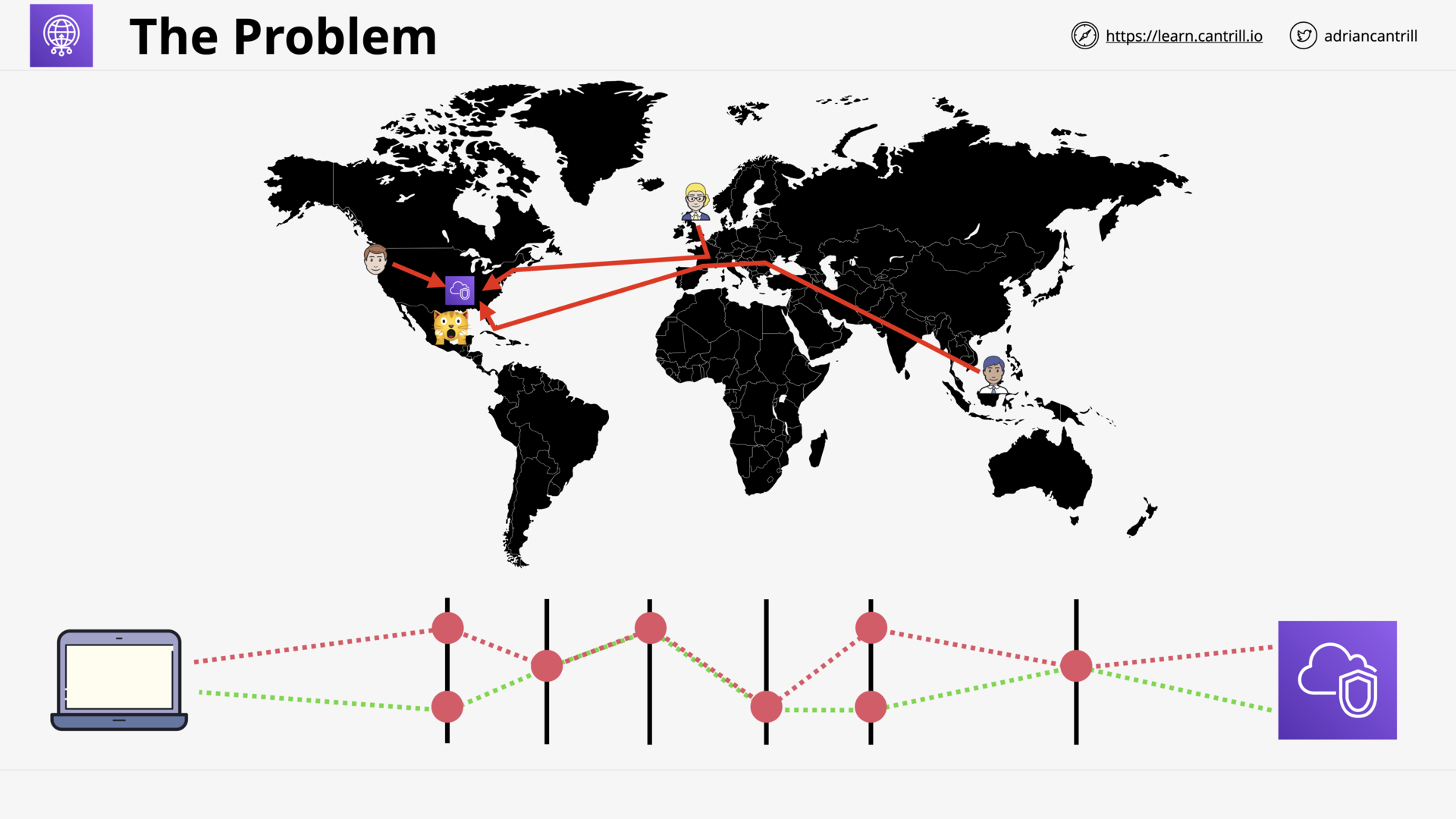 Global Accelerator - The Problem
Global Accelerator - The Problem
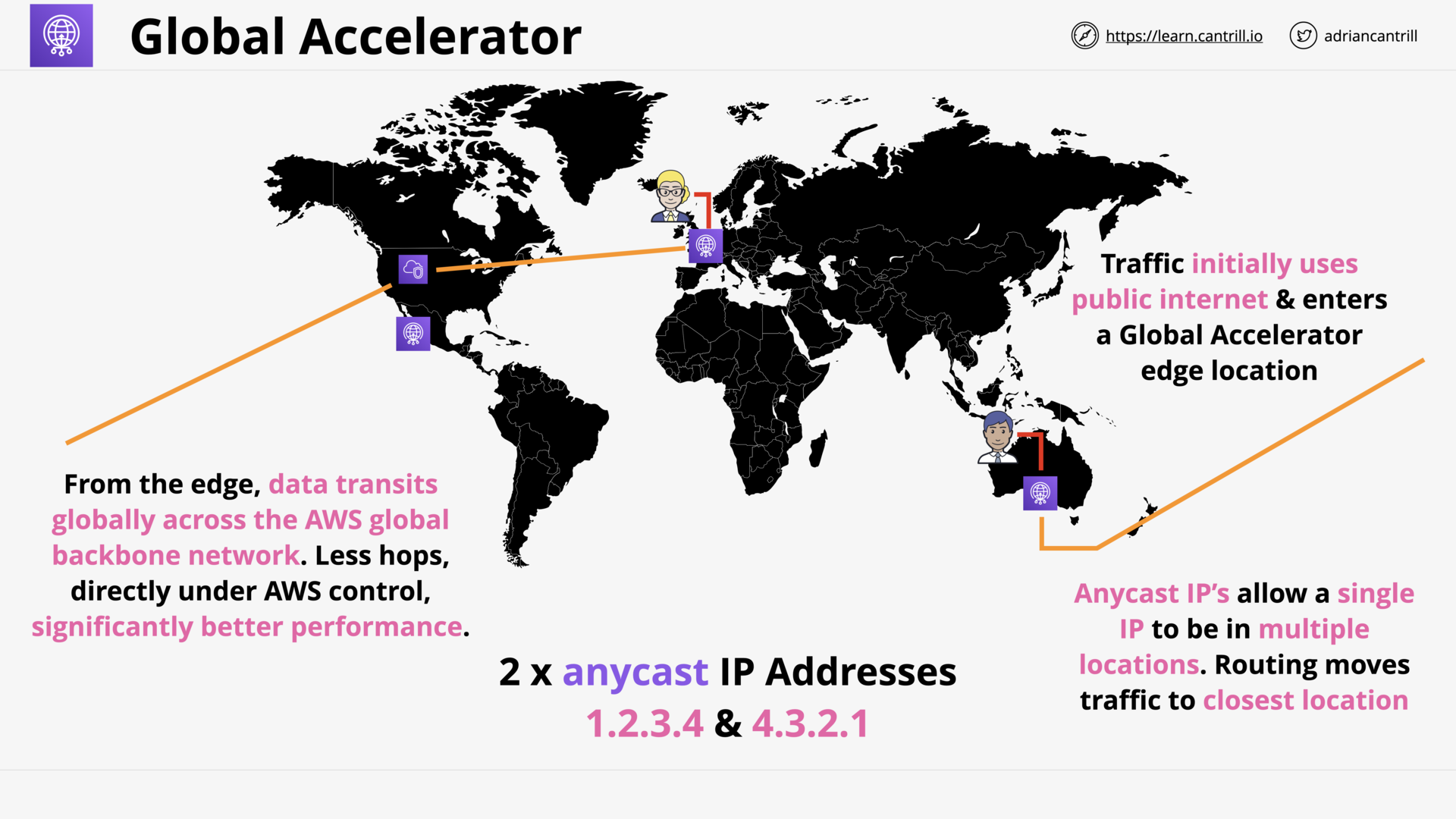 Global Accelerator - Use Anycast to route traffic to AWS global backbone network
Global Accelerator - Use Anycast to route traffic to AWS global backbone network
what is anycast?
Anycast is a network addressing and routing method in which incoming requests can be routed to a variety of different locations (called “nodes”).
Anycast IP allow a single IP to be in multiple locations.
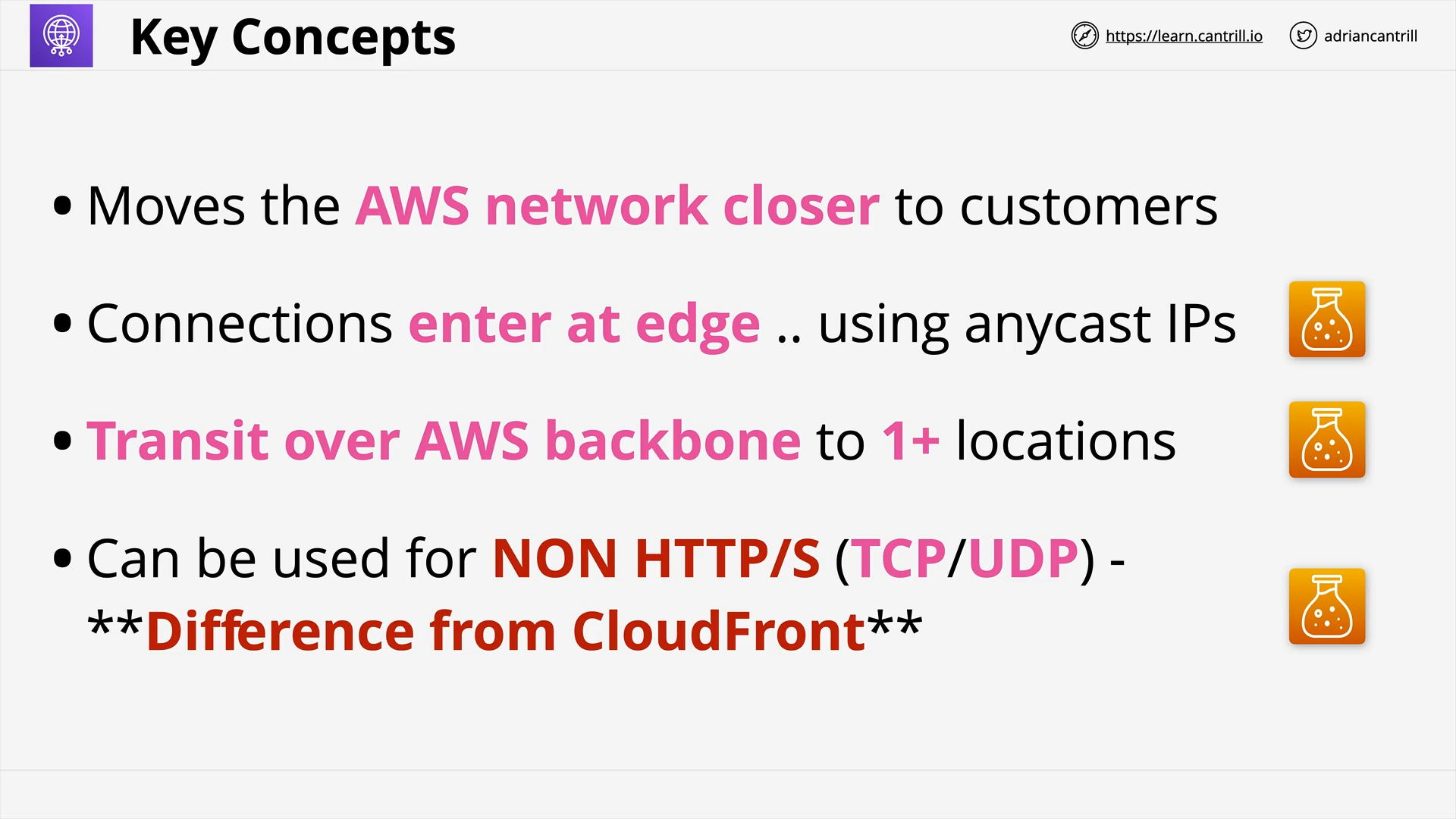 Global Accelerator - Key Concepts
Global Accelerator - Key Concepts
CloudFront Field-Level Encryption
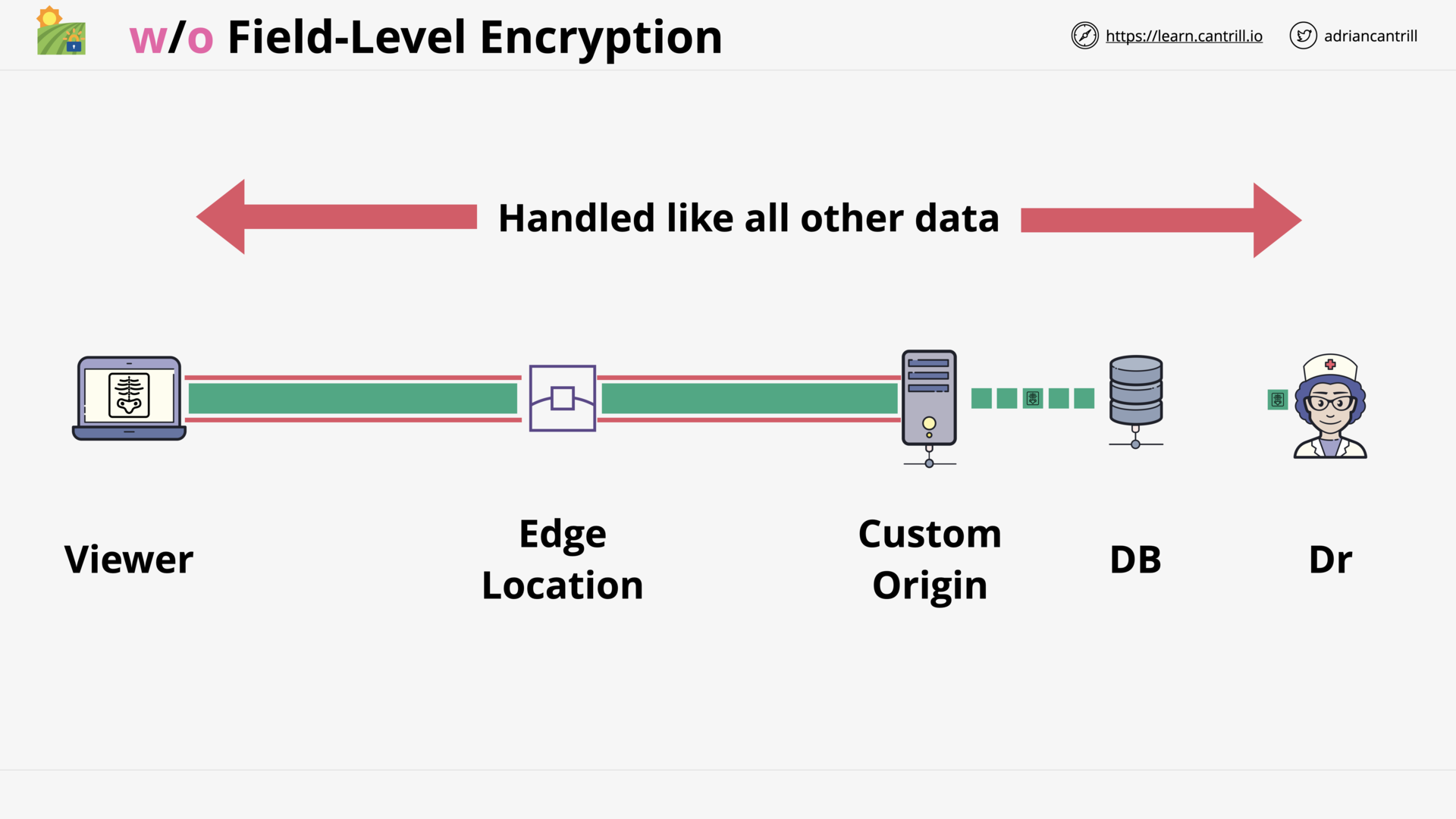 CloudFront - Without Field-Level Encryption
CloudFront - Without Field-Level Encryption
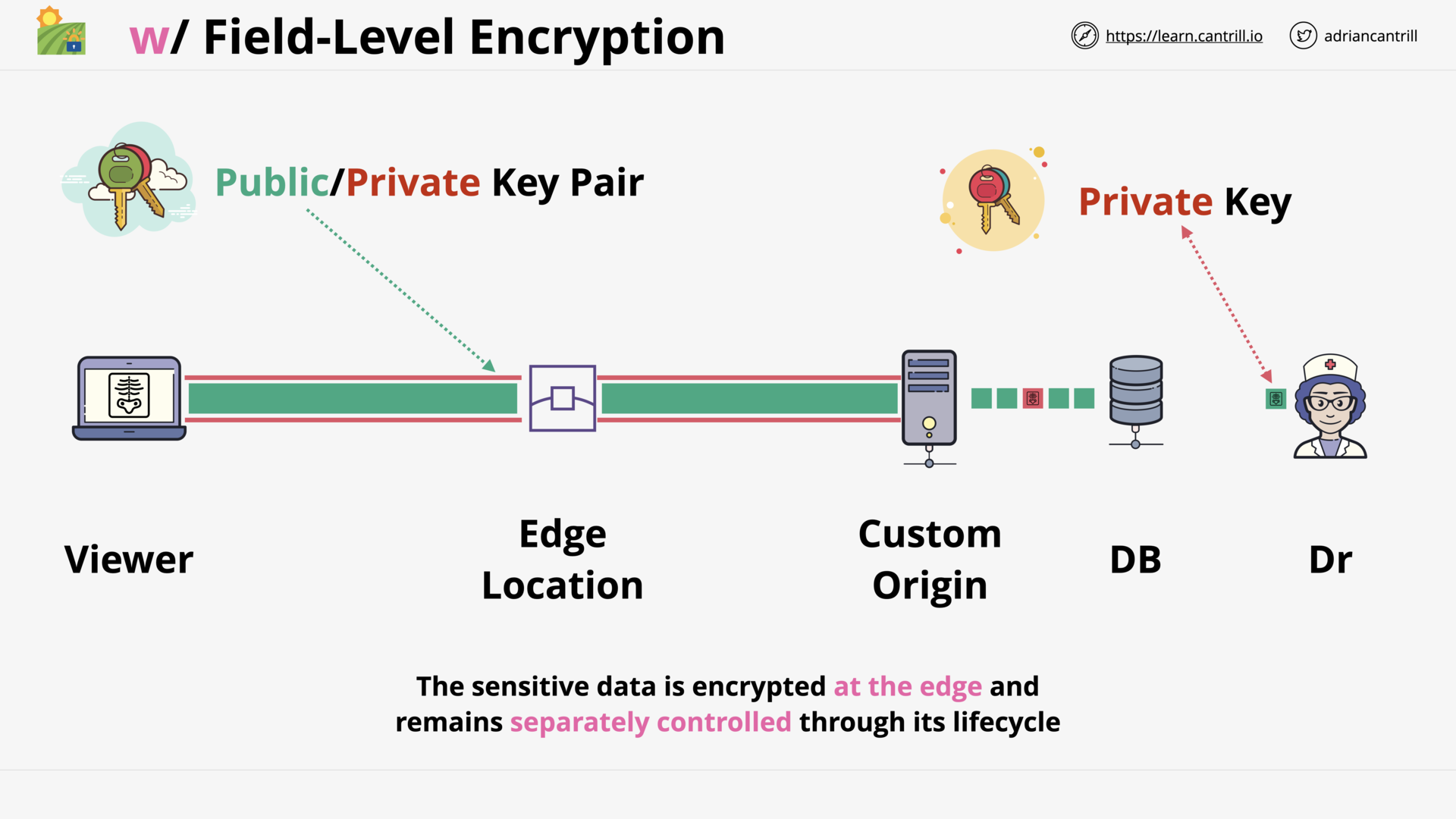 CloudFront - With Field-Level Encryption
CloudFront - With Field-Level Encryption
what does field-level encryption do?
Field-level encryption allows you to enable your users to securely upload sensitive information to your web servers.
(Docs)
CloudFront Geo Restriction (Geo-blocking)
CDN and Optimisation Section Quiz
ADVANCED VPC NETWORKING
VPC Flow Logs (9:56)
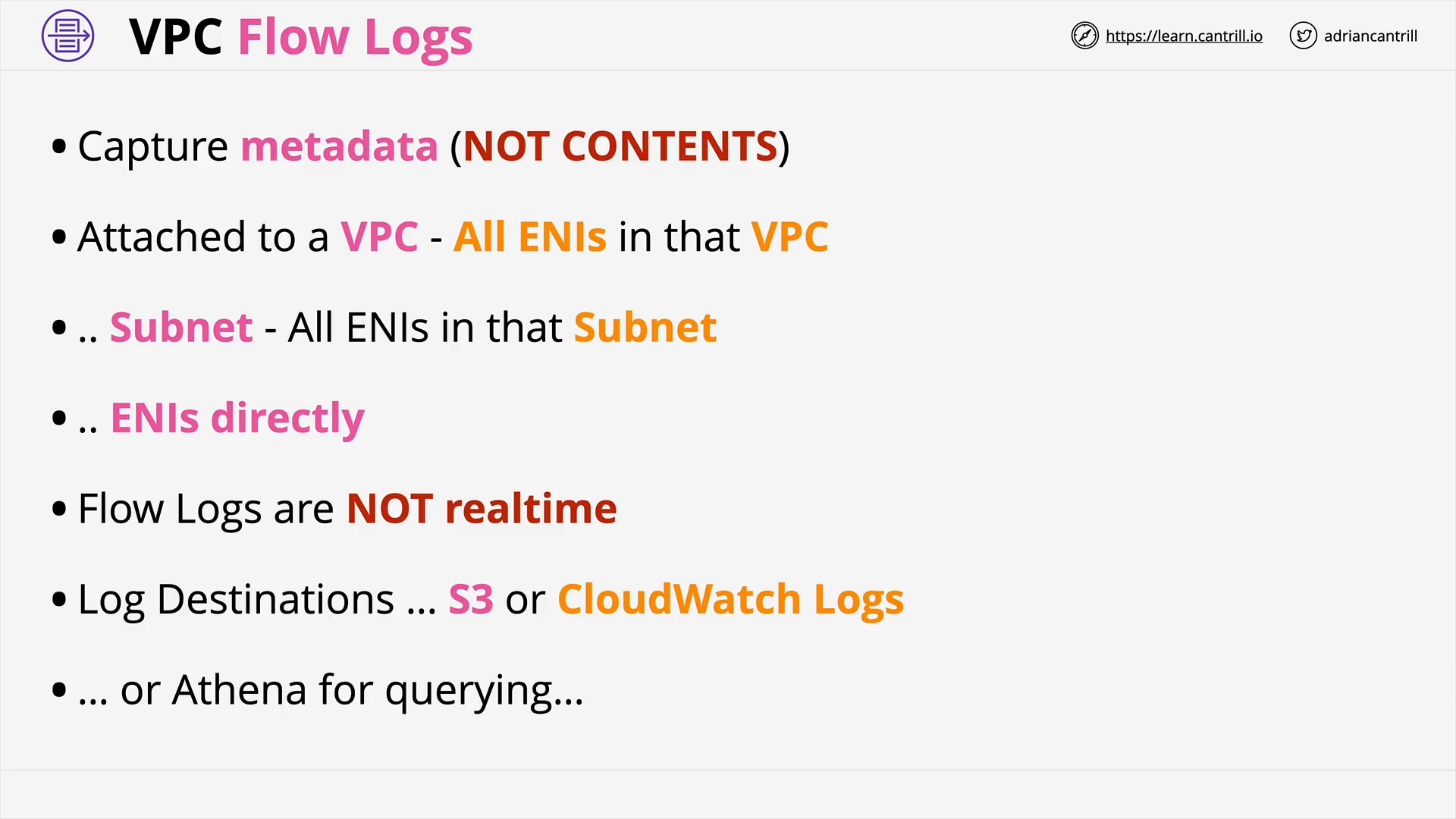 VPC FLow Logs - Capture traffic metadata, NOT capture contents, NOT realtime
VPC FLow Logs - Capture traffic metadata, NOT capture contents, NOT realtime
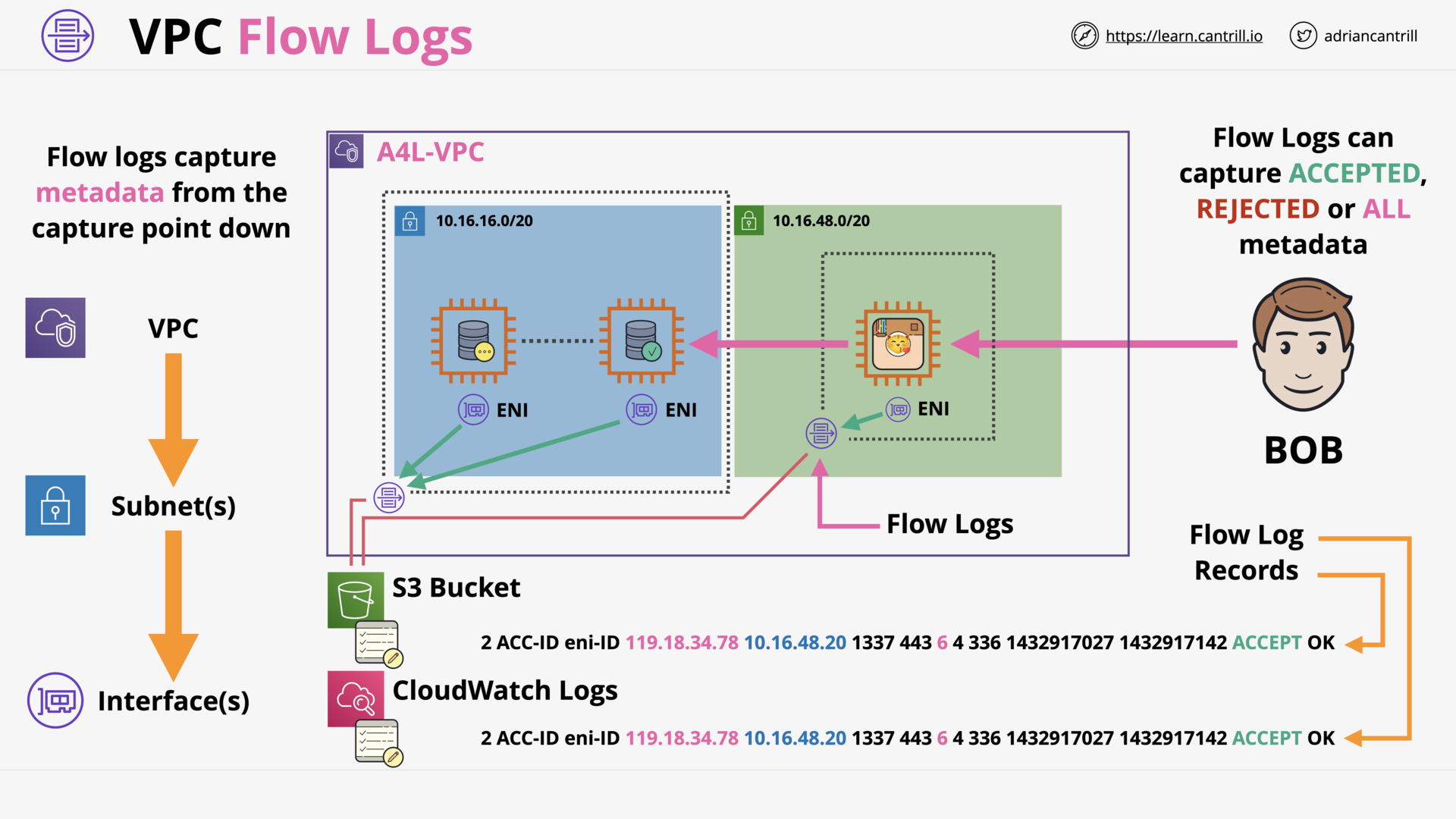 VPC FLow Logs - Architecture
VPC FLow Logs - Architecture
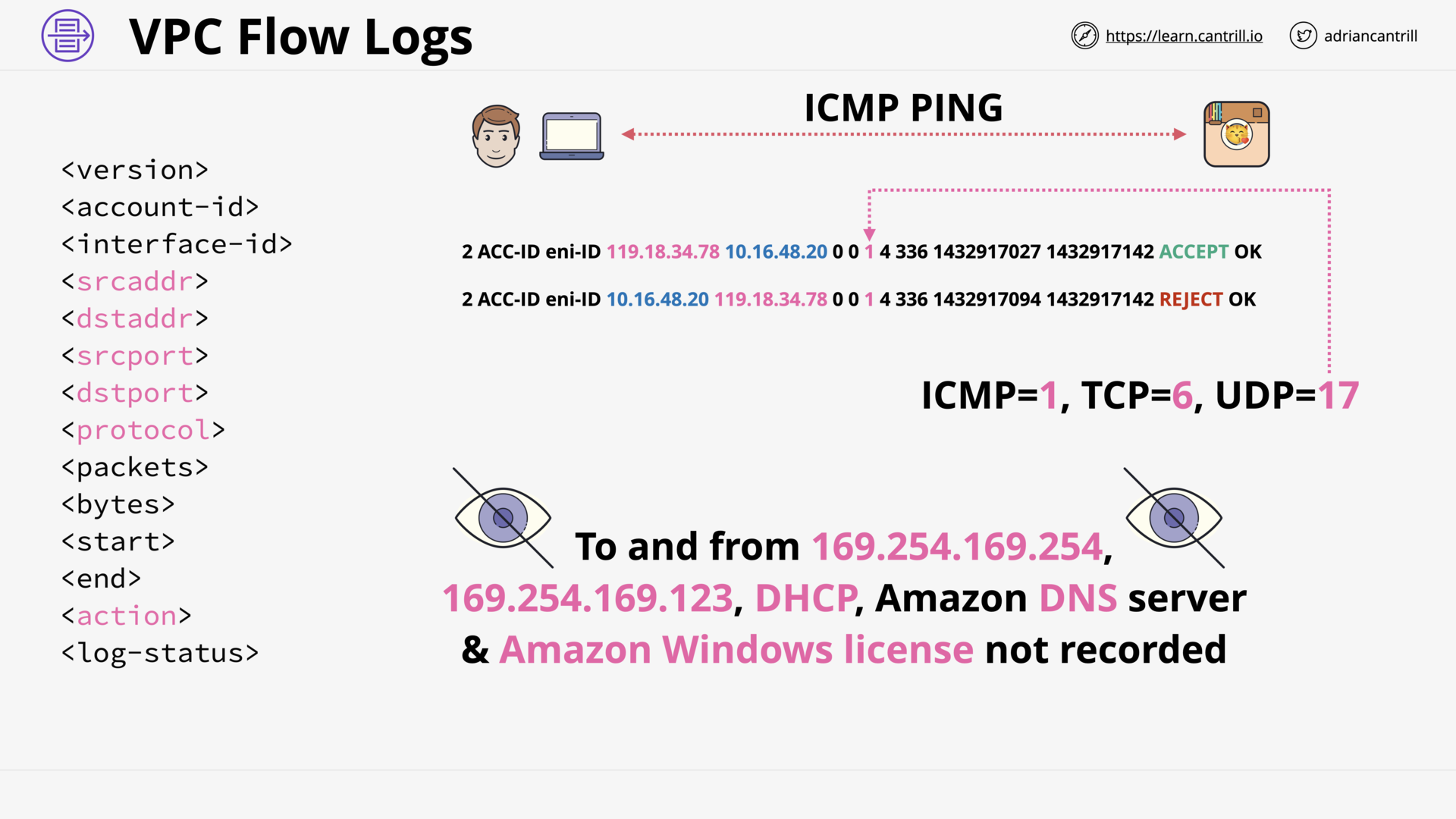 VPC FLow Logs - Flow Log Records
VPC FLow Logs - Flow Log Records
Egress-Only Internet Gateway (6:46)
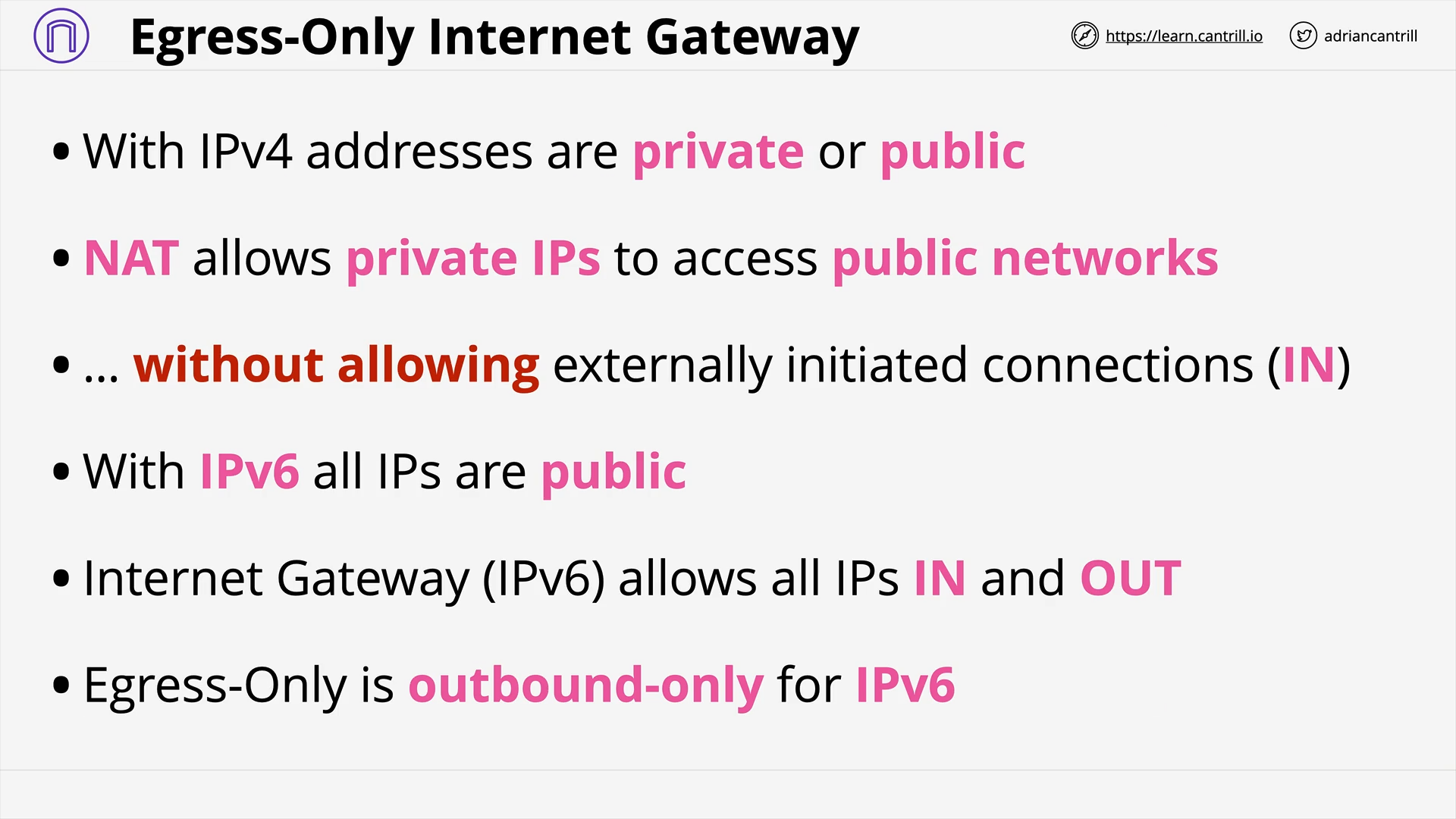 Egress-Only Internet Gateway - Why?
Egress-Only Internet Gateway - Why?
what does egress-only internet gateway do?
Allow outbound (and response) only access to the public AWS services and Public Internet for IPv6 enabled instances or other VPC based services.
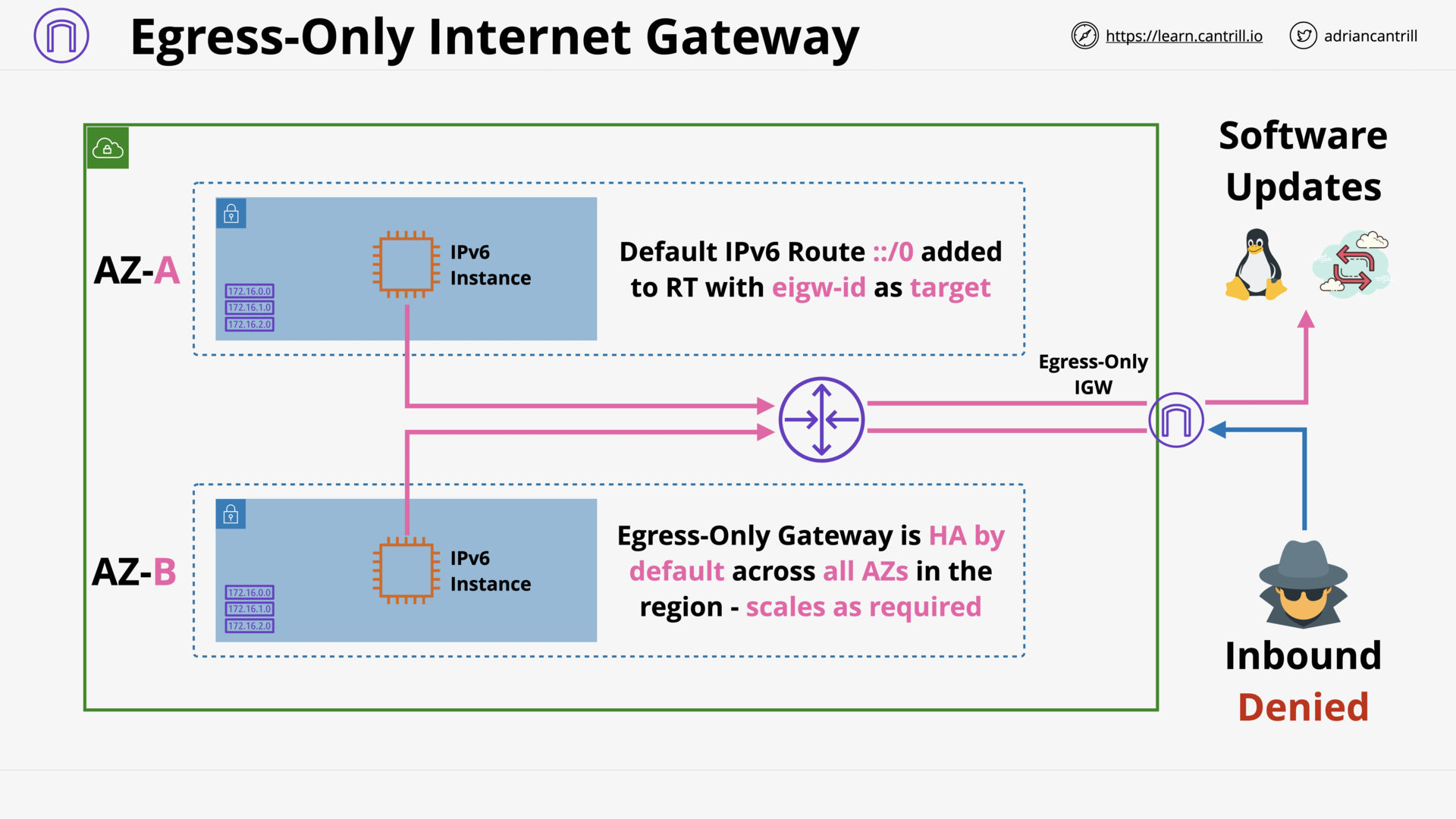 Egress-Only Internet Gateway - Architecture
Egress-Only Internet Gateway - Architecture
VPC Endpoints (Gateway) (11:14)
__lea_%E2%80%94_F.png) VPC Gateway Endpoints: Provide private access to AWS Public Services via Prefix List and Route Table
VPC Gateway Endpoints: Provide private access to AWS Public Services via Prefix List and Route Table
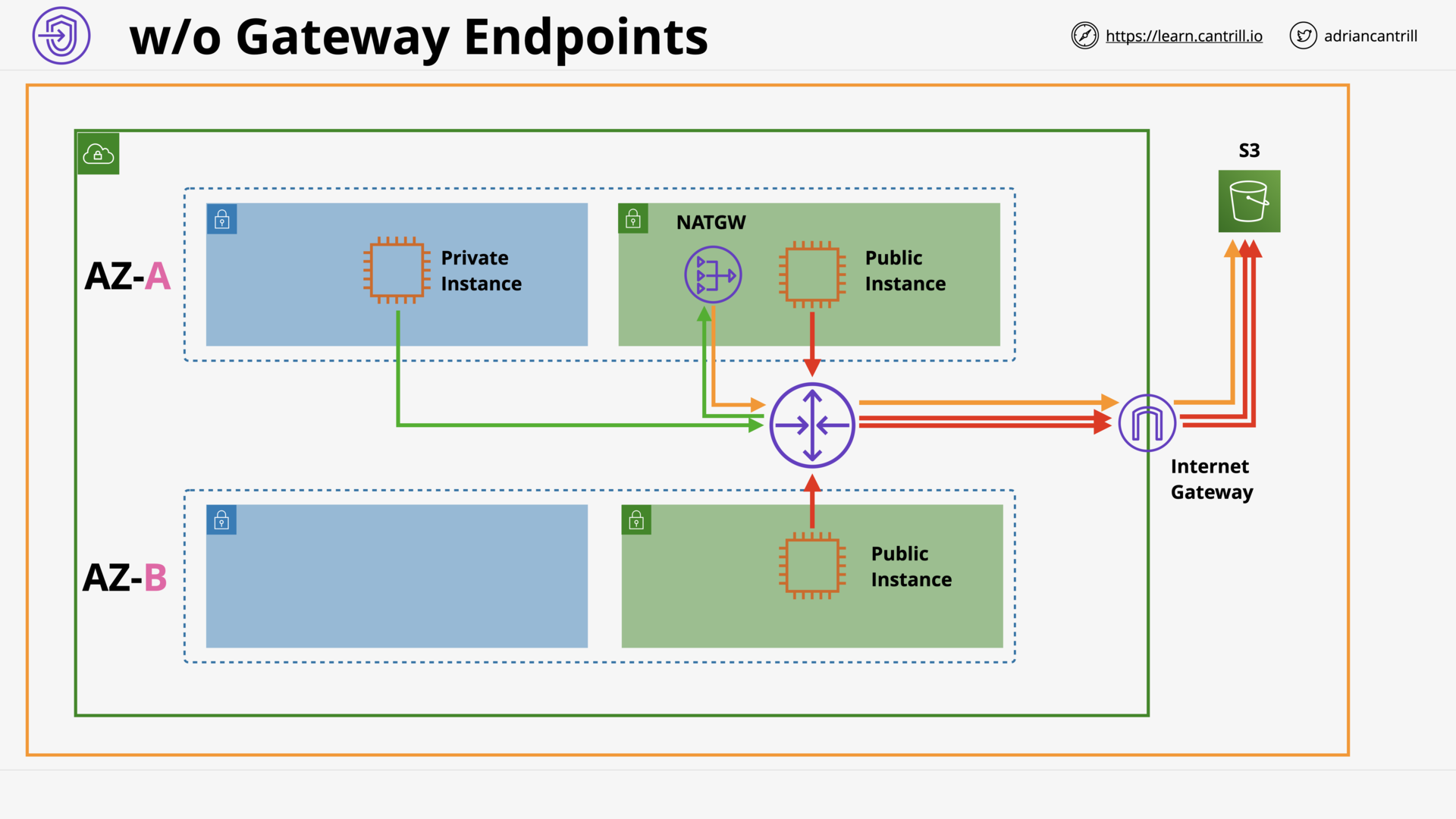 VPC - Without Gateway Endpoints
VPC - Without Gateway Endpoints
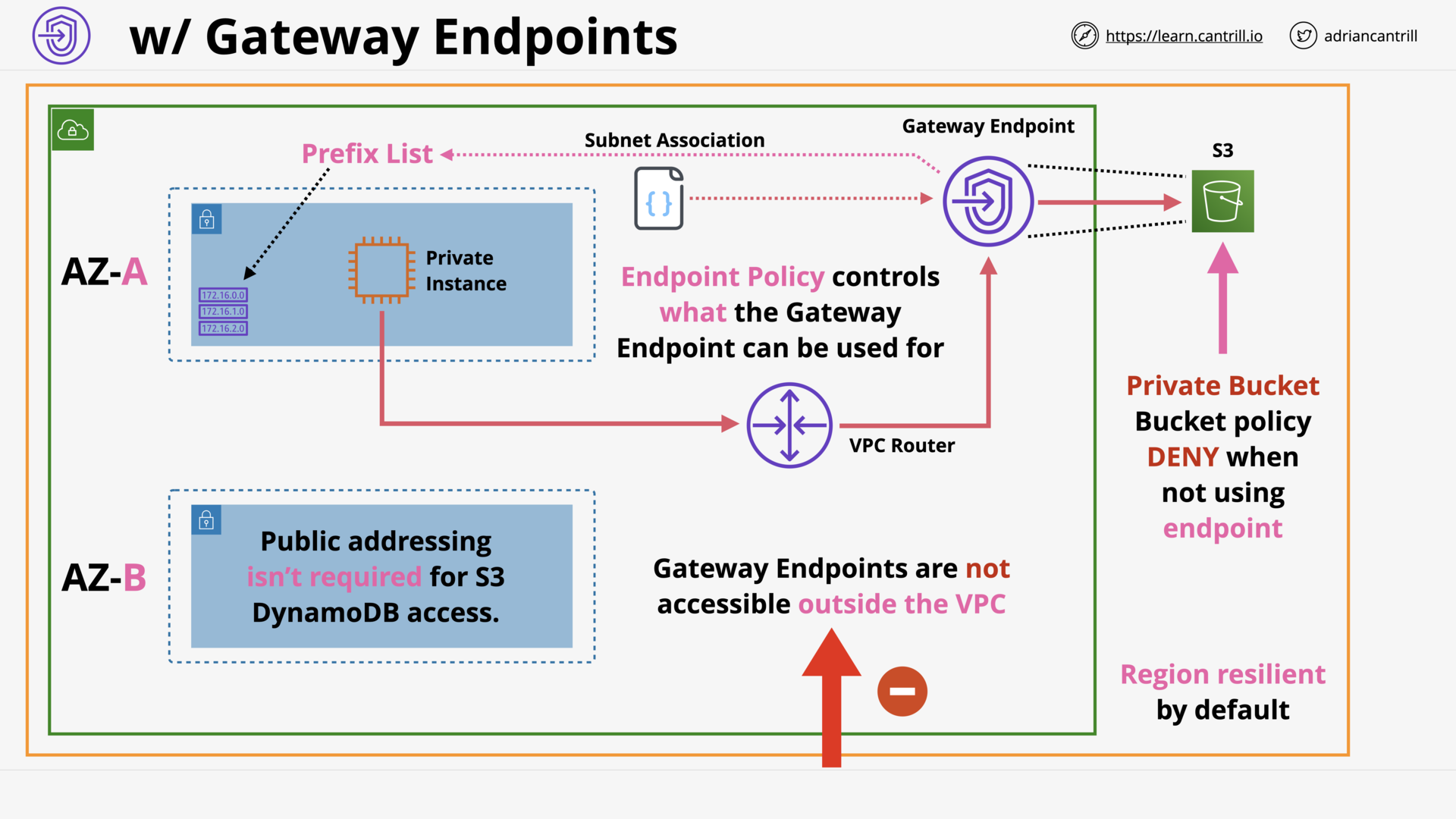 VPC - With Gateway Endpoints
VPC - With Gateway Endpoints
VPC Endpoints (Interface) (11:26)
__lea_%E2%80%94.png) VPC Interface Endpoints - Provide private access to AWS Public Services via DNS
VPC Interface Endpoints - Provide private access to AWS Public Services via DNS
__lea_%E2%80%94.png) VPC Interface Endpoints - PrivateDNS
VPC Interface Endpoints - PrivateDNS
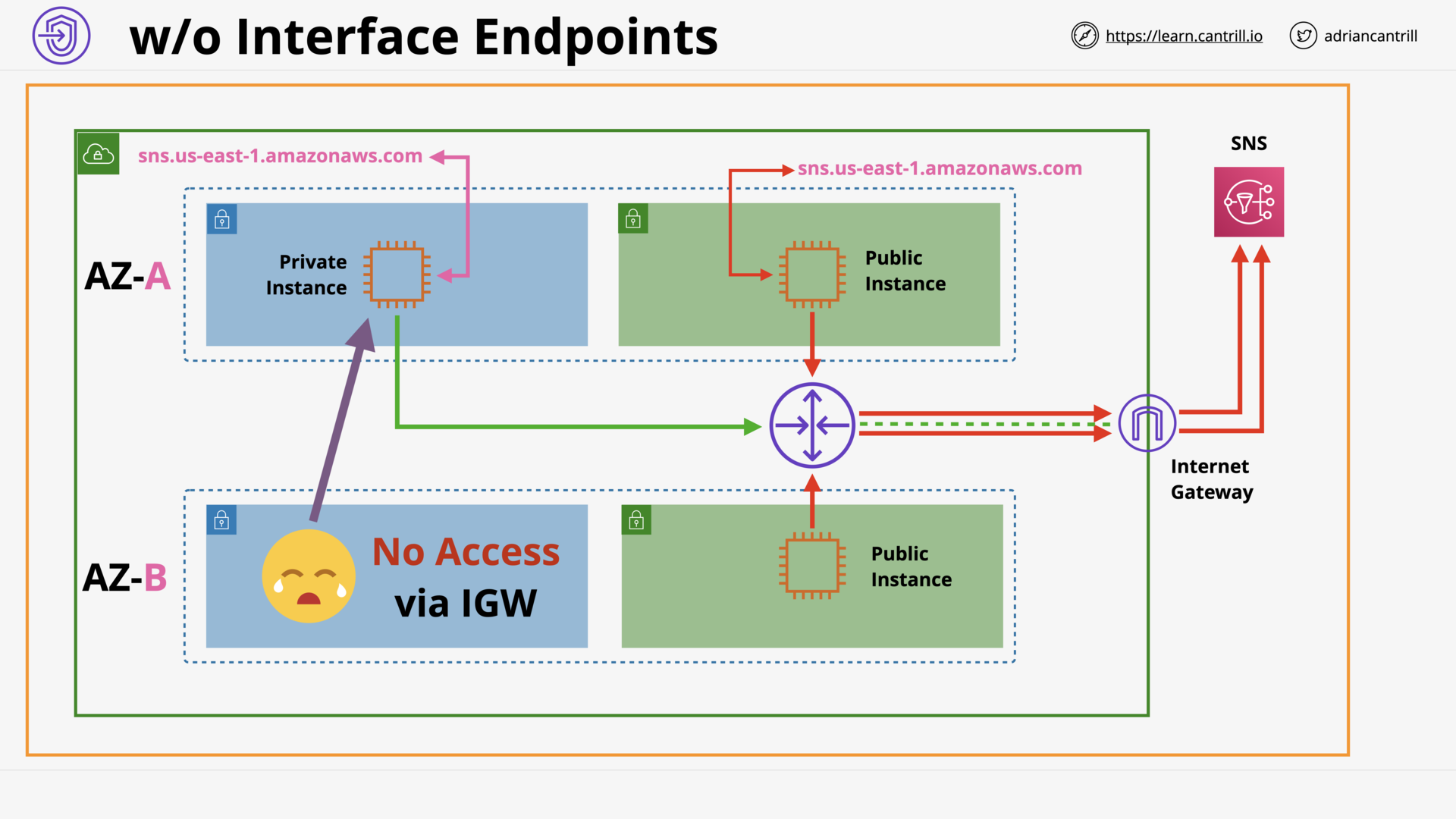 Without Interface Endpoints 🛑
Without Interface Endpoints 🛑
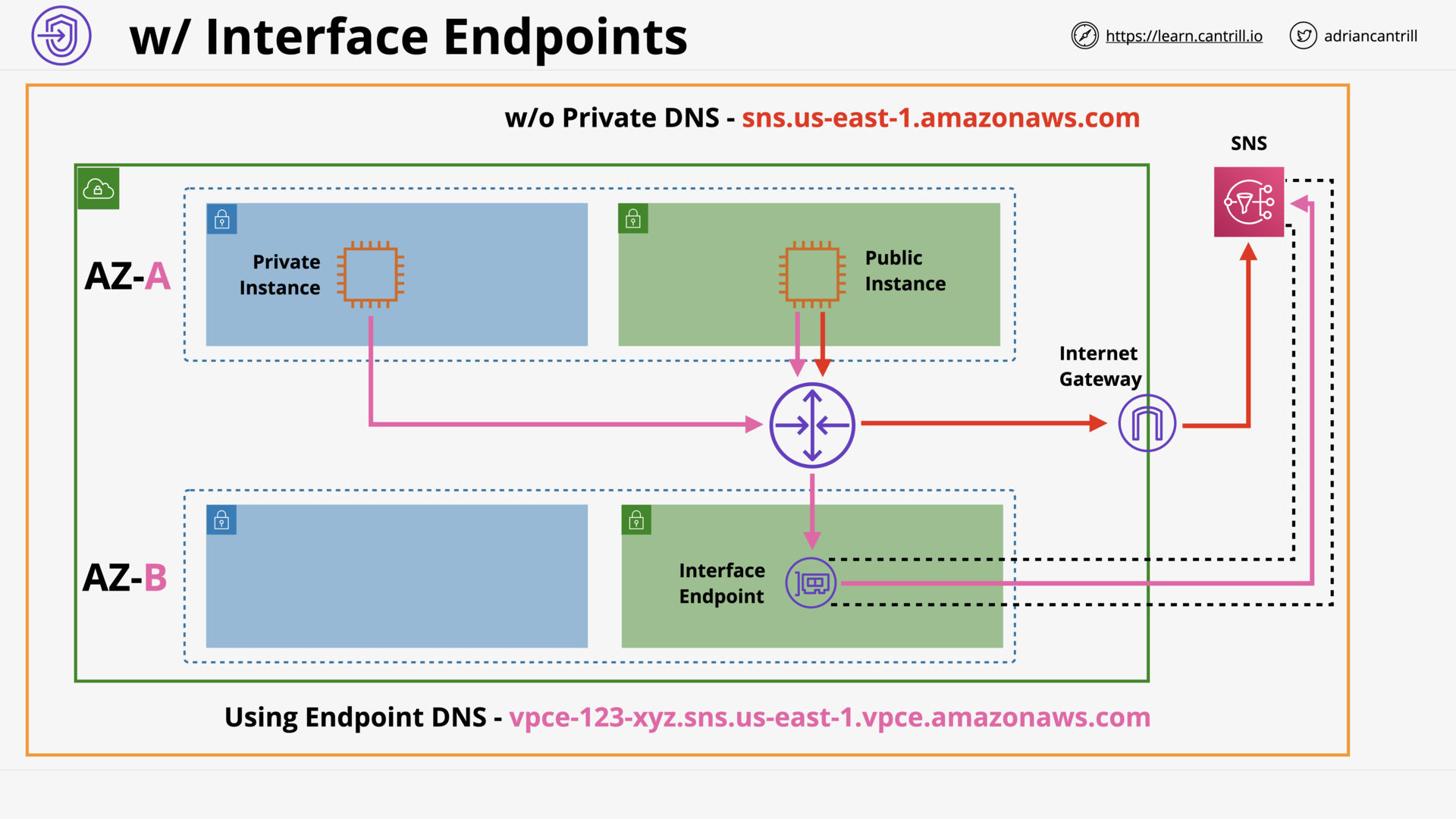 With Interface Endpoints
With Interface Endpoints
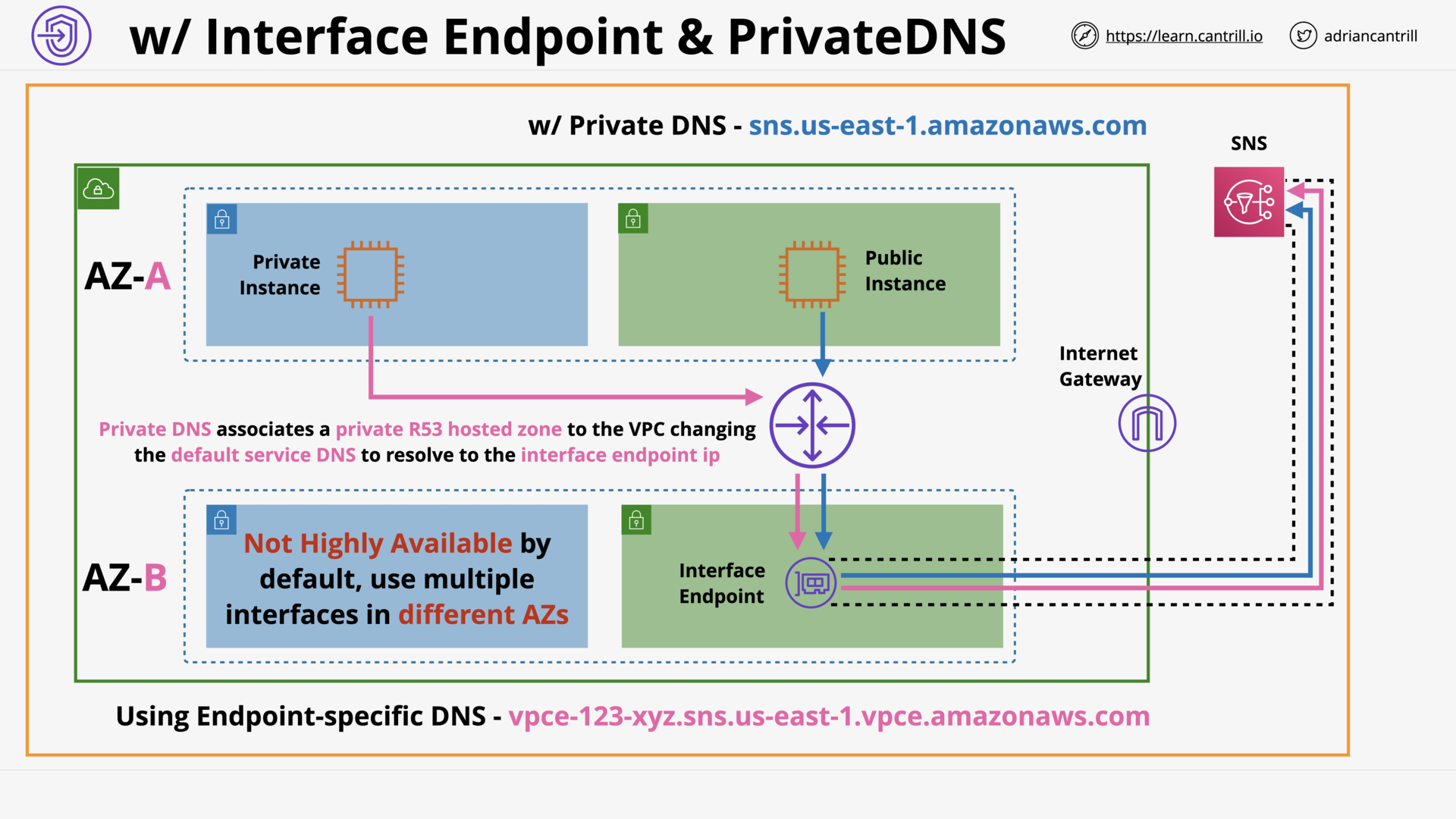 With Interface Endpoints & PrivateDNS
With Interface Endpoints & PrivateDNS
[DEMO] VPC Endpoints - Interface - PART1 (11:59)
[DEMO] VPC Endpoints - Gateway - PART2 (9:59)
[DEMO] Egress-Only Internet Gateway - PART3 (7:57)
VPC Peering (9:04)
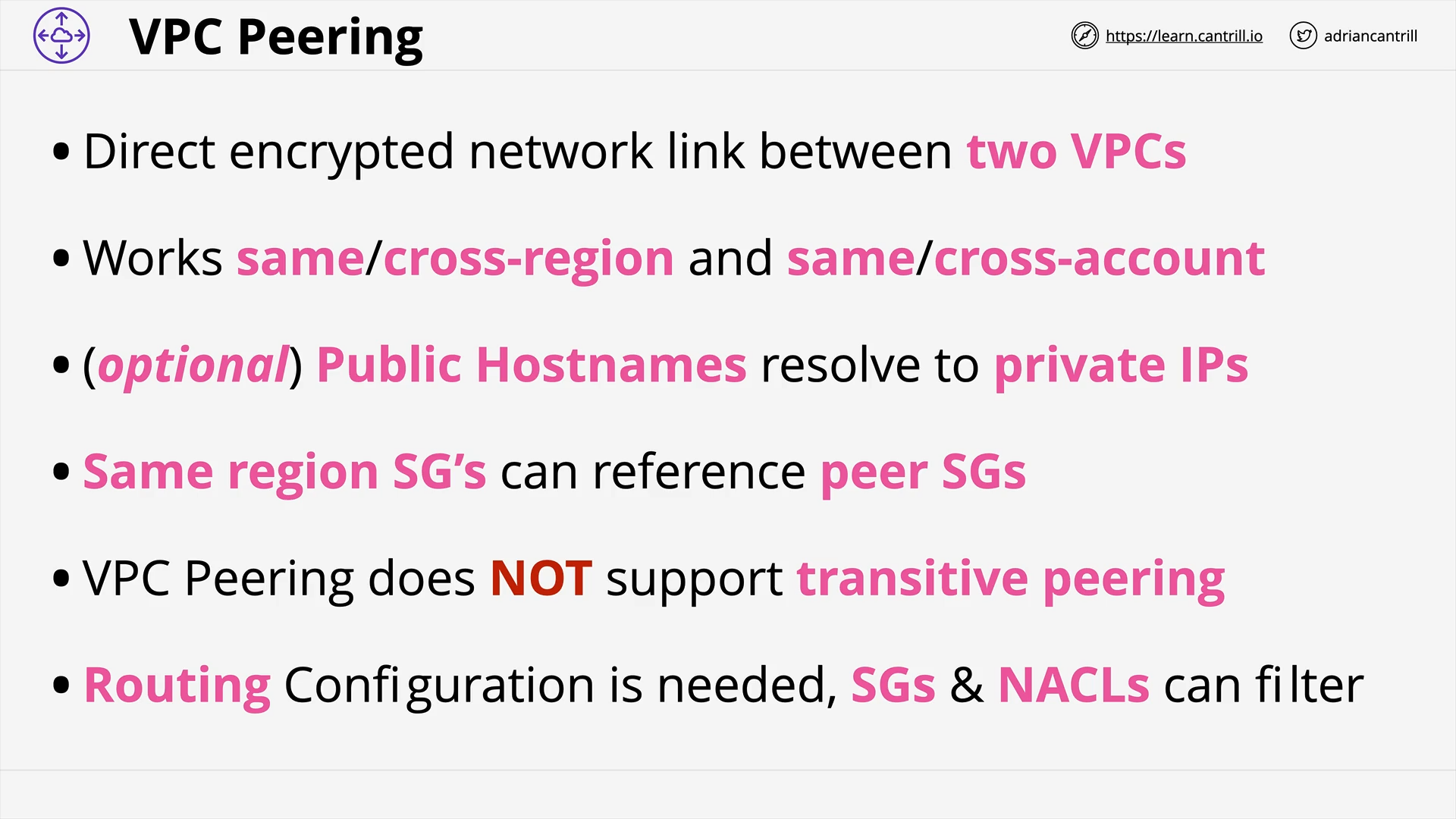 VPC Peering - Overview
VPC Peering - Overview
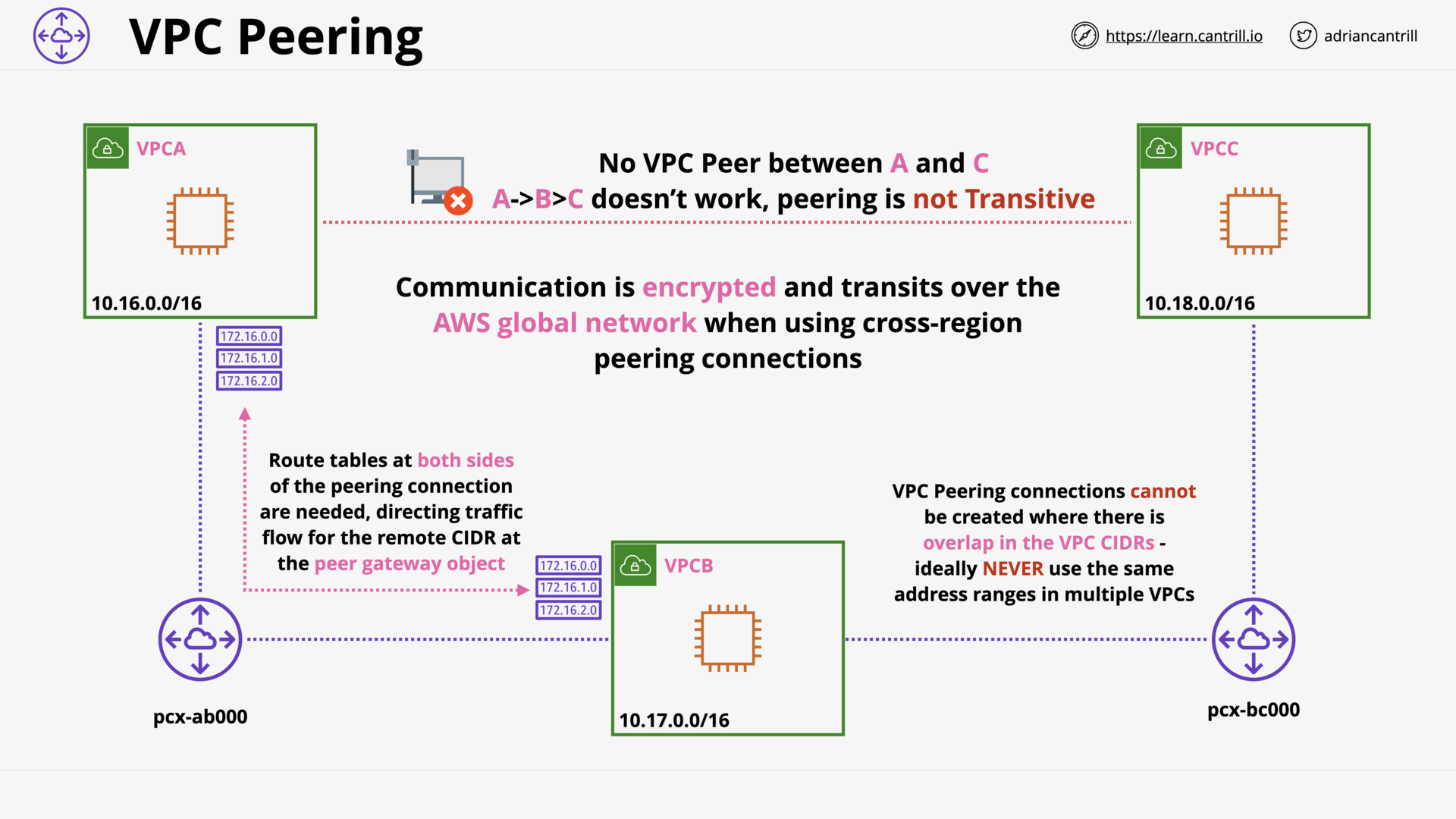 VPC Peering - Architecture
VPC Peering - Architecture
[DEMO] VPC Peering (22:38)
Advanced VPC Section Quiz
HYBRID ENVIRONMENTS AND MIGRATION
Border Gateway Protocol 101 (17:29)
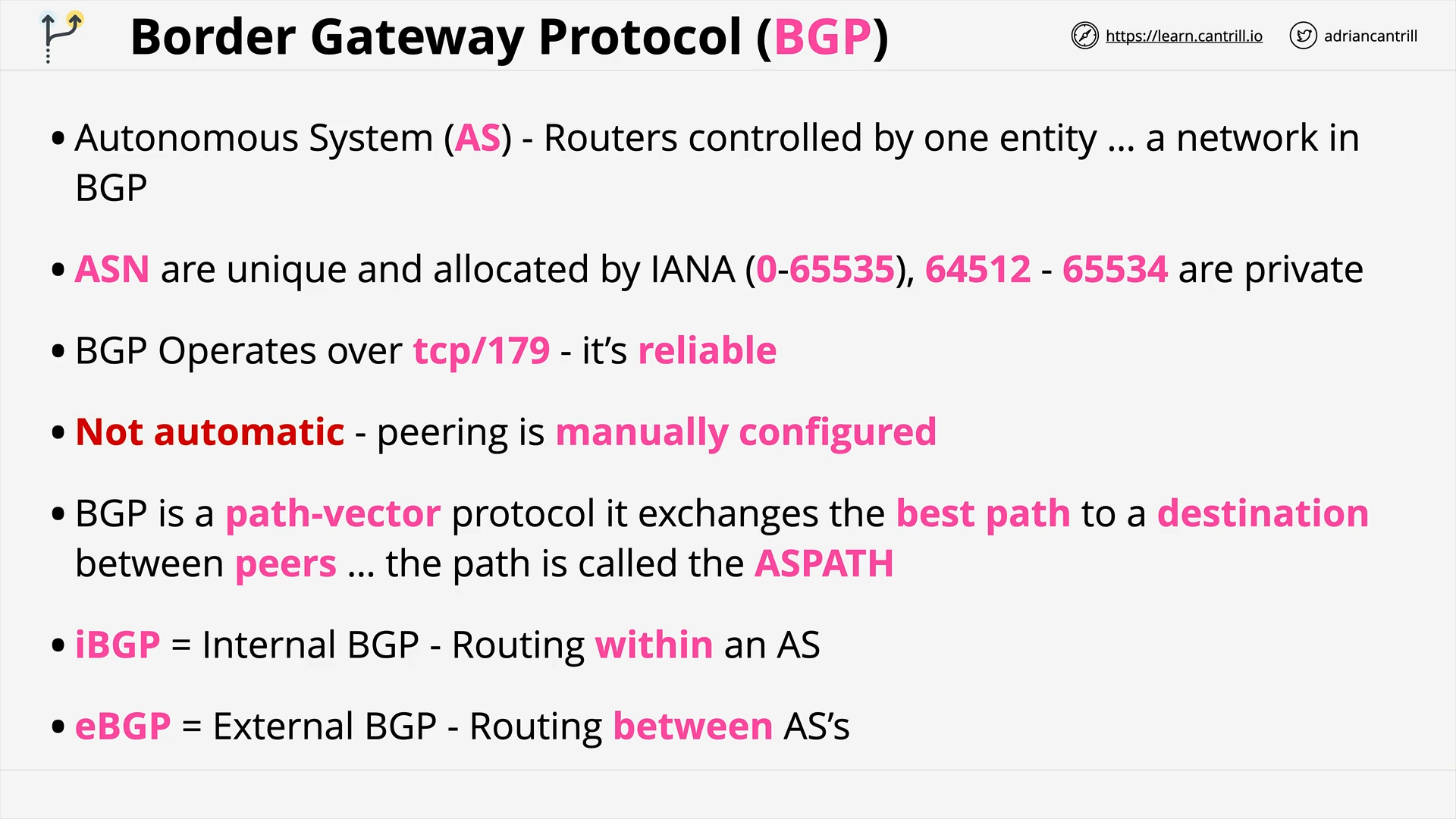 BGP - AS, ASN, ASPATH
BGP - AS, ASN, ASPATH
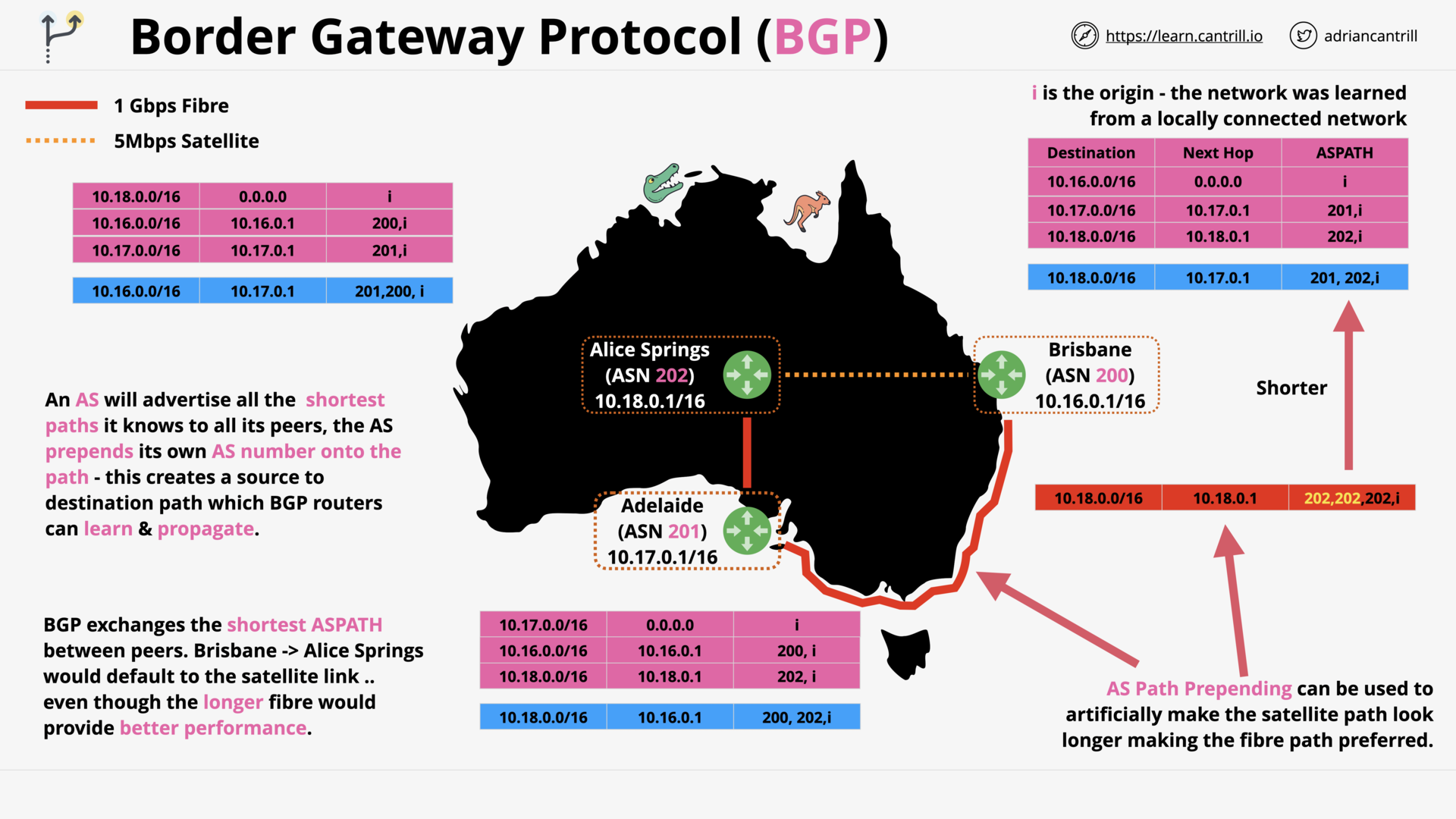 BGP - Architecture
BGP - Architecture
IPSec VPN Fundamentals (14:54)
[Tech Fundamentals | IP Sec VPN Fundamentals]
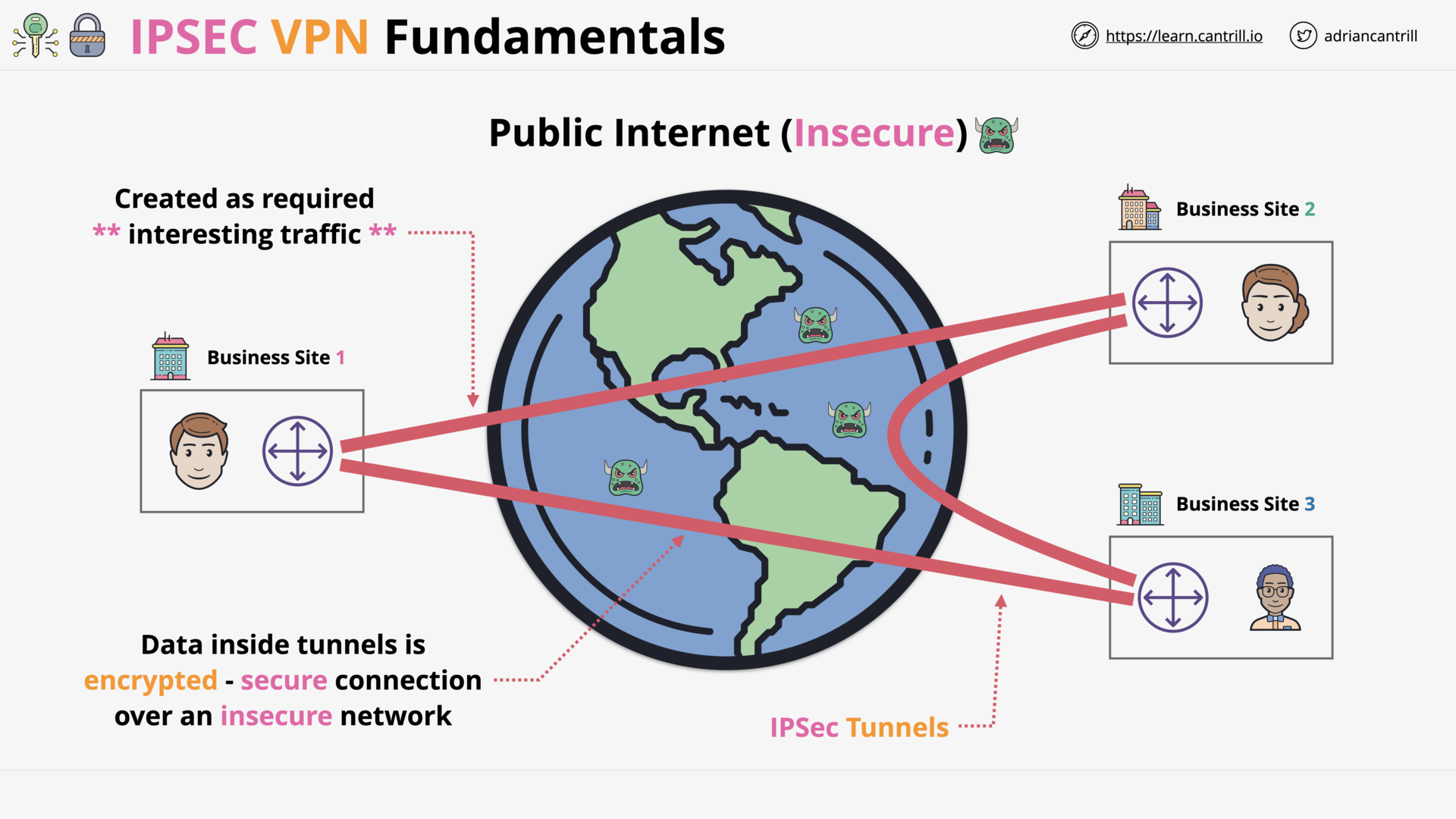
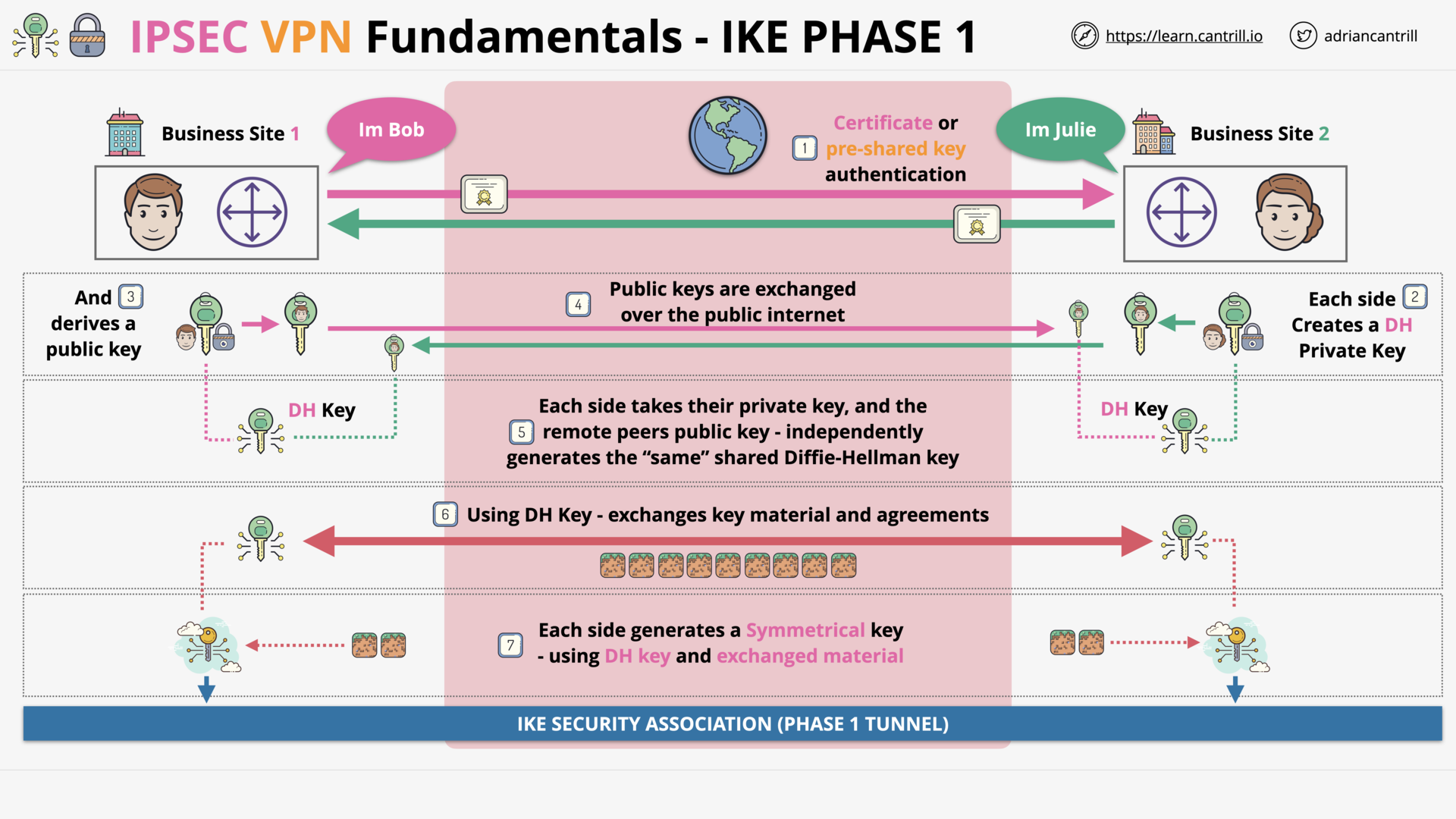
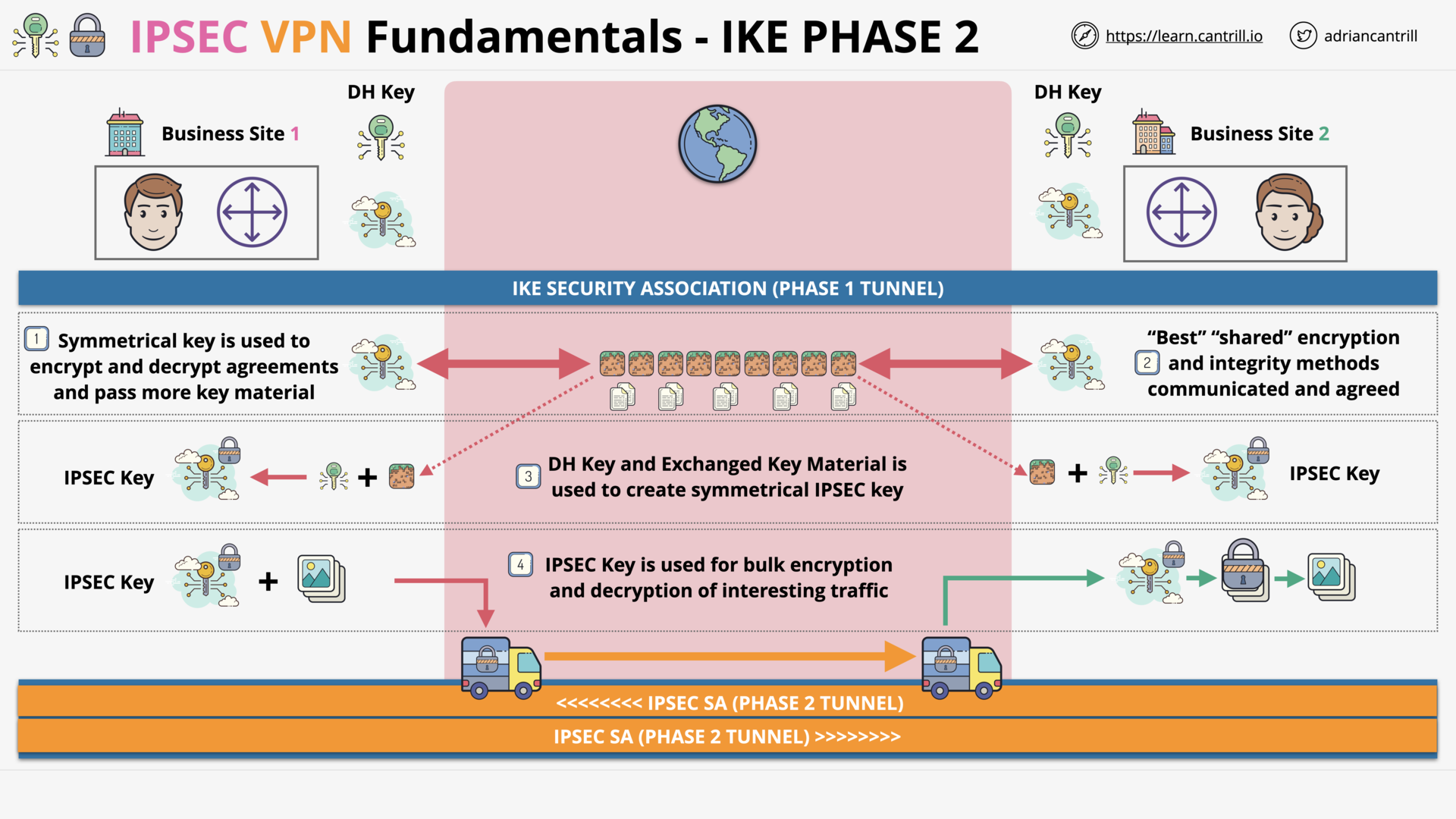
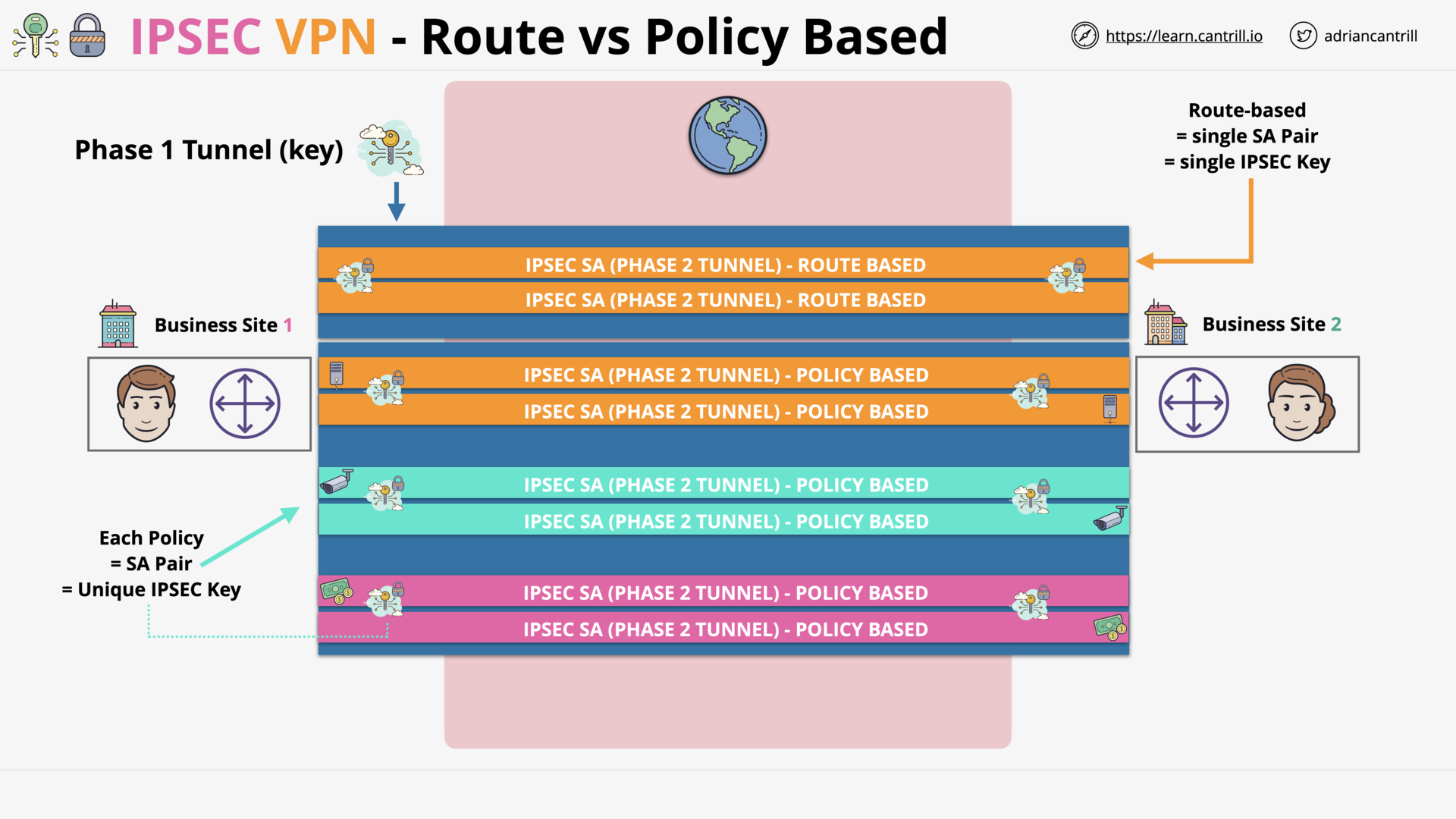
AWS Site-to-Site VPN (18:05)
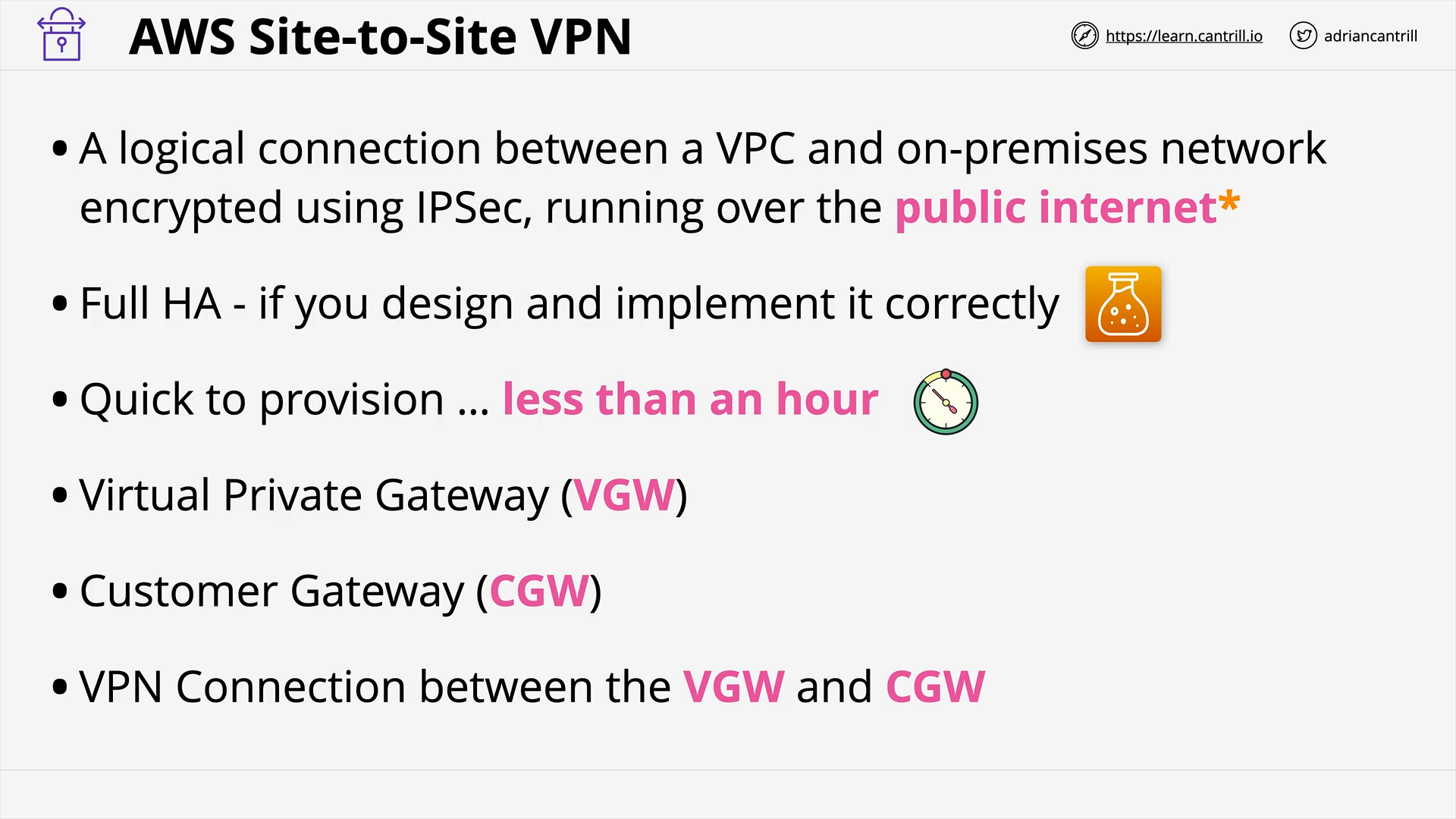 AWS Site-to-Site VPN - Overview
AWS Site-to-Site VPN - Overview
what is a virtual private gateway (vgw)?
