NETWORKING AND TECHNICAL FUNDAMENTALS
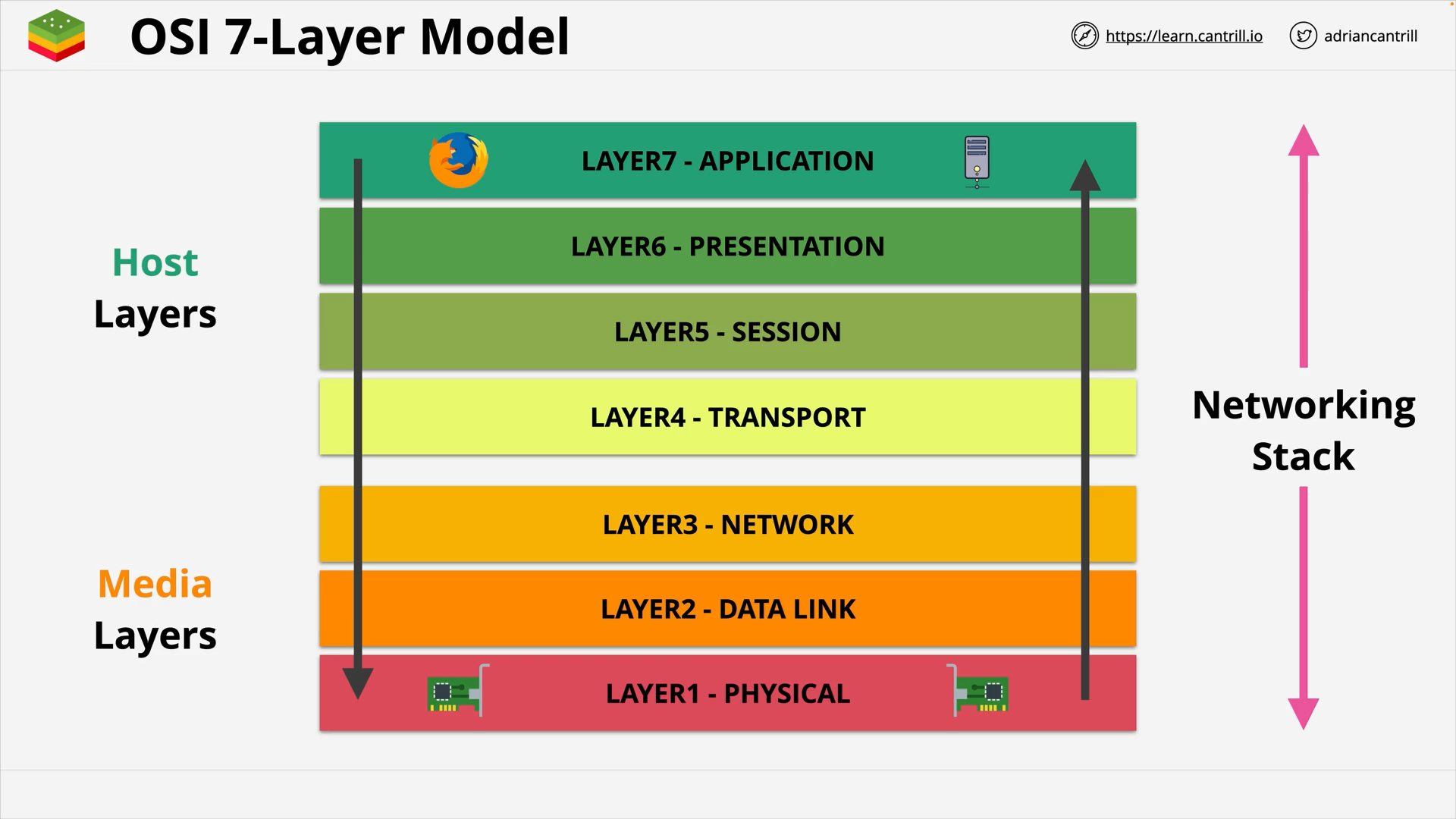
OSI 7-Layer Networking Model
OSI Model Introduction (4:46)

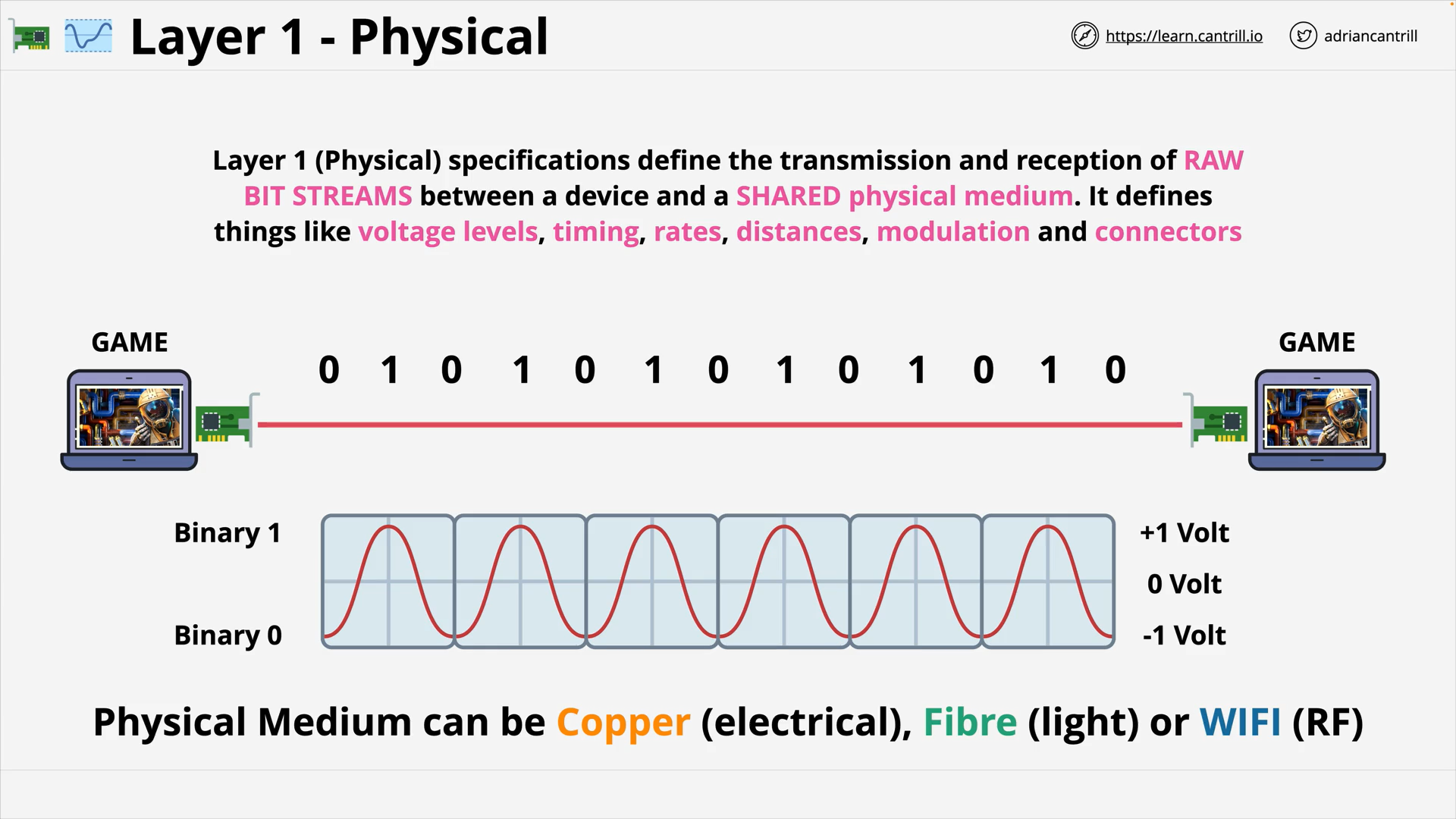
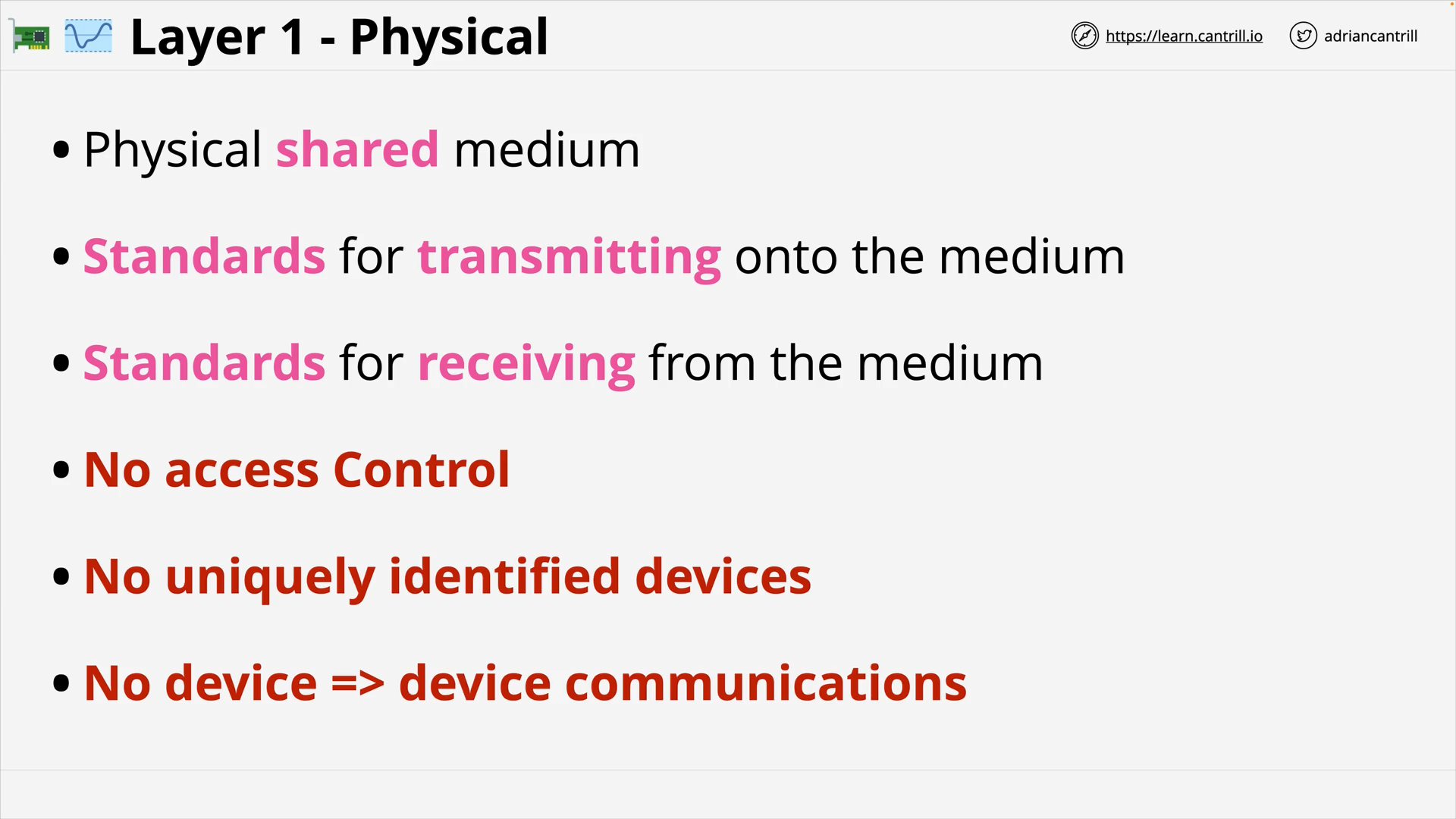
Layer 1 - Physical (10:00)
Layer 2 - DataLink - PART1 (8:47)
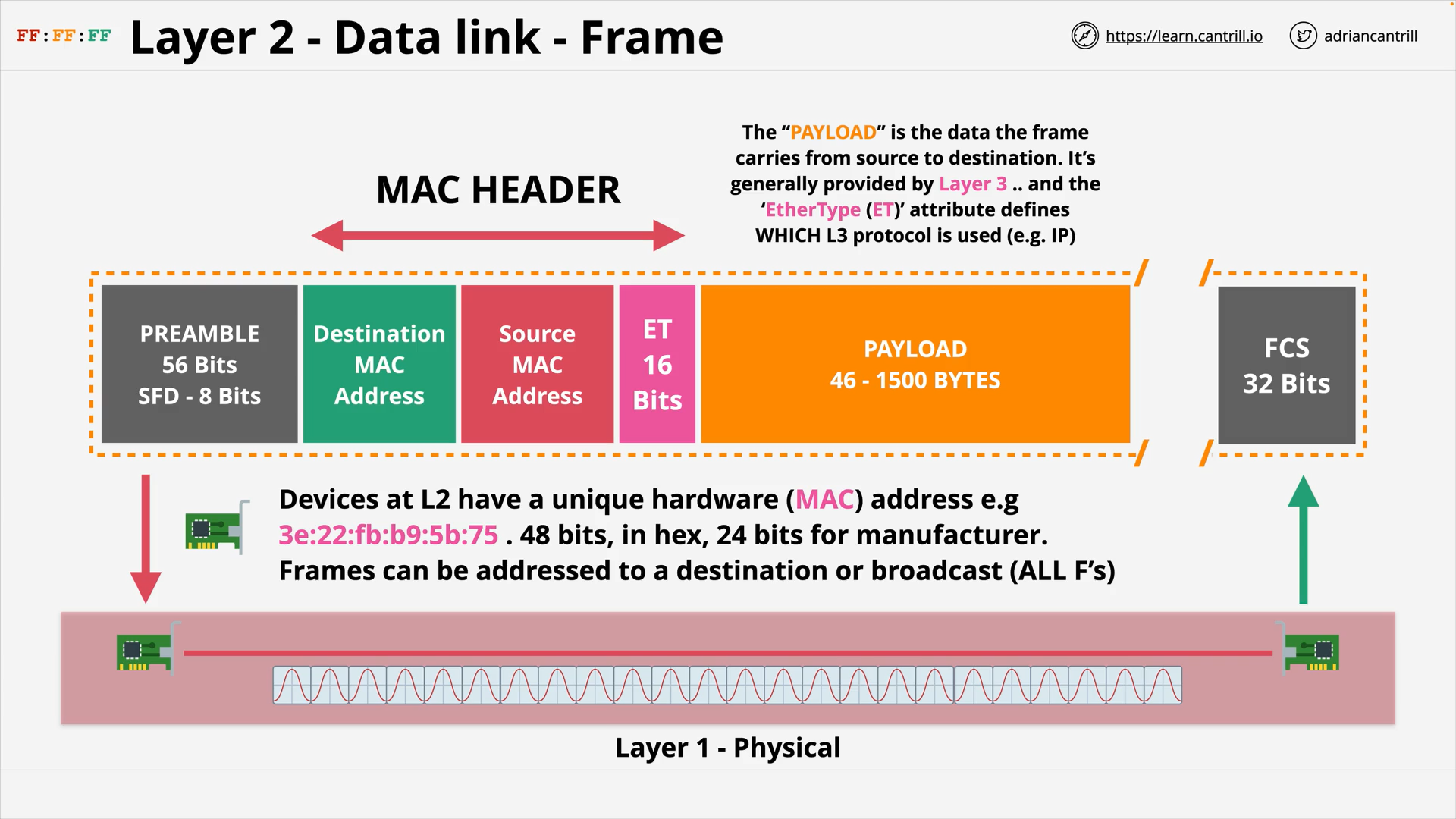
**mac vs mac address**?
-
MAC: Medium Access Control, also called Media Access Control
-
MAC Address: Medium Access Control Address,
- also known as hardware address, or physical address
- a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment
Layer 2 - DataLink - PART2 (14:24)
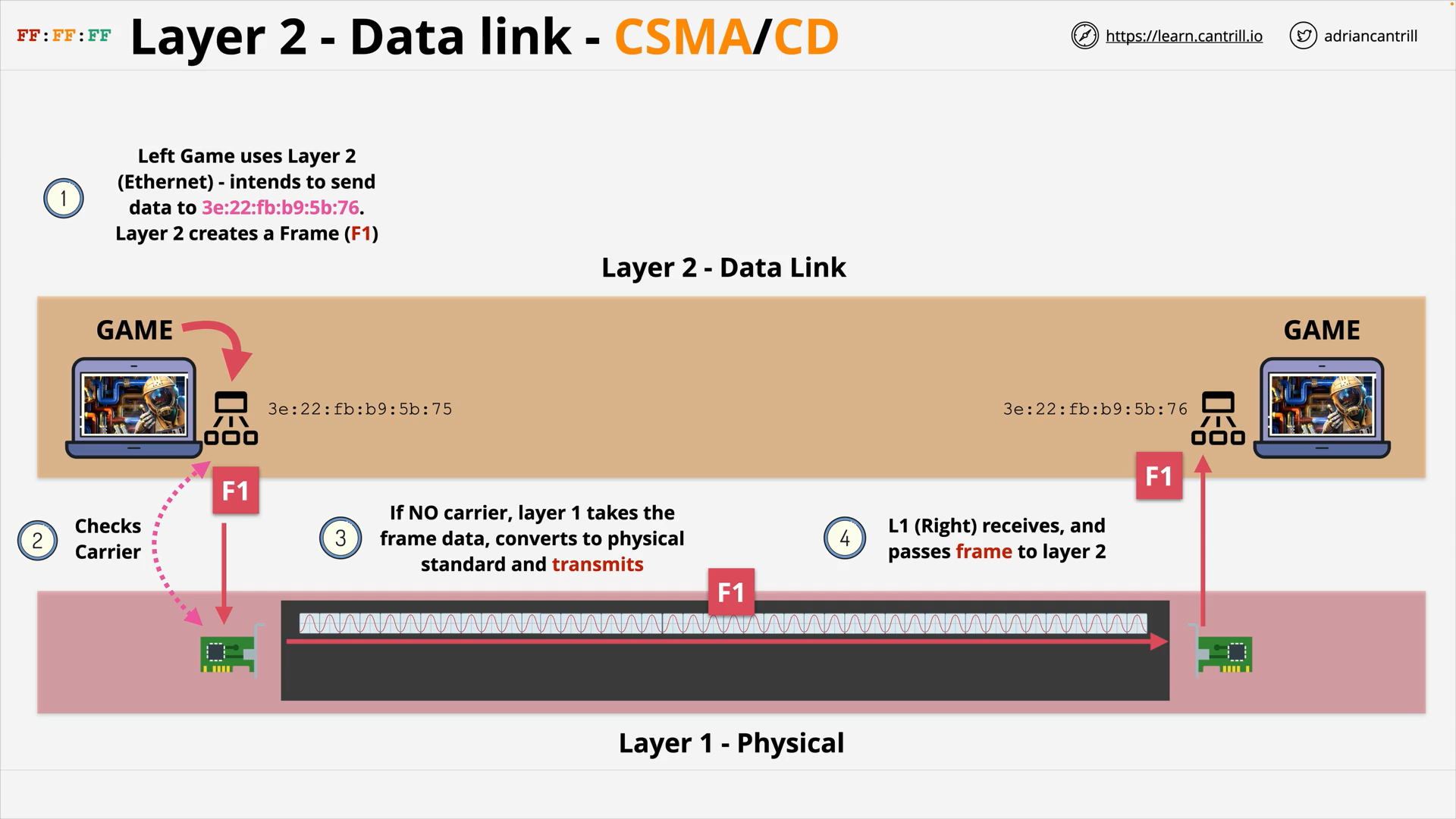 Left game sends Frame F1 to Right game
Left game sends Frame F1 to Right game
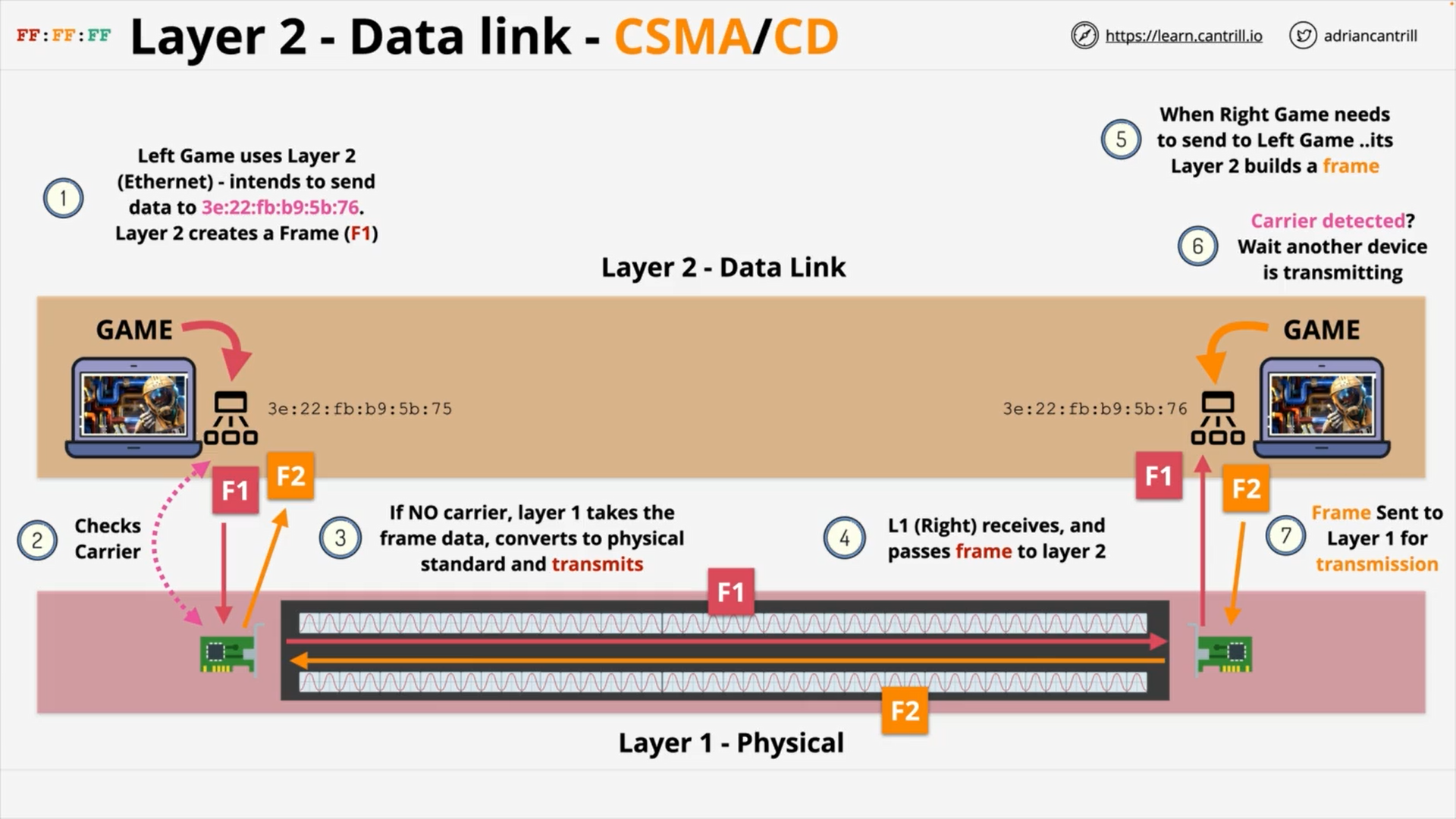 Right game sends Frame F2 to Left game - Carrier Sense Multiple Access (CSMA)
Right game sends Frame F2 to Left game - Carrier Sense Multiple Access (CSMA)
layers are independent
Conceptually, left L2 is talking to right L2.
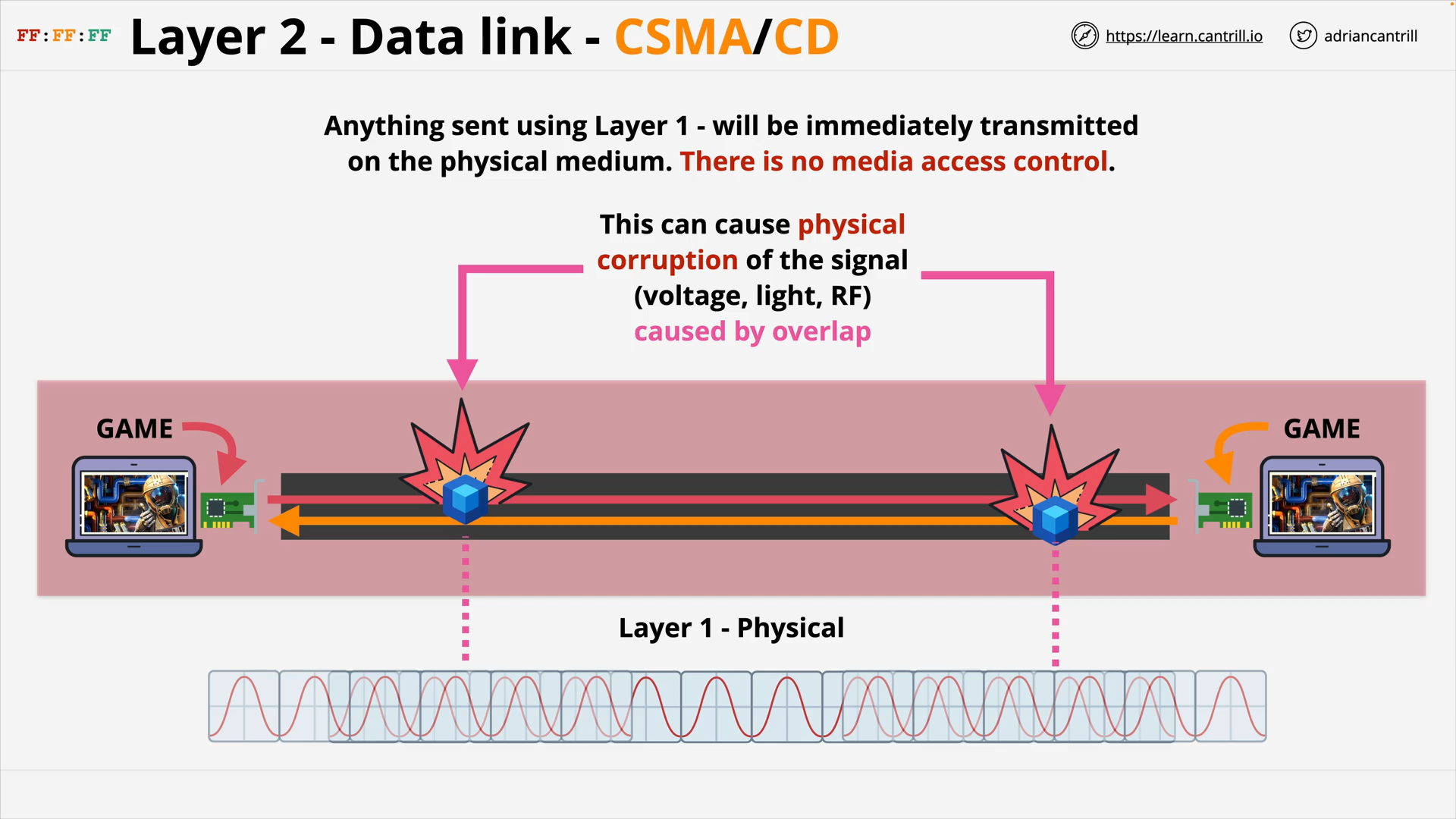
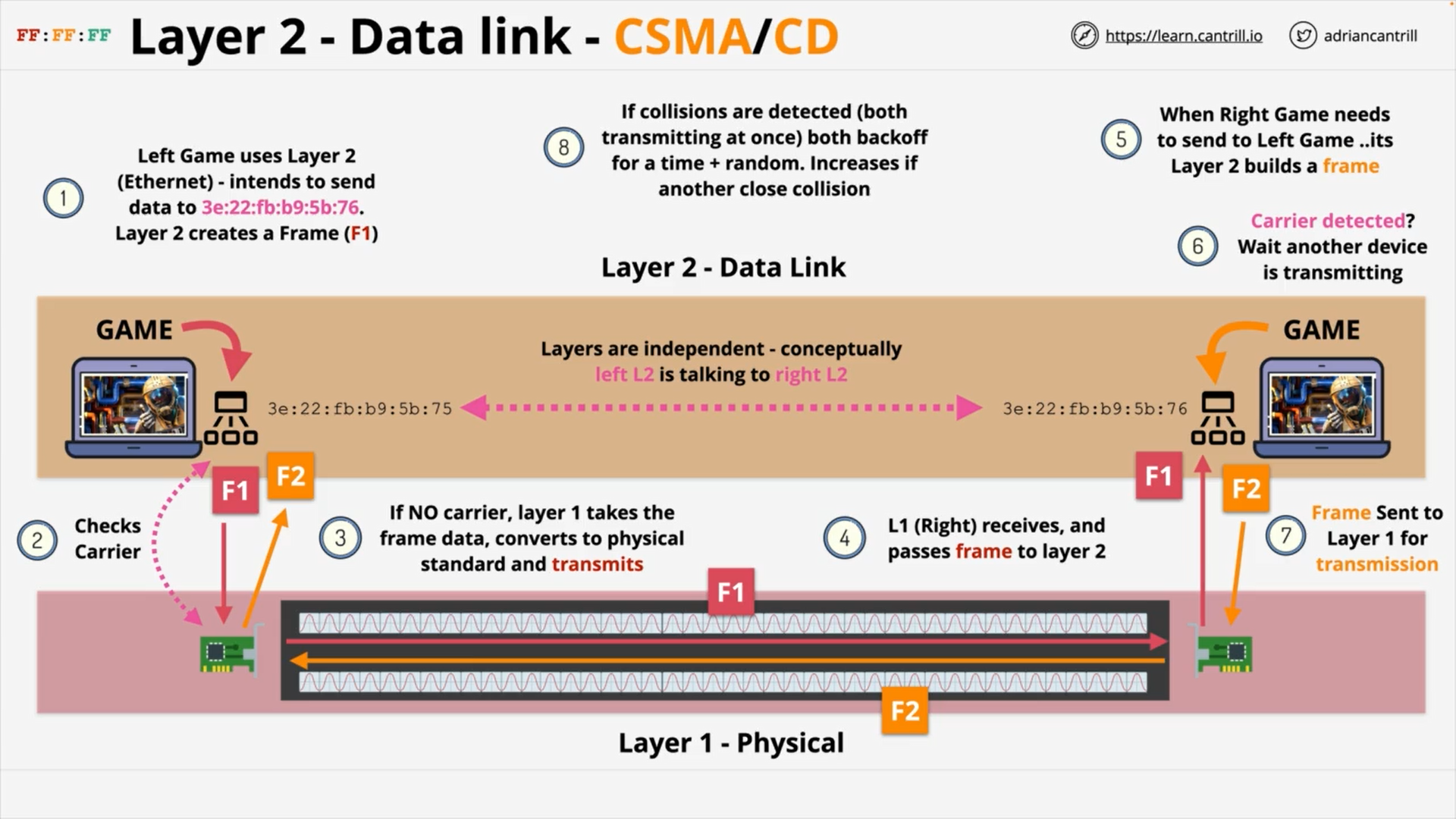 Collision Detection (CD)
Collision Detection (CD)
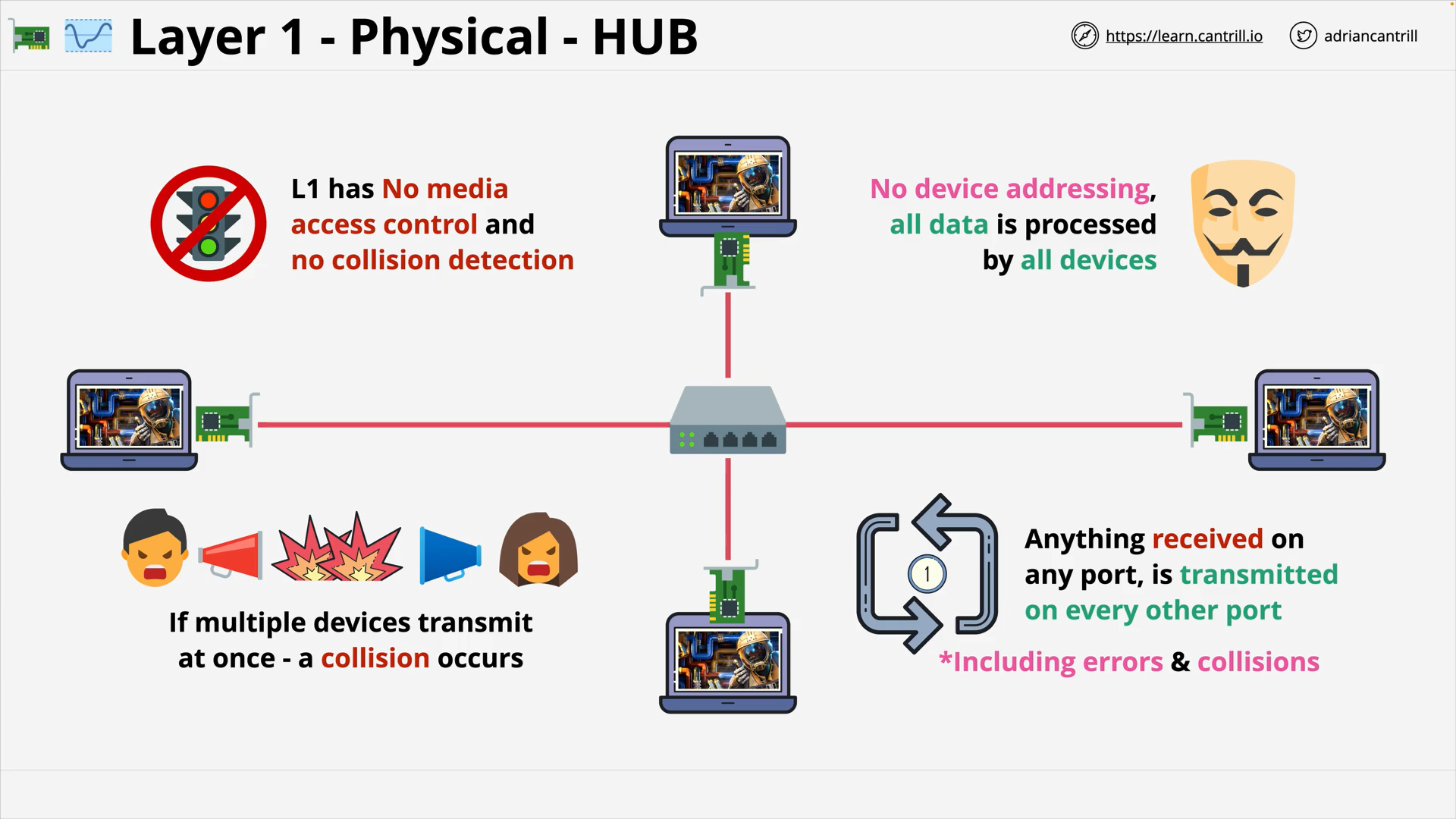
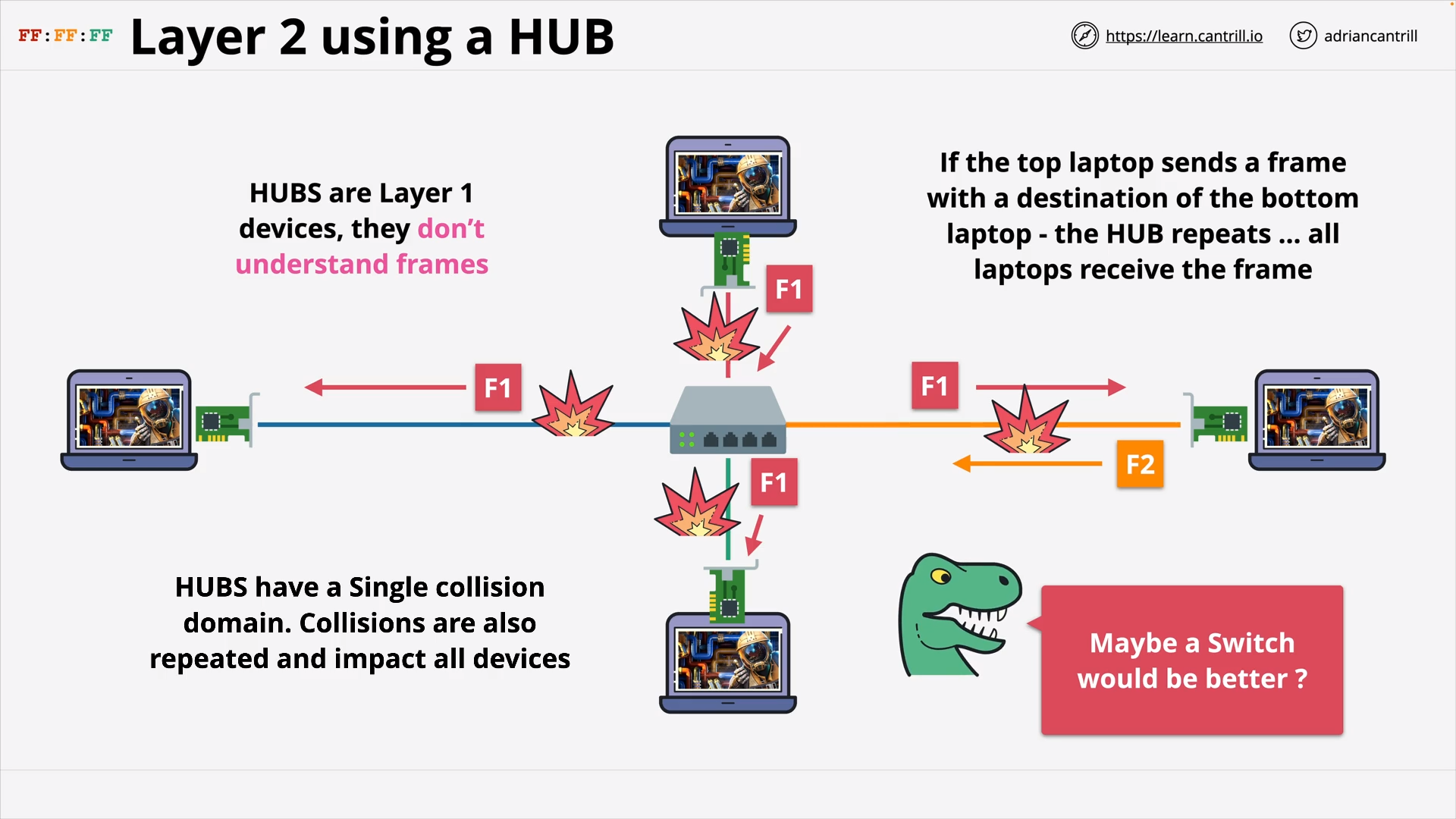 OSI Layer 2 - Try using a Hub
OSI Layer 2 - Try using a Hub
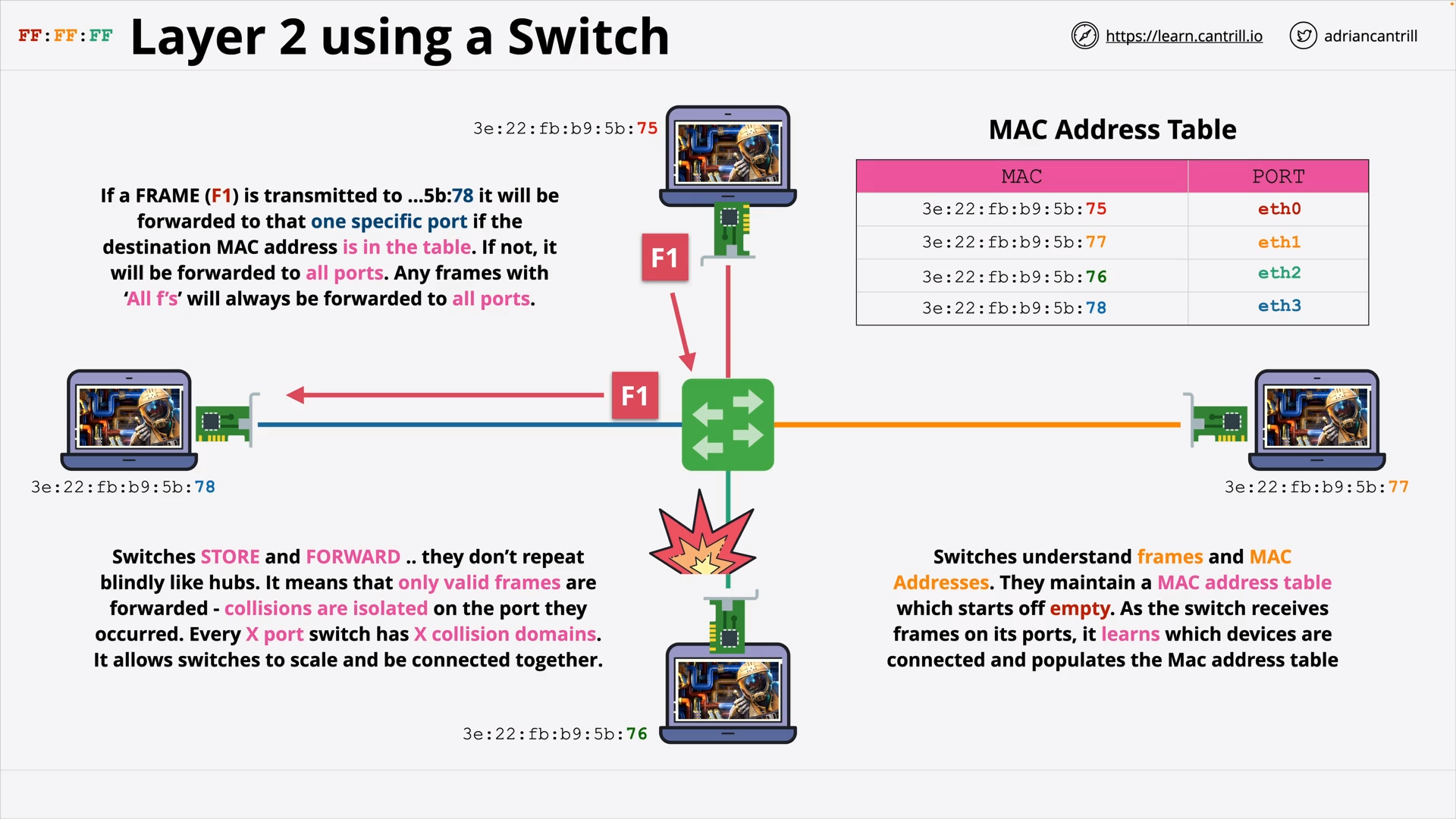 OSI Layer 2 - Using a Switch - MAC Address Table
OSI Layer 2 - Using a Switch - MAC Address Table
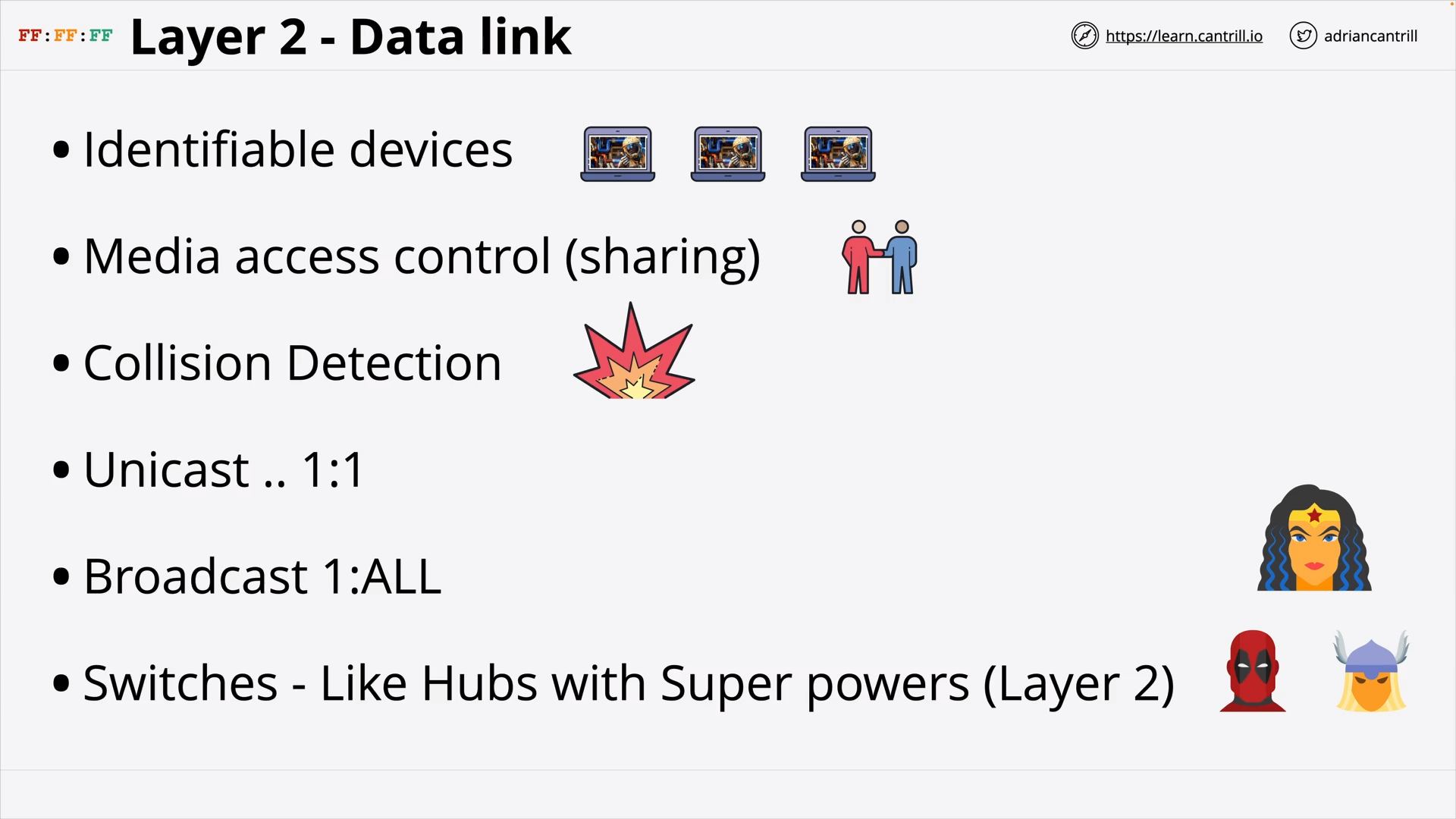 OSI Layer 2 Data Link: MAC Address 👉️ Median Access Control & Collision Detection, Switch
OSI Layer 2 Data Link: MAC Address 👉️ Median Access Control & Collision Detection, Switch
Layer 3 - Network - PART1 (12:06)
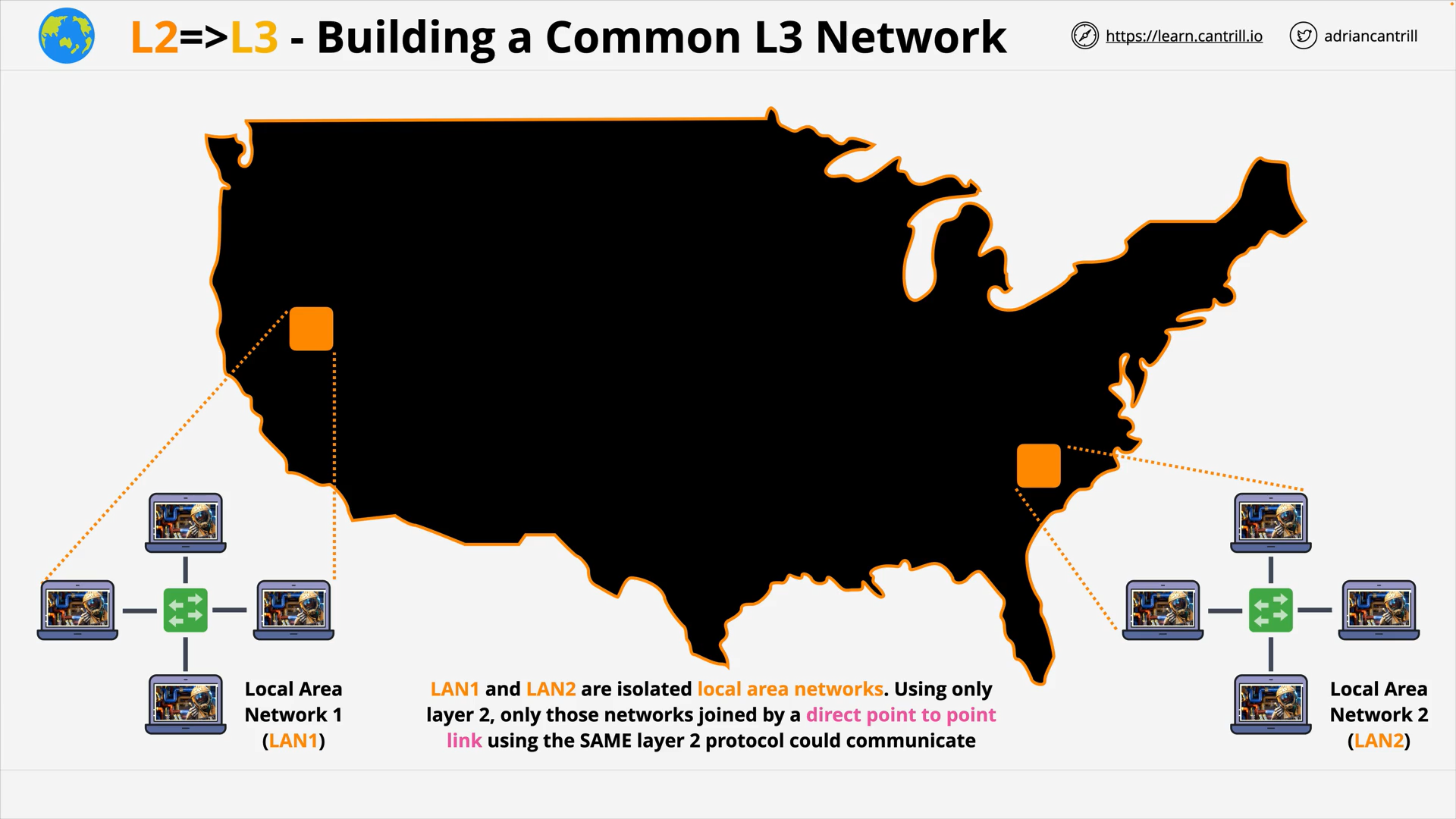 OSI Layer 3 - Layer 3LAN (Local Area Network) use Ethernet protocol
OSI Layer 3 - Layer 3LAN (Local Area Network) use Ethernet protocol
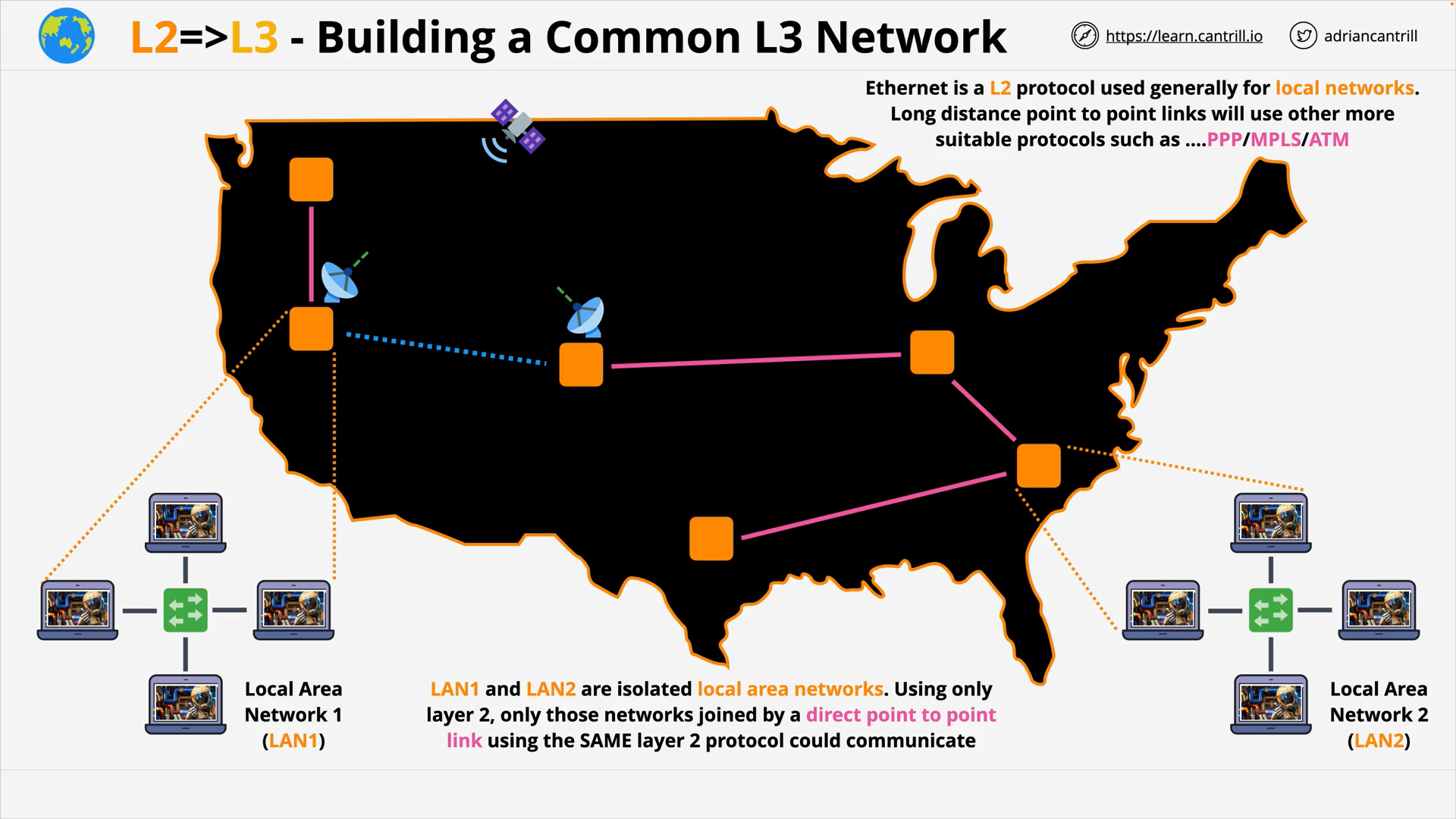 OSI Layer 3 - Long distant point to point (P2P) links use other protocols: PPP/MPLS/ATM…
OSI Layer 3 - Long distant point to point (P2P) links use other protocols: PPP/MPLS/ATM…
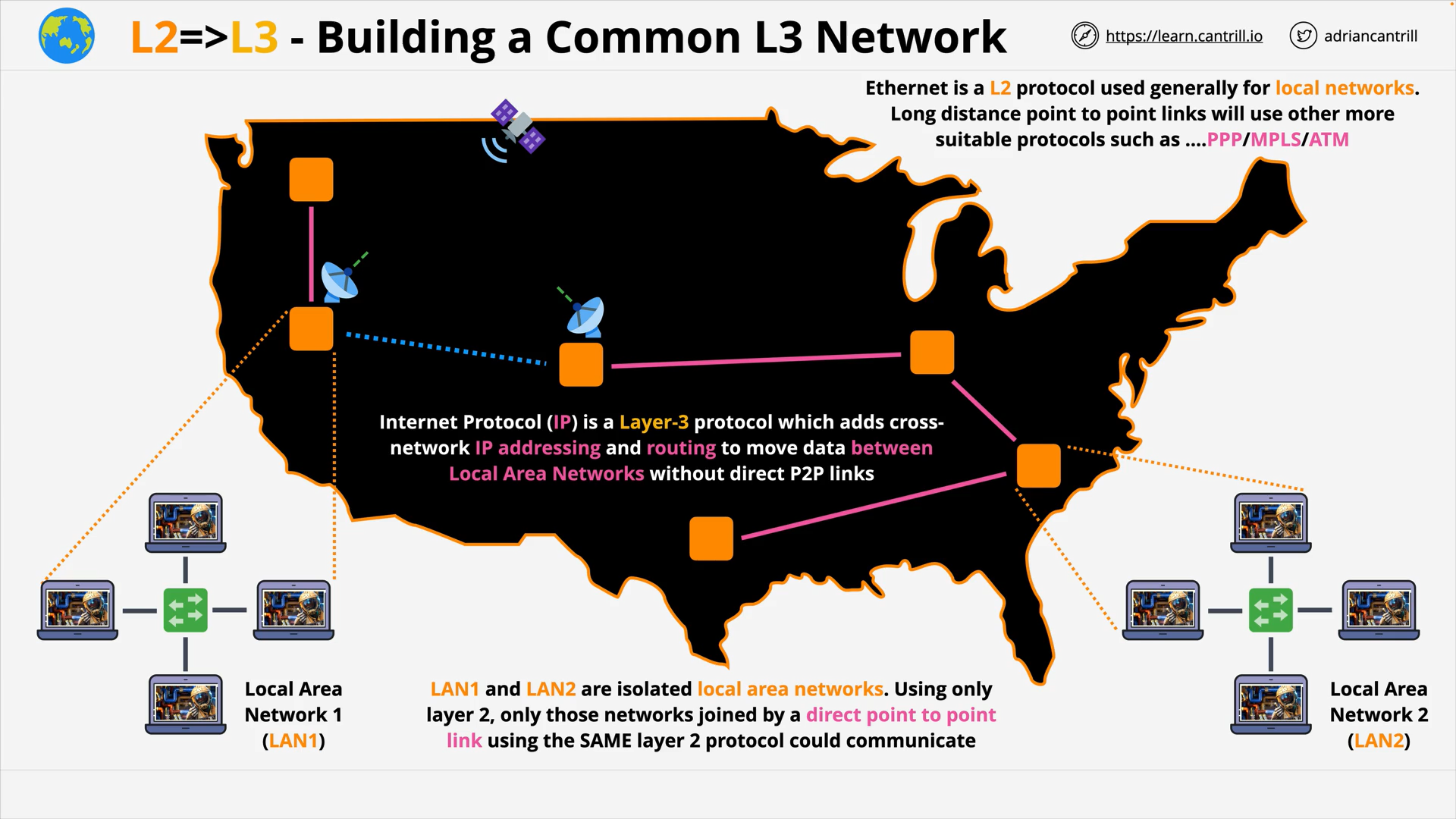 OSI Layer 3 - Internet Protocol (IP), a Layer-3 protocol, moves data between LAN without direct P2P links, by adding cross network IP addressing and routing
OSI Layer 3 - Internet Protocol (IP), a Layer-3 protocol, moves data between LAN without direct P2P links, by adding cross network IP addressing and routing
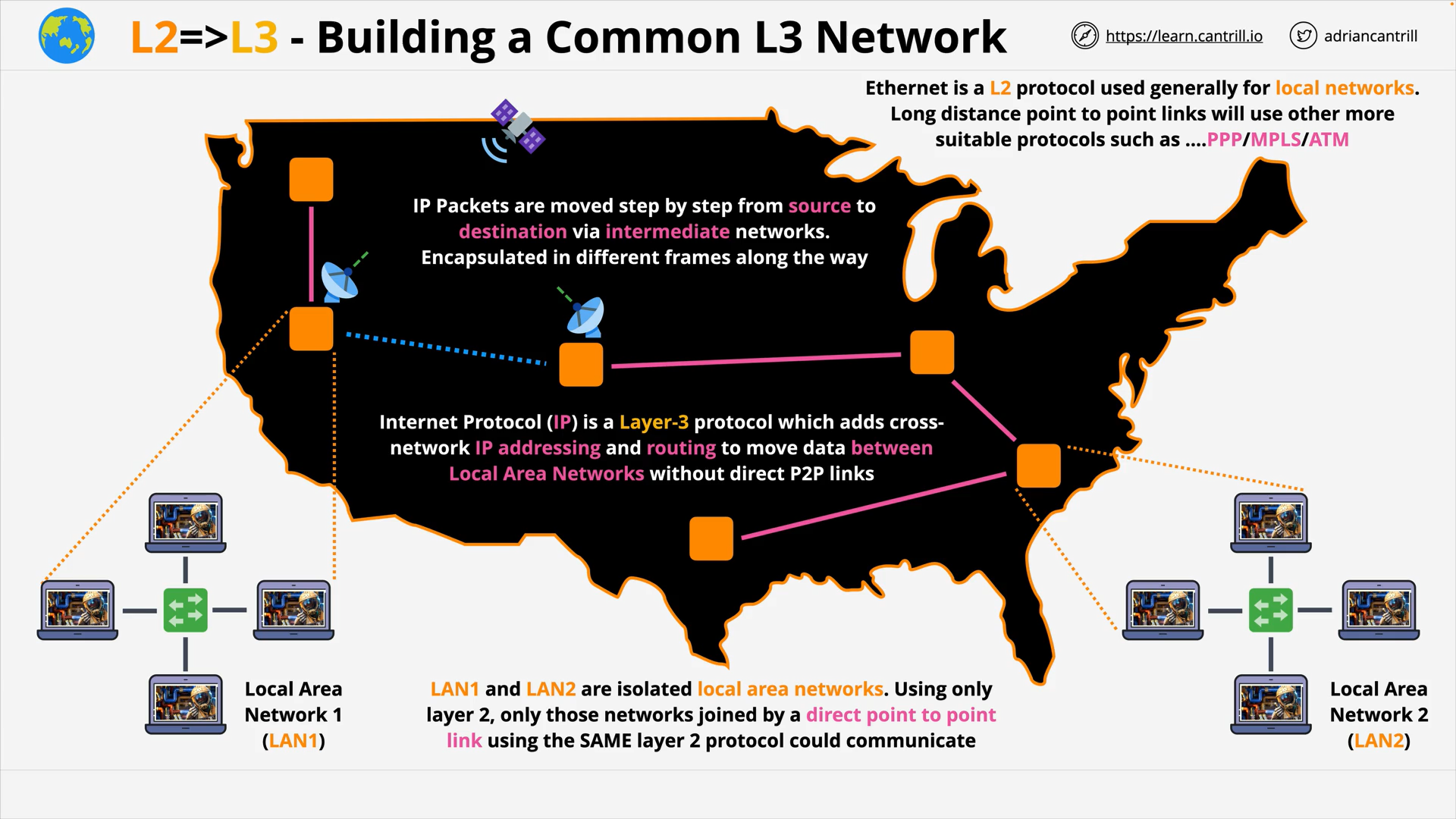 OSI Layer 3 - IP Packets are moved step by step from source to destination via intermediate networks, encapsulated in different frames along the way.
OSI Layer 3 - IP Packets are moved step by step from source to destination via intermediate networks, encapsulated in different frames along the way.
