IAM, ACCOUNTS AND AWS ORGANISATIONS
[ASSOCIATE] IAM Identity Policies (15:52)
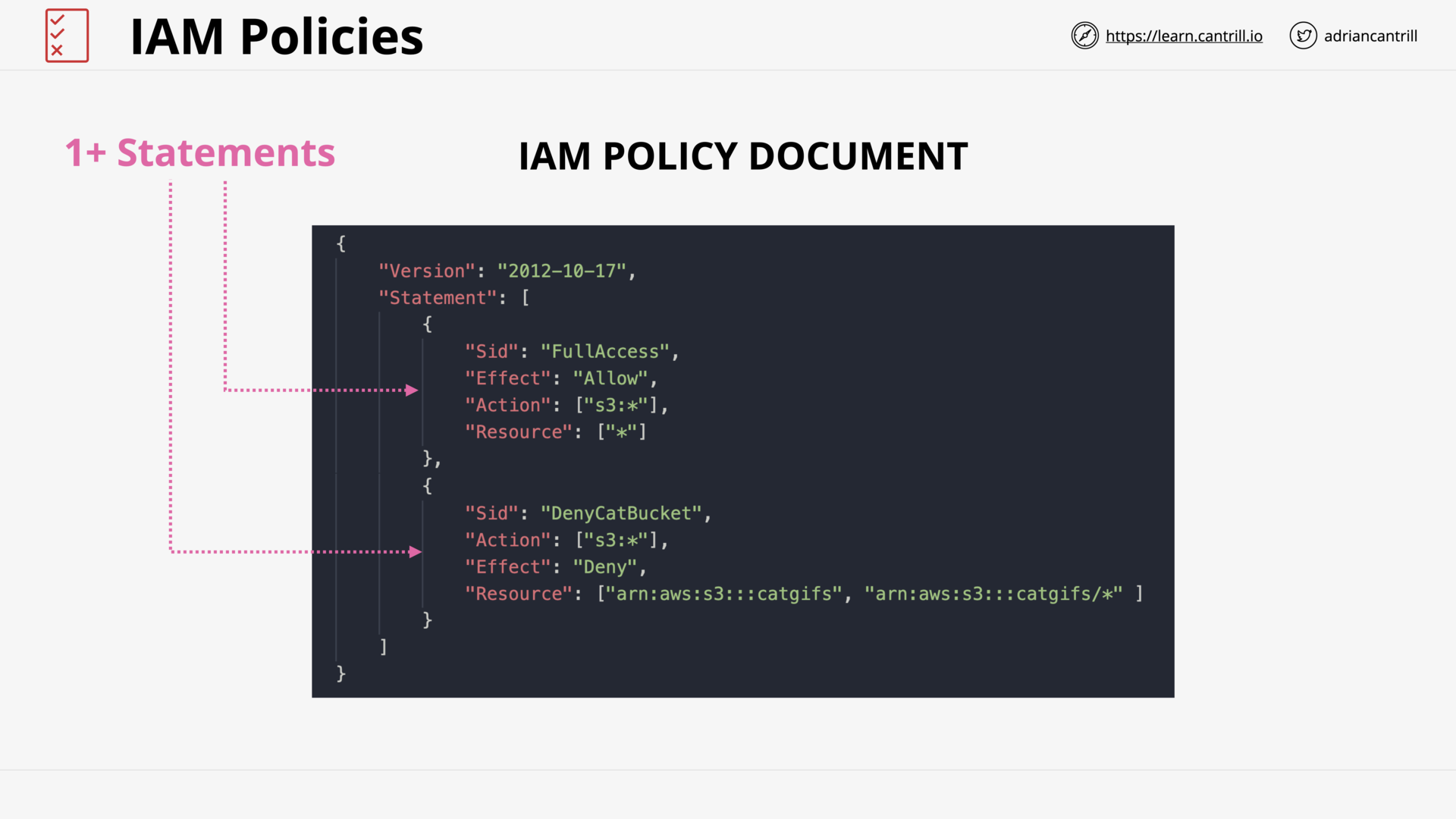 IAM Policy Document
IAM Policy Document
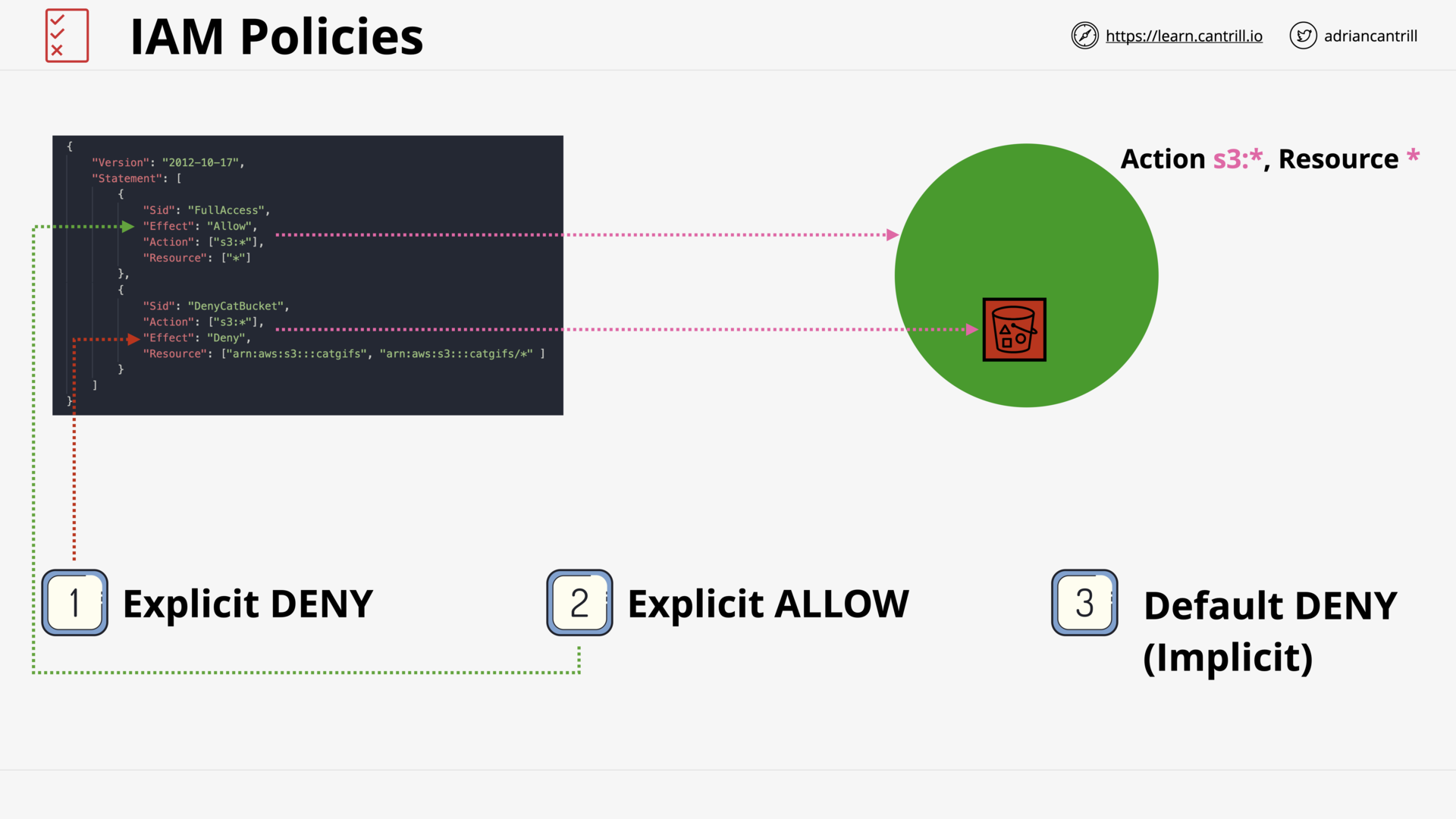 DENY - ALLOW - DENY
DENY - ALLOW - DENY
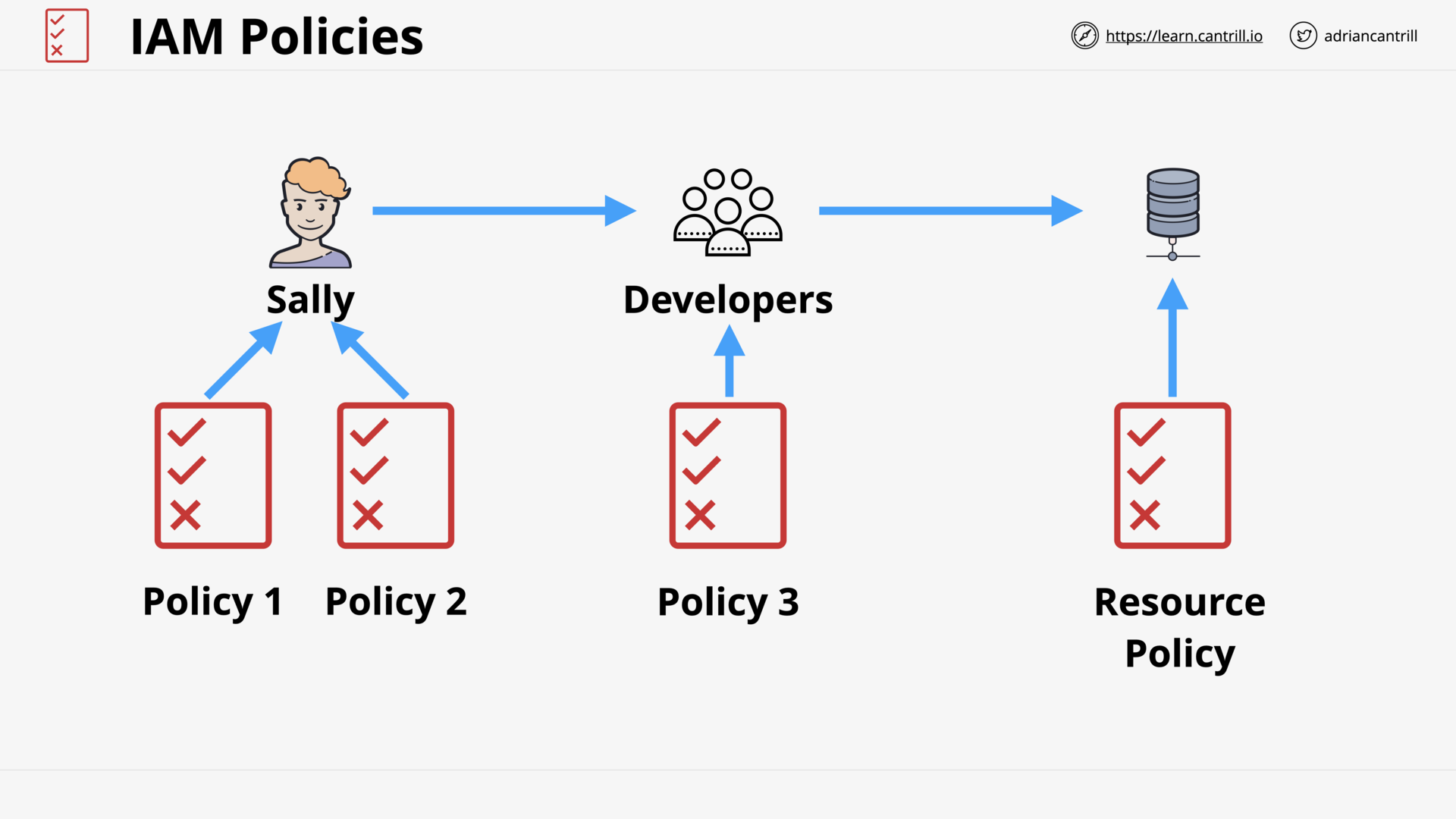 All policies for IAM Identities (User, Role, Group) & AWS Resources are evaluated at the same time.
All policies for IAM Identities (User, Role, Group) & AWS Resources are evaluated at the same time.
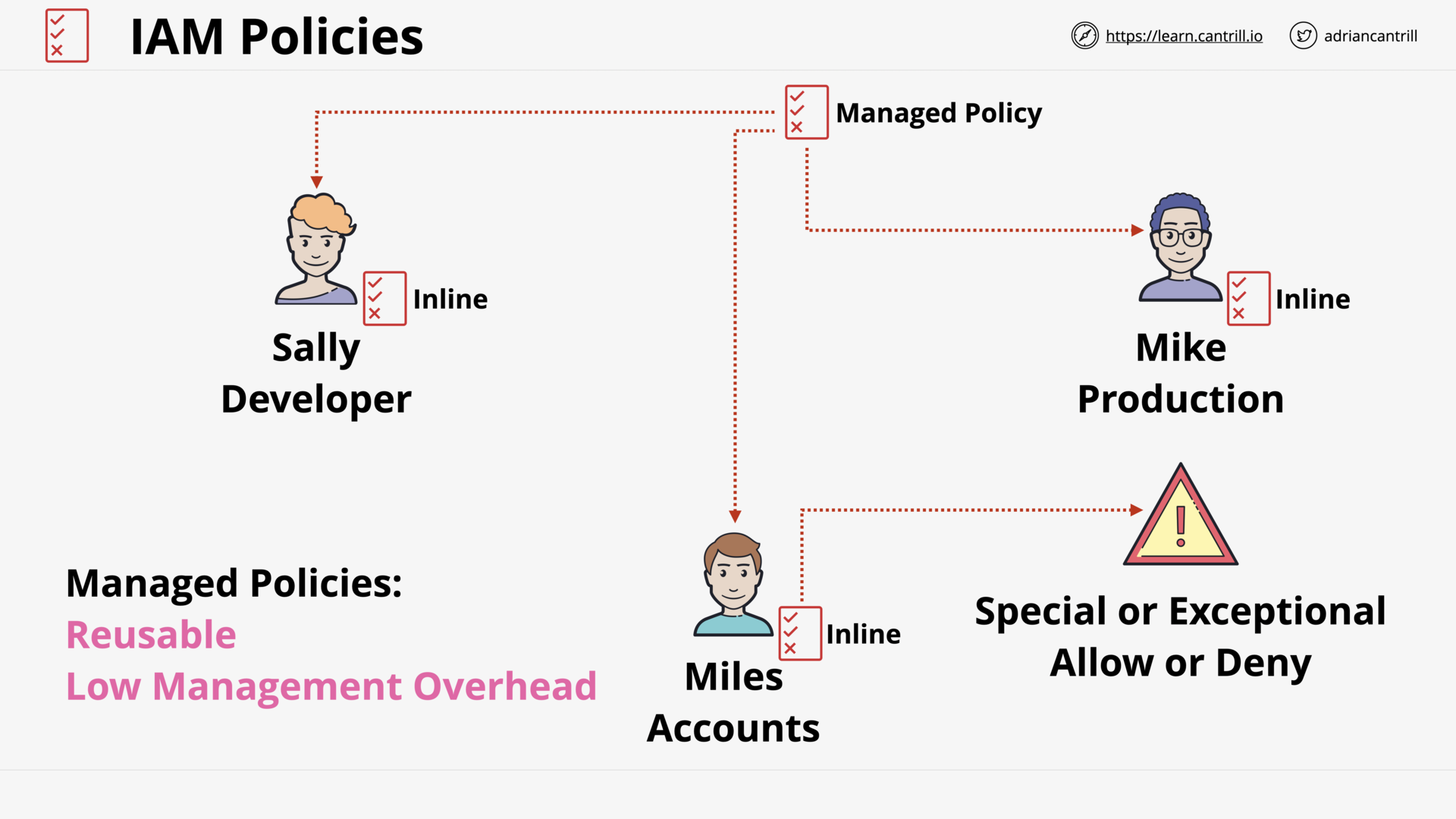 Inline Policy vs Managed Policy
Inline Policy vs Managed Policy
[ASSOCIATE] IAM Users and ARNs (13:49)
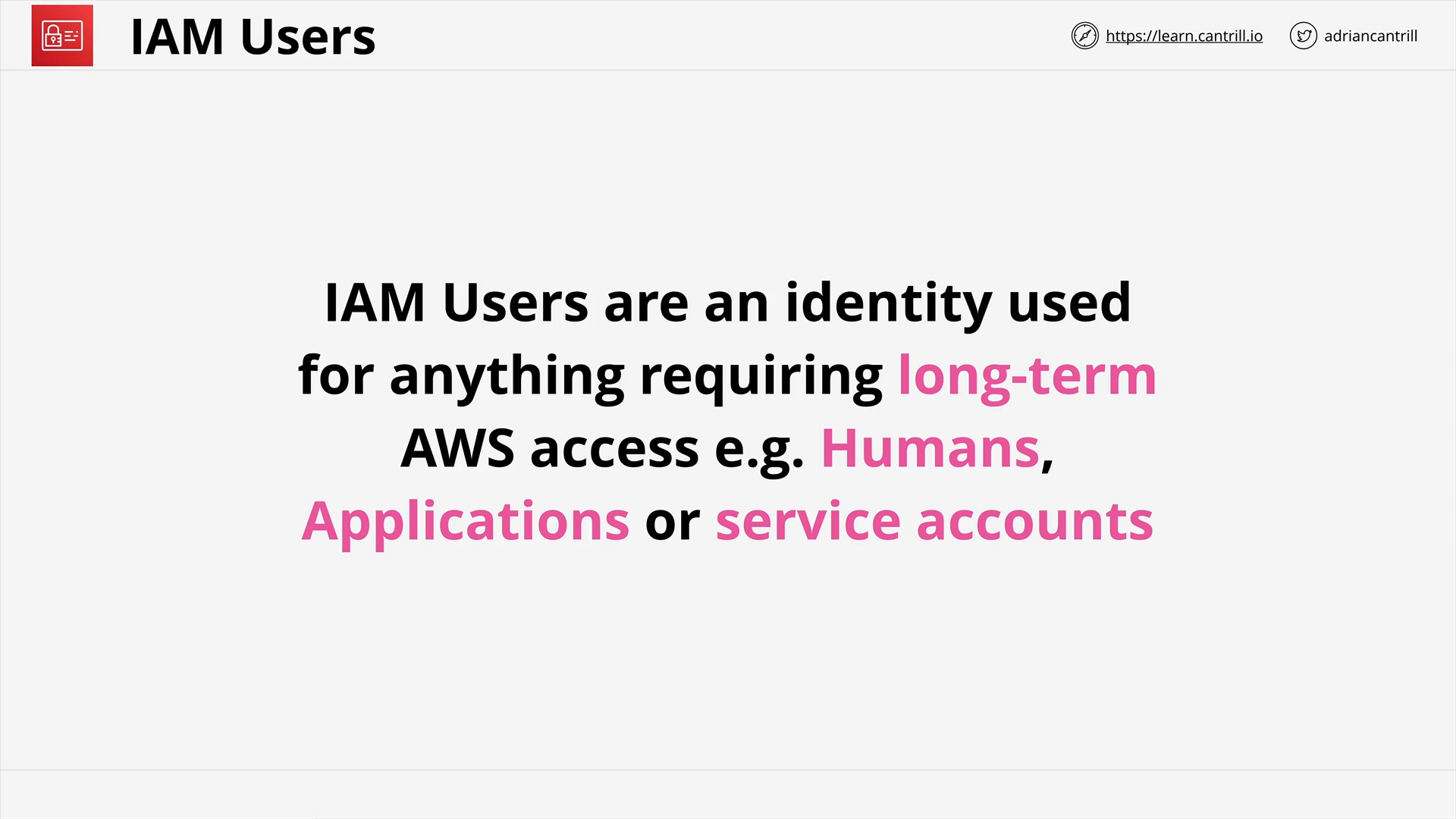 IAM User - What is it?