A virtual private gateway (VGW) is part of a VPC that provides edge routing for AWS managed VPN connections and AWS Direct Connect connections. You associate an AWS Direct Connect gateway with the virtual private gateway for the VPC. (Source)
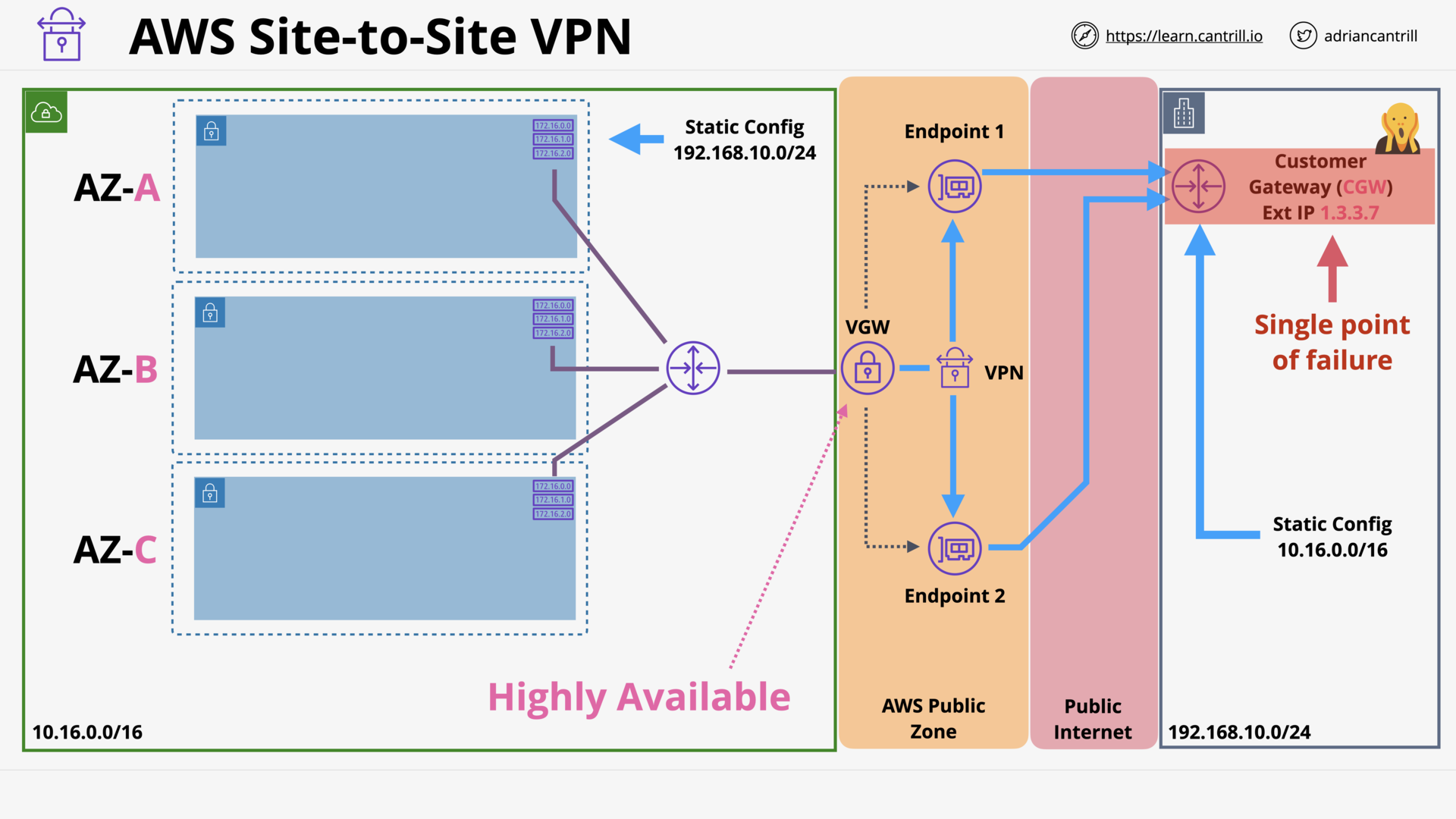 AWS Site-to-Site VPN - Architecture
AWS Site-to-Site VPN - Architecture
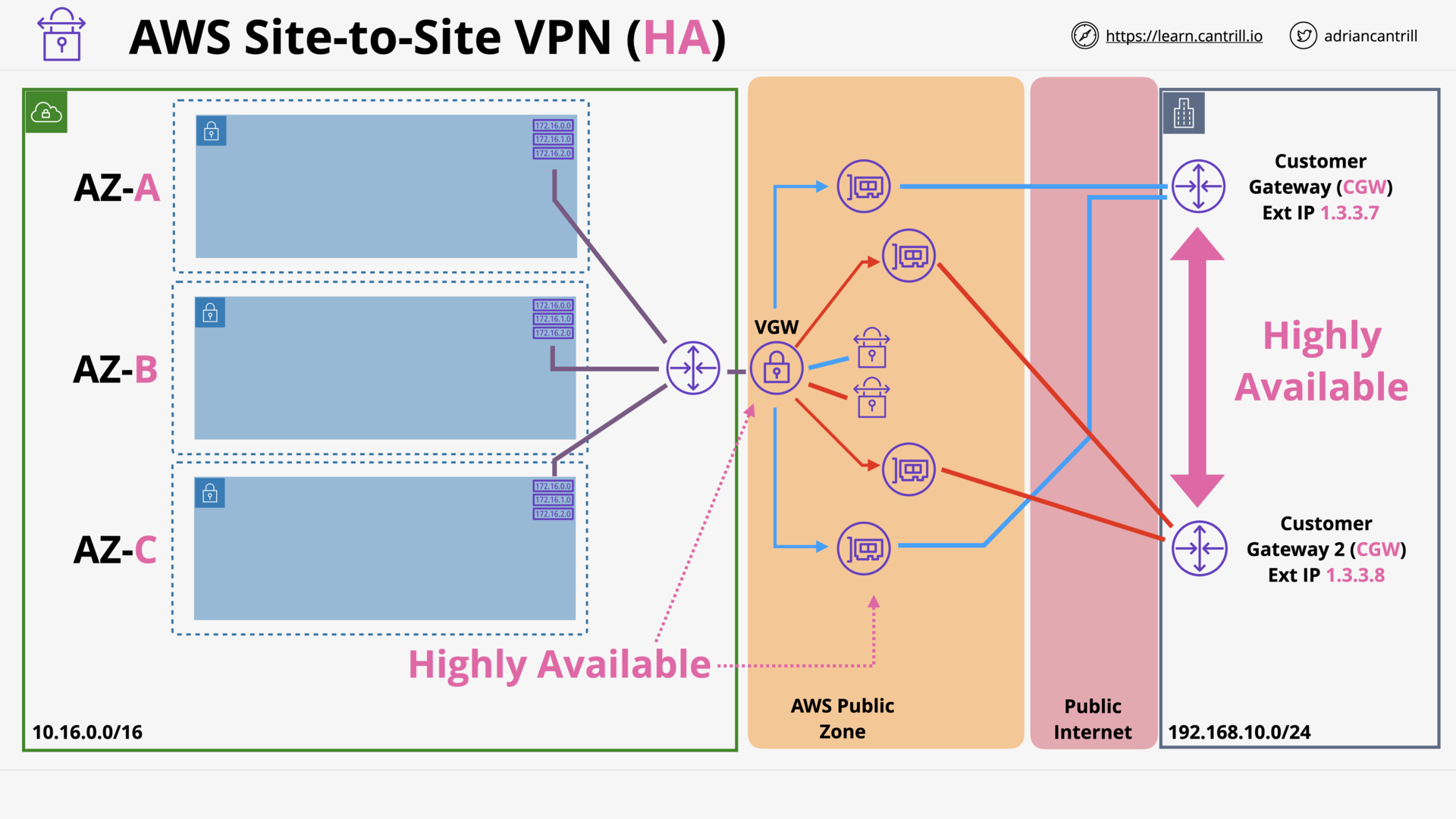 AWS Site-to-Site VPN - Architecture (HA)
AWS Site-to-Site VPN - Architecture (HA)
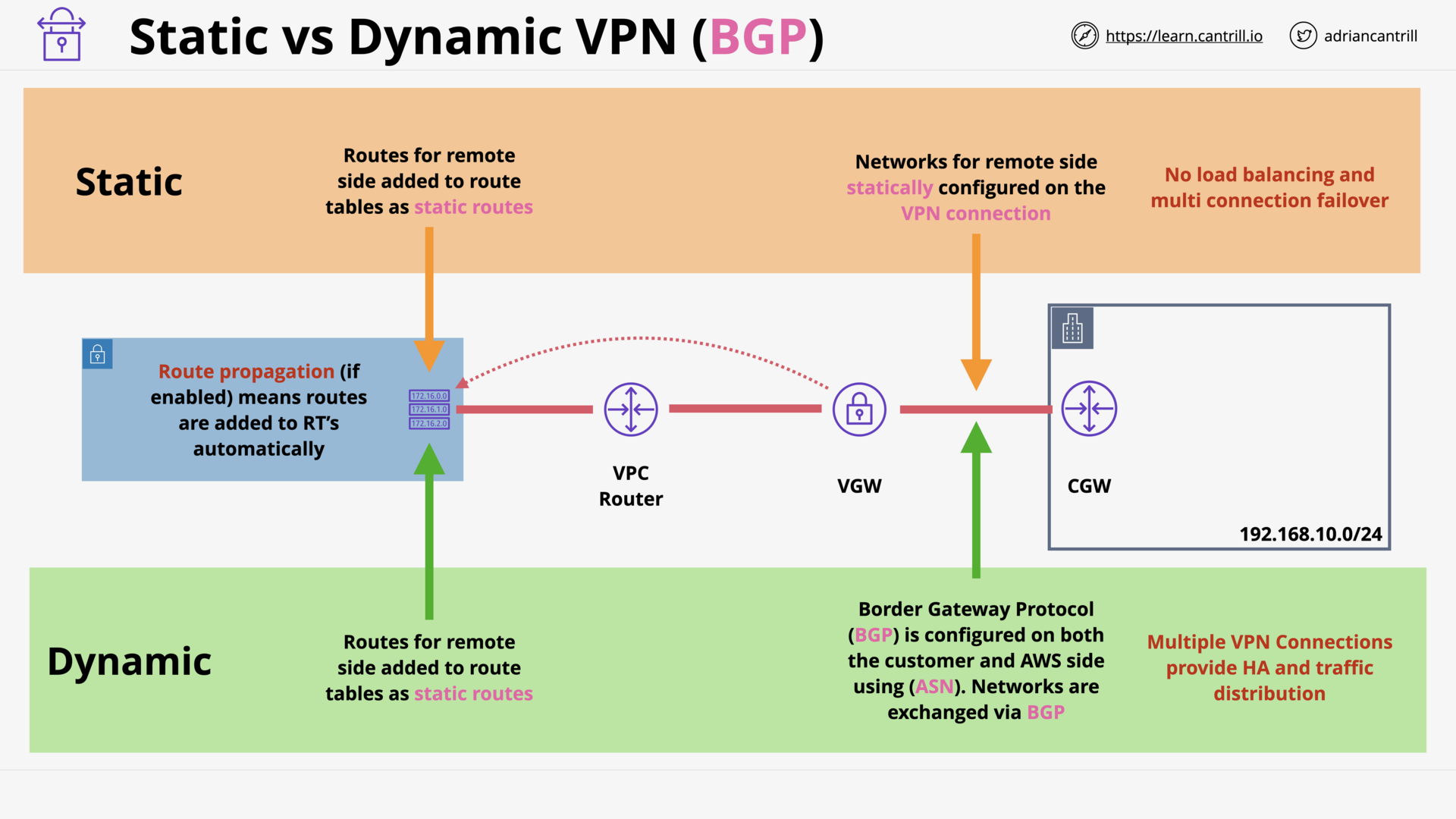 AWS Site-to-Site VPN - Static vs Dynamic VPN (BGP)
AWS Site-to-Site VPN - Static vs Dynamic VPN (BGP)
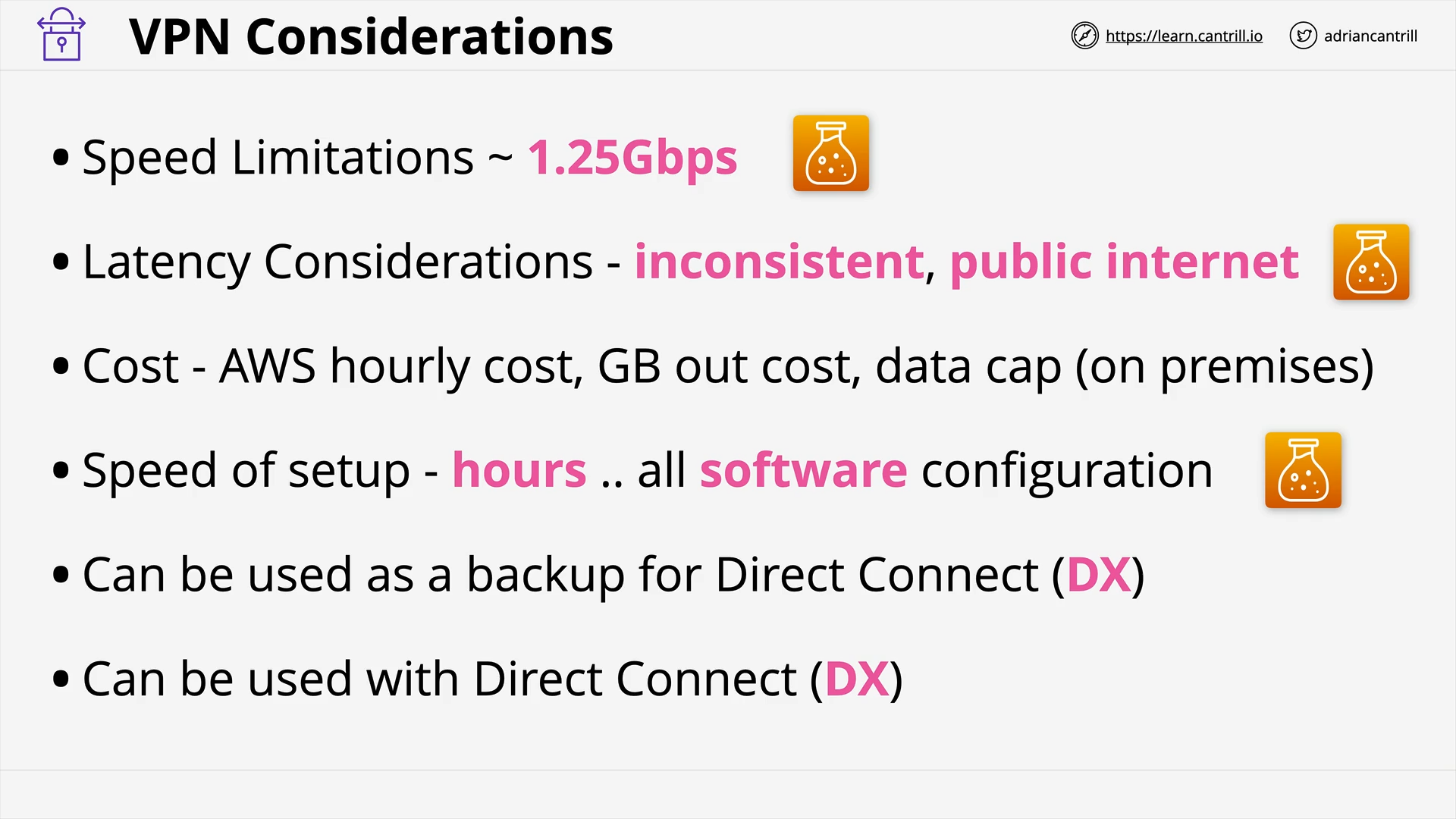 AWS Site-to-Site VPN - Considerations
AWS Site-to-Site VPN - Considerations
[DEMO] Simple Site2Site VPN - STAGE0 - SETUP (4:52)
[DEMO] Simple Site2Site VPN - STAGE1 - AWS VPN (10:01)
[DEMO] Simple Site2Site VPN - STAGE2 - onprep pfSense Config (17:09)
[DEMO] Simple Site2Site VPN - STAGE3 - Routing & Security (10:29)
[DEMO] Simple Site2Site VPN - STAGE4 - Testing (5:42)
[DEMO] Simple Site2Site VPN - STAGE5 - Cleanup (1:50)
AWS Direct Connect (DX) Concepts (9:37)
_Concepts__learn.c_%E2%80%94_Firefox_De.png) DX - Concepts
DX - Concepts
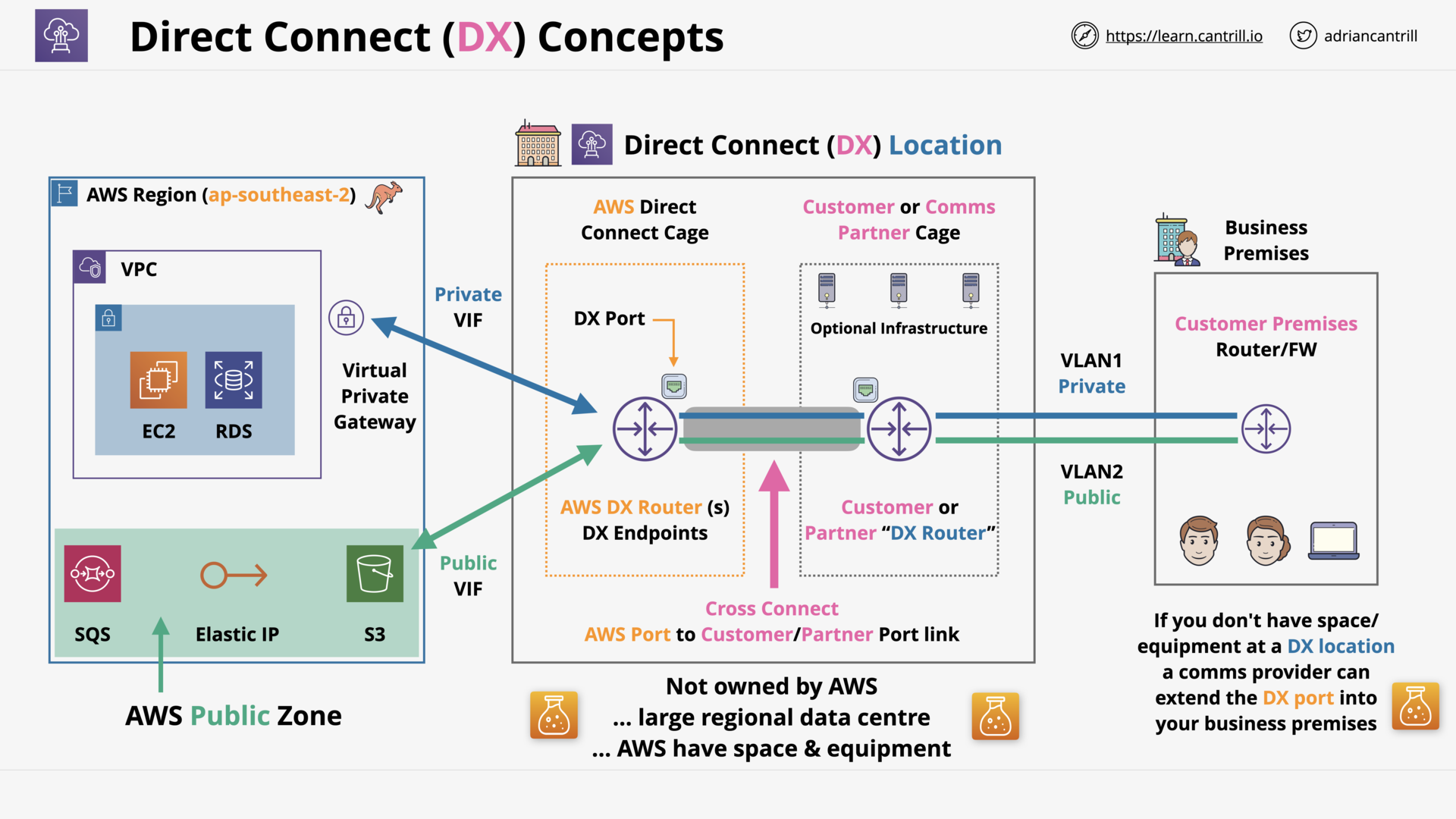 DX - Architecture
DX - Architecture
AWS Direct Connect (DX) Resilience (13:50)
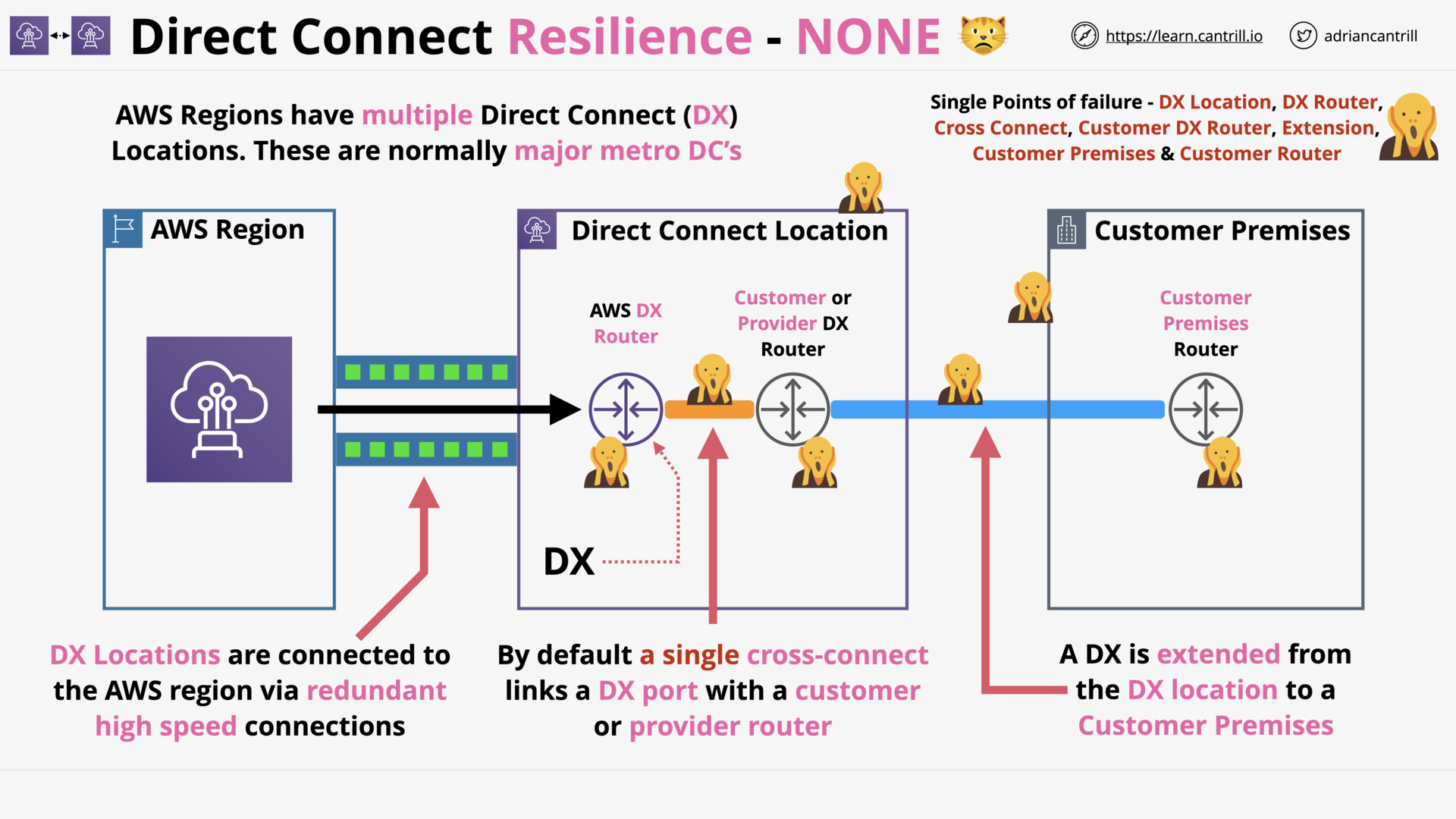 DX Resilience - NONE 😭
DX Resilience - NONE 😭
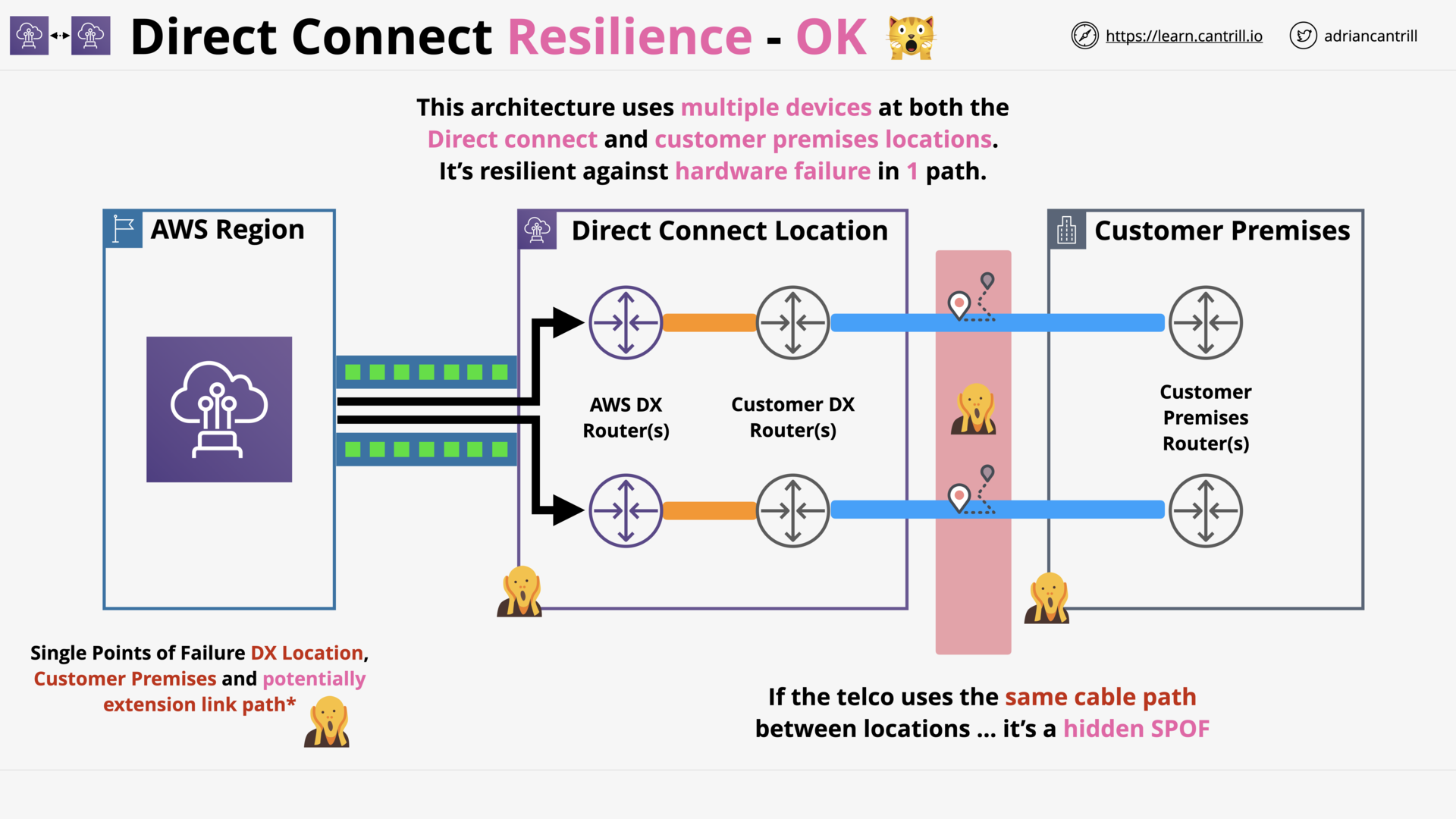 DX Resilience - OK ⭐
DX Resilience - OK ⭐
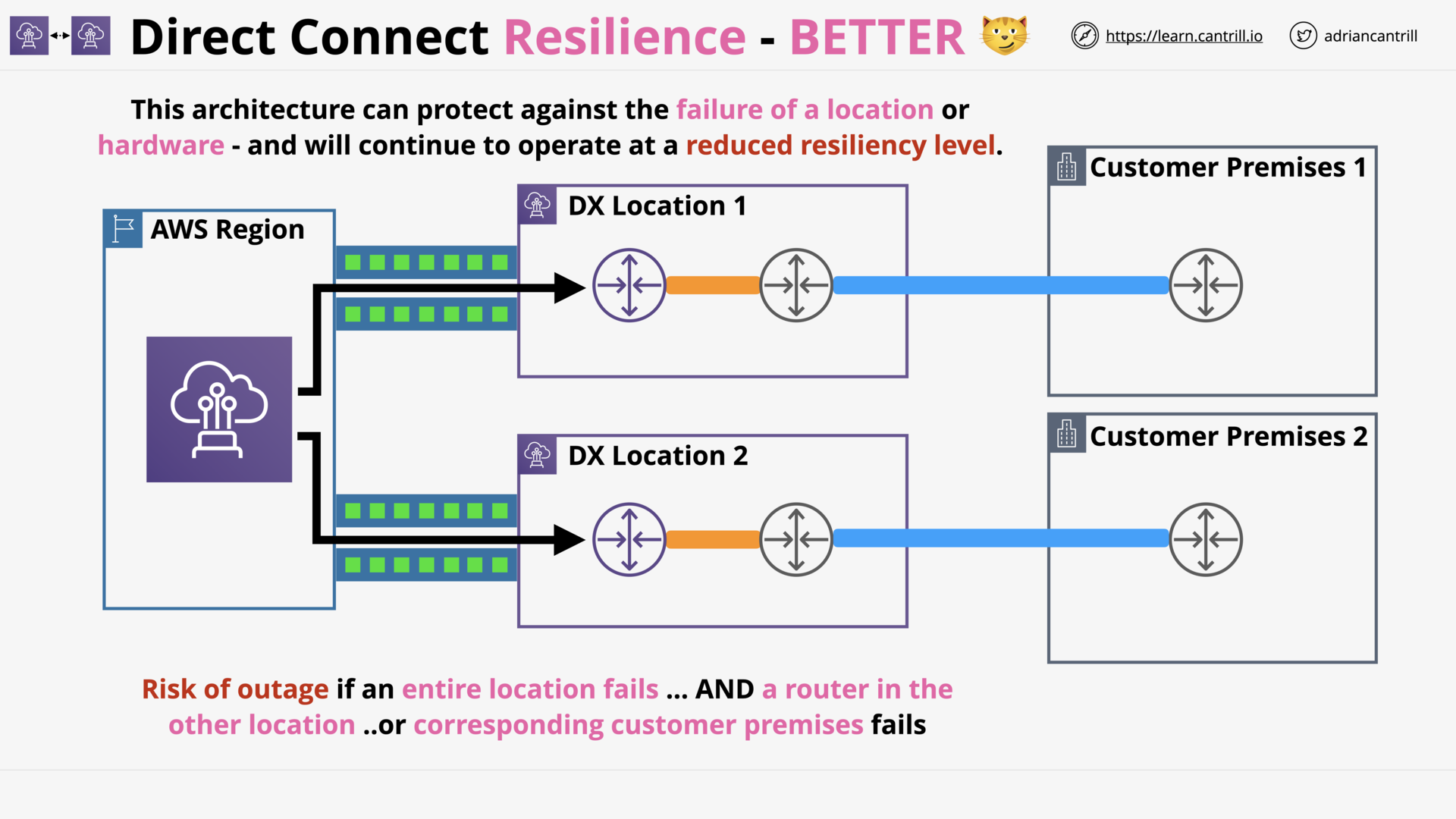 DX Resilience - BETTER ⭐⭐
DX Resilience - BETTER ⭐⭐
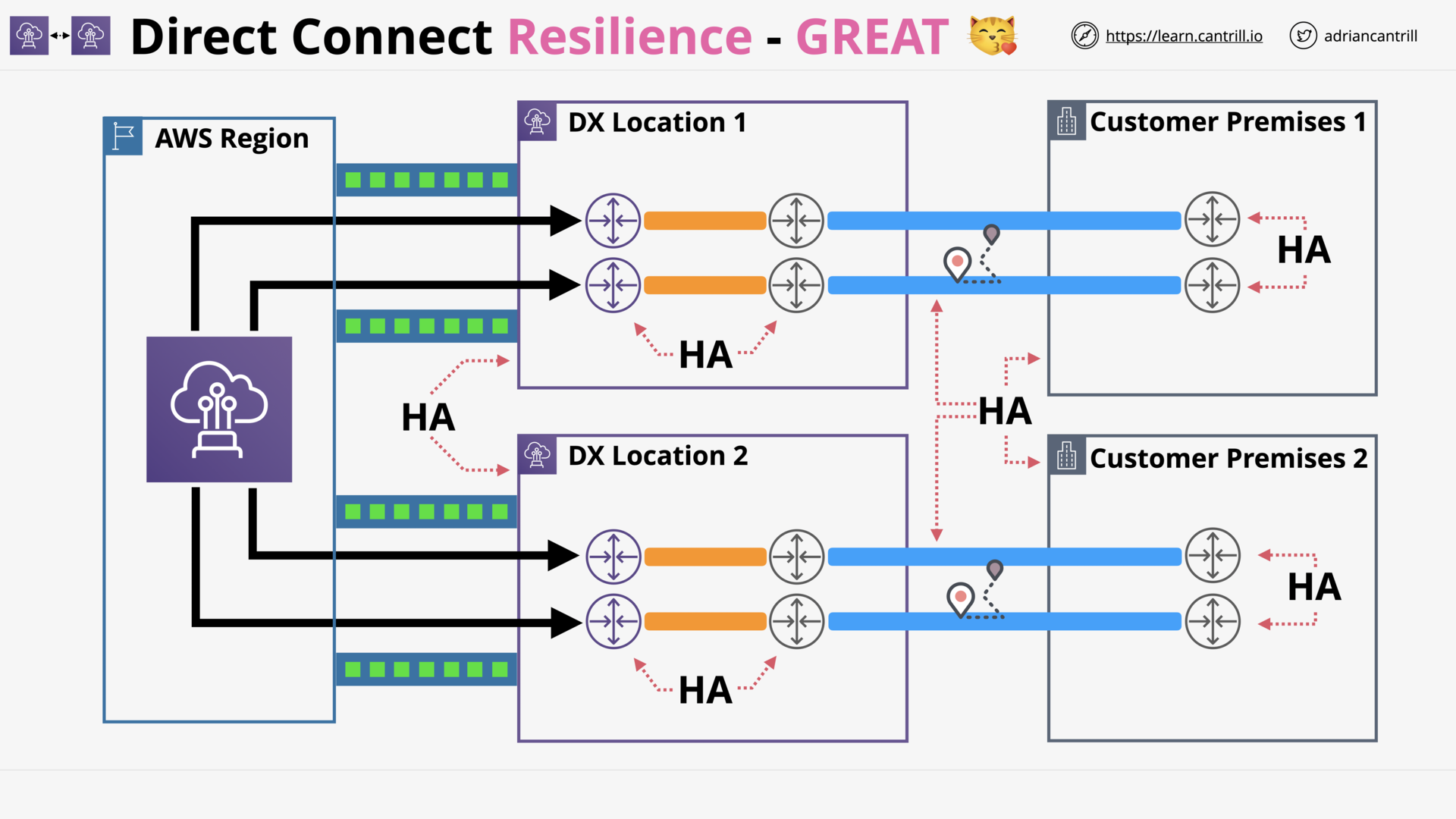 DX Resilience - GREAT ⭐⭐⭐
DX Resilience - GREAT ⭐⭐⭐
Direct Connect (DX) - Public VIF + VPN (Encryption) (6:43)
_-_Public_VIF_+_VPN_(Encryption.png) DX - Public VIF + VPN
DX - Public VIF + VPN
_-_Public_VIF_+_VPN_(Encryption.png) DX - Public VIF + VPN
DX - Public VIF + VPN
what is a virtual interface (vif)?
For AWS Direct Connection, a virtual interface (VIF) is necessary to access AWS services, and is either public or private.
(Source)
Transit Gateway (TGW) (10:26)
 TGW - Overview
TGW - Overview
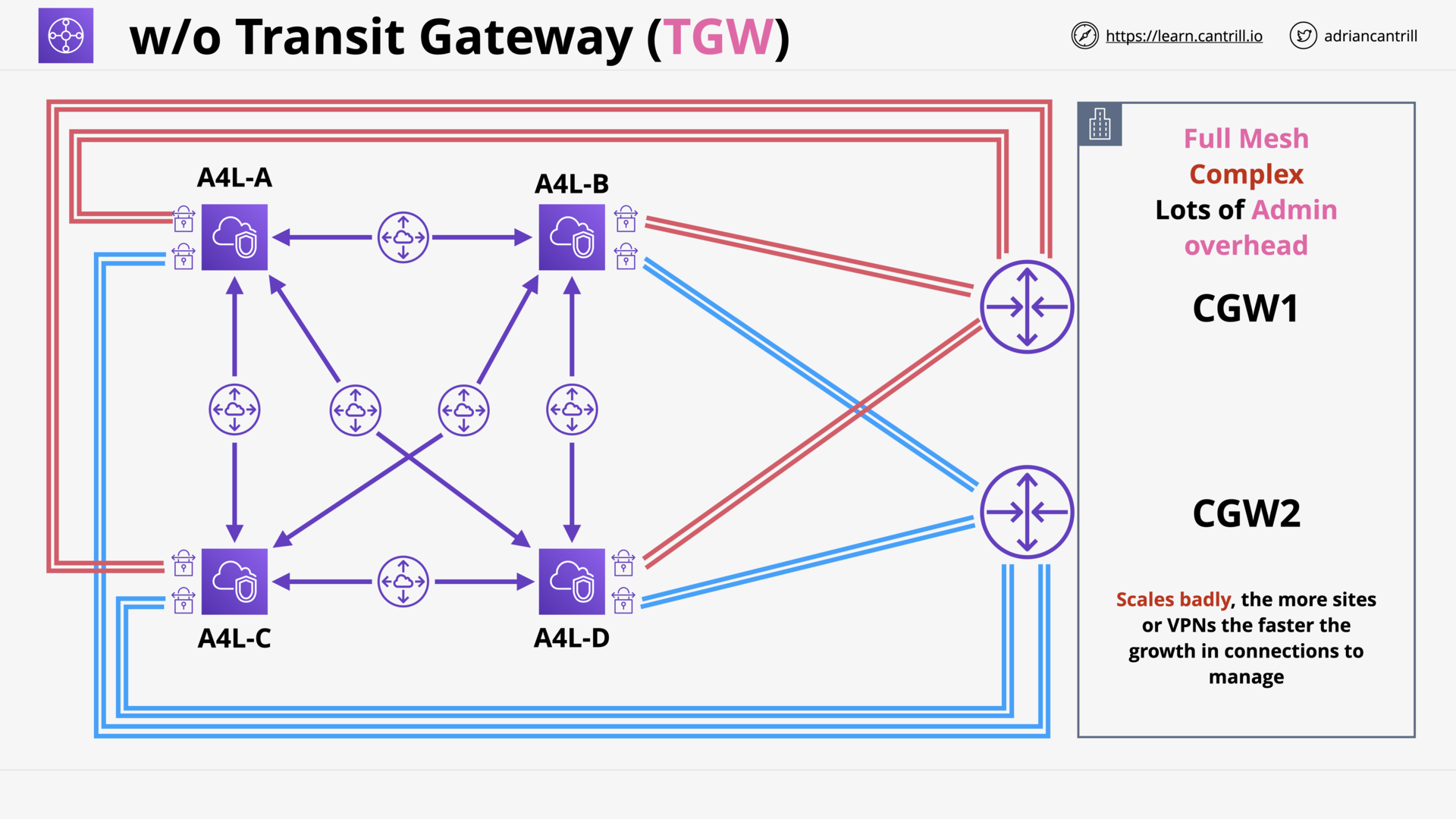 TGW - The Problem
TGW - The Problem
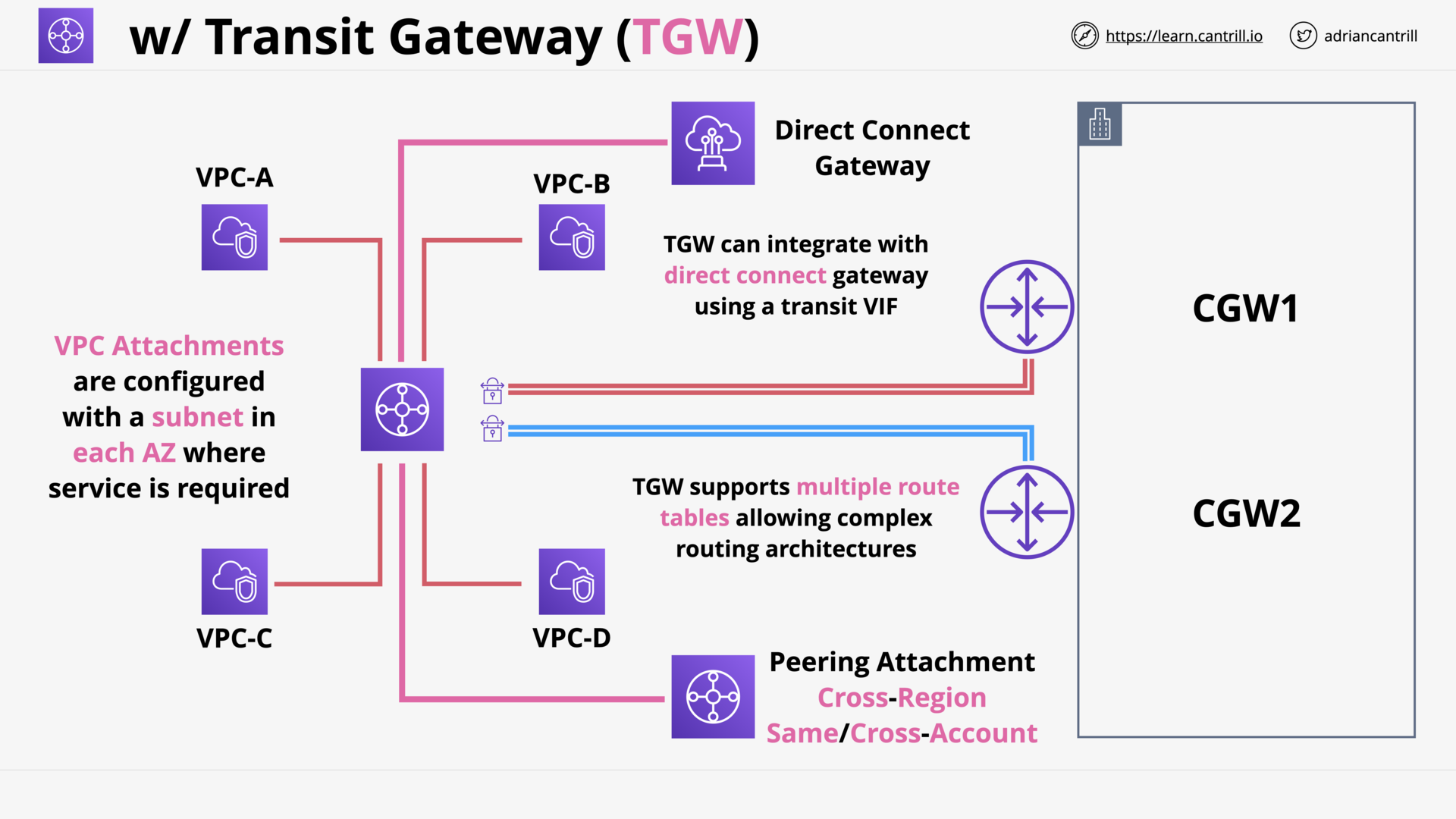 TGW - The Solution
TGW - The Solution
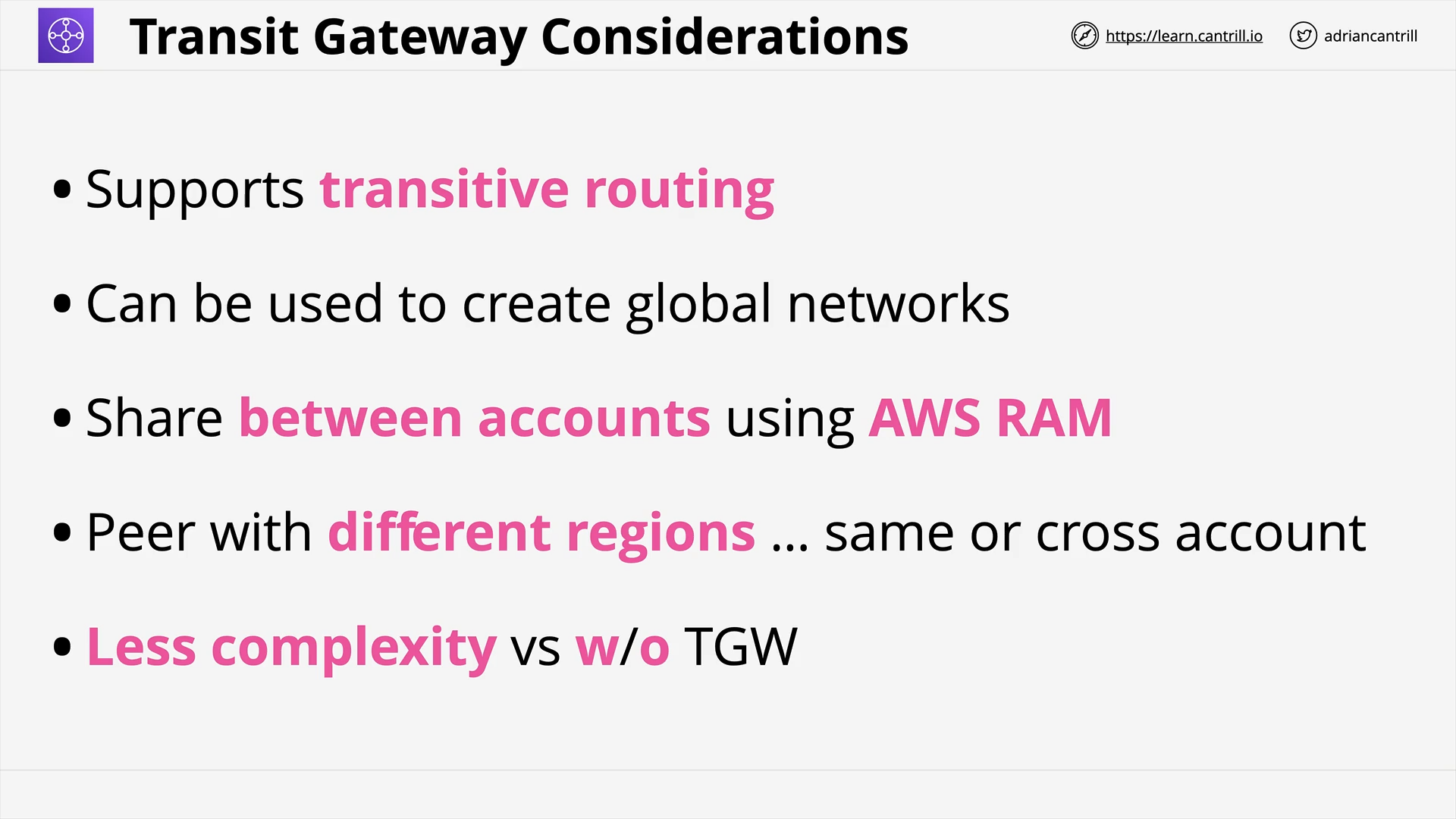 TGW - Considerations
TGW - Considerations
Storage Gateway - Volume Gateway (14:15)
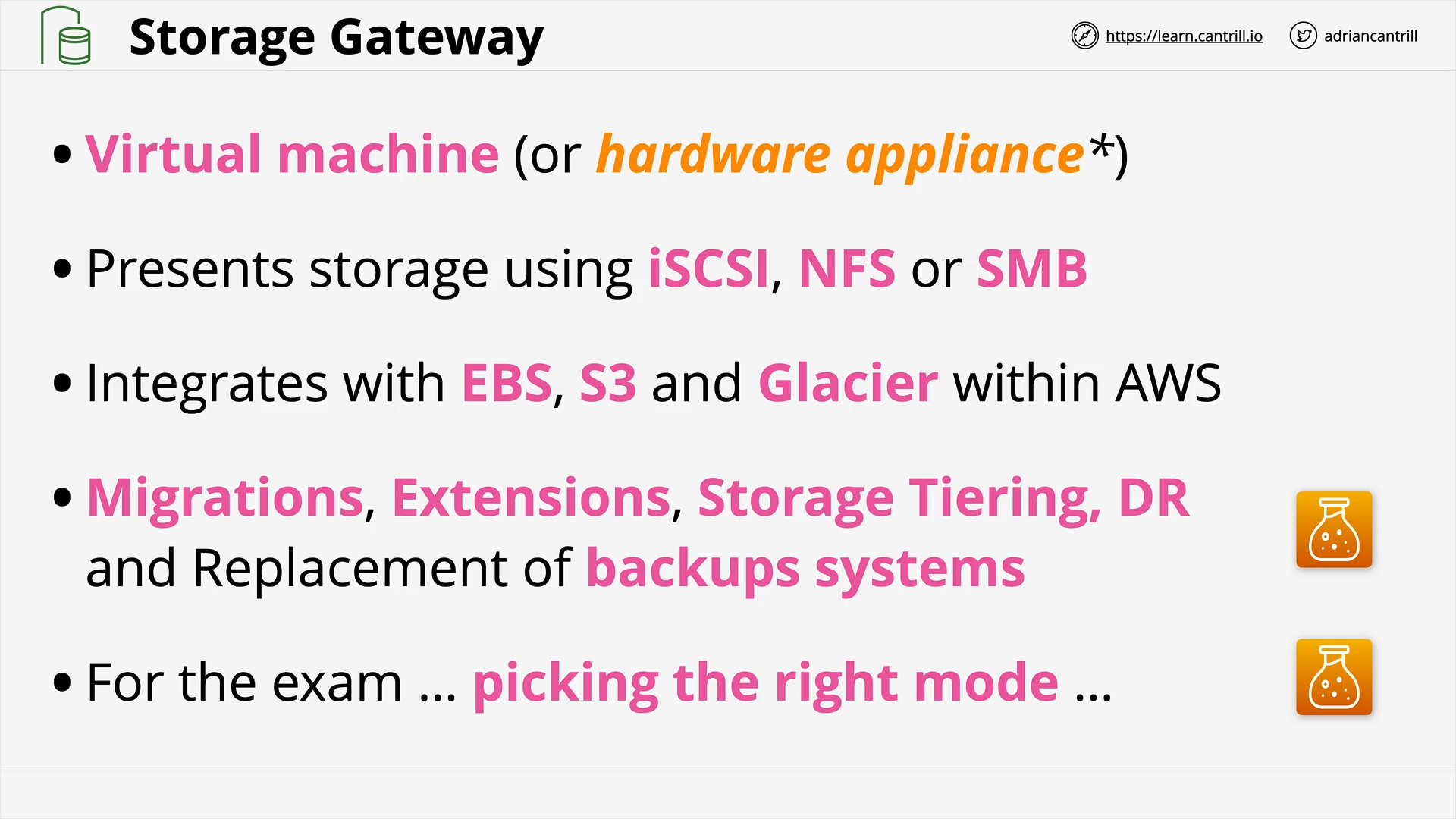 Storage Gateway - Overview
Storage Gateway - Overview
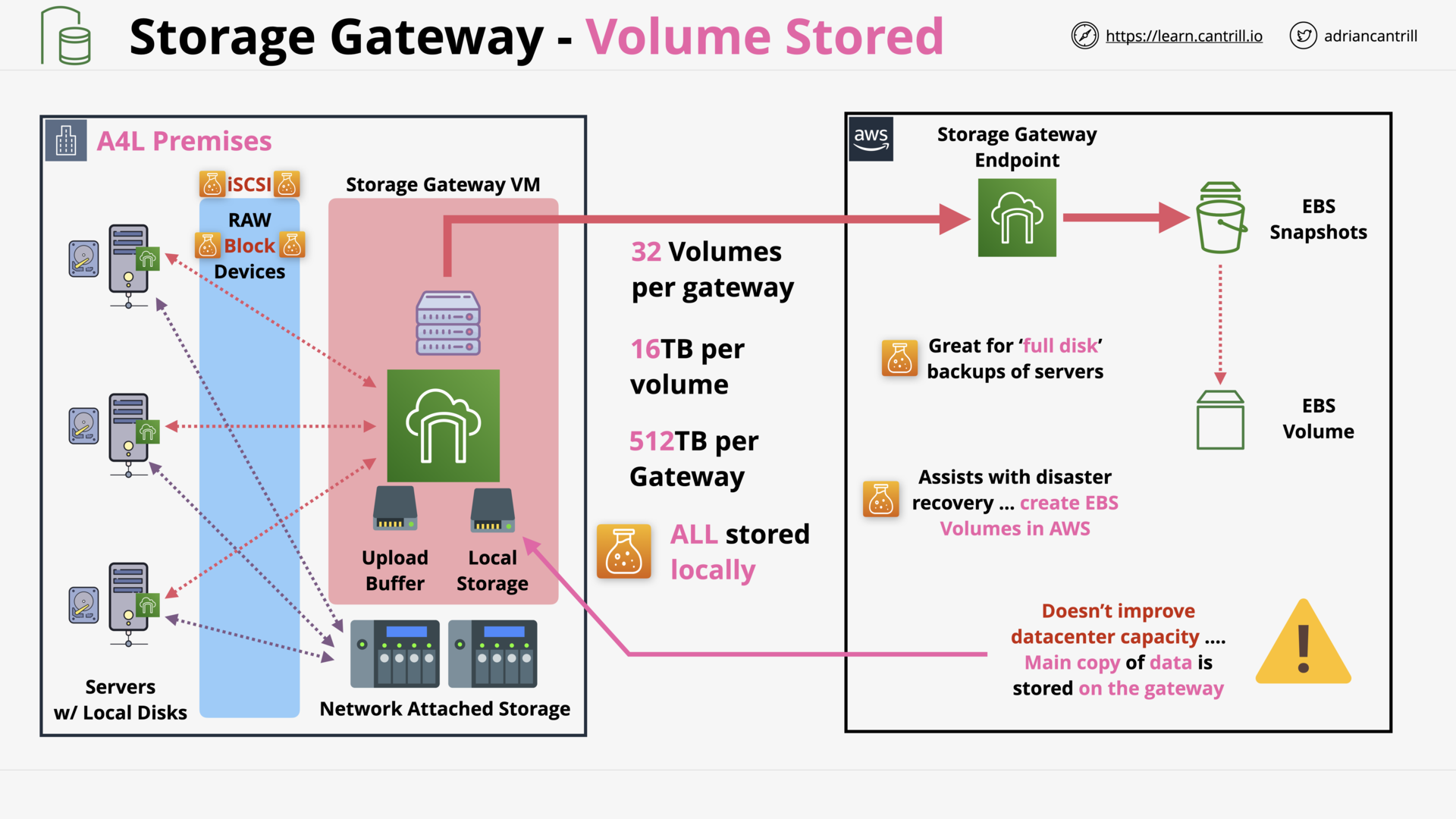 Storage Gateway - Volume Gateway - Stored Mode: Data stored primary on-premise 👈 Backup, DR
Storage Gateway - Volume Gateway - Stored Mode: Data stored primary on-premise 👈 Backup, DR
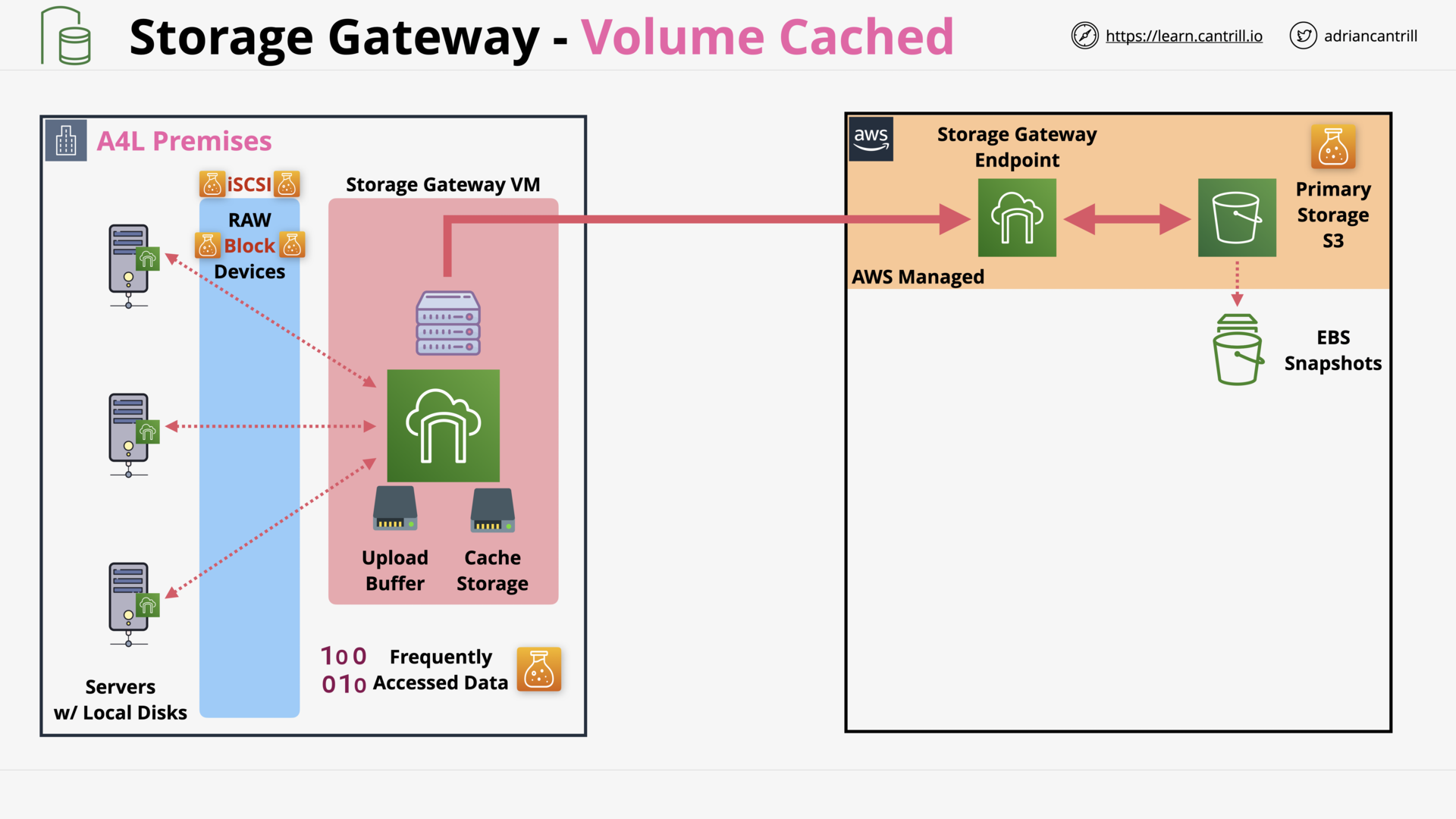 Storage Gateway - Volume Gateway - Cached Mode
Storage Gateway - Volume Gateway - Cached Mode
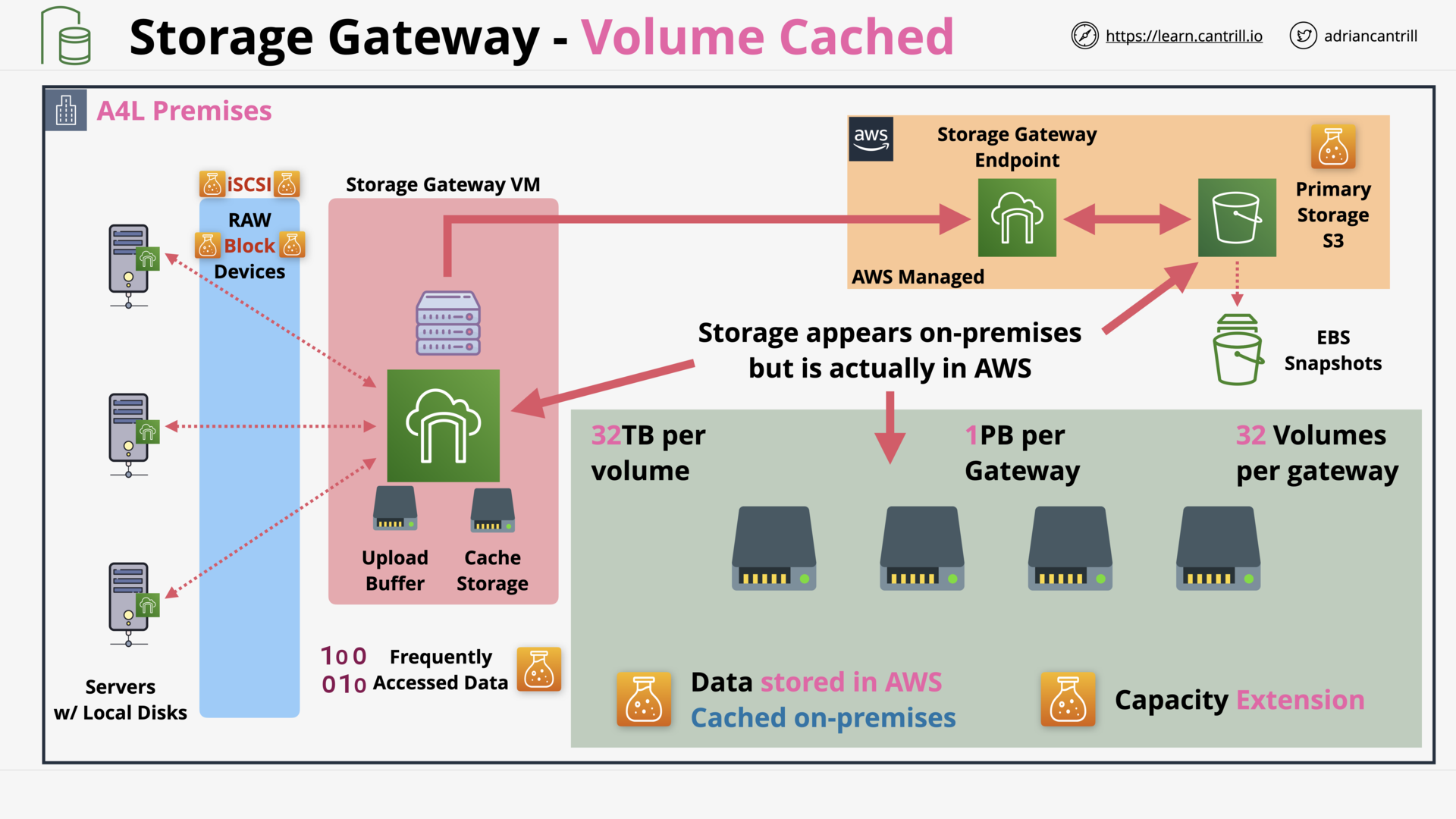 Storage Gateway - Volume Gateway - Cached Mode: Data stored in AWS, cached on-premises 👈 Capacity Expand
Storage Gateway - Volume Gateway - Cached Mode: Data stored in AWS, cached on-premises 👈 Capacity Expand
Storage Gateway - Tape Gateway - virtual tape library (VTL) (12:11)
__learn.c_%E2%80%94_Firefox_De.png) Tape-based Backup - Overview
Tape-based Backup - Overview
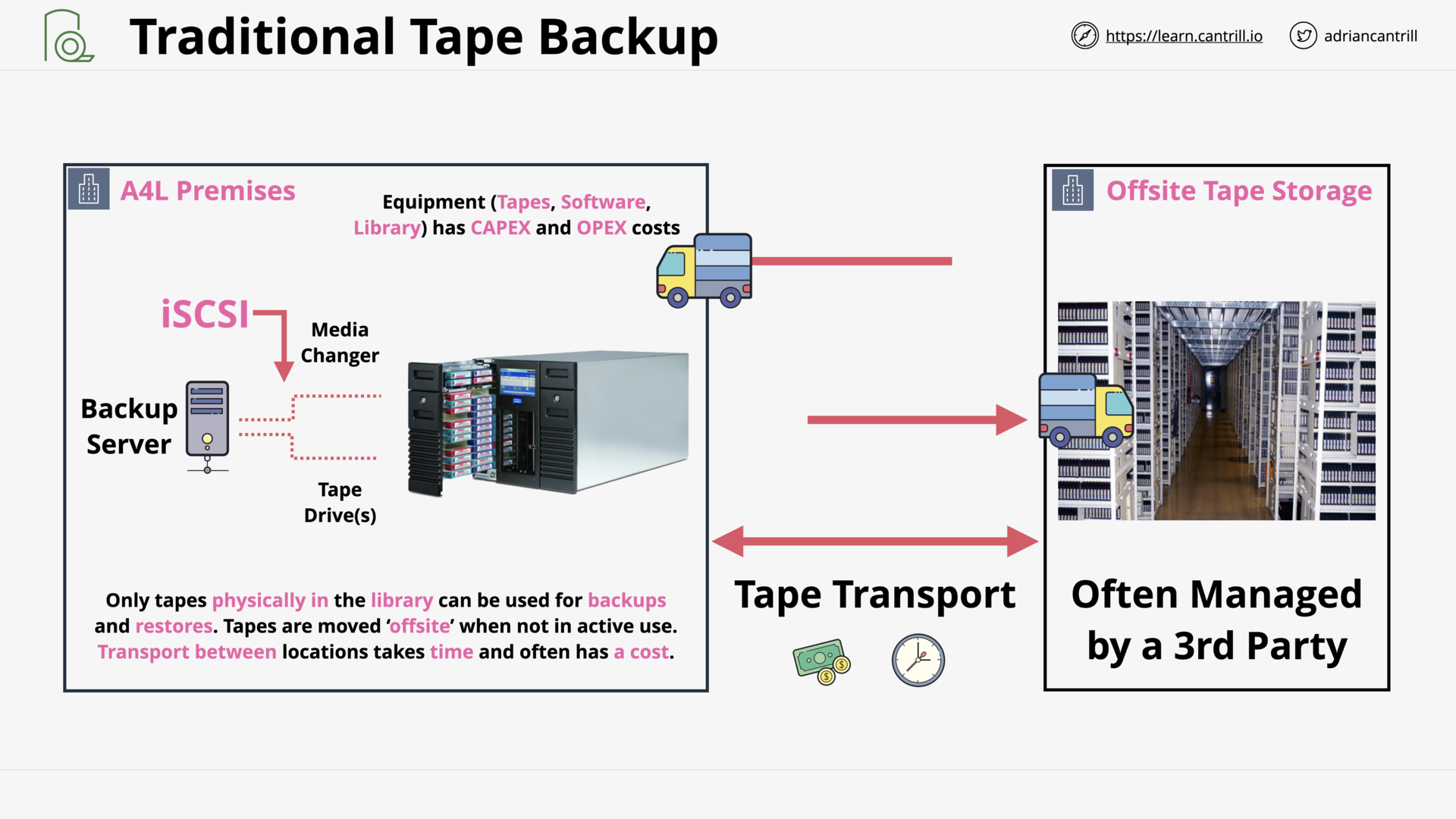 Tape-based Backup - Architecture
Tape-based Backup - Architecture
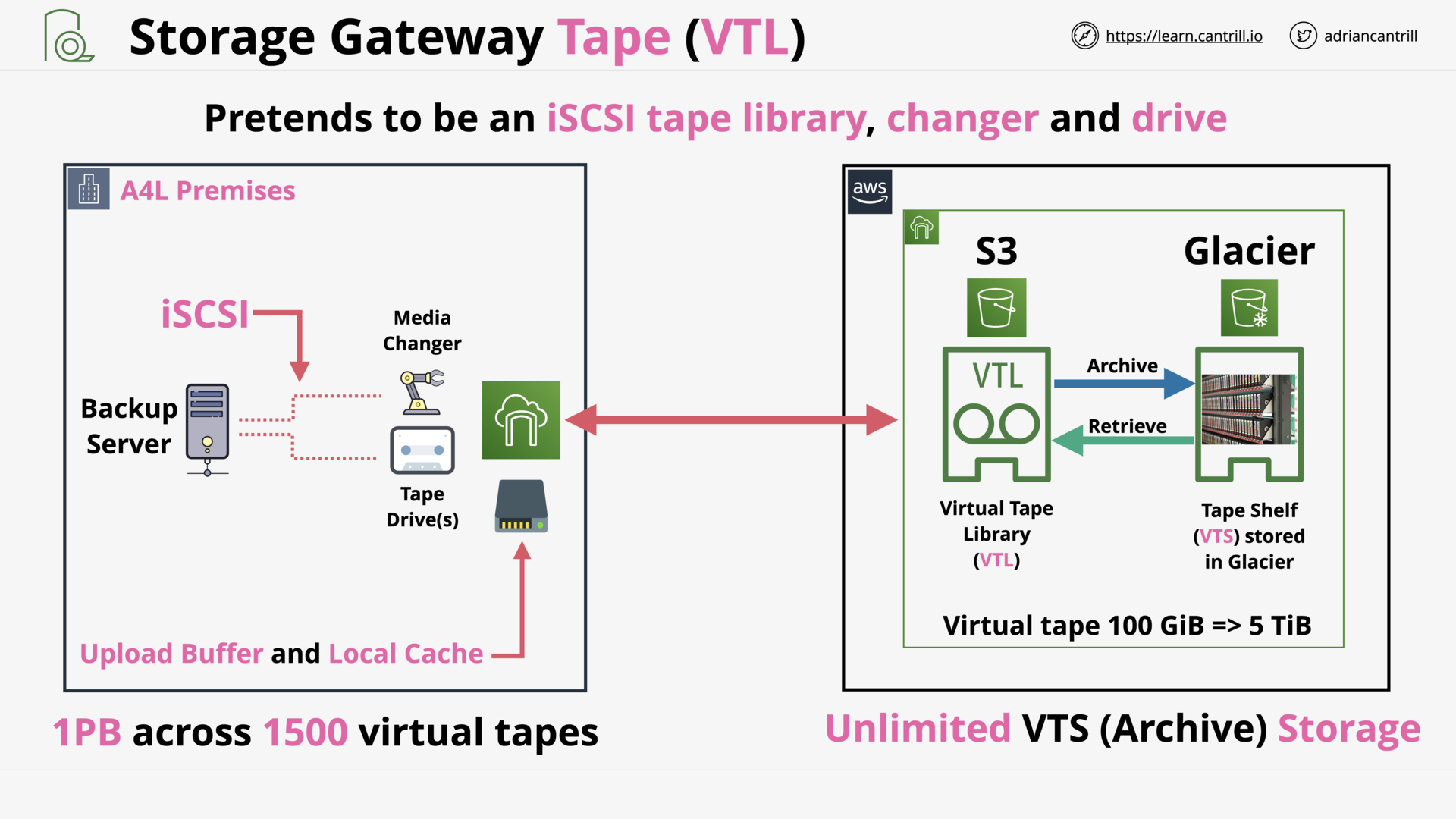 Storage Gateway - Tape Gateway
Storage Gateway - Tape Gateway
Storage Gateway - File Gateway (12:15)
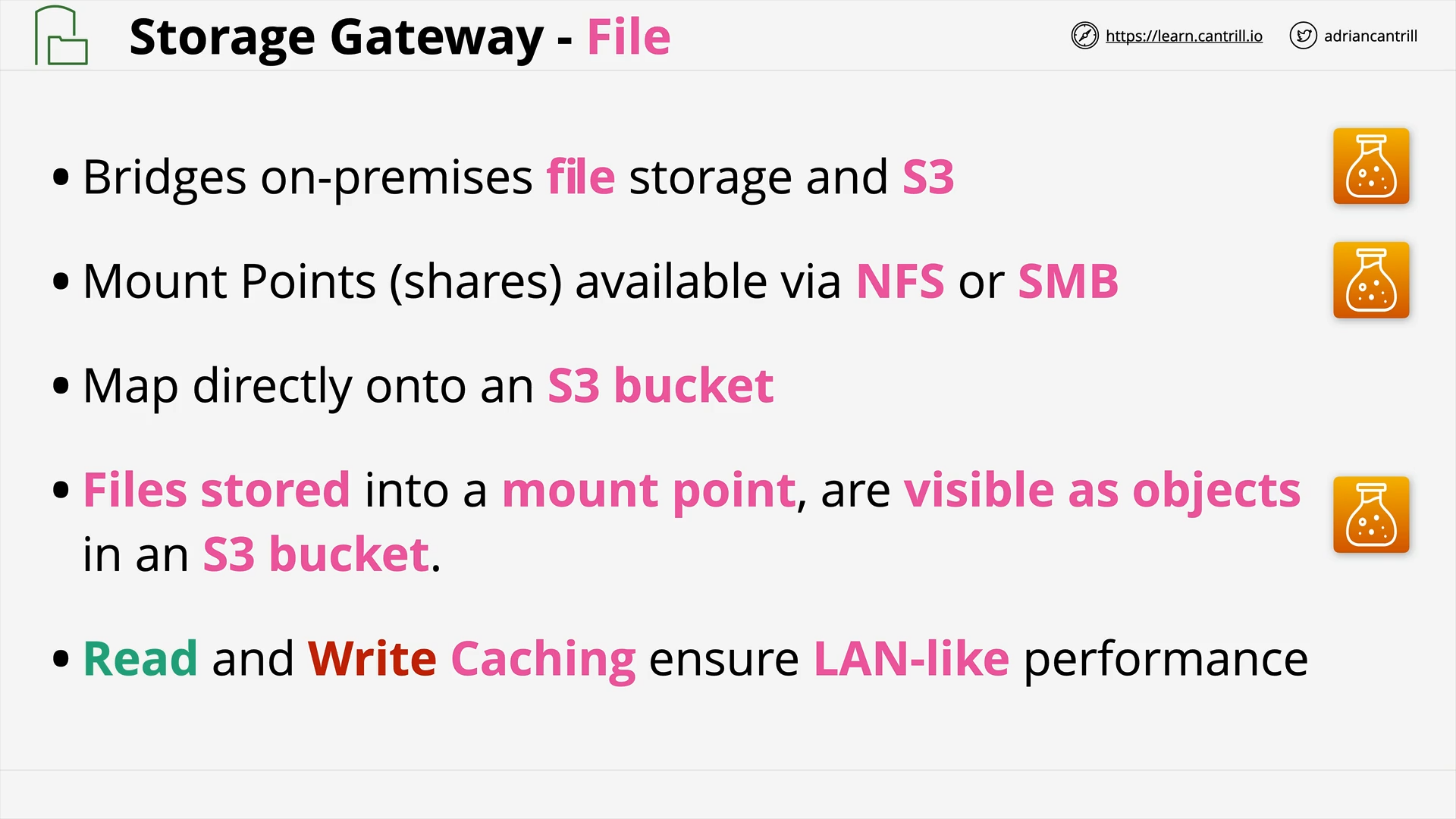 Storage Gateway - File Gateway - Overview
Storage Gateway - File Gateway - Overview
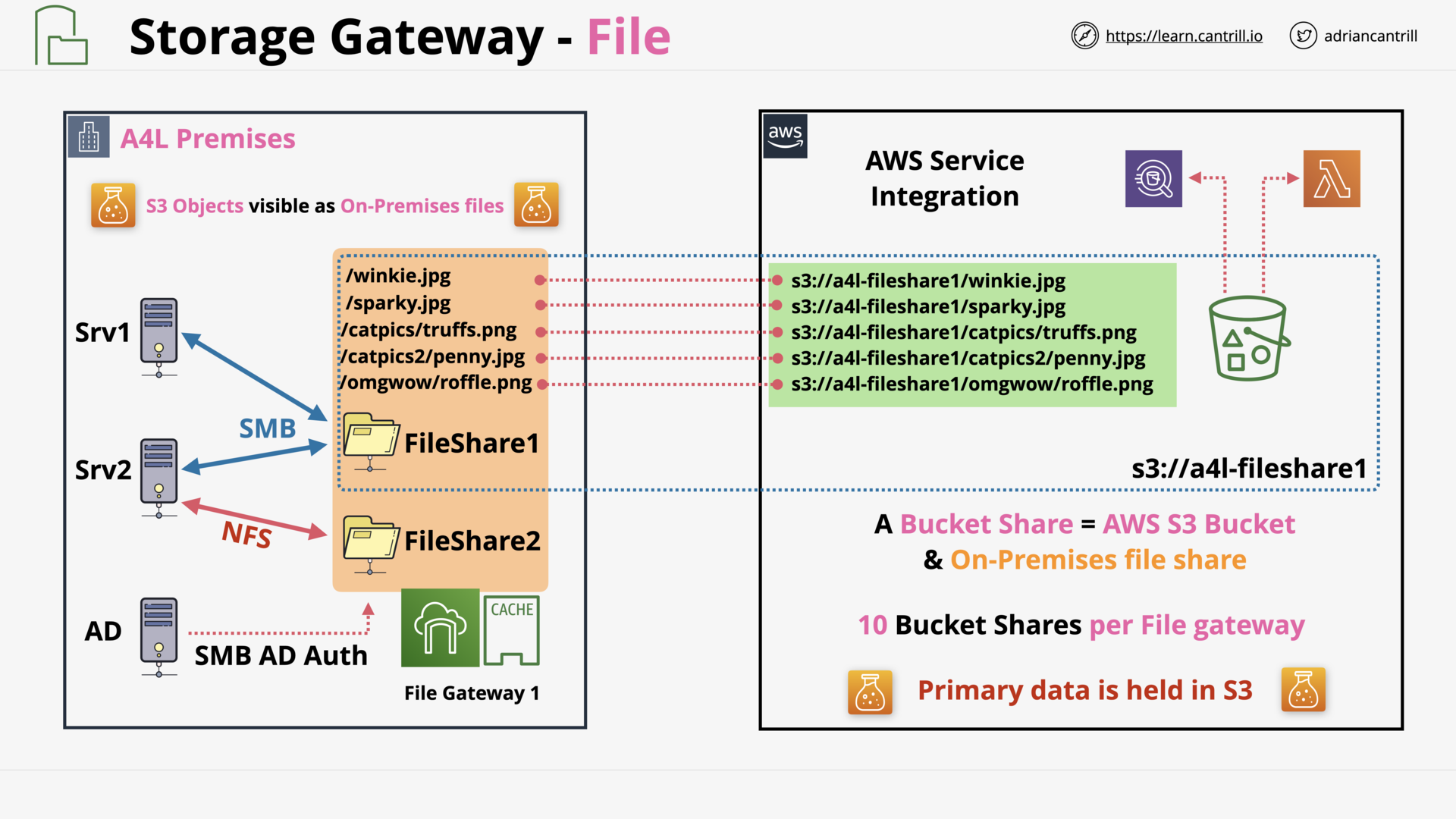 Storage Gateway - File Gateway - Architecture
Storage Gateway - File Gateway - Architecture
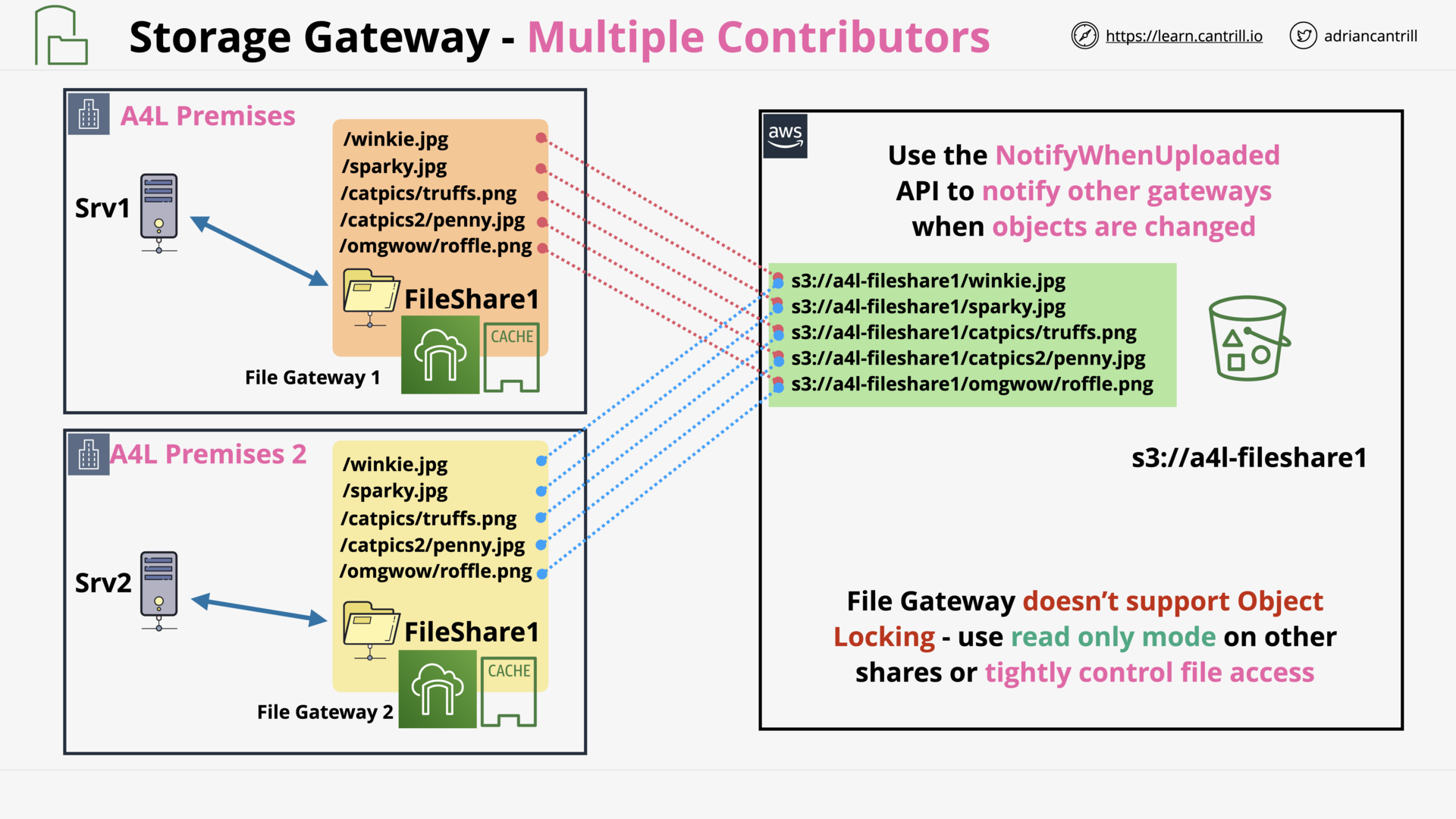 Storage Gateway - File Gateway - Multiple Contributors
Storage Gateway - File Gateway - Multiple Contributors
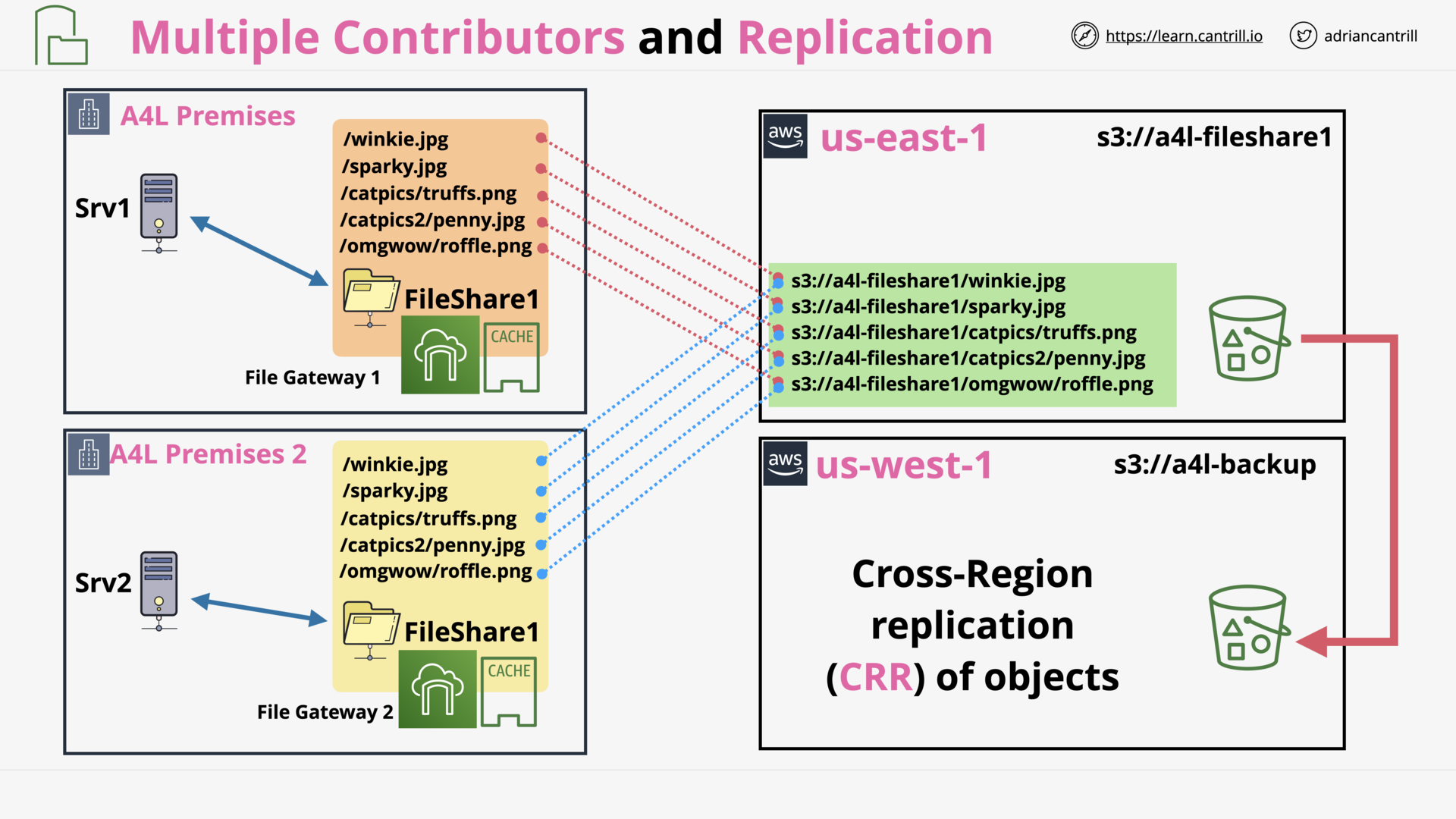 Storage Gateway - File Gateway - Multiple Contributors & Replication
Storage Gateway - File Gateway - Multiple Contributors & Replication
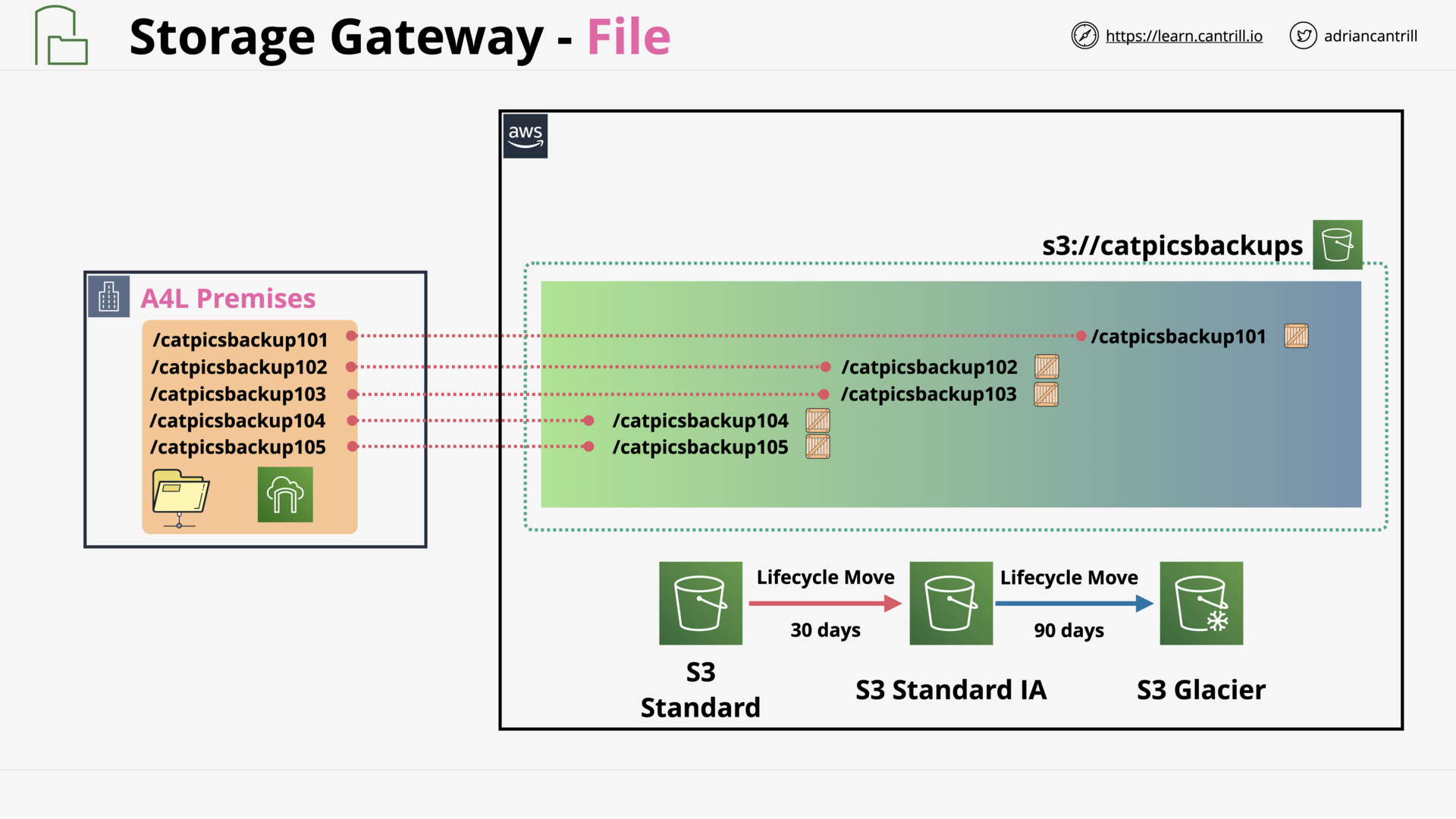 Storage Gateway - File Gateway - S3 Storage Classes
Storage Gateway - File Gateway - S3 Storage Classes
Snowball / Edge / Snowmobile [NEW VERSION COMING SOON] (10:47)
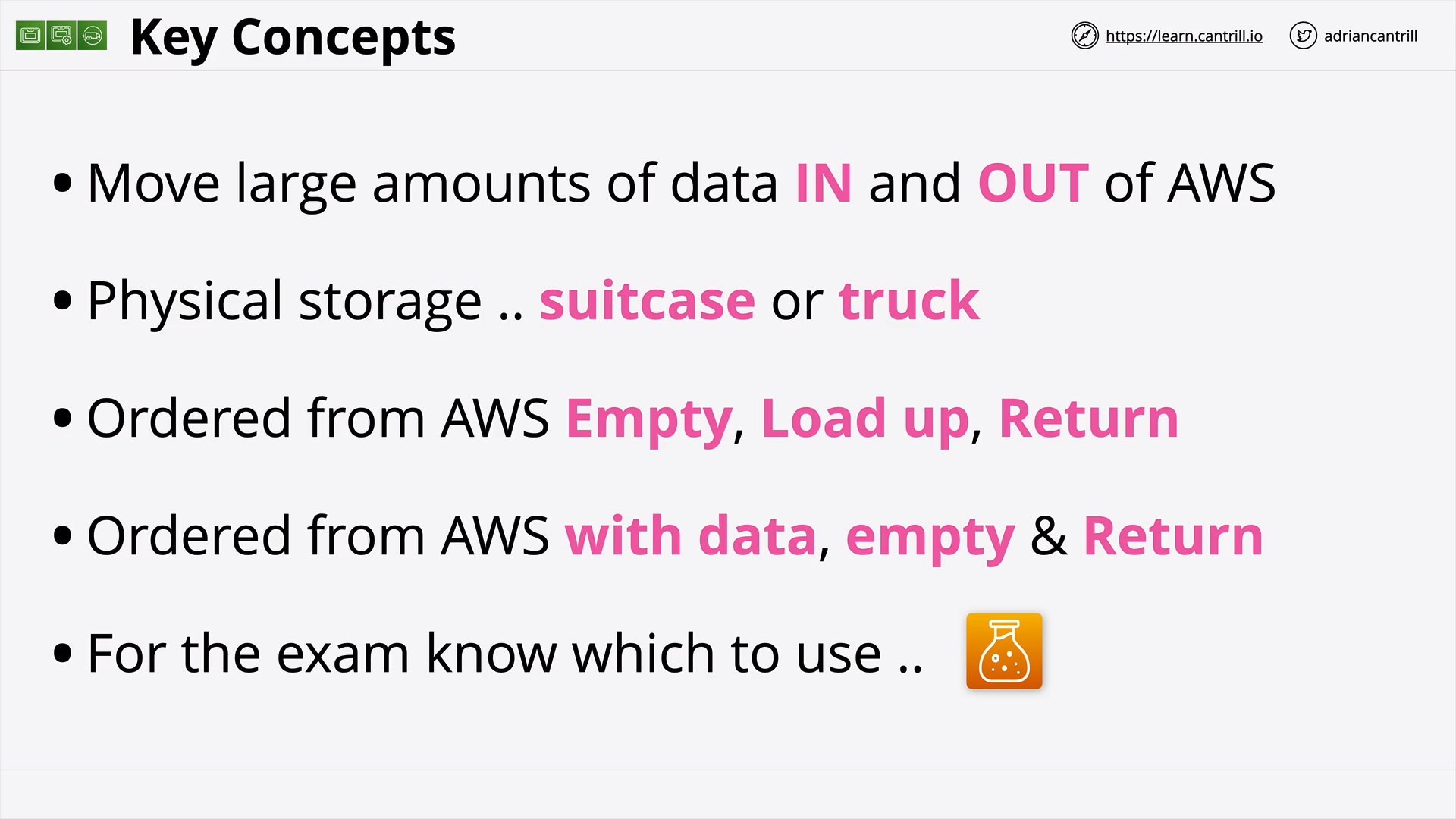 Snowball / Edge / Snowmobile - Key Concepts
Snowball / Edge / Snowmobile - Key Concepts
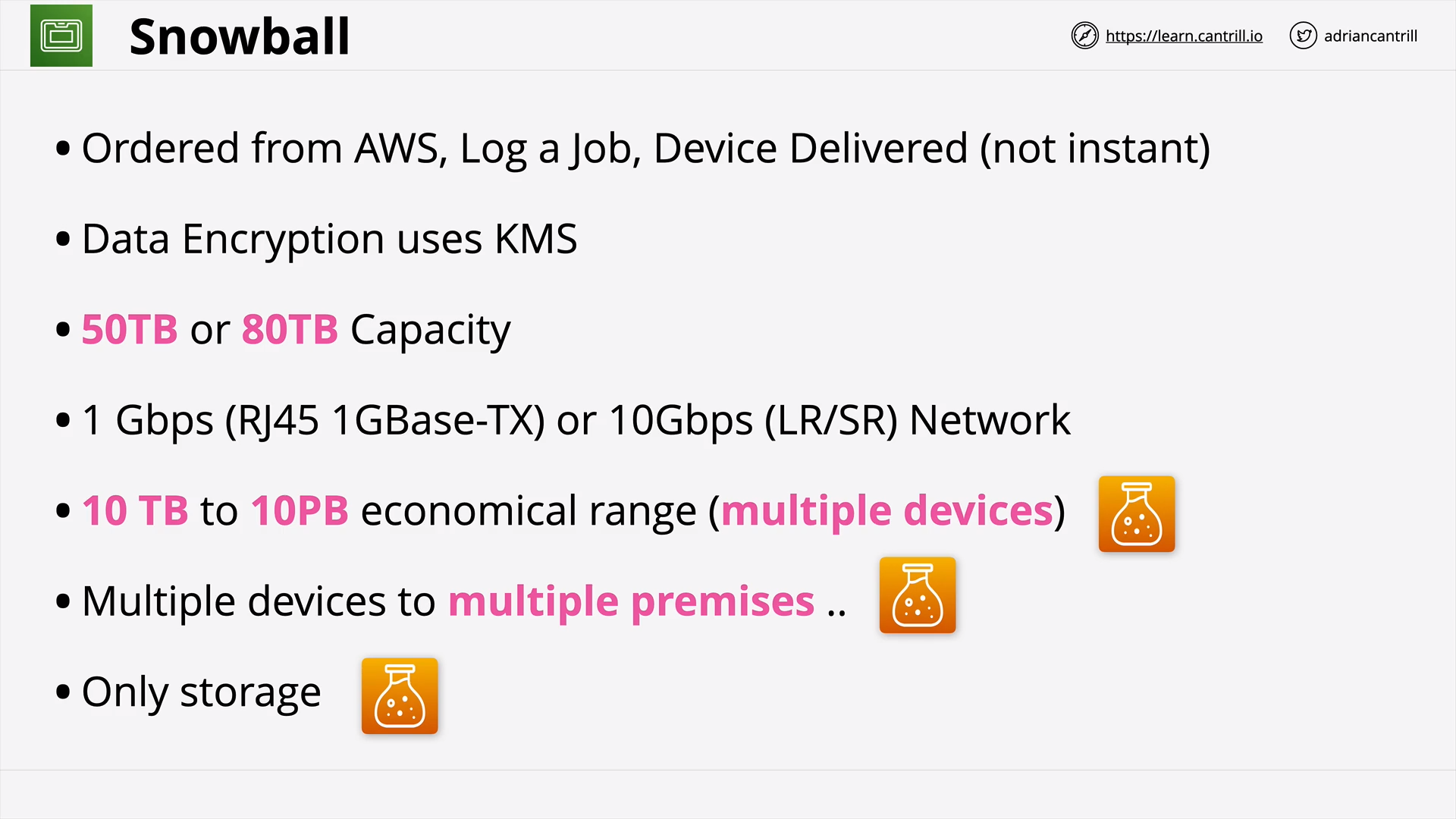 Snowball = Storage
Snowball = Storage
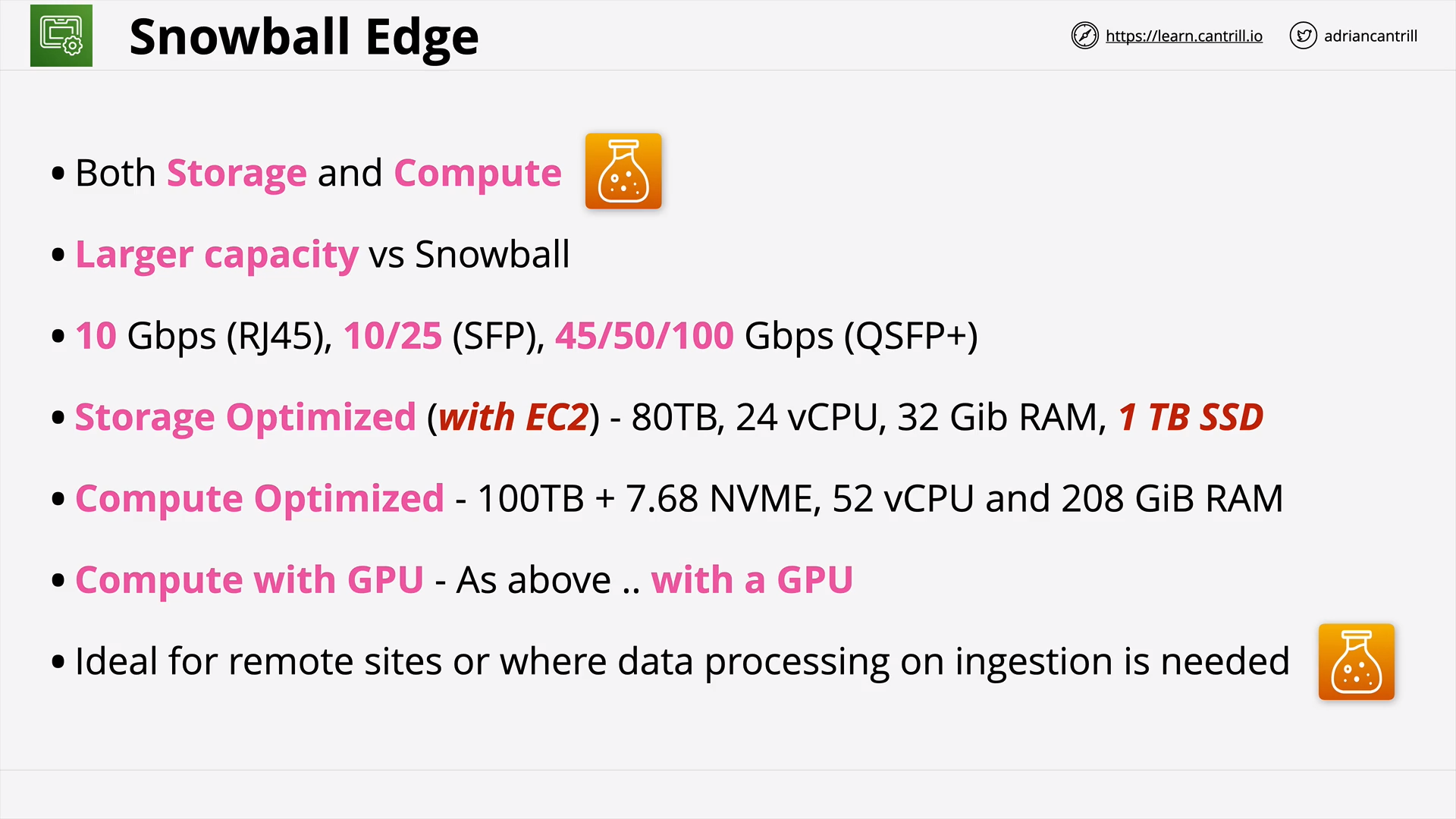 Snowball Edge = Snowball + Compute
Snowball Edge = Snowball + Compute
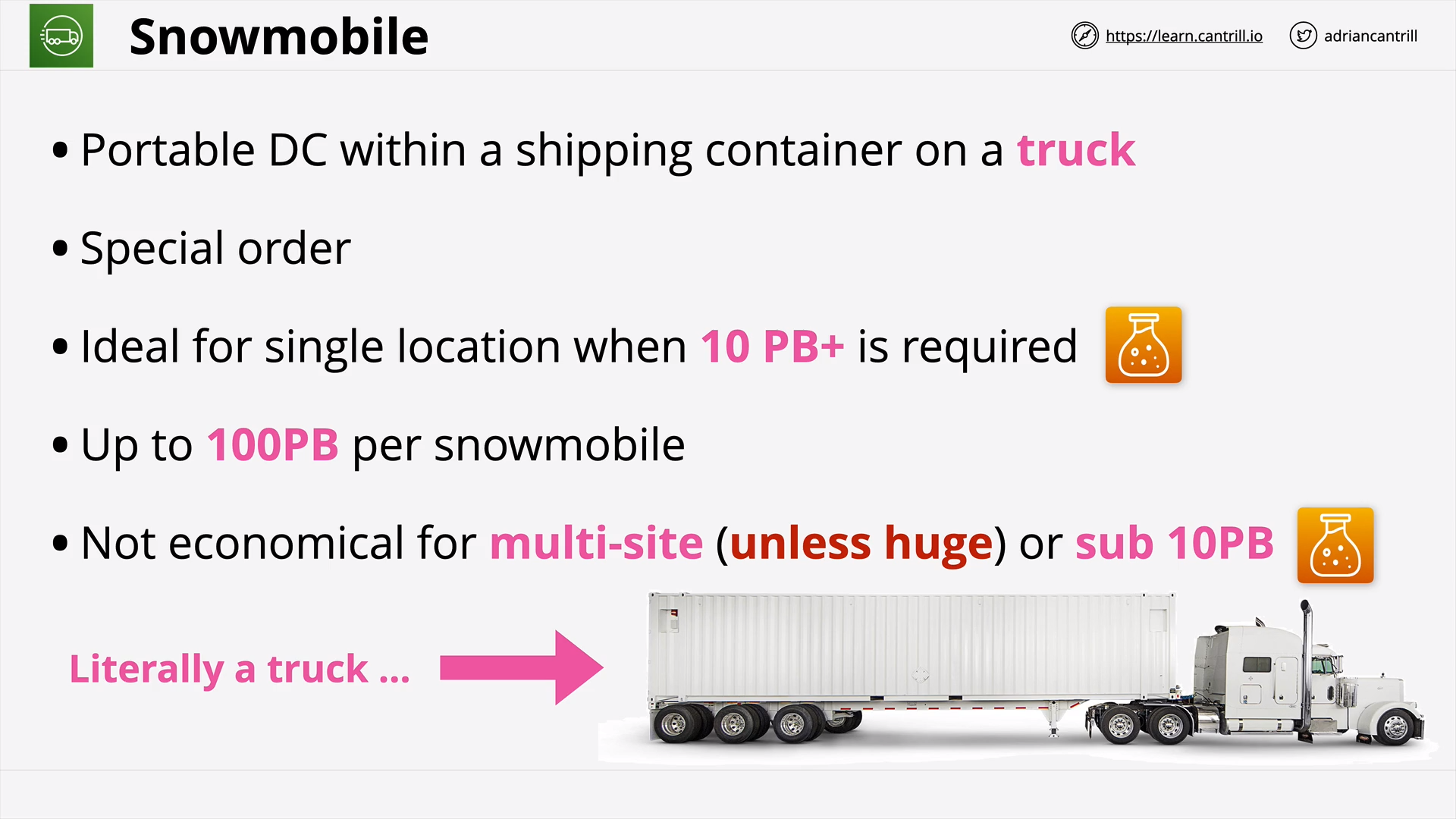 Snowmobile = Data Center in a truck
Snowmobile = Data Center in a truck
Directory Service (15:50)
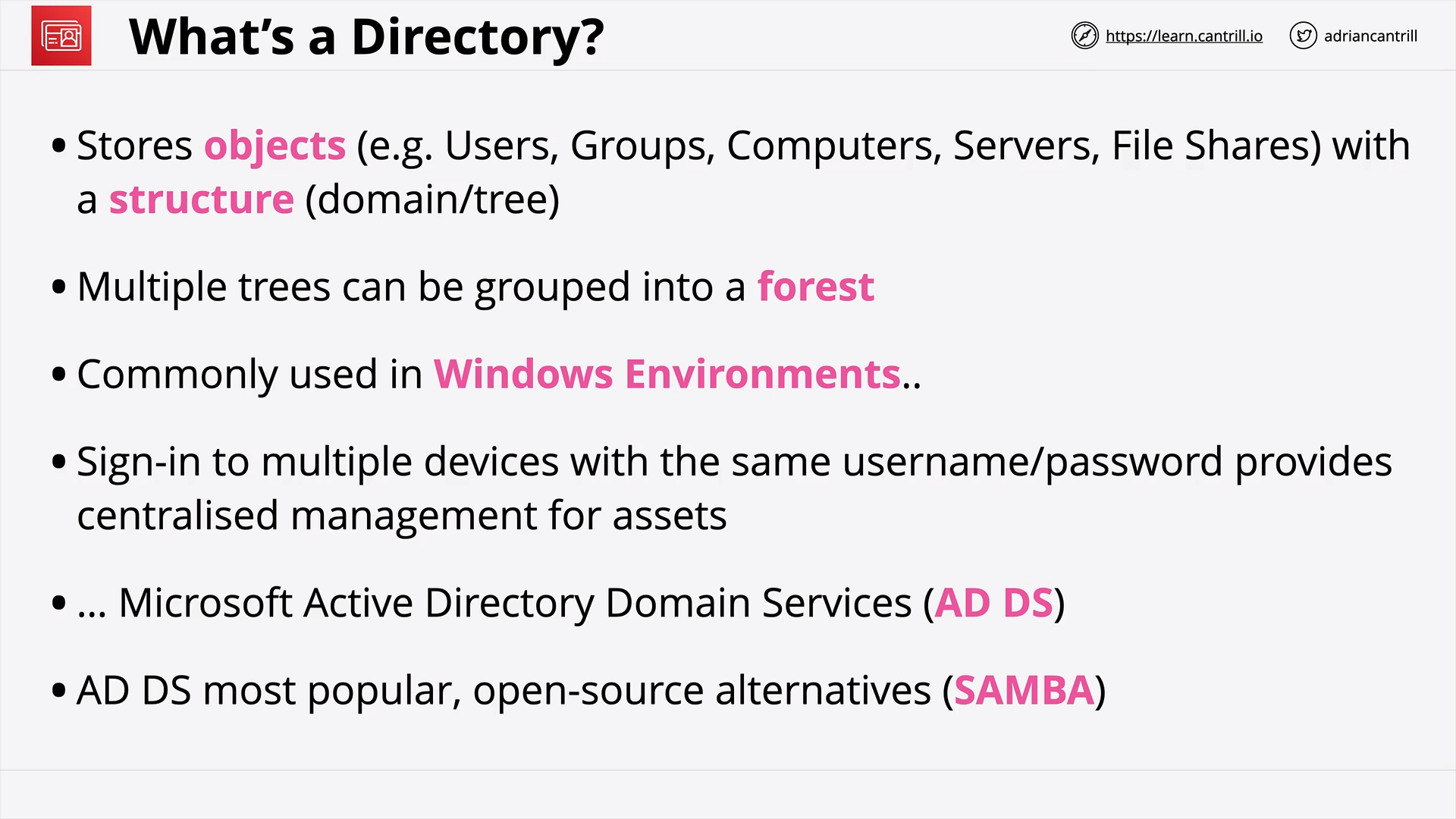 What’s a Directory?