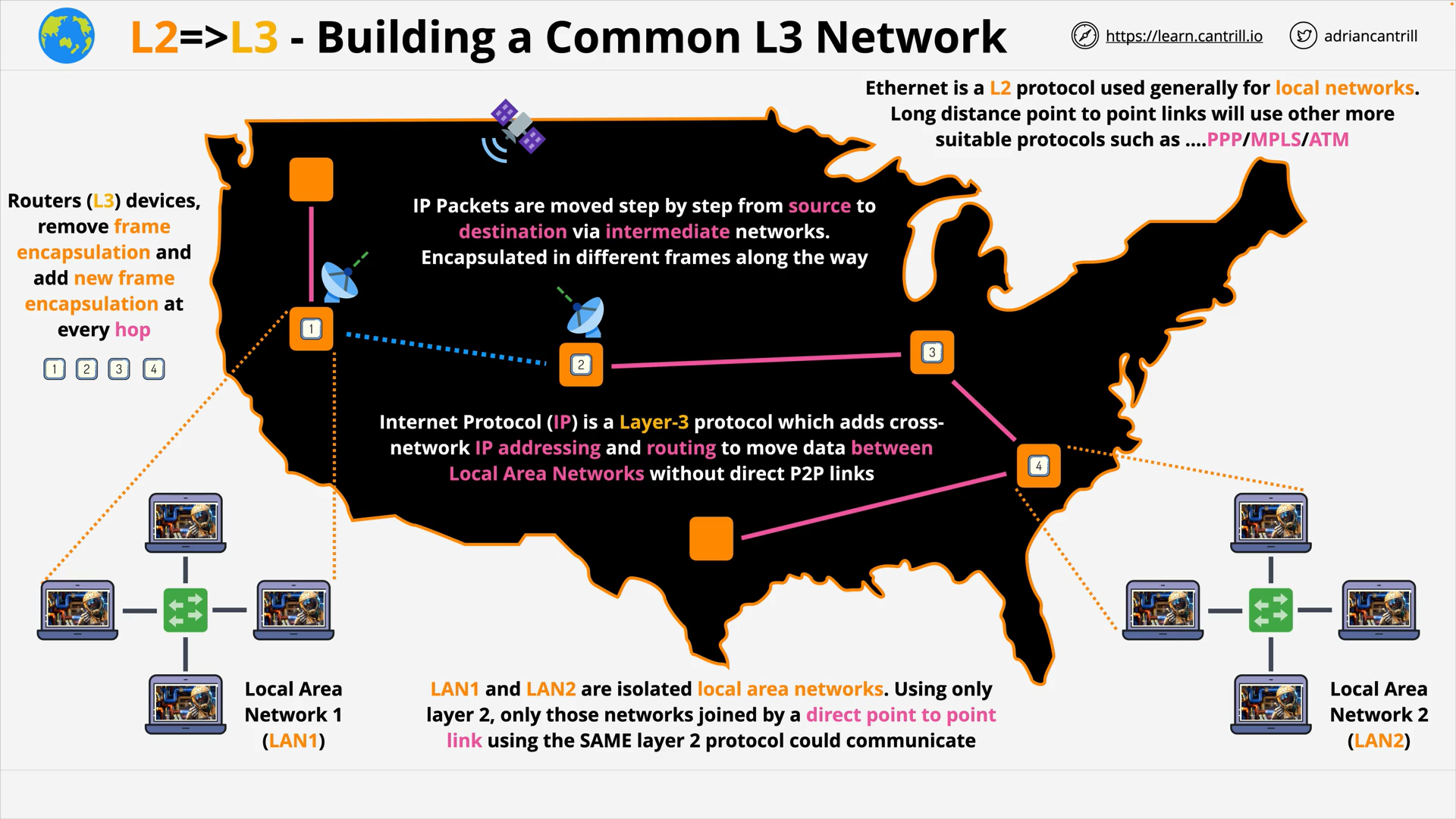 OSI Layer 3 - Routers (L3) devices, remove frame encapsulation and add new frame encapsulation at every hop 1️⃣2️⃣3️⃣4️⃣
OSI Layer 3 - Routers (L3) devices, remove frame encapsulation and add new frame encapsulation at every hop 1️⃣2️⃣3️⃣4️⃣
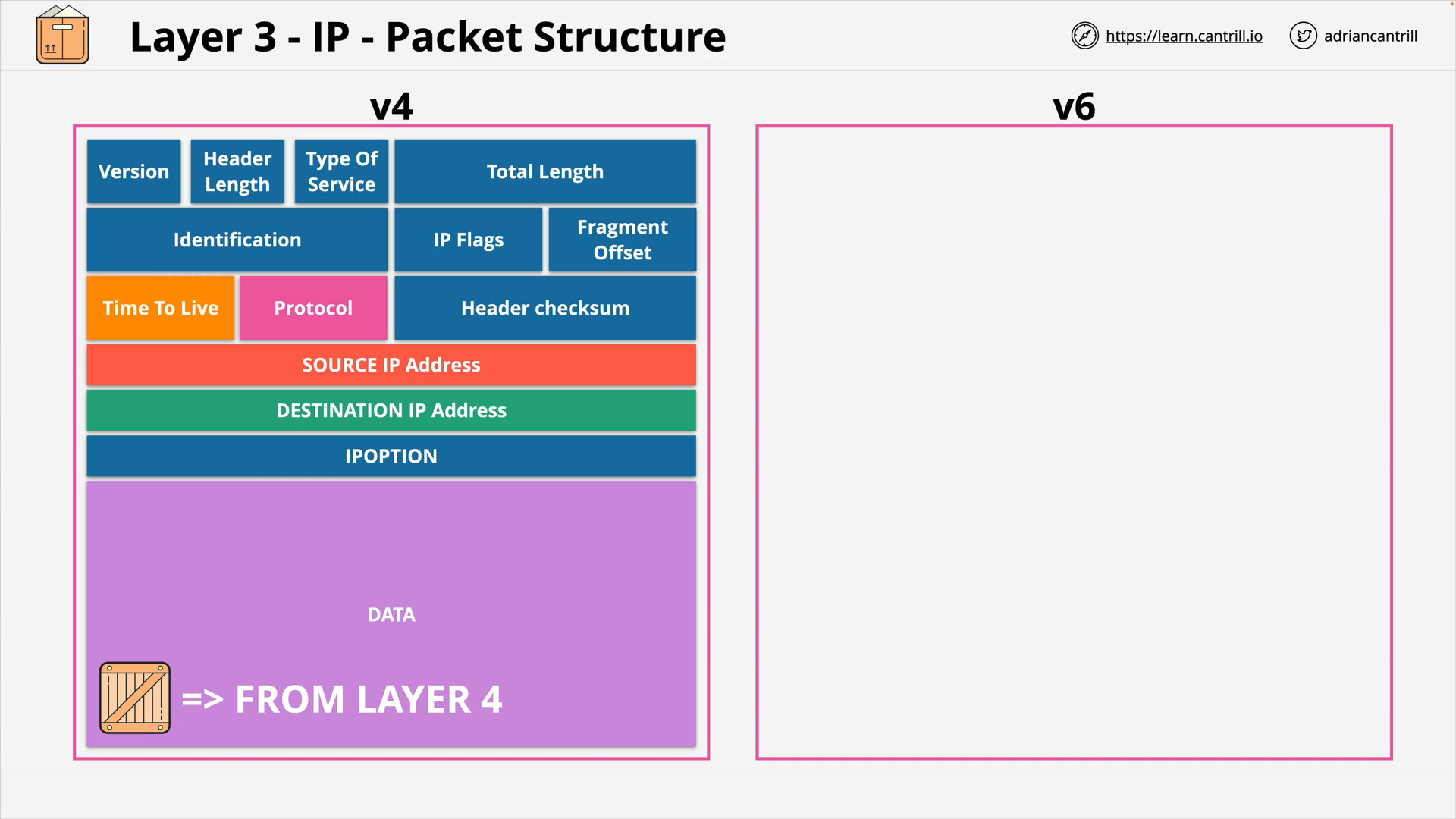 OSI Layer 3 - IP v4 package structure
OSI Layer 3 - IP v4 package structure
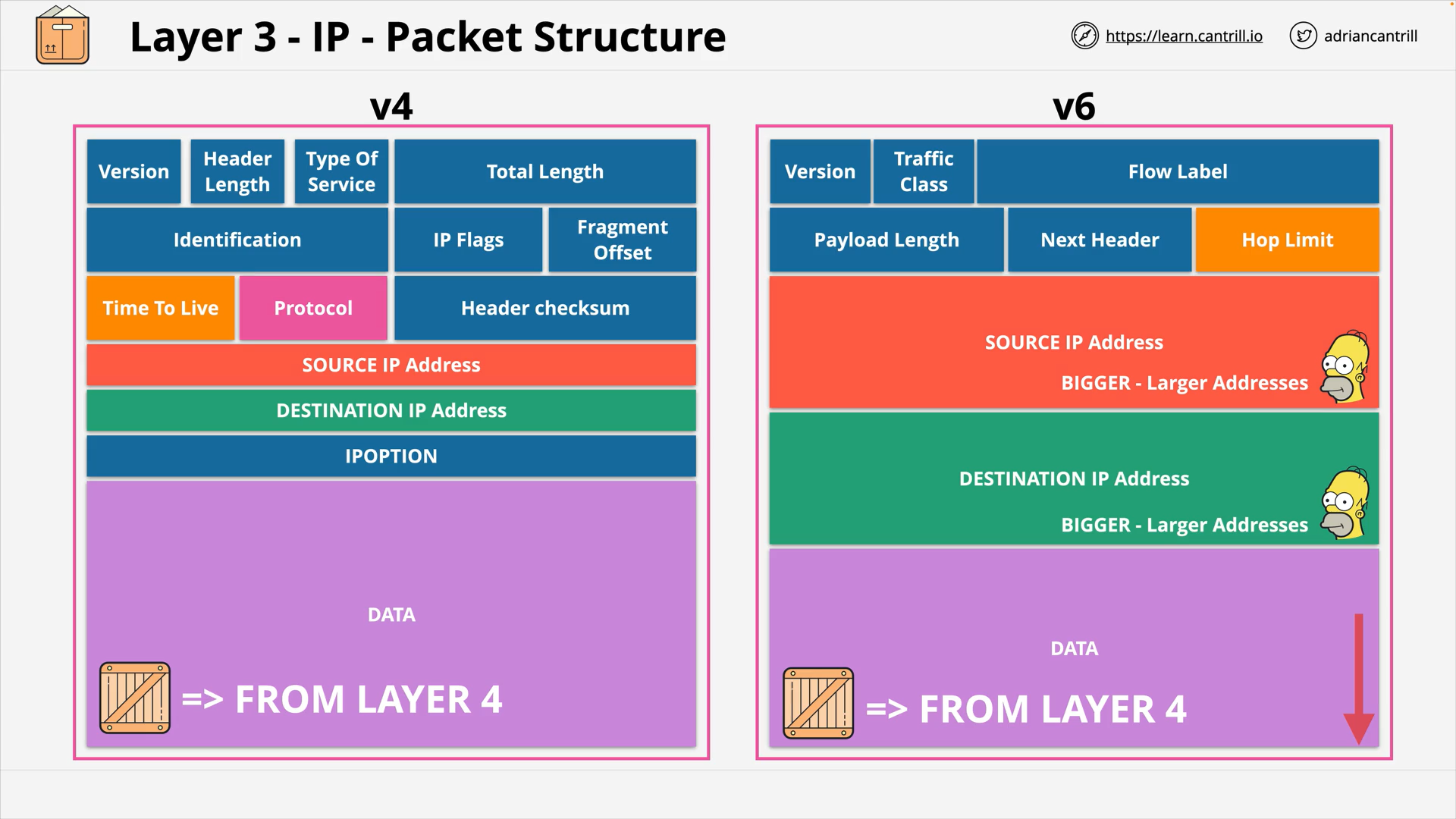 OSI Layer 3 - IP v6 package structure
OSI Layer 3 - IP v6 package structure
Layer 3 - Network - PART2 (19:13)
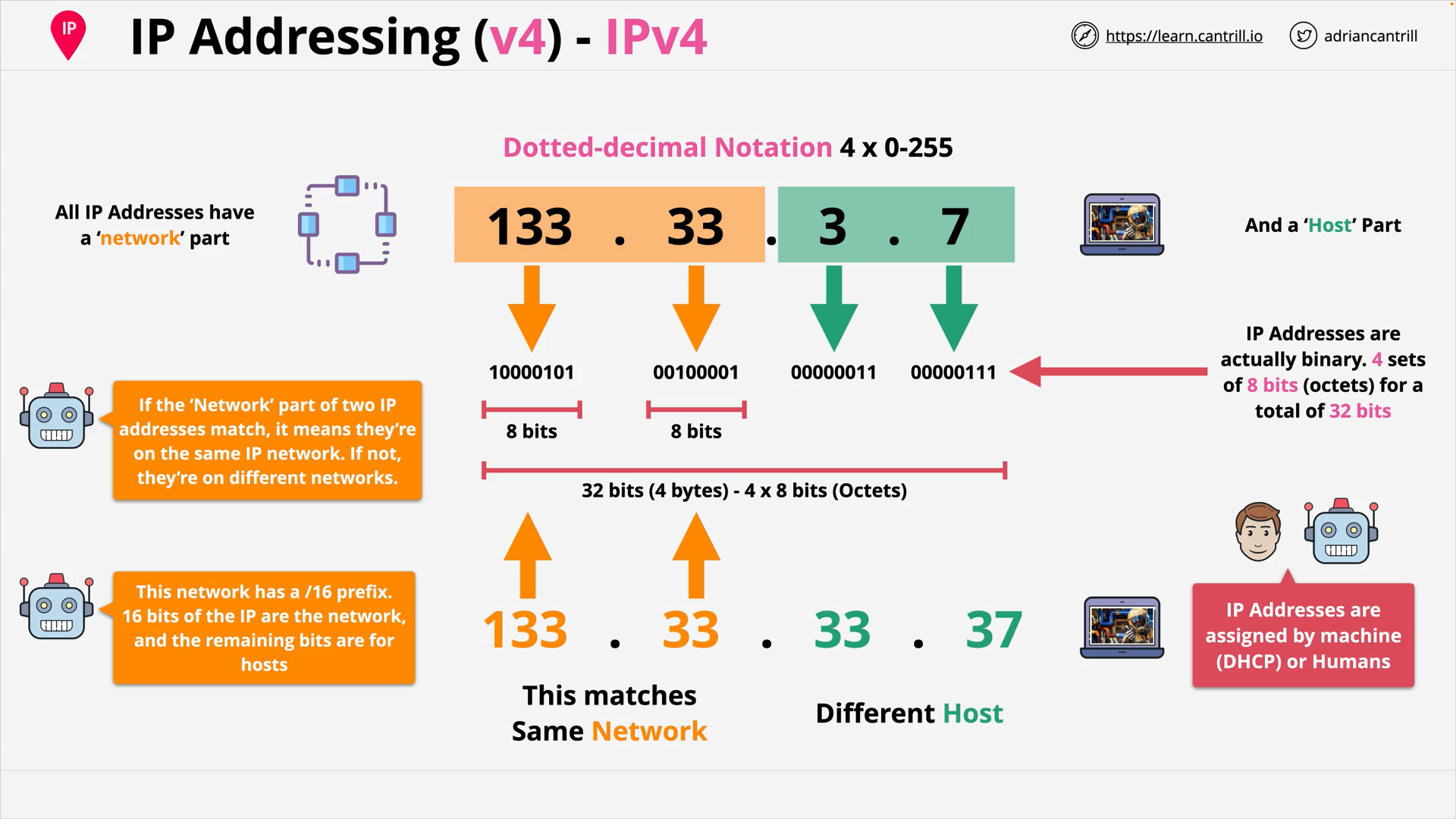 OSI Layer 3 - IPv4 Addressing
OSI Layer 3 - IPv4 Addressing
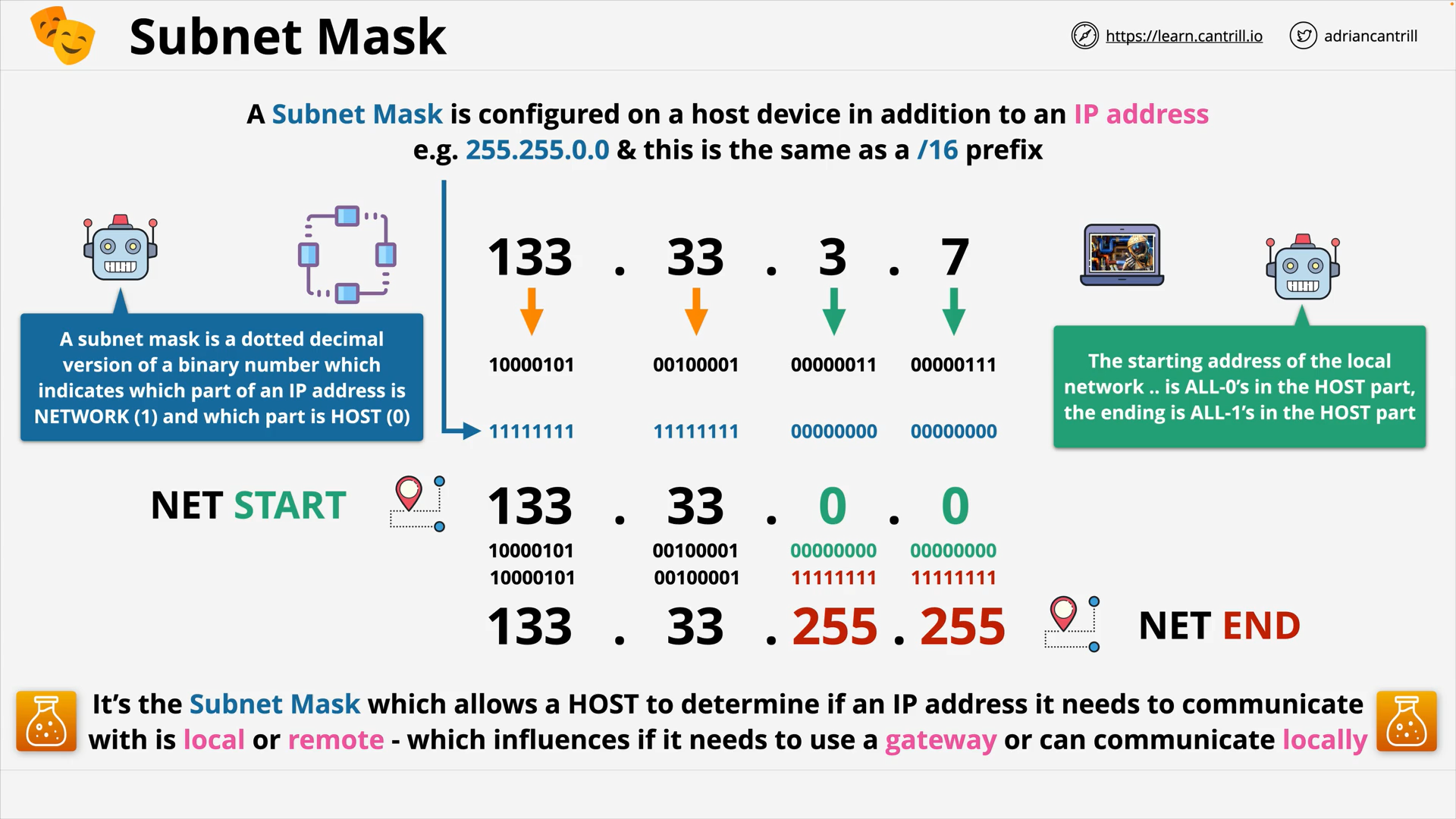 OSI Layer 3 - Subnet Mask
OSI Layer 3 - Subnet Mask
ipv4 classful addressing
Class A, class B, class C
ipv4 reserved ip address
-
Class A
- 0.0.0.0/8: Local network
- 10.0.0.0/8: Private network
- 127.0.0.0./8: Loopback of local host
-
Class B
-
169.254.0.0/16: Link-local address when no IP address is specified
- 169.254.169.254/32: AWS EC2 Instance Metadata Service
-
172.16.0.0/12: Private network
- 127.31.0.0/16: AWS default VPC size
-
-
Class C
- 192.168.0.0/16: Private network
Ref:
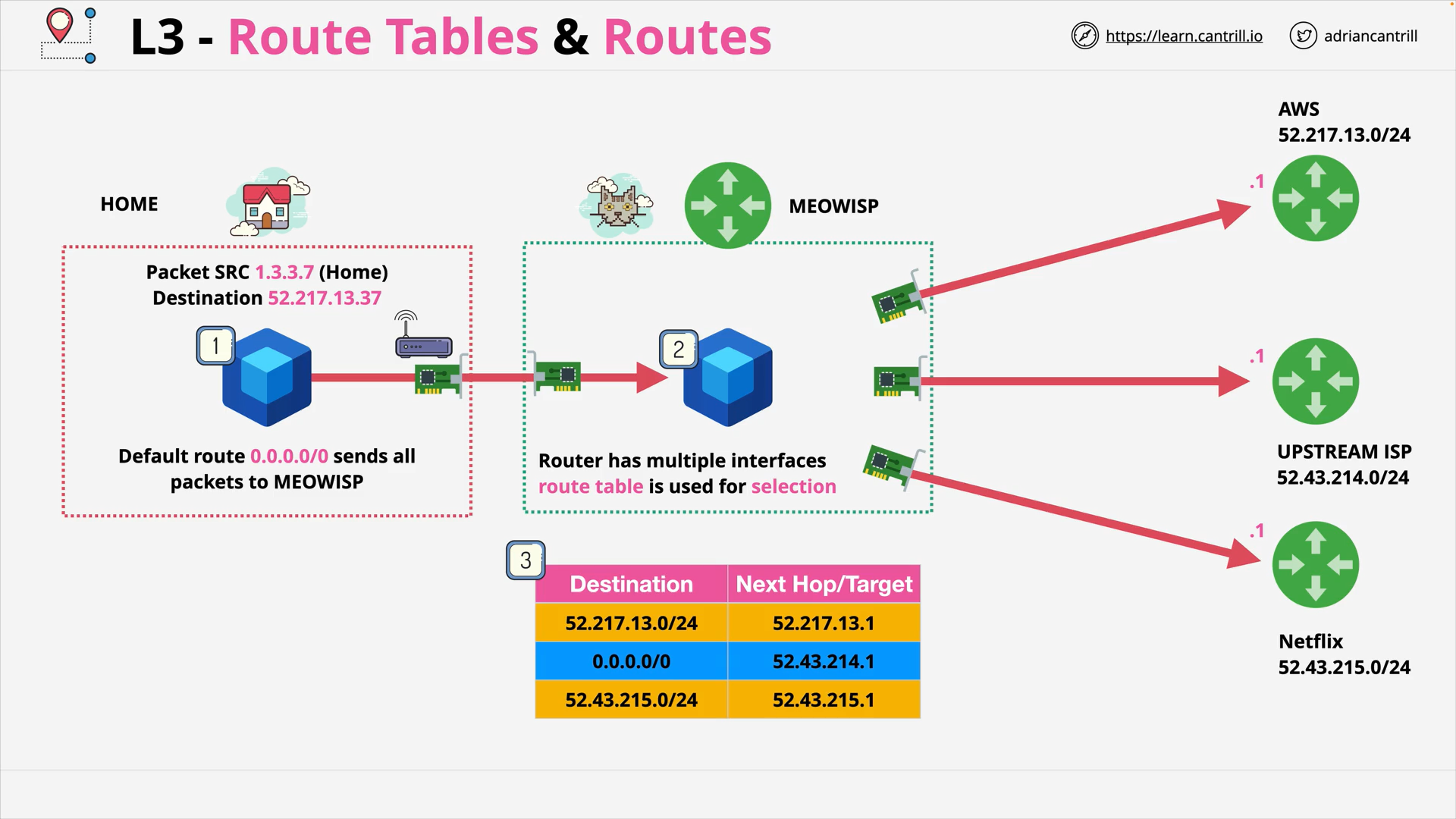 OSI Layer 3 - Route Tables & Routes
OSI Layer 3 - Route Tables & Routes
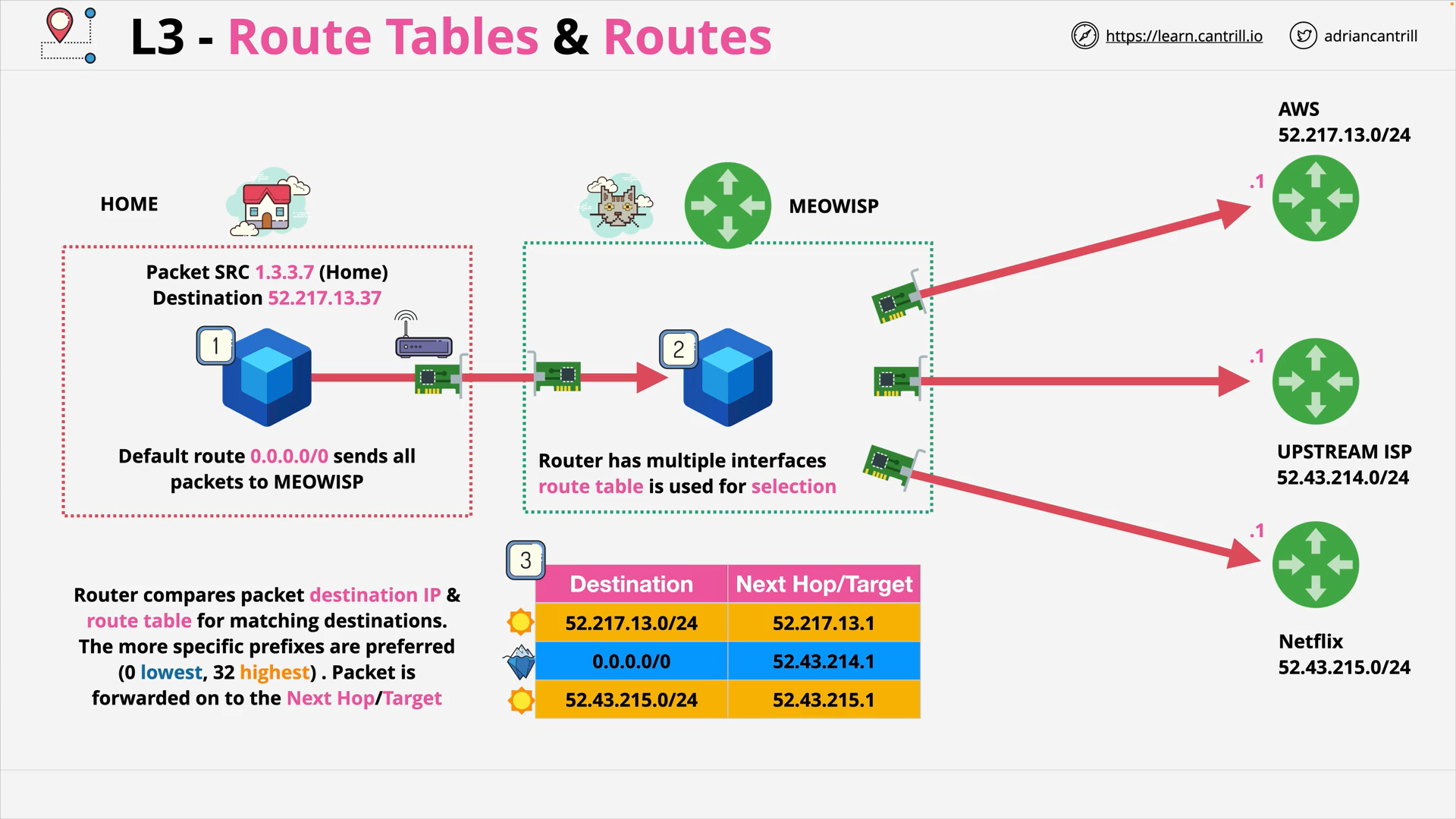 OSI Layer 3 - Router compares packet destination IP & route table for matching destinations and is forwarded on to the Next Hop/Target. The more specific prefixes are preferred (0 lowest. 32 highest)
OSI Layer 3 - Router compares packet destination IP & route table for matching destinations and is forwarded on to the Next Hop/Target. The more specific prefixes are preferred (0 lowest. 32 highest)
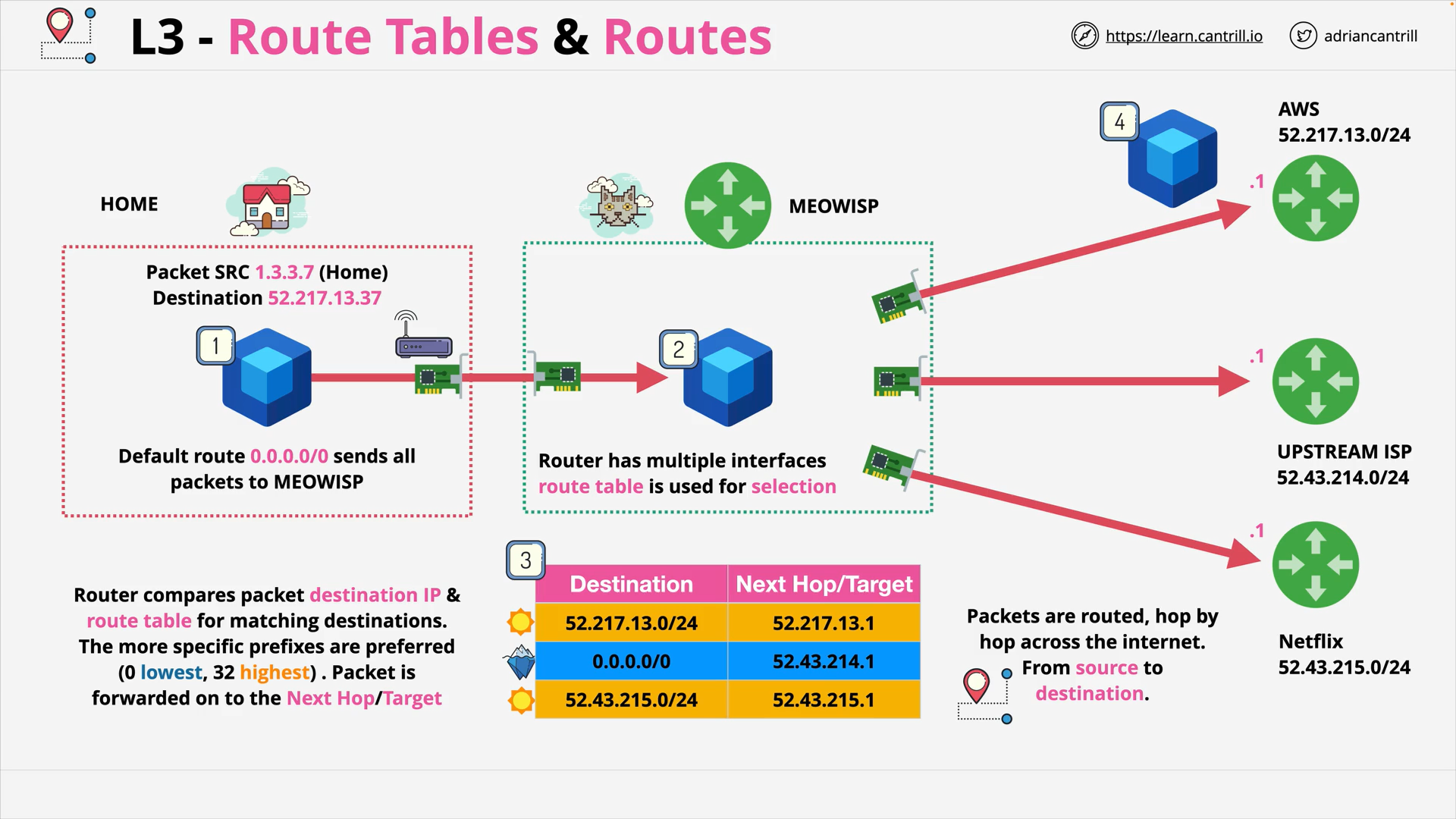 OSI Layer 3 - Packets are routed, hop by hop across the internet. From source to destination.
OSI Layer 3 - Packets are routed, hop by hop across the internet. From source to destination.
Layer 3 - Network - PART3 (15:15)
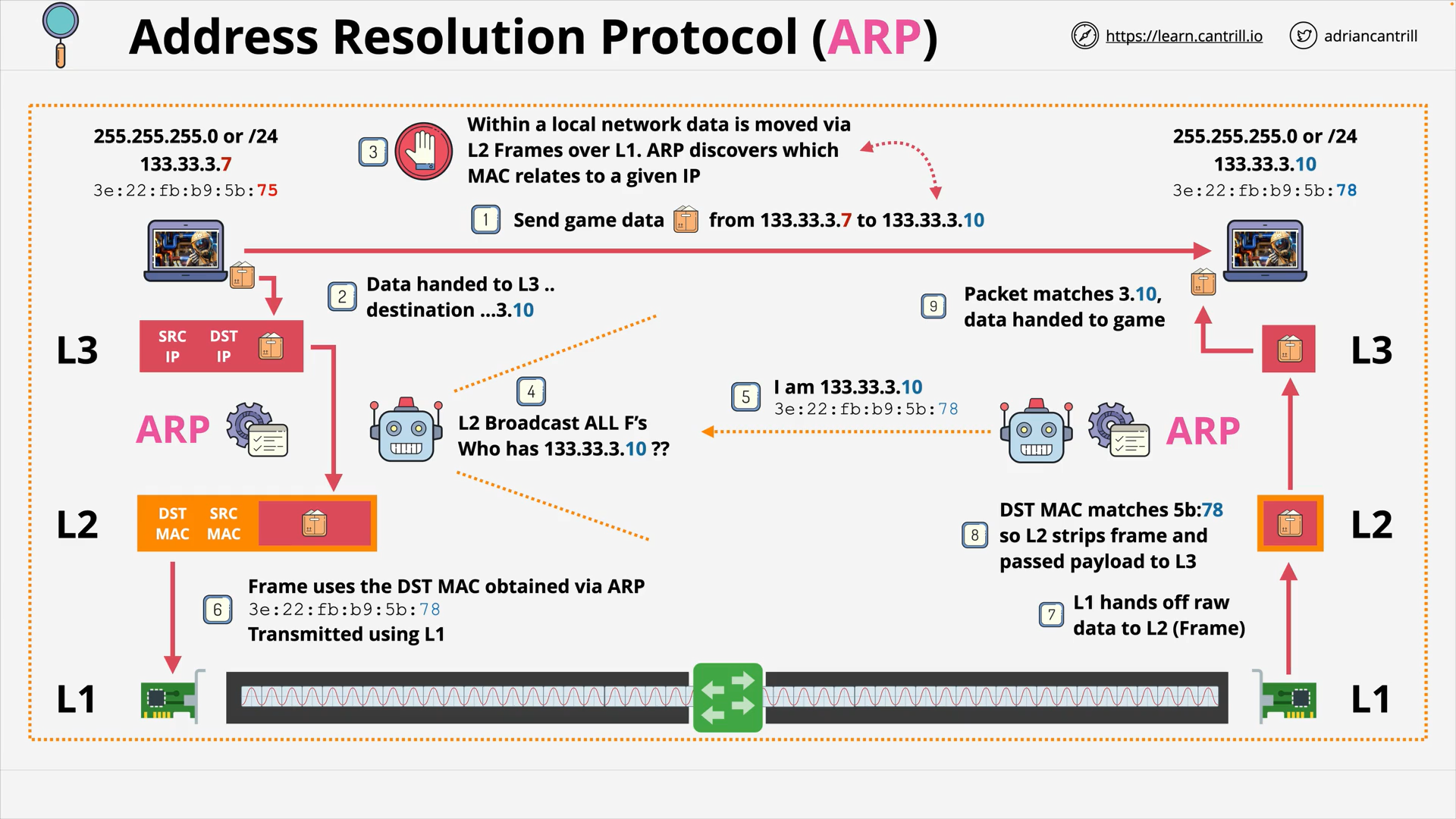 OSI Layer 3 - Address Resolution Protocol (ARP)
OSI Layer 3 - Address Resolution Protocol (ARP)
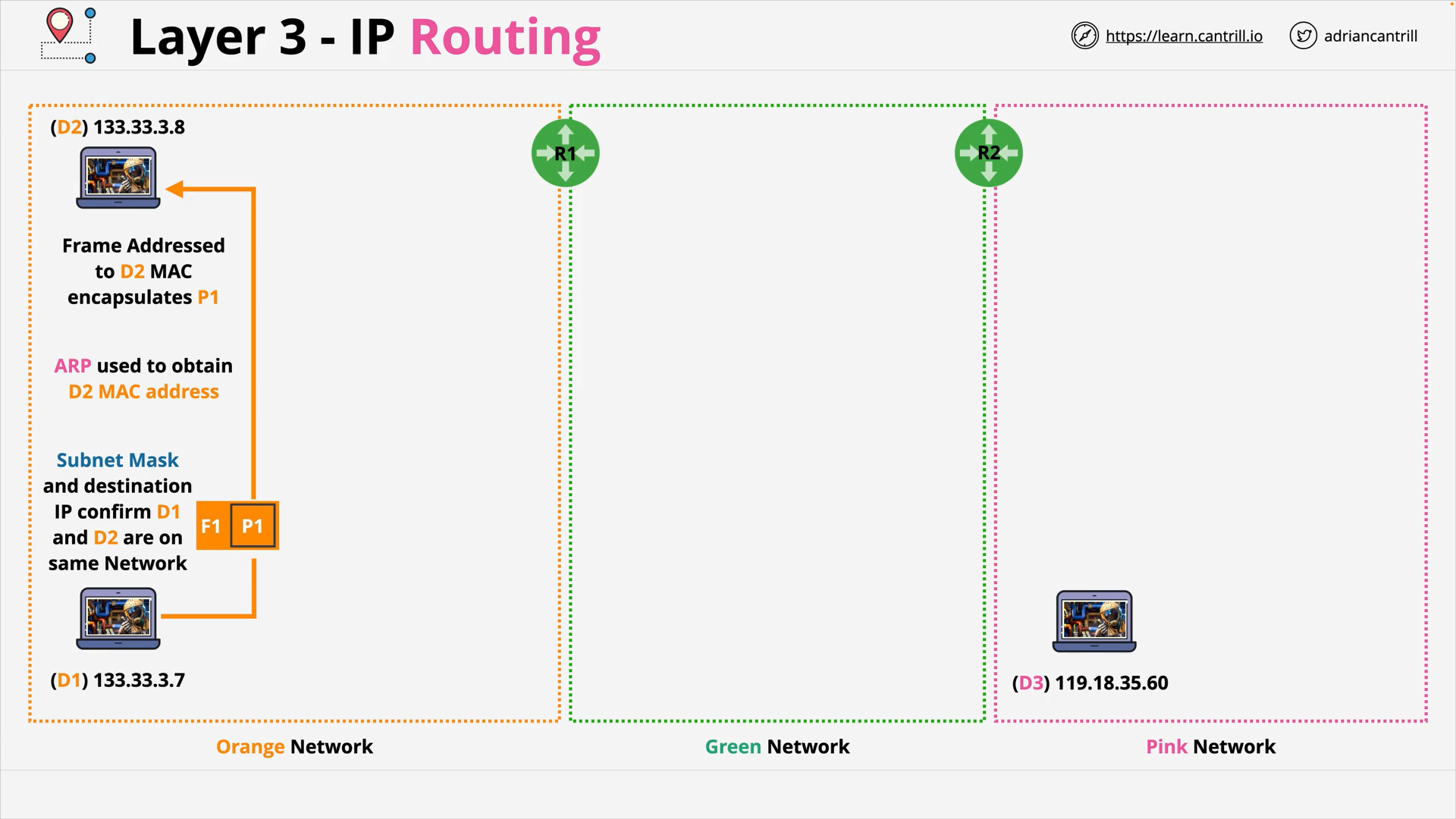 OSI Layer 3 - IP Routing - Same local network
OSI Layer 3 - IP Routing - Same local network
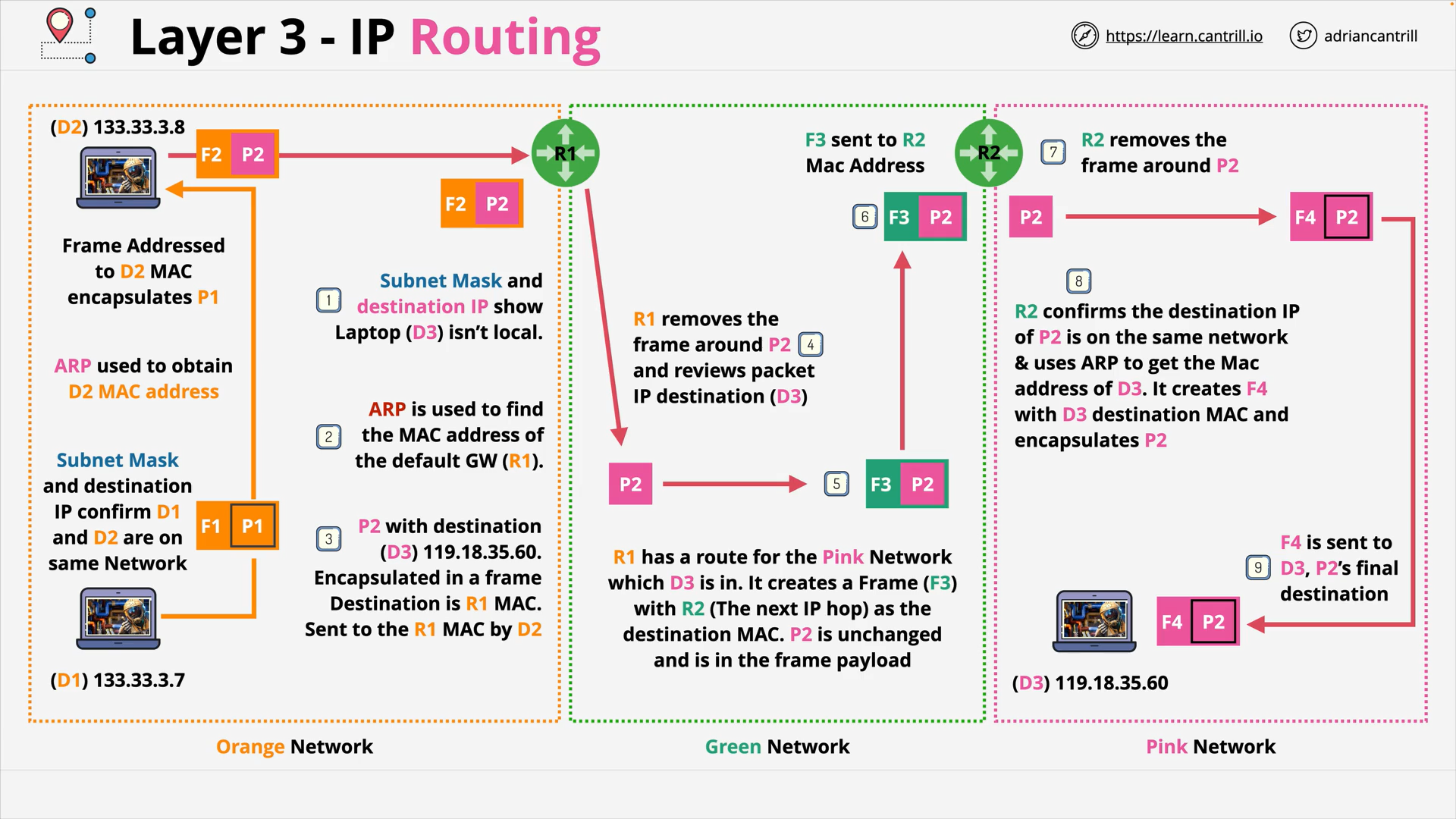 OSI Layer 3 - IP Routing - 2 different networks
OSI Layer 3 - IP Routing - 2 different networks
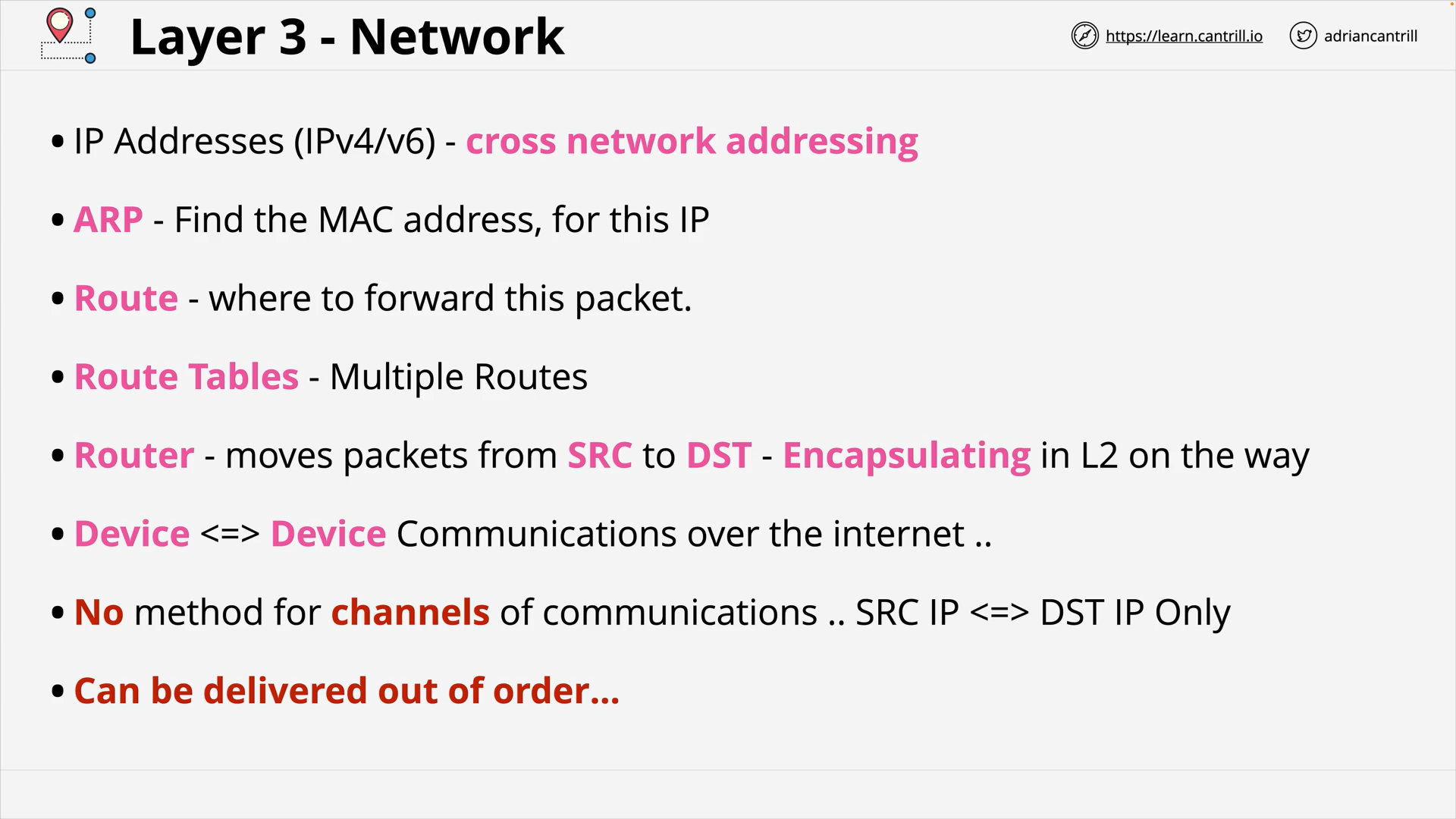 OSI Layer 3 - L3 Summary
OSI Layer 3 - L3 Summary
Layer 4&5 - Transport & Session - PART1 (15:39)
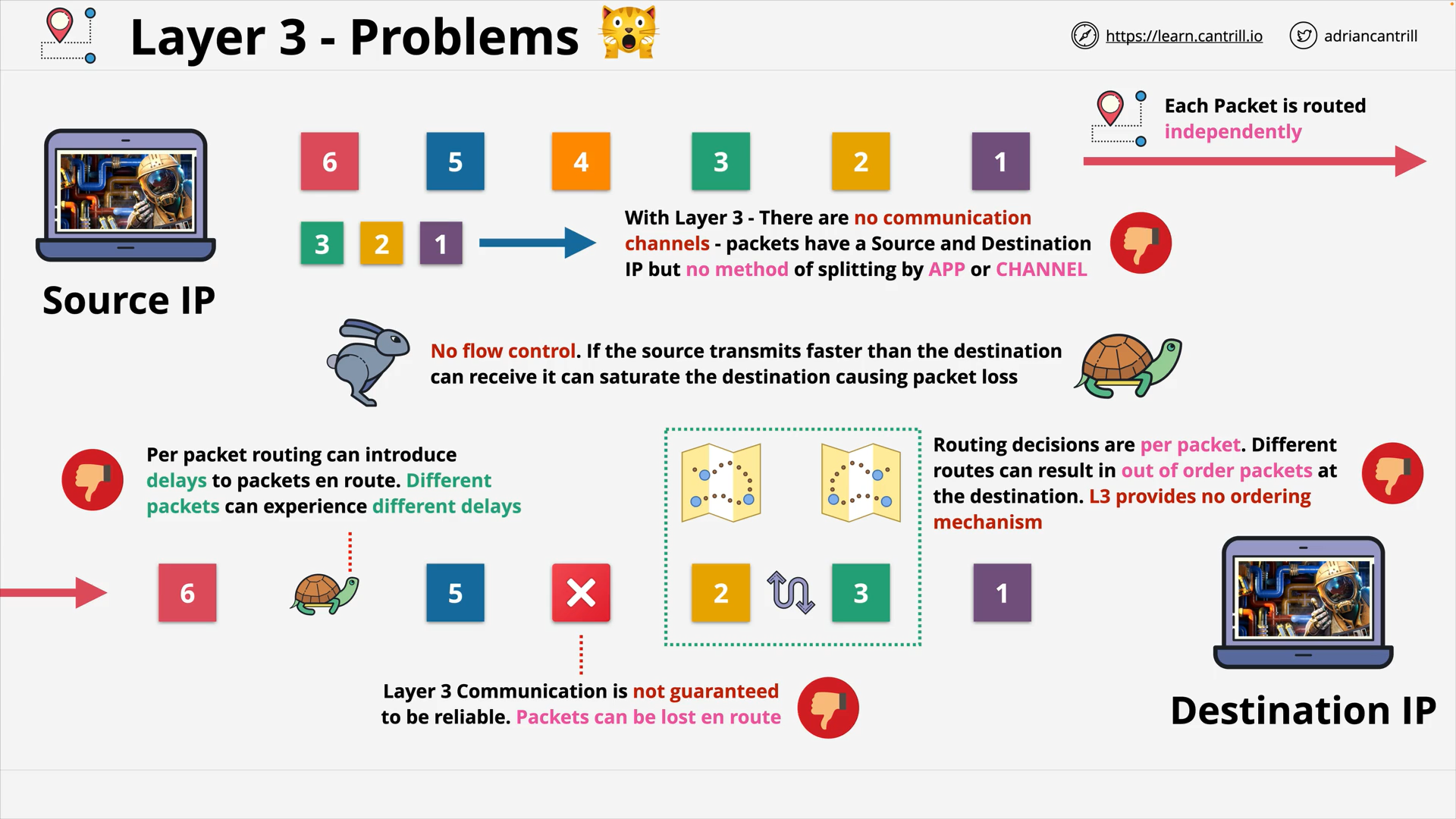 L3 problems
L3 problems
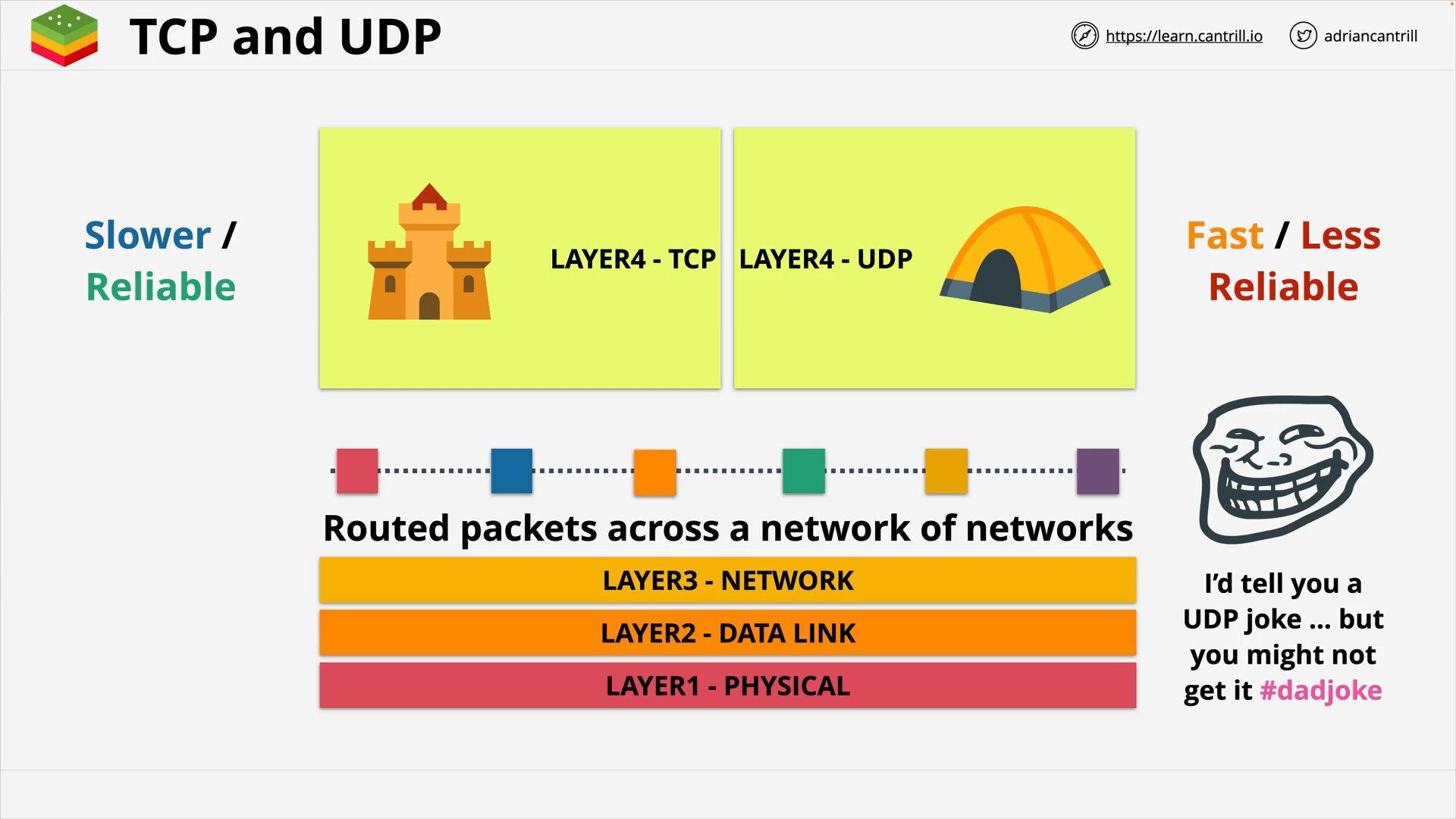 TCP & UDP
TCP & UDP
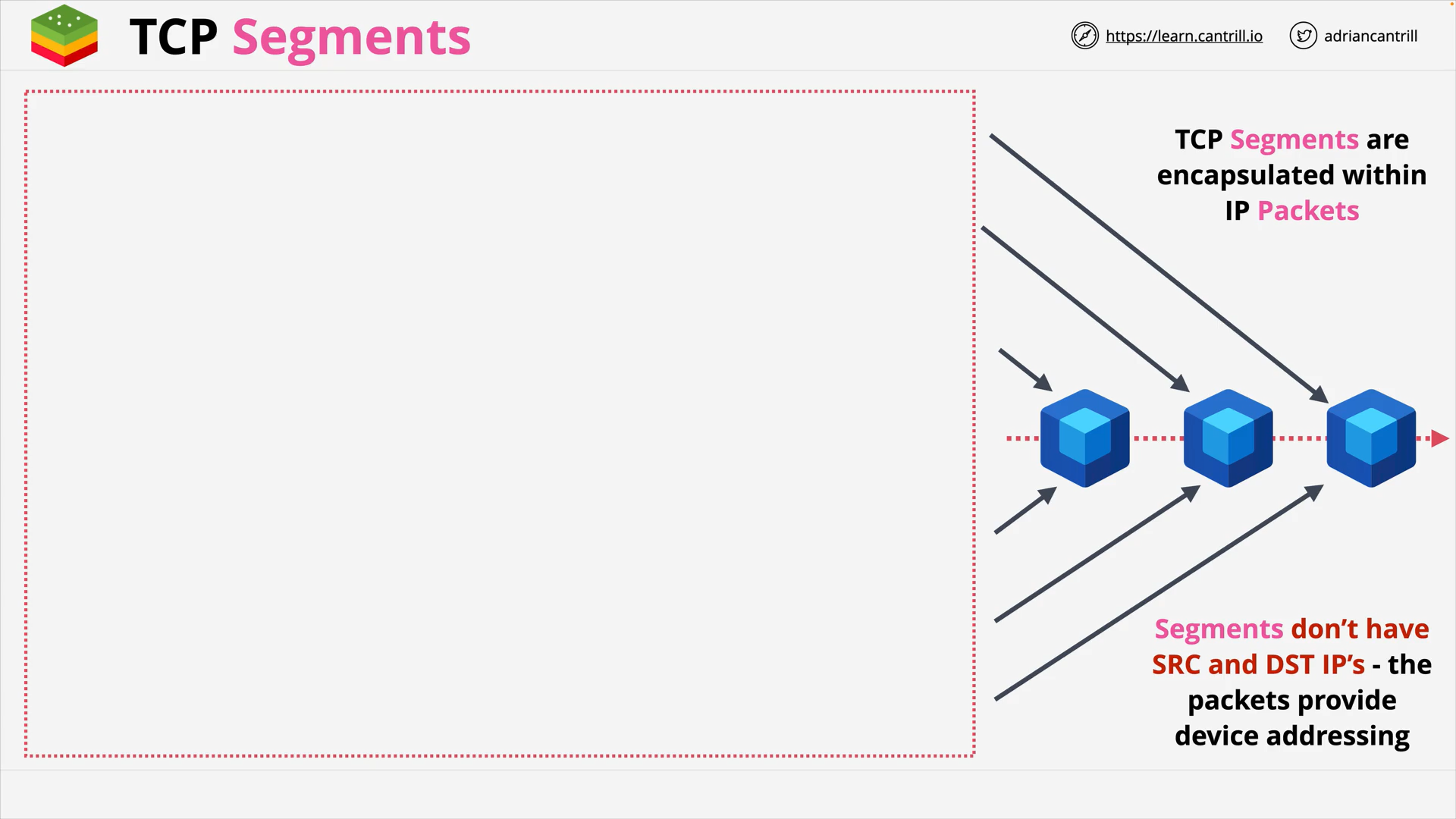 TCP Segments
TCP Segments
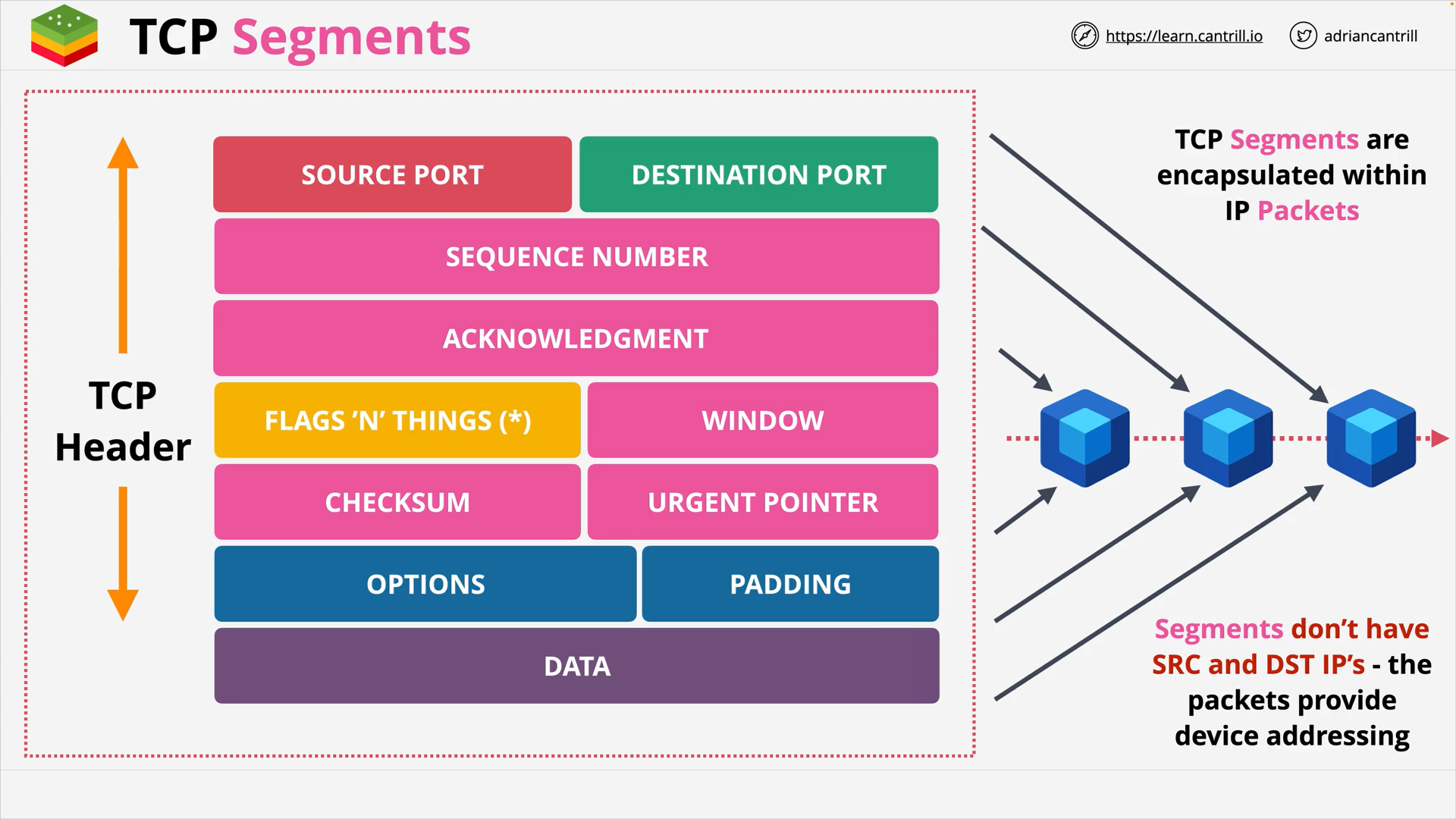 TCP Header
TCP Header
Layer 4&5 - Transport & Session - PART2 (13:54)
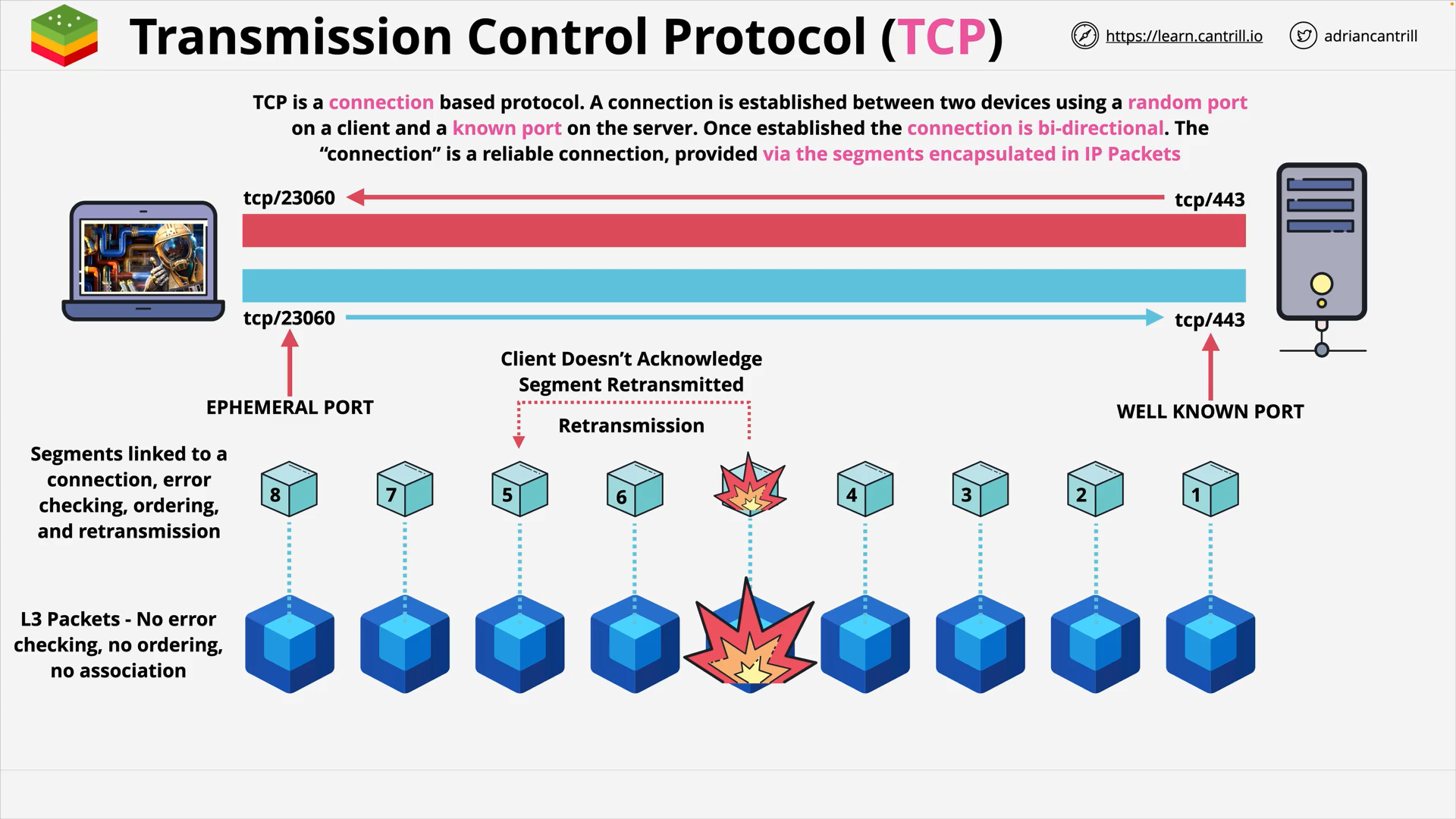 Transmission Control Protocol (TCP) is a connection based protocol.