IAM User - What is it?
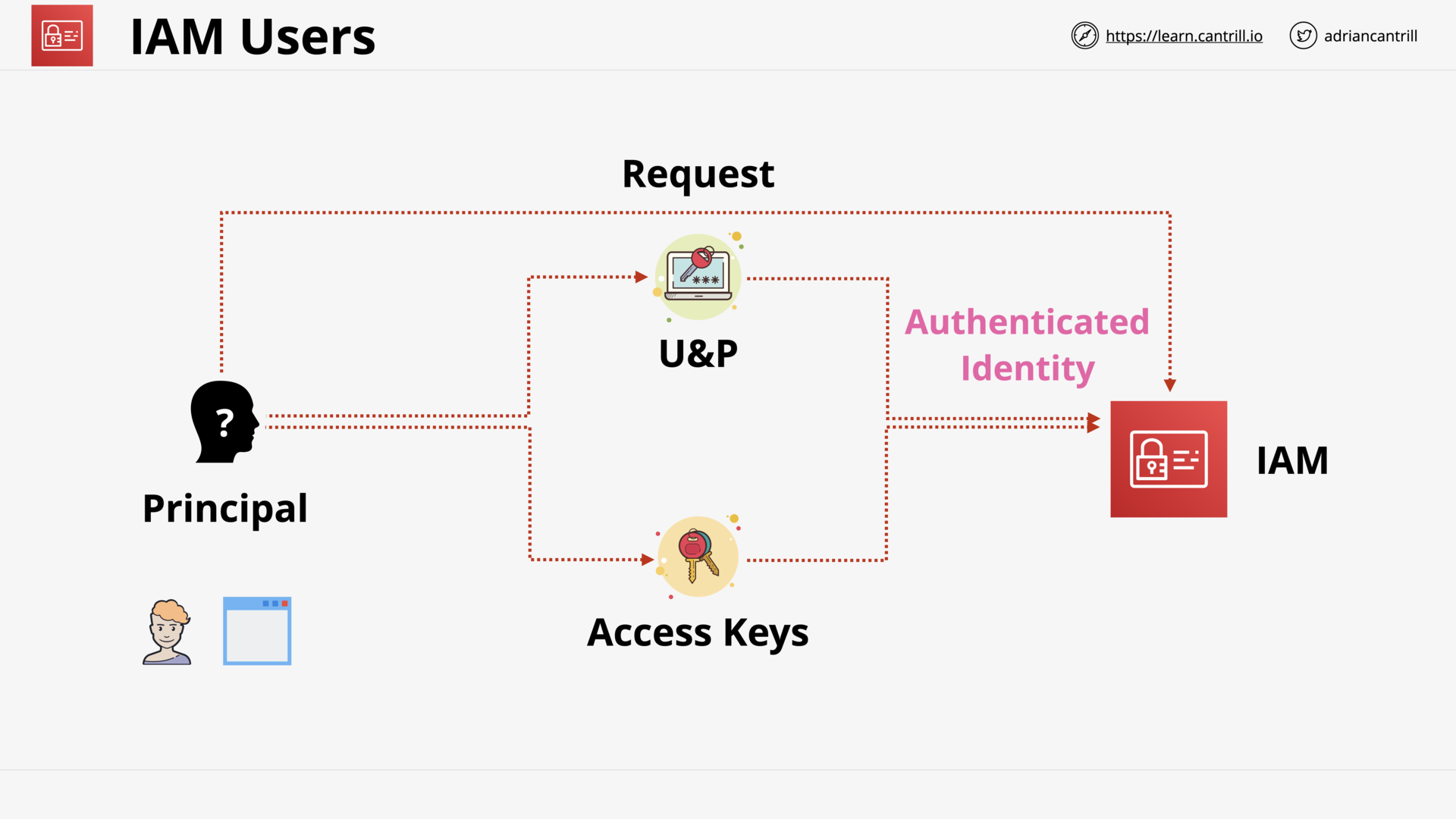 IAM - Principal and Authenticated Identity
IAM - Principal and Authenticated Identity
what is a principal?
Principal is an entity in AWS that can perform actions and access resources.
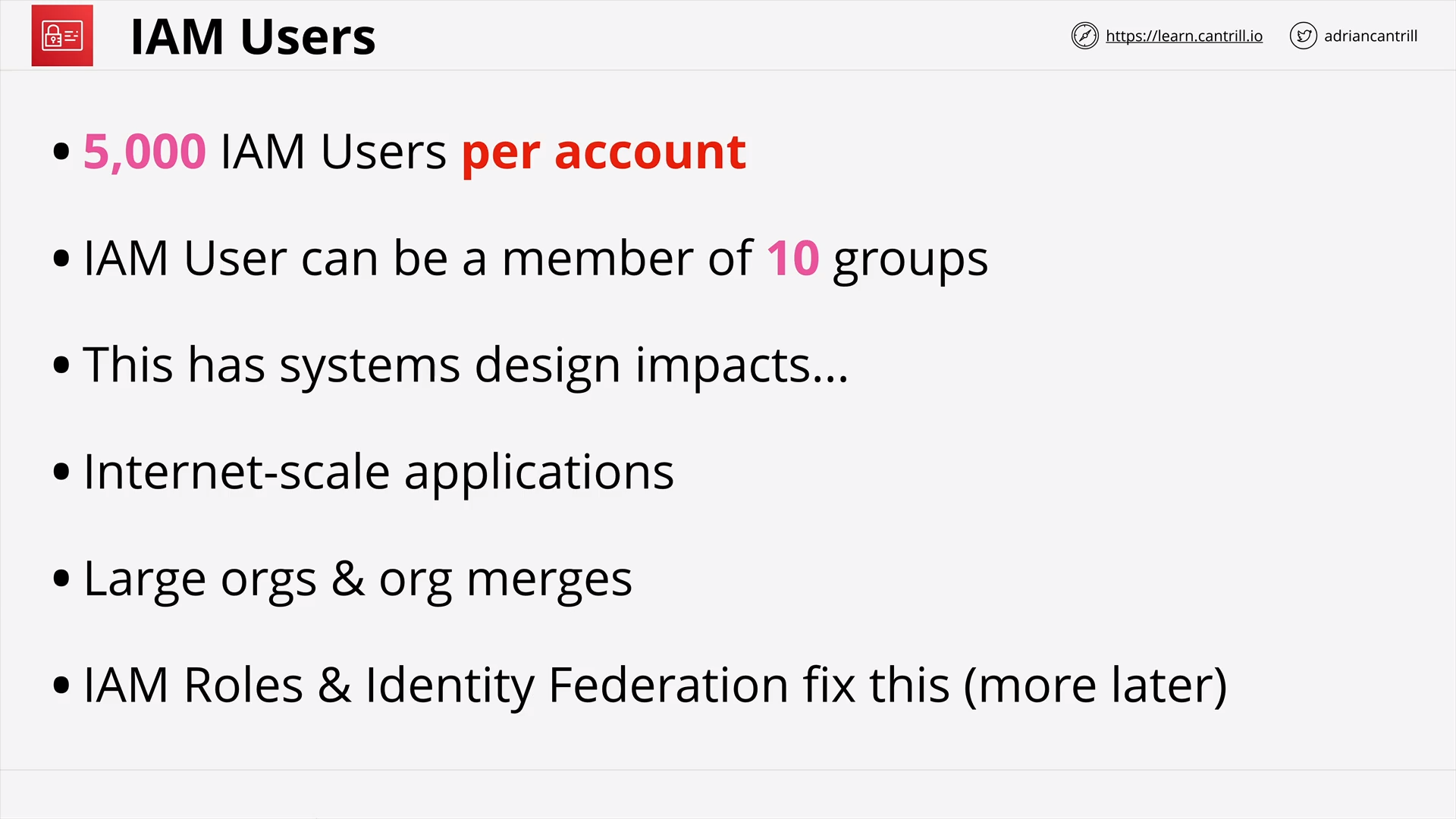 IAM Users - Limitation
IAM Users - Limitation
what is the limit iam users per account?
5.000 IAM Users per AWS account
how many iam groups a iam user can be a member of?
10 IAM groups per IAM User
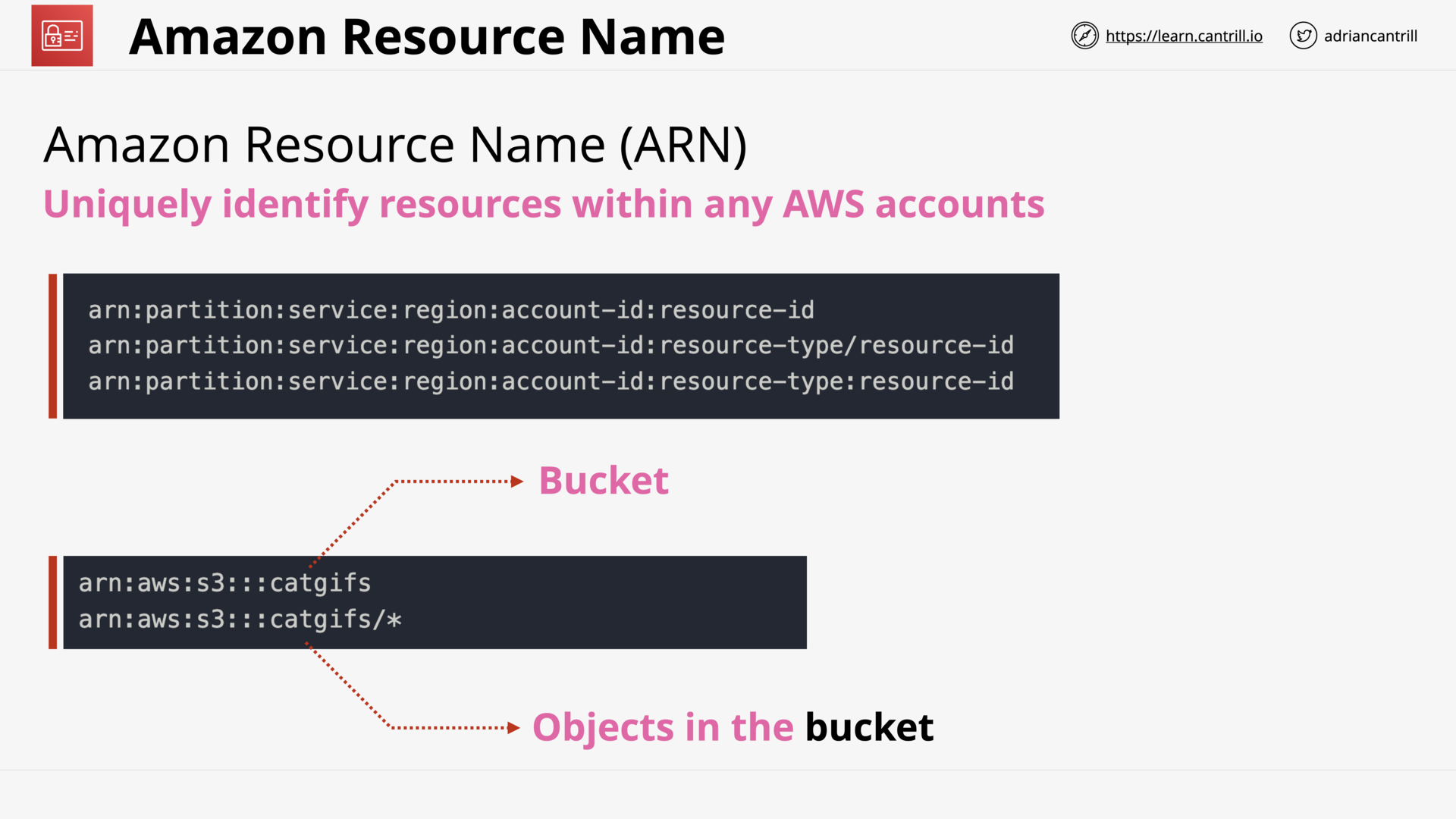 ARNs
ARNs
what is the format of arn?
- arn:partition:service:region:account-id:resource-id
- arn:partition:service:region:account-id:resource-type/resource-id
- arn:partition:service:region:account-id:resource-type:resource-id
👉
- 5 to 6 colon
: - region or/and account-id can be omitted.
| arn | partition | service | region | account-id | resource-type | resource-id |
|---|---|---|---|---|---|---|
awsaws-cnaws-us-gov | iams3ec2… | us-east-1ap-southest-1… | user |
[ASSOCIATE, DEMO] Simple Identity Permissions in AWS (16:06)
[ASSOCIATE] IAM Groups (7:48)
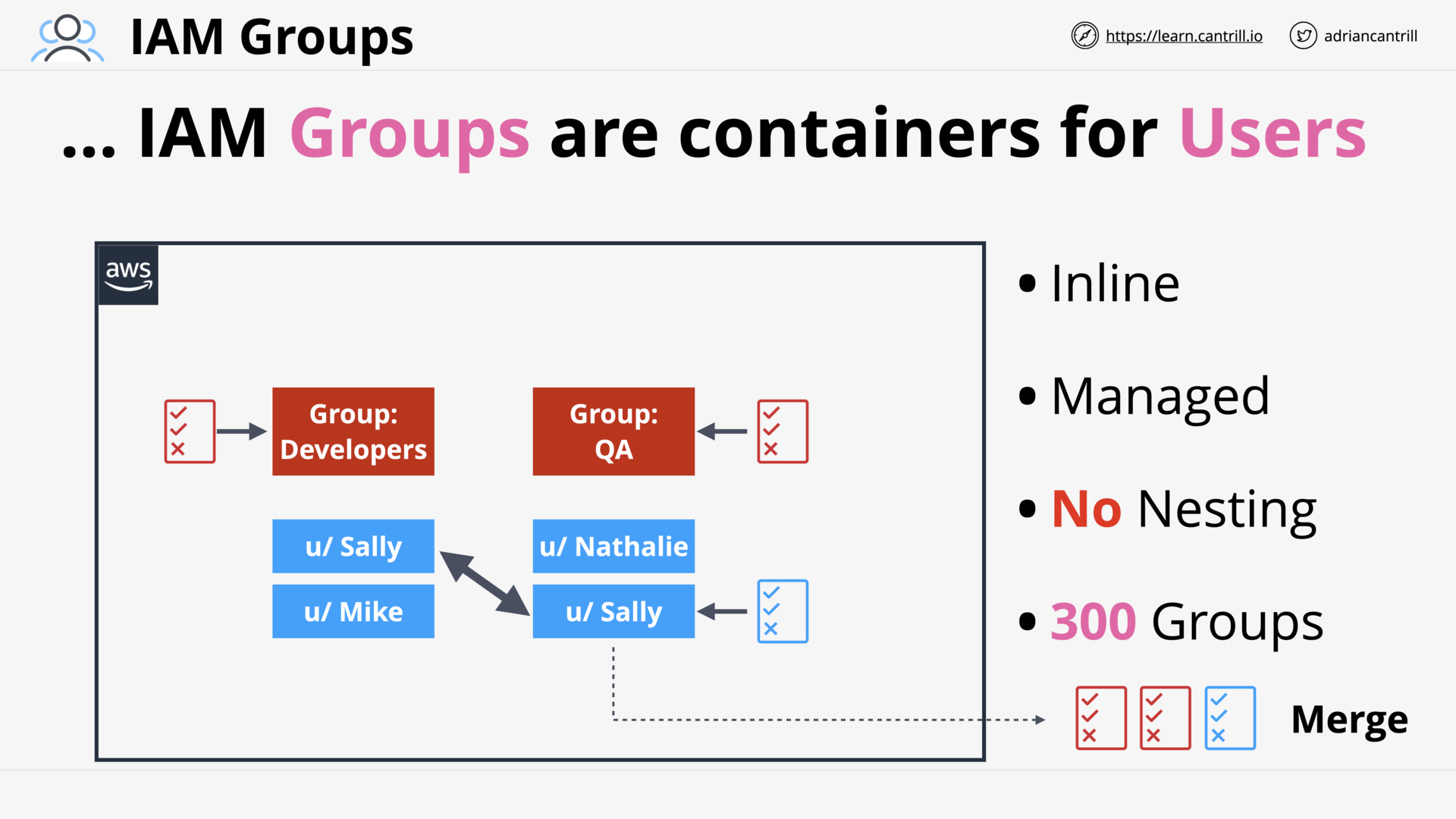 IAM Groups
IAM Groups
what is iam group?
Containers for IAM Users.
what are the limits of iam group?
- No Nesting.
- Limit of 300 Groups.
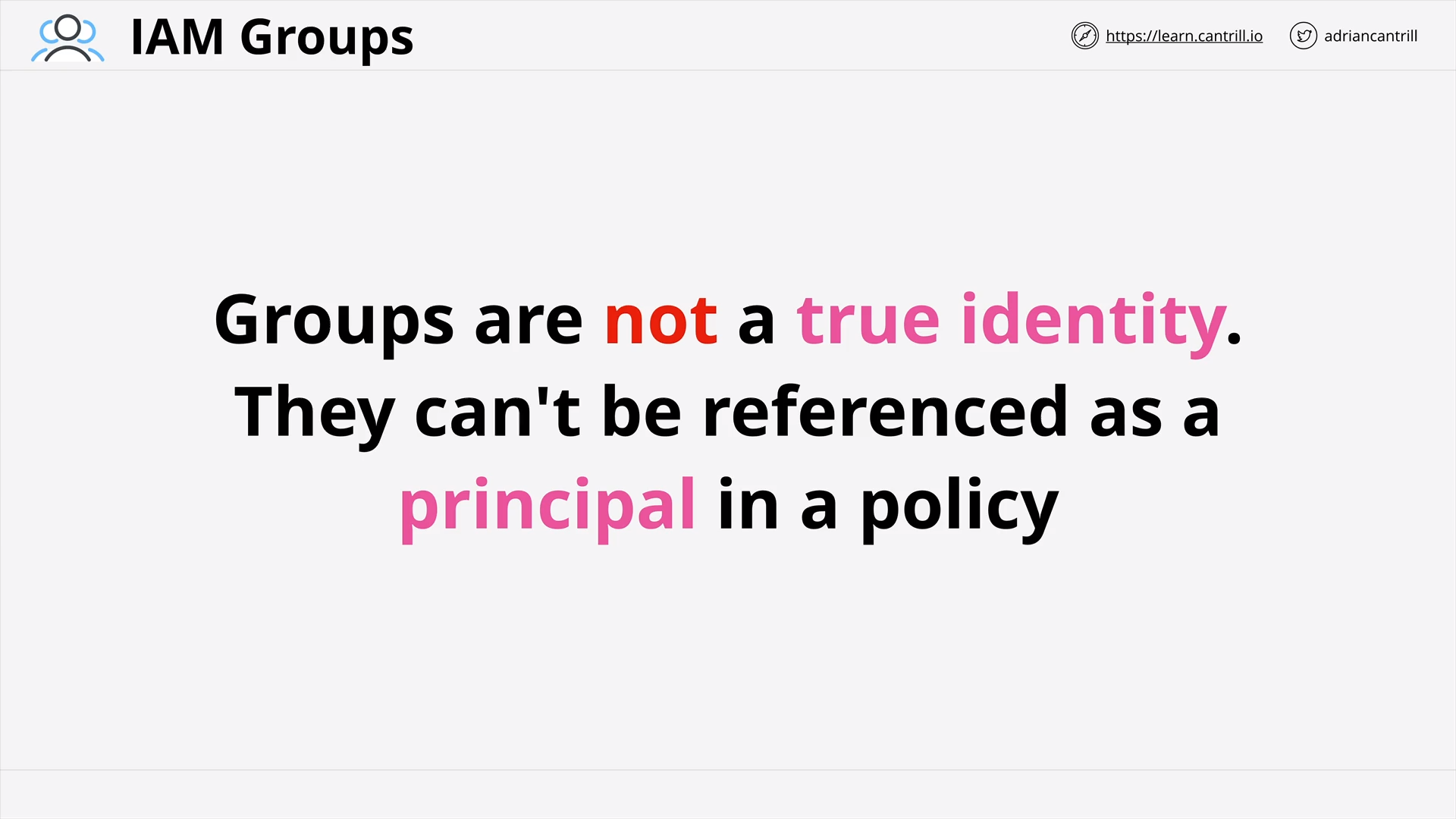 IAM Group is not a true identity
IAM Group is not a true identity
can an iam group be used as a principle in a policy?
