Deploy a DynamoDB table
Table of Content
Add CDK code for DynamoDB table
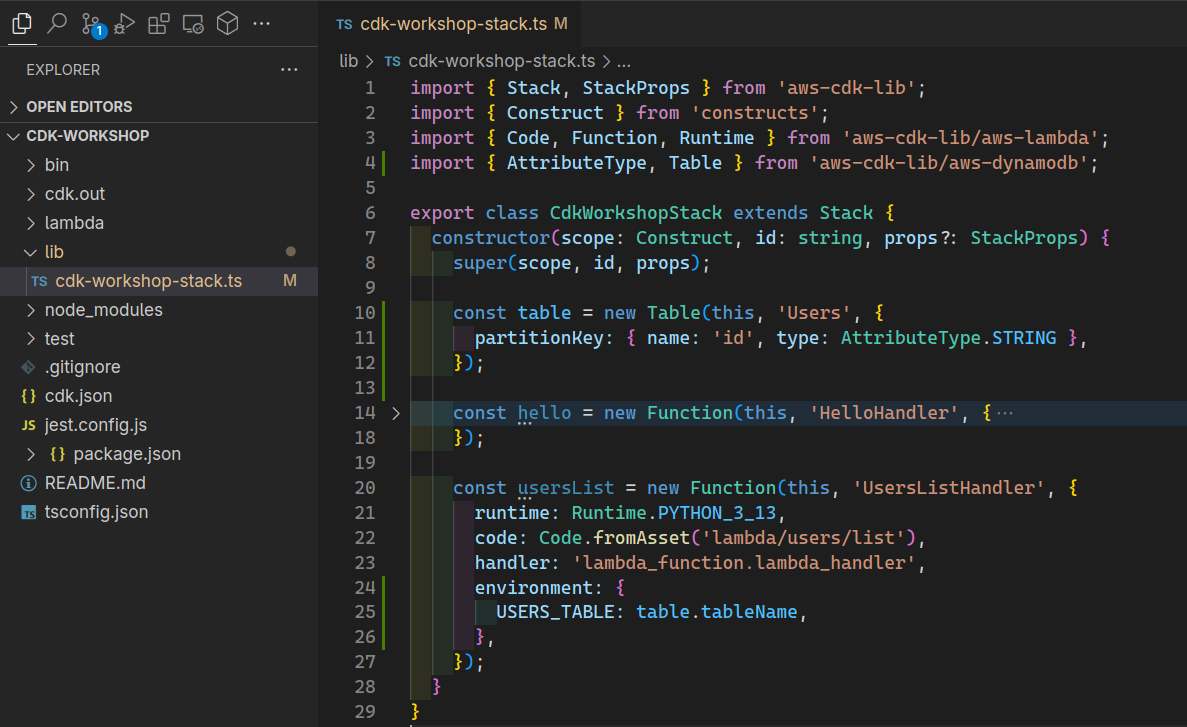
In the CDK stack file (
cdk-workshop-stack.ts), inside the constructor and belowsuper(scope, id, props);, add the following code:const table = new Table(this, "Users", { partitionKey: { name: "id", type: AttributeType.STRING }, });Don’t forget to import
TableandAttributeType:import { AttributeType, Table } from "aws-cdk-lib/aws-dynamodb";Next, pass the DynamoDB table name to
UsersListHandlervia environments:environment: { USERS_TABLE: table.tableName, },The code should looks like this:
[Optional] Run cdk diff to check the difference of your CDK stack
Run