Transmission Control Protocol (TCP) is a connection based protocol.
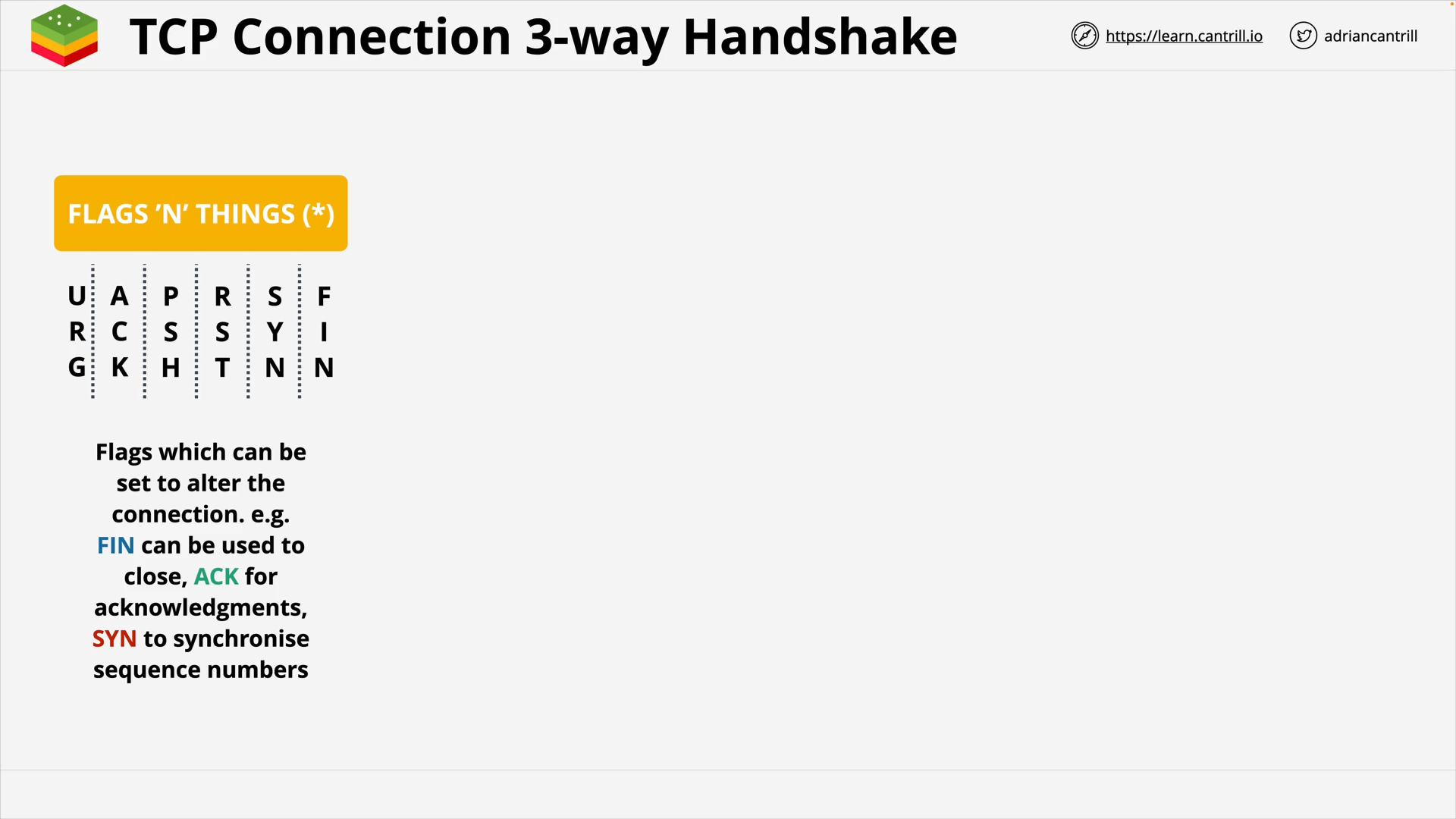 TCP Flags 🏴🏳️
TCP Flags 🏴🏳️
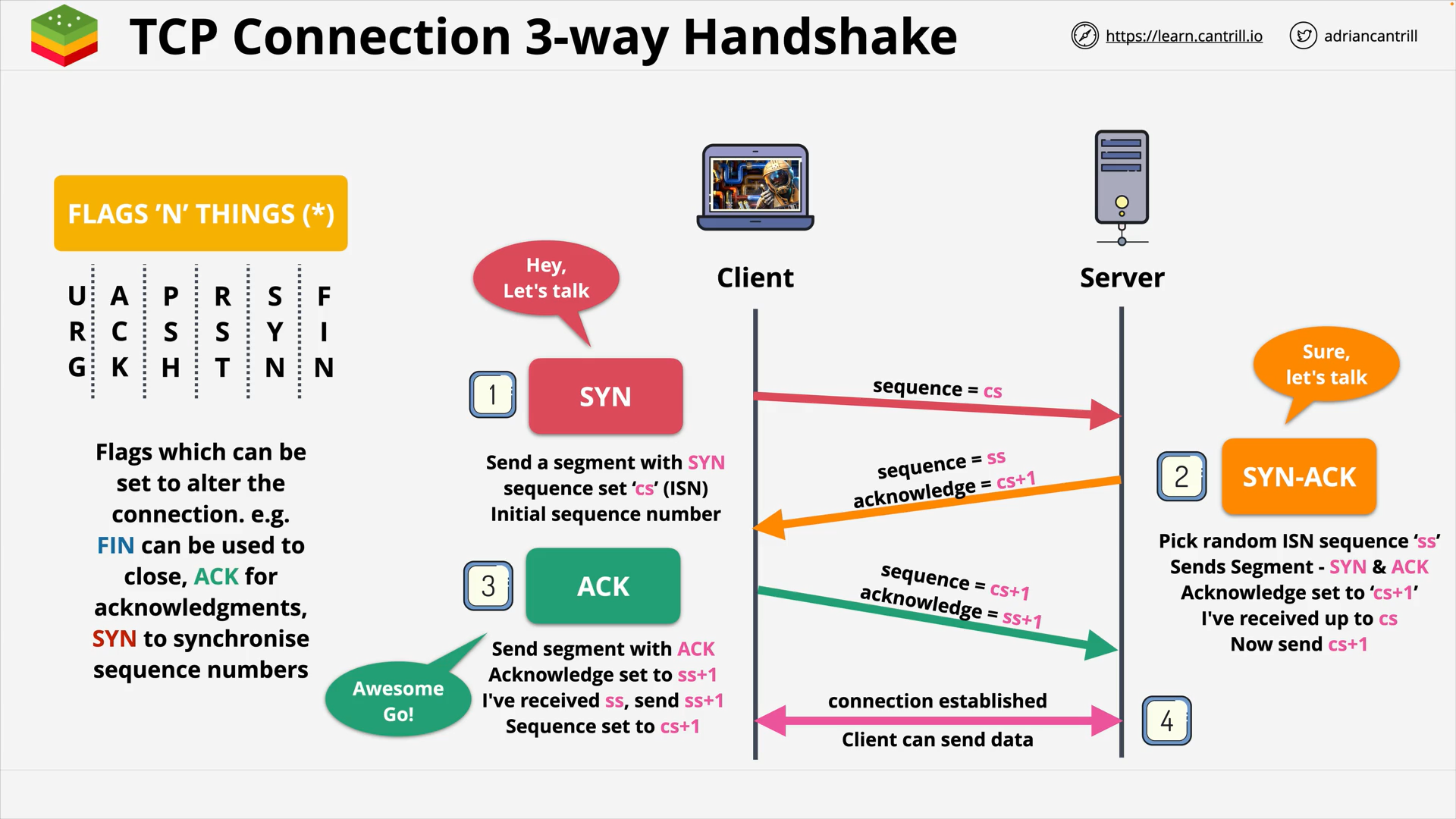 TCP Connection 3-way Handshake 🤝
TCP Connection 3-way Handshake 🤝
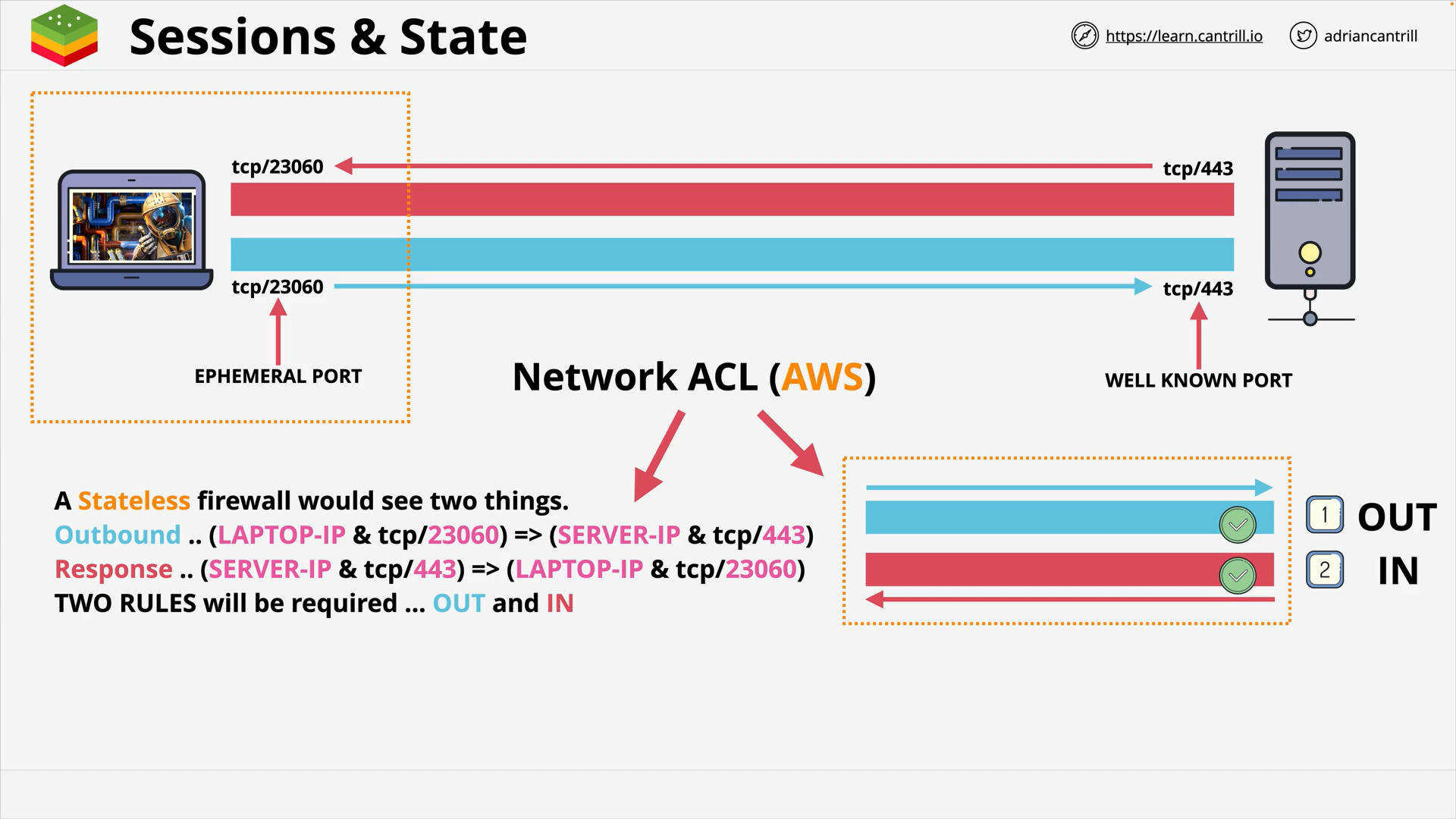 Stateless firewall
Stateless firewall
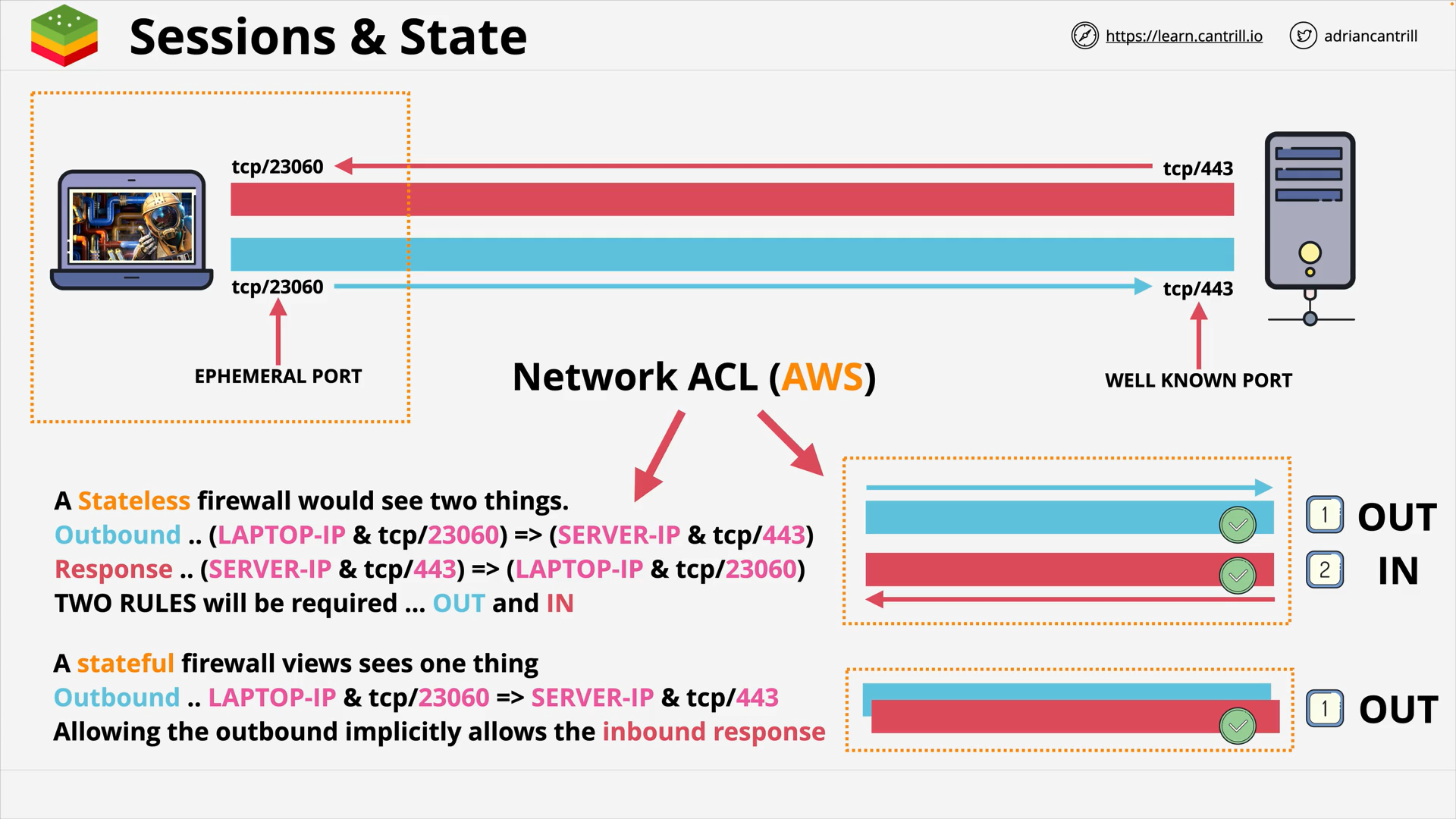 Stateful firewall
Stateful firewall
Other Networking (MORE COMING SOON)
Network Address Translation (NAT) - PART1 (11:00)
_-_PART1__learn.c.png) NAT - Types of NATs
NAT - Types of NATs
why nat?
- Overcome IPv4 shortages.
- Security: hide private IP
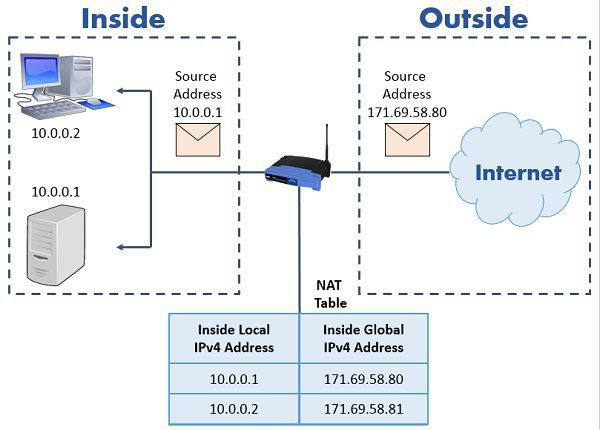
_-_PART1__learn.c.png) Static NAT - Outbound Traffic
Static NAT - Outbound Traffic
static nat maintains a nat table to map privateip : public ip (1:1)>
👉️ In AWS, Internet Gateway (IGW) is a static NAT.
_-_PART1__learn.c.png) Static NAT - Inbound Traffic👉️
Static NAT - Inbound Traffic👉️
Network Address Translation (NAT) - PART2 (9:38)
_-_PART2__learn.c.png) Dynamic NAT
Dynamic NAT
dynamic nat maintains a nat table:
- Dynamic NAT maps PrivateIP : Public IP (1:1 first available).
- Public IP allocations are temporary allocations from a Public IP Pool, the pool may be out-of-public IPs.
_-_PART2__learn.c.png) Port Address Translating (PAT)
Port Address Translating (PAT)
pat records the source (private) ip and source port:
- PAT replaces the source IP with the single Public IP and a public source port
- The Public IP and public source port are allocated from a pool which allows IP Overloading (many to one)
in aws, nat gateway (natgw) is a pat.
nat vs pat
- NAT
- PAT: is a type of Dynamic NAT
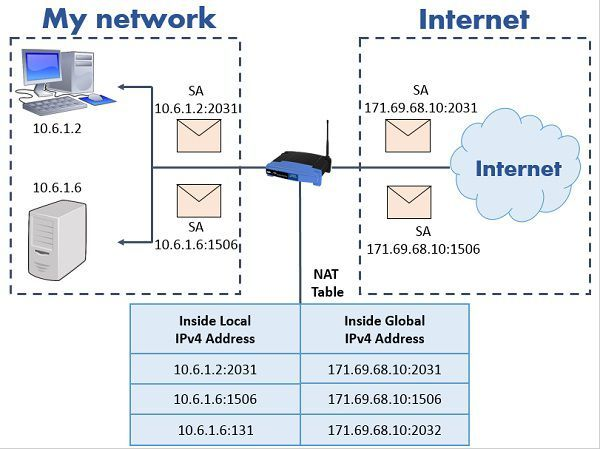
Ref: https://techdifferences.com/difference-between-nat-and-pat.html
IP Address Space & Subnetting - PART1 (14:37)
 IPv4 Addressing
IPv4 Addressing
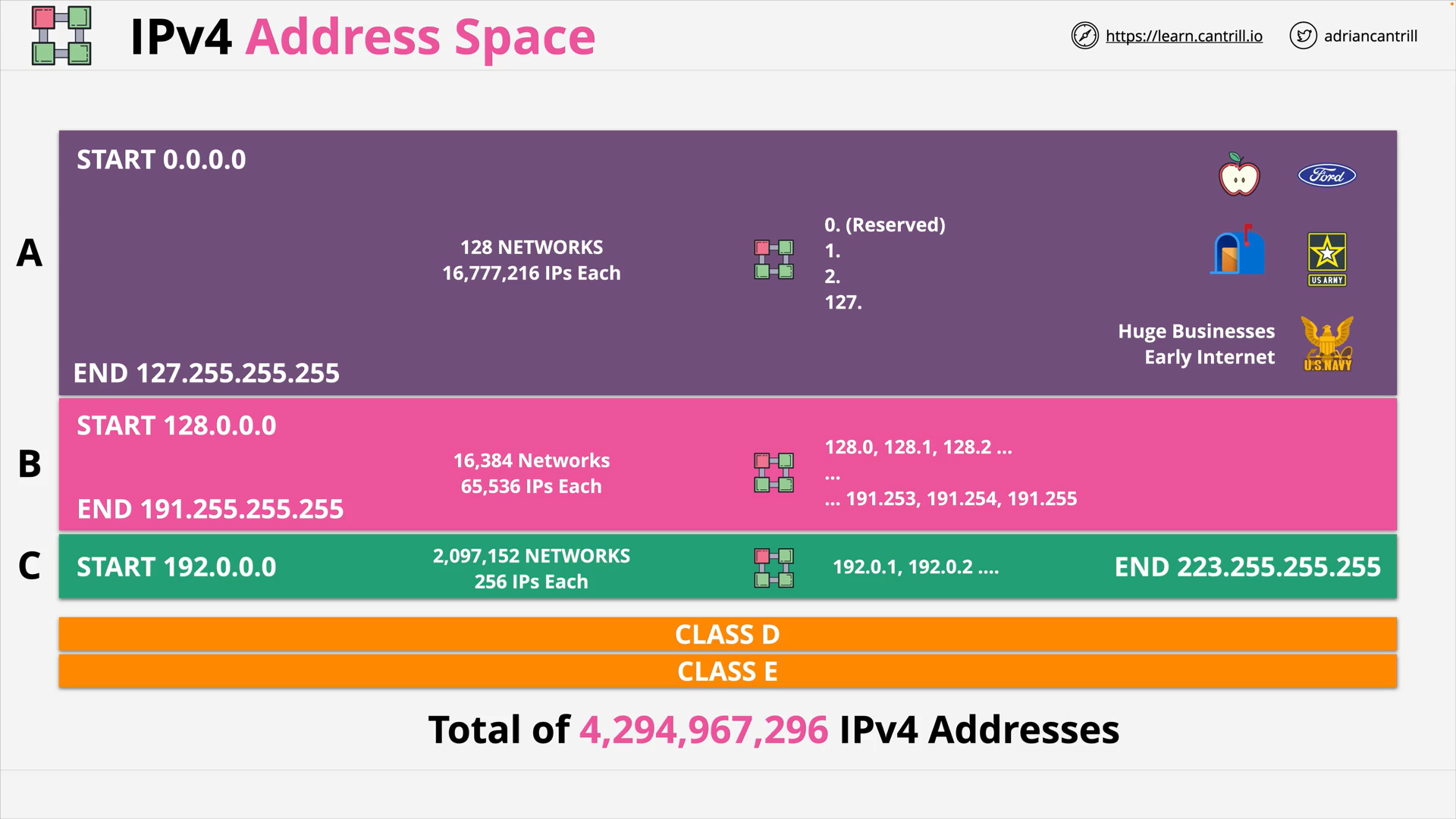 IPv4 Address Space
IPv4 Address Space
IP Address Space & Subnetting - PART2 (10:32)
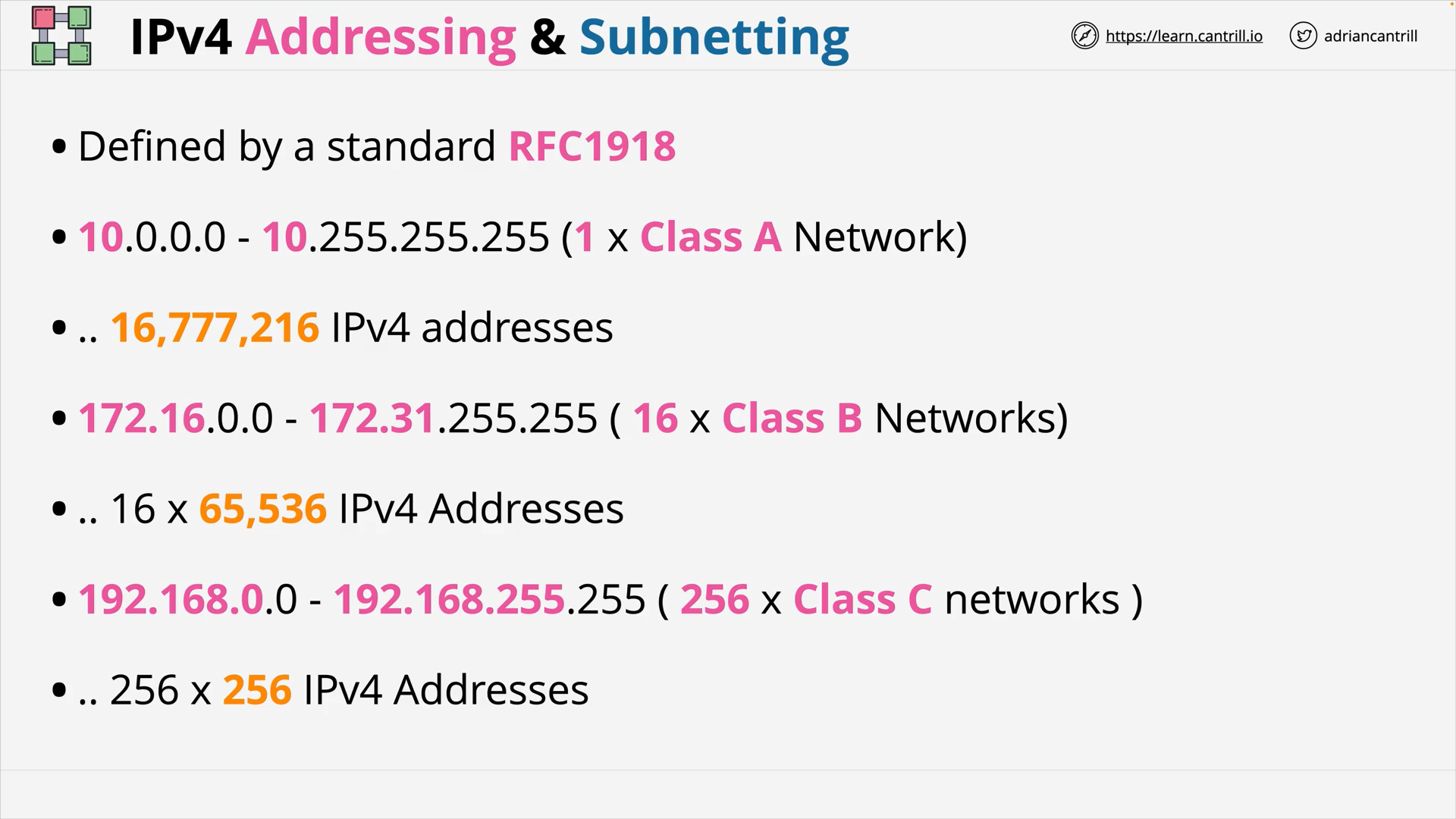 IPv4 - Private Ranges
IPv4 - Private Ranges
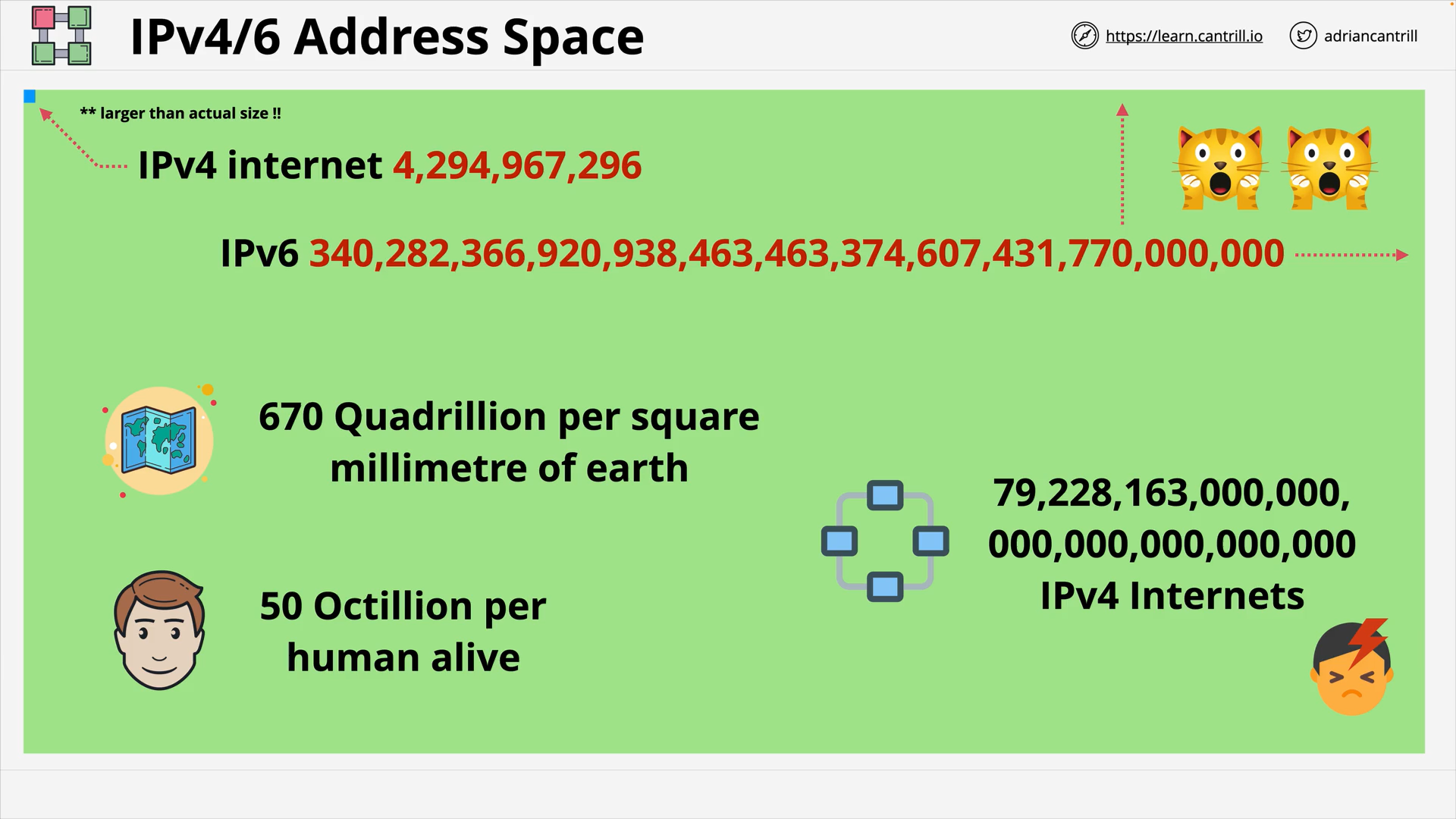 IPv4 vs IPv6 Address Space
IPv4 vs IPv6 Address Space
classless inter-domain routing (cidr)
A method for allocating IP addresses and for IP routing.
CIDR is introduced in 1993 to replace the previous classful network addressing architecture
subnetting
The process of spitting a larger network into more smaller subnets
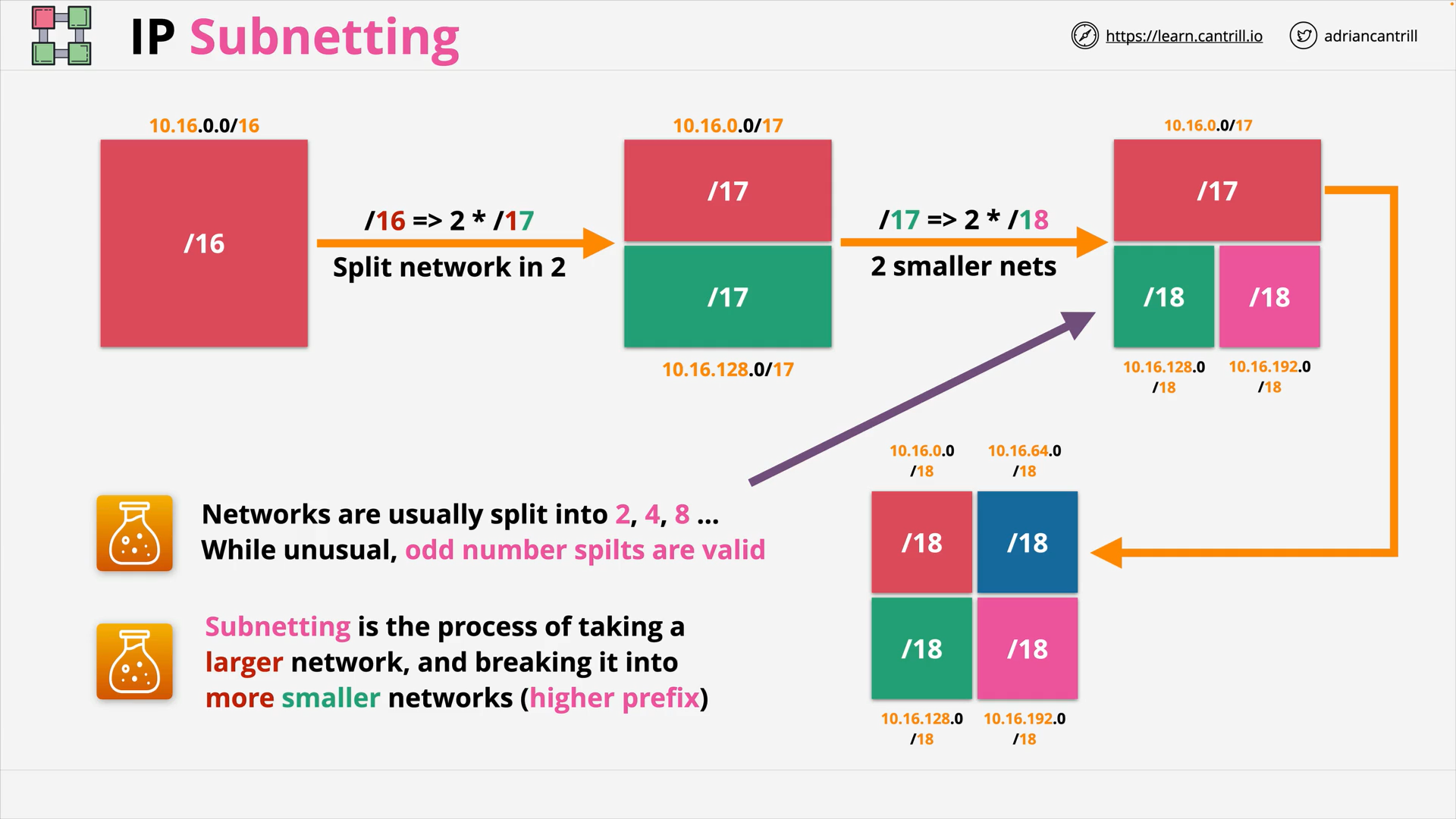 Subnetting and CIDR
Subnetting and CIDR
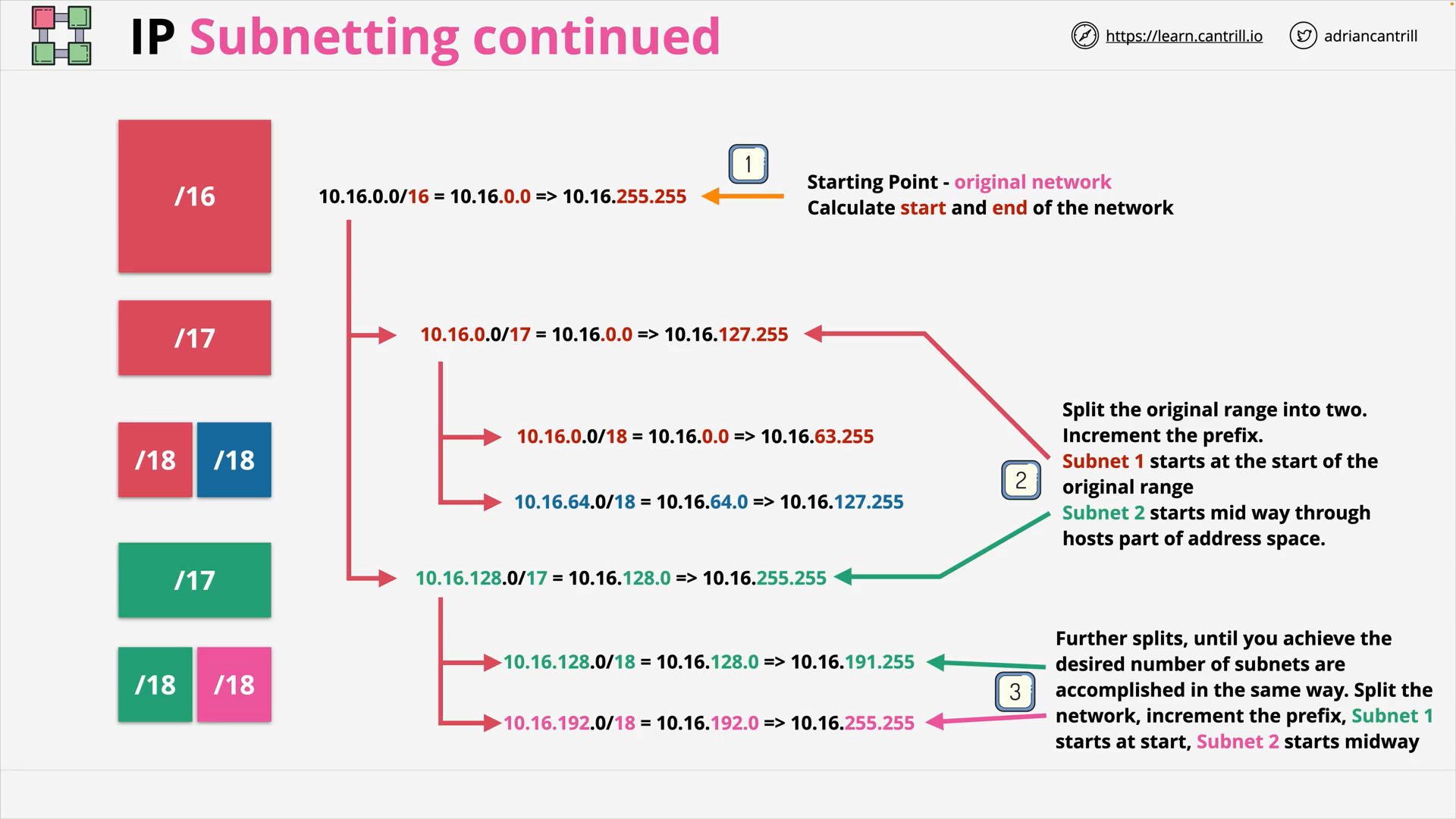 Subnetting - Start and end calculation
Subnetting - Start and end calculation
Distributed Denial of Service (DDOS) Attacks (14:35)
_Attacks__lear.png) DDOS - Overview
DDOS - Overview
ddos types:
- Layer 7:
- HTTP Flood
- DNS Fllod
- Layer 4:
- (TCP) SYN Flood
_Attacks__lear.png) Without DDOS - Normal App
Without DDOS - Normal App
_Attacks__lear.png) DDOS - Application Layer Attack (HTTP Flood)
DDOS - Application Layer Attack (HTTP Flood)
_Attacks__lear.png) DDOS - Protocol Attack (SYN Flood)
DDOS - Protocol Attack (SYN Flood)
_Attacks__lear.png) DDOS - Volumetric / Amplification Attack
DDOS - Volumetric / Amplification Attack
what is a ddos attack?
https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
VLANs, TRUNKS & QinQ (16:14)
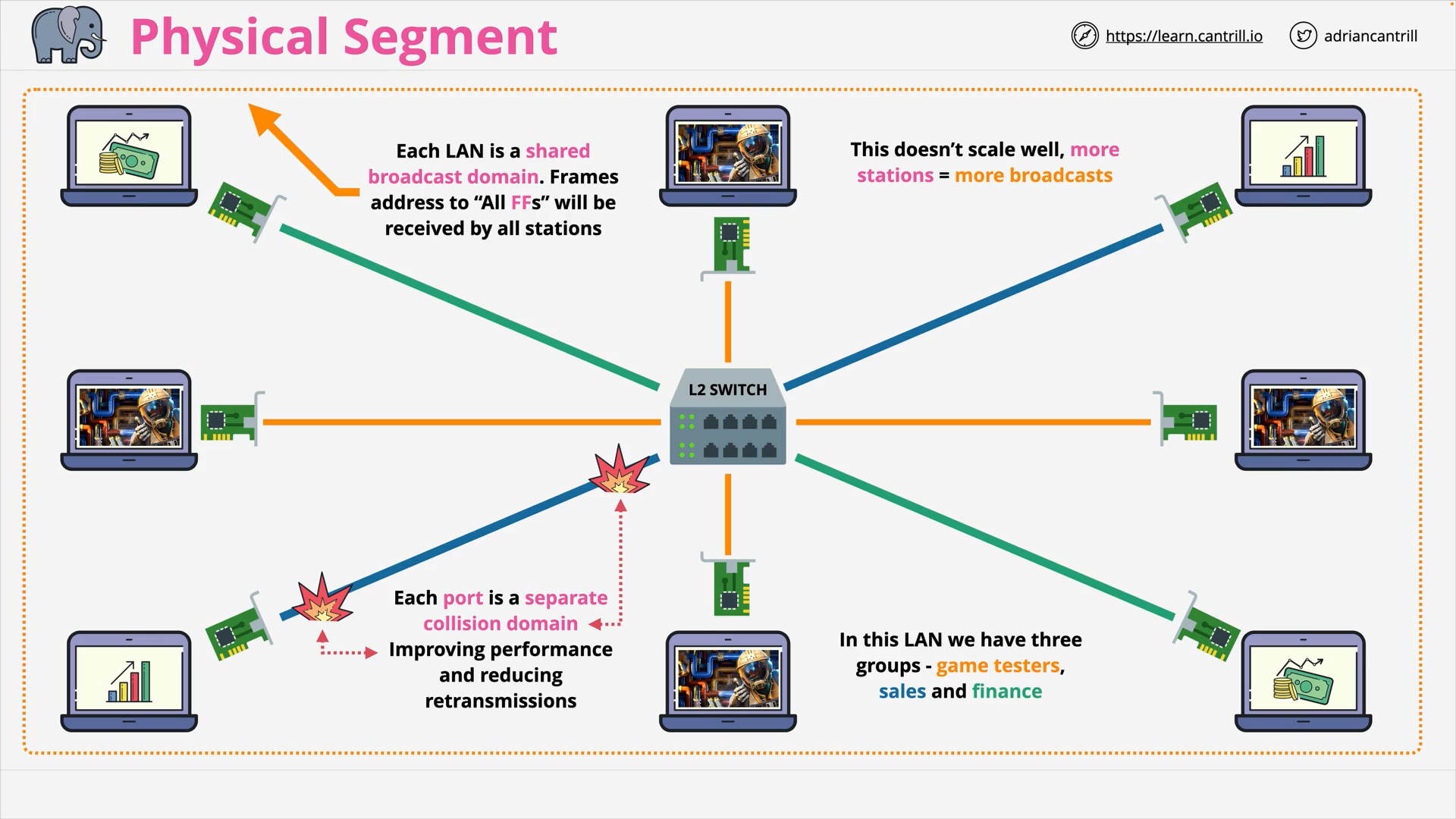 Physical Segment - 1 Switch
Physical Segment - 1 Switch
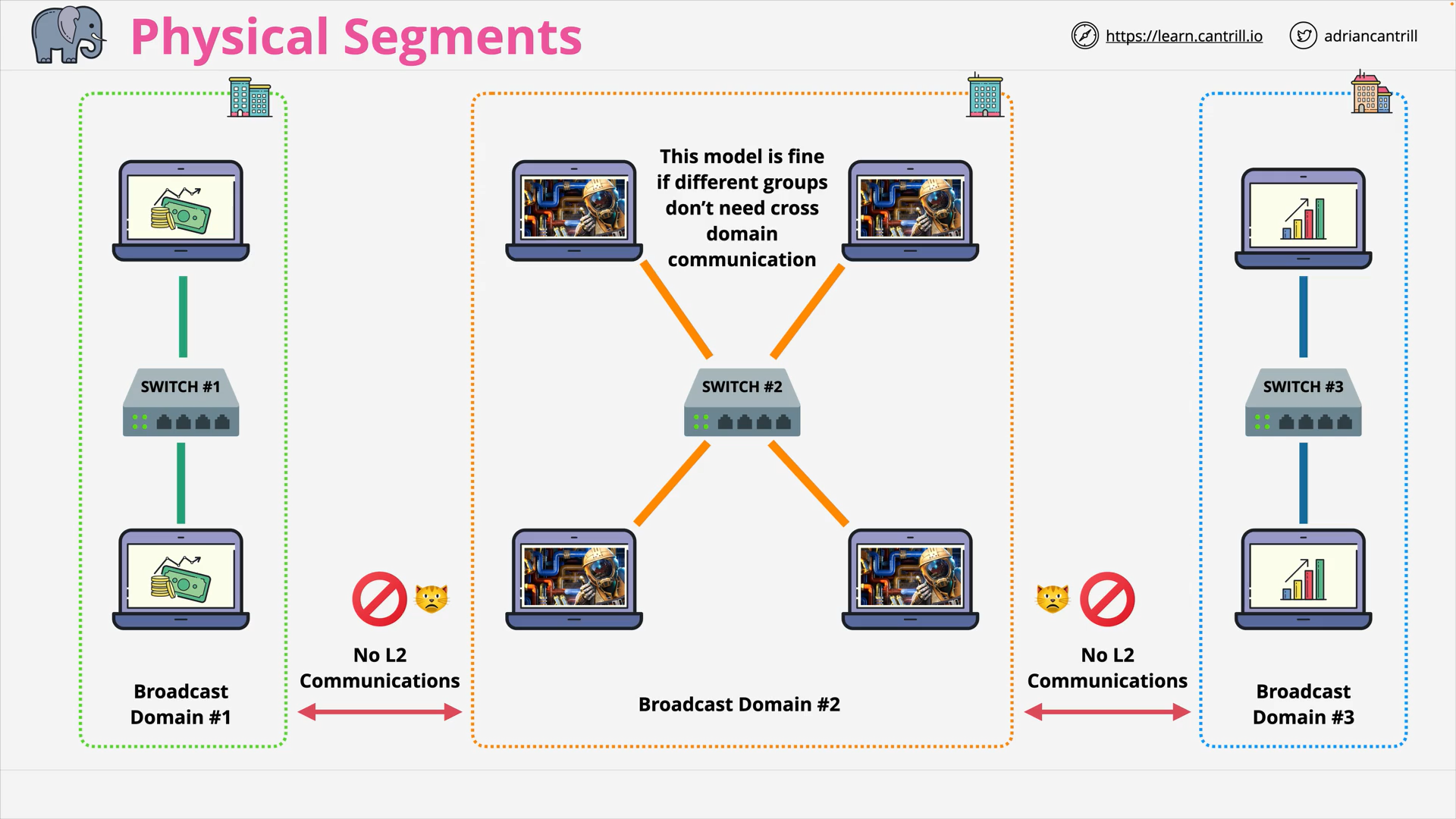 Physical Segment - Multi Switches
Physical Segment - Multi Switches
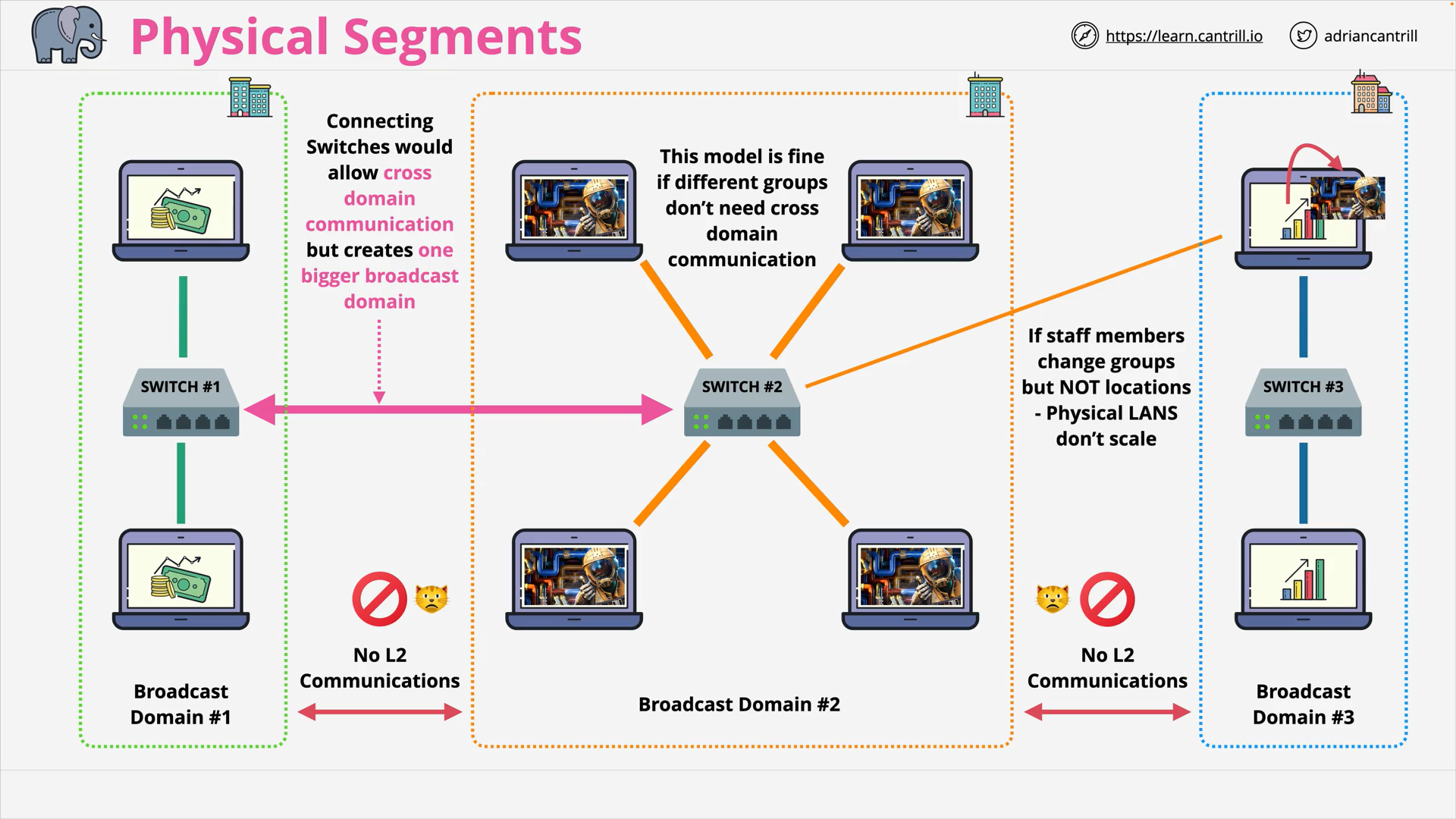 Physical Segment - Connecting Switches
Physical Segment - Connecting Switches
what is vlan?
A way to divide a single physical network into multiple logical networks.
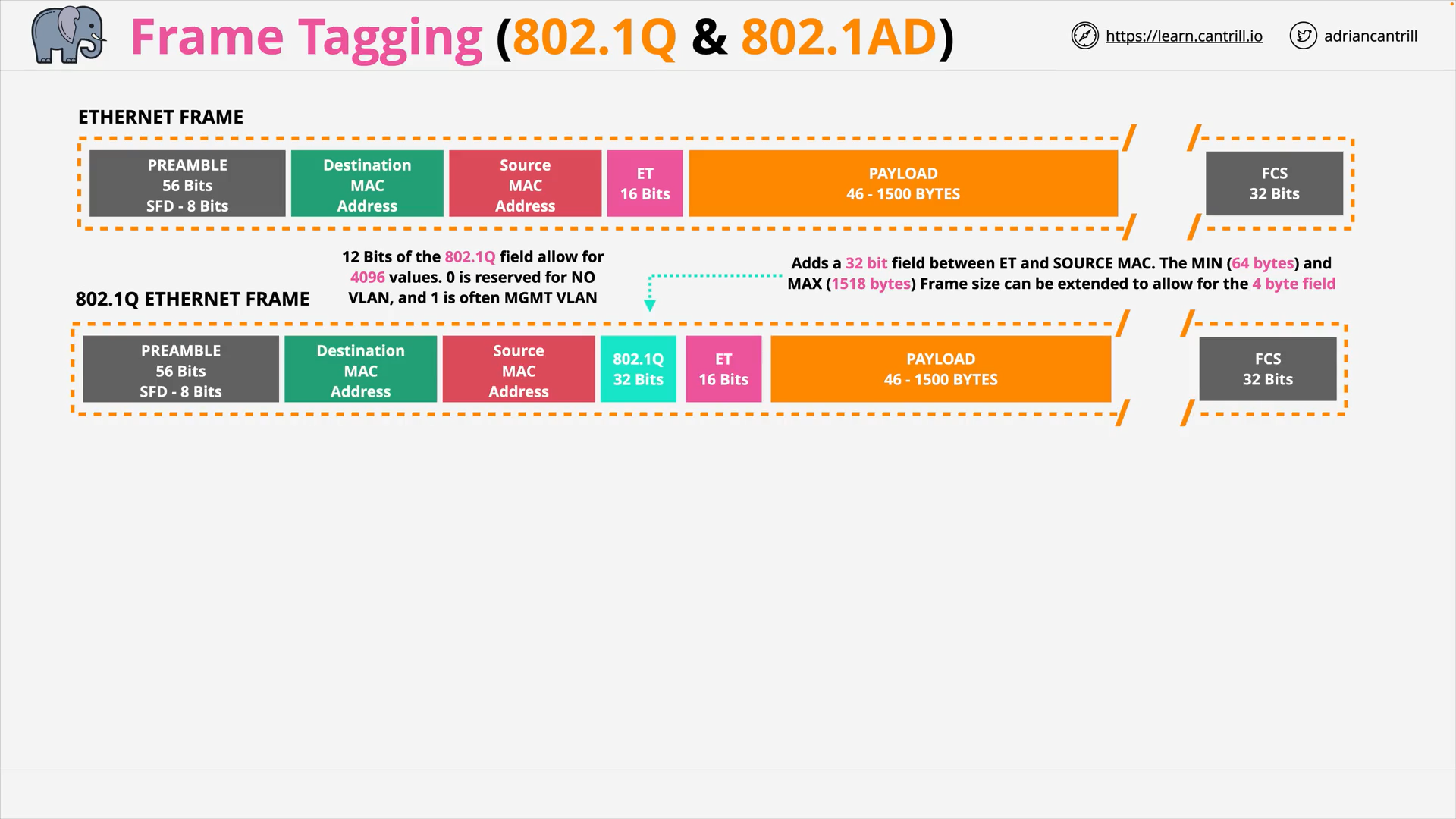 Frame Tagging - 802.1Q
Frame Tagging - 802.1Q
what does 802.1q do?
802.1Q allows multiple “VIRTUAL LANS (VLANS)” to operate over the same L2 physical network.
Each has a separate broadcast domain and is isolated from all others
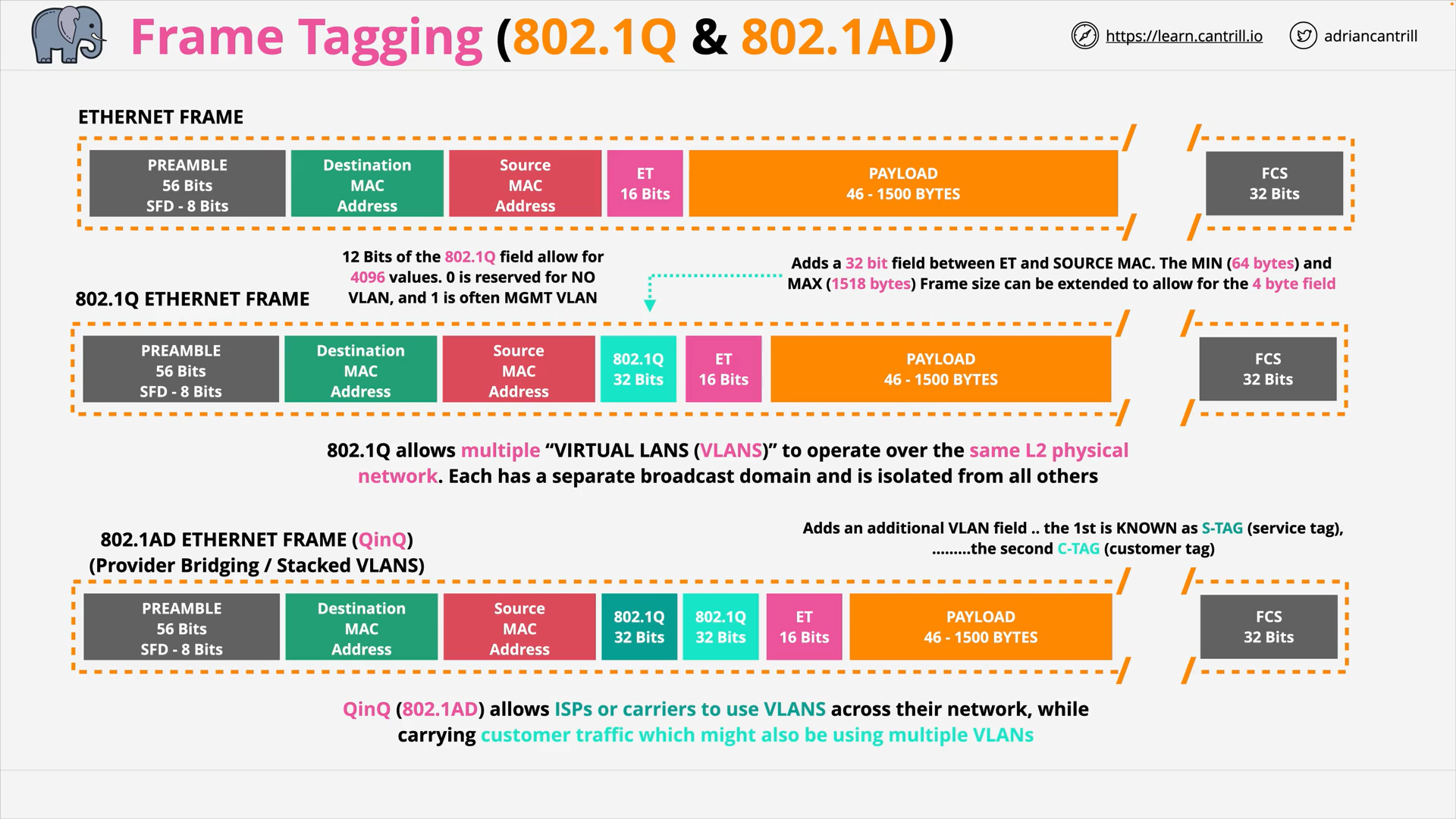 OSI Layer 2 - Frame Tagging - 802.1AD - QinQ
OSI Layer 2 - Frame Tagging - 802.1AD - QinQ
what does 802.1ad do?
802.1AD (QinQ) allows ISPs or carriers to use VLANS across their network, while carrying customer traffic which might also be using multiple VLANs
how does 802.1ad (qinq) work?
It allows multiple VLAN tags to be added to a single Ethernet frame.
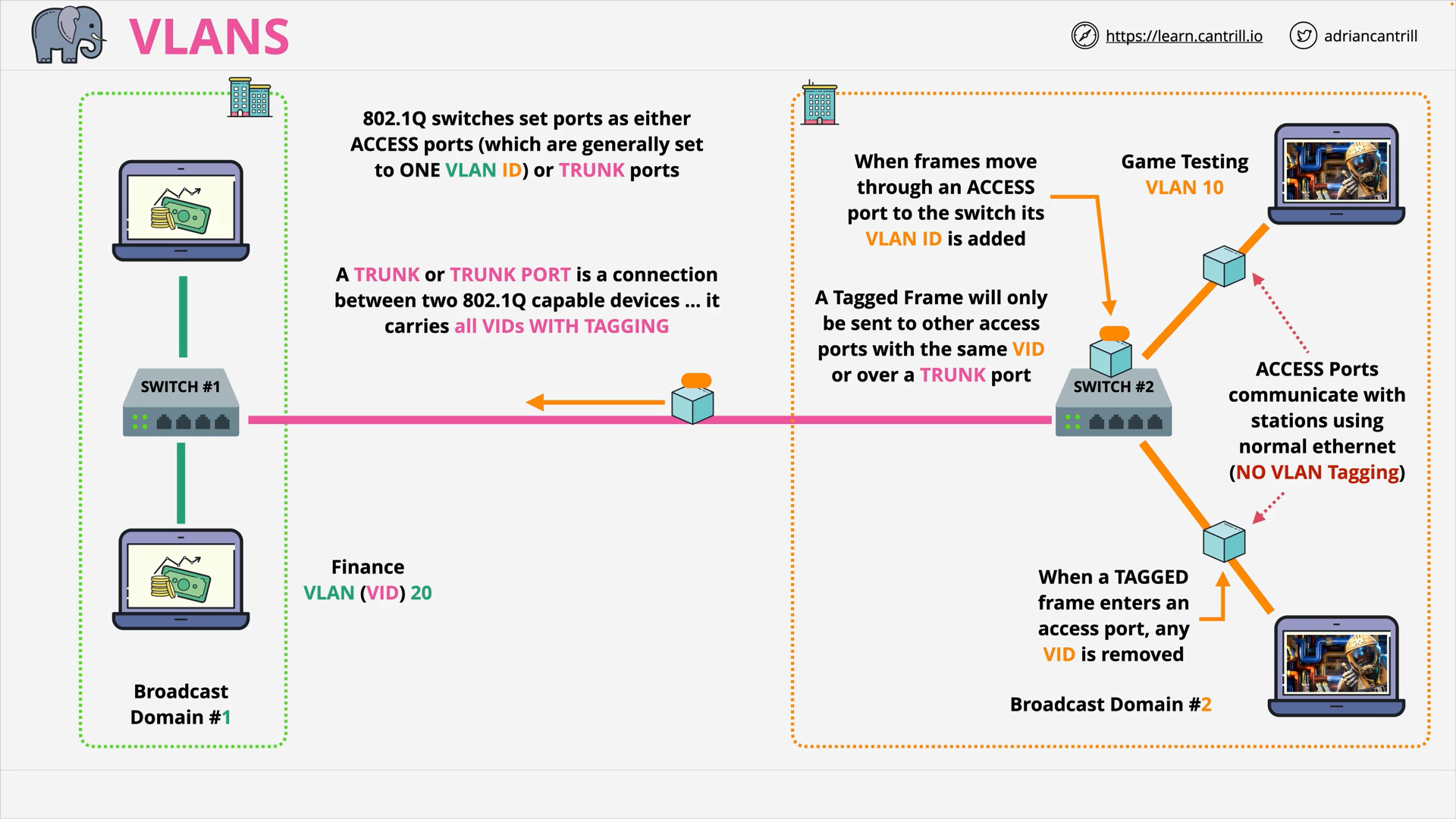 VLAN - Trunk Port vs Access Port
VLAN - Trunk Port vs Access Port
what are trunk port?