IAM Group is NOT a true identity, that
- can NOT be used as a Principle in a policy.
- don’t have credential to login with
[ASSOCIATE, DEMO] Permissions control using IAM Groups (9:24)
[ASSOCIATE] IAM Roles - The Tech (8:13)
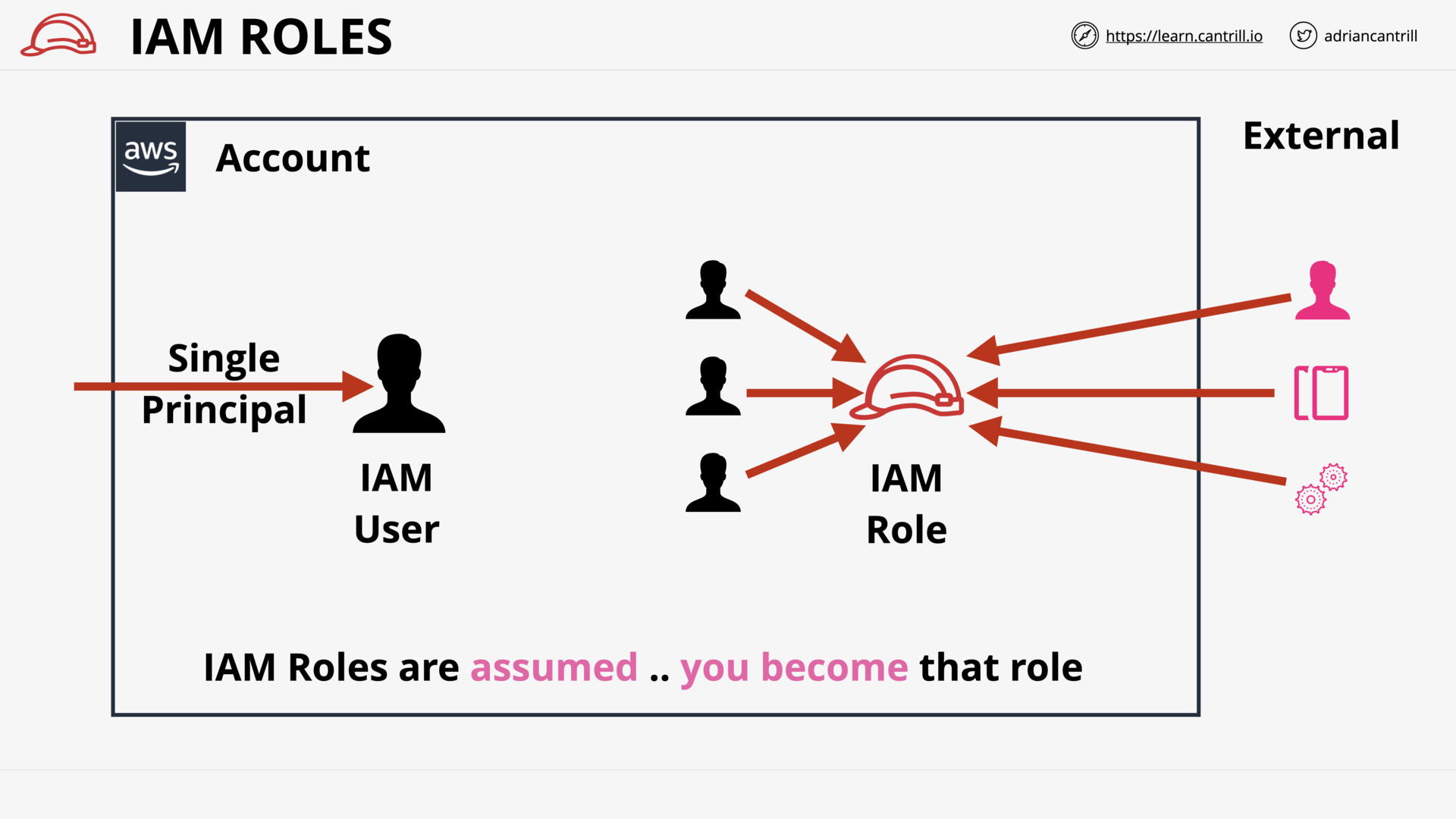 IAM Role and Assuming an IAM Role
IAM Role and Assuming an IAM Role
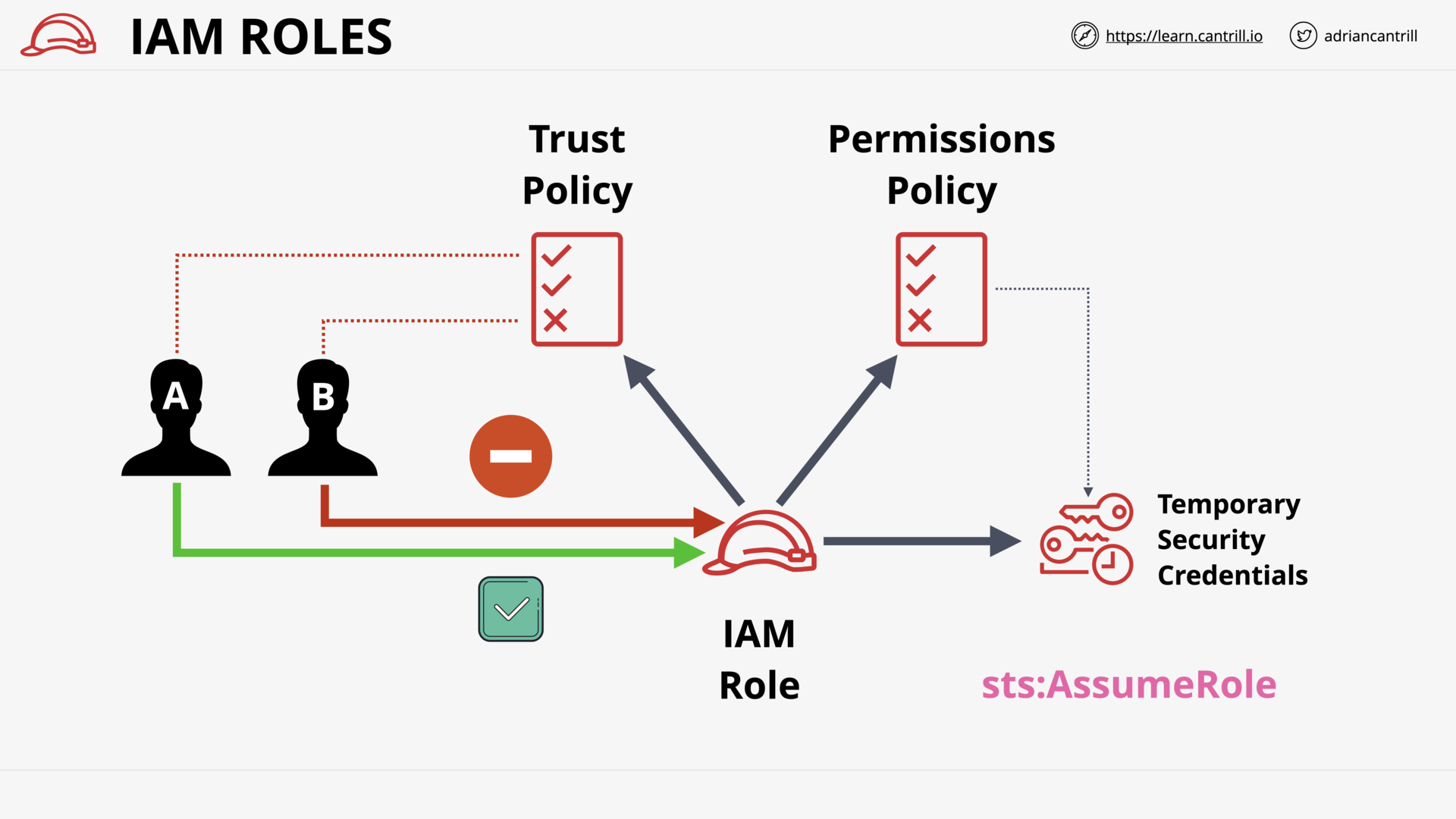 Trust Policy vs Permission Policy
Trust Policy vs Permission Policy
what is trust policy in iam?
The trust policy defines
- which principals can assume the role, and
- under which conditions
See How to use trust policies with IAM roles | AWS Security Blog
[ASSOCIATE] When to use IAM Roles (15:27)
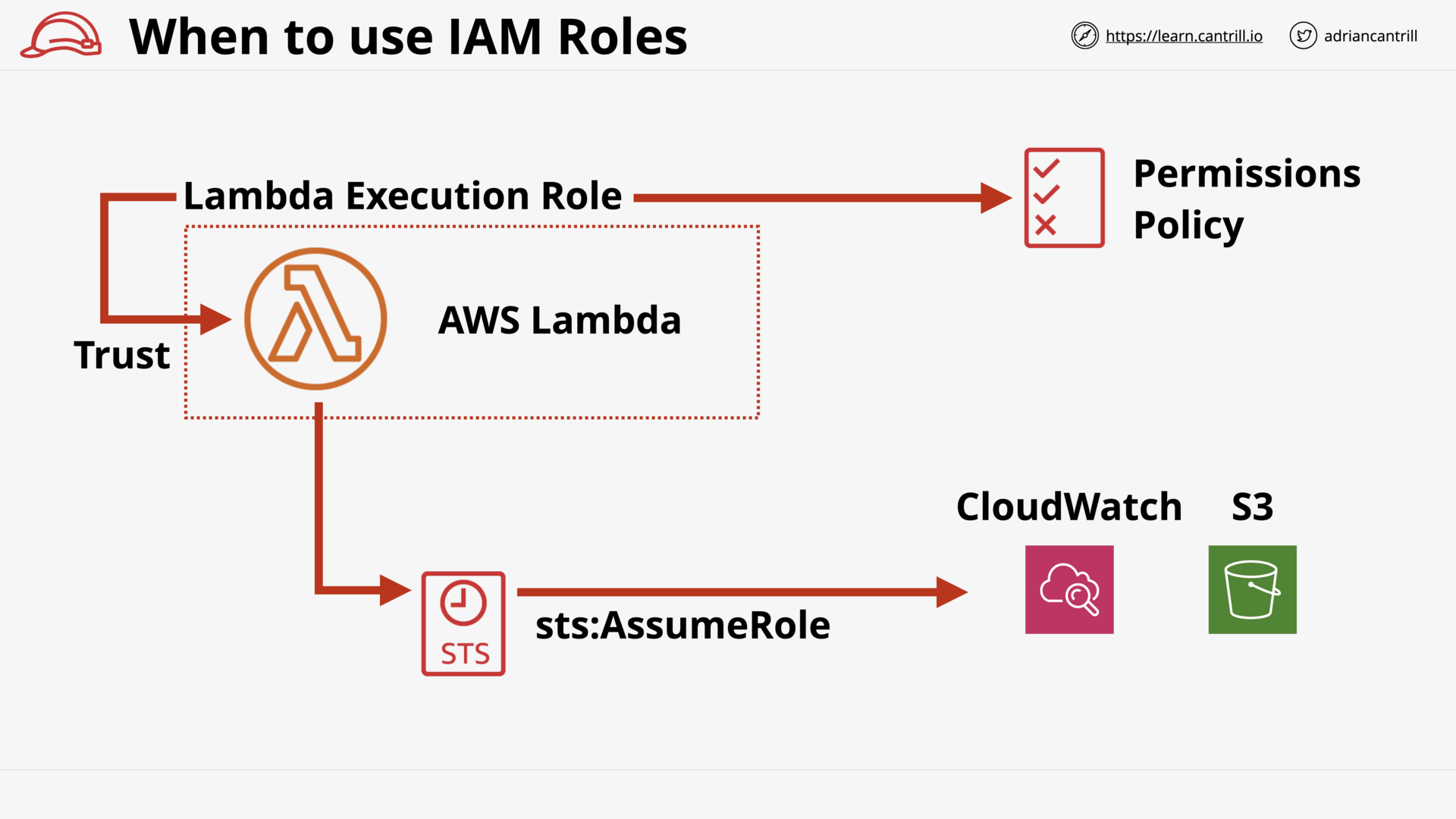 Lambda Execute Role
Lambda Execute Role
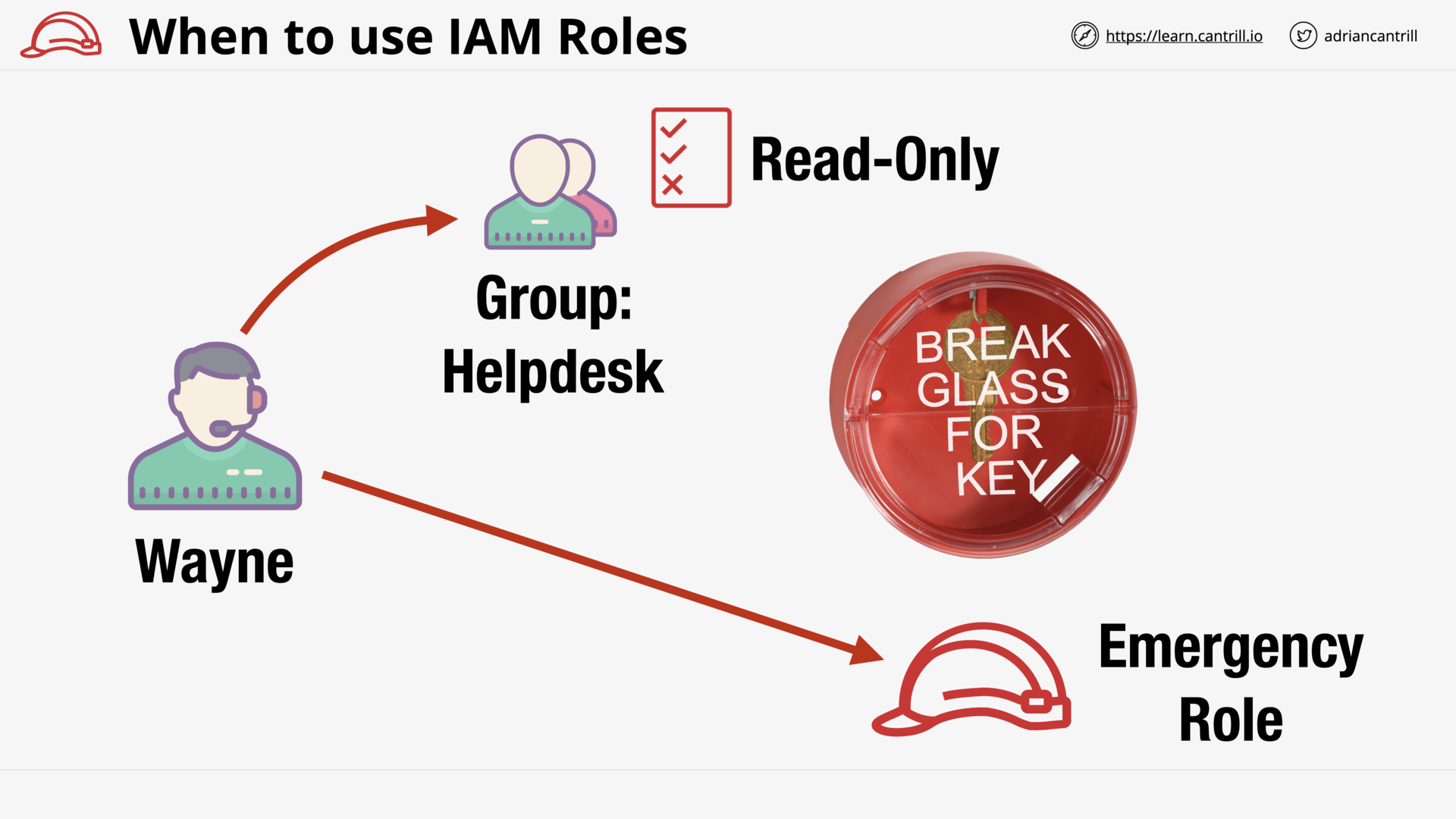 Emergency Role
Emergency Role
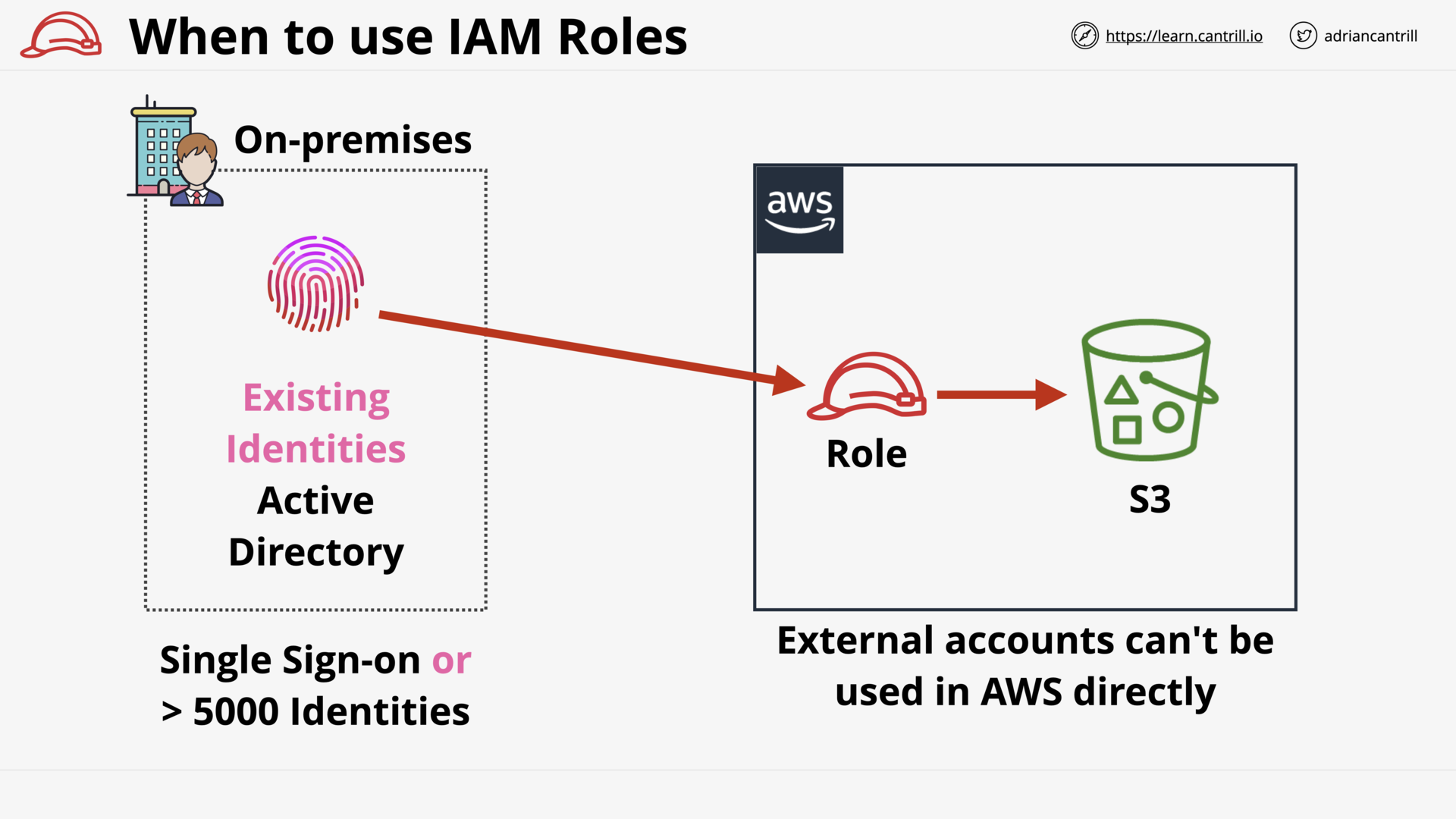 Existing Identities (e.g. Active Directory)
Existing Identities (e.g. Active Directory)
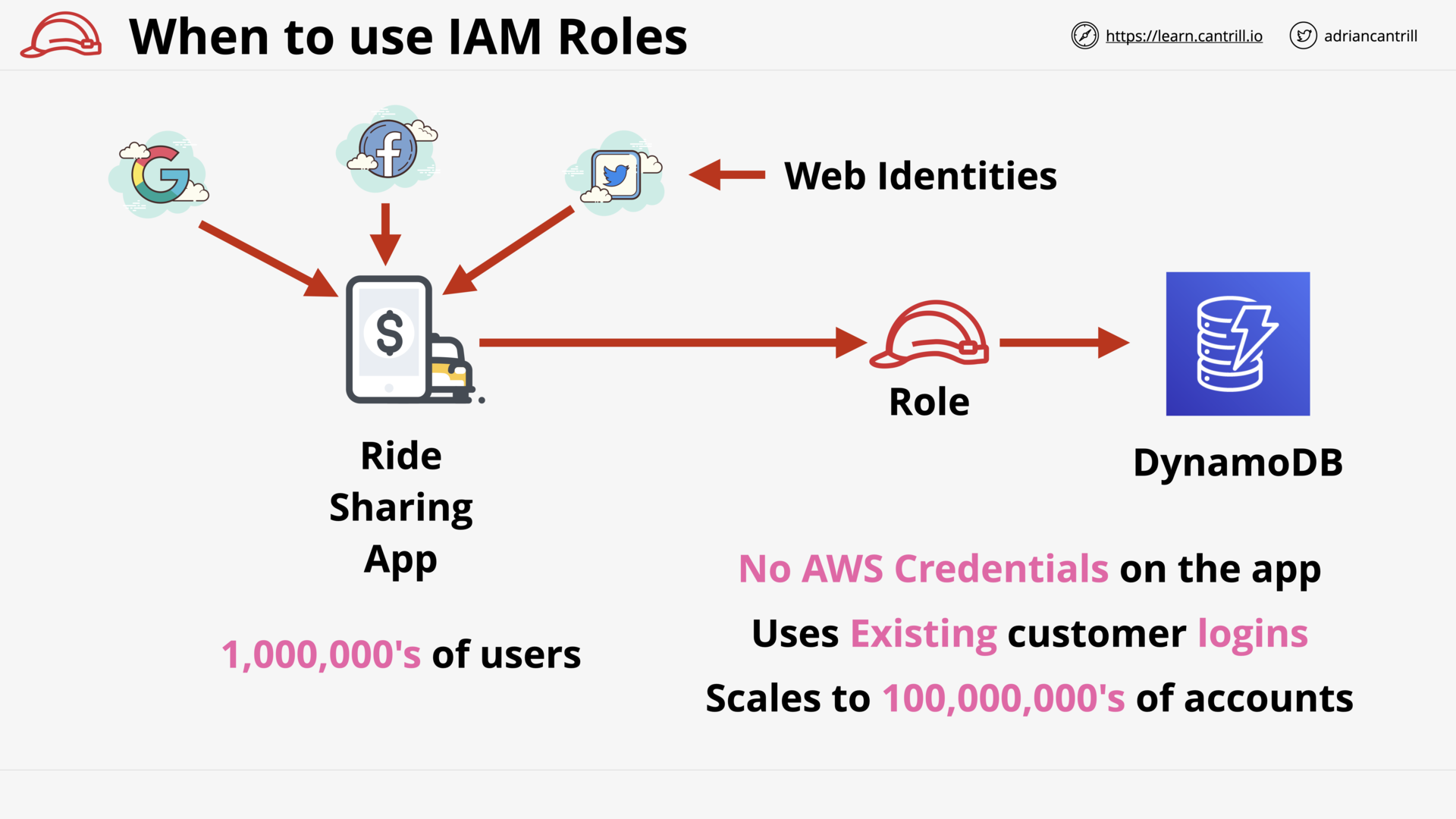 Web Identities (e.g. Google, Facebook)
Web Identities (e.g. Google, Facebook)
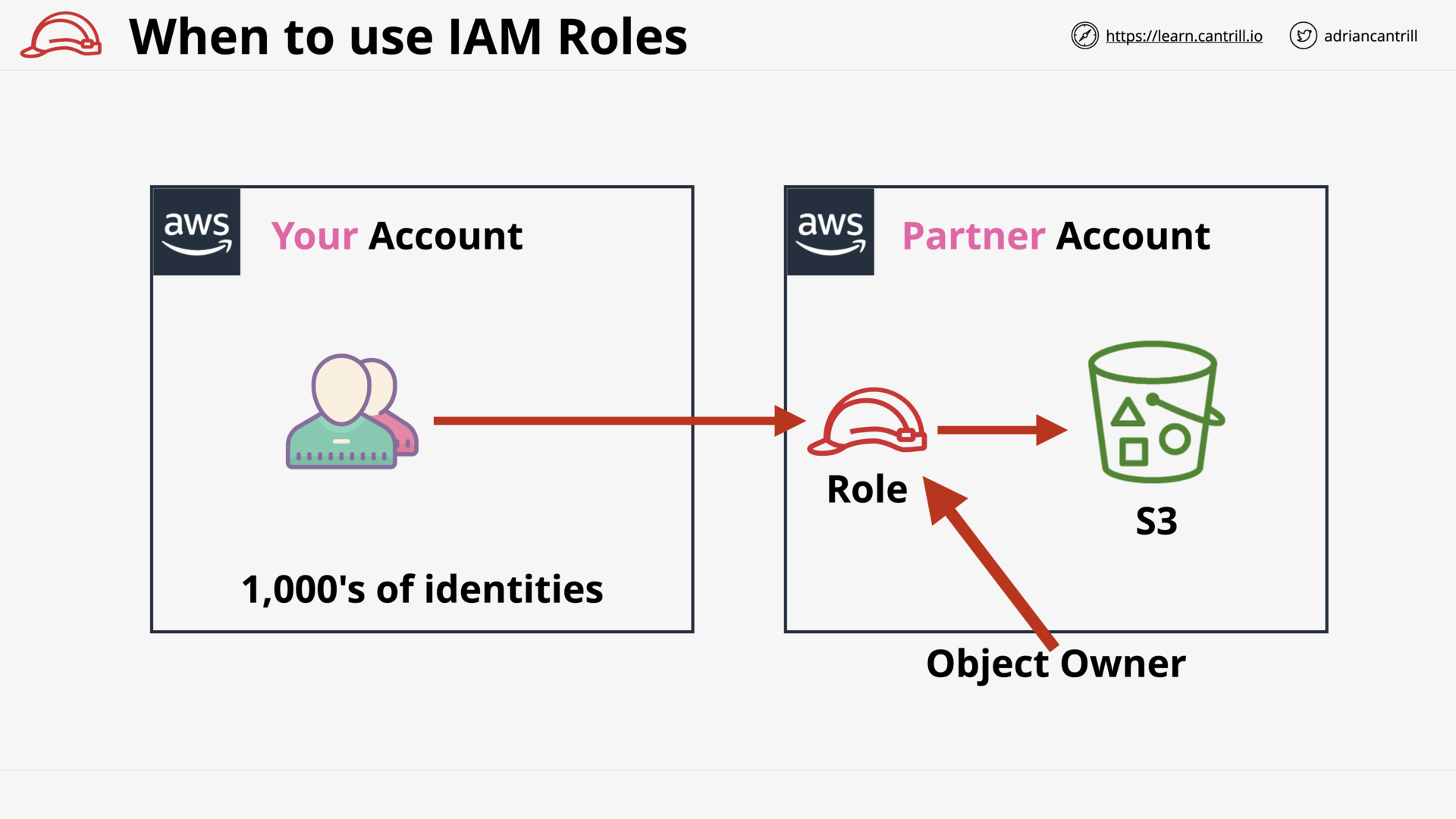 AWS Partner Accounts
AWS Partner Accounts
Service-linked Roles & PassRole (5:16)