What’s a Directory?
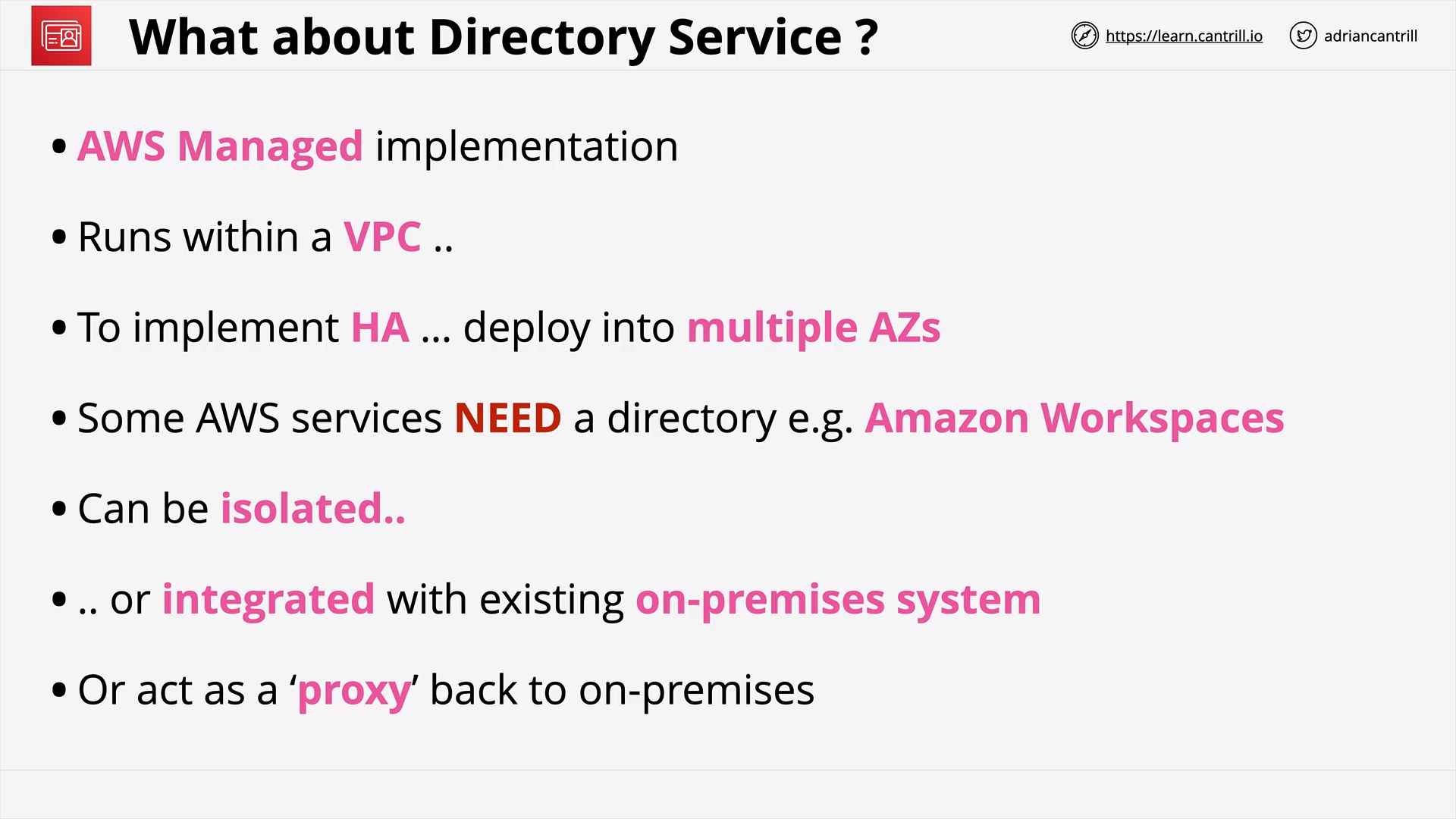 What about Directory Service?
What about Directory Service?
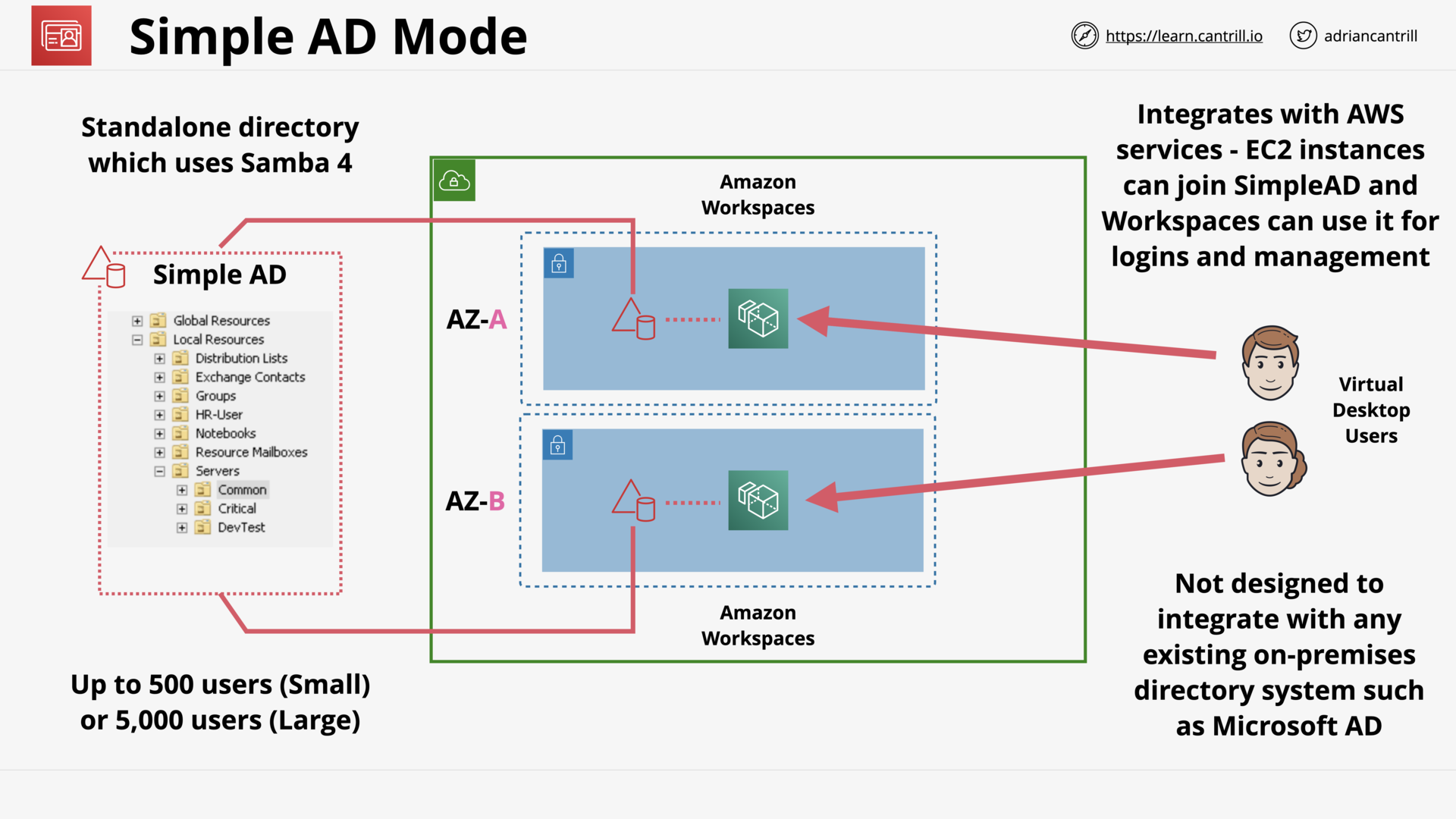 Directory Service - Simple AD Mode
Directory Service - Simple AD Mode
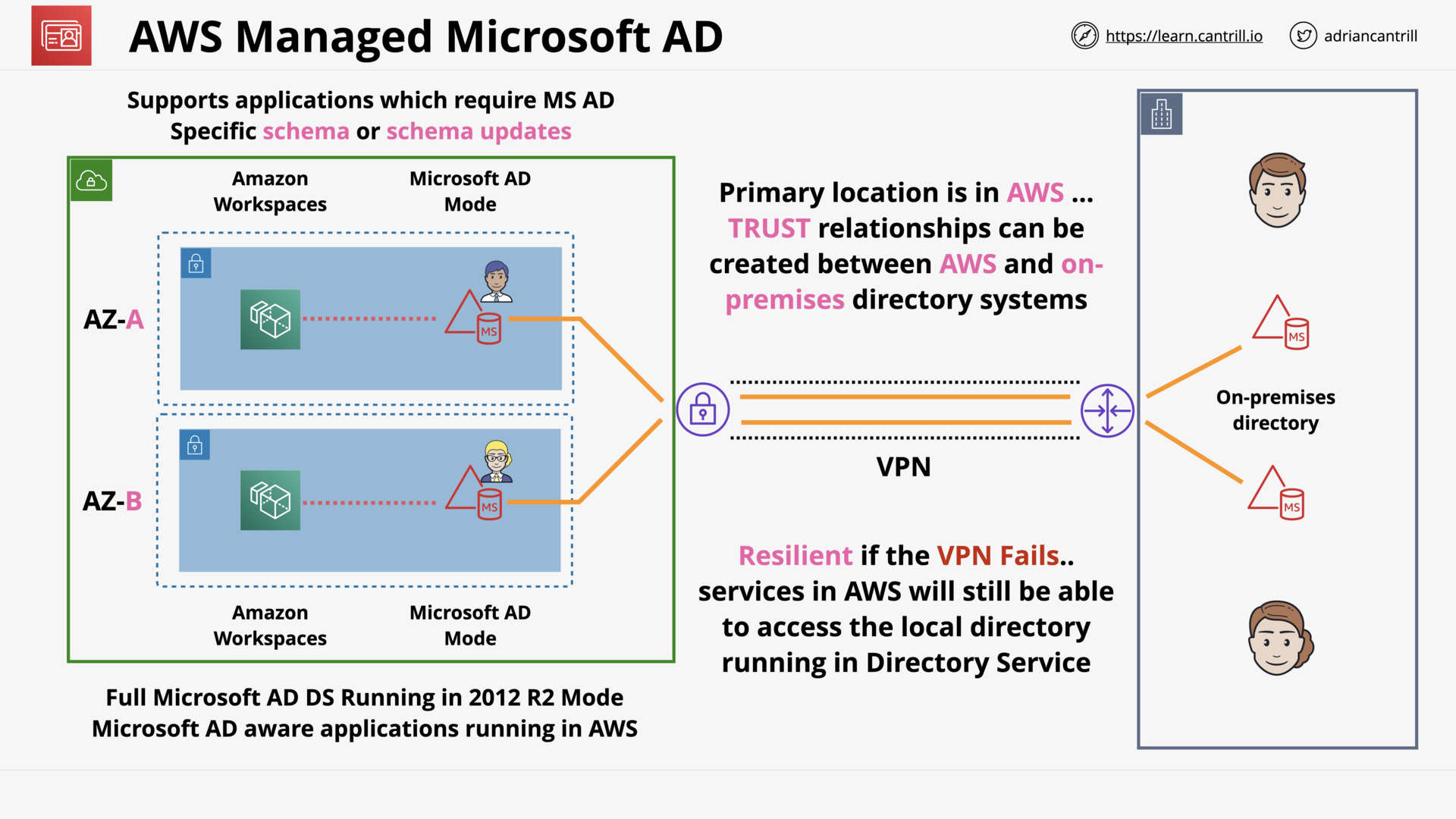 Directory Service - AWS Managed Microsoft AD
Directory Service - AWS Managed Microsoft AD
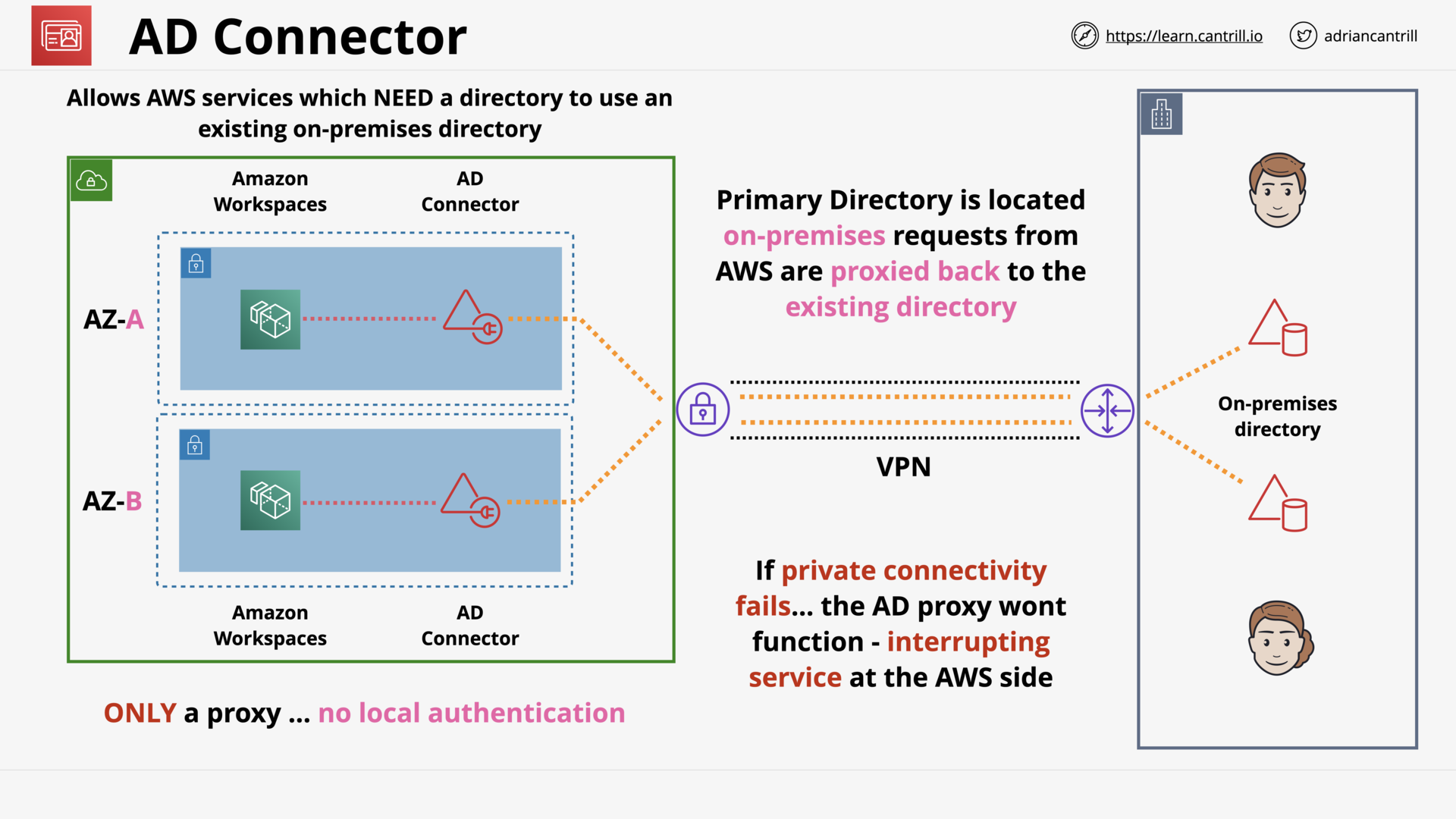 Directory Service - AD Connector
Directory Service - AD Connector
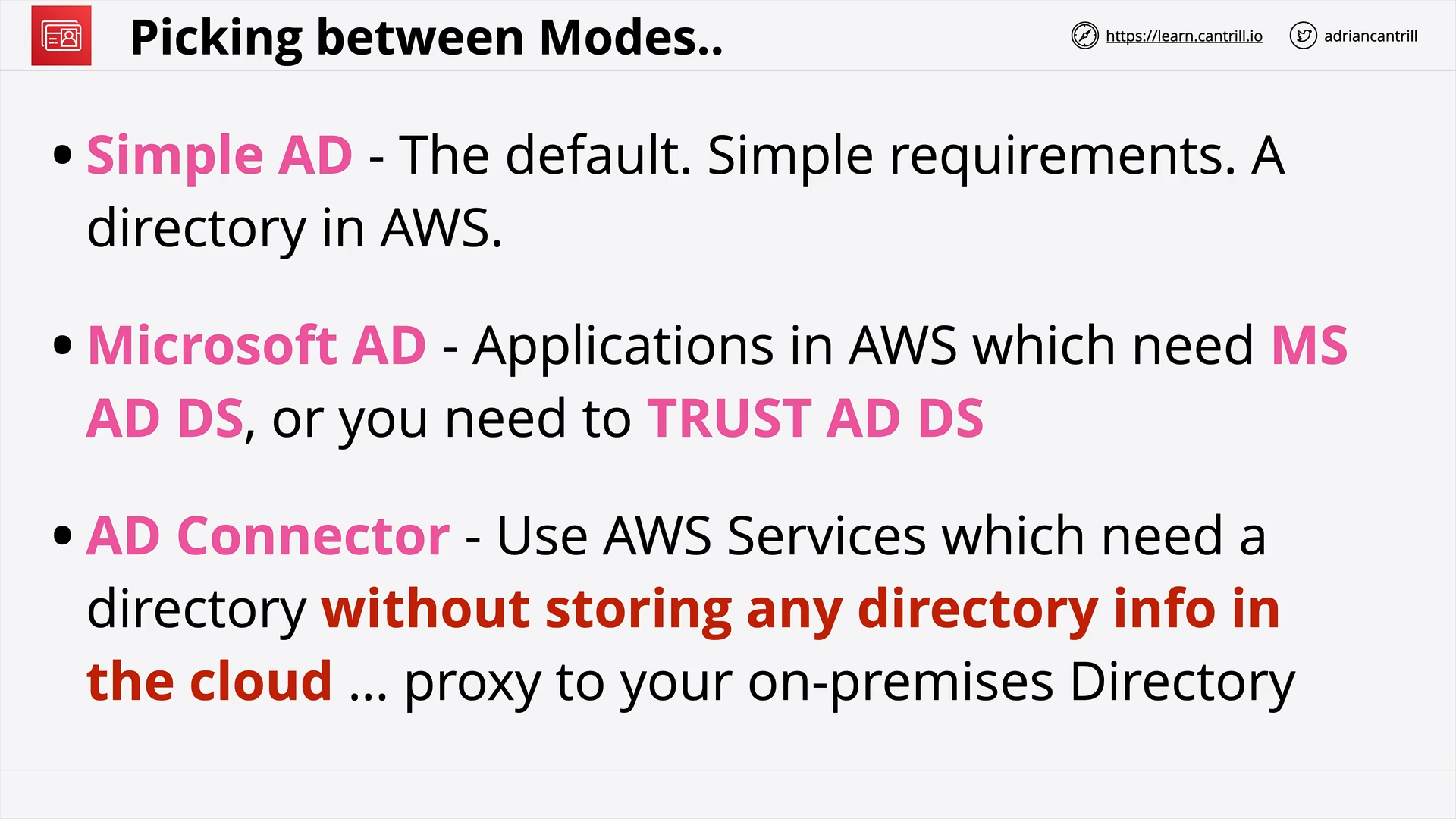 Directory Service - Which one?
Directory Service - Which one?
DataSync (9:27)
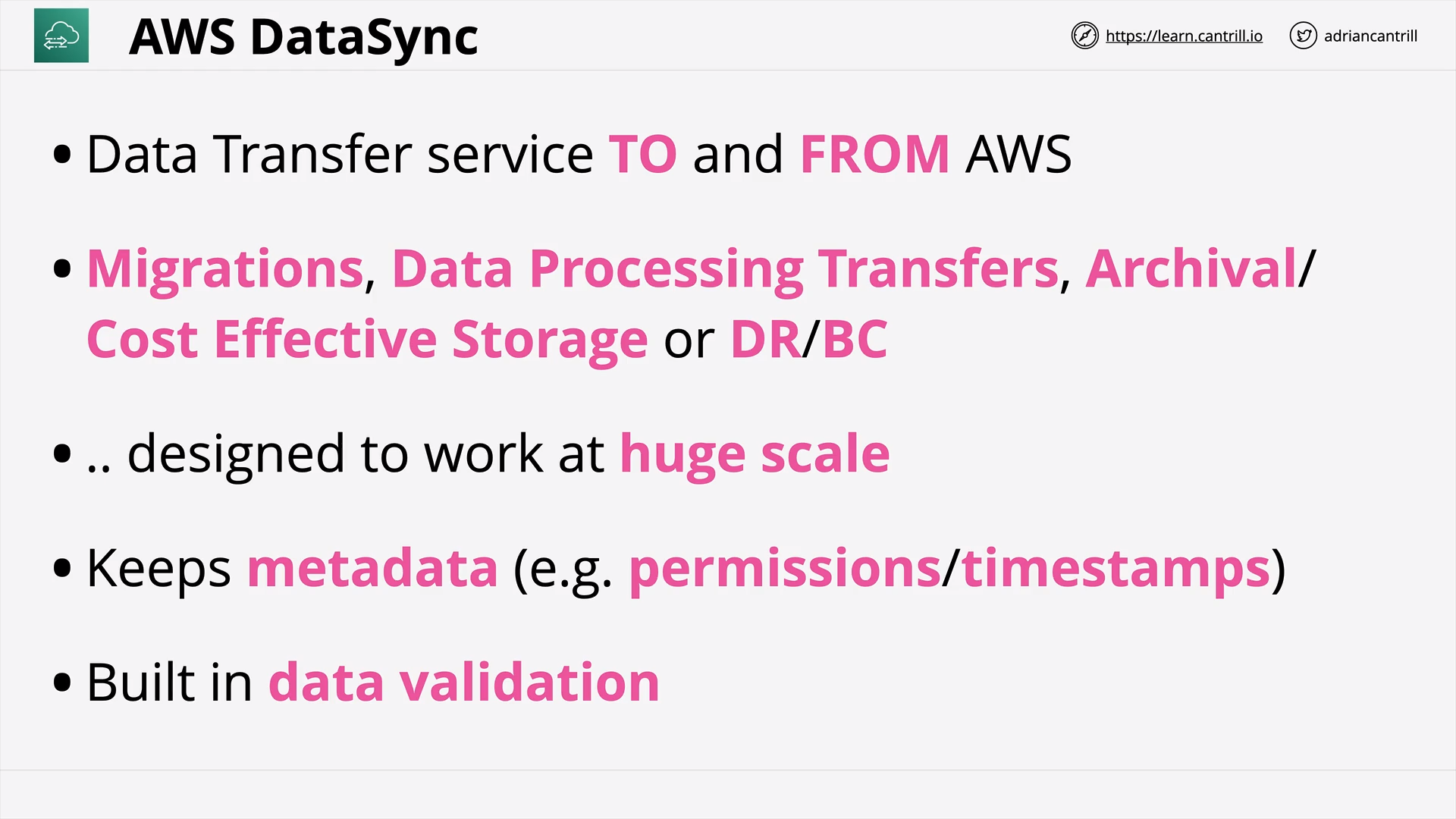 AWS DataSync - Overview
AWS DataSync - Overview
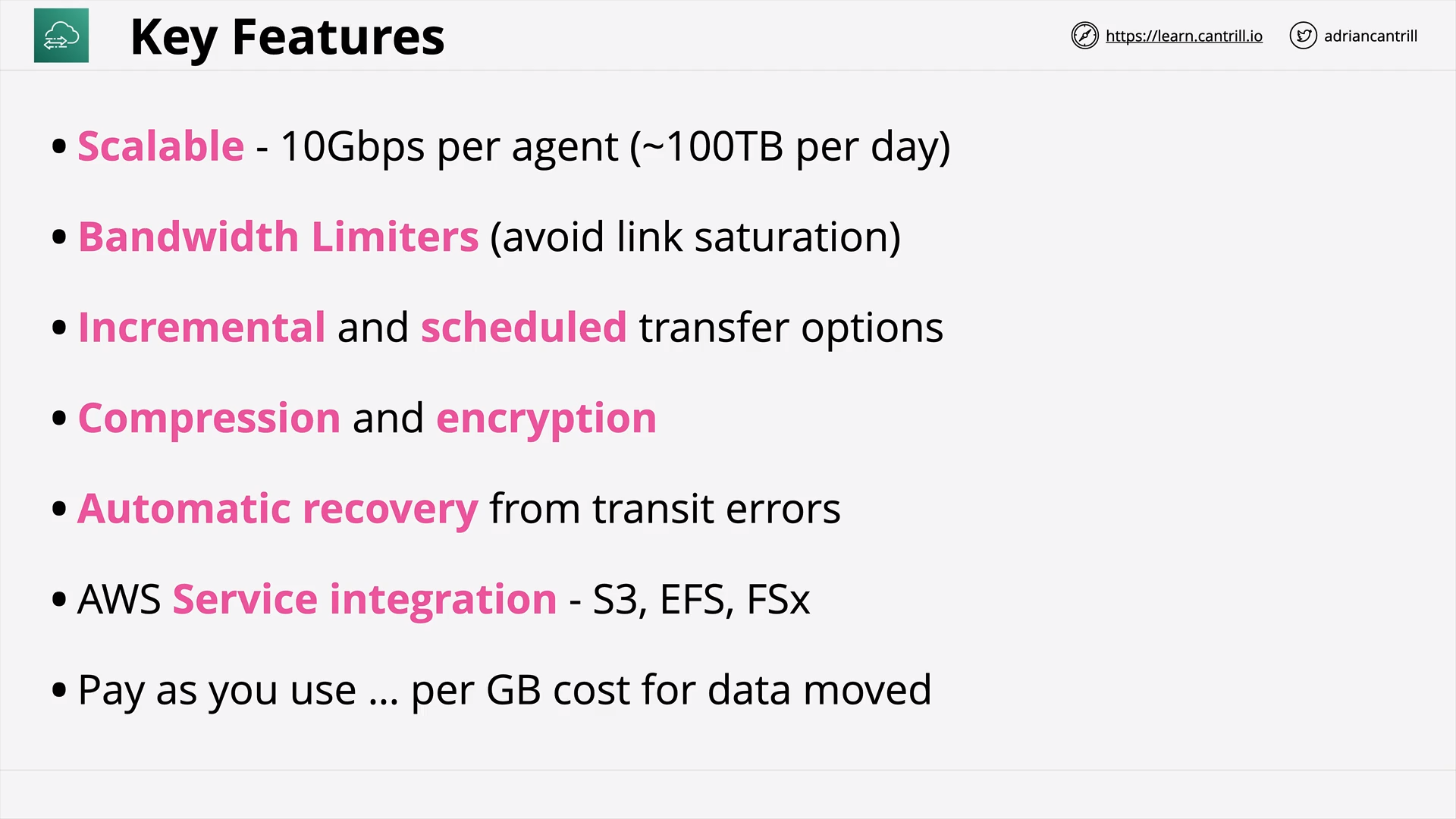 AWS DataSync - Key Features
AWS DataSync - Key Features
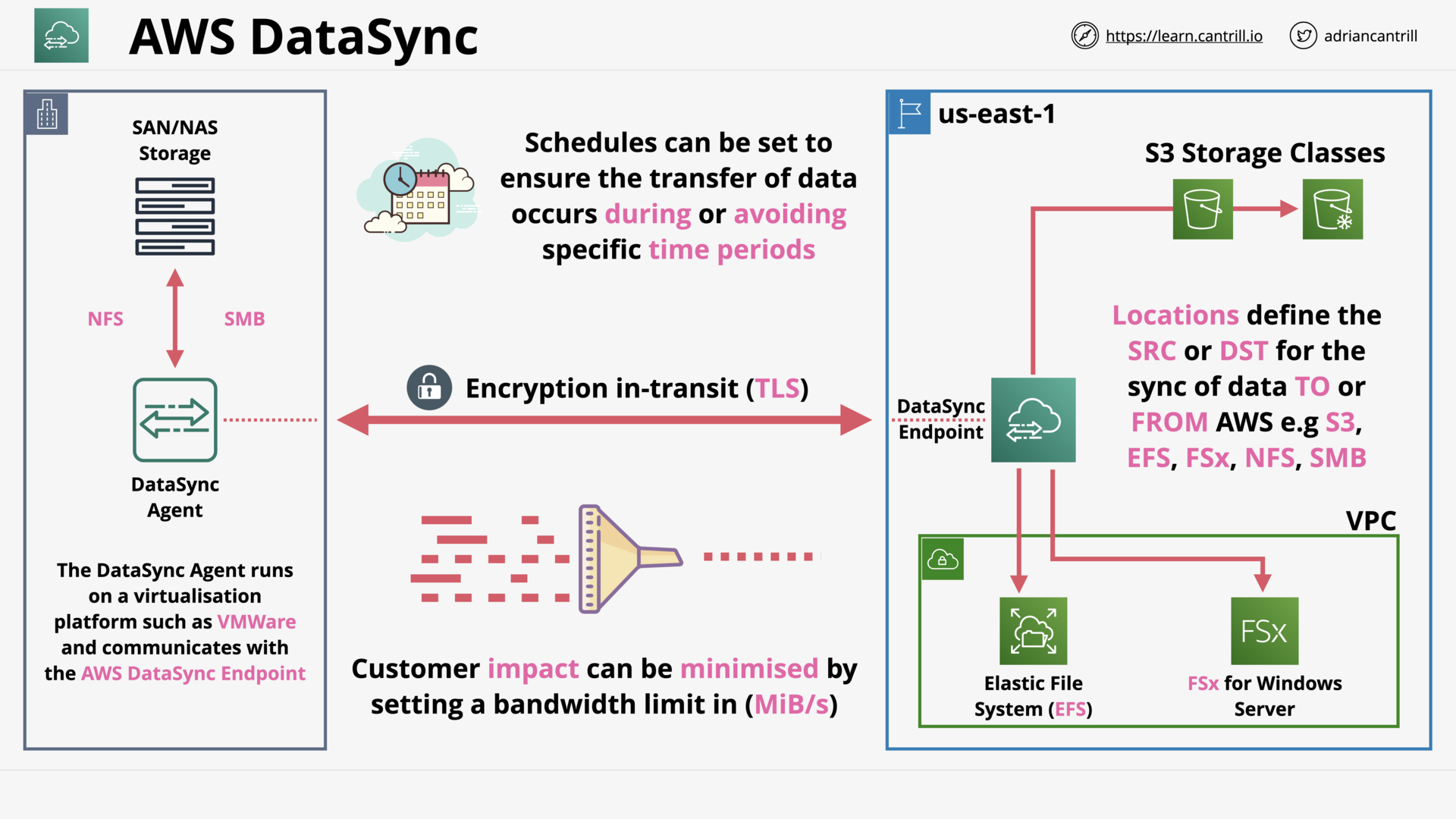 AWS DataSync - Architecture
AWS DataSync - Architecture
FSx for Windows Servers (11:32)
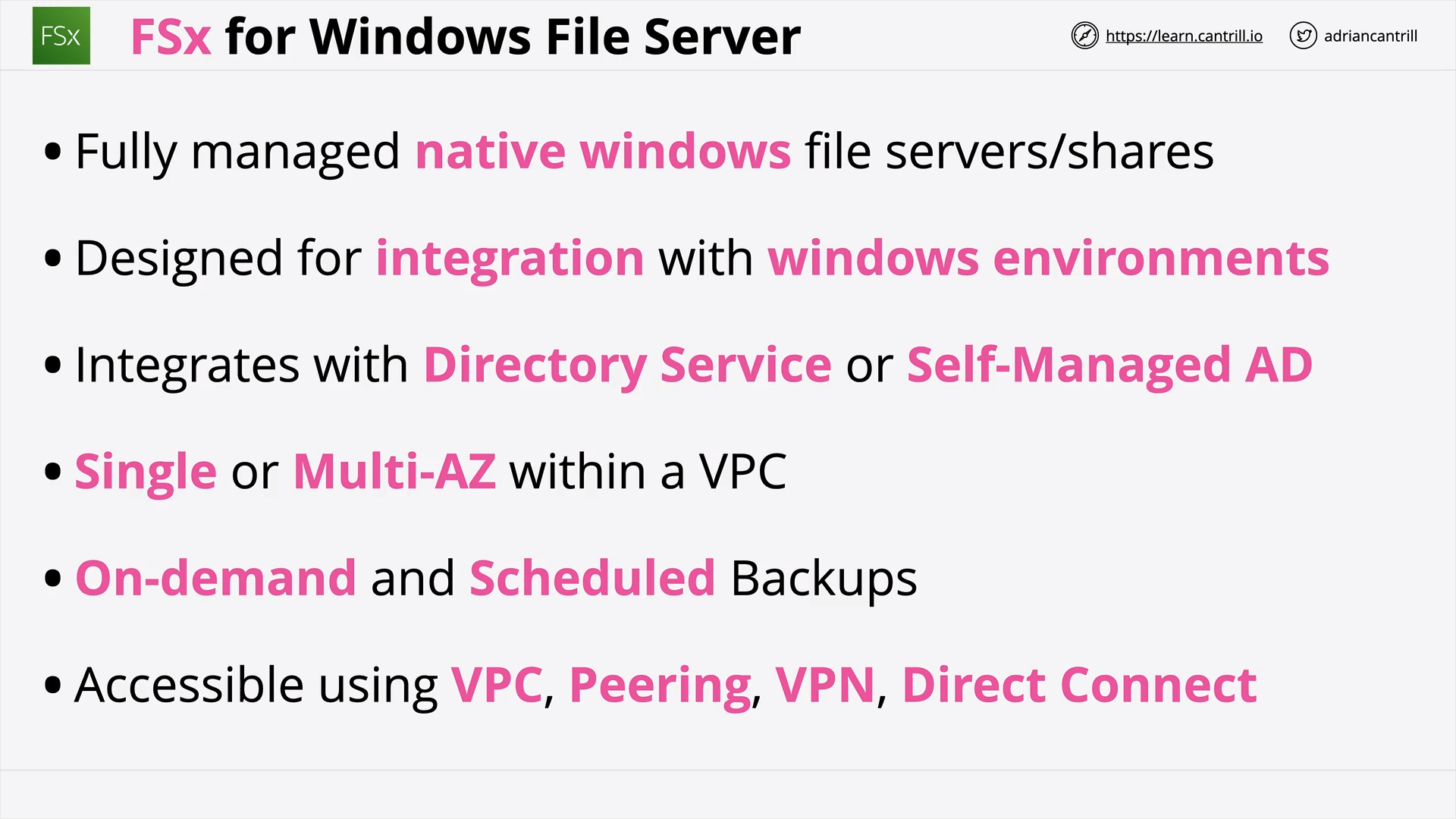 FSx for Windows File Servers - Overview
FSx for Windows File Servers - Overview
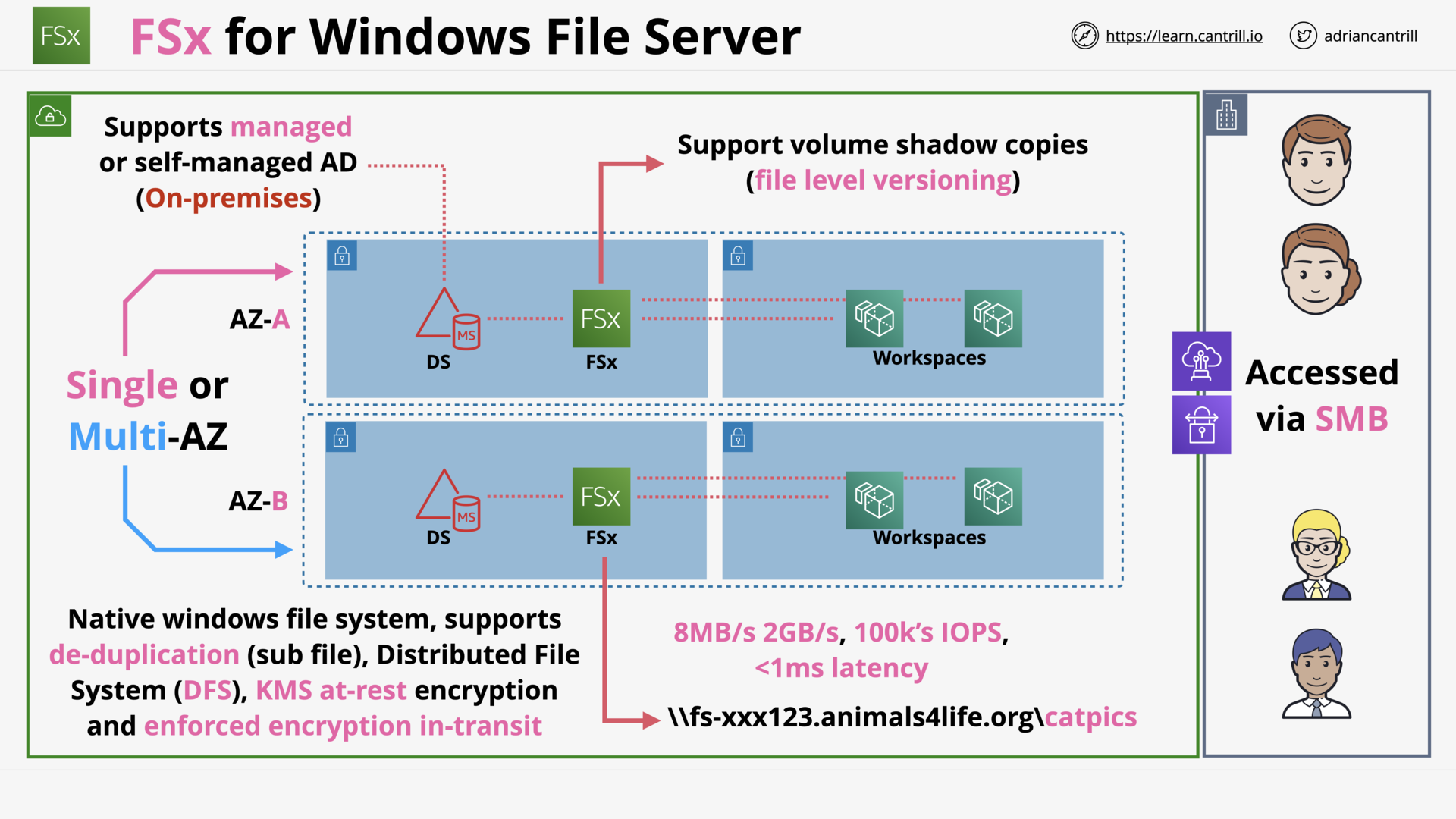 FSx for Windows File Servers - Architecture
FSx for Windows File Servers - Architecture
FSx For Lustre (13:57)
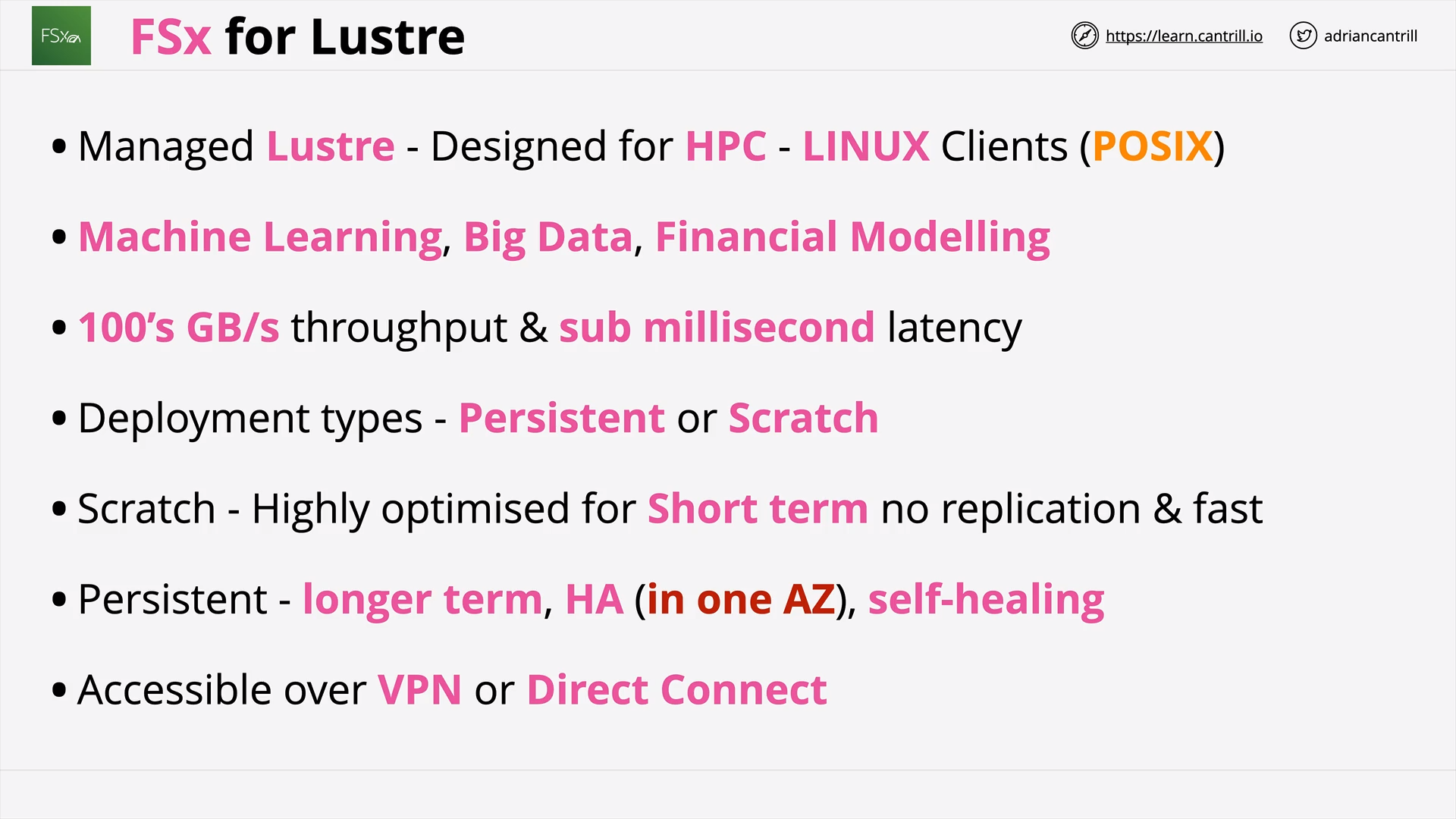 FSx For Lustre - Overview
FSx For Lustre - Overview
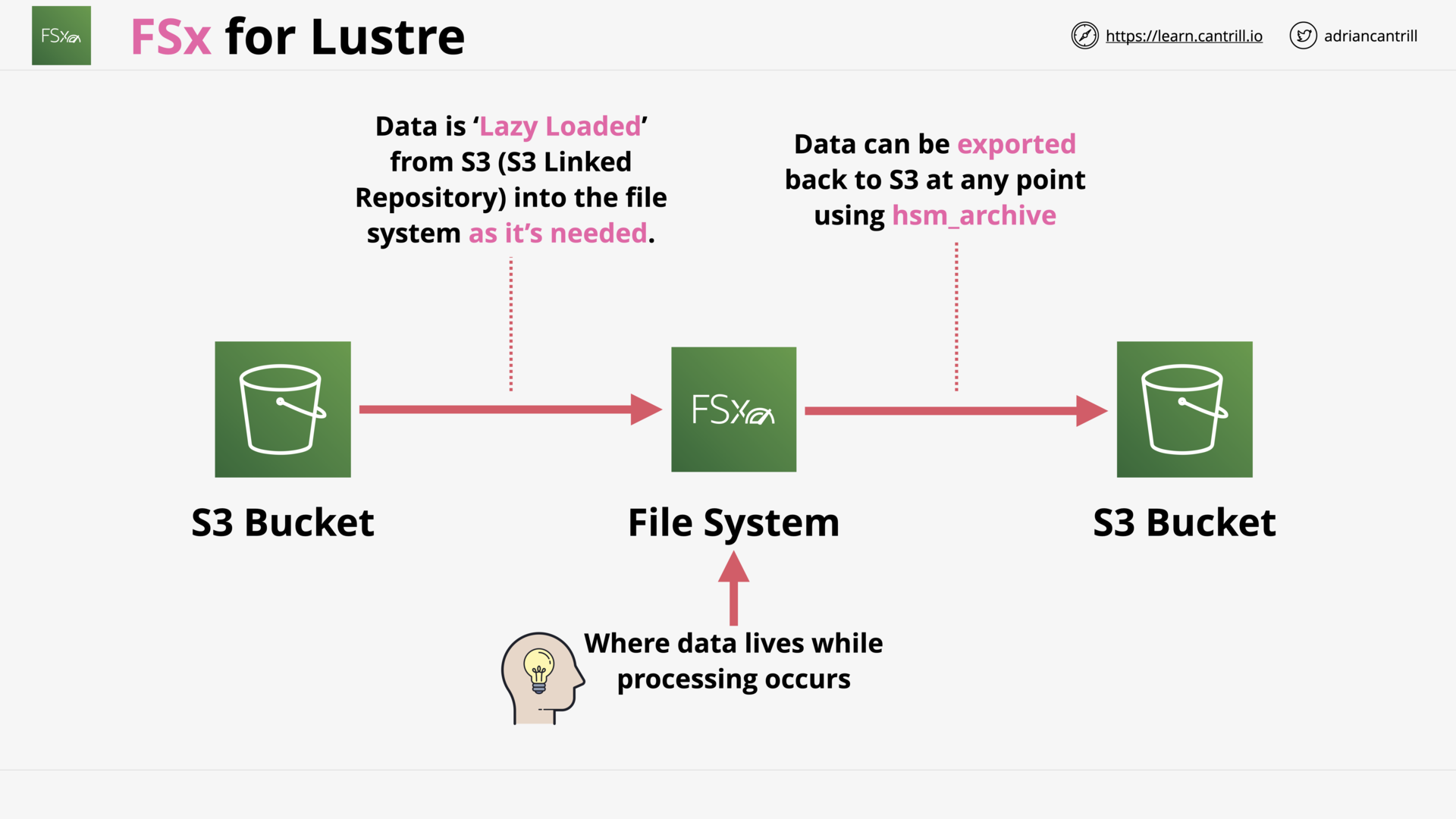 FSx For Lustre - S3 data repository
FSx For Lustre - S3 data repository
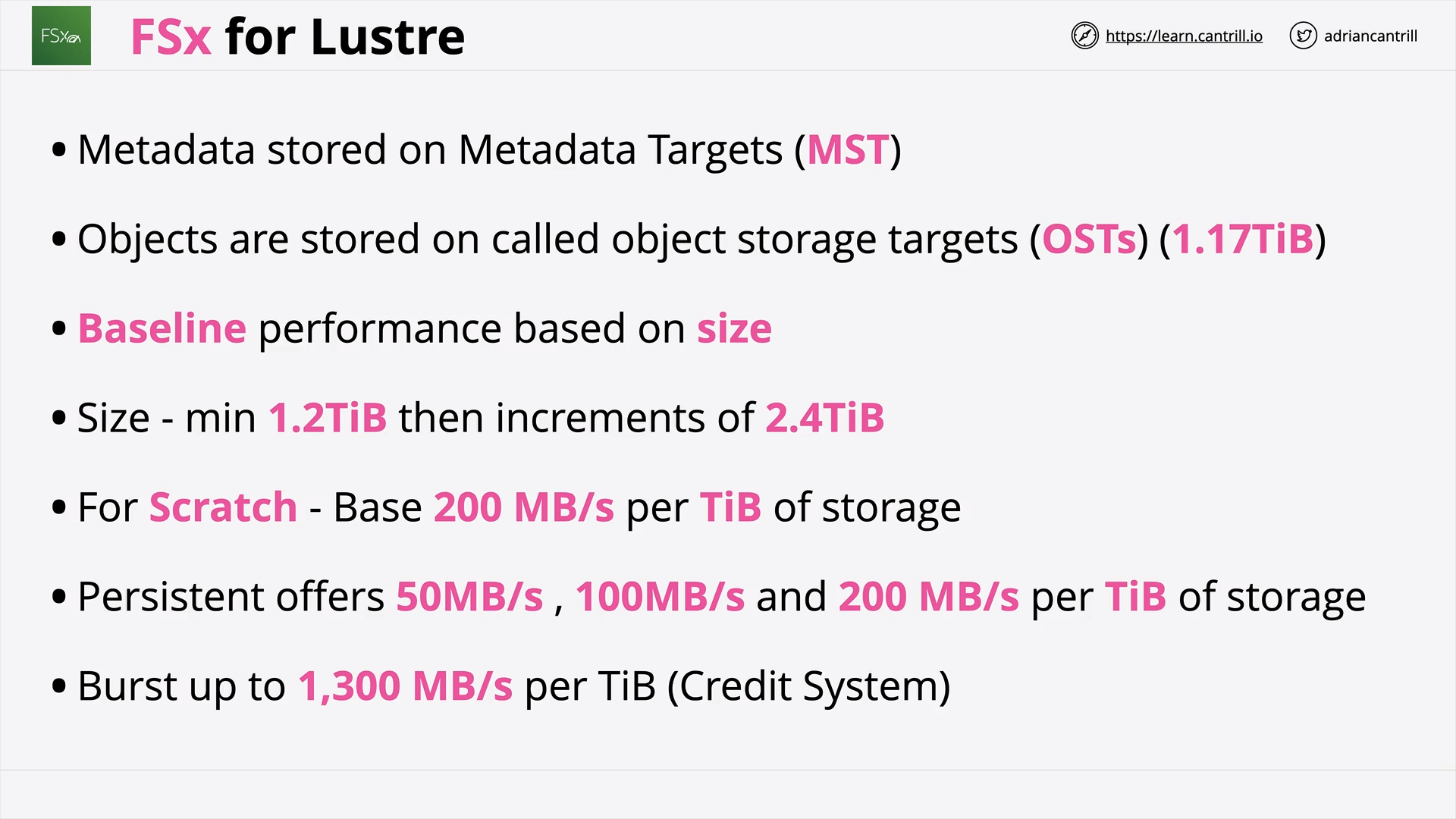 FSx For Lustre - Performance
FSx For Lustre - Performance
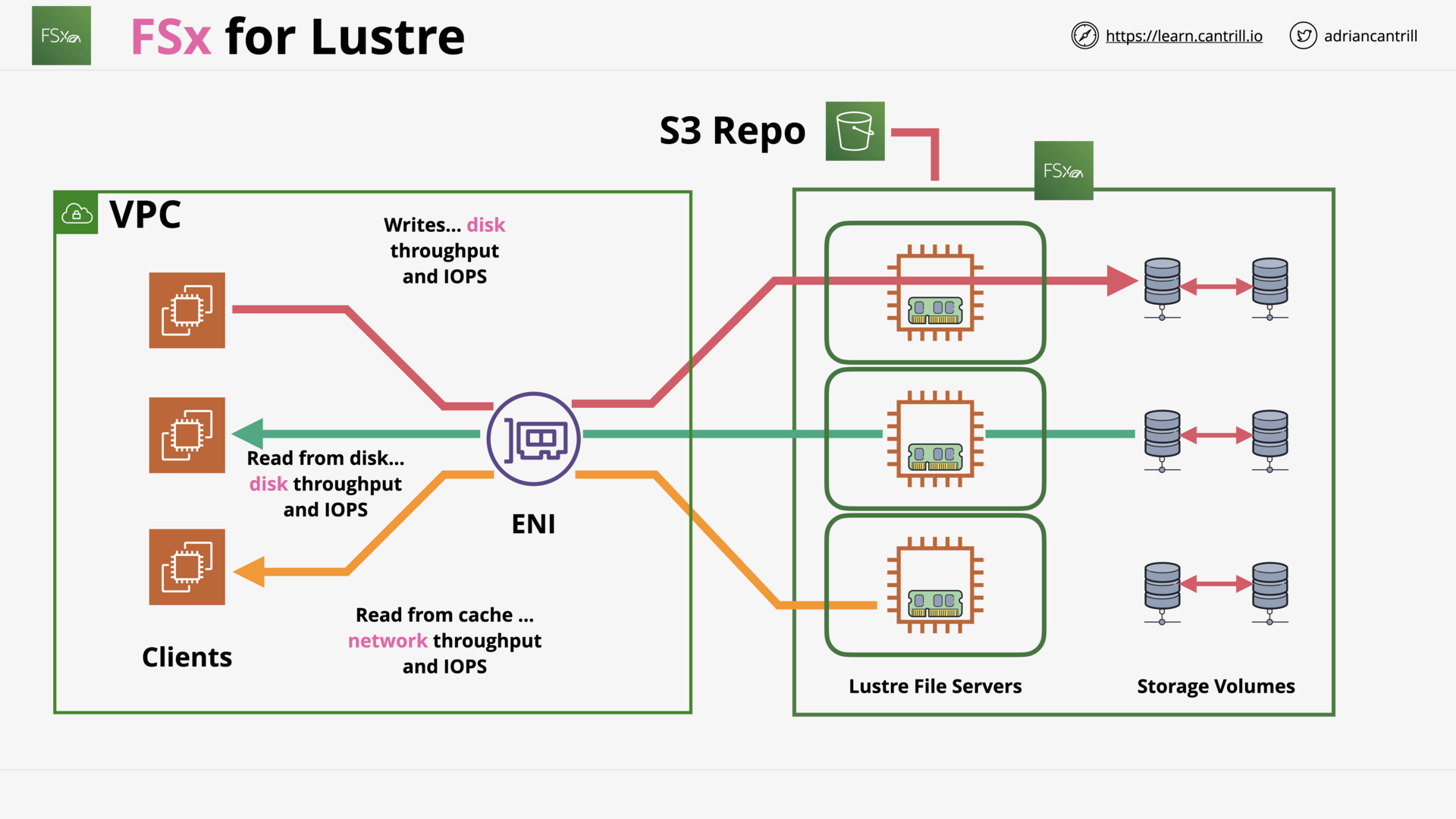 FSx For Lustre - Architecture
FSx For Lustre - Architecture
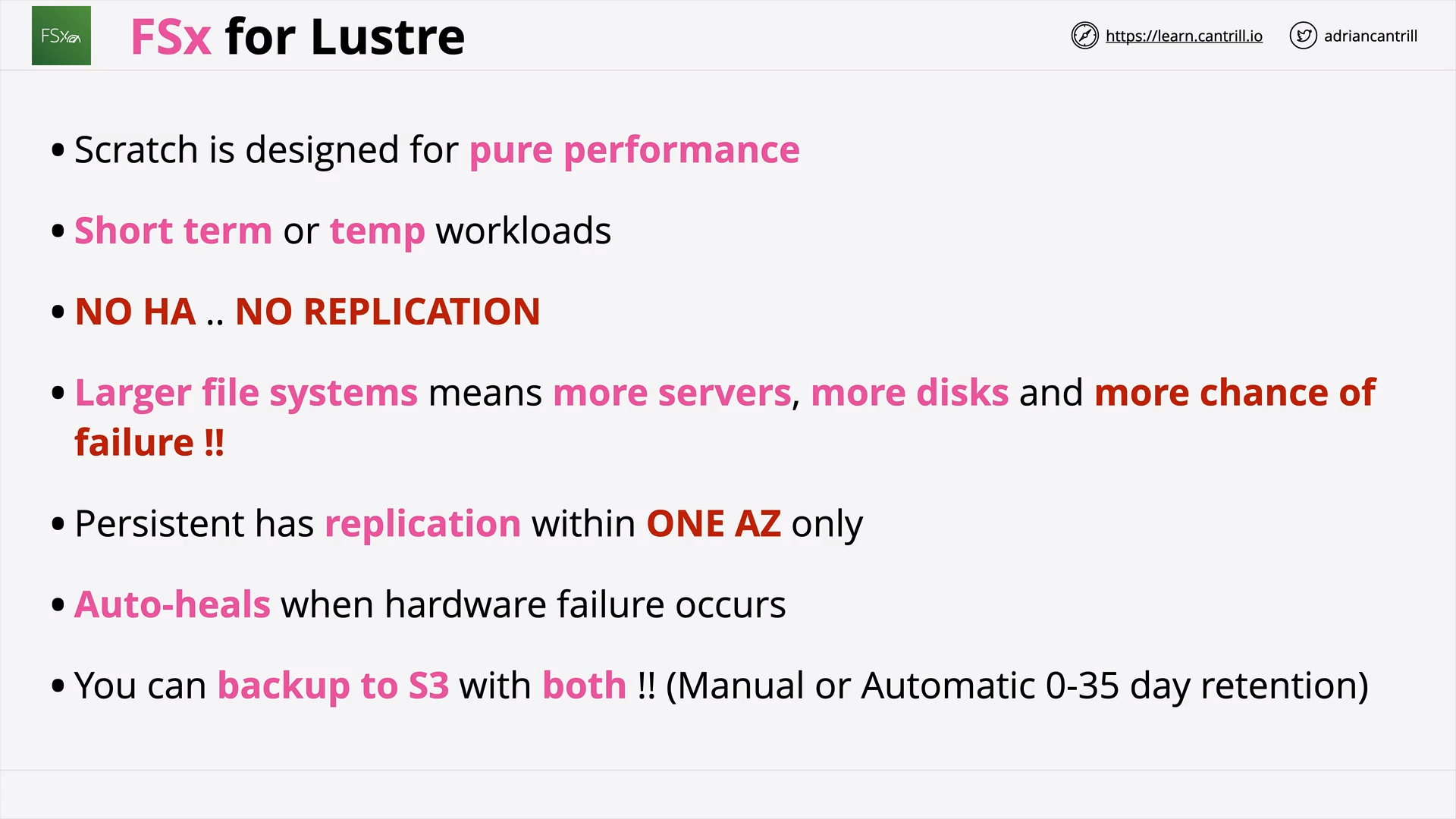 FSx For Lustre - Key Points
FSx For Lustre - Key Points
AWS Transfer Family (10:24)
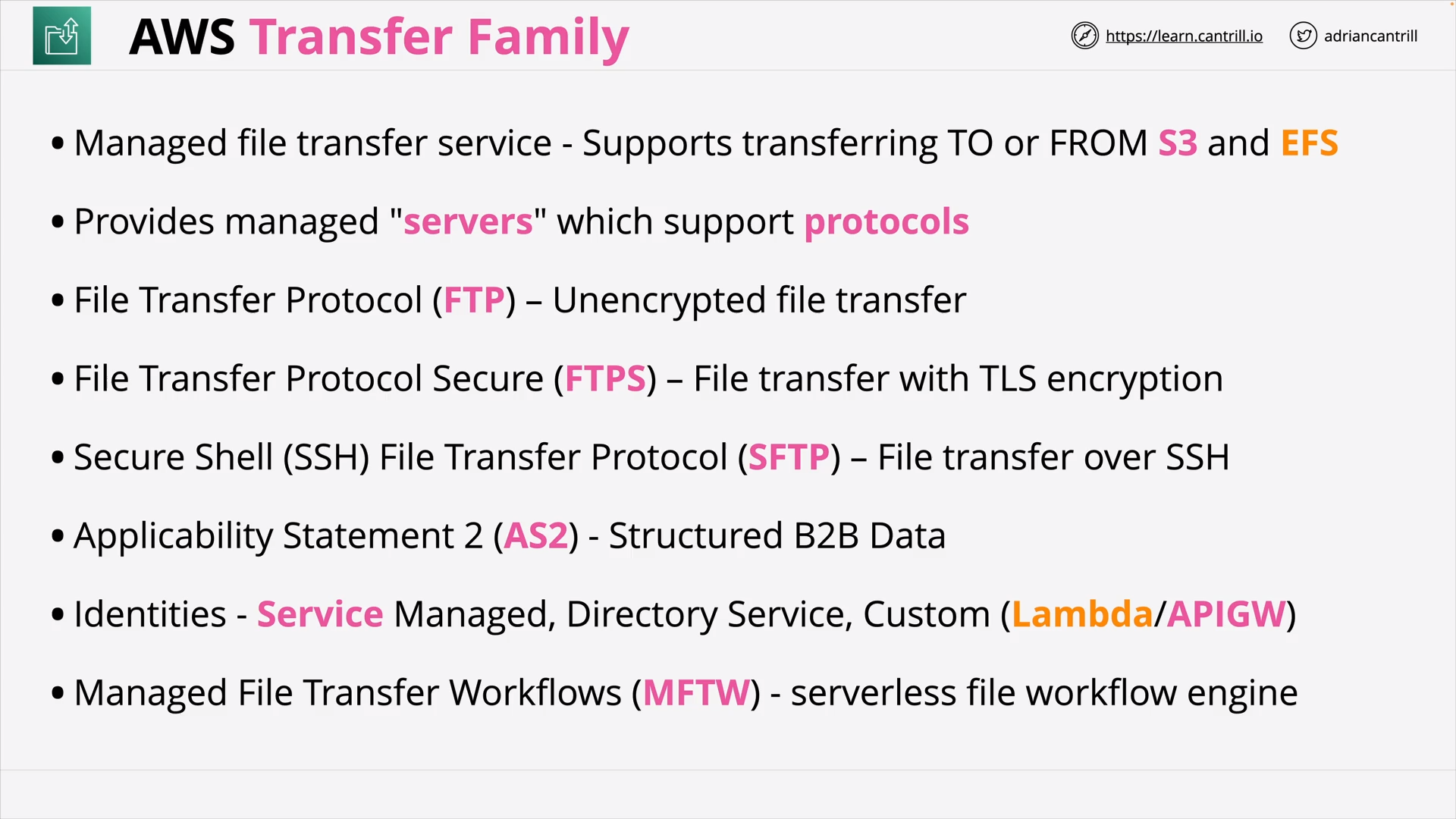 AWS Transfer Family - Overview
AWS Transfer Family - Overview
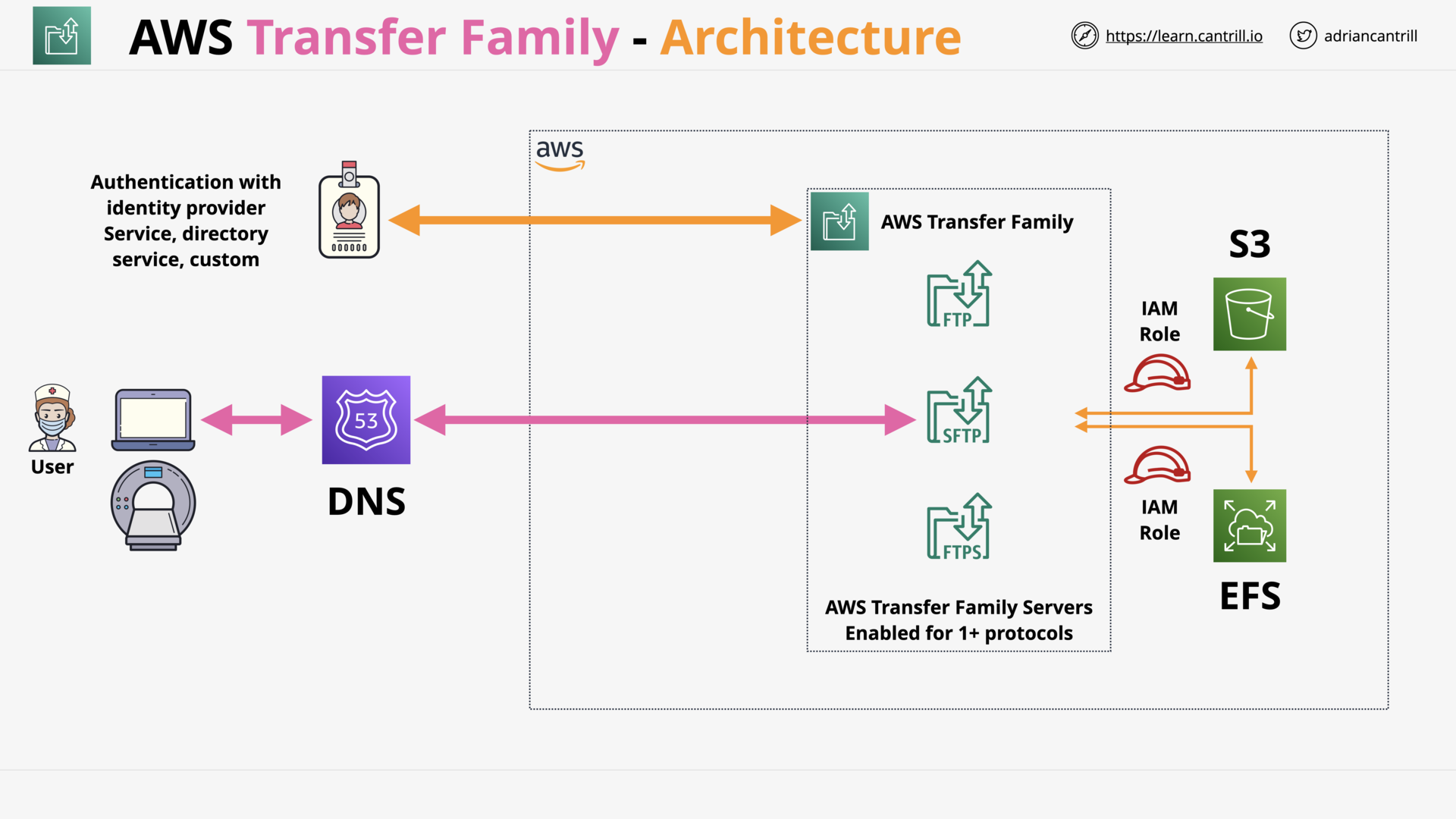 AWS Transfer Family - Architecture
AWS Transfer Family - Architecture
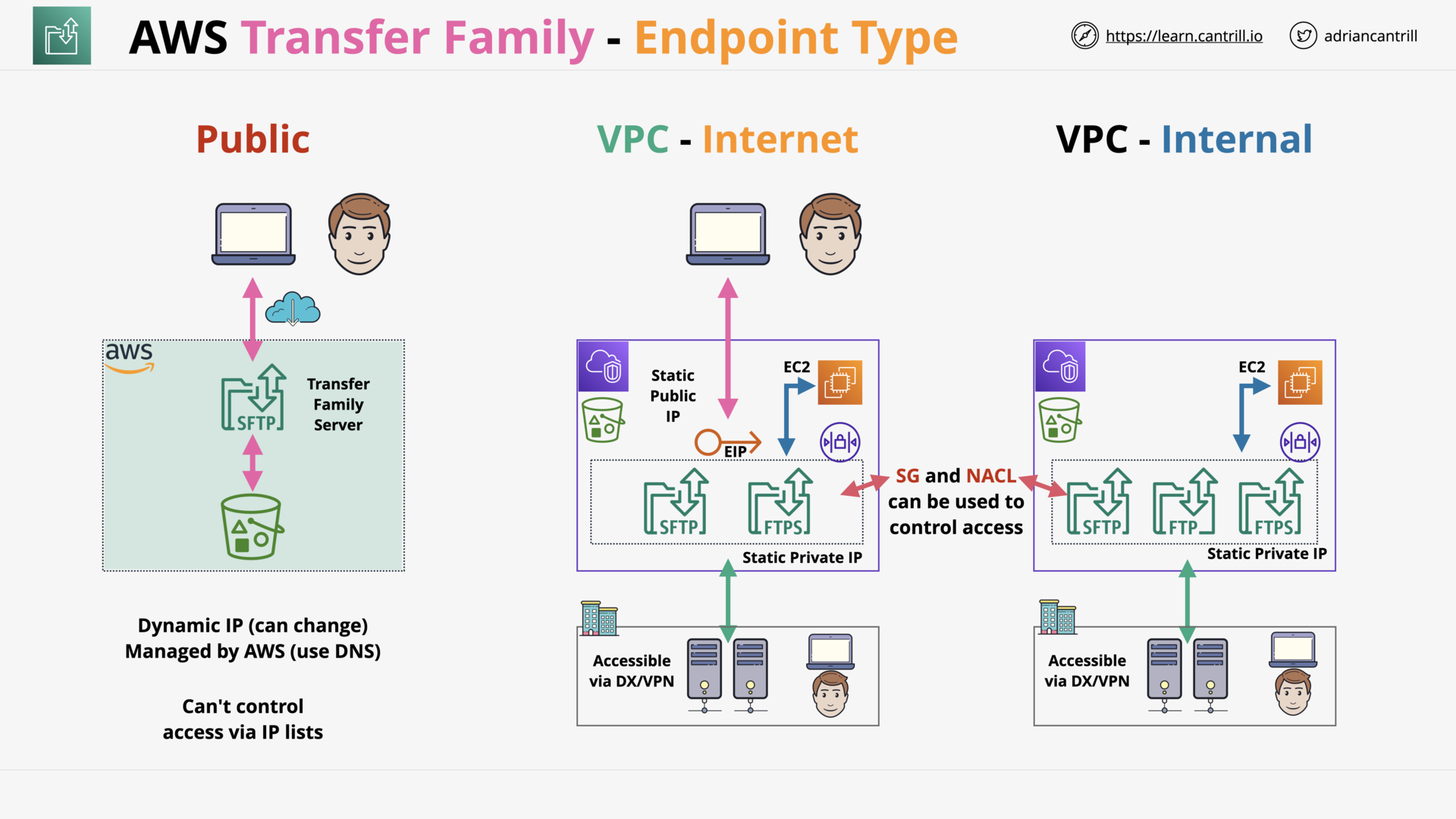 AWS Transfer Family - Endpoint Type
AWS Transfer Family - Endpoint Type
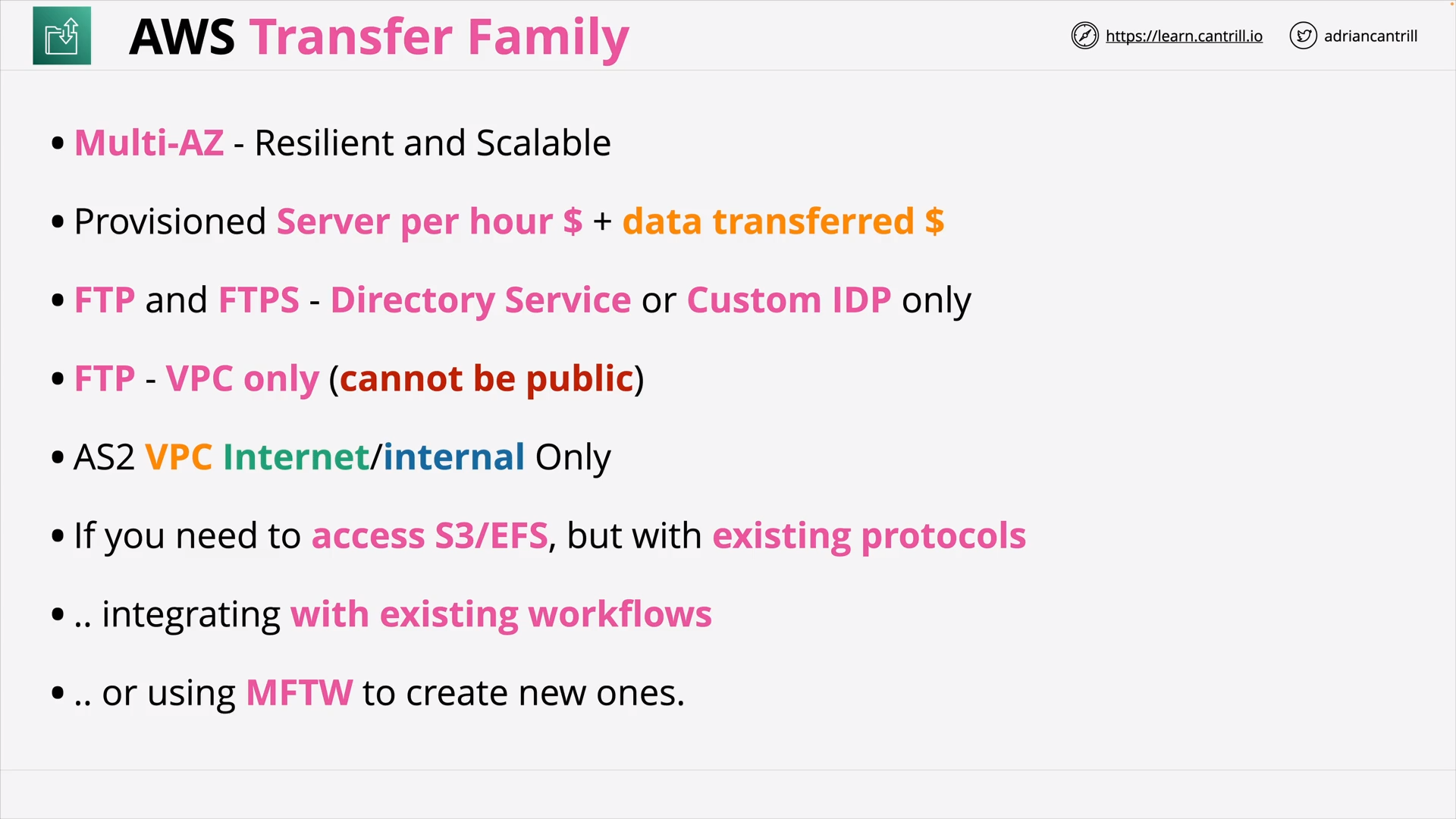 AWS Transfer Family - Key Points
AWS Transfer Family - Key Points
Hybrid and Migration Section Quiz
SECURITY, DEPLOYMENT & OPERATIONS
AWS Secrets Manager (7:44)
 Secrets Manager vs System Manager’s Parameter Store
Secrets Manager vs System Manager’s Parameter Store
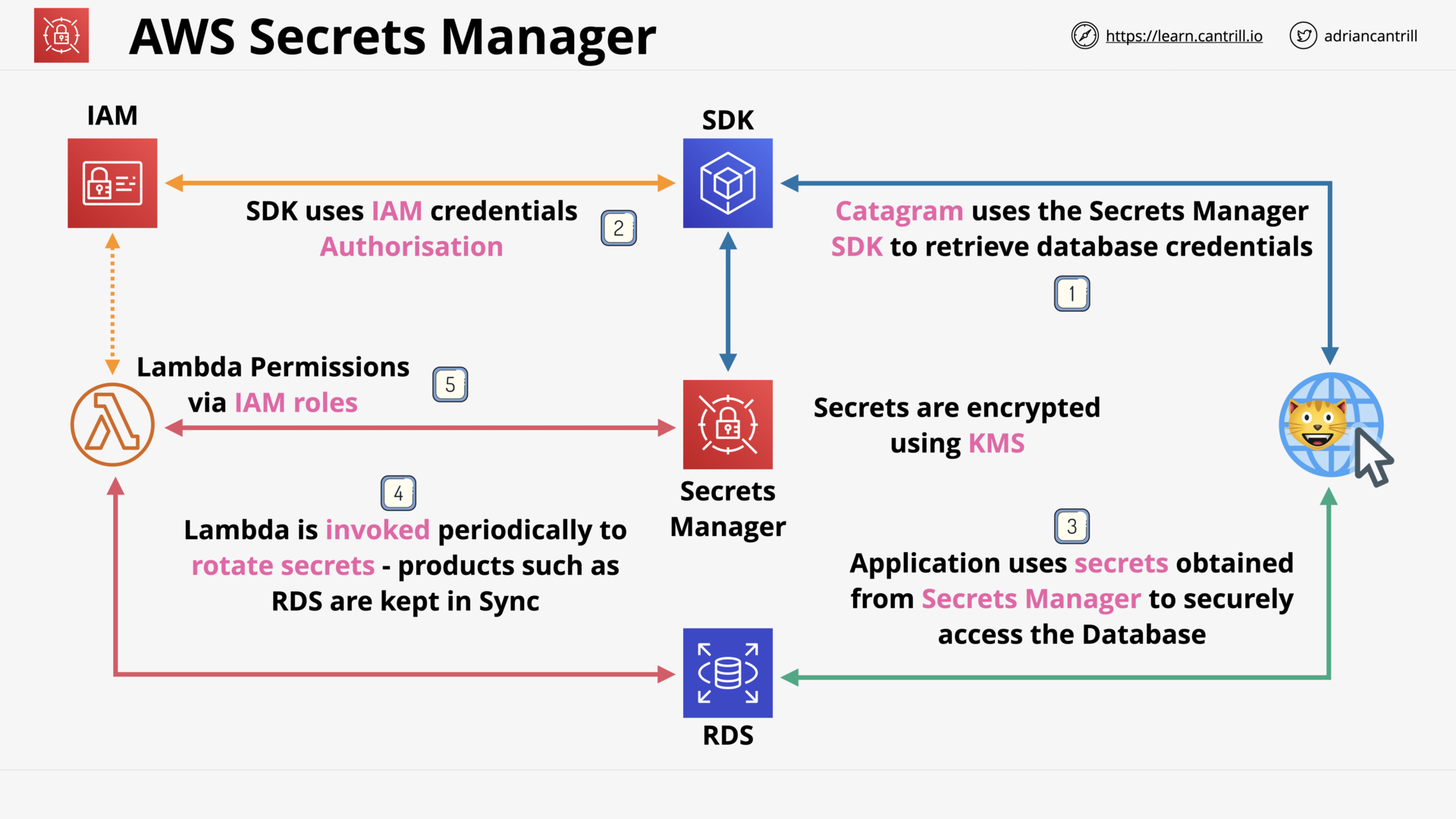 AWS Secrets Manager - Architecture
AWS Secrets Manager - Architecture
Application Layer (L7) Firewall (7:44)
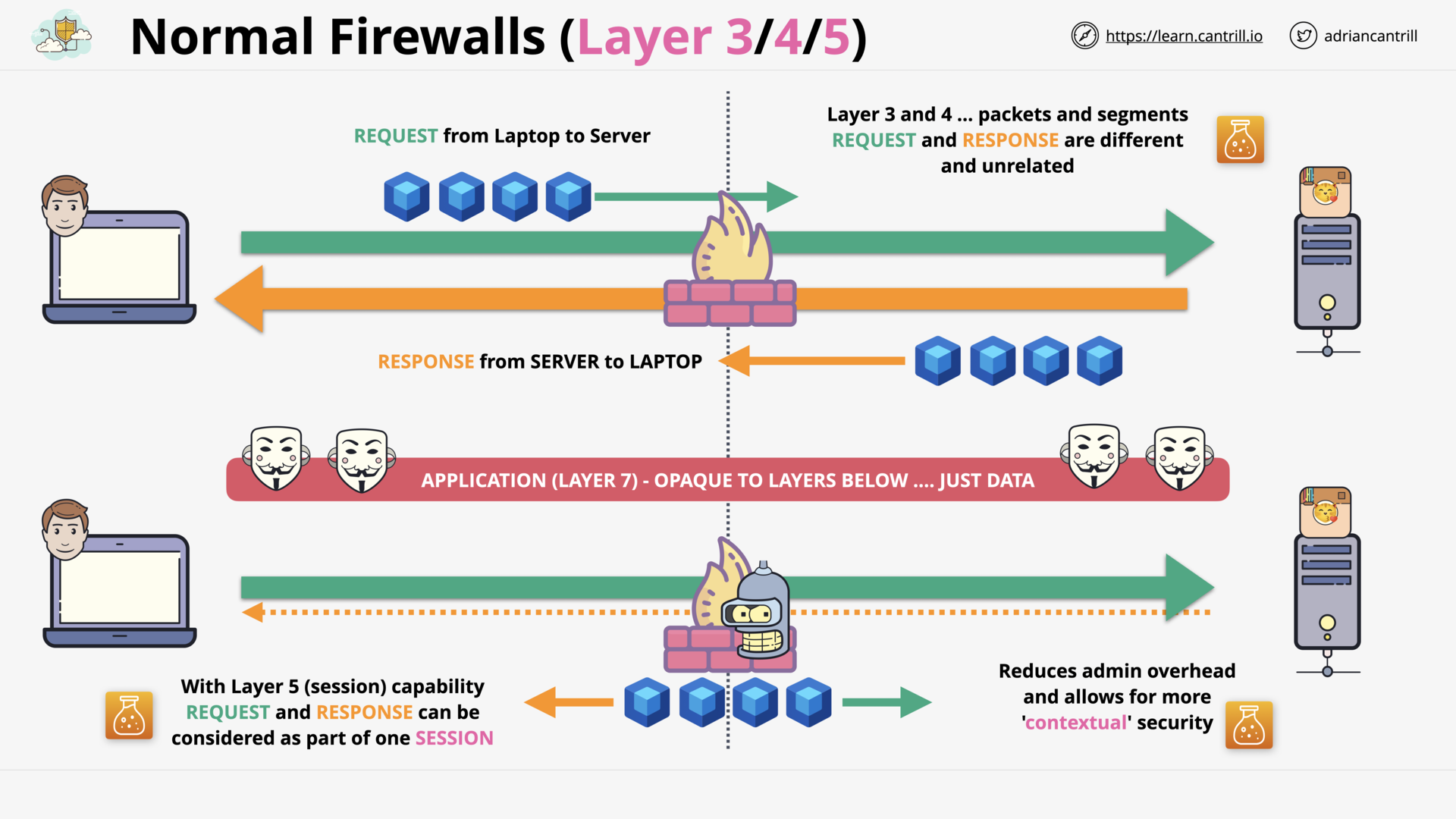 Firewall - Layer 3-4-5
Firewall - Layer 3-4-5
what is the drawback of firewall layer 3-4?