Trunk ports are a way to carry VLAN traffic between network switches
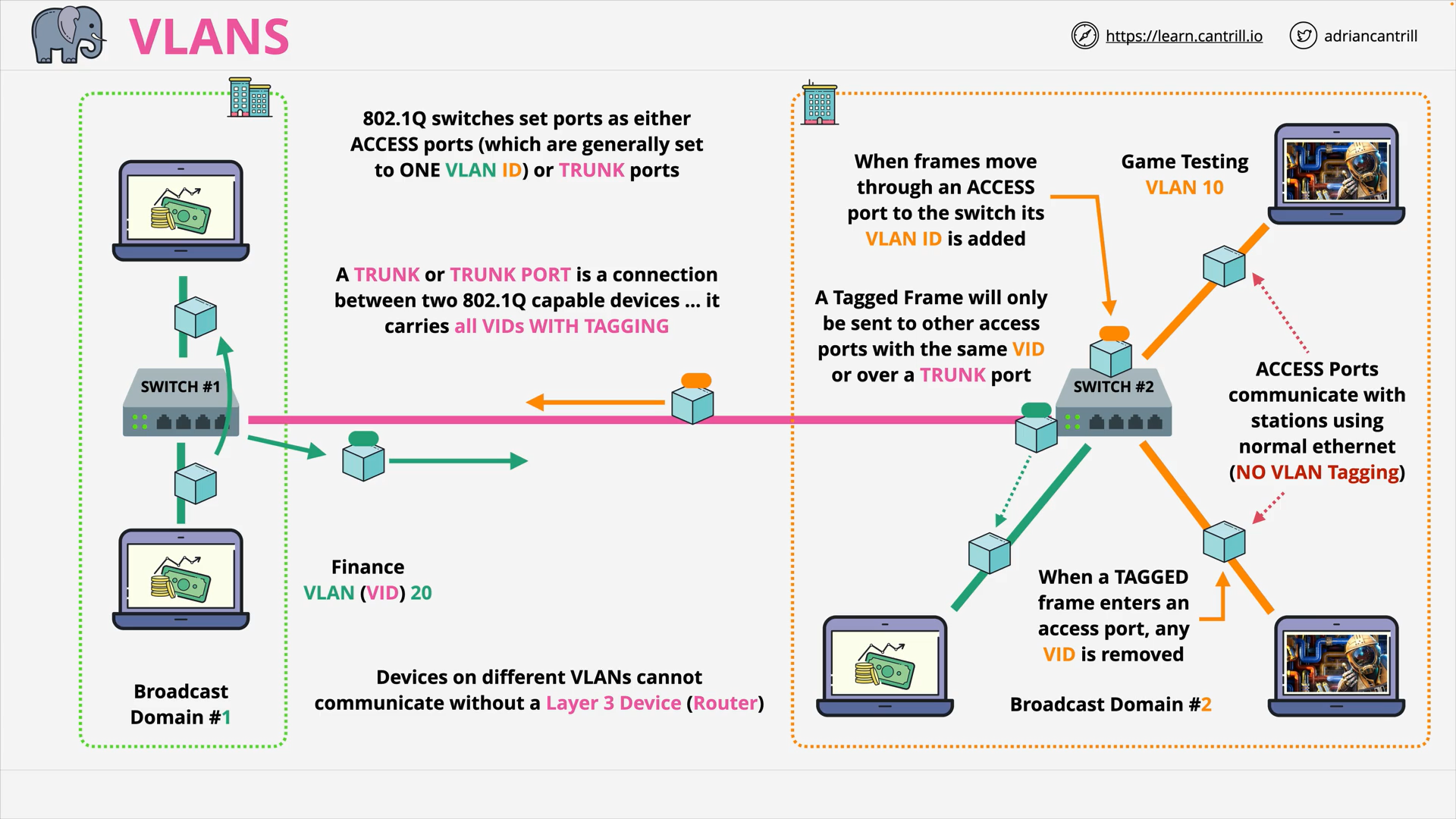 Devices on different VLANs cannot communicate without a Layer 3 Device (Router)
Devices on different VLANs cannot communicate without a Layer 3 Device (Router)
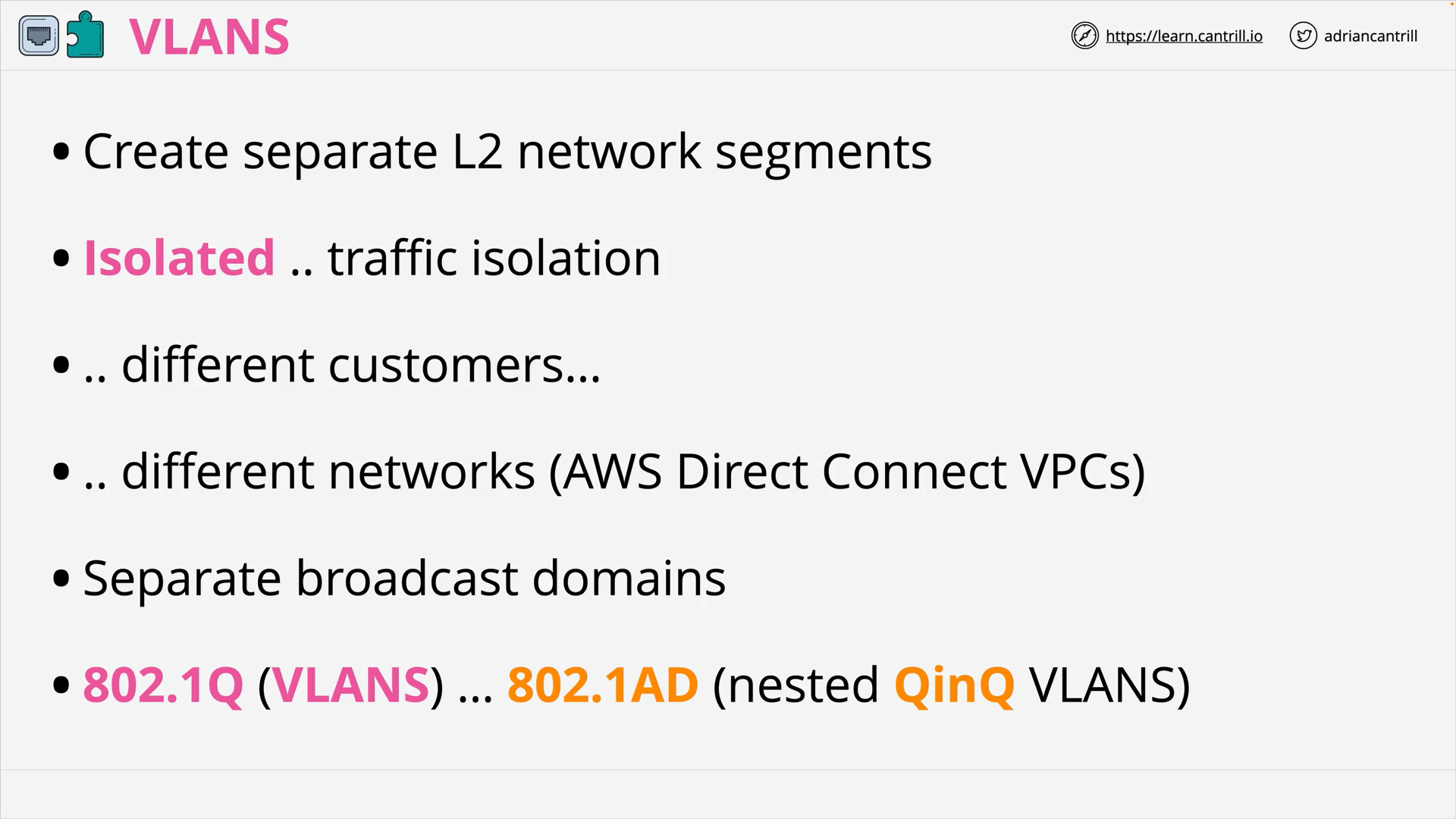 VLAN - Summary
VLAN - Summary
Decimal to Binary Conversion (IP Addressing) (17:12)
__lear.png)
__lear.png)
__lear.png)
SSL & TLS (11:19)
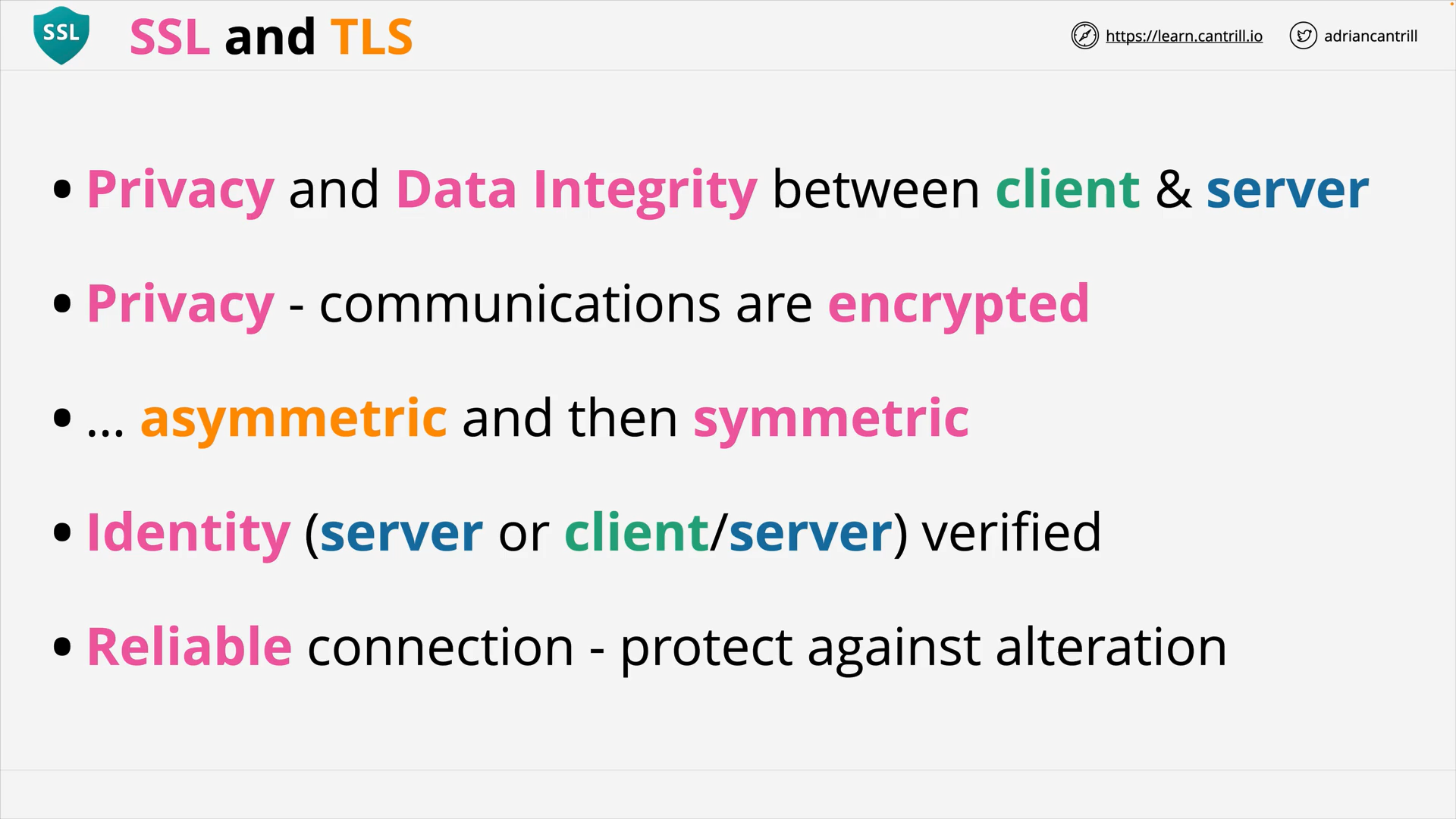
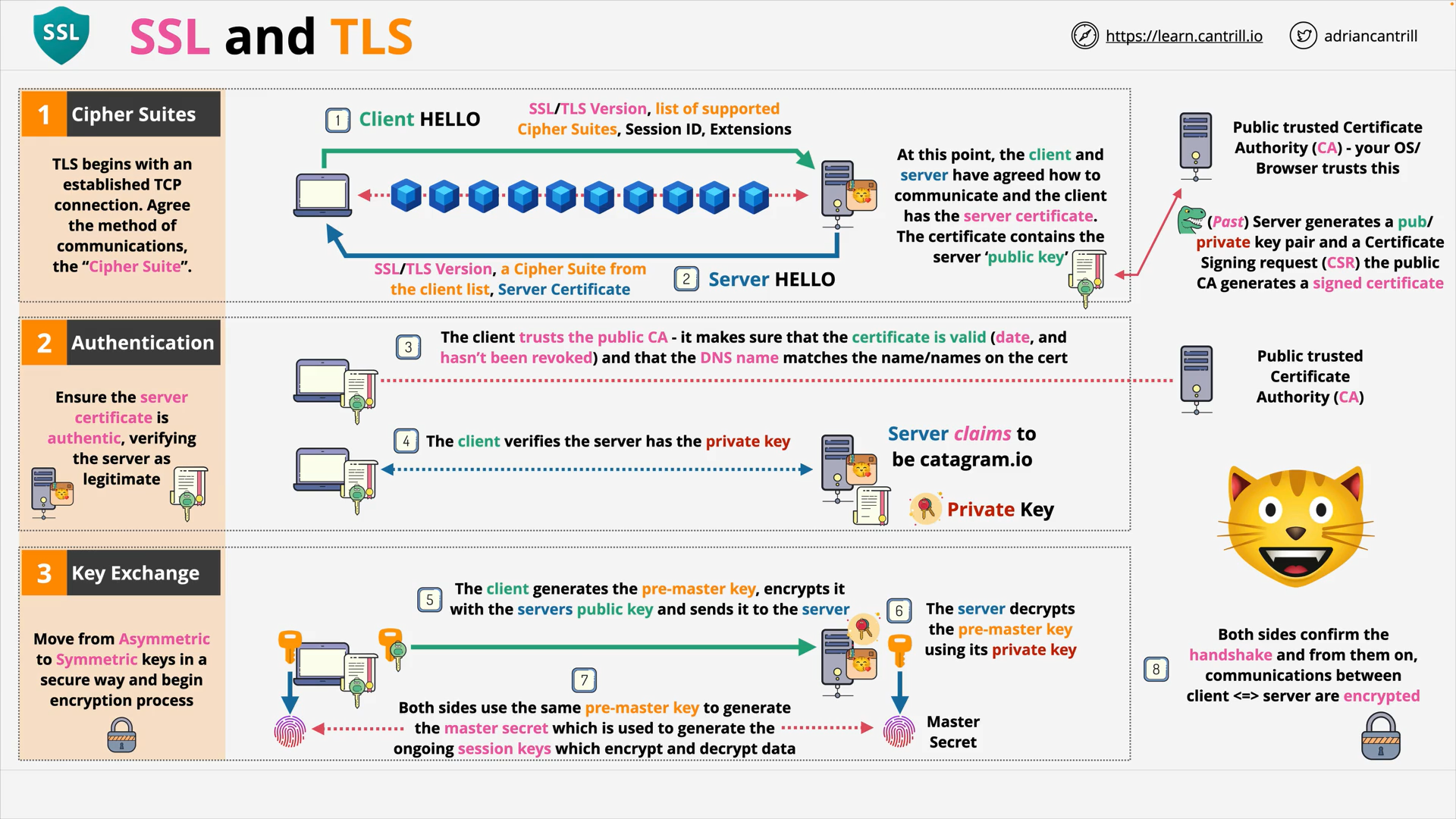
See The First Few Milliseconds of an HTTPS Connection
Border Gateway Protocol (BGP) 101 (17:03)
_101__learn.cantrill..png) BGP: Exchange the best path (ASPATH) to a destination
BGP: Exchange the best path (ASPATH) to a destination
_101__learn.cantrill..png) BGP: AS will advertise all the shortest paths its known to all its peers (and prepends its own ASN onto the path)
BGP: AS will advertise all the shortest paths its known to all its peers (and prepends its own ASN onto the path)
aspath prepending: make a path longer
Stateful vs Stateless Firewalls (14:04)
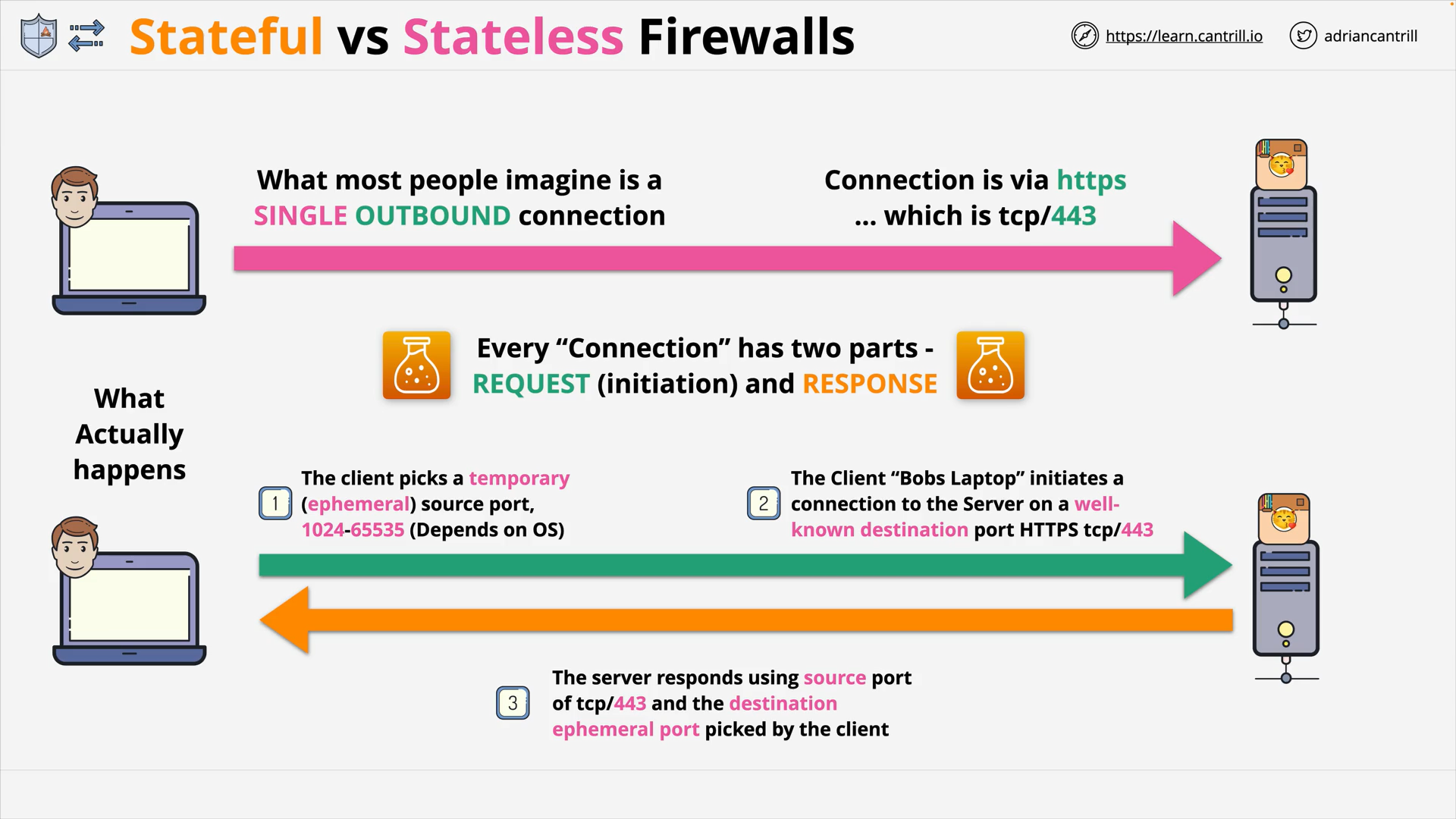 Connection’s Inbound and Outbound
Connection’s Inbound and Outbound
connection and port
A connection has 2 parts:
- Request: From an ephemeral port - chosen by the client - (to a well-known port)
- Response: From the well-known port (to that ephemeral port)
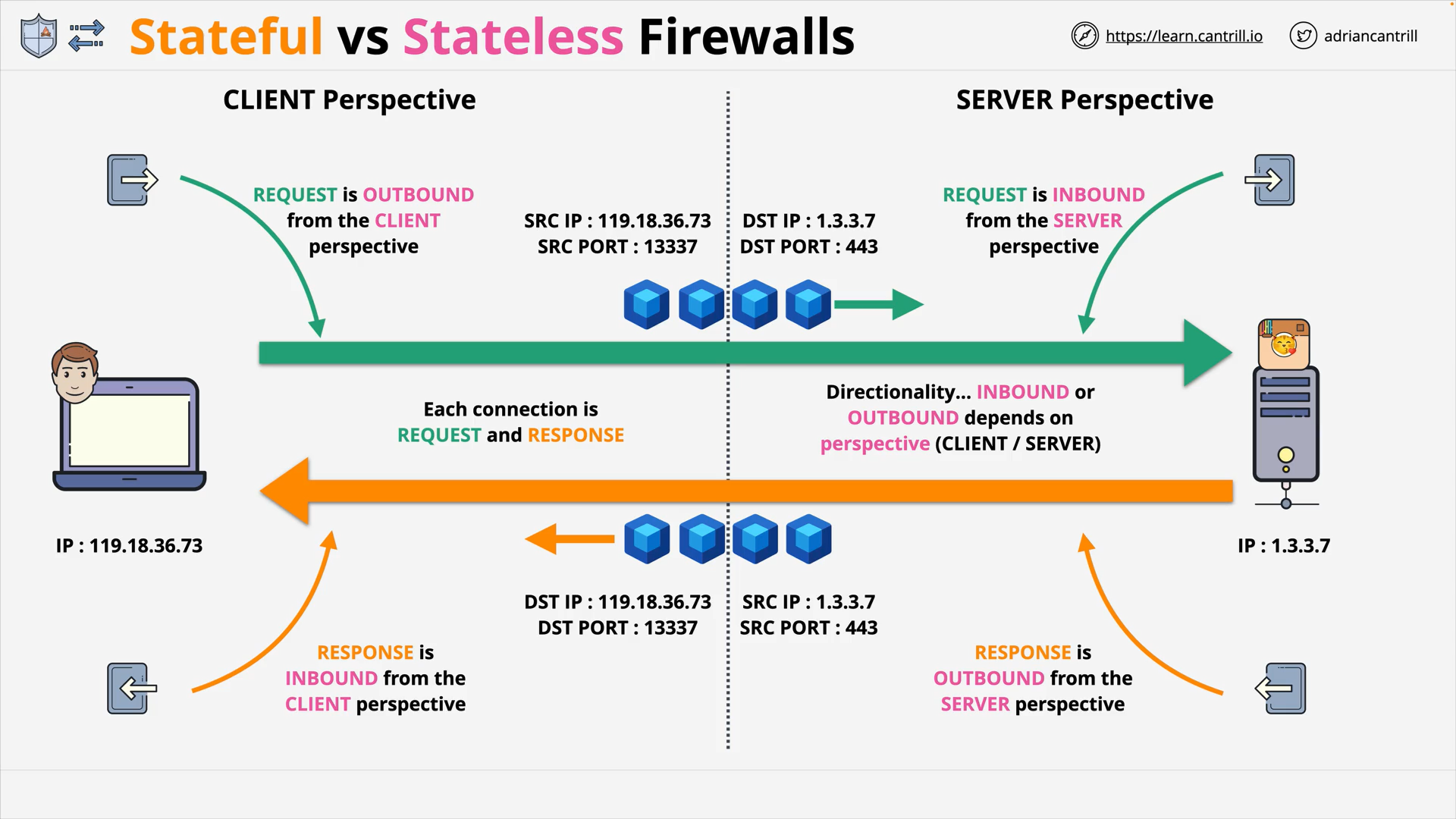 Inbound and Outbound are depend on perspective
Inbound and Outbound are depend on perspective
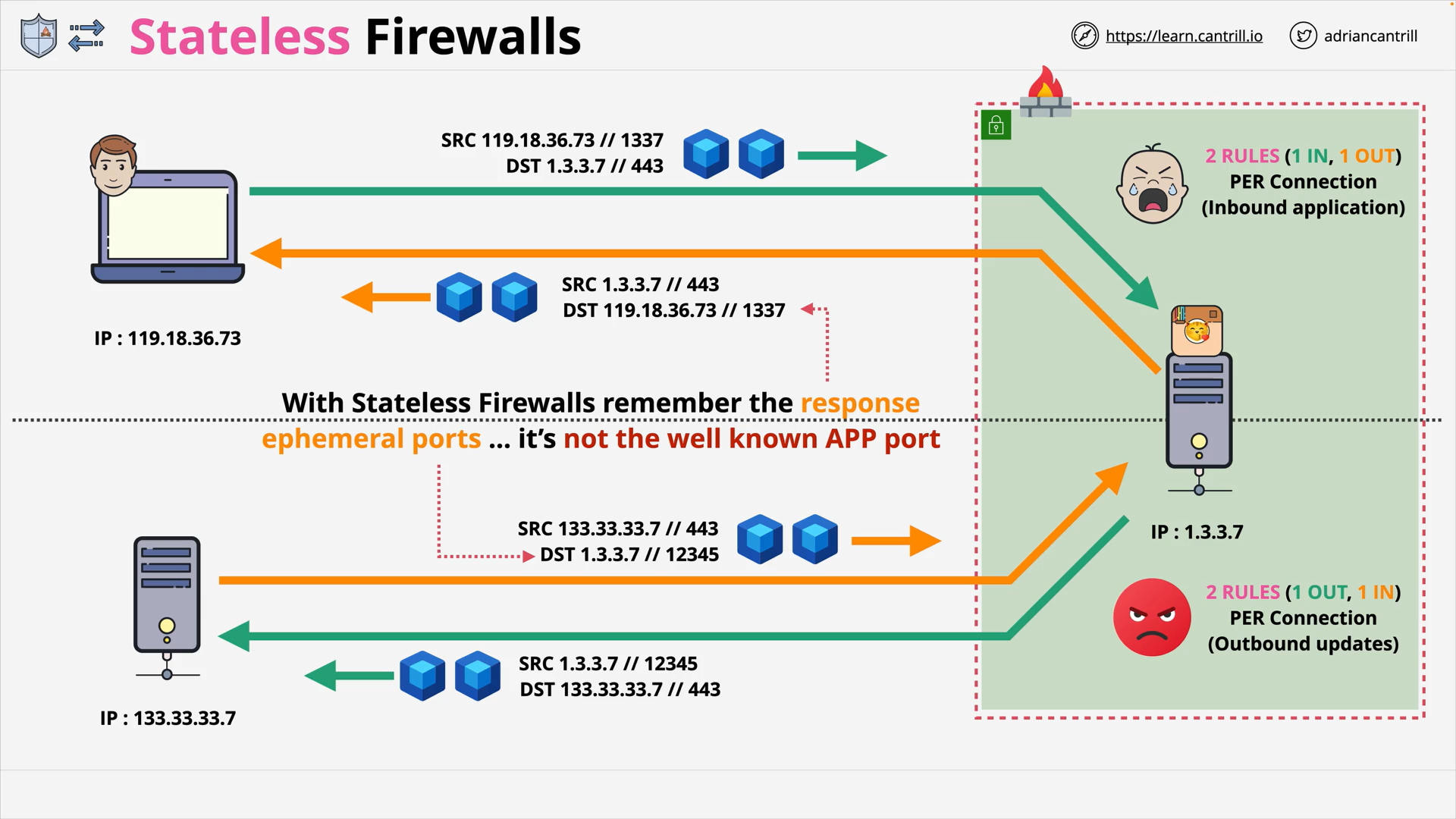 Stateless Firewall
Stateless Firewall
stateless firewall
A Stateless Firewall
- examines each individual network packet in isolation
- makes decisions
- based on predetermined rules
- without any awareness of the state of the network connection
stateless firewall and server
When using stateless firewall with a server, you need to:
- Allow inbound traffic to well-known port, e.g.
443 - Allow outbound traffic to all ephemeral ports, e.g.
1024,65535(randomly chosen by the client)
e.g. AWS Network ACL
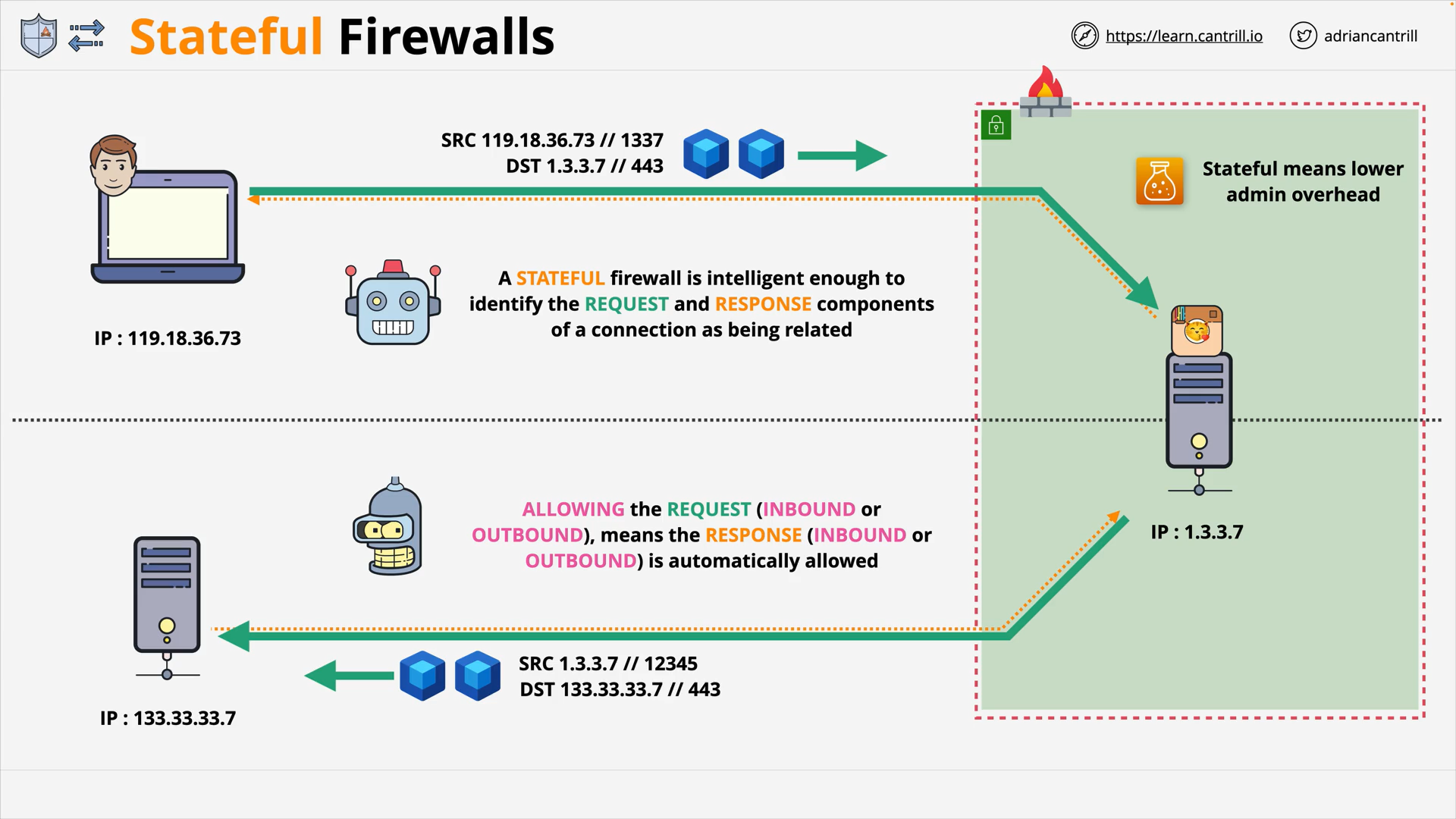 Stateful Firewall
Stateful Firewall
stateful firewall
A stateful firewall
- tracks the state of the network connections:
- knows a response corresponding to which request
- make decisions based on these knowledge:
- do some of the works for you
👉 If
- the request (no matter whether it’s inbound or outbound traffic) is allowed
- the response will be automatically allowed too
e.g. AWS security group
tip
Usually:
- A stateful firewall is called “firewall”.
- A stateless firewall is called ACL.
When something is called firewall, it usually means it’s a stateful firewall.
JumboFrames (4:35)
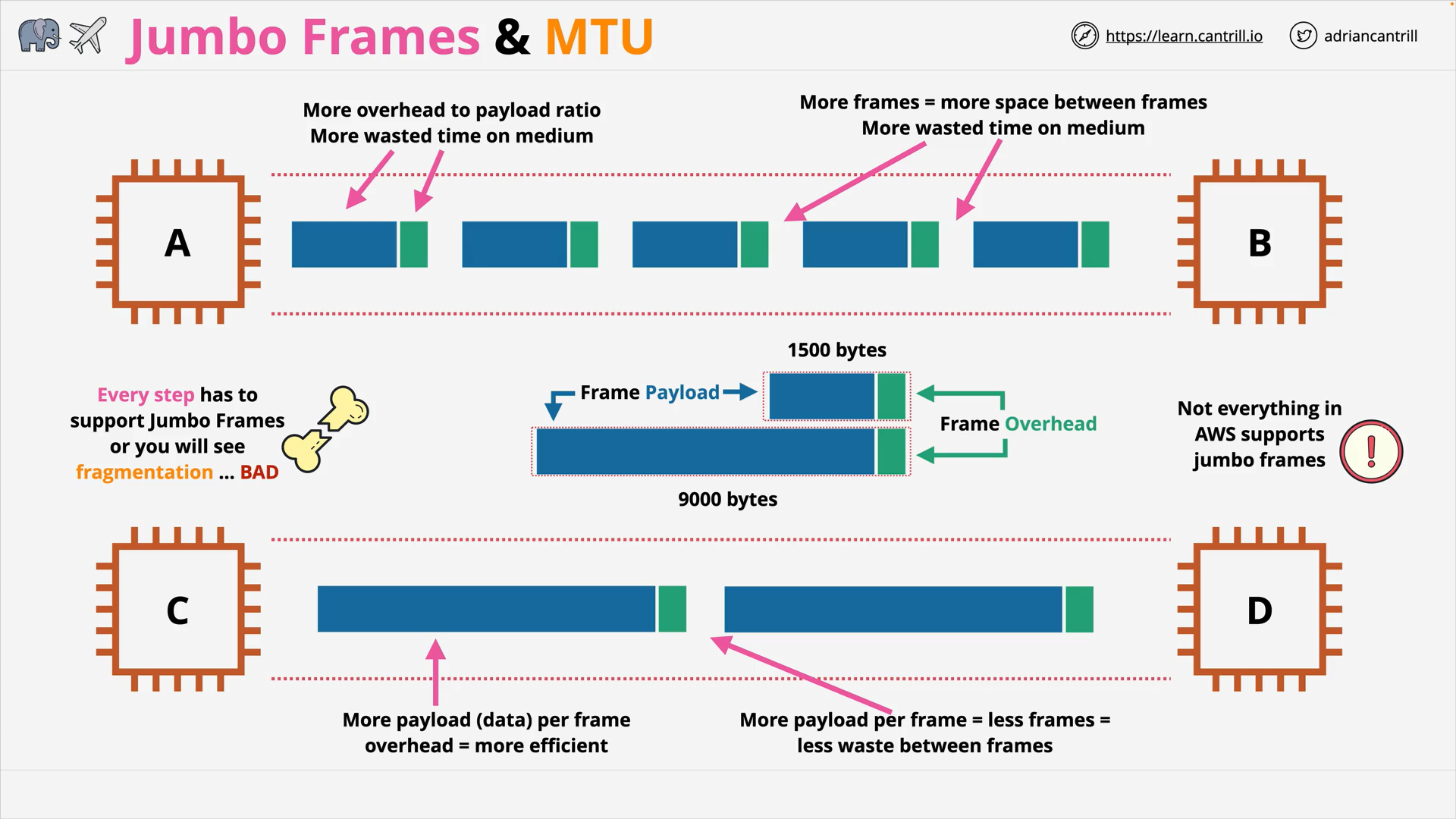 JumboFrame vs normal frame (OSI Layer 2)
JumboFrame vs normal frame (OSI Layer 2)
maximum transmission unit (mtu)
- Traditional Ethernet frames have a MTU of 1500 bytes.
- Jumbo Frames can allow for frames up to 9000 bytes.
why use jumbo frames
- Reduce frame overhead
- Reduce wasted time on medium (between frames)
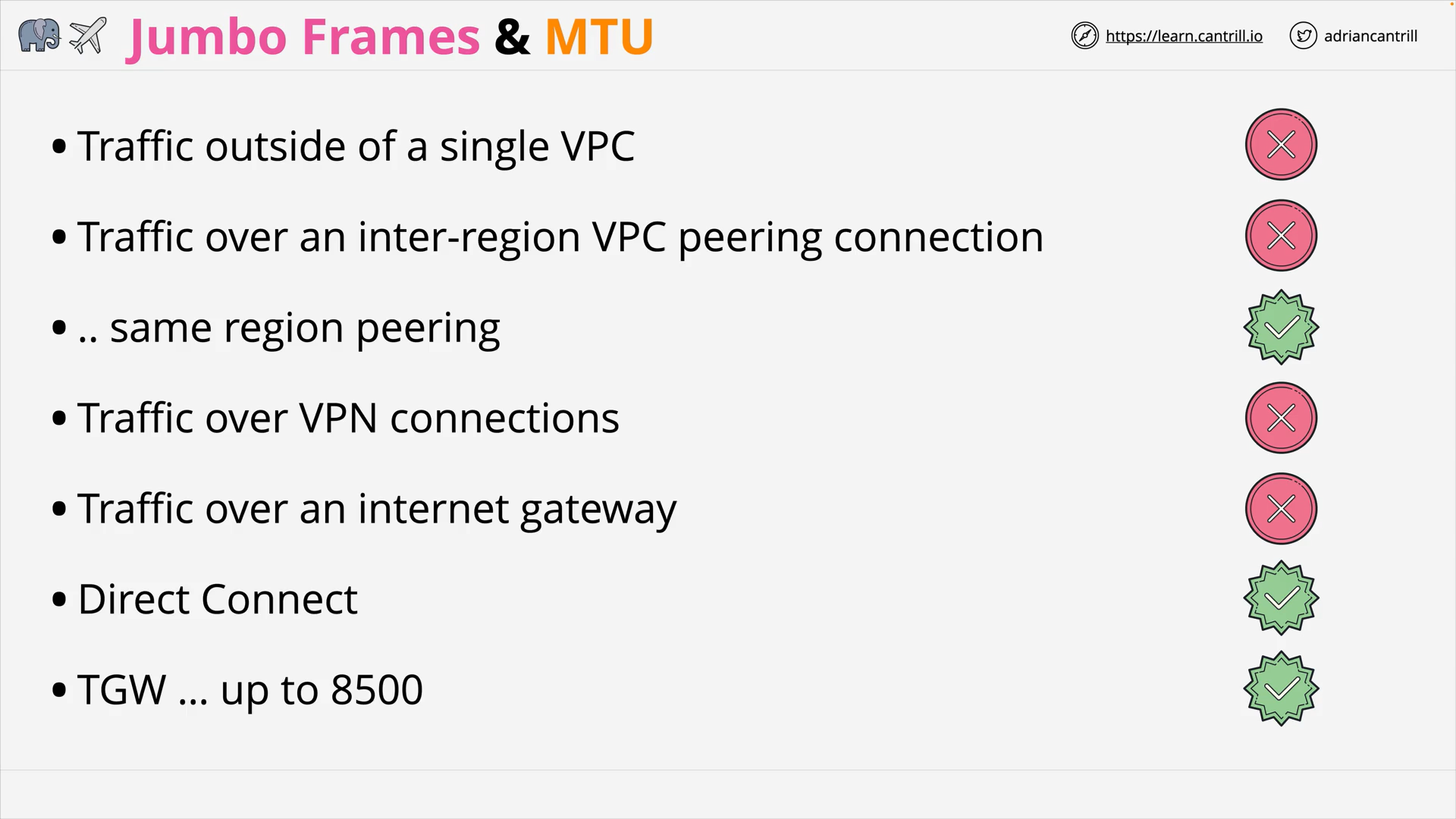 Not everything in AWS supports JumboFrames
Not everything in AWS supports JumboFrames
in aws, which traffic supports jumbo frames?
- VPC Peering in same region
- Direct Connect
- TGW (up to 8500 bytes)
Layer 7 Firewalls (7:44)
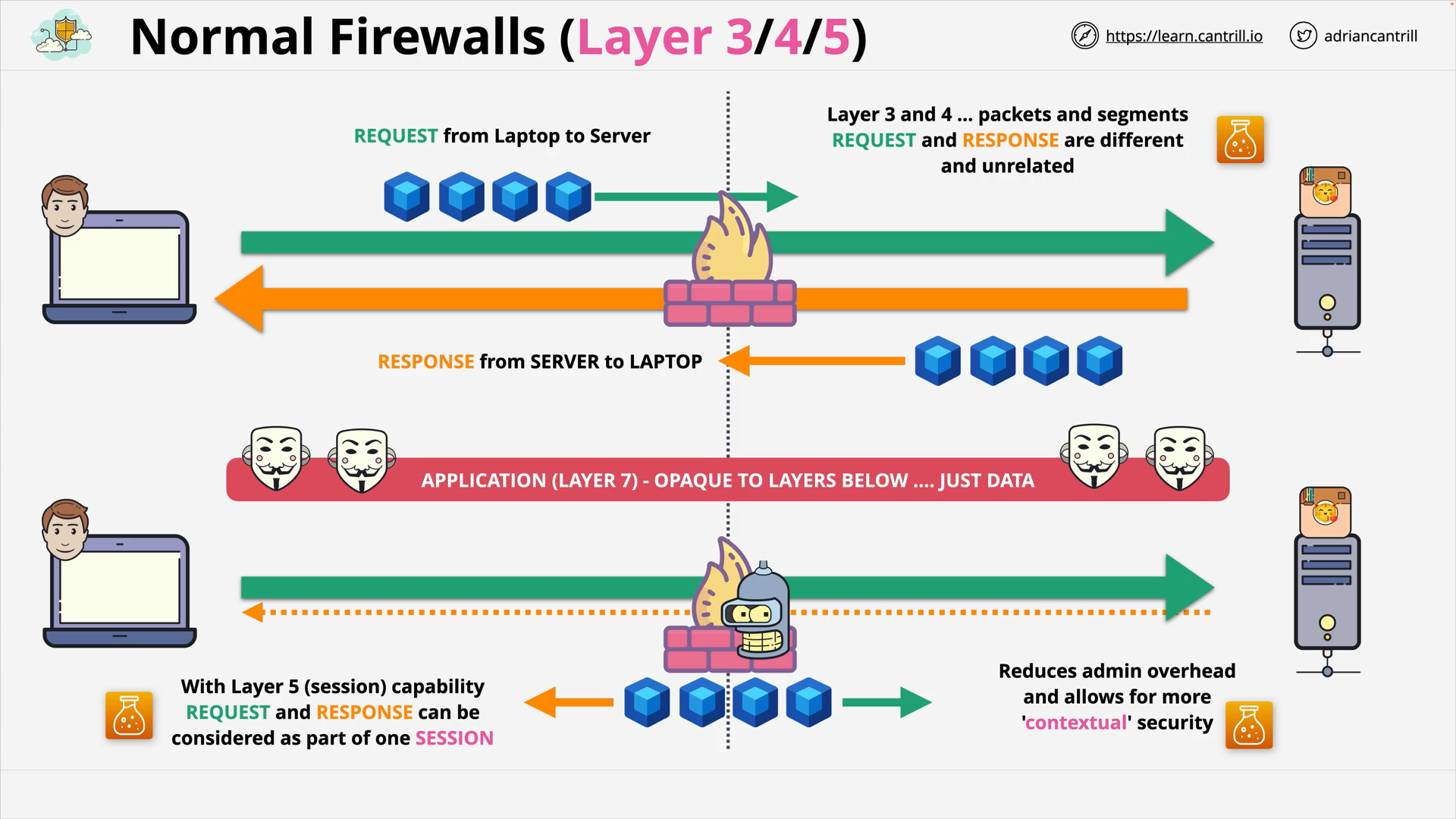 Traditional firewalls, such as packet filtering or stateful inspection firewalls, operate at the network and transport layers and are only capable of filtering traffic based on IP addresses, port numbers, and protocol types.
Traditional firewalls, such as packet filtering or stateful inspection firewalls, operate at the network and transport layers and are only capable of filtering traffic based on IP addresses, port numbers, and protocol types.
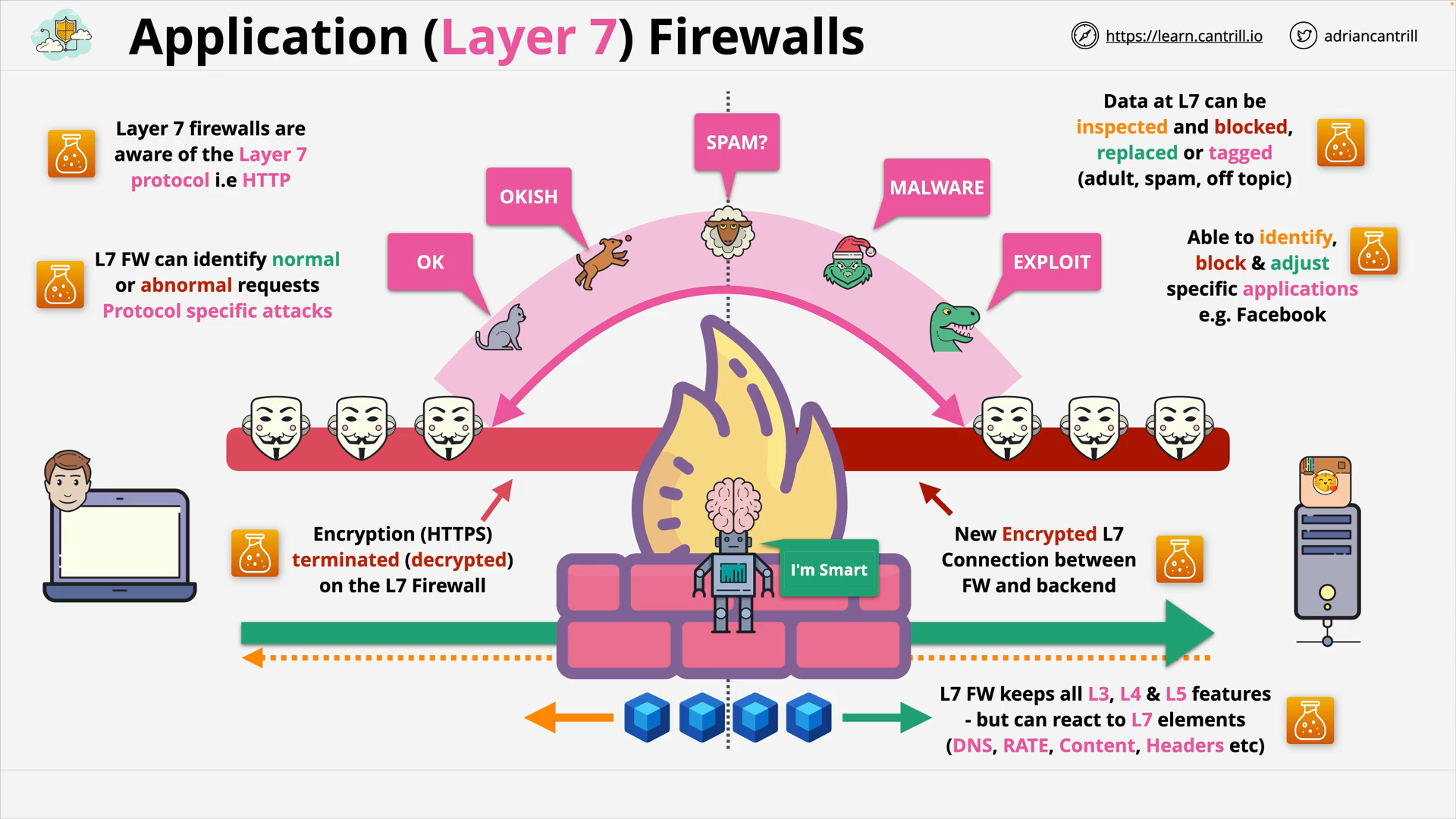 In contrast, layer 7 firewalls have the ability to analyze the content of network traffic, including application protocols such as HTTP, FTP, and SMTP, and can make more granular decisions about which traffic should be allowed or blocked.
In contrast, layer 7 firewalls have the ability to analyze the content of network traffic, including application protocols such as HTTP, FTP, and SMTP, and can make more granular decisions about which traffic should be allowed or blocked.
layer 7 firewall
| Feature | Traditional Firewalls (Packet Filtering/Stateful Inspection) | Layer 7 Firewalls (Application Firewalls) |
|---|---|---|
| Layer of Operation | Network and Transport Layers (Layer 3 & 4) | Application Layer (Layer 7) |
| Filtering Criteria | IP addresses, Port numbers, Protocol types | Application data, HTTP/FTP/SMTP, user inputs |
| Traffic Inspection | Basic packet-level inspection | Deep packet inspection of application data |
| Granularity | Coarse-grained (limited to IP, port, protocol) | Fine-grained (based on application content) |
| Protection against | Basic network attacks (IP spoofing, SYN floods) | Advanced threats (SQL injection, XSS, malware) |
| Policy Control | Limited to low-level network policies | Application-specific policies (e.g., block specific URLs) |
| Performance | Higher throughput due to simpler inspection | Potentially slower due to deep inspection |
| Complexity | Simpler to configure and manage | More complex, requires detailed understanding of applications |
| Use Case | Basic security for network and transport layers | Protection of web and application services |
| Examples of Applications | Firewall rules based on IP, Port, and Protocol | Web Application Firewall (WAF), API Gateways |
See Nord Security - Learning Center
IP Sec VPN Fundamentals (14:48)
 IPSec
IPSec
what does ip sec do?
IP Sec sets up secure tunnel across insecure networks.