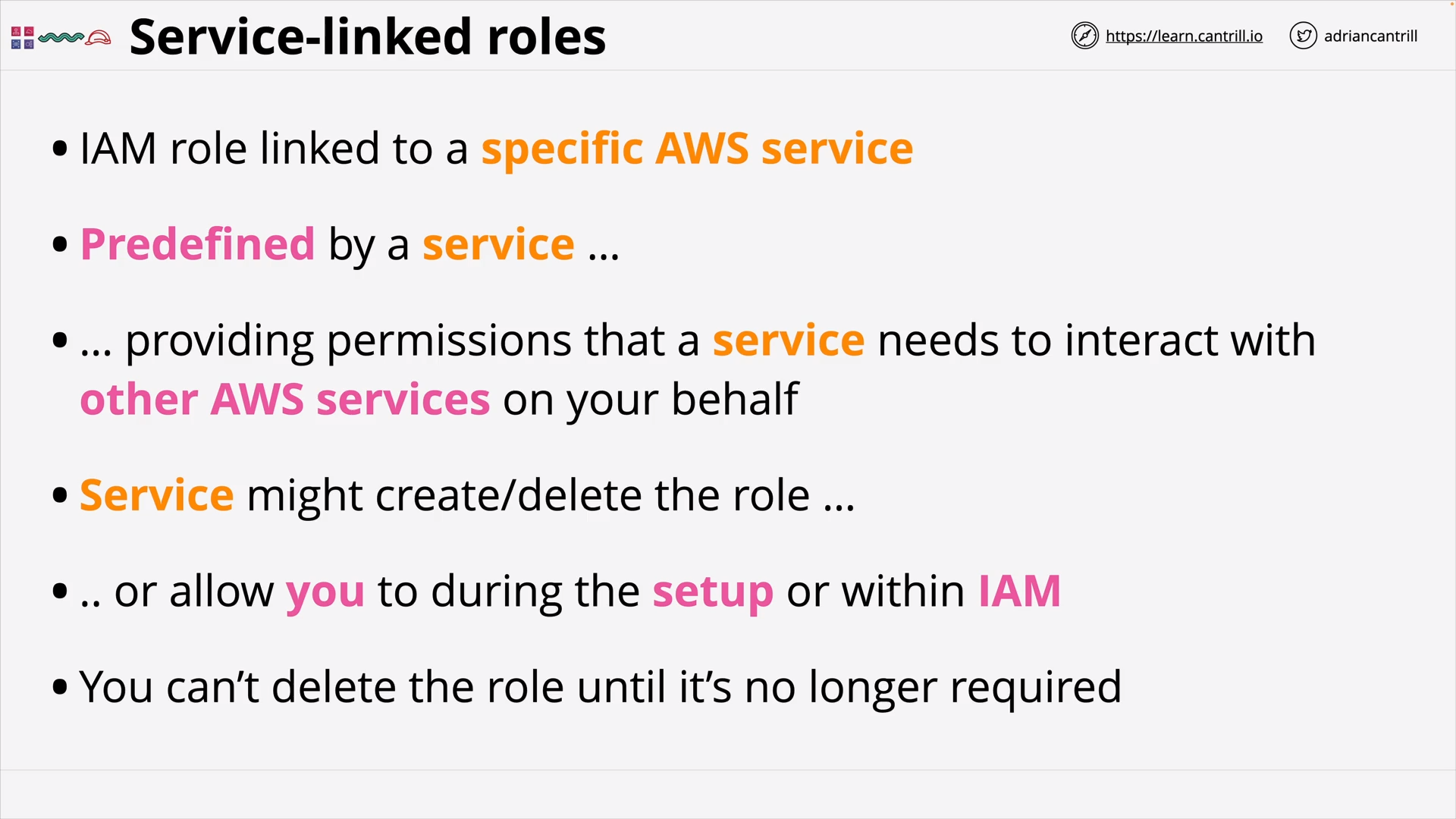 Service-linked Roles
Service-linked Roles
what is service-linked role?
A service-linked role is
- a unique type of IAM role that is linked directly to an AWS service.
- predefined (by the service) to include all the permissions that the service requires (to call other AWS services on your behalf).
why use service-linked role?
A service-linked Role
-
simplify the process of setting up a service because
- you don’t have to manually add permissions for the service to complete actions on your behalf
-
may be created
- automatically (by the service)
- manually using a wizard in the console
- manually using IAM
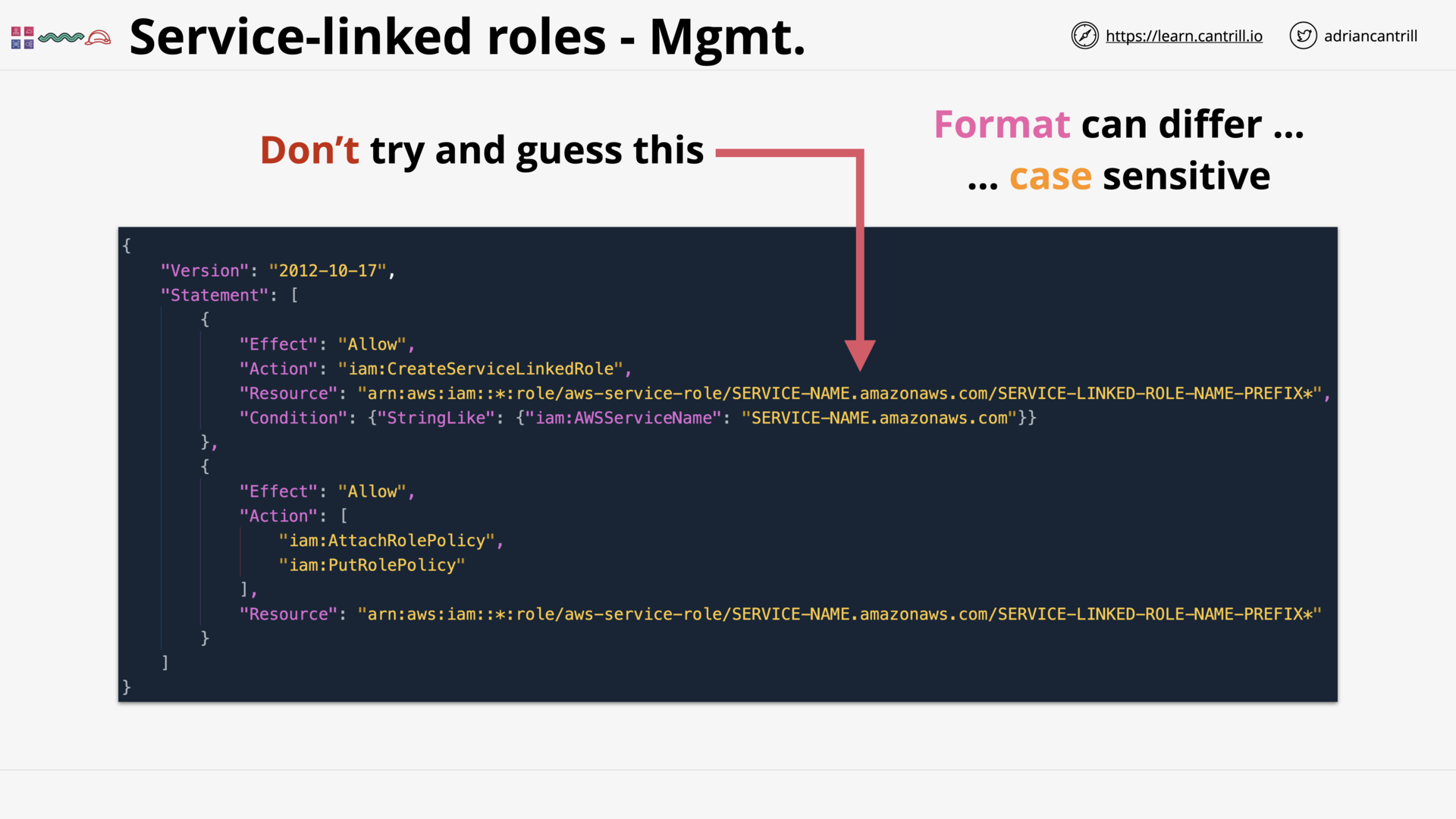 Permissions to allow create/edit the service-linked role
Permissions to allow create/edit the service-linked role
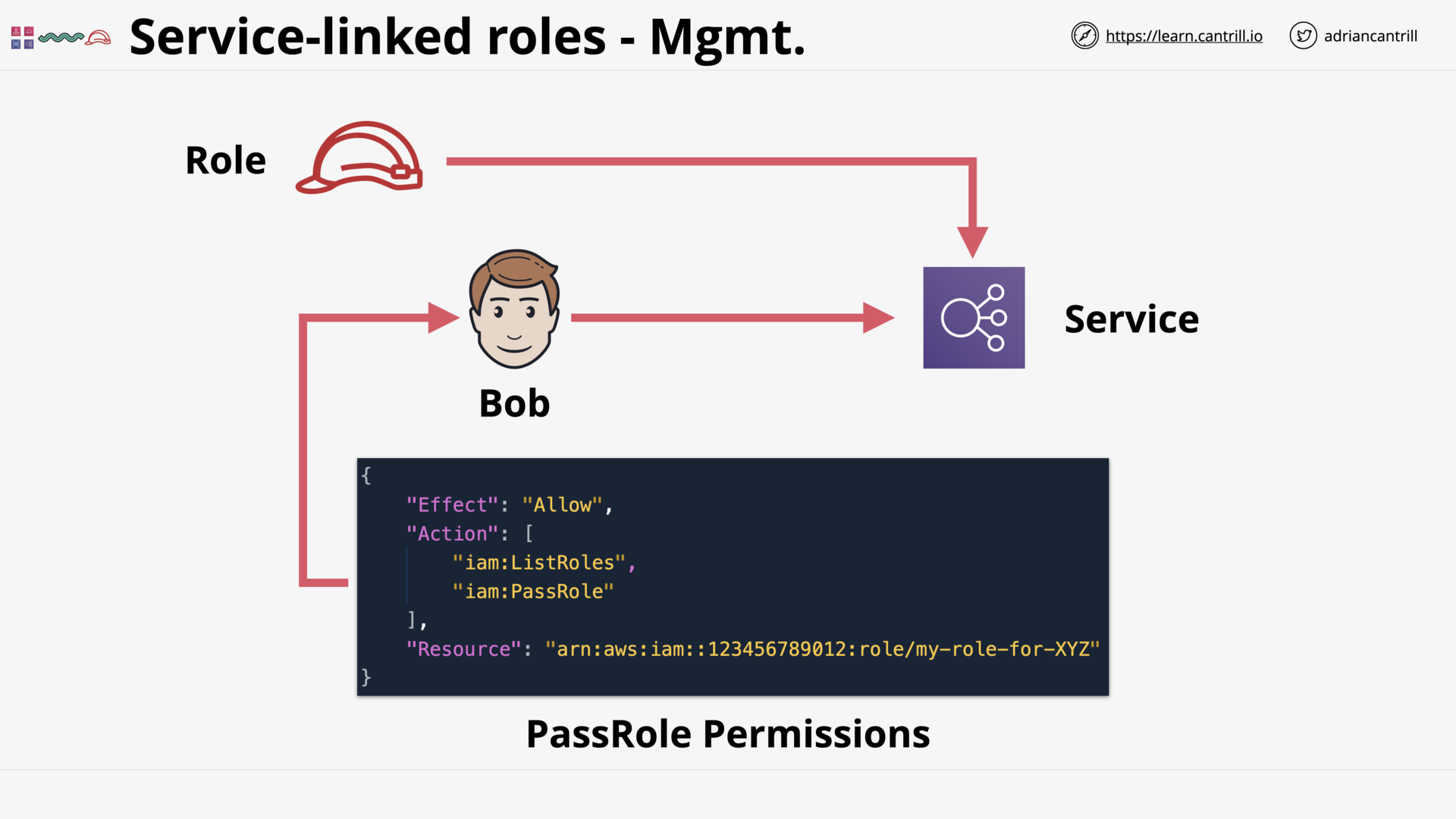 Pass an existing role to the service
Pass an existing role to the service
[ASSOCIATE] AWS Organizations (12:56)
 “Standard” AWS Account
“Standard” AWS Account
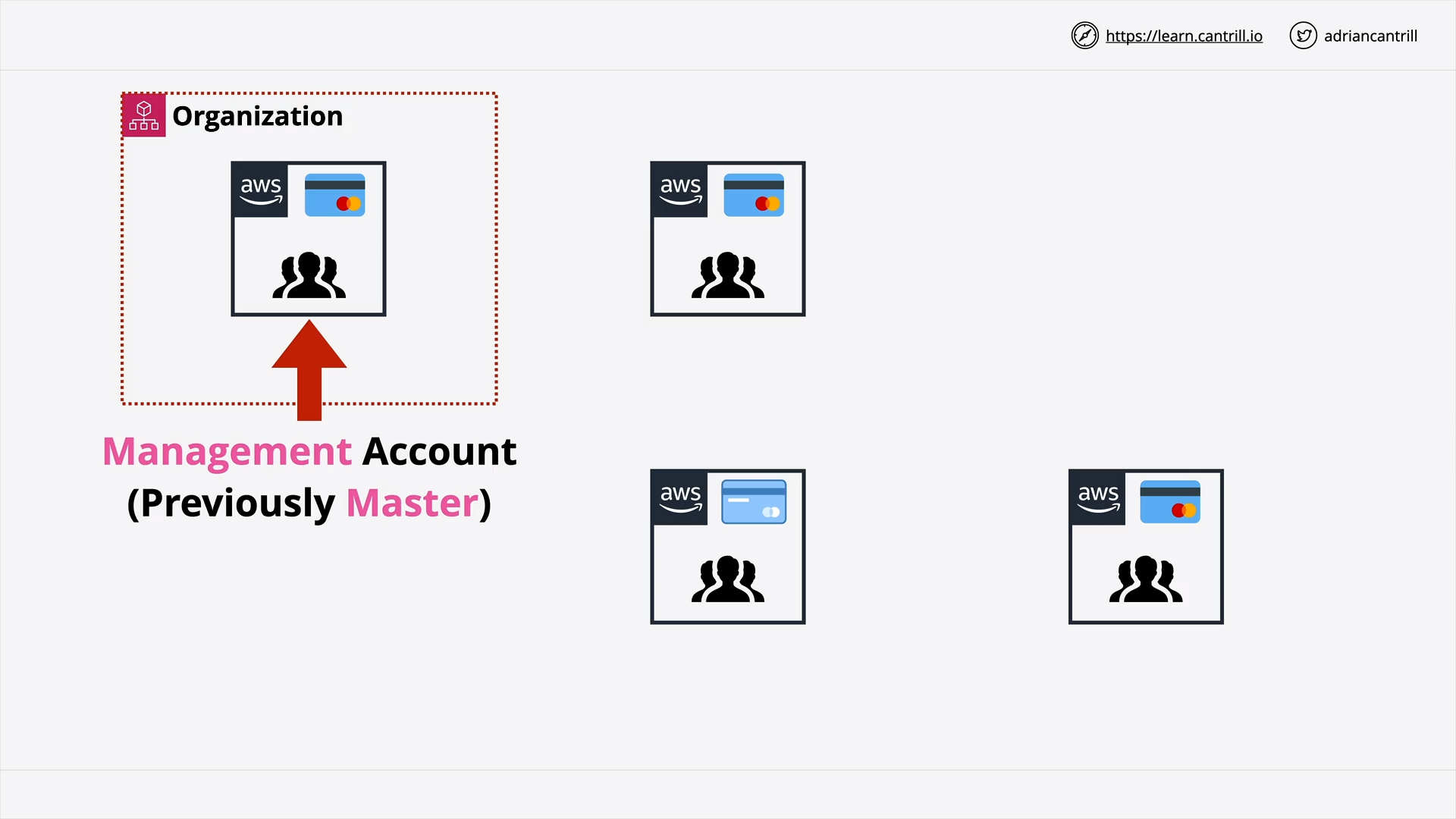 Management/Master Account
Management/Master Account
aws organization and management account, which come first?