Packets & segemnts of REQUEST and REQUEST are different and unrelated.
Because Layer 3-4 don’t know what is the data.
what is a big improve of firewall layer 5?
Firewall Layer 5 understand REQUEST & RESPONSE’s session, it can know which REQUEST and RESPONSE is a pair.
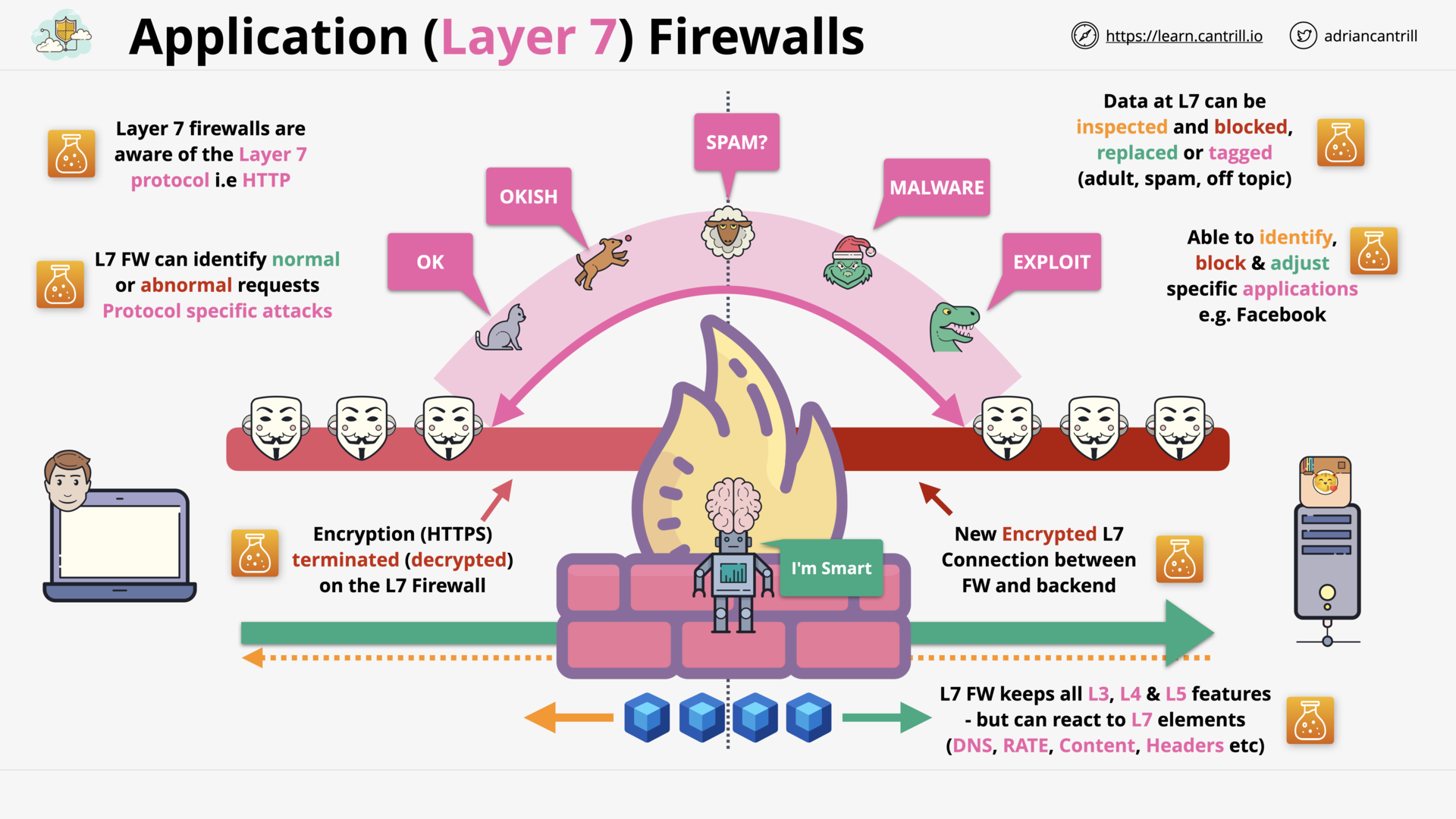 Firewall - Layer 7
Firewall - Layer 7
what does firewall layer 7 do?
Firewall Layer 7 can:
- understand HTTP/HTTPs.
- and even decrypt the data (terminate TLS encryption) and encrypt again for the backend.
👉️ React to:
- HTTP: Content, Headers, DNS, Rate…
- SMTP: Mail metadata
Web Application Firewall (WAF), WEBACLs, Rule Groups and Rules (19:18)
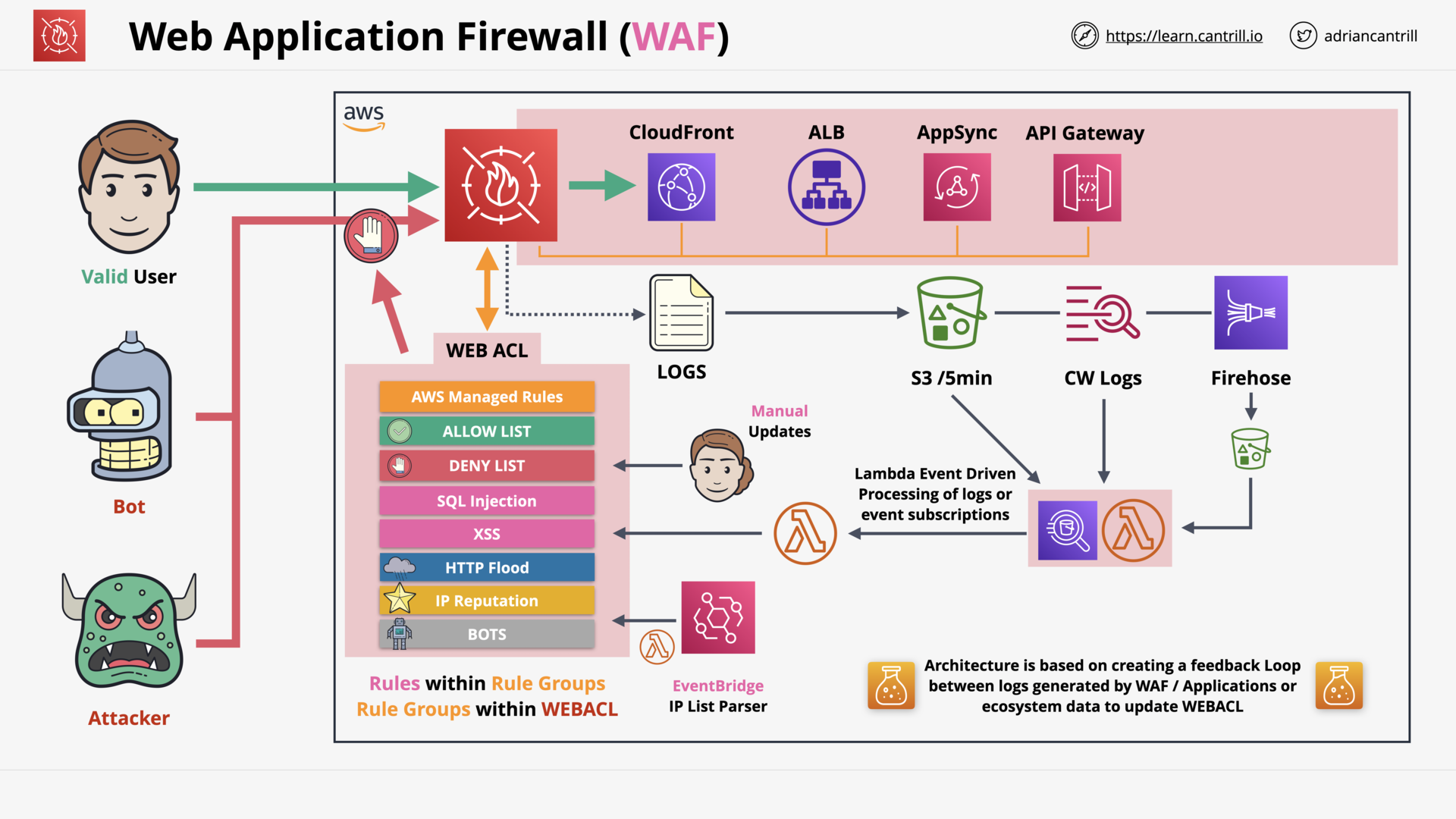 WAF - Architecture
WAF - Architecture
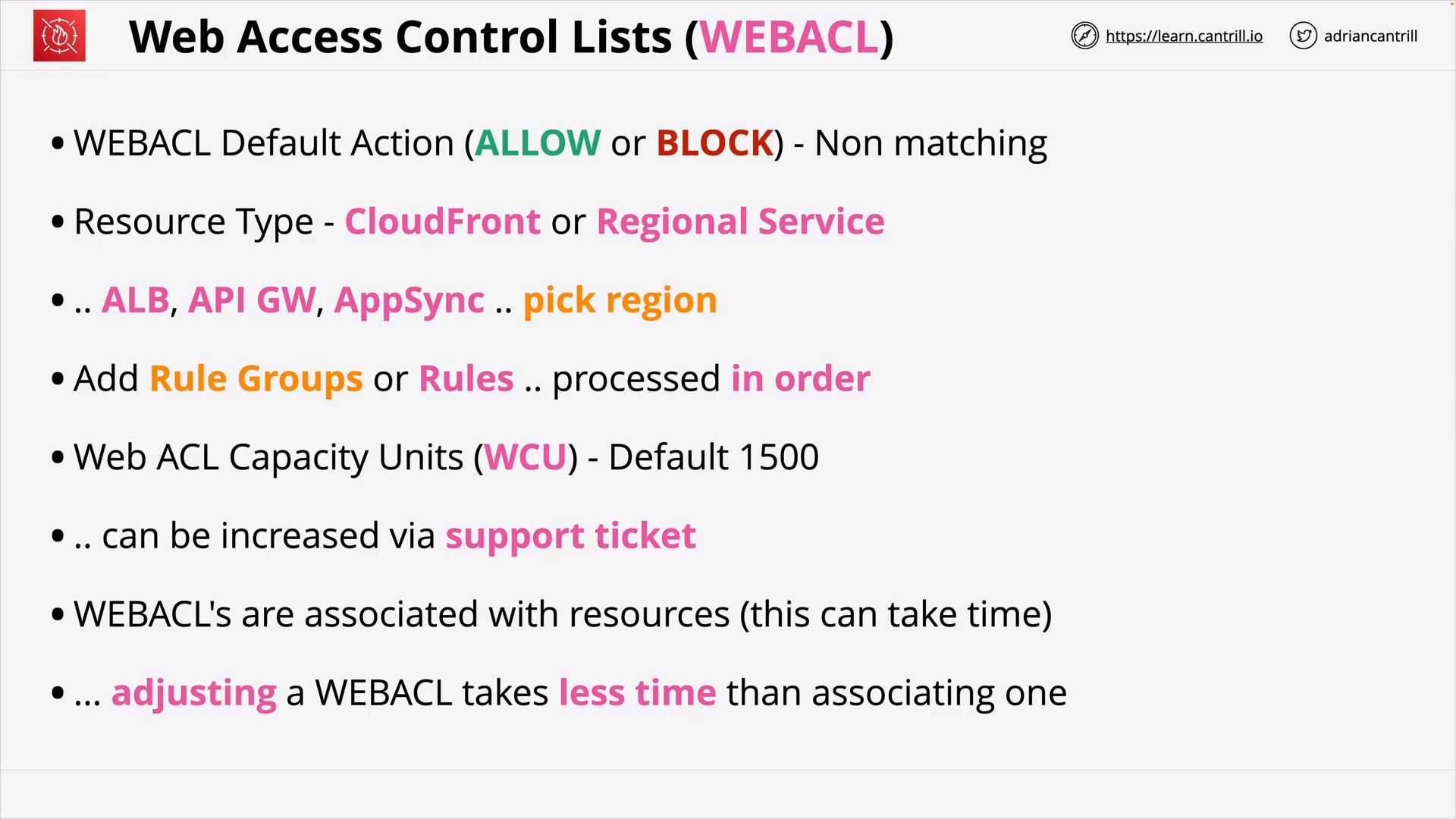 WAF - Web ACL
WAF - Web ACL
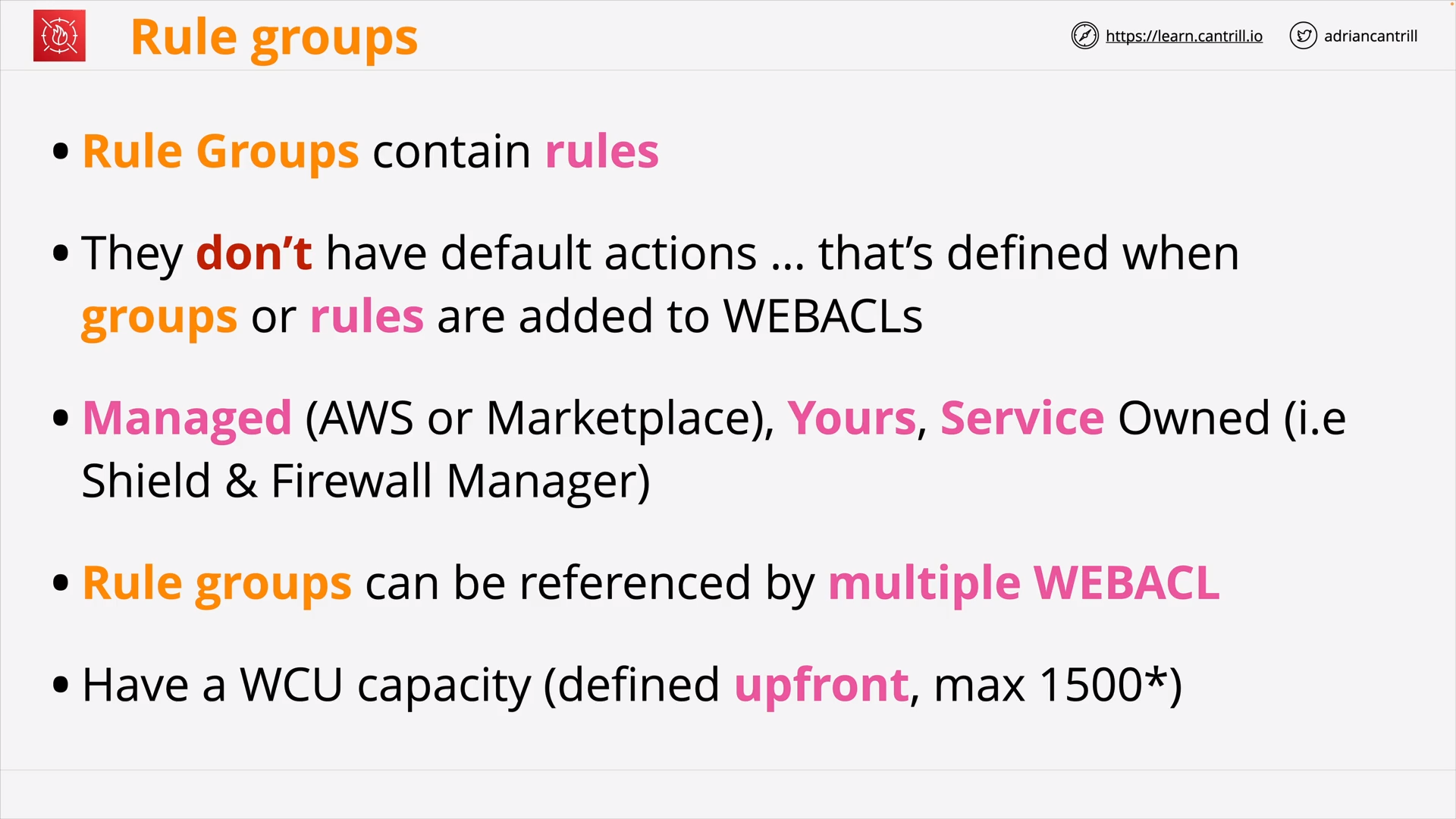 WAF - Rule Groups
WAF - Rule Groups
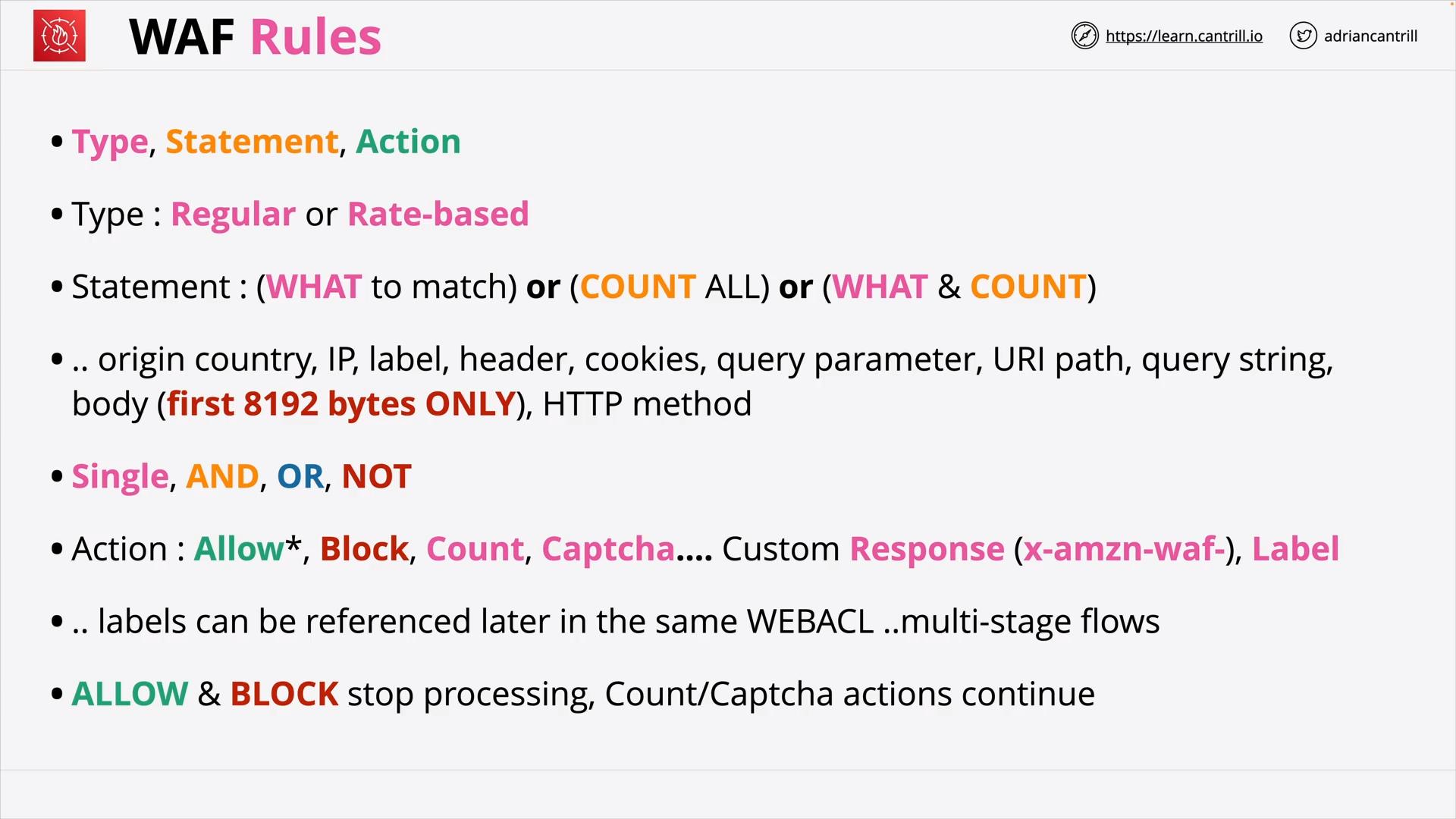 WAF - Rules (Type - Statement - Action)
WAF - Rules (Type - Statement - Action)
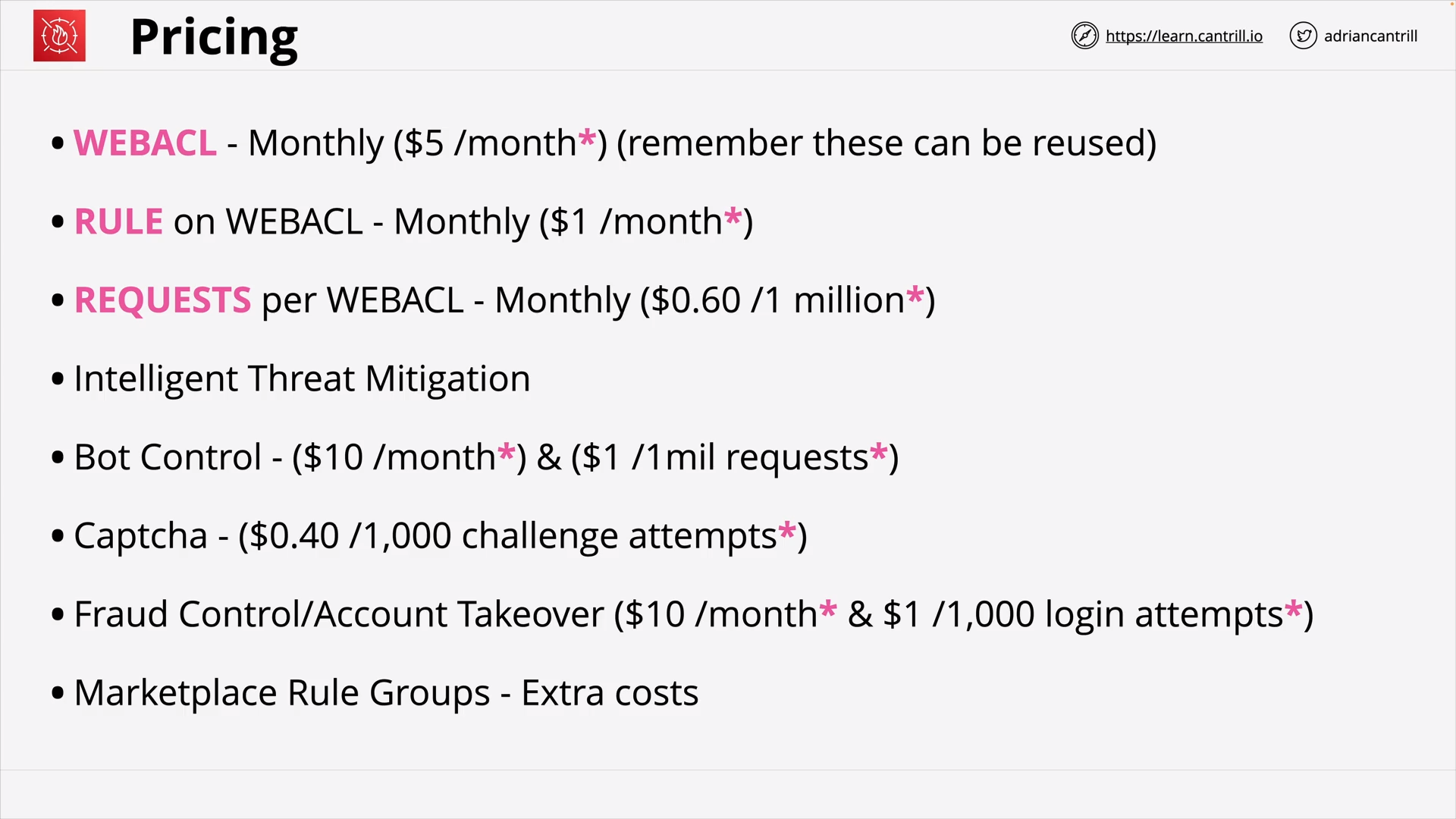 WAF - Pricing
WAF - Pricing
AWS Shield (9:47)
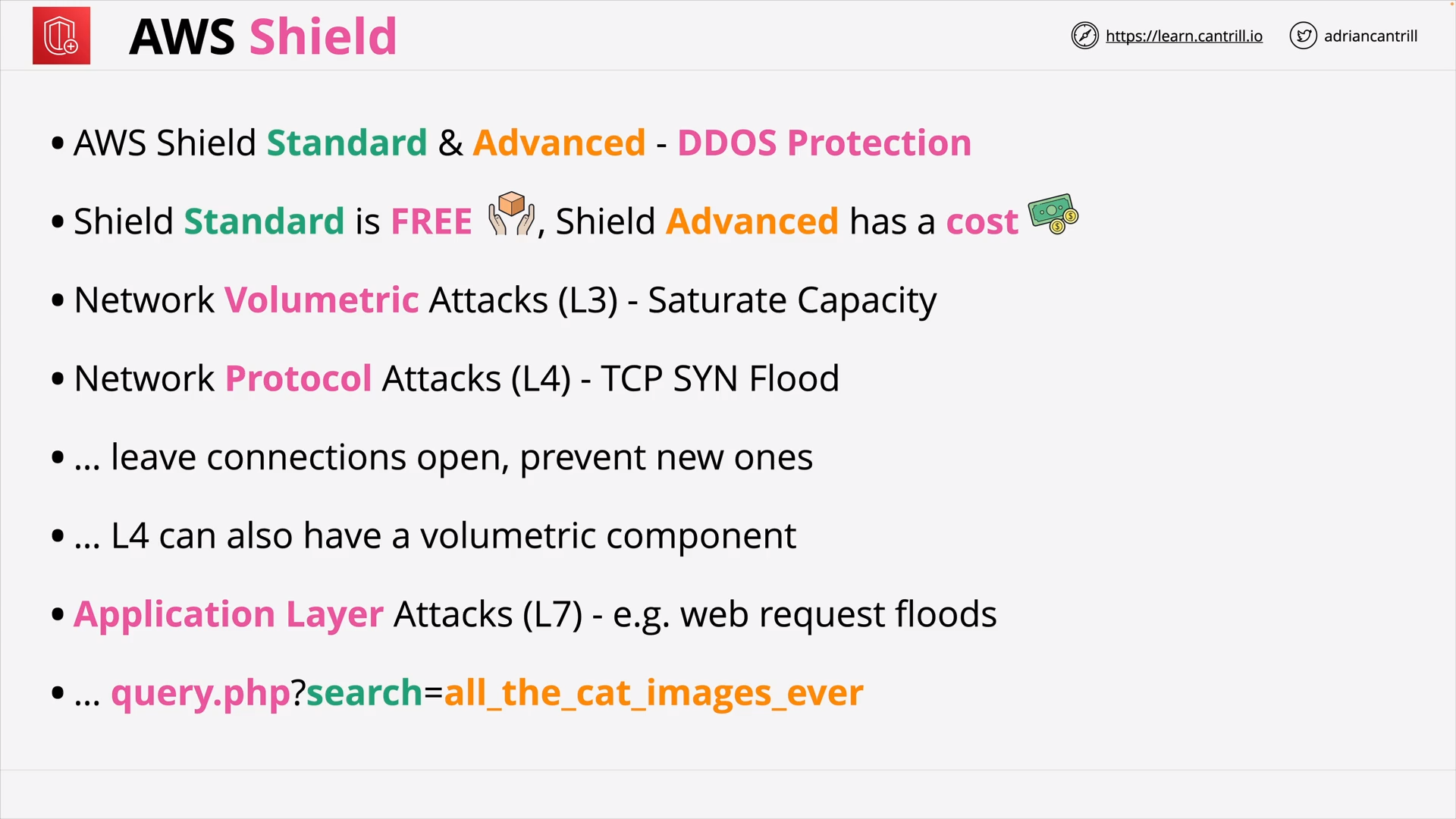 AWS Shield - DDOS Protection
AWS Shield - DDOS Protection
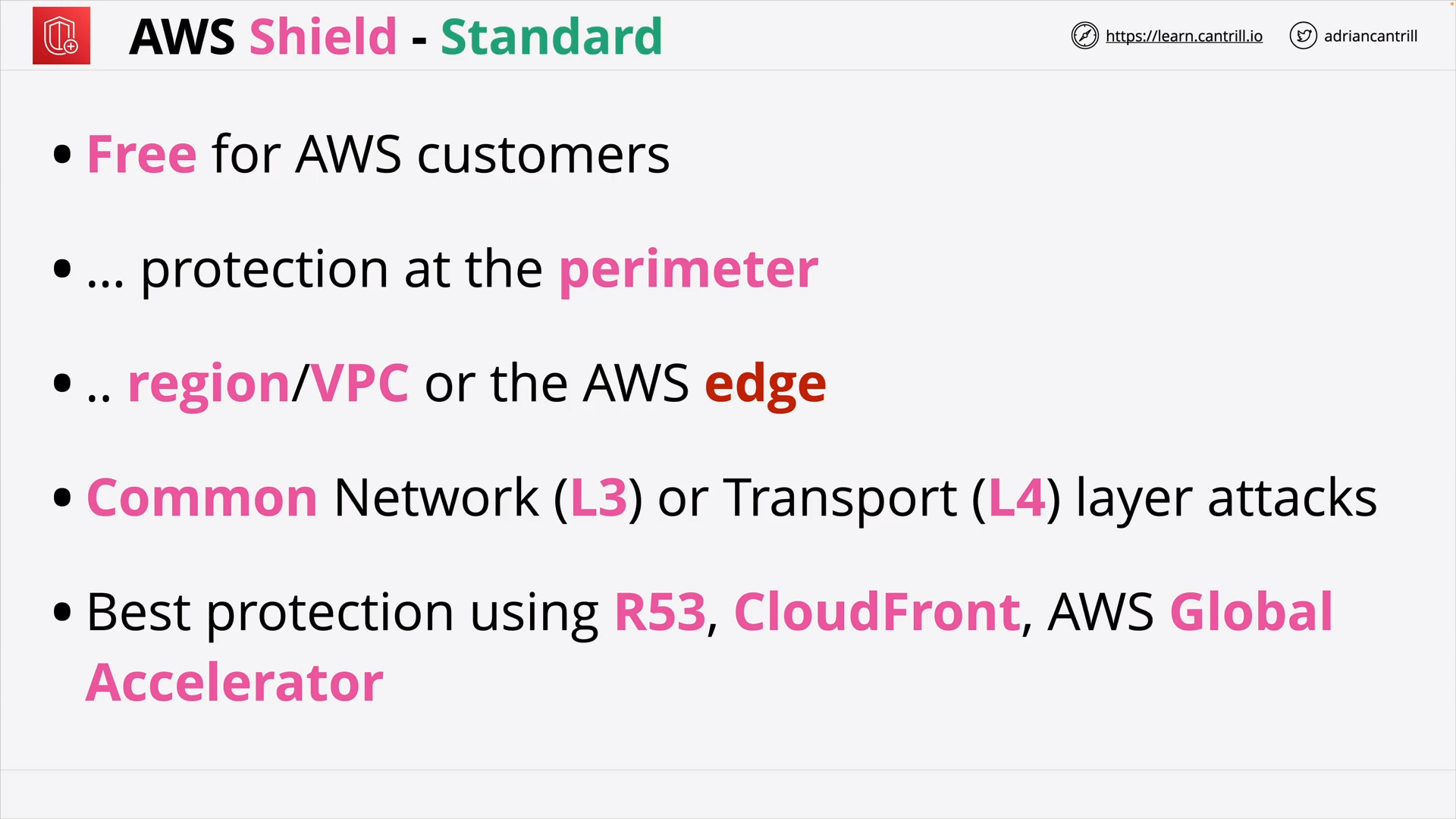 AWS Shield - Standard - Free - L3/L4
AWS Shield - Standard - Free - L3/L4
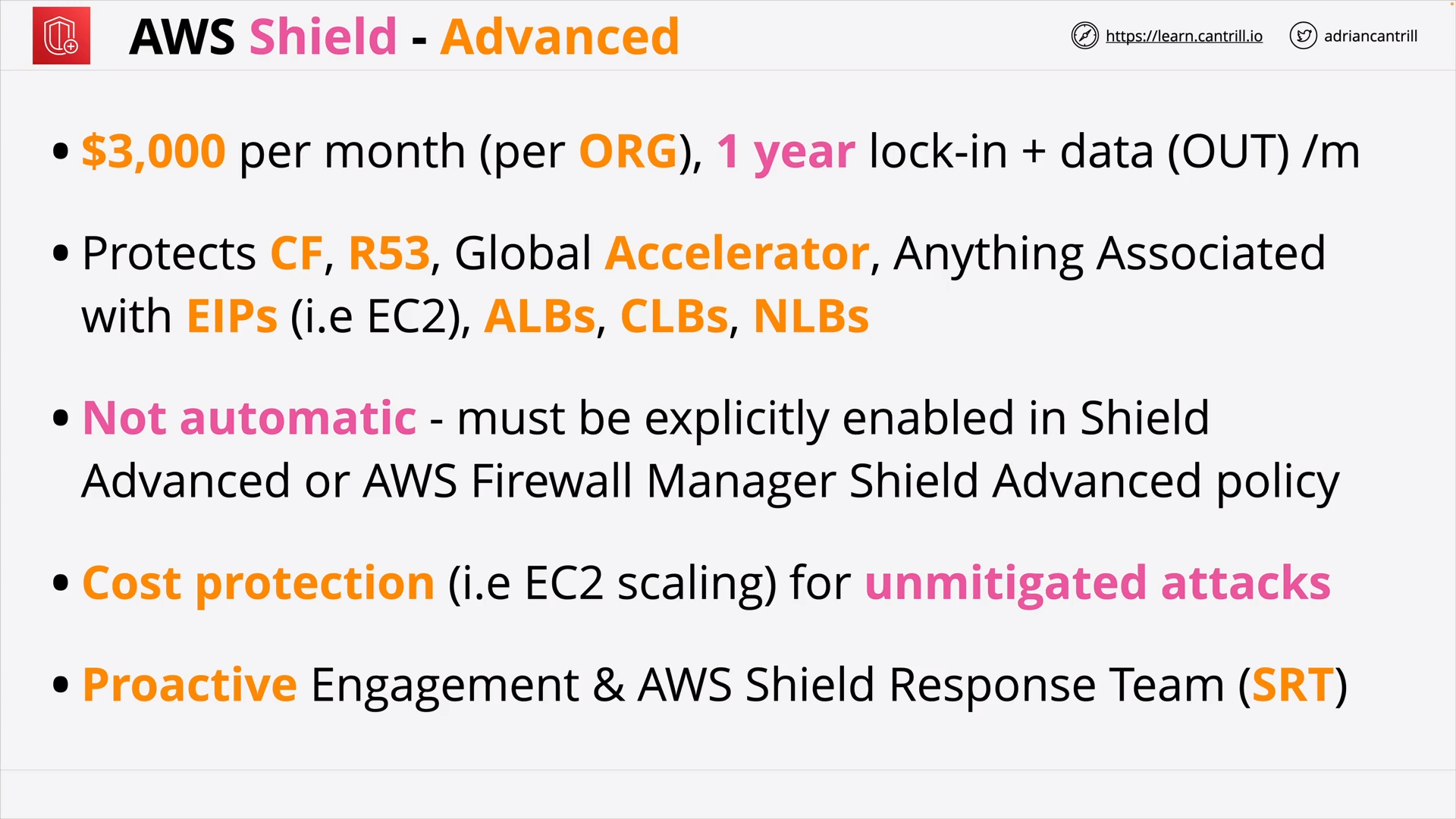 AWS Shield - Advanced - Pricing & Benefit
AWS Shield - Advanced - Pricing & Benefit
 AWS Shield - Advanced - WAF Integration (L7) - Realtime + Health-based
AWS Shield - Advanced - WAF Integration (L7) - Realtime + Health-based
CloudHSM (14:36)
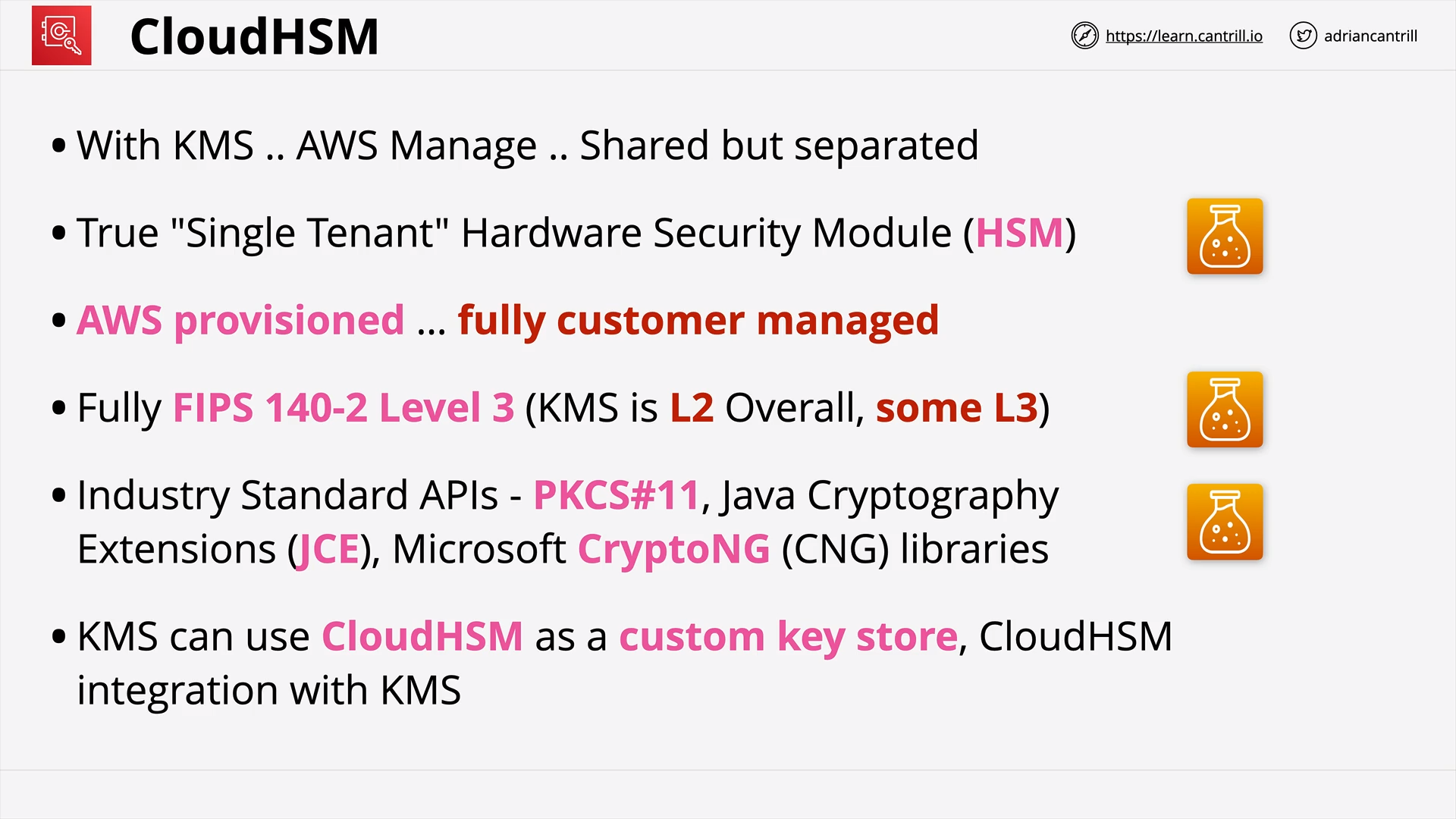 CloudHSM - Overview
CloudHSM - Overview
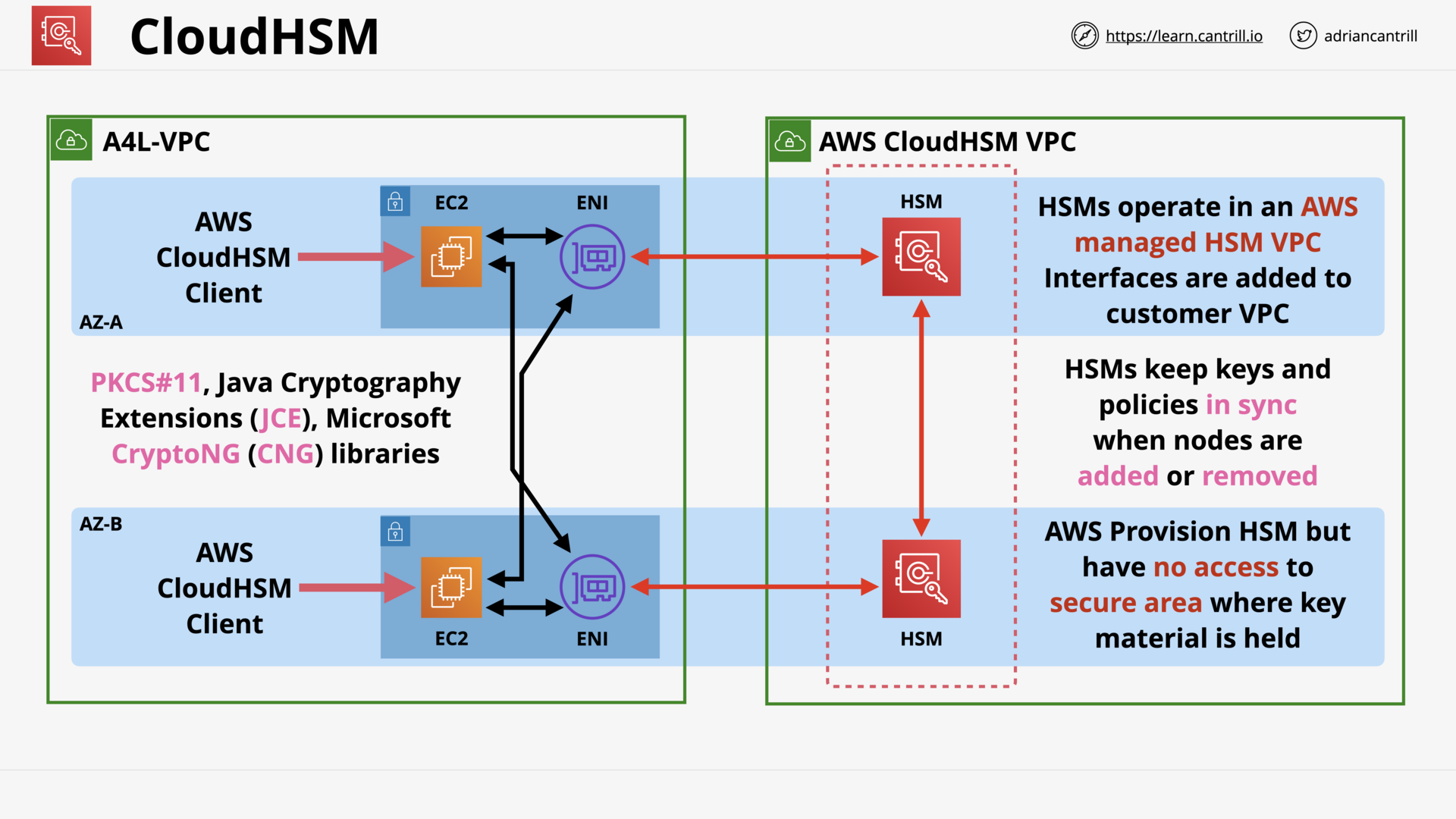 CloudHSM - Architecture
CloudHSM - Architecture
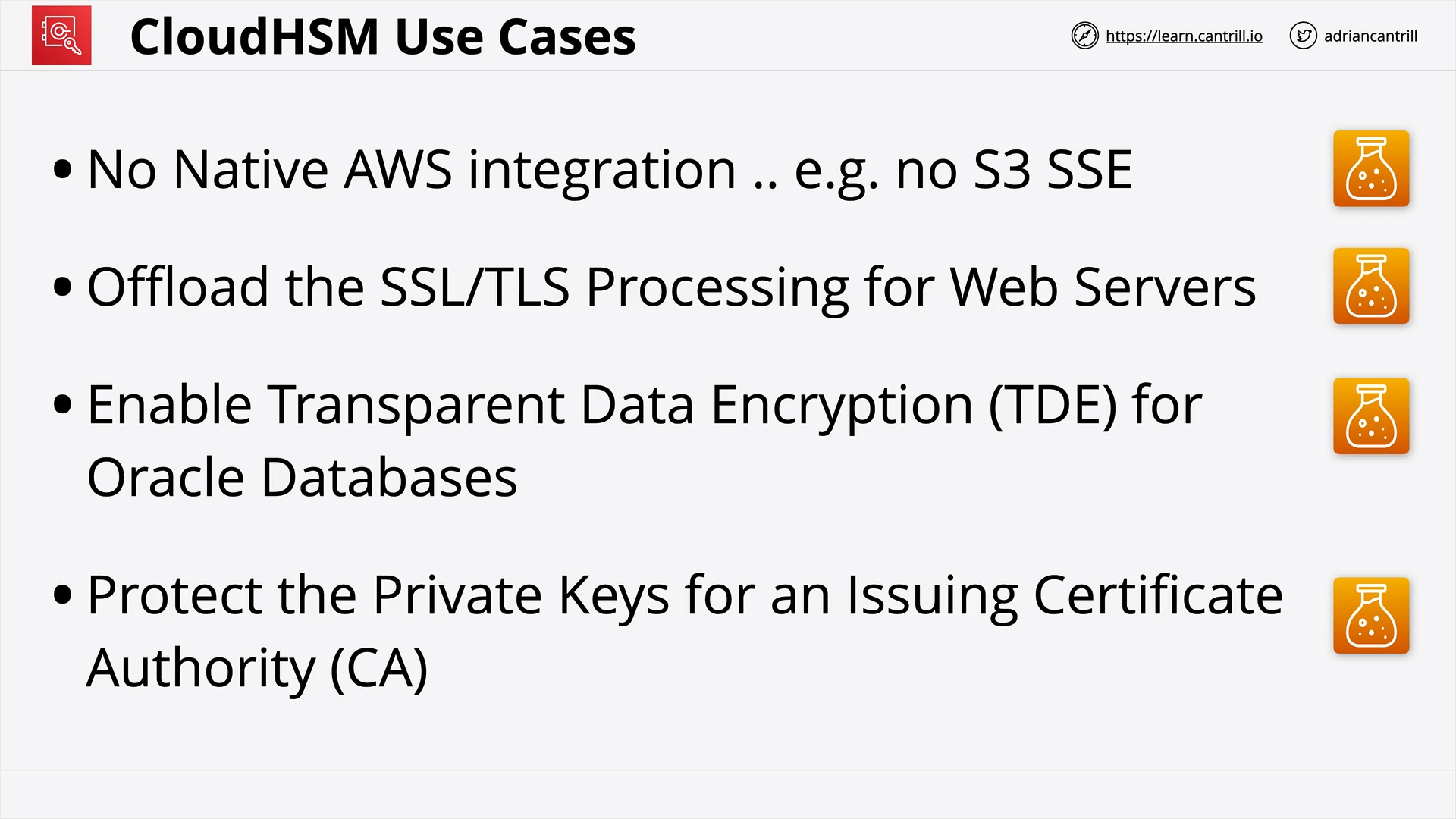 CloudHSM - Use Cases
CloudHSM - Use Cases
AWS Config (6:14)
 AWS Config - Record config changes over time on resources
AWS Config - Record config changes over time on resources
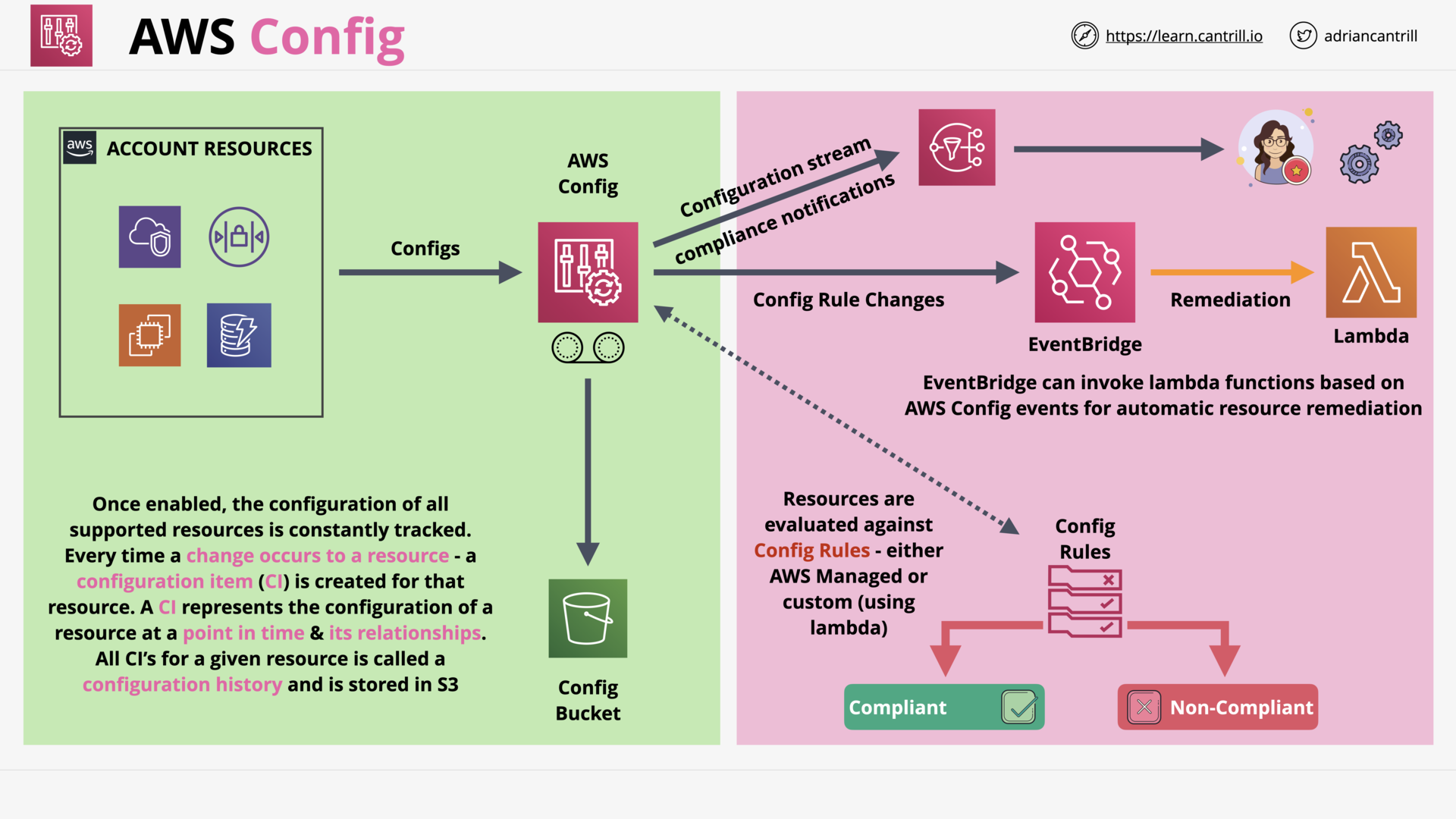 AWS Config - Architecture
AWS Config - Architecture
Amazon Macie (12:04)
 Amazon Macie - Data Security for S3
Amazon Macie - Data Security for S3
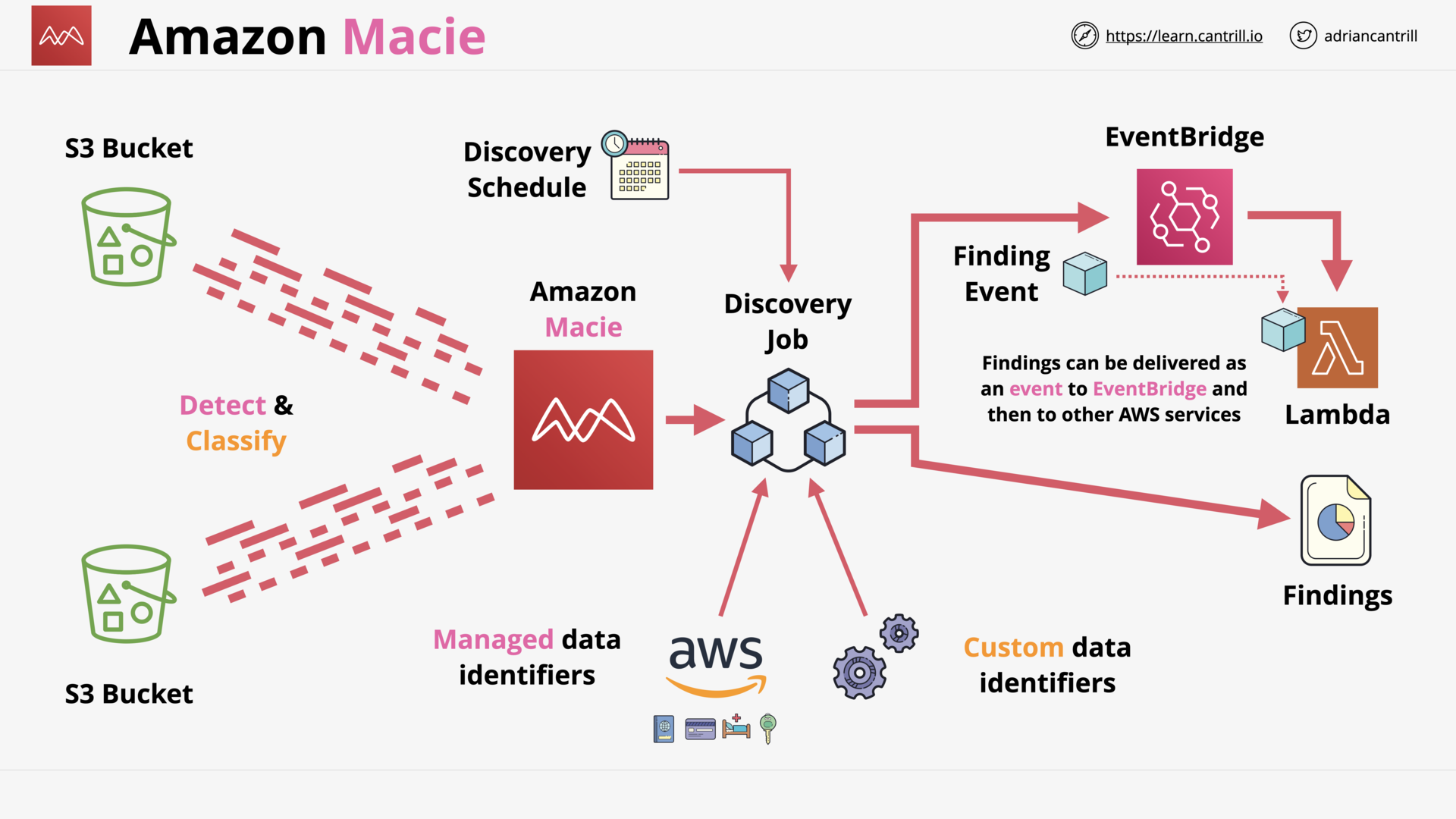 Amazon Macie - Architecture
Amazon Macie - Architecture
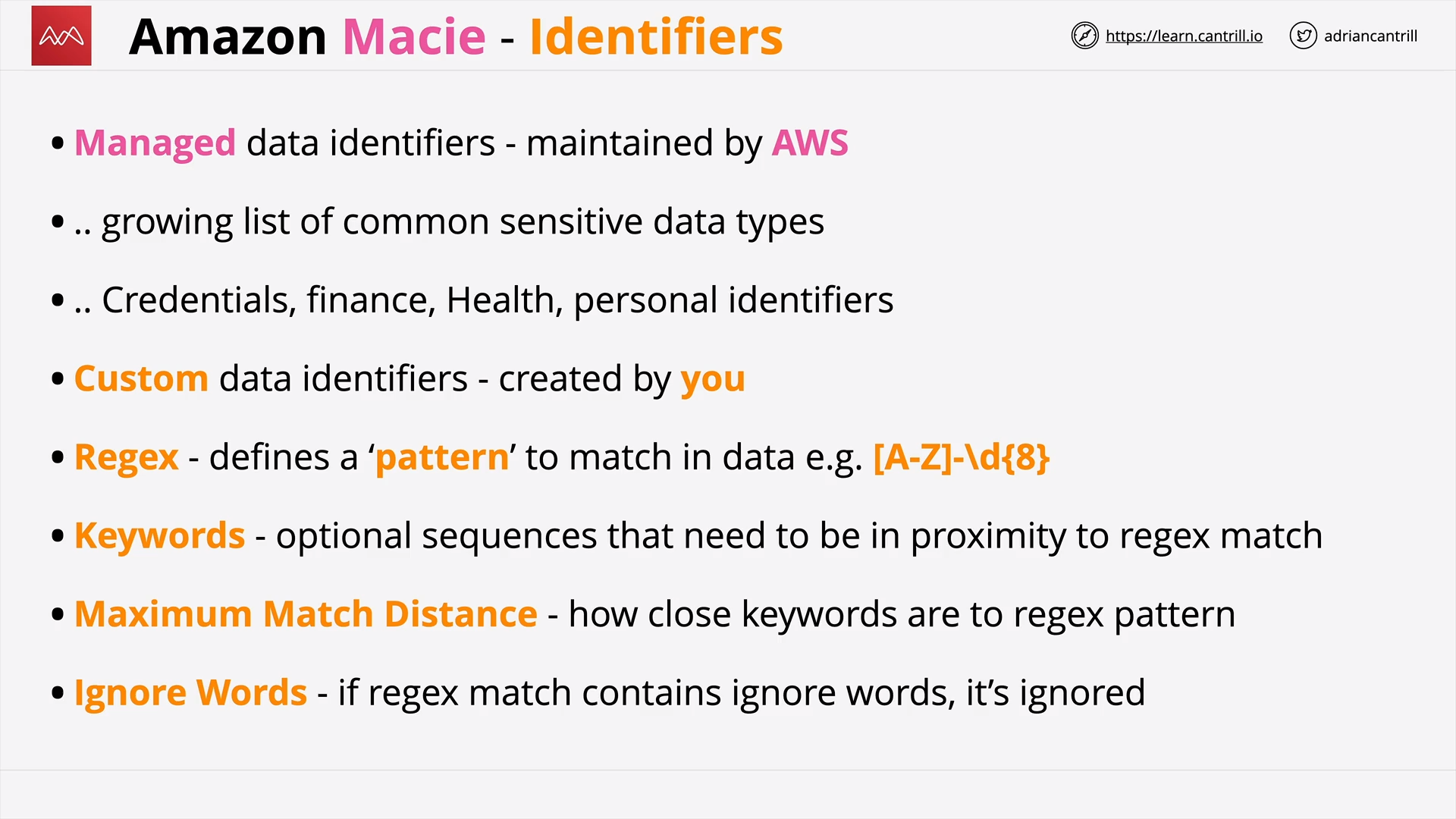 Amazon Macie - Identifiers (AWS-managed / Custom)
Amazon Macie - Identifiers (AWS-managed / Custom)
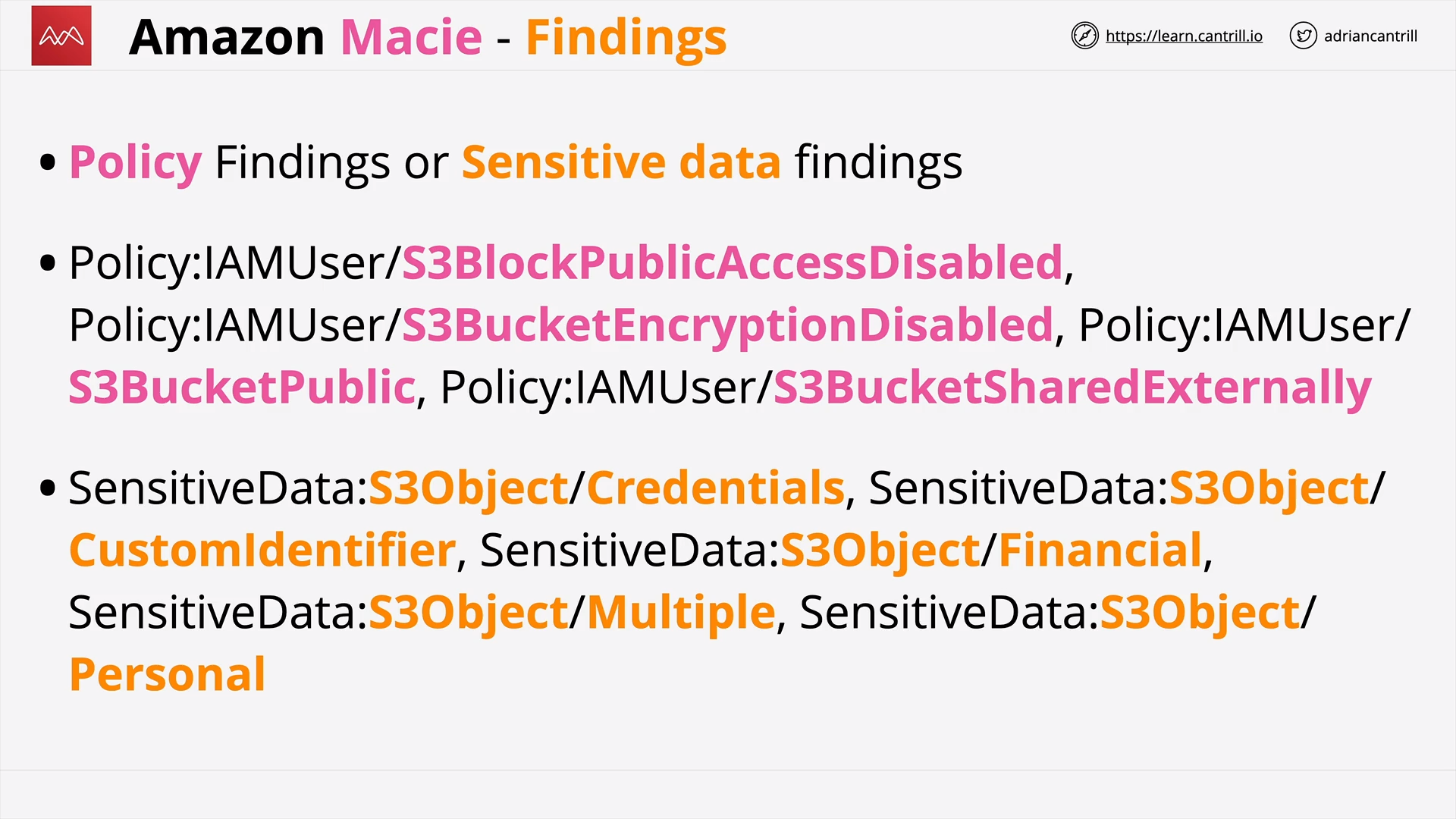 Amazon Macie - Findings (Policy / Sensitive data)
Amazon Macie - Findings (Policy / Sensitive data)
[DEMO] Amazon Macie (15:35)
Amazon Inspector (6:28)
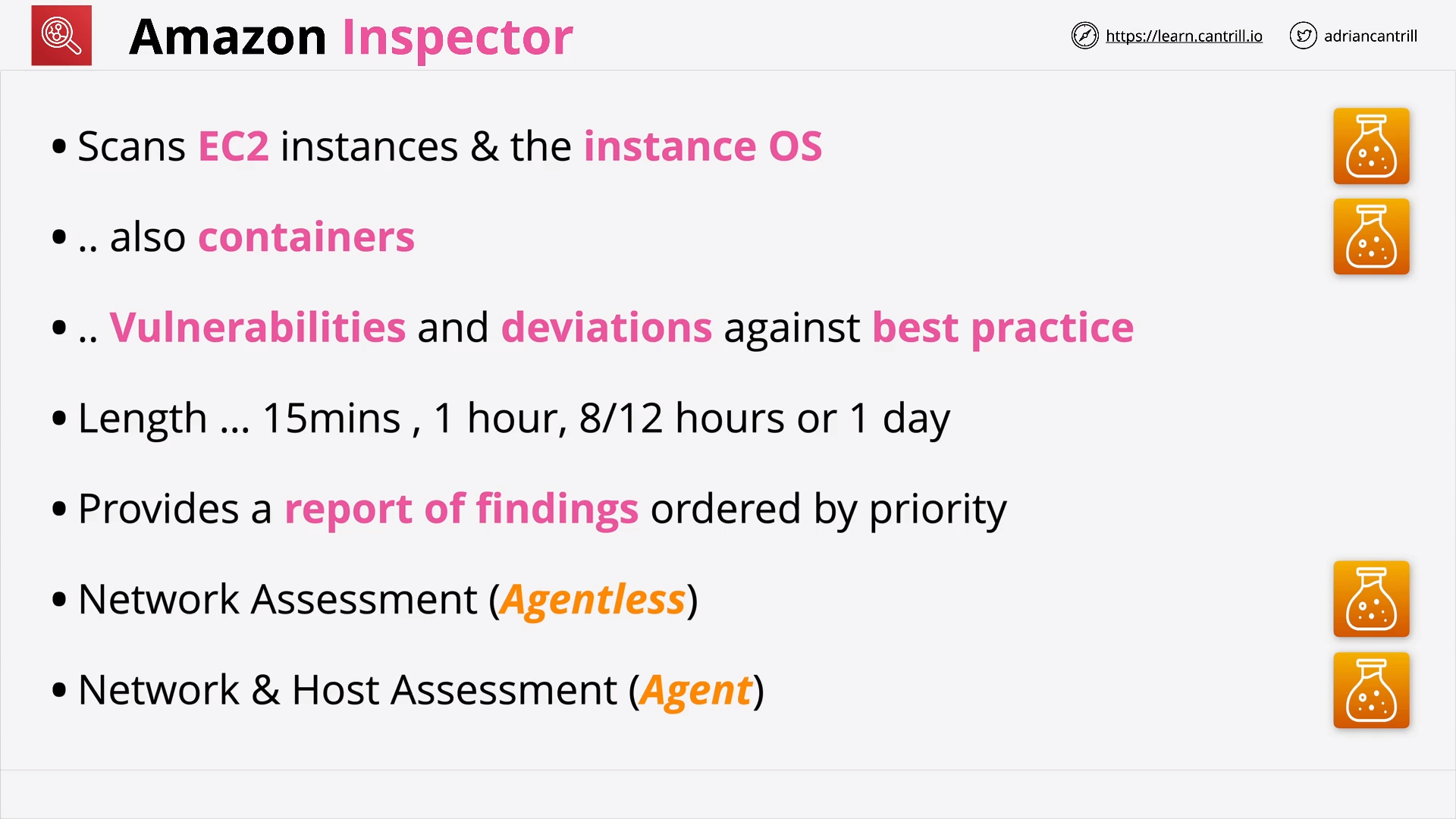 Amazon Inspector - Scan EC2 Instance + OS / Containers
Amazon Inspector - Scan EC2 Instance + OS / Containers
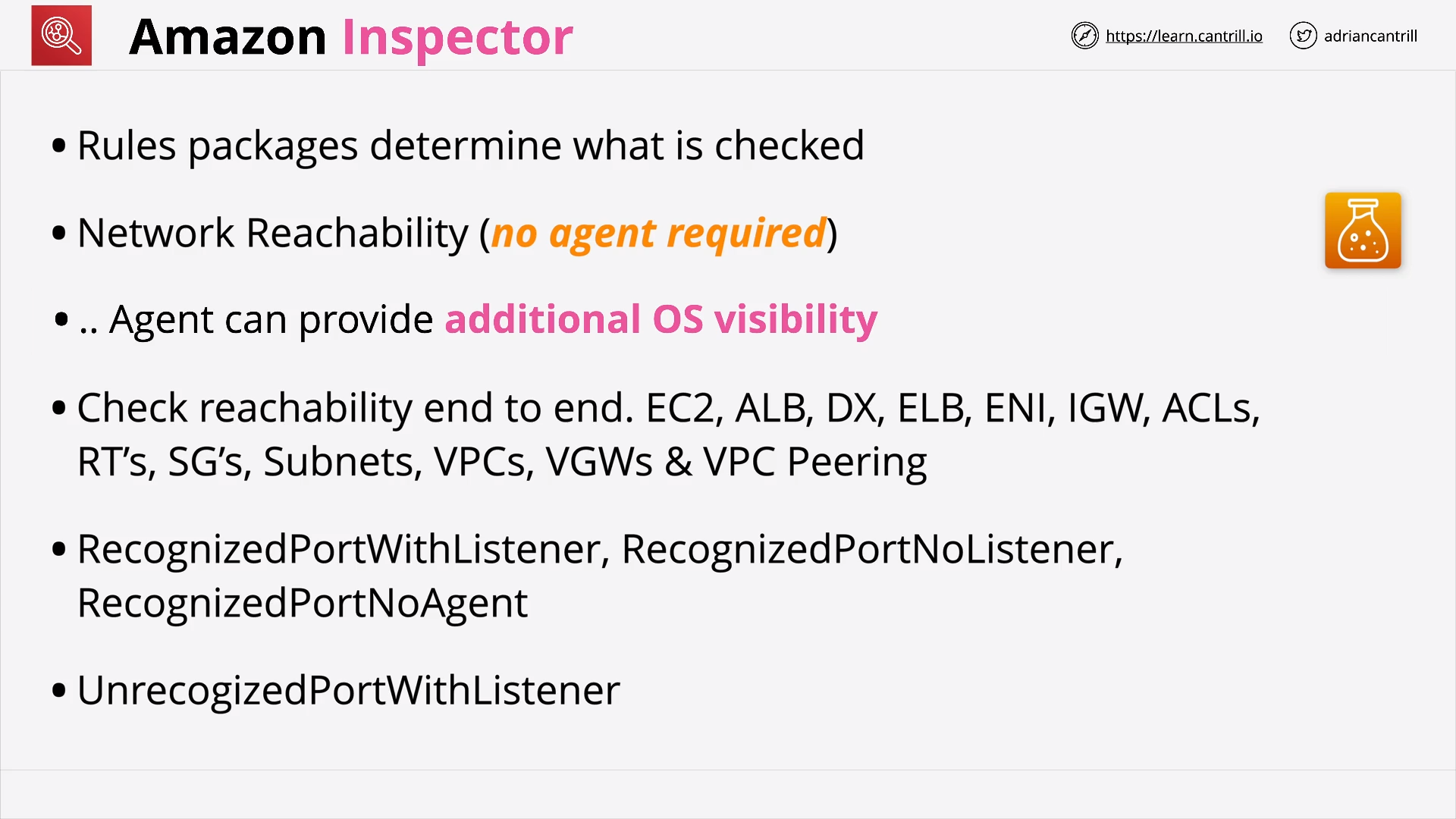 Amazon Inspector - Agentless & Agent
Amazon Inspector - Agentless & Agent
 Amazon Inspector - CVE, CIS, Security Best Practices
Amazon Inspector - CVE, CIS, Security Best Practices
Amazon GuardDuty (4:14)
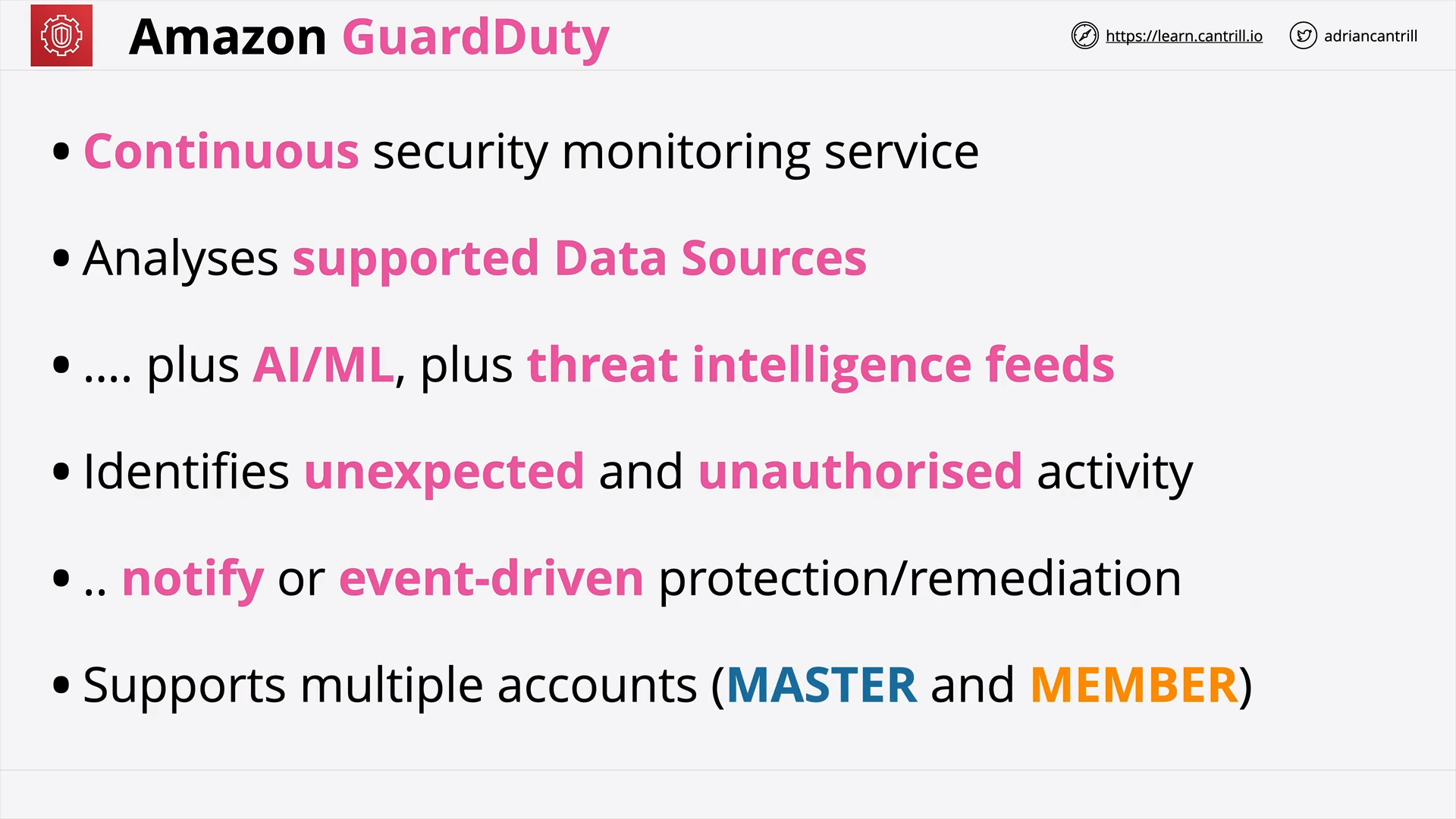 Amazon GuardDuty - Security Monitoring Service (with AI/ML)
Amazon GuardDuty - Security Monitoring Service (with AI/ML)
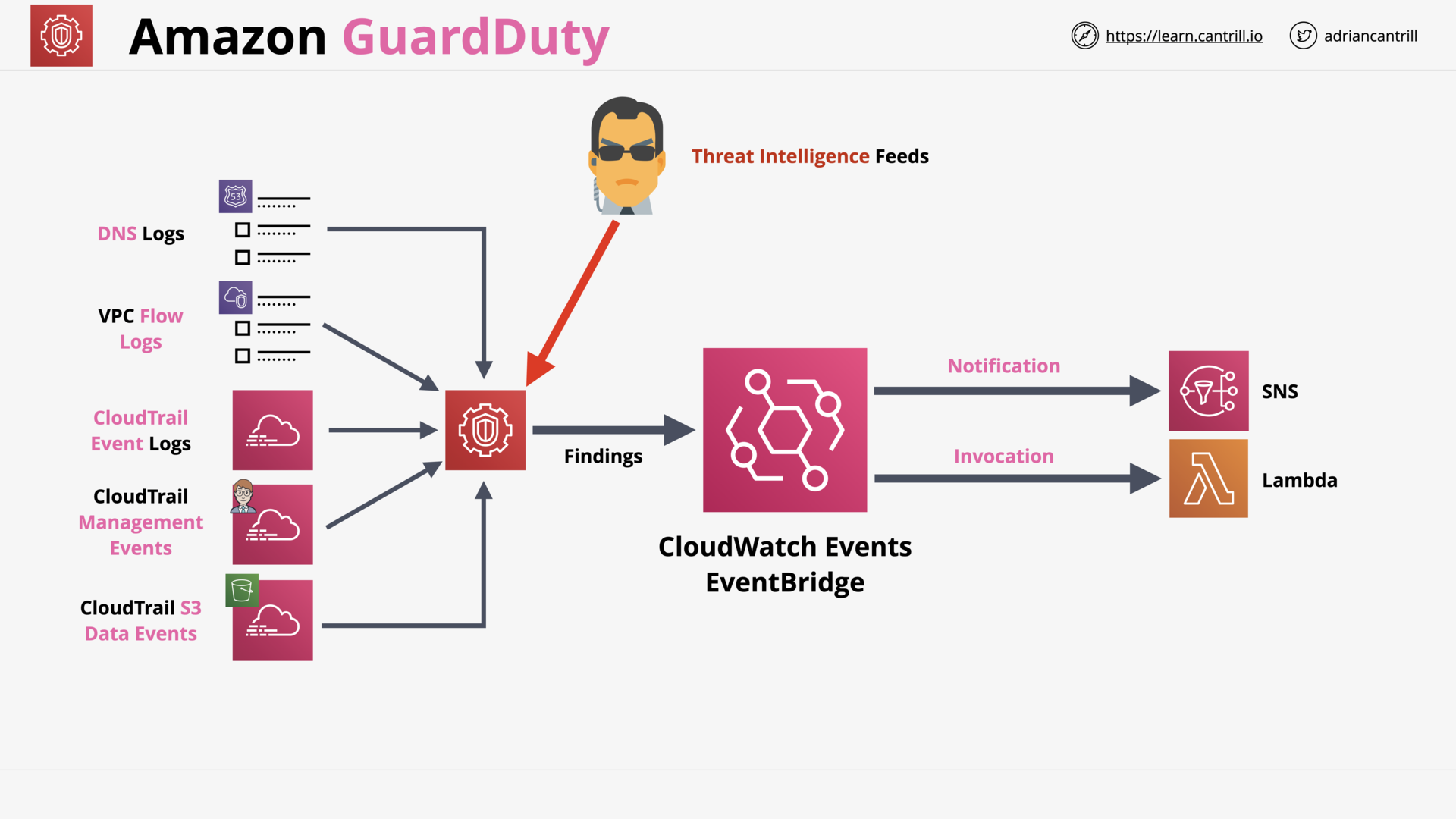 Amazon GuardDuty - Architecture
Amazon GuardDuty - Architecture
Section Quiz
INFRASTRUCTURE AS CODE (CLOUDFORMATION)
CloudFormation Physical & Logical Resources (7:30)
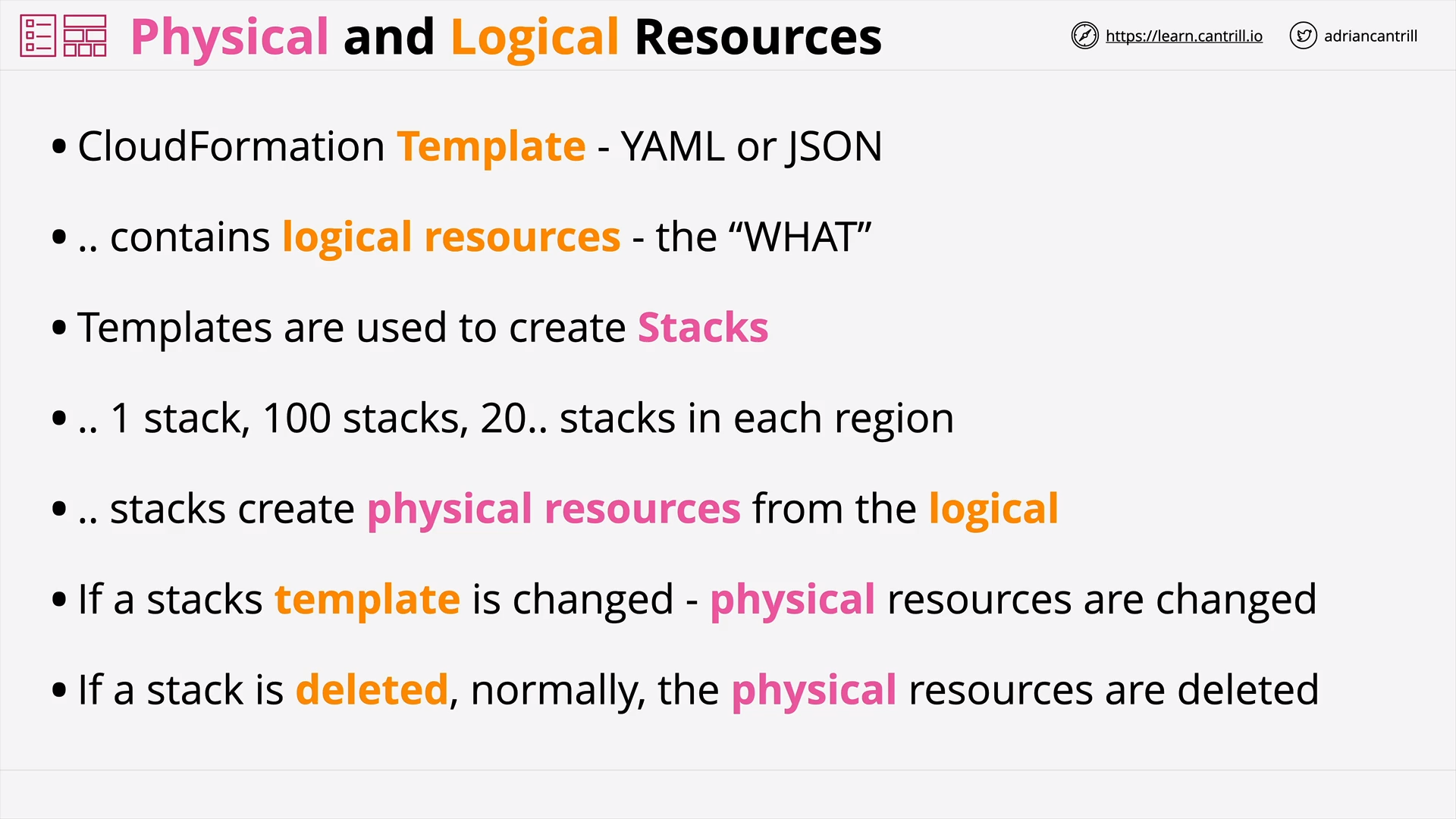 Physical Resource / Logical Resource - Template - Stack
Physical Resource / Logical Resource - Template - Stack
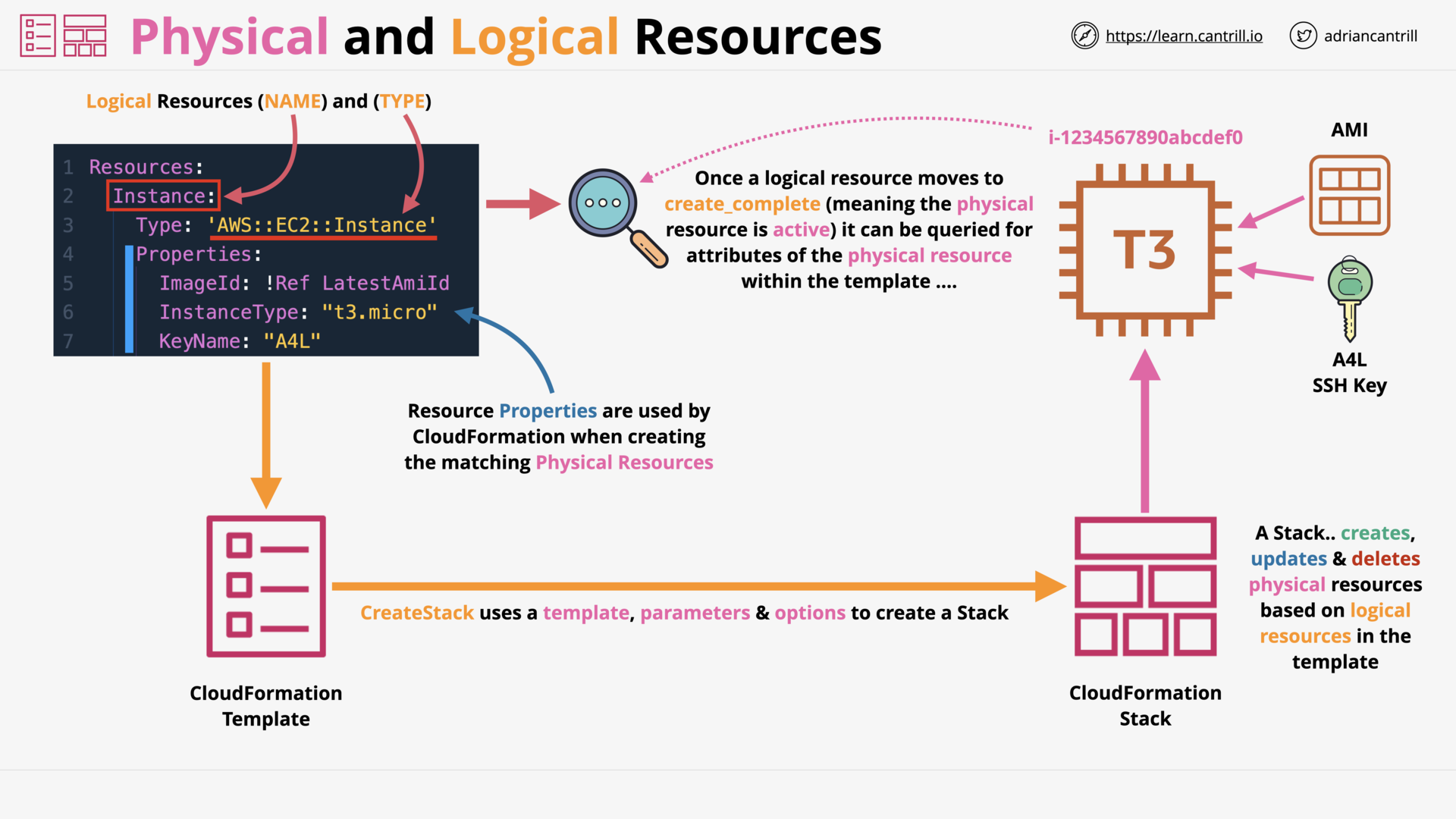 CloudFormation - Architecture
CloudFormation - Architecture
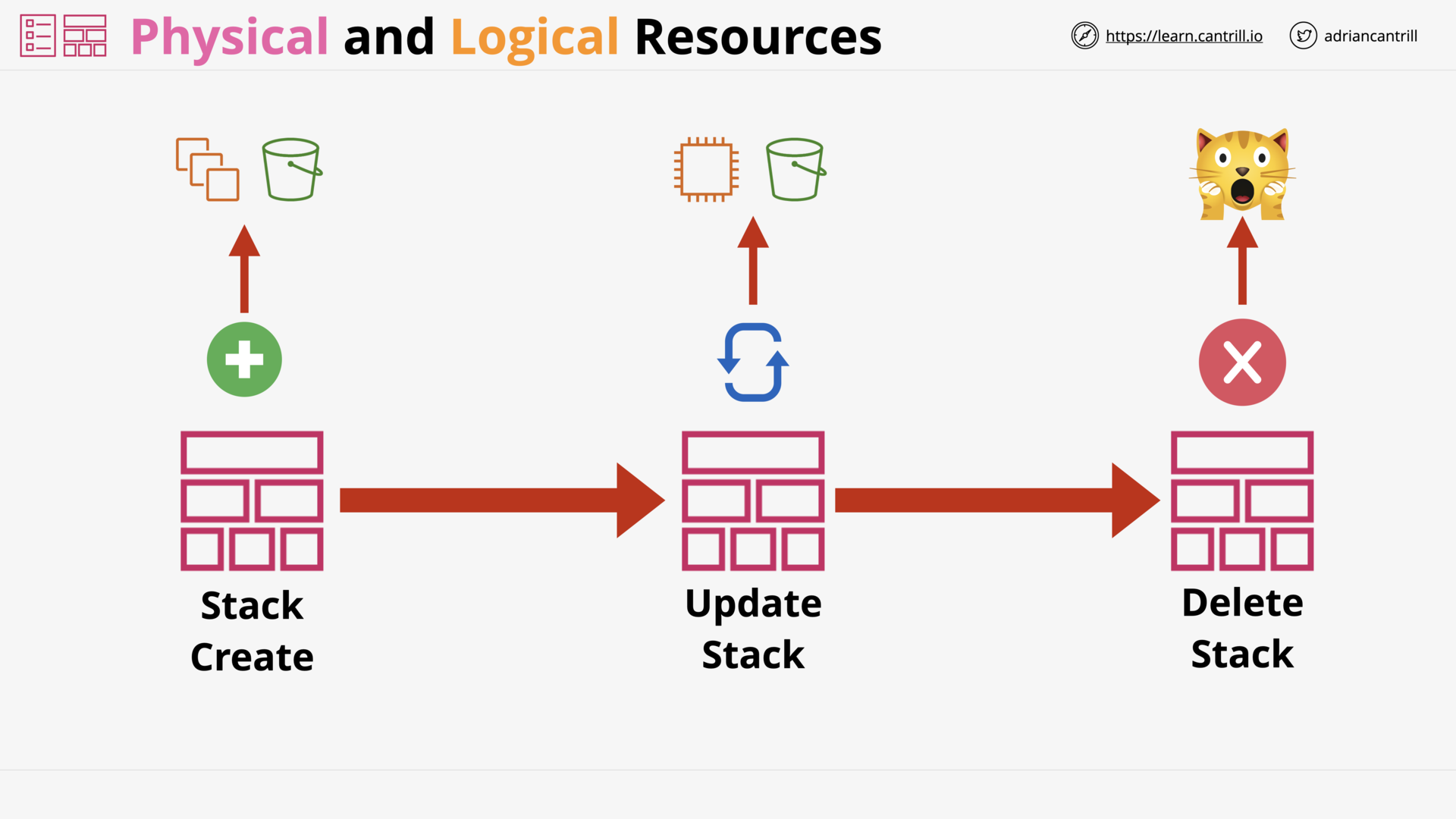 CloudFormation - Stack Create/Update/Delete
CloudFormation - Stack Create/Update/Delete
[DEMO] Simple Non Portable Template - PART1 (10:28)
[DEMO] Simple Non Portable Template - PART2 (11:28)
CloudFormation Template and Pseudo Parameters (6:53)
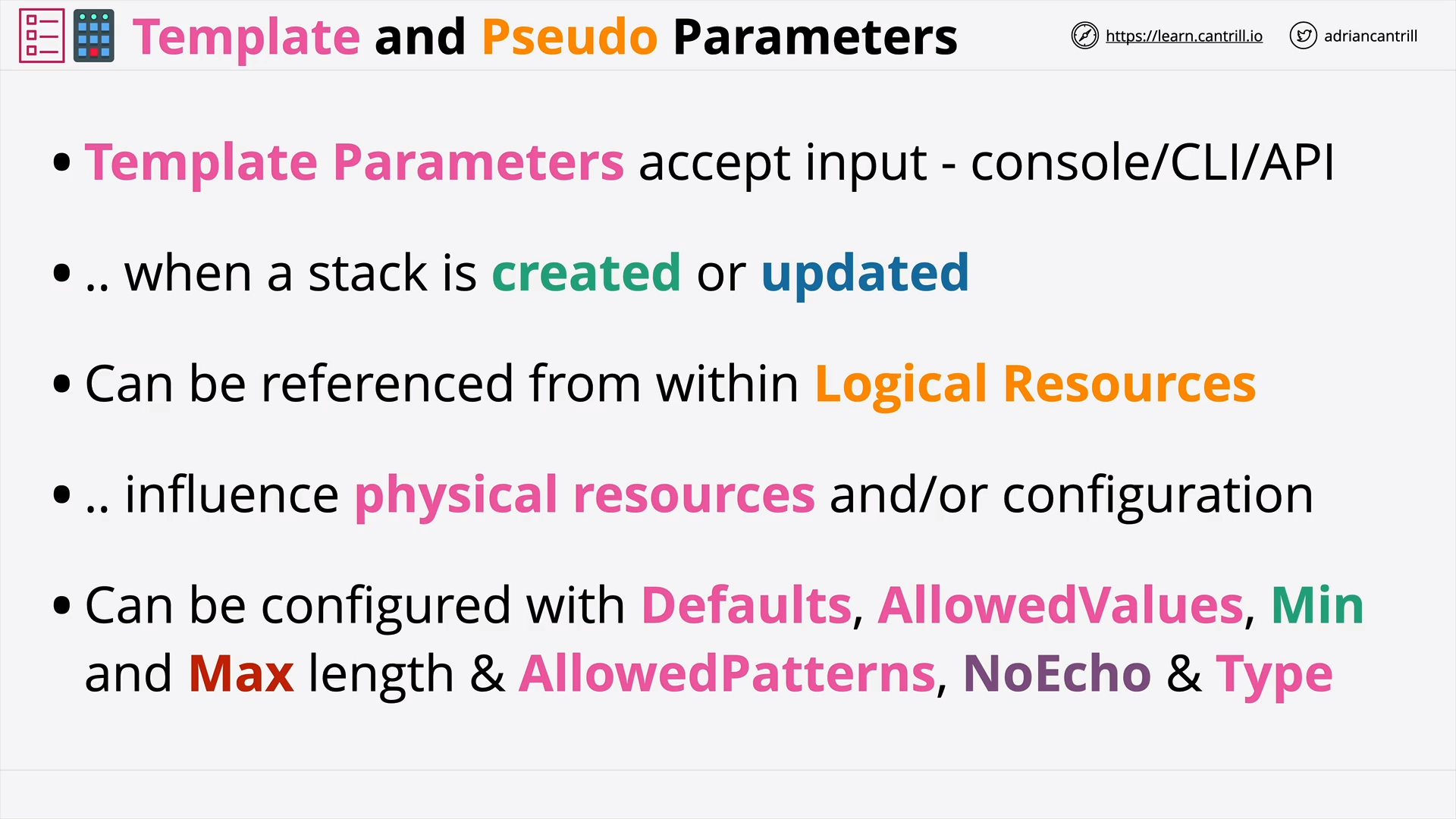 Template/Pseudo Parameters - Overview
Template/Pseudo Parameters - Overview
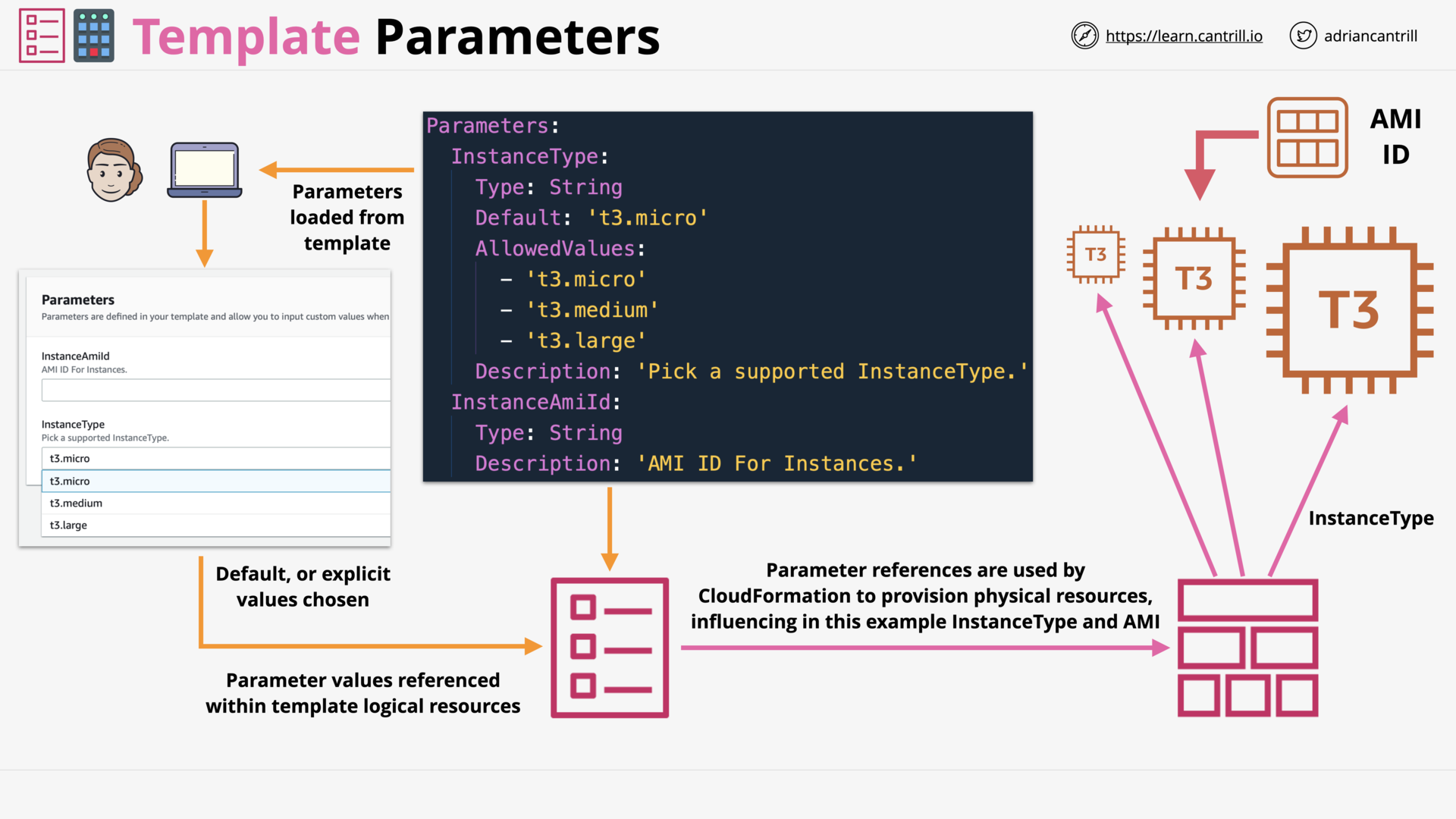 Template Parameters - Input for Cfn Template
Template Parameters - Input for Cfn Template
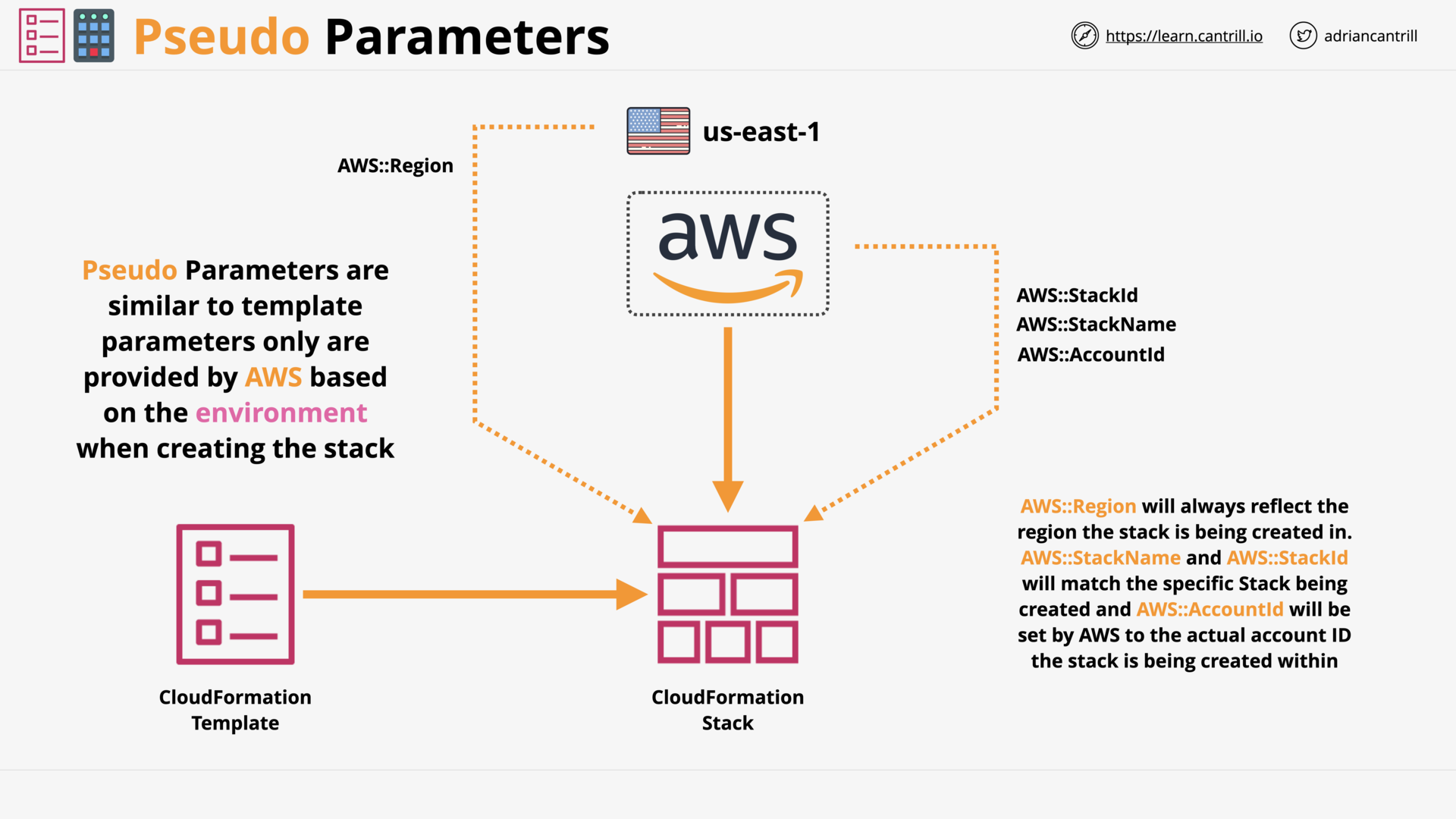 Pseudo Parameters - Provided by AWS based on the Stack environment
Pseudo Parameters - Provided by AWS based on the Stack environment
mindmap
Parameters used in Cfn Template
Template **Parameter**
_Pseudo_ Parameter
_Public_ Parameter<br/>from AWS Systems Manager Parameter Store
what are the difference between _cfn - **pseudo parameters**_ and _aws systems manager - **public parameters**_
-
Cfn - Pseudo Parameters: Parameters predefined by AWS CloudFormation
e.g.