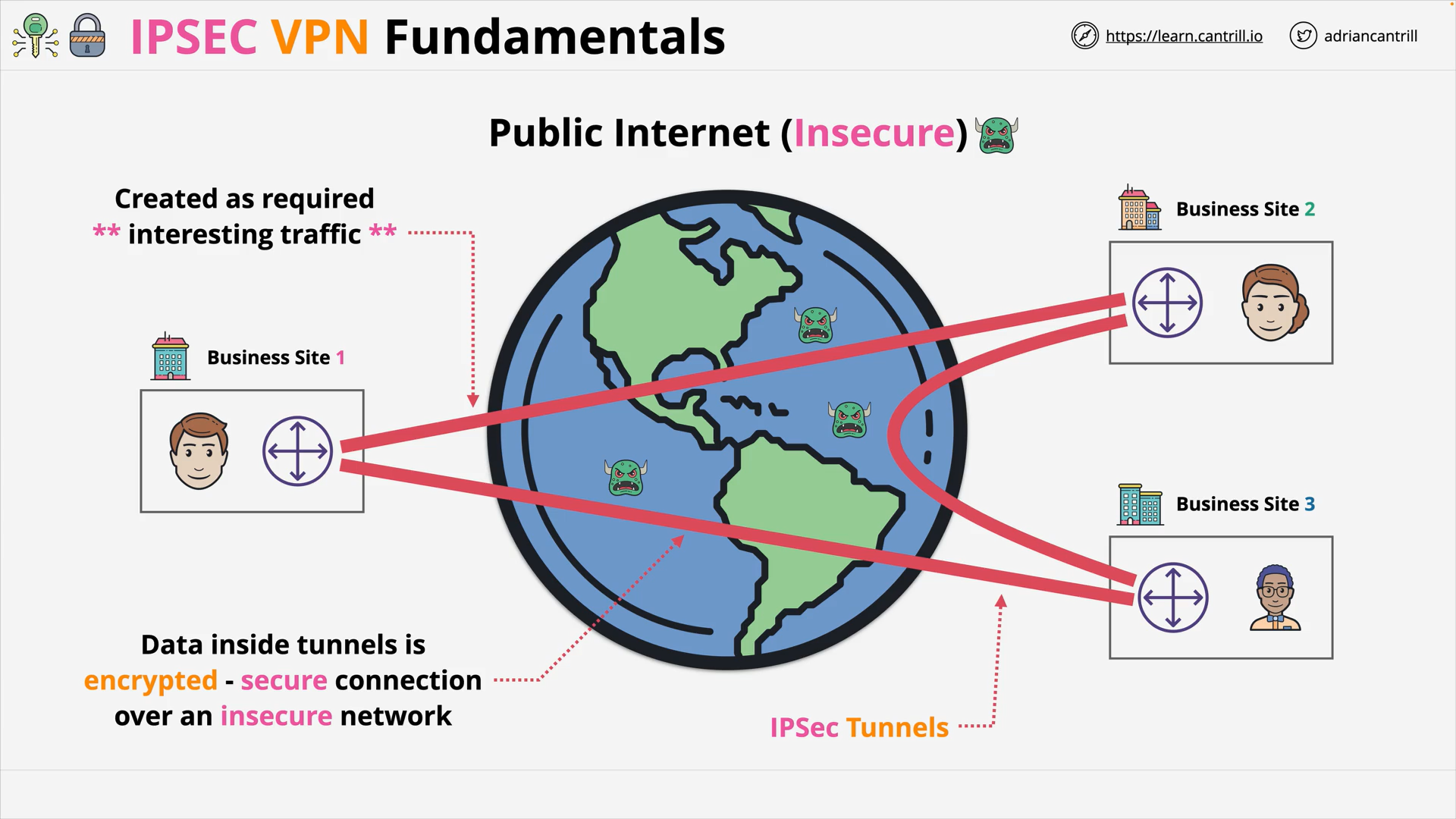 IP Sec Tunnel
IP Sec Tunnel
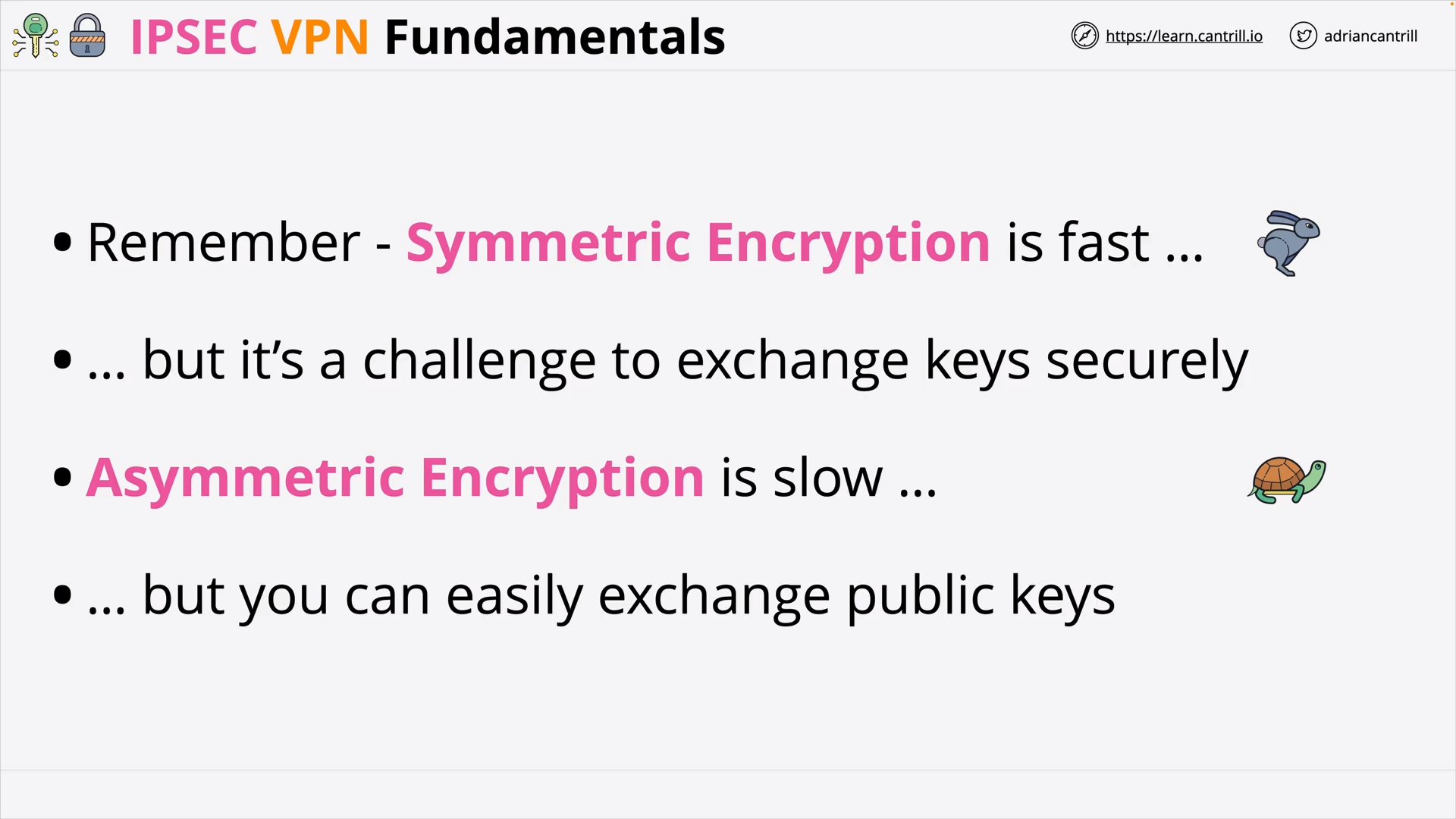 Asymmetric/Symmetric Encryption
Asymmetric/Symmetric Encryption
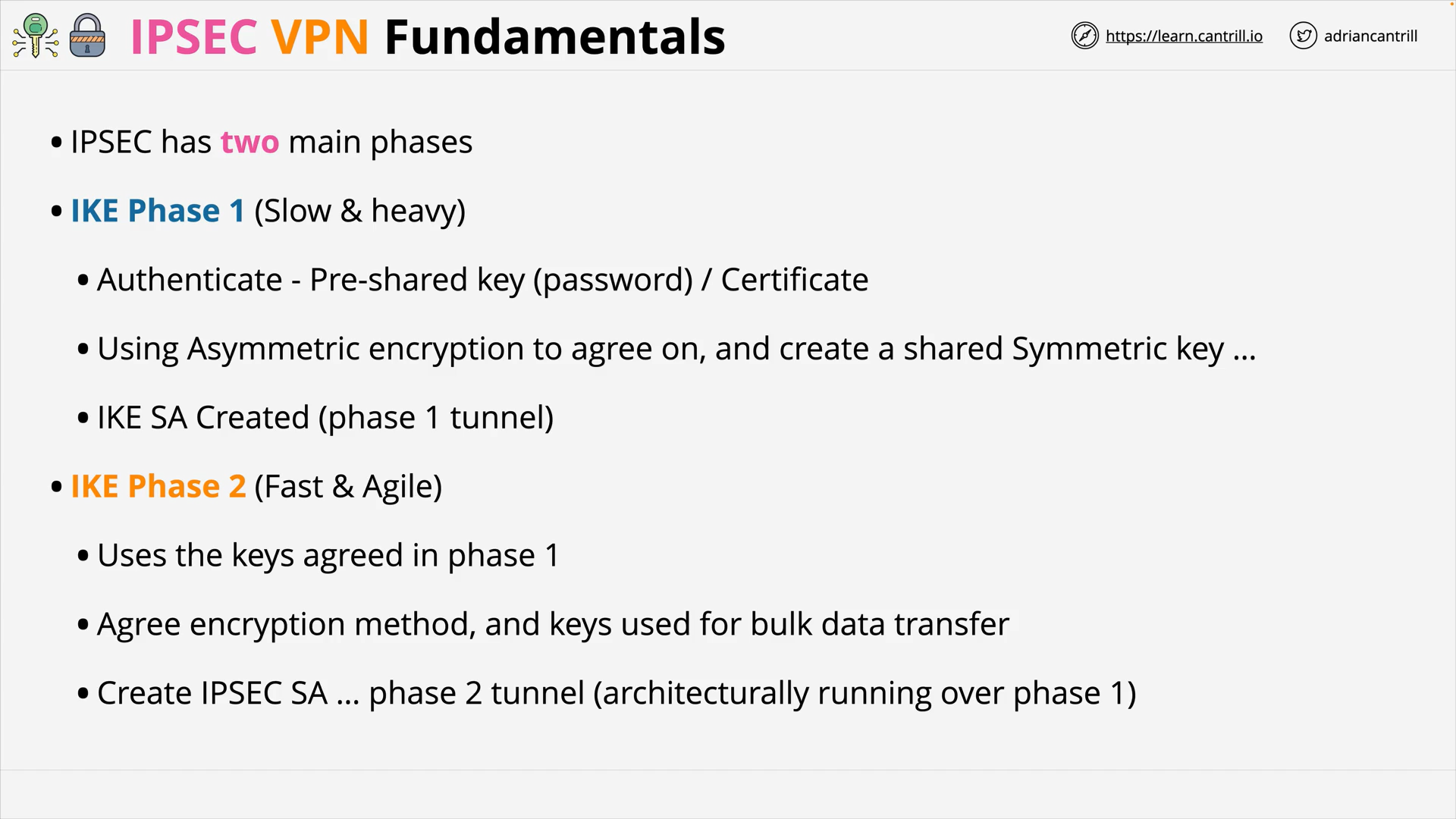 IP Sec’s 2 main phases
IP Sec’s 2 main phases
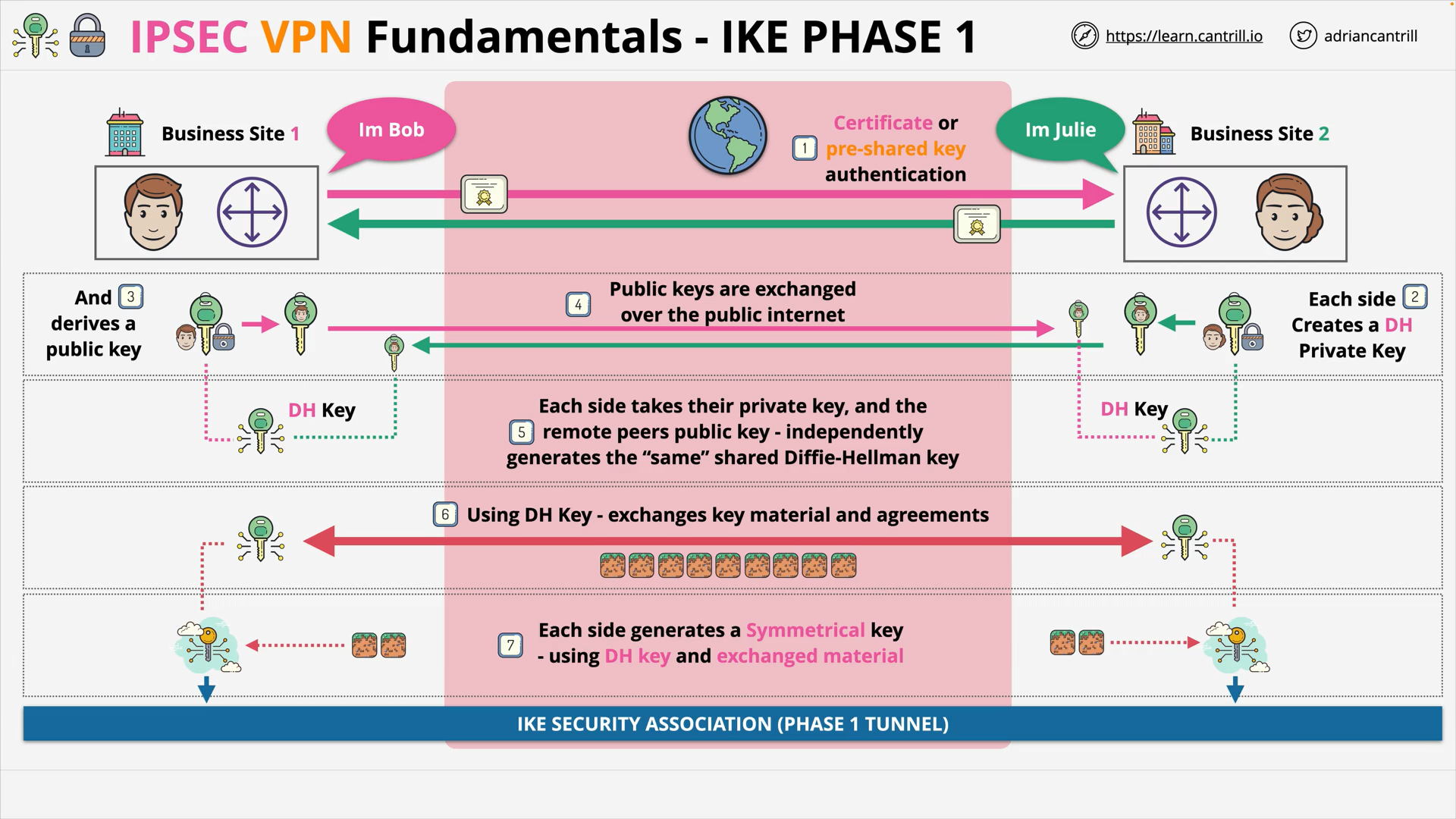 IP Sec - IKE Phase 1
IP Sec - IKE Phase 1
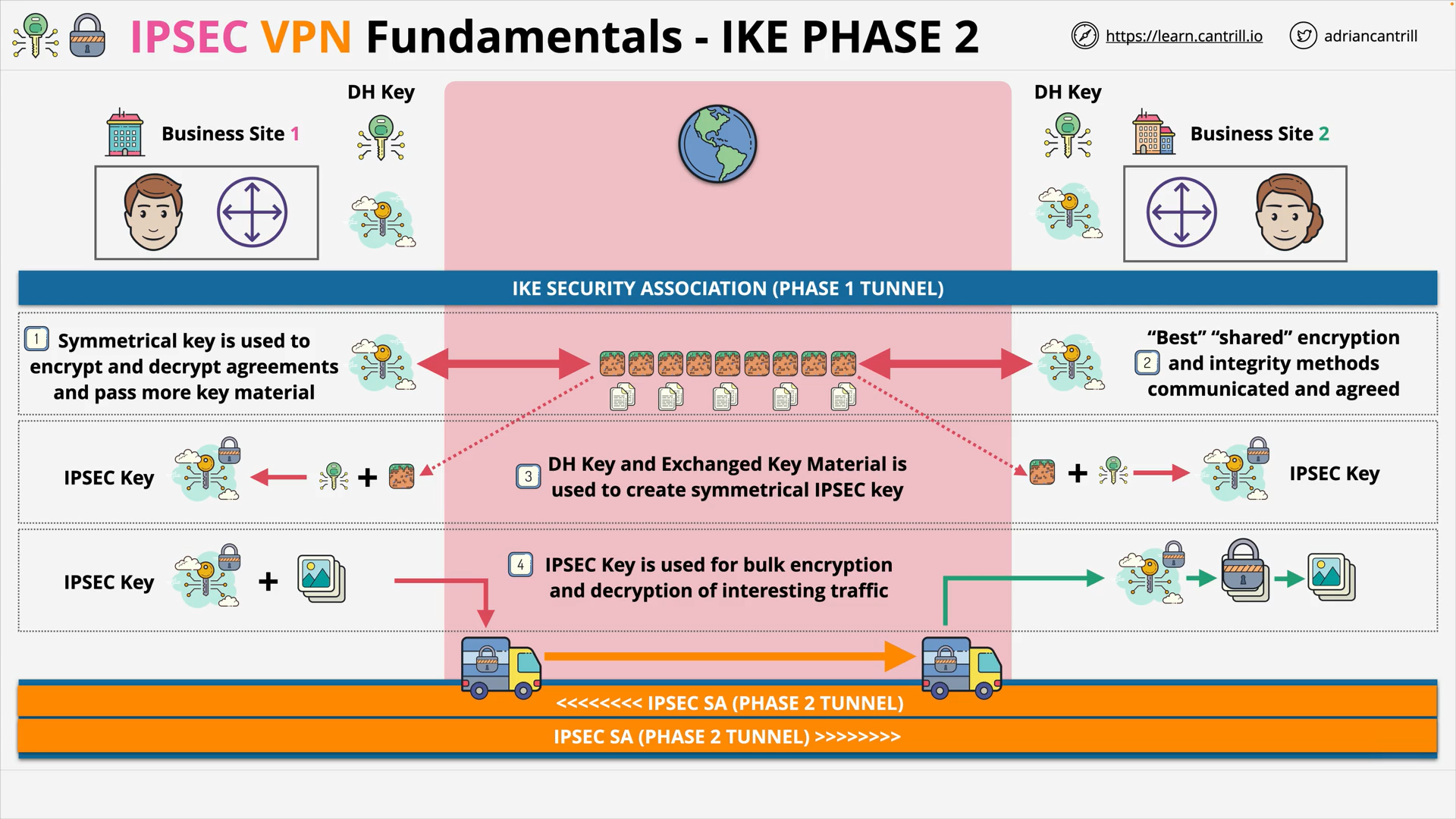 IP Sec - IKE Phase 2
IP Sec - IKE Phase 2
 Route-based VPN / Policy-based VPN
Route-based VPN / Policy-based VPN
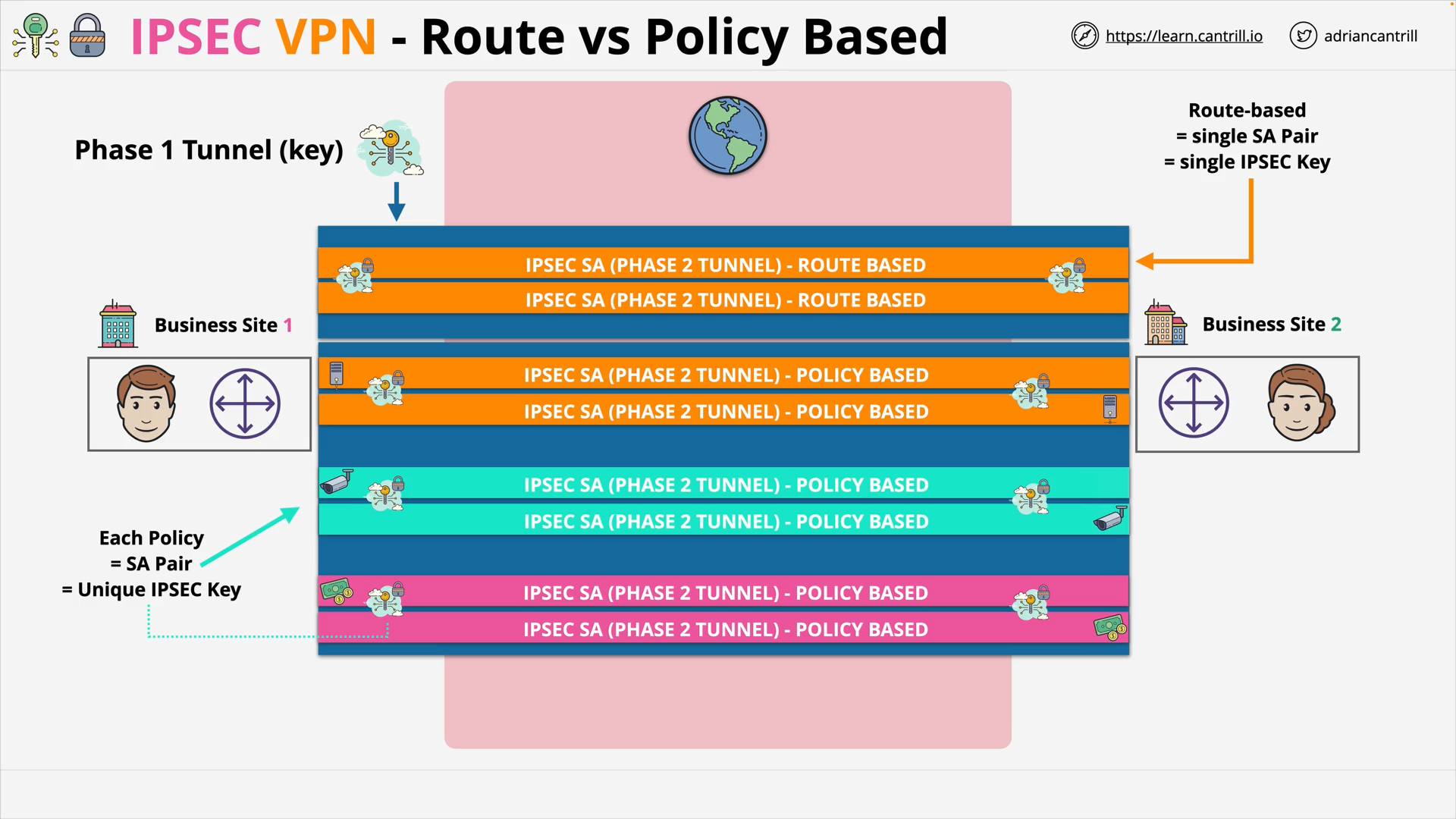 Route-based VPN / Policy-based VPN examples
Route-based VPN / Policy-based VPN examples
Fibre Optic Cable 101 (11:21)
 Fibre Optic Cables
Fibre Optic Cables
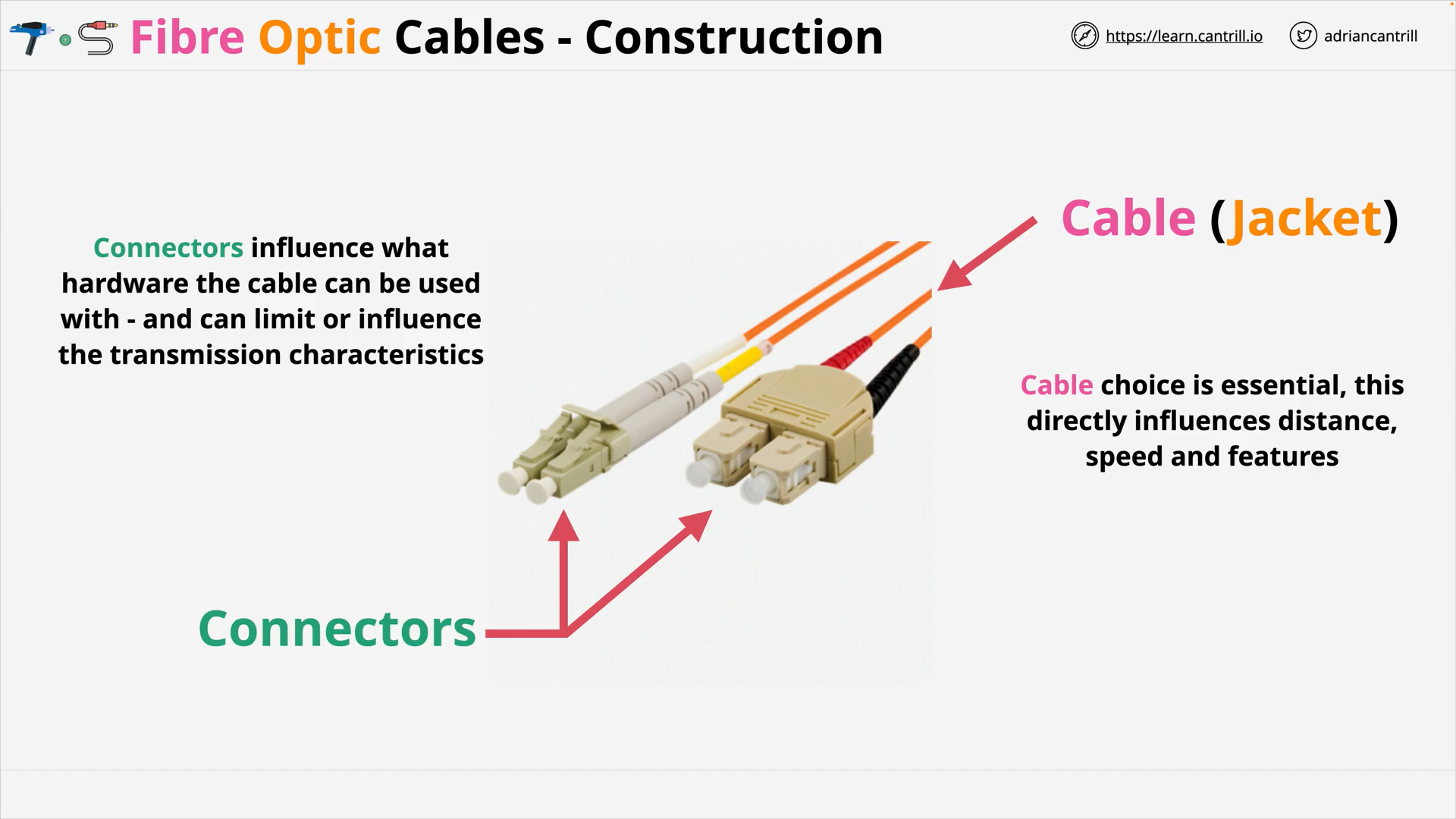 Fibre Optic Cables - Connectors
Fibre Optic Cables - Connectors
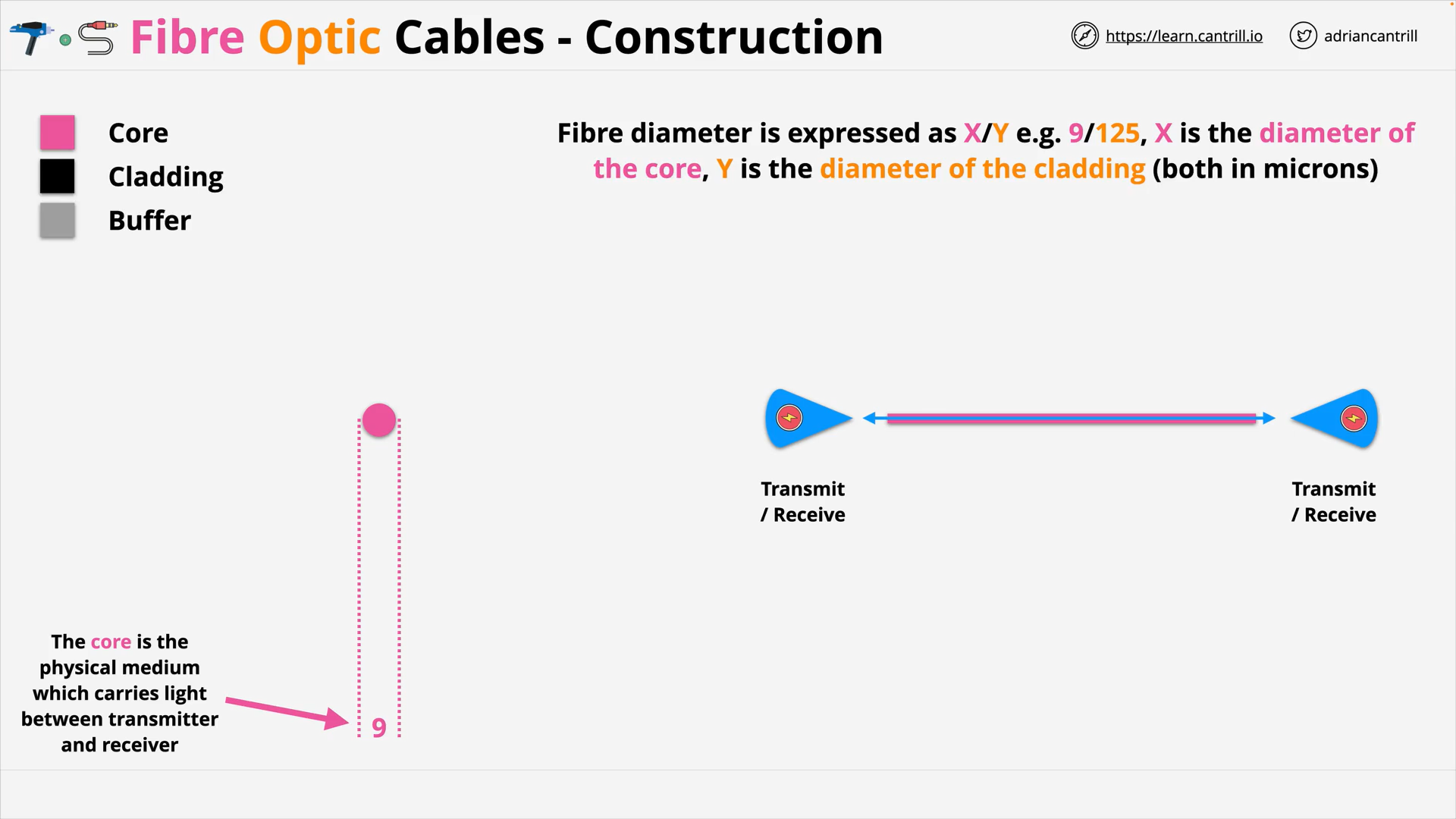 Fibre Optic Cables - Core
Fibre Optic Cables - Core
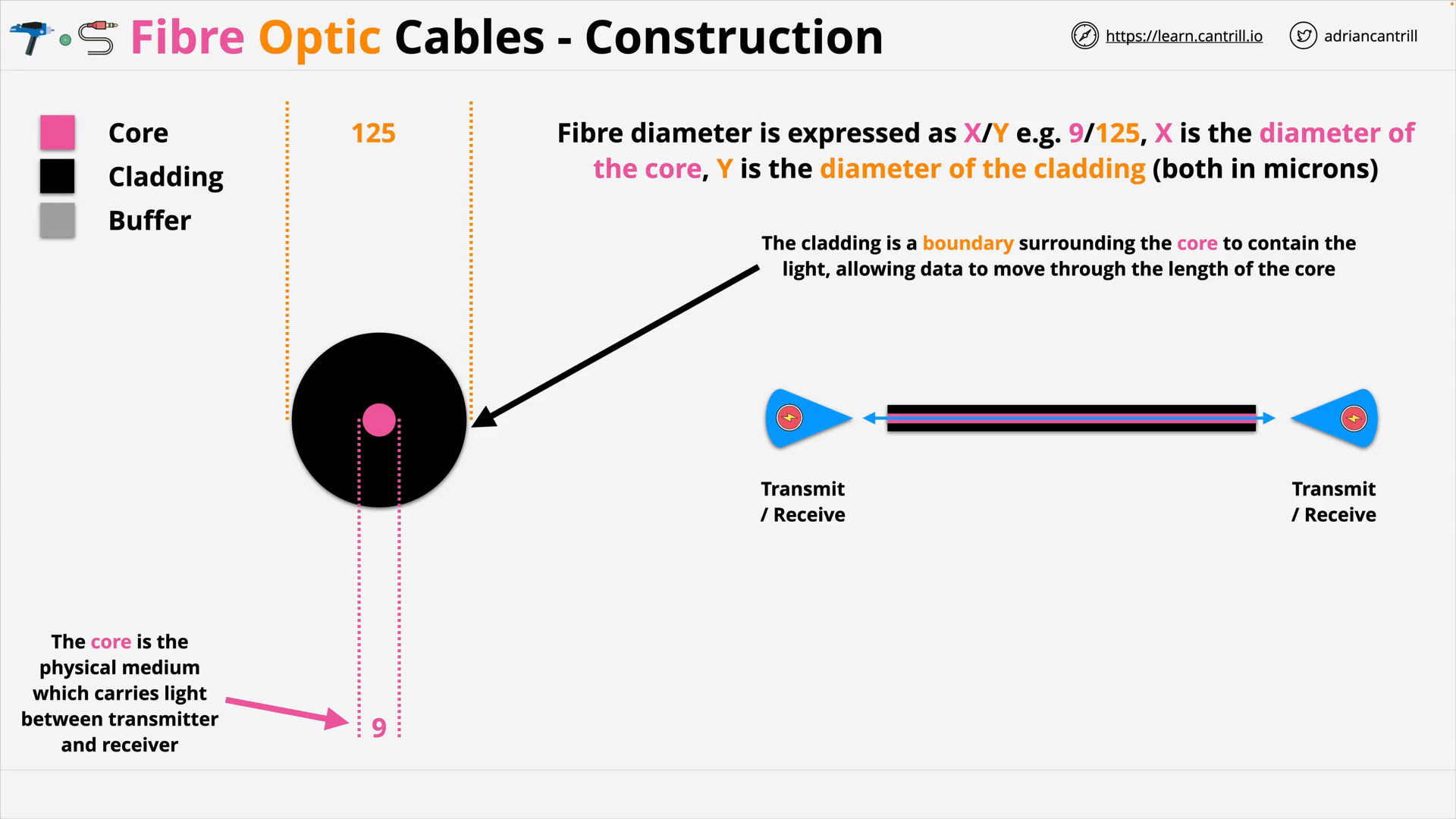 Fibre Optic Cables - Cladding
Fibre Optic Cables - Cladding
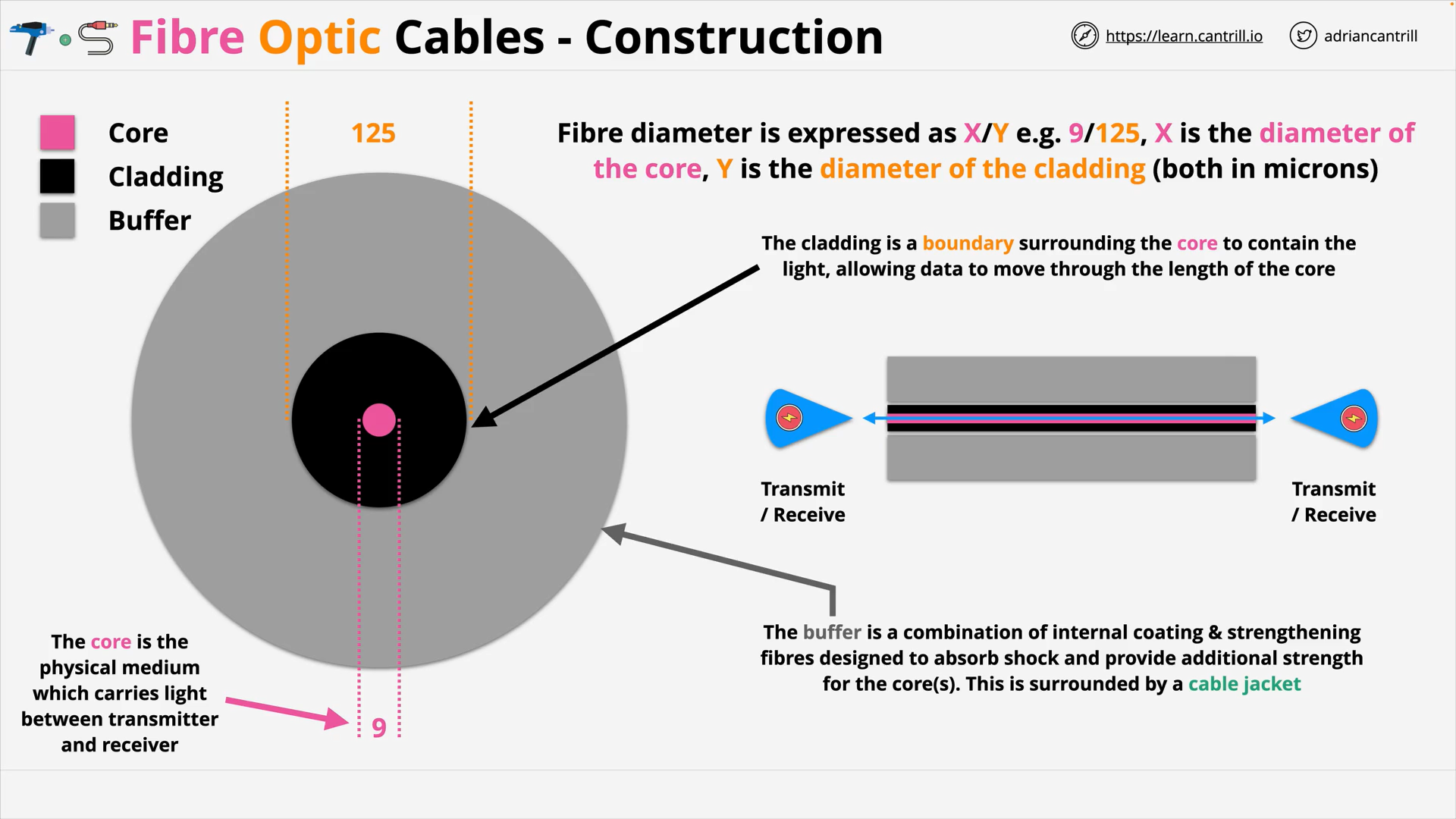 Fibre Optic Cables - Buffer
Fibre Optic Cables - Buffer
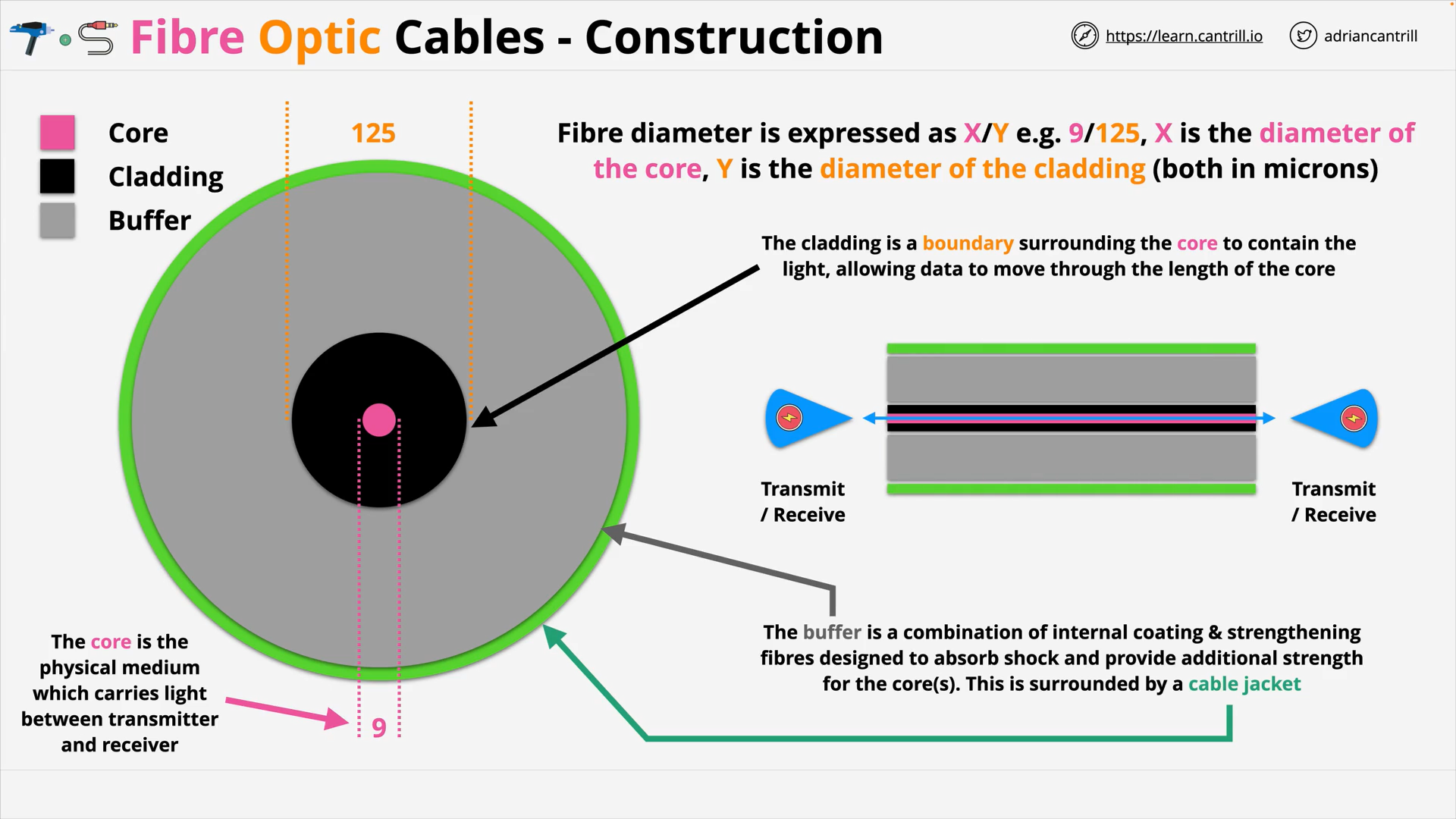 Fibre Optic Cables - Jacket
Fibre Optic Cables - Jacket
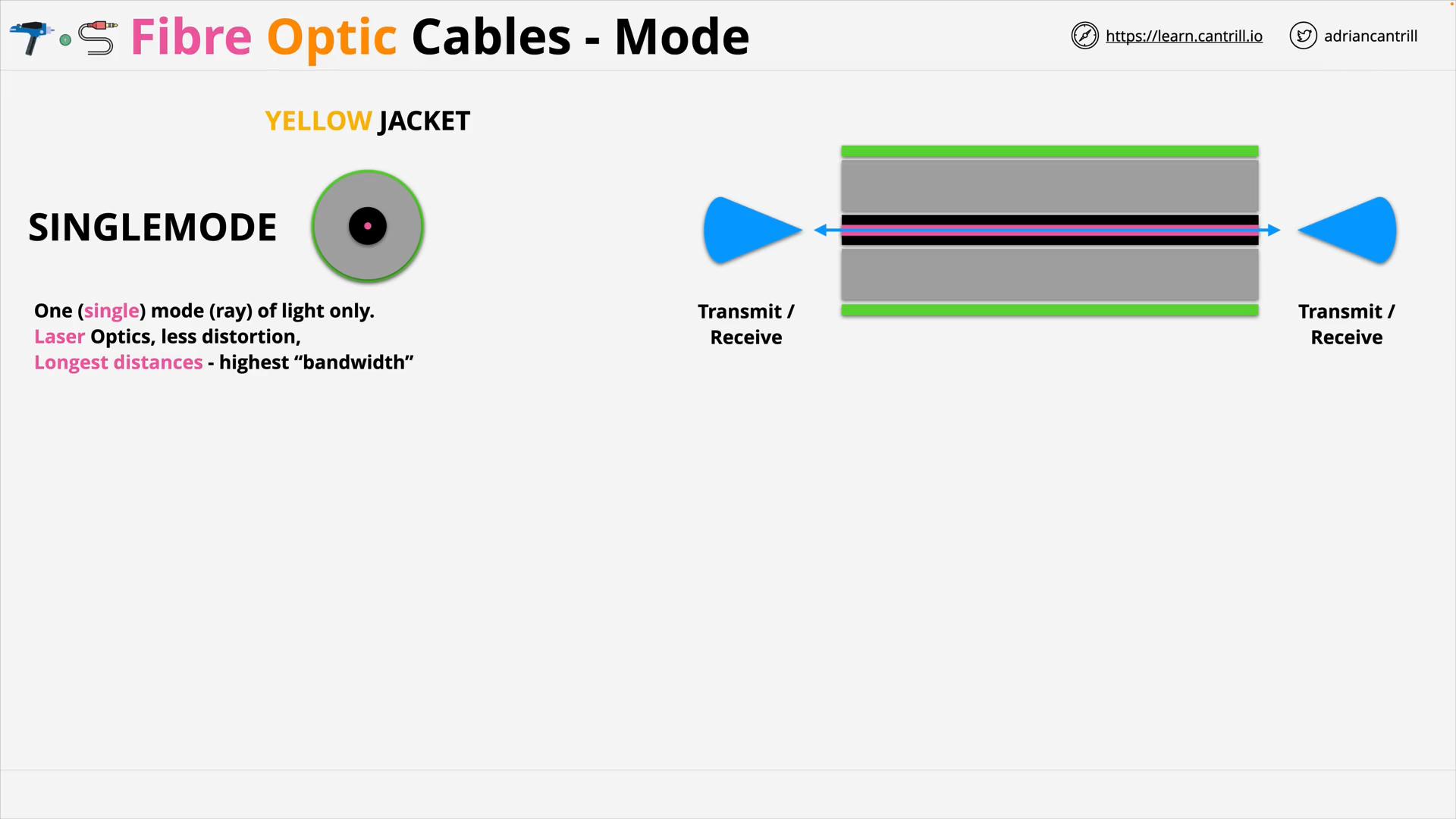 Fibre Optic Cables - Single Mode
Fibre Optic Cables - Single Mode
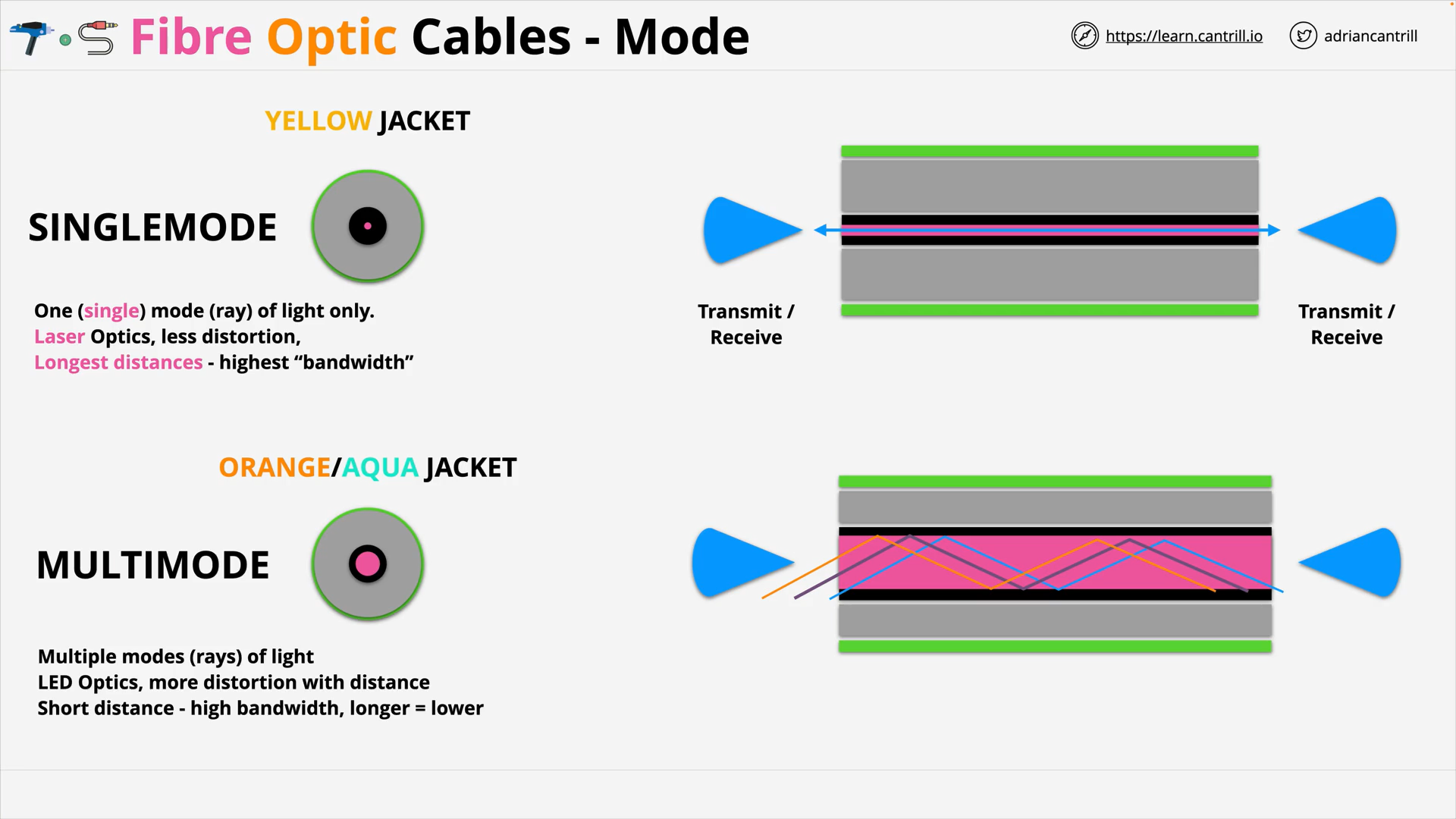 Fibre Optic Cables - Multi Mode
Fibre Optic Cables - Multi Mode
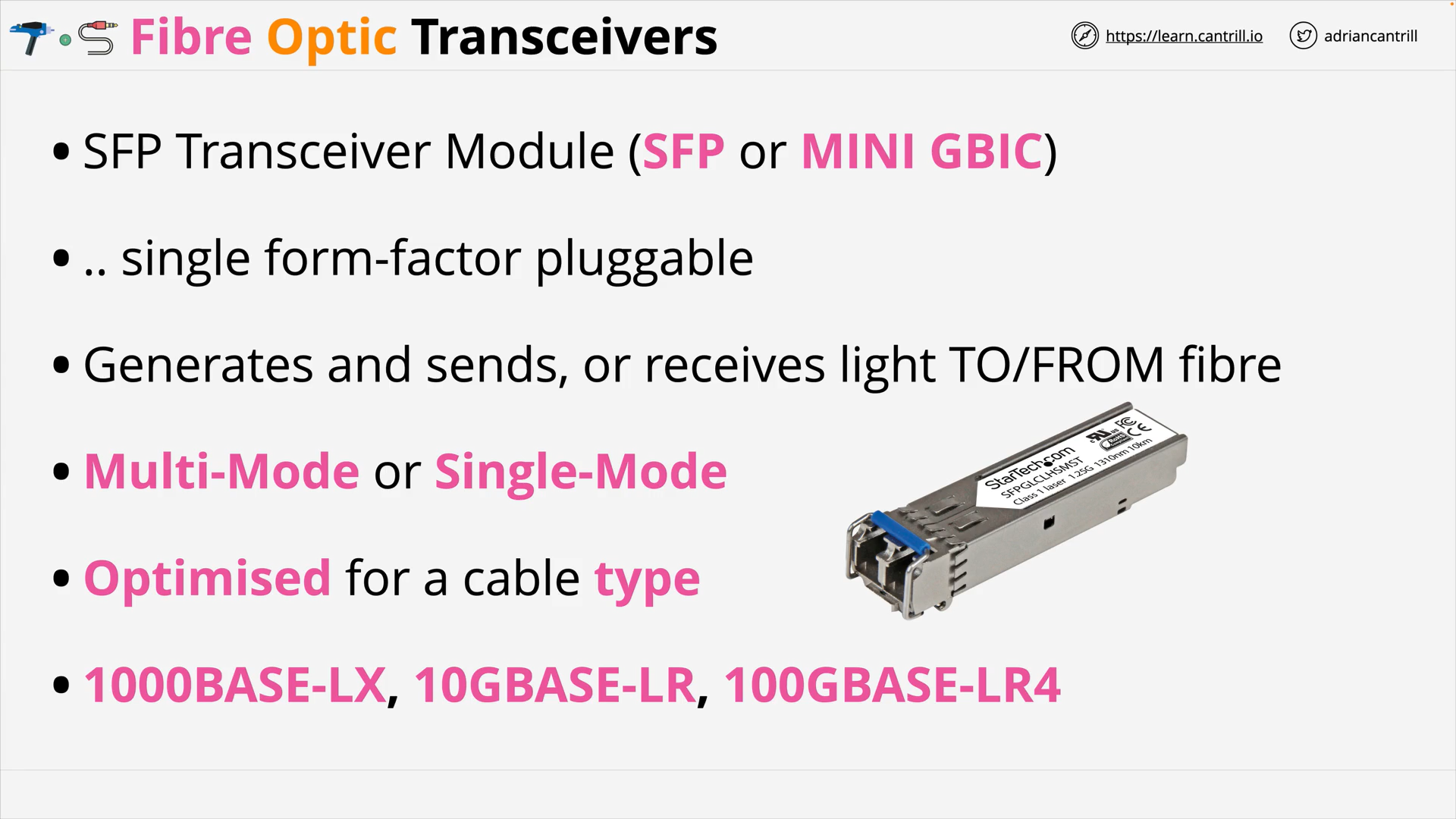 Fibre Optic Transceivers
Fibre Optic Transceivers
Security (MORE COMING SOON)
Encryption 101 - PART1 (13:56)
 Encryption 101
Encryption 101
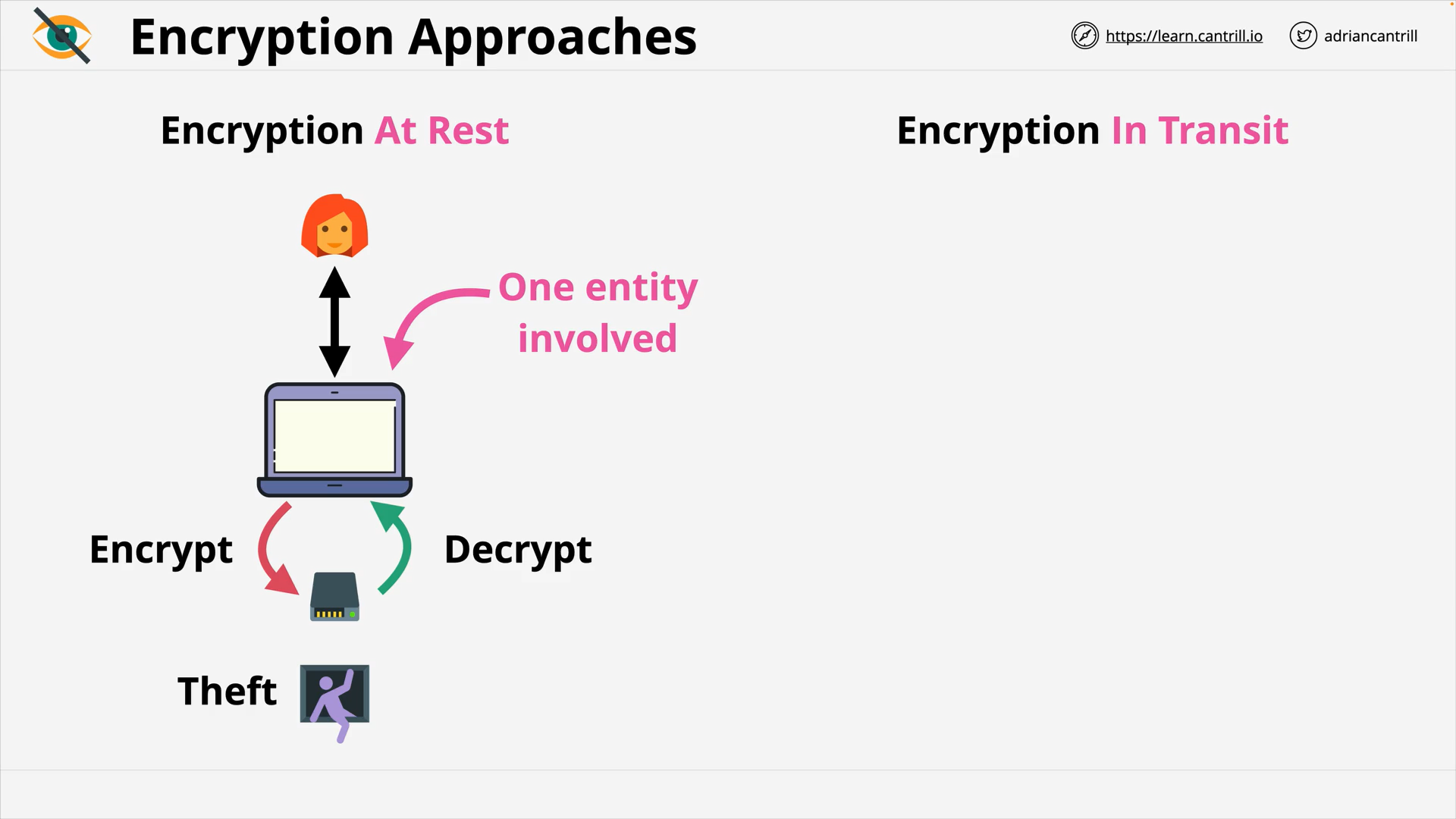 Encryption at Rest
Encryption at Rest
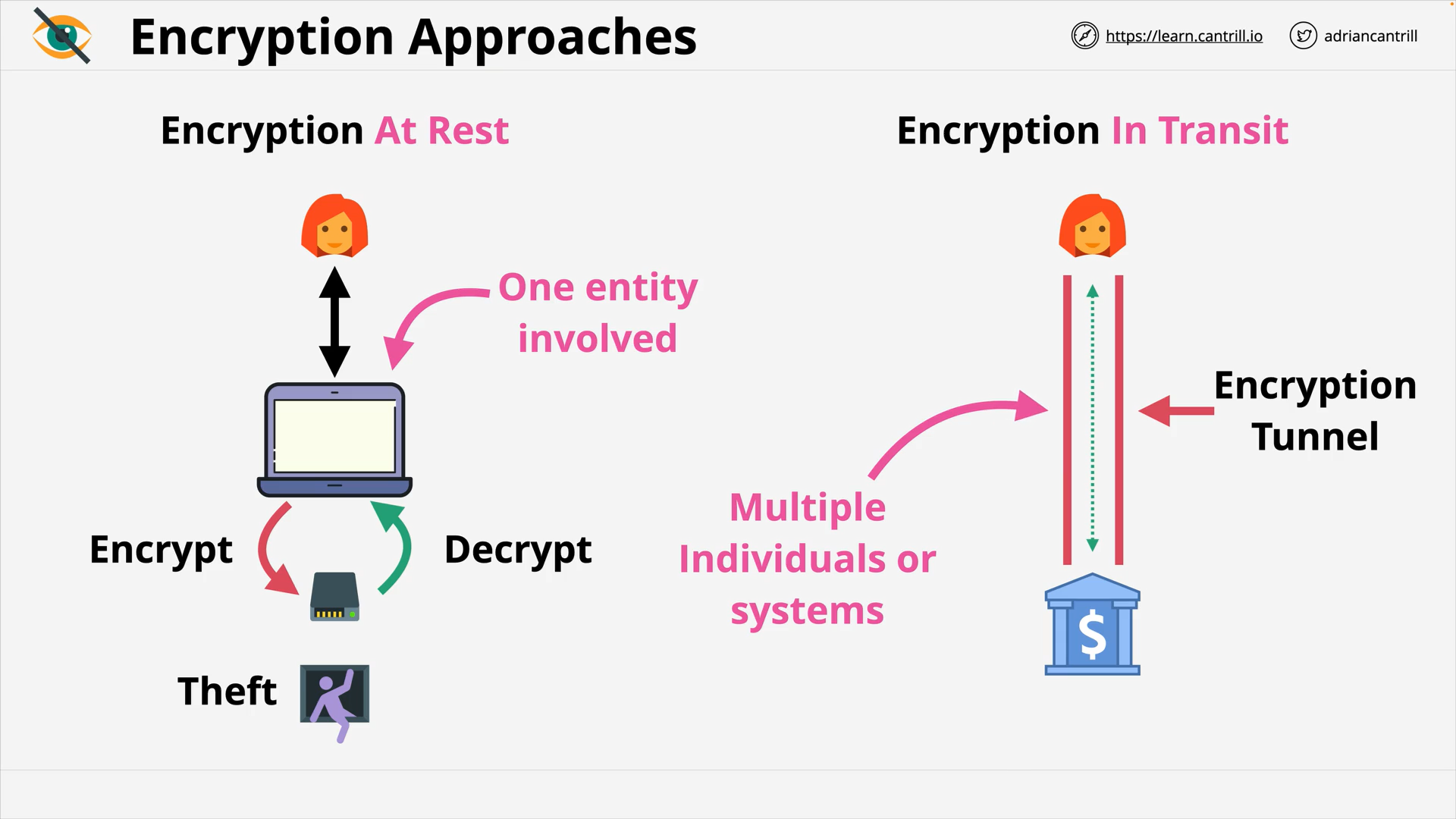 Encryption in Transit
Encryption in Transit
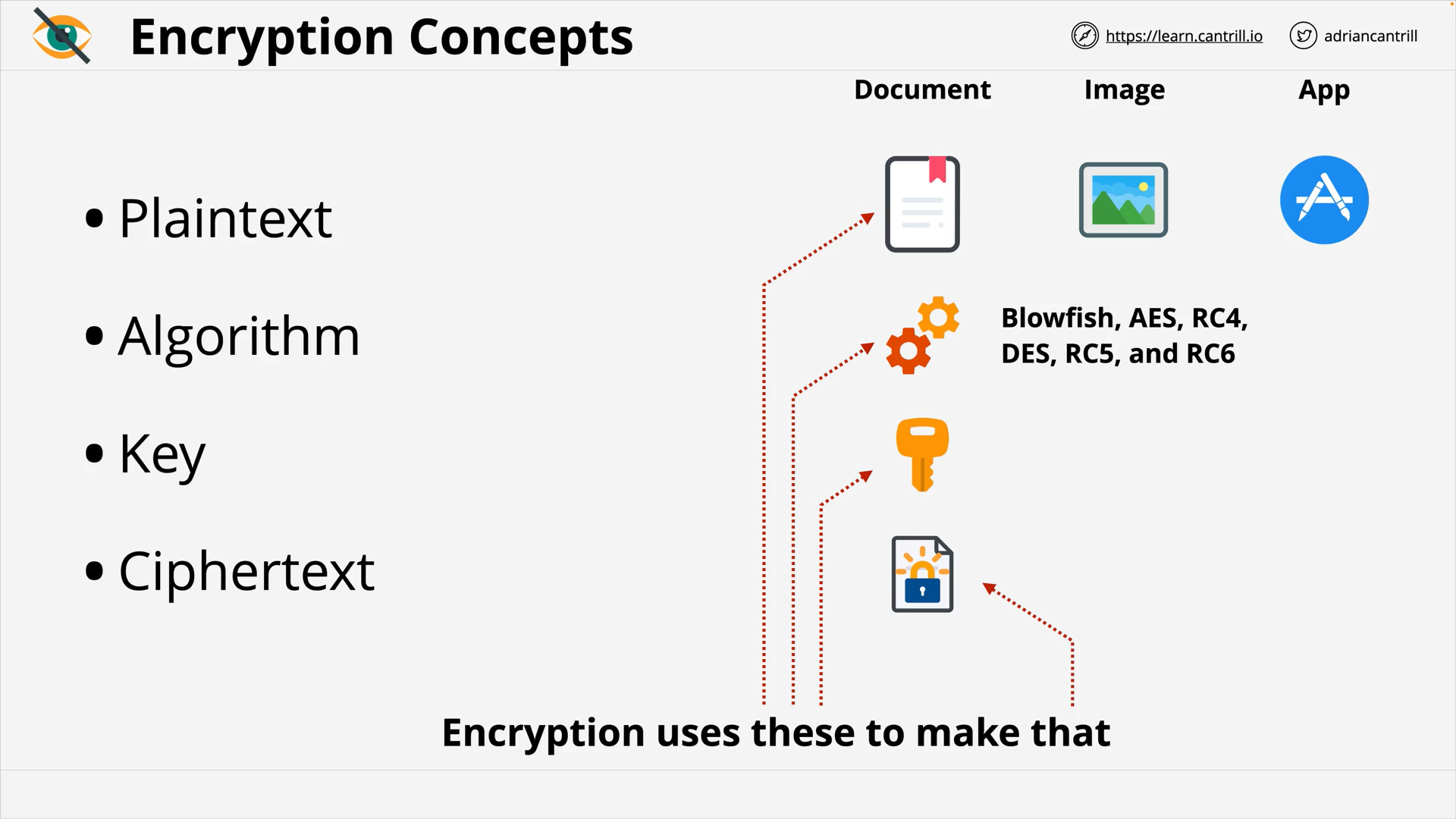 Encryption Concepts: Plaintext, Algorithm, Key and Ciphertext
Encryption Concepts: Plaintext, Algorithm, Key and Ciphertext
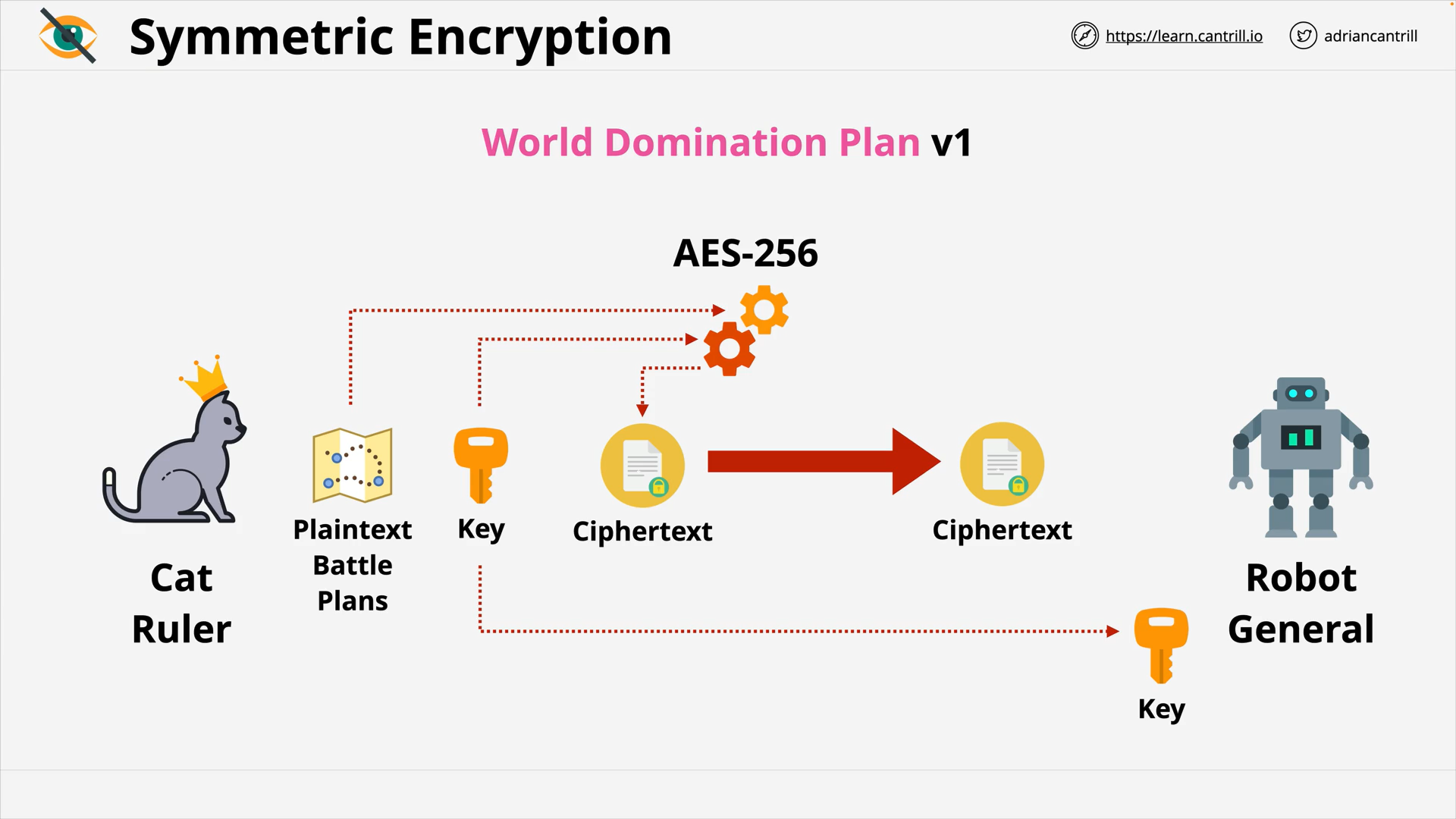 Symmetric Encryption
Symmetric Encryption
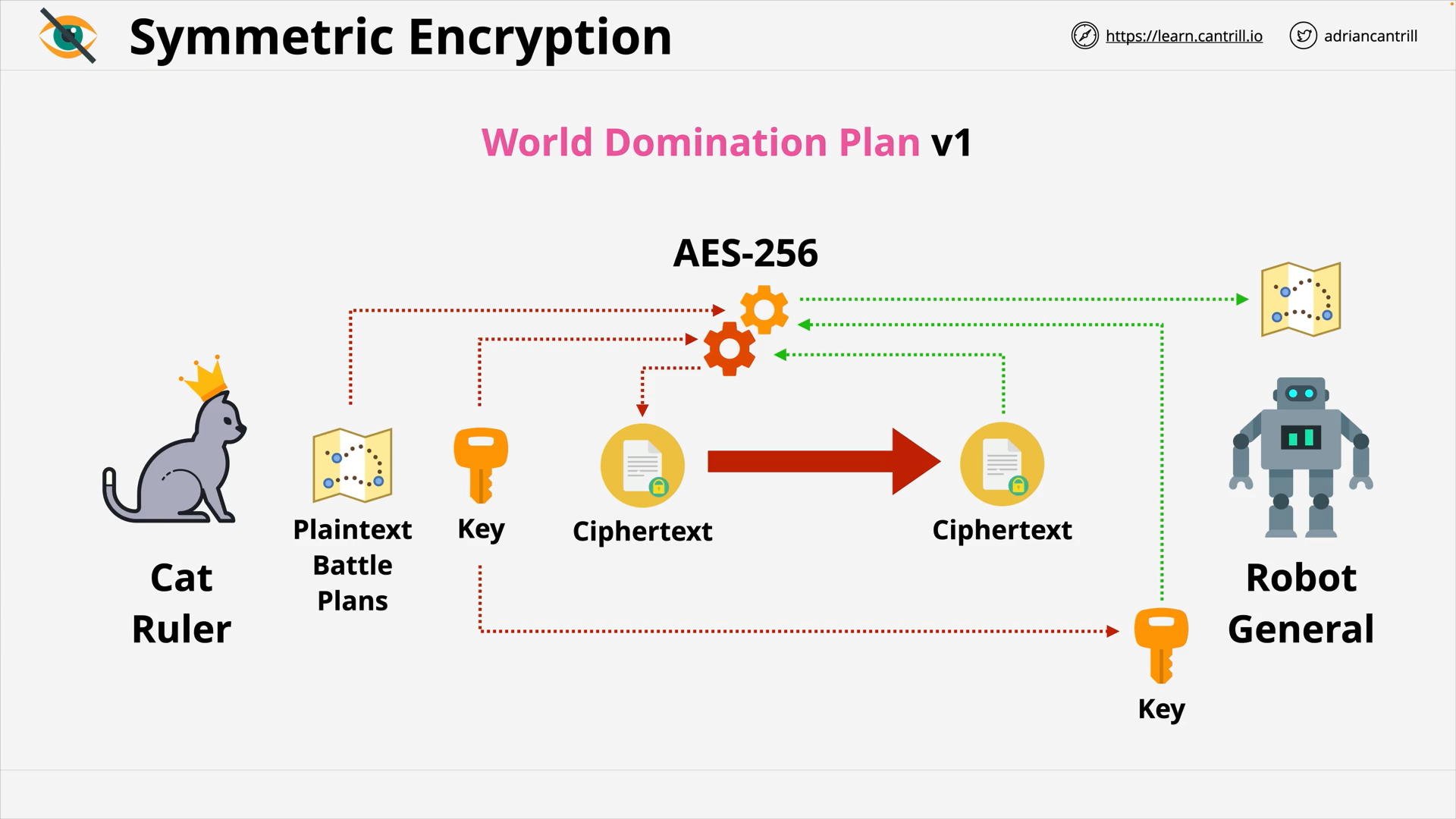 Symmetric Encryption - The same key is used for decryption
Symmetric Encryption - The same key is used for decryption
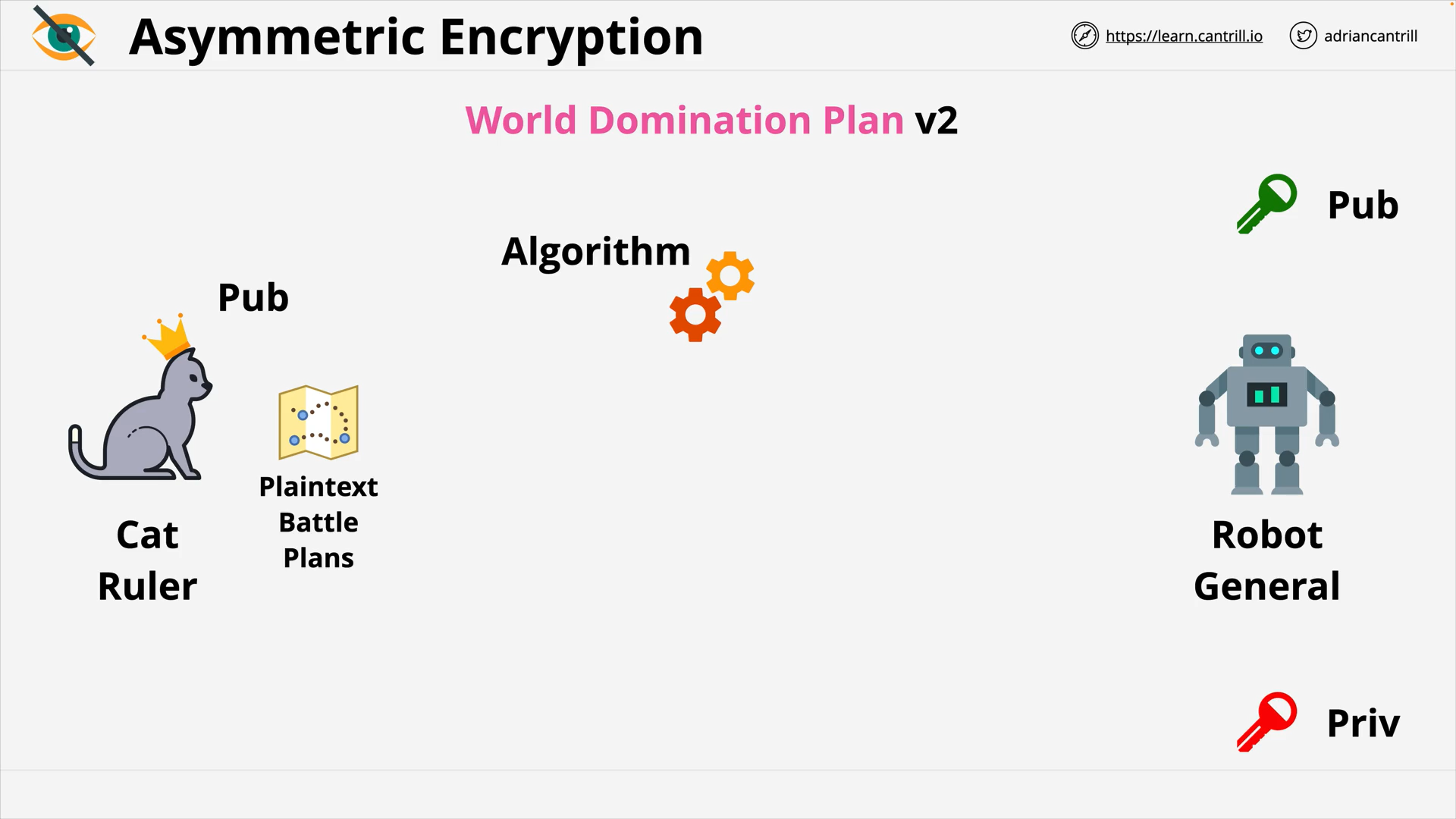 Asymmetric Encryption - Public and Private Key
Asymmetric Encryption - Public and Private Key
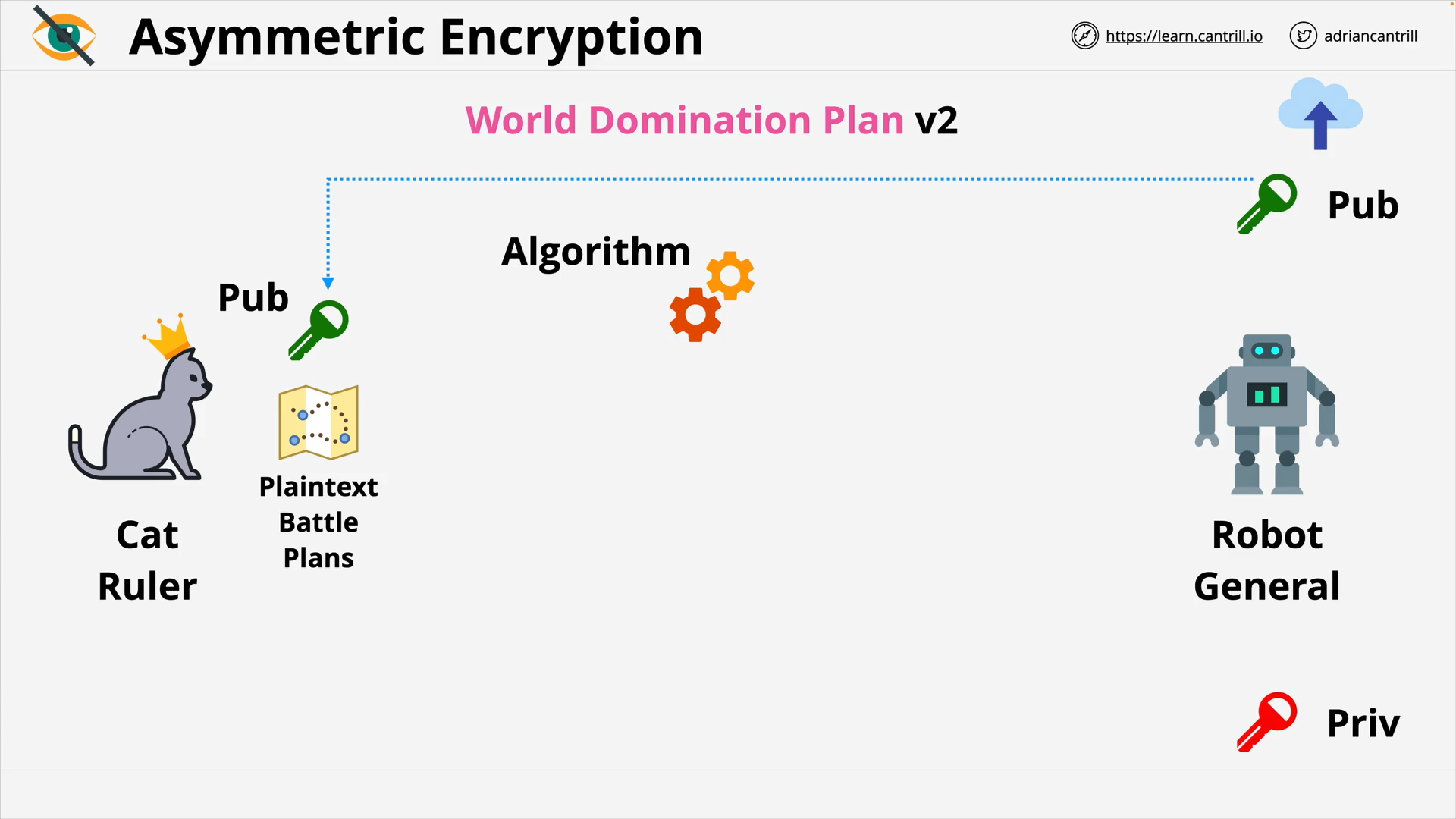 Asymmetric Encryption - Key Exchange
Asymmetric Encryption - Key Exchange
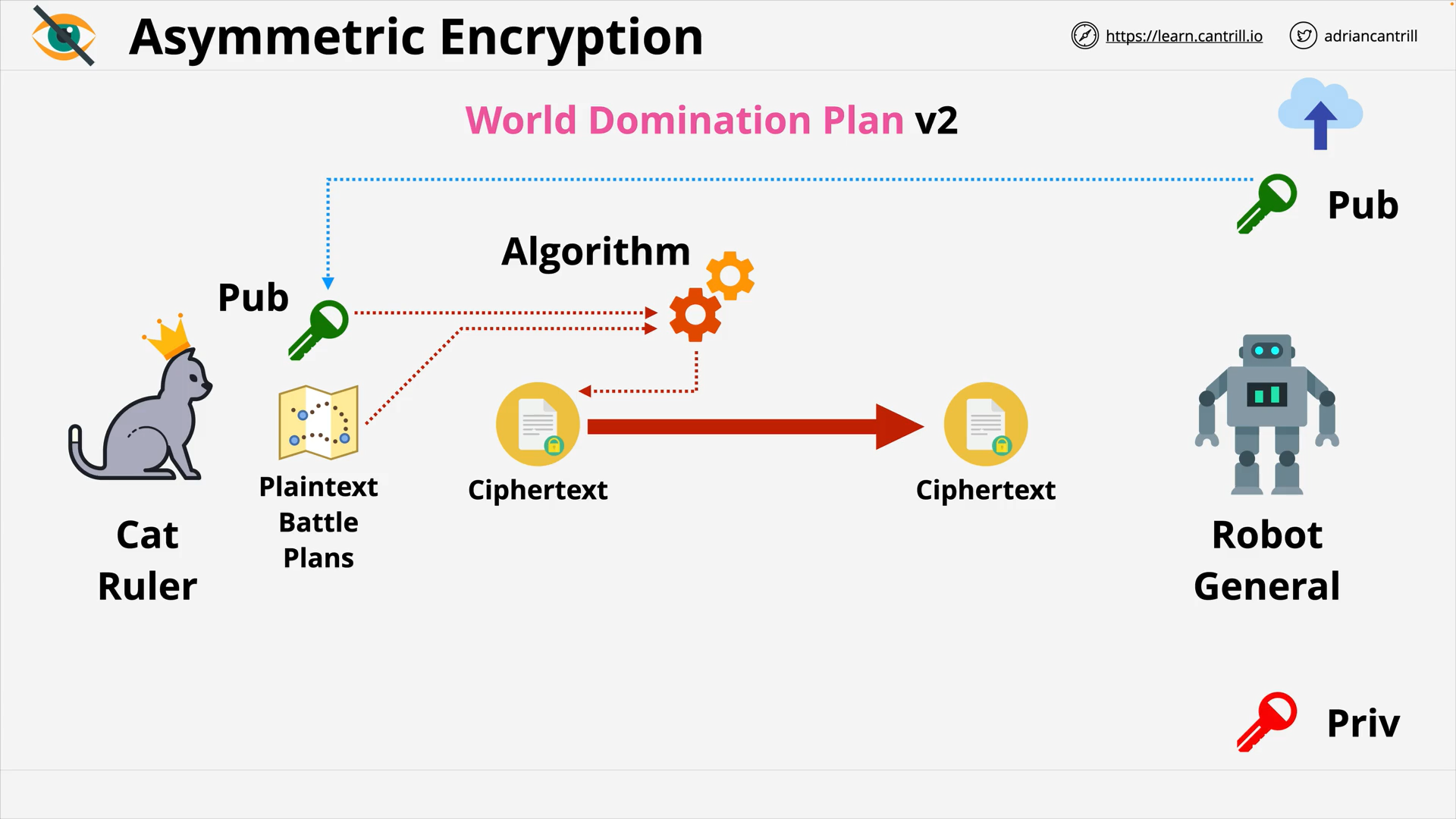 Asymmetric Encryption - Encryption