- First, you use a standard account to create an AWS Organization
- Then that standard account become the management account of the AWS Organization.
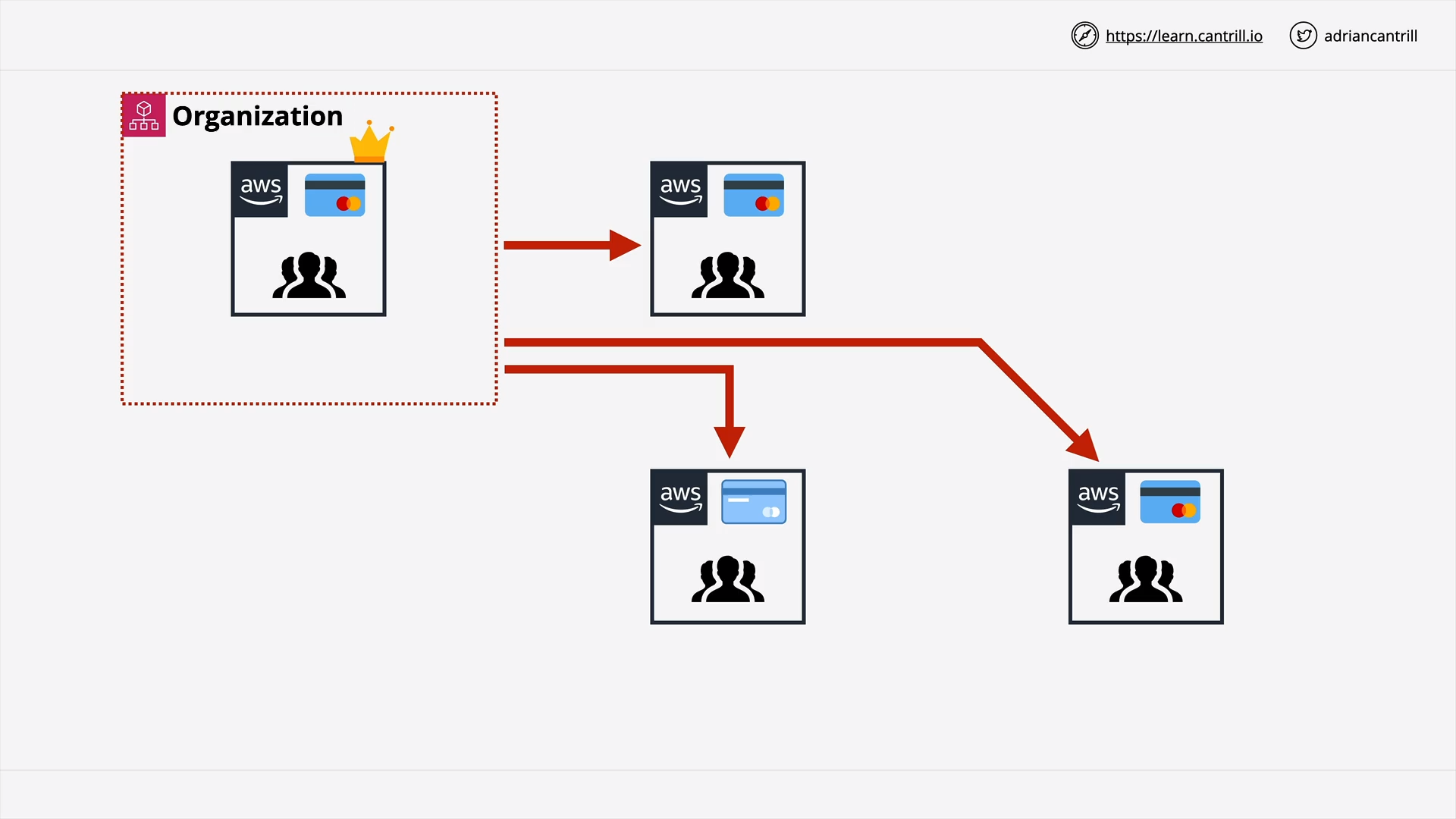 Invite existed standard accounts to an AWS Organization
Invite existed standard accounts to an AWS Organization
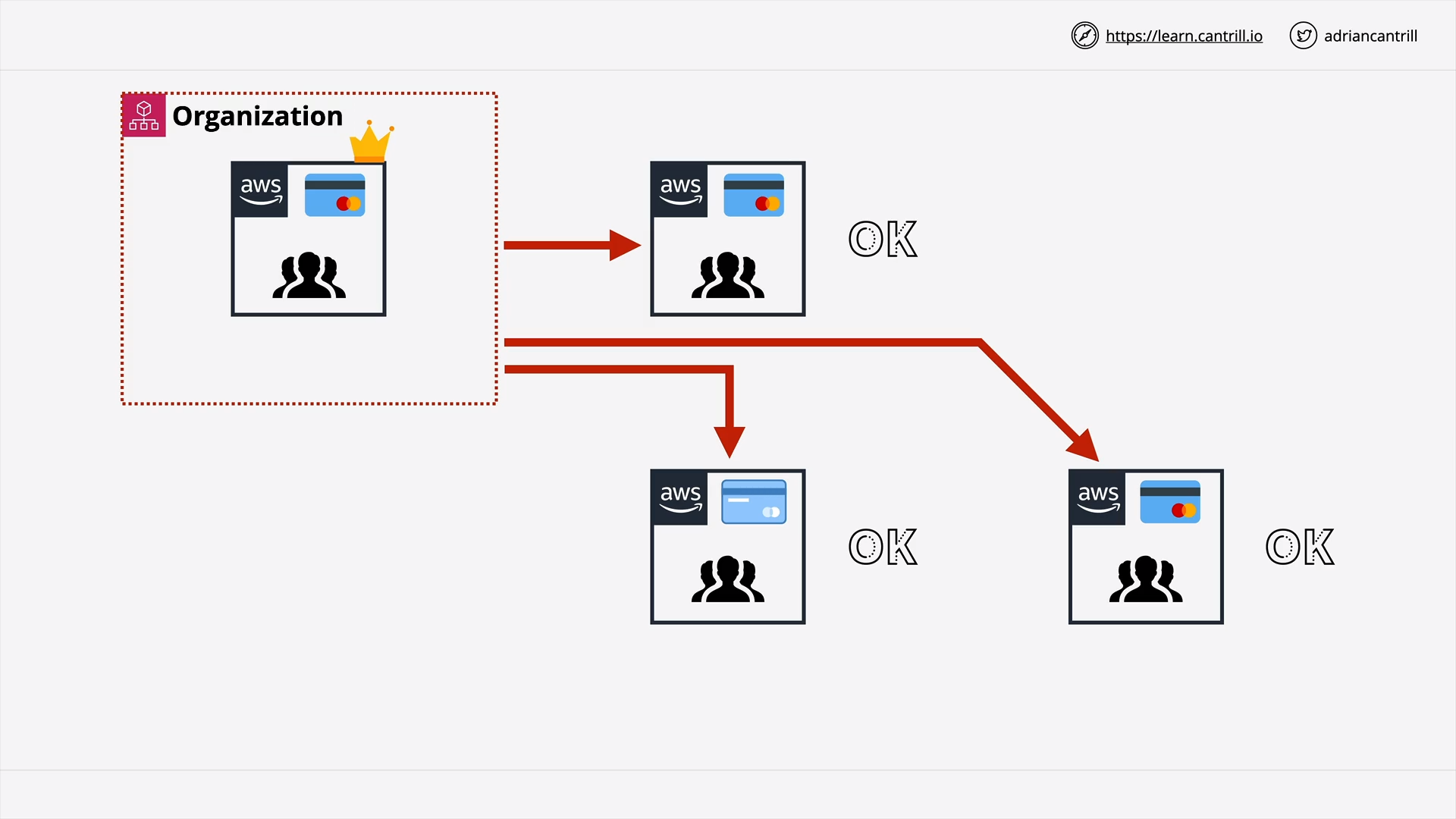 Accepting invitations to become member of an AWS Organization
Accepting invitations to become member of an AWS Organization
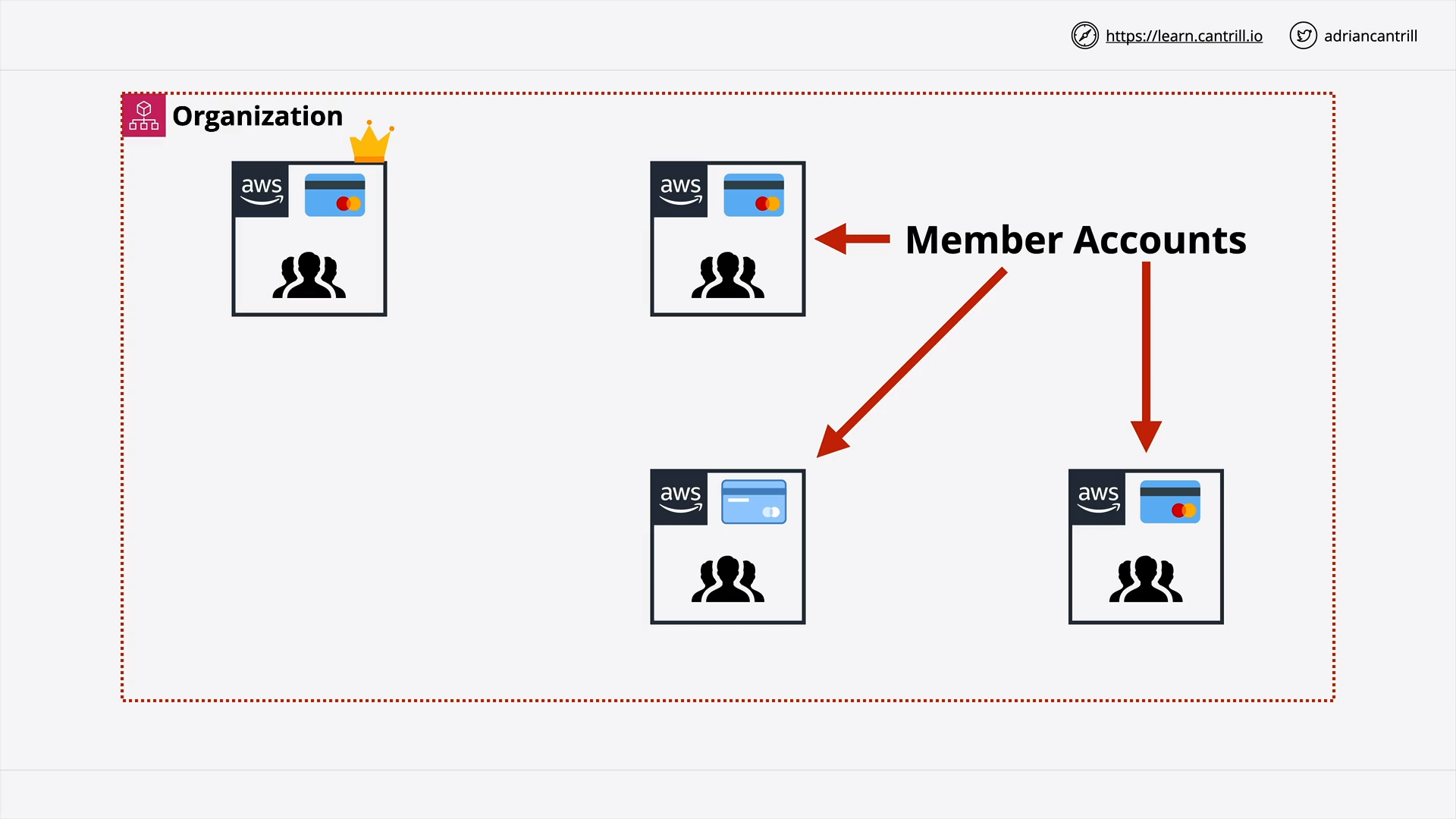 Member Accounts
Member Accounts
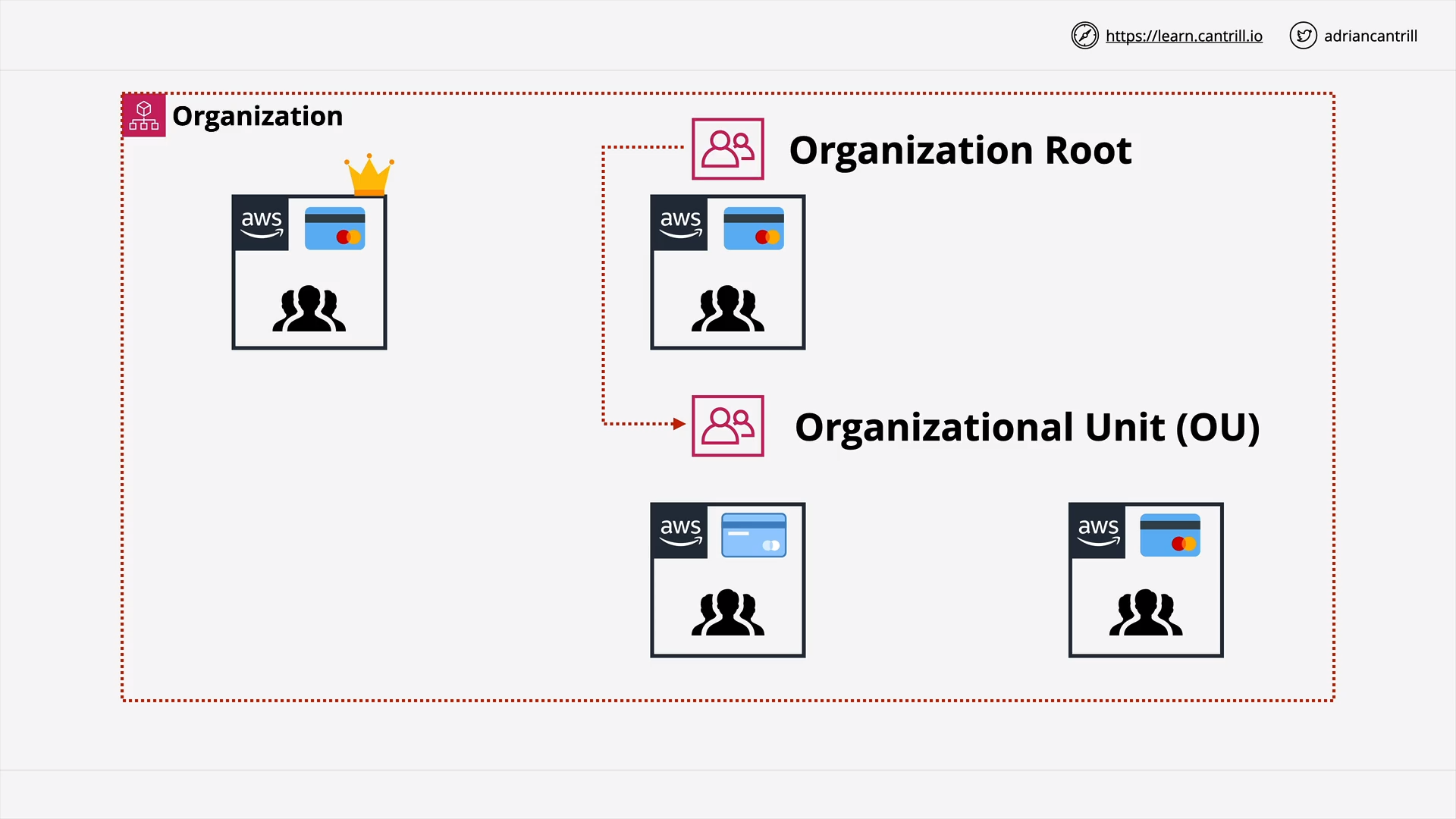 Organization Root & Organization Unit (OU)
Organization Root & Organization Unit (OU)
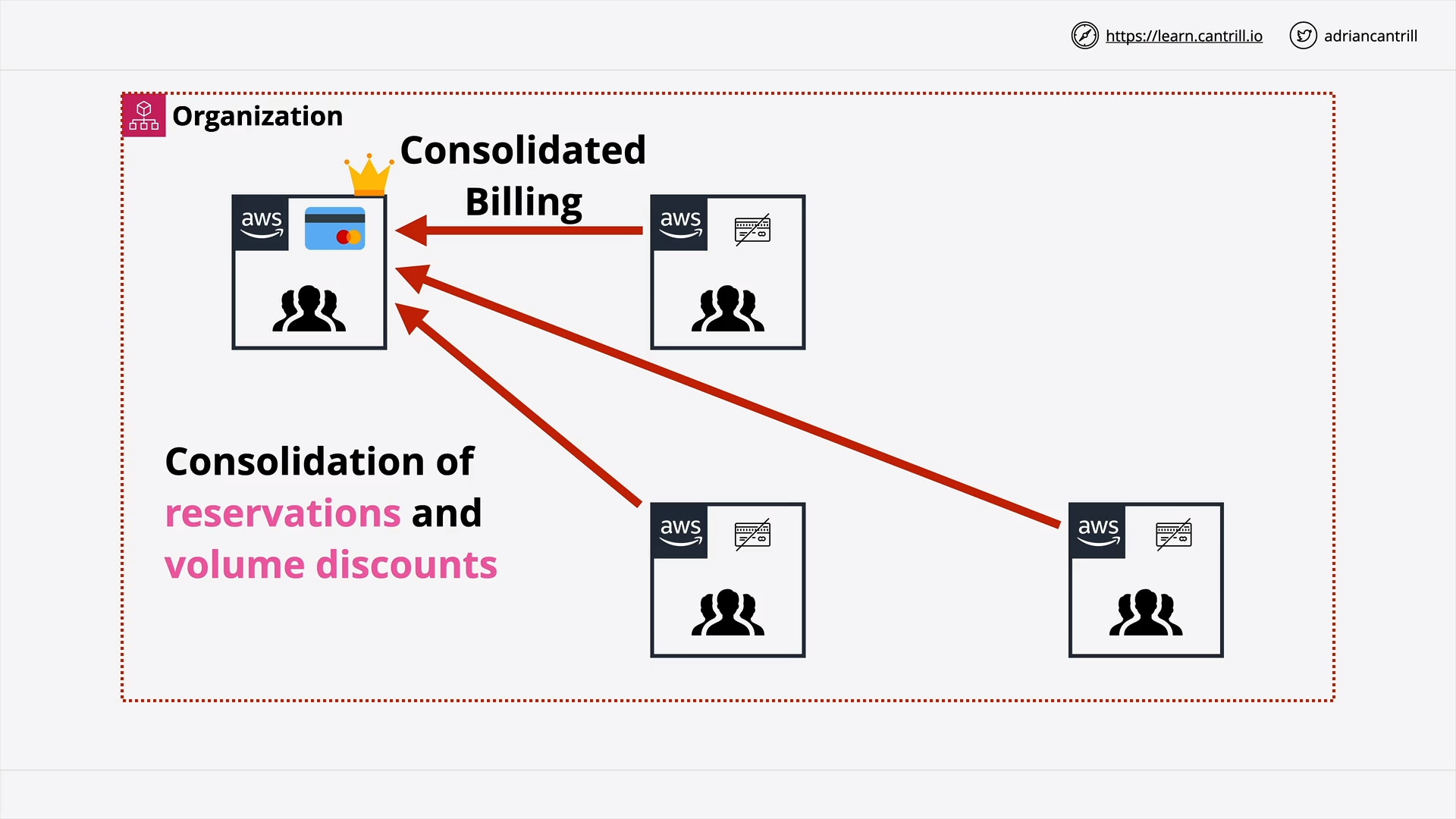 Consolidated Billing
Consolidated Billing
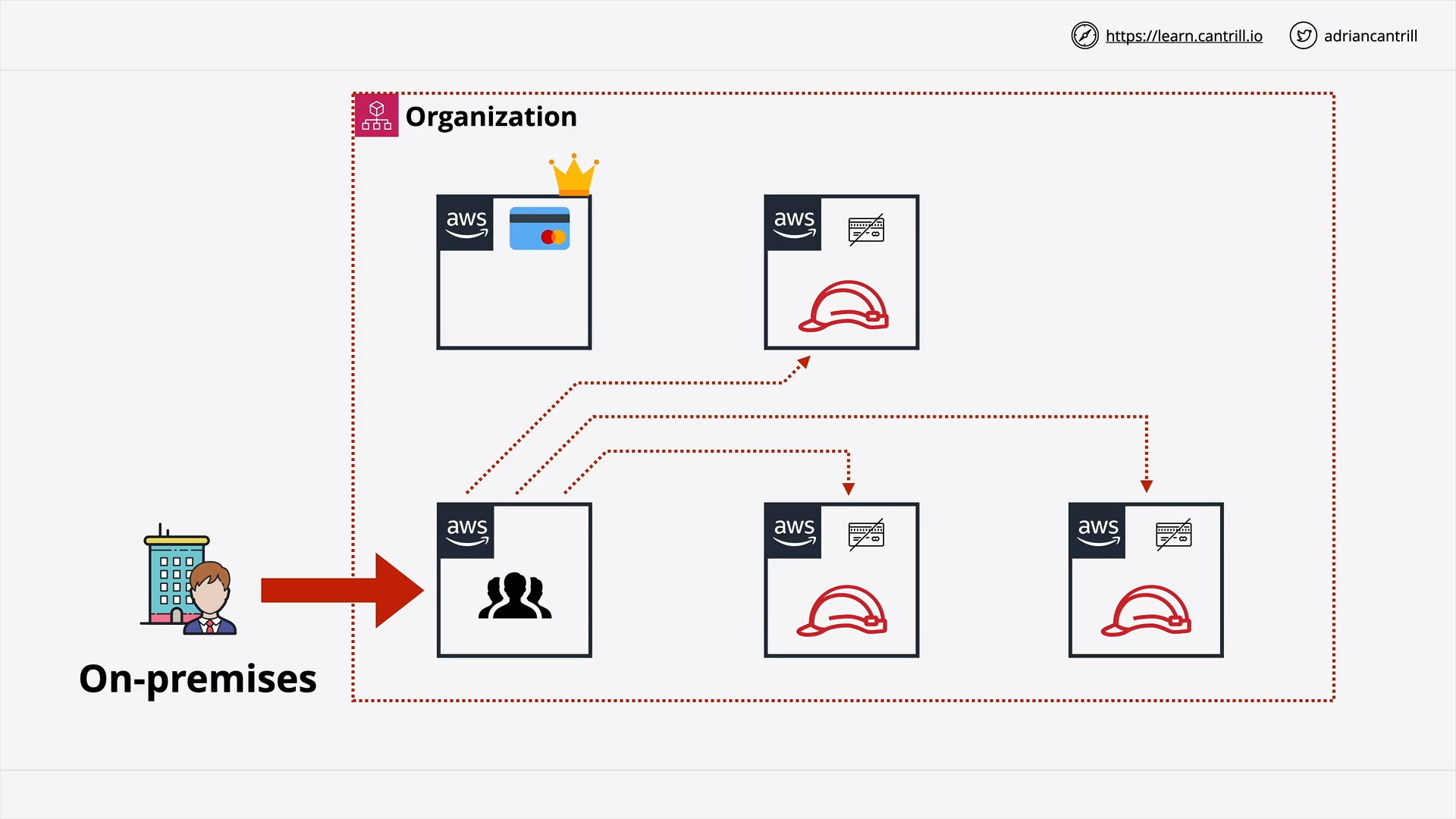 Role Switching
Role Switching
[ALL, DEMO] AWS Organizations (19:48)
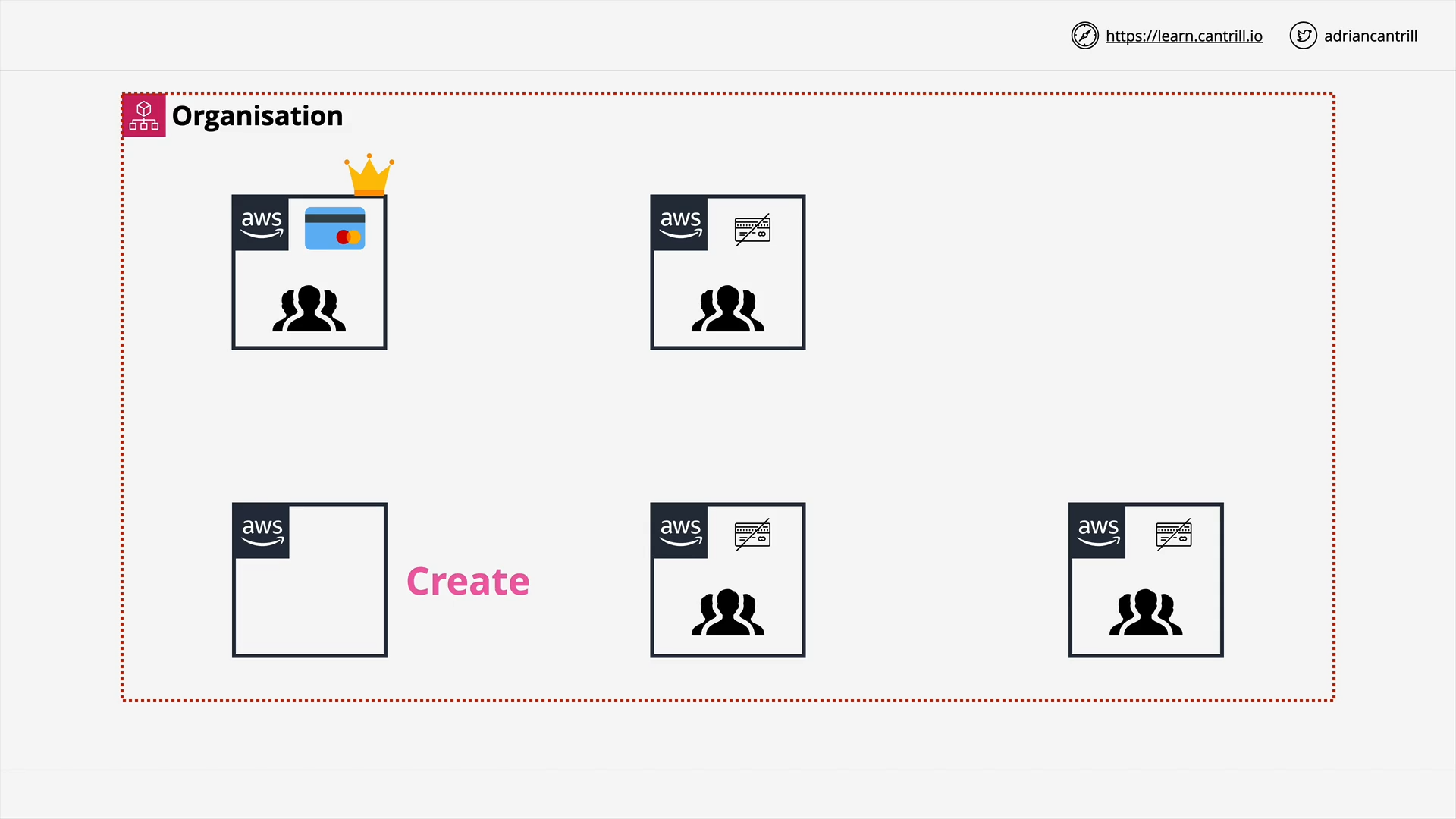 Create an account in your organization
Create an account in your organization
how to access an aws account in an aws organization?
- Using username/password of that AWS account to access that AWS account using its root user
- Using another account to switch role to that account’s IAM role