AWS::AccountIdAWS::RegionAWS::StackIdAWS::StackName
-
AWS Systems Manager Parameter Store - public parameters: Common artifacts published by some AWS services:
e.g.
- EC2: Information about AMIs:
ami-amazon-linux-latestami-windows-latest
- ECS:
/aws/service/ecs/optimized-ami/amazon-linux-2/recommended - EKS:
/aws/service/eks/optimized-ami/1.14/amazon-linux-2/recommended - AWS:
- Services
- Regions
- Availability Zone
- …
See
- EC2: Information about AMIs:
CloudFormation Intrinsic Functions (14:28)
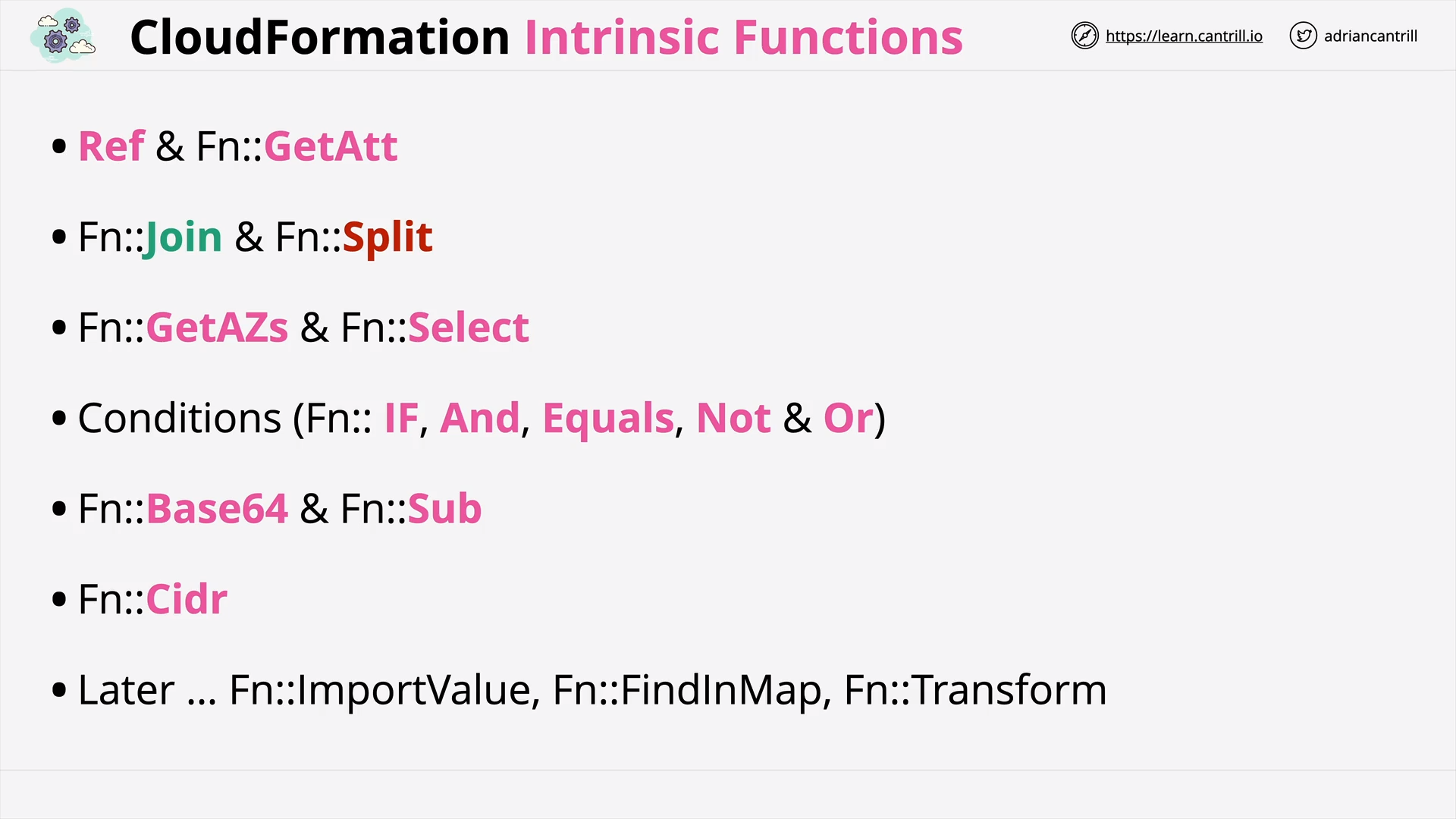 Cfn - Intrinsic Functions
Cfn - Intrinsic Functions
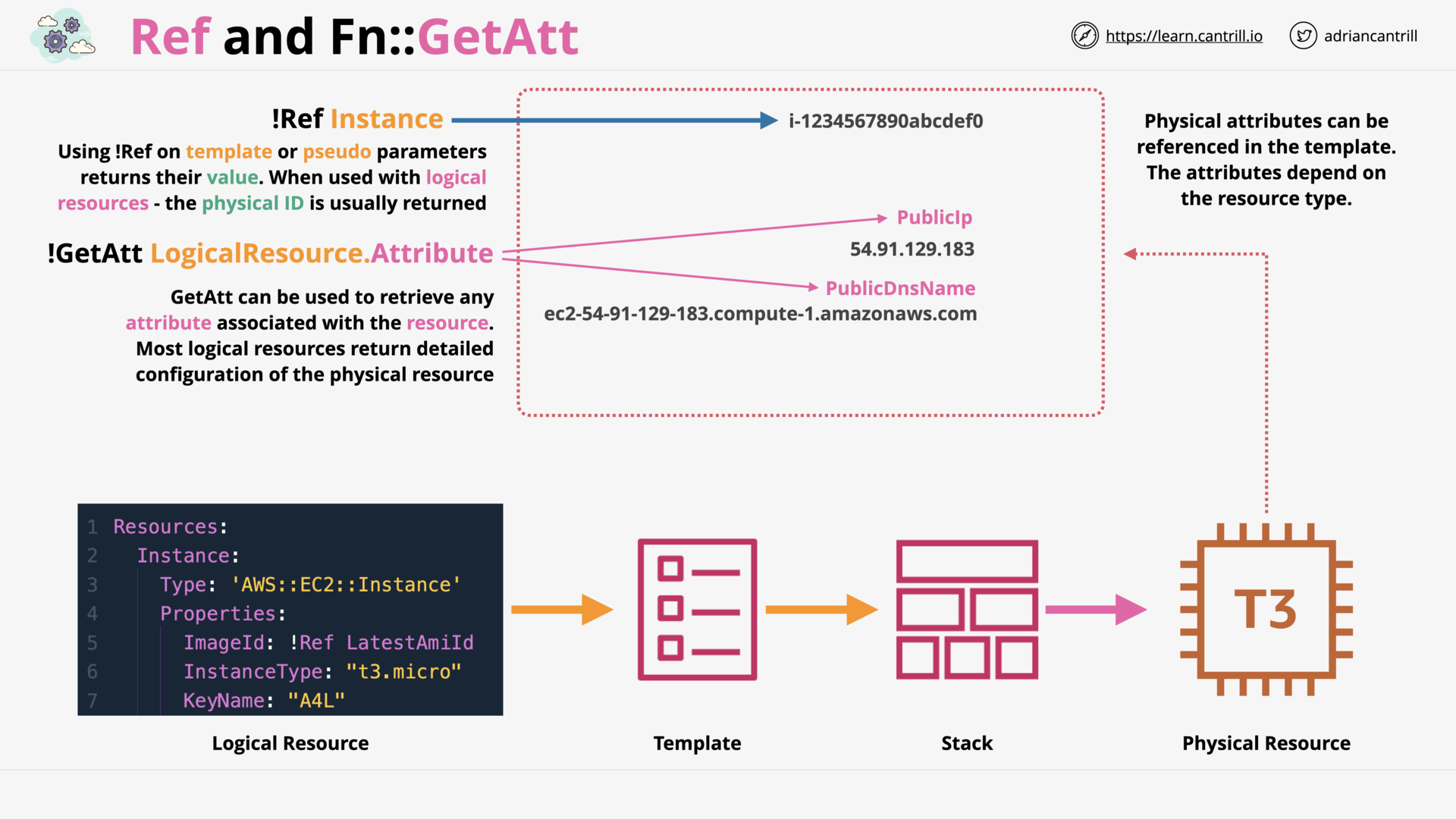 Cfn Intrinsic Functions:
Cfn Intrinsic Functions: Ref & Fn::GetAtt
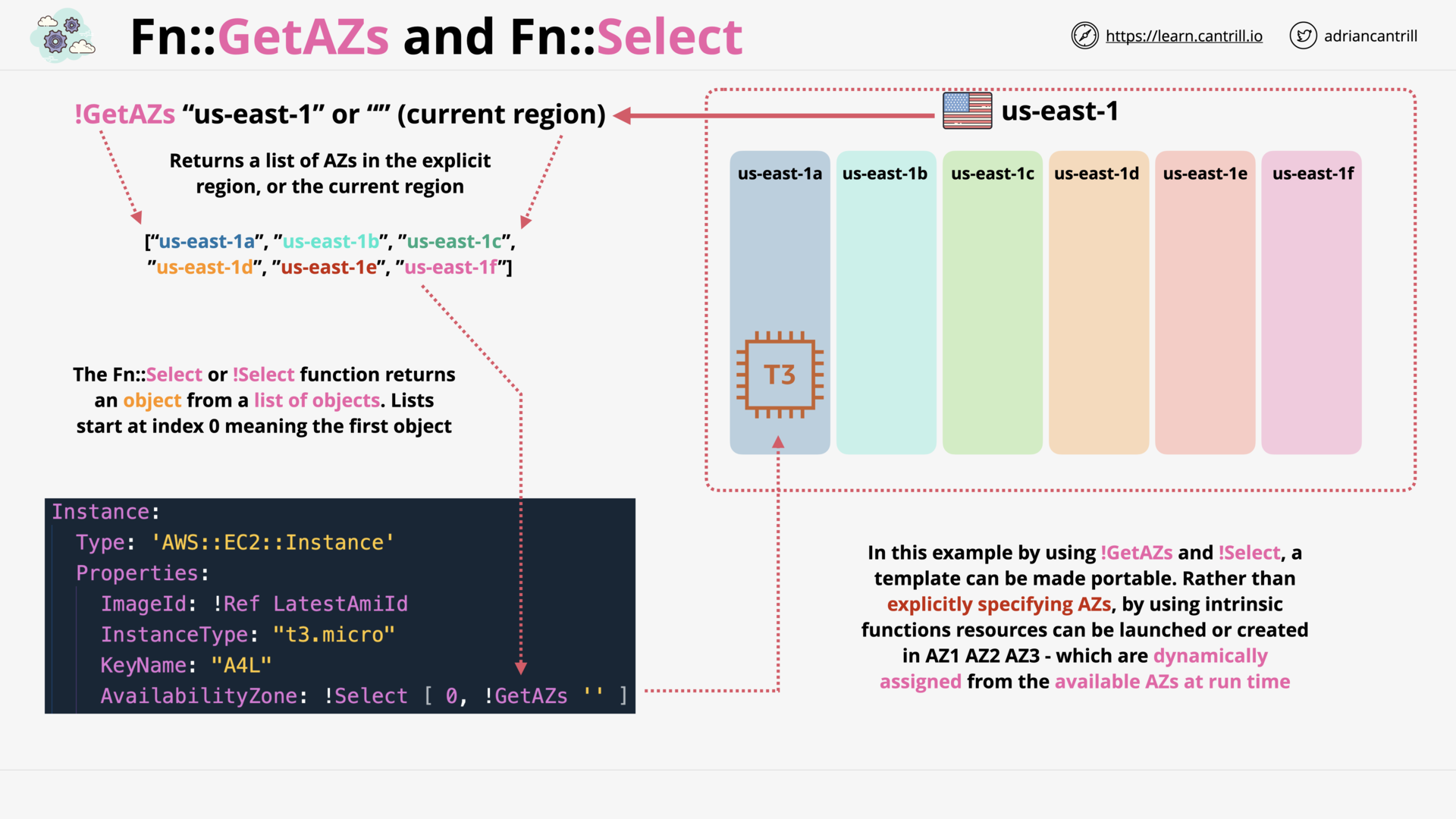 Cfn Intrinsic Functions:
Cfn Intrinsic Functions: Fn:GetAZs & Fn:Select
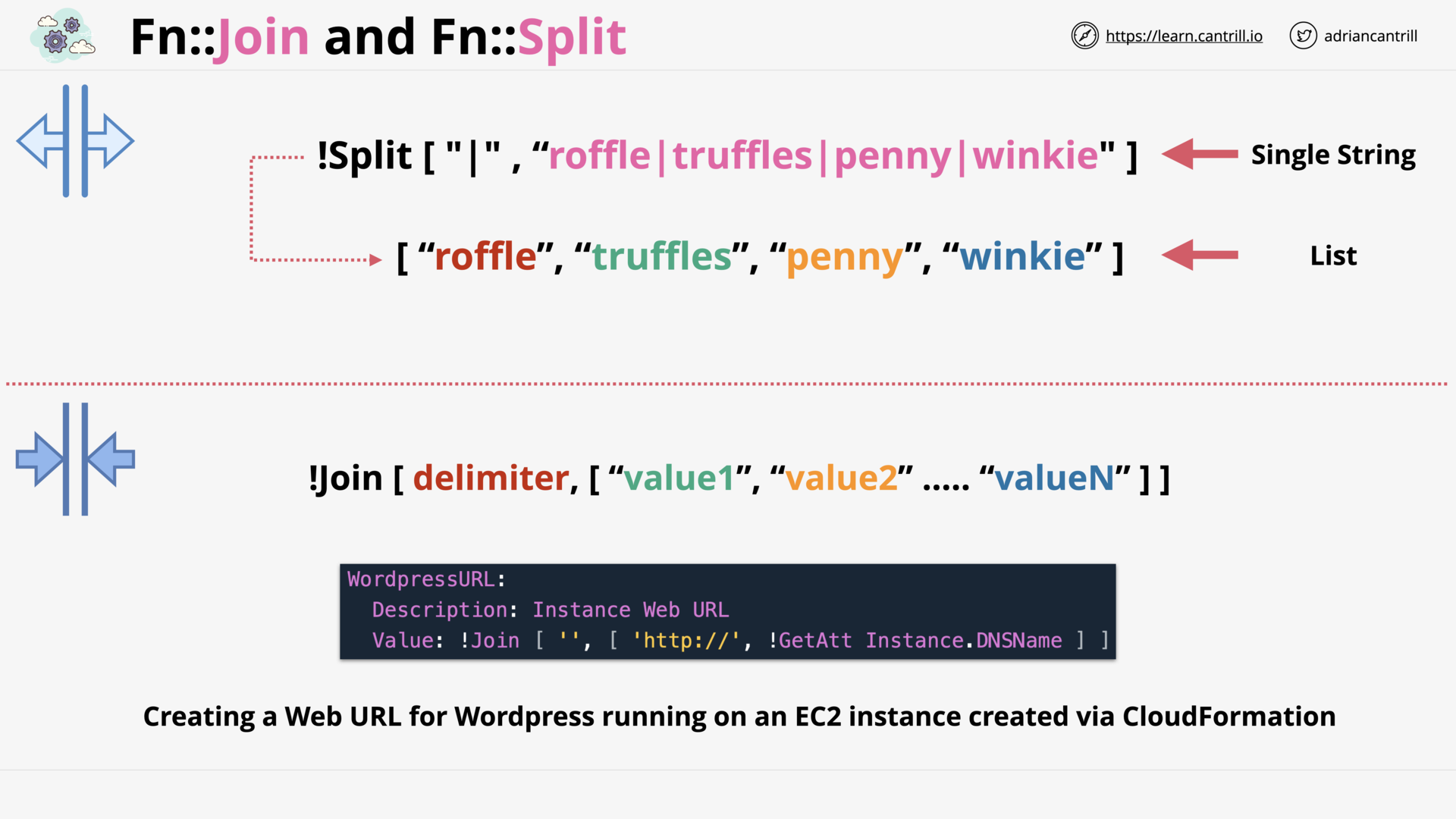 Cfn Intrinsic Functions:
Cfn Intrinsic Functions: Fn:Join & Fn:Split
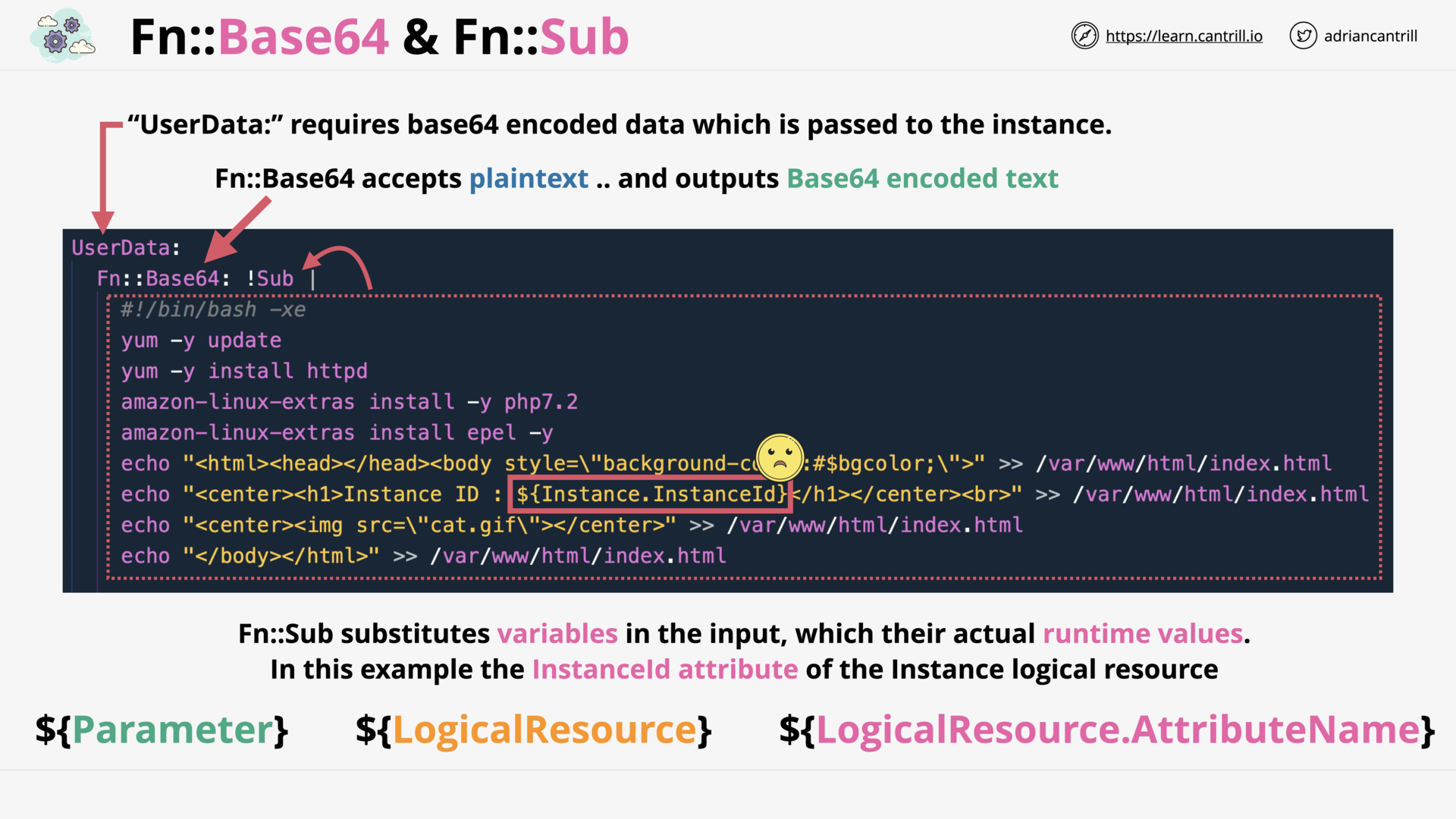 Cfn Intrinsic Functions:
Cfn Intrinsic Functions: Fn:Base64 & Fn:Sub
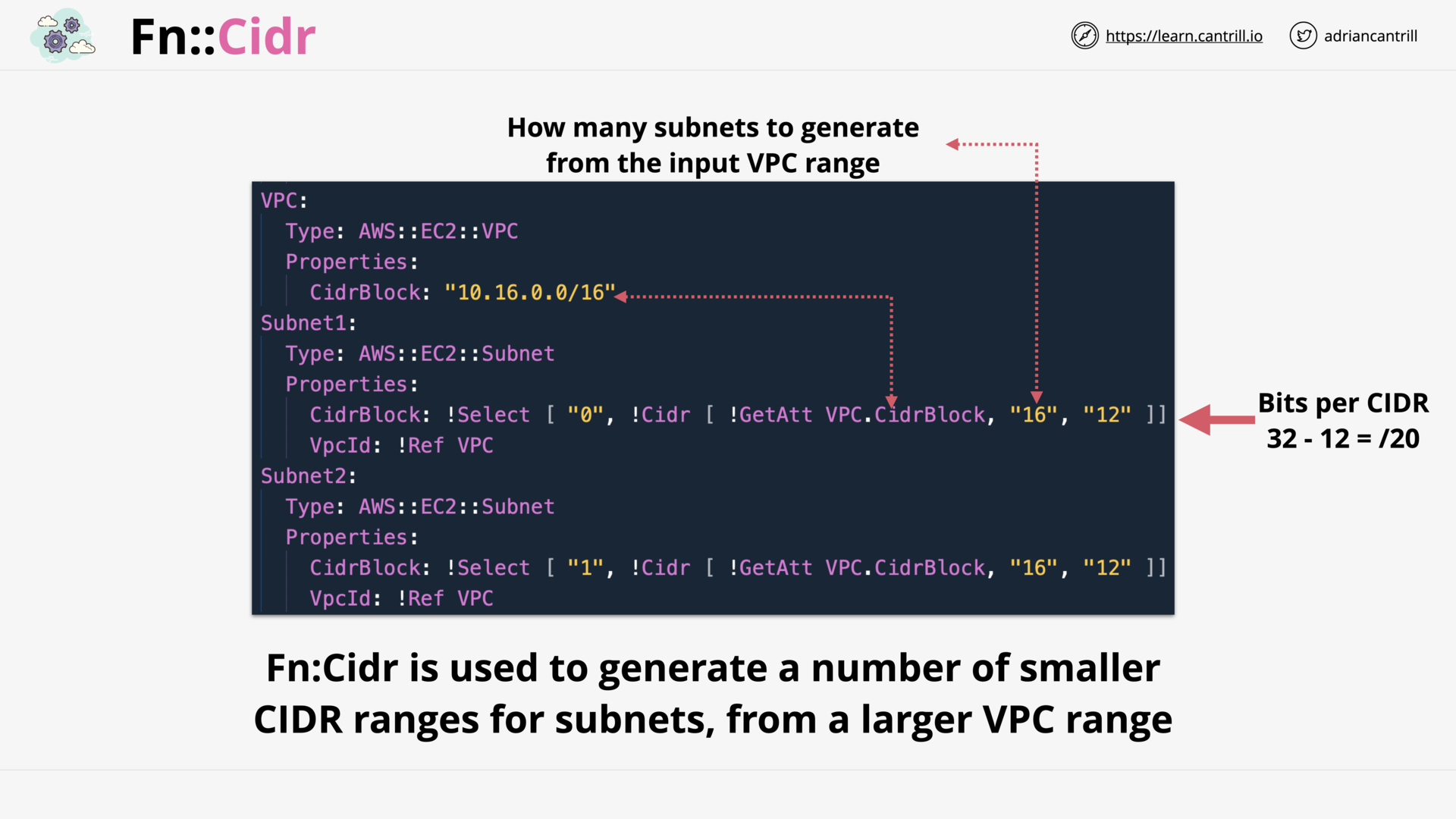 Cfn Intrinsic Functions:
Cfn Intrinsic Functions: Fn:Cidr
note
| Function | YAML Syntax (Short form) | Example usage | Return |
|---|---|---|---|
Ref | !Ref logicalName | !Ref MyInstance | i-1234567891 |
Fn::GetAtt | !GetAtt logicalNameOfResource.attributeName | !GetAtt MyInstance.PublicIp | ec2-1.2.3.4.compute-1.amazonaws.com2 |
Fn::GetAZs | !GetAZs region | !GetAZs '' | [ "us-east-1a", "us-east-1b", "us-east-1c" ]3 |
Fn::Select | !Select [ index, listOfObjects ] | !Select [ "0", [ "apples", "grapes", "oranges" ] ] | "apples"4 |
!Select [ "0", !GetAZs '' ] | "us-east-1a" | ||
Fn::Join | !Join [ delimiter, [ comma-delimited list of values ] ] | !Join [ ":", [ a, b, c ] ] | "a:b:c" |
Fn::Split | !Split [ delimiter, source string ] | !Split [ ":" , "a:b:c" ] | [ a, b, c ] |
Fn::Base64 | !Base64 valueToEncode | !Base64 AWS CloudFormation | QVdTIENsb3VkRm9ybWF0aW9u5 |
Fn::Sub | !Sub String | !Sub "SSH security group for ${AWS::StackName}" | "SSH security group for STACK_NAME" |
Fn::Cidr | !Cidr [ ipBlock, count, cidrBits ] | !Cidr [ "10.16.0.0/16", 16, 12 ] | 16 CIDRs with a subnet mask /20 |
note
| Function | YAML Syntax | |
|---|---|---|
Ref | Short form | !Ref logicalName |
| Full form | Ref: logicalName6 | |
Fn::GetAtt | Short form | !GetAtt logicalNameOfResource.attributeName |
| Full form | Fn::GetAtt: [ logicalNameOfResource, attributeName ] | |
Fn::GetAZs | Short form | !GetAZs region |
| Full form | Fn::GetAZs: region | |
Fn::Select | Short form | !Select [ index, listOfObjects ] |
| Full form | Fn::Select: [ index, listOfObjects ] | |
Fn::Join | Short form | !Join [ delimiter, [ comma-delimited list of values ] ] |
| Full form | Fn::Join: [ delimiter, [ comma-delimited list of values ] ] | |
Fn::Split | Short form | !Split [ delimiter, source string ] |
| Full form | Fn::Split: [ delimiter, source string ] | |
Fn::Base64 | Short form | !Base64 valueToEncode |
| Full form | Fn::Base64: valueToEncode | |
Fn::Base64: !Sub string | ||
Fn::Sub | Short form | !Sub String |
| Full form | Fn::Sub: String | |
Fn::Cidr | Short form | !Cidr [ ipBlock, count, cidrBits ] |
| Full form | Fn::Cidr: - ipBlock - count - cidrBits | |
how to remember full form and short form?
Full form:Fn::FunctionName:Short form:! FunctionName
See Intrinsic function reference - AWS CloudFormation
CloudFormation Mappings (4:30)
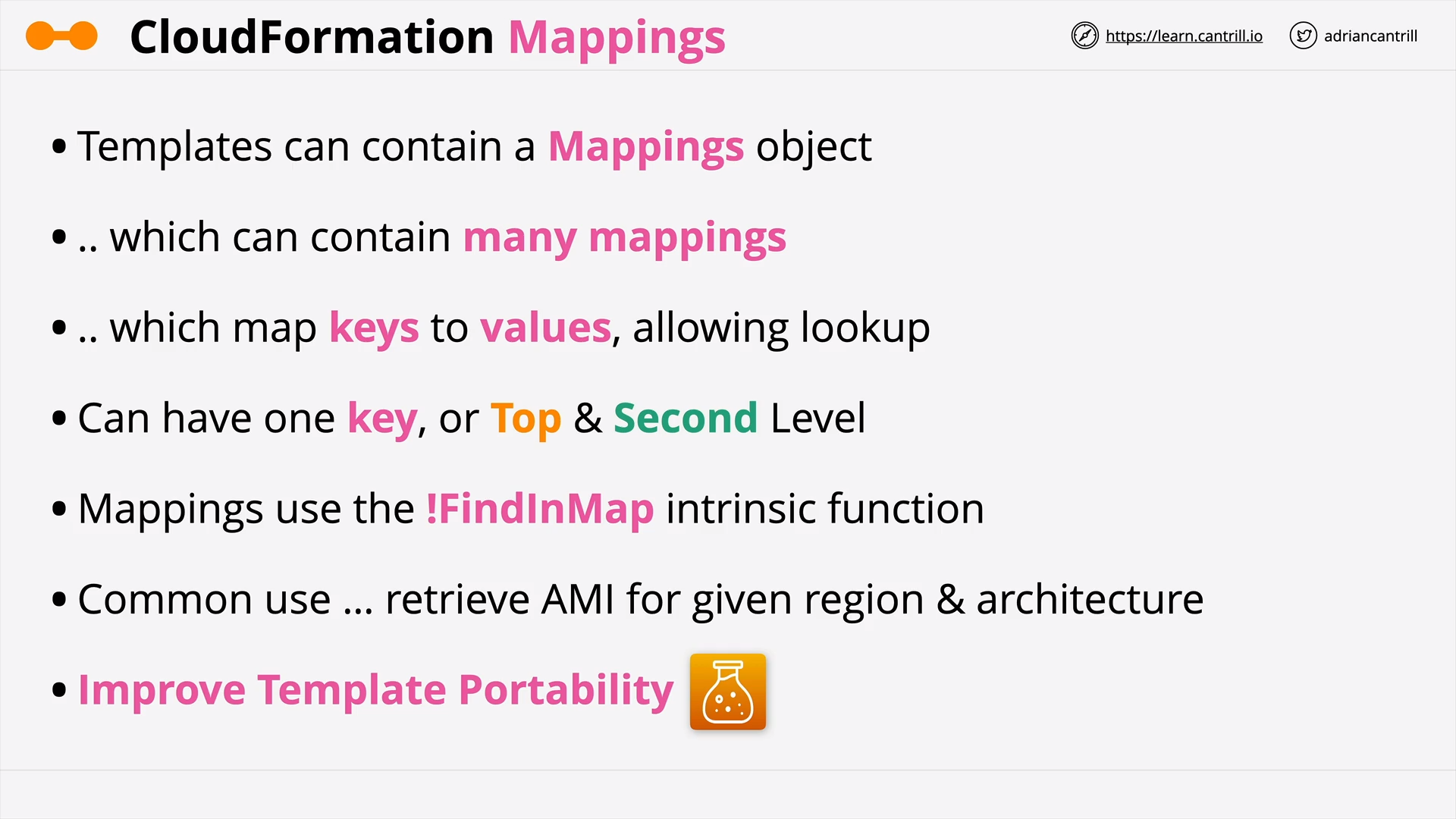 Cfn Mappings (Template):
Cfn Mappings (Template): Mappings section
mappings and key level
The Mappings section can have multiple mappings.
- Each mapping is a
keyof theMappingssection. - Each mapping can have 2 level of keys.
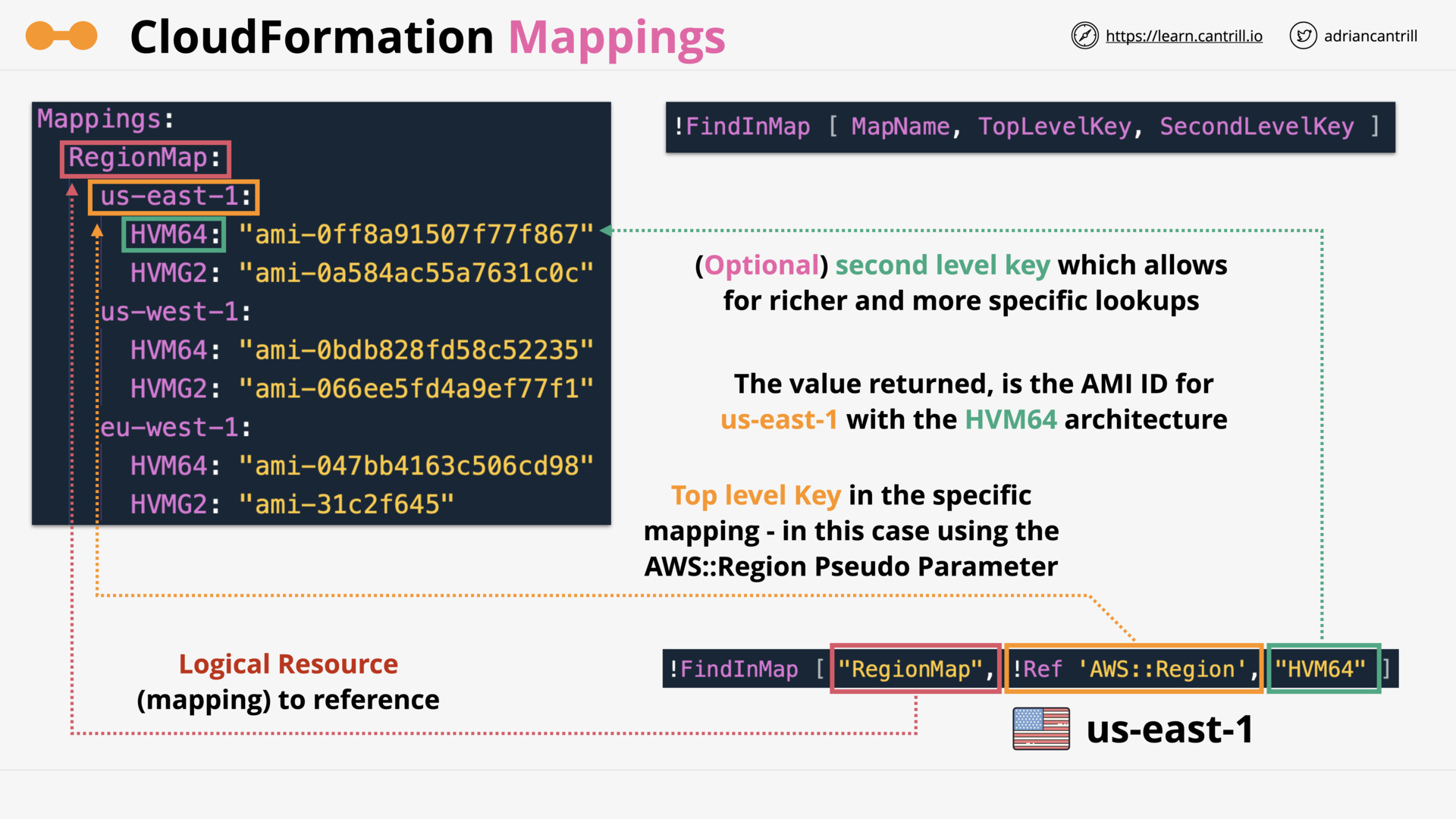 Cfn Mappings:
Cfn Mappings: Fn::FindInMap
findinmap syntax
| Function | YAML Syntax | |
|---|---|---|
Fn::FindInMap | Short form | !FindInMap [ MapName, TopLevelKey, SecondLevelKey ] |
| Long form | Fn::FindInMap: [ MapName, TopLevelKey, SecondLevelKey ] | |
CloudFormation Outputs (3:37)
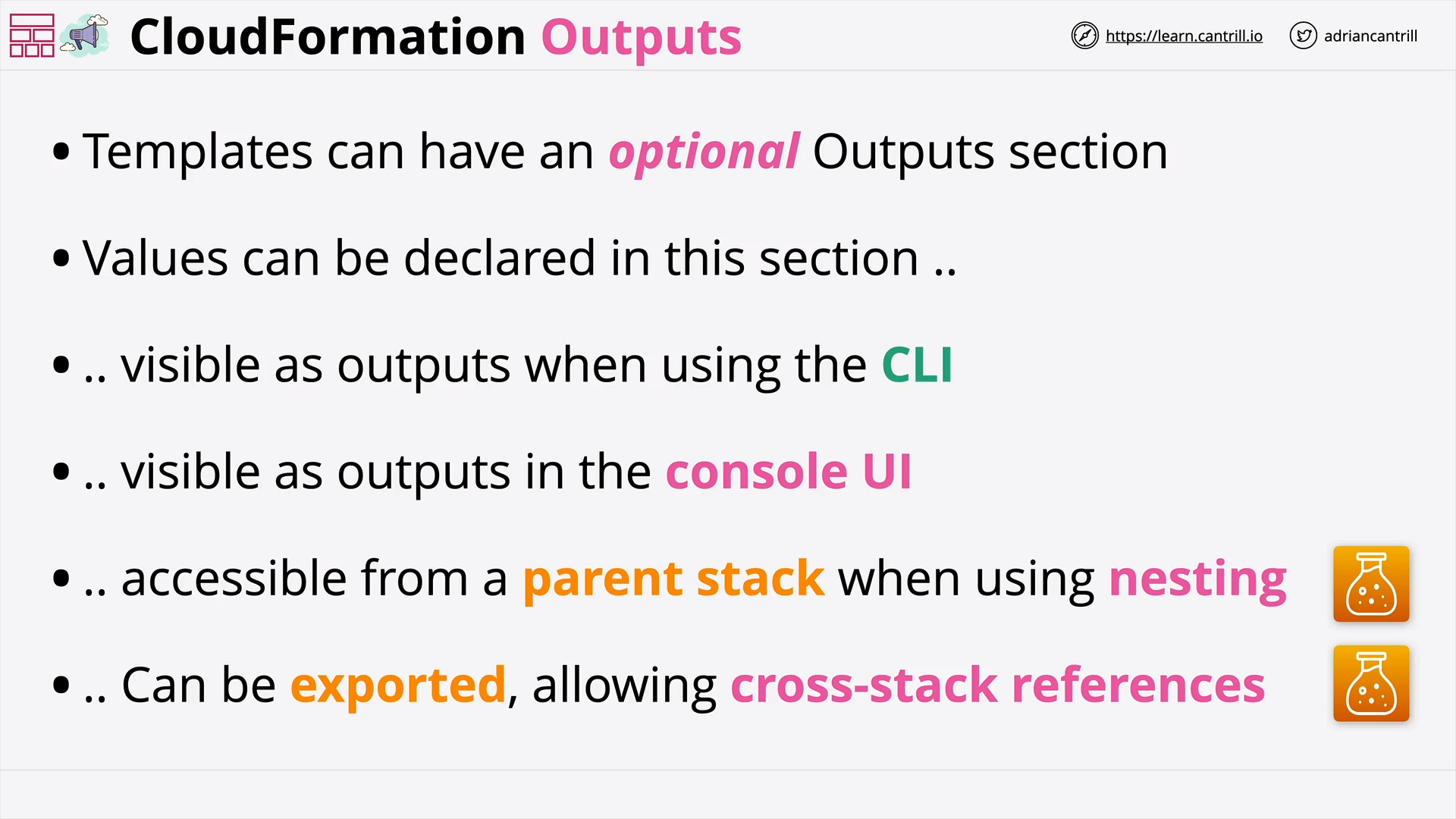 Cfn Outputs (Template): Views in CLI/Console - Used by parent-stack, cross-stack
Cfn Outputs (Template): Views in CLI/Console - Used by parent-stack, cross-stack
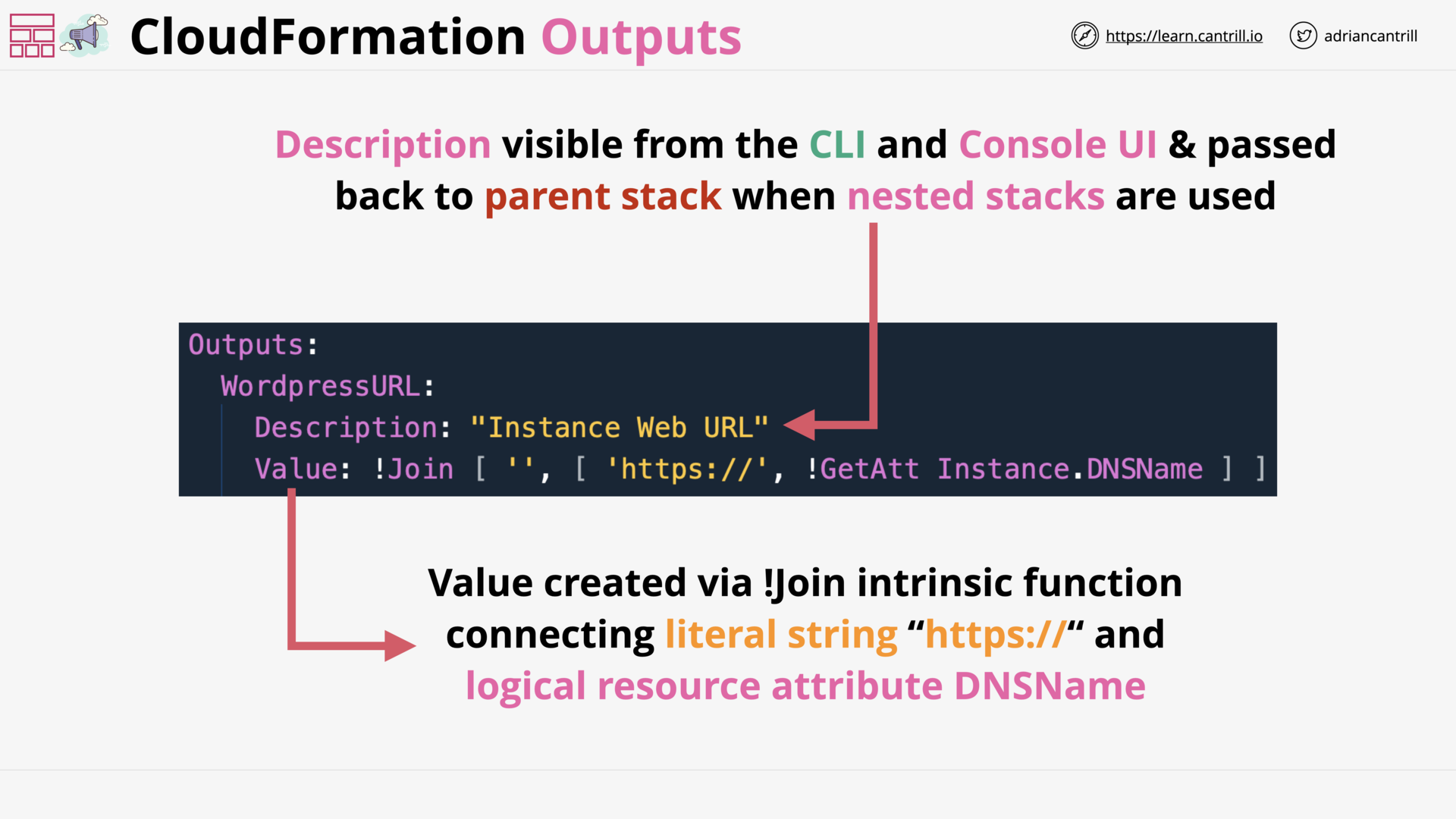 Cfn Outputs: Example
Cfn Outputs: Example
[DEMO] Template v2 - Portable (13:34)
CloudFormation Conditions (7:24)
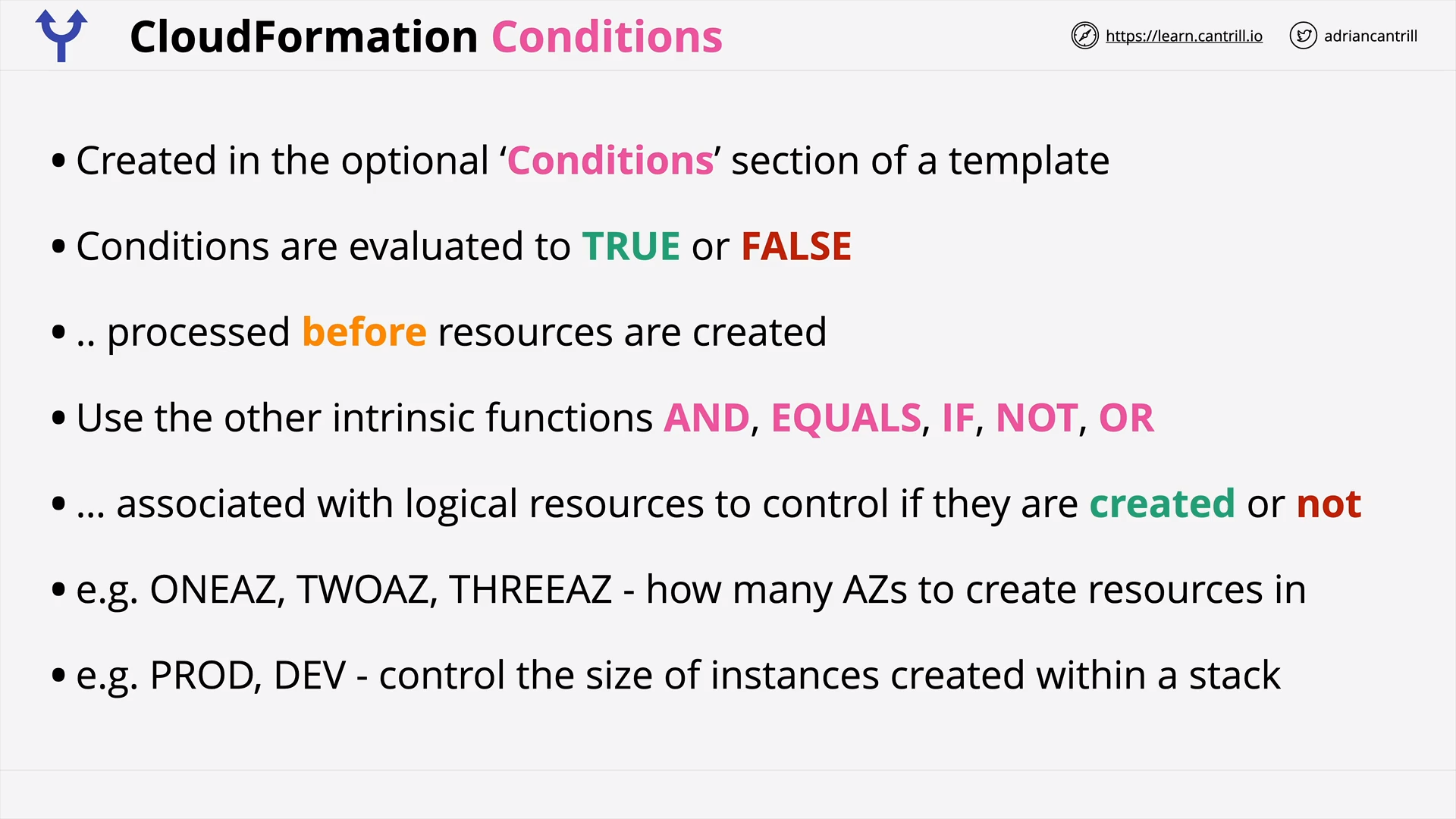 Cfn Conditions (Template): Only create resources if conditions meet
Cfn Conditions (Template): Only create resources if conditions meet
how cfn condition work?
You
- create a condition in the
Conditionssection - associate that condition to logical resources
- to control if they are created or not
why use cfn condition?
With Cfn Condition, you can reuse a template that can create resources in different contexts.
e.g. a test environment versus a production environment
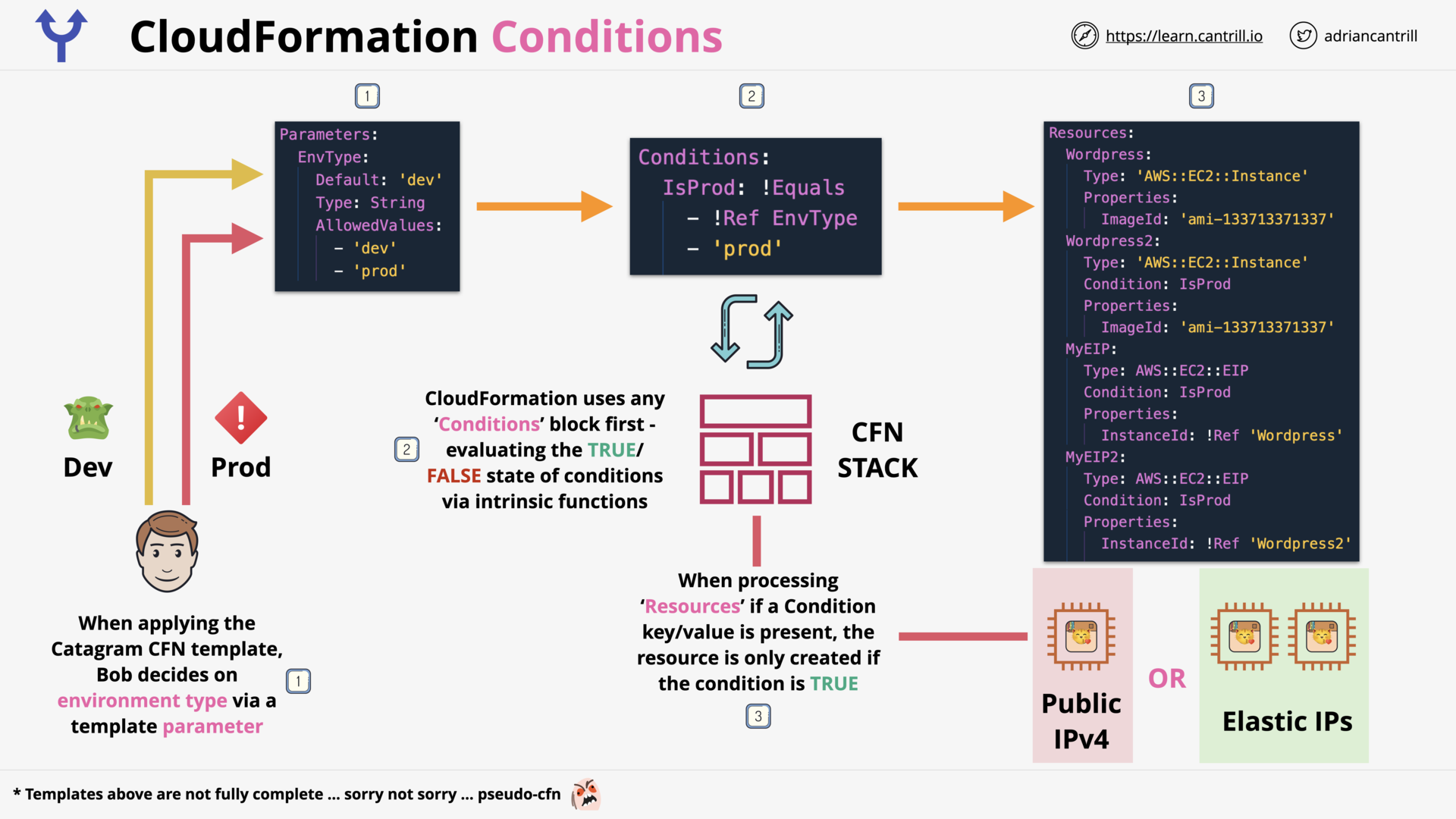 Cfn Conditions: Example
Cfn Conditions: Example
CloudFormation DependsOn (7:14)
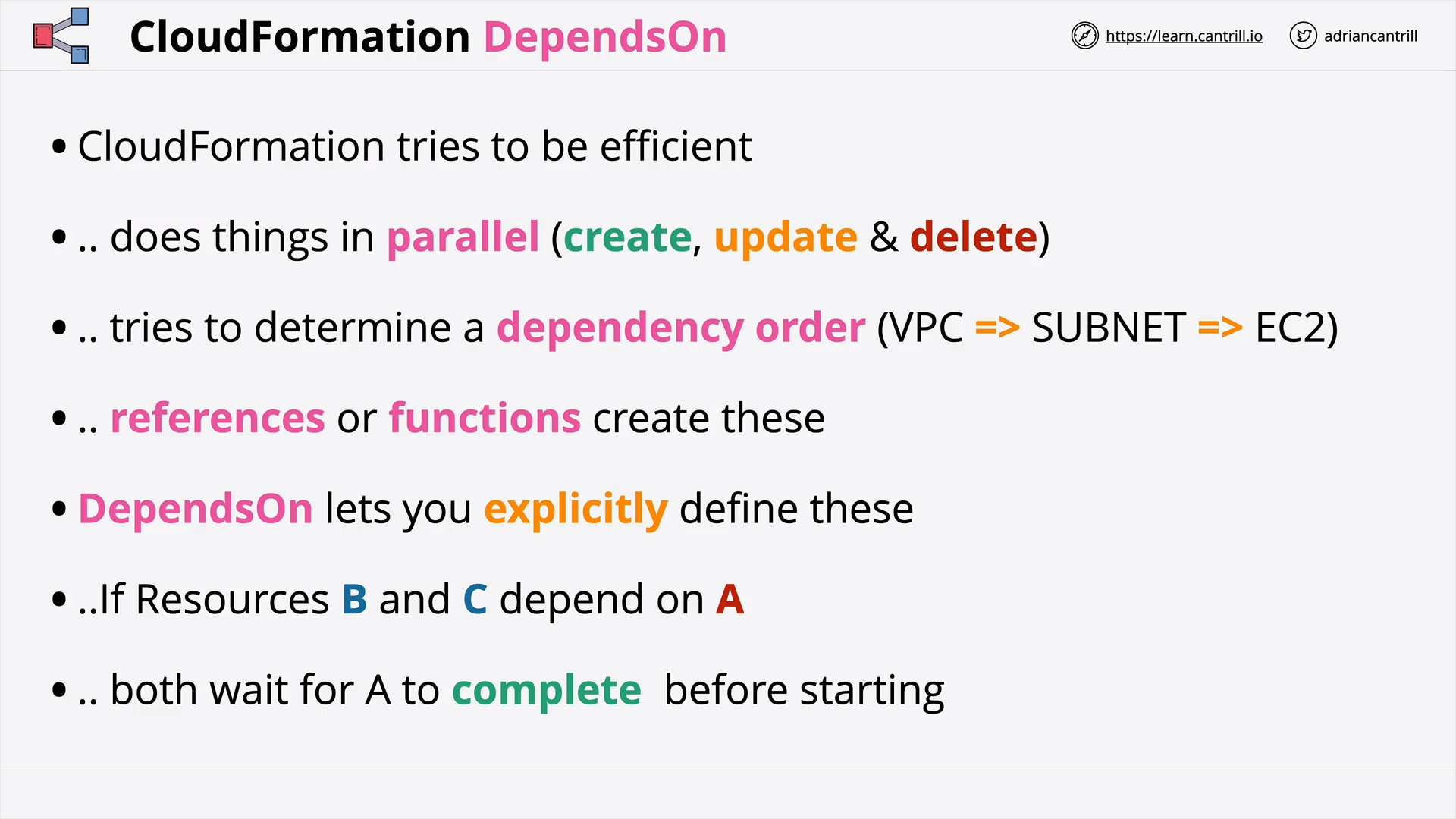 Cfn DependsOn (Resource): Explicitly define resources dependency order
Cfn DependsOn (Resource): Explicitly define resources dependency order
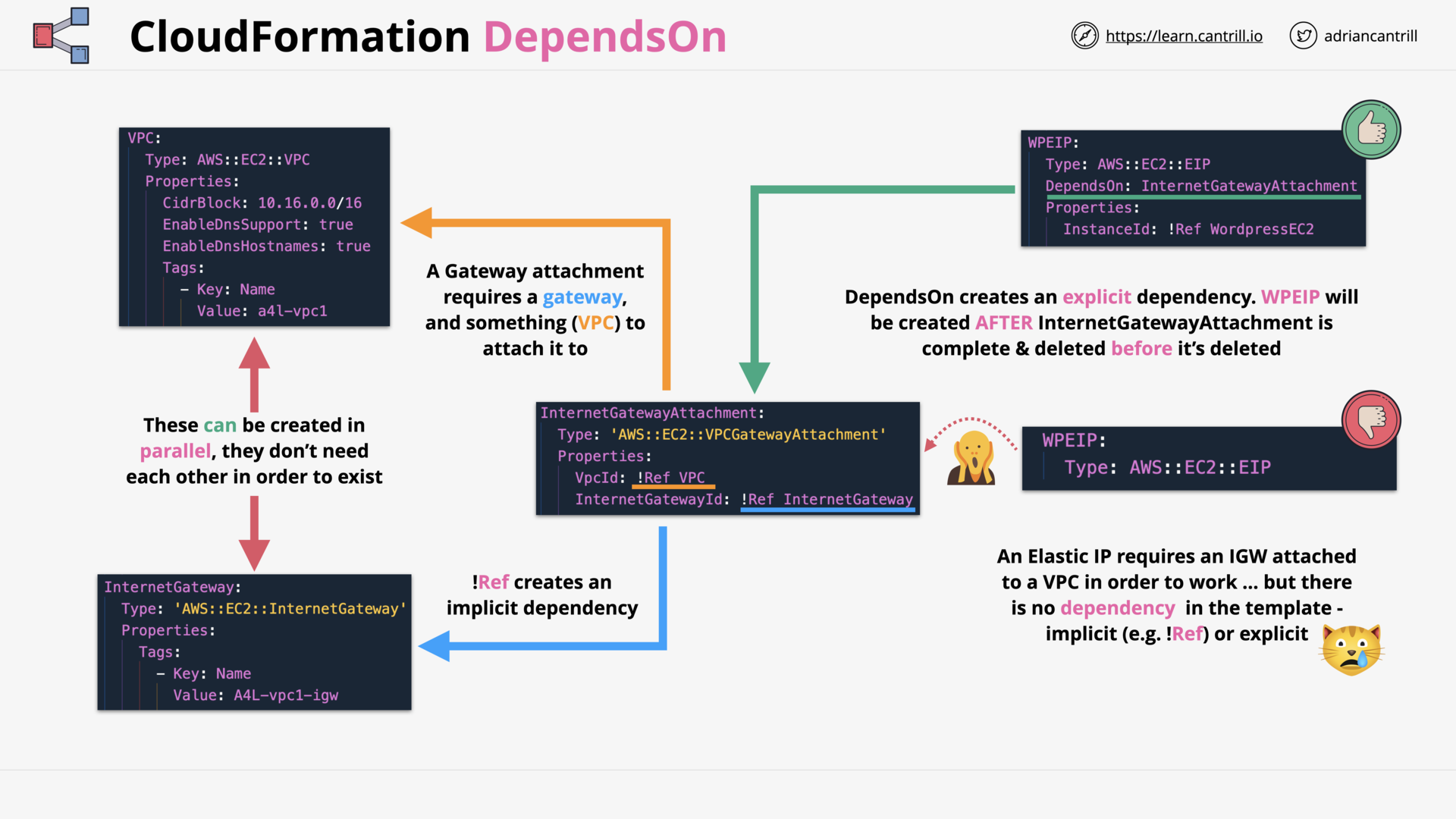 Cfn DependsOn: Example
Cfn DependsOn: Example
CloudFormation Wait Conditions, CreationPolicy & cfn-signal (11:52)
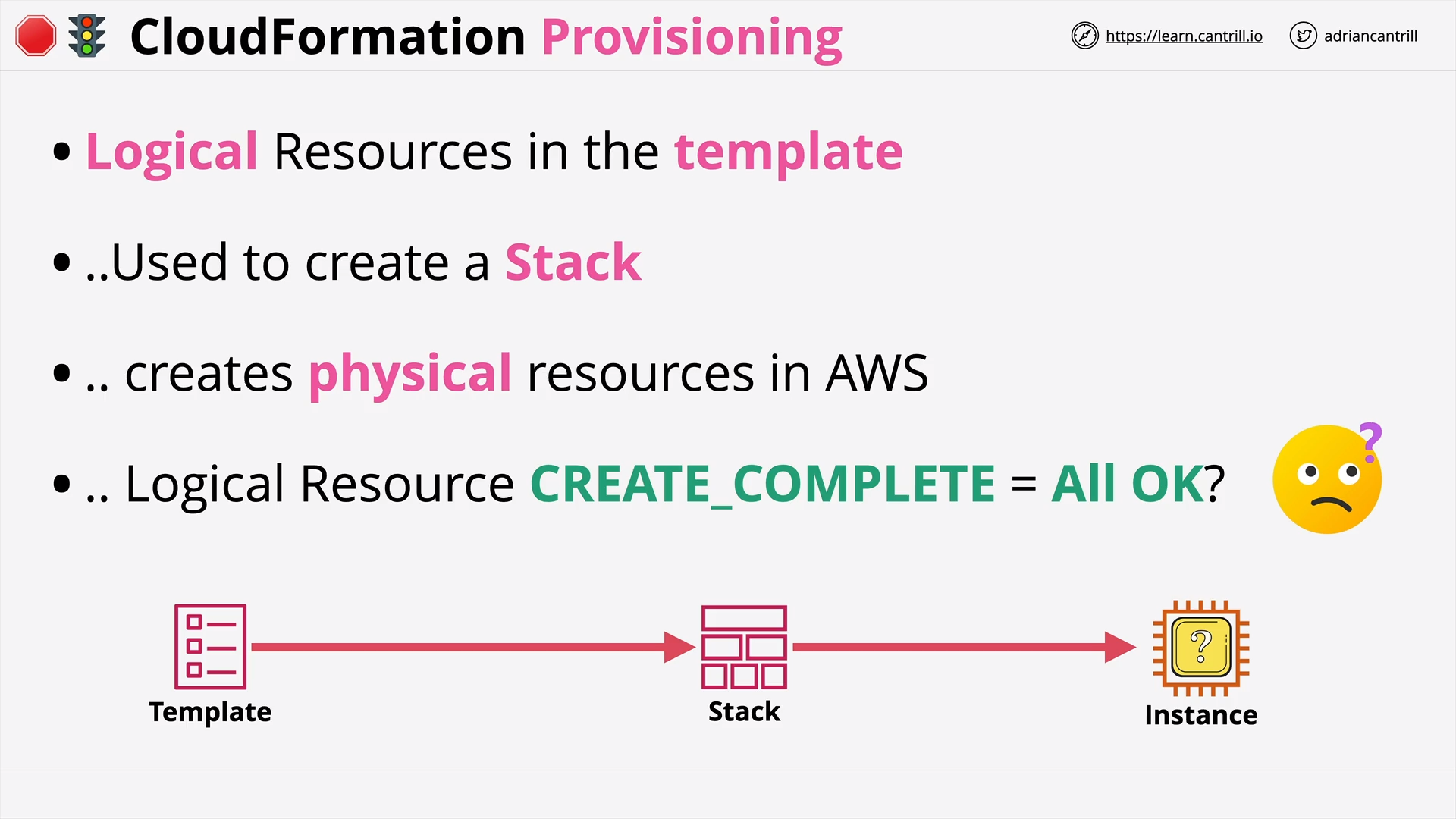 Cfn Provisioning - How do Cfn know that a resource successfully created/update?
Cfn Provisioning - How do Cfn know that a resource successfully created/update?
note
By default, Cfn don’t wait for the resources to be configured/bootstrap and be ready to used.
👉 The stack creation/updating will be finished before all of its resources are ready to used.
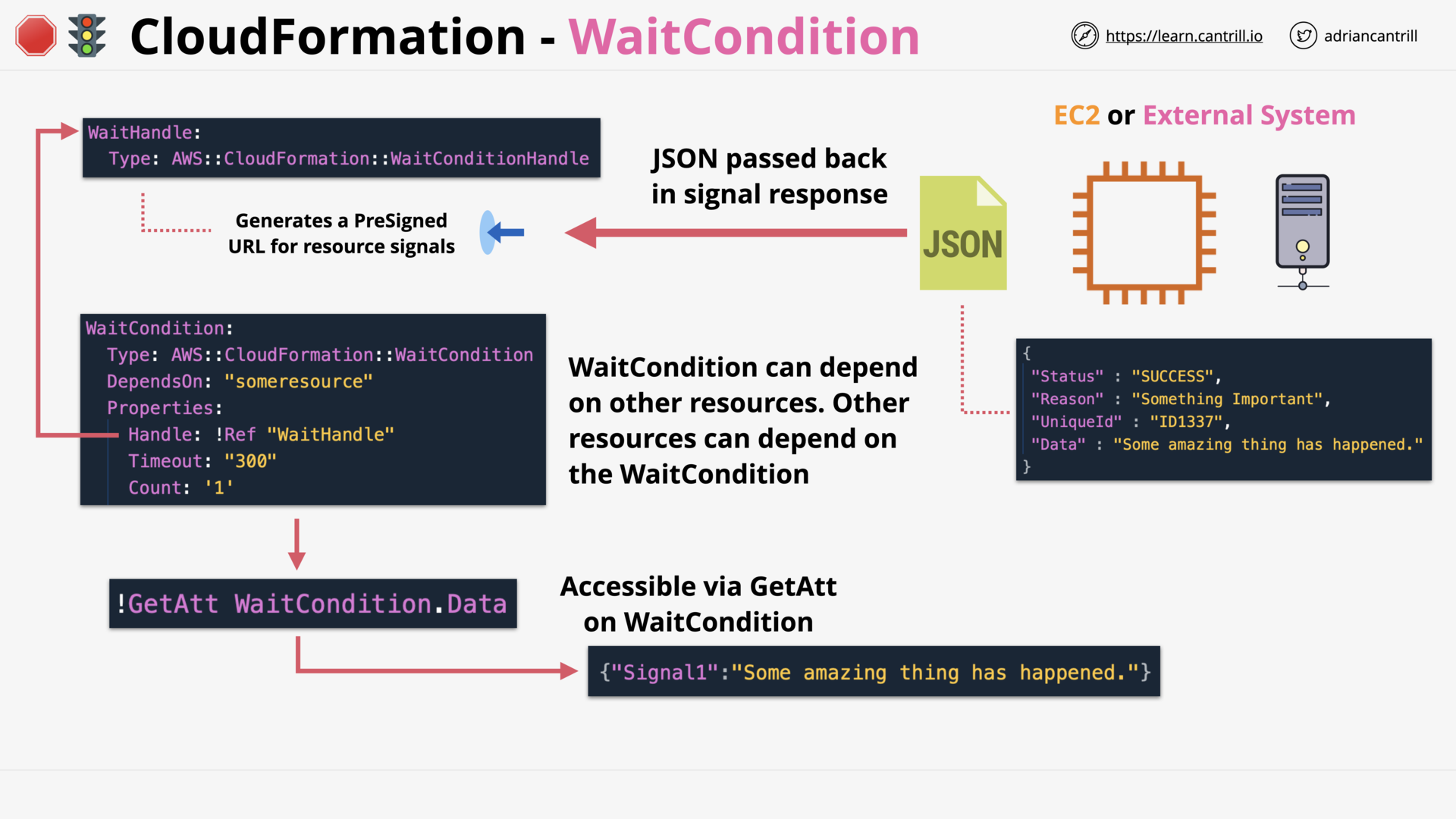 Cfn Wait Conditions (Template): Tell Cfn to pause the creation of a stack and wait for a signal before it continues to create the stack
Cfn Wait Conditions (Template): Tell Cfn to pause the creation of a stack and wait for a signal before it continues to create the stack
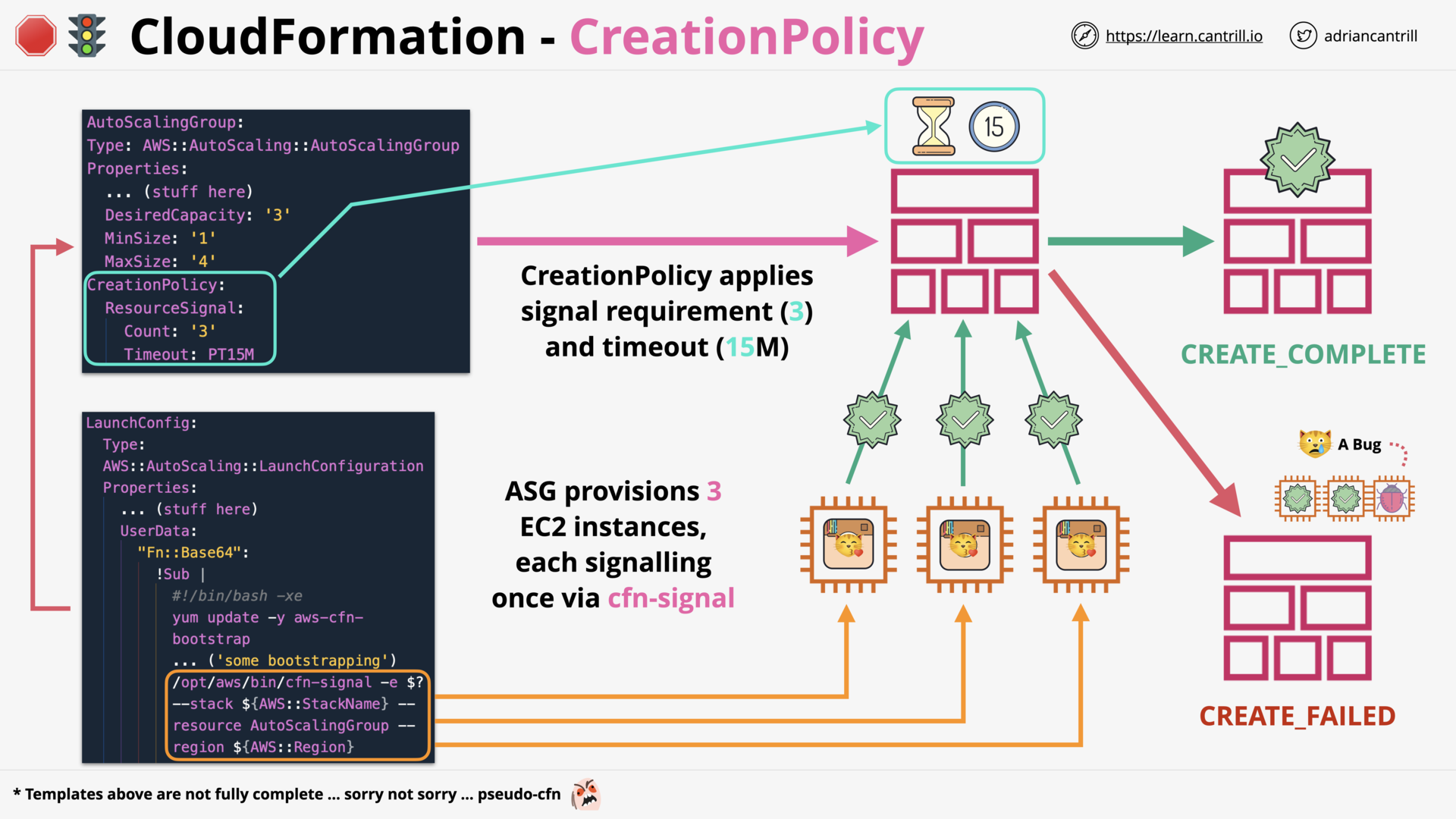 Cfn Creation Policy (Resource): Tell Cfn to wait on resource configuration actions before stack creation proceeds.