Asymmetric Encryption - Encryption
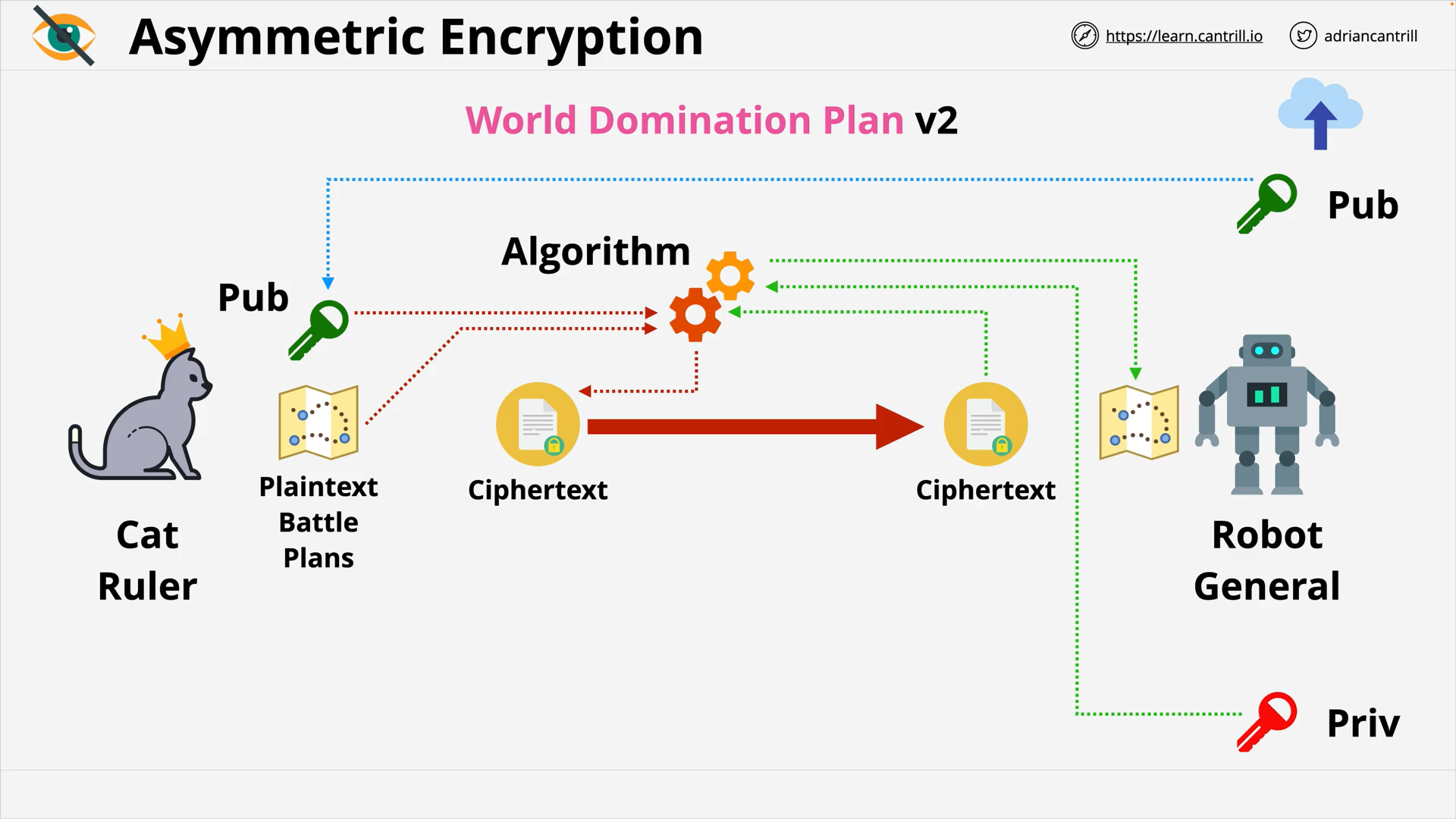 Asymmetric Encryption - Decryption
Asymmetric Encryption - Decryption
Encryption 101 - PART2 (6:42)
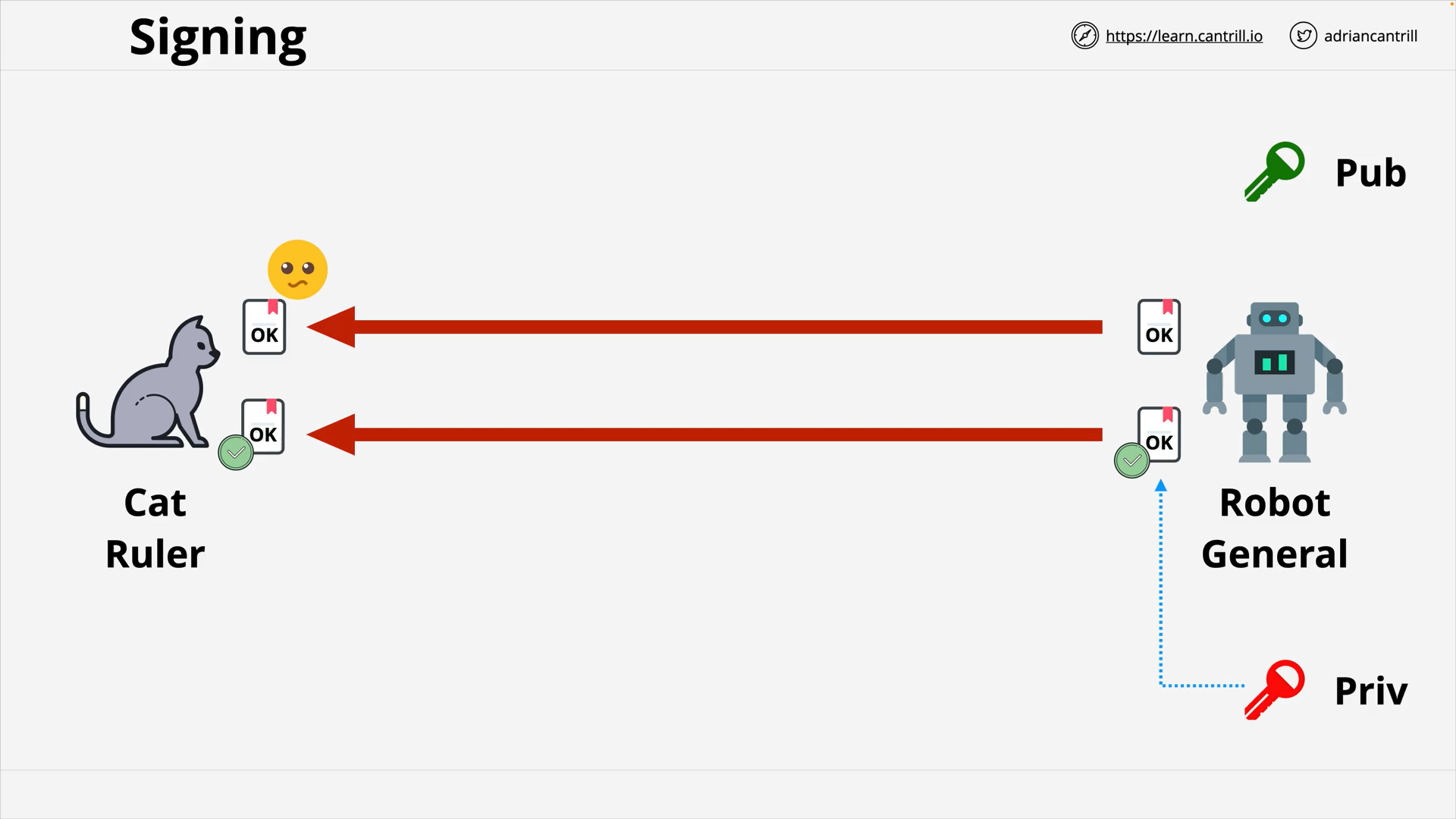
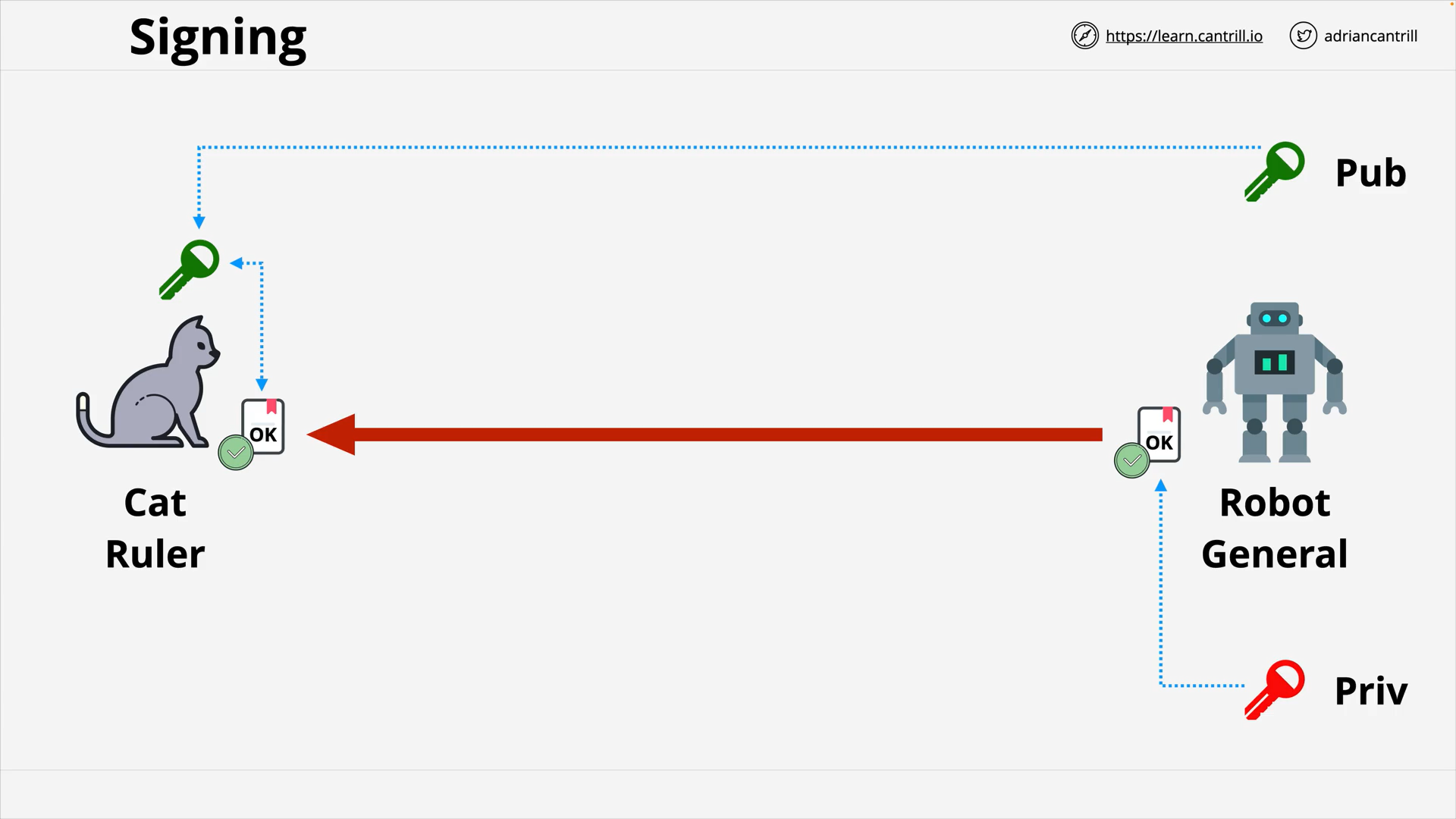 Signing
Signing
signing
The practice of using asymmetric keys to verify the authenticity and integrity of data.
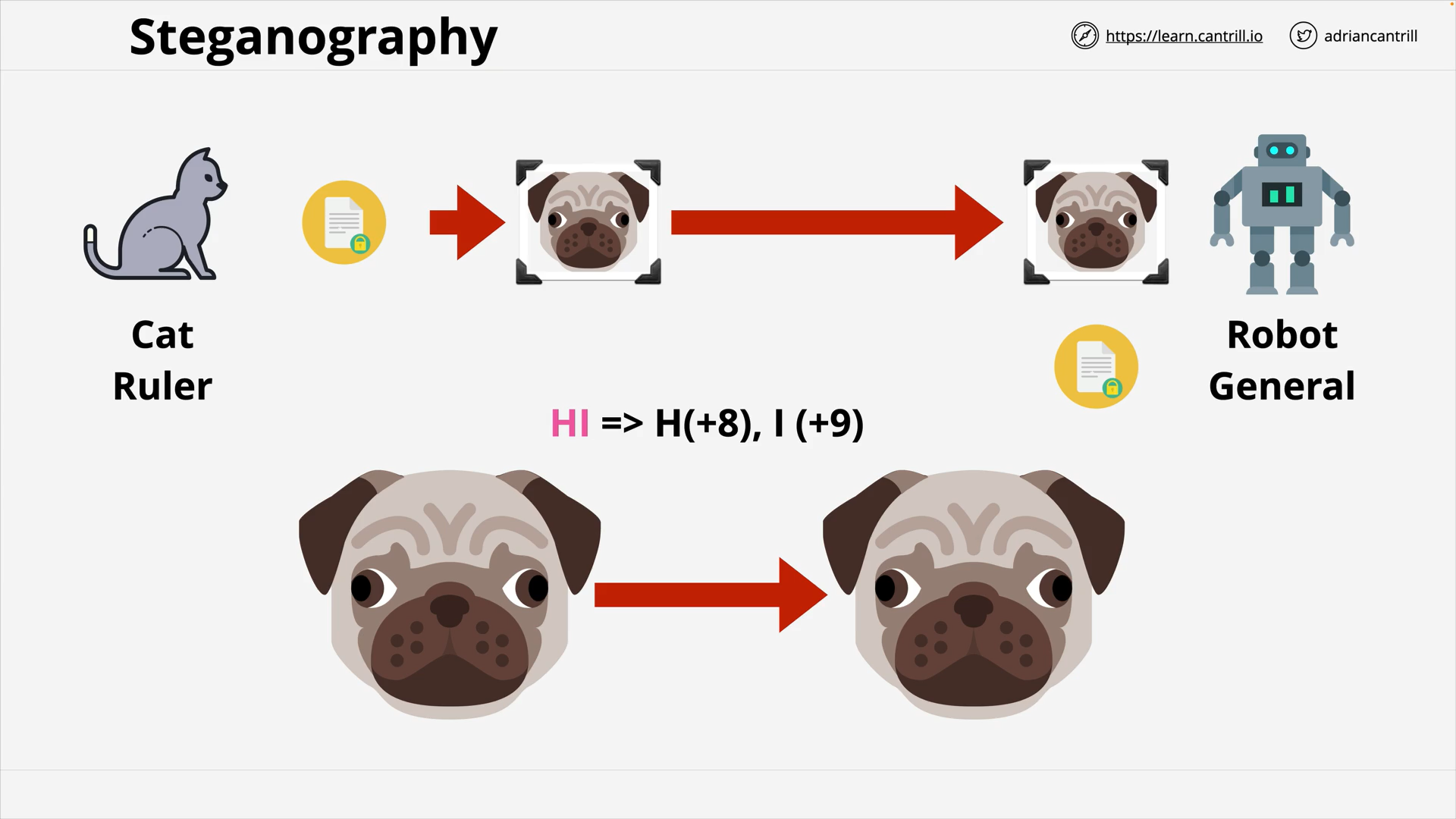
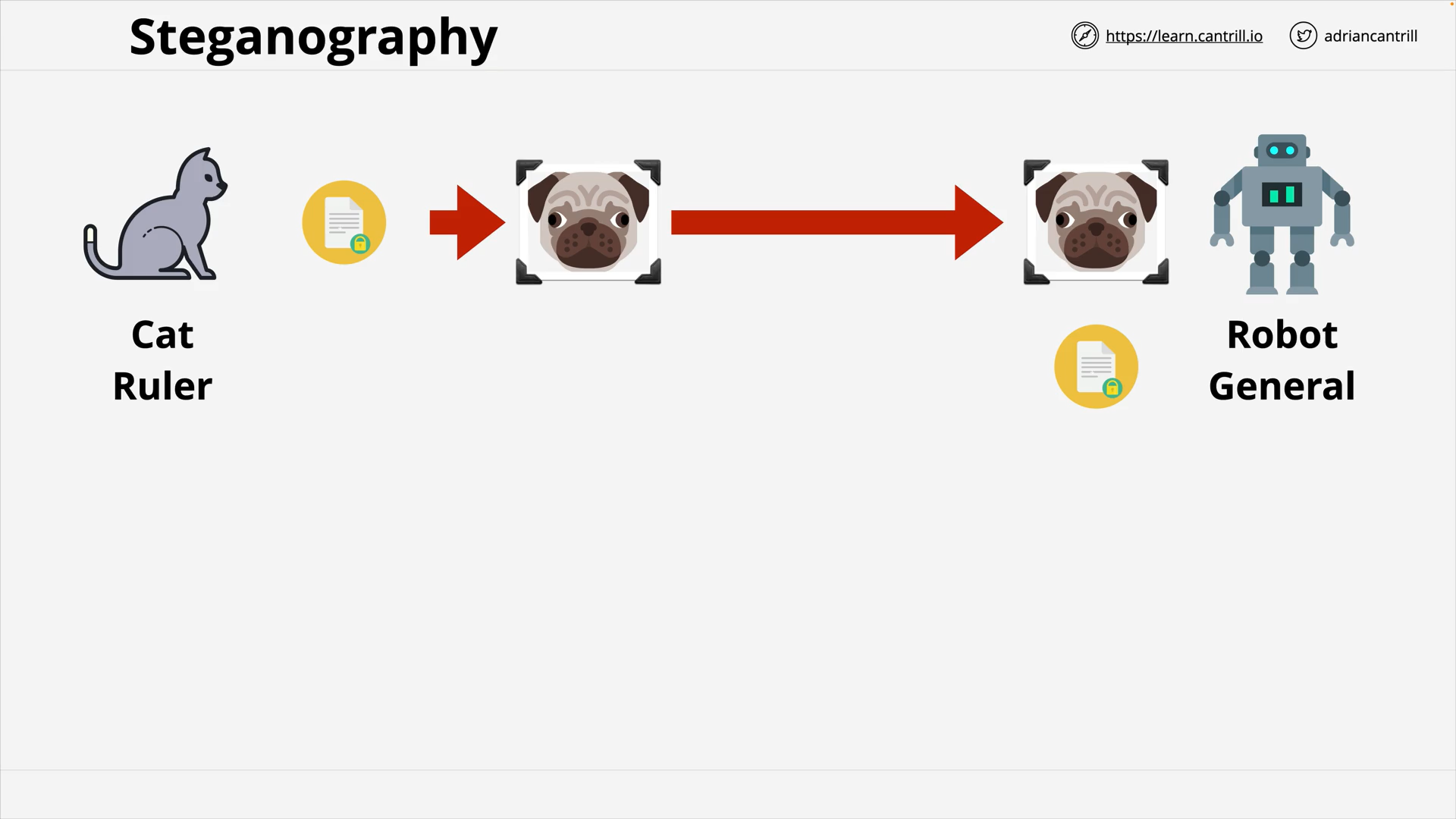 Steganography
Steganography
steganography
The practice of concealing information within another message or physical object to avoid detection.
Envelope Encryption (8:06)
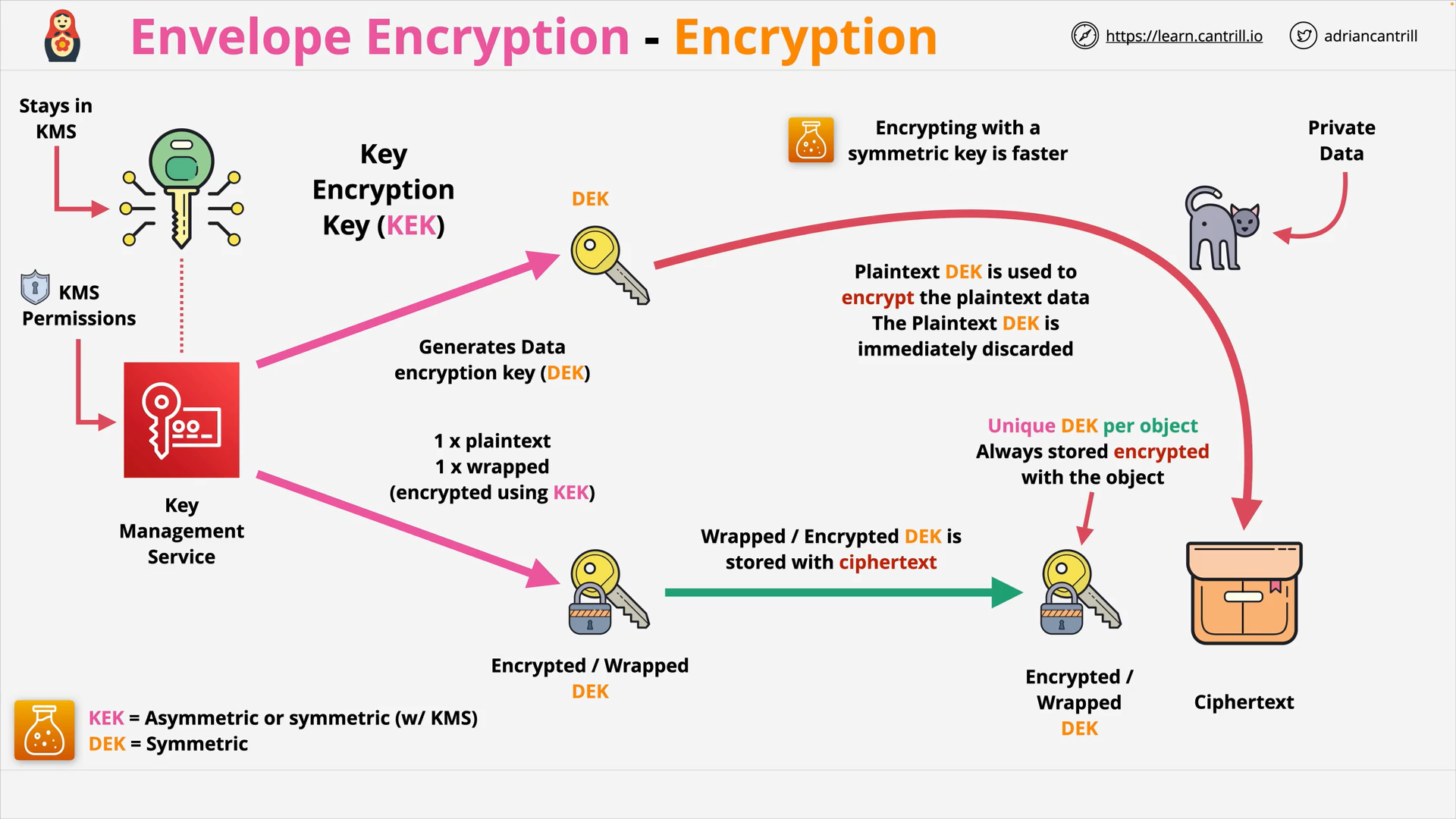 Enveloper Encryption: KEK, DEKs
Enveloper Encryption: KEK, DEKs
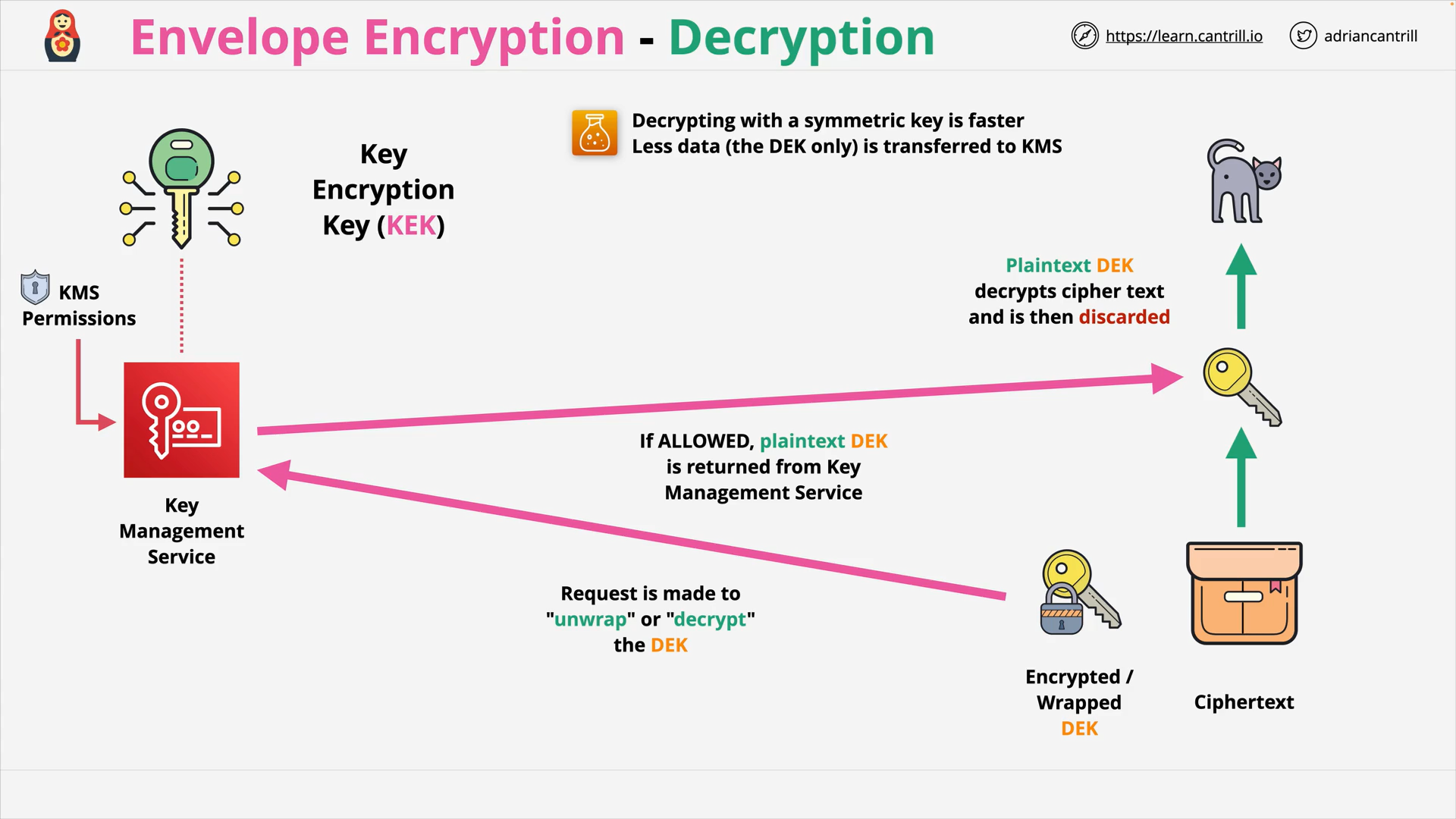 Enveloper Encryption - Decryption
Enveloper Encryption - Decryption
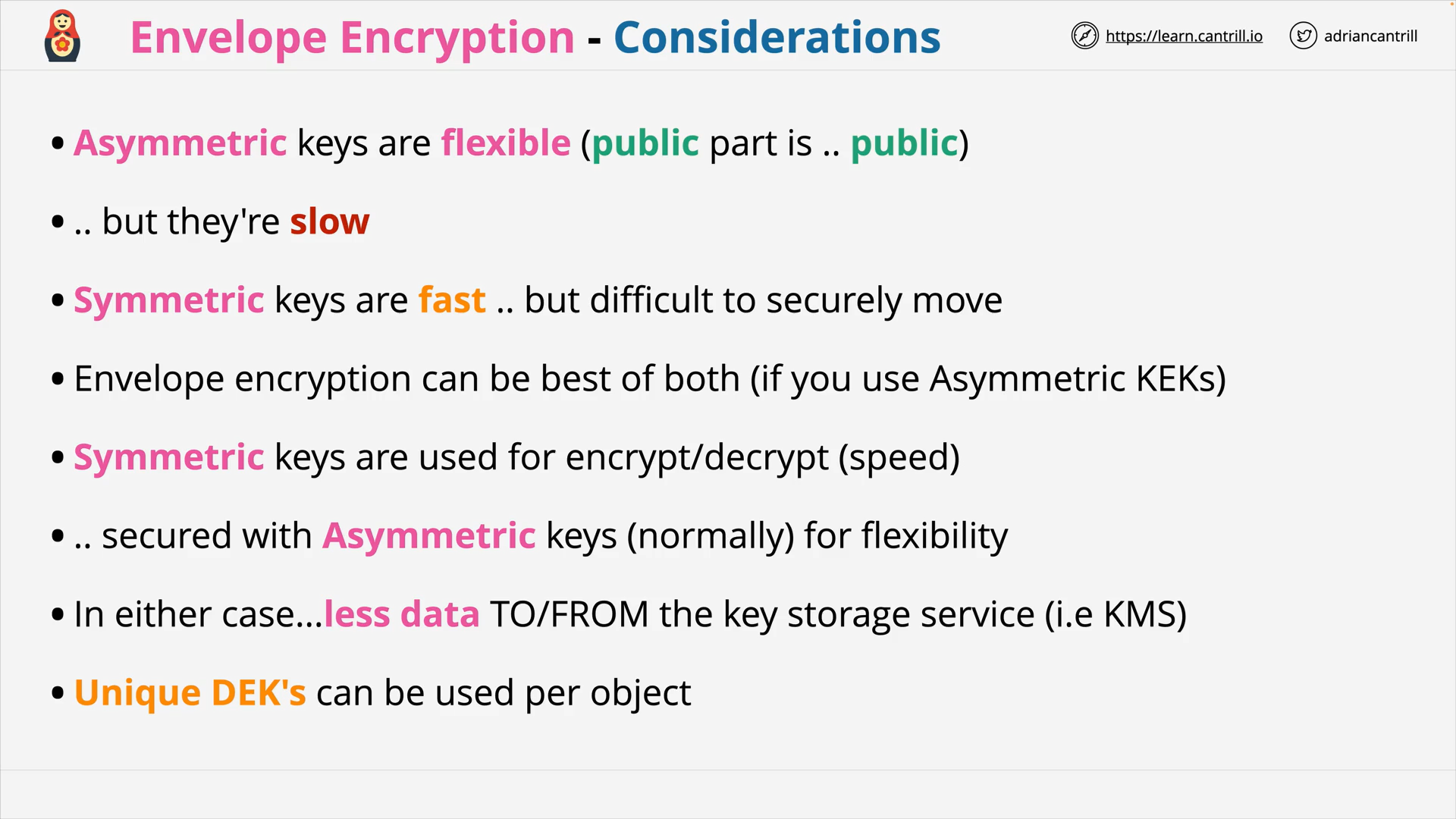 Enveloper Encryption - Considerations
Enveloper Encryption - Considerations
Hardware Security Modules (HSMs) (6:40)
__learn.cantrill.i.png) HSM - Without HSM
HSM - Without HSM
__learn.cantrill.i.png) HSM - With HSM
HSM - With HSM
__learn.cantrill.i.png) HSM - Keys are stored securely inside the HSM
HSM - Keys are stored securely inside the HSM
__learn.cantrill.i.png) HSM - Authenticate takes place inside the HSM
HSM - Authenticate takes place inside the HSM
__learn.cantrill.i.png) HSM - HSMs are tamper proof & hardened against physical logical attacks
HSM - HSMs are tamper proof & hardened against physical logical attacks
__learn.cantrill.i.png) HSM - Accessed via tightly controlled, industry standard APIs
HSM - Accessed via tightly controlled, industry standard APIs
__learn.cantrill.i.png) HSM - Role Separation: HSM admins can update & maintain but don’t always have full access
HSM - Role Separation: HSM admins can update & maintain but don’t always have full access
__learn.cantrill.i.png) HSM - HSM can be used to processing SSL/TLS or PKI Signing certificate
HSM - HSM can be used to processing SSL/TLS or PKI Signing certificate
Hash Functions & Hashing (13:19)
 Hashing
Hashing
hashing
The process of applying a hash function to data to produce a unique and irreversible representation of the original data.
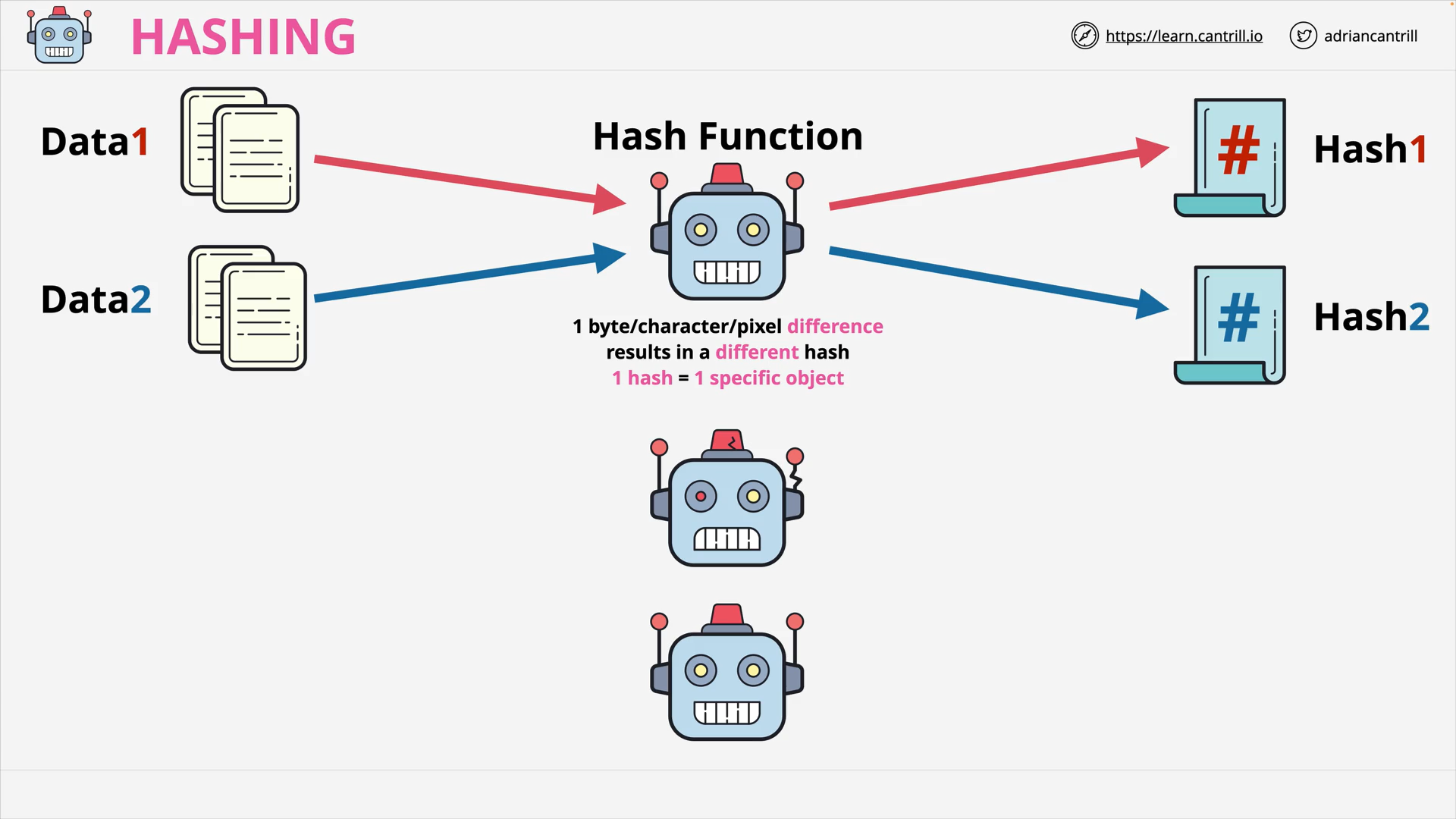 Hash Function
Hash Function
hash function
Mathematical algorithms that transform input data into a fixed-length string of characters, called a hash or message digest.
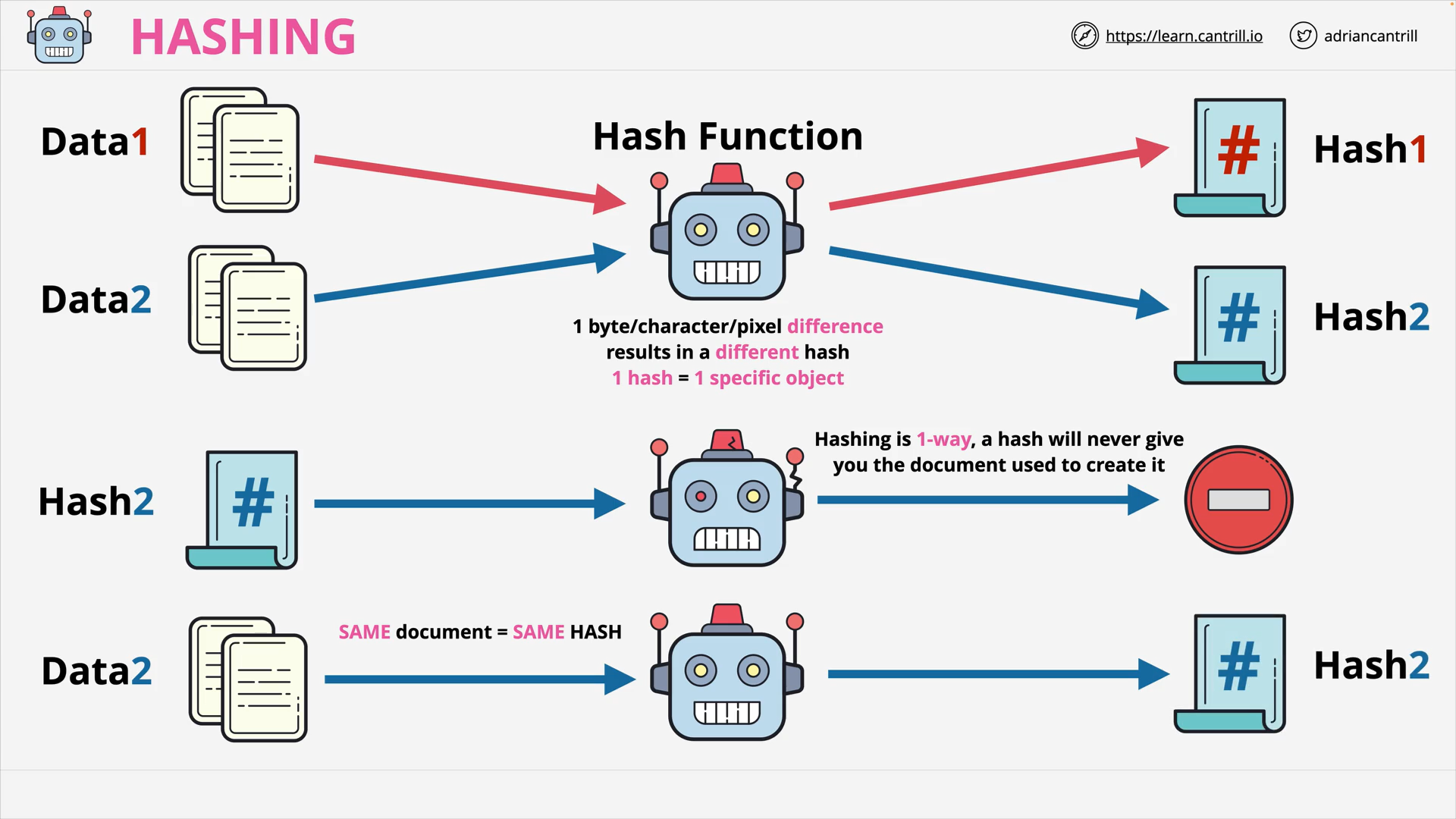 Hashing is 1 way.
Hashing is 1 way.