OrganizationAccountAccessRole - Using the AWS access portal with corporation credentials (Google, Facebook…)
[ASSOCIATE] Service Control Policies (SCPs) (12:44)
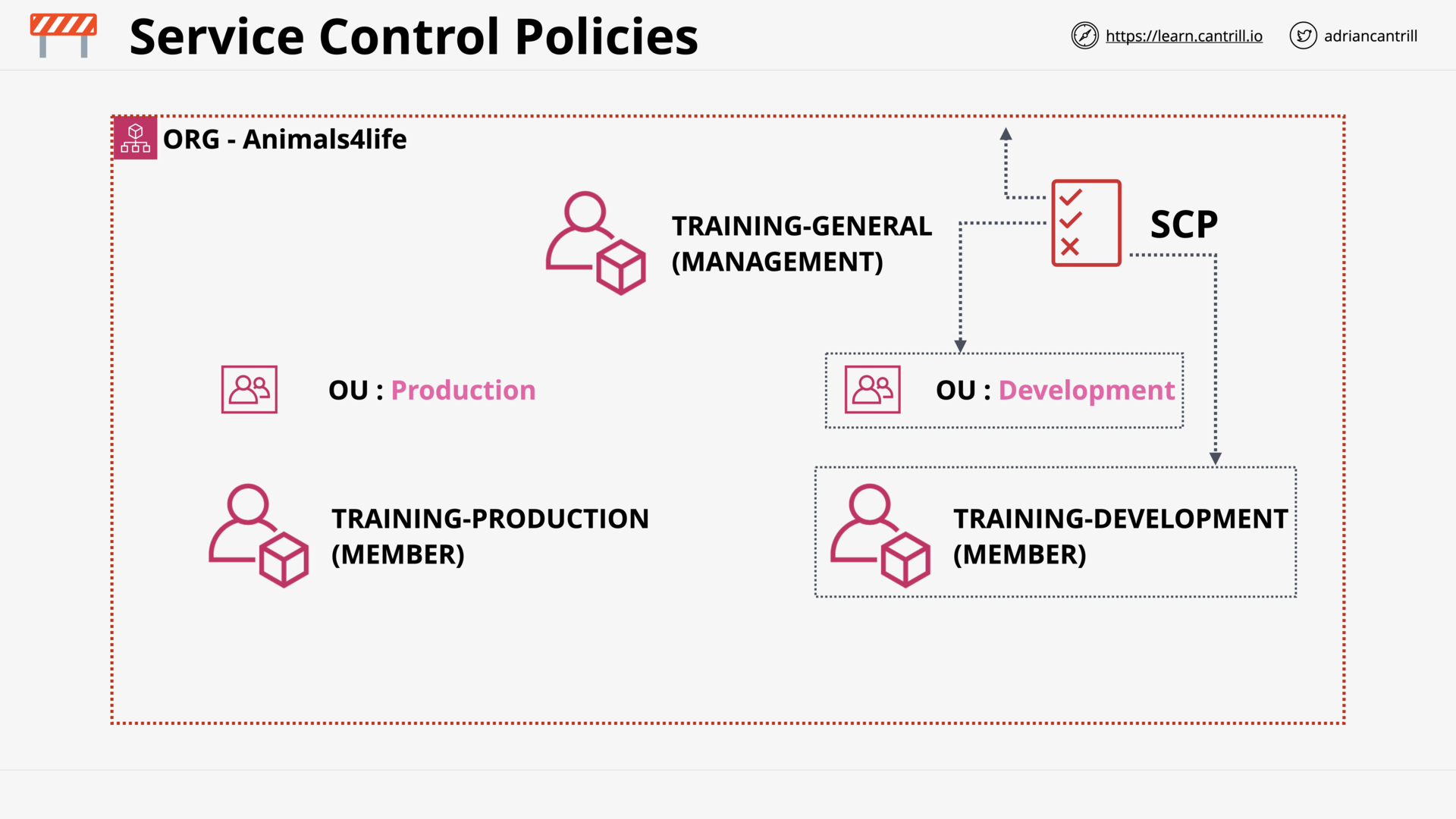 Service Control Policies (SCP)
Service Control Policies (SCP)
_.png) SCP controls account permissions in an organization
SCP controls account permissions in an organization
what does service control policies (scp) do?
SCP
-
restricts permissions for
- IAM users
- IAM roles
- including root user
in member accounts.
-
(do NOT grant permissions)
_.png) SCP - Deny List
SCP - Deny List
sgp - deny list strategy
With deny list strategy, all permissions are allowed unless explicitly denied.
This is the default behavior of AWS Organizations.
- By default, AWS Organizations attaches an AWS managed policy called
FullAWSAccessto all roots, OUs, and accounts. - You
- leave the default
FullAWSAccesspolicy in place (that allow “all”). - then attach additional policies that explicitly deny access to the unwanted services and actions.
- leave the default
_.png) SCP - Allow List
SCP - Allow List
sgp - allow list strategy
With allow list strategy, all permissions are denied unless explicitly allowed.