Cfn Creation Policy (Resource): Tell Cfn to wait on resource configuration actions before stack creation proceeds.
when to use wait conditions & create policy?
You
- Create Policy for EC2 and ASG or simple use cases (most situations)
- Wait Conditions in advance use cases.
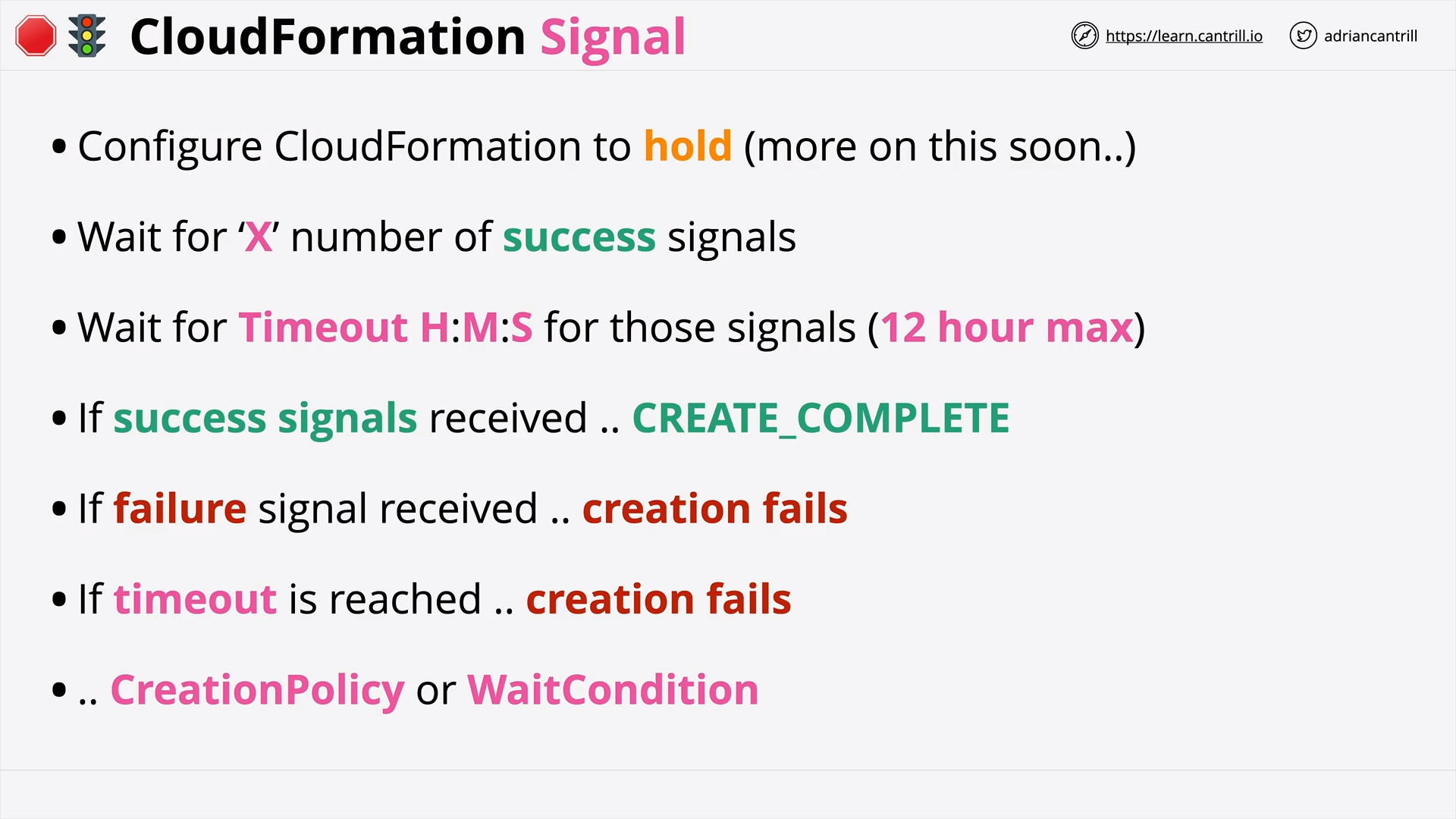 cfn-signal: Signals CloudFormation to indicate whether Amazon EC2 instances have been successfully created/updated
cfn-signal: Signals CloudFormation to indicate whether Amazon EC2 instances have been successfully created/updated
CloudFormation Nested Stacks (13:55)
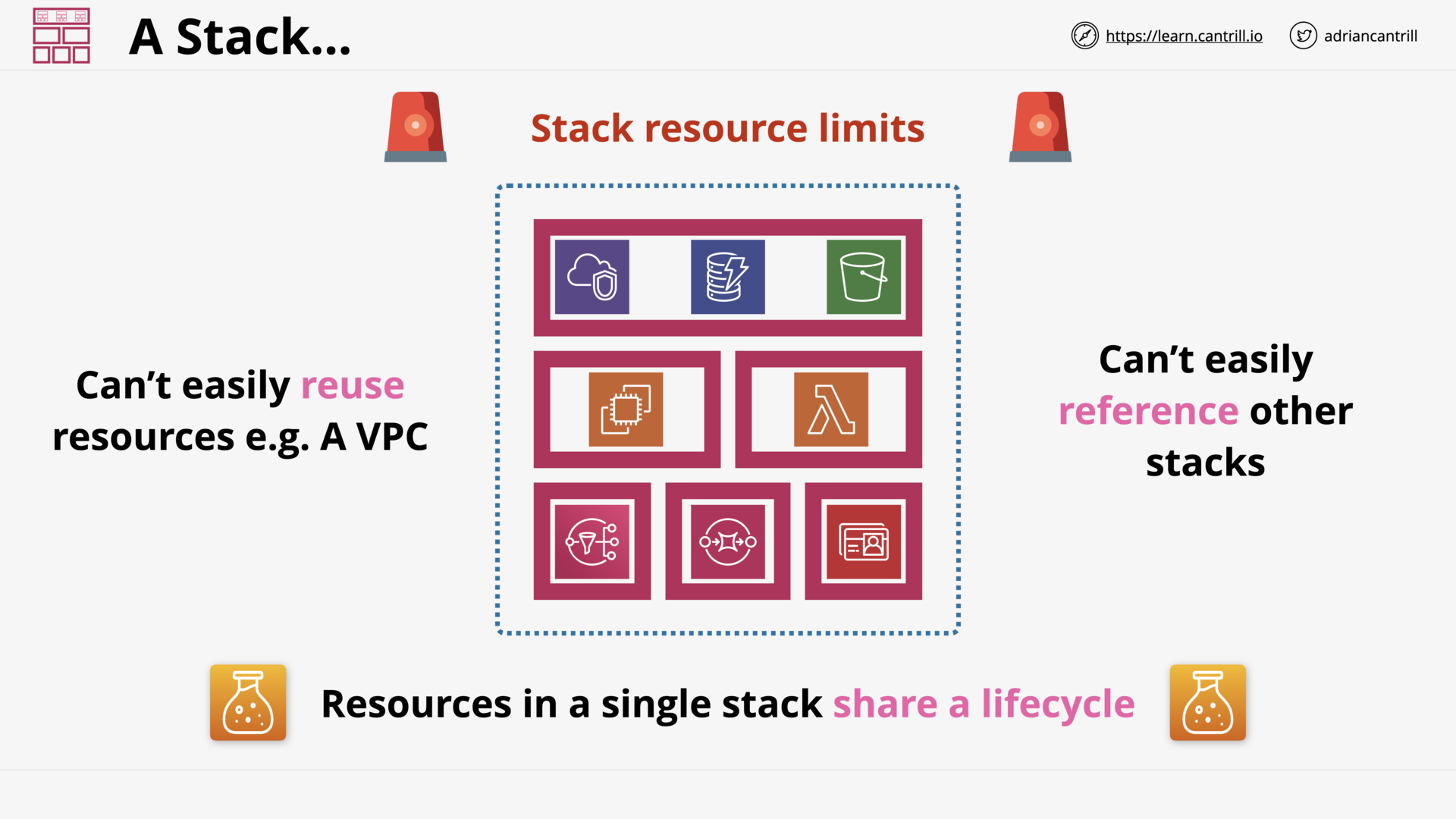 Single Stack - The Problem
Single Stack - The Problem
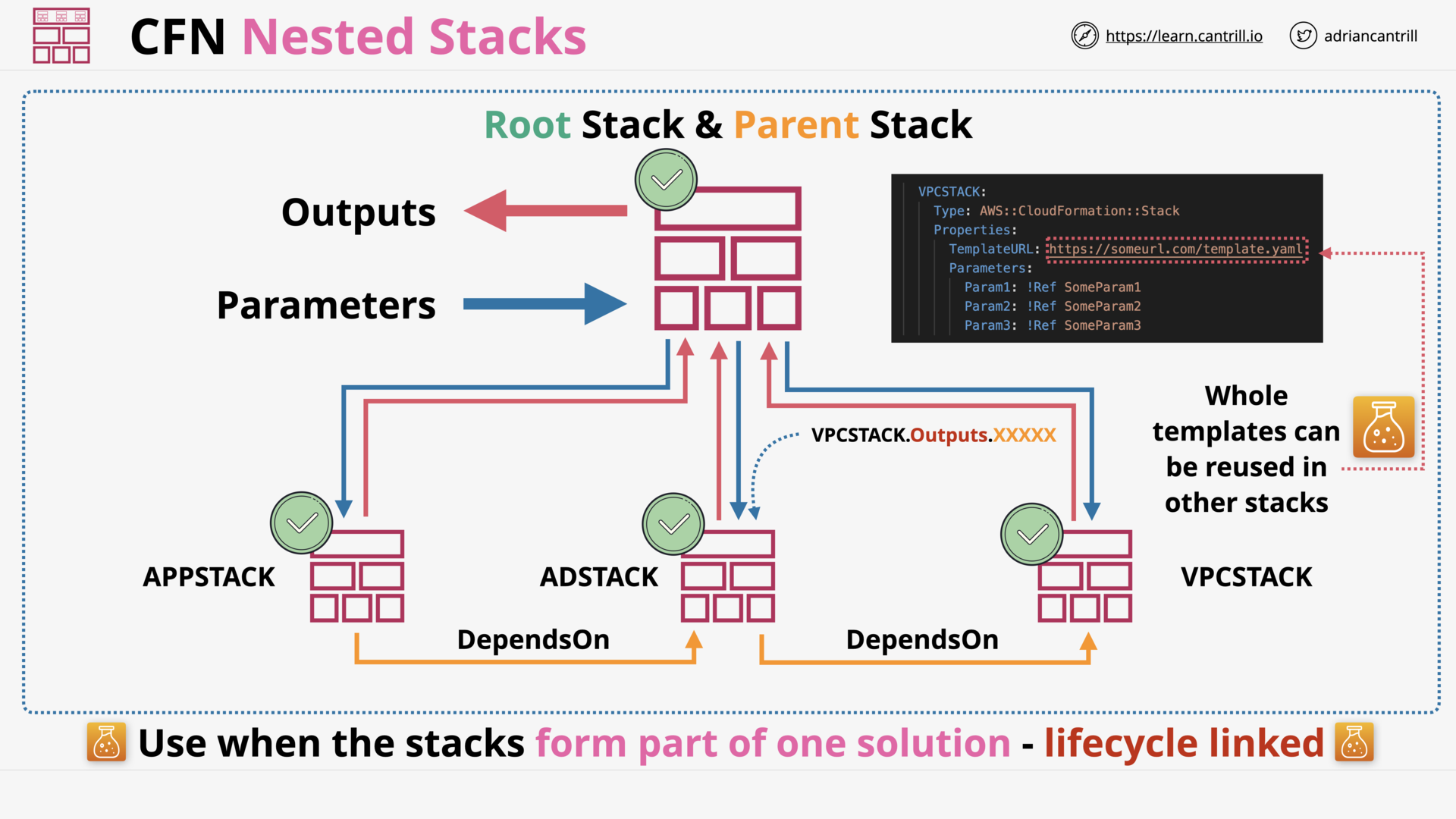 Cfn Nested Stack: Stacks created as part of other stacks 👈️ Allow reusing template (code)
Cfn Nested Stack: Stacks created as part of other stacks 👈️ Allow reusing template (code)
`nested stack`, `root stack`, `parent stack`?
-
Nested Stack: Stacks created as part of other stacks.
-
Root Stack: The top-level stack to which all the nested stacks ultimately belong.
-
Parent Stack: Each nested stack has an immediate parent stack.
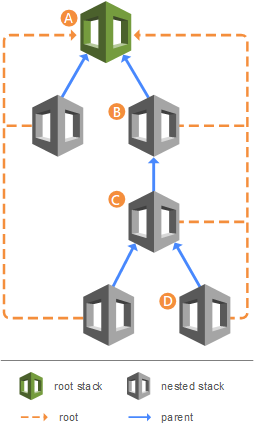
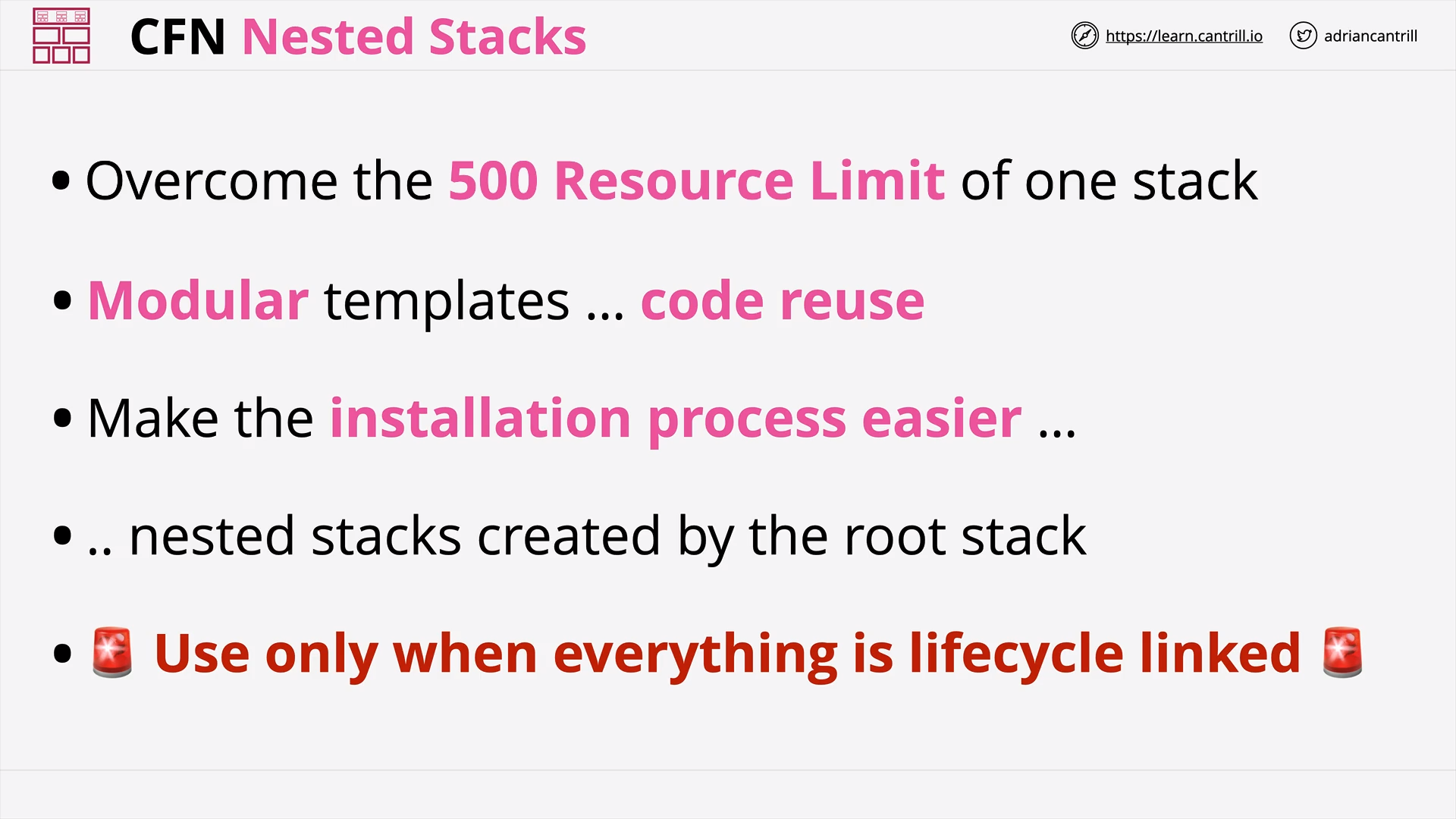 Cfn Nested Stacks - When?
Cfn Nested Stacks - When?
how are lifecycle of nested stacks?
The root stacks and all of its nested stacks share the same lifecycle.
CloudFormation Cross-Stack References (10:05)
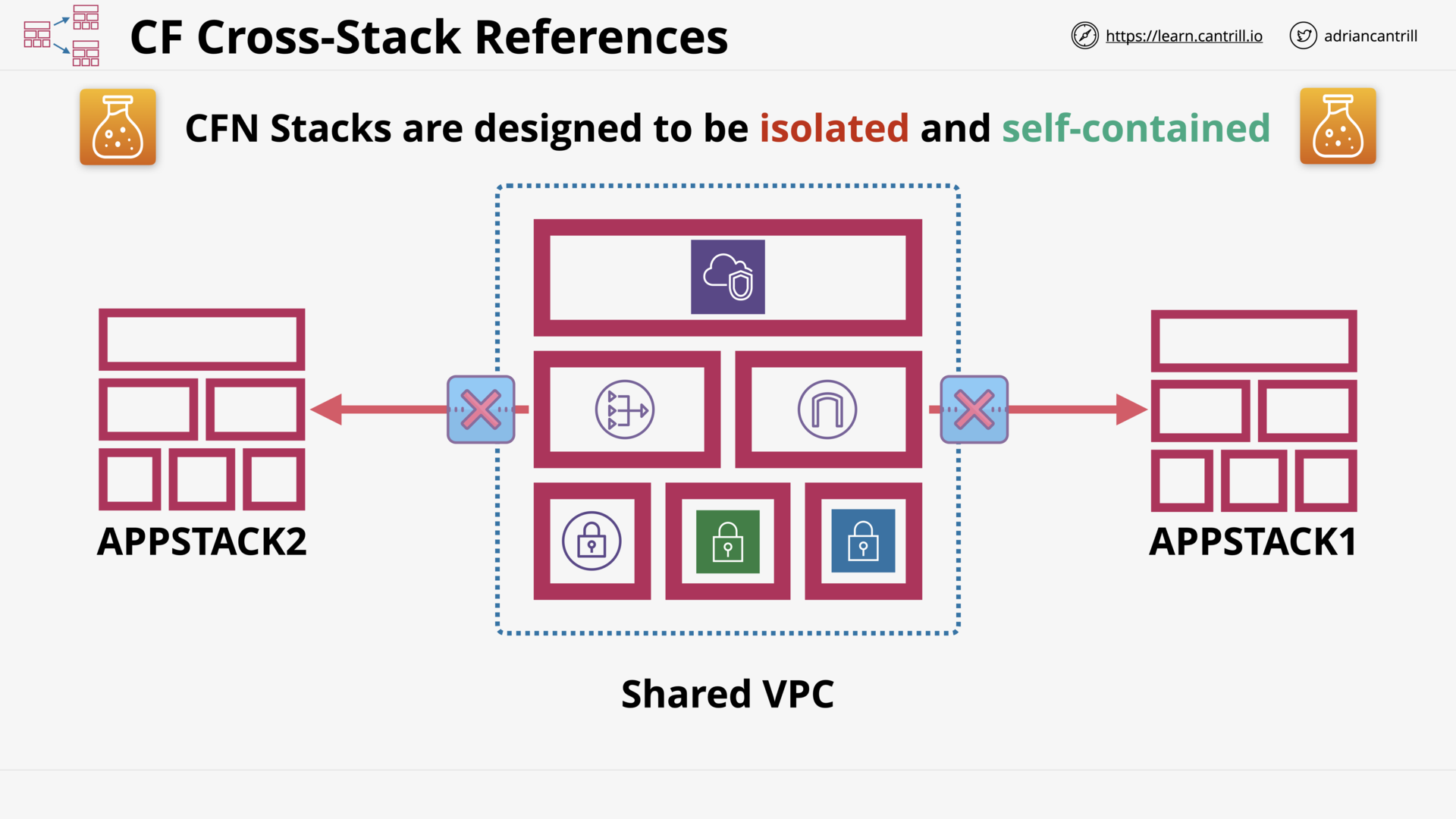 Cfn Stacks are isolated and self-contained
Cfn Stacks are isolated and self-contained
 Cfn
Cfn Outputs Export: Make a stack visible to other stacks (Cross-Stack References)
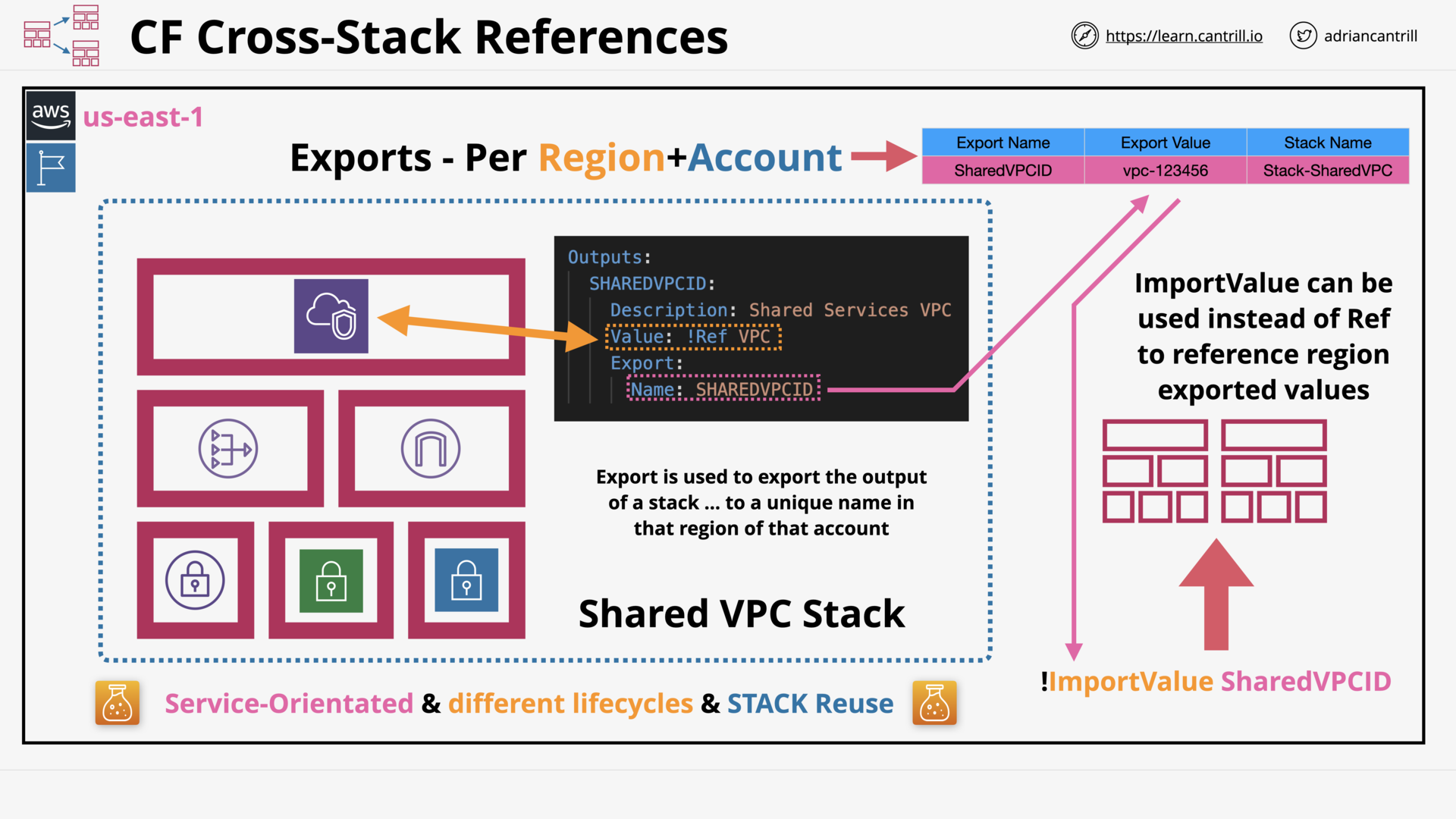 Cfn Cross-Stack References -
Cfn Cross-Stack References - Fn::ImportValue: Import another stack’s Outputs Export
CloudFormation Deletion Policy (5:24)
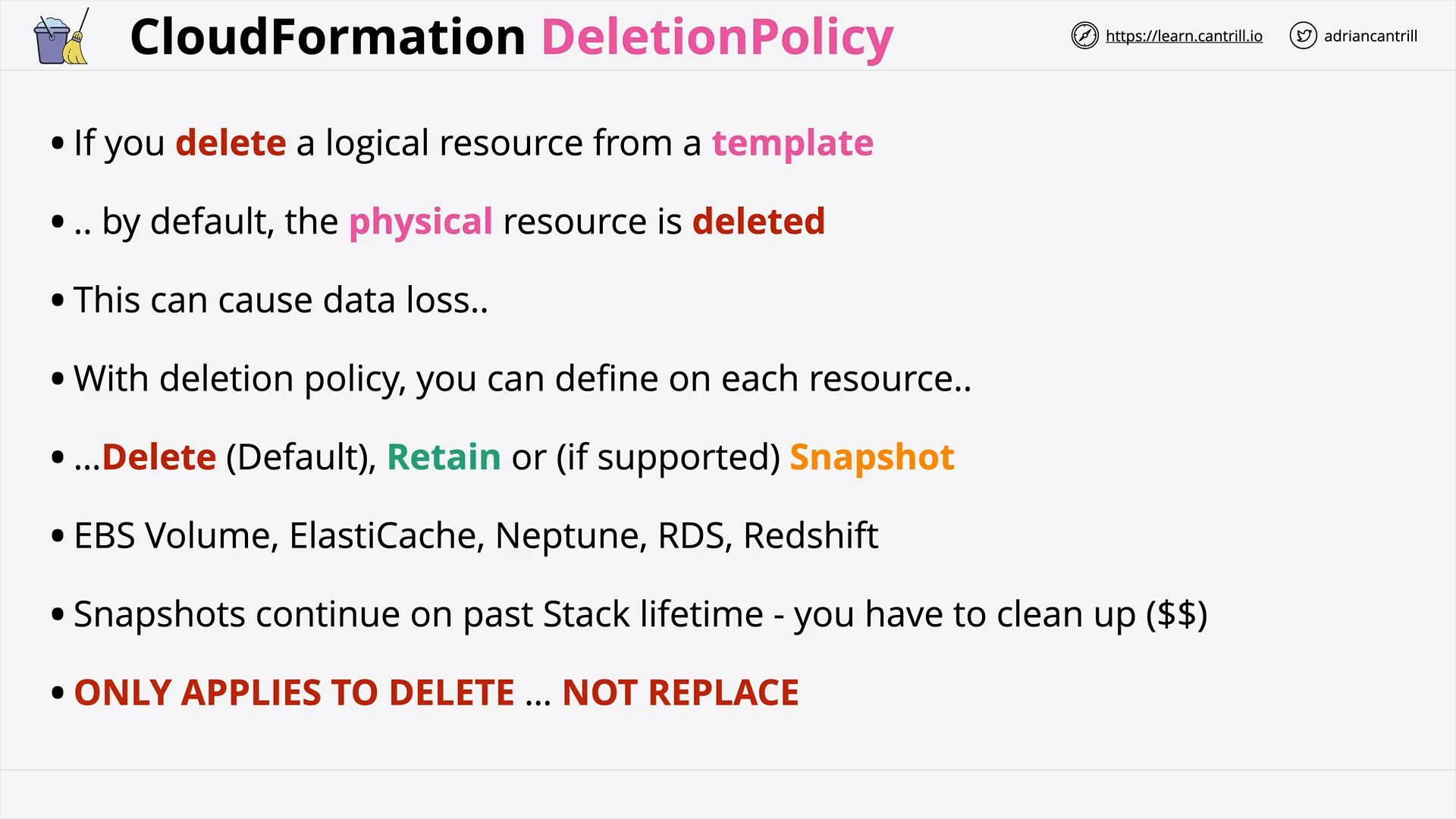 Cfn DeletionPolicy - What happen to physical resource when its logical resource deleted?
Cfn DeletionPolicy - What happen to physical resource when its logical resource deleted?
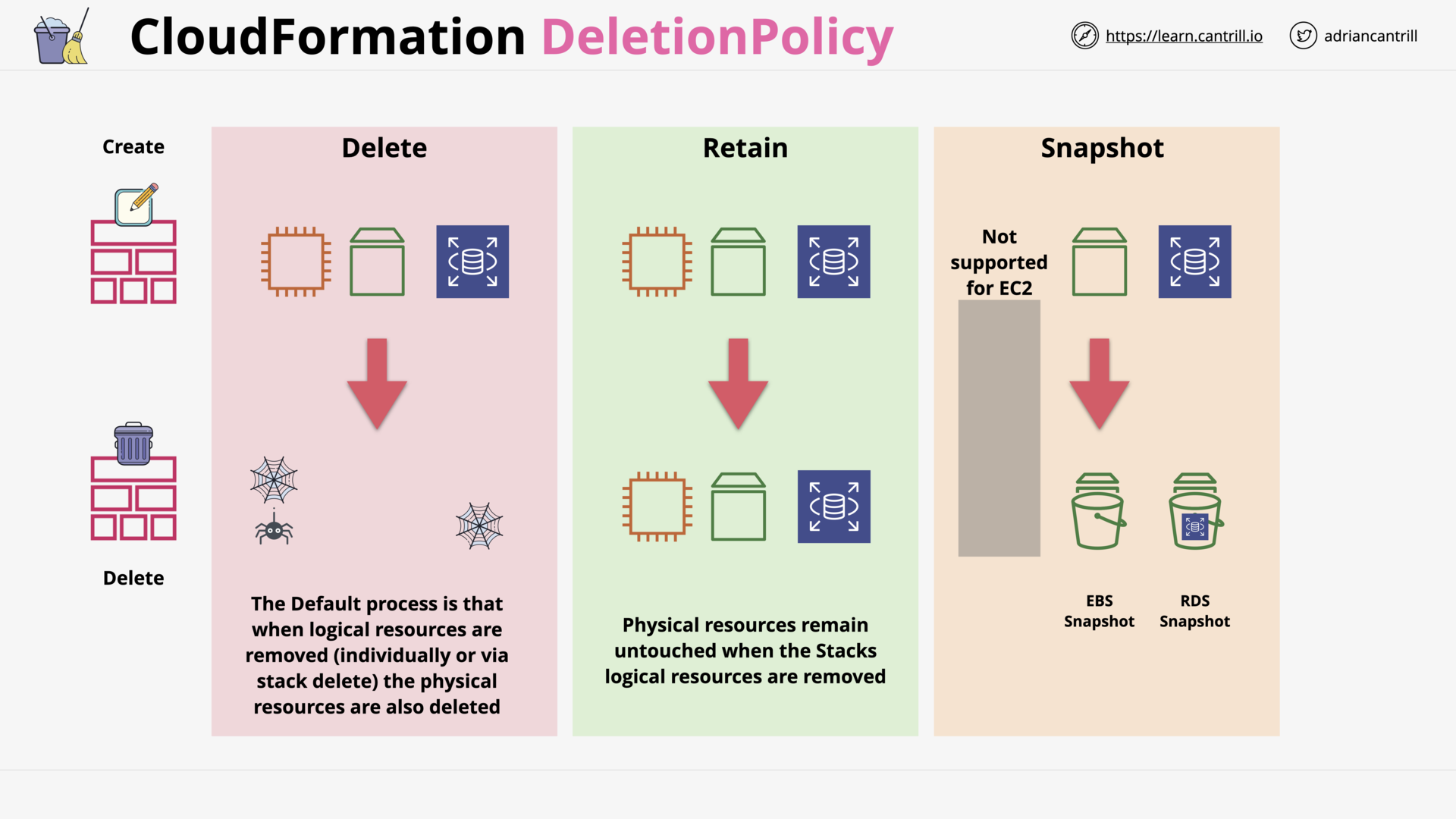 Cfn DeletionPolicy - Delete (Default) / Retain / Snapshot (If supported)
Cfn DeletionPolicy - Delete (Default) / Retain / Snapshot (If supported)
CloudFormation Stack Sets (9:12)
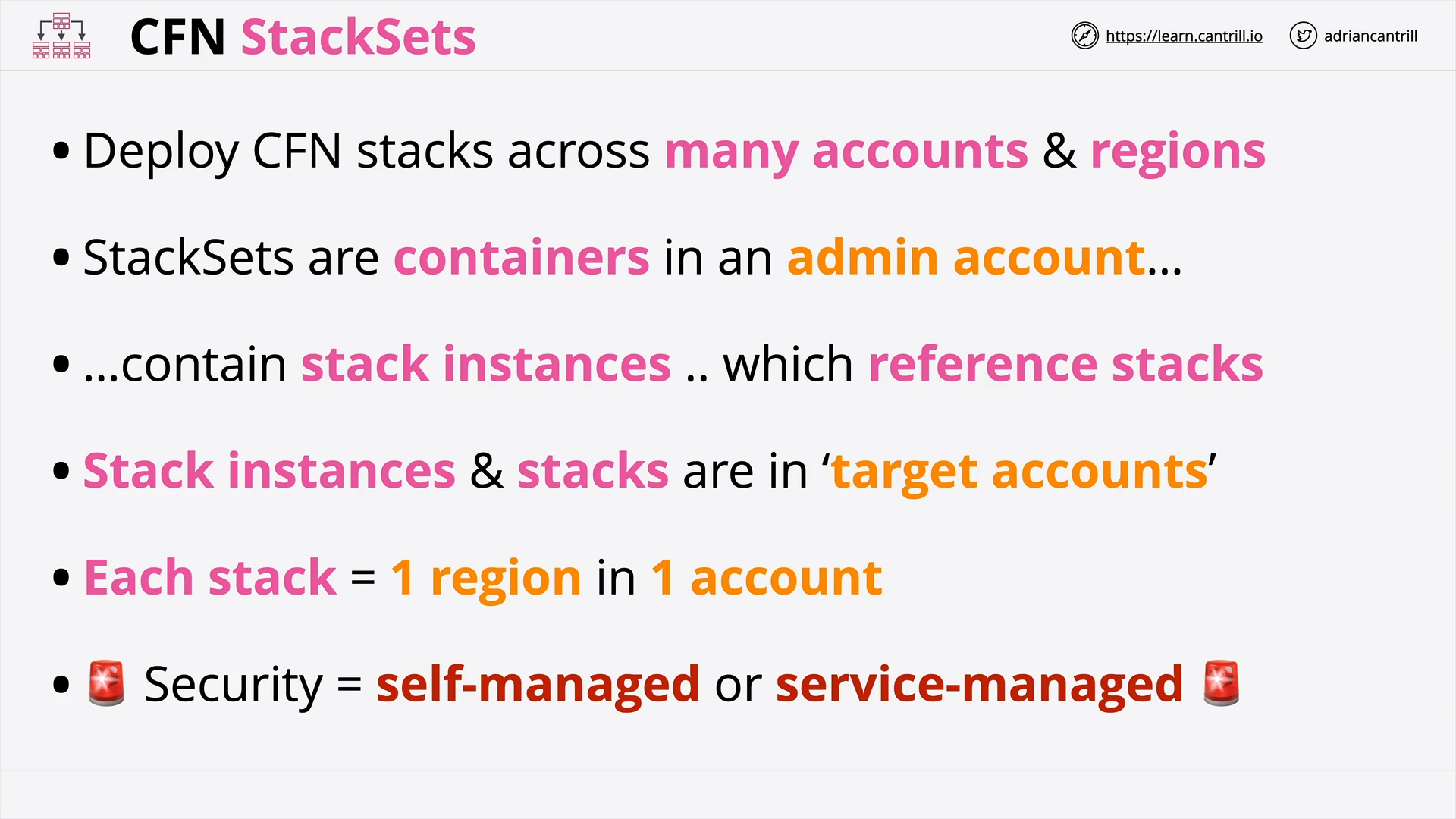 Cfn StackSets - Concepts
Cfn StackSets - Concepts
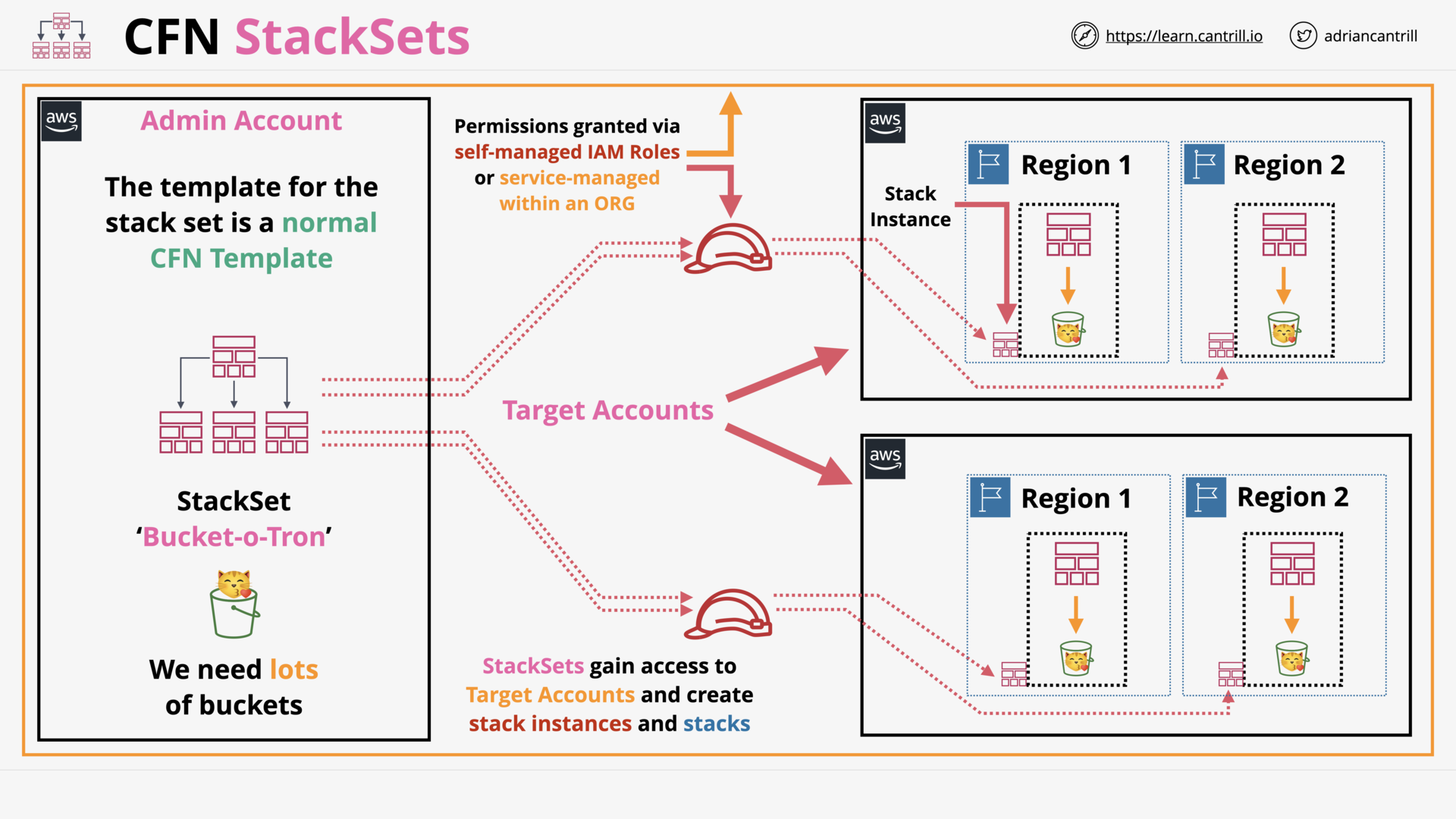 Cfn StackSets - Architecture
Cfn StackSets - Architecture
 Cfn StackSets - Key Points
Cfn StackSets - Key Points
CloudFormation Stack Roles (6:47)
 Cfn Stack Roles - Overview
Cfn Stack Roles - Overview
the identity creating the stack doesn't need permissions for resources.
It only needs permissions for:
- creating the stack
PassRoleto give Cfn the role with permissions for creating resources.
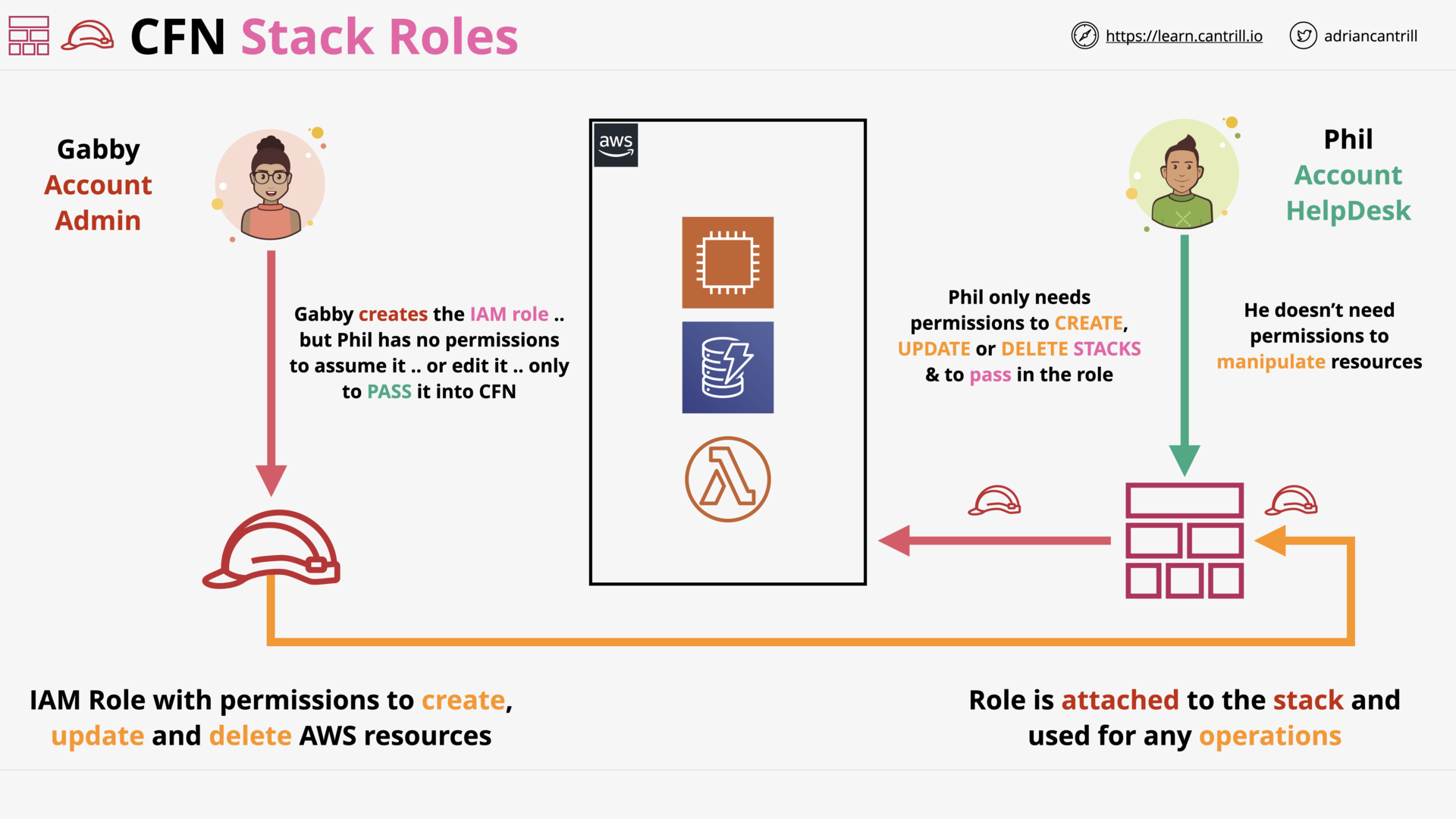 Cfn Stack Roles - Example
Cfn Stack Roles - Example
CloudFormation Init (cfn-init) (8:48)
 cfn-init: Overview
cfn-init: Overview
aws::cloudformation::init vs cfn-init?
AWS::CloudFormation::Init: a part of the logical resource for EC2 (Metadatakey)cfn-init: a helper script in theProperties’sUserData, will run by the EC2 instance
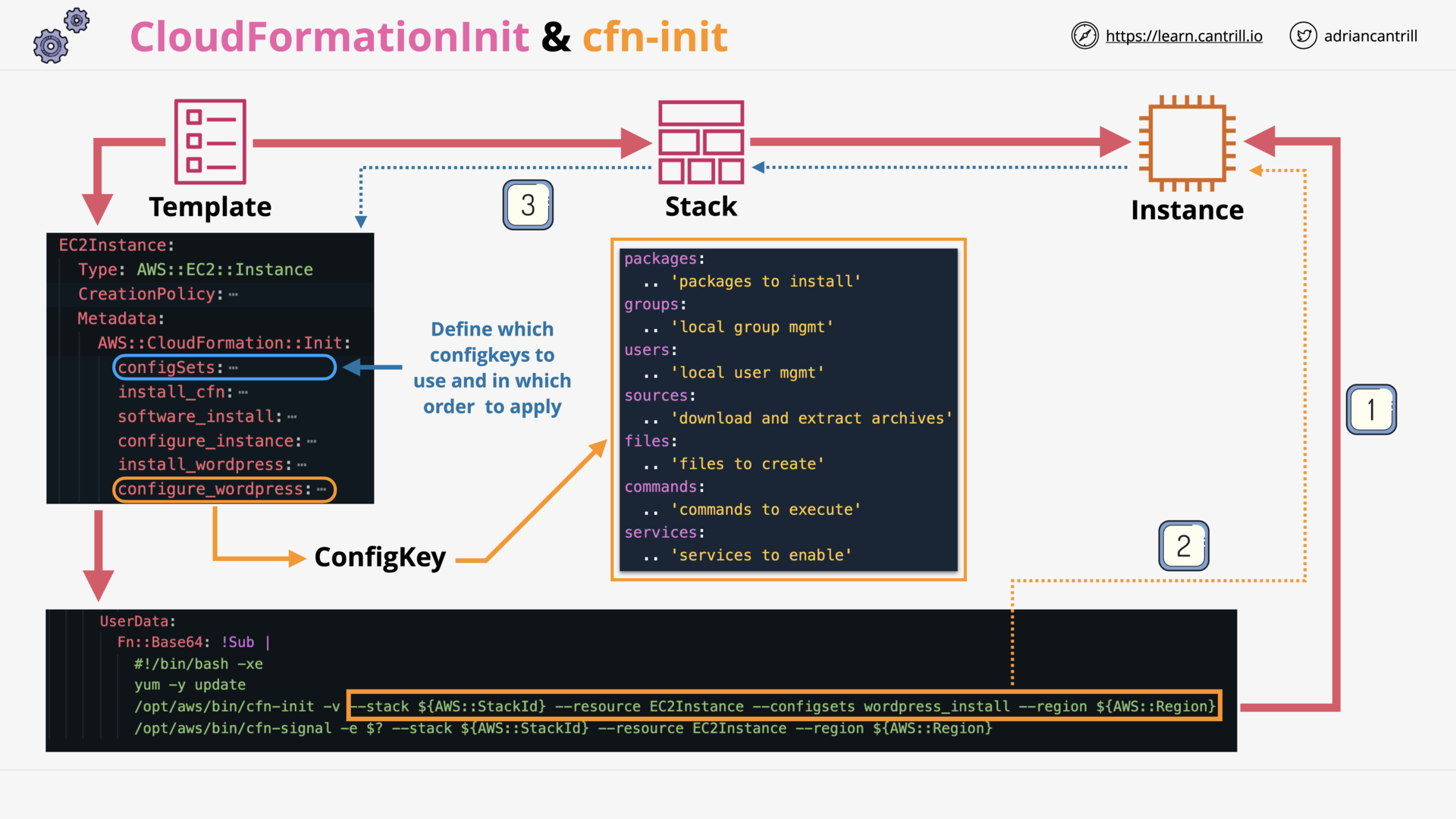 cfn-init: config keys - configsets
cfn-init: config keys - configsets
See:
CloudFormation cfn-hup (4:13)
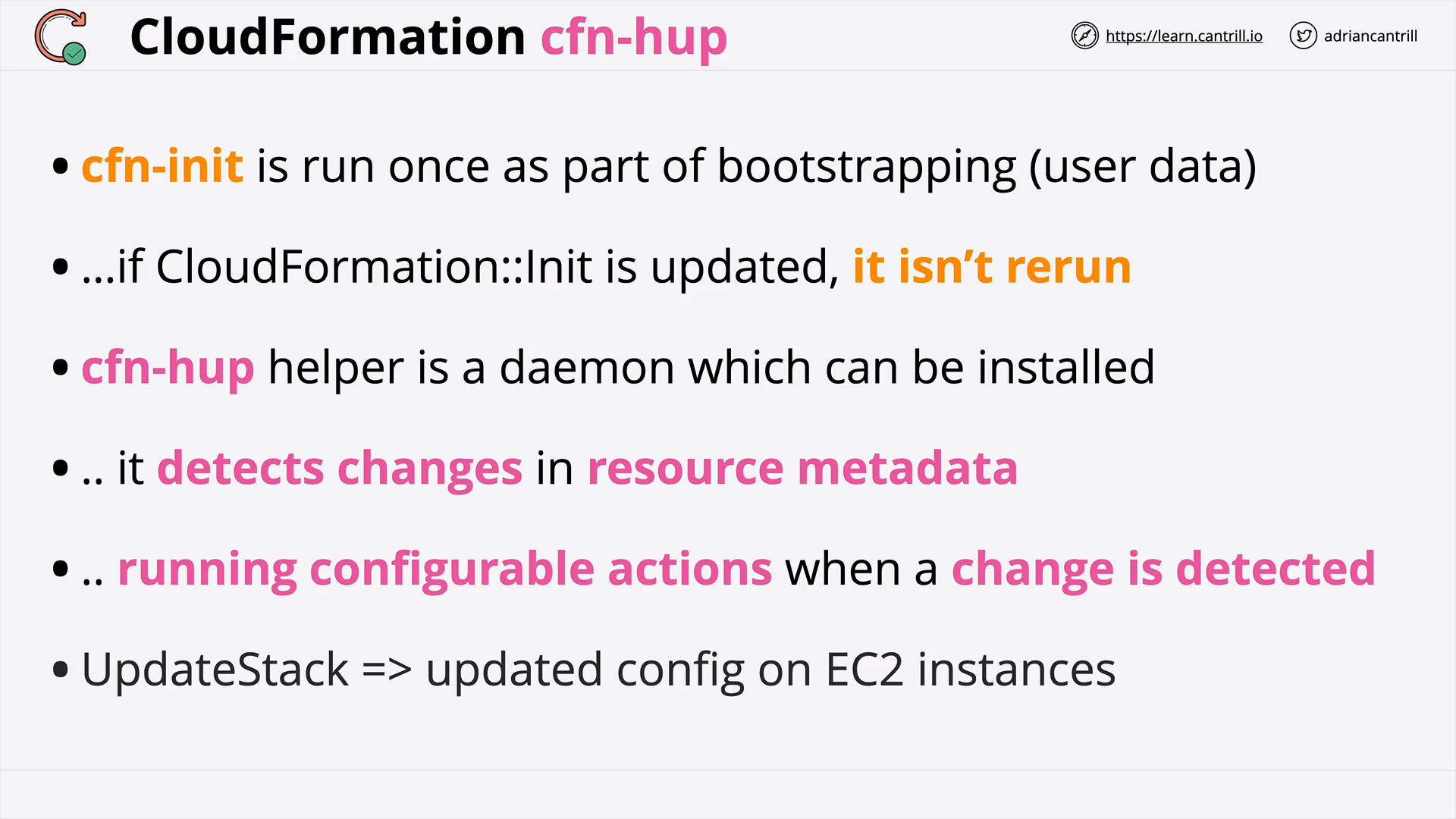 cfn-init: The problem
cfn-init: The problem
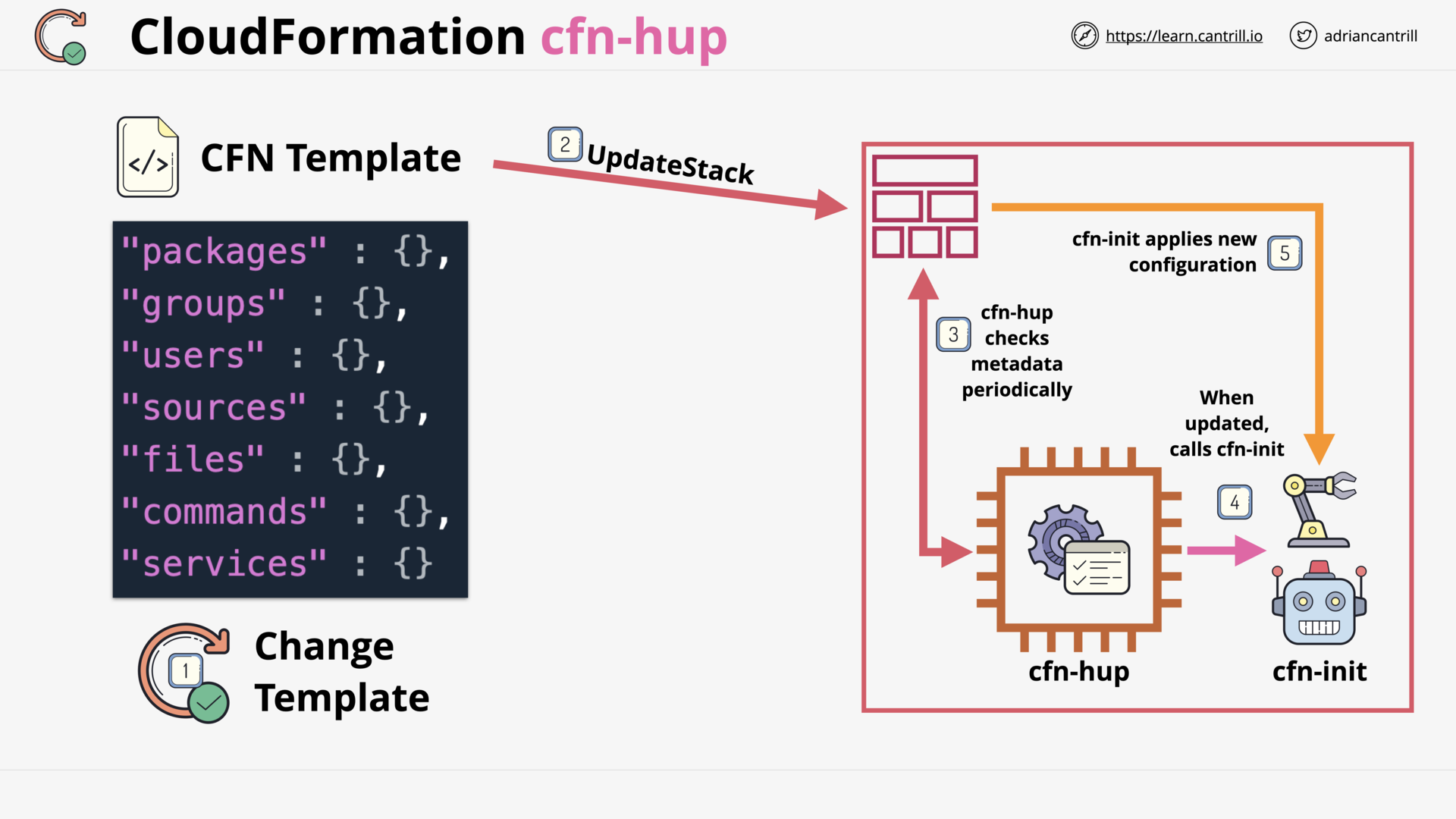 cfn-hup: Rerun config when change detected
cfn-hup: Rerun config when change detected
what cfn-hup stands for?
cfn hot update.
See Update behaviors of stack resources
[DEMO] wait conditions, cfn-signal, cfn-init and cfn-hup-PART1 (12:51)
[DEMO] wait conditions, cfn-signal, cfn-init and cfn-hup-PART2 (14:42)
CloudFormation ChangeSets [NEW VERSION COMING SOON] (11:03)
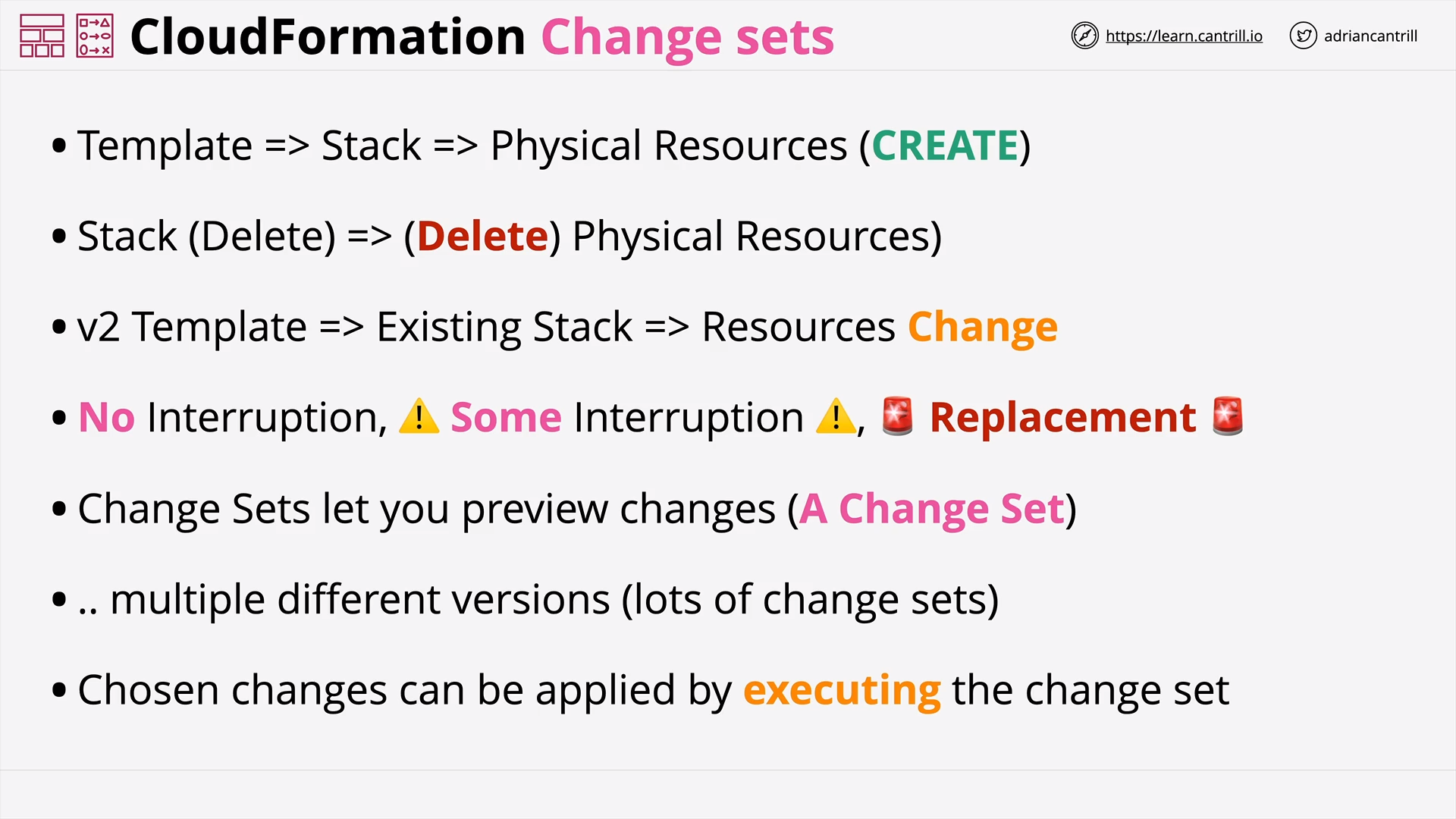 Cfn ChangeSets: Preview changes before execute
Cfn ChangeSets: Preview changes before execute
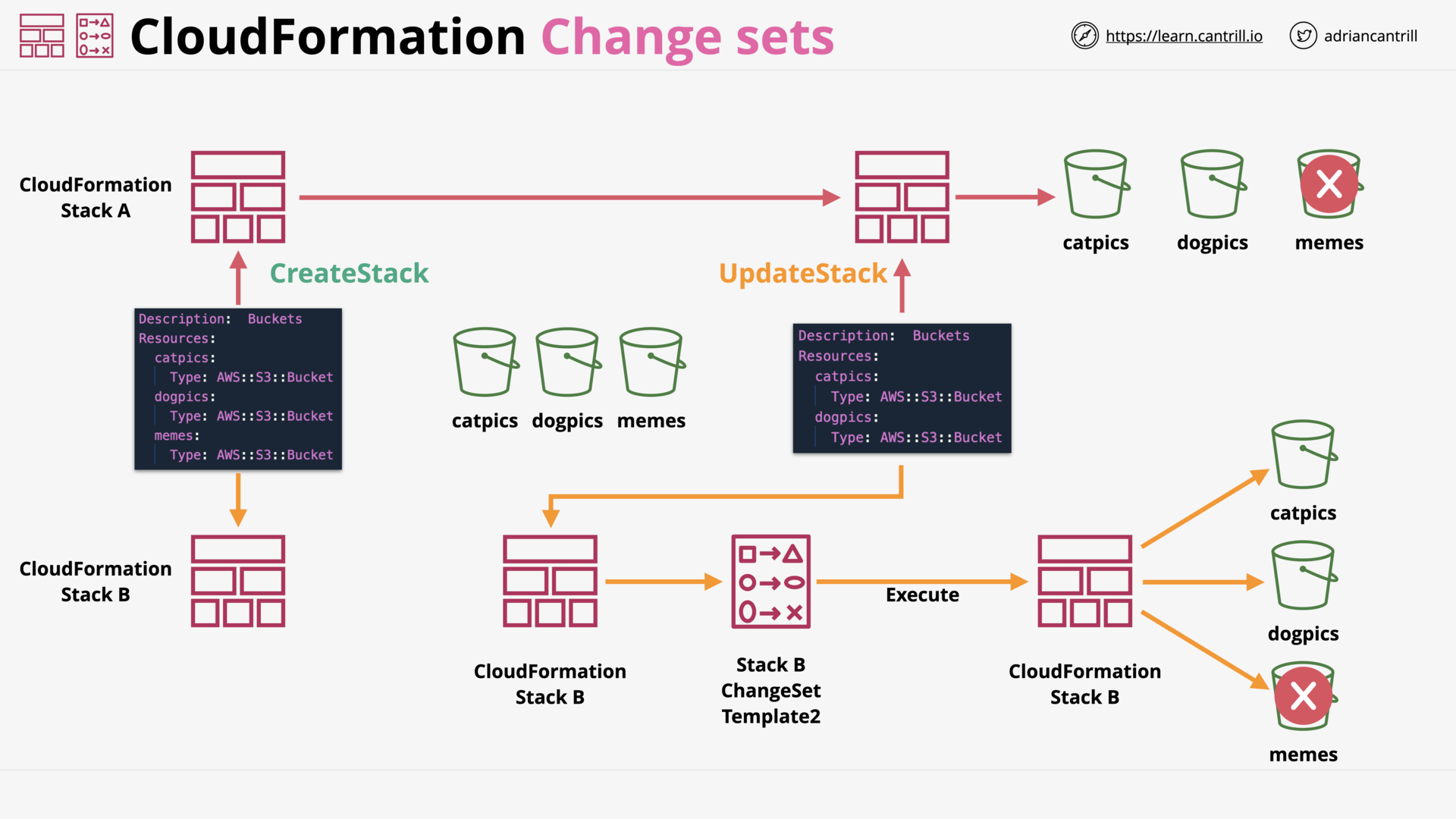 Cfn ChangeSets: Example
Cfn ChangeSets: Example
CloudFormation Custom Resources (11:03)
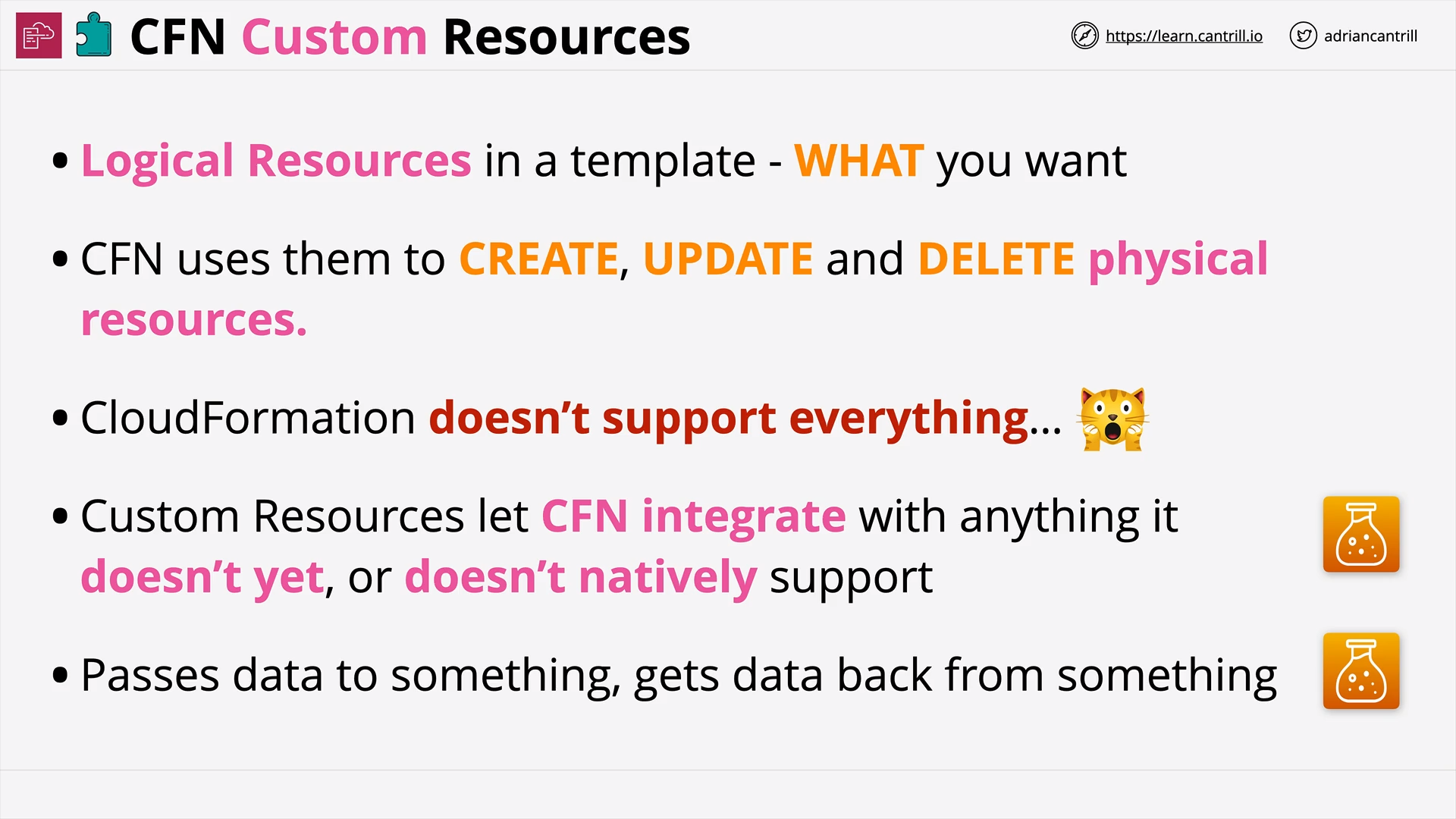 Cfn Custom Resources: Let Cfn integrate with not-natively-support things
Cfn Custom Resources: Let Cfn integrate with not-natively-support things
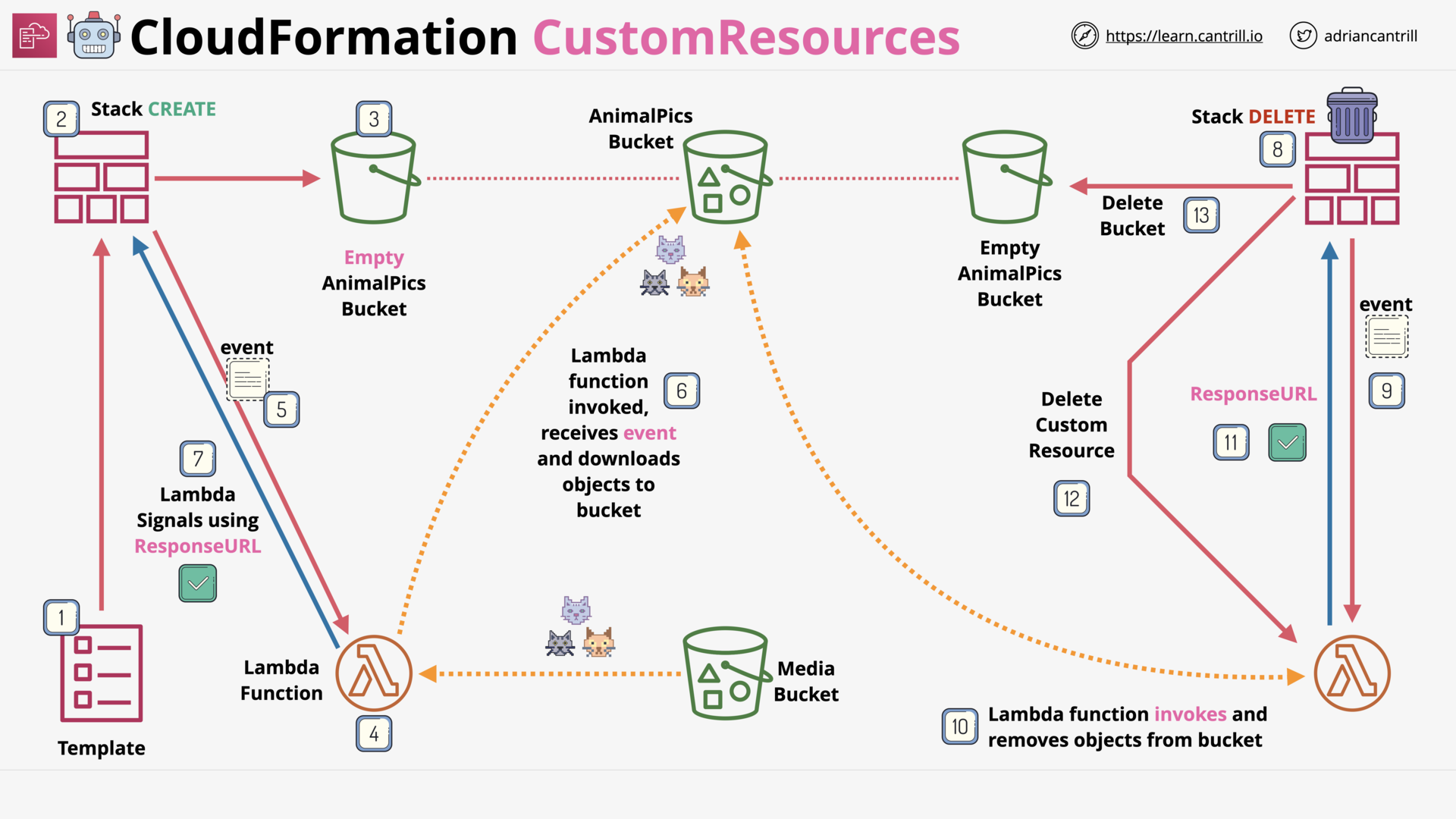 Cfn Custom Resources: Example
Cfn Custom Resources: Example
[DEMO] CloudFormation Custom Resources-PART1 (9:12)
[DEMO] CloudFormation Custom Resources-PART2 (13:27)
Value of the physical ID of the resource or the value of the parameter
Attribute’s value
The list of Availability Zones for the Region.
The selected object (0-index)
echo -n 'AWS CloudFormation' | base64
For Ref, the full form is more simple than the short form
NOSQL DATABASES & DYNAMODB
DynamoDB - Architecture (10:49)
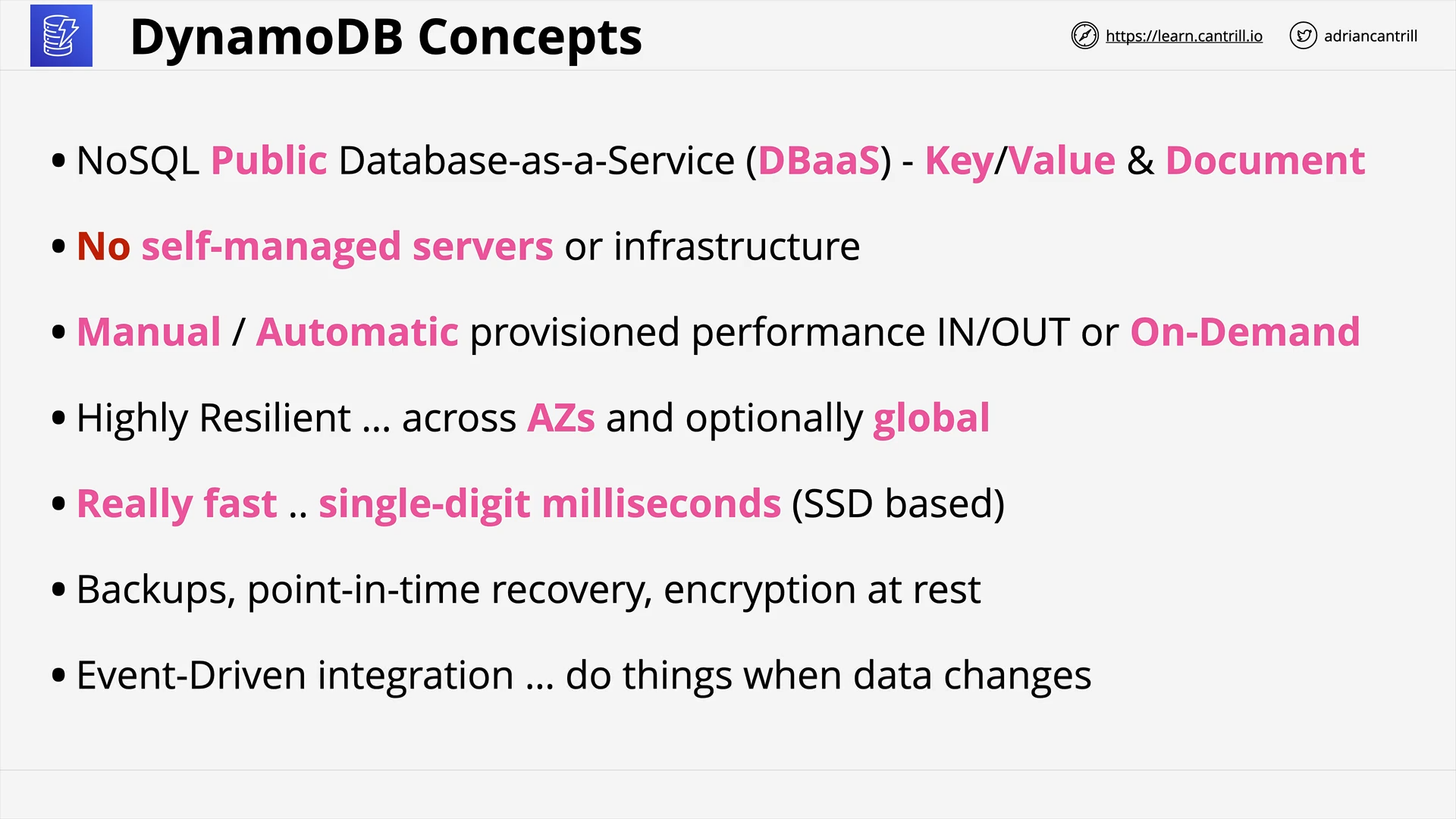 DynamoDB Concepts
DynamoDB Concepts
what is dynamodb?
what is the selling point of dynamodb?
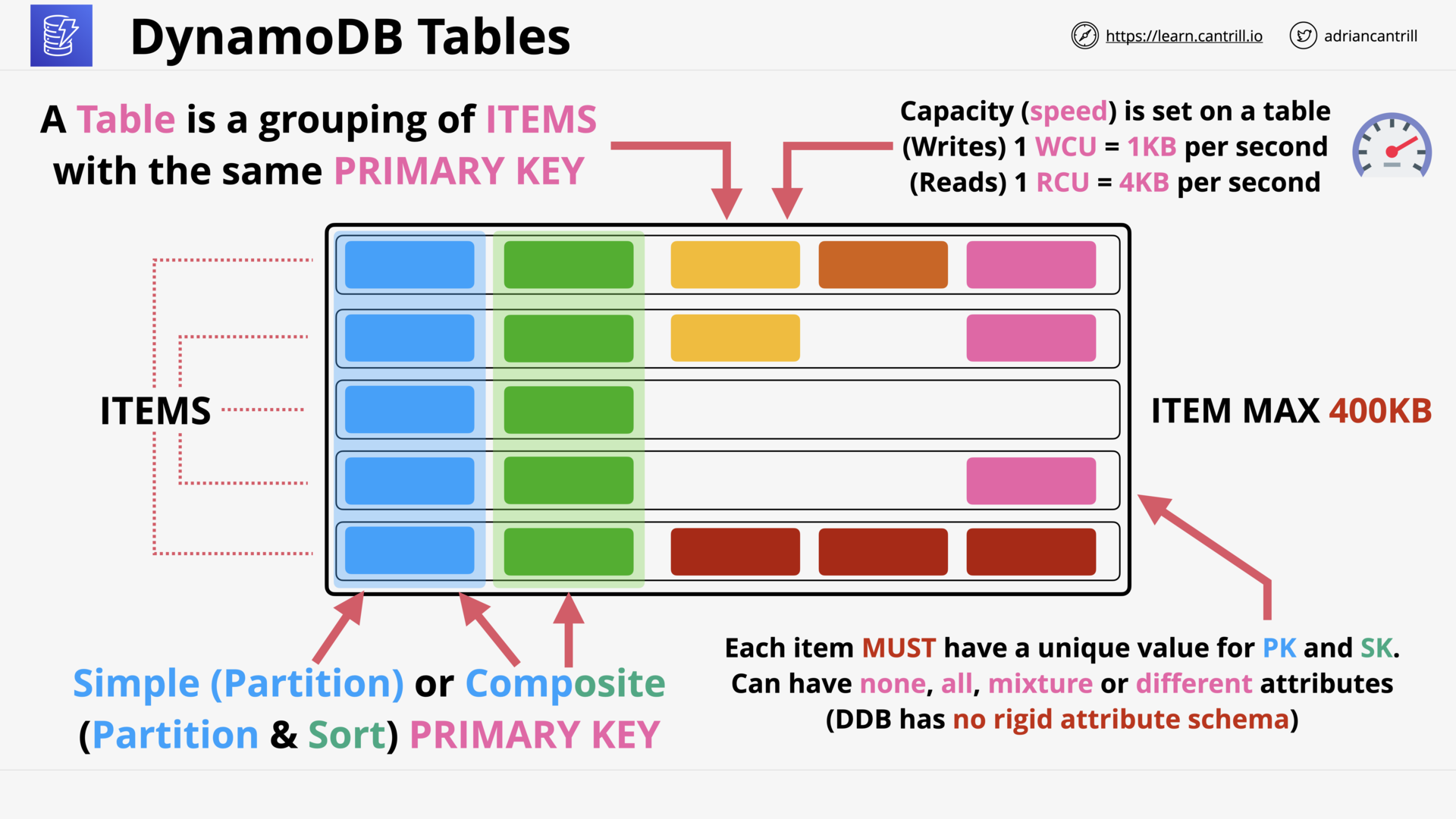 DynamoDB: Tables - Items - Attributes - Primary Key (PK): Partition Key & Sort Key (PK & SK)
DynamoDB: Tables - Items - Attributes - Primary Key (PK): Partition Key & Sort Key (PK & SK)
what is a *primary key*?
Primary key uniquely identifies each item in the table, so that no two items can have the same key.
what is a *partition key*?
Partition key is the required part of primary key.
-
The partition key of an item is also known as its hash attribute.
-
The term hash attribute derives from the use of an internal hash function in DynamoDB that evenly distributes data items across partitions, based on their partition key values.
what is a *sort key*?
Sort key is an optional part of primary key.
- The sort key of an item is also known as its range attribute.
- The term range attribute derives from the way DynamoDB stores items with the same partition key physically close together, in sorted order by the sort key value.
what is capacity of dynamodb?
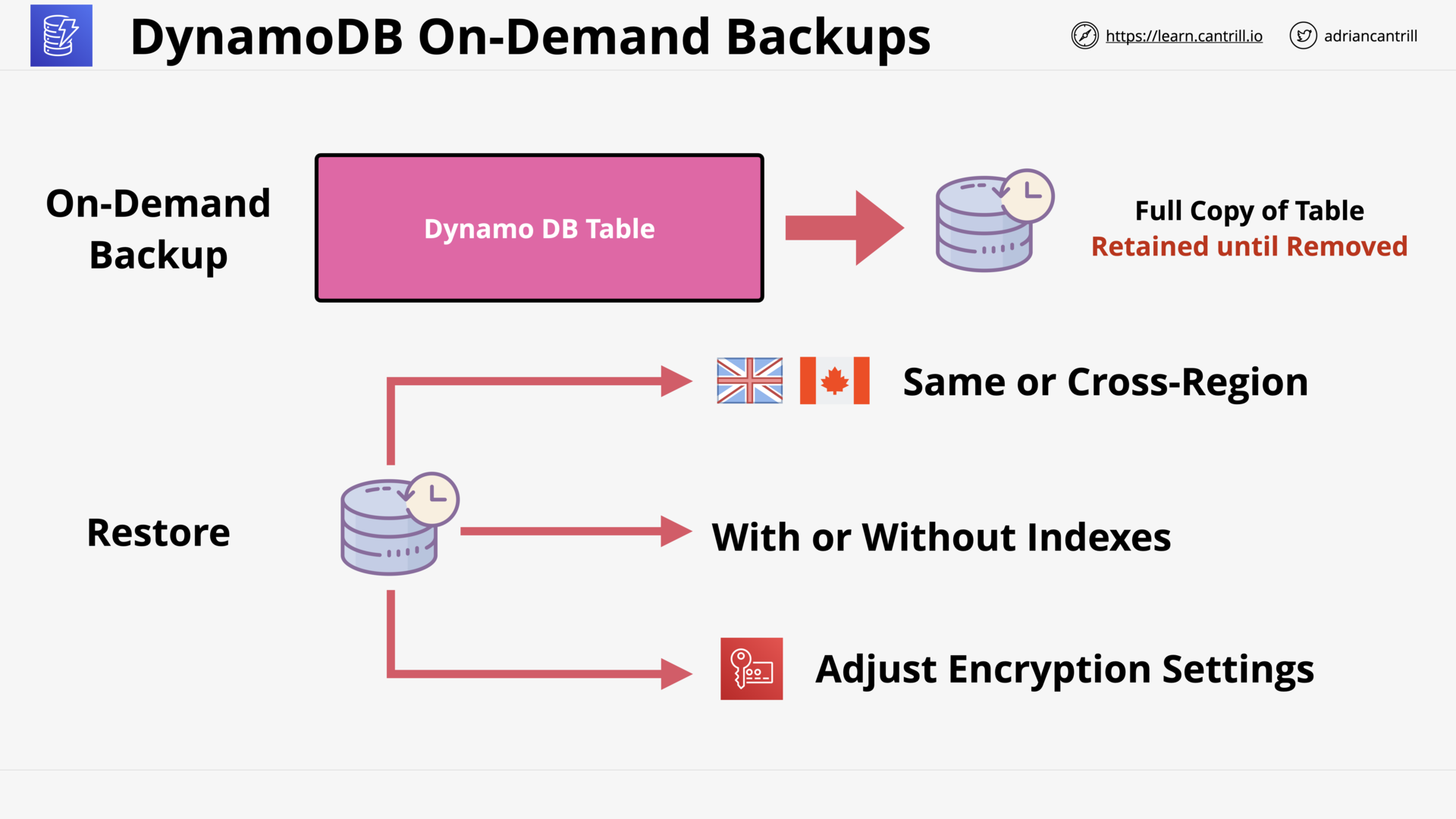 DynamoDB On-Demand Backups
DynamoDB On-Demand Backups
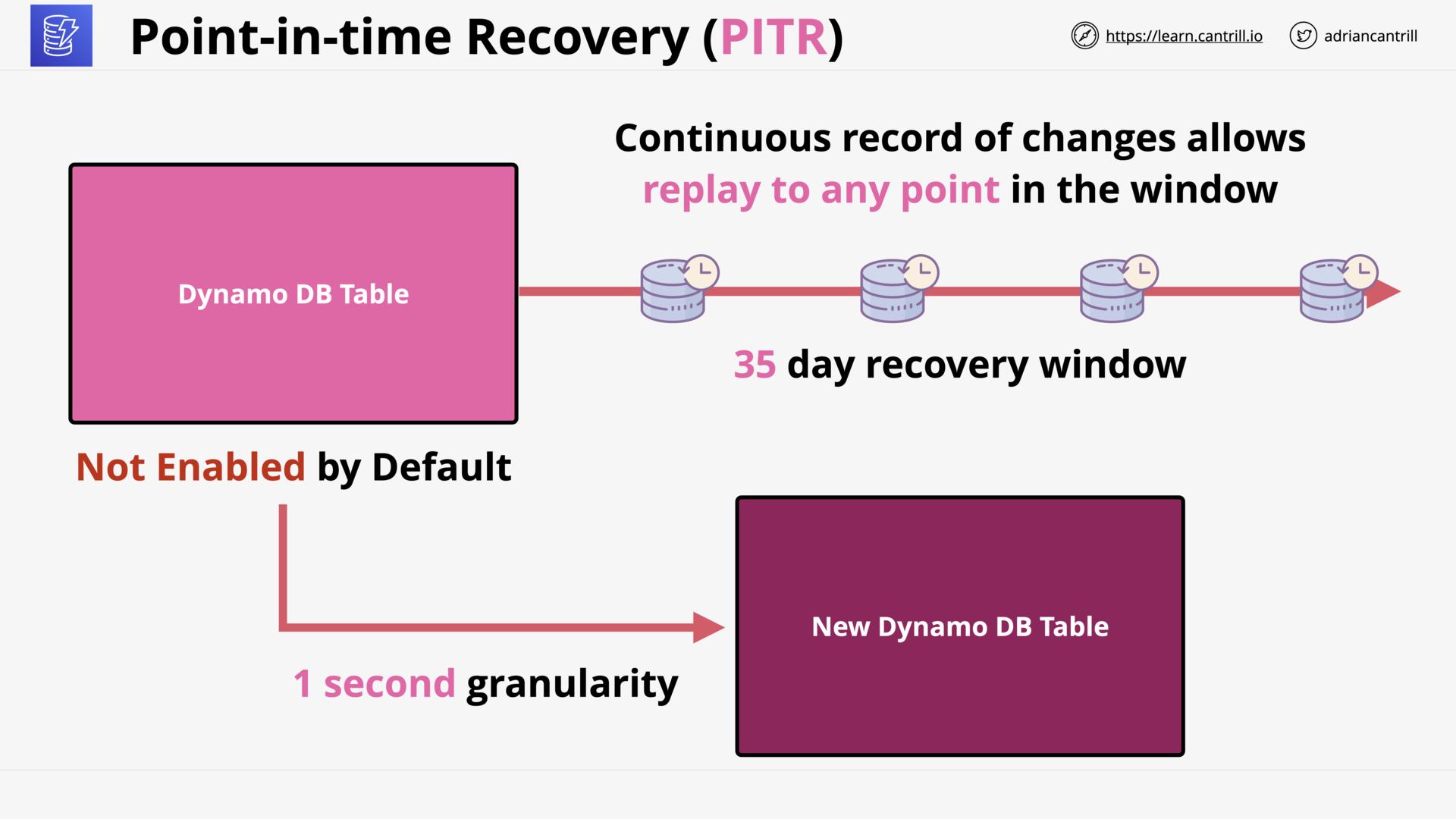 DynamoDB PITR
DynamoDB PITR
 DynamoDB Considerations
DynamoDB Considerations
how is dynamodb billed?