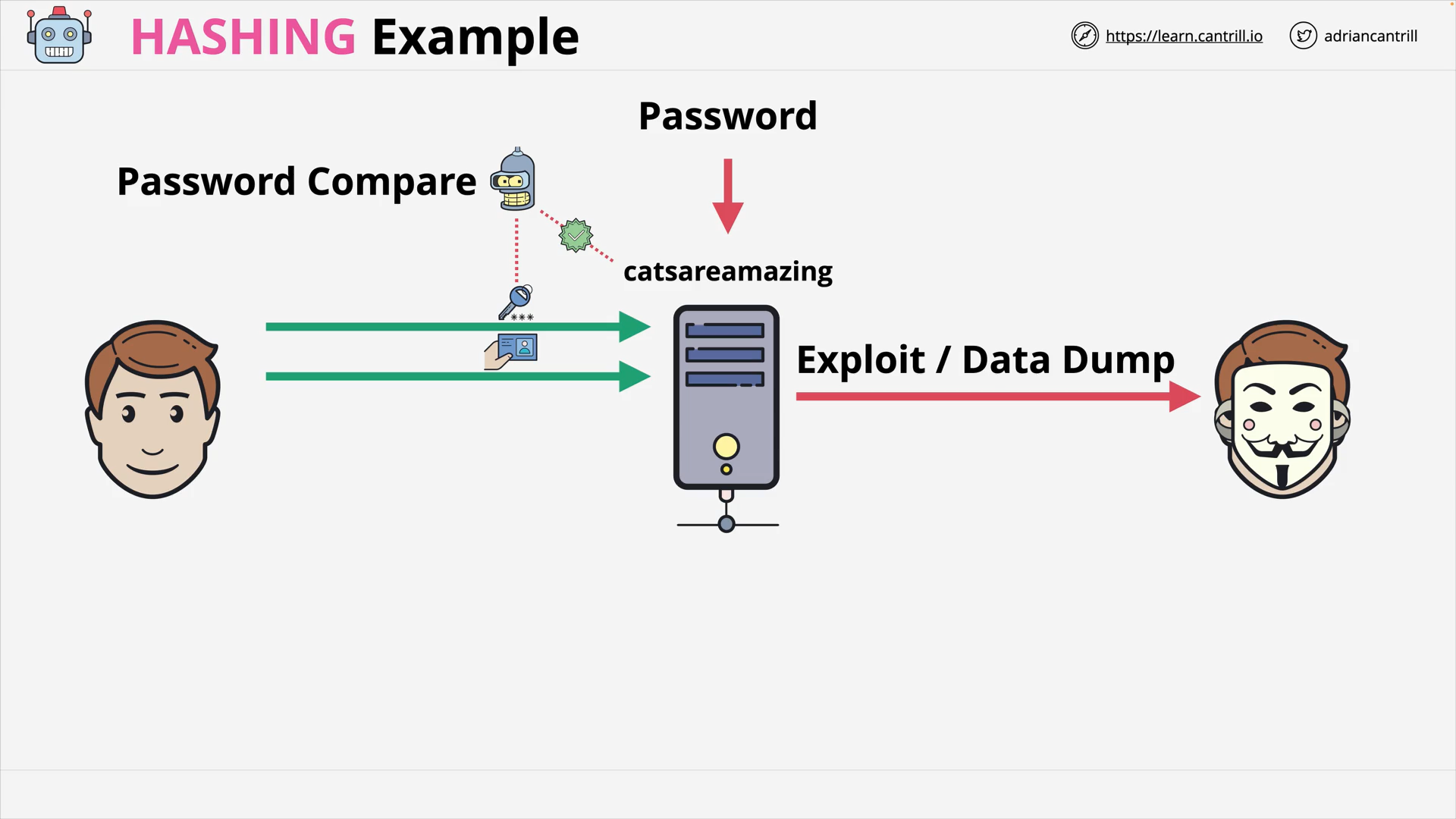 Hashing Example - Raw Password
Hashing Example - Raw Password
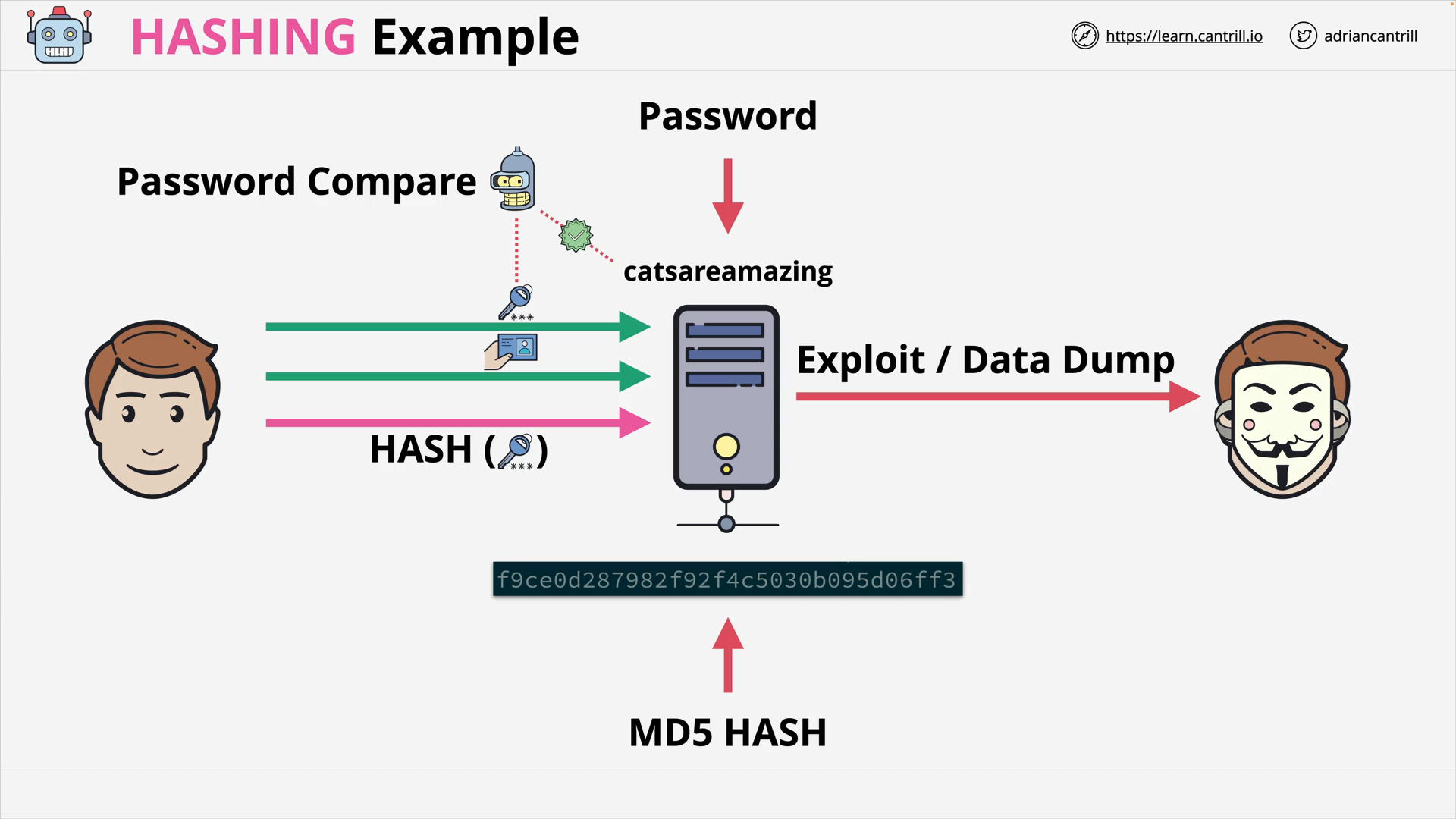 Hashing Example - Hashed Password
Hashing Example - Hashed Password
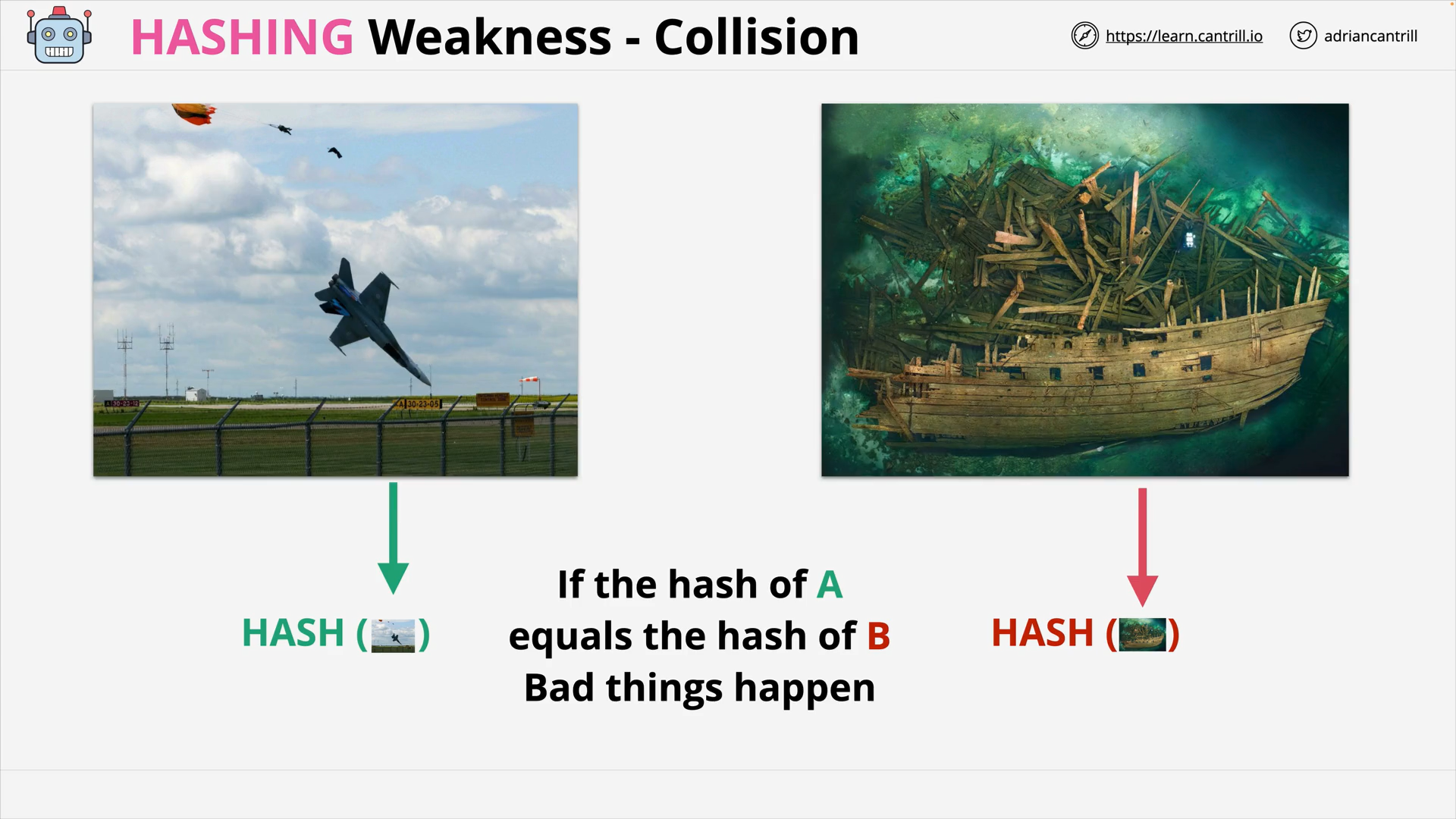 Hashing Collision
Hashing Collision
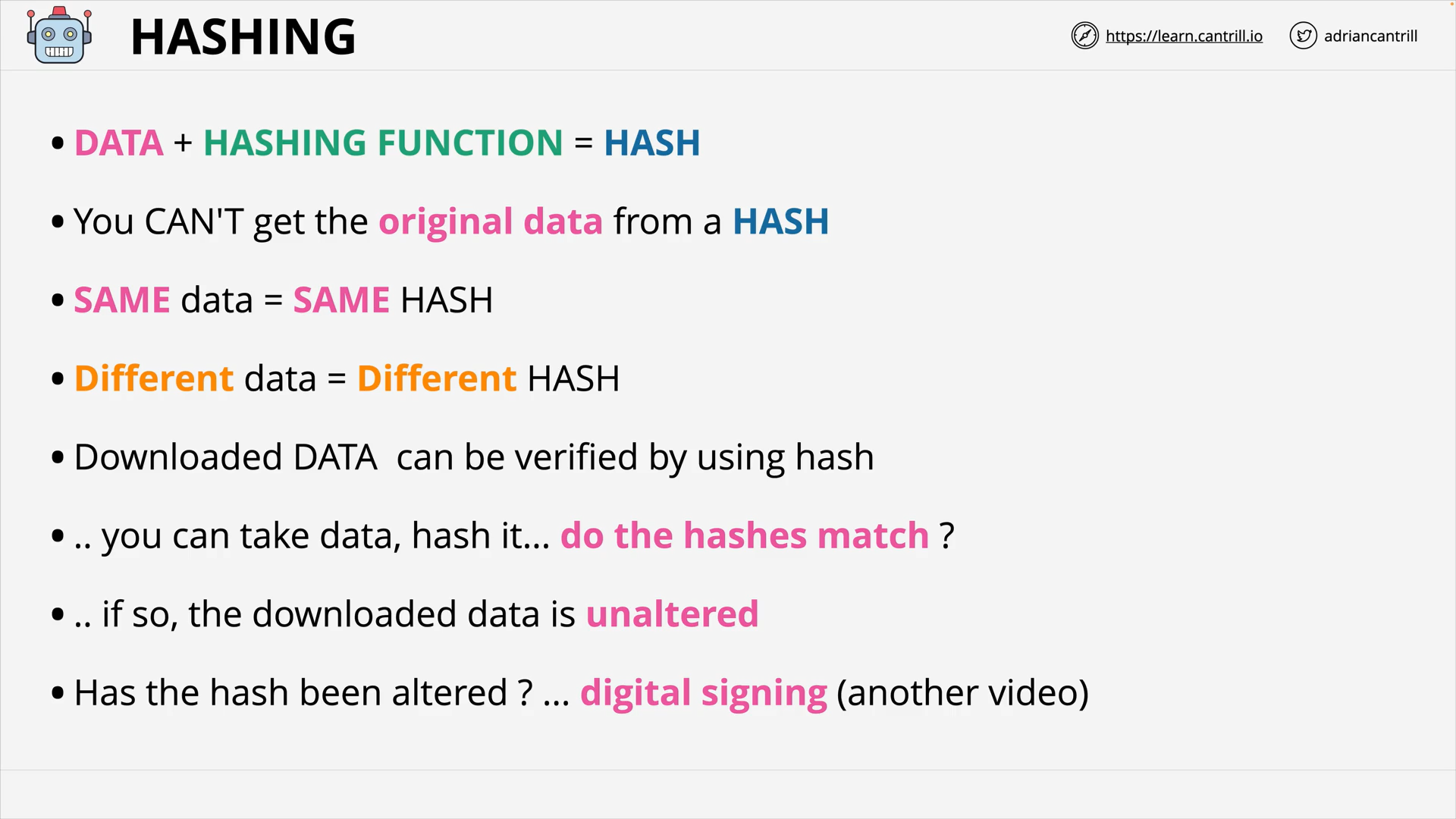 Hashing Summary
Hashing Summary
Digital Signatures (9:26)
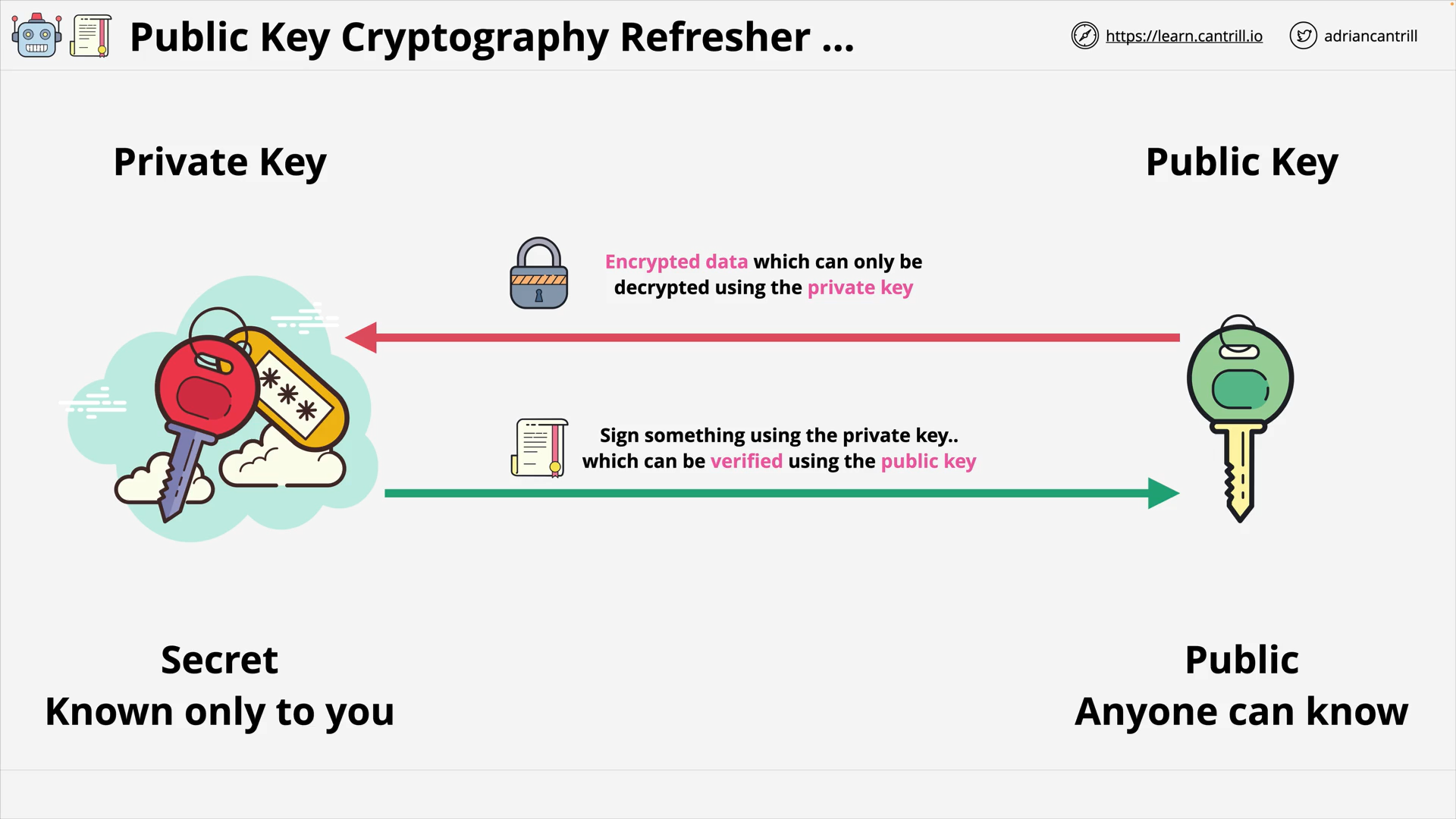 Public Key Cryptography
Public Key Cryptography
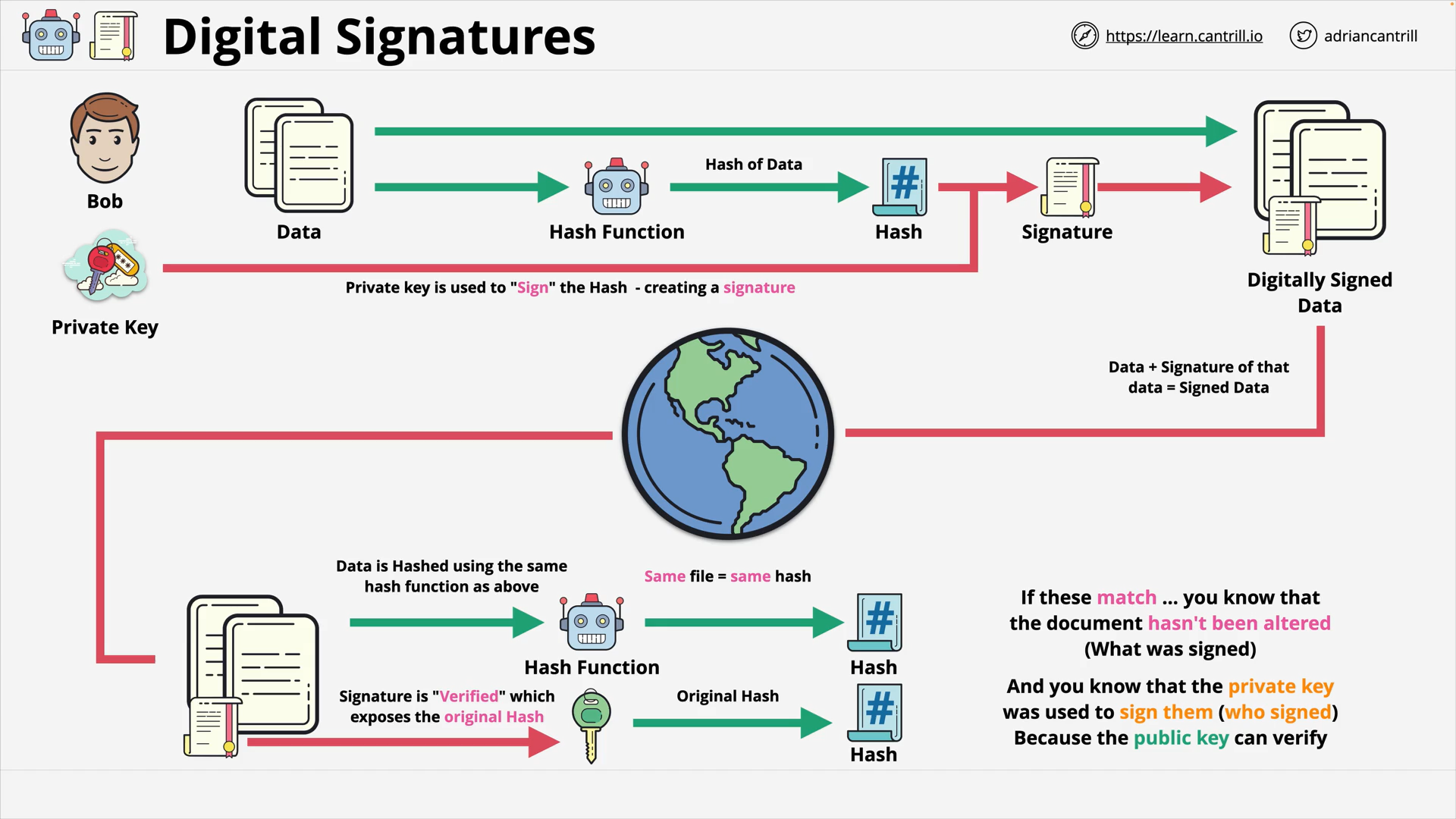
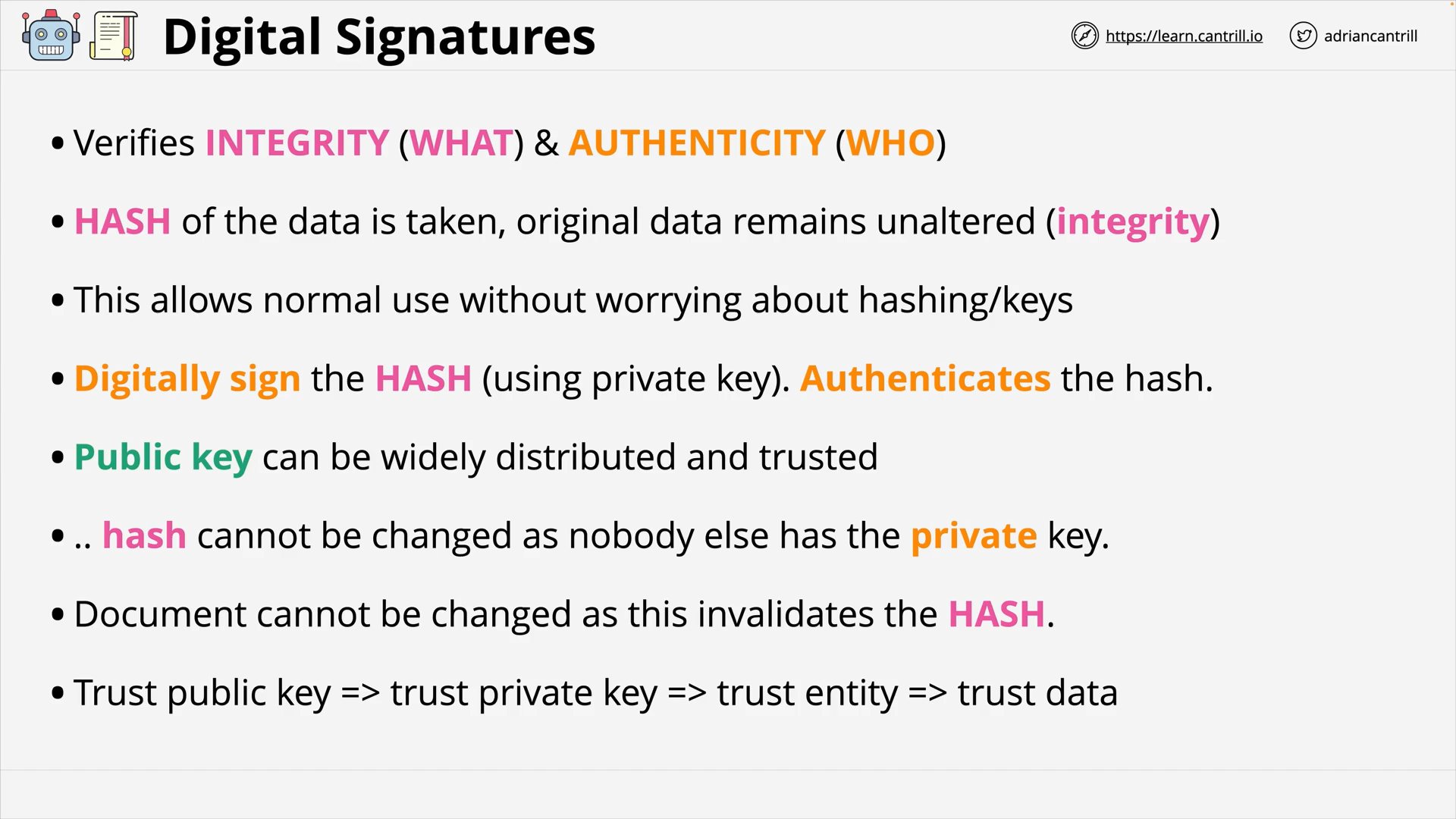 Digital Signatures verifies:
Digital Signatures verifies:
- Integrity (WHAT is sent) 👈 by compare the hash of data
- Authenticity (WHO sent it) 👈 by using the public key to very the signature
DNS & DNSSEC
DNS #1 - What does DNS do (2:56)
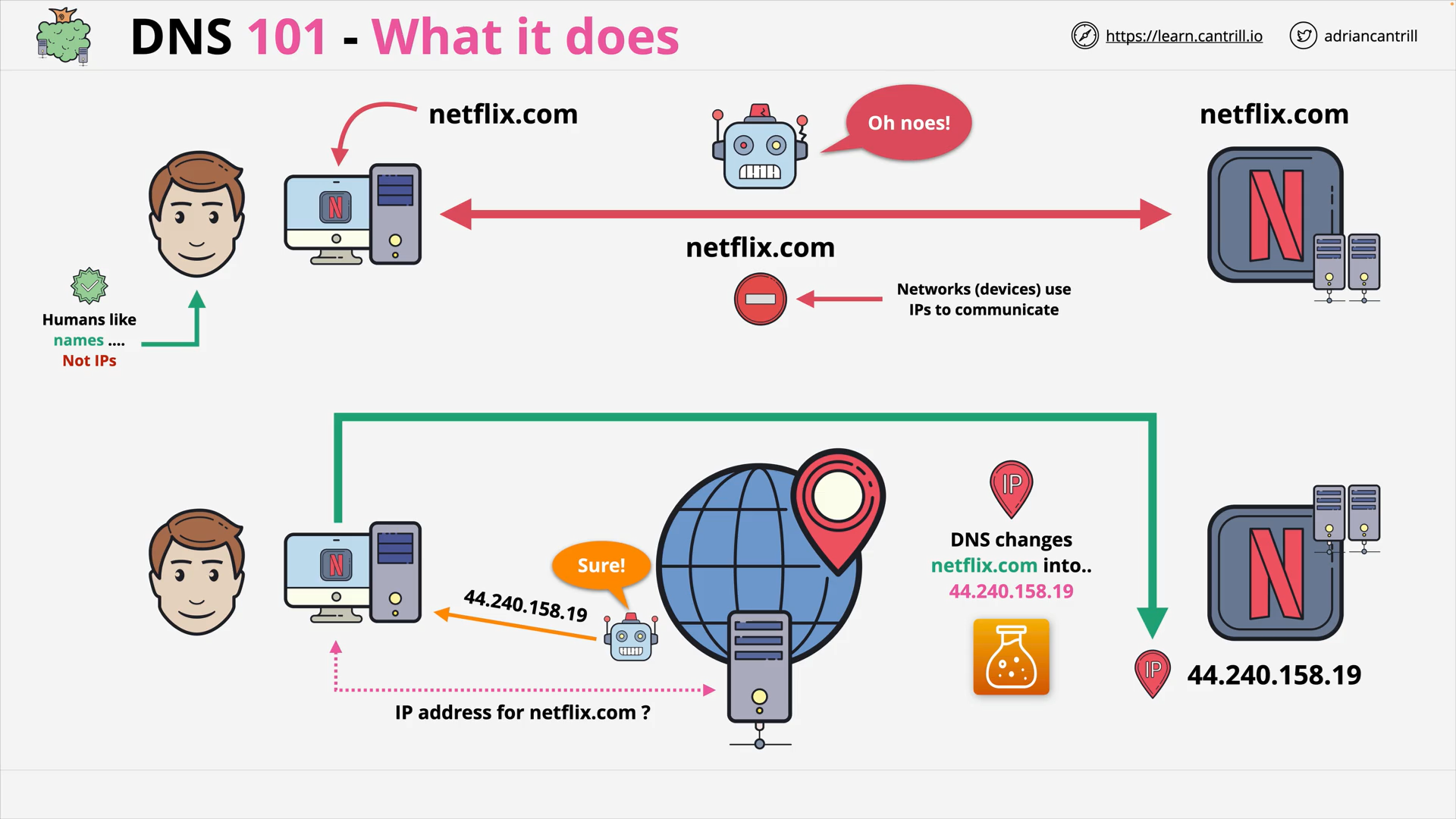 DNS translates human readable domain names (e.g. www.amazon.com) to machine readable IP addresses (e.g. 192.0.2.44)
DNS translates human readable domain names (e.g. www.amazon.com) to machine readable IP addresses (e.g. 192.0.2.44)
DNS #2 - Why does DNS need a complex architecture (13:19)
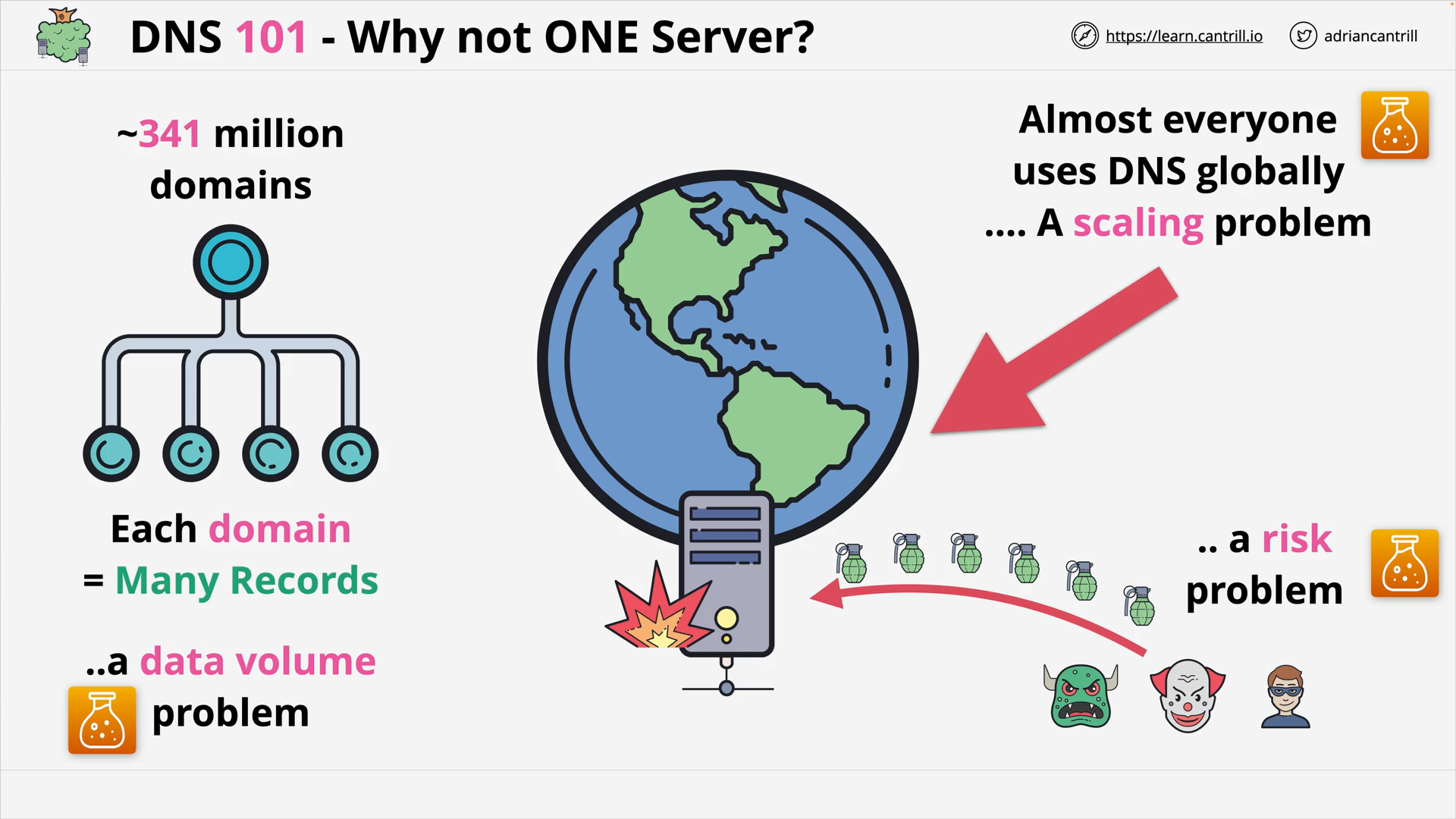 Why not ONE server?
Why not ONE server?
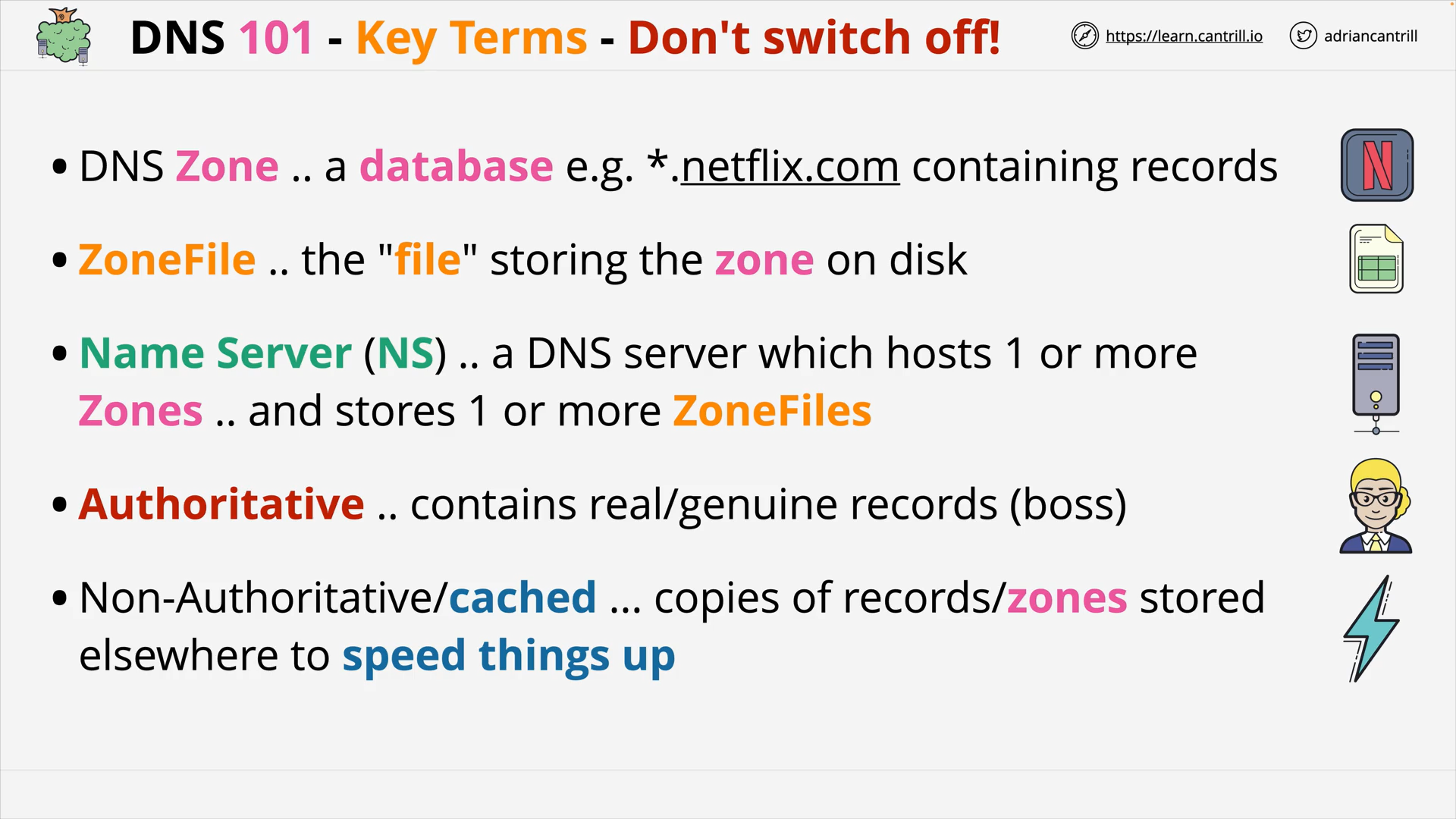 DNS Terms
DNS Terms
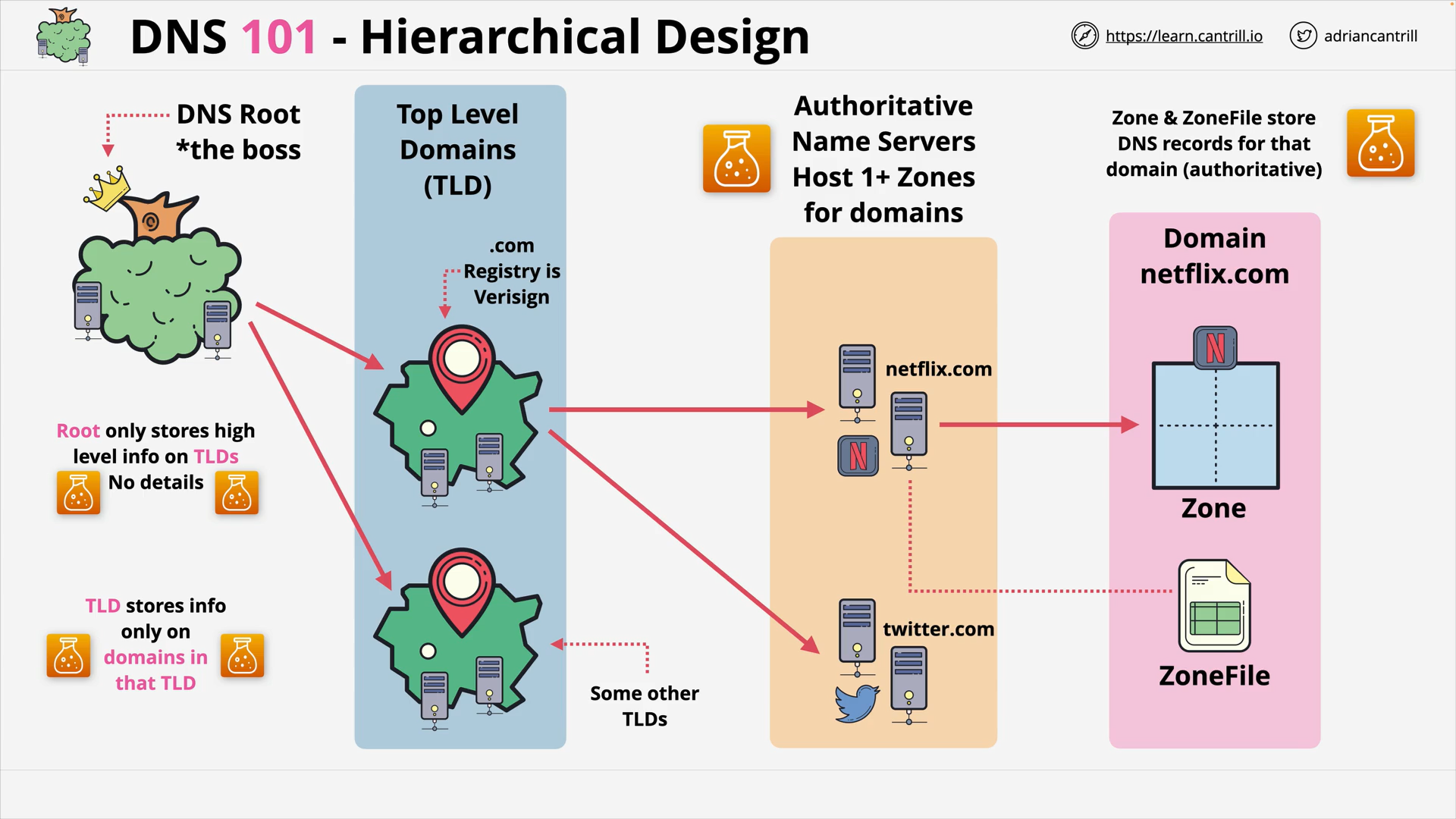 DNS Hierarchical Design
DNS Hierarchical Design
DNS #3 - How DNS actually works … walking the tree (8:46)
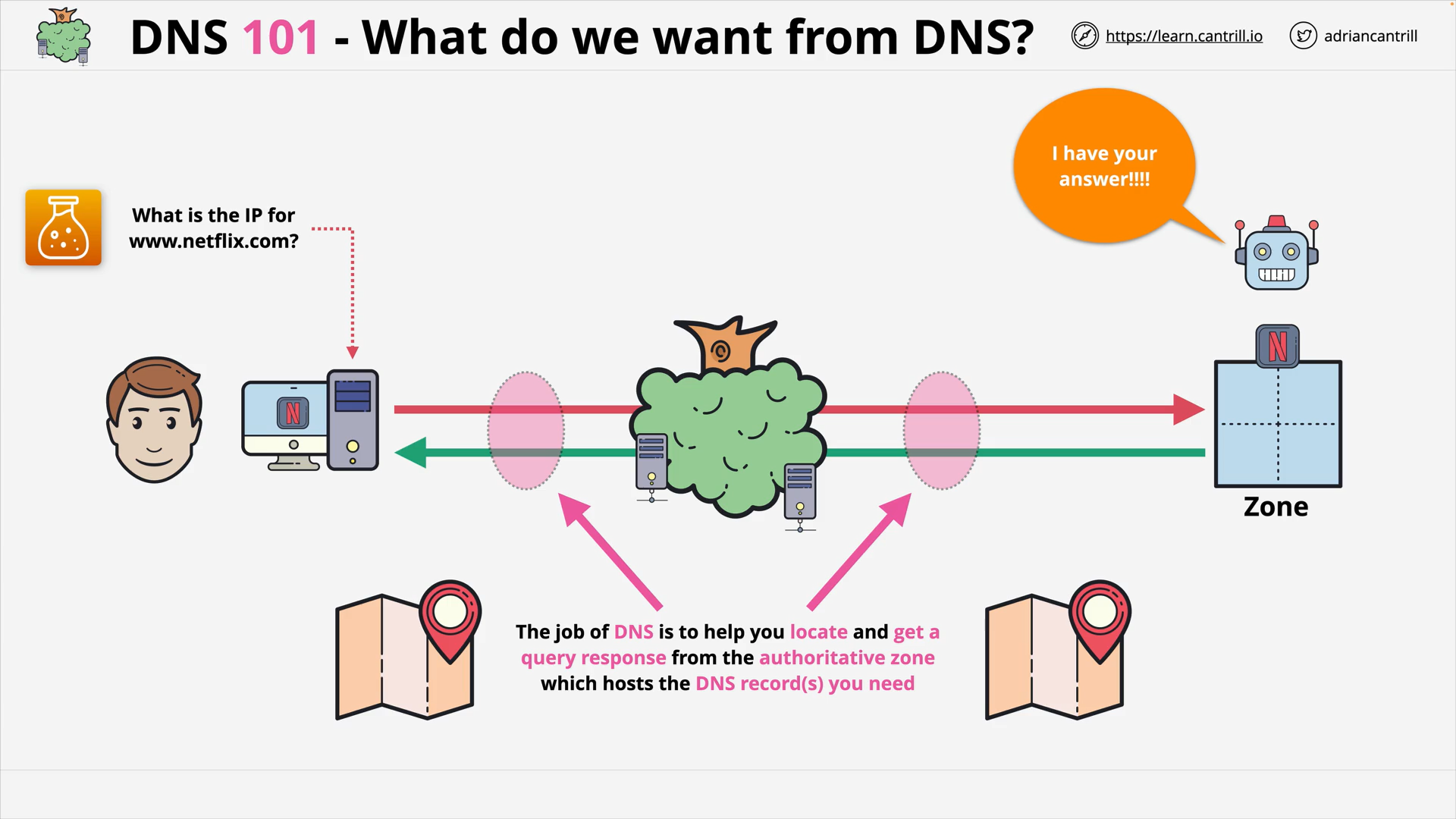 The job of DNS is help us get the DNS records we need.
The job of DNS is help us get the DNS records we need.
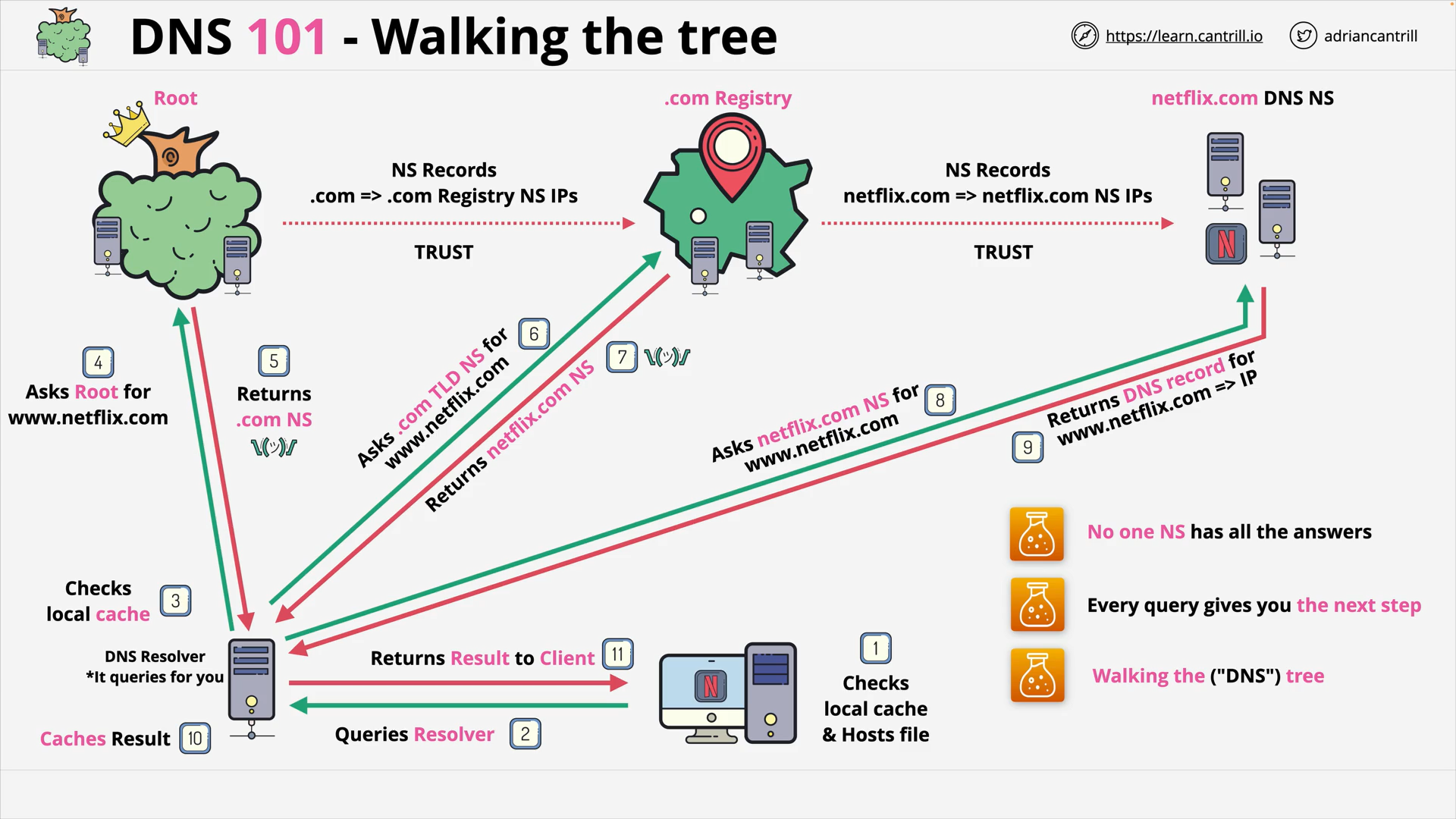 DNS - Walking the tree
DNS - Walking the tree
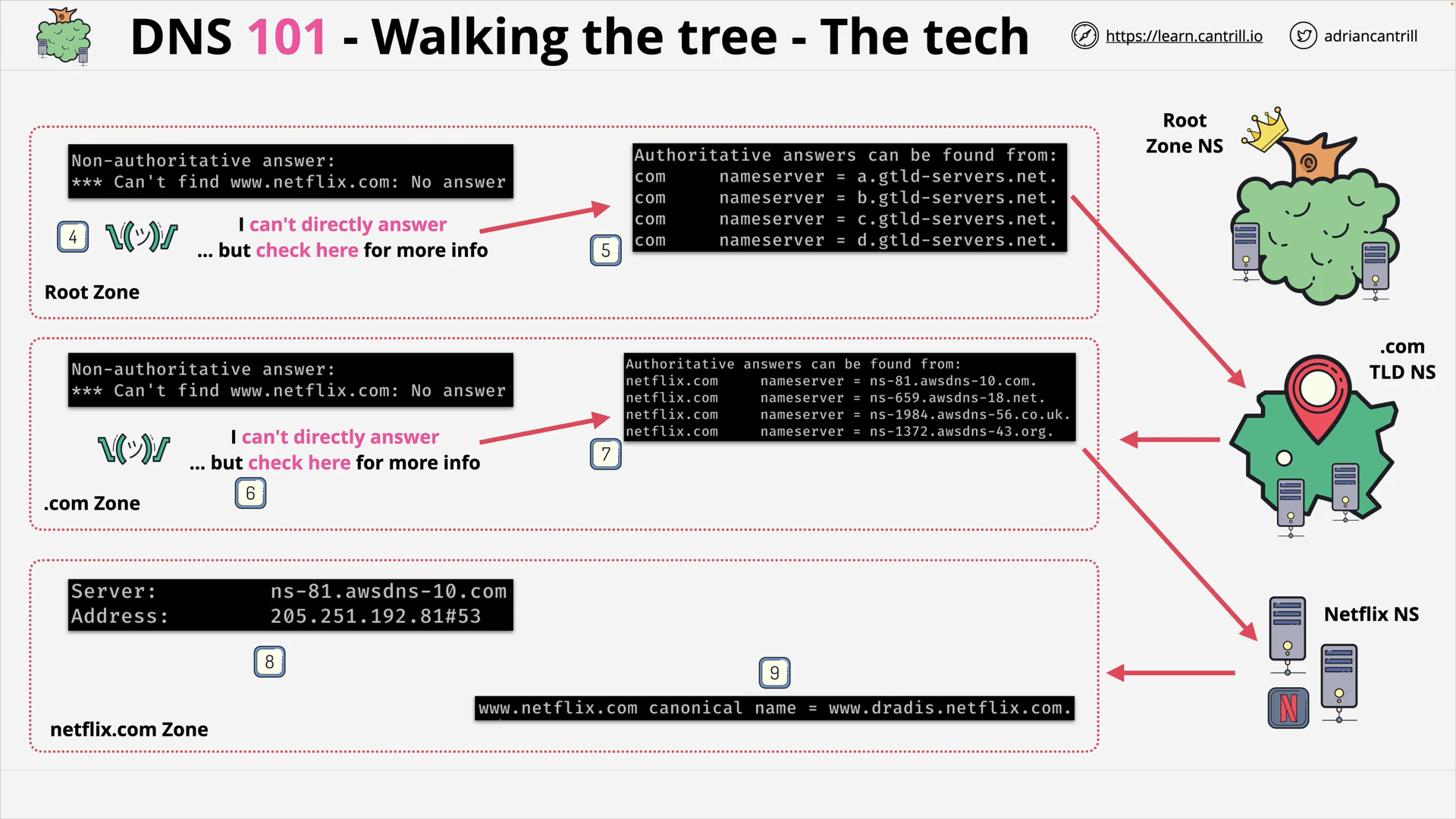 DNS - Walking the tree - Behind the scene
DNS - Walking the tree - Behind the scene
DNS #4 - What happens when a domain is registered? (4:27)
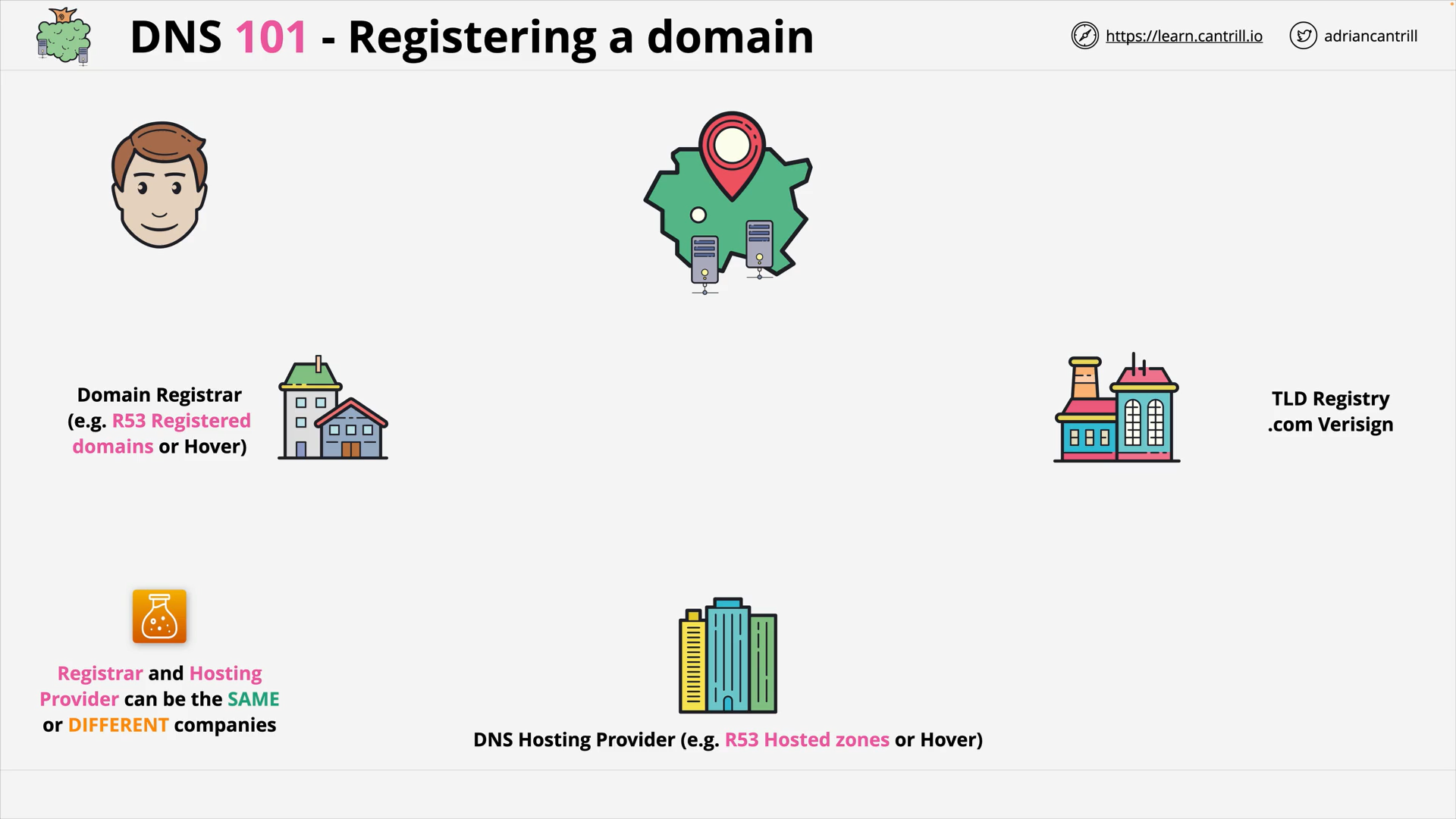 Domain Registrar - DNS Hosting Provider - TLD Registry
Domain Registrar - DNS Hosting Provider - TLD Registry
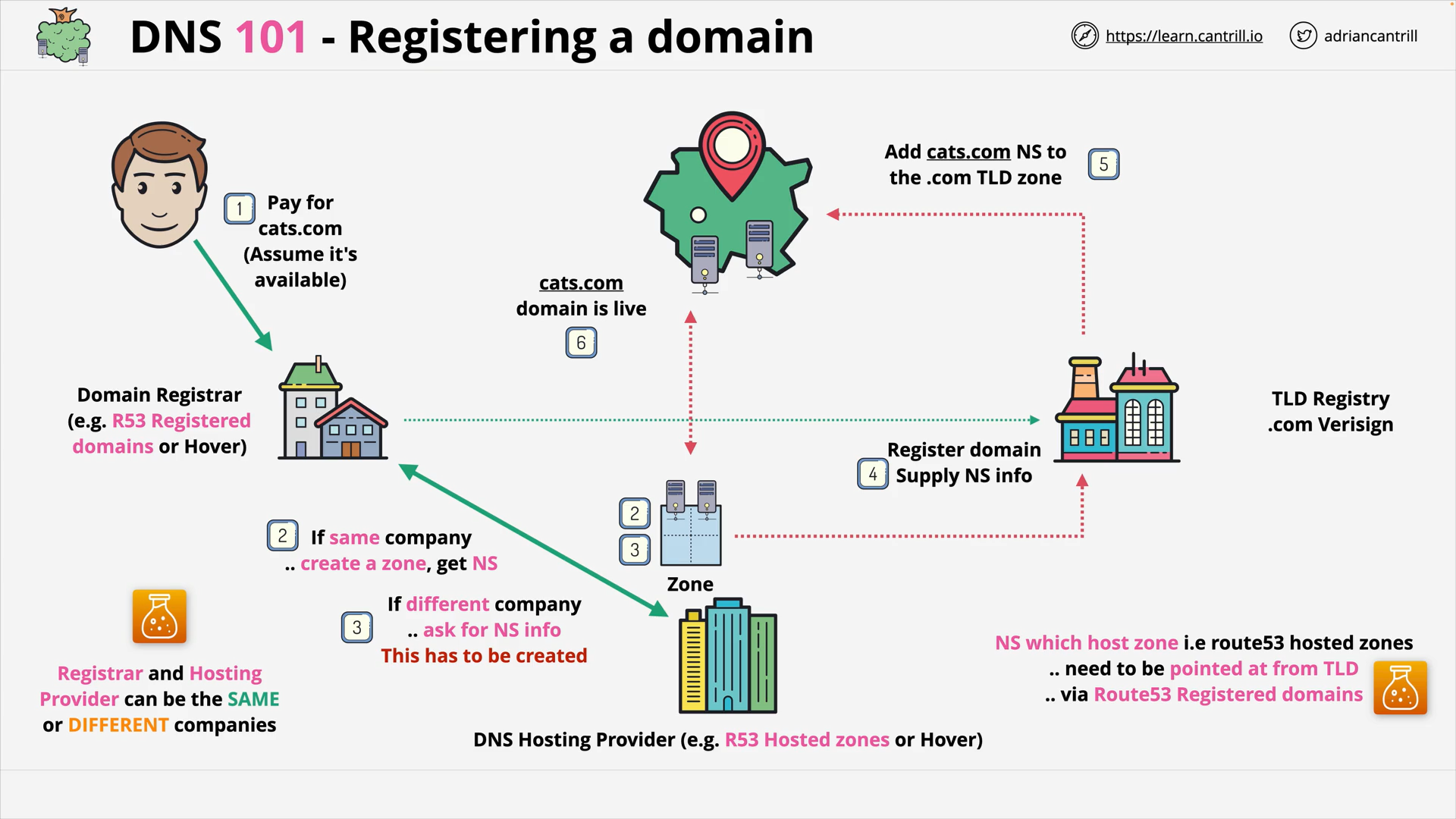 Registering a domain
Registering a domain
DNSSEC #1 - Why do we need DNSSEC (11:08)
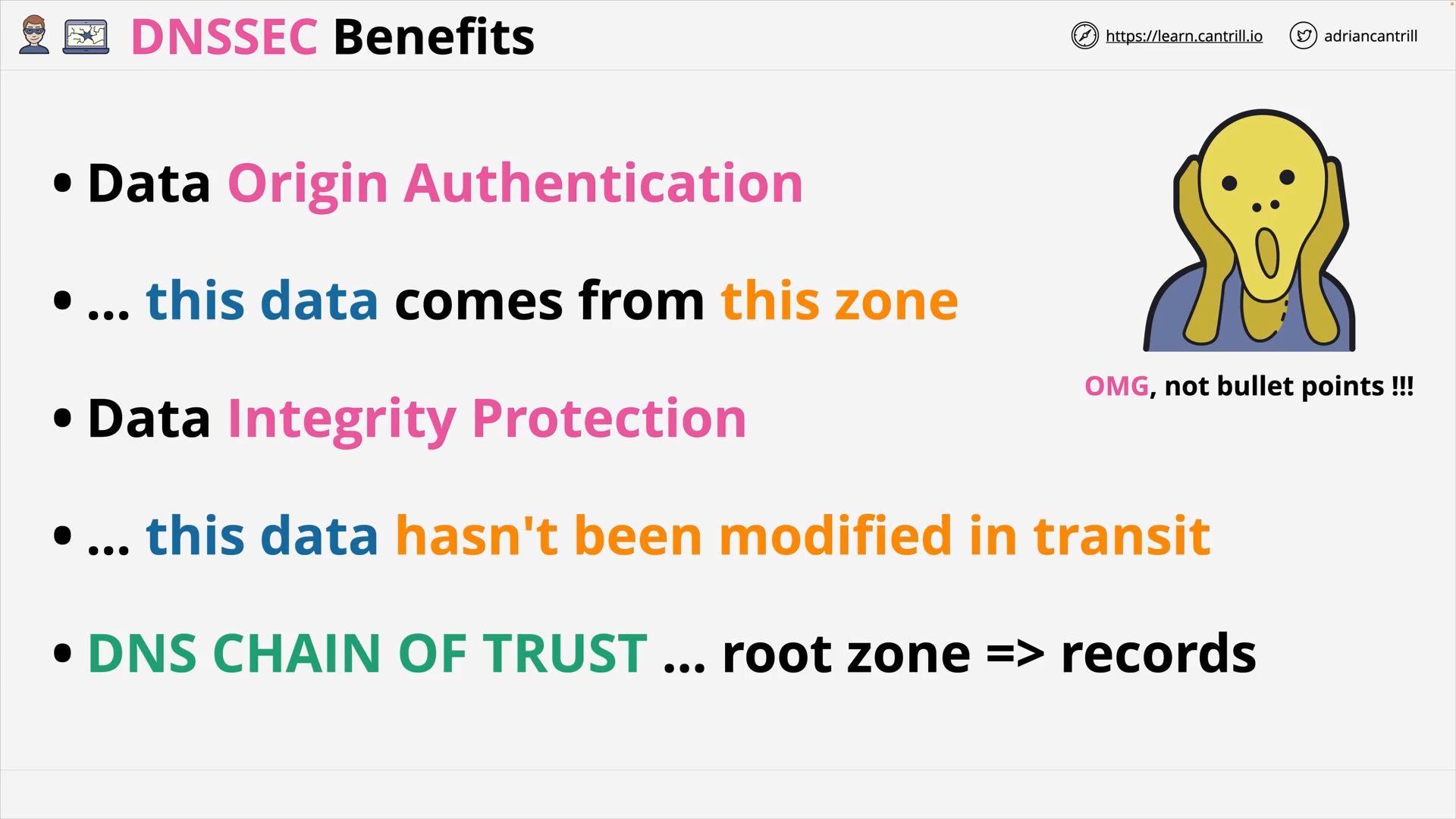 DNSSEC Benefits ~ Digital Signature for DNS Records
DNSSEC Benefits ~ Digital Signature for DNS Records
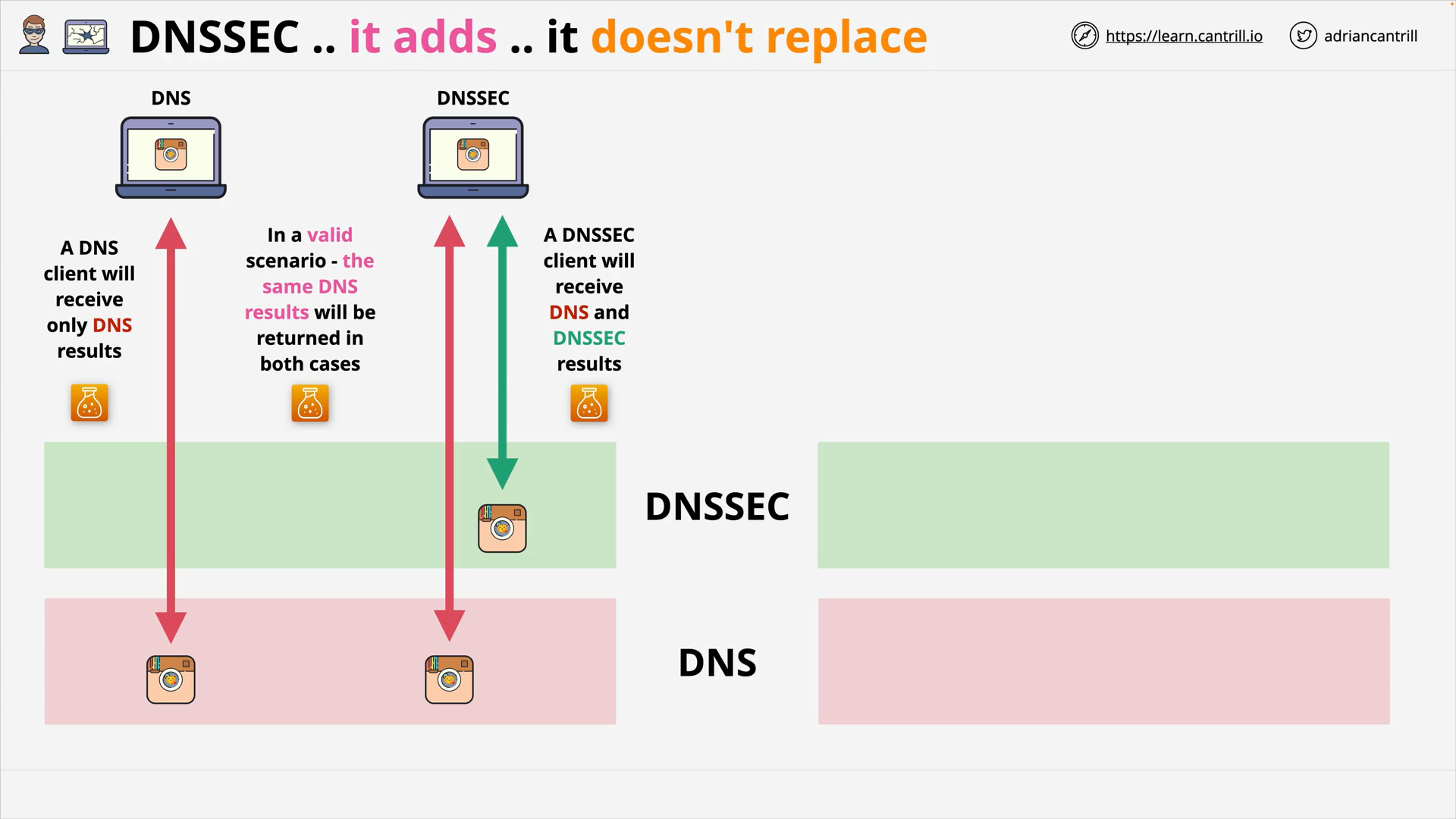 DNSSEC is an extension to DNS. It adds, and doesn’t replace DNS.
DNSSEC is an extension to DNS. It adds, and doesn’t replace DNS.