- By default, AWS Organizations attaches an AWS managed policy called
FullAWSAccessto all roots, OUs, and accounts. - You
- remove the default
FullAWSAccesspolicy - then attach additional policies that explicitly allow access to the wanted services and actions
- remove the default
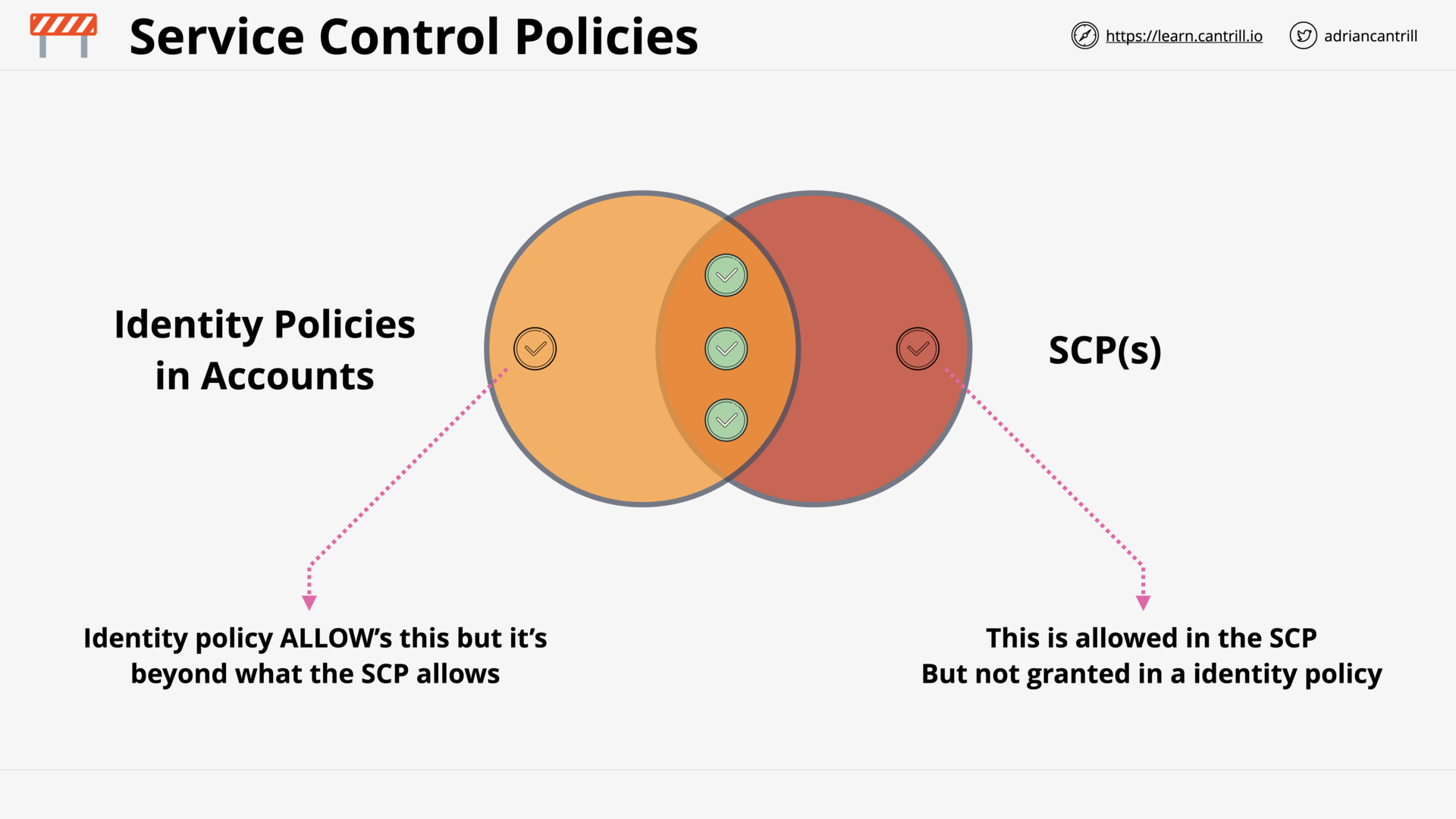 Identity Policies and SCPs
Identity Policies and SCPs
can scp restrict management account?
SCPs don’t affect users or roles in the management account. They affect only the member accounts in your organization.
can scp restrict root user?
SCP can un-directly control the member account’s root user (by control the account’s permission)
[ALL, DEMO] Using Service Control Policies (16:45)
[ASSOCIATE] CloudWatch Logs (7:16)
 CloudWatch Logs - Basic
CloudWatch Logs - Basic
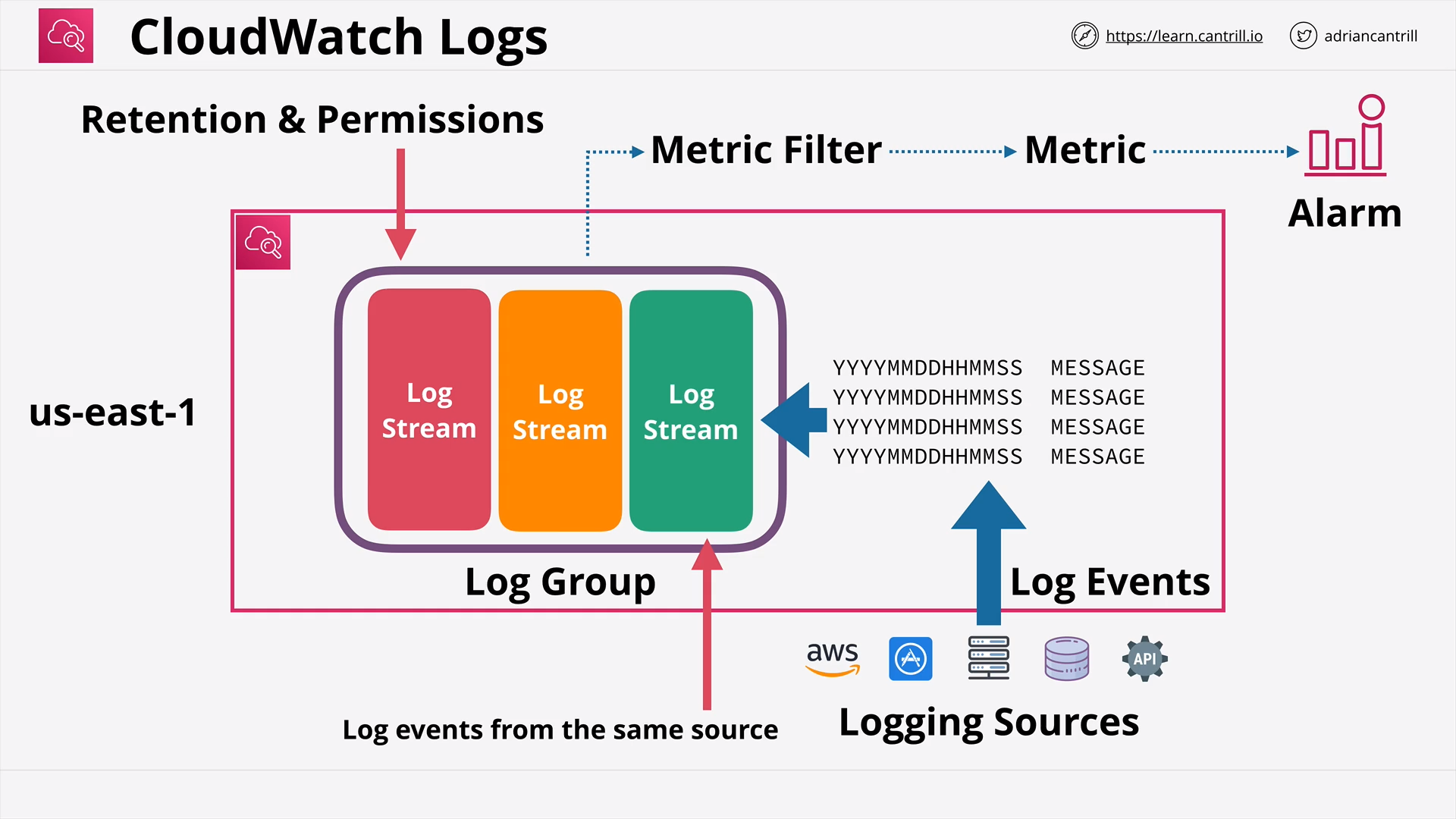
CloudWatch Logs - Architecture
what is log event?
what is log stream?
what is log group?
[ASSOCIATE] CloudTrail (11:40)
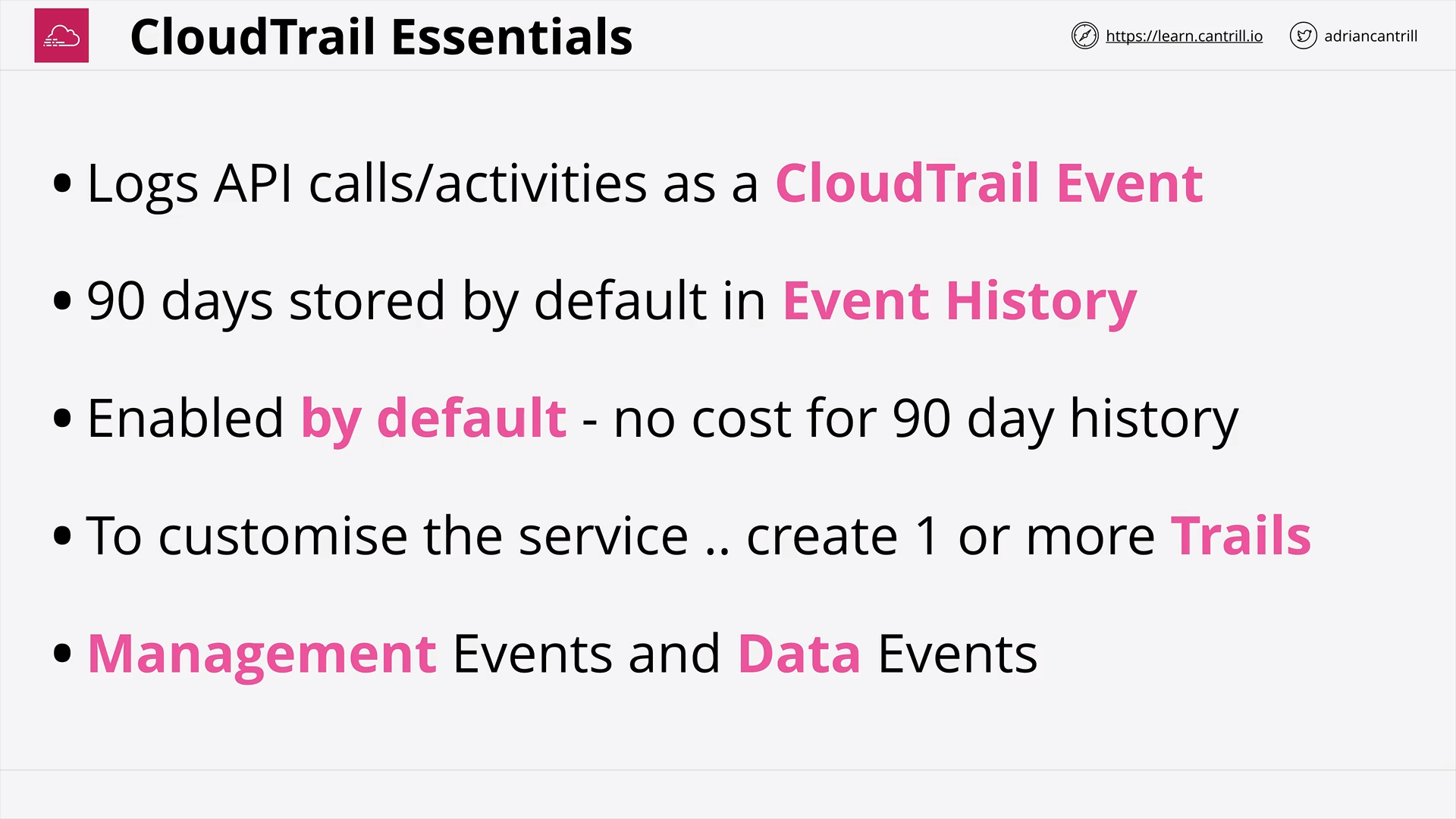
what is cloudtrail event/trail?
how long is the default cloudtrail history?
in cloudtrail, what are management events / data events?
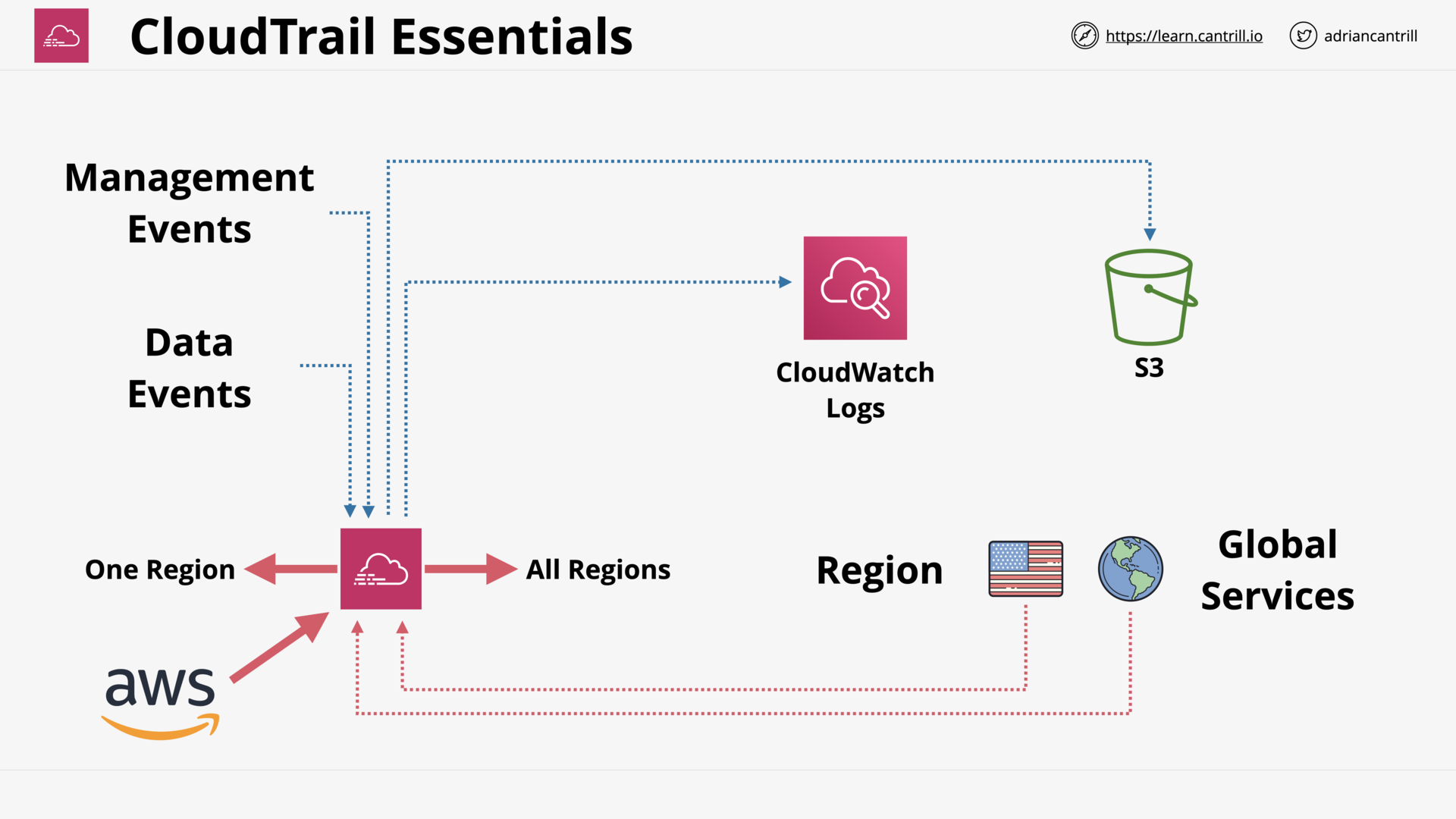
how to implement a central log store for aws organization?
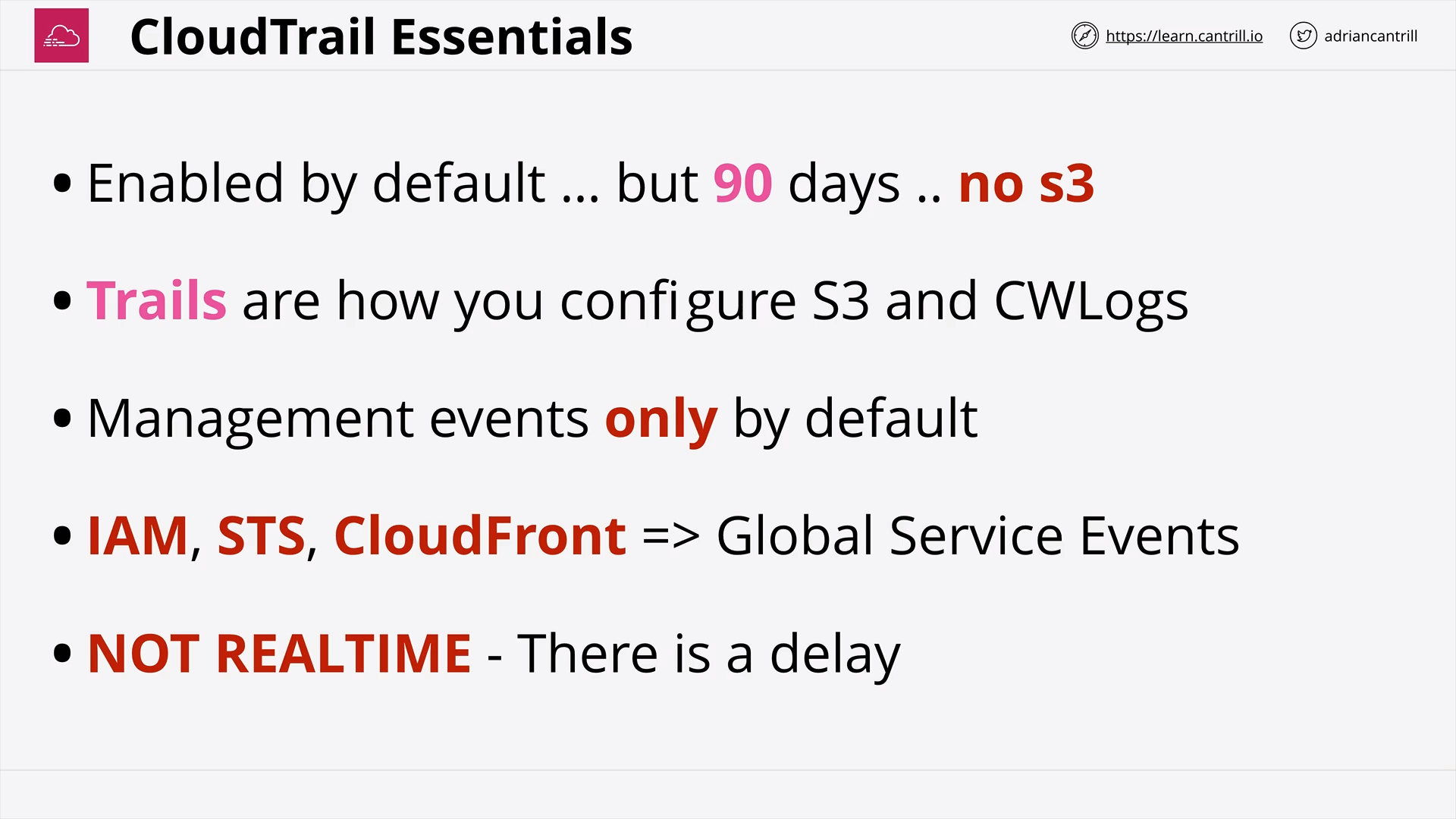
is cloudtrail realtime?