DynamoDB - Operations, Consistency and Performance - PART1 (13:06)
 DynamoDB Reading & Writing: On-Demand / Provisioned
DynamoDB Reading & Writing: On-Demand / Provisioned
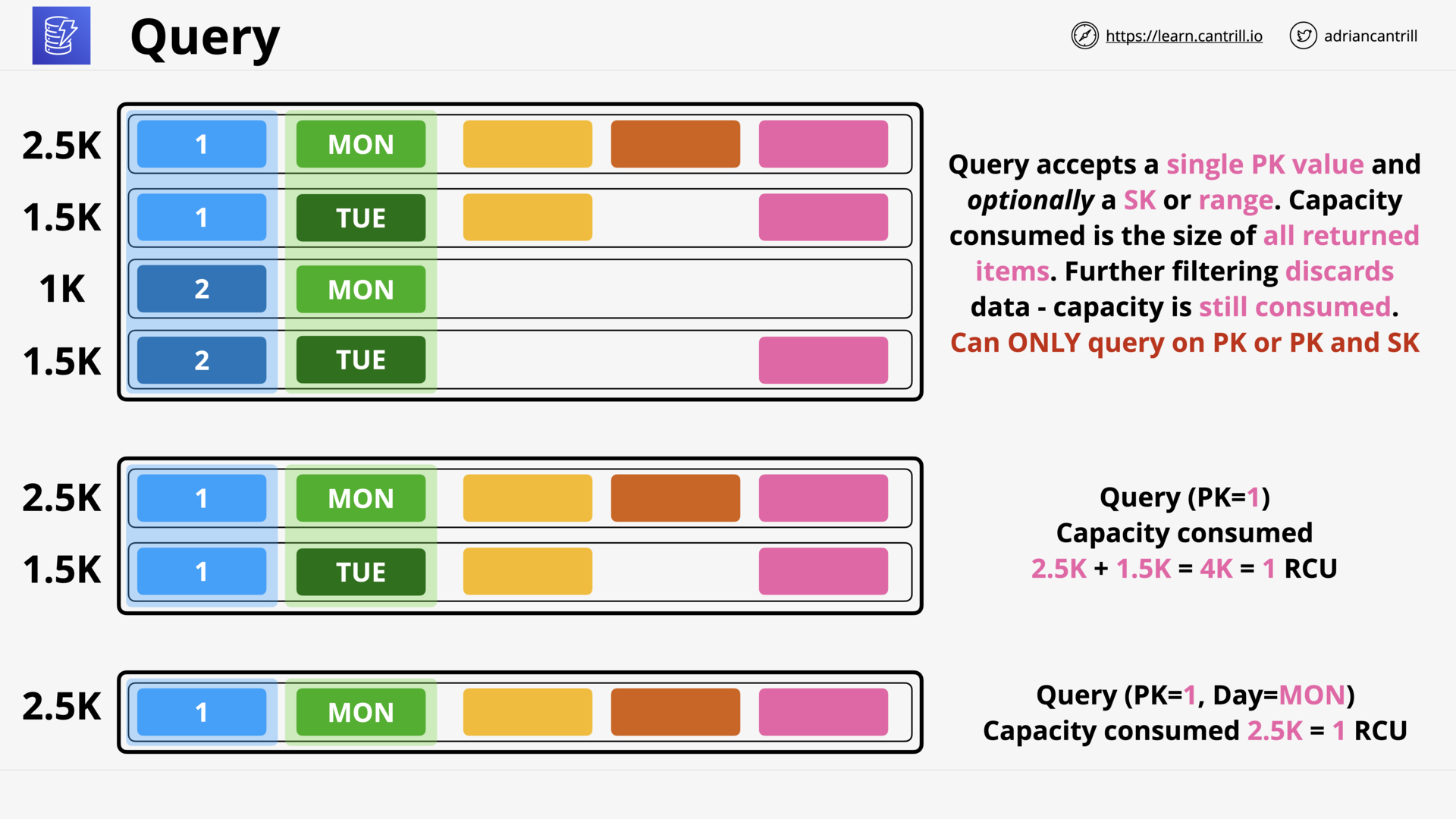 DynamoDB Query: Find items based on primary key values
DynamoDB Query: Find items based on primary key values
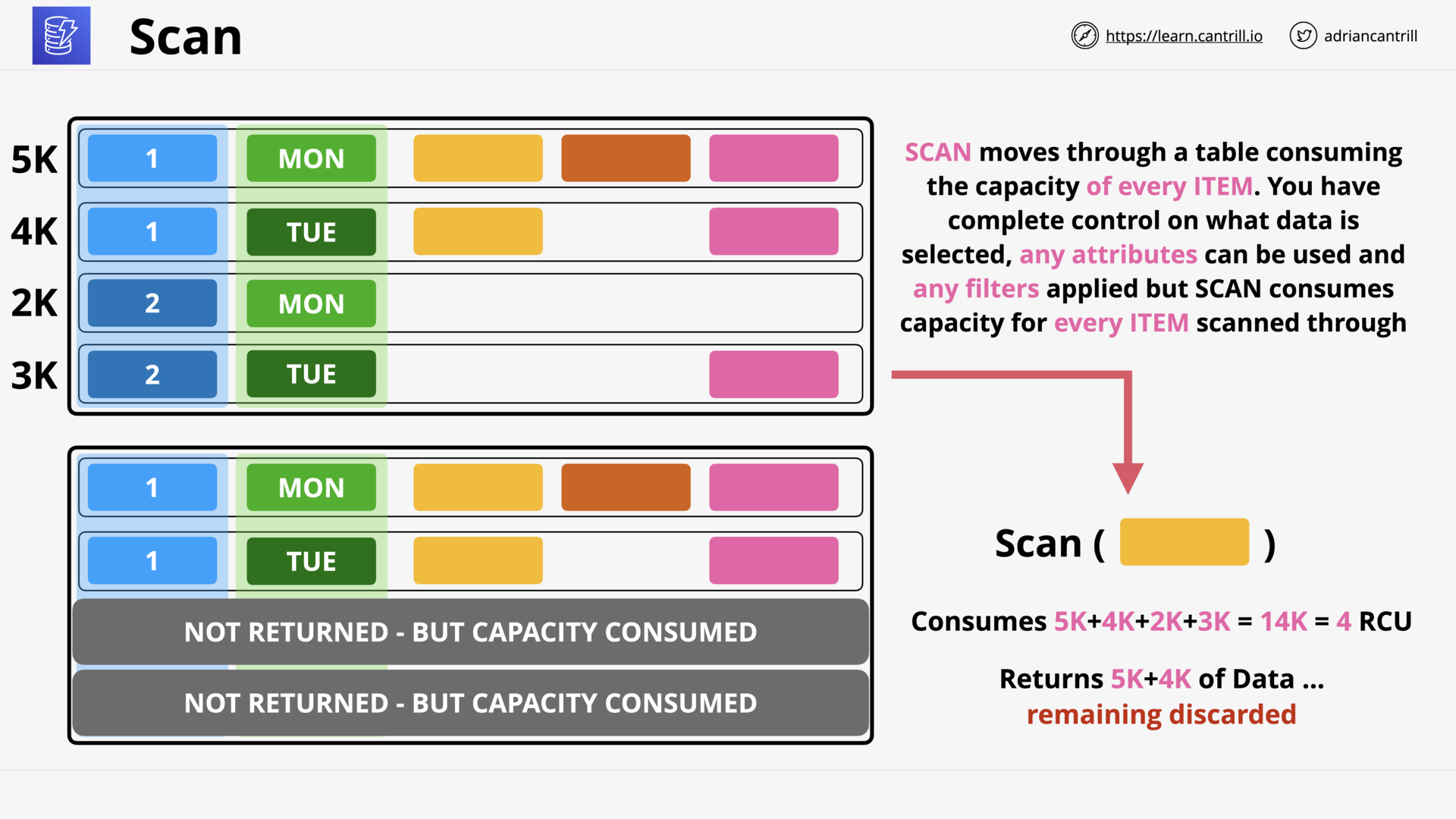 DynamoDB Scan: Reads every item in a table or a secondary index.
DynamoDB Scan: Reads every item in a table or a secondary index.
DynamoDB - Operations, Consistency and Performance - PART2 (11:24)
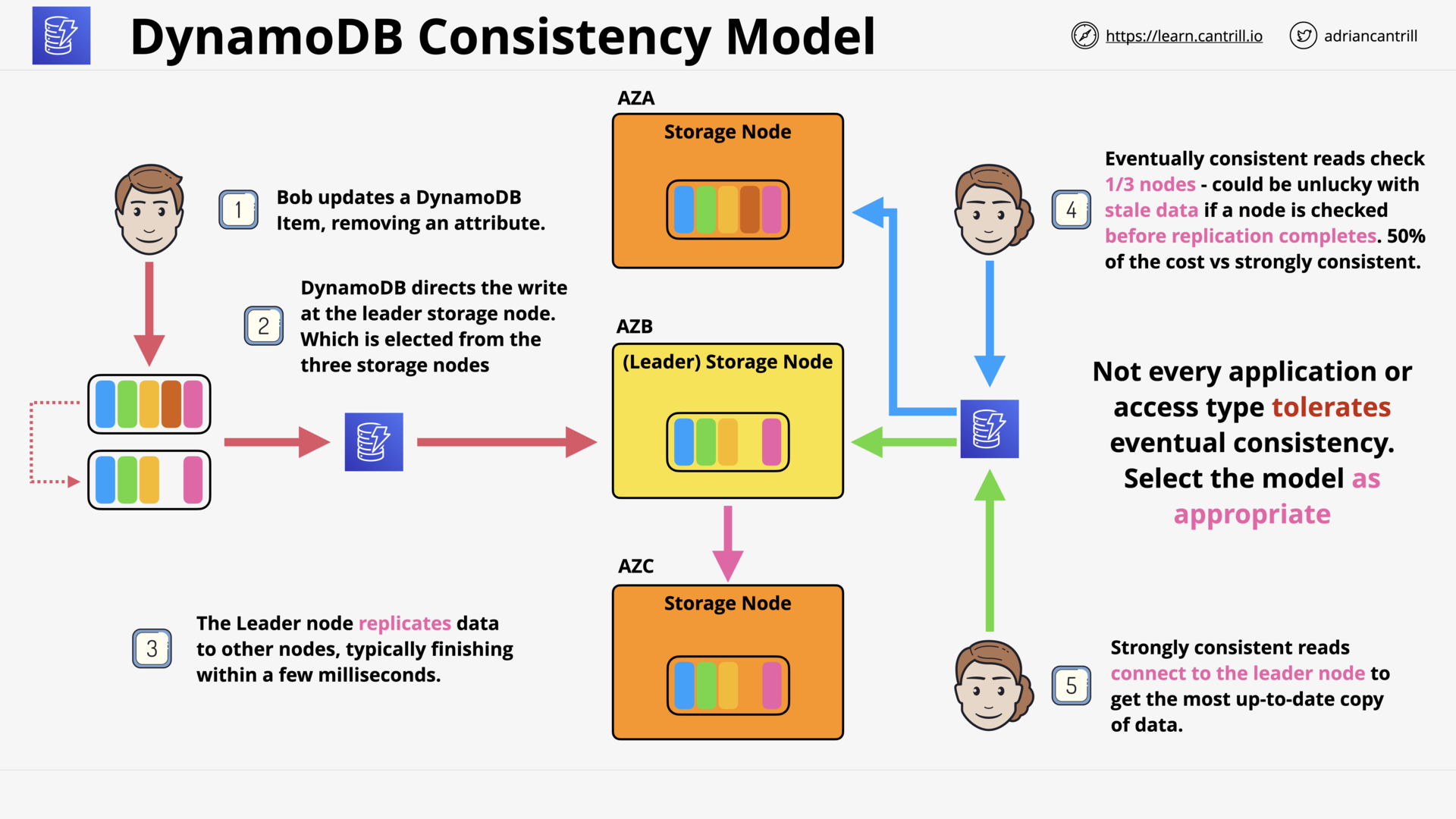 DynamoDB Consistency Model
DynamoDB Consistency Model
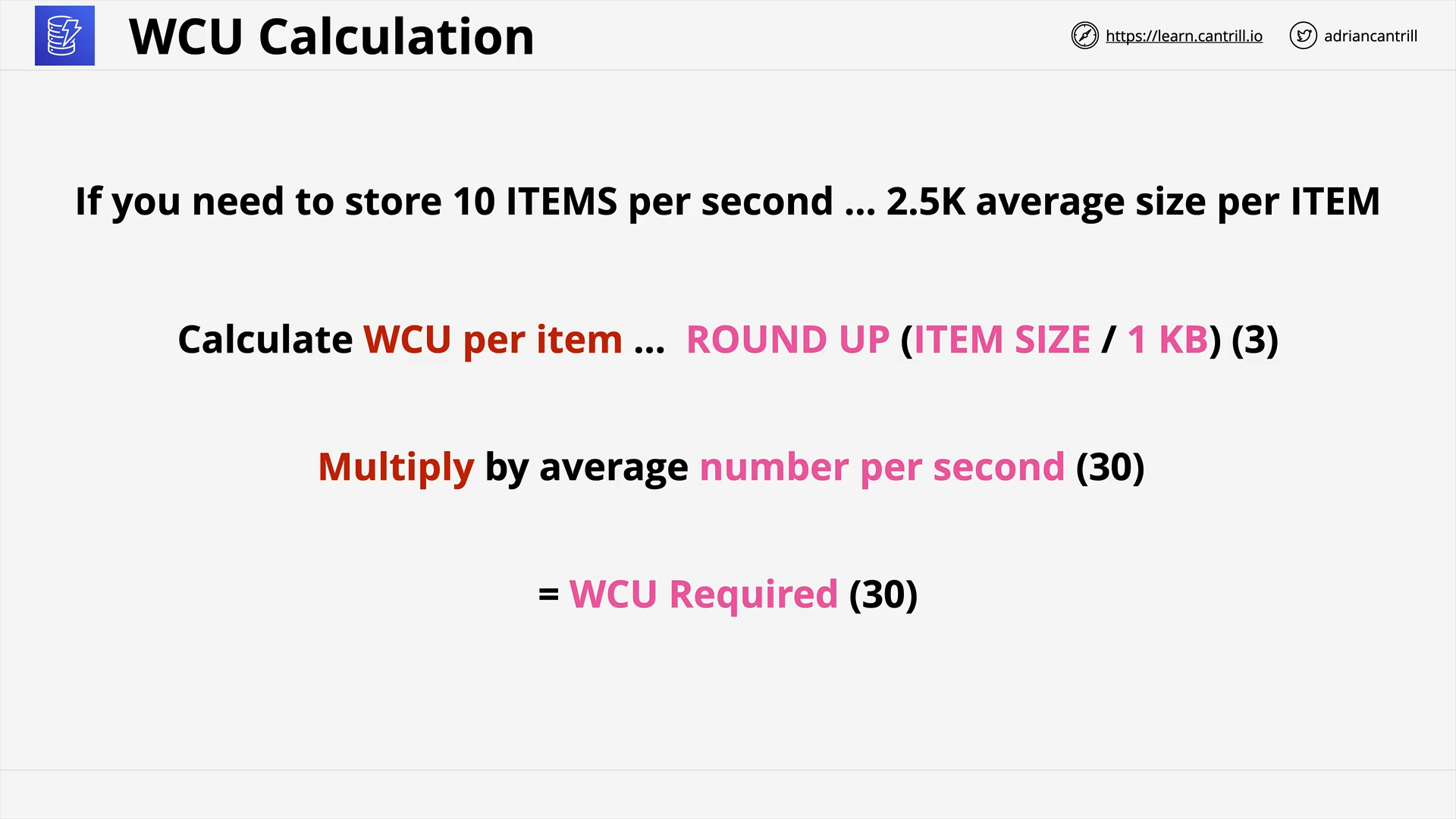 DynamoDB - WCU Calculation
DynamoDB - WCU Calculation
 DynamoDB - RCU Calculation
DynamoDB - RCU Calculation
DynamoDB Local and Global Secondary Indexes (12:35)
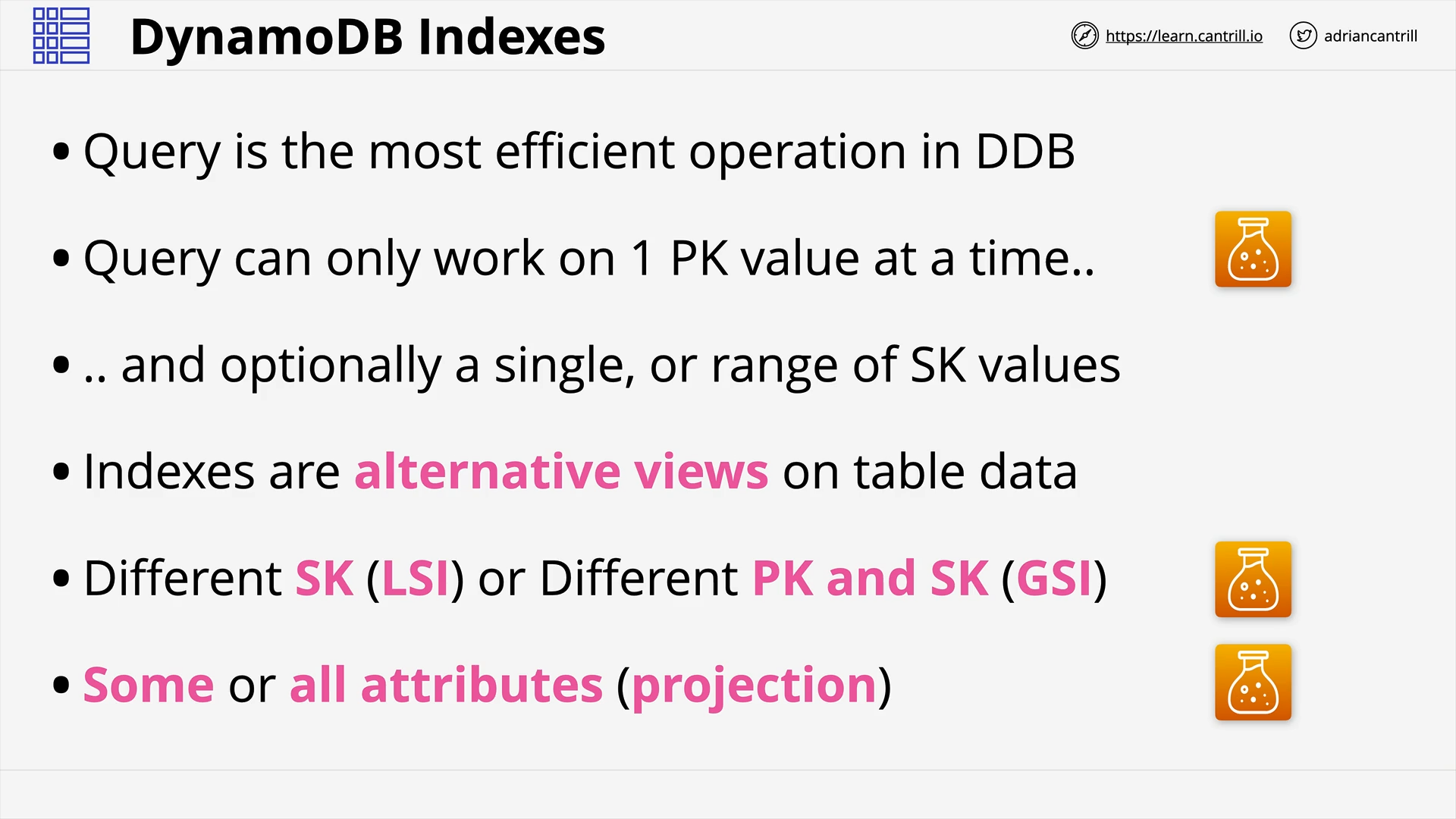 DynamoDB Secondary Indexes: Alternative views on table data
DynamoDB Secondary Indexes: Alternative views on table data
in dynamodb, what is attribute projection?
When you create an index:
- You define an alternate key for the index (partition key and sort key).
- You also define the attributes that you want to be projected, or copied, from the base table into the index.
Every secondary index is associated with exactly one table, from which it obtains its data.
(Source)
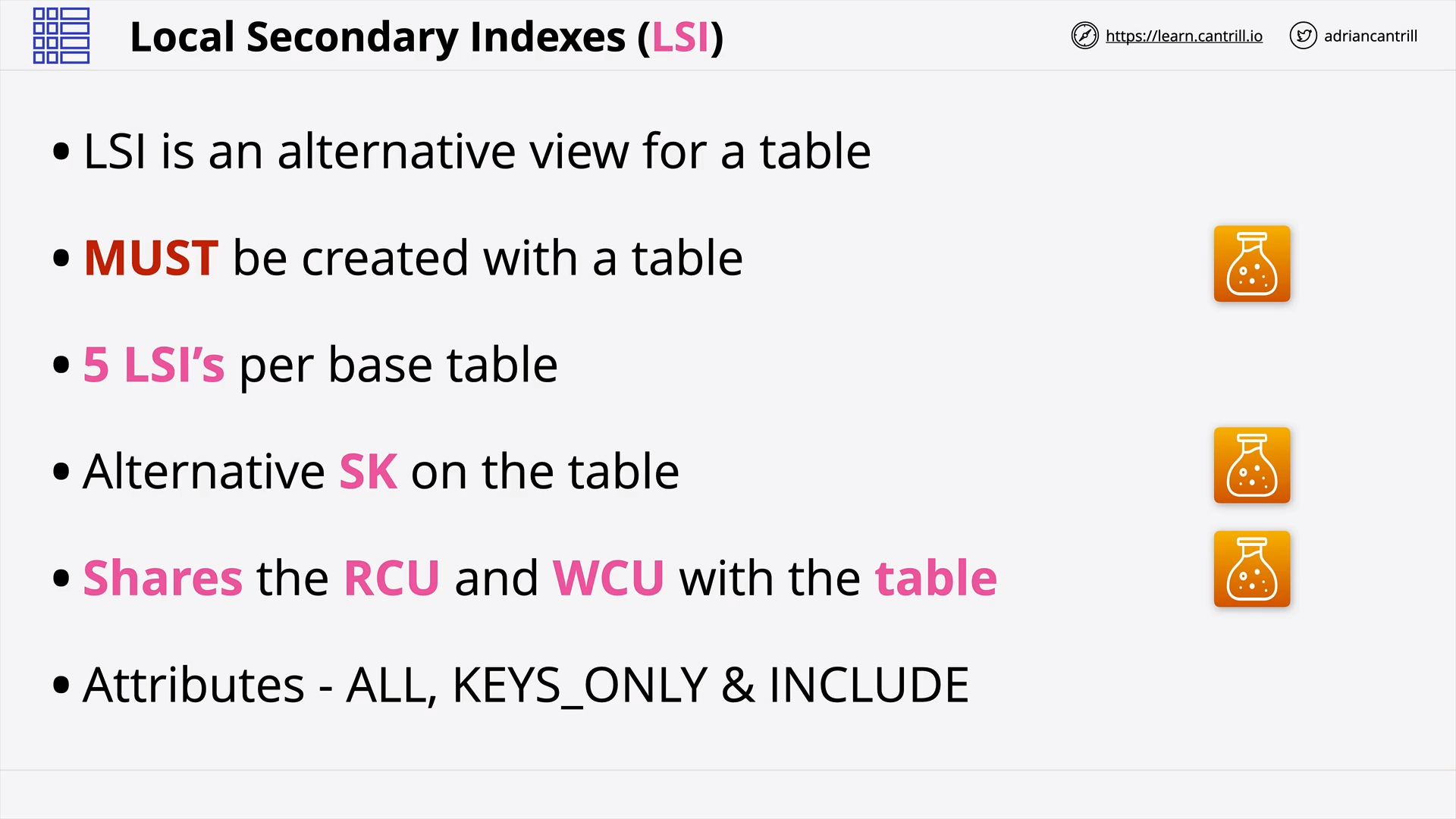 DynamoDB Local Secondary Indexes (LSI): Alternative Sort Key
DynamoDB Local Secondary Indexes (LSI): Alternative Sort Key
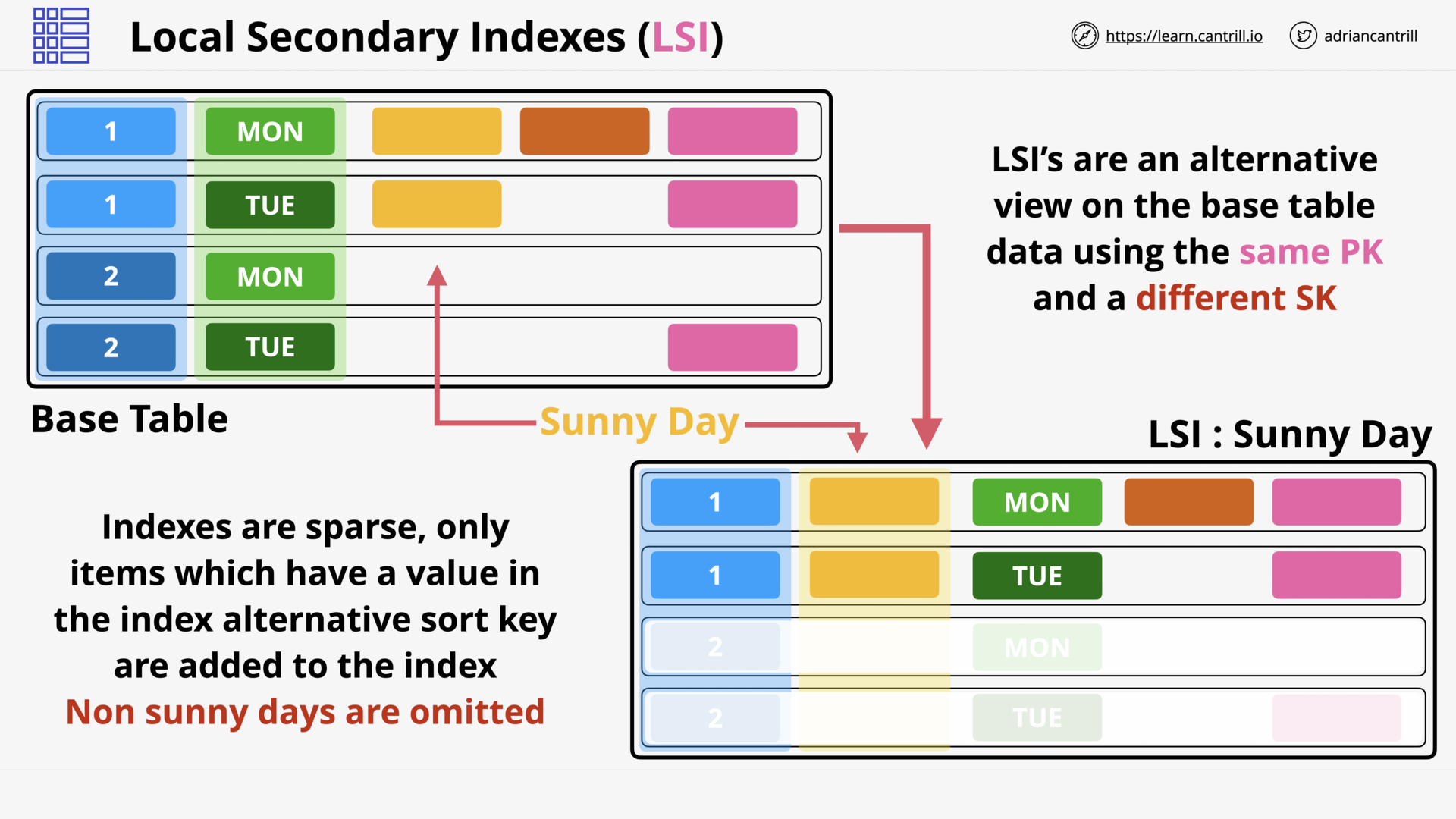 DynamoDB LSI: Using the base table’s primary key
DynamoDB LSI: Using the base table’s primary key
 DynamoDB Global Secondary Indexes (GSI): Alternative Partition Key & Sort Key
DynamoDB Global Secondary Indexes (GSI): Alternative Partition Key & Sort Key
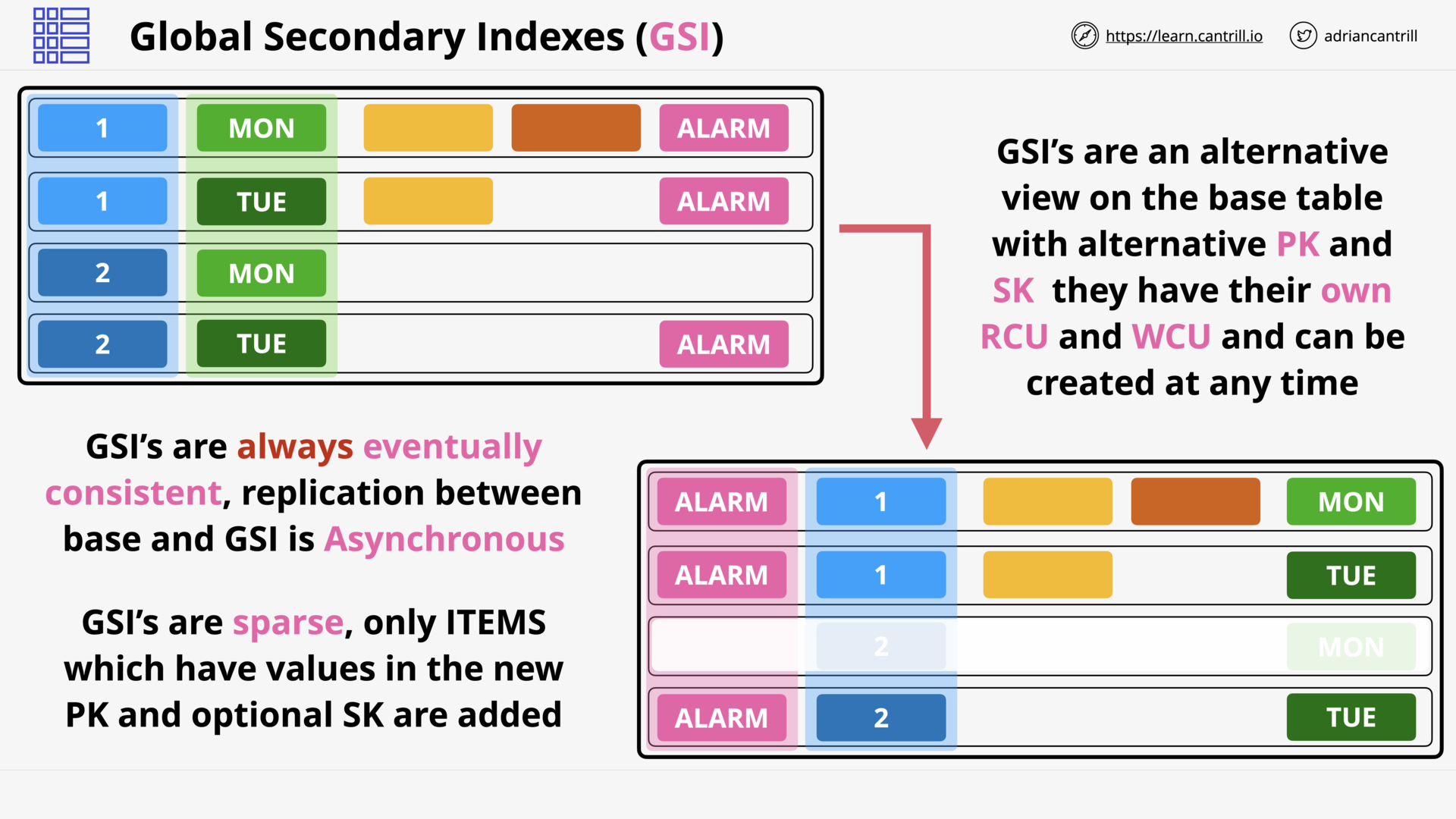 DynamoDB GSI: Always eventually consistent
DynamoDB GSI: Always eventually consistent
 LSI & GSI Considerations
LSI & GSI Considerations
when to use gsi & lci?
Amazon DynamoDB provides fast access to items in a table by specifying primary key values.
However, many applications might benefit from having one or more secondary (or alternate) keys available, to allow efficient access to data with attributes other than the primary key.
-
GSI: Some applications might need to perform many kinds of queries, using a variety of different attributes as query criteria.
-
LSI: Some applications only need to query data using the base table’s primary key. However, there might be situations where an alternative sort key would be helpful.
DynamoDB - Streams & Lambda Triggers (9:10)
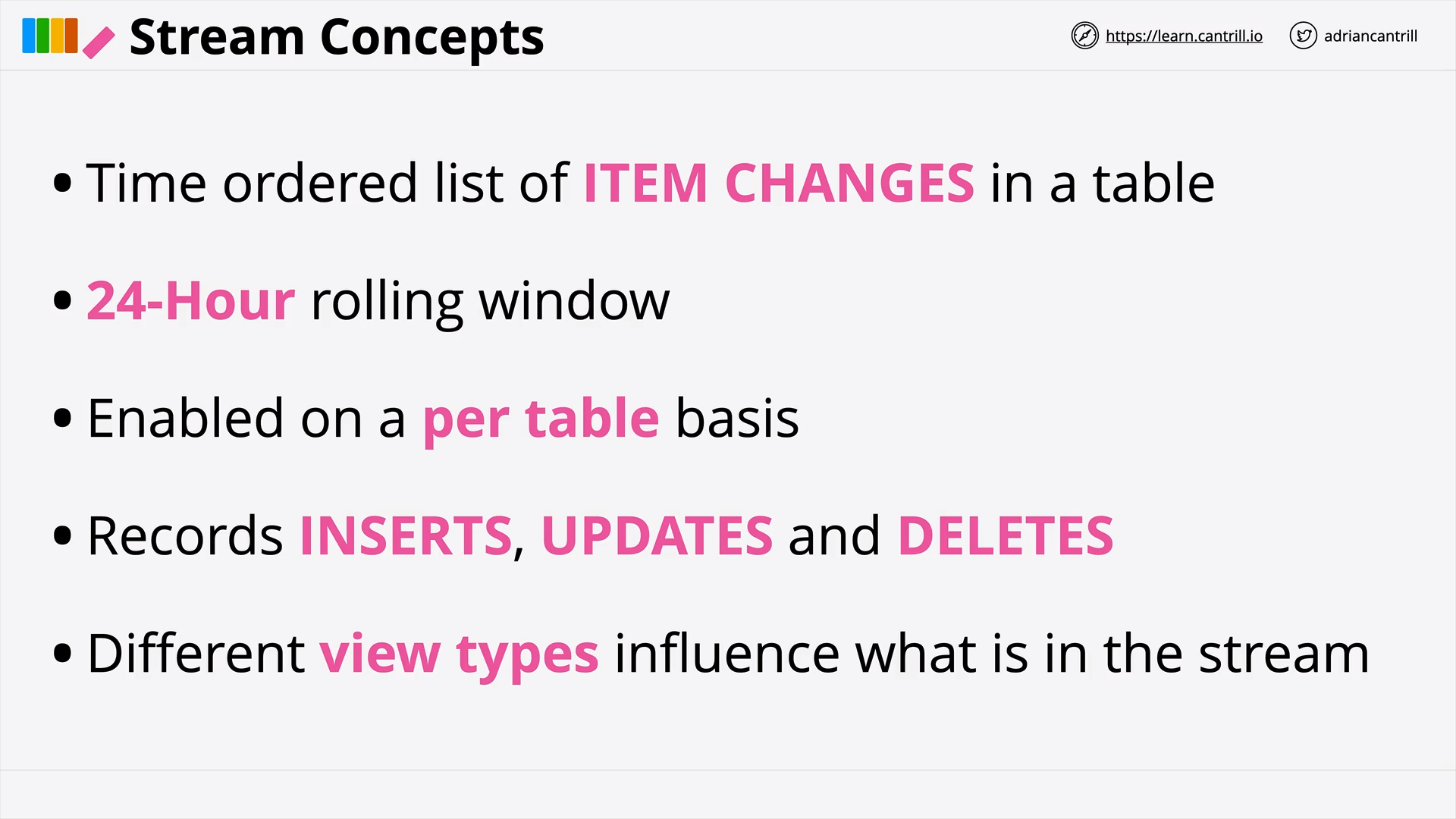 DynamoDB - Stream Concepts
DynamoDB - Stream Concepts
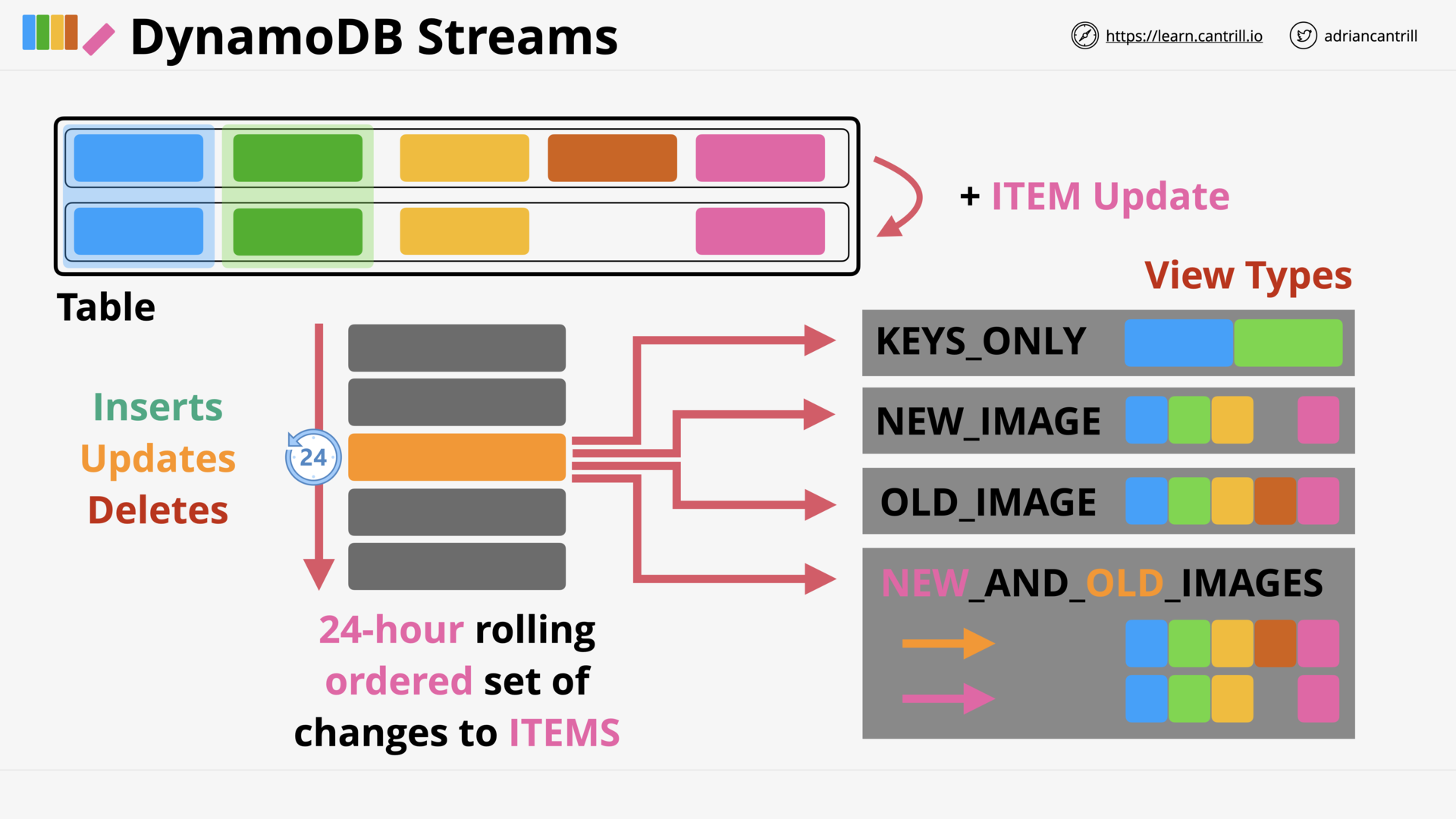 DynamoDB - Stream Architecture
DynamoDB - Stream Architecture
 DynamoDB - Trigger Concepts
DynamoDB - Trigger Concepts
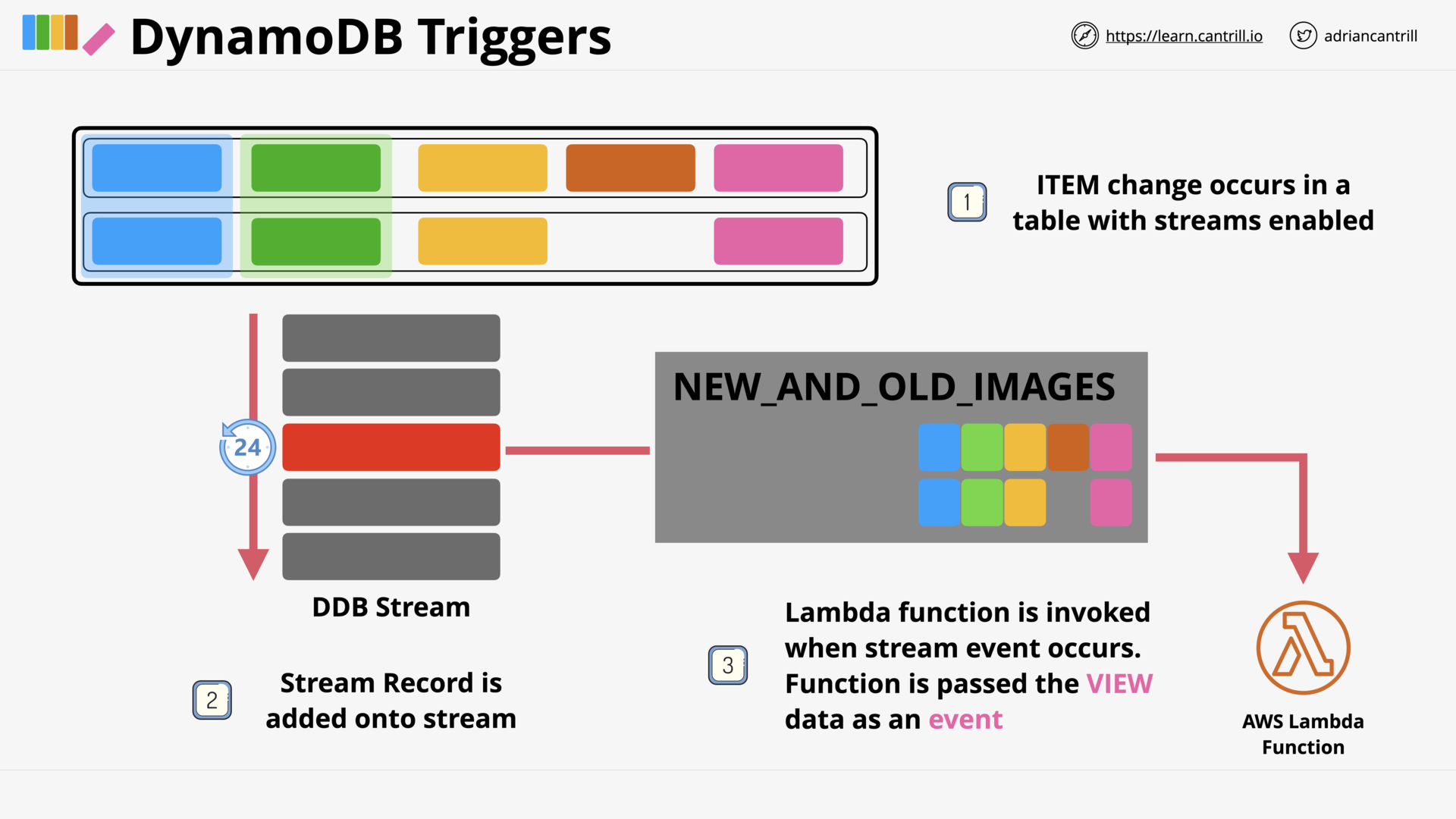 DynamoDB - Trigger Architecture
DynamoDB - Trigger Architecture
DynamoDB - Global Tables (5:09)
 DynamoDB - Global Tables: Overview
DynamoDB - Global Tables: Overview
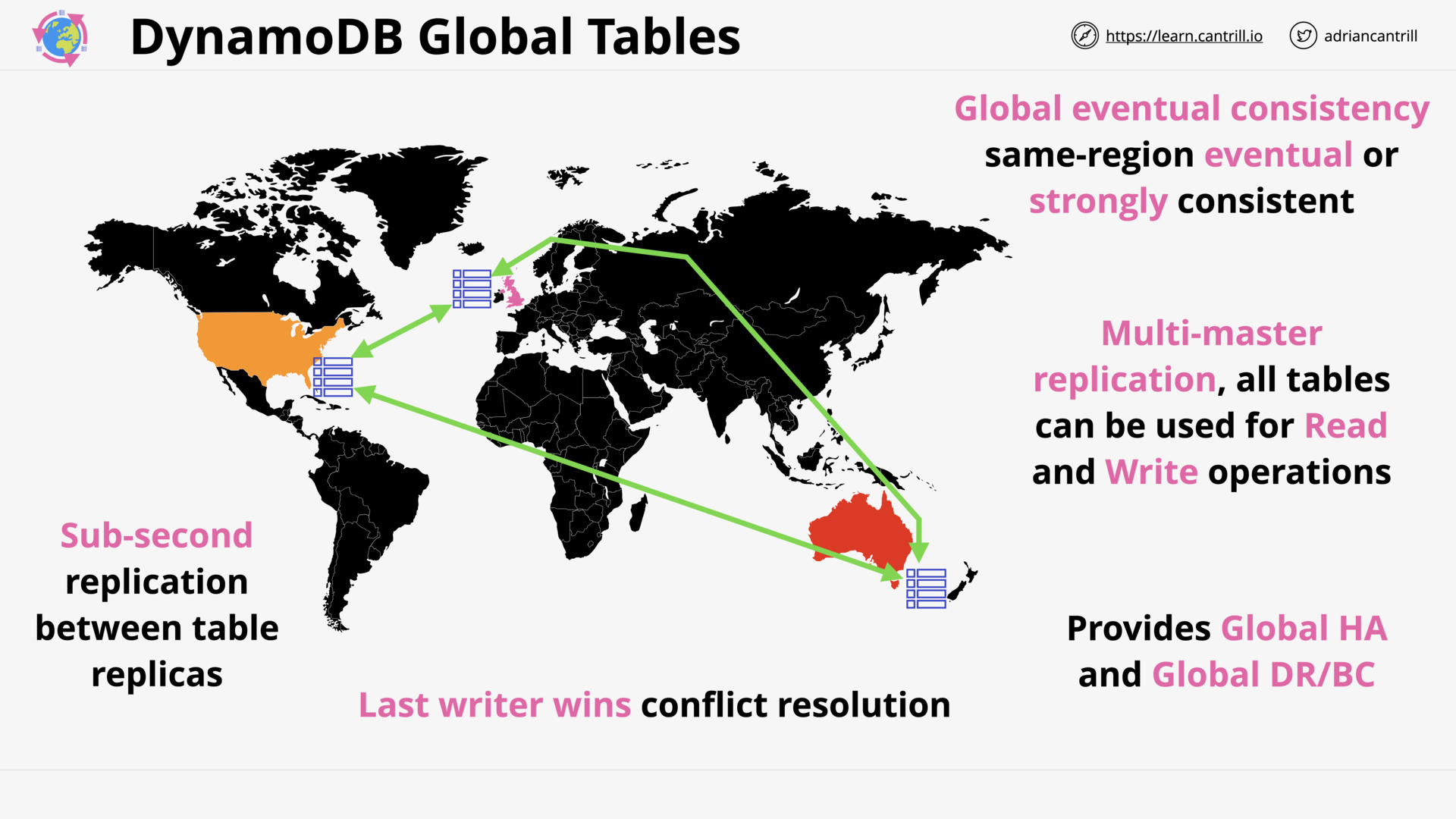 DynamoDB - Global Tables: Architecture
DynamoDB - Global Tables: Architecture
what are exactly a dynamodb *global table*?
A global table is a collection of one or more replica tables, all owned by a single AWS account.
A replica table (or replica, for short) is a single DynamoDB table that functions as a part of a global table.
Source: Global Tables - How it works?
which type are global table's replica tables?
All replica tables are master/active, supports both read and write operations.
Each replica stores the same set of data items.
DynamoDB - Accelerator (DAX) (10:58)
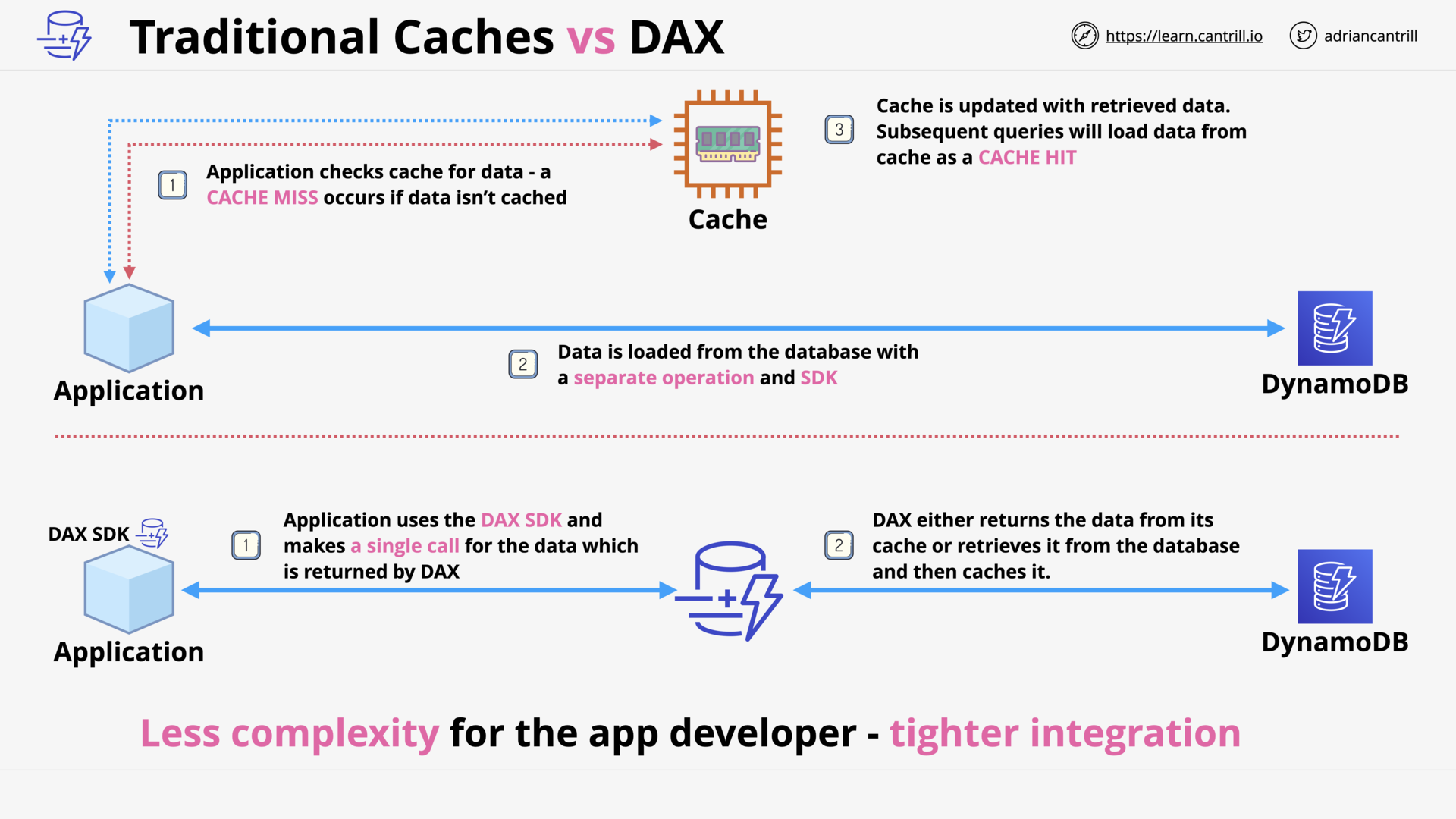 Traditional Caches vs DAX
Traditional Caches vs DAX
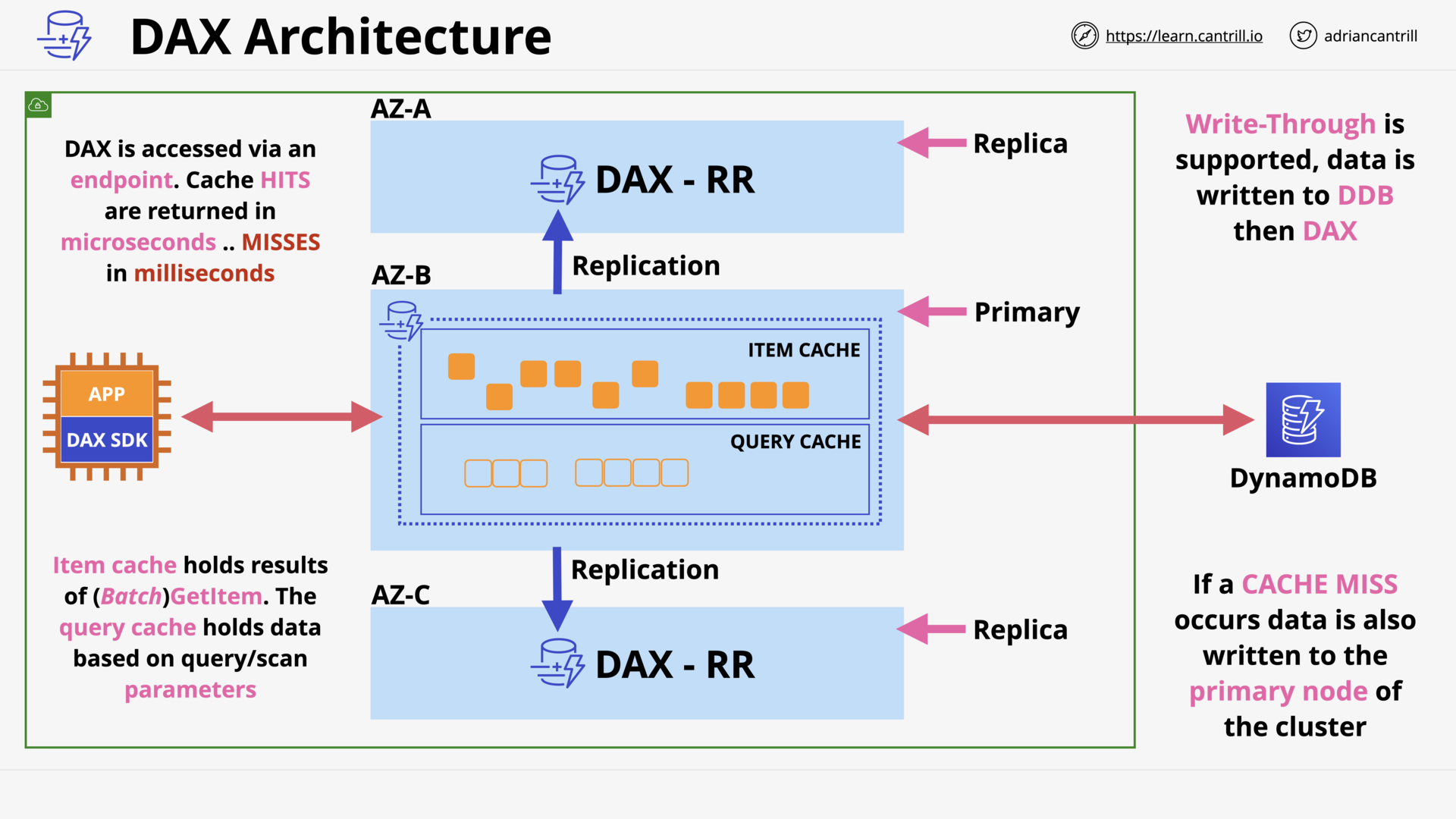 DAX - Architecture
DAX - Architecture
 DAX - Considerations
DAX - Considerations
DynamoDB - TTL (4:49)
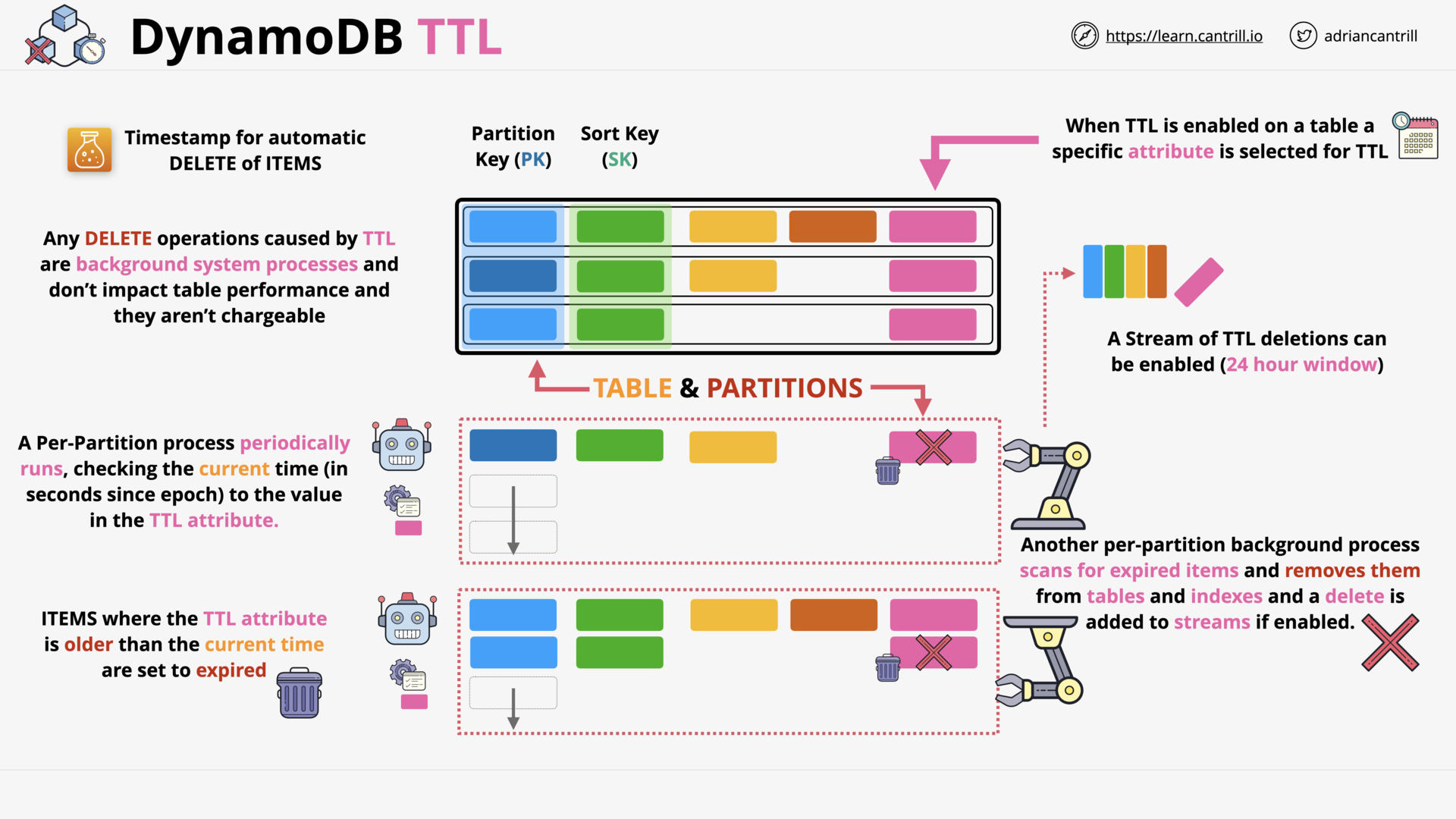 DynamoDB - TTL: Expiring items
DynamoDB - TTL: Expiring items
Amazon Athena (8:19)
 Amazon Athena: Interactive SQL - Serverless Query Service
Amazon Athena: Interactive SQL - Serverless Query Service
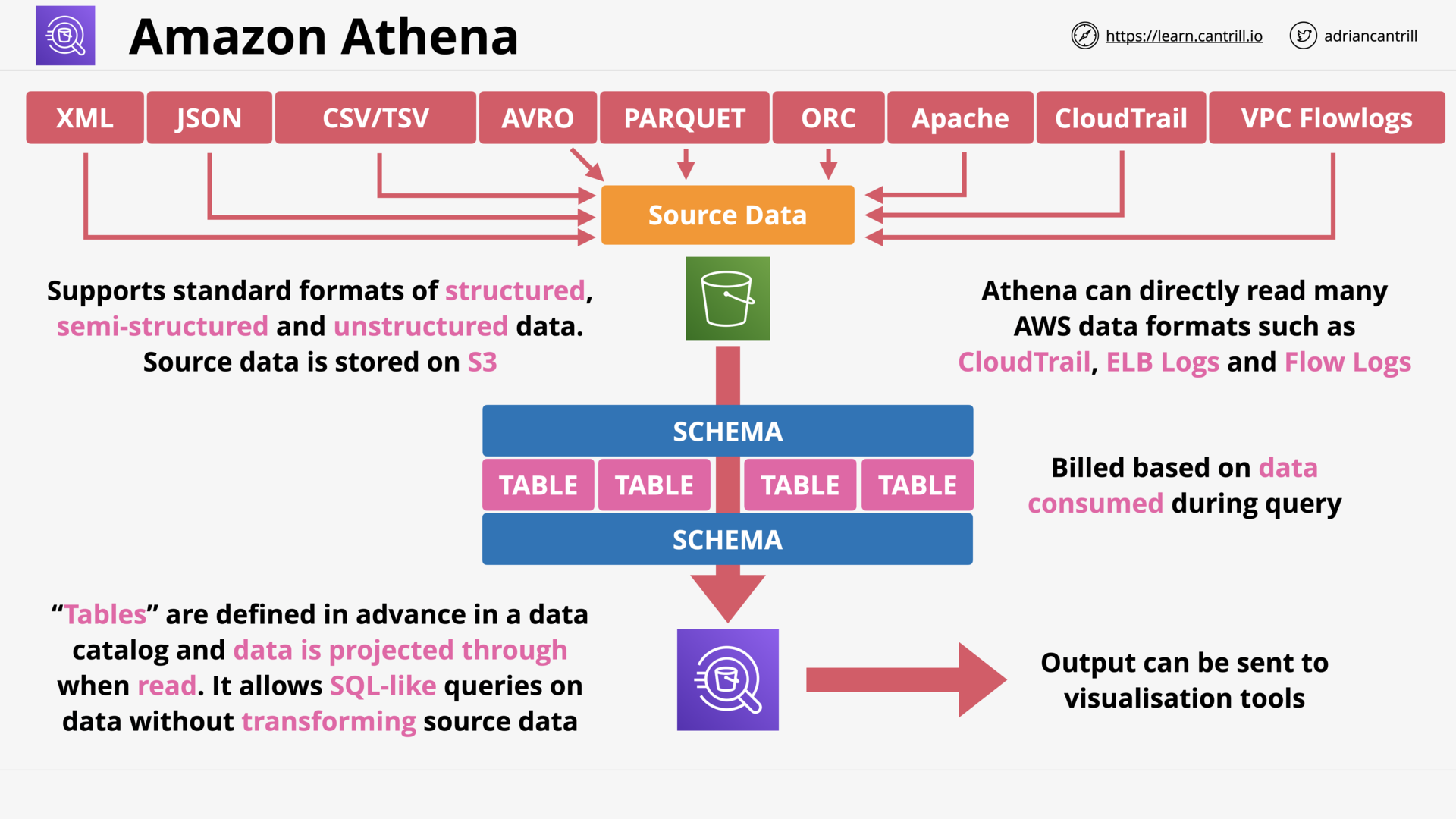 Amazon Athena - Architecture
Amazon Athena - Architecture
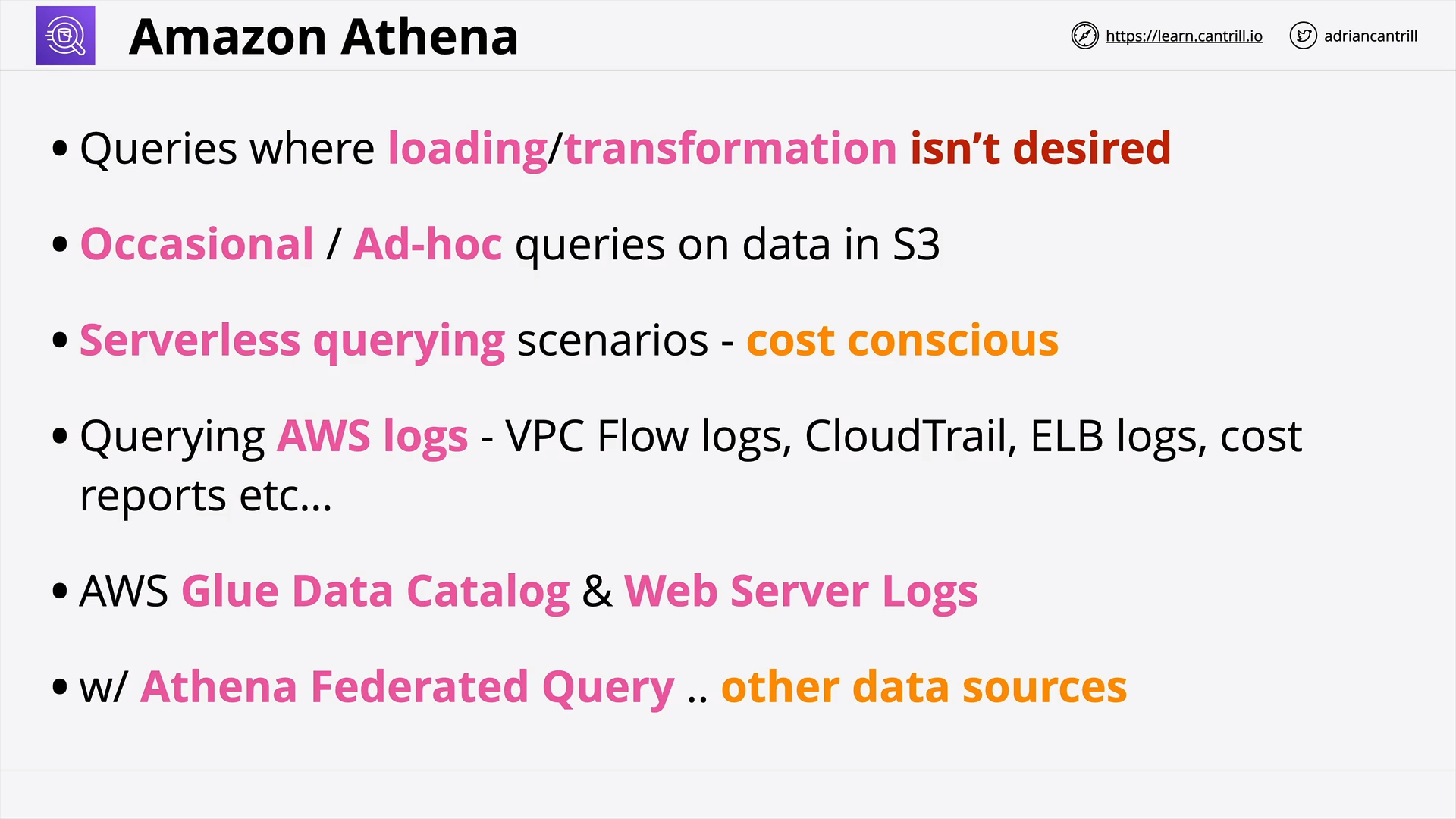 Amazon Athena: Queries without ETL
Amazon Athena: Queries without ETL
[DEMO] Athena Demo - PART1 (13:31)
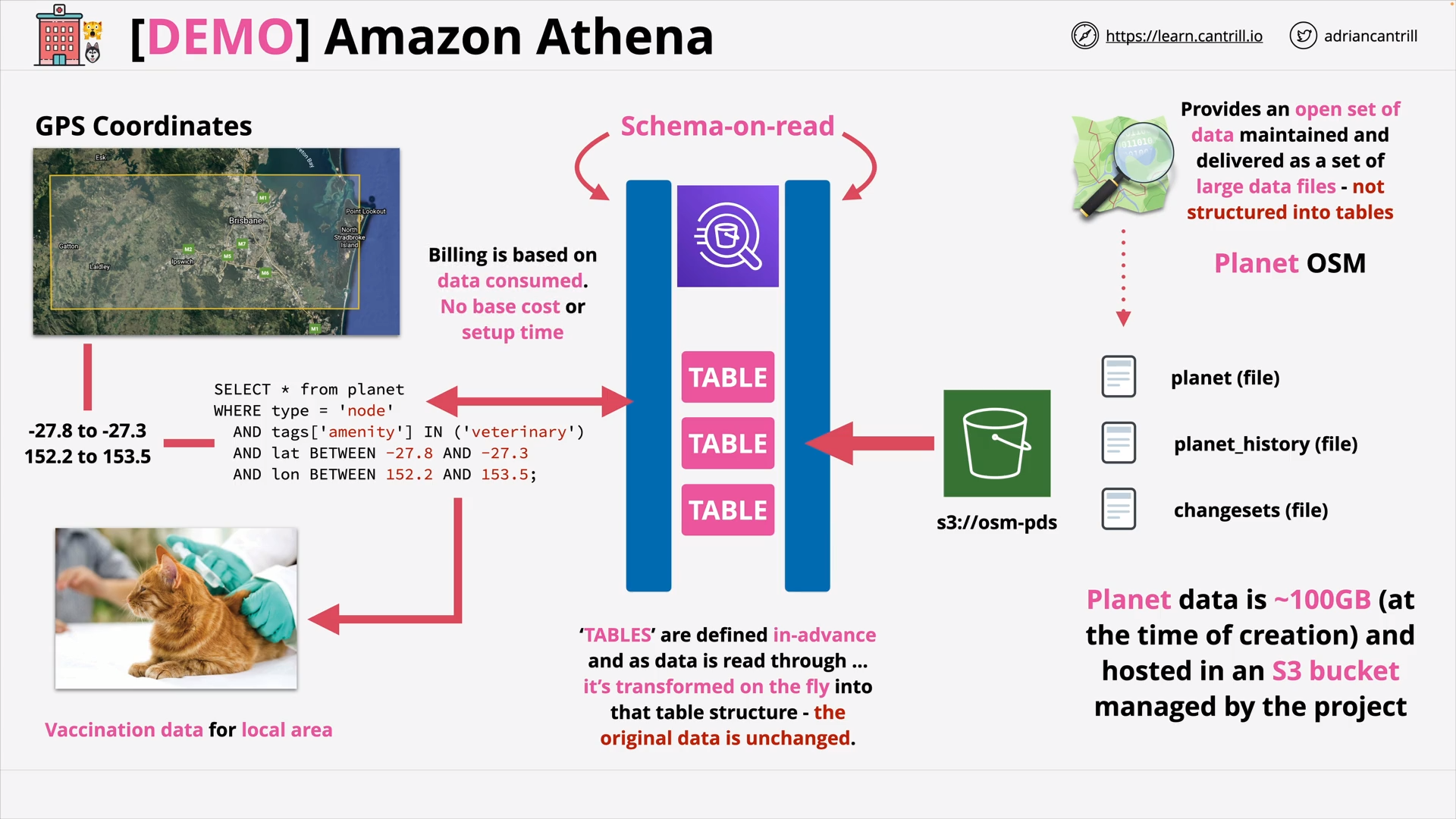 Athena Demo - Architecture
Athena Demo - Architecture
[DEMO] Athena Demo - PART2 (11:37)
Elasticache (12:51)
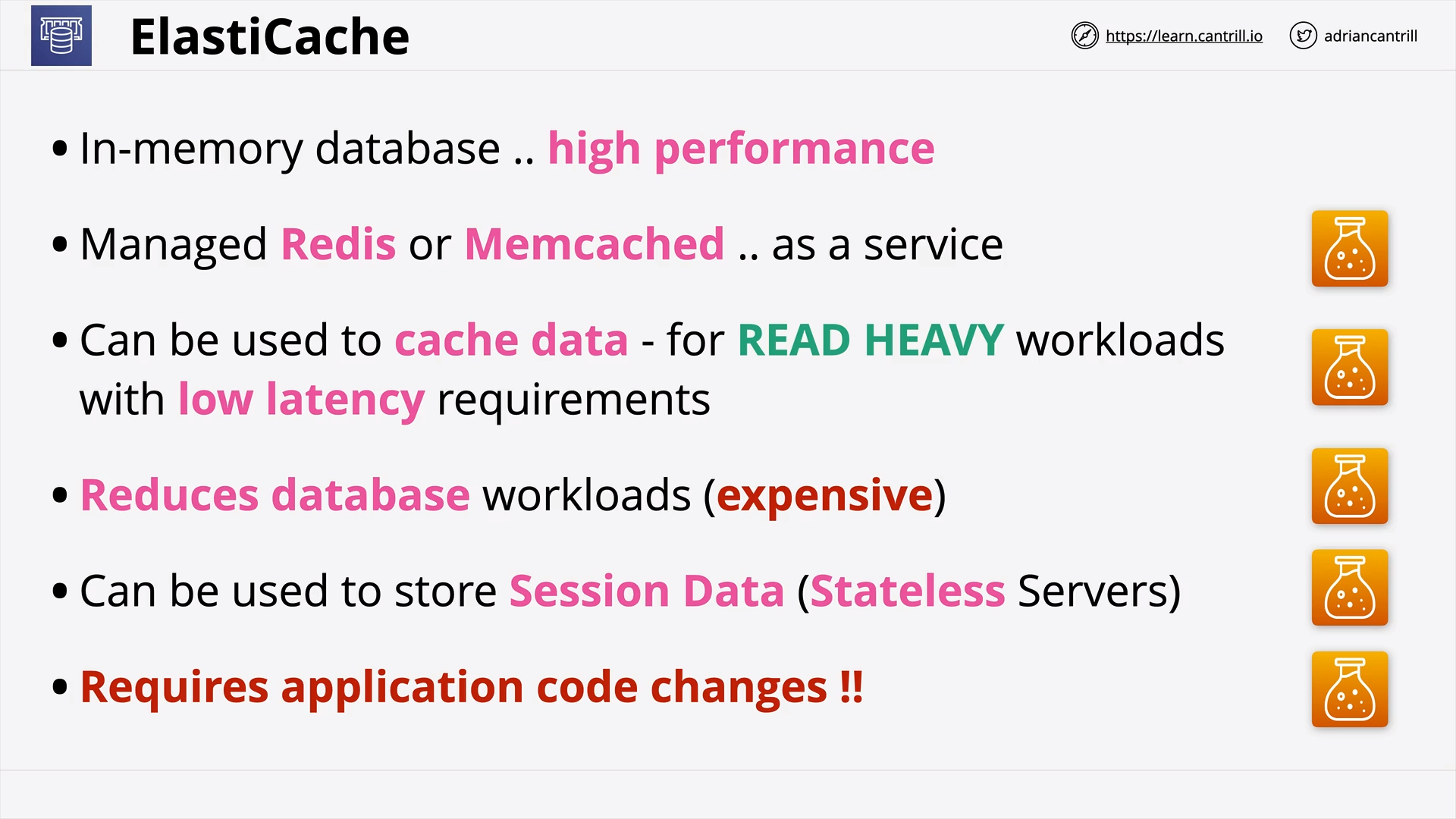 Elasticache - Managed in-memory database: Cache data & Reduce database load
Elasticache - Managed in-memory database: Cache data & Reduce database load
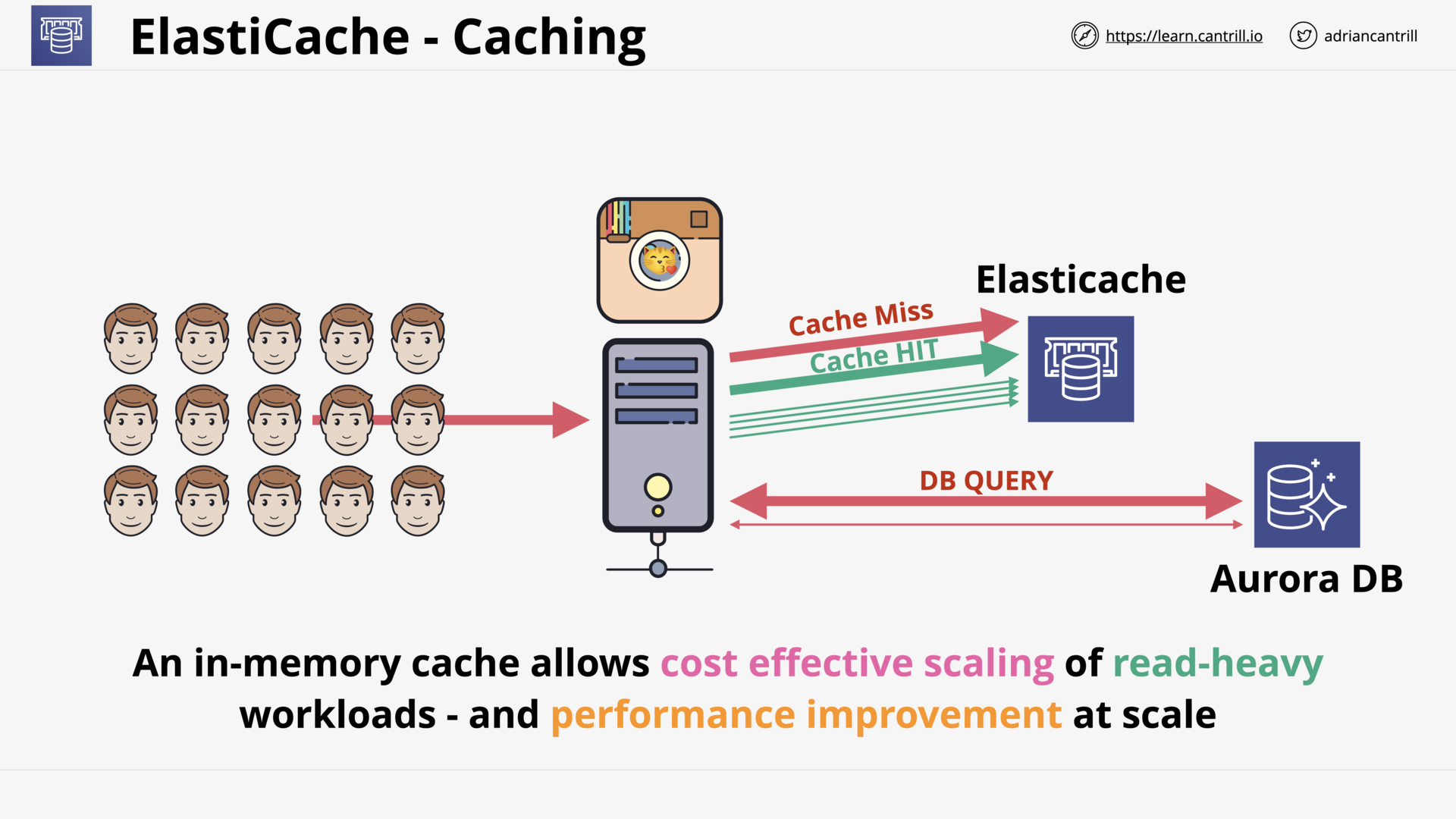 Elasticache - Caching
Elasticache - Caching
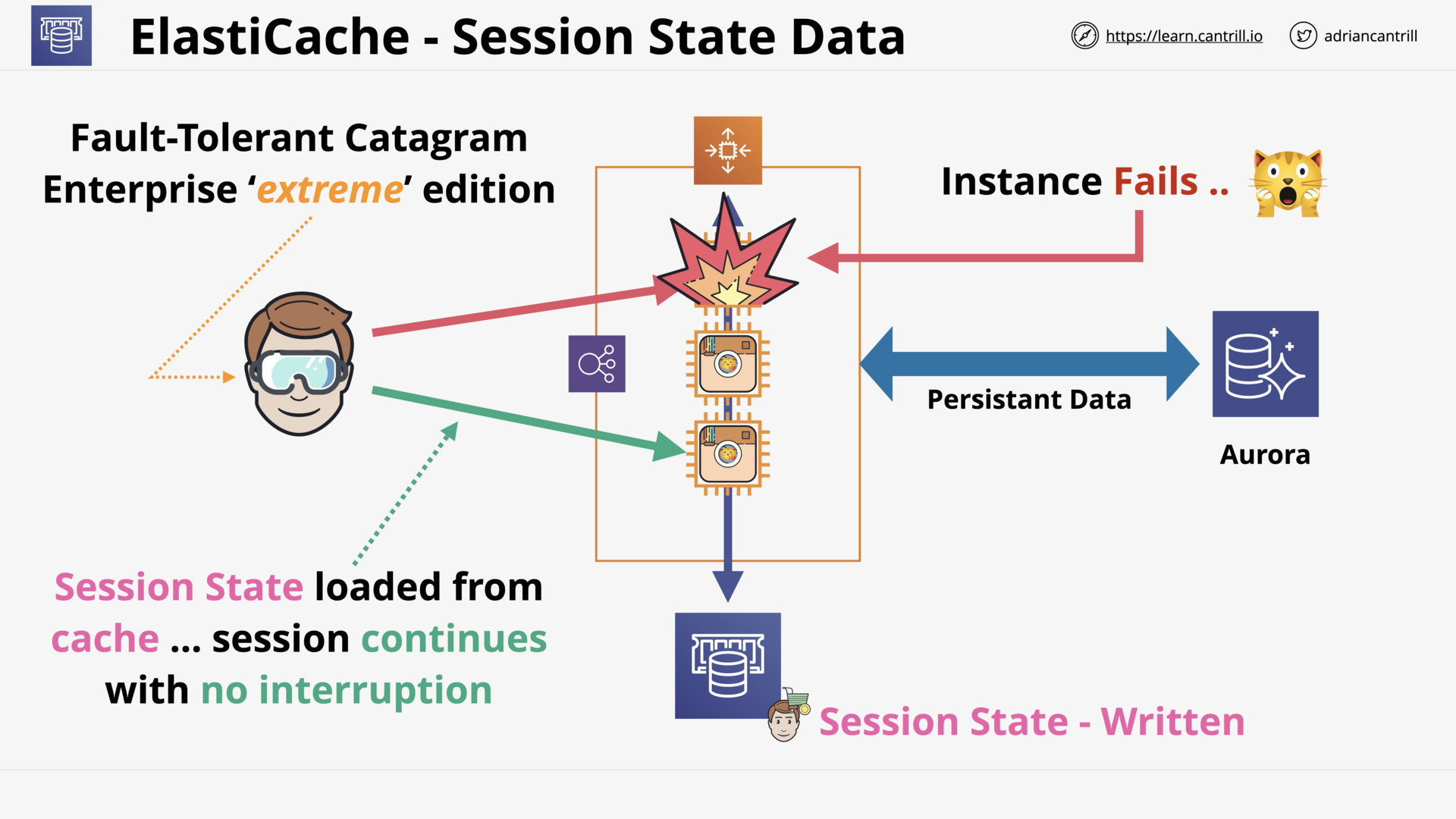 Elasticache - Session State Data
Elasticache - Session State Data
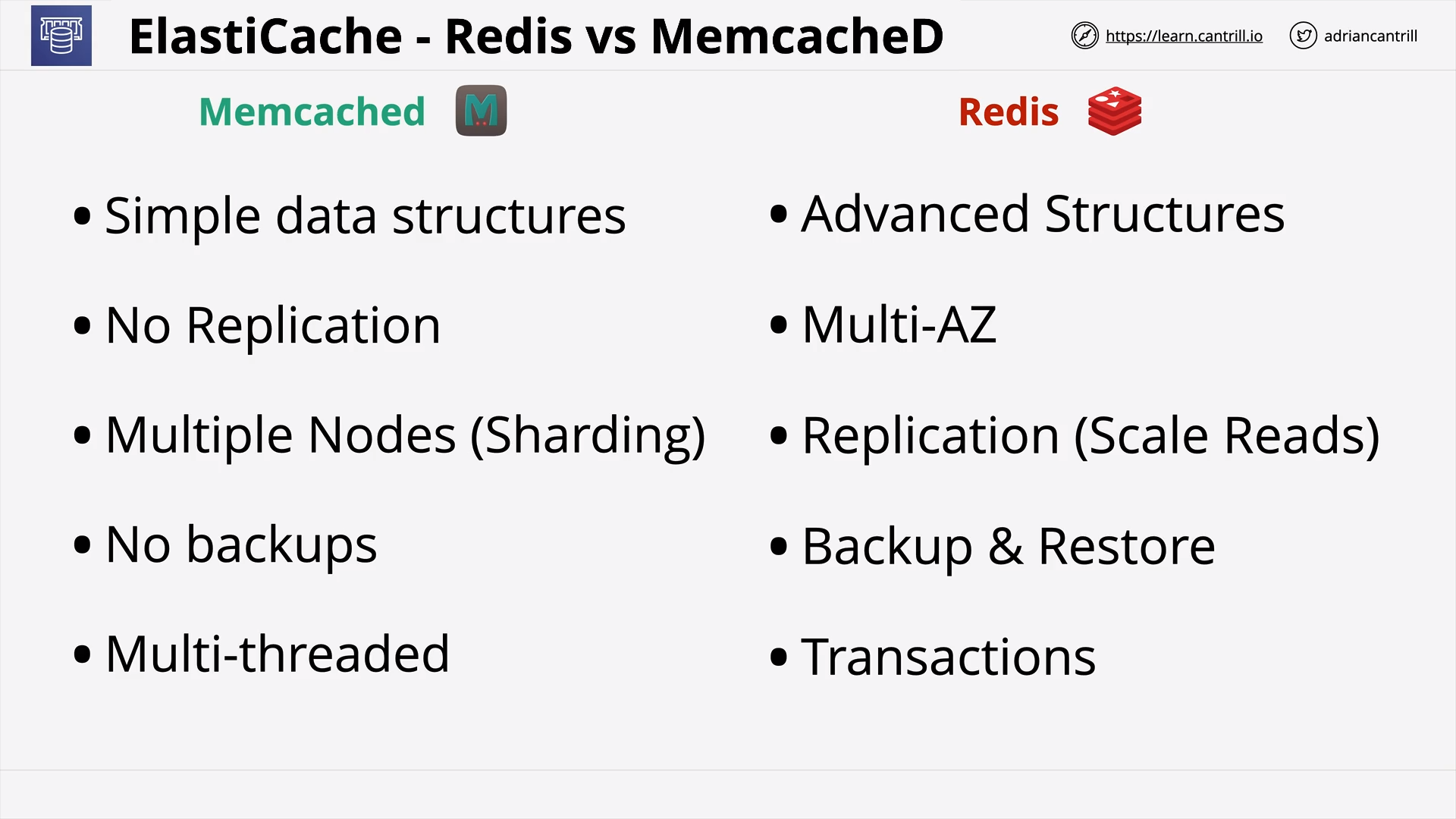 Elasticache - Redis vs MemcacheD
Elasticache - Redis vs MemcacheD
Redshift Architecture (11:32)
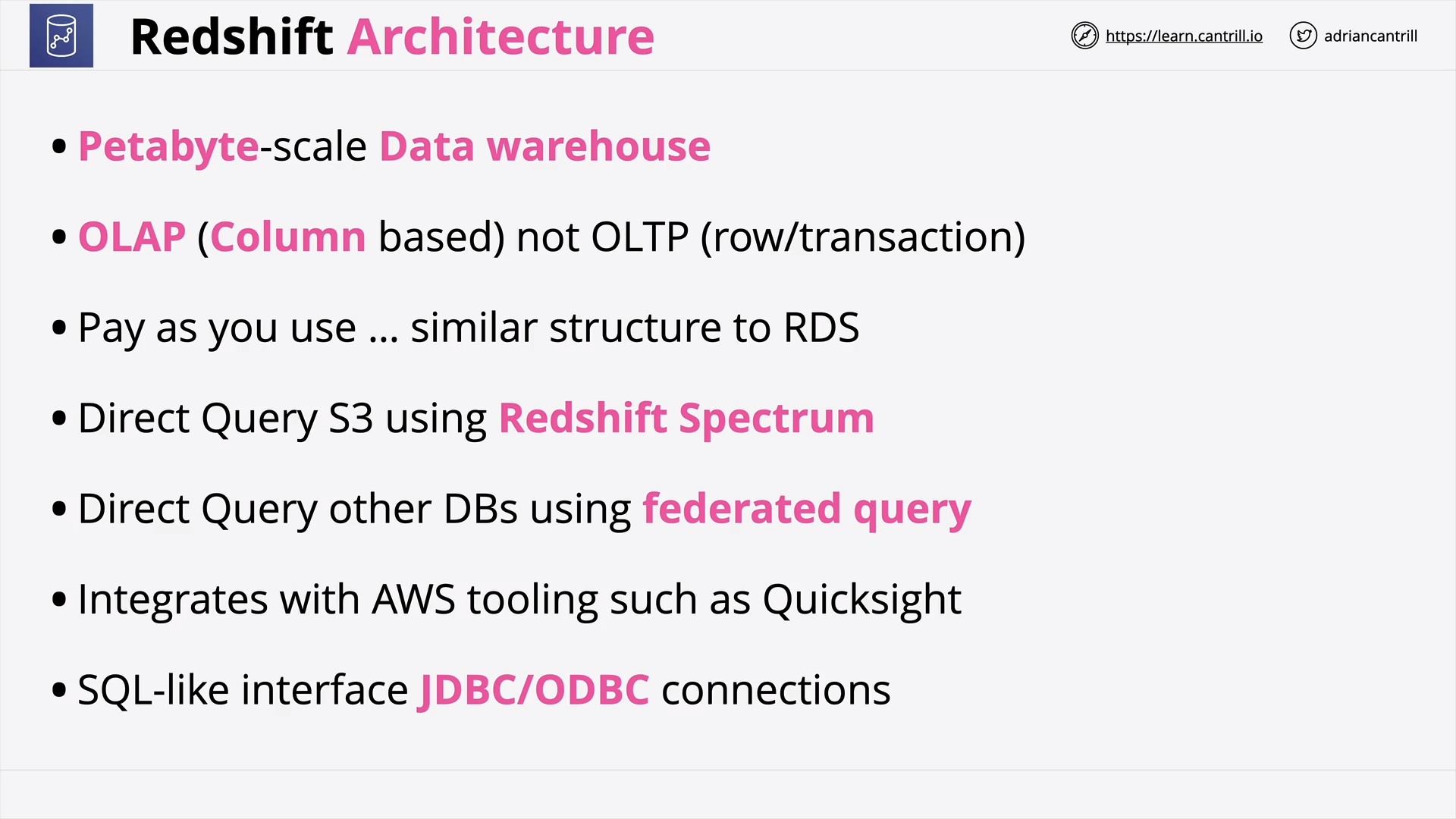 Redshift: Column based, Petabyte-scale Data warehouse (OLAP)
Redshift: Column based, Petabyte-scale Data warehouse (OLAP)
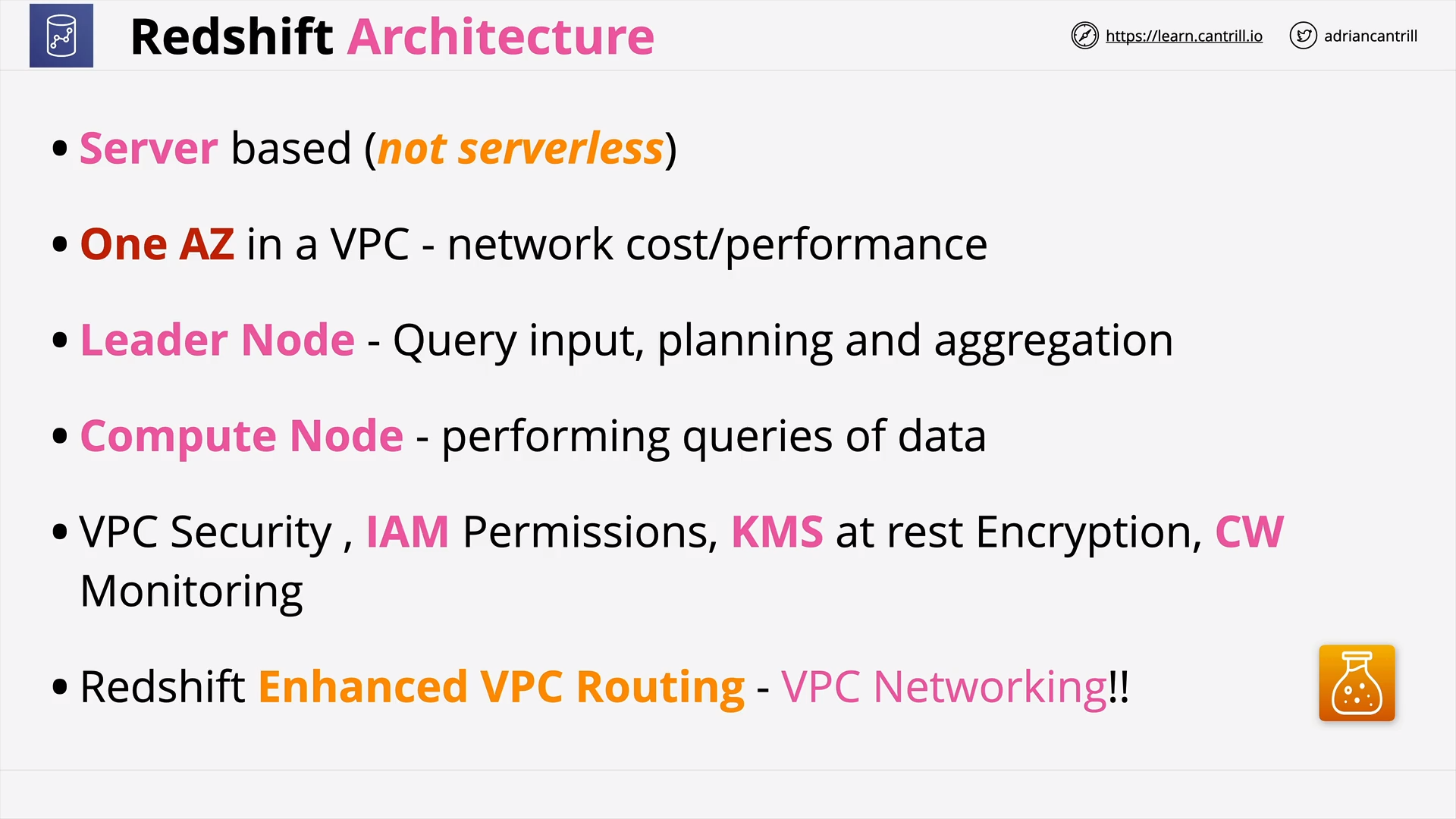 Redshift: Server based
Redshift: Server based
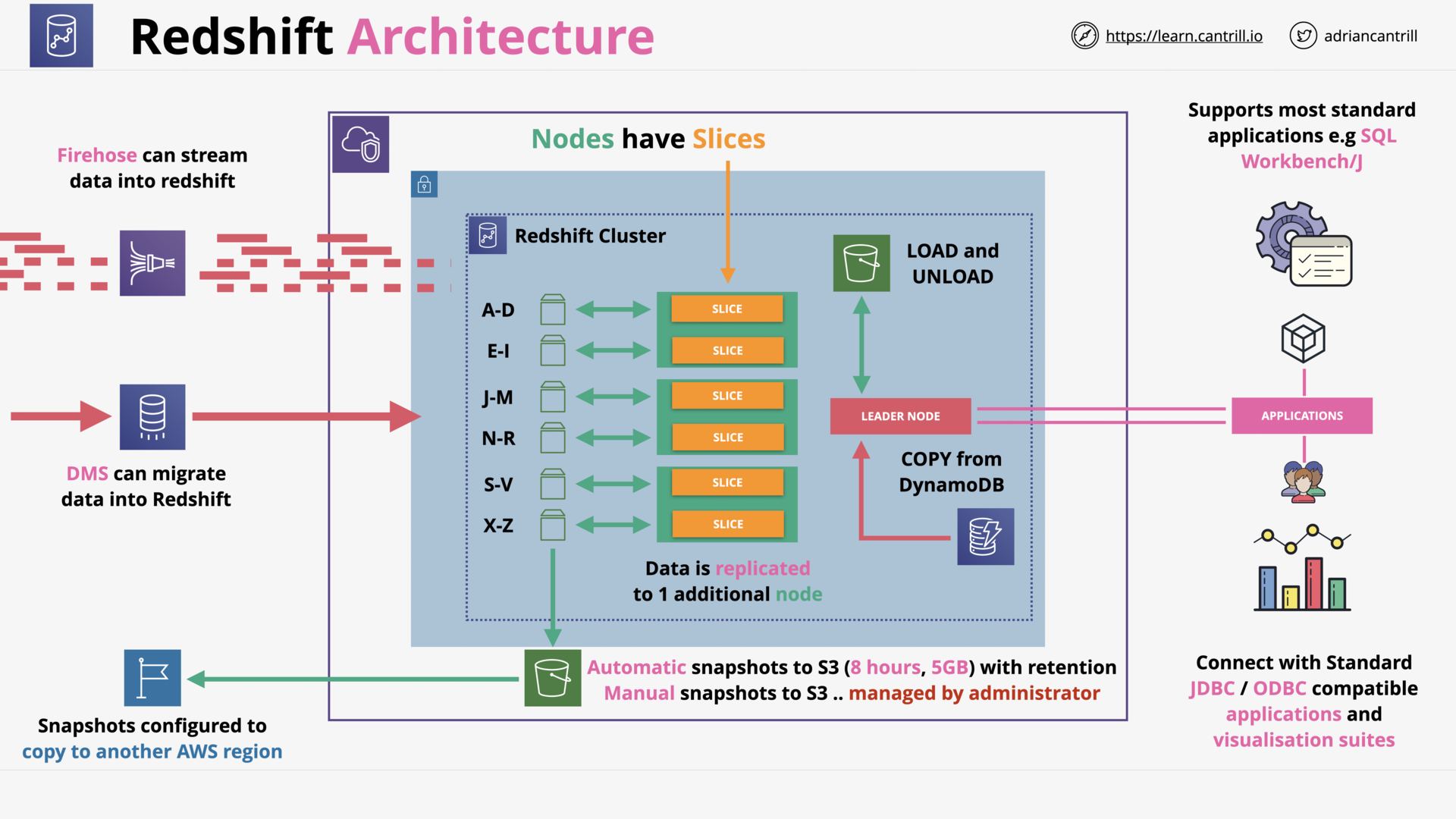 Redshift: Architecture
Redshift: Architecture
Redshift DR and Resilience (3:40)
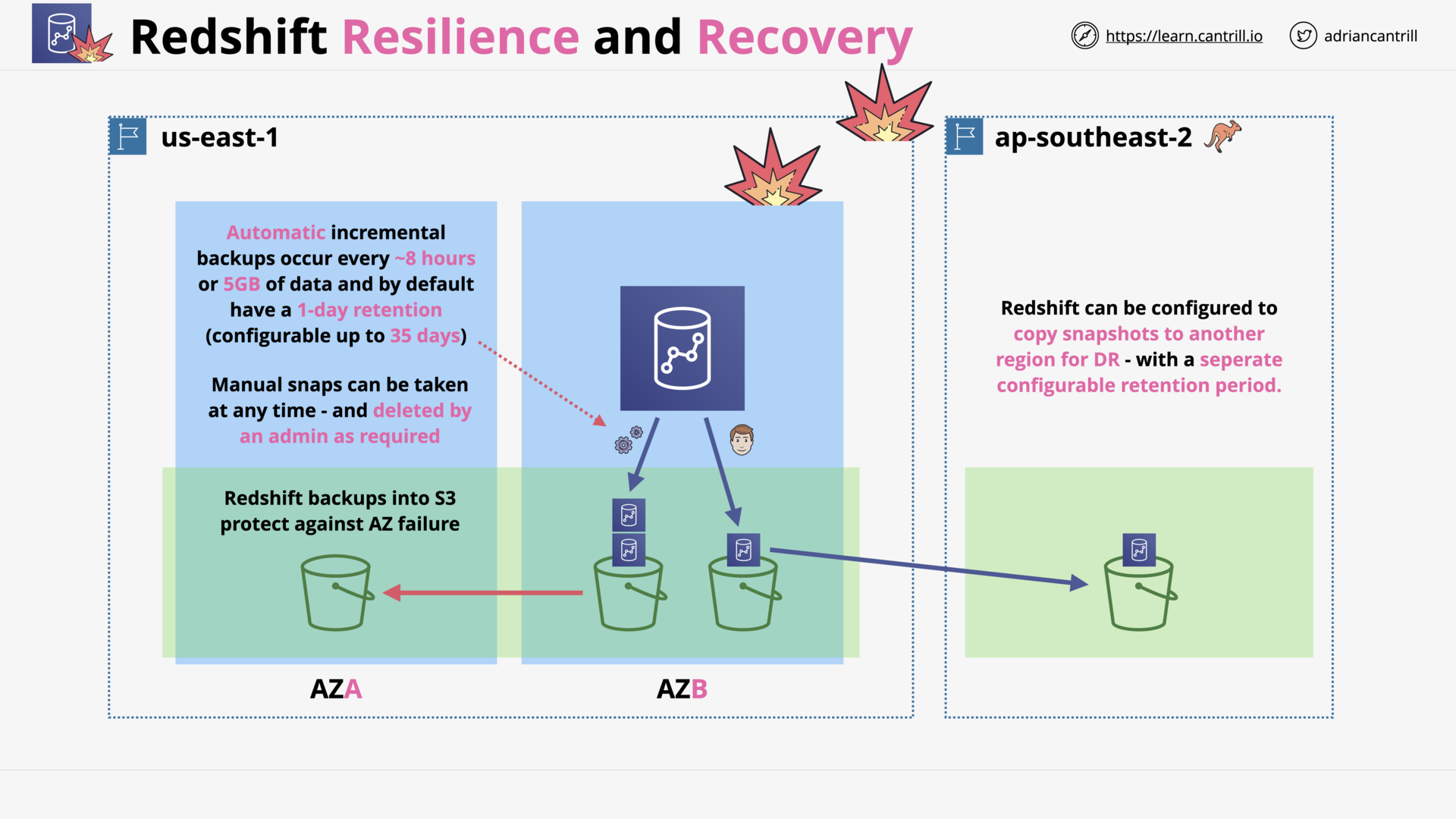 Redshift: DR & Resilience
Redshift: DR & Resilience
NoSQL Section Quiz
MACHINE LEARNING 101
Amazon Comprehend (7:28)
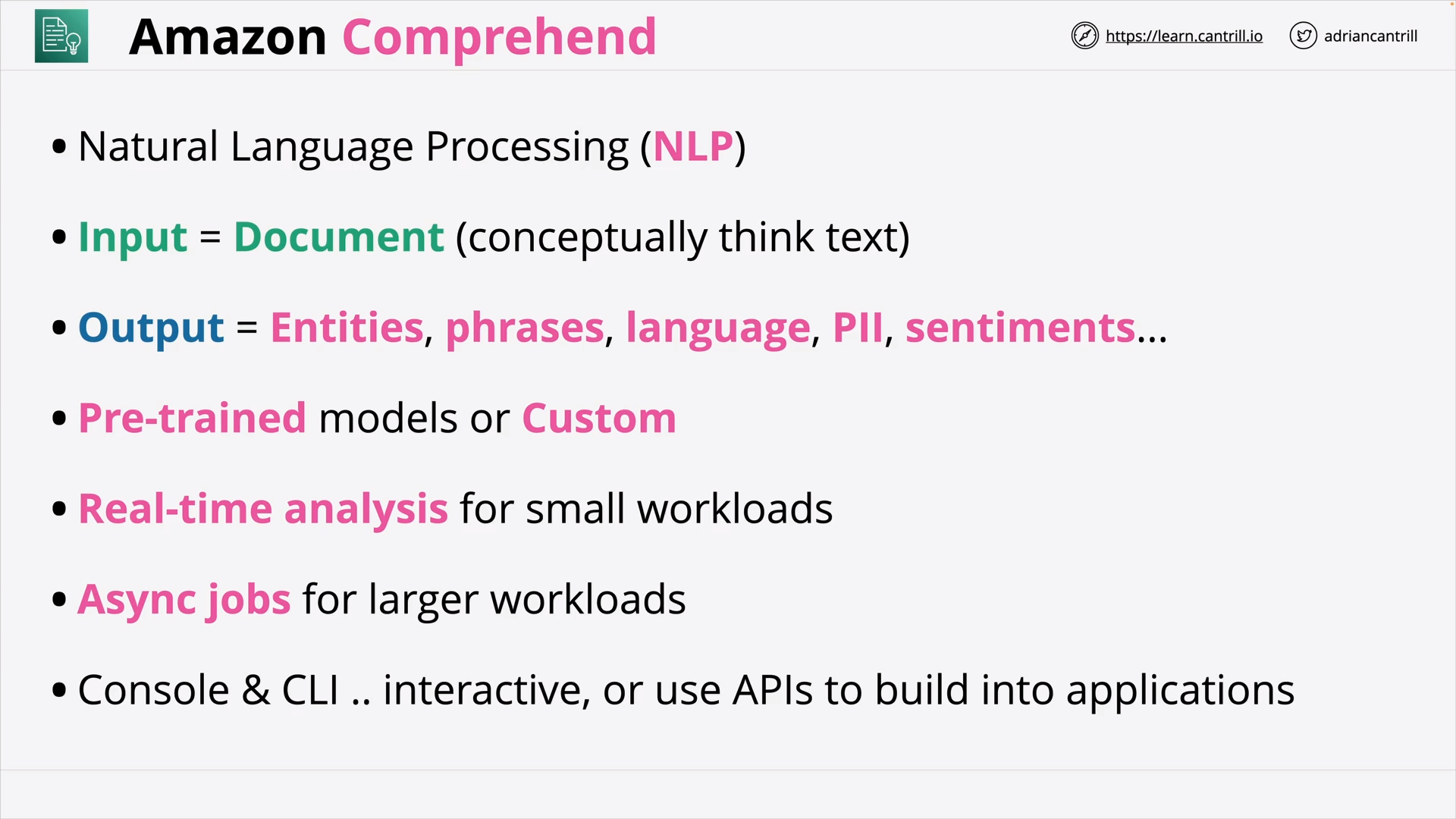 Amazon Comprehend: Discover insights and relationships in text
Amazon Comprehend: Discover insights and relationships in text
[what is amazon comprehend?](https://docs.aws.amazon.com/comprehend/latest/dg/what-is.html)
NLP for a document.