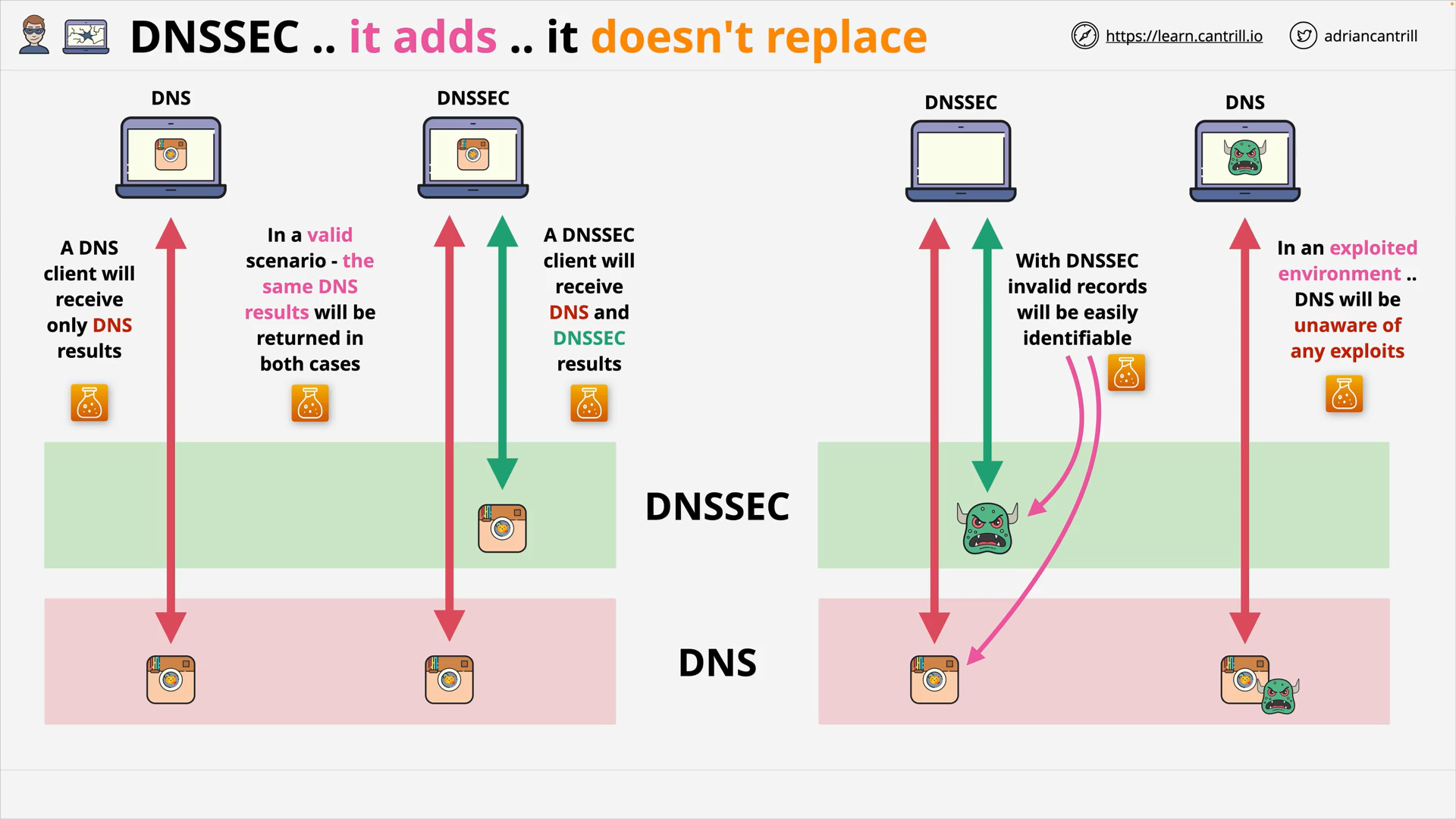 DNSSEC Benefit Example
DNSSEC Benefit Example
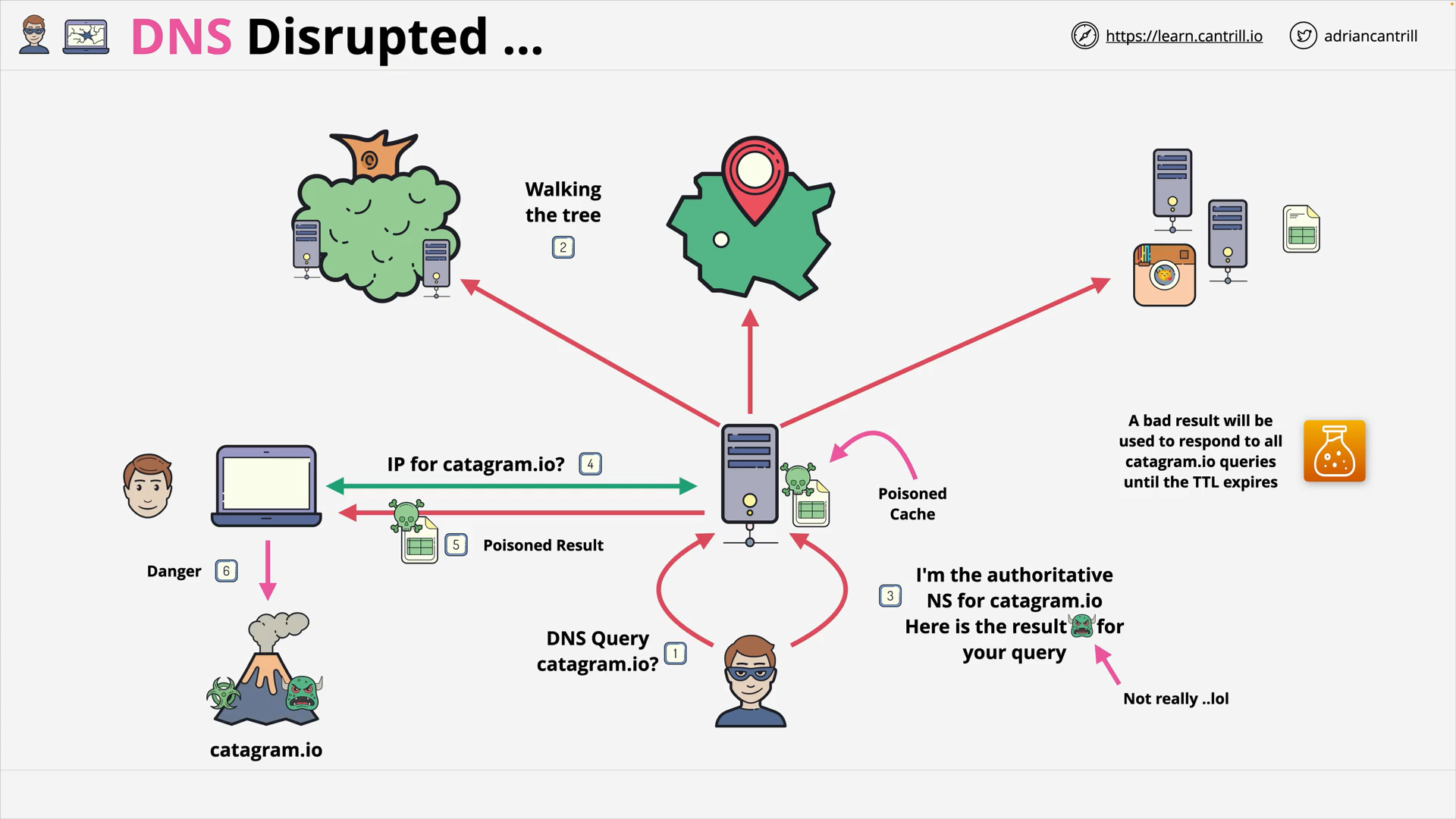 DNS Disrupted
DNS Disrupted
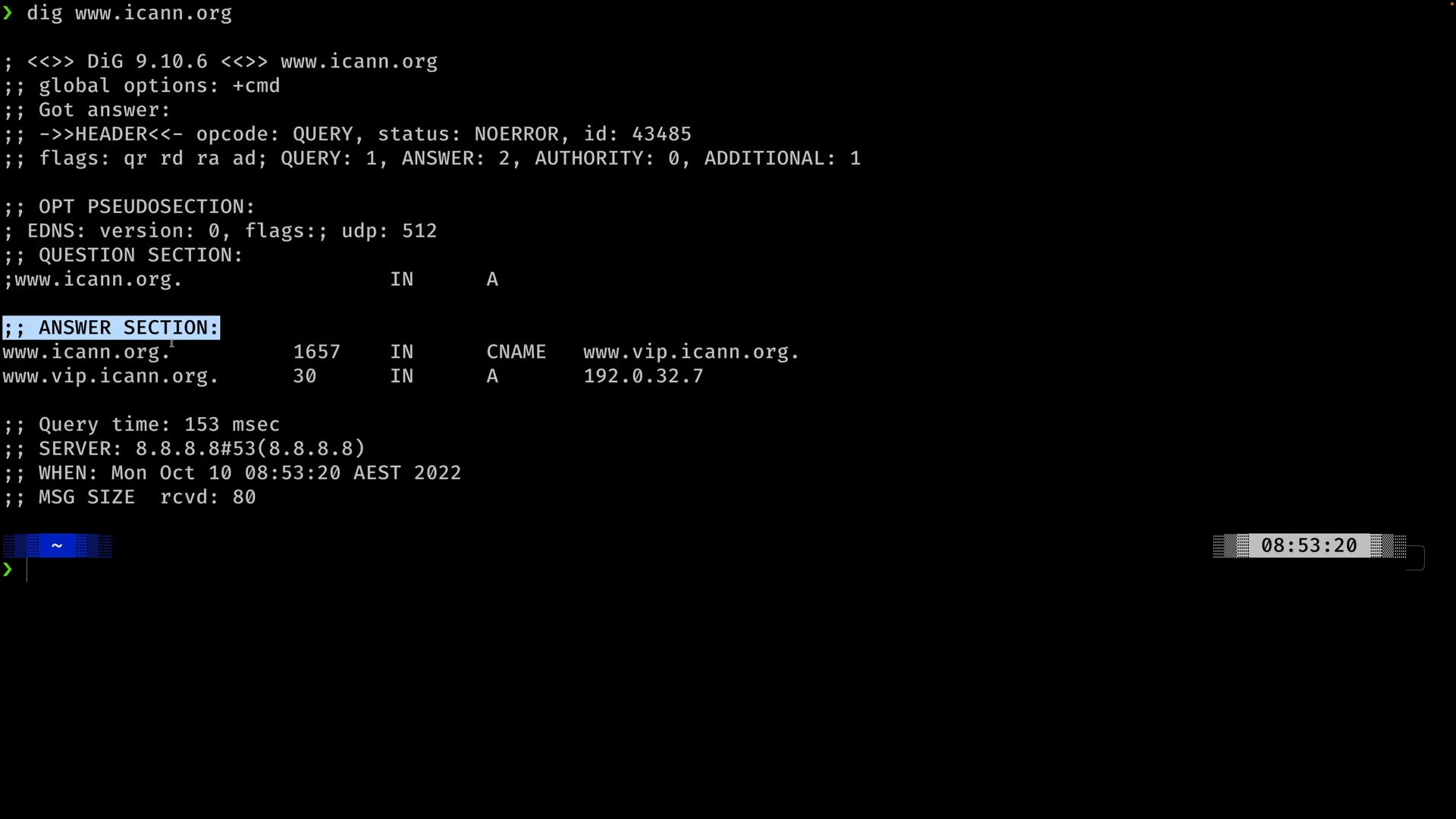 Example: Use dig to query A record for example.com
Example: Use dig to query A record for example.com
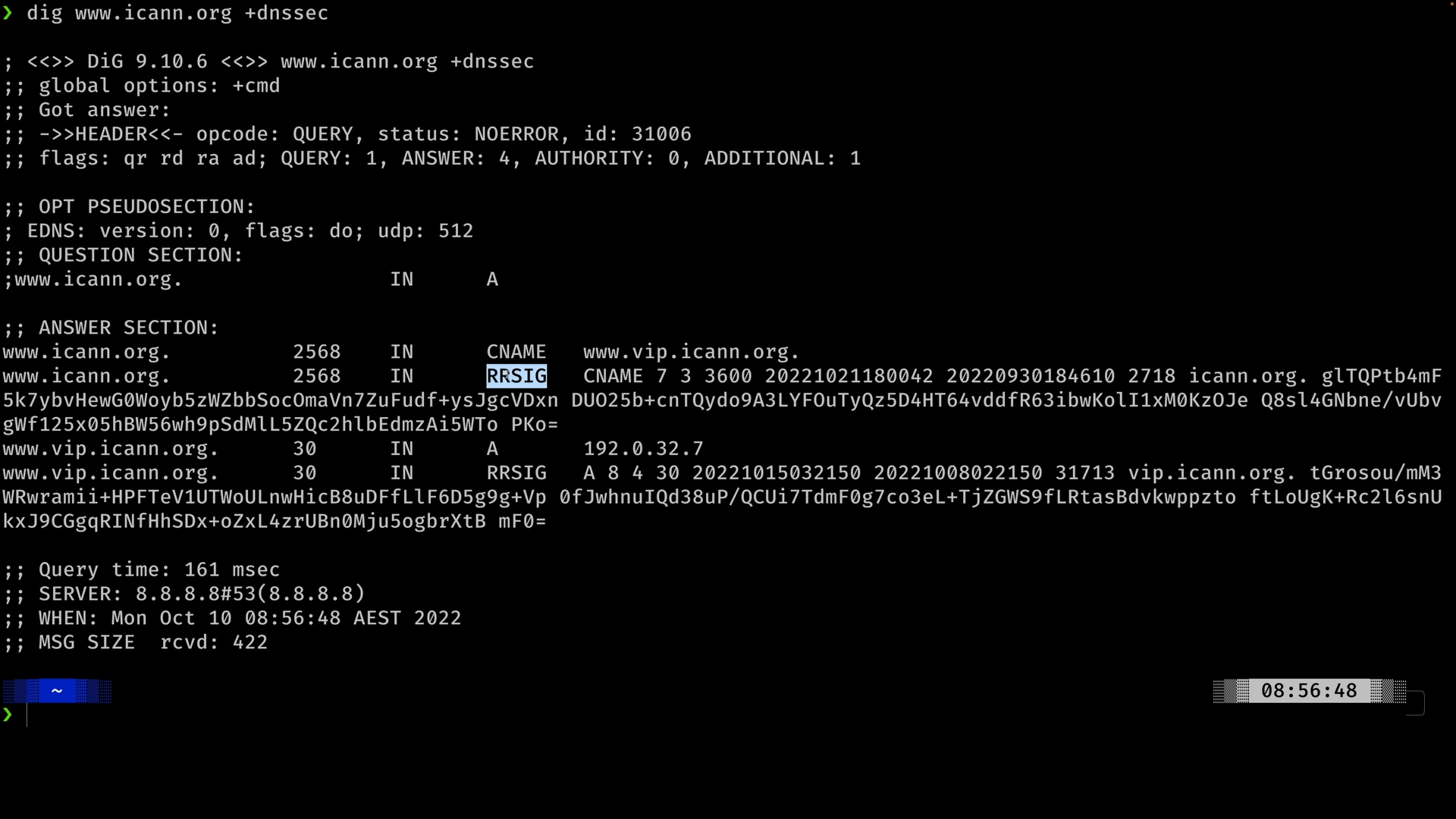 Example: Use dig to query A record and DNSSEC for example.com
Example: Use dig to query A record and DNSSEC for example.com
note
To verify DNSSEC of a domain, you can use:
- dig: if there’s the flag
ad - delv
- Web Tools: DNS Viz, DNSSEC Debugger
See
DNSSEC #2 - How DNSSEC Works within a Zone (17:34)
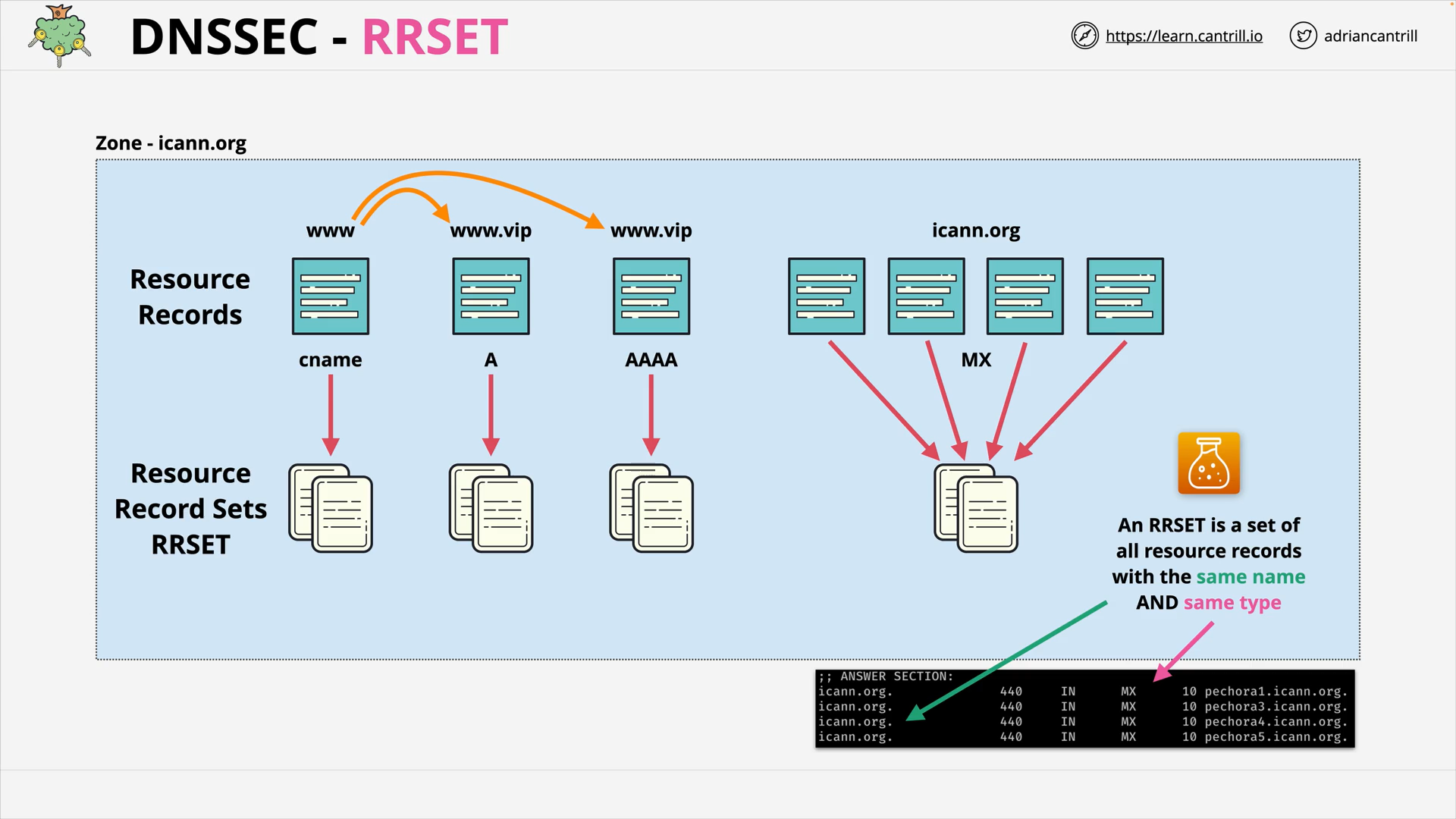 DNSSEC - RRSET
DNSSEC - RRSET
what is a rrset?
A group of all the records with the same type ad same name
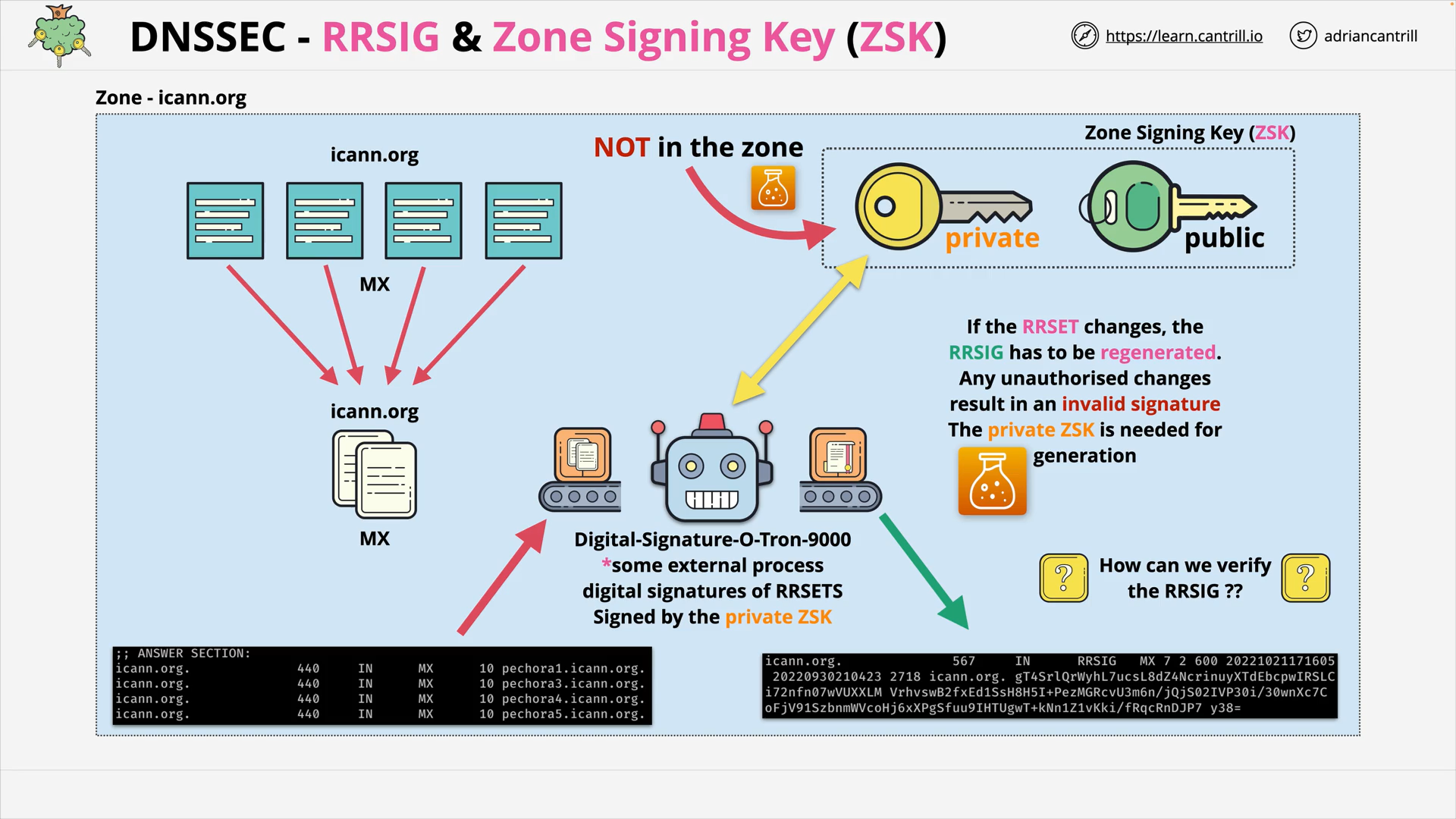 DNSSEC - RRSIG & Zone Signing Key (ZSK)
DNSSEC - RRSIG & Zone Signing Key (ZSK)
what is a rrsig?
A digital signature for a RRSET, signed by the private Zone Signing Key (ZSK).
what is zone signing key (zsk)?
Each zone has a ZSK, which is used to:
- sign 👈 the private ZSK
- verify 👈 the public ZSK
the RRSETs.
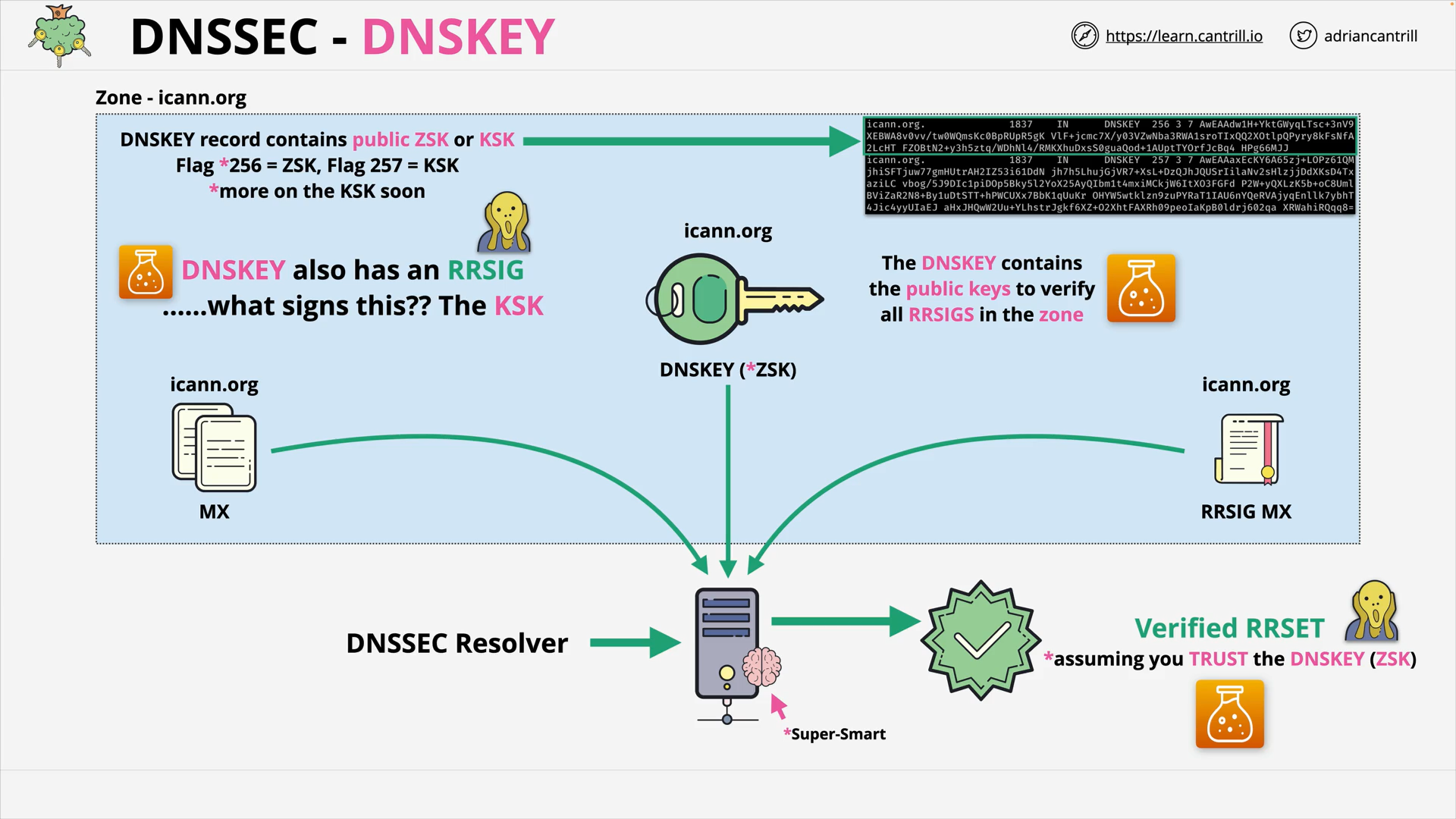 DNSSEC - DNSKEY contains public ZSK to verify all RRSIGs in the zone
DNSSEC - DNSKEY contains public ZSK to verify all RRSIGs in the zone
why the dnskey also has an rrsig?
Because someone can fake the DNSKEY too. 🤯
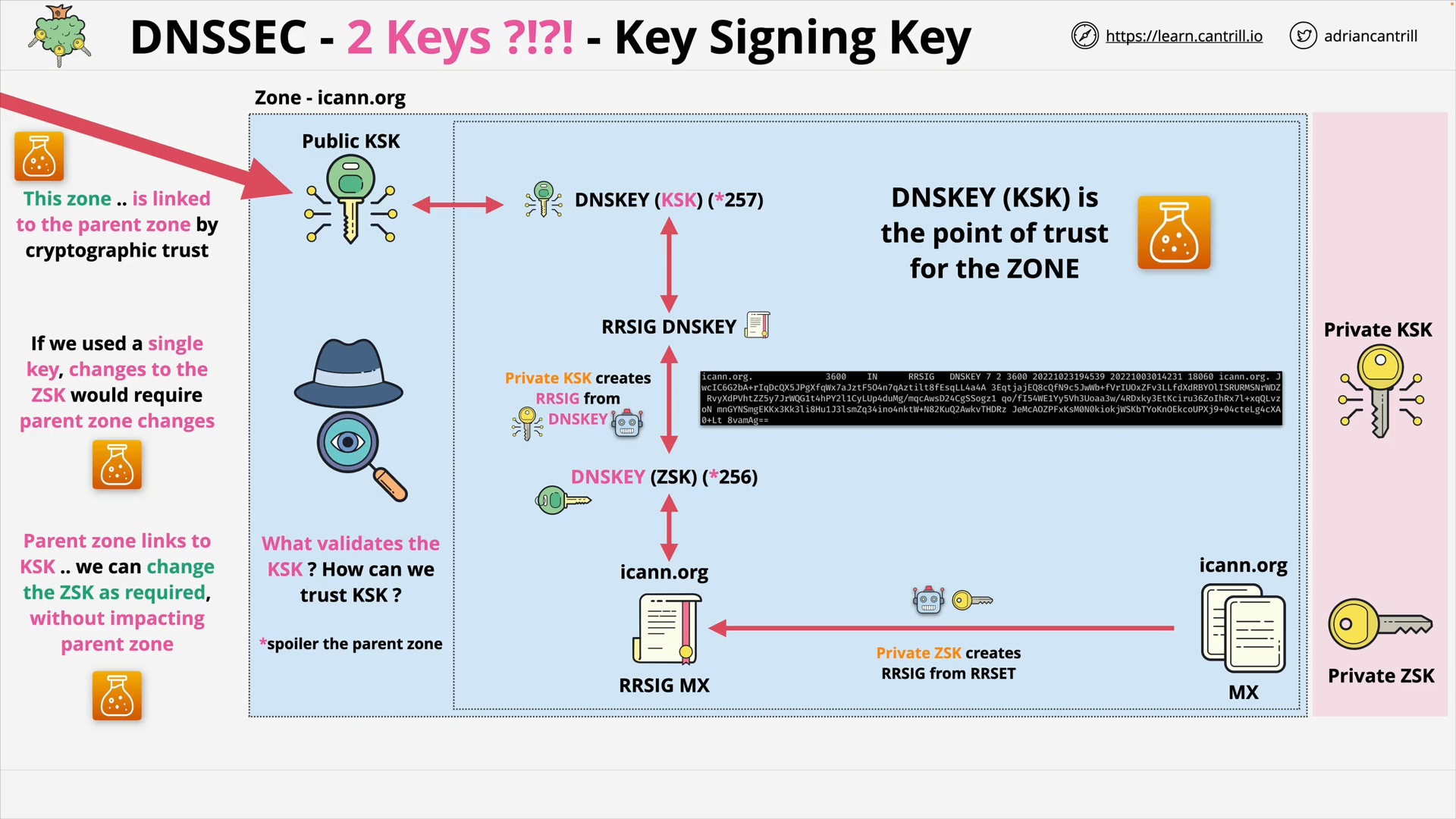 DNSSEC - 2 Keys - Key Signing Key
DNSSEC - 2 Keys - Key Signing Key
what is a ksk?
KSK is used to sign and verify the ZSK
why do we use separate zone-signing keys and key-signing keys?
The KSK is linked to the parent zone.
If we use a single key, changes to the ZSK would requires parent zone changes. 🐌🆘
By using 2 keys, we can change the ZSK as quired, without impacting parent zone. 🤳
 DNSSEC - Summary
DNSSEC - Summary
DNSSEC #3 - DNSSEC Chain of Trust (8:16)
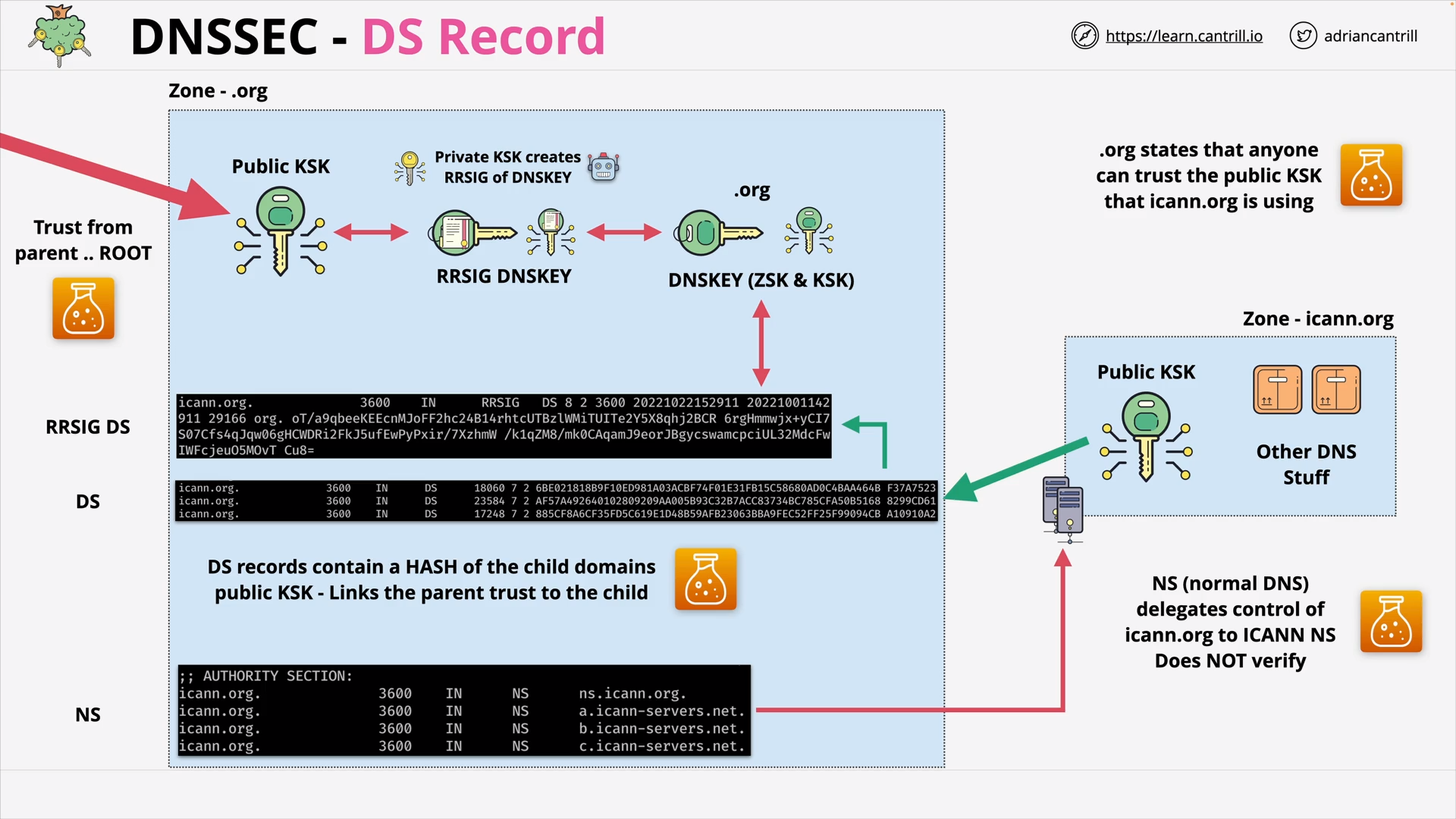 DNSSEC - DS Record
DNSSEC - DS Record
what is ds record?
DS (Delegation Signer) Record, on a parent zone, contains a hash of the KSK in a child zone.
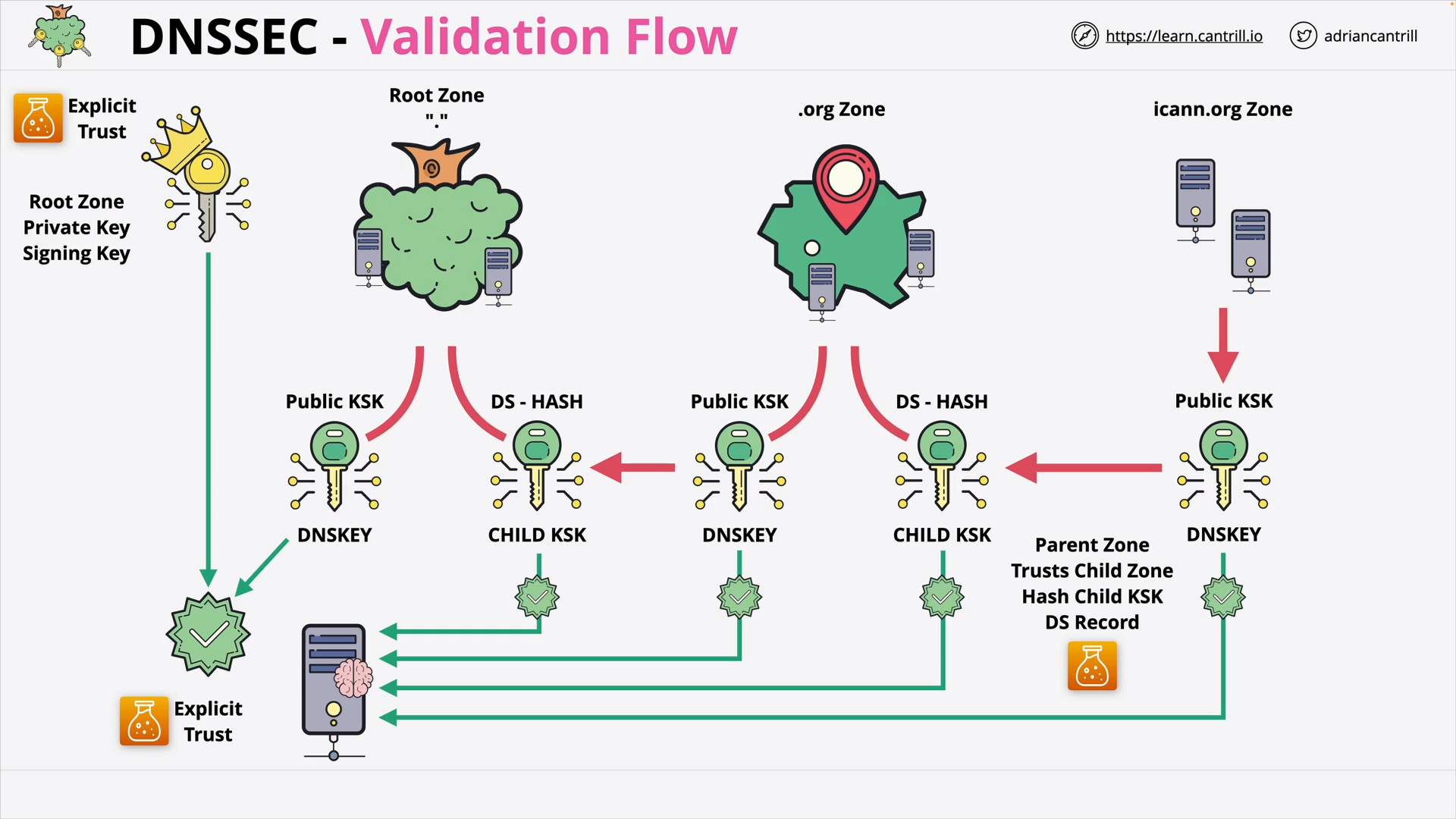 DNSSEC - Validation Flow
DNSSEC - Validation Flow
DNSSEC #4 - DNSSEC Root Signing Ceremony (7:53)
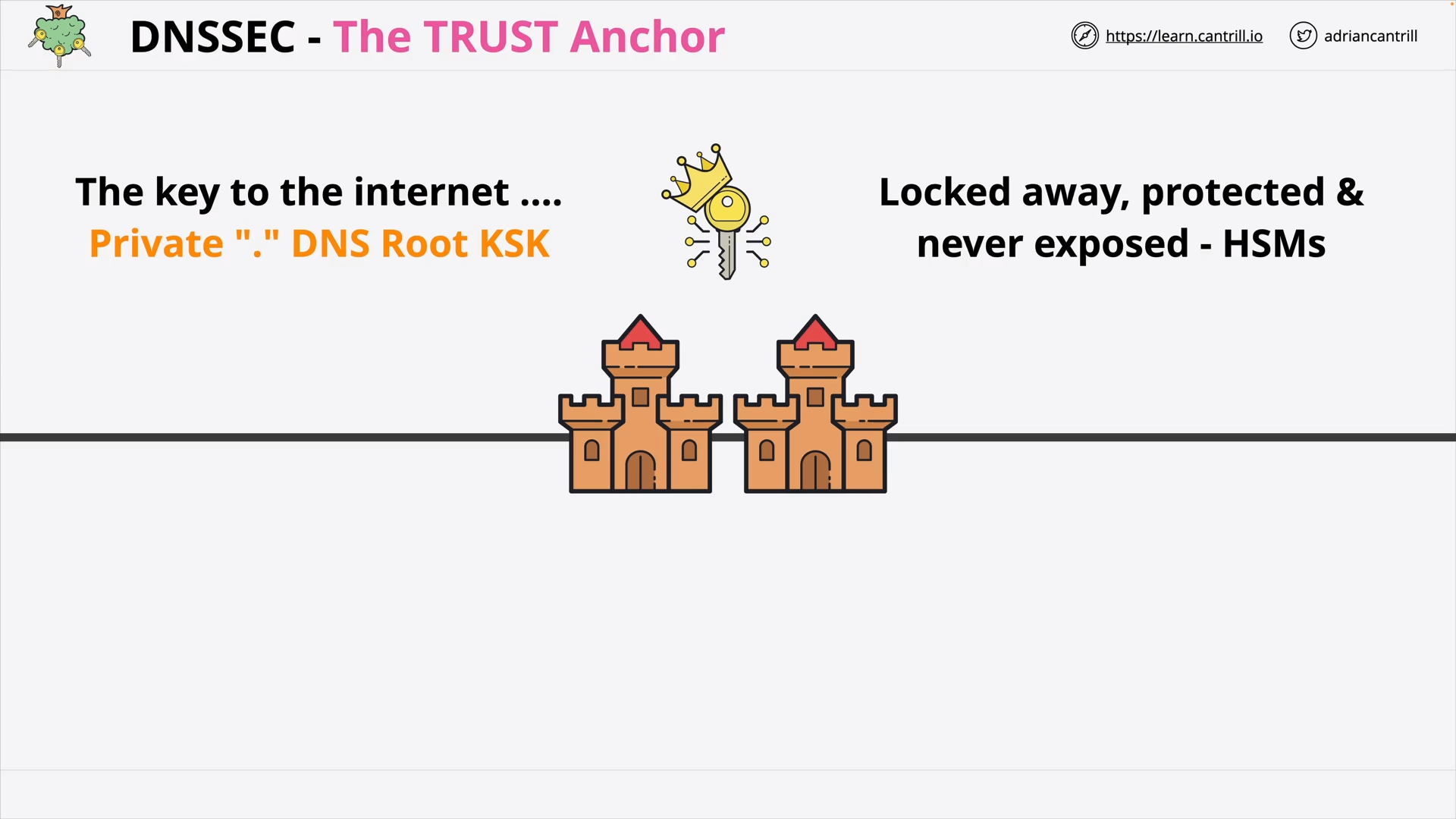 DNSSEC - Root KSK Private
DNSSEC - Root KSK Private
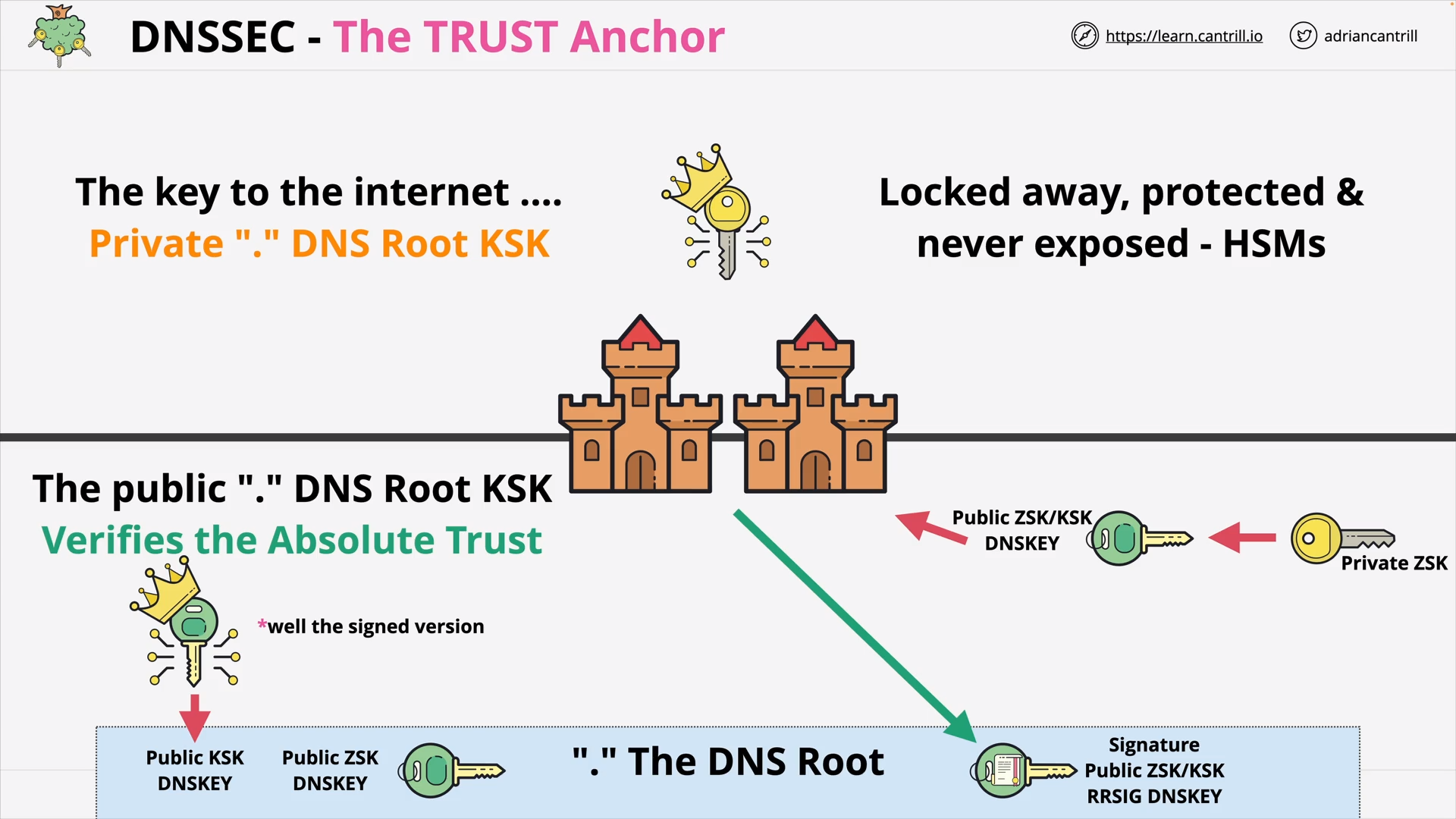 DNSSEC - Root KSK Public
DNSSEC - Root KSK Public
 DNSSEC - The TRUST Anchor (Root KSK)
DNSSEC - The TRUST Anchor (Root KSK)
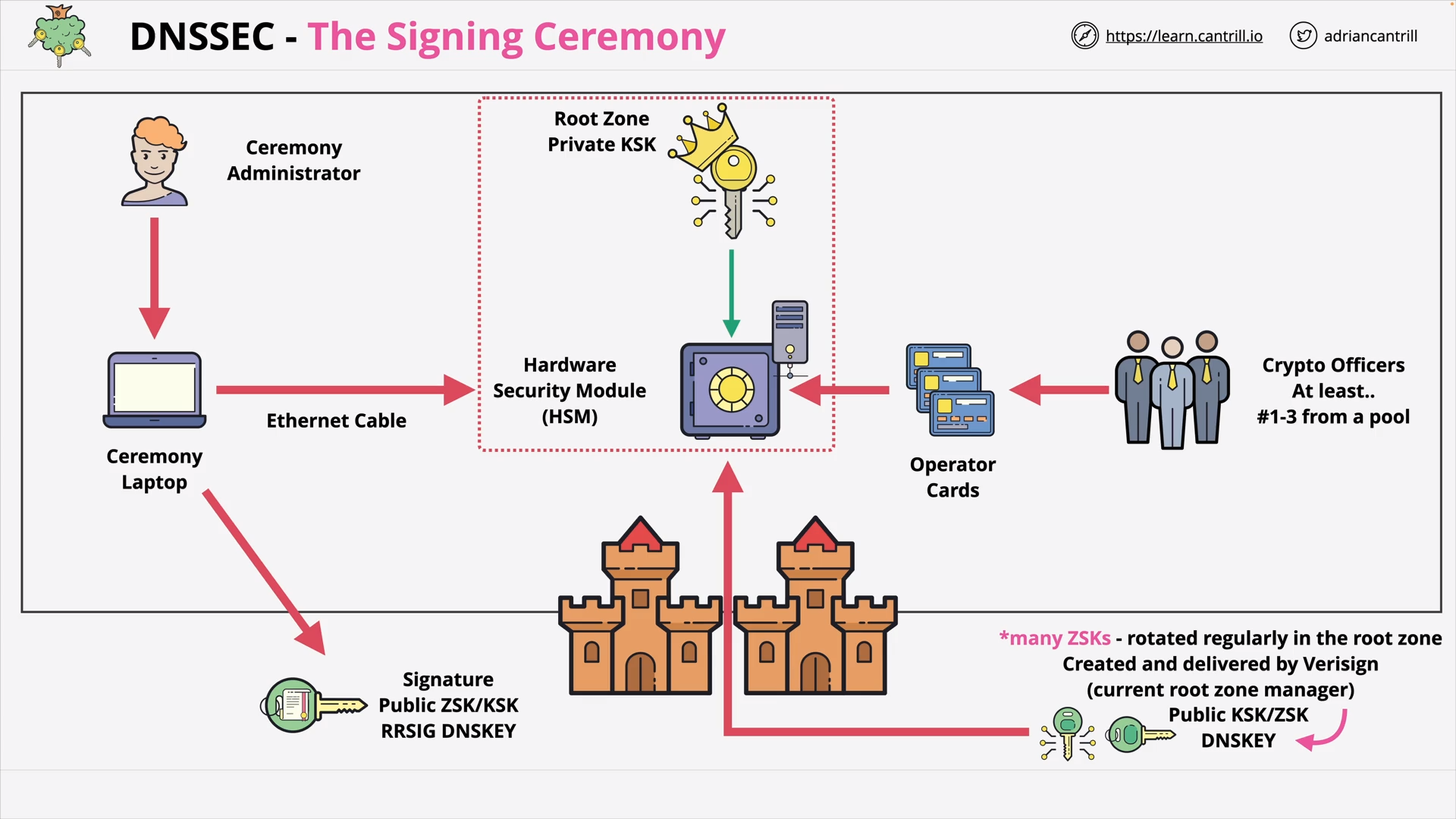 DNSSEC - The Signing Ceremony
DNSSEC - The Signing Ceremony
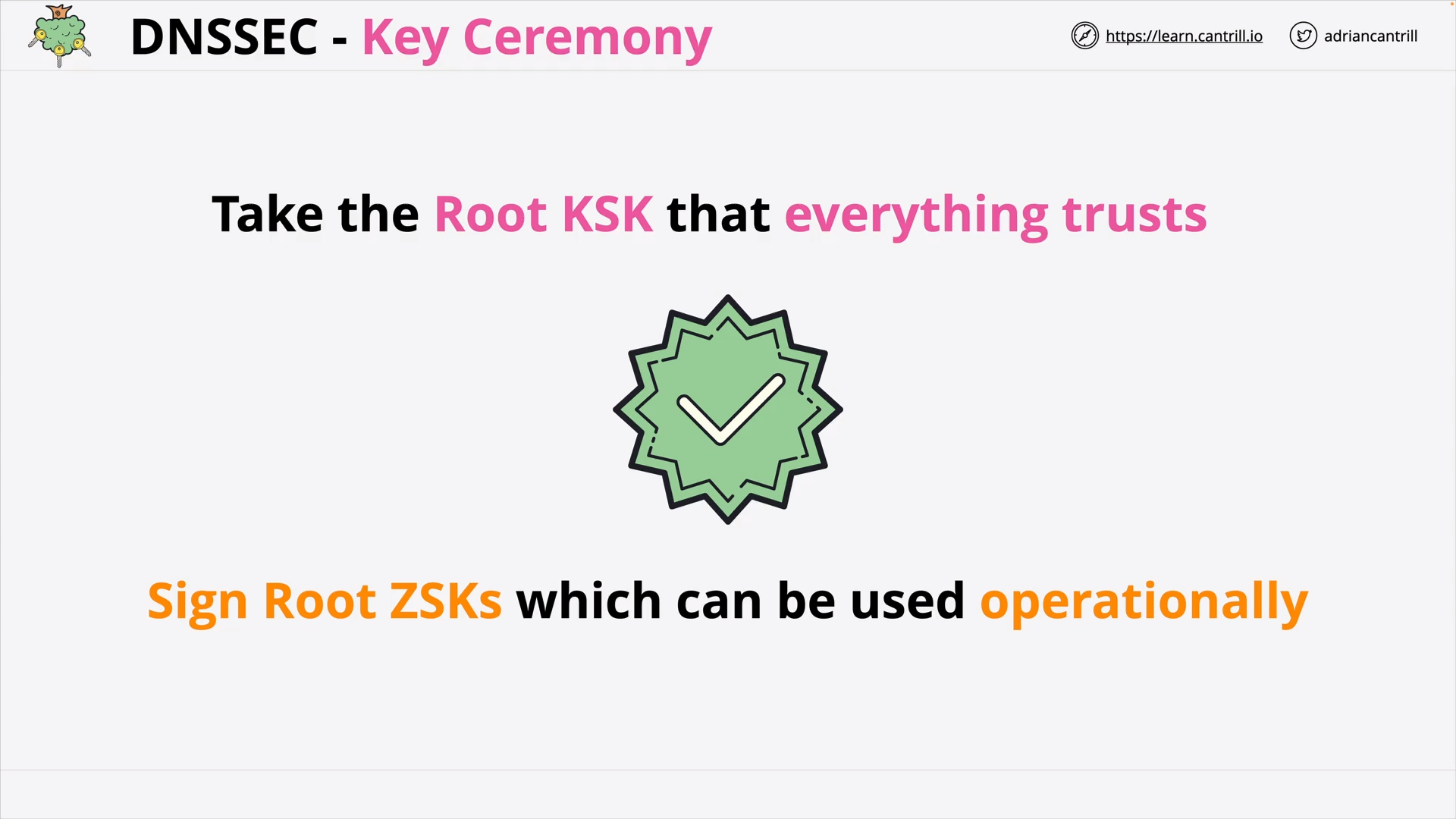 DNSSEC - Key Ceremony
DNSSEC - Key Ceremony
See The Key to the Internet and Key Ceremonies: An Explainer | ICANN
Containers & Virtualization (MORE COMING SOON)
Kubernetes 101 (11:27)
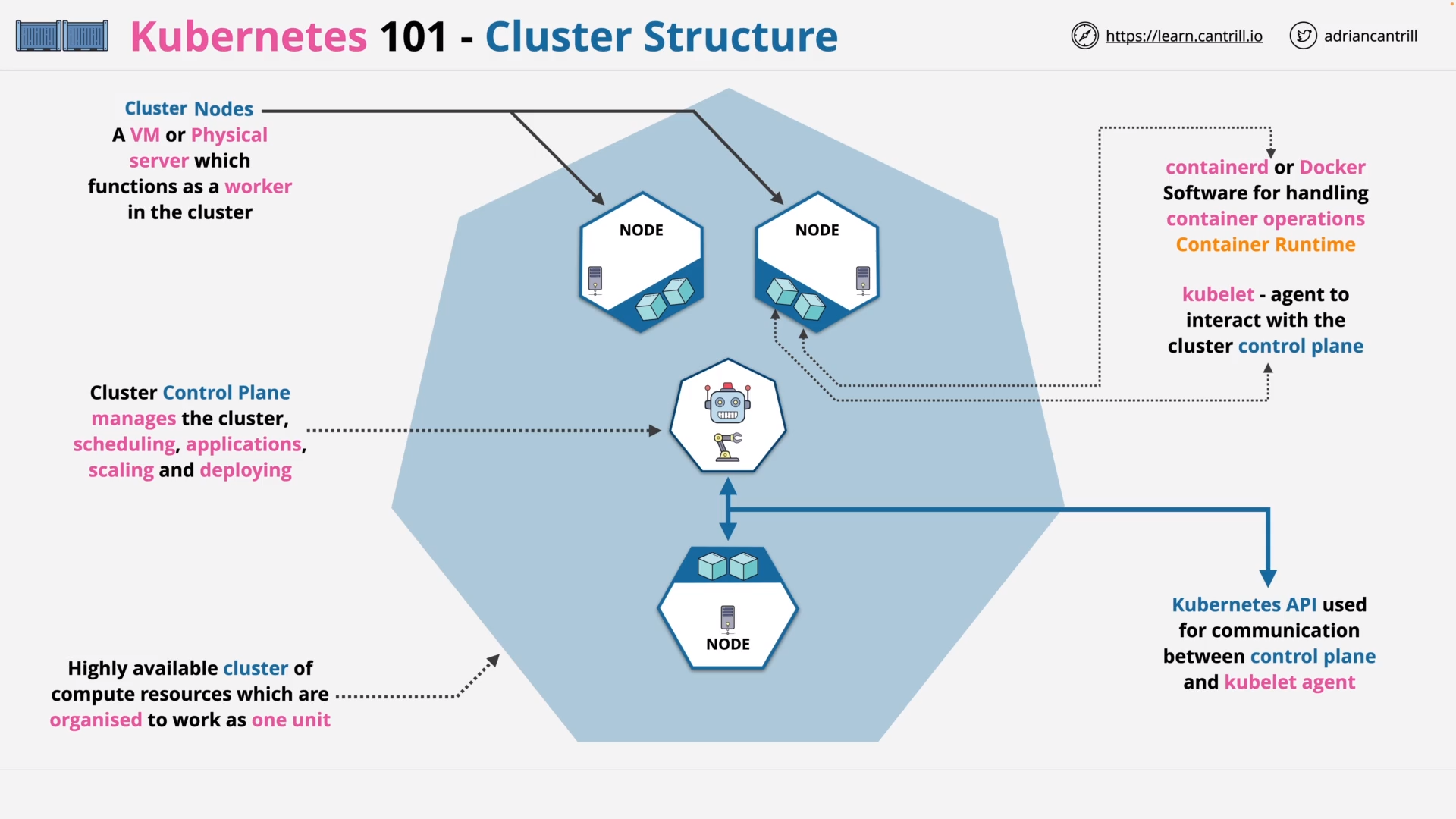 K8s - Cluster Structure
K8s - Cluster Structure
what is the basic structure of a k8s cluster?
A K8s cluster contains:
- Control Plane
- Worker Nodes
what is the control plane in k8s?
The control plane manages the overall state of the cluster
what is a worker node in k8s?
A worker node is the machine that actually run the containers
what are the core components of a worker node?
-
kubelet- Ensures that Pods are running, including their containers.
-
Container runtime
- Software responsible for running containers.
-
kube-proxy(optional)- Maintains network rules on nodes to implement Services.
what is the core component of control plane?
The core of Kubernetes’ control plane is
- the API server
- the HTTP API that it exposes, which is known as the Kubernetes API.
what does the kubernetes api do?
The Kubernetes API
- lets end users, different parts of your cluster, and external components communicate with one another.
- let you query and manipulate the state of API objects in Kubernetes (for example: Pods, Namespaces, ConfigMaps, and Events).
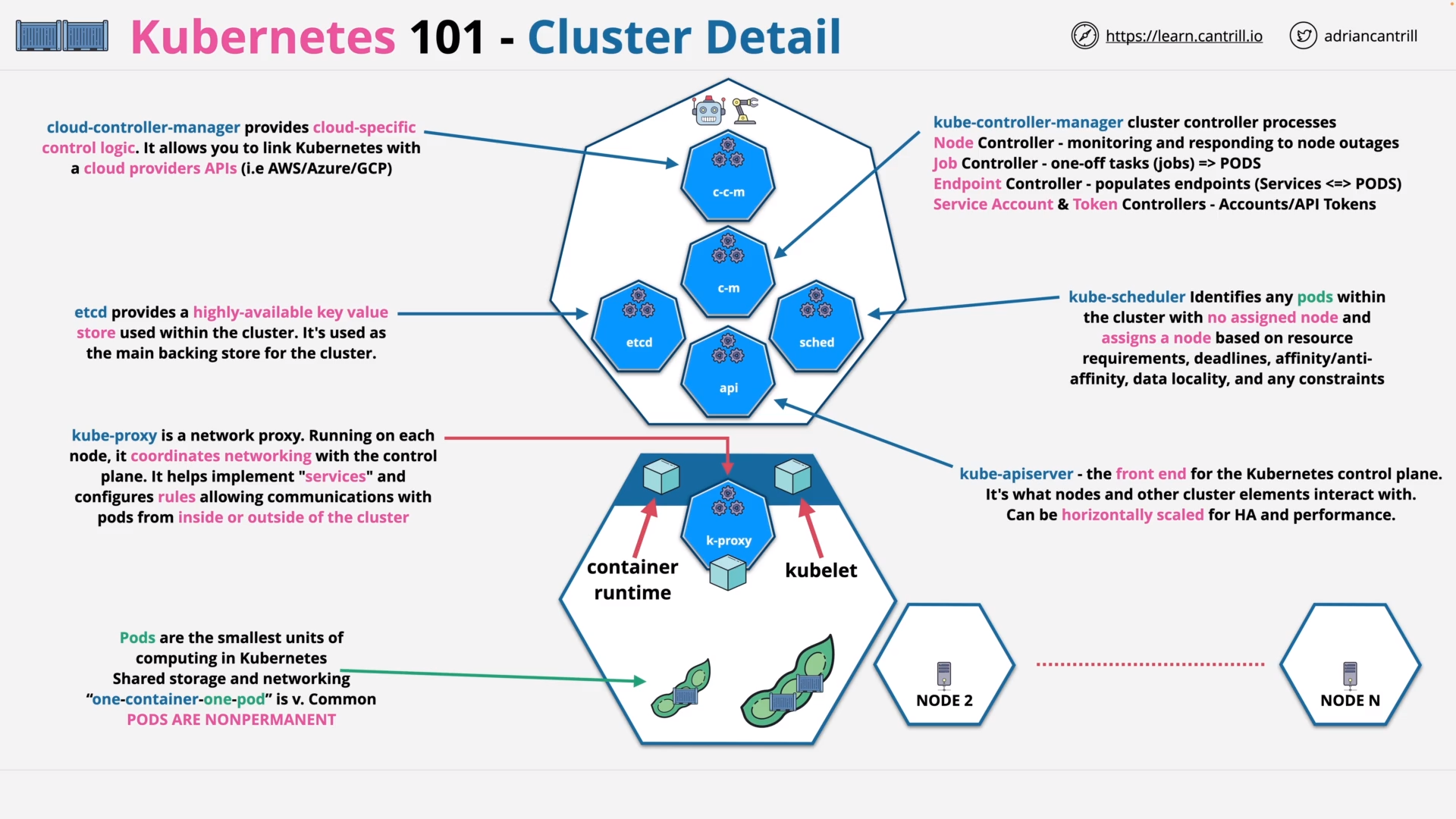 K8s - Cluster Detail
K8s - Cluster Detail
what is a `pod` in k8s?
In Kubernetes, a pod is the smallest unit of computing.
- In Docker, it’s the container.
what are the components of the control plane in k8s?
kube-apiserver: The core component server that exposes the Kubernetes HTTP APIetcd: Consistent and highly-available key value store for all API server datakube-scheduler: Looks for Pods not yet bound to a node, and assigns each Pod to a suitable node.kube-controller-manager: Core control loops of K8s: Runs controllers to implement Kubernetes API behavior.cloud-controller-manager(Optional): Integrates with underlying cloud provider(s).(AWS, Azure, GCP)
what is `kube-controller-manager`?
kube-controller-manager is the core control loops of K8s
- Watches the shared state of the cluster through the
apiserver - Makes changes attempting to move the current state towards the desired state
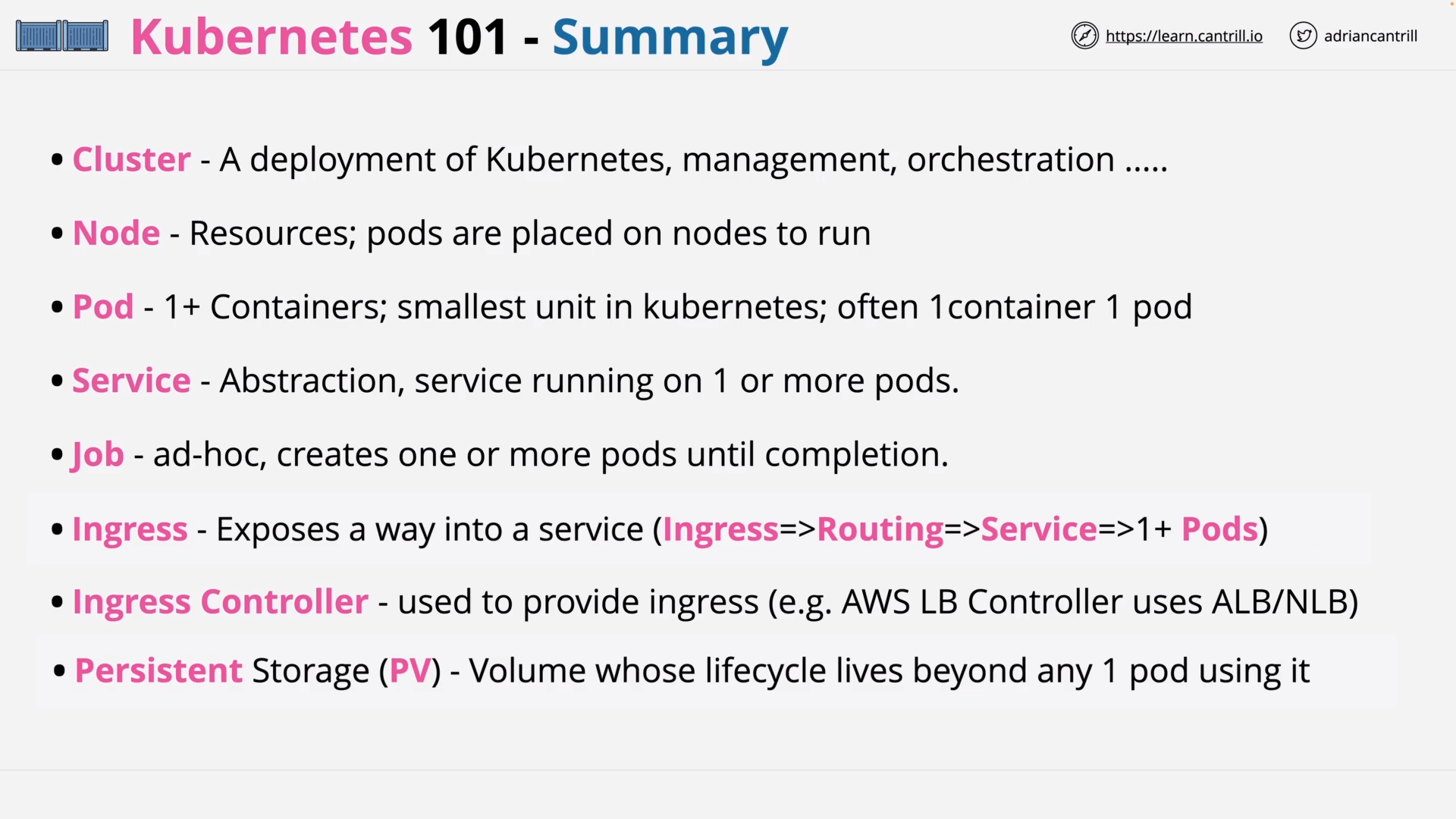 K8s - Summary
K8s - Summary
See Kubernetes Components | Kubernetes Documentation
Backups & DR (MORE COMING SOON)
Recovery Point Objective (RPO) & Recovery Time Objective (RTO) (16:54)
_&_Recovery_Time_Obj.png) Recovery Point Objective (RPO)
Recovery Point Objective (RPO)
what is rpo?
Recovery Point Objective (RPO) is the maximum (amount of) data (in time) can be lost.
_&_Recovery_Time_Obj.png) Recovery Time Objective (RTO)
Recovery Time Objective (RTO)
what is rto?
Recovery Time Objective (RTO) is the maximum of time that the system can be down.
when does rto begin and end?
RTO
- begins at at momne of failure
- ends when the system is operational (and handled back to business)
what need to be cautious about rto?
- How long until we know there is an issue?
- What is the issue?
- Do we need to restore a backup? How to restore the backup?
_&_Recovery_Time_Obj.png) RPO & RTO - Summary
RPO & RTO - Summary
Data Formats & Configuration Formats (MORE COMING SOON)
YAML aint markup language (YAML) 101 (6:12)
_101__learn.cantri.png) A YAML document is an “unordered list” of key:value pairs.
A YAML document is an “unordered list” of key:value pairs.
tip
In YAML, an “unordered list” is called a dictionary
_101__learn.cantri.png) YAML - Ordered list
YAML - Ordered list
tip
In YAML, an “ordered list” is called sequence, which can contains values of different types.
_101__learn.cantri.png) YAML - Structure
YAML - Structure
Javascript Object Notation (JSON) 101 (4:25)
_101__learn.cantr.png) JSON - Introduction
JSON - Introduction
_101__learn.cantr.png) JSON - Object & List
JSON - Object & List
_101__learn.cantr.png) JSON - Nested Object
JSON - Nested Object