[ALL, DEMO] Implementing an Organizational Trail (18:23)
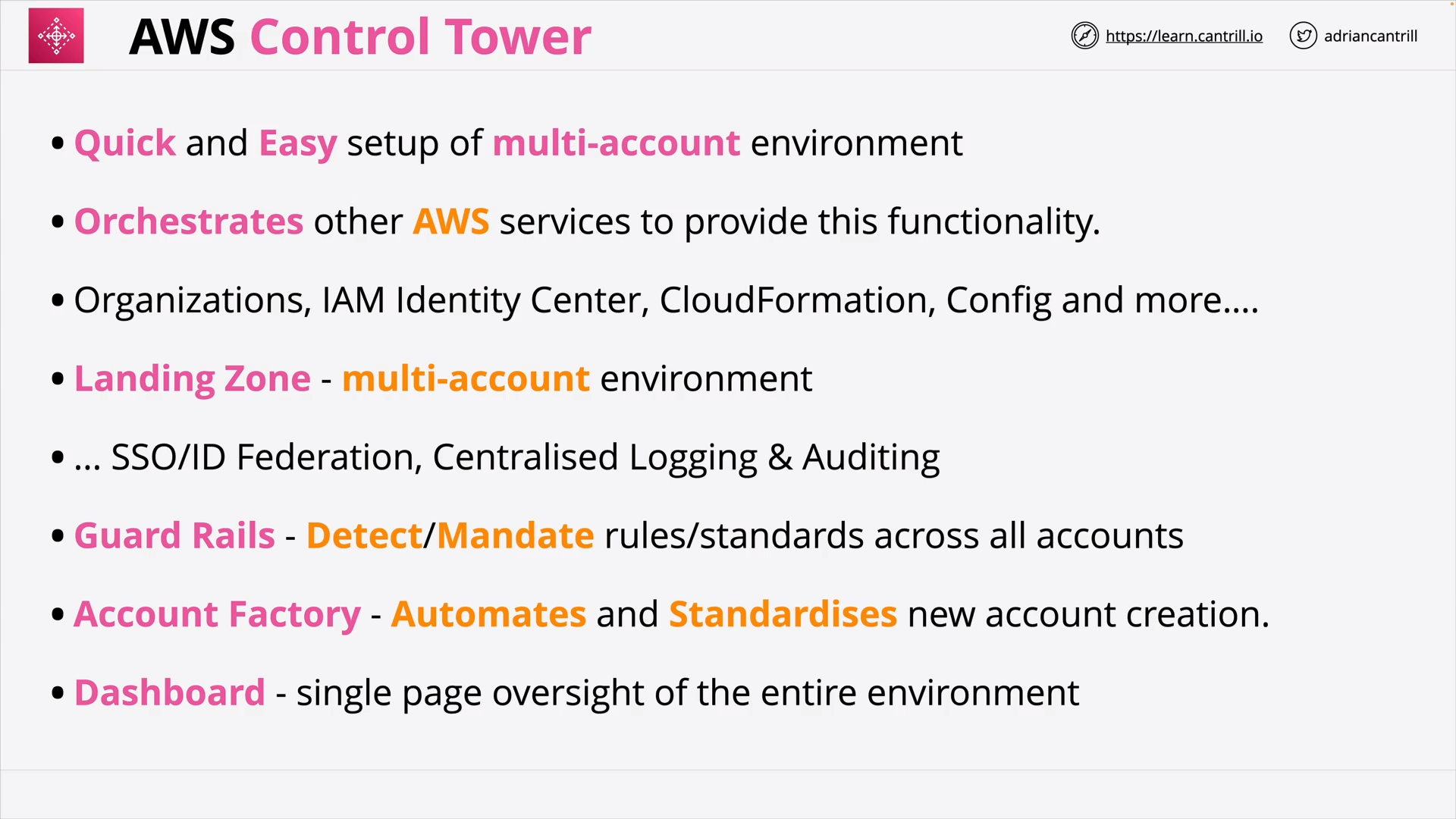
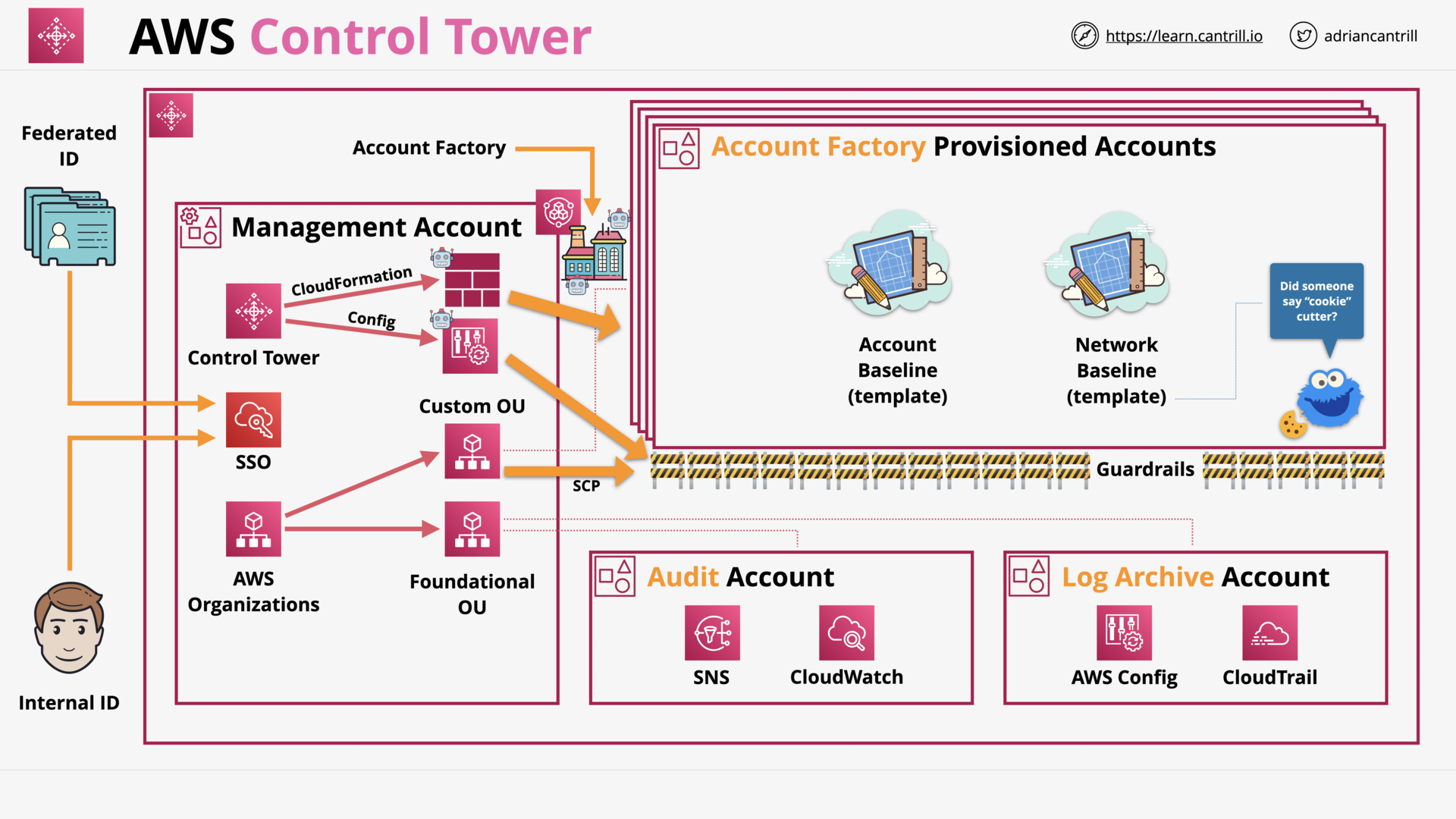
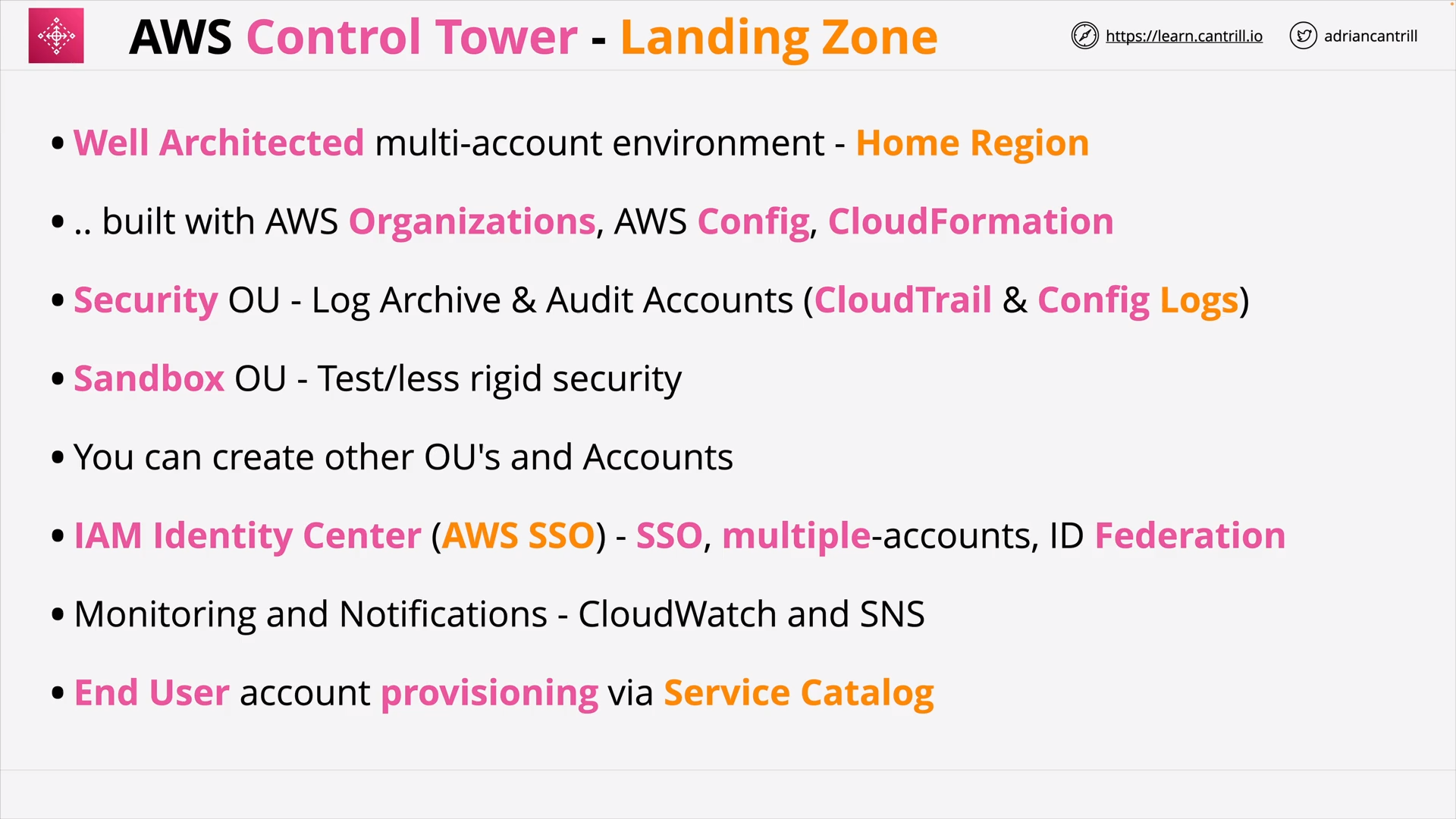
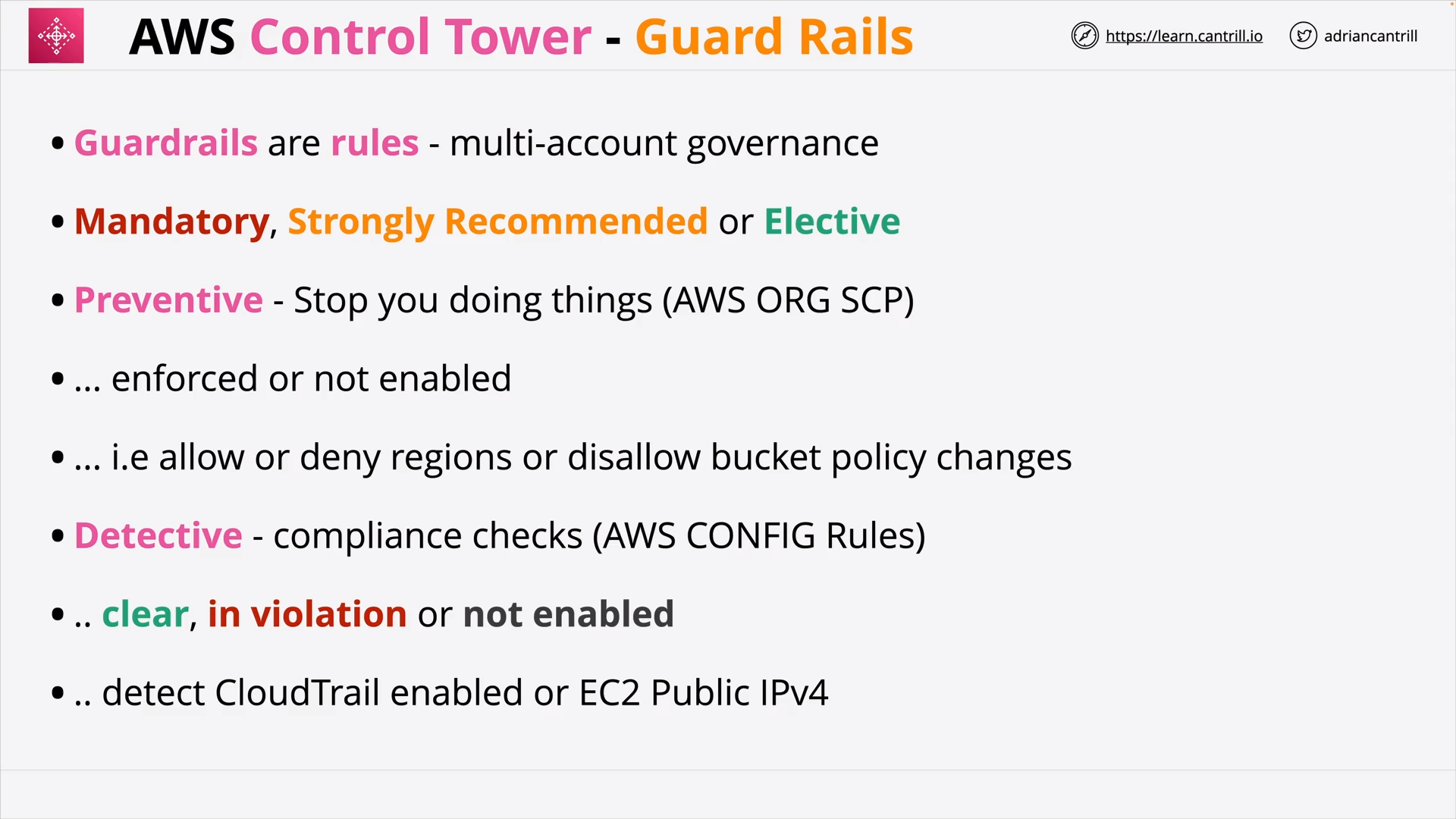
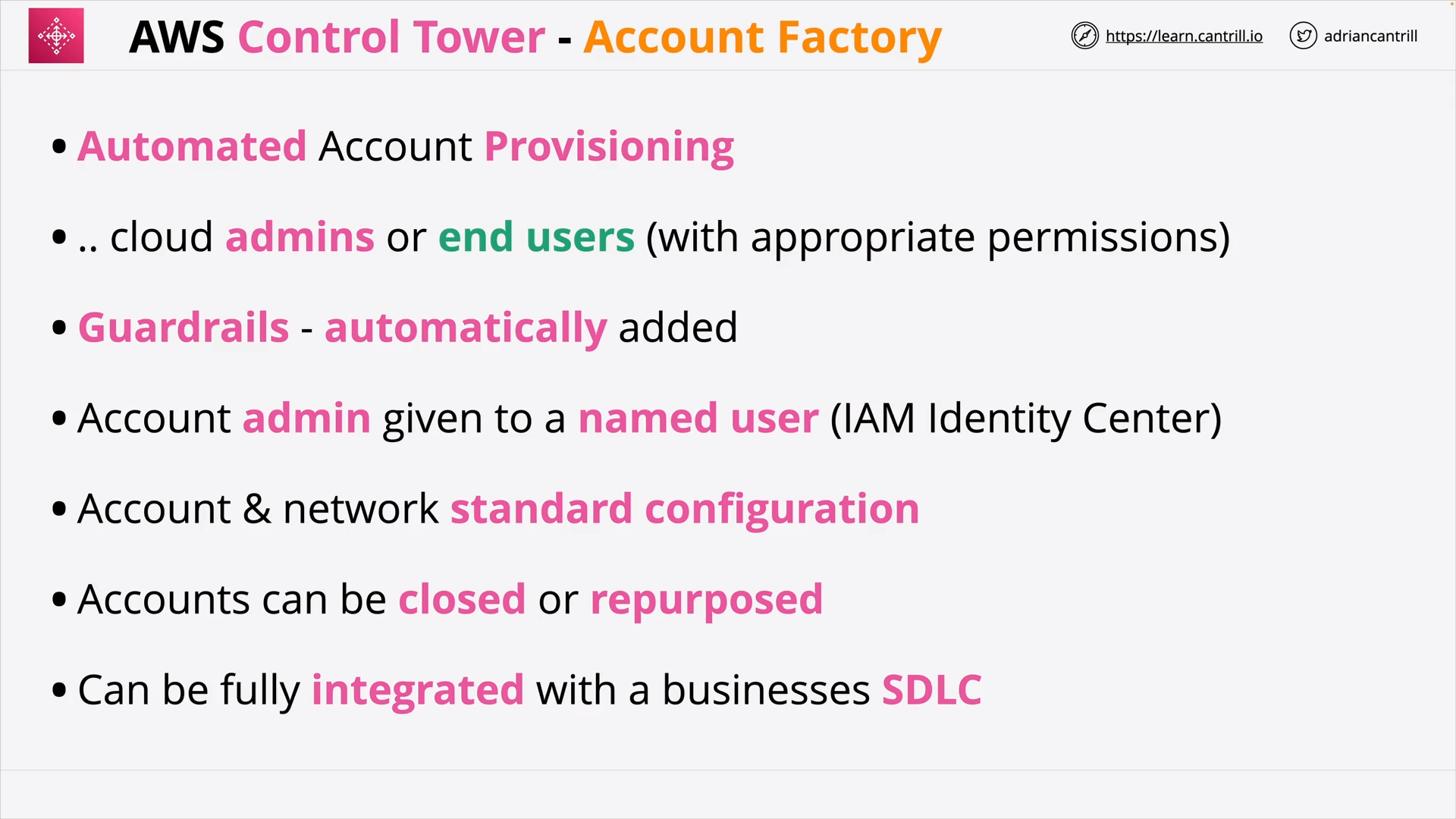
AWS Control Tower 101 (15:42)