Amazon Kendra (5:00)
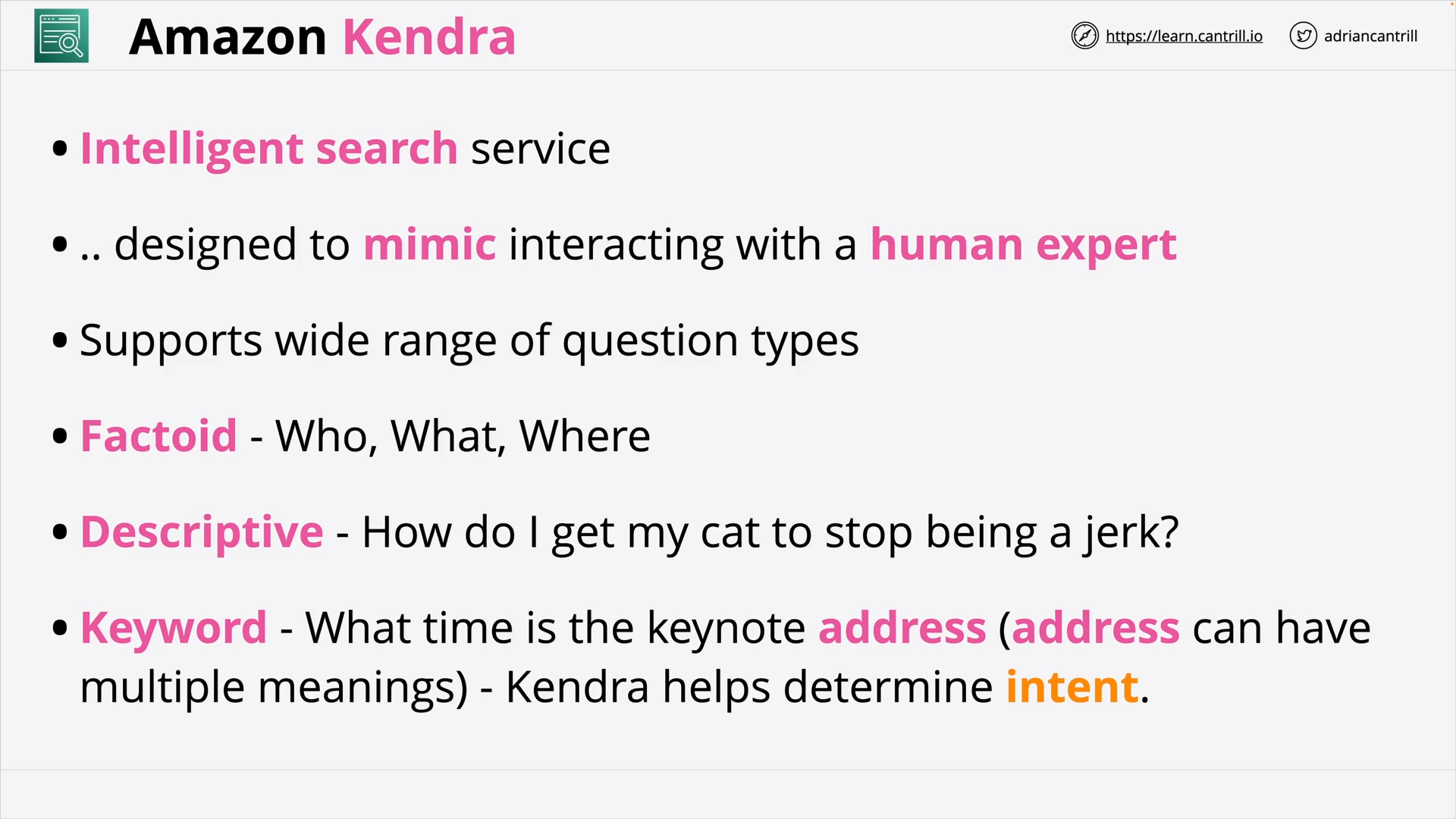 Amazon Kendra: Reinvent enterprise search with ML
Amazon Kendra: Reinvent enterprise search with ML
[what is kendra?](https://docs.aws.amazon.com/kendra/latest/dg/what-is-kendra.html)
NLP for a lot of documents.
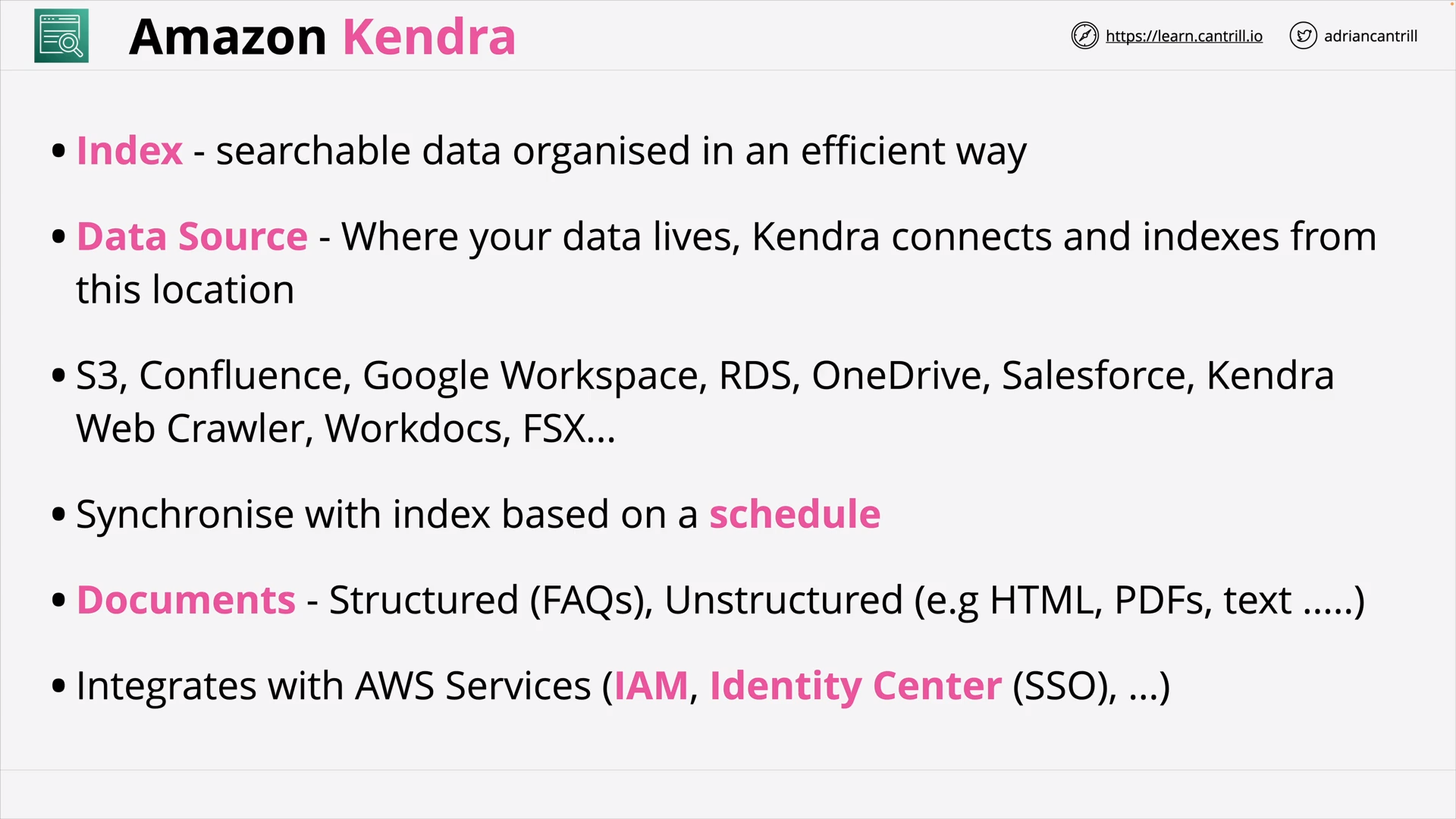 Amazon Kendra Concepts: Index - Documents - Data source (How Amazon Kendra works?)
Amazon Kendra Concepts: Index - Documents - Data source (How Amazon Kendra works?)
Amazon Lex (5:51)
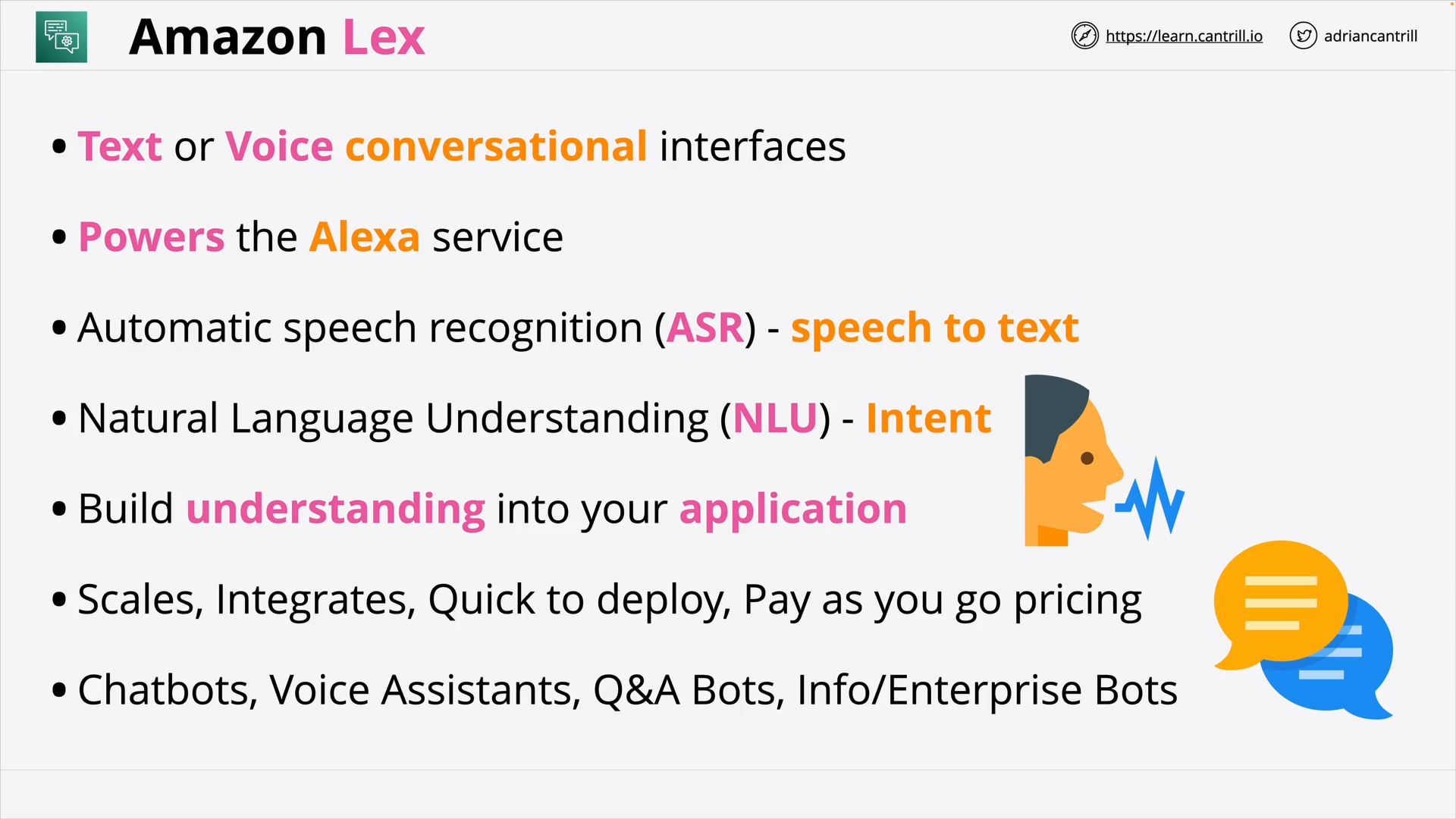 Amazon Lex: Build voice and text chatbots
Amazon Lex: Build voice and text chatbots
[what is amazon lex?](https://docs.aws.amazon.com/lexv2/latest/dg/what-is.html)
Bot with ML, e.g. Alexa
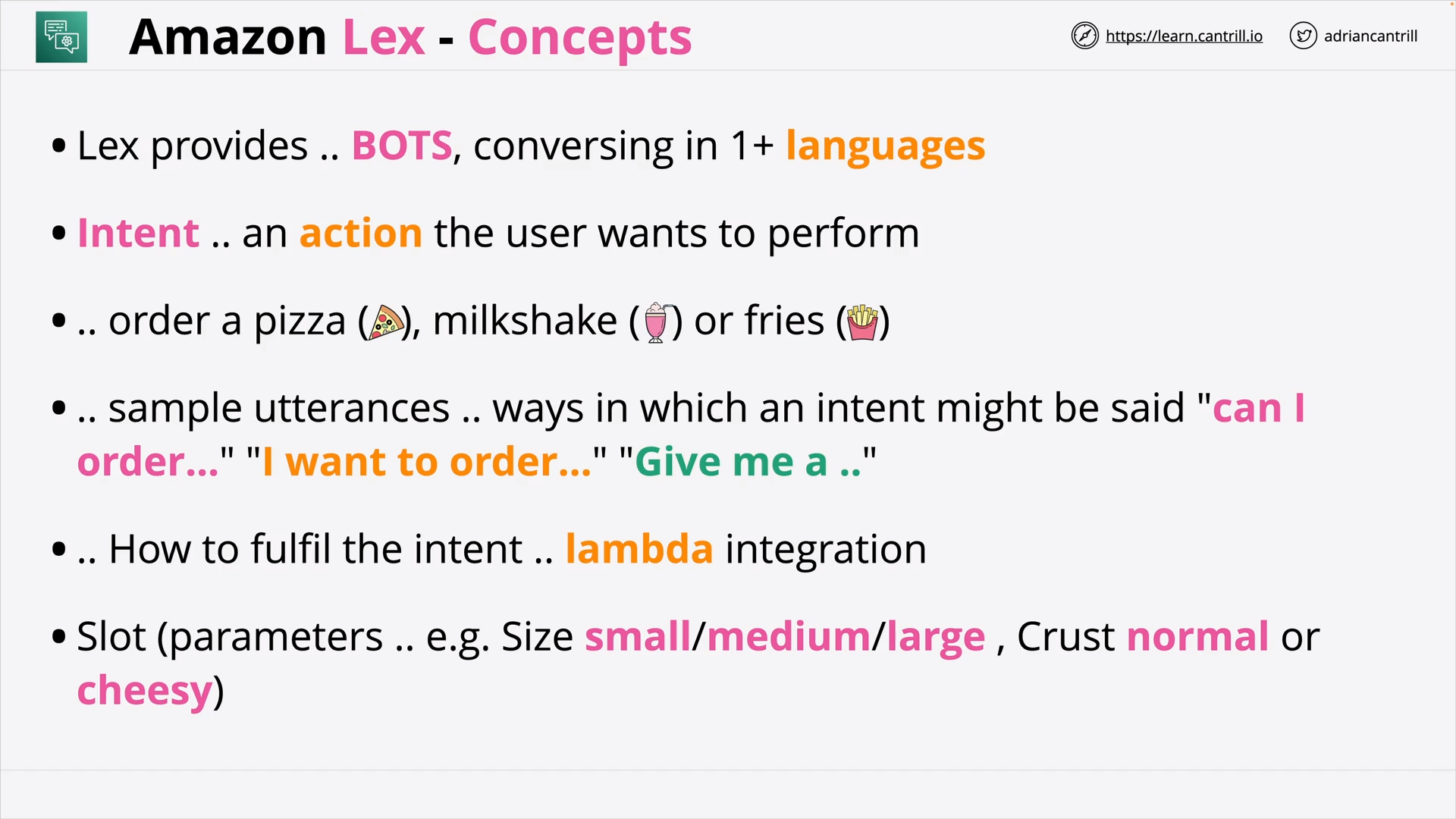 Amazon Lex Concepts: Bot - Language - Intent - Slot (How Lex Works?)
Amazon Lex Concepts: Bot - Language - Intent - Slot (How Lex Works?)
Amazon Polly (4:04)
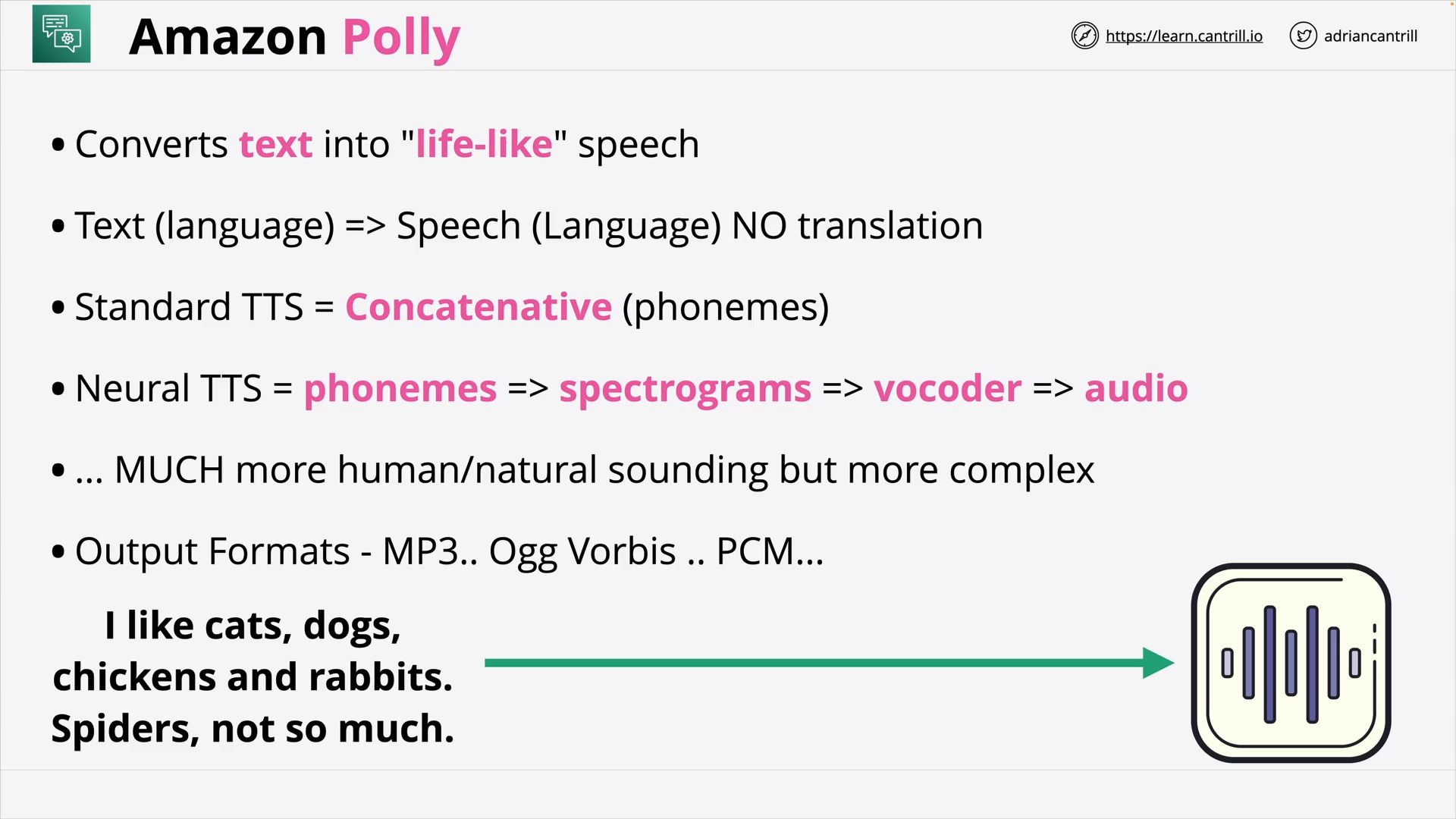 Amazon Polly: Turn text into life-like speech
Amazon Polly: Turn text into life-like speech
[what is amazon polly?](https://docs.aws.amazon.com/polly/latest/dg/what-is.html)
TTS with ML.
 Amazon Polly: Speech Synthesis Markup Language (SSML)
Amazon Polly: Speech Synthesis Markup Language (SSML)
[polly - demo](https://ai-service-demos.go-aws.com/polly)
Amazon Rekognition (4:18)
 Amazon Rekognition: Analyze image and video
Amazon Rekognition: Analyze image and video
[what is rekognition?](https://docs.aws.amazon.com/rekognition/latest/dg/what-is.html)
Image & video processing with ML
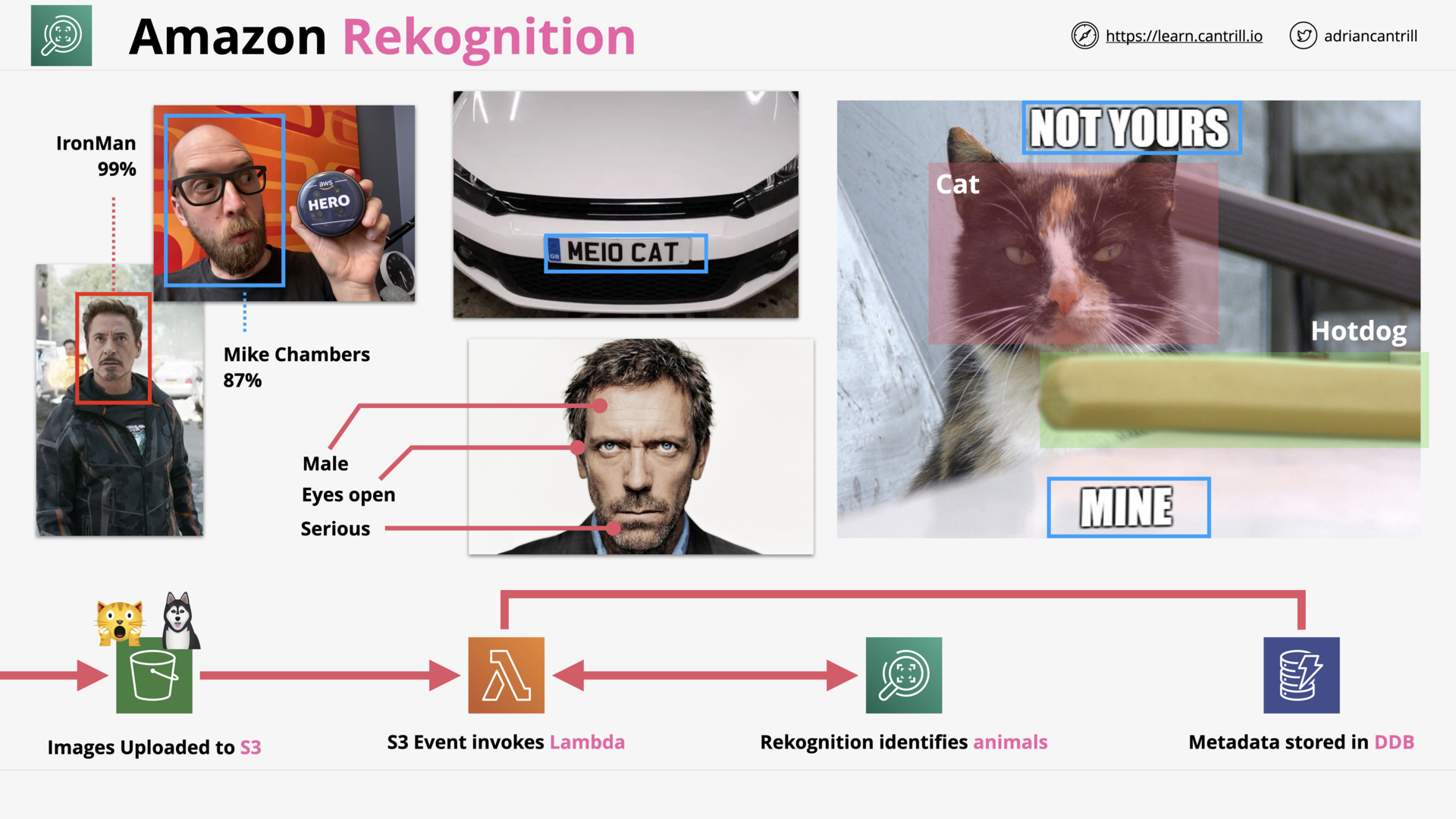 Amazon Rekognition: How is work?
Amazon Rekognition: How is work?
Amazon Textract (8:42)
 Amazon Textract: Extract text and data from documents
Amazon Textract: Extract text and data from documents
[what is amazon textract?](https://docs.aws.amazon.com/textract/latest/dg/what-is.html)
OCR with ML and Analysis
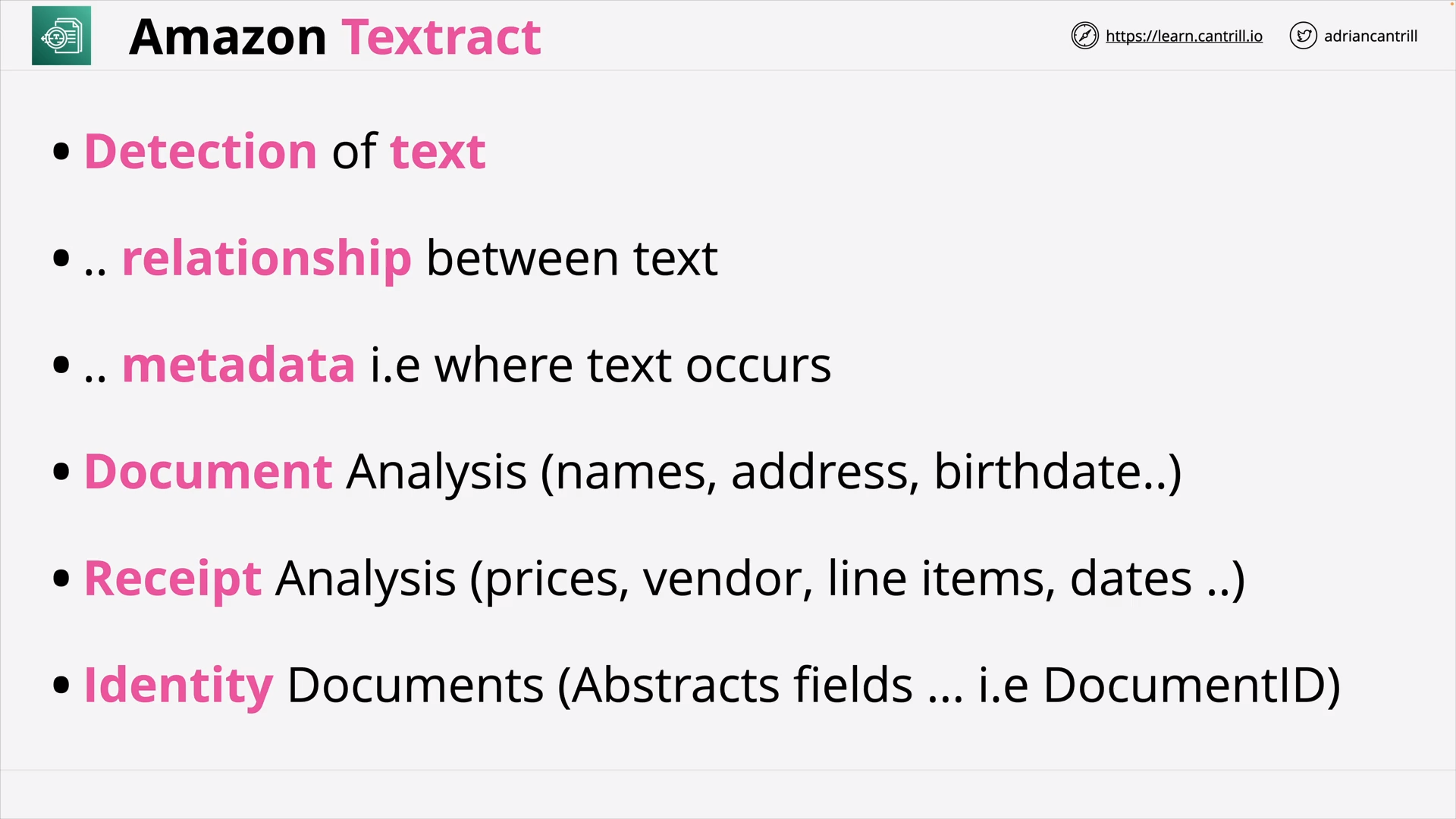 Amazon Textract: Detect and analysis
Amazon Textract: Detect and analysis
Amazon Transcribe (4:55)
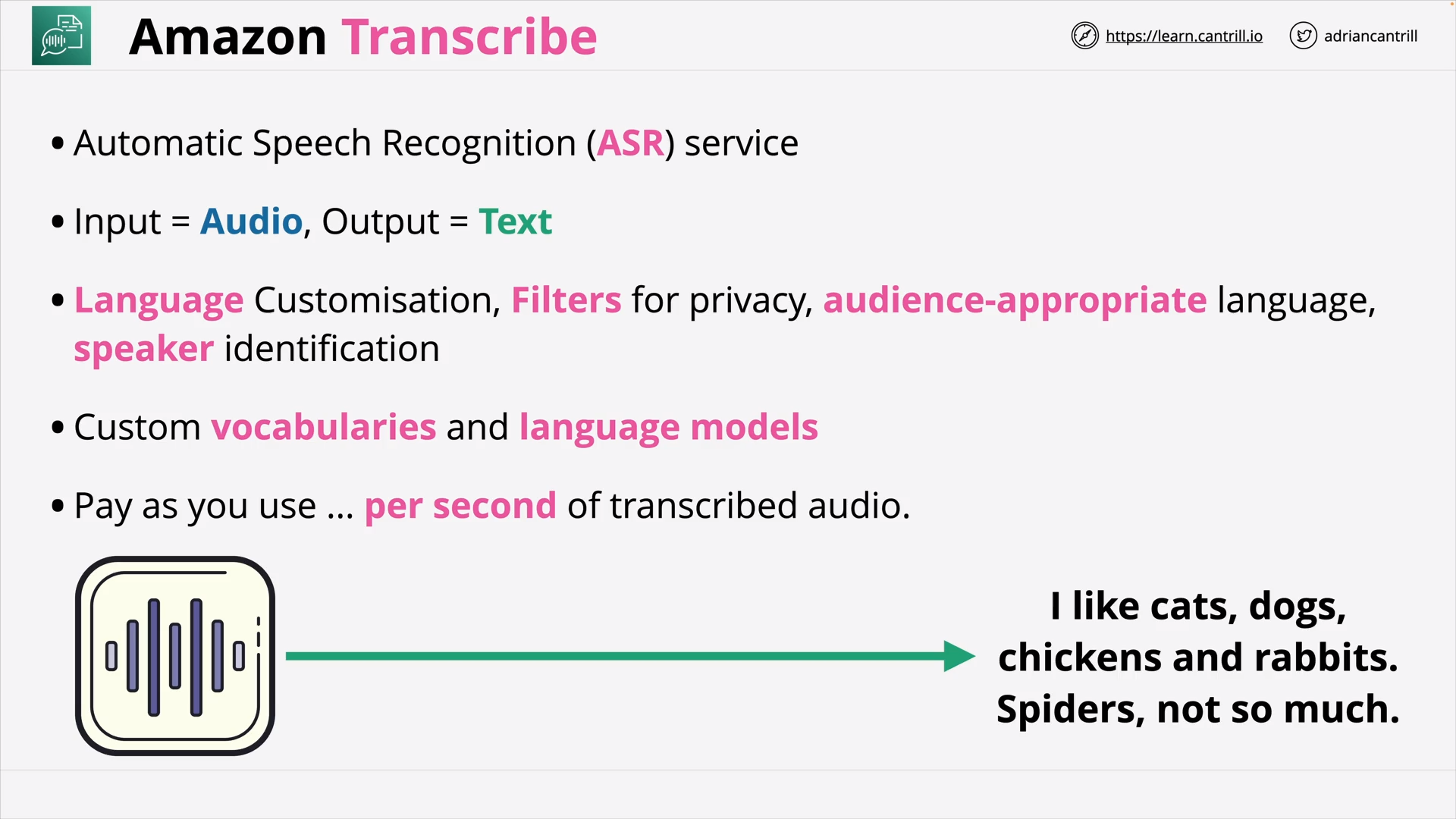 Amazon Transcribe: Automatic speech recognition
Amazon Transcribe: Automatic speech recognition
[what is amazon transcribe?](https://docs.aws.amazon.com/transcribe/latest/dg/what-is.html)
Speech Recognition with ML.
 Amazon Transcribe - Use Cases
Amazon Transcribe - Use Cases
Amazon Translate (4:32)
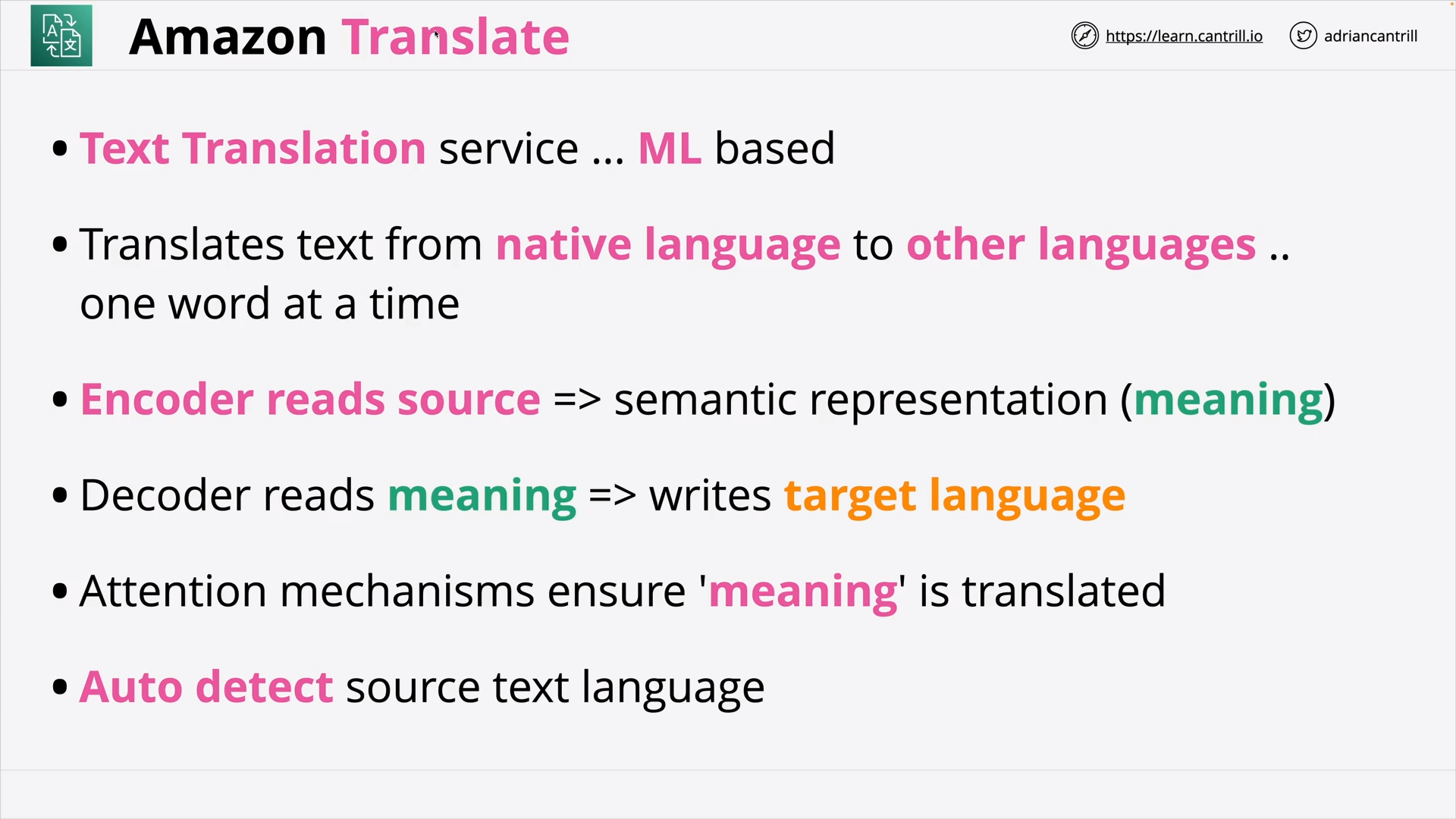 Amazon Translate: Natural and fluent language translation
Amazon Translate: Natural and fluent language translation
[what is amazon translate?](https://docs.aws.amazon.com/translate/latest/dg/what-is.html)
Text translate with ML.
 Amazon Translate - Use Cases
Amazon Translate - Use Cases
Amazon Forecast 101 (4:04)
 Amazon Forecast: Increase forecast accuracy using machine learning
Amazon Forecast: Increase forecast accuracy using machine learning
[what is amazon forecast?](https://docs.aws.amazon.com/forecast/latest/dg/what-is-forecast.html)
Time-series forecasts that uses statistical and machine learning algorithms.
Amazon Fraud Detector (3:34)
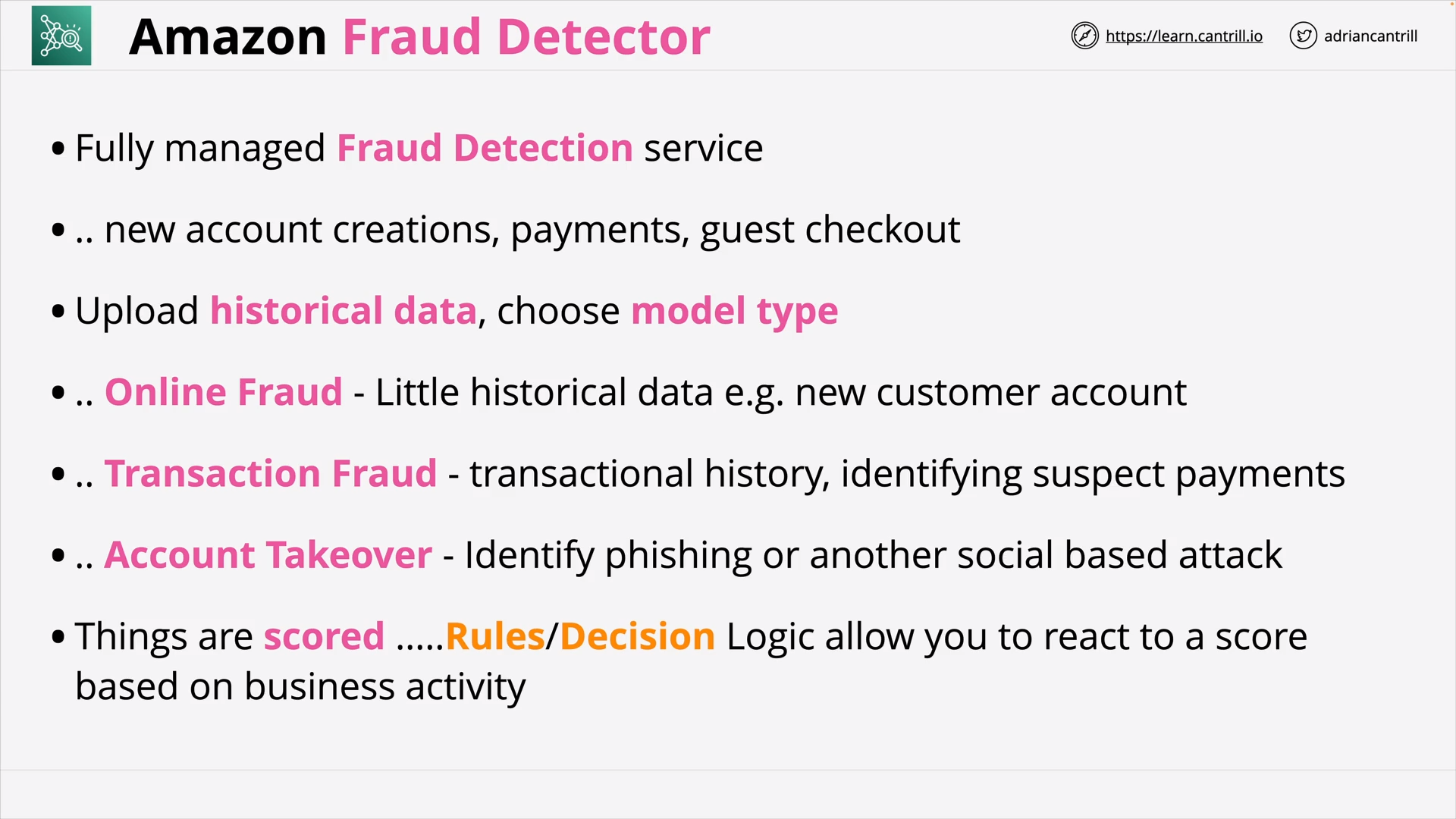 Amazon Fraud Detector: Detect more online fraud faster
Amazon Fraud Detector: Detect more online fraud faster
[what is amazon fraud detector?](https://docs.aws.amazon.com/frauddetector/latest/ug/what-is-frauddetector.html)
Fraud Detector with ML.
Amazon SageMaker (5:39)
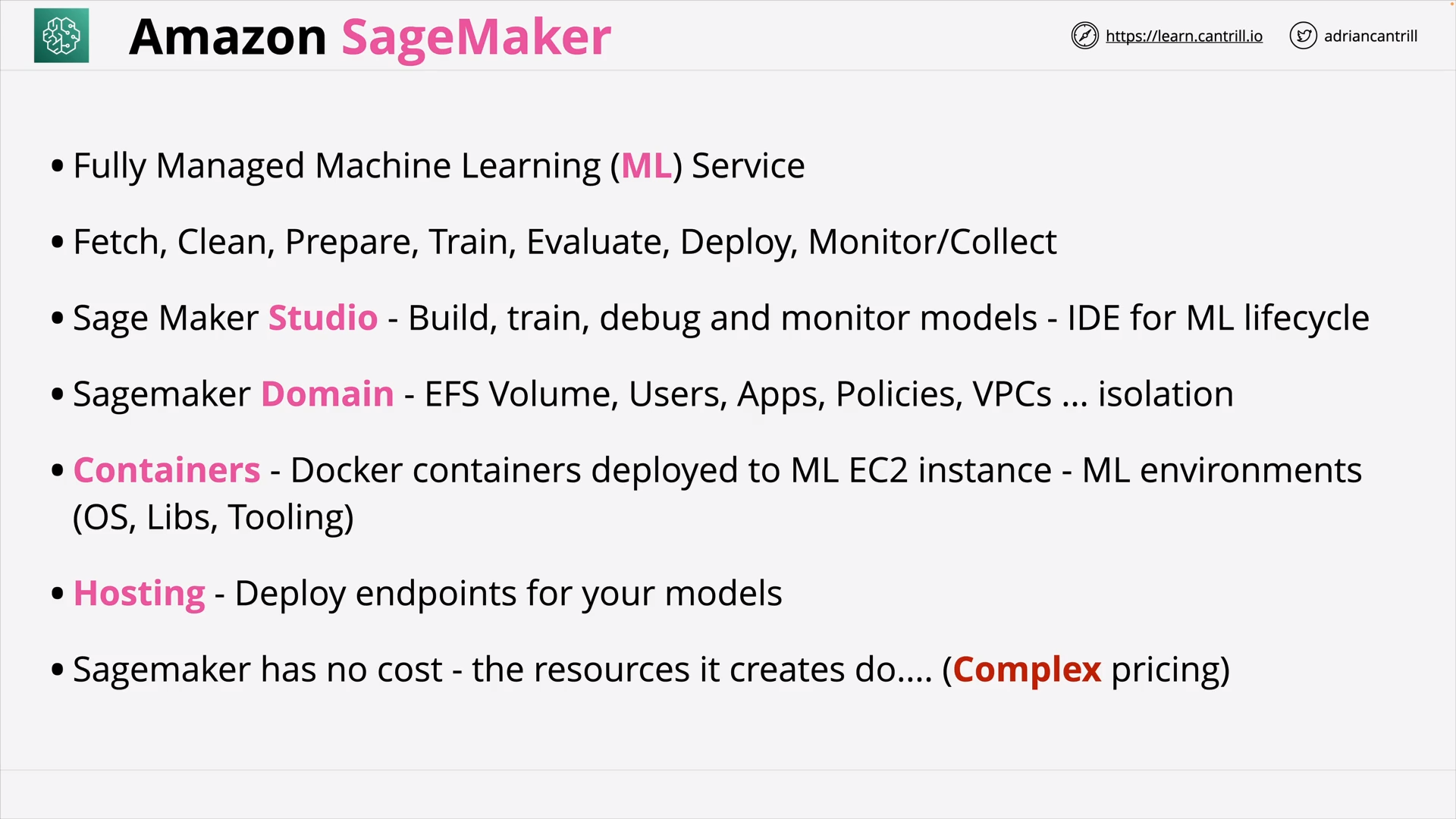 Amazon SageMaker: Build, train, and deploy machine learning models at scale
Amazon SageMaker: Build, train, and deploy machine learning models at scale
[what is amazon sagemaker?](https://docs.aws.amazon.com/sagemaker/latest/dg/whatis.html)
Fully managed machine learning service:
- infrastructure, tools, and workflows…
for building, training, deploying machine learning models.
OTHER SERVICES & FEATURES
AWS Local Zones (8:52)
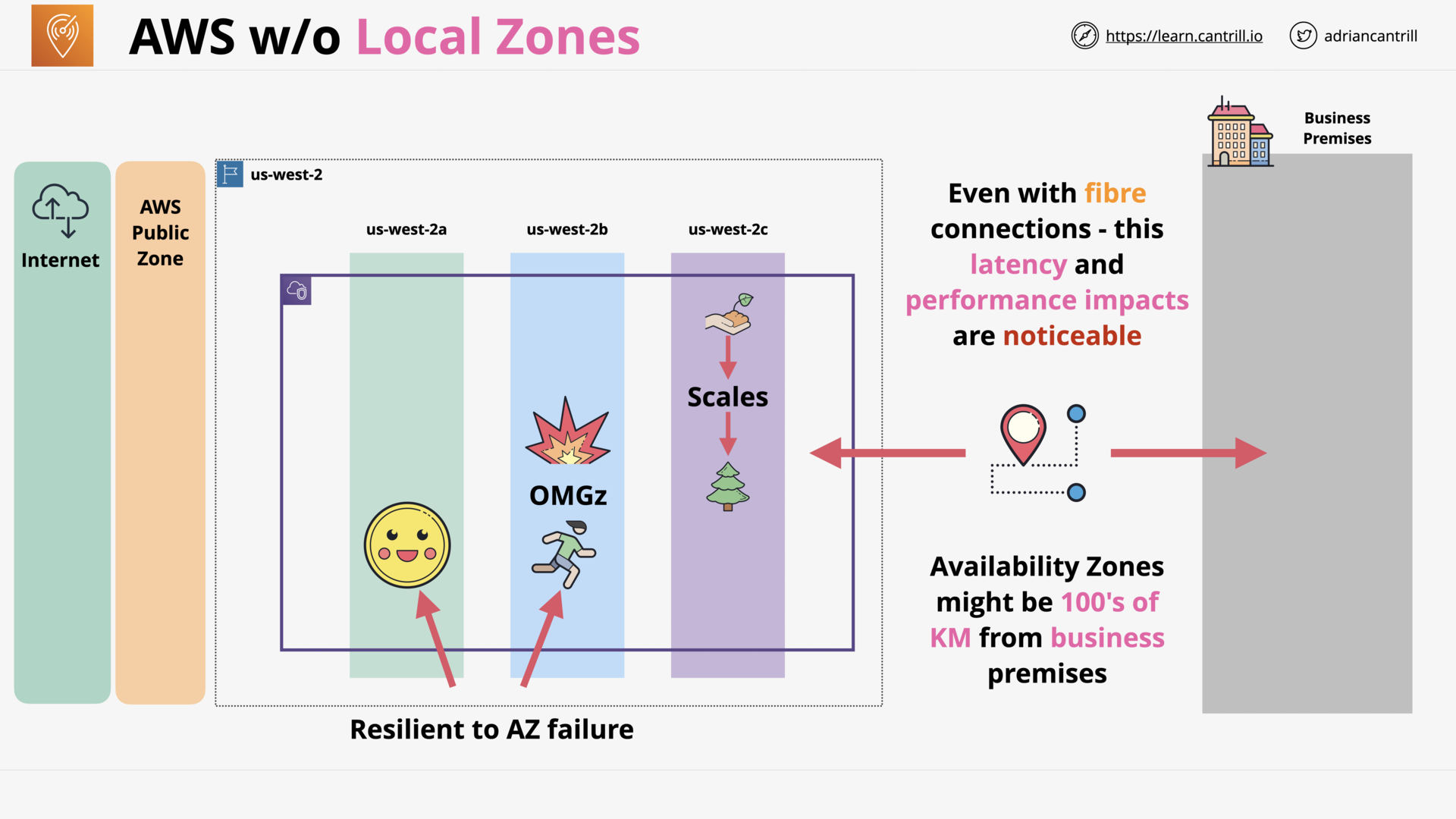 AWS without Local Zones
AWS without Local Zones
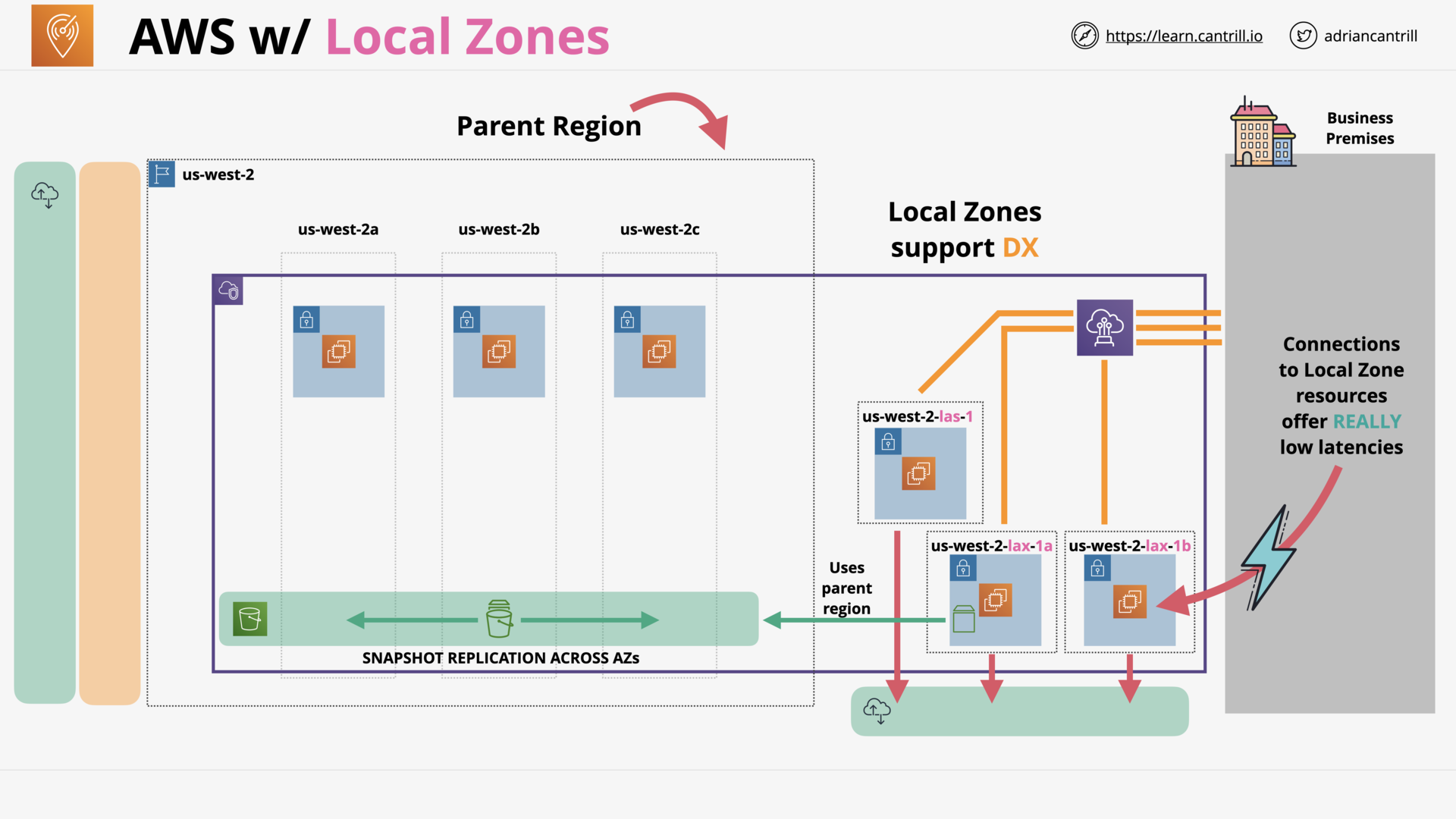 AWS with Local Zones
AWS with Local Zones
 AWS Local Zones
AWS Local Zones
EXAM
General AWS Exam Technique - 3 Phases Approach (8:56)
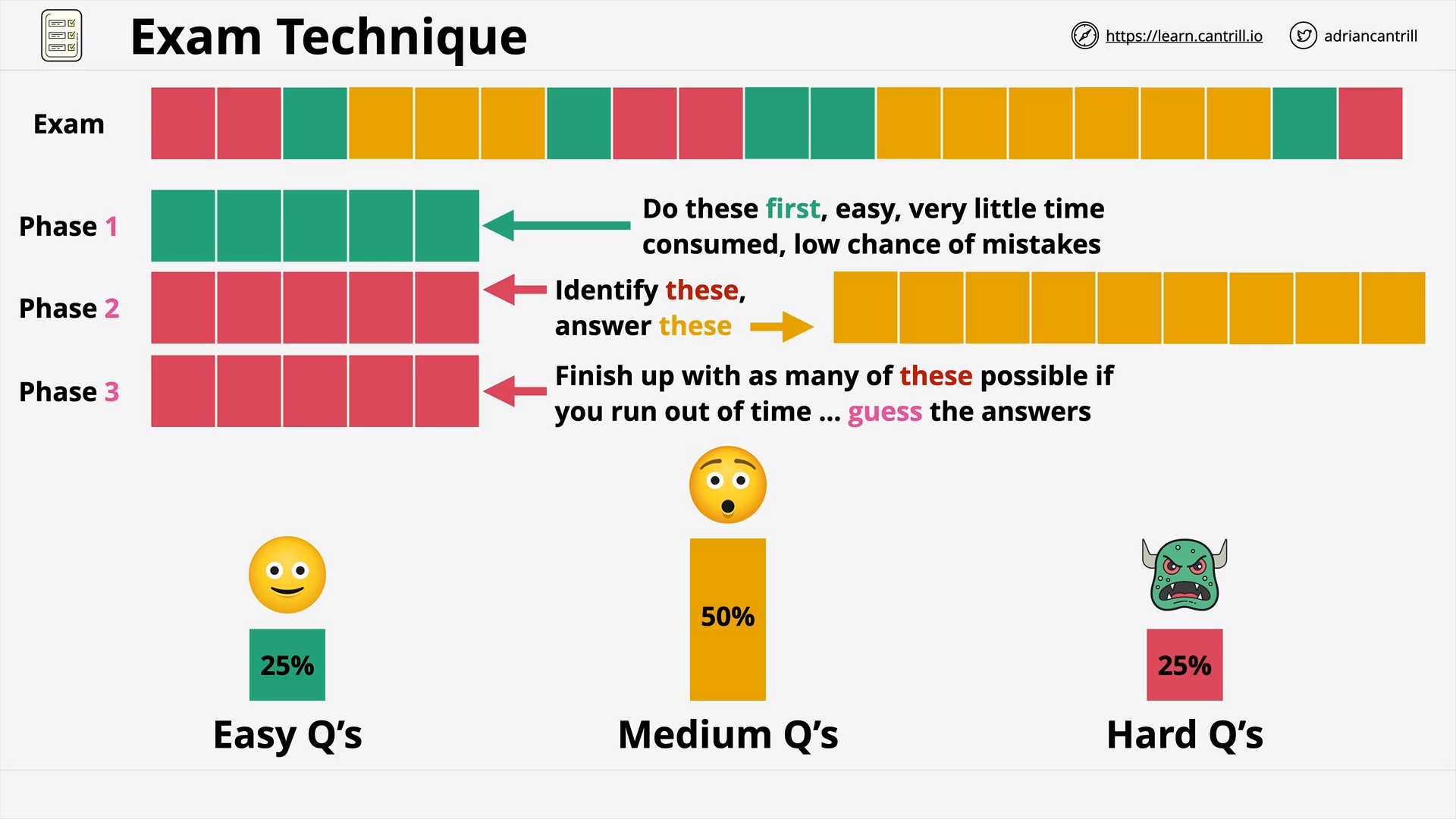 3 Phases Approach
3 Phases Approach
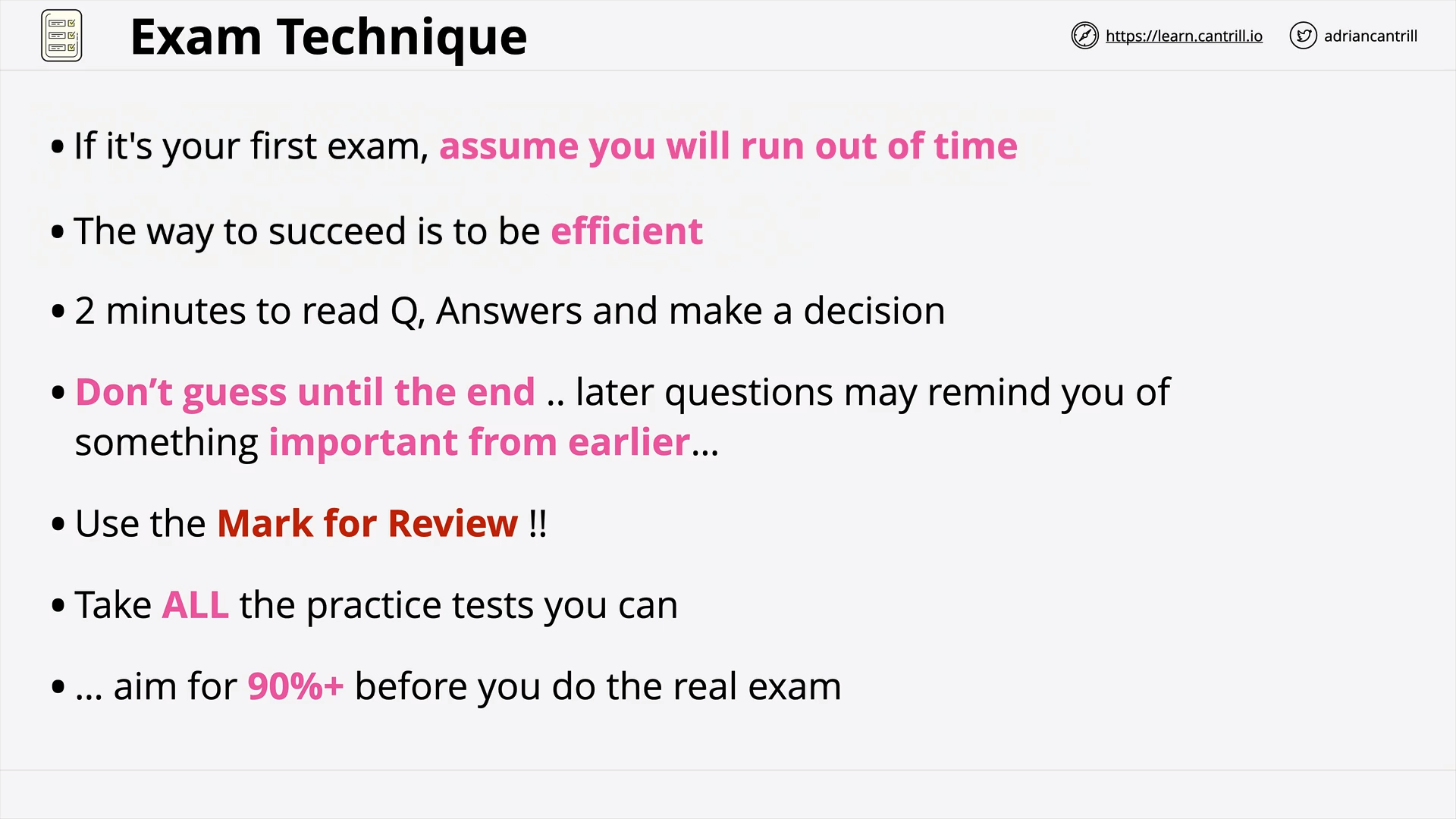 Exam Technique
Exam Technique
General AWS Question Technique - PART1 (14:12)
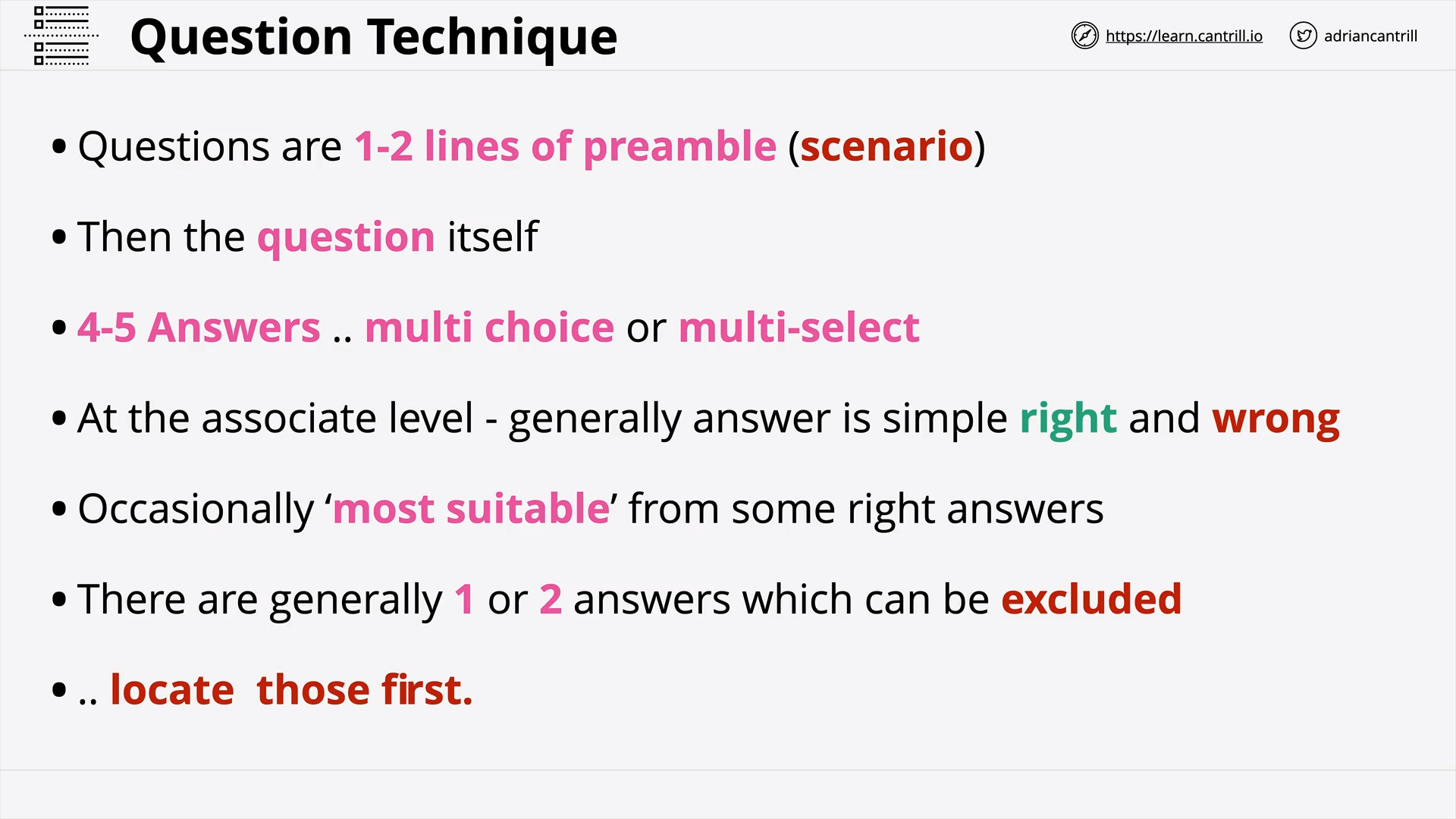 Question Technique: Preamble (scenario)
Question Technique: Preamble (scenario)
 Question Technique: Criteria (restriction)
Question Technique: Criteria (restriction)
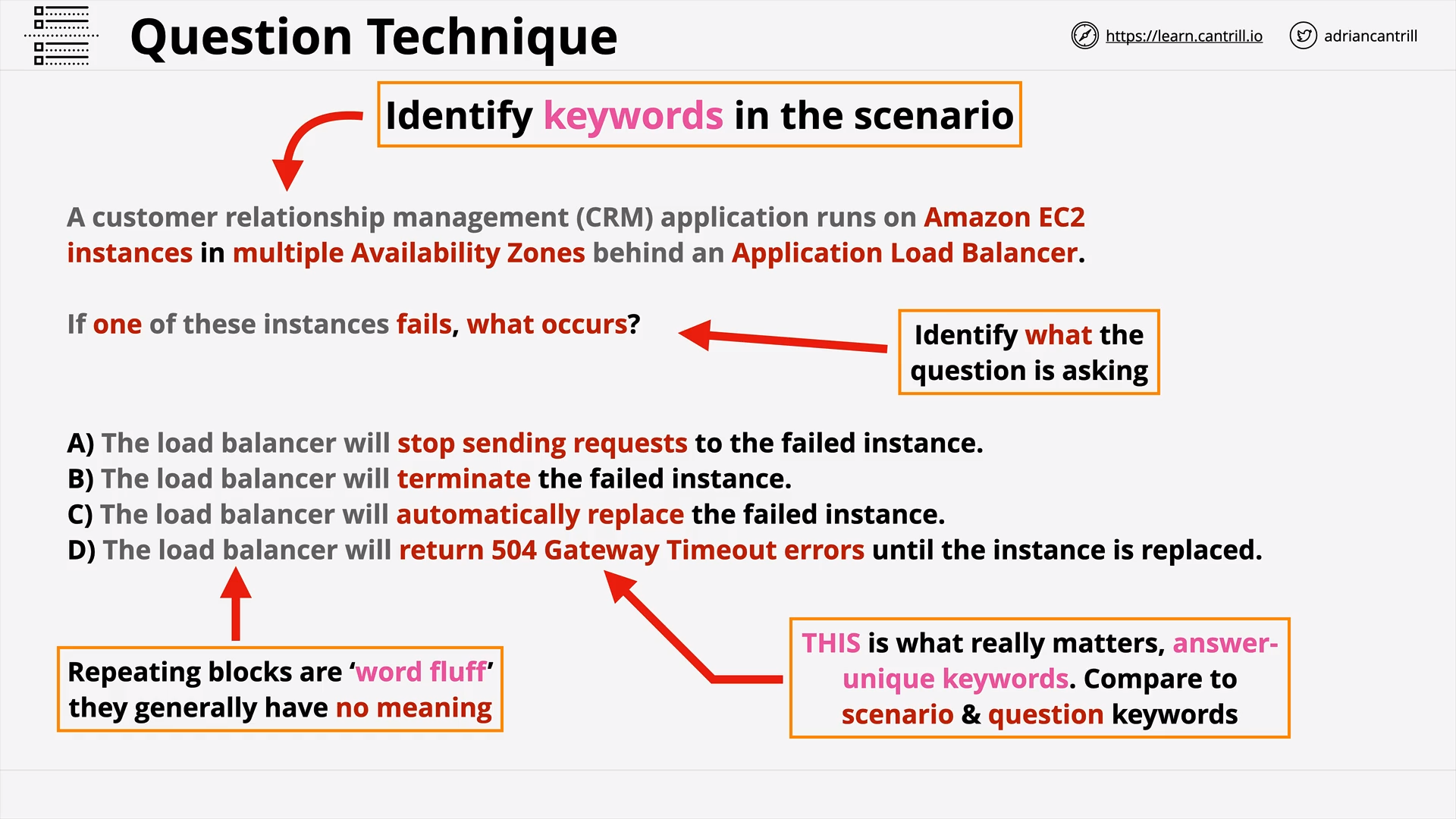 Question Technique: Keywords
Question Technique: Keywords
General AWS Question Technique - PART2 (9:01)
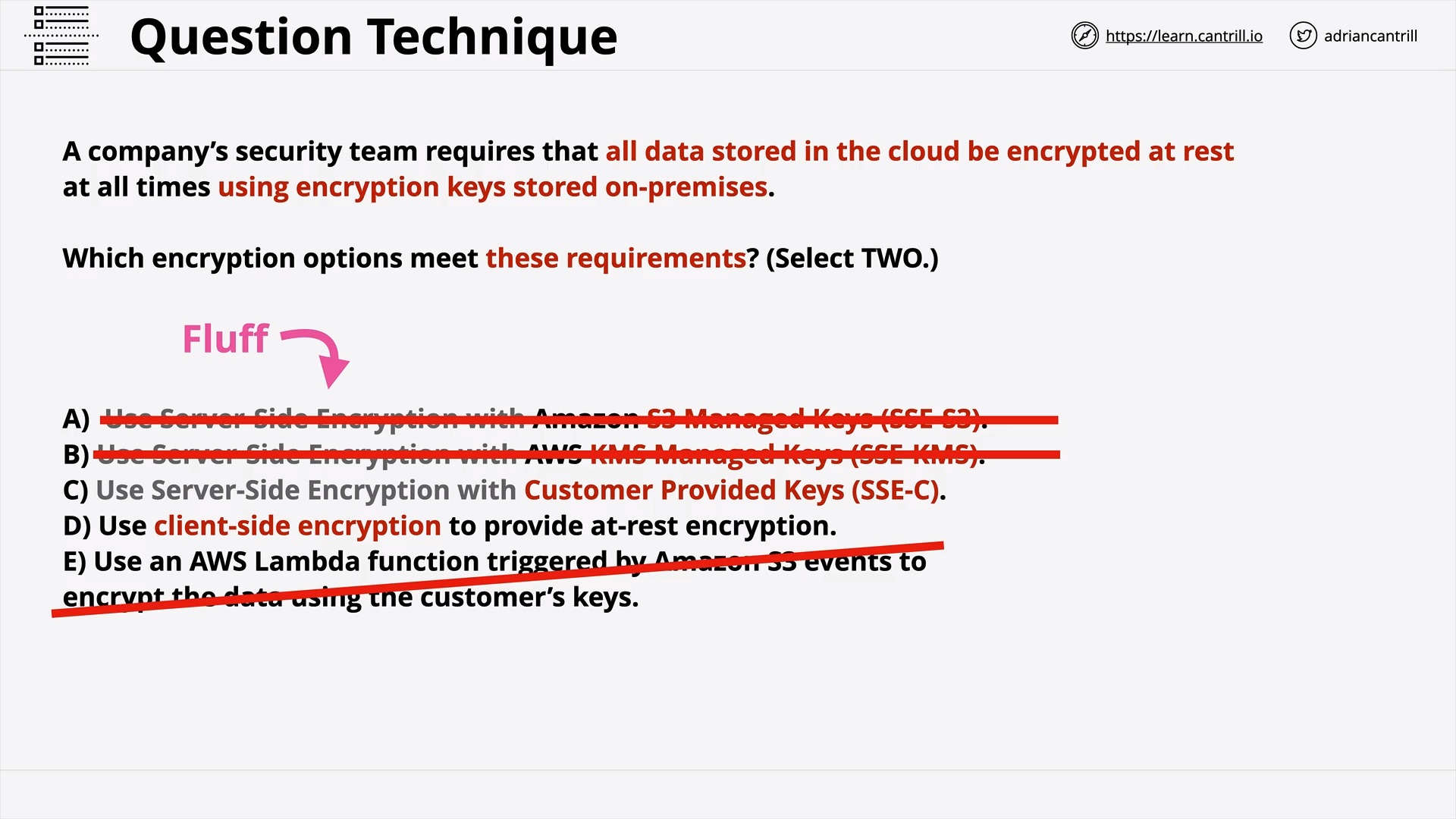 Question Technique: Keywords - Example
Question Technique: Keywords - Example
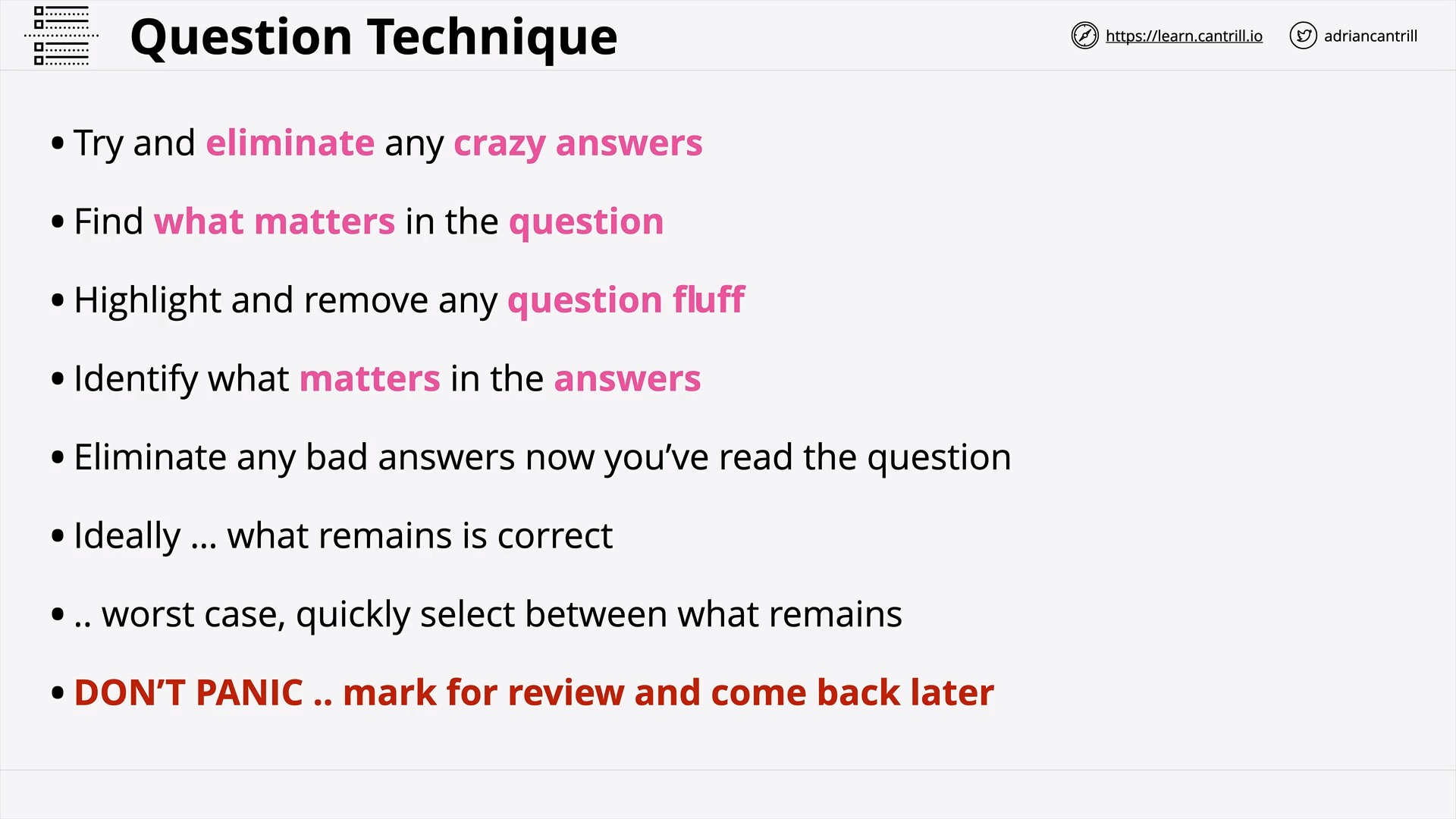 Question Technique: Eliminate crazy answers
Question Technique: Eliminate crazy answers