cdk diffto compare the local stack with the deploy stack:cdk diff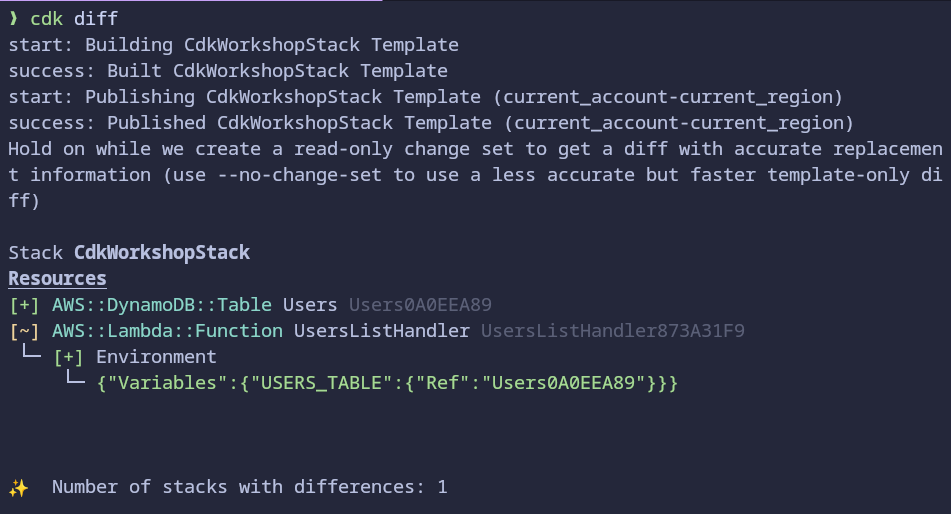
Run cdk deploy to deploy your CDK stack with the DynamoDB table
Run
cdk deployto deploy your CDK stack with the DynamoDB table:cdk deploy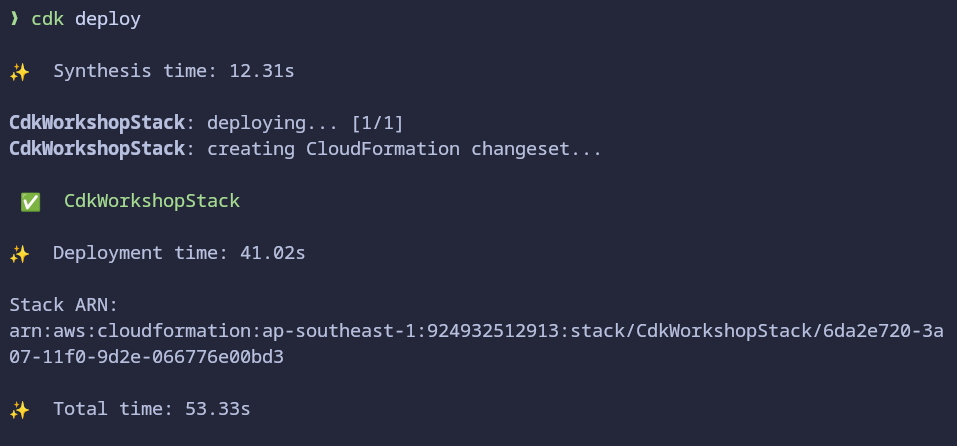
Test the
UsersListHandlerLambda function again, the function should be invoked succeeded. But now the error is a little difference.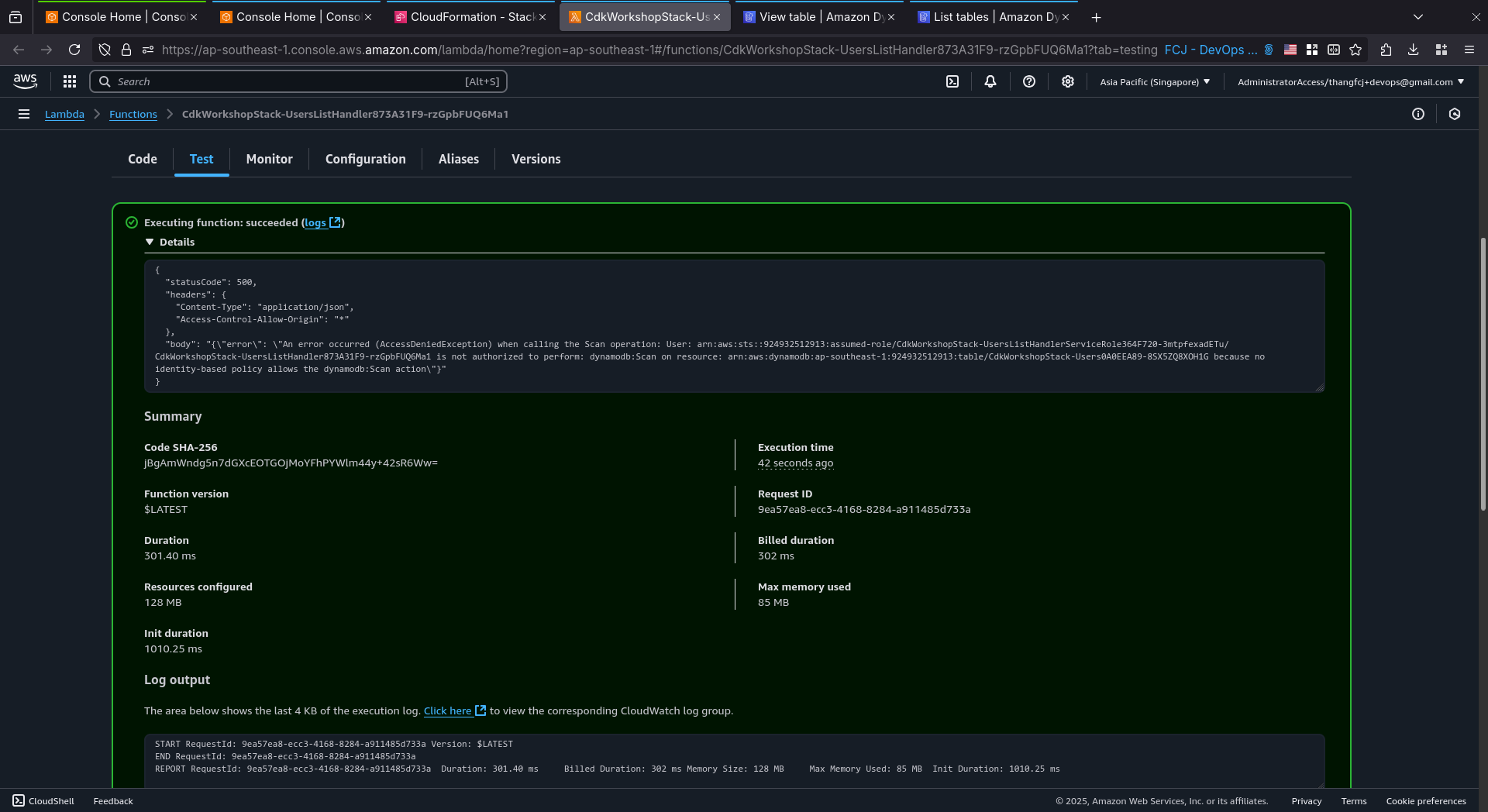
{ "statusCode": 500, "headers": { "Content-Type": "application/json", "Access-Control-Allow-Origin": "*" }, "body": "{\"error\": \"An error occurred (AccessDeniedException) when calling the Scan operation: User: arn:aws:sts::924932512913:assumed-role/CdkWorkshopStack-UsersListHandlerServiceRole364F720-3mtpfexadETu/CdkWorkshopStack-UsersListHandler873A31F9-rzGpbFUQ6Ma1 is not authorized to perform: dynamodb:Scan on resource: arn:aws:dynamodb:ap-southeast-1:924932512913:table/CdkWorkshopStack-Users0A0EEA89-8SX5ZQ8XOH1G because no identity-based policy allows the dynamodb:Scan action\"}" }It’s still an
AccessDeniedException, but the ARN of the DynamoDB table is nowarn:aws:dynamodb:ap-southeast-1:924932512913:table/CdkWorkshopStack-Users0A0EEA89-8SX5ZQ8XOH1G.
If you use IAM Console to manage the IAM role, policy to allow the Lambda function permission to interact with the DynamoDB table, there will be a lot of work.